Intune
This guide covers how to deploy the Cloudflare WARP client using Microsoft Intune.
To deploy WARP on Windows using Intune:
- Download the
Cloudflare_WARP_<VERSION>.msiinstaller. - Log in to your Microsoft Intune account.
- Go to Apps > All Apps > Add.
- In App type, select Line-of-business app from the drop-down menu. Select Select.
- Select Select app package file and upload the
Cloudflare_WARP_<VERSION>.msiinstaller you downloaded previously. - Select OK.
- For Run this script using the logged on credentials, choose No.
- For Enforce script signature check, choose No.
- In the Name field, we recommend entering the version number of the package being uploaded.
- In the Publisher field, we recommend entering
Cloudflare, Inc. - In the Command-line arguments field, enter a valid installation command. For example:
/qn ORGANIZATION="your-team-name" SUPPORT_URL="http://support.example.com"Refer to deployment parameters for a description of each argument. You can change these parameters at any time by pushing a new MDM file. 12. Select Next. 13. Add the users or groups who require Cloudflare WARP and select Next. 14. Review your configuration and select Create.
Intune is now configured to deploy the WARP client.
You can use Intune to update MDM parameters for the WARP client. On Windows, these parameters are stored on the local device in C:\ProgramData\Cloudflare\mdm.xml.
To push a new mdm.xml file using Intune:
-
Log in to your Microsoft Intune account.
-
Go to Devices > Scripts and remediations.
-
Select the Platform scripts tab and select Add.
-
Select Windows 10 and later.
-
Enter a name for the script (for example,
Deploy Cloudflare mdm.xml). -
In PowerShell script, upload the following
.ps1file. Be sure to modify the XML content with your desired parameters.mdm-template.ps1 # Define the path to the file$filePath = "C:\ProgramData\Cloudflare\mdm.xml"# Create the XML content as a string$xmlContent = @"<dict><key>multi_user</key><true/><key>pre_login</key><dict><key>organization</key><string>mycompany</string><key>auth_client_id</key><string>88bf3b6d86161464f6509f7219099e57.access</string><key>auth_client_secret</key><string>bdd31cbc4dec990953e39163fbbb194c93313ca9f0a6e420346af9d326b1d2a5</string></dict><key>configs</key><array><dict><key>organization</key><string>mycompany</string><key>display_name</key><string>Production environment</string></dict><dict><key>organization</key><string>test-org</string><key>display_name</key><string>Test environment</string></dict></array></dict>"@# Ensure the directory exists$directory = Split-Path $filePath -parentif (-not (Test-Path $directory)) {New-Item -ItemType Directory -Path $directory | Out-Null}# Write the XML content to the filetry {$xmlContent | Out-File -Encoding UTF8 -FilePath $filePathWrite-Host "mdm.xml file created successfully at: $filePath"}catch {Write-Error "Failed to create mdm.xml file: $_"} -
In Assignments, select the Windows devices that should receive the new
mdm.xmlfile. -
To deploy the script, select Add.
Intune will now execute the Powershell script on the target devices and overwrite the previous mdm.xml file. Once the new mdm.xml file is created, WARP will immediately start using the new configuration.
After deploying the WARP client, you can check its connection progress using the Connectivity status messages displayed in the WARP GUI.
If you prefer to use Intune's Win32 App tool to run the Powershell script, refer to the Intune documentation ↗.
The following steps outline deploying WARP on macOS using Intune.
- A Microsoft Intune account ↗.
- A Cloudflare account that has a Zero Trust organization.
- macOS devices enrolled in Intune.
- Upload user-side certificate.
- Allow system extensions (bundle ID and team identifier policy).
- Upload MobileConfig (custom configuration policy).
- Upload and assign the WARP
.pkg(application policy).
You must deploy a user-side certificate so that macOS devices managed by Intune can establish trust with Cloudflare when their traffic is inspected.
-
(Optional) Generate a Cloudflare root certificate.
-
In Cloudflare One ↗, find and download a root certificate in
.crtformat.
-
In the Microsoft Intune admin center ↗, go to Devices > select macOS.
-
Under Manage devices, select Configuration.

-
Select Create > New Policy.
-
For Profile Type, select Templates > select Trusted certificate as the Template name > select Create.
-
In Basics, input the necessary field(s) and give your policy a name like
Cloudflare certificate> select Next. -
For Deployment Channel, select Device Channel.
