---
title: 404 - Page Not Found | Cloudflare Docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/404/
md: https://developers.cloudflare.com/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: 1.1.1.1 (DNS Resolver) · Cloudflare 1.1.1.1 docs
description: 1.1.1.1 is Cloudflare’s public DNS resolver. It offers a fast and
private way to browse the Internet. DNS resolvers translate domains like
cloudflare.com into the IP addresses necessary to reach the website (like
104.16.123.96).
lastUpdated: 2025-08-13T12:32:09.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/
md: https://developers.cloudflare.com/1.1.1.1/index.md
---
Speed up your online experience with Cloudflare's public DNS resolver.
Available on all plans
1.1.1.1 is Cloudflare’s public DNS resolver. It offers a fast and private way to browse the Internet. [DNS resolvers](https://www.cloudflare.com/learning/dns/what-is-dns/) translate domains like `cloudflare.com` into the IP addresses necessary to reach the website (like `104.16.123.96`).
Unlike most DNS resolvers, 1.1.1.1 does not sell user data to advertisers. 1.1.1.1 has also been measured to be the [fastest DNS resolver available](https://www.dnsperf.com/#!dns-resolvers) — it is deployed in [hundreds of cities worldwide](https://www.cloudflare.com/network/), and has access to the addresses of millions of domain names on the same servers it runs on.
1.1.1.1 is completely free. Setting it up takes minutes and requires no special software.
***
## Features
### 1.1.1.1 for Families
1.1.1.1 for Families has additional protection against malware and adult content.
[Use 1.1.1.1 for Families](https://developers.cloudflare.com/1.1.1.1/setup/#1111-for-families)
### Encrypted service
1.1.1.1 offers an encrypted service through DNS over HTTPS (DoH) or DNS over TLS (DoT) for increased security and privacy. You can also access 1.1.1.1 [as a Tor hidden service](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-over-tor/).
[Use Encrypted service](https://developers.cloudflare.com/1.1.1.1/encryption/)
***
## Related products
**[WARP Client](https://developers.cloudflare.com/warp-client/)**
Access the Internet in a more secure and private way.
**[DNS](https://developers.cloudflare.com/dns/)**
Cloudflare's global DNS platform provides speed and resilience. DNS customers also benefit from free DNSSEC, and protection against route leaks and hijacking.
**[Cloudflare Spectrum](https://developers.cloudflare.com/spectrum/)**
Secure and accelerate your TCP or UDP based applications.
---
title: Overview · Cloudflare AI Gateway docs
description: Cloudflare's AI Gateway allows you to gain visibility and control
over your AI apps. By connecting your apps to AI Gateway, you can gather
insights on how people are using your application with analytics and logging
and then control how your application scales with features such as caching,
rate limiting, as well as request retries, model fallback, and more. Better
yet - it only takes one line of code to get started.
lastUpdated: 2025-08-19T11:42:14.000Z
chatbotDeprioritize: false
tags: AI
source_url:
html: https://developers.cloudflare.com/ai-gateway/
md: https://developers.cloudflare.com/ai-gateway/index.md
---
Observe and control your AI applications.
Available on all plans
Cloudflare's AI Gateway allows you to gain visibility and control over your AI apps. By connecting your apps to AI Gateway, you can gather insights on how people are using your application with analytics and logging and then control how your application scales with features such as caching, rate limiting, as well as request retries, model fallback, and more. Better yet - it only takes one line of code to get started.
Check out the [Get started guide](https://developers.cloudflare.com/ai-gateway/get-started/) to learn how to configure your applications with AI Gateway.
## Features
### Analytics
View metrics such as the number of requests, tokens, and the cost it takes to run your application.
[View Analytics](https://developers.cloudflare.com/ai-gateway/observability/analytics/)
### Logging
Gain insight on requests and errors.
[View Logging](https://developers.cloudflare.com/ai-gateway/observability/logging/)
### Caching
Serve requests directly from Cloudflare's cache instead of the original model provider for faster requests and cost savings.
[Use Caching](https://developers.cloudflare.com/ai-gateway/features/caching/)
### Rate limiting
Control how your application scales by limiting the number of requests your application receives.
[Use Rate limiting](https://developers.cloudflare.com/ai-gateway/features/rate-limiting/)
### Request retry and fallback
Improve resilience by defining request retry and model fallbacks in case of an error.
[Use Request retry and fallback](https://developers.cloudflare.com/ai-gateway/features/dynamic-routing/)
### Your favorite providers
Workers AI, OpenAI, Azure OpenAI, HuggingFace, Replicate, and more work with AI Gateway.
[Use Your favorite providers](https://developers.cloudflare.com/ai-gateway/usage/providers/)
***
## Related products
**[Workers AI](https://developers.cloudflare.com/workers-ai/)**
Run machine learning models, powered by serverless GPUs, on Cloudflare’s global network.
**[Vectorize](https://developers.cloudflare.com/vectorize/)**
Build full-stack AI applications with Vectorize, Cloudflare's vector database. Adding Vectorize enables you to perform tasks such as semantic search, recommendations, anomaly detection or can be used to provide context and memory to an LLM.
## More resources
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[Use cases](https://developers.cloudflare.com/use-cases/ai/)
Learn how you can build and deploy ambitious AI applications to Cloudflare's global network.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
---
title: Overview · Cloudflare AI Crawl Control docs
description: Monitor and control how AI services access your website content.
lastUpdated: 2025-11-14T15:41:09.000Z
chatbotDeprioritize: false
tags: AI
source_url:
html: https://developers.cloudflare.com/ai-crawl-control/
md: https://developers.cloudflare.com/ai-crawl-control/index.md
---
Available on all plans
Monitor and control how AI services access your website content.
AI companies use web content to train their models and power AI applications. AI Crawl Control (formerly AI Audit) gives you visibility into which AI services are accessing your content, and provides tools to manage access according to your preferences.
With AI Crawl Control, you can:
* **See which AI services access your content** - Monitor the dashboard to see crawler activity and request patterns
* **Control access with granular policies** - Set allow or block rules for individual crawlers
* **Monitor robots.txt compliance** - Track which crawlers follow your directives and create enforcement rules
* **Explore monetization options** - Set up pay per crawl pricing for content access [(private beta)](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/)
* **Deploy with zero configuration** - Works automatically on all Cloudflare plans
[Get started](https://developers.cloudflare.com/ai-crawl-control/get-started/)
***
## Features
### Manage AI crawlers
Control how AI crawlers interact with your domain.
[Manage AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/)
### Analyze AI traffic
Gain insight into how AI crawlers are interacting with your pages.
[Analyze AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/)
### Track robots.txt
Track the health of `robots.txt` files and identify which crawlers are violating your directives.
[Track robots.txt](https://developers.cloudflare.com/ai-crawl-control/features/track-robots-txt/)
### Pay Per Crawl
Allow AI crawlers to access content by paying per crawl.
[Pay per crawl](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/)
***
## Use cases
Publishers and content creators
Publishers and content creators can monitor which AI crawlers are accessing their articles and educational content. Set policies to allow beneficial crawlers while blocking others.
E-commerce and business sites
E-commerce and business sites can identify AI crawler activity on product pages and business information. Control access to sensitive data like pricing and inventory.
Documentation sites
Documentation sites can track how AI crawlers are accessing their technical documentation. Gain insight into how AI crawlers are engaging with your site.
***
## Related Products
**[Bots](https://developers.cloudflare.com/bots/)**
Identify and mitigate automated traffic to protect your domain from bad bots.
**[Web Application Firewall](https://developers.cloudflare.com/waf/)**
Get automatic protection from vulnerabilities and the flexibility to create custom rules.
**[Analytics](https://developers.cloudflare.com/analytics/)**
View and analyze traffic on your domain.
---
title: Agents · Cloudflare Agents docs
description: The Agents SDK enables you to build and deploy AI-powered agents
that can autonomously perform tasks, communicate with clients in real time,
call AI models, persist state, schedule tasks, run asynchronous workflows,
browse the web, query data from your database, support human-in-the-loop
interactions, and a lot more.
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
tags: AI
source_url:
html: https://developers.cloudflare.com/agents/
md: https://developers.cloudflare.com/agents/index.md
---
The Agents SDK enables you to build and deploy AI-powered agents that can autonomously perform tasks, communicate with clients in real time, call AI models, persist state, schedule tasks, run asynchronous workflows, browse the web, query data from your database, support human-in-the-loop interactions, and [a lot more](https://developers.cloudflare.com/agents/api-reference/).
### Ship your first Agent
To use the Agent starter template and create your first Agent with the Agents SDK:
1. Create a new project:
```sh
npx create-cloudflare@latest --template cloudflare/agents-starter
```
1. Install dependencies:
```sh
npm install
```
1. Set up your environment:
Create a `.dev.vars` file:
```env
OPENAI_API_KEY=your_openai_api_key
```
1. Run locally:
```sh
npm start
```
1. Deploy:
```sh
npm run deploy
```
Head to the guide on [building a chat agent](https://developers.cloudflare.com/agents/getting-started/build-a-chat-agent) to learn how the starter project is built and how to use it as a foundation for your own agents.
If you're already building on [Workers](https://developers.cloudflare.com/workers/), you can install the `agents` package directly into an existing project:
```sh
npm i agents
```
And then define your first Agent by creating a class that extends the `Agent` class:
* JavaScript
```js
import { Agent } from "agents";
export class MyAgent extends Agent {
// Define methods on the Agent:
// https://developers.cloudflare.com/agents/api-reference/agents-api/
//
// Every Agent has built in state via this.setState and this.sql
// Built-in scheduling via this.schedule
// Agents support WebSockets, HTTP requests, state synchronization and
// can run for seconds, minutes or hours: as long as the tasks need.
}
```
* TypeScript
```ts
import { Agent } from "agents";
export class MyAgent extends Agent {
// Define methods on the Agent:
// https://developers.cloudflare.com/agents/api-reference/agents-api/
//
// Every Agent has built in state via this.setState and this.sql
// Built-in scheduling via this.schedule
// Agents support WebSockets, HTTP requests, state synchronization and
// can run for seconds, minutes or hours: as long as the tasks need.
}
```
Lastly, add the [Durable Objects](https://developers.cloudflare.com/durable-objects/) binding to your wrangler file:
* wrangler.jsonc
```jsonc
{
"durable_objects": {
"bindings": [
{
"name": "MyAgent",
"class_name": "MyAgent"
}
]
},
"migrations": [
{
"tag": "v1",
"new_sqlite_classes": [
"MyAgent"
]
}
]
}
```
* wrangler.toml
```toml
[[durable_objects.bindings]]
name = "MyAgent"
class_name = "MyAgent"
[[migrations]]
tag = "v1"
new_sqlite_classes = [ "MyAgent" ]
```
Dive into the [Agent SDK reference](https://developers.cloudflare.com/agents/api-reference/agents-api/) to learn more about how to use the Agents SDK package and defining an `Agent`.
### Why build agents on Cloudflare?
We built the Agents SDK with a few things in mind:
* **Batteries (state) included**: Agents come with [built-in state management](https://developers.cloudflare.com/agents/api-reference/store-and-sync-state/), with the ability to automatically sync state between an Agent and clients, trigger events on state changes, and read+write to each Agent's SQL database.
* **Communicative**: You can connect to an Agent via [WebSockets](https://developers.cloudflare.com/agents/api-reference/websockets/) and stream updates back to client in real-time. Handle a long-running response from a reasoning model, the results of an [asynchronous workflow](https://developers.cloudflare.com/agents/api-reference/run-workflows/), or build a chat app that builds on the `useAgent` hook included in the Agents SDK.
* **Extensible**: Agents are code. Use the [AI models](https://developers.cloudflare.com/agents/api-reference/using-ai-models/) you want, bring-your-own headless browser service, pull data from your database hosted in another cloud, add your own methods to your Agent and call them.
Agents built with Agents SDK can be deployed directly to Cloudflare and run on top of [Durable Objects](https://developers.cloudflare.com/durable-objects/) — which you can think of as stateful micro-servers that can scale to tens of millions — and are able to run wherever they need to. Run your Agents close to a user for low-latency interactivity, close to your data for throughput, and/or anywhere in between.
***
### Build on the Cloudflare Platform
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[AI Gateway](https://developers.cloudflare.com/ai-gateway/)**
Observe and control your AI applications with caching, rate limiting, request retries, model fallback, and more.
**[Vectorize](https://developers.cloudflare.com/vectorize/)**
Build full-stack AI applications with Vectorize, Cloudflare’s vector database. Adding Vectorize enables you to perform tasks such as semantic search, recommendations, anomaly detection or can be used to provide context and memory to an LLM.
**[Workers AI](https://developers.cloudflare.com/workers-ai/)**
Run machine learning models, powered by serverless GPUs, on Cloudflare's global network.
**[Workflows](https://developers.cloudflare.com/workflows/)**
Build stateful agents that guarantee executions, including automatic retries, persistent state that runs for minutes, hours, days, or weeks.
---
title: Cloudflare AI Search · Cloudflare AI Search docs
description: Build scalable, fully-managed RAG applications with Cloudflare AI
Search. Create retrieval-augmented generation pipelines to deliver accurate,
context-aware AI without managing infrastructure.
lastUpdated: 2025-09-24T17:03:07.000Z
chatbotDeprioritize: false
tags: AI
source_url:
html: https://developers.cloudflare.com/ai-search/
md: https://developers.cloudflare.com/ai-search/index.md
---
Create AI-powered search for your data
Available on all plans
AI Search (formerly AutoRAG) is Cloudflare’s managed search service. You can connect your data such as websites or unstructured content, and it automatically creates a continuously updating index that you can query with natural language in your applications or AI agents. It natively integrates with Cloudflare’s developer platform tools like Vectorize, AI Gateway, R2, and Workers AI, while also supporting third-party providers and open standards.
It supports retrieval-augmented generation (RAG) patterns, enabling you to build enterprise search, natural language search, and AI-powered chat without managing infrastructure.
[Get started](https://developers.cloudflare.com/ai-search/get-started)
[Watch AI Search demo](https://www.youtube.com/watch?v=JUFdbkiDN2U)
***
## Features
### Automated indexing
Automatically and continuously index your data source, keeping your content fresh without manual reprocessing.
[View indexing](https://developers.cloudflare.com/ai-search/configuration/indexing/)
### Multitenancy support
Create multitenancy by scoping search to each tenant’s data using folder-based metadata filters.
[Add filters](https://developers.cloudflare.com/ai-search/how-to/multitenancy/)
### Workers Binding
Call your AI Search instance for search or AI Search directly from a Cloudflare Worker using the native binding integration.
[Add to Worker](https://developers.cloudflare.com/ai-search/usage/workers-binding/)
### Similarity caching
Cache repeated queries and results to improve latency and reduce compute on repeated requests.
[Use caching](https://developers.cloudflare.com/ai-search/configuration/cache/)
***
## Related products
**[Workers AI](https://developers.cloudflare.com/workers-ai/)**
Run machine learning models, powered by serverless GPUs, on Cloudflare’s global network.
**[AI Gateway](https://developers.cloudflare.com/ai-gateway/)**
Observe and control your AI applications with caching, rate limiting, request retries, model fallback, and more.
**[Vectorize](https://developers.cloudflare.com/vectorize/)**
Build full-stack AI applications with Vectorize, Cloudflare’s vector database.
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[R2](https://developers.cloudflare.com/r2/)**
Store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
***
## More resources
[Get started](https://developers.cloudflare.com/workers-ai/get-started/workers-wrangler/)
Build and deploy your first Workers AI application.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, share what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
---
title: Analytics · Cloudflare Analytics docs
description: Cloudflare visualizes the metadata collected by our products in the
Cloudflare dashboard. Refer to Types of analytics for more information about
the various types of analytics and where they exist in the dashboard.
lastUpdated: 2024-09-20T15:57:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/
md: https://developers.cloudflare.com/analytics/index.md
---
Cloudflare visualizes the metadata collected by our products in the Cloudflare dashboard. Refer to [Types of analytics](https://developers.cloudflare.com/analytics/types-of-analytics/) for more information about the various types of analytics and where they exist in the dashboard.
***
## Features
### Workers Analytics Engine
Send unlimited-cardinality data from your Worker to a time-series database. Query it with SQL.
[Use Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/)
### Account and zone analytics
Provides details about the requests and traffic related to your Cloudflare accounts and zones.
[Use Account and zone analytics](https://developers.cloudflare.com/analytics/account-and-zone-analytics/)
### Cloudflare Network Analytics
Provides near real-time visibility into network and transport-layer traffic patterns and DDoS attacks.
[Use Cloudflare Network Analytics](https://developers.cloudflare.com/analytics/network-analytics/)
### GraphQL Analytics API
Provides all of your performance, security, and reliability data from one endpoint. Select exactly what you need, from one metric for a domain to multiple metrics aggregated for your account.
[Use GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/)
***
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Cloudflare Workers allows developers to build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Logs](https://developers.cloudflare.com/logs/)**
Detailed logs that contain metadata generated by Cloudflare products helpful for debugging, identifying configuration adjustments, and creating analytics.
---
title: Overview · Cloudflare API Shield docs
description: APIs have become the backbone of popular web services, helping the
Internet become more accessible and useful.
lastUpdated: 2025-10-08T15:21:13.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/
md: https://developers.cloudflare.com/api-shield/index.md
---
Identify and address your API vulnerabilities.
Enterprise-only paid add-on
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
## Why care about API security?
APIs have become the [backbone of popular web services](https://blog.postman.com/intro-to-apis-history-of-apis/), helping the Internet become more accessible and useful.
As APIs have become more prevalent, however, so have their problems:
* Many companies have [thousands of APIs](https://developers.cloudflare.com/api-shield/security/api-discovery/), including ones they do not even know about.
* To support a large base of users, many APIs are protected by a negative security model that makes them vulnerable to credential-stuffing attacks and automated scanning tools.
* With so many endpoints and users, it’s difficult to recognize brute-force attacks against [specific endpoints](https://developers.cloudflare.com/api-shield/security/volumetric-abuse-detection/).
* Sophisticated attacks are even harder to recognize, often because even development teams are unaware of common and uncommon [usage patterns](https://developers.cloudflare.com/api-shield/security/sequence-analytics/).
Refer to the [Get started](https://developers.cloudflare.com/api-shield/get-started/) guide to set up API Shield.
## Features
### Security features
Secure your APIs using API Shield's security features.
[Use Security features](https://developers.cloudflare.com/api-shield/security/)
### Management, monitoring, and more
Monitor the health of your API endpoints.
[Use Management, monitoring, and more](https://developers.cloudflare.com/api-shield/management-and-monitoring/)
## Availability
Cloudflare API Security products are available to Enterprise customers only, though anyone can set up [Mutual TLS](https://developers.cloudflare.com/api-shield/security/mtls/) with a Cloudflare-managed certificate authority.
The full API Shield security suite is available as an Enterprise-only paid add-on, but all customers can access [Endpoint Management](https://developers.cloudflare.com/api-shield/management-and-monitoring/) and [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/) functionalities.
Note
API Shield currently does not work for JDCloud customers.
## Related products
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Cloudflare DDoS protection secures websites, applications, and entire networks while ensuring the performance of legitimate traffic is not compromised.
---
title: Overview · Cloudflare Argo Smart Routing docs
description: Argo Smart Routing detects real-time network issues and routes your
web traffic across the most efficient network path, avoiding congestion.
lastUpdated: 2025-10-02T15:01:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/argo-smart-routing/
md: https://developers.cloudflare.com/argo-smart-routing/index.md
---
Speed up your global traffic with a single click
Paid add-on
Smart Shield
This functionality is now offered as part of Cloudflare's origin server safeguard, Smart Shield. [Learn more](https://developers.cloudflare.com/smart-shield/).
Argo Smart Routing detects real-time network issues and routes your web traffic across the most efficient network path, avoiding congestion.
This results in faster loading times, increased reliability, and reduced costs. These benefits are most apparent for users farthest from your origin server.
Learn more about the [benefits of Argo Smart Routing](https://www.cloudflare.com/application-services/products/argo-smart-routing/).
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
***
## Features
### Analytics
Argo Smart Routing includes comprehensive analytics to compare performance improvements with and without Argo enabled.
[Use Analytics](https://developers.cloudflare.com/argo-smart-routing/analytics/)
***
## Related products
**[Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/)**
Increase cache hit ratios to reduce requests to your origin server.
**[China Network](https://developers.cloudflare.com/china-network/)**
Improve security and performance within mainland China.
**[Magic Transit](https://developers.cloudflare.com/magic-transit/)**
Reduce latency and protect from DDoS attacks using the Cloudflare network.
***
## More resources
[Plans](https://www.cloudflare.com/plans/#overview)
Compare available Cloudflare plans
[Pricing](https://dash.cloudflare.com/?to=/:account/:zone/traffic/)
Explore pricing options for Argo in the dashboard
---
title: Overview · Cloudflare Automatic Platform Optimization docs
description: Take your WordPress site’s performance to the next level with
Automatic Platform Optimizations (APO). APO allows Cloudflare to serve your
entire WordPress site from its edge network ensuring consistent, fast
performance for visitors no matter where they are.
lastUpdated: 2025-11-17T22:48:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/automatic-platform-optimization/
md: https://developers.cloudflare.com/automatic-platform-optimization/index.md
---
Take your WordPress site’s performance to the next level with Automatic Platform Optimizations (APO). APO allows Cloudflare to serve your entire WordPress site from its edge network ensuring consistent, fast performance for visitors no matter where they are.
Automatic Platform Optimization is the result of using the power of [Cloudflare Workers](https://developers.cloudflare.com/workers/) to intelligently cache dynamic content. By caching dynamic content, Cloudflare can serve the entire website from our edge network to make a site's time to first byte (TTFB) both fast and consistent.
To read more about the benefits of using APO with your site, see [The Benefits of Automatic Platform Optimization blog](https://blog.cloudflare.com/automatic-platform-optimizations-starting-with-wordpress/#the-benefits-of-automatic-platform-optimization). You must use the Cloudflare for WordPress plugin to begin using APO.
---
title: Overview · Cloudflare Billing docs
description: Manage billing and subscriptions for your account.
lastUpdated: 2025-09-03T15:11:54.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/
md: https://developers.cloudflare.com/billing/index.md
---
Welcome to the Cloudflare Billing and Payment Help Center! Here you will find answers to some of the most common and impactful issues facing our customers today. Most current issues revolve around:
* Payment failures
* Outstanding balances
* Subscription renewals
* Cancellation requests
* Updating payment methods
* Understanding billing cycles
An overview of these issues can be found below:
## Failed Plan Modifications
You may receive an error when attempting to purchase a product, pay a balance or change a paid plan. Review the following guides for possible solutions:
* [Resolve a payment failure](https://developers.cloudflare.com/billing/troubleshoot-failed-payments/)
* [Resolve the zone cannot be upgraded error](https://developers.cloudflare.com/billing/resolve-zone-cannot-be-ugpraded/)
* [Resolve "You cannot modify this subscription"](https://developers.cloudflare.com/billing/resolve-you-cannot-modify-this-subscription/)
If the problems above do not apply to you, there are intermittent issues with subscription upgrades, downgrades, and cancellations. This may result in billing charges being applied without the subscription level being updated. In these instances, you should [contact support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
## Cannot update or remove payment methods
You should be able to add, update, and remove payment methods in your account. If you are seeing difficulties doing this, refer to the following guides for possible solutions:
* [Update billing information](https://developers.cloudflare.com/billing/update-billing-info/)
* [Resolve "Cannot remove payment method"](https://developers.cloudflare.com/billing/resolve-cannot-remove-payment-method/)
If the solutions above do not apply to you, we have observed reports of being unable to update or add payment methods within the dashboard. In these instances, you should [contact support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
## Cancellations
Cancellations are not processed until the end of the billing period. To understand more, refer to [Cancel Cloudflare subscriptions](https://developers.cloudflare.com/billing/cancel-subscription/).
## Non-refundable occurrences
In accordance with the Cloudflare Billing Policy, be aware that some [Non-Refundable occurrences](https://developers.cloudflare.com/billing/billing-policy/#non-refundable-occurrences) cannot be refunded and you should not contact support to request refunds for these.
---
title: Overview · Cloudflare bot solutions docs
description: While Cloudflare offers several products that relate to bot
traffic, this section reviews our bot-specific products, Bot Fight Mode, Super
Bot Fight Mode, and Bot Management for Enterprise.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/bots/
md: https://developers.cloudflare.com/bots/index.md
---
Identify and mitigate automated traffic to protect your domain from bad bots.
Available on all plans
While Cloudflare offers several products that relate to bot traffic, this section reviews our bot-specific products, Bot Fight Mode, Super Bot Fight Mode, and Bot Management for Enterprise.
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
## Which bot solution do I need?
If you have a smaller domain and have identified a bot problem, we recommend Bot Fight Mode or Super Bot Fight Mode, which are included with your plan subscription. You can enable either from your dashboard, but these solutions offer limited configuration options.
If you have a large domain with a lot of traffic, we recommend Bot Management for Enterprise, especially for customers in ecommerce, banking, and security. To enable Bot Management for Enterprise and write rules to customize your bot protection, contact your account team.
To see the differences in features and functionality, visit [Plans](https://developers.cloudflare.com/bots/plans/).
## Features
### Bot Fight Mode
Detect and mitigate bot traffic on your domain.
[Use Bot Fight Mode](https://developers.cloudflare.com/bots/get-started/bot-fight-mode/)
### Super Bot Fight Mode
Identify traffic matching patterns of known bots, challenge or block bots, protect static resources, and view analytics to help you understand bot traffic using Super Bot Fight Mode.
[Use Super Bot Fight Mode](https://developers.cloudflare.com/bots/get-started/super-bot-fight-mode/)
### Bot Analytics
Use Bot Analytics to dynamically examine bot traffic.
[Use Bot Analytics](https://developers.cloudflare.com/bots/bot-analytics/)
### Firewall variables
Access several new variables within the Firewall expression builder.
[Use Firewall variables](https://developers.cloudflare.com/bots/reference/bot-management-variables/)
## Related products
**[API Shield](https://developers.cloudflare.com/api-shield/)**
Identify and address API vulnerabilities using API Shield.
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Detect and mitigate Distributed Denial of Service (DDoS) attacks using Cloudflare's Autonomous Edge.
**[Turnstile](https://developers.cloudflare.com/turnstile/)**
Use Cloudflare's smart CAPTCHA alternative to run less intrusive challenges.
**[WAF](https://developers.cloudflare.com/waf/)**
Get automatic protection from vulnerabilities and the flexibility to create custom rules.
## More resources
[Plans](https://www.cloudflare.com/plans/#overview)
Compare available Cloudflare plans
---
title: Browser Rendering · Cloudflare Browser Rendering docs
description: Control headless browsers with Cloudflare's Workers Browser
Rendering API. Automate tasks, take screenshots, convert pages to PDFs, and
test web apps.
lastUpdated: 2026-01-22T01:35:34.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/
md: https://developers.cloudflare.com/browser-rendering/index.md
---
Run headless Chrome on [Cloudflare's global network](https://developers.cloudflare.com/workers/) for browser automation, web scraping, testing, and content generation.
Available on Free and Paid plans
Browser Rendering enables developers to programmatically control and interact with headless browser instances running on Cloudflare’s global network.
## Use cases
Programmatically load and fully render dynamic webpages or raw HTML and capture specific outputs such as:
* [Markdown](https://developers.cloudflare.com/browser-rendering/rest-api/markdown-endpoint/)
* [Screenshots](https://developers.cloudflare.com/browser-rendering/rest-api/screenshot-endpoint/)
* [PDFs](https://developers.cloudflare.com/browser-rendering/rest-api/pdf-endpoint/)
* [Snapshots](https://developers.cloudflare.com/browser-rendering/rest-api/snapshot/)
* [Links](https://developers.cloudflare.com/browser-rendering/rest-api/links-endpoint/)
* [HTML elements](https://developers.cloudflare.com/browser-rendering/rest-api/scrape-endpoint/)
* [Structured data](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/)
## Key features
* **Scale to thousands of browsers**: Instant access to a global pool of browsers with low cold-start time, ideal for high-volume screenshot generation, data extraction, or automation at scale
* **Global by default**: Browser sessions run on Cloudflare's edge network, opening close to your users for better speed and availability worldwide
* **Easy to integrate**: [REST APIs](https://developers.cloudflare.com/browser-rendering/rest-api/) for common actions, while [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/) and [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) provide familiar automation libraries for complex workflows
* **Session management**: [Reuse browser sessions](https://developers.cloudflare.com/browser-rendering/workers-bindings/reuse-sessions/) across requests to improve performance and reduce cold-start overhead
* **Flexible pricing**: Pay only for browser time used with generous free tier ([view pricing](https://developers.cloudflare.com/browser-rendering/pricing/))
## Integration methods
* **[REST API](https://developers.cloudflare.com/browser-rendering/rest-api/)**: Simple HTTP endpoints for stateless tasks like screenshots, PDFs, and scraping.
* **[Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/)**: Full browser automation within Workers using [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/), [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/), or [Stagehand](https://developers.cloudflare.com/browser-rendering/stagehand/).
| Use case | Recommended | Why |
| - | - | - |
| Simple screenshot, PDF, or scrape | [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) | No code deployment; single HTTP request |
| Browser automation | [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) | Full control with built-in tracing and assertions |
| Porting existing scripts | [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/) or [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) | Minimal code changes from standard libraries |
| AI-powered data extraction | [JSON endpoint](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/) | Structured data via natural language prompts |
| AI agent browsing | [Playwright MCP](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/) | LLMs control browsers via MCP |
| Resilient scraping | [Stagehand](https://developers.cloudflare.com/browser-rendering/stagehand/) | AI finds elements by intent, not selectors |
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Durable Objects](https://developers.cloudflare.com/durable-objects/)**
A globally distributed coordination API with strongly consistent storage. Using Durable Objects to [persist browser sessions](https://developers.cloudflare.com/browser-rendering/workers-bindings/browser-rendering-with-do/) improves performance by eliminating the time that it takes to spin up a new browser session.
**[Agents](https://developers.cloudflare.com/agents/)**
Build AI-powered agents that autonomously navigate websites and perform tasks using [Playwright MCP](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/) or [Stagehand](https://developers.cloudflare.com/browser-rendering/stagehand/).
## More resources
[Get started](https://developers.cloudflare.com/browser-rendering/get-started/)
Choose between REST API and Workers Bindings, then deploy your first project.
[Limits](https://developers.cloudflare.com/browser-rendering/limits/)
Learn about Browser Rendering limits.
[Pricing](https://developers.cloudflare.com/browser-rendering/pricing/)
Learn about Browser Rendering pricing.
[Playwright API](https://developers.cloudflare.com/browser-rendering/playwright/)
Use Cloudflare's fork of Playwright for testing and automation.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
---
title: Bringing Your Own IPs to Cloudflare · Cloudflare BYOIP docs
description: Get Cloudflare's security and performance while using your own IPs.
lastUpdated: 2025-11-21T18:29:21.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/
md: https://developers.cloudflare.com/byoip/index.md
---
Get Cloudflare's security and performance while using your own IPs.
Enterprise-only
Considering [how Cloudflare works as a reverse proxy](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/), for some customers it may be important to maintain this functionality while also keeping their website or application associated with their own public IP space (instead of Cloudflare's[1](#user-content-fn-1)).
With Bring Your Own IP (BYOIP), Cloudflare announces your IPs in all our locations. Use your IPs with [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Spectrum](https://developers.cloudflare.com/spectrum/), [CDN services](https://developers.cloudflare.com/cache/), or Gateway [DNS locations](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/) and [dedicated egress IPs](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/dedicated-egress-ips/).
Learn how to [get started](https://developers.cloudflare.com/byoip/get-started/).
***
## Features
### Service bindings
Control whether traffic destined for a given IP address is routed to Magic Transit, CDN, or Spectrum.
[Use Service bindings](https://developers.cloudflare.com/byoip/service-bindings/)
### Address maps
Specify which IP addresses should be mapped to DNS records when they are proxied through Cloudflare.
[Use Address maps](https://developers.cloudflare.com/byoip/address-maps/)
***
## More resources
[RPKI blog post](https://blog.cloudflare.com/rpki/)
An overview of BGP, RPKI, and other important aspects of Internet routing.
[Reference Architectures](https://developers.cloudflare.com/reference-architecture/)
Explore how you can leverage Cloudflare's platform to create solutions based on your business needs.
## Footnotes
1. Without BYOIP, when your domain's records are `proxied`, Cloudflare responds with a Cloudflare-owned [anycast IP address](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/). [↩](#user-content-fnref-1)
---
title: Cloudflare Cache · Cloudflare Cache (CDN) docs
description: Cache stores copies of frequently accessed content (such as images,
videos, or webpages) in geographically distributed data centers that are
located closer to end users than origin servers, reducing server load and
improving website performance.
lastUpdated: 2025-11-19T12:11:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cache/
md: https://developers.cloudflare.com/cache/index.md
---
Cache content across Cloudflare's global server network.
Available on all plans
Cache stores copies of frequently accessed content (such as images, videos, or webpages) in geographically distributed data centers that are located closer to end users than origin servers, reducing server load and improving website performance.
## Features
### Default cache behavior
Learn about default cache behavior, default cached file extensions and cache responses.
[Use Default cache behavior](https://developers.cloudflare.com/cache/concepts/default-cache-behavior/)
### Cache Rules
Configure Cache Rules to optimize your website by specifying which resources should be cached and for how long.
[Use Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
### Tiered Cache
Enable Tiered Cache to optimize content delivery by caching frequently accessed content in multiple locations for faster delivery and reduced origin traffic.
[Use Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/)
### Cache Reserve
Use Cloudflare's persistent storage to increase cache times.
[Use Cache Reserve](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/)
### Purge
Instantly purge cached files to force Cloudflare to fetch fresh versions from your web server files. You can purge specific files or all at once.
[Use Purge](https://developers.cloudflare.com/cache/how-to/purge-cache/)
***
## Related products
**[Load Balancing](https://developers.cloudflare.com/load-balancing/)**
Cloudflare Load Balancing distributes traffic across your endpoints, reducing endpoint strain and latency and improving the end users experience.
**[Images](https://developers.cloudflare.com/images/)**
A suite of products tailored to your image-processing needs.
**[Workers](https://developers.cloudflare.com/workers/)**
Cloudflare Workers allows developers to build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Rules](https://developers.cloudflare.com/rules/)**
Cloudflare Rules allows you to make adjustments to requests and responses, configure Cloudflare settings, and trigger specific actions for matching requests.
**[Cloudflare Network Interconnect](https://developers.cloudflare.com/network-interconnect/)**
Cloudflare Network Interconnect (CNI) allows you to connect your network infrastructure directly with Cloudflare – rather than using the public Internet – for a more reliable and secure experience.
**[R2](https://developers.cloudflare.com/r2/)**
Cloudflare R2 Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
**[Dedicated CDN Egress IPs](https://developers.cloudflare.com/smart-shield/configuration/dedicated-egress-ips/)**
Smart Shield Advanced provides dedicated egress IPs (from Cloudflare to your origin) for your layer 7 WAF and CDN services, as well as Spectrum.
***
## More resources
[Plans](https://www.cloudflare.com/cdn/)
Compare available Cloudflare plans
[Pricing](https://www.cloudflare.com/plans/#overview)
Explore pricing options for Cache
---
title: Overview · Cloudflare China Network docs
description: The Cloudflare China Network is a package of selected Cloudflare's
performance and security products running on data centers located in Mainland
China and operated by Cloudflare's partner JD Cloud.
lastUpdated: 2025-11-12T19:57:27.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/china-network/
md: https://developers.cloudflare.com/china-network/index.md
---
The [Cloudflare China Network](https://www.cloudflare.com/application-services/products/china-network/) is a package of selected Cloudflare's performance and security products running on data centers located in Mainland China and operated by Cloudflare's partner JD Cloud.
The data centers cover most populated regions in China. Combining Cloudflare's technological leadership and JD Cloud's local operations expertise, the Cloudflare China Network is designed to meet the needs for secure, reliable, and fast-performing content delivery in China. You can use the same configurations that you use with Cloudflare everywhere else in the world and with the same dashboard experience.
## Main features
The Cloudflare China Network provides:
* A single solution for both performance improvement and security services such as [WAF](https://developers.cloudflare.com/waf/), [DDoS](https://developers.cloudflare.com/ddos-protection/), and [bot management](https://developers.cloudflare.com/bots/).
* An unified experience for managing network traffic and security posture. You can manage all configurations on the same dashboard.
* The same customer support capabilities as Cloudflare's global network. You may also have access to premium service and local language support.
* [In-China Authoritative DNS and in-China nameservers](https://developers.cloudflare.com/china-network/concepts/china-dns/) to improve the Time to First Byte (TTFB) performance.
* [Global Acceleration](https://developers.cloudflare.com/china-network/concepts/global-acceleration/) is a suite of connectivity and performance offerings designed to simplify your global assets' deployment in China.
## Availability
The Cloudflare China Network is available as a separate subscription for customers on an [Enterprise plan](https://www.cloudflare.com/plans/enterprise/).
## Important notes
* Not all Cloudflare products are available in the Cloudflare China Network. Refer to [Available products and features](https://developers.cloudflare.com/china-network/reference/available-products/) for details.
* IPv6 support is mandatory for all Internet entities operating in Mainland China. The Cloudflare China Network feature automatically enables IPv6 for domains to fulfill this requirement.
* All the content inside of Mainland China is monitored by local authorities and must comply with local regulations.
* You must have a valid [ICP (Internet Content Provider) filing or license](https://developers.cloudflare.com/china-network/concepts/icp/) for each apex domain you wish to onboard to Cloudflare.
---
title: Client IP Geolocation · Cloudflare Client IP Geolocation docs
description: Cloudflare designed Cloudflare WARP and 1.1.1.1 to make Internet
browsing more private and secure. These applications encrypt last-mile
connections and make it more difficult for others to use client IP addresses
in user fingerprinting.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/client-ip-geolocation/
md: https://developers.cloudflare.com/client-ip-geolocation/index.md
---
Note
Client IP Geolocation is currently in closed Beta testing.
Cloudflare designed [Cloudflare WARP](https://developers.cloudflare.com/warp-client/) and [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/) to make Internet browsing more private and secure. These applications encrypt last-mile connections and make it more difficult for others to use client IP addresses in user fingerprinting.
However, unlike legacy VPN applications, we never designed WARP or 1.1.1.1 to hide user locations or allow users to misrepresent their true geographic location. As a web property operator, you can use **Client IP Geolocation** to map Cloudflare egress IP addresses to specific geolocations.
[Get started ](https://developers.cloudflare.com/client-ip-geolocation/get-started/)[Learn more](https://developers.cloudflare.com/client-ip-geolocation/about/)
Note
Client IP Geolocation is different from the [Cloudflare IP Geolocation setting](https://developers.cloudflare.com/network/ip-geolocation/), which helps you capture country codes for visitors.
---
title: Challenges · Cloudflare challenges docs
description: When a Challenge is issued, Cloudflare asks the browser to perform
a series of checks that help confirm the visitor's legitimacy. This process
involves evaluating client-side signals or asking a visitor to take minimal
action such as checking a box or selecting a button.
lastUpdated: 2025-06-24T17:41:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-challenges/
md: https://developers.cloudflare.com/cloudflare-challenges/index.md
---
Challenges are security mechanisms used by Cloudflare to verify whether a visitor to your site is a real human and not a bot or automated script.
When a Challenge is issued, Cloudflare asks the browser to perform a series of checks that help confirm the visitor's legitimacy. This process involves evaluating client-side signals or asking a visitor to take minimal action such as checking a box or selecting a button.
Challenges are designed to protect your application without introducing unnecessary friction. Most visitors will pass Challenges automatically without interaction.
Cloudflare does not use CAPTCHA puzzles or visual tests like selecting objects or typing distorted characters. All challenge types are lightweight, privacy-preserving, and optimized for real-world traffic.
***
## Related products
**[Turnstile](https://developers.cloudflare.com/turnstile/)**
Use Cloudflare's smart CAPTCHA alternative to run less intrusive Challenges.
**[Bots](https://developers.cloudflare.com/bots/)**
Cloudflare bot solutions identify and mitigate automated traffic to protect your domain from bad bots.
**[WAF](https://developers.cloudflare.com/waf/)**
Get automatic protection from vulnerabilities and the flexibility to create custom rules.
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Detect and mitigate Distributed Denial of Service (DDoS) attacks using Cloudflare's Autonomous Edge.
---
title: Cloudflare for Platforms · Cloudflare for Platforms docs
description: "Cloudflare for Platforms is used by leading platforms big and small to:"
lastUpdated: 2025-12-29T17:29:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-for-platforms/
md: https://developers.cloudflare.com/cloudflare-for-platforms/index.md
---
Build a platform where your customers can deploy code, each with their own subdomain or custom domain.
