Cloudflare Managed Ruleset
Created by the Cloudflare security team, this ruleset provides fast and effective protection for all of your applications. The ruleset is updated frequently to cover new vulnerabilities and reduce false positives.
Cloudflare recommends that you enable the rules whose tags correspond to your technology stack. For example, if you use WordPress, enable the rules tagged with wordpress.
Cloudflare's WAF changelog allows you to monitor ongoing changes to the WAF's managed rulesets.
-
In the Cloudflare dashboard, go to the Security Settings page.
Go to Settings -
(Optional) Filter by Web application exploits.
-
Turn on Cloudflare managed ruleset.
-
Review the deployment settings. Edit the scope, if necessary, to apply the ruleset to a subset of the incoming requests, or configure any custom settings (also known as overrides).
-
Select Save.
-
Log in to the Cloudflare dashboard ↗, and select your account and domain.
-
Go to Security > WAF > Managed rules tab.
-
Under Managed Rulesets, select Deploy next to Cloudflare Managed Ruleset.
This operation deploys the managed ruleset for the current zone, creating a new rule with the Execute action.
You can configure (or override) the Cloudflare Managed Ruleset, overriding its default configuration, at several levels:
When you create several overrides at different levels, more specific configurations (tag and rule level) have priority over less specific configurations (ruleset level). Refer to Override a managed ruleset in the Ruleset Engine documentation for more information.
You can configure (or override) the following Cloudflare Managed Ruleset settings in the Cloudflare dashboard:
-
Scope: When you define a custom filter expression for the scope, the Cloudflare Managed Ruleset applies only to a subset of the incoming requests. By default, a managed ruleset deployed in the dashboard applies to all incoming traffic.
-
Ruleset action: When you define an action for the ruleset, you override the default action defined for each rule. The available actions are: Block, Log, Non-Interactive Challenge, Managed Challenge, and Interactive Challenge. To remove the action override at the ruleset level, set the ruleset action to Default.
-
Ruleset status: Enables or disables all the rules in the ruleset.
-
Payload logging: When enabled, logs the request information (payload) that triggered a specific rule of the managed ruleset. You must configure a public key to encrypt the payload.
Once you have deployed the Cloudflare Managed Ruleset, do the following to configure it in the dashboard:
-
In the Cloudflare dashboard, go to the Security rules page.
Go to Security rules -
(Optional) Filter by Managed rules.
-
Search for Cloudflare Managed Ruleset. Look for a rule with an Execute action.
-
Select the rule name (containing the name of the managed ruleset) to open the deployment configuration page.
-
(Optional) To execute the Cloudflare Managed Ruleset for a subset of incoming requests, select Edit scope and configure the expression that will determine the scope of the current rule deploying the managed ruleset.
-
In the ruleset configuration section, define settings for all the rules in the Cloudflare Managed Ruleset by setting one or more fields using the drop-down lists.
For example, select the action to perform for all the rules in the ruleset.
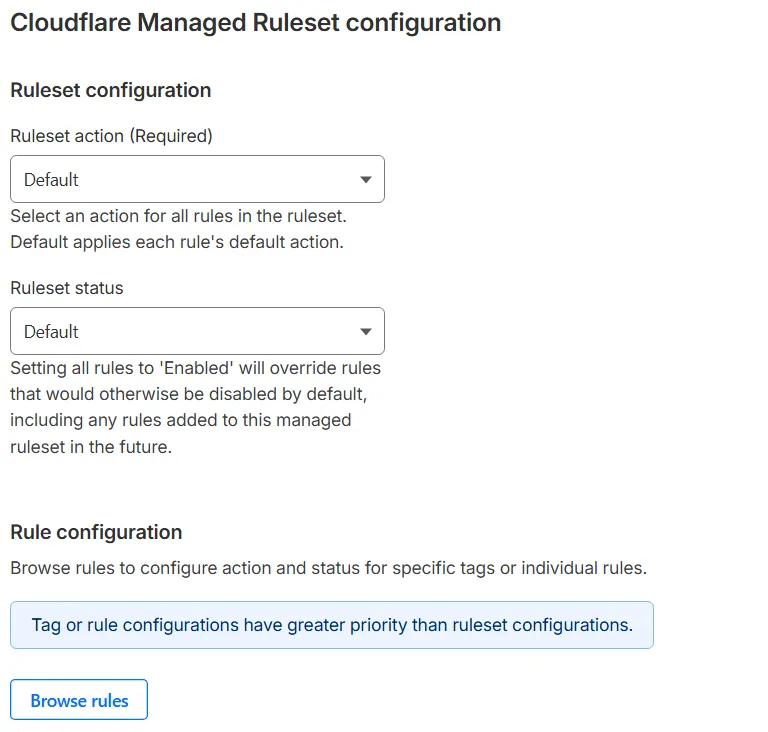
-
Select Save.
