Sumo Logic integration guide
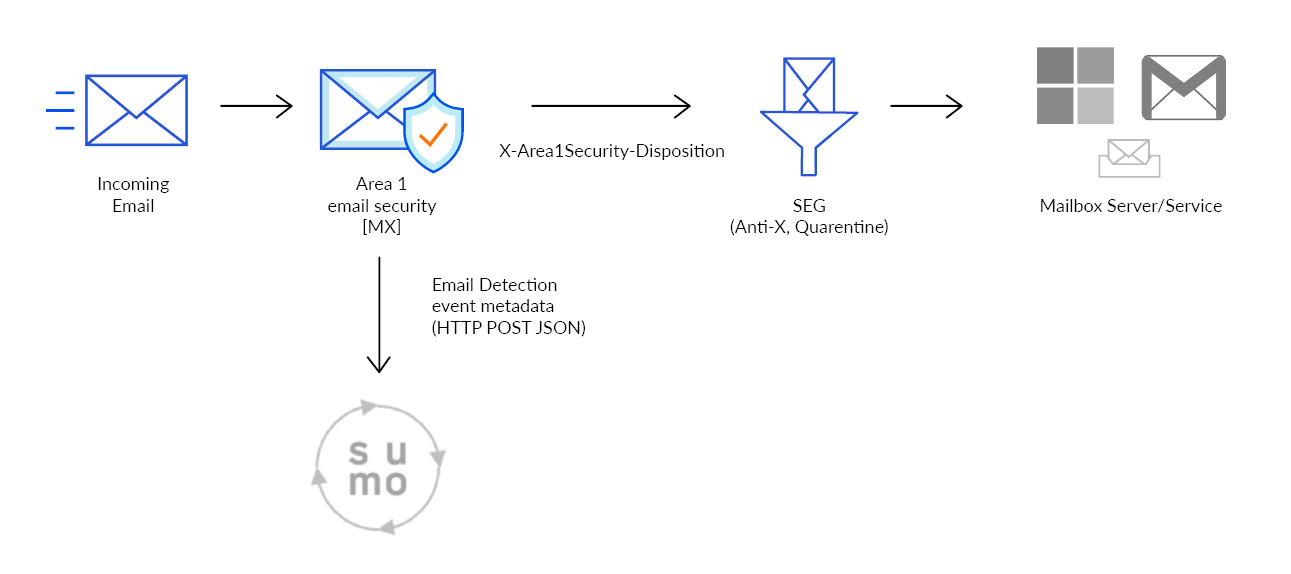
When Cloud Email Security detects a phishing email, the metadata of the detection can be sent directly into your instance of Sumo Logic. This document outlines the steps required to integrate Cloud Email Security with Sumo Logic.
1. Configure the Sumologic Collector
Log in to Sumo Logic with an administrator account.