Cloudflare for Platforms is used by leading platforms big and small to:
* Build application development platforms tailored to specific domains, like ecommerce storefronts or mobile apps
* Power AI coding platforms that let anyone build and deploy software
* Customize product behavior by allowing any user to write a short code snippet
* Offer every customer their own isolated database
* Provide each customer with their own subdomain
***
## Deploy your own platform
Get a working platform running in minutes. Choose a template based on what you are building:
### Platform Starter Kit
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/worker-publisher-template)
An example of a platform where users can deploy code at scale. Each snippet becomes its own isolated Worker, served at `example.com/{app-name}`. Deploying this starter kit automatically configures Workers for Platforms with routing handled for you.
[View demo](https://worker-publisher-template.templates.workers.dev/)
[View on GitHub](https://github.com/cloudflare/templates/tree/main/worker-publisher-template)
### AI vibe coding platform
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/vibesdk)
Build an [AI vibe coding platform](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/) where users describe what they want and AI generates and deploys working applications. Best for: AI-powered app builders, code generation tools, or internal platforms that empower teams to build applications & prototypes.
[VibeSDK](https://github.com/cloudflare/vibesdk) handles AI code generation, code execution in secure sandboxes, live previews, and deployment at scale.
[View demo](https://build.cloudflare.dev/)
[View on GitHub](https://github.com/cloudflare/vibesdk)
***
## Features
* **Isolation and multitenancy** — Each of your customers runs code in their own Worker, a [secure and isolated sandbox](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/reference/worker-isolation/).
* **Programmable routing, ingress, egress, and limits** — You write code that dispatches requests to your customers' code, and can control [ingress](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/dynamic-dispatch/), [egress](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/outbound-workers/), and set [per-customer limits](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/custom-limits/).
* **Databases and storage** — You can provide [databases, object storage, and more](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/bindings/) to your customers as APIs they can call directly, without API tokens, keys, or external dependencies.
* **Custom domains and subdomains** — You [call an API](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/domain-support/) to create custom subdomains or configure custom domains for each of your customers.
To learn how these components work together, refer to [How Workers for Platforms works](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/).
---
title: Overview · Cloudflare One docs
description: Learn how to secure self-hosted and SaaS applications with
Cloudflare One. Configure a unified dashboard for seamless access and
security.
lastUpdated: 2025-10-30T21:17:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/
md: https://developers.cloudflare.com/cloudflare-one/index.md
---
Secure your organization with Cloudflare One — a cloud security platform that replaces legacy perimeters with Cloudflare's global network.
Available on all plans
Cloudflare One is a Secure Access Service Edge (SASE) platform that combines Zero Trust security and enterprise networking services.
By progressively adopting Cloudflare One, organizations can move away from a patchwork of hardware appliances and point solutions, and instead consolidate security and networking through a unified control plane that includes products like [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/), [Secure Web Gateway (SWG)](https://developers.cloudflare.com/cloudflare-one/traffic-policies/), [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/), [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/), [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/), [Cloud Access Security Broker (CASB)](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/), and [Email security](https://developers.cloudflare.com/cloudflare-one/email-security/).
Refer to our [SASE reference architecture](https://developers.cloudflare.com/reference-architecture/architectures/sase/) to learn how to plan, deploy, and manage SASE architecture with Cloudflare.
[Get started](https://developers.cloudflare.com/cloudflare-one/setup/)
[Cloudflare One dashboard](https://one.dash.cloudflare.com/)
[Implementation guides](https://developers.cloudflare.com/cloudflare-one/implementation-guides/)
## Products
**[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)**
Authenticate users accessing your applications, seamlessly onboard third-party users, and log every event and request.
**[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)**
Securely connect your resources to Cloudflare without exposing a public IP by using Cloudflare Tunnel, which establishes outbound-only connections from your infrastructure to Cloudflare's global network via the lightweight `cloudflared` daemon.
**[Secure Web Gateway (SWG)](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)**
Inspect and filter DNS, network, HTTP, and egress traffic to enforce your company's Acceptable Use Policy (UAP), block risky sites with custom blocklists and threat intelligence, and enhance visibility and protection across SaaS applications.
**[WARP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)**
Protect corporate devices by privately sending traffic from those devices to Cloudflare's global network, build device posture rules, and enforce security policies anywhere.
**[Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)**
Mitigate the impact of attacks by executing all browser code in the cloud and securely browse high-risk or sensitive websites in a remote browser.
**[Cloud Access Security Broker (CASB)](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)**
Protect users and sensitive data at rest in SaaS applications and cloud environments, scan for misconfigurations, and detect insider threats as well as unsanctioned application usage to prevent data leaks and compliance violations.
**[Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)**
Scan your web traffic and SaaS applications for the presence of sensitive data such as social security numbers, financial information, secret keys, and source code.
**[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)**
Configure policies to manage your inbox, automatically move emails based on disposition, and use screen criteria to investigate messages.
**[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/)**
Monitor device, network, and application performance across your Zero Trust organization.
***
## More resources
[SASE video series](https://developers.cloudflare.com/learning-paths/sase-overview-course/series/evolution-corporate-networks-1/)
New to Zero Trust and SASE? Get started with our introductory SASE video series.
[Reference architecture](https://developers.cloudflare.com/reference-architecture/architectures/sase/)
Explore our reference architecture to learn how to evolve your network and security architecture to Cloudflare One, our SASE platform.
[Plans](https://www.cloudflare.com/plans/zero-trust-services/)
Cloudflare Zero Trust offers both Free and Paid plans. Access to certain features depends on a customer's plan type.
[Limits](https://developers.cloudflare.com/cloudflare-one/account-limits/)
Learn about account limits. These limits may be increased on Enterprise accounts.
[Support](https://developers.cloudflare.com/support/contacting-cloudflare-support/)
Find answers to common questions or open a ticket with Cloudflare Support.
[Community](https://community.cloudflare.com/)
Ask questions, get answers, and share tips.
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
---
title: Constellation · Constellation docs
description: Constellation allows you to run fast, low-latency inference tasks
on pre-trained machine learning models natively on Cloudflare Workers. It
supports some of the most popular machine learning (ML) and AI runtimes and
multiple classes of models.
lastUpdated: 2024-08-15T18:30:43.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/constellation/
md: https://developers.cloudflare.com/constellation/index.md
---
Run machine learning models with Cloudflare Workers.
Constellation allows you to run fast, low-latency inference tasks on pre-trained machine learning models natively on Cloudflare Workers. It supports some of the most popular machine learning (ML) and AI runtimes and multiple classes of models.
Cloudflare provides a curated list of verified models, or you can train and upload your own.
Functionality you can deploy to your application with Constellation:
* Content generation, summarization, or similarity analysis
* Question answering
* Audio transcription
* Image or audio classification
* Object detection
* Anomaly detection
* Sentiment analysis
***
## More resources
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
---
title: Overview · Cloudflare Containers docs
description: Run code written in any programming language, built for any
runtime, as part of apps built on Workers.
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/
md: https://developers.cloudflare.com/containers/index.md
---
Enhance your Workers with serverless containers
Available on Workers Paid plan
Run code written in any programming language, built for any runtime, as part of apps built on [Workers](https://developers.cloudflare.com/workers).
Deploy your container image to Region:Earth without worrying about managing infrastructure - just define your Worker and [`wrangler deploy`](https://developers.cloudflare.com/workers/wrangler/commands/#deploy).
With Containers you can run:
* Resource-intensive applications that require CPU cores running in parallel, large amounts of memory or disk space
* Applications and libraries that require a full filesystem, specific runtime, or Linux-like environment
* Existing applications and tools that have been distributed as container images
Container instances are spun up on-demand and controlled by code you write in your [Worker](https://developers.cloudflare.com/workers). Instead of chaining together API calls or writing Kubernetes operators, you just write JavaScript:
* Worker Code
```js
import { Container, getContainer } from "@cloudflare/containers";
export class MyContainer extends Container {
defaultPort = 4000; // Port the container is listening on
sleepAfter = "10m"; // Stop the instance if requests not sent for 10 minutes
}
export default {
async fetch(request, env) {
const { "session-id": sessionId } = await request.json();
// Get the container instance for the given session ID
const containerInstance = getContainer(env.MY_CONTAINER, sessionId);
// Pass the request to the container instance on its default port
return containerInstance.fetch(request);
},
};
```
* Worker Config
* wrangler.jsonc
```jsonc
{
"name": "container-starter",
"main": "src/index.js",
"compatibility_date": "2026-02-07",
"containers": [
{
"class_name": "MyContainer",
"image": "./Dockerfile",
"max_instances": 5
}
],
"durable_objects": {
"bindings": [
{
"class_name": "MyContainer",
"name": "MY_CONTAINER"
}
]
},
"migrations": [
{
"new_sqlite_classes": ["MyContainer"],
"tag": "v1"
}
]
}
```
* wrangler.toml
```toml
name = "container-starter"
main = "src/index.js"
compatibility_date = "2026-02-07"
[[containers]]
class_name = "MyContainer"
image = "./Dockerfile"
max_instances = 5
[[durable_objects.bindings]]
class_name = "MyContainer"
name = "MY_CONTAINER"
[[migrations]]
new_sqlite_classes = [ "MyContainer" ]
tag = "v1"
```
* wrangler.jsonc
```jsonc
{
"name": "container-starter",
"main": "src/index.js",
"compatibility_date": "2026-02-07",
"containers": [
{
"class_name": "MyContainer",
"image": "./Dockerfile",
"max_instances": 5
}
],
"durable_objects": {
"bindings": [
{
"class_name": "MyContainer",
"name": "MY_CONTAINER"
}
]
},
"migrations": [
{
"new_sqlite_classes": ["MyContainer"],
"tag": "v1"
}
]
}
```
* wrangler.toml
```toml
name = "container-starter"
main = "src/index.js"
compatibility_date = "2026-02-07"
[[containers]]
class_name = "MyContainer"
image = "./Dockerfile"
max_instances = 5
[[durable_objects.bindings]]
class_name = "MyContainer"
name = "MY_CONTAINER"
[[migrations]]
new_sqlite_classes = [ "MyContainer" ]
tag = "v1"
```
[Get started](https://developers.cloudflare.com/containers/get-started/)
[Containers dashboard](https://dash.cloudflare.com/?to=/:account/workers/containers)
***
## Next Steps
### Deploy your first Container
Build and push an image, call a Container from a Worker, and understand scaling and routing.
[Deploy a Container](https://developers.cloudflare.com/containers/get-started/)
### Container Examples
See examples of how to use a Container with a Worker, including stateless and stateful routing, regional placement, Workflow and Queue integrations, AI-generated code execution, and short-lived workloads.
[See Examples](https://developers.cloudflare.com/containers/examples/)
***
## More resources
[Beta Information](https://developers.cloudflare.com/containers/beta-info/)
Learn about the Containers Beta and upcoming features.
[Wrangler](https://developers.cloudflare.com/workers/wrangler/commands/#containers)
Learn more about the commands to develop, build and push images, and deploy containers with Wrangler.
[Limits](https://developers.cloudflare.com/containers/platform-details/#limits)
Learn about what limits Containers have and how to work within them.
[Containers Discord](https://discord.cloudflare.com)
Connect with other users of Containers on Discord. Ask questions, show what you are building, and discuss the platform with other developers.
---
title: Overview · Cloudflare D1 docs
description: D1 is Cloudflare's managed, serverless database with SQLite's SQL
semantics, built-in disaster recovery, and Worker and HTTP API access.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/
md: https://developers.cloudflare.com/d1/index.md
---
Create new serverless SQL databases to query from your Workers and Pages projects.
Available on Free and Paid plans
D1 is Cloudflare's managed, serverless database with SQLite's SQL semantics, built-in disaster recovery, and Worker and HTTP API access.
D1 is designed for horizontal scale out across multiple, smaller (10 GB) databases, such as per-user, per-tenant or per-entity databases. D1 allows you to build applications with thousands of databases at no extra cost for isolating with multiple databases. D1 pricing is based only on query and storage costs.
Create your first D1 database by [following the Get started guide](https://developers.cloudflare.com/d1/get-started/), learn how to [import data into a database](https://developers.cloudflare.com/d1/best-practices/import-export-data/), and how to [interact with your database](https://developers.cloudflare.com/d1/worker-api/) directly from [Workers](https://developers.cloudflare.com/workers/) or [Pages](https://developers.cloudflare.com/pages/functions/bindings/#d1-databases).
***
## Features
### Create your first D1 database
Create your first D1 database, establish a schema, import data and query D1 directly from an application [built with Workers](https://developers.cloudflare.com/workers/).
[Create your D1 database](https://developers.cloudflare.com/d1/get-started/)
### SQLite
Execute SQL with SQLite's SQL compatibility and D1 Client API.
[Execute SQL queries](https://developers.cloudflare.com/d1/sql-api/sql-statements/)
### Time Travel
Time Travel is D1’s approach to backups and point-in-time-recovery, and allows you to restore a database to any minute within the last 30 days.
[Learn about Time Travel](https://developers.cloudflare.com/d1/reference/time-travel/)
***
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Pages](https://developers.cloudflare.com/pages/)**
Deploy dynamic front-end applications in record time.
***
## More resources
[Pricing](https://developers.cloudflare.com/d1/platform/pricing/)
Learn about D1's pricing and how to estimate your usage.
[Limits](https://developers.cloudflare.com/d1/platform/limits/)
Learn about what limits D1 has and how to work within them.
[Community projects](https://developers.cloudflare.com/d1/reference/community-projects/)
Browse what developers are building with D1.
[Storage options](https://developers.cloudflare.com/workers/platform/storage-options/)
Learn more about the storage and database options you can build on with Workers.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Developer Platform.
---
title: Data Localization Suite · Cloudflare Data Localization Suite docs
description: The Data Localization Suite (DLS) is a collection of tools that
enable customers to choose the location where Cloudflare inspects and stores
data, while maintaining the security and performance benefits of our global
network.
lastUpdated: 2025-02-07T17:34:35.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/
md: https://developers.cloudflare.com/data-localization/index.md
---
Enterprise-only paid add-on
The Data Localization Suite (DLS) is a collection of tools that enable customers to choose the location where Cloudflare inspects and stores data, while maintaining the security and performance benefits of our global network.
***
## Features
### Geo Key Manager
Keep your keys within a specified region, ensuring compliance and data sovereignty.
[Use Geo Key Manager](https://developers.cloudflare.com/data-localization/geo-key-manager/)
### Customer Metadata Boundary
Ensure that any traffic metadata that can identify your end user stays in the region you selected.
[Use Customer Metadata Boundary](https://developers.cloudflare.com/data-localization/metadata-boundary/)
### Regional Services
Comply with regional restrictions by choosing which subset of data centers decrypts and services your HTTPS traffic.
[Use Regional Services](https://developers.cloudflare.com/data-localization/regional-services/)
***
## Related products
**[SSL/TLS](https://developers.cloudflare.com/ssl/)**
Cloudflare SSL/TLS encrypts your web traffic to prevent data theft and other tampering.
**[DNS](https://developers.cloudflare.com/dns/)**
Cloudflare's global DNS platform provides speed and resilience. DNS customers also benefit from free DNSSEC, and protection against route leaks and hijacking.
***
## More resources
[Resource hub](https://www.cloudflare.com/resource-hub/?topic=Privacy)
Refer to our latest resources to learn more about privacy.
[Cloudflare blog](https://blog.cloudflare.com/tag/data-localization-suite)
Read articles about the latest updates to the Data Localization Suite.
---
title: Overview · Cloudflare DDoS Protection docs
description: Cloudflare automatically detects and mitigates distributed
denial-of-service (DDoS) attacks via our autonomous DDoS systems.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/
md: https://developers.cloudflare.com/ddos-protection/index.md
---
Detect and mitigate distributed denial-of-service (DDoS) attacks automatically.
Available on all plans
Cloudflare automatically detects and mitigates [distributed denial-of-service (DDoS) attacks](https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/) via our autonomous DDoS systems.
These systems include multiple dynamic mitigation rules exposed as [DDoS attack protection managed rulesets](https://developers.cloudflare.com/ddos-protection/managed-rulesets/). You can customize the mitigation rules included in these rulesets to optimize and tailor the protection to your needs.
***
## Features
### Managed rulesets
Protect against a variety of DDoS attacks across layers 3/4 (network layer) and layer 7 (application layer) of the OSI model.
[Use Managed rulesets](https://developers.cloudflare.com/ddos-protection/managed-rulesets/)
### Adaptive DDoS protection
Get increased protection against sophisticated DDoS attacks on layer 7 and layers 3/4.
[Use Adaptive DDoS protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/adaptive-protection/)
### Advanced TCP protection
Detect and mitigate sophisticated out-of-state TCP attacks such as randomized and spoofed ACK floods, or SYN and SYN-ACK floods.
[Use Advanced TCP protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-tcp-protection/)
### Advanced DNS protection
Protect against DNS-based DDoS attacks, specifically sophisticated and fully randomized DNS attacks such as random prefix attacks.
[Use Advanced DNS protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-dns-protection/)
***
## Availability
| | Free | Pro | Business | Enterprise | Enterprise with Advanced DDoS Protection add-on |
| - | - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes | Yes |
| Standard, unmetered DDoS protection (layers 3-7) | Yes | Yes | Yes | Yes | Yes |
| HTTP DDoS attack protection | Yes | Yes | Yes | Yes | Yes |
| Network-layer (L3/4) DDoS attack protection | Yes | Yes | Yes | Yes | Yes |
| Managed rules customization | Yes | Yes | Yes | Yes, with Log action | Expression fields & multi-rule support |
| Proactive false positive detection for new rules | No | No | No | Yes | Yes |
| Adaptive DDoS protection | Only error adaptive rules | Only error adaptive rules | Only error adaptive rules | Only error adaptive rules | All adaptive rules |
| Traffic profiling signals for adaptive DDoS protection | Error rates only | Error rates only | Error rates & historical trends | Error rates & historical trends | Error rates & historical trends, client country, user agent, query string, ML-scores |
| Advanced TCP Protection | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers |
| Advanced DNS Protection | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers | Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers |
| Number of ruleset overrides allowed | 1 | 1 | 1 | 1 | 10 |
| Alerts | Yes | Yes | Yes | Yes | Advanced alerts with filtering |
***
## Related products
**[Spectrum](https://developers.cloudflare.com/spectrum/)**
Provides security and acceleration for any TCP or UDP based application.
**[Magic Transit](https://developers.cloudflare.com/magic-transit/)**
A network security and performance solution that offers DDoS protection, traffic acceleration, and more for on-premise, cloud-hosted, and hybrid networks.
**[Web Application Firewall (WAF)](https://developers.cloudflare.com/waf/)**
Get automatic protection from vulnerabilities and the flexibility to create custom rules.
---
title: Docs directory | Cloudflare Docs
description: Explore the different areas of our documentation site.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/directory/
md: https://developers.cloudflare.com/directory/index.md
---
Groups
[1](https://developers.cloudflare.com/1.1.1.1/)
[1.1.1.1](https://developers.cloudflare.com/1.1.1.1/)
[A blazing fast DNS resolver built for private browsing](https://developers.cloudflare.com/1.1.1.1/)
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Determine who can reach your application using policies](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[A](https://developers.cloudflare.com/fundamentals/account/)
[Account](https://developers.cloudflare.com/fundamentals/account/)
[Manage your Cloudflare account and contacts](https://developers.cloudflare.com/fundamentals/account/)
[Agents](https://developers.cloudflare.com/agents/)
[Build AI-powered agents to perform tasks, persist state, browse the web, and communicate in real-time](https://developers.cloudflare.com/agents/)
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
[Analyze and control third-party AI crawlers in your website](https://developers.cloudflare.com/ai-crawl-control/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
[Observe and control your AI applications](https://developers.cloudflare.com/ai-gateway/)
[AI Search](https://developers.cloudflare.com/ai-search/)
[Create fully managed RAG pipelines for your AI applications](https://developers.cloudflare.com/ai-search/)
[Analytics](https://developers.cloudflare.com/analytics/)
[Visualize the performance, security, and reliability data collected by Cloudflare products](https://developers.cloudflare.com/analytics/)
[API documentation](https://developers.cloudflare.com/api/)
[Cloudflare's API tokens allow you to make calls to our API to alter different settings](https://developers.cloudflare.com/api/)
[API Shield](https://developers.cloudflare.com/api-shield/)
[Identify and address your API vulnerabilities](https://developers.cloudflare.com/api-shield/)
[Argo Smart Routing](https://developers.cloudflare.com/argo-smart-routing/)
[Route web traffic across the fastest, most reliable network paths](https://developers.cloudflare.com/argo-smart-routing/)
[Automatic Platform Optimization](https://developers.cloudflare.com/automatic-platform-optimization/)
[Improve WordPress site performance by serving it from Cloudflare's global network](https://developers.cloudflare.com/automatic-platform-optimization/)
[Billing](https://developers.cloudflare.com/billing/)
[Manage billing, plans, and subscriptions for your account](https://developers.cloudflare.com/billing/)
[Bots](https://developers.cloudflare.com/bots/)
[Protect your domain from bad bot traffic](https://developers.cloudflare.com/bots/)
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
[Execute active webpage content in a secure, isolated browser](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
[Control and interact with headless browser instances programmatically](https://developers.cloudflare.com/browser-rendering/)
[BYOIP](https://developers.cloudflare.com/byoip/)
[Get Cloudflare's security and performance while using your own IPs](https://developers.cloudflare.com/byoip/)
[Cache](https://developers.cloudflare.com/cache/)
[Make websites faster by caching content across our global server network](https://developers.cloudflare.com/cache/)
[C](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/)
[Cache Reserve](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/)
[Cache your website content on a persistent data store](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/)
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
[Scan SaaS applications and cloud environments for data security issues](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
[China Network](https://developers.cloudflare.com/china-network/)
[Fast, global network serving visitors inside and outside of China](https://developers.cloudflare.com/china-network/)
[Challenges](https://developers.cloudflare.com/cloudflare-challenges/)
[Verify visitors are not bots with lightweight challenges](https://developers.cloudflare.com/cloudflare-challenges/)
[Cloudflare for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/)
[Build your own multi-tenant platform using Cloudflare as infrastructure](https://developers.cloudflare.com/cloudflare-for-platforms/)
[C](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)
[Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)
[Extend Cloudflare's security and performance to your customers](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
[Replace legacy security perimeters with Cloudflare's network to protect your organization](https://developers.cloudflare.com/cloudflare-one/)
[C](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
[Securely connect resources to Cloudflare without a publicly routable IP address](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
[Containers](https://developers.cloudflare.com/containers/)
[Enhance your Workers with serverless containers](https://developers.cloudflare.com/containers/)
[D1](https://developers.cloudflare.com/d1/)
[Create managed, serverless databases with SQL semantics](https://developers.cloudflare.com/d1/)
[Data Localization Suite](https://developers.cloudflare.com/data-localization/)
[Control where Cloudflare stores and inspects data](https://developers.cloudflare.com/data-localization/)
[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)
[Protect against DDoS attacks automatically with uncompromised performance](https://developers.cloudflare.com/ddos-protection/)
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[Monitor device, network, and application health across your Zero Trust organization](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[D](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
[Scan your web traffic and SaaS applications for sensitive data](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
[DMARC Management](https://developers.cloudflare.com/dmarc-management/)
[Protect your email domain and stop brand impersonation](https://developers.cloudflare.com/dmarc-management/)
[DNS](https://developers.cloudflare.com/dns/)
[Deliver excellent performance and reliability to your domain](https://developers.cloudflare.com/dns/)
[D](https://developers.cloudflare.com/dns/dns-firewall/)
[DNS Firewall](https://developers.cloudflare.com/dns/dns-firewall/)
[Speed up and protect entire authoritative nameservers](https://developers.cloudflare.com/dns/dns-firewall/)
[Durable Objects](https://developers.cloudflare.com/durable-objects/)
[A special kind of Cloudflare Worker combining compute with storage](https://developers.cloudflare.com/durable-objects/)
[Email Routing](https://developers.cloudflare.com/email-routing/)
[Create and manage email addresses and route to your preferred inbox](https://developers.cloudflare.com/email-routing/)
[E](https://developers.cloudflare.com/cloudflare-one/email-security/)
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
[Protect your email, web, and network from phishing and malware attacks](https://developers.cloudflare.com/cloudflare-one/email-security/)
[F](https://developers.cloudflare.com/bots/additional-configurations/sequence-rules/)
[Fraud Detection](https://developers.cloudflare.com/bots/additional-configurations/sequence-rules/)
[Sequence rules use cookies to track the order and timing of requests](https://developers.cloudflare.com/bots/additional-configurations/sequence-rules/)
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
[Learn about using Cloudflare and features that span across Cloudflare products](https://developers.cloudflare.com/fundamentals/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
[Set up policies to inspect DNS, Network, HTTP, and Egress traffic](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
[G](https://developers.cloudflare.com/ssl/edge-certificates/geokey-manager/)
[Geo Key Manager](https://developers.cloudflare.com/ssl/edge-certificates/geokey-manager/)
[Control SSL/TLS key storage for compliance and security](https://developers.cloudflare.com/ssl/edge-certificates/geokey-manager/)
[Google tag gateway for advertisers](https://developers.cloudflare.com/google-tag-gateway/)
[Add a layer of data security and privacy controls when using Google Tag Manager](https://developers.cloudflare.com/google-tag-gateway/)
[G](https://developers.cloudflare.com/analytics/graphql-api/)
[GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/)
[Access data on HTTP requests and Cloudflare products](https://developers.cloudflare.com/analytics/graphql-api/)
[Health Checks](https://developers.cloudflare.com/health-checks/)
[Monitor IPs or hostnames and get notified of issues](https://developers.cloudflare.com/health-checks/)
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
[Accelerate database queries to make databases fast globally](https://developers.cloudflare.com/hyperdrive/)
[Cloudflare Images](https://developers.cloudflare.com/images/)
[Store, transform, optimize, and deliver images at scale](https://developers.cloudflare.com/images/)
[I](https://developers.cloudflare.com/dns/internal-dns/)
[Internal DNS](https://developers.cloudflare.com/dns/internal-dns/)
[Simplify private network management with Cloudflare DNS for internal resources](https://developers.cloudflare.com/dns/internal-dns/)
[Key Transparency Auditor](https://developers.cloudflare.com/key-transparency/)
[Secure the distribution of public keys in E2EE messaging systems](https://developers.cloudflare.com/key-transparency/)
[K](https://developers.cloudflare.com/ssl/keyless-ssl/)
[Keyless SSL](https://developers.cloudflare.com/ssl/keyless-ssl/)
[Use Cloudflare SSL while keeping exclusive access to your private keys](https://developers.cloudflare.com/ssl/keyless-ssl/)
[KV](https://developers.cloudflare.com/kv/)
[Global, low-latency, key-value data storage](https://developers.cloudflare.com/kv/)
[L](https://developers.cloudflare.com/waf/detections/leaked-credentials/)
[Leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/)
[Detect previously leaked credentials in incoming requests](https://developers.cloudflare.com/waf/detections/leaked-credentials/)
[Learning Paths](https://developers.cloudflare.com/learning-paths/)
[Guided modules and projects to help you get started with Cloudflare](https://developers.cloudflare.com/learning-paths/)
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
[Maximize application performance and availability](https://developers.cloudflare.com/load-balancing/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
[Store and explore your logs in the Cloudflare dashboard or API](https://developers.cloudflare.com/log-explorer/)
[Logs](https://developers.cloudflare.com/logs/)
[Access detailed logs with metadata from Cloudflare products](https://developers.cloudflare.com/logs/)
[Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/)
[Automate resource discovery and simplify managing your public cloud infrastructure](https://developers.cloudflare.com/magic-cloud-networking/)
[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
[Protect your enterprise network with advanced firewall-as-a-service protection](https://developers.cloudflare.com/magic-firewall/)
[Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/)
[Visibility into your network and cloud traffic by analyzing network flow data](https://developers.cloudflare.com/magic-network-monitoring/)
[Magic Transit](https://developers.cloudflare.com/magic-transit/)
[Network functions at Cloudflare scale for on-premise, cloud-hosted, and hybrid networks](https://developers.cloudflare.com/magic-transit/)
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
[Replace legacy WAN and securely connect any traffic source to Cloudflare's network](https://developers.cloudflare.com/magic-wan/)
[MoQ](https://developers.cloudflare.com/moq/)
[Protocol for live media](https://developers.cloudflare.com/moq/)
[Network](https://developers.cloudflare.com/network/)
[Manage Cloudflare network settings for your website](https://developers.cloudflare.com/network/)
[Network Error Logging](https://developers.cloudflare.com/network-error-logging/)
[Review connectivity issues to learn when and where an incident is happening and its impact](https://developers.cloudflare.com/network-error-logging/)
[Network Interconnect](https://developers.cloudflare.com/network-interconnect/)
[Faster, more reliable, and more secure than connecting over the Internet](https://developers.cloudflare.com/network-interconnect/)
[Notifications](https://developers.cloudflare.com/notifications/)
[Define what you want to be notified about and how](https://developers.cloudflare.com/notifications/)
[Page Shield](https://developers.cloudflare.com/page-shield/)
[Provide client-side protection for your website visitors](https://developers.cloudflare.com/page-shield/)
[Pages](https://developers.cloudflare.com/pages/)
[Build full-stack, serverless applications globally with minimal configuration](https://developers.cloudflare.com/pages/)
[Pipelines](https://developers.cloudflare.com/pipelines/)
[Ingest real time data streams and load into R2](https://developers.cloudflare.com/pipelines/)
[Privacy Gateway](https://developers.cloudflare.com/privacy-gateway/)
[Implement the Oblivious HTTP IETF standard to improve client privacy](https://developers.cloudflare.com/privacy-gateway/)
[Privacy Proxy](https://developers.cloudflare.com/privacy-proxy/)
[A MASQUE-based forward proxy that protects user privacy while preserving geolocation accuracy](https://developers.cloudflare.com/privacy-proxy/)
[Pulumi](https://developers.cloudflare.com/pulumi/)
[Create, deploy, and manage Cloudflare resources in various programming languages](https://developers.cloudflare.com/pulumi/)
[Queues](https://developers.cloudflare.com/queues/)
[Reliably send and receive messages without the egress fees](https://developers.cloudflare.com/queues/)
[R2](https://developers.cloudflare.com/r2/)
[Store large amounts of unstructured data without egress fees](https://developers.cloudflare.com/r2/)
[R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/)
[Create, manage, and query Iceberg tables stored in R2](https://developers.cloudflare.com/r2/data-catalog/)
[R2 SQL](https://developers.cloudflare.com/r2-sql/)
[Cloudflare's serverless, distributed query engine for data stored in R2 Data Catalog](https://developers.cloudflare.com/r2-sql/)
[Radar](https://developers.cloudflare.com/radar/)
[Investigate Internet usage around the world using Cloudflare's data](https://developers.cloudflare.com/radar/)
[Randomness Beacon](https://developers.cloudflare.com/randomness-beacon/)
[Explore drand, a distributed service providing randomness to applications](https://developers.cloudflare.com/randomness-beacon/)
[R](https://developers.cloudflare.com/waf/rate-limiting-rules/)
[Rate limiting](https://developers.cloudflare.com/waf/rate-limiting-rules/)
[Control the rate of incoming requests matching an expression](https://developers.cloudflare.com/waf/rate-limiting-rules/)
[Realtime](https://developers.cloudflare.com/realtime/)
[RealtimeKit, SFU and TURN](https://developers.cloudflare.com/realtime/)
[RealtimeKit](https://developers.cloudflare.com/realtime/realtimekit/)
[SDKs and APIs to build real-time applications with lowest latency at any scale](https://developers.cloudflare.com/realtime/realtimekit/)
[Realtime SFU](https://developers.cloudflare.com/realtime/sfu/)
[Infrastructure for real-time serverless video, audio, and data applications](https://developers.cloudflare.com/realtime/sfu/)
[TURN Service](https://developers.cloudflare.com/realtime/turn/)
[Ensure connectivity with a relay point for traffic between WebRTC clients](https://developers.cloudflare.com/realtime/turn/)
[Reference Architecture](https://developers.cloudflare.com/reference-architecture/)
[Guides and diagrams explain Cloudflare products and how to integrate with IT architectures](https://developers.cloudflare.com/reference-architecture/)
[Registrar](https://developers.cloudflare.com/registrar/)
[Buy and renew your domain at cost, add another layer of security to your DNS records for free](https://developers.cloudflare.com/registrar/)
[Rules](https://developers.cloudflare.com/rules/)
[Modify incoming requests, change Cloudflare settings, or trigger actions](https://developers.cloudflare.com/rules/)
[Ruleset Engine](https://developers.cloudflare.com/ruleset-engine/)
[Create rulesets and rules for different Cloudflare products](https://developers.cloudflare.com/ruleset-engine/)
[Sandbox SDK](https://developers.cloudflare.com/sandbox/)
[Build secure, isolated code execution environments](https://developers.cloudflare.com/sandbox/)
[S](https://developers.cloudflare.com/sdk/)
[SDK](https://developers.cloudflare.com/sdk/)
[Language software development kits (SDKs) to interact with the Cloudflare API in language-specific syntax](https://developers.cloudflare.com/sdk/)
[Secrets Store](https://developers.cloudflare.com/secrets-store/)
[Encrypt and store sensitive information as secrets that are securely reusable across an account](https://developers.cloudflare.com/secrets-store/)
[Security Center](https://developers.cloudflare.com/security-center/)
[Enhance your security posture with a range of security products and one-click solutions](https://developers.cloudflare.com/security-center/)
[Smart Shield](https://developers.cloudflare.com/smart-shield/)
[Safeguard your origin with just a few clicks.](https://developers.cloudflare.com/smart-shield/)
[Spectrum](https://developers.cloudflare.com/spectrum/)
[Secure and accelerate any TCP or UDP-based application](https://developers.cloudflare.com/spectrum/)
[Speed](https://developers.cloudflare.com/speed/)
[Improve the performance of your website or web application](https://developers.cloudflare.com/speed/)
[SSL/TLS](https://developers.cloudflare.com/ssl/)
[Encrypt your web traffic to prevent data theft and other tampering](https://developers.cloudflare.com/ssl/)
[Stream](https://developers.cloudflare.com/stream/)
[Store, encode, deliver, and play videos on sites and applications](https://developers.cloudflare.com/stream/)
[Support](https://developers.cloudflare.com/support/)
[Cloudflare Support-focused documentation](https://developers.cloudflare.com/support/)
[Tenant](https://developers.cloudflare.com/tenant/)
[Provision and manage Cloudflare accounts and services for your team or customers](https://developers.cloudflare.com/tenant/)
[Terraform](https://developers.cloudflare.com/terraform/)
[Define and store Cloudflare configurations in source code repositories like GitHub](https://developers.cloudflare.com/terraform/)
[Time Services](https://developers.cloudflare.com/time-services/)
[Cloudflare's suite of time services: NTP, NTS, and Roughtime](https://developers.cloudflare.com/time-services/)
[Turnstile](https://developers.cloudflare.com/turnstile/)
[Turnstile is Cloudflare's smart CAPTCHA alternative](https://developers.cloudflare.com/turnstile/)
[Vectorize](https://developers.cloudflare.com/vectorize/)
[Store, query, and manage high-dimensional vector databases](https://developers.cloudflare.com/vectorize/)
[Version Management](https://developers.cloudflare.com/version-management/)
[Safely manage configurations on Cloudflare's global network with versioning, staging, and rollbacks](https://developers.cloudflare.com/version-management/)
[WAF](https://developers.cloudflare.com/waf/)
[Filter incoming traffic and protect against web app vulnerabilities](https://developers.cloudflare.com/waf/)
[Waiting Room](https://developers.cloudflare.com/waiting-room/)
[Create a virtual waiting room to manage peak traffic](https://developers.cloudflare.com/waiting-room/)
[WARP Client](https://developers.cloudflare.com/warp-client/)
[Allows individuals or organizations to have a faster, more secure connection to the Internet](https://developers.cloudflare.com/warp-client/)
[Cloudflare Web Analytics](https://developers.cloudflare.com/web-analytics/)
[Get vital web analytics for your website](https://developers.cloudflare.com/web-analytics/)
[Web3](https://developers.cloudflare.com/web3/)
[Gateways to networks to help you develop applications without worrying about running infrastructure](https://developers.cloudflare.com/web3/)
[Workers](https://developers.cloudflare.com/workers/)
[Build, deploy, and scale serverless applications globally with low latency and minimal configuration](https://developers.cloudflare.com/workers/)
[Workers AI](https://developers.cloudflare.com/workers-ai/)
[Run AI models in Workers, Pages, or via API](https://developers.cloudflare.com/workers-ai/)
[W](https://developers.cloudflare.com/analytics/analytics-engine/)
[Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/)
[Unlimited-cardinality analytics at scale via an API to write data from Workers and a SQL API to query that data](https://developers.cloudflare.com/analytics/analytics-engine/)
[W](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
[Deploy custom code for your users or let them directly deploy code to your platform](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
[Workers VPC](https://developers.cloudflare.com/workers-vpc/)
[Connect Cloudflare Worker's Virtual Private Cloud to your private clouds to build cross-cloud apps.](https://developers.cloudflare.com/workers-vpc/)
[Workflows](https://developers.cloudflare.com/workflows/)
[Build durable, multi-step applications using the Workers platform](https://developers.cloudflare.com/workflows/)
[Zaraz](https://developers.cloudflare.com/zaraz/)
[Run third-party tools and services on the cloud for improved speed and security](https://developers.cloudflare.com/zaraz/)
[Z](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
[Connect corporate devices to your Zero Trust organization](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
---
title: Overview · Cloudflare DMARC Management docs
description: Stop brand impersonation.
lastUpdated: 2026-02-03T18:17:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dmarc-management/
md: https://developers.cloudflare.com/dmarc-management/index.md
---
Stop brand impersonation.
Available on all plans
Cloudflare DMARC Management helps you track every source that is sending emails from your domain and review [Domain-based Message Authentication Reporting and Conformance (DMARC)](https://www.cloudflare.com/learning/dns/dns-records/dns-dmarc-record/) reports for each source. DMARC reports will help you understand if messages sent from your domain are passing DMARC authentication, [DomainKeys Identified Mail (DKIM)](https://www.cloudflare.com/learning/dns/dns-records/dns-dkim-record/) authentication, and [Sender Policy Framework (SPF)](https://www.cloudflare.com/learning/dns/dns-records/dns-spf-record/) policies.
Note
DMARC Management is available to all Cloudflare customers with [Cloudflare DNS](https://developers.cloudflare.com/dns/).
***
## Related products
**[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)**
Protect your email inbox with Email security.
**[Cloudflare DNS](https://developers.cloudflare.com/dns/)**
Fast, resilient and easy-to-manage DNS service.
---
title: Cloudflare DNS · Cloudflare DNS docs
description: Cloudflare DNS is a fast, resilient, and easy-to-manage
authoritative DNS service. It delivers excellent performance and reliability
to your domain while also protecting your business from DDoS attacks and route
leaks and hijacking. To know where to begin, refer to Get started.
lastUpdated: 2025-12-12T11:59:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/
md: https://developers.cloudflare.com/dns/index.md
---
Leverage Cloudflare's global network to deliver excellent performance and reliability to your domain.
Available on all plans
Cloudflare DNS is a fast, resilient, and easy-to-manage authoritative DNS service. It delivers excellent performance and reliability to your domain while also protecting your business from [DDoS attacks](https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/) and [route leaks and hijacking](https://www.cloudflare.com/learning/security/glossary/bgp-hijacking/). To know where to begin, refer to [Get started](https://developers.cloudflare.com/dns/get-started/).
Enterprise customers can also use Cloudflare DNS for their private network with [Internal DNS (Beta)](https://developers.cloudflare.com/dns/internal-dns/).
***
## Features
### DNS records
DNS records make resources available on your domain, and allow you to configure services such as email.
[Use DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/)
### DNSSEC
DNS Security Extensions (DNSSEC) adds cryptographic signatures to your DNS records, preventing anyone else from redirecting traffic intended for your domain.
Cloudflare also supports [Multi-signer DNSSEC](https://developers.cloudflare.com/dns/dnssec/multi-signer-dnssec/).
[Use DNSSEC](https://developers.cloudflare.com/dns/dnssec/)
### CNAME flattening
CNAME flattening delivers better performance and allows you to add a CNAME record at your apex domain (`example.com`). Paid accounts can choose to flatten all CNAME records on their domain.
[Use CNAME flattening](https://developers.cloudflare.com/dns/cname-flattening/)
Refer to [DNS features and availability](https://developers.cloudflare.com/dns/reference/all-features/) for a complete list of features and their availability according to different Cloudflare plans.