-
Upload your file (Intune may request
.cerformat, though.crtfiles are also accepted) > select Next. -
In Assignments, select an option (for example, Add all devices or Add all users) that is valid for your scope. This will be the same scope for all steps. Select Next.
-
Review your configuration in Review + create and select Create.
Sharing this certificate with Intune automates the installation of this certificate on your user devices, creating trust between browsers on a user's device and Cloudflare.
Before deploying WARP, you need to allow its system extensions.
-
In the Microsoft Intune admin center ↗, go to Devices > macOS.
-
Under Manage devices, select Configuration.
-
Select Create > New Policy.
-
For Profile type, select Settings catalog > select Create.
-
In Basics, input the necessary field(s) and give your policy a name like
WARP System Extensions> select Next. -
In Configuration settings, select Add settings.
-
In the Settings picker, search for System Extensions under System Configuration.
-
Enable Allowed System Extensions.
-
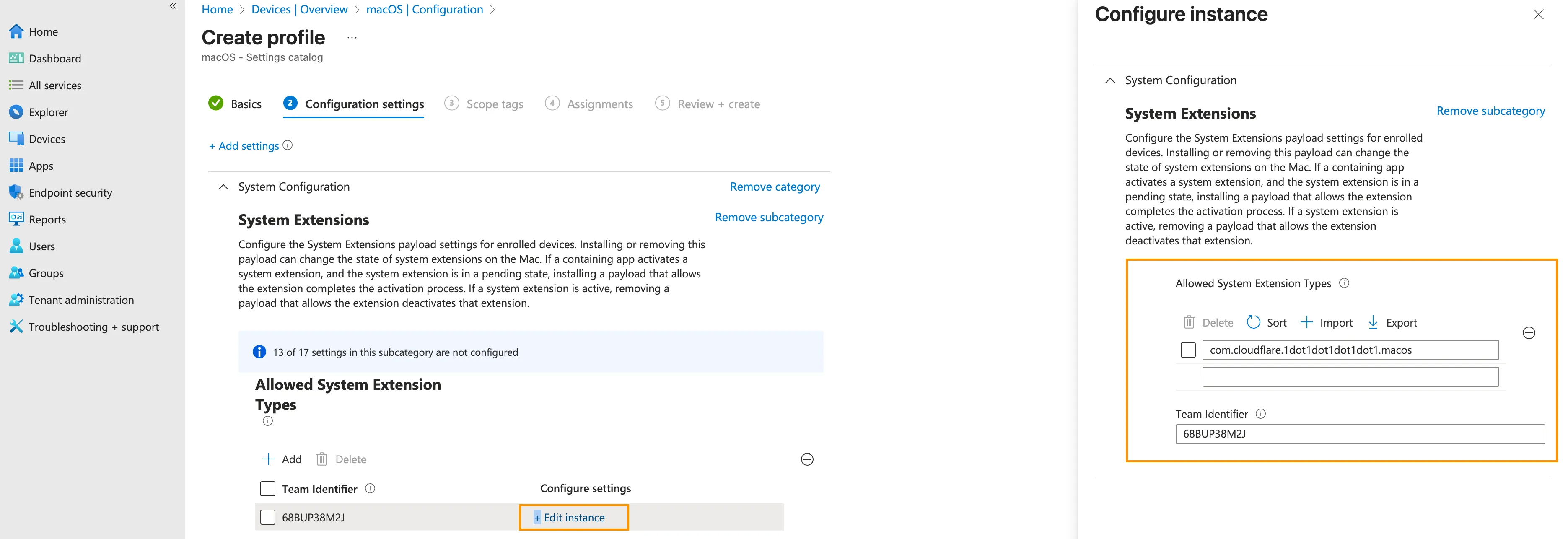
Select Edit instance and add:
- Bundle Identifier:
com.cloudflare.1dot1dot1dot1dot1.macos - Team Identifier:
68BUP38M2J
- Bundle Identifier:
-
Select Save.
-
In Scope tags, select Next.
-
In Assignments, select an option (for example, Add all devices or Add all users) that is valid for your scope. This will be the same scope for all steps. Select Next.
-
Review your configuration and select Create.
This step allows WARP to install without user interaction. By completing this step, you allow WARP to install and manage its required system extensions without end-user prompts.