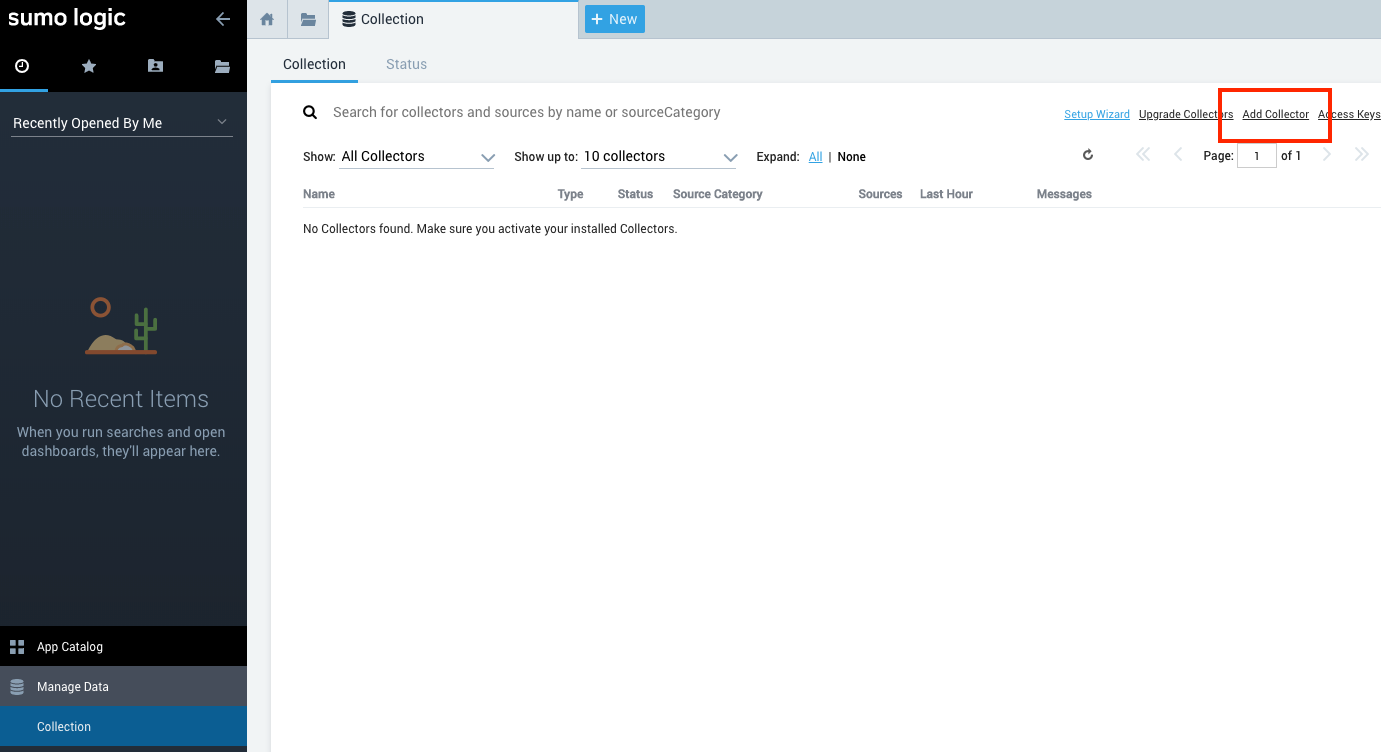
Go to Manage Data > Collection to open the collector configuration pane.
Select Add Collector.
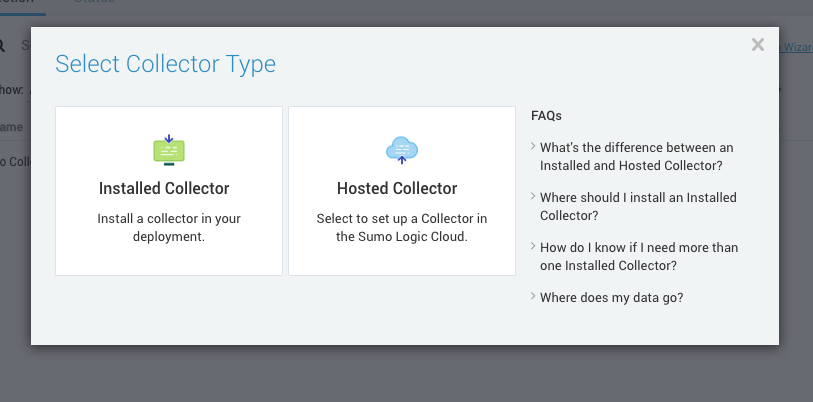
In Select Collector Type, select Hosted Collector.