***
## Related products
**[Registrar](https://developers.cloudflare.com/registrar/)**
Before you can start using Cloudflare DNS you must first have a domain. Buy and renew your domain at cost with Cloudflare Registrar.
**[DNS Resolver](https://developers.cloudflare.com/1.1.1.1/)**
Cloudflare DNS focuses on businesses and their domain administration. If you are a consumer and want a more private way to browse the Internet, check out 1.1.1.1, Cloudflare's public DNS Resolver.
---
title: Overview · Cloudflare Durable Objects docs
description: Durable Objects provide a building block for stateful applications
and distributed systems.
lastUpdated: 2026-01-06T18:52:43.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/
md: https://developers.cloudflare.com/durable-objects/index.md
---
Create AI agents, collaborative applications, real-time interactions like chat, and more without needing to coordinate state, have separate storage, or manage infrastructure.
Available on Free and Paid plans
Durable Objects provide a building block for stateful applications and distributed systems.
Use Durable Objects to build applications that need coordination among multiple clients, like collaborative editing tools, interactive chat, multiplayer games, live notifications, and deep distributed systems, without requiring you to build serialization and coordination primitives on your own.
[Get started](https://developers.cloudflare.com/durable-objects/get-started/)
Note
SQLite-backed Durable Objects are now available on the Workers Free plan with these [limits](https://developers.cloudflare.com/durable-objects/platform/pricing/).
[SQLite storage](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/) and corresponding [Storage API](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/) methods like `sql.exec` have moved from beta to general availability. New Durable Object classes should use wrangler configuration for [SQLite storage](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#wrangler-configuration-for-sqlite-durable-objects).
### What are Durable Objects?
A Durable Object is a special kind of [Cloudflare Worker](https://developers.cloudflare.com/workers/) which uniquely combines compute with storage. Like a Worker, a Durable Object is automatically provisioned geographically close to where it is first requested, starts up quickly when needed, and shuts down when idle. You can have millions of them around the world. However, unlike regular Workers:
* Each Durable Object has a **globally-unique name**, which allows you to send requests to a specific object from anywhere in the world. Thus, a Durable Object can be used to coordinate between multiple clients who need to work together.
* Each Durable Object has some **durable storage** attached. Since this storage lives together with the object, it is strongly consistent yet fast to access.
Therefore, Durable Objects enable **stateful** serverless applications.
For more information, refer to the full [What are Durable Objects?](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/) page.
***
## Features
### In-memory State
Learn how Durable Objects coordinate connections among multiple clients or events.
[Use In-memory State](https://developers.cloudflare.com/durable-objects/reference/in-memory-state/)
### Storage API
Learn how Durable Objects provide transactional, strongly consistent, and serializable storage.
[Use Storage API](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/)
### WebSocket Hibernation
Learn how WebSocket Hibernation allows you to manage the connections of multiple clients at scale.
[Use WebSocket Hibernation](https://developers.cloudflare.com/durable-objects/best-practices/websockets/#websocket-hibernation-api)
### Durable Objects Alarms
Learn how to use alarms to trigger a Durable Object and perform compute in the future at customizable intervals.
[Use Durable Objects Alarms](https://developers.cloudflare.com/durable-objects/api/alarms/)
***
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Cloudflare Workers provides a serverless execution environment that allows you to create new applications or augment existing ones without configuring or maintaining infrastructure.
**[D1](https://developers.cloudflare.com/d1/)**
D1 is Cloudflare's SQL-based native serverless database. Create a database by importing data or defining your tables and writing your queries within a Worker or through the API.
**[R2](https://developers.cloudflare.com/r2/)**
Cloudflare R2 Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
***
## More resources
[Limits](https://developers.cloudflare.com/durable-objects/platform/limits/)
Learn about Durable Objects limits.
[Pricing](https://developers.cloudflare.com/durable-objects/platform/pricing/)
Learn about Durable Objects pricing.
[Storage options](https://developers.cloudflare.com/workers/platform/storage-options/)
Learn more about storage and database options you can build with Workers.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Developer Platform.
---
title: Overview · Cloudflare Email Routing docs
description: Cloudflare Email Routing is designed to simplify the way you create
and manage email addresses, without needing to keep an eye on additional
mailboxes. With Email Routing, you can create any number of custom email
addresses to use in situations where you do not want to share your primary
email address, such as when you subscribe to a new service or newsletter.
Emails are then routed to your preferred email inbox, without you ever having
to expose your primary email address.
lastUpdated: 2025-10-27T15:00:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/
md: https://developers.cloudflare.com/email-routing/index.md
---
Create custom email addresses for your domain and route incoming emails to your preferred mailbox.
Available on all plans
Cloudflare Email Routing is designed to simplify the way you create and manage email addresses, without needing to keep an eye on additional mailboxes. With Email Routing, you can create any number of custom email addresses to use in situations where you do not want to share your primary email address, such as when you subscribe to a new service or newsletter. Emails are then routed to your preferred email inbox, without you ever having to expose your primary email address.
Email Routing is free and private by design. Cloudflare will not store or access the emails routed to your inbox.
It is available to all Cloudflare customers [using Cloudflare as an authoritative nameserver](https://developers.cloudflare.com/dns/zone-setups/full-setup/).
***
## Features
### Email Workers
Leverage the power of Cloudflare Workers to implement any logic you need to process your emails. Create rules as complex or simple as you need.
[Use Email Workers](https://developers.cloudflare.com/email-routing/email-workers/)
### Custom addresses
With Email Routing you can have many custom email addresses to use for specific situations.
[Use Custom addresses](https://developers.cloudflare.com/email-routing/get-started/enable-email-routing/)
### Analytics
Email Routing includes metrics to help you check on your email traffic history.
[Use Analytics](https://developers.cloudflare.com/email-routing/get-started/email-routing-analytics/)
***
## Related products
**[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)**
Cloudflare Email security is a cloud based service that stops phishing attacks, the biggest cybersecurity threat, across all traffic vectors - email, web and network.
**[DNS](https://developers.cloudflare.com/dns/)**
Email Routing is available to customers using Cloudflare as an authoritative nameserver.
---
title: Overview · Cloudflare Email security (formerly Area 1) docs
description: Phishing is the root cause of upwards of 90% of breaches that lead
to financial loss and brand damage. Email Security (formerly Area 1) is a
cloud-native service that stops phishing attacks across all threat vectors
either at the edge or in the cloud.
lastUpdated: 2025-10-27T15:00:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/
md: https://developers.cloudflare.com/email-security/index.md
---
Stop phishing attacks with Email security (formerly Area 1) cloud-native email security service.
Available on paid plans
Area 1 has been renamed
Area 1 is now **Email security (formerly Area 1)**. Customers who purchased the new Email security can access the documentation by going to Cloudflare Zero Trust > [Email security](https://developers.cloudflare.com/cloudflare-one/email-security/).
Access to Area 1
Beginning October 1, 2025, access and support for Email Security (formerly Area 1) will only be available through the Cloudflare dashboard. Your Email Security protection will not change, but you will no longer be able to access the Area 1 dashboard or send support requests to `@area1security.com` email addresses. For help accessing the Cloudflare dashboard, reach out to .
Phishing is the root cause of upwards of 90% of breaches that lead to financial loss and brand damage. Email Security (formerly Area 1) is a cloud-native service that stops phishing attacks across all threat vectors either at the [edge](https://www.cloudflare.com/learning/serverless/glossary/what-is-edge-computing/) or in the cloud.
With globally distributed sensors and comprehensive attack analytics, Email Security (formerly Area 1) proactively identifies phishing campaigns, attacker infrastructure, and attack delivery mechanisms during the earliest stages of a phishing attack cycle. Using flexible enforcement platforms, the Email Security (formerly Area 1) solution allows customers to take preemptive action against targeted phishing, including malware, spoofing attacks, payload-less Business Email Compromise attacks, supply chain phishing, and other advanced threats.
***
## Features
### Deployment
Email security (formerly Area 1) provides two architectures to protect your organization: inline or API setup. Inline architecture evaluates email messages before they reach a user's inbox. API architecture evaluates emails when they have already reached a user's inbox.
[Evaluate deployment options](https://developers.cloudflare.com/email-security/deployment/)
### SSO integration
In addition to standard logins, Email security (formerly Area 1) offers support for SAML based single sign-on (SSO) logins to your dashboard.
[Use SSO integration](https://developers.cloudflare.com/email-security/account-setup/sso/)
### Business email compromise
Attackers often try to impersonate executives within an organization when sending malicious emails. The Business email compromise (BEC) feature protects against these attacks.
[Use Business email compromise](https://developers.cloudflare.com/email-security/email-configuration/enhanced-detections/business-email-compromise/)
***
## Related products
**[Cloudflare Zero Trust](https://developers.cloudflare.com/cloudflare-one/)**
Cloudflare Zero Trust replaces legacy security perimeters with Cloudflare's global network, making the Internet faster and safer for teams around the world.
**[Email Routing](https://developers.cloudflare.com/email-routing/)**
Email Routing simplifies the way you create and manage custom email addresses. Email security (formerly Area 1) helps secure your mail infrastructure from phishing attacks.
**[DMARC Management](https://developers.cloudflare.com/dmarc-management/)**
Stop brand impersonation. Track and manage every source that is sending emails from your domain.
***
## More resources
[Pricing](https://www.cloudflare.com/products/zero-trust/email-security/)
Email security (formerly Area 1) is available as a standalone product purchase.
---
title: Cloudflare Firewall Rules (deprecated) · Cloudflare Firewall Rules
(deprecated) docs
description: Cloudflare Firewall Rules allows you to create rules that inspect
incoming traffic and block, challenge, log, or allow specific requests.
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/firewall/
md: https://developers.cloudflare.com/firewall/index.md
---
Cloudflare Firewall Rules allows you to create rules that inspect incoming traffic and block, challenge, log, or allow specific requests.
Deprecation notice
Cloudflare Firewall Rules has been deprecated. Cloudflare has moved existing firewall rules to [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/). For more information on this change, refer to the [upgrade guide](https://developers.cloudflare.com/waf/reference/legacy/firewall-rules-upgrade/).
## Main features
* **Rule-based protection**: Use pre-defined rulesets provided by Cloudflare, or define your own firewall rules. Create rules in the Cloudflare dashboard or via API.
* **Complex custom rules**: Each rule's expression can reference multiple fields from all the available HTTP request parameters and fields, allowing you to create complex rules.
## Availability
This table outlines the Firewall Rules features and entitlements available with each customer plan:
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 5 | 20 | 100 | 1,000 |
| Supported actions | All except Log | All except Log | All except Log | All |
| Regex support | No | No | Yes | Yes |
## Next steps
* Unless you are already an advanced user, refer to [Expressions](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/) and [Actions](https://developers.cloudflare.com/firewall/cf-firewall-rules/actions/) to learn more about the basic elements of firewall rules.
* To start building your own firewall rules, refer to one of the following pages:
* [Manage firewall rules in the dashboard](https://developers.cloudflare.com/firewall/cf-dashboard/create-edit-delete-rules/)
* [Manage firewall rules via the APIs](https://developers.cloudflare.com/firewall/api/)
* You can also manage firewall rules through Terraform. For more information, refer to [Getting Started with Terraform](https://blog.cloudflare.com/getting-started-with-terraform-and-cloudflare-part-1/).
## Related resources
* [Cloudflare Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/)
---
title: Overview · Cloudflare Fundamentals docs
description: Cloudflare is one of the world's largest connectivity cloud
networks. Today, anyone with an Internet presence can have faster and more
secure websites and applications thanks to Cloudflare. This includes bloggers,
businesses, and even non-profits.
lastUpdated: 2025-07-18T14:20:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/fundamentals/
md: https://developers.cloudflare.com/fundamentals/index.md
---
Cloudflare is one of the world's largest [connectivity cloud networks](https://blog.cloudflare.com/welcome-to-connectivity-cloud). Today, anyone with an Internet presence can have faster and more secure websites and applications thanks to Cloudflare. This includes bloggers, businesses, and even non-profits.
Millions of Internet properties are on Cloudflare, and our network is growing by tens of thousands each day. Cloudflare powers Internet requests for millions of websites and serves 55 million HTTP requests per second on average.
Before you get started, we recommend reviewing [Concepts](https://developers.cloudflare.com/fundamentals/concepts/) to learn about key concepts related to using different Cloudflare products.
## Additional resources
Refer to the list below for additional Cloudflare resources.
* [Cloudflare blog](https://blog.cloudflare.com)
* [Cloudflare's Go library](https://github.com/cloudflare/cloudflare-go)
* [Cloudflare system status](https://www.cloudflarestatus.com/)
* [Cloudflare Radar](https://radar.cloudflare.com)
* [Cloudflare TV](https://cloudflare.tv/schedule)
* [Terraform](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
---
title: Glossary | Cloudflare Docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/glossary/
md: https://developers.cloudflare.com/glossary/index.md
---
Beta
| Term | Definition | Product |
| - | - | - |
| account | Accounts group one or more members together with specific roles or permissions. Accounts can be associated with any number of domains. | Fundamentals |
| ACK (Acknowledge) | The final step in the TCP three-way handshake, confirming the establishment of a connection. | Spectrum |
| active zone | A DNS zone that is active on Cloudflare requires changing its nameservers to Cloudflare's for management. | DNS |
| address map | A data structure enabling customers with BYOIP prefixes or account-level static IPs to specify which IP addresses should be mapped to DNS records when they are proxied through Cloudflare. | BYOIP |
| AI crawler | A bot which scrapes content from websites in support of an AI model, including by scraping content for indexing, retrieval augmented generation, or training. | AI Crawl Control |
| AI models | [An AI model](https://developers.cloudflare.com/workers-ai/models) is a trained system that processes input data to generate predictions, decisions, or outputs based on patterns it has learned. | Workers AI |
| alarm | A Durable Object alarm is a mechanism that allows you to schedule the Durable Object to be woken up at a time in the future. | Durable Objects |
| allowlist | An allowlist is a list of items (usually websites, IP addresses, email addresses, etc.) that are permitted to access a system. | WAF |
| anycast | Anycast is a network addressing and routing method in which incoming requests can be routed to a variety of different locations. Anycast typically routes incoming traffic to the nearest data center with the capacity to process the request efficiently. | Magic WAN |
| apex domain | Apex domain is used to refer to a domain that does not contain a subdomain part, such as `example.com` (without `www.`). It is also known as "root domain" or "naked domain". | DNS |
| API call | Also known as an API request. An API call is a message sent to a server asking an API to provide a service or information. | API Shield |
| API endpoint | The API endpoint is the location where API calls or requests are fulfilled. API Shield defines endpoints as a host, method, and path tuple. | API Shield |
| API key | An API key is unique to each Cloudflare user and used to confirm identity when using the [Cloudflare API](https://developers.cloudflare.com/api/). | Fundamentals |
| API schema | The API schema defines which API requests are valid based on several request properties like target endpoint, path or query variable format, and HTTP method. | API Shield |
| API token | API tokens authorize access to specific Cloudflare dashboard pages, accounts, and zones. API tokens are associated to the user that created them. | Fundamentals |
| API Tokens | [API Tokens](https://developers.cloudflare.com/workers-ai/get-started/rest-api/) are authentication credentials used to securely access and manage Workers AI resources via the REST API. | Workers AI |
| App Launcher | The App Launcher portal provides end users with a single dashboard to open applications secured by Cloudflare One. | Cloudflare One |
| application | The resource protected by Cloudflare One, which can be a subdomain, a path, or a SaaS application. | Cloudflare One |
| application token | A piece of data that grants a user access to a specific Access application for a period of time. Can be stored in a browser cookie or passed to the application in place of a normal password. | Cloudflare One |
| attack score | A number from 1 (likely malicious) to 99 (likely clean) classifying how likely an incoming request is malicious or not. Allows you to detect new attack techniques before they are publicly known. | WAF |
| attribute | Traffic that flows through Area 1 can receive one or more attributes, which indicate that a specific condition has been met. | Area 1 |
| Authenticated Origin Pulls | Authenticated Origin Pulls allow origin web servers to validate that a web request came from Cloudflare using TLS client certificate authentication. | SSL/TLS |
| autonomous system numbers (ASNs) | A large network or group of networks that has a unified routing policy. Every computer or device that connects to the Internet is connected to an autonomous system. | BYOIP |
| Auxiliary Worker | A Worker created locally via the [Workers Vitest integration](https://developers.cloudflare.com/workers/testing/vitest-integration/) that runs in a separate isolate to the test runner, with a different global scope. | Workers |
| backup codes | Backup codes allow restoration of Cloudflare account access outside the normal [two-factor authentication process](https://developers.cloudflare.com/fundamentals/user-profiles/2fa/). A backup code becomes invalid after use. | Fundamentals |
| bandwidth | The maximum rate of data transfer across a network. | Speed |
| binding | [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) allow your Workers to interact with resources on the Cloudflare Developer Platform. | Workers |
| bit field matching | Matches raw bits in a packet to certain values specified in your rules. | Magic Firewall |
| blocklist | A blocklist is a list of items (usually websites, IP addresses, email addresses, etc.) that are prevented from accessing a system. | WAF |
| bookmark | A bookmark represents the state of a database at a specific point in time.- Bookmarks are lexicographically sortable. Sorting orders a list of bookmarks from oldest-to-newest. | D1 |
| bookmark | A bookmark is a mostly alphanumeric string like `0000007b-0000b26e-00001538-0c3e87bb37b3db5cc52eedb93cd3b96b` which represents a specific state of a SQLite database at a certain point in time. Bookmarks are designed to be lexically comparable: a bookmark representing an earlier point in time compares less than one representing a later point, using regular string comparison. | Durable Objects |
| Border Gateway Protocol (BGP) | The routing protocol for the Internet, which is responsible for picking the most efficient routes to deliver Internet traffic. | BYOIP |
| bot | A software application programmed to do tasks that can be used for good (chatbots, search engine crawlers) or for evil (inventory hoarding, credential stuffing). | Bots |
| bot score | A score from 1 to 99 that indicates how likely that request came from a bot, in which 1 to 29 is likely automated and 30 to 99 is likely human. | Bots |
| bot tags | Additional information about a bot request, such as why Cloudflare has given it a bot score and whether the request came from a verified bot or a category of verified bots. | Bots |
| brotli compression | Brotli compression is a data compression algorithm developed by Google, optimized for web content, and designed to achieve higher compression ratios than traditional algorithms like Gzip. | Speed |
| C3 | [C3](https://developers.cloudflare.com/learning-paths/workers/get-started/c3-and-wrangler/) is a command-line tool designed to help you set up and deploy new applications to Cloudflare. | Workers |
| cache | A temporary storage area where frequently accessed data is stored for quick retrieval. | Cache |
| cache hit | When a requested piece of content is found in the cache, reducing the need to fetch it from the origin server. | Cache |
| cache lock | Cache lock (or mutex) is a mechanism employed by CDN data centers, comprising numerous servers, to prevent the overloading of origin servers. This mechanism ensures that only one server can request a specific file from the origin at any given time, facilitating efficient coordination among the servers. | Cache |
| cache miss | When a requested piece of content is not found in the cache, requiring the server to fetch it from the origin server. | Cache |
| cached bandwidth (cached egress bandwidth) | The amount of bandwidth served from Cloudflare without hitting the origin server. Cached bandwidth is the sum of all `EdgeResponseBytes` where `CacheCacheStatus` equals `hit`, `stale`, `updating`, `ignored`, or `revalidated`. | Cache |
| cached requests | The number of requests served from Cloudflare without having to hit the origin server. Cached requests are the sum of all requests where `CacheCacheStatus` equals `hit`, `stale`, `updating`, `ignored`. This does not include `revalidated` since the request had to be sent to the origin server. | Cache |
| cacheTtl | CacheTtl is a parameter that defines the length of time in seconds that a KV result is cached in the global network location it is accessed from. | KV |
| caching | The process of storing copies of files or data in a cache to accelerate future requests. | Cache |
| CAPTCHA | A CAPTCHA test is designed to determine if an online user is really a human and not a bot. CAPTCHA is an acronym that stands for "Completely Automated Public Turing test to tell Computers and Humans Apart." | Turnstile |
| captive portal | A login screen shown to users when they connect to a public Wi-Fi. Captive portals typically occur in places such as airports, cafes, and hotels. | Cloudflare One |
| certificate | SSL certificates enable encryption over HTTPS for traffic between a client and a website. SSL certificates contain the website's public key and the website's identity along with related information. Devices attempting to communicate with the origin web server reference the SSL certificate to obtain the public key and verify the server's identity. Cloudflare provides a [Universal SSL certificate](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/) for each active Cloudflare domain. | SSL/TLS |
| Certificate Authority (CA) | A CA is a trusted third party that provides SSL certificates for encrypting network traffic. | SSL/TLS |
| certificate packs | Certificate packs allow Cloudflare to fallback to a different SSL certificate for browsers that do not support the latest standards. Certificate packs allow Custom SSL certificates to contain different signature algorithms for the same hostnames listed within the SSL certificate without taking up additional Custom SSL certificate quota for your Cloudflare account. | SSL/TLS |
| certificate pinning | A security mechanism used to prevent on-path attacks on the Internet by hardcoding information about the certificate that the application expects to receive. If the wrong certificate is received, even if it is trusted by the system, the application will refuse to connect. | SSL/TLS |
| Certification Authority Authorization (CAA) record | A CAA record declares which CAs are allowed to issue an SSL certificate for a domain. | SSL/TLS |
| cf-aig-backoff | Header to customize the backoff type for [request retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) of a request. | AI Gateway |
| cf-aig-cache-key | The [cf-aig-cache-key-aig-cache-key](https://developers.cloudflare.com/ai-gateway/features/caching/#custom-cache-key-cf-aig-cache-key) let you override the default cache key in order to precisely set the cacheability setting for any resource. | AI Gateway |
| cf-aig-cache-status | [Status indicator for caching](https://developers.cloudflare.com/ai-gateway/features/caching/#default-configuration), showing if a request was served from cache. | AI Gateway |
| cf-aig-cache-ttl | Specifies the [cache time-to-live for responses](https://developers.cloudflare.com/ai-gateway/features/caching/#cache-ttl-cf-aig-cache-ttl). | AI Gateway |
| cf-aig-collect-log | The [cf-aig-collect-log](https://developers.cloudflare.com/ai-gateway/observability/logging/#collect-logs-cf-aig-collect-log) header allows you to bypass the default log setting for the gateway. | AI Gateway |
| cf-aig-custom-cost | Allows the [customization of request cost](https://developers.cloudflare.com/ai-gateway/configuration/custom-costs/#custom-cost) to reflect user-defined parameters. | AI Gateway |
| cf-aig-event-id | [cf-aig-event-id](https://developers.cloudflare.com/ai-gateway/evaluations/add-human-feedback-api/#3-retrieve-the-cf-aig-log-id) is a unique identifier for an event, used to trace specific events through the system. | AI Gateway |
| cf-aig-log-id | The [cf-aig-log-id](https://developers.cloudflare.com/ai-gateway/evaluations/add-human-feedback-api/#3-retrieve-the-cf-aig-log-id) is a unique identifier for the specific log entry to which you want to add feedback. | AI Gateway |
| cf-aig-max-attempts | Header to customize the number of max attempts for [request retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) of a request. | AI Gateway |
| cf-aig-metadata | [Custom metadata](https://developers.cloudflare.com/ai-gateway/configuration/custom-metadata/)allows you to tag requests with user IDs or other identifiers, enabling better tracking and analysis of your requests. | AI Gateway |
| cf-aig-request-timeout | Header to trigger a fallback provider based on a [predetermined response time](https://developers.cloudflare.com/ai-gateway/configuration/fallbacks/#request-timeouts) (measured in milliseconds). | AI Gateway |
| cf-aig-retry-delay | Header to customize the retry delay for [request retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) of a request. | AI Gateway |
| cf-aig-skip-cache | Header to [bypass caching for a specific request](https://developers.cloudflare.com/ai-gateway/features/caching/#skip-cache-cf-aig-skip-cache). | AI Gateway |
| cf-aig-step | [cf-aig-step](https://developers.cloudflare.com/ai-gateway/configuration/fallbacks/#response-headercf-aig-step) identifies the processing step in the AI Gateway flow for better tracking and debugging. | AI Gateway |
| cf-cache-ttl | Deprecated: This header is replaced by `cf-aig-cache-ttl`. It specifies cache time-to-live. | AI Gateway |
| cf-skip-cache | Deprecated: This header is replaced by `cf-aig-skip-cache`. It bypasses caching for a specific request. | AI Gateway |
| Challenge solve rate (CSR) | The percentage of issued challenges that were solved. | Bots |
| CIDR | CIDR stands for Classless Inter-Domain Routing. CIDR often refers to CIDR notation, which is an IP address represented as a series of four 8-bit octets, separated by dots (e.g., 192.168.1.1). Additionally, CIDR notation includes a suffix that indicates the number of bits used for the network portion of the address. The format is typically written as "/X," where X is the number of bits in the network portion. | Fundamentals |
| cipher suite | A set of encryption algorithms for establishing a secure communications connection. There are several cipher suites in wide use, and a client and server agree on the cipher suite to use when establishing the TLS connection. Support of multiple cipher suites allows compatibility across various clients. | SSL/TLS |
| client-side resource | A file with JavaScript code loaded by your visitors' browser, or a connection made by one of the loaded scripts. | Page Shield |
| cloud | A network of remote servers used to store and maintain data. | Fundamentals |
| Cloudflare Access | Cloudflare Access replaces corporate VPNs with Cloudflare's network. It verifies attributes such as identity and device posture to grant users secure access to internal tools. | Cloudflare One |
| Cloudflare Browser Isolation | Cloudflare Browser Isolation seamlessly executes active webpage content in a secure isolated browser to protect users from zero-day attacks, malware, and phishing. | Cloudflare One |
| Cloudflare CASB | Cloudflare CASB provides comprehensive visibility and control over SaaS apps to prevent data leaks and compliance violations. It helps detect insider threats, shadow IT, risky data sharing, and bad actors. | Cloudflare One |
| Cloudflare Dashboard | [Cloudflare Dashboard](https://developers.cloudflare.com/workers-ai/get-started/dashboard/) is a web-based interface that allows users to manage Workers AI services, including model deployment and monitoring. | Workers AI |
| Cloudflare Data Loss Prevention (DLP) | Cloudflare [Data Loss Prevention](https://www.cloudflare.com/learning/access-management/what-is-dlp/) (DLP) allows you to scan your web traffic and SaaS applications for the presence of sensitive data such as social security numbers, financial information, secret keys, and source code. | Cloudflare One |
| Cloudflare DEX | Cloudflare Digital Experience Monitoring (DEX) provides visibility into device, network, and application performance across your Zero Trust Organization. | Cloudflare One |
| Cloudflare Gateway | Cloudflare Gateway is a modern next-generation firewall between your user, device, or network and the public Internet. It includes DNS filtering to inspect and apply policies to all Internet-bound DNS queries. | Cloudflare One |
| Cloudflare One | The name for Cloudflare's Secure Access Service Edge (SASE) platform, which includes Zero Trust and network services. | Cloudflare One |
| Cloudflare One Agent | The name of the Cloudflare WARP client app on iOS and Android devices. | Cloudflare One |
| Cloudflare Tunnel | Cloudflare Tunnel uses software agents (`cloudflared` or WARP Connector) to establish a secure connection between a private network and Cloudflare. | Cloudflare One |
| Cloudflare Zero Trust | Cloudflare Zero Trust provides the power of Cloudflare's global network to your internal teams and infrastructure. It empowers users with secure, fast, and seamless access to any device on the Internet. | Cloudflare One |
| cloudflared | The software powering Cloudflare Tunnel. It runs on origin servers to connect applications or private networks to Cloudflare. | Cloudflare One |
| cloudflared replica | An additional instance of `cloudflared` that points to the same Cloudflare Tunnel. It ensures that your network remains online in case a single host running `cloudflared` goes down. | Cloudflare One |
| CNAME setup | Also known as partial setup, a CNAME setup allows you to use Cloudflare's reverse proxy without using Cloudflare for your authoritative nameservers. | DNS |
| code example | A code example illustrates how to use a programming element to implement specific functionality | Fundamentals |
| compression | The process of reducing the size of files or data to speed up their transfer over the network. | Speed |
| consumer | A consumer is the term for a client that is subscribing to or consuming messages from a queue. | Queues |
| content delivery network (CDN) | A geographically distributed group of servers which work together to provide fast delivery of Internet content. | Fundamentals |
| content object | A content object is any binary part of a request body (as detected by Cloudflare systems) that does not match any of the following content types: `text/html`, `text/x-shellscript`, `application/json`, `text/csv`, or `text/xml`. | WAF |
| content security policy (CSP) | An added layer of security that helps detect and mitigate certain types of attacks such as cross-site scripting (XSS) attacks. | Fundamentals |
| Context Window | In generative AI, the context window is the sum of the number of input, reasoning, and completion or response tokens a model supports. You can find the context window limit on each [model page](https://developers.cloudflare.com/workers-ai/models/). | Workers AI |
| core web vitals | Core web vitals are a set of user-centric performance metrics, including Largest Contentful Paint (LCP), Cumulative Layout Shift (CLS), and First Input Delay (FID), used by Google to assess the overall user experience of a webpage. | Speed |
| CPU time | [CPU time](https://developers.cloudflare.com/workers/platform/limits/#cpu-time) is the amount of time the central processing unit (CPU) actually spends doing work, during a given request. | Workers |
| credential stuffing | Credential stuffing is the automated injection of stolen username and password pairs (known as "credentials") into website login forms, trying to gain access to user accounts. | WAF |
| credit | An amount applied to a specific Cloudflare account as credit for recurring subscriptions or plan payments. The Cloudflare billing system automatically applies credits in the next billing cycle. | Fundamentals |
| Cron Triggers | [Cron Triggers](https://developers.cloudflare.com/workers/configuration/cron-triggers/) allow users to map a cron expression to a Worker using a [`scheduled()` handler](https://developers.cloudflare.com/workers/runtime-apis/handlers/scheduled/) that enables Workers to be executed on a schedule. | Workers |
| cumulative layout shift (CLS) | Cumulative layout shift (CLS) is a web performance metric that quantifies the visual stability of a webpage by measuring the sum of unexpected layout shifts of elements during the page's loading and rendering process. | Speed |
| D1 | [D1](https://developers.cloudflare.com/d1/) is Cloudflare's managed, serverless database with SQLite's SQL semantics, built-in disaster recovery, and Worker and HTTP API access. | Workers AI |
| D1 | [D1](https://developers.cloudflare.com/d1/) is Cloudflare's native serverless database. | Workers |
| daemon | A program that performs tasks without active management or maintenance. | Cloudflare One |
| data center | A physical location where servers run and other IT operations are hosted. | Fundamentals |
| data packet | A data packet is a unit of data consisting of user and control information. Information in a network is broken down into packets, that might follow different paths to their final destination. | Magic WAN |
| debugging | The process of identifying and resolving errors or issues within software applications or systems, often facilitated by analyzing log data. | Logs |
| demo application | A demo application is a functional application in GitHub that you can clone and deploy on your own. | Fundamentals |
| denial-of-service (DoS) attack | A DoS attack is a type of cyber attack in which an attacker aims to render a computer or other device unavailable to its intended users by interrupting the device's normal functioning. | Fundamentals |
| deployment | [Deployments](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/#deployments) track the version(s) of your Worker that are actively serving traffic. | Workers |
| deprecation | Deprecation in software development involves officially labeling a feature as outdated. While a deprecated software feature remains within the software, users are warned and encouraged to adopt alternatives. Eventually, deprecated features may be removed. This approach ensures backward compatibility and gives programmers time to update their code. | Logs |
| detection ID | Static rules that are used to detect predictable bot behavior with no overlap with human traffic. | Bots |
| device posture | A way to evaluate the security of a user's device, for example by verifying its serial number or checking if it has the latest software updates. | Cloudflare One |
| device profile | A collection of WARP client settings applied to a specific set of devices in your organization. | Cloudflare One |
| device registration | An individual session of the WARP client on a physical device, with associated configuration including a unique public key, device profile, and virtual IP addresses (one IPv4 and one IPv6). | Cloudflare One |
| disposition | Represents Area 1's evaluation of a specific message. For example, after evaluating an email it may get a disposition of `malicious`. Email messages with this disposition exhibit characteristics typical of malicious emails. | Area 1 |
| distributed denial-of-service (DDoS) attack | A DDoS attack is a malicious attempt to disrupt normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. | Fundamentals |
| DNS filtering | DNS filtering uses the Domain Name System to block malicious websites and filter out harmful content, enhancing security and access control. | Cloudflare One |
| DNS location | DNS locations are a collection of DNS endpoints which can be mapped to physical entities such as offices, homes, or data centers. | Cloudflare One |
| DNS over HTTPS | DNS over HTTPS (DoH) is a standard for encrypting DNS traffic via the HTTPS protocol, preventing tracking and spoofing of DNS queries. | DNS |
| DNS over TLS | DNS over TLS (DoT) is a standard for encrypting DNS traffic using its own port (`853`) and TLS encryption. | DNS |
| DNS record | DNS records are instructions that live in authoritative DNS servers and provide information about a domain, including what IP address is associated with that domain and how to handle requests for that domain. | DNS |
| DNS server | DNS servers translate human-readable domain names into IP addresses, eliminating the need to remember complex IP addresses. | DNS |
| DNS zone | A portion of the DNS namespace that is managed by a specific organization or administrator. | DNS |
| DoH subdomain | A unique DoH subdomain for each DNS location in Cloudflare One used in WARP client settings. | Cloudflare One |
| domain | The domain name of your application on Cloudflare. | Fundamentals |
| domain control validation (DCV) | Process by which a certificate authority (CA) can verify domain ownership before issuing an SSL/TLS certificate. | SSL/TLS |
| Domain Name System (DNS) | The Domain Name System (DNS) is the phonebook of the Internet. DNS translates domain names to IP addresses. | DNS |
| downtime | Downtime is the duration during which a system, service, or equipment is not operational or unavailable for use. | Waiting Room |
| Durable Execution | "Durable Execution" is a programming model that allows applications to execute reliably, automatically persist state, retry, and be resistant to errors caused by API, network or even machine/infrastructure failures. Cloudflare Workflows provide a way to build and deploy applications that align with this model. | Workflows |
| Durable Object | A Durable Object is an individual instance of a Durable Object class. A Durable Object is globally unique (referenced by ID), provides a global point of coordination for all methods/requests sent to it, and has private, persistent storage that is not shared with other Durable Objects within a namespace. | Durable Objects |
| Durable Object class | The JavaScript class that defines the methods (RPC) and handlers (`fetch`, `alarm`) as part of your Durable Object, and/or an optional `constructor`. All Durable Objects within a single namespace share the same class definition. | Durable Objects |
| Durable Objects | The product name, or the collective noun referring to more than one Durable Object. | Durable Objects |
| Durable Objects | [Durable Objects](https://developers.cloudflare.com/durable-objects/) is a globally distributed coordination API with strongly consistent storage. | Workers |
| duration | [Duration](https://developers.cloudflare.com/workers/platform/limits/#duration) is a measurement of wall-clock time — the total amount of time from the start to end of an invocation of a Worker. | Workers |
| dynamic content | Dynamic content refers to website content that changes based on factors specific to the user such as time of visit, location, and device. News websites or social media are examples of this type of content. For this type of website, content has to be fetched from the origin server every time it is requested. | Cache |
| edge certificate | The SSL/TLS certificates that Cloudflare presents to clients visiting your website or application.Because of [how Cloudflare works](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/), there can actually be [two certificates involved in a single request](https://developers.cloudflare.com/ssl/concepts/): an edge certificate and an origin certificate. | SSL/TLS |
| edge response status code | HTTP response code sent from Cloudflare to the client (end user). The Cloudflare dashboard **Analytics** app uses the edge response status code. | Fundamentals |
| edge server | A server located at the edge of a network, typically within a CDN, that serves content to end-users. | Cache |
| EDNS Client Subnet (ECS) | ECS is a DNS extension that enables recursive DNS resolvers to include client IP address information in their DNS queries.Not all resolvers use ECS but, if they do, usually a part of the IP address is omitted. Sending ECS headers is generally intended to reduce latency and speed up content delivery in connection to [CDNs](https://developers.cloudflare.com/glossary/?term=cdn) and [load balancers](https://www.cloudflare.com/learning/performance/what-is-load-balancing/). The ECS mechanism is specified in [RFC 7871](https://www.rfc-editor.org/rfc/rfc7871.html). | DNS |
| encryption algorithm | An encryption algorithm is a set of mathematical operations performed on data to ensure the data is only understood by the intended recipient. | SSL/TLS |
| endpoint | Any service or hardware that intercepts and processes incoming public or private traffic.Examples of endpoints include origins, hostnames, private or public IP addresses, virtual IP addresses (VIPs), servers, and other dedicated hardware boxes. | Load Balancing |
| environment | [Environments](https://developers.cloudflare.com/workers/wrangler/environments/) allow you to deploy the same Worker application with different configuration for each environment. Only available for use with a [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/). | Workers |
| environment variable | [Environment variables](https://developers.cloudflare.com/workers/configuration/environment-variables/) are a type of binding that allow you to attach text strings or JSON values to your Worker. | Workers |
| Environment Variables | [Environment Variables](https://developers.cloudflare.com/workers-ai/configuration/bindings/) are dynamic values that can be used within Workers to manage configuration settings, including those related to AI integrations. | Workers AI |
| equal-cost multi-path routing | A technique that uses hashes calculated from packet data to determine the route chosen. | Magic WAN |
| error page | An error page is a webpage shown to users when they try to access a specific webpage or resource that is unavailable due to a server error, broken link, or other issues. It typically includes details about the encountered error and offers potential solutions or guidance to help users navigate the problem. | Waiting Room |
| event | An occurrence or happening that is significant and worthy of being recorded in a log. | Logs |
| Event | The event that triggered the Workflow instance. A `WorkflowEvent` may contain optional parameters (data) that a Workflow can operate on. | Workflows |
| example | Hello, world! You can use **Markdown** features inside of your `tooltips`. | Style Guide |
| Extended Validation (EV) certificate | EV certificates provide maximum trust to visitors, but require the most validation effort by the CA. EV certificates show the name of the company or organization in the address bar of the visitor’s browser. An EV certificate requires additional documentation by the company or organization in order for the CA to approve the certificate. | SSL/TLS |
| feature | A feature is a setting in the Cloudflare dashboard that corresponds to functionality within a Cloudflare product or API. | Fundamentals |
| Fine-Tuning | [Fine-Tuning](https://developers.cloudflare.com/workers-ai/fine-tunes/) is a general term for modifying an AI model by continuing to train it with additional data. | Workers AI |
| firewall | A firewall is a security system that monitors and controls network traffic based on a set of security rules. | WAF |
| firewall-as-a-service | Also known as cloud firewall. A security product that is hosted in the cloud. | Magic Firewall |
| first contentful paint (FCP) | First contentful paint (FCP) is a web performance metric that measures the time it takes for the first piece of content to be rendered on the screen during the loading of a web page. | Speed |
| first input delay (FID) | First input delay (FID) is a web performance metric that measures the delay between a user's first interaction with a page (for example, clicking a button) and the moment the browser responds, indicating the page's interactivity and responsiveness. | Speed |
| fleet | A fleet is a collection of user devices. All devices in a fleet have WARP installed and are connected to a [Zero Trust Organization](https://developers.cloudflare.com/cloudflare-one/setup/#create-a-zero-trust-organization). | Cloudflare One |
| flow data | Represents records of communication between devices. There are a number of flow data protocols, such as NetFlow or sFlow. | Magic Network Monitoring |
| FTP (File Transfer Protocol) | A standard network protocol used for transferring files from one host to another over a TCP-based network. | Spectrum |
| FTPS (File Transfer Protocol Secure) | An extension of FTP that adds support for the Transport Layer Security (TLS) or Secure Sockets Layer (SSL) cryptographic protocols. | Spectrum |
| Function Calling | [Function Calling](https://developers.cloudflare.com/workers-ai/function-calling/) enables people to take Large Language Models (LLMs) and use the model response to execute functions or interact with external APIs. | Workers AI |
| GRE tunnel | Stands for generic routing encapsulation. It is a protocol wrapping one data packet within another type of data packet. This is useful for enabling protocols that are not normally supported by a network. | Magic WAN |
| handler | [Handlers](https://developers.cloudflare.com/workers/runtime-apis/handlers/) are methods on Workers that can receive and process external inputs, and can be invoked from outside your Worker. | Workers |
| health check | Requests issued by a monitor at regular interval and — depending on the monitor settings — return a **pass** or **fail** value to make sure an endpoint is still able to receive traffic.Each health monitor request is trying to answer two questions:1) **Is the endpoint offline?**: Does the endpoint respond to the health monitor request at all? If so, does it respond quickly enough (as specified in the monitor's **Timeout** field)?