-
Open a text editor and paste in the following
.mobileconfigtemplate:<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"><plist version="1.0"><dict><key>PayloadDisplayName</key><string>Cloudflare WARP</string><key>PayloadIdentifier</key><string>cloudflare_warp</string><key>PayloadOrganization</key><string>Cloudflare, Ltd.</string><key>PayloadRemovalDisallowed</key><false/><key>PayloadType</key><string>Configuration</string><key>PayloadScope</key><string>System</string><key>PayloadUUID</key><string>YOUR_PAYLOAD_UUID_HERE</string><key>PayloadVersion</key><integer>1</integer><key>PayloadContent</key><array><dict><key>organization</key><string>YOUR_TEAM_NAME_HERE</string><key>auto_connect</key><integer>120</integer><key>onboarding</key><false/><key>PayloadDisplayName</key><string>Warp Configuration</string><key>PayloadIdentifier</key><string>com.cloudflare.warp.YOUR_PAYLOAD_UUID_HERE</string><key>PayloadOrganization</key><string>Cloudflare Ltd.</string><key>PayloadType</key><string>com.cloudflare.warp</string><key>PayloadUUID</key><string>YOUR_PAYLOAD_UUID_HERE</string><key>PayloadVersion</key><integer>1</integer></dict></array></dict></plist> -
Open your macOS Terminal and run
uuidgen. This will generate a value forPayloadUUID. Use this value to replace the default value (YOUR_PAYLOAD_UUID_HERE) used in the template (three locations total). -
Update your organization's string (
YOUR_TEAM_NAME_HERE) with your team name. -
Modify the file with your desired deployment parameters.
<array><dict><key>organization</key><string>YOUR_TEAM_NAME_HERE</string>// add desired deployment parameters here -
In the Microsoft Intune admin center ↗, go to Devices > macOS.
-
Under Manage devices, select Configuration.
-
Select Create > New Policy.
-
For Profile Type, select Templates > select Custom as the Template name > select Create.
-
In Basics, input the necessary field(s) > select Next.
-
In Custom configuration profile name, input a name.
-
For Deployment Channel, select Device Channel.
-
Under Configuration profile file, upload the
.mobileconfigfile that you created in your text editor in step 1 > select Next. -
In Assignments, select an option (for example, Add all devices or Add all users) that is valid for your scope. This will be the same scope for all steps.
-
Review your configuration and create your policy.
By completing this step, you preconfigure WARP with your team settings so it connects automatically upon installation.
-
In Cloudflare One ↗, download the WARP client in
.pkgformat. -
Log in to the Microsoft Intune admin center ↗, and go to Apps > macOS.
-
Select Create.
-
For App type, select macOS app (PKG).
-
In App information, select the
.pkgfile you downloaded and input required details. EnterCloudflareas the Publisher. -
In Requirements, refer to the OS versions listed in stable releases for macOS and find what matches for you.
-
In Detection rules, note that the WARP package will have filled in the App bundle ID and App version.
-
In Assignments, select an option (for example, Add all devices or Add all users) that is valid for your scope. Select Next.
-
Review your configuration in Review + create and select Create.
By completing this step, you deliver the WARP client to targeted macOS devices, either automatically (assignment scope set as Required) or on-demand (assignment scope as Available) through your company portal.
The following steps outline how to deploy the Cloudflare One Agent (WARP client) on iOS using Microsoft Intune and preconfigure it with MDM parameters.
- A Microsoft Intune account ↗
- A Cloudflare account that has a Zero Trust organization
- iOS/iPadOS devices enrolled in Intune
- TLS decryption enabled in Cloudflare Gateway (if you plan to inspect HTTPS traffic)
You must deploy a user-side certificate so that iOS devices managed by Intune can establish trust with Cloudflare when their traffic is inspected.
-
(Optional) Generate a Cloudflare root certificate.
-
In Cloudflare One ↗, find and download a root certificate in
.crtformat.
-
In the Microsoft Intune admin center ↗, go to Devices > select iOS/iPadOS.

-
Under Manage devices, select Configuration.

-
Select Create > New Policy.
-
For Profile Type, select Templates > select Trusted certificate as the Template name > select Create.
-
In Basics, input the necessary field(s) and give your policy a name like
Cloudflare certificate> select Next. -
For Deployment Channel, select Device Channel.
-
Upload your file (Intune may request
.cerformat, though.crtfiles are also accepted) > select Next. -
In Assignments, select an option (for example, Add all devices or Add all users) that is valid for your scope. This will be the same scope for all steps. Select Next.
-
Review your configuration in Review + create and select Create.
Sharing this certificate with Intune automates the installation of this certificate on your user devices, creating trust between browsers on a user's device and Cloudflare.