-
Log in to the Cloudflare dashboard ↗, and select your account and domain.
-
Go to Security > WAF > Managed rules tab.
-
Next to the Execute rule deploying the Cloudflare Managed Ruleset, select the managed ruleset name.
If you have not deployed the managed ruleset yet, select Cloudflare Managed Ruleset under Managed Rulesets. -
(Optional) To execute the Cloudflare Managed Ruleset for a subset of incoming requests, select Edit scope and configure the expression that will determine the scope of the current rule deploying the managed ruleset.
-
Under Ruleset configuration, define settings for all the rules in the Cloudflare Managed Ruleset using the drop-down lists.
For example, select the action to perform for all the rules in the ruleset.

-
If you have not deployed the Cloudflare Managed Ruleset yet:
- Select Deploy to deploy the ruleset immediately.
- Select Save as Draft to save your deployment settings for later.
If you are editing a managed ruleset you already deployed, select Save.
You can configure (or override) the following Cloudflare Managed Ruleset settings in the dashboard for rules tagged with at least one of the selected tags:
-
Rule action: Sets the rule action for all the rules with the selected tags. The available actions are: Block, Log, Non-Interactive Challenge, Managed Challenge, and Interactive Challenge.
-
Rule status: Sets the rule status for all the rules with the selected tags.
Once you have deployed the Cloudflare Managed Ruleset, do the following to configure rules with specific tags in the dashboard:
-
In the Cloudflare dashboard, go to the Security rules page.
Go to Security rules -
(Optional) Filter by Managed rules.
-
Search for Cloudflare Managed Ruleset. Look for a rule with an Execute action.
-
Select the rule name (containing the name of the managed ruleset), and then select Browse rules.
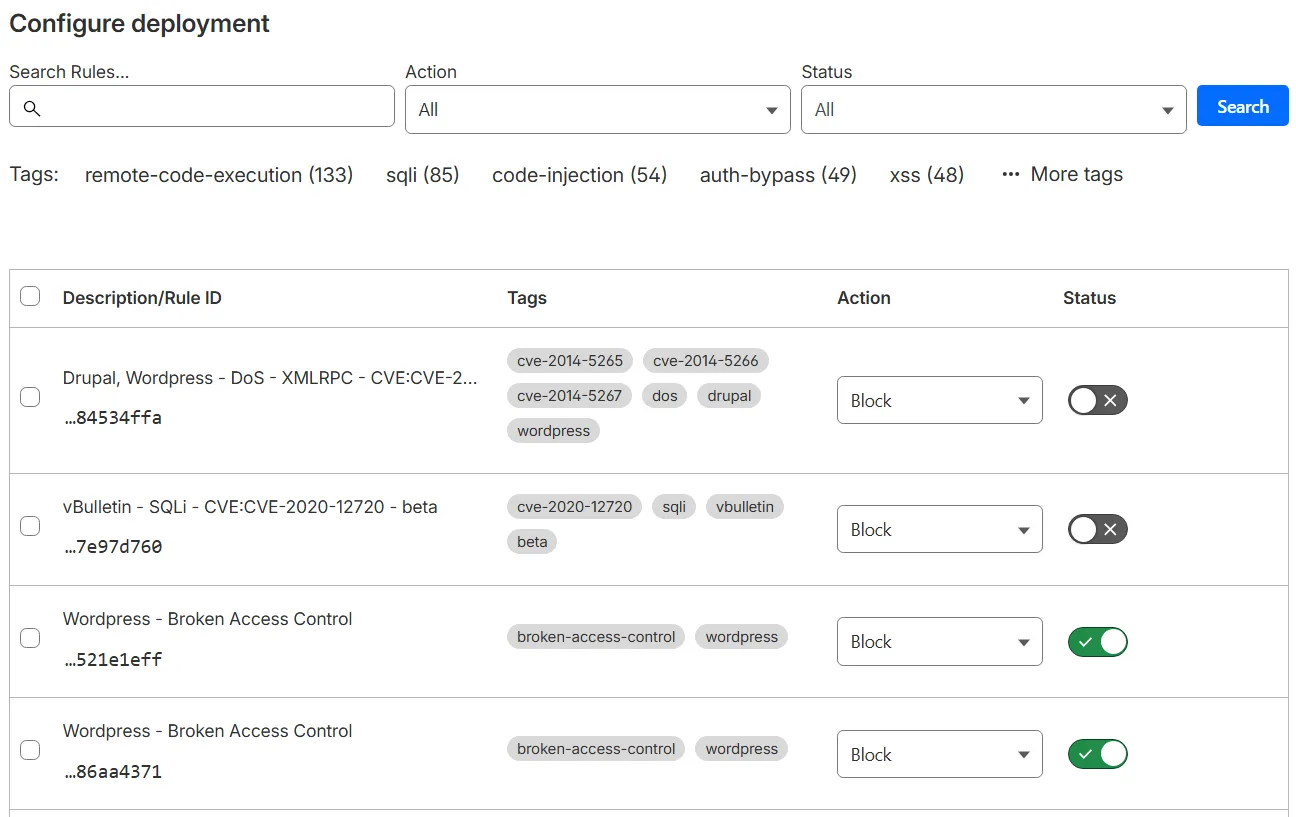
-
Select one or more tags under the search input to filter the rules with those tags, and then select the checkbox in the top left corner of the table to select all the rules shown in the current page.
If not all the rules are displayed in the current page, extend your selection to all rules with the selected tags across all pages by selecting Select all <NUMBER> rules.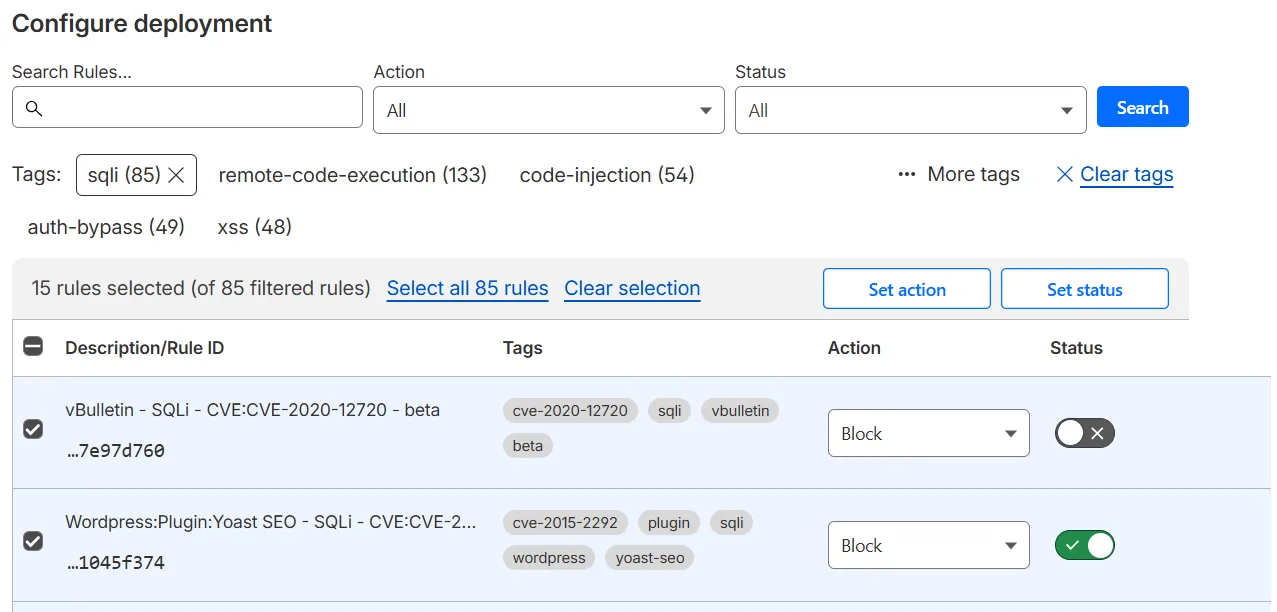
-
Update one or more settings for the selected rules using the buttons displayed in the top right corner of the table (for example, Set status).