2) **Is the endpoint working as expected?**: Does the endpoint respond with the expected HTTP response codes? Does it include specific information in the response body?If the answer to either of these questions is "No", then the endpoint fails the health monitor request. | Load Balancing |
| Hops | Hops refer to the stops an email makes as it travels from the sender to the recipient. | Cloudflare One |
| hostname | The name given to a server or node on a network, often the public DNS name of a server. | DNS |
| HTTP request | An HTTP request is the way Internet communications platforms such as web browsers ask for the information they need to load a website. | Fundamentals |
| ICMP | Internet Control Message Protocol (ICMP) is used by network devices to send error messages and other operational information. ICMP is useful for diagnostic purposes, for example. | Magic WAN |
| identity provider | An identity provider (IdP) stores and manages users' digital identities, enabling single sign-on and authentication for multiple applications. | Cloudflare One |
| idle connection | When a TCP connection is in an idle state, it means that the connection has been established, but neither endpoint is sending any data. In the context of HTTP, an idle connection is when an established connection between a client and a server is not currently transmitting any HTTP requests or responses. | Fundamentals |
| iFrame | An iFrame, short for Inline Frame, is an HTML element used to embed and display external content within a webpage, allowing the incorporation of another document or web page seamlessly within the main document. | Waiting Room |
| In-band pricing | A pricing model where pricing information is transmitted within the same communication channel as the content itself. In Pay Per Crawl, in-band pricing means the price is included in the HTTP response headers (`crawler-price`) alongside the actual content, rather than being retrieved from a separate system or API call. When custom pricing is enabled, Cloudflare sets the `cf-pay-per-crawl` header to `pricing=in-band`, indicating that the origin server or Worker can dynamically set prices by including a `crawler-price` header in the response. | AI Crawl Control |
| Inference | [Inference](https://developers.cloudflare.com/workers-ai/fine-tunes/public-loras/#running-inference-with-public-loras) refers to the process of using a trained machine learning model to make predictions or generate outputs based on new data. | Workers AI |
| initial resolved IP | A unique, ephemeral IP address that Gateway assigns to DNS queries when filtering network traffic by hostname. The IP is randomly selected from the `100.80.0.0/16` (IPv4) or `2606:4700:0cf1:4000::/64` (IPv6) range. | Cloudflare One |
| input gate | While a storage operation is executing, no events shall be delivered to a Durable Object except for storage completion events. Any other events will be deferred until such a time as the object is no longer executing JavaScript code and is no longer waiting for any storage operations. We say that these events are waiting for the "input gate" to open. | Durable Objects |
| instance | See "Durable Object". | Durable Objects |
| instance | A specific instance (running, paused, errored) of a Workflow. A Workflow can have a potentially infinite number of instances. | Workflows |
| interaction to next paint (INP) | Interaction to next paint (INP) is a web performance metric that measures the time it takes for a web page to become interactive and respond to user input after the initial paint, providing insights into the user experience during the interaction phase of page loading. | Speed |
| intermediate certificate | For security purposes, CAs issue intermediate certificates for signing website certificates. Intermediate certificates provide a means for the CA to revoke a single intermediate certificate, thus affecting only a small subset of website certificates. | SSL/TLS |
| Internet | The Internet is a global system of computer networks that provides a wide range of information and communication facilities. | Fundamentals |
| Internet key exchange (IKE) | The protocol Cloudflare uses to create the IPsec tunnel between Magic WAN and the customer's device. | Magic WAN |
| Internet Routing Registry (IRR) | A globally distributed database of routing information which contains announced routes and routing policies in a common format. Network operators use this information, as well as [RPKI](https://developers.cloudflare.com/byoip/concepts/route-filtering-rpki/), to configure backbone routers. | BYOIP |
| IP address | IP stands for Internet Protocol, which is the set of rules that makes it possible for devices to communicate over the Internet. With billions of people accessing the Internet every day, unique identifiers are necessary to keep track of who is doing what. The Internet Protocol solves this by assigning IP numbers to every device accessing the Internet. Every assigned number is an IP address. | Fundamentals |
| IP spoofing | IP spoofing is the creation of Internet Protocol (IP) packets which have a modified source address to hide the identity of the sender, impersonate another computer system, or both. | DDoS Protection |
| IPsec tunnel | Stands for Internet Protocol secure. It is a group of protocols for securing connections between devices, by encrypting IP packets. | Magic WAN |
| isolate | [Isolates](https://developers.cloudflare.com/workers/reference/how-workers-works/#isolates) are lightweight contexts that provide your code with variables it can access and a safe environment to be executed within. | Workers |
| JA3 fingerprint | JA3 and JA4 fingerprints profile specific SSL/TLS clients across different destination IPs, Ports, and X509 certificates. | Bots |
| JSON web token | A compact way to securely transmit information between parties as a JSON object, often used for authentication. | Cloudflare One |
| JSON web token (JWT) | A common authentication and authorization method used in web applications and APIs. | Rules |
| JSON-friendly | JSON-friendly refers to data or formats that are easily and naturally represented in JSON (JavaScript Object Notation), a lightweight data interchange format, without requiring complex transformations or modifications. | Waiting Room |
| KV | [Workers KV](https://developers.cloudflare.com/kv/) is Cloudflare's key-value data storage. | Workers |
| KV API | API methods part of Storage API that support persisting key-value data. | Durable Objects |
| KV namespace | A KV namespace is a key-value database replicated to Cloudflare’s global network. A KV namespace must require a binding and an id. | KV |
| largest contentful paint (LCP) | Largest contentful paint (LCP) is a web performance metric that measures the time it takes for the largest content element to be fully rendered and visible to the user during the loading of a web page. | Speed |
| latency | The delay between a user action and the corresponding response from the system. | Speed |
| layer 3 | The network layer in the OSI model, responsible for logical addressing, routing, and forwarding of data between devices on different networks. | Spectrum |
| layer 4 | The transport layer in the OSI model, managing end-to-end communication, error-checking, and flow control. | Spectrum |
| lazy loading | Loading images or other resources only when they are about to be displayed, rather than loading everything at once. | Speed |
| leaked credentials | Leaked credentials refers to sensitive authentication information disclosed in some way (for example, due to misconfigurations, data breaches, or simple human error), allowing other parties to gain access to digital resources.Credentials may include usernames, passwords, API keys, authentication tokens, or private keys. | WAF |
| legitimate traffic | Legitimate traffic refers to authorized and permissible network activity, data transmissions, or communications that adhere to established norms and rules within a given system or network. | Waiting Room |
| letter of agency | Sometimes referred to as a Letter of Authorization. A document that authorizes Cloudflare to advertise your prefixes. This is required so transit providers can accept the routes Cloudflare advertises on your behalf. | Magic Transit |
| LLM | A machine learning model that can comprehend and generate human language text. It works by analyzing massive data sets of language. | WAF |
| locally-managed tunnel | A Cloudflare Tunnel that was created by running `cloudflared tunnel create ` on the command line. Tunnel configuration is stored in your local `cloudflared` directory. | Cloudflare One |
| log | A chronological record of events, actions, or transactions, typically used for tracking and troubleshooting purposes. | Logs |
| log file | A file containing a collection of log entries, usually stored in a structured or semi-structured format. | Logs |
| logging | The process of recording events, actions, or transactions in a log. | Logs |
| LoRA Adapters | [LoRA Adapters](https://developers.cloudflare.com/workers-ai/fine-tunes/loras/) (Low-Rank Adaptation adapters) are used in machine learning to fine-tune models efficiently by adjusting a small number of parameters, allowing for customization of AI models in Workers AI.[Public LoRA Adapters](https://developers.cloudflare.com/workers-ai/fine-tunes/public-loras/) are pre-trained Low-Rank Adaptation adapters available for public use. | Workers AI |
| managed network | A network location, such as an office, that is associated with a specific WARP client device profile. | Cloudflare One |
| maximum segment size (MSS) | MSS limits the size of packets, or small chunks of data, that travel across a network, such as the Internet. | Magic WAN |
| Maximum Tokens | In generative AI, the user-defined property `max_tokens` defines the maximum number of tokens at which the model should stop responding. This limit cannot exceed the context window. | Workers AI |
| MCP client | A Model Context Protocol (MCP) client is an AI program that can request information and receive responses from an MCP server. Examples of MCP clients include Claude Desktop, Cursor AI, and Windsurf. | Cloudflare One |
| MCP server | A web application that allows AI agents to access third-party data sources and APIs using the Model Context Protocol (MCP). For example, you can use an MCP server to connect an AI assistant to your Google Drive account. | Cloudflare One |
| MCP server portal | A web application in Cloudflare One that serves as a gateway to multiple MCP servers. | Cloudflare One |
| MCP server tool | An integration provided by an MCP server which allows an AI agent to perform a limited set of actions on a third-party system. | Cloudflare One |
| MDM file | A Mobile Device Management (MDM) file is a configuration file that allows organizations to manage the software, settings, and certificates installed on their devices. | Cloudflare One |
| member or user | A member or user is an email account in Cloudflare that you can grant access to your organization account. Members belonging to multiple accounts can select which account to manage via the Cloudflare dashboard. | Fundamentals |
| Merchant of Record | The entity who facilitates "buying and selling". For pay per crawl, Cloudflare is the merchant of record. | AI Crawl Control |
| metadata | A metadata is a serializable value you append to each KV entry. | KV |
| MFA | Multi-factor authentication (MFA) checks multiple aspects of a user's identity, not only their username and password, before allowing them access to an application. | Cloudflare One |
| migration | A Durable Object migration is a mapping process from a class name to a runtime state. Initiate a Durable Object migration when you need to:- Create a new Durable Object class.
- Rename a Durable Object class.
- Delete a Durable Object class.
- Transfer an existing Durable Objects class. | Durable Objects |
| minification | The process of removing unnecessary characters from code (such as whitespace or comments) to reduce file size and improve loading times. | Speed |
| mitigated request | A request to which Cloudflare applied a terminating action such as block or challenge. | WAF |
| Model Catalog | [Model Catalog](https://developers.cloudflare.com/workers-ai/models/) is a curated collection of AI models available within Workers AI, providing developers with a variety of pre-trained models for different tasks. | Workers AI |
| module Worker | Refers to a Worker written in [module syntax](https://developers.cloudflare.com/workers/reference/migrate-to-module-workers/). | Workers |
| monitor | A monitor issues health monitor requests at regular intervals to evaluate the health of each endpoint within a [pool](https://developers.cloudflare.com/load-balancing/pools/).When a pool [becomes unhealthy](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/), your load balancer takes that pool out of the endpoint rotation. | Load Balancing |
| MQTT (Message Queuing Telemetry Transport) | A lightweight, publish-subscribe messaging protocol often used for communication in the Internet of Things (IoT) and other resource-constrained scenarios. | Spectrum |
| mTLS (mutual TLS) | [Mutual TLS (mTLS)](https://www.cloudflare.com/learning/access-management/what-is-mutual-tls/) authentication is a common security practice that uses client certificates to ensure traffic between client and server is bidirectionally secure and trusted. mTLS also allows requests that do not authenticate via an identity provider — such as Internet-of-things (IoT) devices — to demonstrate they can reach a given resource. | SSL/TLS |
| nameserver | A nameserver is a dedicated server that translates human readable hostnames (`www.example.com`) into IP addresses.Nameservers like root servers, TLD servers, and [authoritative nameservers](https://developers.cloudflare.com/dns/nameservers/) are fundamental components of the Domain Name System (DNS). | DNS |
| namespace | A logical collection of Durable Objects that all share the same Durable Object (class) definition. A single namespace can have (tens of) millions of Durable Objects. Metrics are scoped per namespace.- The binding name of the namespace (as it will be exposed inside Worker code) is defined in the Wrangler file under the `durable_objects.bindings.name` key. Note that the binding name may not uniquely identify a namespace within an account. Instead, each namespace has a unique namespace ID, which you can view from the Cloudflare dashboard.
- You can instantiate a unique Durable Object within a namespace using [Durable Object namespace methods](https://developers.cloudflare.com/durable-objects/api/namespace/#methods). | Durable Objects |
| NetFlow | Network protocol developed by Cisco to collect and monitor network traffic flow data. | Magic Network Monitoring |
| non-browser traffic | Non-browser traffic refers to data exchanges and communication occurring between devices or systems that do not involve web browsers, such as a mobile app or web apps. | Waiting Room |
| OAuth | A protocol for authorizing users, allowing them to perform actions and view data on different platforms without sharing credentials. | Cloudflare One |
| OIDC | OpenID Connect (OIDC) is an identity authentication protocol built on top of OAuth 2.0. It is used verifying user identity and obtaining basic profile information. | Cloudflare One |
| on-ramp | Refers to a way of connecting a business network to Cloudflare. Examples of on-ramps, or ways to connect to Cloudflare, are Anycast GRE tunnels, Anycast IPsec tunnels, Cloudflare Network Interconnect (CNI), Cloudflare Tunnel, and WARP. | Cloudflare One |
| on-ramp | Refers to a way of connecting a business network to Cloudflare. Examples of on-ramps, or ways to connect to Cloudflare, are Anycast GRE tunnels, Anycast IPsec tunnels, Cloudflare Network Interconnect (CNI), Cloudflare Tunnel, and WARP. | Magic WAN |
| Operator | The company or organization that owns and operates an AI crawler. Examples include OpenAI, Microsoft, Google, ByteDance, Anthropic, and Meta. In AI Crawl Control, crawlers are grouped by their operators. | AI Crawl Control |
| Organization Validated (OV) certificate | OV certificates are used by corporations or governments to portray an extra layer of confidence for their visitors. Rather than just validating domain ownership, the CA also validates the company’s registration using qualified independent information sources. The organization’s name is listed in the certificate. | SSL/TLS |
| origin | [Origin](https://www.cloudflare.com/learning/cdn/glossary/origin-server/) generally refers to the web server behind Cloudflare where your application is hosted. | Workers |
| origin bandwidth (origin egress bandwidth) | The amount of data transferred from the origin server to Cloudflare within a certain period of time. Origin bandwidth is the sum of all `EdgeResponseBytes` where `OriginResponseStatus` does not equal `0`. | Cache |
| origin certificate | A Cloudflare Origin Certificate is a free SSL/TLS certificate issued by Cloudflare that can be installed on your origin server to facilitate making sure your data is encrypted in transit from Cloudflare to your origin server using HTTPS. | SSL/TLS |
| origin request | An origin request is a request served from the origin server. | Fundamentals |
| origin response status code | An origin response status code is an HTTP response code sent from the origin server to Cloudflare. | Fundamentals |
| origin server | The original server where the web content is hosted before it is distributed to edge servers in a CDN. | Cache |
| origin/host server | The server where the website content is hosted. | Fundamentals |
| OSI model (Open Systems Interconnection model) | A conceptual framework that standardizes the functions of a telecommunication or computing system into seven abstraction layers. | Spectrum |
| output gate | When a storage write operation is in progress, any new outgoing network messages will be held back until the write has completed. We say that these messages are waiting for the "output gate" to open. If the write ultimately fails, the outgoing network messages will be discarded and replaced with errors, while the Durable Object will be shut down and restarted from scratch. | Durable Objects |
| PAC file | A file containing a JavaScript function which can instruct a browser to forward traffic to a proxy server instead of directly to the destination server. | Cloudflare One |
| page load time | The time it takes for a web page to fully load in a user's browser. | Speed |
| Pages | [Cloudflare Pages](https://developers.cloudflare.com/pages/) is Cloudflare's product offering for building and deploying full-stack applications. | Workers |
| paranoia level | Classifies rules of the OWASP managed ruleset according to their aggressiveness. | WAF |
| phishing | The practice of trying to acquire sensitive data through fraudulent emails or other means. Usually, the perpetrators try to pass for a legitimate company when asking for sensitive data. | Area 1 |
| plan | Plans distinguish the breadth of Cloudflare features accessible to a specific domain. Plan options include [Free, Pro, Business, or Enterprise](https://www.cloudflare.com/plans/). | Fundamentals |
| policy | A set of rules that regulate network activity, such as login access and website reachability. | Cloudflare One |
| policy-based routing | Policy-based routing (PBR) is a technique used to make routing decisions based on policies set by your administrador. | Magic Transit |
| pool | Within Cloudflare, pools represent your endpoints and how they are organized. As such, a pool can be a group of several endpoints, or you could also have only one endpoint (an origin server, for example) per pool.If you are familiar with DNS terminology, think of a pool as a “record set,” except Cloudflare only returns addresses that are considered healthy. You can attach health monitors to individual pools for customized monitoring. A pool can have either a single monitor or a monitor group attached — but not both. | Load Balancing |
| prefix | A number that identifies the network portion of an IP address. It tells devices if an IP address is on the same network or not. It is shown as a number after a slash (for example, `/31`) at the end of the IP address.Using an analogy, the prefix is like a street address. If an IP is in the same street, it belongs to the same network of devices. | Magic Transit |
| primary certificate / secondary certificate | Primary and secondary indicates the order in which Custom SSL certificates were uploaded to Cloudflare. The primary certificate is the first certificate added to a pack. The primary certificate defines the hostnames covered by the certificate. | SSL/TLS |
| primary database instance | The primary database instance is the original instance of a database. This database instance only exists in one location in the world. | D1 |
| producer | A producer is the term for a client that is publishing or producing messages on to a queue. | Queues |
| Prompt Engineering | [Prompt Engineering](https://developers.cloudflare.com/workers-ai/guides/prompting/) is the practice of designing and refining input prompts to effectively elicit desired responses from AI models. | Workers AI |
| prompt injection | The process of overwriting the system prompt for a large language model (LLM), which instructs the LLM on how to respond to user input. | WAF |
| Prompt Templates | [Prompt Templates](https://developers.cloudflare.com/workers-ai/guides/prompting/) are predefined structures that guide the input provided to AI models, enhancing consistency and effectiveness in responses. | Workers AI |
| protocol | A protocol is a set of rules governing the exchange or transmission of data between devices. | Fundamentals |
| proxy protocol | A protocol used by network proxies to convey client connection information to the destination server, facilitating proper handling of client requests. | Spectrum |
| proxy read timeout | A proxy read timeout is the maximum amount of time a proxy server waits for a response from the origin server before terminating the connection. | Fundamentals |
| proxy server | The server that sits between the origin server and the client. Cloudflare is a proxy server for example. | Fundamentals |
| proxy status | The proxy status of a DNS record defines whether requests for your domain will route through Cloudflare (`proxied`) or not (`DNS-only`).When a [DNS record is proxied](https://developers.cloudflare.com/dns/proxy-status/), requests are processed according to your configurations, and Cloudflare can optimize, cache, and protect your domain. Refer to [How Cloudflare works](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/) for details. | DNS |
| proxy write timeout | A proxy write timeout is the maximum amount of time a proxy server allows for sending data to the client before terminating the connection. | Fundamentals |
| public key / private key | SSL public and private keys are essentially long strings of characters used for encrypting and decrypting data. Data encrypted with the public key can only be decrypted with the private key, and vice versa. Private keys are kept secret and unshared. | SSL/TLS |
| purge | The process of removing outdated content from the cache to make room for updated content and ensure the delivery of the latest content. | Cache |
| Quarantine policies | Policies that block specific types of emails (usually malicious and suspicious emails), preventing emails from reaching the end-user or the next mail service provider. Emails that are quarantined are reviewed by administrators and potentially released if falsely flagged. | Cloudflare One |
| query planner | A component in a database management system which takes a user query and generates the most efficient plan of executing that query (the query plan). For example, the query planner decides which indices to use, or which table to access first. | D1 |
| queue | A queue is a buffer or list that automatically scales as messages are written to it, and allows a consumer Worker to pull messages from that same queue. | Queues |
| Queues | [Queues](https://developers.cloudflare.com/queues/) integrates with Cloudflare Workers and enables you to build applications that can guarantee delivery. | Workers |
| R2 | [R2](https://developers.cloudflare.com/r2/) is an S3-compatible distributed object storage designed to eliminate the obstacles of sharing data across clouds. | Workers |
| rate limiting | Rate limiting is a technique used in computer systems to control the rate at which requests are processed. It can be used as a security measure to prevent attacks, or to limit resource usage in your origin servers. | WAF |
| RDP | Remote Desktop Protocol (RDP) allows remote desktop connections to a computer, often used on Windows and Mac operating systems. | Cloudflare One |
| read replica | A read replica is an eventually-replicated copy of the primary database instance which only serve read requests. There may be multiple read replicas for a single primary database instance. | D1 |
| real user monitoring (RUM) | Real user monitoring (RUM) is a web performance monitoring technique that collects and analyzes data based on actual user interactions and experiences, providing insights into how users interact with a website or application in real-time. | Speed |
| redirect | URL redirects navigate the user from a source URL to a target URL using a given HTTP status code. URL redirection is also known as URL forwarding. | Fundamentals |
| reference architecture | A reference architecture provides a high-level view of how all or part of the Cloudflare platform is built and how Cloudflare products would fit into a customer's existing infrastructure. | Fundamentals |
| Referrals | Traffic referred to your website by AI services, identified by the referrer URL and whether it is owned by an AI operator. | AI Crawl Control |
| remotely-managed tunnel | A Cloudflare Tunnel whose configuration is stored on Cloudflare rather than on your local machine. You can manage the tunnel in the dashboard under **Networks** > **Connectors** or by using the API. | Cloudflare One |
| render time | The time it takes for a browser to display a fully rendered web page after receiving the necessary resources. | Speed |
| replica lag | The time it takes for the primary database instance to replicate its changes to a specific read replica. | D1 |
| request | A request is a message that is sent between a client, or web browser, to a server. Each request that has been processed through the Cloudflare network generates a record. | Fundamentals |
| Resource Public Key Infrastructure (RPKI) | A cryptographic method of signing records that associate a route with an originating autonomous system number. | BYOIP |
| REST API | [REST API](https://developers.cloudflare.com/workers-ai/get-started/rest-api/) is an application programming interface that allows developers to interact with Workers AI services over HTTP, enabling model management and inference requests. | Workers AI |
| reverse proxy | A server that handles requests on behalf of clients, forwarding them to backend servers and managing tasks like load balancing and security. | Spectrum |
| robots.txt | A text file which lists pages in your website that are off-limits for bots. Well-behaved bots respect this file, but some bots may violate it. You can enforce `robots.txt` with Cloudflare WAF custom rules. | AI Crawl Control |
| roles | Authorize which Cloudflare products and features a member is allowed to access in a Cloudflare account. Learn more about [roles](https://developers.cloudflare.com/fundamentals/manage-members/roles/). | Fundamentals |
| rollback | [Rollbacks](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/rollbacks/) are a way to deploy an older deployment to the Cloudflare global network. | Workers |
| root certificate | A root certificate is generated by a CA and is used to sign certificates. Every browser includes a root store of trusted root certificates. Any certificate signed with the private key of a root certificate is automatically trusted by a browser. | SSL/TLS |
| Route Origin Authorization (ROA) | The RPKI-signed object that states an autonomous system is authorized to originate a particular IP address prefix or set of prefixes. | BYOIP |
| rule characteristics | The set of parameters of a rate limiting rule that define how Cloudflare tracks the rate for the rule. | WAF |
| Rule group | A set of Access rules that can be configured once and then quickly applied across many Access policies. | Cloudflare One |
| SafeSearch | SafeSearch is a feature of search engines that filters explicit or offensive content from search results. | Cloudflare One |
| SAML | Security Assertion Markup Language (SAML) enables single sign-on and authentication for multiple applications. | Cloudflare One |
| sampling | In the context of Magic Network Monitoring, sampling is the process of taking samples of packets for a specific period to identify potential attacks. | Magic Network Monitoring |
| SASE | Secure Access Service Edge (SASE) is a cloud-based security model bundling networking and security functions. | Cloudflare One |
| saved bandwidth (saved egress bandwidth) | The percentage of bandwidth saved by caching on the Cloudflare network. | Cache |
| SCIM | System for Cross-domain Identity Management (SCIM) is an open standard protocol that allows identity providers (such as Okta or Microsoft Entra ID) to synchronize user identity information with cloud applications and services. | Cloudflare One |
| search engine optimization (SEO) | SEO, or search engine optimization, is the practice of optimizing online content to improve its visibility and ranking in search engine results, thereby increasing organic traffic and relevance. | Speed |
| seat | A unique, billable user within your Zero Trust organization who has performed [an authentication event](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/seat-management/#authentication-events). Service tokens do not consume seats. | Cloudflare One |
| secret | [Secrets](https://developers.cloudflare.com/workers/configuration/secrets/) are a type of binding that allow you to attach encrypted text values to your Worker. | Workers |
| secret key | The secret key allows communication between your application backend and the Cloudflare Turnstile server to validate the widget response. | Turnstile |
| Secure Sockets Layer (SSL) | SSL was a widely used cryptographic protocol for providing data security for Internet communications. SSL was superseded by TLS; however, most people still refer to Internet cryptographic protocols as SSL. | SSL/TLS |
| SEO crawlers | SEO crawlers, or web crawlers, are automated programs employed by search engines to systematically browse and index web content, gathering information about the structure and relevance of pages to determine search result rankings. | Waiting Room |
| Server Name Indication (SNI) | SNI allows a server to host multiple TLS Certificates for multiple websites using a single IP address. SNI adds the website hostname in the TLS handshake to inform the server which website to present when using shared IPs.Cloudflare uses SNI for all Universal SSL certificates. | SSL/TLS |
| server response time | The time it takes for a server to respond to a request from a user's browser. | Speed |
| Serverless GPUs | [Serverless GPUs](https://developers.cloudflare.com/workers-ai/) are graphics processing units provided by Cloudflare in a serverless environment, enabling scalable and efficient execution of machine learning models without the need for managing underlying hardware. | Workers AI |
| Service Level Agreement (SLA) | An SLA is a contractual obligation for Cloudflare to maintain a specific level of service. Read the [Service Level Agreement (SLA) for the Cloudflare Business plan](https://www.cloudflare.com/business-sla/). Enterprise customers refer to the Enterprise SLA provided with their contract. | Fundamentals |
| service provider (SP) | A service provider (SP) provides federated access to an application for a user from an identity provider (IdP). | Cloudflare One |
| service token | Authentication credentials generated by Cloudflare Access which enable automated systems to access protected applications. | Cloudflare One |
| service Worker | Refers to a Worker written in [service worker](https://developer.mozilla.org/en-US/docs/Web/API/Service_Worker_API) [syntax](https://developers.cloudflare.com/workers/reference/migrate-to-module-workers/). | Workers |
| session | An event generated when a user logs in to an Access application. | Cloudflare One |
| session | A session encapsulates all the queries from one logical session for your application. For example, a session may correspond to all queries coming from a particular web browser session. | D1 |
| session identifier | A session identifier is a unique identifier that a website assigns to identify a specific user for the duration of their visit. | API Shield |
| Set-Cookie | Set-Cookie is an HTTP header used by web servers to send a cookie to a user's browser during an HTTP response, enabling the server to store information on the client side, often used for session management and user preferences. | Waiting Room |
| sFlow | An industry standard packet sampling protocol to monitor network devices. | Magic Network Monitoring |
| SFTP (Secure File Transfer Protocol) | A secure file transfer protocol that uses the Secure Socket Shell (SSH) protocol for encryption and authentication. | Spectrum |
| shadow IT | Shadow IT is the unsanctioned use of software, hardware, or other systems and services within an organization, often without the knowledge of that organization's information technology (IT) department.For more information, refer to the [Cloudflare Learning Center](https://www.cloudflare.com/learning/access-management/what-is-shadow-it/). | Cloudflare One |
| SIEM | A Security Information and Event Management (SIEM) solution collects, analyzes, and correlates data to help manage security incidents, detect anomalies, and meet compliance requirements. | WAF |
| sitekey | The sitekey is used to invoke Turnstile on your site. | Turnstile |
| SMB | Secure Messaging Block (SMB) is a network file sharing protocol used for accessing files and services on a network. | Cloudflare One |
| SMTP | Stands for Simple Mail Transfer Protocol. It is an Internet standard based on TCP/IP to send and receive email. | Area 1 |
| SMTP Server (Simple Mail Transfer Protocol Server) | A server responsible for sending, receiving, and relaying email messages over a network, following the SMTP protocol. | Spectrum |
| Snippets subrequest | Any request that a Snippet makes to either Internet resources using the Fetch API or requests to other Cloudflare services. | Rules |
| source endpoint | The source endpoint is the endpoint managed by API Shield in Endpoint Management by its routing feature. | API Shield |
| speed index | Speed index is a web performance metric that quantifies how quickly a user perceives a webpage to load by measuring the visual progression of content rendering over time, providing a comprehensive assessment of the overall user experience during page loading. | Speed |
| SQL API | API methods part of Storage API that support SQL querying. | Durable Objects |
| SSH | Secure Shell (SSH) protocol allows users to connect to infrastructure remotely and execute commands. | Cloudflare One |
| SSO | Single Sign-On (SSO) is a technology that combines multiple application logins into one, requiring users to enter credentials only once. | Cloudflare One |
| static content | Static content, like images, stylesheets, and JavaScript, remains the same for all users. It can be directly served from the cache without fetching from the origin server because it does not change without manual intervention. | Cache |
| static route | A fixed configuration to route traffic through Anycast tunnels from Cloudflare global network to the customer's locations. | Magic WAN |
| step | A step is self-contained, individually retriable component of a Workflow. Steps may emit (optional) state that allows a Workflow to persist and continue from that step, even if a Workflow fails due to a network or infrastructure issue. A Workflow can have one or more steps up to the [step limit](https://developers.cloudflare.com/workflows/reference/limits/). | Workflows |
| Storage API | The transactional and strongly consistent (serializable) [Storage API](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/) for persisting data within each Durable Object. State stored within a unique Durable Object is "private" to that Durable Object, and not accessible from other Durable Objects.Storage API includes key-value (KV) API, SQL API, and point-in-time-recovery (PITR) API.- Durable Object classes with the key-value storage backend can use KV API.
- Durable Object classes with the SQLite storage backend can use KV API, SQL API, and PITR API. | Durable Objects |
| Storage Backend | By default, a Durable Object class can use Storage API that leverages a key-value storage backend. New Durable Object classes can opt-in to using a [SQLite storage backend](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#sqlite-storage-backend). | Durable Objects |
| stub | An object that refers to a unique Durable Object within a namespace and allows you to call into that Durable Object via RPC methods or the `fetch` API. For example, `let stub = env.MY_DURABLE_OBJECT.get(id)` | Durable Objects |
| Subject Alternative Names (SANs) | The SAN field of an SSL certificate specifies additional hostnames (sites, IP addresses, common names, subdomains, apex domains, etc.) protected by a single SSL Certificate. | SSL/TLS |
| subnet | Also known as subnetwork. It refers to a network that is part of another network. | Magic WAN |
| subrequest | A subrequest is any request that a Worker makes to either Internet resources using the [Fetch API](https://developers.cloudflare.com/workers/runtime-apis/fetch/) or requests to other Cloudflare services like [R2](https://developers.cloudflare.com/r2/), [KV](https://developers.cloudflare.com/kv/), or [D1](https://developers.cloudflare.com/d1/). | Workers |
| SYN (Synchronize) | The initial step in establishing a TCP connection, where a device requests a connection with another by sending a SYN packet. | Spectrum |
| SYN-ACK (Synchronize-Acknowledge) | The second step in the TCP three-way handshake, where the server responds to a SYN request with a SYN-ACK packet. | Spectrum |
| synthetic test | A synthetic test is an artificial simulation of user interactions and system behaviors designed to evaluate and measure the performance, responsiveness, and functionality of a website or application under controlled conditions. | Speed |
| Tail Worker | A [Tail Worker](https://developers.cloudflare.com/workers/observability/logs/tail-workers/) receives information about the execution of other Workers (known as producer Workers), such as HTTP statuses, data passed to `console.log()` or uncaught exceptions. | Workers |
| target | A resource with an IP address or hostname that is reachable by Cloudflare, such as a server or web application. | Cloudflare One |
| target endpoint | The target endpoint is the ultimate destination that a request is sent to by API Shield's routing feature. | API Shield |
| target hostname | A label used to identify a set of targets in an Access for Infrastructure application. | Cloudflare One |
| TCP (Transmission Control Protocol) | A connection-oriented protocol in the transport layer of the Internet Protocol Suite, providing reliable and ordered delivery of data between devices. | Spectrum |
| TCP Fast Open (TFO) | TCP Fast Open (TFO) is a protocol extension that can significantly improve the speed of establishing TCP connections by allowing data to be sent in the initial SYN packet, rather than requiring a separate handshake before data transmission begins. | Fundamentals |
| TCP Keep-Alive | A TCP keep-alive is used to maintain a connection between two endpoints by sending packets to check if the connection is still active. This helps prevent idle connections from being prematurely closed. If a response is not received after a defined period, the connection is terminated. | Fundamentals |
| TCP RST (reset) | A TCP Reset (RST) packet is used by a TCP sender to close a connection. | Fundamentals |
| TCP three-way handshake | TCP uses a three-way handshake to establish a reliable connection (SYN, SYN-ACK, ACK) over an IP based connection. SYN is short for synchronize, and ACK is short for acknowledgement. | Fundamentals |
| team domain | A unique subdomain assigned to your Cloudflare account (for example, `.cloudflareaccess.com`), where users will find the apps you have secured behind Cloudflare One. | Cloudflare One |
| team name | The customizable portion of your team domain (`.cloudflareaccess.com`). You can view your team name in Cloudflare One under **Settings**. | Cloudflare One |
| Terraform | An infrastructure as code software tool that allows you to deploy services from different providers using a standardized configuration syntax. | Cloudflare One |
| threat score | The threat score was a score from `0` (zero risk) to `100` (high risk) classifying the IP reputation of a visitor. Currently, the threat score is always `0` (zero). | WAF |
| time to first byte (TTFB) | Time to first byte (TTFB) is the duration measured from the initiation of a web page request to the moment the first byte of data is received by the user's browser from the web server, indicating the server's initial response time. | Speed |
| time to interactive (TTI) | Time to interactive (TTI) is a web performance metric that measures the time it takes for a web page to become fully interactive and responsive to user input, indicating when users can effectively engage with and use the page. | Speed |
| time-to-live (TTL) | The duration for which a cached copy of a resource is considered valid before it needs to be refreshed or revalidated. | Cache |
| timestamp | A data field indicating the date and time when an event occurred, often used for sequencing and analysis. | Logs |
| TLS (Transport Layer Security) | TLS is a cryptographic protocol that ensures data security over a computer network, such as the Internet. It encrypts the data that is transmitted between a user's computer and a web server. | SSL/TLS |
| total bandwidth (total egress bandwidth, edge bandwidth) | Total bandwidth is the amount of data transferred from Cloudflare to end users within a certain period of time. Total bandwidth equals the sum of all `EdgeResponseBytes` for a certain period of time. | Cache |
| total blocking time (TBT) | Total blocking time (TBT) is a web performance metric that measures the total amount of time between First Contentful Paint (FCP) and Time to Interactive (TTI) where the main thread was blocked for long enough to prevent input responsiveness. | Speed |
| traffic | Traffic is the data sent and received by visitors to a website. Cloudflare serves and protects this data as it passes through the Cloudflare network. | Fundamentals |
| traffic management | The process of controlling and optimizing the flow of network data to ensure efficient and reliable communication. | Waiting Room |
| traffic steering | Cloudflare evaluates your route's health and steers traffic according to priorities defined by you and / or tunnel health. | Magic WAN |
| tunnel | A secure pathway for network traffic to flow between a device and Cloudflare's global network. | Cloudflare One |
| tunnel health-check | A probe sent by Cloudflare to check for tunnel health. If a tunnel is not considered healthy, Cloudflare reroutes traffic to one that is considered healthy. | Magic WAN |
| tutorial | A tutorial is a practical lesson that takes you from a clear starting to ending point.The goal is to connect products to real-world scenarios to meet a user’s goal. | Fundamentals |
| two-factor authentication (2FA) | Two-factor authentication (2FA) is a security process in which a user provides two different authentication factors to verify their identity. In addition to something you know, typically your password, 2FA adds an extra layer of security to user logins by requiring users to also present something they have, such as Yubikey or a one-time login code, or something you are, such as a fingerprint.It adds an extra layer of security to user logins by requiring users to present two or more separate pieces of evidence (factors) that establish their identity. | Fundamentals |
| UDP (User Datagram Protocol) | UDP (User Datagram Protocol) is a connectionless transport layer protocol that provides fast and lightweight data transmission between devices on a network, prioritizing speed over reliability. | Spectrum |
| uncached bandwidth (uncached egress bandwidth) | Uncached bandwidth is the amount of bandwidth that is not cached and therefore is served from the origin. Uncached bandwidth is the sum of all `EdgeResponseBytes` where `CacheCacheStatus` does not equal `hit`, `stale`, `updating`, `ignored`, or `revalidated`. | Cache |
| uncached requests | Uncached requests are requests that are not cached and therefore are served from the origin server. Uncached requests are the sum of all requests where `CacheCacheStatus` does not equal to `hit`, `stale`, `updating`, or `ignored`. | Cache |
| Unicast Reverse Path Forwarding (uRPF) | A security feature that can prevent spoofing attacks. | BYOIP |
| Universal SSL certificate | By default, Cloudflare issues — and [renews](https://developers.cloudflare.com/ssl/reference/certificate-validity-periods/#universal-ssl) — free, unshared, publicly trusted SSL certificates to all domains [added to](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/) and [activated on](https://developers.cloudflare.com/dns/zone-setups/reference/domain-status/) Cloudflare. | SSL/TLS |
| URL normalization | The process of modifying the URLs of incoming requests so that they conform to a consistent formatting standard. | Rules |
| URL rewrite | An operation performed by a server that converts a source URL into a target URL. | Rules |
| User risk score | Ranks the likelihood of a user to introduce risk to your organization's systems and data based on the detection of security risk behaviors. Risk scores add user and entity behavior analytics (UEBA) to the Cloudflare One platform. | Cloudflare One |
| User risk score level | Cloudflare One assigns a risk score of Low, Medium or High based on detections of users' activities, posture, and settings. A user's risk score is equal to the highest-level risk behavior they trigger. | Cloudflare One |
| V8 | Chrome V8 is a [JavaScript engine](https://www.cloudflare.com/learning/serverless/glossary/what-is-chrome-v8/), which means that it [executes JavaScript code](https://developers.cloudflare.com/workers/reference/how-workers-works/). | Workers |
| validation level | The level to which a certificate authority validates domain ownership before issuing an SSL/TLS certificate.The different certificate validation levels are DV (Domain Validated), OV (Organization Validated), or EV (Extended Validation). | SSL/TLS |
| verified bot | Bots that are transparent about who they are and what they do. | Bots |
| version | A [version](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/#versions) is defined by the state of code as well as the state of configuration in a Worker's Wrangler file. | Workers |
| Virtual network | A software abstraction that allows you to logically segregate resources on a private network. Virtual networks are especially useful for exposing resources which have overlapping IP routes. | Cloudflare One |
| Virtual Private Cloud | A logically isolated section of cloud infrastructure that provides secure, private networking within a public cloud environment. | Workers VPC |
| Virtual Private Cloud (VPC) | A secure, isolated private network hosted on public cloud infrastructure. Examples of public cloud providers include Google Cloud, AWS, and Microsoft Azure. | Cloudflare One |
| Virtual Private Network (VPN) | A tool that allows users to send and receive data across shared or public networks as if their devices were directly connected to the private network. For example, employees working from home can use a VPN to access files on the corporate network. | Cloudflare One |
| virtual waiting room | A virtual waiting room is an online system or feature that manages and controls access to a website or service during periods of high traffic, preventing server overload by placing users in a queue until they can be accommodated, ensuring a more equitable and efficient user experience. | Waiting Room |
| wall-clock time | [Wall-clock time](https://developers.cloudflare.com/workers/platform/limits/#duration) is the total amount of time from the start to end of an invocation of a Worker. | Workers |
| WAN | Stands for Wide Area Network. It refers to a computer network that connects groups of computers over large distances. WANs are often used by businesses to connect their office networks. The objective is to make each of the local area networks (LANs) be remotely connected and accessible. | Magic WAN |
| WARP CGNAT IP | A unique, virtual IP address assigned to each WARP device from the `100.96.0.0/12` range. | Cloudflare One |
| WARP client | An application that connects corporate devices to Cloudflare for private network access, advanced web filtering, and other security functions. | Cloudflare One |
| WARP Connector | An extension of the WARP client used to establish site-to-site, bidirectional, and mesh networking connectivity. WARP Connector software installs on a Linux server within a private network, which then becomes a gateway for other local networks that need to on-ramp traffic to Cloudflare. | Cloudflare One |
| website | A website is a collection of web pages and related content that is identified by a common domain name and published on at least one web server. | Fundamentals |
| Worker Bindings | [Worker Bindings](https://developers.cloudflare.com/workers-ai/configuration/bindings/) are configurations that connect Workers scripts to external resources, such as AI models, enabling seamless integration and functionality. | Workers AI |
| workerd | [`workerd`](https://github.com/cloudflare/workerd?cf_target_id=D15F29F105B3A910EF4B2ECB12D02E2A) is a JavaScript / Wasm server runtime based on the same code that powers Cloudflare Workers. | Workers |
| Workers AI | [Workers AI](https://developers.cloudflare.com/workers-ai/) is a Cloudflare service that enables running machine learning models on Cloudflare's global network, utilizing serverless GPUs. It allows developers to integrate AI capabilities into their applications using Workers, Pages, or via the REST API. | Workers AI |
| Workers KV | [Workers KV](https://developers.cloudflare.com/kv/)is a data storage that allows you to store and retrieve data globally. | Workers AI |
| Workflow | The named Workflow definition, associated with a single Workers script. | Workflows |
| Wrangler | [Wrangler](https://developers.cloudflare.com/learning-paths/workers/get-started/c3-and-wrangler/) is the Cloudflare Developer Platform command-line interface (CLI) that allows you to manage projects, such as Workers, created from the Cloudflare Developer Platform product offering. | Workers |
| Wrangler CLI | [Wrangler CLI](https://developers.cloudflare.com/workers-ai/get-started/workers-wrangler/) is a command-line tool for building and deploying Cloudflare Workers, facilitating the integration of AI models into applications. | Workers AI |
| wrangler.toml / wrangler.json / wrangler.jsonc | The [configuration](https://developers.cloudflare.com/workers/wrangler/configuration/) used to customize the development and deployment setup for a Worker or a Pages Function. | Workers |
| Zero Trust Security | Zero Trust Security is an IT security model that requires strict identity verification for every person and device accessing resources on a network. | Cloudflare One |
| zone | A zone is a portion of DNS namespace that is managed by a specific organization or administrator. | Fundamentals |
| zone apex | Zone apex refers to the domain or subdomain on which the control of DNS records starts. | DNS |
---
title: Changelogs | Cloudflare Docs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/
md: https://developers.cloudflare.com/changelog/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)
Select...