-
In the Microsoft Intune admin center ↗, select Apps > iOS/iPadOS.
-
Select Create.
-
For App type, select iOS store app > select Select to continue.
-
Select Search the App Store and search for the Cloudflare One Agent. After you have found the Cloudflare One Agent, select it and select Select to continue.
-
The fields in App information will be filled in automatically. Select Next to continue.
-
In Assignments, select an option (for example, Add all devices or Add all users) that is valid for your scope. Select Next.
-
Review your configuration in Review + create and select Create.
By completing this step, you deliver the WARP client to targeted iOS devices, either automatically (assignment scope set as Required) or on-demand (assignment scope as Available) through your company portal.
-
In the Microsoft Intune admin center ↗, select Apps > Manage apps > Configuration.
-
Select Create > Managed devices.
-
In Basics, input the necessary field(s) and give your policy an easily identifiable name like
Cloudflare One Agent. Select iOS/iPadOS for Platform and target the Cloudflare One Agent app. Select Next. -
In Settings, select Enter XML data and copy and paste the following:
<dict><key>organization</key><string>YOUR_TEAM_NAME_HERE</string><key>auto_connect</key><integer>1</integer></dict>Replace
YOUR_TEAM_NAME_HEREwith your team name. Review the definitions of the above parameters in the Parameters documentation. -
In Assignments, select an option (for example, Add all devices or Add all users) that is valid for your scope. Select Next.
-
Review your configuration in Review + create and select Create.
By completing this step, you preconfigure the Cloudflare One Agent with your Zero Trust organization and connection settings so that enrolled iOS devices automatically apply a consistent WARP configuration when the app installs.
Intune allows you to insert predefined variables ↗ into the XML configuration file. For example, you can set the unique_client_id key to {{deviceid}} for a device UUID posture check deployment.
Before proceeding with per-app VPN configuration, you must make sure Auto connect is disabled in Zero Trust. To disable Auto connect:
- In Cloudflare One ↗, go to Team & Resources > Devices > Device profiles.
- Under Profiles, select your device profile and select Edit.
- Turn off Auto Connect.
To configure per-app VPN:
- Log in to Microsoft Intune admin center for your organization.
- Go to Devices > iOS/iPadOS Devices > Manage Devices > Configuration > select + Create > New Policy.
- Select Templates in the Profile Type dropdown menu, then select VPN as the Template Name and select Create.
- Give the configuration a name, and an optional description, if you desire, then select Next.
- Select Custom VPN from the Connection Type dropdown menu.
- Expand the Base VPN section.
- Give the VPN connection a name.
- Enter "1.1.1.1" as the VPN server address (this value is not actually used.)
- Set Username and password as the Authentication method.
- Enter "com.cloudflare.cloudflareoneagent" as the VPN identifier.
- Enter any Key and Value into the custom VPN attributes (Cloudflare One does not use these but Intunes requires at least one entry.)
- Expand the Automatic VPN section.
- Select Per-app VPN as the Type of automatic VPN.
- Select packet-tunnel as the Provider Type. Select Next.
- Add any Groups, Users, or Devices to which you want to distribute this configuration and select Next.
- Review the settings and select Create.
- Go to Apps > iOS/iPadOS Apps and select + Add.
- Select iOS store app from the App Type dropdown > Select.
- Select Search the App Store, then search for the app whose traffic you want to go through the VPN > select the desired app > Select.
- Review the selected app settings and select Next.
- Select + Add Group to add the group of users to which to distribute this app. Then select None underneath VPN.
- Select the configuration you just created from the VPN dropdown menu and select OK.
- Select Next, review the settings, then select Create.
- Repeat steps 10-16 for each app you want to use the VPN with.
To deploy WARP on Android devices:
-
Log in to your Microsoft Intune account.
-
Go to Apps > Android >Add.
-
In App type, select Managed Google Play app.
-
Add the Cloudflare One Agent app from the Google Play store. Its application ID is
com.cloudflare.cloudflareoneagent. -
Go to Apps > App Configuration policies > Add.
-
Select Managed devices.
-
In Name, enter
Cloudflare One Agent. -
For Platform, select Android Enterprise.
-
Choose your desired Profile Type.
-
For Targeted app, select Cloudflare One Agent. Select Next.