In Add Hosted Collector, enter the following settings:
- Name:
Cloud Email Security Collector - Description:
Cloud Email Security Security Collectors - Category: Anti-Phishing
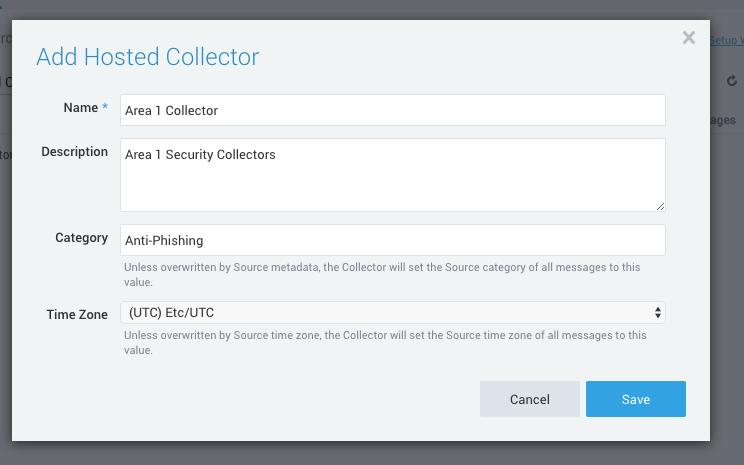
- Name:
Select Save > OK to confirm the addition of the new Collector.
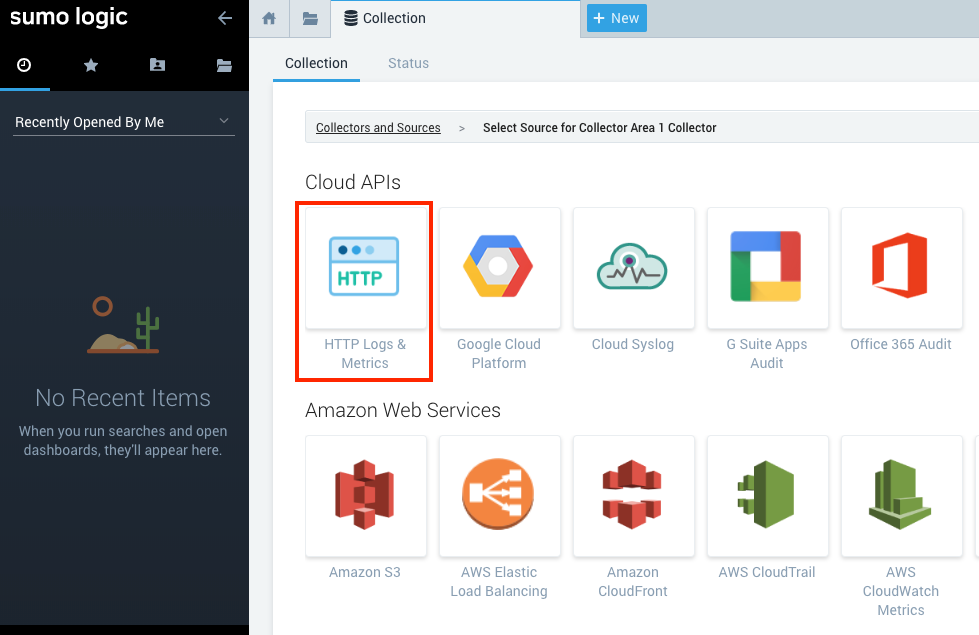
In Cloud APIs, select HTTP Logs and Metrics to start the configuration of the data source.
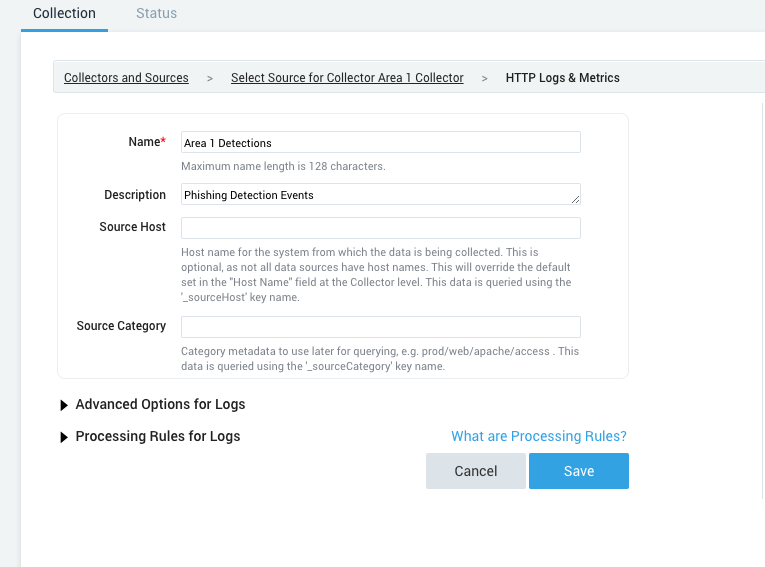
Enter a descriptive Name and Description, and select Save.