Feb 06, 2026
1. ### [Visualize data, share links, and create exports with the new Workers Observability dashboard](https://developers.cloudflare.com/changelog/2026-02-06-observability-ui-refresh/)
[Workers](https://developers.cloudflare.com/workers/)
The [Workers Observability dashboard](https://dash.cloudflare.com/?to=/:account/workers-and-pages/observability/) has some major updates to make it easier to debug your application's issues and share findings with your team.

You can now:
* **Create visualizations** — Build charts from your Worker data directly in a Worker's Observability tab
* **Export data as JSON or CSV** — Download logs and traces for offline analysis or to share with teammates
* **Share events and traces** — Generate direct URLs to specific events, invocations, and traces that open standalone pages with full context
* **Customize table columns** — Improved field picker to add, remove, and reorder columns in the events table
* **Expandable event details** — Expand events inline to view full details without leaving the table
* **Keyboard shortcuts** — Navigate the dashboard with hotkey support

These updates are now live in the Cloudflare dashboard, both in a Worker's Observability tab and in the account-level Observability dashboard for a unified experience. To get started, go to **Workers & Pages** > select your Worker > **Observability**.
Feb 04, 2026
1. ### [Cloudflare Queues now available on Workers Free plan](https://developers.cloudflare.com/changelog/2026-02-04-queues-free-plan/)
[Queues](https://developers.cloudflare.com/queues/)
[Cloudflare Queues](https://developers.cloudflare.com/queues) is now part of the Workers free plan, offering guaranteed message delivery across up to **10,000 queues** to either [Cloudflare Workers](https://developers.cloudflare.com/workers) or [HTTP pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers). Every Cloudflare account now includes **10,000 operations per day** across reads, writes, and deletes. For more details on how each operation is defined, refer to [Queues pricing](https://developers.cloudflare.com/workers/platform/pricing/#queues).
All features of the existing Queues functionality are available on the free plan, including unlimited [event subscriptions](https://developers.cloudflare.com/queues/event-subscriptions/). Note that the maximum retention period on the free tier, however, is 24 hours rather than 14 days.
If you are new to Cloudflare Queues, follow [this guide](https://developers.cloudflare.com/queues/get-started/) or try one of our [tutorials](https://developers.cloudflare.com/queues/tutorials/) to get started.
Feb 04, 2026
1. ### [Visualize your Workflows in the Cloudflare dashboard](https://developers.cloudflare.com/changelog/2026-02-03-workflows-visualizer/)
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
Cloudflare Workflows now automatically generates visual diagrams from your code
Your Workflow is parsed to provide a visual map of the Workflow structure, allowing you to:
* Understand how steps connect and execute
* Visualize loops and nested logic
* Follow branching paths for conditional logic

You can collapse loops and nested logic to see the high-level flow, or expand them to see every step.
Workflow diagrams are available in beta for all JavaScript and TypeScript Workflows. Find your Workflows in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/workers/workflows) to see their diagrams.
Feb 03, 2026
1. ### [Agents SDK v0.3.7: Workflows integration, synchronous state, and scheduleEvery()](https://developers.cloudflare.com/changelog/2026-02-03-agents-workflows-integration/)
[Agents ](https://developers.cloudflare.com/agents/)[Workflows](https://developers.cloudflare.com/workflows/)
The latest release of the [Agents SDK](https://github.com/cloudflare/agents) brings first-class support for [Cloudflare Workflows](https://developers.cloudflare.com/workflows/), synchronous state management, and new scheduling capabilities.
#### Cloudflare Workflows integration
Agents excel at real-time communication and state management. Workflows excel at durable execution. Together, they enable powerful patterns where Agents handle WebSocket connections while Workflows handle long-running tasks, retries, and human-in-the-loop flows.
Use the new `AgentWorkflow` class to define workflows with typed access to your Agent:
* JavaScript
```js
import { AgentWorkflow } from "agents/workflows";
export class ProcessingWorkflow extends AgentWorkflow {
async run(event, step) {
// Call Agent methods via RPC
await this.agent.updateStatus(event.payload.taskId, "processing");
// Non-durable: progress reporting to clients
await this.reportProgress({ step: "process", percent: 0.5 });
this.broadcastToClients({ type: "update", taskId: event.payload.taskId });
// Durable via step: idempotent, won't repeat on retry
await step.mergeAgentState({ taskProgress: 0.5 });
const result = await step.do("process", async () => {
return processData(event.payload.data);
});
await step.reportComplete(result);
return result;
}
}
```
* TypeScript
```ts
import { AgentWorkflow } from "agents/workflows";
import type { AgentWorkflowEvent, AgentWorkflowStep } from "agents/workflows";
export class ProcessingWorkflow extends AgentWorkflow {
async run(event: AgentWorkflowEvent, step: AgentWorkflowStep) {
// Call Agent methods via RPC
await this.agent.updateStatus(event.payload.taskId, "processing");
// Non-durable: progress reporting to clients
await this.reportProgress({ step: "process", percent: 0.5 });
this.broadcastToClients({ type: "update", taskId: event.payload.taskId });
// Durable via step: idempotent, won't repeat on retry
await step.mergeAgentState({ taskProgress: 0.5 });
const result = await step.do("process", async () => {
return processData(event.payload.data);
});
await step.reportComplete(result);
return result;
}
}
```
Start workflows from your Agent with `runWorkflow()` and handle lifecycle events:
* JavaScript
```js
export class MyAgent extends Agent {
async startTask(taskId, data) {
const instanceId = await this.runWorkflow("PROCESSING_WORKFLOW", {
taskId,
data,
});
return { instanceId };
}
async onWorkflowProgress(workflowName, instanceId, progress) {
this.broadcast(JSON.stringify({ type: "progress", progress }));
}
async onWorkflowComplete(workflowName, instanceId, result) {
console.log(`Workflow ${instanceId} completed`);
}
async onWorkflowError(workflowName, instanceId, error) {
console.error(`Workflow ${instanceId} failed:`, error);
}
}
```
* TypeScript
```ts
export class MyAgent extends Agent {
async startTask(taskId: string, data: string) {
const instanceId = await this.runWorkflow("PROCESSING_WORKFLOW", {
taskId,
data,
});
return { instanceId };
}
async onWorkflowProgress(
workflowName: string,
instanceId: string,
progress: unknown,
) {
this.broadcast(JSON.stringify({ type: "progress", progress }));
}
async onWorkflowComplete(
workflowName: string,
instanceId: string,
result?: unknown,
) {
console.log(`Workflow ${instanceId} completed`);
}
async onWorkflowError(
workflowName: string,
instanceId: string,
error: unknown,
) {
console.error(`Workflow ${instanceId} failed:`, error);
}
}
```
Key workflow methods on your Agent:
* `runWorkflow(workflowName, params, options?)` — Start a workflow with optional metadata
* `getWorkflow(workflowId)` / `getWorkflows(criteria?)` — Query workflows with cursor-based pagination
* `approveWorkflow(workflowId)` / `rejectWorkflow(workflowId)` — Human-in-the-loop approval flows
* `pauseWorkflow()`, `resumeWorkflow()`, `terminateWorkflow()` — Workflow control
#### Synchronous setState()
State updates are now synchronous with a new `validateStateChange()` validation hook:
* JavaScript
```js
export class MyAgent extends Agent {
validateStateChange(oldState, newState) {
// Return false to reject the change
if (newState.count < 0) return false;
// Return modified state to transform
return { ...newState, lastUpdated: Date.now() };
}
}
```
* TypeScript
```ts
export class MyAgent extends Agent {
validateStateChange(oldState: State, newState: State): State | false {
// Return false to reject the change
if (newState.count < 0) return false;
// Return modified state to transform
return { ...newState, lastUpdated: Date.now() };
}
}
```
#### scheduleEvery() for recurring tasks
The new `scheduleEvery()` method enables fixed-interval recurring tasks with built-in overlap prevention:
* JavaScript
```js
// Run every 5 minutes
await this.scheduleEvery("syncData", 5 * 60 * 1000, { source: "api" });
```
* TypeScript
```ts
// Run every 5 minutes
await this.scheduleEvery("syncData", 5 * 60 * 1000, { source: "api" });
```
#### Callable system improvements
* **Client-side RPC timeout** — Set timeouts on callable method invocations
* **`StreamingResponse.error(message)`** — Graceful stream error signaling
* **`getCallableMethods()`** — Introspection API for discovering callable methods
* **Connection close handling** — Pending calls are automatically rejected on disconnect
- JavaScript
```js
await agent.call("method", [args], {
timeout: 5000,
stream: { onChunk, onDone, onError },
});
```
- TypeScript
```ts
await agent.call("method", [args], {
timeout: 5000,
stream: { onChunk, onDone, onError },
});
```
#### Email and routing enhancements
**Secure email reply routing** — Email replies are now secured with HMAC-SHA256 signed headers, preventing unauthorized routing of emails to agent instances.
**Routing improvements:**
* `basePath` option to bypass default URL construction for custom routing
* Server-sent identity — Agents send `name` and `agent` type on connect
* New `onIdentity` and `onIdentityChange` callbacks on the client
- JavaScript
```js
const agent = useAgent({
basePath: "user",
onIdentity: (name, agentType) => console.log(`Connected to ${name}`),
});
```
- TypeScript
```ts
const agent = useAgent({
basePath: "user",
onIdentity: (name, agentType) => console.log(`Connected to ${name}`),
});
```
#### Upgrade
To update to the latest version:
```sh
npm i agents@latest
```
For the complete Workflows API reference and patterns, see [Run Workflows](https://developers.cloudflare.com/agents/api-reference/run-workflows/).
Feb 03, 2026
1. ### [Improve Global Upload Performance with R2 Local Uploads - Now in Open Beta](https://developers.cloudflare.com/changelog/2026-02-03-r2-local-uploads/)
[R2](https://developers.cloudflare.com/r2/)
[Local Uploads](https://developers.cloudflare.com/r2/buckets/local-uploads/) is now available in open beta. Enable it on your [R2](https://developers.cloudflare.com/r2/) bucket to improve upload performance when clients upload data from a different region than your bucket. With Local Uploads enabled, object data is written to storage infrastructure near the client, then asynchronously replicated to your bucket. The object is immediately accessible and remains strongly consistent throughout. Refer to [How R2 works](https://developers.cloudflare.com/r2/how-r2-works/) for details on how data is written to your bucket.
In our tests, we observed **up to 75% reduction in Time to Last Byte (TTLB)** for upload requests when Local Uploads is enabled.
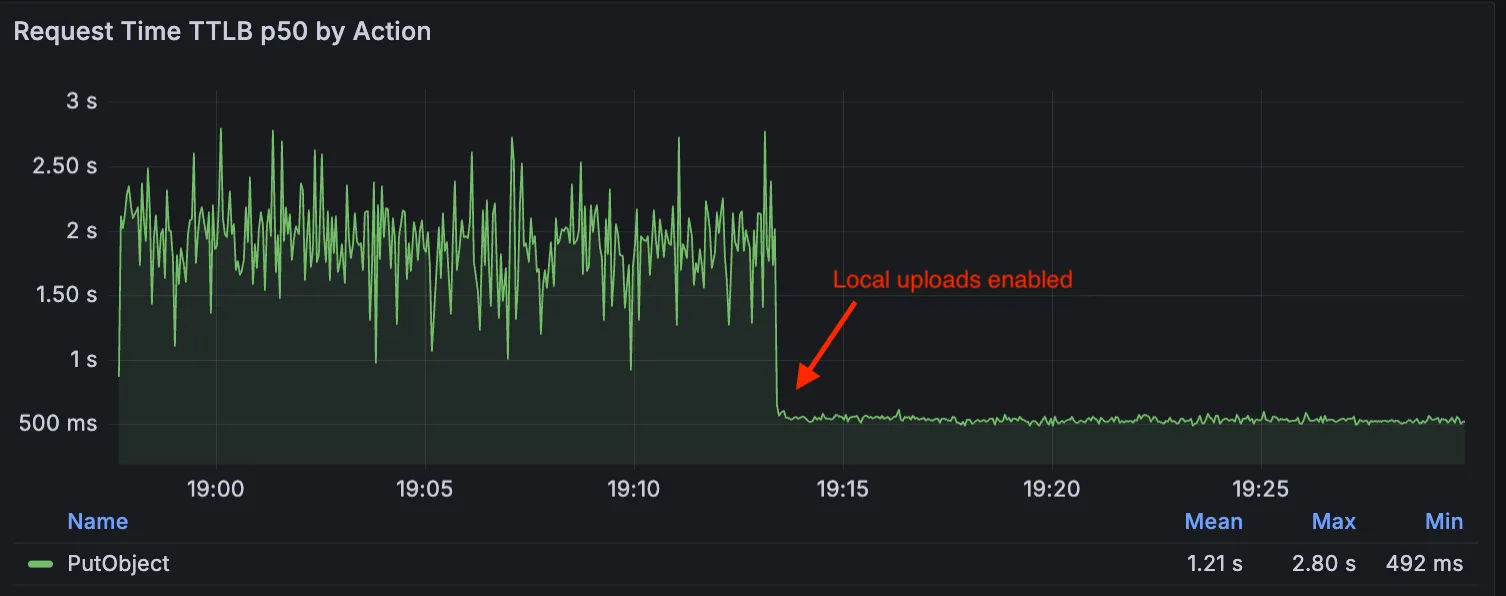
This feature is ideal when:
* Your users are globally distributed
* Upload performance and reliability is critical to your application
* You want to optimize write performance without changing your bucket's primary location
To enable Local Uploads on your bucket, find **Local Uploads** in your bucket settings in the [Cloudflare Dashboard](https://dash.cloudflare.com/?to=/:account/r2/overview), or run:
```sh
npx wrangler r2 bucket local-uploads enable
```
Enabling Local Uploads on a bucket is seamless: existing uploads will complete as expected and there’s no interruption to traffic. There is no additional cost to enable Local Uploads. Upload requests incur the standard [Class A operation costs](https://developers.cloudflare.com/r2/pricing/) same as upload requests made without Local Uploads.
For more information, refer to [Local Uploads](https://developers.cloudflare.com/r2/buckets/local-uploads/).
Feb 03, 2026
1. ### [Threat actor identification with "also known as" aliases](https://developers.cloudflare.com/changelog/2026-02-03-threat-actor-name-mapping/)
[Security Center](https://developers.cloudflare.com/security-center/)
Identifying threat actors can be challenging, because naming conventions often vary across the security industry. To simplify your research, **Cloudflare Threat Events** now include an **Also known as** field, providing a list of common aliases and industry-standard names for the groups we track.
This new field is available in both the Cloudflare dashboard and via the API. In the dashboard, you can view these aliases by expanding the event details side panel (under the **Attacker** field) or by adding it as a column in your configurable table view.
#### Key benefits
* Easily map Cloudflare-tracked actors to the naming conventions used by other vendors without manual cross-referencing.
* Quickly identify if a detected threat actor matches a group your team is already monitoring via other intelligence feeds.
For more information on how to access this data, refer to the [Threat Events API documentation](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/threat_events/).
Feb 03, 2026
1. ### [WAF Release - Scheduled changes for 2026-02-09](https://developers.cloudflare.com/changelog/scheduled-waf-release/)
[WAF](https://developers.cloudflare.com/waf/)
| Announcement Date | Release Date | Release Behavior | Legacy Rule ID | Rule ID | Description | Comments |
| - | - | - | - | - | - | - |
| 2026-02-03 | 2026-02-09 | Log | N/A | a219dd28a0694faea0f942d4b0089874 | Zimbra - Local File Inclusion - CVE:CVE-2025-68645 | This is a new detection. |
| 2026-02-03 | 2026-02-09 | Log | N/A | b10164cf42ab47b7ab274b9573b09f52 | Vite - WASM Import Path Traversal - CVE:CVE-2025-31125 | This is a new detection. |
Feb 02, 2026
1. ### [WAF Release - 2026-02-02](https://developers.cloudflare.com/changelog/2026-02-02-waf-release/)
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces new detections for CVE-2025-64459 and CVE-2025-24893.
**Key Findings**
* CVE-2025-64459: Django versions prior to 5.1.14, 5.2.8, and 4.2.26 are vulnerable to SQL injection via crafted dictionaries passed to QuerySet methods and the `Q()` class.
* CVE-2025-24893: XWiki allows unauthenticated remote code execution through crafted requests to the SolrSearch endpoint, affecting the entire installation.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 7a47683eacce4abd870ab2c630698ff3 | N/A | XWiki - Remote Code Execution - CVE:CVE-2025-24893 2 | Log | Block | This is a new detection. |
| Cloudflare Managed Ruleset | ad5c52f6ca334ef4a844e5e5da8ba7e6 | N/A | Django SQLI - CVE:CVE-2025-64459 | Log | Block | This is a new detection. |
| Cloudflare Managed Ruleset | 8f0d5c98bd24460a9305a1558d667511 | N/A | NoSQL, MongoDB - SQLi - Comparison - 2 | Block | Block | Rule metadata description refined. Detection unchanged. |
Jan 30, 2026
1. ### [Reduced minimum cache TTL for Workers KV to 30 seconds](https://developers.cloudflare.com/changelog/2026-01-30-kv-reduced-minimum-cachettl/)
[KV](https://developers.cloudflare.com/kv/)
The minimum `cacheTtl` parameter for Workers KV has been reduced from 60 seconds to 30 seconds. This change applies to both `get()` and `getWithMetadata()` methods.
This reduction allows you to maintain more up-to-date cached data and have finer-grained control over cache behavior. Applications requiring faster data refresh rates can now configure cache durations as low as 30 seconds instead of the previous 60-second minimum.
The `cacheTtl` parameter defines how long a KV result is cached at the global network location it is accessed from:
```js
// Read with custom cache TTL
const value = await env.NAMESPACE.get("my-key", {
cacheTtl: 30, // Cache for minimum 30 seconds (previously 60)
});
// getWithMetadata also supports the reduced cache TTL
const valueWithMetadata = await env.NAMESPACE.getWithMetadata("my-key", {
cacheTtl: 30, // Cache for minimum 30 seconds
});
```
The default cache TTL remains unchanged at 60 seconds. Upgrade to the latest version of Wrangler to be able to use 30 seconds `cacheTtl`.
This change affects all KV read operations using the binding API. For more information, consult the [Workers KV cache TTL documentation](https://developers.cloudflare.com/kv/api/read-key-value-pairs/#cachettl-parameter).
Jan 30, 2026
1. ### [BGP over GRE and IPsec tunnels](https://developers.cloudflare.com/changelog/2026-01-30-bgp-over-tunnels/)
[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using IPsec and GRE tunnel on-ramps (beta).
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via IPsec and GRE tunnel on-ramps.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
For configuration details, refer to:
* [Configure BGP routes for Magic WAN](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes)
* [Configure BGP routes for Magic Transit](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes)
Jan 28, 2026
1. ### [Launching FLUX.2 \[klein\] 9B on Workers AI](https://developers.cloudflare.com/changelog/2026-01-28-flux-2-klein-9b-workers-ai/)
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We have partnered with Black Forest Labs (BFL) again to bring their optimized FLUX.2 \[klein] 9B model to Workers AI. This distilled model offers enhanced quality compared to the 4B variant, while maintaining cost-effective pricing. With a fixed 4-step inference process, Klein 9B is ideal for rapid prototyping and real-time applications where both speed and quality matter.
Read the [BFL blog](https://bfl.ai/blog) to learn more about the model itself, or try it out yourself on our [multi modal playground](https://multi-modal.ai.cloudflare.com/).
Pricing documentation is available on the [model page](https://developers.cloudflare.com/workers-ai/models/flux-2-klein-9b/) or [pricing page](https://developers.cloudflare.com/workers-ai/platform/pricing/).
#### Workers AI platform specifics
The model hosted on Workers AI is optimized for speed with a **fixed 4-step inference process** and supports up to 4 image inputs. Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted. Like FLUX.2 \[dev] and FLUX.2 \[klein] 4B, this image model uses multipart form data inputs, even if you just have a prompt.
With the REST API, the multipart form data input looks like this:
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-9b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=a sunset at the alps' \
--form width=1024 \
--form height=1024
```
With the Workers AI binding, you can use it as such:
```javascript
const form = new FormData();
form.append("prompt", "a sunset with a dog");
form.append("width", "1024");
form.append("height", "1024");
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-9b", {
multipart: {
body: form,
contentType: "multipart/form-data",
},
});
```
The parameters you can send to the model are detailed here:
JSON Schema for Model
**Required Parameters**
* `prompt` (string) - Text description of the image to generate
**Optional Parameters**
* `input_image_0` (string) - Binary image
* `input_image_1` (string) - Binary image
* `input_image_2` (string) - Binary image
* `input_image_3` (string) - Binary image
* `guidance` (float) - Guidance scale for generation. Higher values follow the prompt more closely
* `width` (integer) - Width of the image, default `1024` Range: 256-1920
* `height` (integer) - Height of the image, default `768` Range: 256-1920
* `seed` (integer) - Seed for reproducibility
**Note:** Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted.
#### Multi-reference images
The FLUX.2 klein-9b model supports generating images based on reference images, just like FLUX.2 \[dev] and FLUX.2 \[klein] 4B. You can use this feature to apply the style of one image to another, add a new character to an image, or iterate on past generated images. You would use it with the same multipart form data structure, with the input images in binary. The model supports up to 4 input images.
For the prompt, you can reference the images based on the index, like `take the subject of image 1 and style it like image 0` or even use natural language like `place the dog beside the woman`.
You must name the input parameter as `input_image_0`, `input_image_1`, `input_image_2`, `input_image_3` for it to work correctly. All input images must be smaller than 512x512.
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-9b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=take the subject of image 1 and style it like image 0' \
--form input_image_0=@/Users/johndoe/Desktop/icedoutkeanu.png \
--form input_image_1=@/Users/johndoe/Desktop/me.png \
--form width=1024 \
--form height=1024
```
Through Workers AI Binding:
```javascript
//helper function to convert ReadableStream to Blob
async function streamToBlob(stream: ReadableStream, contentType: string): Promise {
const reader = stream.getReader();
const chunks = [];
while (true) {
const { done, value } = await reader.read();
if (done) break;
chunks.push(value);
}
return new Blob(chunks, { type: contentType });
}
const image0 = await fetch("http://image-url");
const image1 = await fetch("http://image-url");
const form = new FormData();
const image_blob0 = await streamToBlob(image0.body, "image/png");
const image_blob1 = await streamToBlob(image1.body, "image/png");
form.append('input_image_0', image_blob0)
form.append('input_image_1', image_blob1)
form.append('prompt', 'take the subject of image 1 and style it like image 0')
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-9b", {
multipart: {
body: form,
contentType: "multipart/form-data"
}
})
```
Jan 27, 2026
1. ### [WARP client for Windows (version 2026.1.89.1)](https://developers.cloudflare.com/changelog/2026-01-27-warp-windows-beta/)
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes, improvements, and new features.
**Changes and improvements**
* Improvements to [multi-user mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/). Fixed an issue where when switching from a pre-login registration to a user registration, Mobile Device Management (MDM) configuration association could be lost.
* Added a new feature to [manage NetBIOS over TCP/IP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#netbios-over-tcpip) functionality on the Windows client. NetBIOS over TCP/IP on the Windows client is now disabled by default and can be enabled in [device profile settings](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/device-profiles/).
* Fixed an issue causing failure of the [local network exclusion](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#allow-users-to-enable-local-network-exclusion) feature when configured with a timeout of `0`.
* Improvement for the Windows [client certificate posture check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/) to ensure logged results are from checks that run once users log in.
* Improvement for more accurate reporting of device colocation information in the Cloudflare One dashboard.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
Jan 27, 2026
1. ### [WARP client for macOS (version 2026.1.89.1)](https://developers.cloudflare.com/changelog/2026-01-27-warp-macos-beta/)
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue causing failure of the [local network exclusion](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#allow-users-to-enable-local-network-exclusion) feature when configured with a timeout of `0`.
* Improvement for more accurate reporting of device colocation information in the Cloudflare One dashboard.
Jan 27, 2026
1. ### [Added Timezone preferences settings](https://developers.cloudflare.com/changelog/2026-01-27-timezone-preferences/)
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
You can now set the timezone in the Cloudflare dashboard as Coordinated Universal Time (UTC) or your browser or system's timezone.
#### What's New
Unless otherwise specified in the user interface, all dates and times in the Cloudflare dashboard are now displayed in the selected timezone.
You can change the timezone setting from the user profile dropdown.

The page will reload to apply the new timezone setting.
Jan 27, 2026
1. ### [Configure Cloudflare source IPs (beta)](https://developers.cloudflare.com/changelog/2026-01-27-configure-cloudflare-source-ips/)
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Cloudflare source IPs are the IP addresses used by Cloudflare services (such as Load Balancing, Gateway, and Browser Isolation) when sending traffic to your private networks.
For customers using legacy mode routing, traffic to private networks is sourced from public Cloudflare IPs, which may cause IP conflicts. For customers using Unified Routing mode (beta), traffic to private networks is sourced from dedicated, non-Internet-routable private IPv4 range to ensure:
* Symmetric routing over private network connections
* Proper firewall state preservation
* Private traffic stays on secure paths
Key details:
* **IPv4**: Sourced from `100.64.0.0/12` by default, configurable to any `/12` CIDR
* **IPv6**: Sourced from `2606:4700:cf1:5000::/64` (not configurable)
* **Affected connectors**: GRE, IPsec, CNI, WARP Connector, and WARP Client (Cloudflare Tunnel is not affected)
Configuring Cloudflare source IPs requires Unified Routing (beta) and the `Cloudflare One Networks Write` permission.
For configuration details, refer to [Configure Cloudflare source IPs](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-cloudflare-source-ips/).
Jan 27, 2026
1. ### [Control request and response body buffering in Configuration Rules](https://developers.cloudflare.com/changelog/2026-01-27-body-buffering-settings/)
[Rules](https://developers.cloudflare.com/rules/)
You can now control how Cloudflare buffers HTTP request and response bodies using two new settings in [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/).
#### Request body buffering
Controls how Cloudflare buffers HTTP request bodies before forwarding them to your origin server:
| Mode | Behavior |
| - | - |
| **Standard** (default) | Cloudflare can inspect a prefix of the request body for enabled functionality such as WAF and Bot Management. |
| **Full** | Buffers the entire request body before sending to origin. |
| **None** | No buffering — the request body streams directly to origin without inspection. |
#### Response body buffering
Controls how Cloudflare buffers HTTP response bodies before forwarding them to the client:
| Mode | Behavior |
| - | - |
| **Standard** (default) | Cloudflare can inspect a prefix of the response body for enabled functionality. |
| **None** | No buffering — the response body streams directly to the client without inspection. |
Warning
Setting body buffering to **None** may break security functionality that requires body inspection, including the Web Application Firewall (WAF) and Bot Management. Ensure that any paths where you disable buffering do not require security inspection.
Availability
These settings only take effect on zones running Cloudflare's [latest CDN proxy](https://blog.cloudflare.com/20-percent-internet-upgrade/). Enterprise customers can contact their account team to enable the latest proxy on their zones.
#### API example
```json
{
"action": "set_config",
"action_parameters": {
"request_body_buffering": "standard",
"response_body_buffering": "none"
}
}
```
For more information, refer to [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/).
Jan 26, 2026
1. ### [WAF Release - 2026-01-26](https://developers.cloudflare.com/changelog/2026-01-26-waf-release/)
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces new detections for denial-of-service attempts targeting React CVE-2026-23864 ().
**Key Findings**
* CVE-2026-23864 () affects `react-server-dom-parcel`, `react-server-dom-turbopack`, and `react-server-dom-webpack` packages.
* Attackers can send crafted HTTP requests to Server Function endpoints, causing server crashes, out-of-memory exceptions, or excessive CPU usage.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | aaede80b4d414dc89c443cea61680354 | N/A | React Server - DOS - CVE:CVE-2026-23864 - 1 | N/A | Block | This is a new detection. |
| Cloudflare Managed Ruleset | 3e93c9faaafa447c83a525f2dcdffcf8 | N/A | React Server - DOS - CVE:CVE-2026-23864 - 2 | N/A | Block | This is a new detection. |
| Cloudflare Managed Ruleset | 930020d567684f19b05fb35b349edbc6 | N/A | React Server - DOS - CVE:CVE-2026-23864 - 3 | N/A | Block | This is a new detection. |
Jan 23, 2026
1. ### [New 2FA Experience for Login](https://developers.cloudflare.com/changelog/2026-01-23-new-2fa-experience/)
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
In an effort to improve overall user security, users without 2FA will be prompted upon login to enroll in email 2FA. This will improve user security posture while minimizing friction. Users without email 2FA enabled will see a prompt to secure their account with additional factors upon logging in. Enrolling in 2FA remains optional, but strongly encouraged as it is the best way to prevent account takeovers.
We also made changes to existing 2FA screens to improve the user experience. Now we have distinct experiences for each 2FA factor type, reflective of the way that factor works.
#### For more information
* [Configure Email Two Factor Authentication](https://developers.cloudflare.com/fundamentals/user-profiles/2fa/#configure-email-two-factor-authentication)
Jan 23, 2026
1. ### [Increased Pages file limit to 100,000 for paid plans](https://developers.cloudflare.com/changelog/2026-01-23-pages-file-limit-increase/)
[Pages](https://developers.cloudflare.com/pages/)
Paid plans can now have up to 100,000 files per Pages site, increased from the previous limit of 20,000 files.
To enable this increased limit, set the environment variable `PAGES_WRANGLER_MAJOR_VERSION=4` in your Pages project settings.
The Free plan remains at 20,000 files per site.
For more details, refer to the [Pages limits documentation](https://developers.cloudflare.com/pages/platform/limits/#files).
Jan 23, 2026
1. ### [Vectorize indexes now support up to 10 million vectors](https://developers.cloudflare.com/changelog/2026-01-23-increased-index-capacity/)
[Vectorize](https://developers.cloudflare.com/vectorize/)
You can now store up to 10 million vectors in a single Vectorize index, doubling the previous limit of 5 million vectors. This enables larger-scale semantic search, recommendation systems, and retrieval-augmented generation (RAG) applications without splitting data across multiple indexes.
Vectorize continues to support indexes with up to 1,536 dimensions per vector at 32-bit precision. Refer to the [Vectorize limits documentation](https://developers.cloudflare.com/vectorize/platform/limits/) for complete details.
Jan 22, 2026
1. ### [New cryptographic functions — encode\_base64() and sha256()](https://developers.cloudflare.com/changelog/2026-01-22-sha256-base64-encode-functions/)
[Rules](https://developers.cloudflare.com/rules/)
Cloudflare Rulesets now includes `encode_base64()` and `sha256()` functions, enabling you to generate signed request headers directly in rule expressions. These functions support common patterns like constructing a canonical string from request attributes, computing a SHA256 digest, and Base64-encoding the result.
***
#### New functions
| Function | Description | Availability |
| - | - | - |
| `encode_base64(input, flags)` | Encodes a string to Base64 format. Optional `flags` parameter: `u` for URL-safe encoding, `p` for padding (adds `=` characters to make the output length a multiple of 4, as required by some systems). By default, output is standard Base64 without padding. | All plans (in header transform rules) |
| `sha256(input)` | Computes a SHA256 hash of the input string. | Requires enablement |
Note
The `sha256()` function is available as an Enterprise add-on and requires a specific entitlement. Contact your account team to enable it.
***
#### Examples
**Encode a string to Base64 format:**
```txt
encode_base64("hello world")
```
Returns: `aGVsbG8gd29ybGQ`
**Encode a string to Base64 format with padding:**
```txt
encode_base64("hello world", "p")
```
Returns: `aGVsbG8gd29ybGQ=`
**Perform a URL-safe Base64 encoding of a string:**
```txt
encode_base64("hello world", "u")
```
Returns: `aGVsbG8gd29ybGQ`
**Compute the SHA256 hash of a secret token:**
```txt
sha256("my-token")
```
Returns a hash that your origin can validate to authenticate requests.
**Compute the SHA256 hash of a string and encode the result to Base64 format:**
```txt
encode_base64(sha256("my-token"))
```
Combines hashing and encoding for systems that expect Base64-encoded signatures.
For more information, refer to the [Functions reference](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/).
Jan 22, 2026
1. ### [New Placement Hints for Workers](https://developers.cloudflare.com/changelog/2026-01-22-explicit-placement-hints/)
[Workers](https://developers.cloudflare.com/workers/)
You can now configure Workers to run close to infrastructure in legacy cloud regions to minimize latency to existing services and databases. This is most useful when your Worker makes multiple round trips.
To [set a placement hint](https://developers.cloudflare.com/workers/configuration/placement/#use-placement-hints), set the `placement.region` property in your Wrangler configuration file:
* wrangler.jsonc
```jsonc
{
"placement": {
"region": "aws:us-east-1",
},
}
```
* wrangler.toml
```toml
[placement]
region = "aws:us-east-1"
```
Placement hints support Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure region identifiers. Workers run in the [Cloudflare data center](https://www.cloudflare.com/network/) with the lowest latency to the specified cloud region.
If your existing infrastructure is not in these cloud providers, expose it to placement probes with `placement.host` for layer 4 checks or `placement.hostname` for layer 7 checks. These probes are designed to locate single-homed infrastructure and are not suitable for anycasted or multicasted resources.
* wrangler.jsonc
```jsonc
{
"placement": {
"host": "my_database_host.com:5432",
},
}
```
* wrangler.toml
```toml
[placement]
host = "my_database_host.com:5432"
```
- wrangler.jsonc
```jsonc
{
"placement": {
"hostname": "my_api_server.com",
},
}
```
- wrangler.toml
```toml
[placement]
hostname = "my_api_server.com"
```
This is an extension of [Smart Placement](https://developers.cloudflare.com/workers/configuration/placement/#use-smart-placement), which automatically places your Workers closer to back-end APIs based on measured latency. When you do not know the location of your back-end APIs or have multiple back-end APIs, set `mode: "smart"`:
* wrangler.jsonc
```jsonc
{
"placement": {
"mode": "smart",
},
}
```
* wrangler.toml
```toml
[placement]
mode = "smart"
```
Jan 20, 2026
1. ### [Create AI Search instances programmatically via REST API](https://developers.cloudflare.com/changelog/2026-01-20-ai-search-simplified-api/)
[AI Search](https://developers.cloudflare.com/ai-search/)
You can now create [AI Search](https://developers.cloudflare.com/ai-search/) instances programmatically using the [API](https://developers.cloudflare.com/ai-search/get-started/api/). For example, use the API to create instances for each customer in a multi-tenant application or manage AI Search alongside your other infrastructure.
If you have created an AI Search instance via the [dashboard](https://developers.cloudflare.com/ai-search/get-started/dashboard/) before, you already have a [service API token](https://developers.cloudflare.com/ai-search/configuration/service-api-token/) registered and can start creating instances programmatically right away. If not, follow the [API guide](https://developers.cloudflare.com/ai-search/get-started/api/) to set up your first instance.
For example, you can now create separate search instances for each language on your website:
```bash
for lang in en fr es de; do
curl -X POST "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/ai-search/instances" \
-H "Authorization: Bearer $API_TOKEN" \
-H "Content-Type: application/json" \
--data '{
"id": "docs-'"$lang"'",
"type": "web-crawler",
"source": "example.com",
"source_params": {
"path_include": ["**/'"$lang"'/**"]
}
}'
done
```
Refer to the [REST API reference](https://developers.cloudflare.com/api/resources/ai_search/subresources/instances/methods/create/) for additional configuration options.
Jan 20, 2026
1. ### [AI Search path filtering for website and R2 data sources](https://developers.cloudflare.com/changelog/2026-01-20-ai-search-path-filtering/)
[AI Search](https://developers.cloudflare.com/ai-search/)
[AI Search](https://developers.cloudflare.com/ai-search/) now includes [path filtering](https://developers.cloudflare.com/ai-search/configuration/path-filtering/) for both [website](https://developers.cloudflare.com/ai-search/configuration/data-source/website/#path-filtering) and [R2](https://developers.cloudflare.com/ai-search/configuration/data-source/r2/#path-filtering) data sources. You can now control which content gets indexed by defining include and exclude rules for paths.
By controlling what gets indexed, you can improve the relevance and quality of your search results. You can also use path filtering to split a single data source across multiple AI Search instances for specialized search experiences.
Path filtering uses [micromatch](https://github.com/micromatch/micromatch) patterns, so you can use `*` to match within a directory and `**` to match across directories.
| Use case | Include | Exclude |
| - | - | - |
| Index docs but skip drafts | `**/docs/**` | `**/docs/drafts/**` |
| Keep admin pages out of results | — | `**/admin/**` |
| Index only English content | `**/en/**` | — |
Configure path filters when creating a new instance or update them anytime from **Settings**. Check out [path filtering](https://developers.cloudflare.com/ai-search/configuration/path-filtering/) to learn more.
Jan 20, 2026
1. ### [New Workers KV Dashboard UI](https://developers.cloudflare.com/changelog/2026-01-20-kv-dash-ui-homepage/)
[KV](https://developers.cloudflare.com/kv/)
[Workers KV](https://developers.cloudflare.com/kv/) has an updated dashboard UI with new dashboard styling that makes it easier to navigate and see analytics and settings for a KV namespace.
The new dashboard features a **streamlined homepage** for easy access to your namespaces and key operations, with consistent design with the rest of the dashboard UI updates. It also provides an **improved analytics view**.

The updated dashboard is now available for all Workers KV users. Log in to the [Cloudflare Dashboard](https://dash.cloudflare.com/) to start exploring the new interface.
Jan 20, 2026
1. ### [Cloudflare Typescript SDK v6.0.0-beta.1 now available](https://developers.cloudflare.com/changelog/2026-01-20-cloudflare-typescript-v600-beta1/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[SDK](https://developers.cloudflare.com/sdk/)
> **Disclaimer:** Please note that v6.0.0-beta.1 is in Beta and we are still testing it for stability.
Full Changelog: [v5.2.0...v6.0.0-beta.1](https://github.com/cloudflare/cloudflare-typescript/compare/v5.2.0...v6.0.0-beta.1)
In this release, you'll see a large number of breaking changes. This is primarily due to a change in OpenAPI definitions, which our libraries are based off of, and codegen updates that we rely on to read those OpenAPI definitions and produce our SDK libraries. As the codegen is always evolving and improving, so are our code bases.