-
For Configuration settings format, select Enter JSON data. Enter your desired deployment parameters in the
managedPropertyfield. For example:{"kind": "androidenterprise#managedConfiguration","productId": "app:com.cloudflare.cloudflareoneagent","managedProperty": [{"key": "app_config_bundle_list","valueBundleArray": [{"managedProperty": [{"key": "organization","valueString": "your-team-name"},{"key": "display_name","valueString": "Production environment"},{"key": "service_mode","valueString": "warp"},{"key": "onboarding","valueBool": false},{"key": "support_url","valueString": "https://support.example.com/"}]},{"managedProperty": [{"key": "organization","valueString": "test-org"},{"key": "display_name","valueString": "Test environment"}]}]}]}Alternatively, if you do not want to copy and paste the JSON data, you can change Configuration settings format to Use configuration designer and manually configure each deployment parameter.
Once you have configured the deployment parameters, select Next.
-
Assign users or groups to this policy and select Next.
-
Save the app configuration policy.
-
Assign users or groups to the application:
- Go to Apps > Android > Cloudflare One Agent > Manage Properties.
- Select Edit and add users or groups.
- Select Review + save > Save.
Intune will now deploy the Cloudflare One Agent to user devices.
Review the following steps to approve and deploy the Cloudflare One Agent application in Microsoft Intune and use a configuration policy to set up the per-app VPN. To use the per-app VPN, the admin must have linked the Microsoft Intune account with the Google-managed Play account. For more information, refer to Connect your Intune account to your managed Google Play account in the Microsoft documentation ↗.
- Log into the Microsoft Intune admin center.
- Go to Apps > All apps > select Add.
- In App type, select Managed Google Play.
- Search for Cloudflare One Agent > select the app > select Sync.
- Once the sync is successful, admin will see the Cloudflare One Agent app within the All apps view in the Microsoft Intune admin center.
To configure your Cloudflare One Agent app policy:
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > select Add > Managed Devices.
-
Fill out the basic details of your configuration policy:
- Enter the Name of the profile. (For example: Cloudflare One Agent - configuration policy)
- Select the Platform as Android Enterprise.
- Select the desired Profile Type. (For example: Personally-Owned Work Profile Only)
- Select Cloudflare One Agent as the Targeted app.
- Select Next.
-
Fill out the settings for the configuration policy.
-
Select Configuration setting format as Enter JSON data.
-
Enter your desired deployment parameters in the
managedPropertyfield. For example:Terminal window {"kind": "androidenterprise#managedConfiguration","productId": "app:com.cloudflare.cloudflareoneagent","managedProperty": [{"key": "app_config_bundle_list","valueBundleArray": [{"managedProperty": [{"key": "organization","valueString": "${ORGANIZATION_NAME-1}"},{"key": "service_mode","valueString": "warp"},{"key": "onboarding","valueBool": true},{"key": "display_name","valueString": "${UNIQUE_DISPLAY_NAME-1}"},{"key": "warp_tunnel_protocol","valueString": "MASQUE"},{"key": "tunneled_apps","valueBundleArray" :[{"managedProperty": [{"key": "app_identifier","valueString": "com.android.chrome" # Application package name/unique bundle identifier for the Chrome app browser},{"key": "is_browser","valueBool": true}]},{"managedProperty": [{"key": "app_identifier","valueString": "com.google.android.gm" # Application package name/unique bundle identifier for the Gmail app},{"key": "is_browser","valueBool": false # Default value is false, if a user does not define `is_browser` property our app would not treat `app_identifier` package name as a browser.}]}]}]},{"managedProperty": [{"key": "organization","valueString": "${ORGANIZATION_NAME-1}"},{"key": "service_mode","valueString": "warp"},{"key": "display_name","valueString": "${UNIQUE_DISPLAY_NAME-2}"},{"key": "warp_tunnel_protocol","valueString": "wireguard"}]}]}]}Refer to Per-app VPN parameters to learn more about the MDM parameters introduced to support the per-app VPN for Android devices.
-
After you have configured the deployment parameters, click Next.
-
-
Fill out the assignments for the configuration policy. The admin can
IncludeorExcludespecific groups of users to this policy. After you finish, select Next. -
Review the policy and select Create.
- Go to Apps > All Apps > select Cloudflare One Agent.
- Under Manage, select Properties and near Assignments, select Edit.
- Add the groups of users in the assignments > select Review + Save > select Save.
Intune will now deploy the Cloudflare One Agent application on a user's device with the managed parameters.
After deploying the WARP client, you can check its connection progress using the Connectivity status messages displayed in the WARP GUI.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Directory
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- © 2026 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark
-