Enable Device Information Only
Feature availability
| System | Availability |
|---|---|
| Windows | ✅ |
| macOS | ✅ |
| Linux | ✅ |
| iOS | ✅ |
| Android | ✅ |
| ChromeOS | ✅ |
Device Information Only mode allows you to enforce device posture rules when a user connects to your self-hosted Access application. This mode relies on a client certificate generated from your account to establish trust between the Access application and the device.
Using the API, enable client certificate provisioning for your zone:
Required API token permissions
At least one of the following token permissions
is required:
SSL and Certificates Write
curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/devices/policy/certificates" \ --request PATCH \ --header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \ --json '{ "enabled": true }'-
In Cloudflare One ↗, go to Team & Resources > Devices > Device profiles.
-
Under Profiles, choose a device profile and select Edit.
-
For Service mode, select Device Information Only.
-
Select Save profile.
-
Enroll your device into your Zero Trust organization.
When enrolled in Device Information Only mode, the WARP client will automatically generate a client certificate and install the certificate on the device. This certificate is necessary to confirm the source of outgoing traffic.
-
To view the client certificates installed on the device:
- Open the Start menu and select Run.
- Enter
certlm.msc. - Go to Personal > Certificates.
- Open Keychain Access.
- Go to System > My Certificates.
Open a terminal window and run the following command:
Terminal window $ certutil -L -d sql:/etc/pki/nssdbGo to Settings > General > About > Certificate Trust Settings.
The location of the client certificate may vary depending on the Android device.
- Samsung: Go to Settings > Security > Other security settings > View security certificates.
- Google Pixel: Go to Security > Advanced settings > Encryption & credentials > Credential storage.
Go to Settings > Apps > Google Play Store > Manage Android Preferences > Security > Credentials.
The client certificate name should match the Device ID in your WARP client Preferences.
-
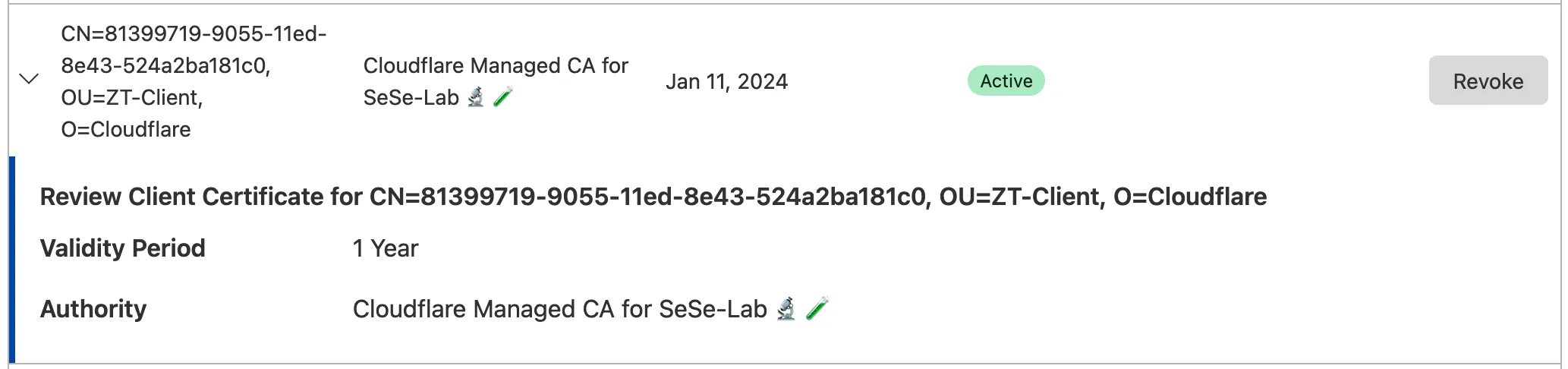
To verify the client certificate in your Cloudflare account:
- In the Cloudflare dashboard ↗, select the zone for which you enabled client certificates.
- Go to SSL/TLS > Client Certificates.
The certificate name is the WARP enrollment Device ID.
To block traffic from devices that do not have a valid client certificate:
- In the Cloudflare dashboard ↗, go to SSL/TLS > Client Certificates.
- Under Hosts, select Edit and enter the hostname of your Access application (for example,
app.mycompany.com). This enables mTLS authentication for the application. - Select Create mTLS rule.
- Create a WAF custom rule that checks all requests to your application for a valid client certificate:
Field Operator Value Logic Action Client Certificate equals Off And Block Hostname equals app.mycompany.com - Select Deploy.
Device Information Only mode is now enabled on the device. To start enforcing device posture, set up a WARP client check and add a Require device posture rule to your Access policy. When the device connects to the Access application for the first time, the browser will ask to use the client certificate installed by WARP.
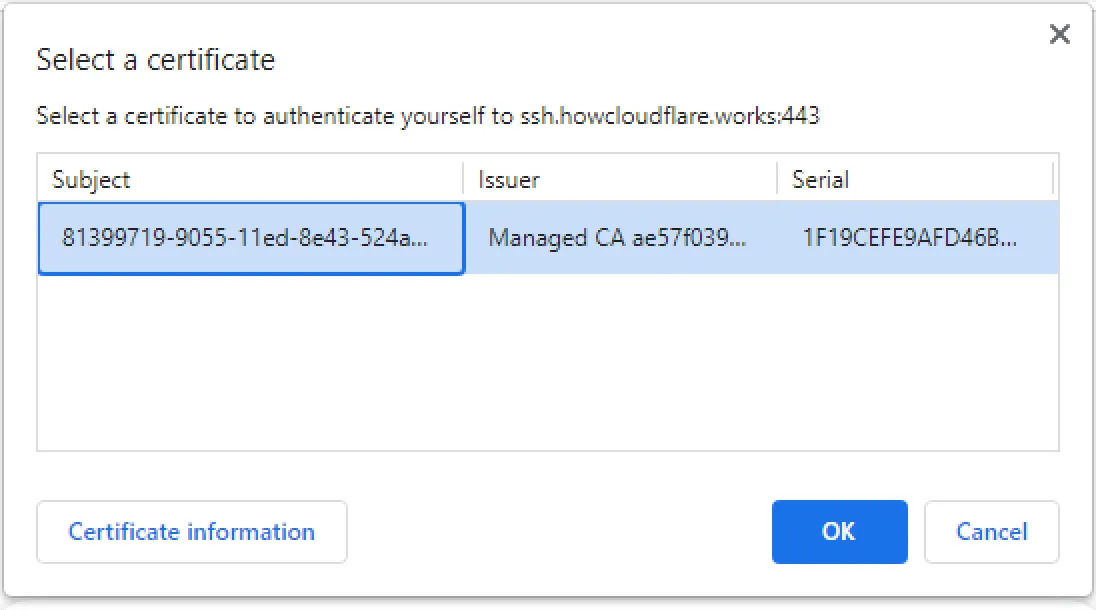
Device Information mode is not compatible with the Windows pre-login feature. The user must be logged into Windows because WARP needs to install a certificate in the user store.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Directory
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- © 2026 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark
-