Some breaking changes were introduced due to bug fixes, also listed below.
Please ensure you read through the list of changes below before moving to this version - this will help you understand any down or upstream issues it may cause to your environments.
***
#### Breaking Changes
#### Addressing - Parameter Requirements Changed
* `BGPPrefixCreateParams.cidr`: optional → **required**
* `PrefixCreateParams.asn`: `number | null` → `number`
* `PrefixCreateParams.loa_document_id`: required → **optional**
* `ServiceBindingCreateParams.cidr`: optional → **required**
* `ServiceBindingCreateParams.service_id`: optional → **required**
#### API Gateway
* `ConfigurationUpdateResponse` removed
* `PublicSchema` → `OldPublicSchema`
* `SchemaUpload` → `UserSchemaCreateResponse`
* `ConfigurationUpdateParams.properties` removed; use `normalize`
#### CloudforceOne - Response Type Changes
* `ThreatEventBulkCreateResponse`: `number` → complex object with counts and errors
#### D1 Database - Query Parameters
* `DatabaseQueryParams`: simple interface → union type (`D1SingleQuery | MultipleQueries`)
* `DatabaseRawParams`: same change
* Supports batch queries via `batch` array
#### DNS Records - Type Renames (21 types)
All record type interfaces renamed from `*Record` to short names:
* `RecordResponse.ARecord` → `RecordResponse.A`
* `RecordResponse.AAAARecord` → `RecordResponse.AAAA`
* `RecordResponse.CNAMERecord` → `RecordResponse.CNAME`
* `RecordResponse.MXRecord` → `RecordResponse.MX`
* `RecordResponse.NSRecord` → `RecordResponse.NS`
* `RecordResponse.PTRRecord` → `RecordResponse.PTR`
* `RecordResponse.TXTRecord` → `RecordResponse.TXT`
* `RecordResponse.CAARecord` → `RecordResponse.CAA`
* `RecordResponse.CERTRecord` → `RecordResponse.CERT`
* `RecordResponse.DNSKEYRecord` → `RecordResponse.DNSKEY`
* `RecordResponse.DSRecord` → `RecordResponse.DS`
* `RecordResponse.HTTPSRecord` → `RecordResponse.HTTPS`
* `RecordResponse.LOCRecord` → `RecordResponse.LOC`
* `RecordResponse.NAPTRRecord` → `RecordResponse.NAPTR`
* `RecordResponse.SMIMEARecord` → `RecordResponse.SMIMEA`
* `RecordResponse.SRVRecord` → `RecordResponse.SRV`
* `RecordResponse.SSHFPRecord` → `RecordResponse.SSHFP`
* `RecordResponse.SVCBRecord` → `RecordResponse.SVCB`
* `RecordResponse.TLSARecord` → `RecordResponse.TLSA`
* `RecordResponse.URIRecord` → `RecordResponse.URI`
* `RecordResponse.OpenpgpkeyRecord` → `RecordResponse.Openpgpkey`
#### IAM Resource Groups
* `ResourceGroupCreateResponse.scope`: optional single → **required array**
* `ResourceGroupCreateResponse.id`: optional → **required**
#### Origin CA Certificates - Parameter Requirements Changed
* `OriginCACertificateCreateParams.csr`: optional → **required**
* `OriginCACertificateCreateParams.hostnames`: optional → **required**
* `OriginCACertificateCreateParams.request_type`: optional → **required**
#### Pages
* Renamed: `DeploymentsSinglePage` → `DeploymentListResponsesV4PagePaginationArray`
* Domain response fields: many optional → **required**
#### Pipelines - v0 to v1 Migration
* Entire v0 API deprecated; use v1 methods (`createV1`, `listV1`, etc.)
* New sub-resources: `Sinks`, `Streams`
#### R2
* `EventNotificationUpdateParams.rules`: optional → **required**
* Super Slurper: `bucket`, `secret` now required in source params
#### Radar
* `dataSource`: `string` → typed enum (23 values)
* `eventType`: `string` → typed enum (6 values)
* V2 methods require `dimension` parameter (breaking signature change)
#### Resource Sharing
* Removed: `status_message` field from all recipient response types
#### Schema Validation
* Consolidated `SchemaCreateResponse`, `SchemaListResponse`, `SchemaEditResponse`, `SchemaGetResponse` → `PublicSchema`
* Renamed: `SchemaListResponsesV4PagePaginationArray` → `PublicSchemasV4PagePaginationArray`
#### Spectrum
* Renamed union members: `AppListResponse.UnionMember0` → `SpectrumConfigAppConfig`
* Renamed union members: `AppListResponse.UnionMember1` → `SpectrumConfigPaygoAppConfig`
#### Workers
* Removed: `WorkersBindingKindTailConsumer` type (all occurrences)
* Renamed: `ScriptsSinglePage` → `ScriptListResponsesSinglePage`
* Removed: `DeploymentsSinglePage`
#### Zero-Trust DLP
* `datasets.create()`, `update()`, `get()` return types changed
* `PredefinedGetResponse` union members renamed to `UnionMember0-5`
#### Zero-Trust Tunnels
* Removed: `CloudflaredCreateResponse`, `CloudflaredListResponse`, `CloudflaredDeleteResponse`, `CloudflaredEditResponse`, `CloudflaredGetResponse`
* Removed: `CloudflaredListResponsesV4PagePaginationArray`
***
#### Features
#### Abuse Reports (`client.abuseReports`)
* **Reports**: `create`, `list`, `get`
* **Mitigations**: sub-resource for abuse mitigations
#### AI Search (`client.aisearch`)
* **Instances**: `create`, `update`, `list`, `delete`, `read`, `stats`
* **Items**: `list`, `get`
* **Jobs**: `create`, `list`, `get`, `logs`
* **Tokens**: `create`, `update`, `list`, `delete`, `read`
#### Connectivity (`client.connectivity`)
* **Directory Services**: `create`, `update`, `list`, `delete`, `get`
* Supports IPv4, IPv6, dual-stack, and hostname configurations
#### Organizations (`client.organizations`)
* **Organizations**: `create`, `update`, `list`, `delete`, `get`
* **OrganizationProfile**: `update`, `get`
* Hierarchical organization support with parent/child relationships
#### R2 Data Catalog (`client.r2DataCatalog`)
* **Catalog**: `list`, `enable`, `disable`, `get`
* **Credentials**: `create`
* **MaintenanceConfigs**: `update`, `get`
* **Namespaces**: `list`
* **Tables**: `list`, maintenance config management
* Apache Iceberg integration
#### Realtime Kit (`client.realtimeKit`)
* **Apps**: `get`, `post`
* **Meetings**: `create`, `get`, participant management
* **Livestreams**: 10+ methods for streaming
* **Recordings**: start, pause, stop, get
* **Sessions**: transcripts, summaries, chat
* **Webhooks**: full CRUD
* **ActiveSession**: polls, kick participants
* **Analytics**: organization analytics
#### Token Validation (`client.tokenValidation`)
* **Configuration**: `create`, `list`, `delete`, `edit`, `get`
* **Credentials**: `update`
* **Rules**: `create`, `list`, `delete`, `bulkCreate`, `bulkEdit`, `edit`, `get`
* JWT validation with RS256/384/512, PS256/384/512, ES256, ES384
#### Alerting Silences (`client.alerting.silences`)
* `create`, `update`, `list`, `delete`, `get`
#### IAM SSO (`client.iam.sso`)
* `create`, `update`, `list`, `delete`, `get`, `beginVerification`
#### Pipelines v1 (`client.pipelines`)
* **Sinks**: `create`, `list`, `delete`, `get`
* **Streams**: `create`, `update`, `list`, `delete`, `get`
#### Zero-Trust AI Controls / MCP (`client.zeroTrust.access.aiControls.mcp`)
* **Portals**: `create`, `update`, `list`, `delete`, `read`
* **Servers**: `create`, `update`, `list`, `delete`, `read`, `sync`
#### Accounts
* `managed_by` field with `parent_org_id`, `parent_org_name`
#### Addressing LOA Documents
* `auto_generated` field on `LOADocumentCreateResponse`
#### Addressing Prefixes
* `delegate_loa_creation`, `irr_validation_state`, `ownership_validation_state`, `ownership_validation_token`, `rpki_validation_state`
#### AI
* Added `toMarkdown.supported()` method to get all supported conversion formats
#### AI Gateway
* `zdr` field added to all responses and params
#### Alerting
* New alert type: `abuse_report_alert`
* `type` field added to PolicyFilter
#### Browser Rendering
* `ContentCreateParams`: refined to discriminated union (`Variant0 | Variant1`)
* Split into URL-based and HTML-based parameter variants for better type safety
#### Client Certificates
* `reactivate` parameter in edit
#### CloudforceOne
* `ThreatEventCreateParams.indicatorType`: required → optional
* `hasChildren` field added to all threat event response types
* `datasetIds` query parameter on `AttackerListParams`, `CategoryListParams`, `TargetIndustryListParams`
* `categoryUuid` field on `TagCreateResponse`
* `indicators` array for multi-indicator support per event
* `uuid` and `preserveUuid` fields for UUID preservation in bulk create
* `format` query parameter (`'json' | 'stix2'`) on `ThreatEventListParams`
* `createdAt`, `datasetId` fields on `ThreatEventEditParams`
#### Content Scanning
* Added `create()`, `update()`, `get()` methods
#### Custom Pages
* New page types: `basic_challenge`, `under_attack`, `waf_challenge`
#### D1
* `served_by_colo` - colo that handled query
* `jurisdiction` - `'eu' | 'fedramp'`
* **Time Travel** (`client.d1.database.timeTravel`): `getBookmark()`, `restore()` - point-in-time recovery
#### Email Security
* New fields on `InvestigateListResponse`/`InvestigateGetResponse`: `envelope_from`, `envelope_to`, `postfix_id_outbound`, `replyto`
* New detection classification: `'outbound_ndr'`
* Enhanced `Finding` interface with `attachment`, `detection`, `field`, `portion`, `reason`, `score`
* Added `cursor` query parameter to `InvestigateListParams`
#### Gateway Lists
* New list types: `CATEGORY`, `LOCATION`, `DEVICE`
#### Intel
* New issue type: `'configuration_suggestion'`
* `payload` field: `unknown` → typed `Payload` interface with `detection_method`, `zone_tag`
#### Leaked Credential Checks
* Added `detections.get()` method
#### Logpush
* New datasets: `dex_application_tests`, `dex_device_state_events`, `ipsec_logs`, `warp_config_changes`, `warp_toggle_changes`
#### Load Balancers
* `Monitor.port`: `number` → `number | null`
* `Pool.load_shedding`: `LoadShedding` → `LoadShedding | null`
* `Pool.origin_steering`: `OriginSteering` → `OriginSteering | null`
#### Magic Transit
* `license_key` field on connectors
* `provision_license` parameter for auto-provisioning
* IPSec: `custom_remote_identities` with FQDN support
* Snapshots: Bond interface, `probed_mtu` field
#### Pages
* New response types: `ProjectCreateResponse`, `ProjectListResponse`, `ProjectEditResponse`, `ProjectGetResponse`
* Deployment methods return specific response types instead of generic `Deployment`
#### Queues
* Added `subscriptions.get()` method
* Enhanced `SubscriptionGetResponse` with typed event source interfaces
* New event source types: Images, KV, R2, Vectorize, Workers AI, Workers Builds, Workflows
#### R2
* Sippy: new provider `s3` (S3-compatible endpoints)
* Sippy: `bucketUrl` field for S3-compatible sources
* Super Slurper: `keys` field on source response schemas (specify specific keys to migrate)
* Super Slurper: `pathPrefix` field on source schemas
* Super Slurper: `region` field on S3 source params
#### Radar
* Added `geolocations.list()`, `geolocations.get()` methods
* Added V2 dimension-based methods (`summaryV2`, `timeseriesGroupsV2`) to radar sub-resources
#### Resource Sharing
* Added `terminal` boolean field to Resource Error interfaces
#### Rules
* Added `id` field to `ItemDeleteParams.Item`
#### Rulesets
* New buffering fields on `SetConfigRule`: `request_body_buffering`, `response_body_buffering`
#### Secrets Store
* New scopes: `'dex'`, `'access'` (in addition to `'workers'`, `'ai_gateway'`)
#### SSL Certificate Packs
* Response types now proper interfaces (was `unknown`)
* Fields now required: `id`, `certificates`, `hosts`, `status`, `type`
#### Security Center
* `payload` field: `unknown` → typed `Payload` interface with `detection_method`, `zone_tag`
#### Shared Types
* Added: `CloudflareTunnelsV4PagePaginationArray` pagination class
#### Workers
* Added `subdomains.delete()` method
* `Worker.references` - track external dependencies (domains, Durable Objects, queues)
* `Worker.startup_time_ms` - startup timing
* `Script.observability` - observability settings with logging
* `Script.tag`, `Script.tags` - immutable ID and tags
* Placement: support for region, hostname, host-based placement
* `tags`, `tail_consumers` now accept `| null`
* Telemetry: `traces` field, `$containers` event info, `durableObjectId`, `transactionName`, `abr_level` fields
#### Workers for Platforms
* `ScriptUpdateResponse`: new fields `entry_point`, `observability`, `tag`, `tags`
* `placement` field now union of 4 variants (smart mode, region, hostname, host)
* `tags`, `tail_consumers` now nullable
* `TagUpdateParams.body` now accepts `null`
#### Workflows
* `instance_retention`: `unknown` → typed `InstanceRetention` interface with `error_retention`, `success_retention`
* New status option: `'restart'` added to `StatusEditParams.status`
#### Zero-Trust Devices
* External emergency disconnect settings (4 new fields)
* `antivirus` device posture check type
* `os_version_extra` documentation improvements
#### Zones
* New response types: `SubscriptionCreateResponse`, `SubscriptionUpdateResponse`, `SubscriptionGetResponse`
#### Zero-Trust Access Applications
* New `ApplicationType` values: `'mcp'`, `'mcp_portal'`, `'proxy_endpoint'`
* New destination type: `ViaMcpServerPortalDestination` for MCP server access
#### Zero-Trust Gateway
* Added `rules.listTenant()` method
#### Zero-Trust Gateway - Proxy Endpoints
* `ProxyEndpoint`: interface → discriminated union (`ZeroTrustGatewayProxyEndpointIP | ZeroTrustGatewayProxyEndpointIdentity`)
* `ProxyEndpointCreateParams`: interface → union type
* Added `kind` field: `'ip' | 'identity'`
#### Zero-Trust Tunnels
* `WARPConnector*Response`: union type → interface
***
#### Deprecations
* **API Gateway**: `UserSchemas`, `Settings`, `SchemaValidation` resources
* **Audit Logs**: `auditLogId.not` (use `id.not`)
* **CloudforceOne**: `ThreatEvents.get()`, `IndicatorTypes.list()`
* **Devices**: `public_ip` field (use DEX API)
* **Email Security**: `item_count` field in Move responses
* **Pipelines**: v0 methods (use v1)
* **Radar**: old `summary()` and `timeseriesGroups()` methods (use V2)
* **Rulesets**: `disable_apps`, `mirage` fields
* **WARP Connector**: `connections` field
* **Workers**: `environment` parameter in Domains
* **Zones**: `ResponseBuffering` page rule
***
#### Bug Fixes
* **mcp:** correct code tool API endpoint ([599703c](https://github.com/cloudflare/cloudflare-typescript/commit/599703c45672dc899455d74b124018efd4b75095))
* **mcp:** return correct lines on typescript errors ([5d6f999](https://github.com/cloudflare/cloudflare-typescript/commit/5d6f9998ed9999aaa95e1bda8cf50929f3555cf1))
* **organization\_profile:** fix bad reference ([d84ea77](https://github.com/cloudflare/cloudflare-typescript/commit/d84ea77094400055c06554812b84c2f0c8d00cc4))
* **schema\_validation:** correctly reflect model to openapi mapping ([bb86151](https://github.com/cloudflare/cloudflare-typescript/commit/bb861516774b159d80e0f46a5f3abc5a4c9f9d49))
* **workers:** fix tests ([2ee37f7](https://github.com/cloudflare/cloudflare-typescript/commit/2ee37f7adf5a4637d65f61fc225e135eec2579fc))
***
#### Documentation
* Added deprecation notices with migration paths
* **api\_gateway:** deprecate API Shield Schema Validation resources ([8a4b20f](https://github.com/cloudflare/cloudflare-typescript/commit/8a4b20f7a572422f74179fbdb4f1c4fb555e3e40))
* Improved JSDoc examples across all resources
* **workers:** expose subdomain delete documentation ([4f7cc1f](https://github.com/cloudflare/cloudflare-typescript/commit/4f7cc1f2b8861a5b8abc193d287f78264a425062))
Jan 20, 2026
1. ### [New functions for array and map operations](https://developers.cloudflare.com/changelog/2026-01-20-array-map-functions/)
[Rules](https://developers.cloudflare.com/rules/)
#### New functions for array and map operations
Cloudflare Rulesets now include new functions that enable advanced expression logic for evaluating arrays and maps. These functions allow you to build rules that match against lists of values in request or response headers, enabling use cases like country-based blocking using custom headers.
***
#### New functions
| Function | Description |
| - | - |
| `split(source, delimiter)` | Splits a string into an array of strings using the specified delimiter. |
| `join(array, delimiter)` | Joins an array of strings into a single string using the specified delimiter. |
| `has_key(map, key)` | Returns `true` if the specified key exists in the map. |
| `has_value(map, value)` | Returns `true` if the specified value exists in the map. |
***
#### Example use cases
**Check if a country code exists in a header list:**
```txt
has_value(split(http.response.headers["x-allow-country"][0], ","), ip.src.country)
```
**Check if a specific header key exists:**
```txt
has_key(http.request.headers, "x-custom-header")
```
**Join array values for logging or comparison:**
```txt
join(http.request.headers.names, ", ")
```
For more information, refer to the [Functions reference](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/).
Jan 20, 2026
1. ### [Terraform v5.16.0 now available](https://developers.cloudflare.com/changelog/2026-01-20-terraform-v5160-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
In January 2025, we announced the launch of the new Terraform v5 Provider. We greatly appreciate the proactive engagement and valuable feedback from the Cloudflare community following the v5 release. In response, we've established a consistent and rapid [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) for releasing targeted improvements, demonstrating our commitment to stability and reliability.
With the help of the community, we have a growing number of resources that we have marked as [stable](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237), with that list continuing to grow with every release. The most used [resources](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) are on track to be stable by the end of March 2026, when we will also be releasing a new migration tool to you migrate from v4 to v5 with ease.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes bug fixes, the stabilization of even more popular resources, and more.
#### Features
* **custom\_pages:** add "waf\_challenge" as new supported error page type identifier in both resource and data source schemas
* **list:** enhance CIDR validator to check for normalized CIDR notation requiring network address for IPv4 and IPv6
* **magic\_wan\_gre\_tunnel:** add automatic\_return\_routing attribute for automatic routing control
* **magic\_wan\_gre\_tunnel:** add BGP configuration support with new BGP model attribute
* **magic\_wan\_gre\_tunnel:** add bgp\_status computed attribute for BGP connection status information
* **magic\_wan\_gre\_tunnel:** enhance schema with BGP-related attributes and validators
* **magic\_wan\_ipsec\_tunnel:** add automatic\_return\_routing attribute for automatic routing control
* **magic\_wan\_ipsec\_tunnel:** add BGP configuration support with new BGP model attribute
* **magic\_wan\_ipsec\_tunnel:** add bgp\_status computed attribute for BGP connection status information
* **magic\_wan\_ipsec\_tunnel:** add custom\_remote\_identities attribute for custom identity configuration
* **magic\_wan\_ipsec\_tunnel:** enhance schema with BGP and identity-related attributes
* **ruleset:** add request body buffering support
* **ruleset:** enhance ruleset data source with additional configuration options
* **workers\_script:** add observability logs attributes to list data source model
* **workers\_script:** enhance list data source schema with additional configuration options
#### Bug Fixes
* **account\_member**: fix resource importability issues
* **dns\_record:** remove unnecessary fmt.Sprintf wrapper around LoadTestCase call in test configuration helper function
* **load\_balancer:** fix session\_affinity\_ttl type expectations to match Float64 in initial creation and Int64 after migration
* **workers\_kv:** handle special characters correctly in URL encoding
#### Documentation
* **account\_subscription:** update schema description for rate\_plan.sets attribute to clarify it returns an array of strings
* **api\_shield:** add resource-level description for API Shield management of auth ID characteristics
* **api\_shield:** enhance auth\_id\_characteristics.name attribute description to include JWT token configuration format requirements
* **api\_shield:** specify JSONPath expression format for JWT claim locations
* **hyperdrive\_config:** add description attribute to name attribute explaining its purpose in dashboard and API identification
* **hyperdrive\_config:** apply description improvements across resource, data source, and list data source schemas
* **hyperdrive\_config:** improve schema descriptions for cache settings to clarify default values
* **hyperdrive\_config:** update port description to clarify defaults for different database types
#### For more information
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
* [List of stabilized resources](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237)
Jan 20, 2026
1. ### [WAF Release - 2026-01-20](https://developers.cloudflare.com/changelog/2026-01-20-waf-release/)
[WAF](https://developers.cloudflare.com/waf/)
This week's release focuses on improvements to existing detections to enhance coverage.
**Key Findings**
* Existing rule enhancements have been deployed to improve detection resilience against SQL injection.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | a291bd530fa346d18cc1ce5a68d90c8f | N/A | SQLi - Comment - Beta | Log | Block | This rule is merged into the original rule "SQLi - Comment" (ID: 42c424998d2a42c9808ab49c6d8d8fe4 ) |
| Cloudflare Managed Ruleset | da289f9e692e4f5397d915fbfaa045cf | N/A | SQLi - Comparison - Beta | Log | Block | This rule is merged into the original rule "SQLi - Comparison" (ID: 8166da327a614849bfa29317e7907480 ) |
Jan 20, 2026
1. ### [Use auxiliary Workers alongside full-stack frameworks](https://developers.cloudflare.com/changelog/2026-01-20-auxiliary-workers/)
[Workers](https://developers.cloudflare.com/workers/)
Auxiliary Workers are now fully supported when using full-stack frameworks, such as [React Router](https://developers.cloudflare.com/workers/framework-guides/web-apps/react-router/) and [TanStack Start](https://developers.cloudflare.com/workers/framework-guides/web-apps/tanstack-start/), that integrate with the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/reference/api/). They are included alongside the framework's build output in the build output directory. Note that this feature requires Vite 7 or above.
Auxiliary Workers are additional Workers that can be called via [service bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/service-bindings/) from your main (entry) Worker. They are defined in the plugin config, as in the example below:
```ts
import { defineConfig } from "vite";
import { tanstackStart } from "@tanstack/react-start/plugin/vite";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [
tanstackStart(),
cloudflare({
viteEnvironment: { name: "ssr" },
auxiliaryWorkers: [{ configPath: "./wrangler.aux.jsonc" }],
}),
],
});
```
See the Vite plugin [API docs](https://developers.cloudflare.com/workers/vite-plugin/reference/api/) for more info.
Jan 20, 2026
1. ### [Import SQL files as additional modules by default](https://developers.cloudflare.com/changelog/2026-01-20-sql-module-rule/)
[Workers](https://developers.cloudflare.com/workers/)
The `.sql` file extension is now automatically configured to be importable in your Worker code when using [Wrangler](https://developers.cloudflare.com/workers/wrangler/bundling/#including-non-javascript-modules) or the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/reference/non-javascript-modules/). This is particular useful for importing migrations in Durable Objects and means you no longer need to configure custom rules when using [Drizzle](https://orm.drizzle.team/docs/connect-cloudflare-do).
SQL files are imported as JavaScript strings:
```ts
// `example` will be a JavaScript string
import example from "./example.sql";
```
Jan 19, 2026
1. ### [Enhanced HTTP/3 request cancellation visibility](https://developers.cloudflare.com/changelog/2026-01-19-http3-499-reporting-improvement/)
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
#### Enhanced HTTP/3 request cancellation visibility
Cloudflare now provides more accurate visibility into HTTP/3 client request cancellations, giving you better insight into real client behavior and reducing unnecessary load on your origins.
Previously, when an HTTP/3 client cancelled a request, the cancellation was not always actioned immediately. This meant requests could continue through the CDN — potentially all the way to your origin — even after the client had abandoned them. In these cases, logs would show the upstream response status (such as `200` or a timeout-related code) rather than reflecting the client cancellation.
Now, Cloudflare terminates cancelled HTTP/3 requests immediately and accurately logs them with a `499` status code.
***
#### Better observability for client behavior
When HTTP/3 clients cancel requests, Cloudflare now immediately reflects this in your logs with a `499` status code. This gives you:
* **More accurate traffic analysis**: Understand exactly when and how often clients cancel requests.
* **Clearer debugging**: Distinguish between true errors and intentional client cancellations.
* **Better availability metrics**: Separate client-initiated cancellations from server-side issues.
***
#### Reduced origin load
Cloudflare now terminates cancelled requests faster, which means:
* **Less wasted compute**: Your origin no longer processes requests that clients have already abandoned.
* **Lower bandwidth usage**: Responses are no longer generated and transmitted for cancelled requests.
* **Improved efficiency**: Resources are freed up to handle active requests.
***
#### What to expect in your logs
You may notice an increase in `499` status codes for HTTP/3 traffic. For HTTP/3, a `499` indicates the client [cancelled the request stream](https://datatracker.ietf.org/doc/html/rfc9114#section-4.1.1) before receiving a complete response — the underlying connection may remain open. This is a normal part of web traffic.
**Tip**: If you use `499` codes in availability calculations, consider whether client-initiated cancellations should be excluded from error rates. These typically represent normal user behavior — such as closing a browser, navigating away from a page, mobile network drops, or cancelling a download — rather than service issues.
***
For more information, refer to [Error 499](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/4xx-client-error/error-499/).
Jan 15, 2026
1. ### [Verify WARP Connector connectivity with a simple ping](https://developers.cloudflare.com/changelog/2026-01-15-warp-connector-ping-support/)
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
We have made it easier to validate connectivity when deploying [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) as part of your [software-defined private network](https://developers.cloudflare.com/reference-architecture/architectures/sase/#connecting-networks).
You can now `ping` the WARP Connector host directly on its LAN IP address immediately after installation. This provides a fast, familiar way to confirm that the Connector is online and reachable within your network before testing access to downstream services.
Starting with [version 2025.10.186.0](https://developers.cloudflare.com/changelog/2026-01-13-warp-linux-ga/), WARP Connector responds to traffic addressed to its own LAN IP, giving you immediate visibility into Connector reachability.
Learn more about deploying [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) and building private network connectivity with [Cloudflare One](https://developers.cloudflare.com/cloudflare-one/).
Jan 15, 2026
1. ### [Network Services navigation update](https://developers.cloudflare.com/changelog/2026-01-15-networking-navigation-update/)
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic Firewall ](https://developers.cloudflare.com/magic-firewall/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/)
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.
Jan 15, 2026
1. ### [Support for CrowdStrike device scores in User Risk Scoring](https://developers.cloudflare.com/changelog/2026-1-15-crowdstrike-score/)
[Risk Score](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)
Cloudflare One has expanded its \[User Risk Scoring] (/cloudflare-one/insights/risk-score/) capabilities by introducing two new behaviors for organizations using the \[CrowdStrike integration] (/cloudflare-one/integrations/service-providers/crowdstrike/).
Administrators can now automatically escalate the risk score of a user if their device matches specific CrowdStrike Zero Trust Assessment (ZTA) score ranges. This allows for more granular security policies that respond dynamically to the health of the endpoint.
New risk behaviors The following risk scoring behaviors are now available:
* CrowdStrike low device score: Automatically increases a user's risk score when the connected device reports a "Low" score from CrowdStrike.
* CrowdStrike medium device score: Automatically increases a user's risk score when the connected device reports a "Medium" score from CrowdStrike.
These scores are derived from \[CrowdStrike device posture attributes] (/cloudflare-one/integrations/service-providers/crowdstrike/#device-posture-attributes), including OS signals and sensor configurations.
Jan 15, 2026
1. ### [WAF Release - 2026-01-15](https://developers.cloudflare.com/changelog/2026-01-15-waf-release/)
[WAF](https://developers.cloudflare.com/waf/)
This week's release focuses on improvements to existing detections to enhance coverage.
**Key Findings**
* Existing rule enhancements have been deployed to improve detection resilience against SQL Injection.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | eb3f44c07266448b9fa54ee7ad7dad3e | N/A | SQLi - String Function - Beta | Log | Block | This rule is merged into the original rule "SQLi - String Function" (ID: 63e03eecddfc4b3fb0cad587d32b798c ) |
| Cloudflare Managed Ruleset | adf076af09b2484ca9e7881f9e553ad3 | N/A | SQLi - Sub Query - Beta | Log | Block | This rule is merged into the original rule "SQLi - Sub Query" (ID: 6ec5ecf52c094330aff99a38743e66b1 ) |
Jan 15, 2026
1. ### [Launching FLUX.2 \[klein\] 4B on Workers AI](https://developers.cloudflare.com/changelog/2026-01-15-flux-2-klein-4b-workers-ai/)
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We've partnered with Black Forest Labs (BFL) again to bring their optimized FLUX.2 \[klein] 4B model to Workers AI! This distilled model offers faster generation and cost-effective pricing, while maintaining great output quality. With a fixed 4-step inference process, Klein 4B is ideal for rapid prototyping and real-time applications where speed matters.
Read the [BFL blog](https://bfl.ai/blog) to learn more about the model itself, or try it out yourself on our [multi modal playground](https://multi-modal.ai.cloudflare.com/).
Pricing documentation is available on the [model page](https://developers.cloudflare.com/workers-ai/models/flux-2-klein-4b/) or [pricing page](https://developers.cloudflare.com/workers-ai/platform/pricing/).
#### Workers AI Platform specifics
The model hosted on Workers AI is optimized for speed with a **fixed 4-step inference process** and supports up to 4 image inputs. Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted. Like FLUX.2 \[dev], this image model uses multipart form data inputs, even if you just have a prompt.
With the REST API, the multipart form data input looks like this:
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-4b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=a sunset at the alps' \
--form width=1024 \
--form height=1024
```
With the Workers AI binding, you can use it as such:
```javascript
const form = new FormData();
form.append("prompt", "a sunset with a dog");
form.append("width", "1024");
form.append("height", "1024");
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-4b", {
multipart: {
body: formStream,
contentType: formContentType,
},
});
const formStream = formRequest.body;
const formContentType =
formRequest.headers.get("content-type") || "multipart/form-data";
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-4b", {
multipart: {
body: formStream,
contentType: formContentType,
},
});
```
The parameters you can send to the model are detailed here:
JSON Schema for Model
**Required Parameters**
* `prompt` (string) - Text description of the image to generate
**Optional Parameters**
* `input_image_0` (string) - Binary image
* `input_image_1` (string) - Binary image
* `input_image_2` (string) - Binary image
* `input_image_3` (string) - Binary image
* `guidance` (float) - Guidance scale for generation. Higher values follow the prompt more closely
* `width` (integer) - Width of the image, default `1024` Range: 256-1920
* `height` (integer) - Height of the image, default `768` Range: 256-1920
* `seed` (integer) - Seed for reproducibility
**Note:** Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted.
````plaintext
## Multi-Reference Images
The FLUX.2 klein-4b model supports generating images based on reference images, just like FLUX.2 [dev]. You can use this feature to apply the style of one image to another, add a new character to an image, or iterate on past generated images. You would use it with the same multipart form data structure, with the input images in binary. The model supports up to 4 input images.
For the prompt, you can reference the images based on the index, like `take the subject of image 1 and style it like image 0` or even use natural language like `place the dog beside the woman`.
Note: you have to name the input parameter as `input_image_0`, `input_image_1`, `input_image_2`, `input_image_3` for it to work correctly. All input images must be smaller than 512x512.
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-4b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=take the subject of image 1 and style it like image 0' \
--form input_image_0=@/Users/johndoe/Desktop/icedoutkeanu.png \
--form input_image_1=@/Users/johndoe/Desktop/me.png \
--form width=1024 \
--form height=1024
````
Through Workers AI Binding:
```javascript
//helper function to convert ReadableStream to Blob
async function streamToBlob(stream: ReadableStream, contentType: string): Promise {
const reader = stream.getReader();
const chunks = [];
while (true) {
const { done, value } = await reader.read();
if (done) break;
chunks.push(value);
}
return new Blob(chunks, { type: contentType });
}
const image0 = await fetch("http://image-url");
const image1 = await fetch("http://image-url");
const form = new FormData();
const image_blob0 = await streamToBlob(image0.body, "image/png");
const image_blob1 = await streamToBlob(image1.body, "image/png");
form.append('input_image_0', image_blob0)
form.append('input_image_1', image_blob1)
form.append('prompt', 'take the subject of image 1 and style it like image 0')
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-4b", {
multipart: {
body: form,
contentType: "multipart/form-data"
}
})
```
Jan 14, 2026
1. ### [URL Scanner now supports PDF report downloads](https://developers.cloudflare.com/changelog/2026-01-14-download-url-scanner-report-pdf/)
[Security Center](https://developers.cloudflare.com/security-center/)
We have expanded the reporting capabilities of the Cloudflare URL Scanner. In addition to existing JSON and HAR exports, users can now generate and download a **PDF report** directly from the Cloudflare dashboard. This update streamlines how security analysts can share findings with stakeholders who may not have access to the Cloudflare dashboard or specialized tools to parse JSON and HAR files.
**Key Benefits:**
* Consolidate scan results, including screenshots, security signatures, and metadata, into a single, portable document
* Easily share professional-grade summaries with non-technical stakeholders or legal teams for faster incident response
**What’s new:**
* **PDF Export Button:** A new download option is available in the URL Scanner results page within the Cloudflare dashboard
* **Unified Documentation:** Access all scan details—from high-level summaries to specific security flags—in one offline-friendly file
To get started with the URL Scanner and explore our reporting capabilities, visit the [URL Scanner API documentation](https://developers.cloudflare.com/api/resources/url_scanner/).
***
Jan 13, 2026
1. ### [WARP client for Windows (version 2025.10.186.0)](https://developers.cloudflare.com/changelog/2026-01-13-warp-windows-ga/)
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features. New features include the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/), and a new WARP client device posture check for [Antivirus](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/antivirus/).
**Changes and improvements**
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
* Fixed an issue that caused occasional audio degradation and increased CPU usage on Windows by optimizing route configurations for large [domain-based split tunnel rules](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/split-tunnels/#domain-based-split-tunnels).
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where sending large messages to the daemon by Inter-Process Communication (IPC) could cause the daemon to fail and result in service interruptions.
* Added support for a new WARP client device posture check for [Antivirus](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/antivirus/). The check confirms the presence of an antivirus program on a Windows device with the option to check if the antivirus is up to date.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
Jan 13, 2026
1. ### [WARP client for macOS (version 2025.10.186.0)](https://developers.cloudflare.com/changelog/2026-01-13-warp-macos-ga/)
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features, including the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/).
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
Jan 13, 2026
1. ### [WARP client for Linux (version 2025.10.186.0)](https://developers.cloudflare.com/changelog/2026-01-13-warp-linux-ga/)
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features, including the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/).
WARP client version 2025.8.779.0 introduced an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com).
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* Linux [disk encryption posture check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/disk-encryption/) now supports non-filesystem encryption types like `dm-crypt`.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where the GUI becomes unresponsive when the **Re-Authenticate in browser** button is clicked.
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
Jan 13, 2026
1. ### [AI Crawl Control Read Only role now available](https://developers.cloudflare.com/changelog/2026-01-13-ai-crawl-control-read-only-role/)
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
Account administrators can now assign the **AI Crawl Control Read Only** role to provide read-only access to AI Crawl Control at the domain level.
Users with this role can view the **Overview**, **Crawlers**, **Metrics**, **Robots.txt**, and **Settings** tabs but cannot modify crawler actions or settings.
This role is specific for AI Crawl Control. You still require correct permissions to access other areas / features of the dashboard.
To assign, go to **Manage Account** > **Members** and add a policy with the **AI Crawl Control Read Only** role scoped to the desired domain.
Jan 13, 2026
1. ### [\`wrangler types\` now generates types for all environments](https://developers.cloudflare.com/changelog/2026-01-13-wrangler-types-multi-environment/)
[Workers](https://developers.cloudflare.com/workers/)
The `wrangler types` command now generates TypeScript types for bindings from **all environments** defined in your Wrangler configuration file by default.
Previously, `wrangler types` only generated types for bindings in the top-level configuration (or a single environment when using the `--env` flag). This meant that if you had environment-specific bindings — for example, a KV namespace only in production or an R2 bucket only in staging — those bindings would be missing from your generated types, causing TypeScript errors when accessing them.
Now, running `wrangler types` collects bindings from all environments and includes them in the generated `Env` type. This ensures your types are complete regardless of which environment you deploy to.
#### Generating types for a specific environment
If you want the previous behavior of generating types for only a specific environment, you can use the `--env` flag:
```sh
wrangler types --env production
```
Learn more about [generating types for your Worker](https://developers.cloudflare.com/workers/wrangler/commands/#types) in the Wrangler documentation.
Jan 12, 2026
1. ### [Enhanced visibility for post-delivery actions](https://developers.cloudflare.com/changelog/2026-01-12-enhanced-visibility-post-delivery-actions/)
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
The Action Log now provides enriched data for post-delivery actions to improve troubleshooting. In addition to success confirmations, failed actions now display the targeted Destination folder and a specific failure reason within the Activity field.
Note
Error messages will vary depending on whether you are using Google Workspace or Microsoft 365.
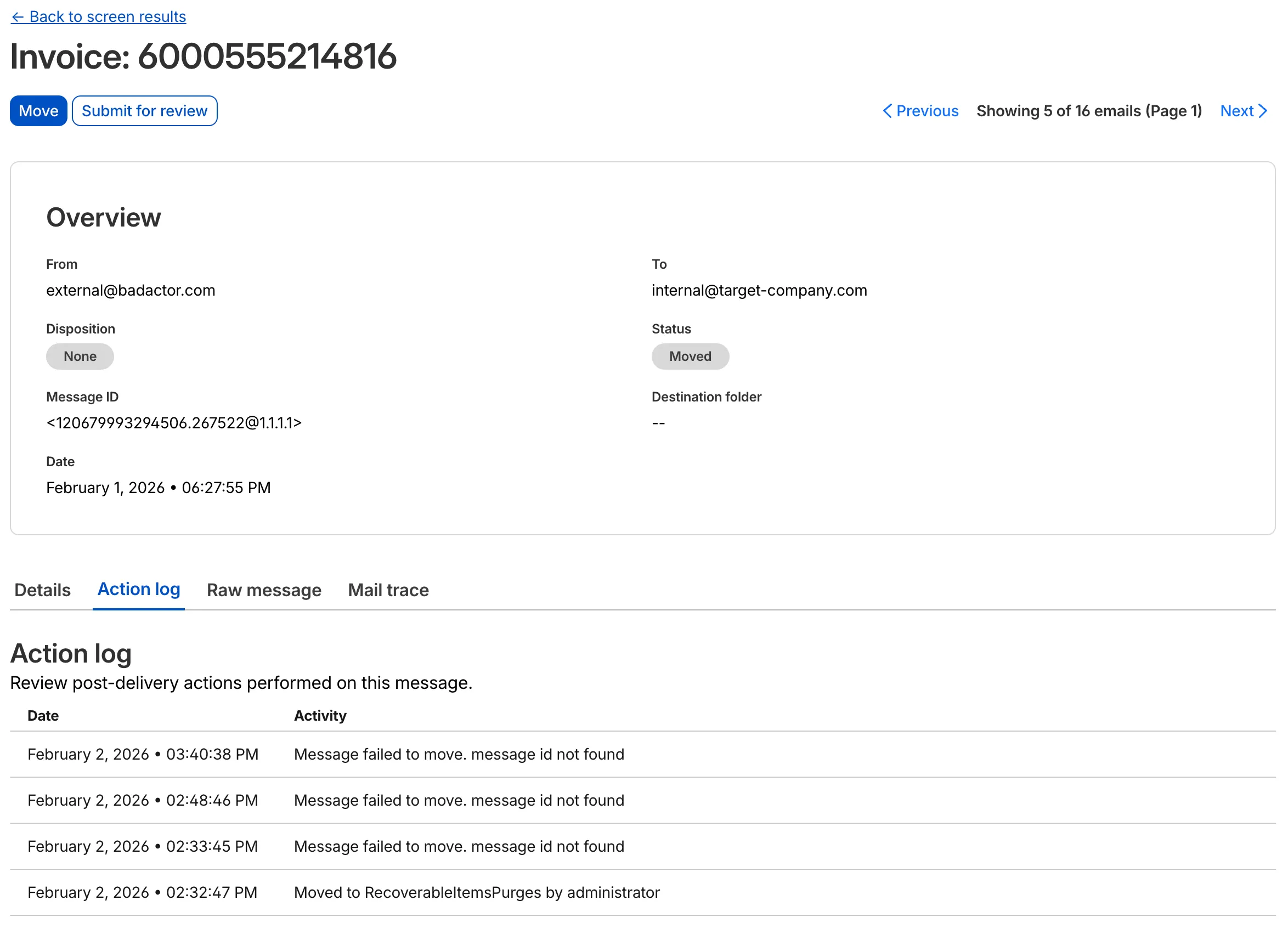
This update allows you to see the full lifecycle of a failed action. For instance, if an administrator tries to move an email that has already been deleted or moved manually, the log will now show the multiple retry attempts and the specific destination error.