-
Select Next.
-
A dialog appears asking you if any new rules with the selected tags should be configured with the field values you selected.
- Select Include new rules if you want to apply your configurations to any new rules with the select tags.
- Select Only selected rules to apply your configurations to the selected rules only.
-
Select Save.
-
Log in to the Cloudflare dashboard ↗, and select your account and domain.
-
Go to Security > WAF > Managed rules tab.
-
If you have already deployed the Cloudflare Managed Ruleset, select the ruleset name in the list of deployed managed rulesets. Alternatively, select the three dots > Edit next to the Execute rule deploying the Cloudflare Managed Ruleset.
If you have not deployed the managed ruleset, select Cloudflare Managed Ruleset under Managed Rulesets.
-
Select Browse rules.

-
Select one or more tags under the search input to filter the rules with those tags, and then select the checkbox in the top left corner of the table to select all the rules shown in the current page.
If not all the rules are displayed in the current page, extend your selection to all rules with the selected tags across all pages by selecting Select all <NUMBER> rules.
-
Update one or more settings for the selected rules using the buttons displayed in the top right corner of the table (for example, Set status).
-
Select Next.
-
A dialog appears asking you if any new rules with the selected tags should be configured with the field values you selected.
- Select Include new rules if you want to apply your configurations to any new rules with the select tags.
- Select Only selected rules to apply your configurations to the selected rules only.
-
Select Save.
You can configure (or override) the following Cloudflare Managed Ruleset settings in the dashboard for the selected rules:
-
Rule action: Sets the action of a single rule or, if you select multiple rules, for the selected rules. The available actions are: Block, Log, Non-Interactive Challenge, Managed Challenge, and Interactive Challenge. Once you have changed the configuration of a rule, you have the option to reset the configuration back to the default one as defined in the Cloudflare Managed Ruleset.
-
Rule status: Sets the status (enabled or disabled) of a single rule or, if you select multiple rules, for the selected rules.
Once you have deployed the Cloudflare Managed Ruleset, do the following to configure individual ruleset rules in the dashboard:
-
In the Cloudflare dashboard, go to the Security rules page.
Go to Security rules -
(Optional) Filter by Managed rules.
-
Search for Cloudflare Managed Ruleset. Look for a rule with an Execute action.
-
Select the rule name (containing the name of the managed ruleset), and then select Browse rules.

-
Search for rules using the available filters.
-
In the results list, change the values for each rule as desired, using the displayed drop-down lists and toggles. For example, change the status of a rule using the Status toggle next to the rule.
To configure multiple rules with the same value, select the checkboxes for all the rules you want to configure. If not all the rules are displayed in the current page, you can extend your selection to all rules across all pages by selecting Select all <NUMBER> rules. Then, use the buttons displayed in the top right corner of the table — for example, Set status — to update one or more fields for the selected rules.

-
Select Next, and then select Save.
-
Log in to the Cloudflare dashboard ↗, and select your account and domain.
-
Go to Security > WAF > Managed rules tab.
-
If you have already deployed the Cloudflare Managed Ruleset, select the ruleset name in the list of deployed managed rulesets. Alternatively, select the three dots > Edit next to the Execute rule deploying the Cloudflare Managed Ruleset.
If you have not deployed the managed ruleset, select Cloudflare Managed Ruleset under Managed Rulesets.
-
Select Browse rules.

-
Search for rules using the available filters.
-
In the results list, change the values for each rule as desired, using the displayed drop-down lists and toggles. For example, change the status of a rule using the Status toggle next to the rule.
To configure multiple rules with the same value, select the checkboxes for all the rules you want to configure. If not all the rules are displayed in the current page, you can extend your selection to all rules across all pages by selecting Select all <NUMBER> rules. Then, use the buttons displayed in the top right corner of the table — for example, Set status — to update one or more fields for the selected rules.

-
Select Next, and then select Save.
To deploy the Cloudflare Managed Ruleset for a given zone via API, create a rule with execute action in the entry point ruleset for the http_request_firewall_managed phase.