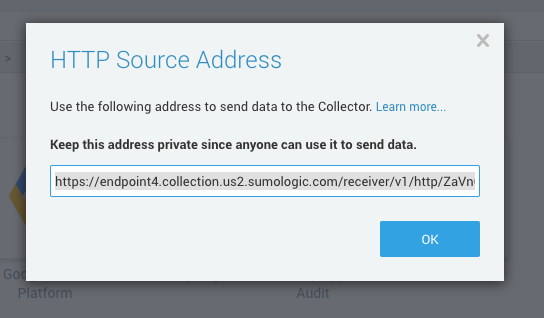
The system will present you a dialog box with the HTTP endpoint. Save it, as this will be required to configure Cloud Email Security later.
2. Configure Cloud Email Security
The next step is to configure Cloud Email Security to push the Email Detection Events to the Sumologic HTTP Collector.
- Log in to the Cloud Email Security dashboard.
- Go to Email Configuration > Alert Webhooks, and select New Webhook.
- In the Add Webhooks page, enter the following settings:
- App type: Select SIEM > Splunk. In Auth code, enter
Sumologic. - Target: Enter the HTTP endpoint you saved in the previous section.
- For the dispositions (
MALICIOUS,SUSPICIOUS,SPOOF,SPAM,BULK) choose which (if any) you want to send to the webhook. SendingSPAMandBULKdispositions will generate a high number of events.
- App type: Select SIEM > Splunk. In Auth code, enter
- Select Publish Webhook.
Your Sumo Logic integration will now show up in the All Webhooks panel.
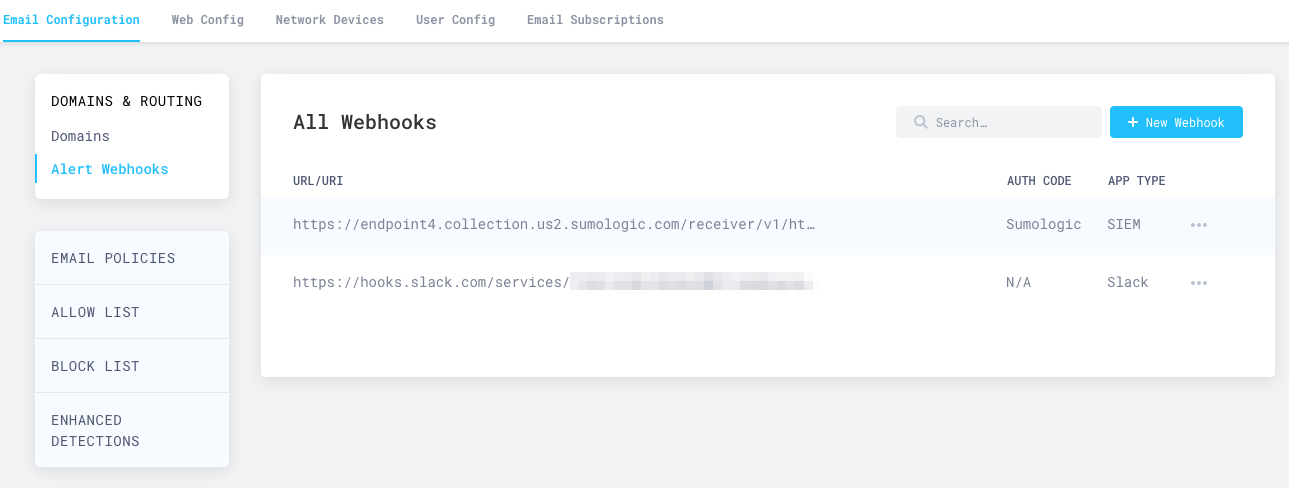
It will take about ten minutes for the configuration to fully propagate through the infrastructure of Cloudflare Cloud Email Security, and for events to start to appear in your searches. Once the configuration is propagated, events will start to appear in your instance of Sumo Logic.