This applies to all Email Security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
Jan 12, 2026
1. ### [Metro code field now available in Rules](https://developers.cloudflare.com/changelog/2026-01-12-dma-metro-code-field/)
[Rules](https://developers.cloudflare.com/rules/)
The `ip.src.metro_code` field in the Ruleset Engine is now populated with DMA (Designated Market Area) data.
You can use this field to build rules that target traffic based on geographic market areas, enabling more granular location-based policies for your applications.
#### Field details
| Field | Type | Description |
| - | - | - |
| `ip.src.metro_code` | String \| null | The metro code (DMA) of the incoming request's IP address. Returns the designated market area code for the client's location. |
Example filter expression:
```plaintext
ip.src.metro_code eq "501"
```
For more information, refer to the [Fields reference](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/ip.src.metro_code/).
Jan 12, 2026
1. ### [Cloudflare Threat Events now support STIX2 format](https://developers.cloudflare.com/changelog/2026-01-12-stix2-available-for-threat-events-api/)
[Security Center](https://developers.cloudflare.com/security-center/)
We are excited to announce that **Cloudflare Threat Events** now supports the **STIX2 (Structured Threat Information Expression)** format. This was a highly requested feature designed to streamline how security teams consume and act upon our threat intelligence.
By adopting this industry-standard format, you can now integrate Cloudflare's threat events data more effectively into your existing security ecosystem.
#### Key benefits
* Eliminate the need for custom parsers, as STIX2 allows for "out of the box" ingestion into major **Threat Intel Platforms (TIPs)**, **SIEMs**, and **SOAR** tools.
* STIX2 provides a standardized way to represent relationships between indicators, sightings, and threat actors, giving your analysts a clearer picture of the threat landscape.
For technical details on how to query events using this format, please refer to our [Threat Events API Documentation](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/threat_events/methods/list/).
***
Jan 09, 2026
1. ### [Get notified when your Workers builds succeed or fail](https://developers.cloudflare.com/changelog/2025-12-11-builds-event-subscriptions/)
[Workers ](https://developers.cloudflare.com/workers/)[Queues](https://developers.cloudflare.com/queues/)
You can now receive notifications when your Workers' builds start, succeed, fail, or get cancelled using [Event Subscriptions](https://developers.cloudflare.com/queues/event-subscriptions/).
[Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/) publishes events to a [Queue](https://developers.cloudflare.com/queues/) that your Worker can read messages from, and then send notifications wherever you need — Slack, Discord, email, or any webhook endpoint.
You can deploy [this Worker](https://github.com/cloudflare/templates/tree/main/workers-builds-notifications-template) to your own Cloudflare account to send build notifications to Slack:
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/workers-builds-notifications-template)
The template includes:
* Build status with Preview/Live URLs for successful deployments
* Inline error messages for failed builds
* Branch, commit hash, and author name
For setup instructions, refer to the [template README](https://github.com/cloudflare/templates/tree/main/workers-builds-notifications-template#readme) or the [Event Subscriptions documentation](https://developers.cloudflare.com/queues/event-subscriptions/manage-event-subscriptions/).
Jan 08, 2026
1. ### [Cloudflare admin activity logs capture creation of DNS over HTTP (DoH) users](https://developers.cloudflare.com/changelog/2026-01-08-access-audit-log-for-doh-users/)
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
Cloudflare [admin activity logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) now capture each time a [DNS over HTTP (DoH) user](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/dns-over-https/) is created.
These logs can be viewed from the [Cloudflare One dashboard](https://one.dash.cloudflare.com/), pulled via the [Cloudflare API](https://developers.cloudflare.com/api/), and exported through [Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/).
Jan 07, 2026
1. ### [Workers Analytics Engine SQL now supports filtering using HAVING and LIKE](https://developers.cloudflare.com/changelog/2026-01-07-analytics-engine-support-for-like-and-having/)
[Workers Analytics Engine ](https://developers.cloudflare.com/analytics/analytics-engine/)[Workers](https://developers.cloudflare.com/workers/)
You can now use the `HAVING` clause and `LIKE` pattern matching operators in [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/).
Workers Analytics Engine allows you to ingest and store high-cardinality data at scale and query your data through a simple SQL API.
#### Filtering using `HAVING`
The `HAVING` clause complements the `WHERE` clause by enabling you to filter groups based on aggregate values. While `WHERE` filters rows before aggregation, `HAVING` filters groups after aggregation is complete.
You can use `HAVING` to filter groups where the average exceeds a threshold:
```sql
SELECT
blob1 AS probe_name,
avg(double1) AS average_temp
FROM temperature_readings
GROUP BY probe_name
HAVING average_temp > 10
```
You can also filter groups based on aggregates such as the number of items in the group:
```sql
SELECT
blob1 AS probe_name,
count() AS num_readings
FROM temperature_readings
GROUP BY probe_name
HAVING num_readings > 100
```
#### Pattern matching using `LIKE`
The new pattern matching operators enable you to search for strings that match specific patterns using wildcard characters:
* `LIKE` - case-sensitive pattern matching
* `NOT LIKE` - case-sensitive pattern exclusion
* `ILIKE` - case-insensitive pattern matching
* `NOT ILIKE` - case-insensitive pattern exclusion
Pattern matching supports two wildcard characters: `%` (matches zero or more characters) and `_` (matches exactly one character).
You can match strings starting with a prefix:
```sql
SELECT *
FROM logs
WHERE blob1 LIKE 'error%'
```
You can also match file extensions (case-insensitive):
```sql
SELECT *
FROM requests
WHERE blob2 ILIKE '%.jpg'
```
Another example is excluding strings containing specific text:
```sql
SELECT *
FROM events
WHERE blob3 NOT ILIKE '%debug%'
```
#### Ready to get started?
Learn more about the [`HAVING` clause](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/statements/#having-clause) or [pattern matching operators](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/operators/#pattern-matching-operators) in the Workers Analytics Engine SQL reference documentation.
Jan 05, 2026
1. ### [Custom container instance types now available for all users](https://developers.cloudflare.com/changelog/2026-01-05-custom-instance-types/)
[Containers](https://developers.cloudflare.com/containers/)
Custom instance types are now enabled for all [Cloudflare Containers](https://developers.cloudflare.com/containers) users. You can now specify specific vCPU, memory, and disk amounts, rather than being limited to pre-defined [instance types](https://developers.cloudflare.com/containers/platform-details/limits/#instance-types). Previously, only select Enterprise customers were able to customize their instance type.
To use a custom instance type, specify the `instance_type` property as an object with `vcpu`, `memory_mib`, and `disk_mb` fields in your Wrangler configuration:
```toml
[[containers]]
image = "./Dockerfile"
instance_type = { vcpu = 2, memory_mib = 6144, disk_mb = 12000 }
```
Individual limits for custom instance types are based on the `standard-4` instance type (4 vCPU, 12 GiB memory, 20 GB disk). You must allocate at least 1 vCPU for custom instance types. For workloads requiring less than 1 vCPU, use the predefined instance types like `lite` or `basic`.
See the [limits documentation](https://developers.cloudflare.com/containers/platform-details/limits/#custom-instance-types) for the full list of constraints on custom instance types. See the [getting started guide](https://developers.cloudflare.com/containers/get-started/) to deploy your first Container,
Dec 31, 2025
1. ### [Breakout traffic visibility via NetFlow](https://developers.cloudflare.com/changelog/2025-12-31-connector-breakout-traffic-netflow/)
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Magic WAN Connector now exports NetFlow data for breakout traffic to Magic Network Monitoring (MNM), providing visibility into traffic that bypasses Cloudflare's security filtering.
This feature allows you to:
* Monitor breakout traffic statistics in the Cloudflare dashboard.
* View traffic patterns for applications configured to bypass Cloudflare.
* Maintain visibility across all traffic passing through your Magic WAN Connector.
For more information, refer to [NetFlow statistics](https://developers.cloudflare.com/magic-wan/analytics/netflow-analytics/).
Dec 22, 2025
1. ### [Agents SDK v0.3.0, workers-ai-provider v3.0.0, and ai-gateway-provider v3.0.0 with AI SDK v6 support](https://developers.cloudflare.com/changelog/2025-12-22-agents-sdk-ai-sdk-v6/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We've shipped a new release for the [Agents SDK](https://github.com/cloudflare/agents) v0.3.0 bringing full compatibility with [AI SDK v6](https://ai-sdk.dev/docs/introduction) and introducing the unified tool pattern, dynamic tool approval, and enhanced React hooks with improved tool handling.
This release includes improved streaming and tool support, dynamic tool approval (for "human in the loop" systems), enhanced React hooks with `onToolCall` callback, improved error handling for streaming responses, and seamless migration from v5 patterns.
This makes it ideal for building production AI chat interfaces with Cloudflare Workers AI models, agent workflows, human-in-the-loop systems, or any application requiring reliable tool execution and approval workflows.
Additionally, we've updated **workers-ai-provider v3.0.0**, the official provider for Cloudflare Workers AI models, and **ai-gateway-provider v3.0.0**, the provider for Cloudflare AI Gateway, to be compatible with AI SDK v6.
#### Agents SDK v0.3.0
#### Unified Tool Pattern
AI SDK v6 introduces a unified tool pattern where all tools are defined on the server using the `tool()` function. This replaces the previous client-side `AITool` pattern.
#### Server-Side Tool Definition
```ts
import { tool } from "ai";
import { z } from "zod";
// Server: Define ALL tools on the server
const tools = {
// Server-executed tool
getWeather: tool({
description: "Get weather for a city",
inputSchema: z.object({ city: z.string() }),
execute: async ({ city }) => fetchWeather(city)
}),
// Client-executed tool (no execute = client handles via onToolCall)
getLocation: tool({
description: "Get user location from browser",
inputSchema: z.object({})
// No execute function
}),
// Tool requiring approval (dynamic based on input)
processPayment: tool({
description: "Process a payment",
inputSchema: z.object({ amount: z.number() }),
needsApproval: async ({ amount }) => amount > 100,
execute: async ({ amount }) => charge(amount)
})
};
```
#### Client-Side Tool Handling
```ts
// Client: Handle client-side tools via onToolCall callback
import { useAgentChat } from "agents/ai-react";
const { messages, sendMessage, addToolOutput } = useAgentChat({
agent,
onToolCall: async ({ toolCall, addToolOutput }) => {
if (toolCall.toolName === "getLocation") {
const position = await new Promise((resolve, reject) => {
navigator.geolocation.getCurrentPosition(resolve, reject);
});
addToolOutput({
toolCallId: toolCall.toolCallId,
output: {
lat: position.coords.latitude,
lng: position.coords.longitude
}
});
}
}
});
```
**Key benefits of the unified tool pattern:**
* **Server-defined tools**: All tools are defined in one place on the server
* **Dynamic approval**: Use `needsApproval` to conditionally require user confirmation
* **Cleaner client code**: Use `onToolCall` callback instead of managing tool configs
* **Type safety**: Full TypeScript support with proper tool typing
#### useAgentChat(options)
Creates a new chat interface with enhanced v6 capabilities.
```ts
// Basic chat setup with onToolCall
const { messages, sendMessage, addToolOutput } = useAgentChat({
agent,
onToolCall: async ({ toolCall, addToolOutput }) => {
// Handle client-side tool execution
await addToolOutput({
toolCallId: toolCall.toolCallId,
output: { result: "success" }
});
}
});
```
#### Dynamic Tool Approval
Use `needsApproval` on server tools to conditionally require user confirmation:
```ts
const paymentTool = tool({
description: "Process a payment",
inputSchema: z.object({
amount: z.number(),
recipient: z.string()
}),
needsApproval: async ({ amount }) => amount > 1000,
execute: async ({ amount, recipient }) => {
return await processPayment(amount, recipient);
}
});
```
#### Tool Confirmation Detection
The `isToolUIPart` and `getToolName` functions now check both static and dynamic tool parts:
```ts
import { isToolUIPart, getToolName } from "ai";
const pendingToolCallConfirmation = messages.some((m) =>
m.parts?.some(
(part) => isToolUIPart(part) && part.state === "input-available",
),
);
// Handle tool confirmation
if (pendingToolCallConfirmation) {
await addToolOutput({
toolCallId: part.toolCallId,
output: "User approved the action"
});
}
```
If you need the v5 behavior (static-only checks), use the new functions:
```ts
import { isStaticToolUIPart, getStaticToolName } from "ai";
```
#### convertToModelMessages() is now async
The `convertToModelMessages()` function is now asynchronous. Update all calls to await the result:
```ts
import { convertToModelMessages } from "ai";
const result = streamText({
messages: await convertToModelMessages(this.messages),
model: openai("gpt-4o")
});
```
#### ModelMessage type
The `CoreMessage` type has been removed. Use `ModelMessage` instead:
```ts
import { convertToModelMessages, type ModelMessage } from "ai";
const modelMessages: ModelMessage[] = await convertToModelMessages(messages);
```
#### generateObject mode option removed
The `mode` option for `generateObject` has been removed:
```ts
// Before (v5)
const result = await generateObject({
mode: "json",
model,
schema,
prompt
});
// After (v6)
const result = await generateObject({
model,
schema,
prompt
});
```
#### Structured Output with generateText
While `generateObject` and `streamObject` are still functional, the recommended approach is to use `generateText`/`streamText` with the `Output.object()` helper:
```ts
import { generateText, Output, stepCountIs } from "ai";
const { output } = await generateText({
model: openai("gpt-4"),
output: Output.object({
schema: z.object({ name: z.string() })
}),
stopWhen: stepCountIs(2),
prompt: "Generate a name"
});
```
> **Note**: When using structured output with `generateText`, you must configure multiple steps with `stopWhen` because generating the structured output is itself a step.
#### workers-ai-provider v3.0.0
Seamless integration with Cloudflare Workers AI models through the updated workers-ai-provider v3.0.0 with AI SDK v6 support.
#### Model Setup with Workers AI
Use Cloudflare Workers AI models directly in your agent workflows:
```ts
import { createWorkersAI } from "workers-ai-provider";
import { useAgentChat } from "agents/ai-react";
// Create Workers AI model (v3.0.0 - enhanced v6 internals)
const model = createWorkersAI({
binding: env.AI,
})("@cf/meta/llama-3.2-3b-instruct");
```
#### Enhanced File and Image Support
Workers AI models now support v6 file handling with automatic conversion:
```ts
// Send images and files to Workers AI models
sendMessage({
role: "user",
parts: [
{ type: "text", text: "Analyze this image:" },
{
type: "file",
data: imageBuffer,
mediaType: "image/jpeg",
},
],
});
// Workers AI provider automatically converts to proper format
```
#### Streaming with Workers AI
Enhanced streaming support with automatic warning detection:
```ts
// Streaming with Workers AI models
const result = await streamText({
model: createWorkersAI({ binding: env.AI })("@cf/meta/llama-3.2-3b-instruct"),
messages: await convertToModelMessages(messages),
onChunk: (chunk) => {
// Enhanced streaming with warning handling
console.log(chunk);
},
});
```
#### ai-gateway-provider v3.0.0
The ai-gateway-provider v3.0.0 now supports AI SDK v6, enabling you to use Cloudflare AI Gateway with multiple AI providers including Anthropic, Azure, AWS Bedrock, Google Vertex, and Perplexity.
#### AI Gateway Setup
Use Cloudflare AI Gateway to add analytics, caching, and rate limiting to your AI applications:
```ts
import { createAIGateway } from "ai-gateway-provider";
// Create AI Gateway provider (v3.0.0 - enhanced v6 internals)
const model = createAIGateway({
gatewayUrl: "https://gateway.ai.cloudflare.com/v1/your-account-id/gateway",
headers: {
"Authorization": `Bearer ${env.AI_GATEWAY_TOKEN}`
}
})({
provider: "openai",
model: "gpt-4o"
});
```
#### Migration from v5
#### Deprecated APIs
The following APIs are deprecated in favor of the unified tool pattern:
| Deprecated | Replacement |
| - | - |
| `AITool` type | Use AI SDK's `tool()` function on server |
| `extractClientToolSchemas()` | Define tools on server, no client schemas needed |
| `createToolsFromClientSchemas()` | Define tools on server with `tool()` |
| `toolsRequiringConfirmation` option | Use `needsApproval` on server tools |
| `experimental_automaticToolResolution` | Use `onToolCall` callback |
| `tools` option in `useAgentChat` | Use `onToolCall` for client-side execution |
| `addToolResult()` | Use `addToolOutput()` |
#### Breaking Changes Summary
1. **Unified Tool Pattern**: All tools must be defined on the server using `tool()`
2. **`convertToModelMessages()` is async**: Add `await` to all calls
3. **`CoreMessage` removed**: Use `ModelMessage` instead
4. **`generateObject` mode removed**: Remove `mode` option
5. **`isToolUIPart` behavior changed**: Now checks both static and dynamic tool parts
#### Installation
Update your dependencies to use the latest versions:
```bash
npm install agents@^0.3.0 workers-ai-provider@^3.0.0 ai-gateway-provider@^3.0.0 ai@^6.0.0 @ai-sdk/react@^3.0.0 @ai-sdk/openai@^3.0.0
```
#### Resources
* [Migration Guide](https://github.com/cloudflare/agents/blob/main/docs/migration-to-ai-sdk-v6.md) - Comprehensive migration documentation from v5 to v6
* [AI SDK v6 Documentation](https://ai-sdk.dev/docs/migration-guides/migration-guide-6-0) - Official AI SDK migration guide
* [AI SDK v6 Announcement](https://vercel.com/blog/ai-sdk-6) - Learn about new features in v6
* [AI SDK Documentation](https://sdk.vercel.ai/docs) - Complete AI SDK reference
* [GitHub Issues](https://github.com/cloudflare/agents/issues) - Report bugs or request features
#### Feedback Welcome
We'd love your feedback! We're particularly interested in feedback on:
* **Migration experience** - How smooth was the upgrade from v5 to v6?
* **Unified tool pattern** - How does the new server-defined tool pattern work for you?
* **Dynamic tool approval** - Does the `needsApproval` feature meet your needs?
* **AI Gateway integration** - How well does the new provider work with your setup?
Dec 19, 2025
1. ### [Terraform v5.15.0 now available](https://developers.cloudflare.com/changelog/2025-12-19-terraform-v5150-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new Terraform v5 Provider. We are aware of the high number of issues reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) to ensure its stability and reliability, including the v5.15 release. We have also pivoted from an [issue-to-issue approach to a resource-per-resource approach](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) - we will be focusing on specific resources to not only stabilize the resource but also ensure it is migration-friendly for those migrating from v4 to v5.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes bug fixes, the stabilization of even more popular resources, and more.
#### Features
* **ai\_search:** Add AI Search endpoints ([6f02adb](https://github.com/cloudflare/terraform-provider-cloudflare/commit/6f02adb420e872457f71f95b49cb527663388915))
* **certificate\_pack:** Ensure proper Terraform resource ID handling for path parameters in API calls ([081f32a](https://github.com/cloudflare/terraform-provider-cloudflare/commit/081f32acab4ce9a194a7ff51c8e9fcabd349895a))
* **worker\_version:** Support `startup_time_ms` ([286ab55](https://github.com/cloudflare/terraform-provider-cloudflare/commit/286ab55bea8d5be0faa5a2b5b8b157e4a2214eba))
* **zero\_trust\_dlp\_custom\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_dlp\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_dlp\_integration\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_dlp\_predefined\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_gateway\_policy:** Support `forensic_copy` ([5741fd0](https://github.com/cloudflare/terraform-provider-cloudflare/commit/5741fd0ed9f7270d20731cc47ec45eb0403a628b))
* **zero\_trust\_list:** Support additional types (category, location, device) ([5741fd0](https://github.com/cloudflare/terraform-provider-cloudflare/commit/5741fd0ed9f7270d20731cc47ec45eb0403a628b))
#### Bug fixes
* **access\_rules:** Add validation to prevent state drift. Ideally, we'd use Semantic Equality but since that isn't an option, this will remove a foot-gun. ([4457791](https://github.com/cloudflare/terraform-provider-cloudflare/commit/44577911b3cbe45de6279aefa657bdee73c0794d))
* **cloudflare\_pages\_project:** Addressing drift issues ([6edffcf](https://github.com/cloudflare/terraform-provider-cloudflare/commit/6edffcfcf187fdc9b10b624b9a9b90aed2fb2b2e)) ([3db318e](https://github.com/cloudflare/terraform-provider-cloudflare/commit/3db318e747423bf10ce587d9149e90edcd8a77b0))
* **cloudflare\_worker:** Can be cleanly imported ([4859b52](https://github.com/cloudflare/terraform-provider-cloudflare/commit/4859b52968bb25570b680df9813f8e07fd50728f))
* **cloudflare\_worker:** Ensure clean imports ([5b525bc](https://github.com/cloudflare/terraform-provider-cloudflare/commit/5b525bc478a4e2c9c0d4fd659b92cc7f7c18016a))
* **list\_items:** Add validation for IP List items to avoid inconsistent state ([b6733dc](https://github.com/cloudflare/terraform-provider-cloudflare/commit/b6733dc4be909a5ab35895a88e519fc2582ccada))
* **zero\_trust\_access\_application:** Remove all conditions from sweeper ([3197f1a](https://github.com/cloudflare/terraform-provider-cloudflare/commit/3197f1aed61be326d507d9e9e3b795b9f1d18fd7))
* **spectrum\_application:** Map missing fields during spectrum resource import ([#6495](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6495)) ([ddb4e72](https://github.com/cloudflare/terraform-provider-cloudflare/commit/ddb4e722b82c735825a549d651a9da219c142efa))
#### Upgrade to newer version
We suggest waiting to migrate to v5 while we work on stabilization. This helps with avoiding any blocking issues while the Terraform resources are actively being [stabilized](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237). We will be releasing a new migration tool in March 2026 to help support v4 to v5 transitions for our most popular resources.
#### For more information
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Dec 18, 2025
1. ### [New AI Crawl Control Overview tab](https://developers.cloudflare.com/changelog/2025-12-18-overview-tab/)
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
The **Overview** tab is now the default view in AI Crawl Control. The previous default view with controls for individual AI crawlers is available in the **Crawlers** tab.
#### What's new
* **Executive summary** — Monitor total requests, volume change, most common status code, most popular path, and high-volume activity
* **Operator grouping** — Track crawlers by their operating companies (OpenAI, Microsoft, Google, ByteDance, Anthropic, Meta)
* **Customizable filters** — Filter your snapshot by date range, crawler, operator, hostname, or path
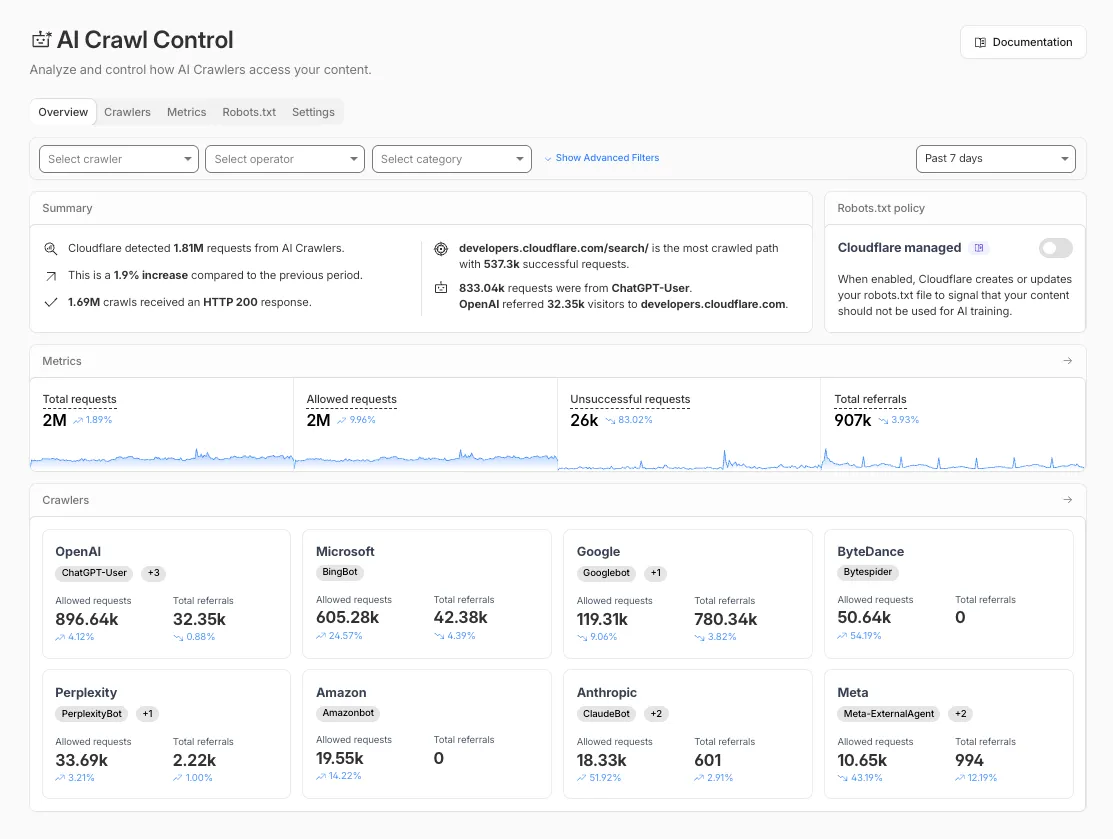
#### Get started
1. Log in to the Cloudflare dashboard and select your account and domain.
2. Go to **AI Crawl Control**, where the **Overview** tab opens by default with your activity snapshot.
3. Use filters to customize your view by date range, crawler, operator, hostname, or path.
4. Navigate to the **Crawlers** tab to manage controls for individual crawlers.
Learn more about [analyzing AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/) and [managing AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/).
Dec 18, 2025
1. ### [R2 Data Catalog now supports automatic snapshot expiration](https://developers.cloudflare.com/changelog/2025-12-18-r2-data-catalog-snapshot-expiration/)
[R2](https://developers.cloudflare.com/r2/)
[R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) now supports automatic snapshot expiration for Apache Iceberg tables.
In Apache Iceberg, a snapshot is metadata that represents the state of a table at a given point in time. Every mutation creates a new snapshot which enable powerful features like time travel queries and rollback capabilities but will accumulate over time.
Without regular cleanup, these accumulated snapshots can lead to:
* Metadata overhead
* Slower table operations
* Increased storage costs.
Snapshot expiration in R2 Data Catalog automatically removes old table snapshots based on your configured retention policy, improving performance and storage costs.
```bash
# Enable catalog-level snapshot expiration
# Expire snapshots older than 7 days, always retain at least 10 recent snapshots
npx wrangler r2 bucket catalog snapshot-expiration enable my-bucket \
--older-than-days 7 \
--retain-last 10
```
Snapshot expiration uses two parameters to determine which snapshots to remove:
* `--older-than-days`: age threshold in days
* `--retain-last`: minimum snapshot count to retain
Both conditions must be met before a snapshot is expired, ensuring you always retain recent snapshots even if they exceed the age threshold.
This feature complements [automatic compaction](https://developers.cloudflare.com/r2/data-catalog/table-maintenance/), which optimizes query performance by combining small data files into larger ones. Together, these automatic maintenance operations keep your Iceberg tables performant and cost-efficient without manual intervention.
To learn more about snapshot expiration and how to configure it, visit our [table maintenance documentation](https://developers.cloudflare.com/r2/data-catalog/table-maintenance/) or see [how to manage catalogs](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/).
Dec 18, 2025
1. ### [Workers for Platforms - Dashboard Improvements](https://developers.cloudflare.com/changelog/2025-12-18-dashboard-improvements/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/) lets you build multi-tenant platforms on [Cloudflare Workers](https://developers.cloudflare.com/workers/), allowing your end users to deploy and run their own code on your platform. It's designed for anyone building an AI vibe coding platform, e-commerce platform, website builder, or any product that needs to securely execute user-generated code at scale.
Previously, setting up Workers for Platforms required using the API. Now, the Workers for Platforms UI supports namespace creation, dispatch worker templates, and tag management, making it easier for Workers for Platforms customers to build and manage multi-tenant platforms directly from the Cloudflare dashboard.
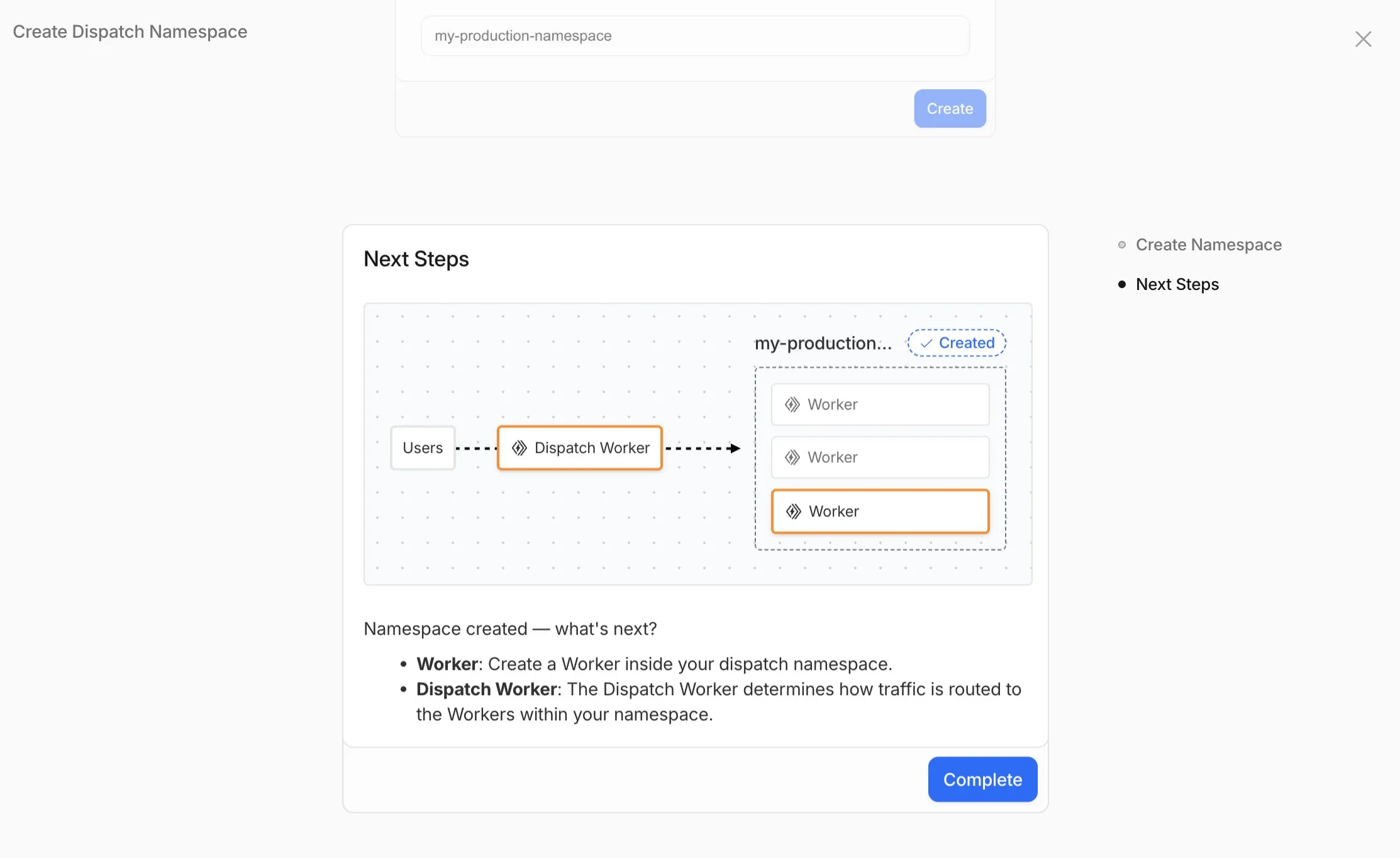
#### Key improvements
* **Namespace Management:** You can now create and configure [dispatch namespaces](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/#dispatch-namespace) directly within the dashboard to start a new platform setup.
* **Dispatch Worker Templates:** New Dispatch Worker templates allow you to quickly define how traffic is routed to individual Workers within your namespace. Refer to the [Dynamic Dispatch documentation](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/dynamic-dispatch/) for more examples.
* **Tag Management:** You can now set and update [tags](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/tags/) on User Workers, making it easier to group and manage your Workers.
* **Binding Visibility:** [Bindings](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/bindings/) attached to User Workers are now visible directly within the User Worker view.
* **Deploy Vibe Coding Platform in one-click:** Deploy a [reference implementation](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/) of an AI vibe coding platform directly from the dashboard. Powered by the Cloudflare's [VibeSDK](https://github.com/cloudflare/vibesdk), this starter kit integrates with Workers for Platforms to handle the deployment of AI-generated projects at scale.
To get started, go to **Workers for Platforms** under **Compute & AI** in the [Cloudflare dashboard](https://dash.cloudflare.com/).
Dec 17, 2025
1. ### [Shadow IT - domain level SaaS analytics](https://developers.cloudflare.com/changelog/2025-12-17-shadow-it-domain-analytics/)
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust has again upgraded its **Shadow IT analytics**, providing you with unprecedented visibility into your organizations use of SaaS tools. With this dashboard, you can review who is using an application and volumes of data transfer to the application.
With this update, you can review data transfer metrics at the domain level, rather than just the application level, providing more granular insight into your data transfer patterns.
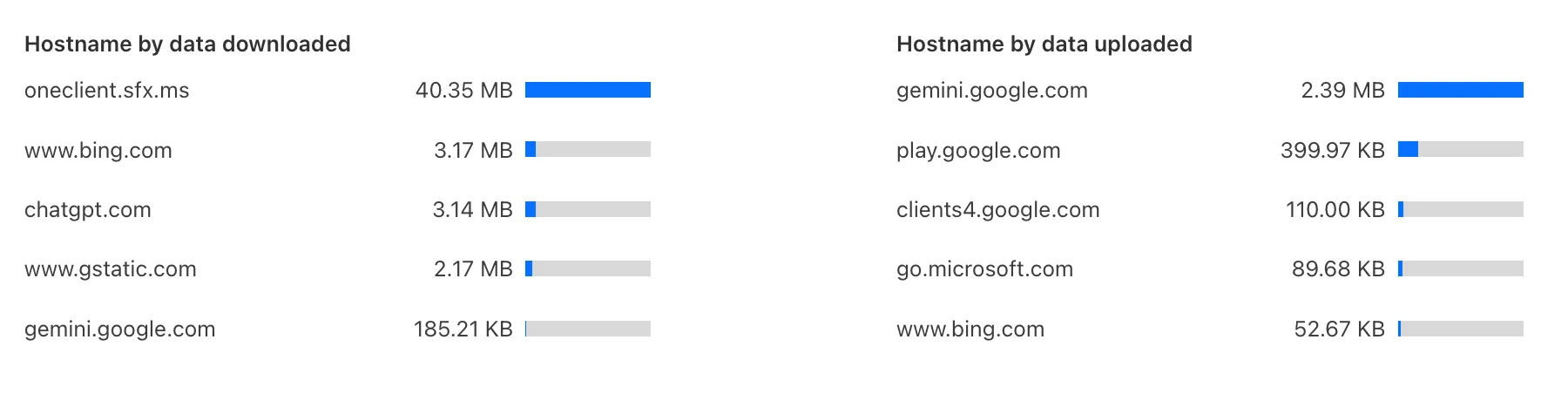
These metrics can be filtered by all available filters on the dashboard, including user, application, or content category.
Both the analytics and policies are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
Dec 16, 2025
1. ### [New duplicate action for supported Cloudflare One resources](https://developers.cloudflare.com/changelog/2025-12-16-new-duplicate-action-for-supported-cloudflare-one-resources/)
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
You can now duplicate specific Cloudflare One resources with a single click from the dashboard.
Initially supported resources:
* Access Applications
* Access Policies
* Gateway Policies
To try this out, simply click on the overflow menu (⋮) from the resource table and click *Duplicate*. We will continue to add the Duplicate action for resources throughout 2026.
Dec 15, 2025
1. ### [New Best Practices guide for Durable Objects](https://developers.cloudflare.com/changelog/2025-12-15-rules-of-durable-objects/)
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
A new [Rules of Durable Objects](https://developers.cloudflare.com/durable-objects/best-practices/rules-of-durable-objects/) guide is now available, providing opinionated best practices for building effective Durable Objects applications. This guide covers design patterns, storage strategies, concurrency, and common anti-patterns to avoid.
Key guidance includes:
* **Design around your "atom" of coordination** — Create one Durable Object per logical unit (chat room, game session, user) instead of a global singleton that becomes a bottleneck.
* **Use SQLite storage with RPC methods** — SQLite-backed Durable Objects with typed RPC methods provide the best developer experience and performance.
* **Understand input and output gates** — Learn how Cloudflare's runtime prevents data races by default, how write coalescing works, and when to use `blockConcurrencyWhile()`.
* **Leverage Hibernatable WebSockets** — Reduce costs for real-time applications by allowing Durable Objects to sleep while maintaining WebSocket connections.
The [testing documentation](https://developers.cloudflare.com/durable-objects/examples/testing-with-durable-objects/) has also been updated with modern patterns using `@cloudflare/vitest-pool-workers`, including examples for testing SQLite storage, alarms, and direct instance access:
* JavaScript
```js
import { env, runDurableObjectAlarm } from "cloudflare:test";
import { it, expect } from "vitest";
it("can test Durable Objects with isolated storage", async () => {
const stub = env.COUNTER.getByName("test");
// Call RPC methods directly on the stub
await stub.increment();
expect(await stub.getCount()).toBe(1);
// Trigger alarms immediately without waiting
await runDurableObjectAlarm(stub);
});
```
* TypeScript
```ts
import { env, runDurableObjectAlarm } from "cloudflare:test";
import { it, expect } from "vitest";
it("can test Durable Objects with isolated storage", async () => {
const stub = env.COUNTER.getByName("test");
// Call RPC methods directly on the stub
await stub.increment();
expect(await stub.getCount()).toBe(1);
// Trigger alarms immediately without waiting
await runDurableObjectAlarm(stub);
});
```
Dec 12, 2025
1. ### [Billing for SQLite Storage](https://developers.cloudflare.com/changelog/2025-12-12-durable-objects-sqlite-storage-billing/)
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
Storage billing for SQLite-backed Durable Objects will be enabled in January 2026, with a target date of January 7, 2026 (no earlier).
To view your SQLite storage usage, go to the **Durable Objects** page
[Go to **Durable Objects**](https://dash.cloudflare.com/?to=/:account/workers/durable-objects)
If you do not want to incur costs, please take action such as optimizing queries or deleting unnecessary stored data in order to reduce your SQLite storage usage ahead of the January 7th target. Only usage on and after the billing target date will incur charges.
Developers on the Workers Paid plan with Durable Object's SQLite storage usage beyond included limits will incur charges according to [SQLite storage pricing](https://developers.cloudflare.com/durable-objects/platform/pricing/#sqlite-storage-backend) announced in September 2024 with the [public beta](https://blog.cloudflare.com/sqlite-in-durable-objects/). Developers on the Workers Free plan will not be charged.
Compute billing for SQLite-backed Durable Objects has been enabled since the initial public beta. SQLite-backed Durable Objects currently incur [charges for requests and duration](https://developers.cloudflare.com/durable-objects/platform/pricing/#compute-billing), and no changes are being made to compute billing.
For more information about SQLite storage pricing and limits, refer to the [Durable Objects pricing documentation](https://developers.cloudflare.com/durable-objects/platform/pricing/#sqlite-storage-backend).
Dec 12, 2025
1. ### [R2 SQL now supports aggregations and schema discovery](https://developers.cloudflare.com/changelog/2025-12-12-aggregation-support-and-more/)
[R2 SQL](https://developers.cloudflare.com/r2-sql/)
R2 SQL now supports aggregation functions, `GROUP BY`, `HAVING`, along with schema discovery commands to make it easy to explore your data catalog.
