Error 526
This error indicates that Cloudflare is unable to verify the SSL certificate on your origin server, preventing a secure connection from being established.
This error occurs when these two conditions are true:
- Cloudflare cannot validate the SSL certificate at your origin web server.
- Full SSL (Strict) SSL is set in the Overview tab of your Cloudflare SSL/TLS app.
Here are some options to fix or workaround this issue:
-
For a potential quick fix, set SSL to Full instead of Full (strict) in the Overview tab of your Cloudflare SSL/TLS app for the domain.
-
Add your self-signed SSL certificate to the Custom Origin Trust Store. This allows the Cloudflare edge to recognize your self-signed SSL certificate as valid.
-
Request your server administrator or hosting provider to review the origin web server's SSL certificates and verify that:
- Certificate is not expired.
- Certificate is not revoked.
- Certificate is signed by a Certificate Authority ↗ (not self-signed).
- The requested or target domain name and hostname are in the certificate's Common Name or Subject Alternative Name.
- Your origin web server accepts connections over port SSL port
443. - Temporarily pause Cloudflare and visit https://www.sslshopper.com/ssl-checker.html#hostname=www.example.com ↗ (replace
www.example.comwith your hostname and domain) to verify no issues exists with the origin SSL certificate:
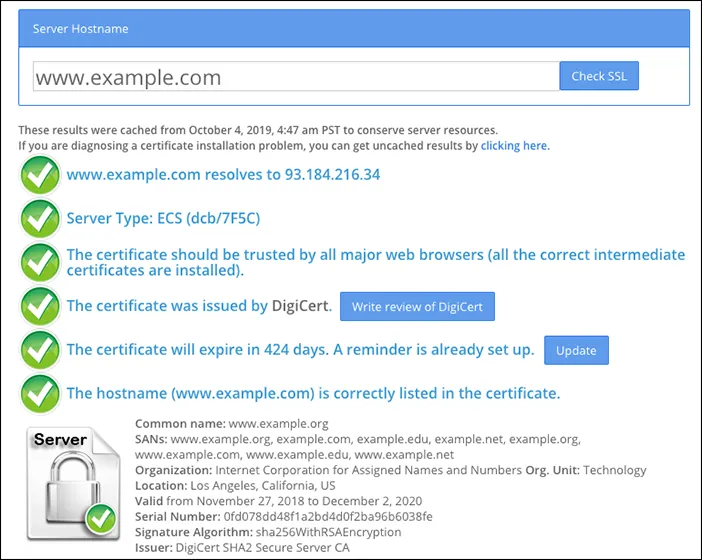
When using Cloudflare Gateway, an HTTP Error 526 might be returned in the following cases:
-
An untrusted certificate is presented from the origin to Gateway. Gateway will consider a certificate is untrusted if any of these conditions are true:
- The server certificate issuer is unknown or is not trusted by the service.
- The server certificate is revoked and fails a CRL check.
- There is at least one expired certificate in the certificate chain for the server certificate.
- The common name on the certificate does not match the URL you are trying to reach.
- The common name on the certificate contains invalid characters (such as underscores). Gateway uses BoringSSL ↗ to validate certificates. Chrome's validation logic ↗ allows non-RFC 1305 compliant certificates, which is why the website may load when you turn off WARP.
-
The connection from Gateway to the origin is insecure. Gateway does not trust origins which:
- Only offer insecure cipher suites (such as RC4, RC4-MD5, or 3DES). You can use the SSL Server Test tool ↗ to check which ciphers are supported by the origin.
- Do not support FIPS-compliant ciphers (if you have enabled FIPS compliance mode). In order to load the page, you can either disable FIPS mode or create a Do Not Inspect policy for this host (which has the effect of disabling FIPS compliance for this origin).
- Redirect all HTTPS requests to HTTP.
Workers subrequests to any hostname outside your Cloudflare zone that is not proxied by Cloudflare are always made using the Full (strict) SSL mode, regardless of the Workers zone configuration.
-
Make sure the SSL certificate configured at the origin is valid.
-
Add your self-signed SSL certificate to the Custom Origin Trust Store and enable the
cots_on_external_fetchcompatibility flag in your Worker's configuration. This flag enables the use of the Custom Origin Trust Store when making external (grey-clouded) subrequests from a Cloudflare Worker.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark
-