Changelog
DNS Firewall Analytics — now in the Cloudflare dashboard
Access GraphQL-powered DNS Firewall analytics directly in the Cloudflare dashboard.
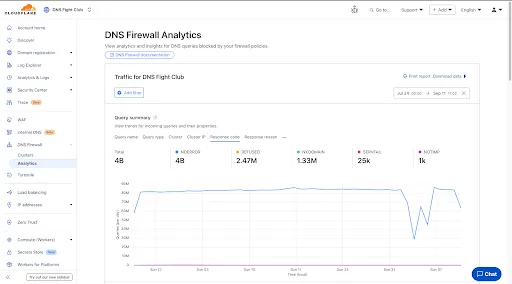
- Query summary: Describes trends over time, segmented by dimensions.
- Query statistics: Describes totals, cached/uncached queries, and processing/response times.
- DNS queries by data center: Describes global view and the top 10 data centers.
- Top query statistics: Shows a breakdown by key dimensions, with search and expand options (up to top 100 items).
Additional features:
- Apply filters and time ranges once. Changes reflect across all panels.
- Filter by dimensions like query name, query type, cluster, data center, protocol (UDP/TCP), IP version, response code/reason, and more.
- Access up to 62 days of historical data with flexible intervals.
Available to all DNS Firewall customers as part of their existing subscription.
-
In the Cloudflare dashboard, go to the DNS Firewall page.
Go to Analytics -
Refer to the DNS Firewall Analytics to learn more.
Account-level DNS analytics now available via GraphQL Analytics API
Authoritative DNS analytics are now available on the account level via the Cloudflare GraphQL Analytics API.
This allows users to query DNS analytics across multiple zones in their account, by using the accounts filter.
Here is an example to retrieve the most recent DNS queries across all zones in your account that resulted in an NXDOMAIN response over a given time frame. Please replace a30f822fcd7c401984bf85d8f2a5111c with your actual account ID.
query GetLatestNXDOMAINResponses { viewer { accounts(filter: { accountTag: "a30f822fcd7c401984bf85d8f2a5111c" }) { dnsAnalyticsAdaptive( filter: { date_geq: "2025-06-16" date_leq: "2025-06-18" responseCode: "NXDOMAIN" } limit: 10000 orderBy: [datetime_DESC] ) { zoneTag queryName responseCode queryType datetime } } }}To learn more and get started, refer to the DNS Analytics documentation.
Internal DNS (beta) now manageable in the Cloudflare dashboard
Participating beta testers can now fully configure Internal DNS directly in the Cloudflare dashboard ↗.
-
Map internal hostnames to private IPs for services, devices, and applications not exposed to the public Internet
-
Resolve internal DNS queries securely through Cloudflare Gateway
-
Use split-horizon DNS to return different responses based on network context
-
Consolidate internal and public DNS zones within a single management platform
- Beta participants can now create and manage internal zones and views in the Cloudflare dashboard
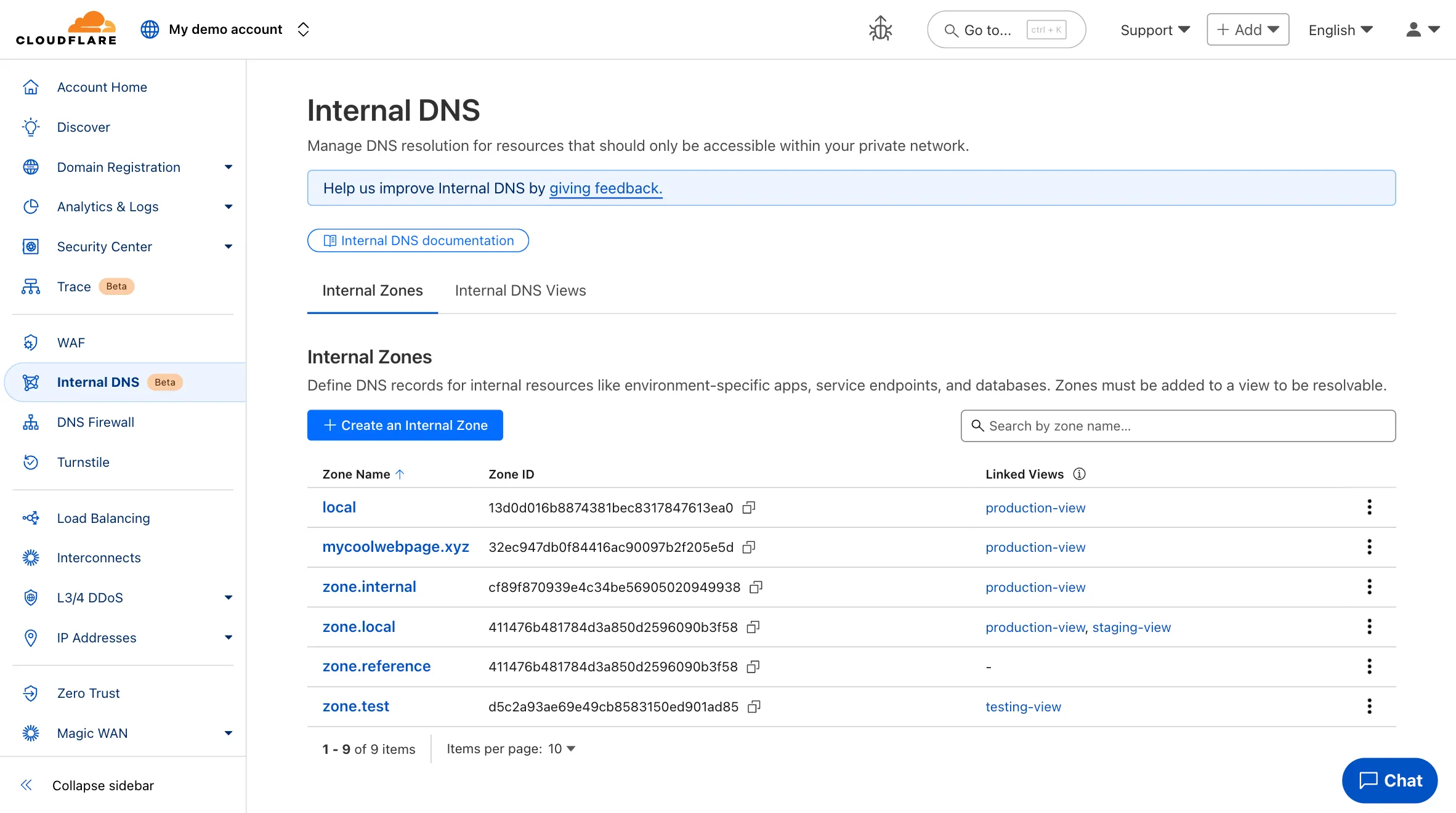
To learn more and get started, refer to the Internal DNS documentation.
NSEC3 support for DNSSEC
Enterprise customers can now select NSEC3 as method for proof of non-existence on their zones.
What's new:
-