The following example deploys the Cloudflare Managed Ruleset to the http_request_firewall_managed phase of a given zone ($ZONE_ID) by creating a rule that executes the managed ruleset.
-
Invoke the Get a zone entry point ruleset operation to obtain the definition of the entry point ruleset for the
http_request_firewall_managedphase. You will need the zone ID for this task.Get a zone entry point ruleset curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/rulesets/phases/http_request_firewall_managed/entrypoint" \--request GET \--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN"{"result": {"description": "Zone-level phase entry point","id": "<RULESET_ID>","kind": "zone","last_updated": "2024-03-16T15:40:08.202335Z","name": "zone","phase": "http_request_firewall_managed","rules": [// ...],"source": "firewall_managed","version": "10"},"success": true,"errors": [],"messages": []} -
If the entry point ruleset already exists (that is, if you received a
200 OKstatus code and the ruleset definition), take note of the ruleset ID in the response. Then, invoke the Create a zone ruleset rule operation to add anexecuterule to the existing ruleset deploying the Cloudflare Managed Ruleset (with IDefb7b8c949ac4650a09736fc376e9aee). By default, the rule will be added at the end of the list of rules already in the ruleset.Create a zone ruleset rule curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/rulesets/$RULESET_ID/rules" \--request POST \--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \--json '{"action": "execute","action_parameters": {"id": "efb7b8c949ac4650a09736fc376e9aee"},"expression": "true","description": "Execute the Cloudflare Managed Ruleset"}'{"result": {"id": "<RULESET_ID>","name": "Zone-level phase entry point","description": "","kind": "zone","version": "11","rules": [// ... any existing rules{"id": "<RULE_ID>","version": "1","action": "execute","action_parameters": {"id": "efb7b8c949ac4650a09736fc376e9aee","version": "latest"},"expression": "true","description": "Execute the Cloudflare Managed Ruleset","last_updated": "2024-03-18T18:08:14.003361Z","ref": "<RULE_REF>","enabled": true}],"last_updated": "2024-03-18T18:08:14.003361Z","phase": "http_request_firewall_managed"},"success": true,"errors": [],"messages": []} -
If the entry point ruleset does not exist (that is, if you received a
404 Not Foundstatus code in step 1), create it using the Create a zone ruleset operation. Include a single rule in therulesarray that executes the Cloudflare Managed Ruleset (with IDefb7b8c949ac4650a09736fc376e9aee) for all incoming requests in the zone.Create a zone ruleset curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/rulesets" \--request POST \--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \--json '{"name": "My ruleset","description": "Entry point ruleset for WAF managed rulesets","kind": "zone","phase": "http_request_firewall_managed","rules": [{"action": "execute","action_parameters": {"id": "efb7b8c949ac4650a09736fc376e9aee"},"expression": "true","description": "Execute the Cloudflare Managed Ruleset"}]}'
To configure the Cloudflare Managed Ruleset via API, create overrides using the Rulesets API. You can perform the following configurations:
- Specify the action to perform for all the rules in the ruleset by creating a ruleset override.
Disable or customize the action of individual rules by creating rule overrides.
For examples of creating overrides using the API, refer to Override a managed ruleset.
For more information on working with managed rulesets via API, refer to Work with managed rulesets in the Ruleset Engine documentation.
The following example deploys the Cloudflare Managed Ruleset for a zone and overrides the action and status of a specific rule.
# Configure a ruleset at the zone level for the "http_request_firewall_managed" phaseresource "cloudflare_ruleset" "zone_level_managed_waf" { zone_id = "<ZONE_ID>" name = "Managed WAF entry point ruleset" description = "Zone-level WAF Managed Rules config" kind = "zone" phase = "http_request_firewall_managed"
# Execute Cloudflare Managed Ruleset rules { ref = "execute_cloudflare_managed_ruleset" description = "Execute Cloudflare Managed Ruleset on my zone-level phase entry point ruleset" expression = "true" action = "execute" action_parameters { id = "efb7b8c949ac4650a09736fc376e9aee" overrides { rules { id = "5de7edfa648c4d6891dc3e7f84534ffa" action = "log" enabled = true } } } }}For more information, refer to WAF Managed Rules configuration using Terraform.