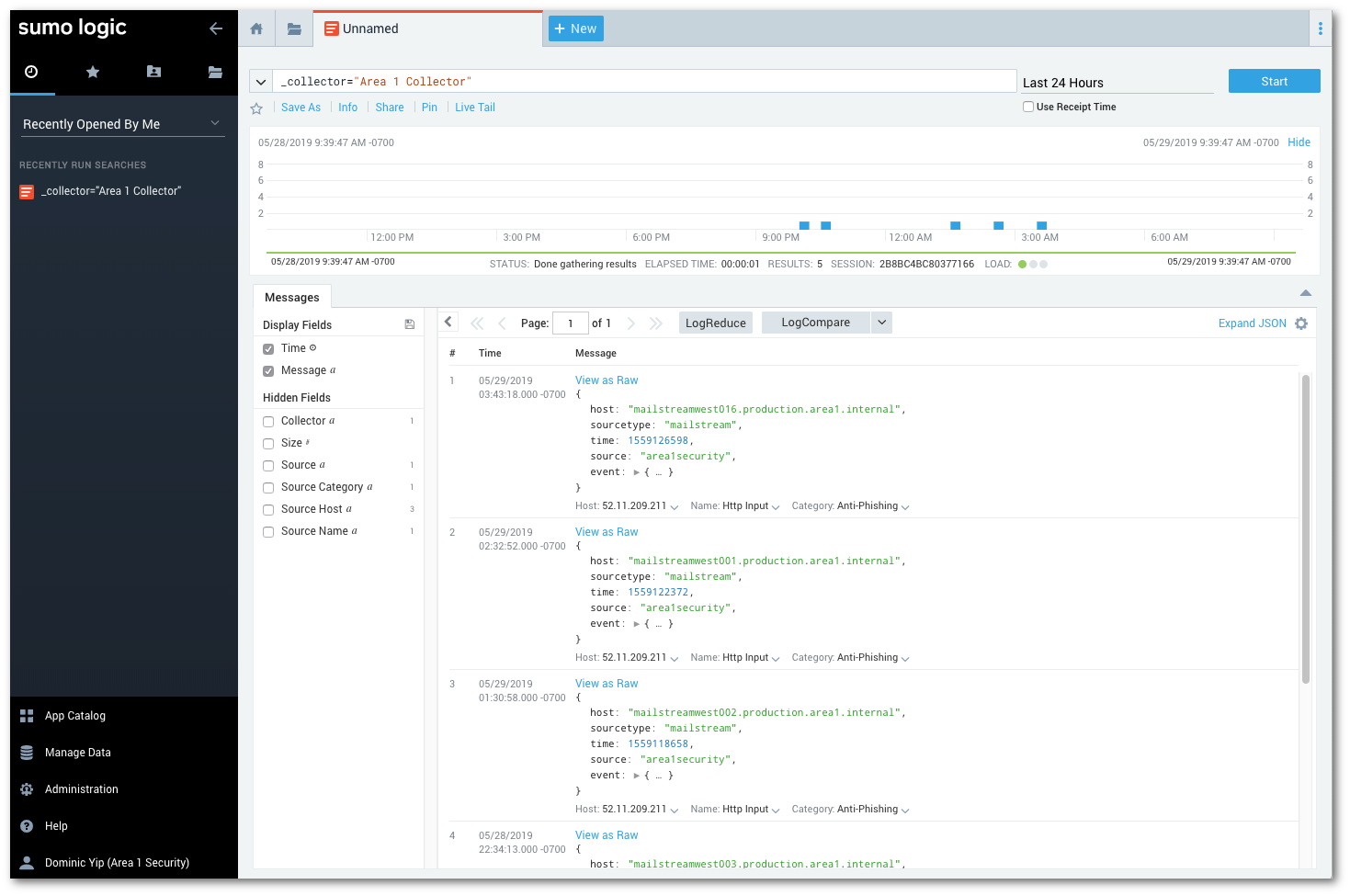
To view logs, hover your mouse over the Cloud Email Security Collector, and select Open in Log Search.