NSEC3 support for live-signed zones – For both primary and secondary zones that are configured to be live-signed (also known as "on-the-fly signing"), NSEC3 can now be selected as proof of non-existence.
-
NSEC3 support for pre-signed zones – Secondary zones that are transferred to Cloudflare in a pre-signed setup now also support NSEC3 as proof of non-existence.
For more information and how to enable NSEC3, refer to the NSEC3 documentation.
Improved onboarding for Shopify merchants
Shopify merchants can now onboard to Orange-to-Orange (O2O) automatically, without needing to contact support or community members.
What's new:
-
Automatic enablement – O2O is available for all mutual Cloudflare and Shopify customers.
-
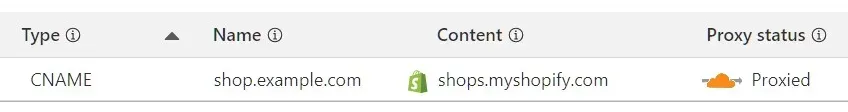
Branded record display – Merchants see a Shopify logo in DNS records, complete with helpful tooltips.
-
Checkout protection – Workers and Snippets are blocked from running on the checkout path to reduce risk and improve security.
For more information, refer to the provider guide.
Removed unused meta fields from DNS records
Cloudflare is removing five fields from the meta object of DNS records. These fields have been unused for more than a year and are no longer set on new records. This change may take up to four weeks to fully roll out.
The affected fields are:
- the
auto_addedboolean - the
managed_by_appsboolean and correspondingapps_install_id - the
managed_by_argo_tunnelboolean and correspondingargo_tunnel_id
An example record returned from the API would now look like the following:
{ "result": { "id": "<ID>", "zone_id": "<ZONE_ID>", "zone_name": "example.com", "name": "www.example.com", "type": "A", "content": "192.0.2.1", "proxiable": true, "proxied": false, "ttl": 1, "locked": false, "meta": { "auto_added": false, "managed_by_apps": false, "managed_by_argo_tunnel": false, "source": "primary" }, "comment": null, "tags": [], "created_on": "2025-03-17T20:37:05.368097Z", "modified_on": "2025-03-17T20:37:05.368097Z" }, "success": true, "errors": [], "messages": []}For more guidance, refer to Manage DNS records.
Zone IDs and names on individual DNS records
Records returned by the API will no longer contain the zone_id and zone_name fields. This change may take up to four weeks to fully roll out. The affected fields were deprecated with an End of Life (EOL) date of November 30, 2024.
Quote validation for TXT records added via dashboard
When creating TXT records via the dashboard you will now find:
- Field validation errors if double quotes
"are added inconsistently. - Automatically quoted TXT content upon save if no quotes exist in the record content field.
API support for per-record CNAME flattening
Paid zones now have the option to flatten specific CNAME records. When using the API, specify the setting cname_flatten as true or false. Refer to the documentation for details.