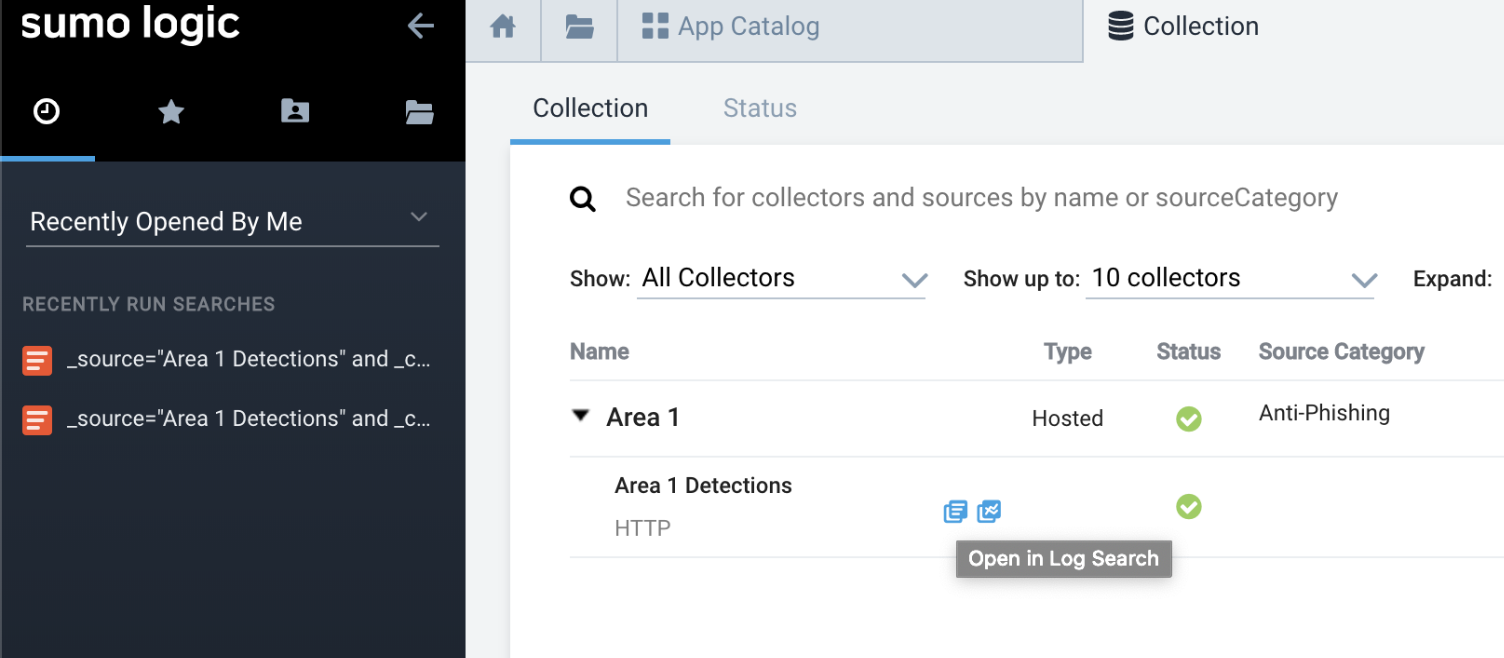
Once events start to flow, select New > Log search to search for the detection events with your search criteria (for example, _collector="Cloud Email Security Collector").