#### Aggregation Functions
You can now perform aggregations on Apache Iceberg tables in [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) using standard SQL functions including `COUNT(*)`, `SUM()`, `AVG()`, `MIN()`, and `MAX()`. Combine these with `GROUP BY` to analyze data across dimensions, and use `HAVING` to filter aggregated results.
```sql
-- Calculate average transaction amounts by department
SELECT department, COUNT(*), AVG(total_amount)
FROM my_namespace.sales_data
WHERE region = 'North'
GROUP BY department
HAVING COUNT(*) > 50
ORDER BY AVG(total_amount) DESC
```
```sql
-- Find high-value departments
SELECT department, SUM(total_amount)
FROM my_namespace.sales_data
GROUP BY department
HAVING SUM(total_amount) > 50000
```
#### Schema Discovery
New metadata commands make it easy to explore your data catalog and understand table structures:
* `SHOW DATABASES` or `SHOW NAMESPACES` - List all available namespaces
* `SHOW TABLES IN namespace_name` - List tables within a namespace
* `DESCRIBE namespace_name.table_name` - View table schema and column types
```bash
❯ npx wrangler r2 sql query "{ACCOUNT_ID}_{BUCKET_NAME}" "DESCRIBE default.sales_data;"
⛅️ wrangler 4.54.0
─────────────────────────────────────────────
┌──────────────────┬────────────────┬──────────┬─────────────────┬───────────────┬───────────────────────────────────────────────────────────────────────────────────────────────────┐
│ column_name │ type │ required │ initial_default │ write_default │ doc │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sale_id │ BIGINT │ false │ │ │ Unique identifier for each sales transaction │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sale_timestamp │ TIMESTAMPTZ │ false │ │ │ Exact date and time when the sale occurred (used for partitioning) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ department │ TEXT │ false │ │ │ Product department (8 categories: Electronics, Beauty, Home, Toys, Sports, Food, Clothing, Books) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ category │ TEXT │ false │ │ │ Product category grouping (4 categories: Premium, Standard, Budget, Clearance) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ region │ TEXT │ false │ │ │ Geographic sales region (5 regions: North, South, East, West, Central) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ product_id │ INT │ false │ │ │ Unique identifier for the product sold │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ quantity │ INT │ false │ │ │ Number of units sold in this transaction (range: 1-50) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ unit_price │ DECIMAL(10, 2) │ false │ │ │ Price per unit in dollars (range: $5.00-$500.00) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ total_amount │ DECIMAL(10, 2) │ false │ │ │ Total sale amount before tax (quantity × unit_price with discounts applied) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ discount_percent │ INT │ false │ │ │ Discount percentage applied to this sale (0-50%) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ tax_amount │ DECIMAL(10, 2) │ false │ │ │ Tax amount collected on this sale │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ profit_margin │ DECIMAL(10, 2) │ false │ │ │ Profit margin on this sale as a decimal percentage │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ customer_id │ INT │ false │ │ │ Unique identifier for the customer who made the purchase │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ is_online_sale │ BOOLEAN │ false │ │ │ Boolean flag indicating if sale was made online (true) or in-store (false) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sale_date │ DATE │ false │ │ │ Calendar date of the sale (extracted from sale_timestamp) │
└──────────────────┴────────────────┴──────────┴─────────────────┴───────────────┴───────────────────────────────────────────────────────────────────────────────────────────────────┘
Read 0 B across 0 files from R2
On average, 0 B / s
```
To learn more about the new aggregation capabilities and schema discovery commands, check out the [SQL reference](https://developers.cloudflare.com/r2-sql/sql-reference/). If you're new to R2 SQL, visit our [getting started guide](https://developers.cloudflare.com/r2-sql/get-started/) to begin querying your data.
Dec 11, 2025
1. ### [SentinelOne as Logpush destination](https://developers.cloudflare.com/changelog/2025-12-11-sentinelone-destination/)
[Logs](https://developers.cloudflare.com/logs/)
Cloudflare Logpush now supports **SentinelOne** as a native destination.
Logs from Cloudflare can be sent to [SentinelOne AI SIEM](https://www.sentinelone.com/) via [Logpush](https://developers.cloudflare.com/logs/logpush/). The destination can be configured through the Logpush UI in the Cloudflare dashboard or by using the [Logpush API](https://developers.cloudflare.com/api/resources/logpush/subresources/jobs/).
For more information, refer to the [Destination Configuration](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/sentinelone/) documentation.
Dec 10, 2025
1. ### [Pay Per Crawl (Private beta) - Discovery API, custom pricing, and advanced configuration](https://developers.cloudflare.com/changelog/2025-12-10-pay-per-crawl-enhancements/)
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
Pay Per Crawl is introducing enhancements for both AI crawler operators and site owners, focusing on programmatic discovery, flexible pricing models, and granular configuration control.
#### For AI crawler operators
#### Discovery API
A new authenticated API endpoint allows verified crawlers to programmatically discover domains participating in Pay Per Crawl. Crawlers can use this to build optimized crawl queues, cache domain lists, and identify new participating sites. This eliminates the need to discover payable content through trial requests.
The API endpoint is `GET https://crawlers-api.ai-audit.cfdata.org/charged_zones` and requires Web Bot Auth authentication. Refer to [Discover payable content](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/discover-payable-content/) for authentication steps, request parameters, and response schema.
#### Payment header signature requirement
Payment headers (`crawler-exact-price` or `crawler-max-price`) must now be included in the Web Bot Auth `signature-input` header components. This security enhancement prevents payment header tampering, ensures authenticated payment intent, validates crawler identity with payment commitment, and protects against replay attacks with modified pricing. Crawlers must add their payment header to the list of signed components when [constructing the signature-input header](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/#22-sign-your-request-with-web-bot-auth).
#### New `crawler-error` header
Pay Per Crawl error responses now include a new `crawler-error` header with 11 specific [error codes](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/#error-code-reference) for programmatic handling. Error response bodies remain unchanged for compatibility. These codes enable robust error handling, automated retry logic, and accurate spending tracking.
#### For site owners
#### Configure free pages
Site owners can now offer free access to specific pages like homepages, navigation, or discovery pages while charging for other content. Create a [Configuration Rule](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-site-owner/advanced-configuration/#disable-pay-per-crawl-by-uri-pattern) in **Rules** > **Configuration Rules**, set your URI pattern using wildcard, exact, or prefix matching on the **URI Full** field, and enable the **Disable Pay Per Crawl** setting. When disabled for a URI pattern, crawler requests pass through without blocking or charging.
Some paths are always free to crawl. These paths are: `/robots.txt`, `/sitemap.xml`, `/security.txt`, `/.well-known/security.txt`, `/crawlers.json`.
#### Get started
**AI crawler operators**: [Discover payable content](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/discover-payable-content/) | [Crawl pages](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/)
**Site owners**: [Advanced configuration](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-site-owner/advanced-configuration/)
Dec 05, 2025
1. ### [Terraform v5.14.0 now available](https://developers.cloudflare.com/changelog/2025-12-05-terraform-v5140-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new Terraform v5 Provider. We are aware of the high number of issues reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) to ensure its stability and reliability, including the v5.14 release. We have also pivoted from an [issue-to-issue approach to a resource-per-resource approach](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) - we will be focusing on specific resources to not only stabilize the resource but also ensure it is migration-friendly for those migrating from v4 to v5.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes bug fixes, the stabilization of even more popular resources, and more.
#### Deprecation notice
Resource affected: `api_shield_discovery_operation`
Cloudflare continuously discovers and updates API endpoints and web assets of your web applications. To improve the maintainability of these dynamic resources, we are working on reducing the need to actively engage with discovered operations.
The corresponding public API endpoint of [discovered operations](https://developers.cloudflare.com/api/resources/api_gateway/subresources/discovery/subresources/operations/) is not affected and will continue to be supported.
#### Features
* **pages\_project**: Add v4 -> v5 migration tests ([#6506](https://github.com/cloudflare/terraform-provider-cloudflare/pull/6506))
#### Bug fixes
* **account\_members**: Makes member policies a set ([#6488](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6488))
* **pages\_project**: Ensures non empty refresh plans ([#6515](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6515))
* **R2**: Improves sweeper ([#6512](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6512))
* **workers\_kv**: Ignores value import state for verify ([#6521](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6521))
* **workers\_script**: No longer treats the migrations attribute as WriteOnly ([#6489](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6489))
* **workers\_script**: Resolves resource drift when worker has unmanaged secret ([#6504](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6504))
* **zero\_trust\_device\_posture\_rule**: Preserves input.version and other fields ([#6500](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6500)) and ([#6503](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6503))
* **zero\_trust\_dlp\_custom\_profile**: Adds sweepers for `dlp_custom_profile`
* **zone\_subscription|account\_subscription**: Adds `partners_ent` as valid enum for `rate_plan.id` ([#6505](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6505))
* **zone**: Ensures datasource model schema parity ([#6487](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6487))
* **subscription**: Updates import signature to accept account\_id/subscription\_id to import account subscription ([#6510](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6510))
#### Upgrade to newer version
We suggest waiting to migrate to v5 while we work on stabilization. This helps with avoiding any blocking issues while the Terraform resources are actively being [stabilized](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237). We will be releasing a new migration tool in March 2026 to help support v4 to v5 transitions for our most popular resources.
#### For more information
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Dec 04, 2025
1. ### [Connect to remote databases during local development with wrangler dev](https://developers.cloudflare.com/changelog/2025-12-04-hyperdrive-remote-database-local-dev/)
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
You can now connect directly to remote databases and databases requiring TLS with `wrangler dev`. This lets you run your Worker code locally while connecting to remote databases, without needing to use `wrangler dev --remote`.
The `localConnectionString` field and `CLOUDFLARE_HYPERDRIVE_LOCAL_CONNECTION_STRING_` environment variable can be used to configure the connection string used by `wrangler dev`.
```jsonc
{
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "your-hyperdrive-id",
"localConnectionString": "postgres://user:password@remote-host.example.com:5432/database?sslmode=require"
}
]
}
```
Learn more about [local development with Hyperdrive](https://developers.cloudflare.com/hyperdrive/configuration/local-development/).
Dec 03, 2025
1. ### [Reclassifications to Submissions](https://developers.cloudflare.com/changelog/2025-12-03-submission-terminology-update/)
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
We have updated the terminology “Reclassify” and “Reclassifications” to “Submit” and “Submissions” respectively. This update more accurately reflects the outcome of providing these items to Cloudflare.
Submissions are leveraged to tune future variants of campaigns. To respect data sanctity, providing a submission does not change the original disposition of the emails submitted.
This applies to all Email Security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
Nov 26, 2025
1. ### [Agents SDK v0.2.24 with resumable streaming, MCP improvements, and schedule fixes](https://developers.cloudflare.com/changelog/2025-11-26-agents-resumable-streaming/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
The latest release of [@cloudflare/agents](https://github.com/cloudflare/agents) brings resumable streaming, significant MCP client improvements, and critical fixes for schedules and Durable Object lifecycle management.
#### Resumable streaming
`AIChatAgent` now supports resumable streaming, allowing clients to reconnect and continue receiving streamed responses without losing data. This is useful for:
* Long-running AI responses
* Users on unreliable networks
* Users switching between devices mid-conversation
* Background tasks where users navigate away and return
* Real-time collaboration where multiple clients need to stay in sync
Streams are maintained across page refreshes, broken connections, and syncing across open tabs and devices.
#### Other improvements
* Default JSON schema validator added to MCP client
* [Schedules](https://developers.cloudflare.com/agents/api-reference/schedule-tasks/) can now safely destroy the agent
#### MCP client API improvements
The `MCPClientManager` API has been redesigned for better clarity and control:
* **New `registerServer()` method**: Register MCP servers without immediately connecting
* **New `connectToServer()` method**: Establish connections to registered servers
* **Improved reconnect logic**: `restoreConnectionsFromStorage()` now properly handles failed connections
```ts
// Register a server to Agent
const { id } = await this.mcp.registerServer({
name: "my-server",
url: "https://my-mcp-server.example.com",
});
// Connect when ready
await this.mcp.connectToServer(id);
// Discover tools, prompts and resources
await this.mcp.discoverIfConnected(id);
```
The SDK now includes a formalized `MCPConnectionState` enum with states: `idle`, `connecting`, `authenticating`, `connected`, `discovering`, and `ready`.
#### Enhanced MCP discovery
MCP discovery fetches the available tools, prompts, and resources from an MCP server so your agent knows what capabilities are available. The `MCPClientConnection` class now includes a dedicated `discover()` method with improved reliability:
* Supports cancellation via AbortController
* Configurable timeout (default 15s)
* Discovery failures now throw errors immediately instead of silently continuing
#### Bug fixes
* Fixed a bug where [schedules](https://developers.cloudflare.com/agents/api-reference/schedule-tasks/) meant to fire immediately with this.schedule(0, ...) or `this.schedule(new Date(), ...)` would not fire
* Fixed an issue where schedules that took longer than 30 seconds would occasionally time out
* Fixed SSE transport now properly forwards session IDs and request headers
* Fixed AI SDK stream events convertion to UIMessageStreamPart
#### Upgrade
To update to the latest version:
```sh
npm i agents@latest
```
Nov 25, 2025
1. ### [Audit Logs for Cache Purge Events](https://developers.cloudflare.com/changelog/2025-11-25-audit-logs-for-cache-purge-events/)
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now review detailed audit logs for cache purge events, giving you visibility into what purge requests were sent, what they contained, and by whom. Audit your purge requests via the Dashboard or API for all purge methods:
* Purge everything
* List of prefixes
* List of tags
* List of hosts
* List of files
#### Example
The detailed audit payload is visible within the Cloudflare Dashboard (under **Manage Account** > **Audit Logs**) and via the API. Below is an example of the Audit Logs v2 payload structure:
```json
{
"action": {
"result": "success",
"type": "create"
},
"actor": {
"id": "1234567890abcdef",
"email": "user@example.com",
"type": "user"
},
"resource": {
"product": "purge_cache",
"request": {
"files": [
"https://example.com/images/logo.png",
"https://example.com/css/styles.css"
]
}
},
"zone": {
"id": "023e105f4ecef8ad9ca31a8372d0c353",
"name": "example.com"
}
}
```
#### Get started
To get started, refer to the [Audit Logs documentation](https://developers.cloudflare.com/fundamentals/account/account-security/audit-logs/).
Nov 25, 2025
1. ### [Launching FLUX.2 \[dev\] on Workers AI](https://developers.cloudflare.com/changelog/2025-11-25-flux-2-dev-workers-ai/)
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We've partnered with Black Forest Labs (BFL) to bring their latest FLUX.2 \[dev] model to Workers AI! This model excels in generating high-fidelity images with physical world grounding, multi-language support, and digital asset creation. You can also create specific super images with granular controls like JSON prompting.
Read the [BFL blog](https://bfl.ai/flux2) to learn more about the model itself. Read our [Cloudflare blog](https://blog.cloudflare.com/flux-2-workers-ai) to see the model in action, or try it out yourself on our [multi modal playground](https://multi-modal.ai.cloudflare.com/).
Pricing documentation is available on the [model page](https://developers.cloudflare.com/workers-ai/models/flux-2-dev/) or [pricing page](https://developers.cloudflare.com/workers-ai/platform/pricing/). Note, we expect to drop pricing in the next few days after iterating on the model performance.
#### Workers AI Platform specifics
The model hosted on Workers AI is able to support up to 4 image inputs (512x512 per input image). Note, this image model is one of the most powerful in the catalog and is expected to be slower than the other image models we currently support. One catch to look out for is that this model takes multipart form data inputs, even if you just have a prompt.
With the REST API, the multipart form data input looks like this:
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-dev' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=a sunset at the alps' \
--form steps=25
--form width=1024
--form height=1024
```
With the Workers AI binding, you can use it as such:
```javascript
const form = new FormData();
form.append('prompt', 'a sunset with a dog');
form.append('width', '1024');
form.append('height', '1024');
//this dummy request is temporary hack
//we're pushing a change to address this soon
const formRequest = new Request('http://dummy', {
method: 'POST',
body: form
});
const formStream = formRequest.body;
const formContentType = formRequest.headers.get('content-type') || 'multipart/form-data';
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-dev", {
multipart: {
body: formStream,
contentType: formContentType
}
});
```
The parameters you can send to the model are detailed here:
JSON Schema for Model
**Required Parameters**
* `prompt` (string) - Text description of the image to generate
**Optional Parameters**
* `input_image_0` (string) - Binary image
* `input_image_1` (string) - Binary image
* `input_image_2` (string) - Binary image
* `input_image_3` (string) - Binary image
* `steps` (integer) - Number of inference steps. Higher values may improve quality but increase generation time
* `guidance` (float) - Guidance scale for generation. Higher values follow the prompt more closely
* `width` (integer) - Width of the image, default `1024` Range: 256-1920
* `height` (integer) - Height of the image, default `768` Range: 256-1920
* `seed` (integer) - Seed for reproducibility
````plaintext
## Multi-Reference Images
The FLUX.2 model is great at generating images based on reference images. You can use this feature to apply the style of one image to another, add a new character to an image, or iterate on past generate images. You would use it with the same multipart form data structure, with the input images in binary.
For the prompt, you can reference the images based on the index, like `take the subject of image 1 and style it like image 0` or even use natural language like `place the dog beside the woman`.
Note: you have to name the input parameter as `input_image_0`, `input_image_1`, `input_image_2` for it to work correctly. All input images must be smaller than 512x512.
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-dev' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=take the subject of image 1 and style it like image 0' \
--form input_image_0=@/Users/johndoe/Desktop/icedoutkeanu.png \
--form input_image_1=@/Users/johndoe/Desktop/me.png \
--form steps=25
--form width=1024
--form height=1024
````
Through Workers AI Binding:
```javascript
//helper function to convert ReadableStream to Blob
async function streamToBlob(stream: ReadableStream, contentType: string): Promise {
const reader = stream.getReader();
const chunks = [];
while (true) {
const { done, value } = await reader.read();
if (done) break;
chunks.push(value);
}
return new Blob(chunks, { type: contentType });
}
const image0 = await fetch("http://image-url");
const image1 = await fetch("http://image-url");
const form = new FormData();
const image_blob0 = await streamToBlob(image0.body, "image/png");
const image_blob1 = await streamToBlob(image1.body, "image/png");
form.append('input_image_0', image_blob0)
form.append('input_image_1', image_blob1)
form.append('prompt', 'take the subject of image 1and style it like image 0')
//this dummy request is temporary hack
//we're pushing a change to address this soon
const formRequest = new Request('http://dummy', {
method: 'POST',
body: form
});
const formStream = formRequest.body;
const formContentType = formRequest.headers.get('content-type') || 'multipart/form-data';
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-dev", {
multipart: {
body: form,
contentType: "multipart/form-data"
}
})
```
#### JSON Prompting
The model supports prompting in JSON to get more granular control over images. You would pass the JSON as the value of the 'prompt' field in the multipart form data. See the JSON schema below on the base parameters you can pass to the model.
JSON Prompting Schema
```json
{
"type": "object",
"properties": {
"scene": {
"type": "string",
"description": "Overall scene setting or location"
},
"subjects": {
"type": "array",
"items": {
"type": "object",
"properties": {
"type": {
"type": "string",
"description": "Type of subject (e.g., desert nomad, blacksmith, DJ, falcon)"
},
"description": {
"type": "string",
"description": "Physical attributes, clothing, accessories"
},
"pose": {
"type": "string",
"description": "Action or stance"
},
"position": {
"type": "string",
"enum": ["foreground", "midground", "background"],
"description": "Depth placement in scene"
}
},
"required": ["type", "description", "pose", "position"]
}
},
"style": {
"type": "string",
"description": "Artistic rendering style (e.g., digital painting, photorealistic, pixel art, noir sci-fi, lifestyle photo, wabi-sabi photo)"
},
"color_palette": {
"type": "array",
"items": { "type": "string" },
"minItems": 3,
"maxItems": 3,
"description": "Exactly 3 main colors for the scene (e.g., ['navy', 'neon yellow', 'magenta'])"
},
"lighting": {
"type": "string",
"description": "Lighting condition and direction (e.g., fog-filtered sun, moonlight with star glints, dappled sunlight)"
},
"mood": {
"type": "string",
"description": "Emotional atmosphere (e.g., harsh and determined, playful and modern, peaceful and dreamy)"
},
"background": {
"type": "string",
"description": "Background environment details"
},
"composition": {
"type": "string",
"enum": [
"rule of thirds",
"circular arrangement",
"framed by foreground",
"minimalist negative space",
"S-curve",
"vanishing point center",
"dynamic off-center",
"leading leads",
"golden spiral",
"diagonal energy",
"strong verticals",
"triangular arrangement"
],
"description": "Compositional technique"
},
"camera": {
"type": "object",
"properties": {
"angle": {
"type": "string",
"enum": ["eye level", "low angle", "slightly low", "bird's-eye", "worm's-eye", "over-the-shoulder", "isometric"],
"description": "Camera perspective"
},
"distance": {
"type": "string",
"enum": ["close-up", "medium close-up", "medium shot", "medium wide", "wide shot", "extreme wide"],
"description": "Framing distance"
},
"focus": {
"type": "string",
"enum": ["deep focus", "macro focus", "selective focus", "sharp on subject", "soft background"],
"description": "Focus type"
},
"lens": {
"type": "string",
"enum": ["14mm", "24mm", "35mm", "50mm", "70mm", "85mm"],
"description": "Focal length (wide to telephoto)"
},
"f-number": {
"type": "string",
"description": "Aperture (e.g., f/2.8, the smaller the number the more blurry the background)"
},
"ISO": {
"type": "number",
"description": "Light sensitivity value (comfortable range between 100 & 6400, lower = less sensitivity)"
}
}
},
"effects": {
"type": "array",
"items": { "type": "string" },
"description": "Post-processing effects (e.g., 'lens flare small', 'subtle film grain', 'soft bloom', 'god rays', 'chromatic aberration mild')"
}
},
"required": ["scene", "subjects"]
}
```
#### Other features to try
* The model also supports the most common latin and non-latin character languages
* You can prompt the model with specific hex codes like `#2ECC71`
* Try creating digital assets like landing pages, comic strips, infographics too!
Nov 24, 2025
1. ### [Cloud Services Observability in Cloudflare Radar](https://developers.cloudflare.com/changelog/2025-11-24-radar-cloud-observability/)
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) introduces HTTP Origins insights, providing visibility into the status of traffic between Cloudflare's global network and cloud-based origin infrastructure.
The new [`Origins`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/) API provides provides the following endpoints:
* [`/origins`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/list/) - Lists all origins (cloud providers and associated regions).
* [`/origins/{origin}`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/get/) - Retrieves information about a specific origin (cloud provider).
* [`/origins/timeseries`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/timeseries/) - Retrieves normalized time series data for a specific origin, including the following metrics:
* `REQUESTS`: Number of requests
* `CONNECTION_FAILURES`: Number of connection failures
* `RESPONSE_HEADER_RECEIVE_DURATION`: Duration of the response header receive
* `TCP_HANDSHAKE_DURATION`: Duration of the TCP handshake
* `TCP_RTT`: TCP round trip time
* `TLS_HANDSHAKE_DURATION`: Duration of the TLS handshake
* [`/origins/summary`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/summary/) - Retrieves HTTP requests to origins summarized by a dimension.
* [`/origins/timeseries_groups`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/timeseries_groups/) - Retrieves timeseries data for HTTP requests to origins grouped by a dimension.
The following dimensions are available for the `summary` and `timeseries_groups` endpoints:
* `region`: Origin region
* `success_rate`: Success rate of requests (2XX versus 5XX response codes)
* `percentile`: Percentiles of metrics listed above
Additionally, the [`Annotations`](https://developers.cloudflare.com/api/resources/radar/subresources/annotations/) and [`Traffic Anomalies`](https://developers.cloudflare.com/api/resources/radar/subresources/traffic_anomalies/) APIs have been extended to support origin outages and anomalies, enabling automated detection and alerting for origin infrastructure issues.
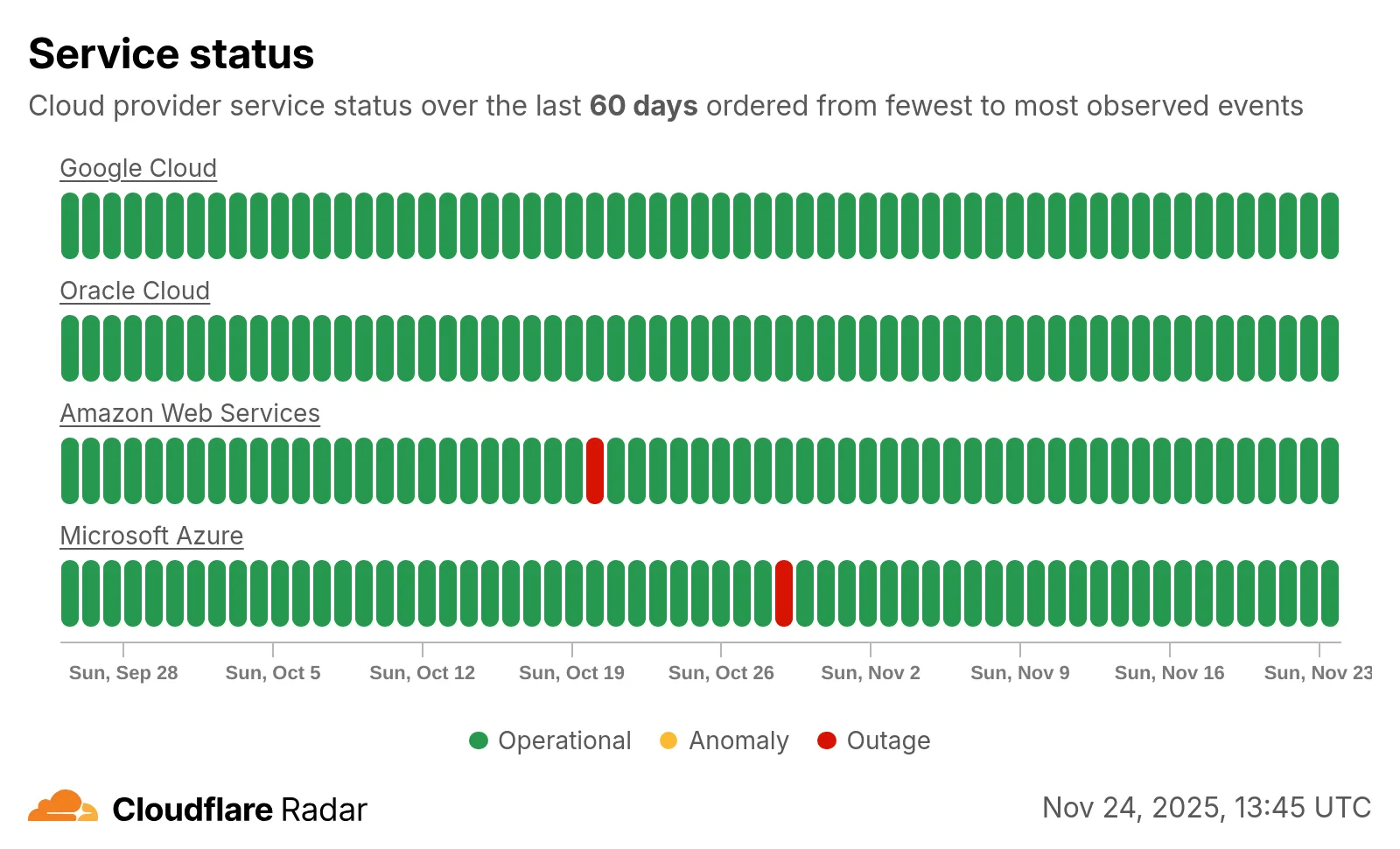
Check out the [new Radar page](https://radar.cloudflare.com/cloud-observatory).
Nov 21, 2025
1. ### [Mount R2 buckets in Containers](https://developers.cloudflare.com/changelog/2025-11-21-fuse-support-in-containers/)
[Containers ](https://developers.cloudflare.com/containers/)[R2](https://developers.cloudflare.com/r2/)
[Containers](https://developers.cloudflare.com/containers/) now support mounting R2 buckets as FUSE (Filesystem in Userspace) volumes, allowing applications to interact with [R2](https://developers.cloudflare.com/r2/) using standard filesystem operations.
Common use cases include:
* Bootstrapping containers with datasets, models, or dependencies for [sandboxes](https://developers.cloudflare.com/sandbox/) and [agent](https://developers.cloudflare.com/agents/) environments
* Persisting user configuration or application state without managing downloads
* Accessing large static files without bloating container images or downloading at startup
FUSE adapters like [tigrisfs](https://github.com/tigrisdata/tigrisfs), [s3fs](https://github.com/s3fs-fuse/s3fs-fuse), and [gcsfuse](https://github.com/GoogleCloudPlatform/gcsfuse) can be installed in your container image and configured to mount buckets at startup.
```dockerfile
FROM alpine:3.20
# Install FUSE and dependencies
RUN apk update && \
apk add --no-cache ca-certificates fuse curl bash
# Install tigrisfs
RUN ARCH=$(uname -m) && \
if [ "$ARCH" = "x86_64" ]; then ARCH="amd64"; fi && \
if [ "$ARCH" = "aarch64" ]; then ARCH="arm64"; fi && \
VERSION=$(curl -s https://api.github.com/repos/tigrisdata/tigrisfs/releases/latest | grep -o '"tag_name": "[^"]*' | cut -d'"' -f4) && \
curl -L "https://github.com/tigrisdata/tigrisfs/releases/download/${VERSION}/tigrisfs_${VERSION#v}_linux_${ARCH}.tar.gz" -o /tmp/tigrisfs.tar.gz && \
tar -xzf /tmp/tigrisfs.tar.gz -C /usr/local/bin/ && \
rm /tmp/tigrisfs.tar.gz && \
chmod +x /usr/local/bin/tigrisfs
# Create startup script that mounts bucket
RUN printf '#!/bin/sh\n\
set -e\n\
mkdir -p /mnt/r2\n\
R2_ENDPOINT="https://${R2_ACCOUNT_ID}.r2.cloudflarestorage.com"\n\
/usr/local/bin/tigrisfs --endpoint "${R2_ENDPOINT}" -f "${BUCKET_NAME}" /mnt/r2 &\n\
sleep 3\n\
ls -lah /mnt/r2\n\
' > /startup.sh && chmod +x /startup.sh
CMD ["/startup.sh"]
```
See the [Mount R2 buckets with FUSE](https://developers.cloudflare.com/containers/examples/r2-fuse-mount/) example for a complete guide on mounting R2 buckets and/or other S3-compatible storage buckets within your containers.
Nov 21, 2025
1. ### [New CPU Pricing for Containers and Sandboxes](https://developers.cloudflare.com/changelog/2025-11-21-new-cpu-pricing/)
[Containers](https://developers.cloudflare.com/containers/)
[Containers](https://developers.cloudflare.com/containers/) and [Sandboxes](https://developers.cloudflare.com/sandbox/) pricing for CPU time is now based on active usage only, instead of provisioned resources.
This means that you now pay less for Containers and Sandboxes.
#### An Example Before and After
Imagine running the `standard-2` instance type for one hour, which can use up to 1 vCPU, but on average you use only 20% of your CPU capacity.
CPU-time is priced at *$0.00002 per vCPU-second*.
Previously, you would be charged for the CPU allocated to the instance multiplied by the time it was active, in this case 1 hour.
CPU cost would have been: **$0.072** — 1 vCPU \* 3600 seconds \* $0.00002
Now, since you are only using 20% of your CPU capacity, your CPU cost is cut to 20% of the previous amount.
CPU cost is now: **$0.0144** — 1 vCPU \* 3600 seconds \* $0.00002 \* 20% utilization
This can significantly reduce costs for Containers and Sandboxes.
Note
Memory cost and disk pricing remain unchanged, and is still calculated based on *provisioned* resources.
See the documentation to learn more about [Containers](https://developers.cloudflare.com/containers/get-started/), [Sandboxes](https://developers.cloudflare.com/sandbox/), and [associated pricing](https://developers.cloudflare.com/containers/pricing).
Nov 21, 2025
1. ### [Threat insights are now available in the Threat Events platform](https://developers.cloudflare.com/changelog/2025-11-21-threat-events-now-show-events-insights/)
[Security Center](https://developers.cloudflare.com/security-center/)
The threat events platform now has threat insights available for some relevant parent events. Threat intelligence analyst users can access these insights for their threat hunting activity. Insights are also highlighted in the Cloudflare dashboard by a small `lightning icon` and the insights can refer to multiple, connected events, potentially part of the same attack or campaign and associated with the same threat actor.
For more information, refer to [Analyze threat events](https://developers.cloudflare.com/security-center/cloudforce-one/#analyze-threat-events).
Nov 20, 2025
1. ### [Terraform v5.13.0 now available](https://developers.cloudflare.com/changelog/2025-11-20-terraform-v5130-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new Terraform v5 Provider. We are aware of the high number of issues reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) to ensure its stability and reliability, including the v5.13 release. We have also pivoted from an [issue-to-issue approach to a resource-per-resource approach](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) - we will be focusing on specific resources to not only stabilize the resource but also ensure it is migration-friendly for those migrating from v4 to v5.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes new features, new resources and data sources, bug fixes, updates to our Developer Documentation, and more.
#### Breaking Change
Please be aware that there are breaking changes for the `cloudflare_api_token` and `cloudflare_account_token` resources. These changes eliminate configuration drift caused by policy ordering differences in the Cloudflare API.
For more specific information about the changes or the actions required, please see the [detailed Repository changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.13.0).
#### Features
* **New resources and data sources added**
* cloudflare\_connectivity\_directory
* cloudflare\_sso\_connector
* cloudflare\_universal\_ssl\_setting
* **api\_token+account\_tokens:** state upgrader and schema bump ([#6472](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6472))
* **docs:** make docs explicit when a resource does not have import support
* **magic\_transit\_connector:** support self-serve license key ([#6398](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6398))
* **worker\_version:** add content\_base64 support
* **worker\_version:** boolean support for run\_worker\_first ([#6407](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6407))
* **workers\_script\_subdomains:** add import support ([#6375](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6375))
* **zero\_trust\_access\_application:** add proxy\_endpoint for ZT Access Application ([#6453](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6453))
* **zero\_trust\_dlp\_predefined\_profile:** Switch DLP Predefined Profile endpoints, introduce enabled\_entries attribut
#### Bug Fixes
* **account\_token:** token policy order and nested resources ([#6440](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6440))
* allow r2\_bucket\_event\_notification to be applied twice without failing ([#6419](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6419))
* **cloudflare\_worker+cloudflare\_worker\_version:** import for the resources ([#6357](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6357))
* **dns\_record:** inconsistent apply error ([#6452](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6452))
* **pages\_domain:** resource tests ([#6338](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6338))
* **pages\_project:** unintended resource state drift ([#6377](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6377))
* **queue\_consumer:** id population ([#6181](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6181))
* **workers\_kv:** multipart request ([#6367](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6367))
* **workers\_kv:** updating workers metadata attribute to be read from endpoint ([#6386](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6386))
* **workers\_script\_subdomain:** add note to cloudflare\_workers\_script\_subdomain about redundancy with cloudflare\_worker ([#6383](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6383))
* **workers\_script:** allow config.run\_worker\_first to accept list input
* **zero\_trust\_device\_custom\_profile\_local\_domain\_fallback:** drift issues ([#6365](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6365))
* **zero\_trust\_device\_custom\_profile:** resolve drift issues ([#6364](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6364))
* **zero\_trust\_dex\_test:** correct configurability for 'targeted' attribute to fix drift
* **zero\_trust\_tunnel\_cloudflared\_config:** remove warp\_routing from cloudflared\_config ([#6471](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6471))
#### Upgrading
We suggest holding off on migration to v5 while we work on stabilization. This help will you avoid any blocking issues while the Terraform resources are actively being stabilized. We will be releasing a new migration tool in March 2026 to help support v4 to v5 transitions for our most popular resources.
#### For more info
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Nov 19, 2025
1. ### [AI Search support for crawling login protected website content](https://developers.cloudflare.com/changelog/2025-11-19-add-extra-headers-for-website-crawling/)
[AI Search](https://developers.cloudflare.com/ai-search/)
[AI Search](https://developers.cloudflare.com/ai-search/) now supports [custom HTTP headers](https://developers.cloudflare.com/ai-search/configuration/data-source/website/#access-protected-content) for website crawling, solving a common problem where valuable content behind authentication or access controls could not be indexed.
Previously, AI Search could only crawl publicly accessible pages, leaving knowledge bases, documentation, and other protected content out of your search results. With custom headers support, you can now include authentication credentials that allow the crawler to access this protected content.
This is particularly useful for indexing content like:
* **Internal documentation** behind corporate login systems
* **Premium content** that requires users to provide access to unlock
* **Sites protected by Cloudflare Access** using service tokens
To add custom headers when creating an AI Search instance, select **Parse options**. In the **Extra headers** section, you can add up to five custom headers per Website data source.

For example, to crawl a site protected by [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/), you can add service token credentials as custom headers:
```plaintext
CF-Access-Client-Id: your-token-id.access
CF-Access-Client-Secret: your-token-secret
```
The crawler will automatically include these headers in all requests, allowing it to access protected pages that would otherwise be blocked.
Learn more about [configuring custom headers for website crawling](https://developers.cloudflare.com/ai-search/configuration/data-source/website/#access-protected-content) in AI Search.
Nov 18, 2025
1. ### [Adjustment to Final Disposition Column](https://developers.cloudflare.com/changelog/2025-11-18-temporary-adjustment-to-final-disposition-column/)
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
#### Adjustment to Final Disposition column
#### The **Final Disposition** column in **Submissions** > **Team Submissions** tab is changing for non-Phishguard customers.
#### What's Changing
* Column will be called **Status** instead of **Final Disposition**
* Column status values will now be: **Submitted**, **Accepted** or **Rejected**.
#### Next Steps
We will listen carefully to your feedback and continue to find comprehensive ways to communicate updates on your submissions. Your submissions will continue to be addressed at an even greater rate than before, fuelling faster and more accurate email security improvement.
Nov 17, 2025
1. ### [New Cloudflare One Navigation and Product Experience](https://developers.cloudflare.com/changelog/new-cloudflare-one-navigation-and-product-experience/)
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
The Zero Trust dashboard and navigation is receiving significant and exciting updates. The dashboard is being restructured to better support common tasks and workflows, and various pages have been moved and consolidated.
There is a new guided experience on login detailing the changes, and you can use the Zero Trust dashboard search to find product pages by both their new and old names, as well as your created resources. To replay the guided experience, you can find it in Overview > Get Started.
Notable changes
* Product names have been removed from many top-level navigation items to help bring clarity to what they help you accomplish. For example, you can find Gateway policies under ‘Traffic policies' and CASB findings under ‘Cloud & SaaS findings.'
* You can view all analytics, logs, and real-time monitoring tools from ‘Insights.'
* ‘Networks' better maps the ways that your corporate network interacts with Cloudflare. Some pages like Tunnels, are now a tab rather than a full page as part of these changes. You can find them at Networks > Connectors.
* Settings are now located closer to the tools and resources they impact. For example, this means you'll find your WARP configurations at Team & Resources > Devices.
No changes to our API endpoint structure or to any backend services have been made as part of this effort.
Nov 14, 2025
1. ### [Generate Cloudflare Access SSH certificate authority (CA) directly from the Cloudflare dashboard](https://developers.cloudflare.com/changelog/2025-11-14-ssh-ca-enhancements/)
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
SSH with [Cloudflare Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/) allows you to use short-lived SSH certificates to eliminate SSH key management and reduce security risks associated with lost or stolen keys.
Previously, users had to generate this certificate by using the [Cloudflare API](https://developers.cloudflare.com/api/) directly. With this update, you can now create and manage this certificate in the [Cloudflare One dashboard](https://one.dash.cloudflare.com) from the **Access controls** > **Service credentials** page.
For more details, refer to [Generate a Cloudflare SSH CA](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/#generate-a-cloudflare-ssh-ca).
Nov 14, 2025
1. ### [New SaaS Security weekly digests with API CASB](https://developers.cloudflare.com/changelog/2025-11-14-casb-digest/)
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
You can now stay on top of your SaaS security posture with the new **CASB Weekly Digest** notification. This opt-in email digest is delivered to your inbox every Monday morning and provides a high-level summary of your organization's Cloudflare API CASB findings from the previous week.
This allows security teams and IT administrators to get proactive, at-a-glance visibility into new risks and integration health without having to log in to the dashboard.
To opt in, navigate to **Manage Account** > **Notifications** in the Cloudflare dashboard to configure the **CASB Weekly Digest** alert type.
#### Key capabilities
* **At-a-glance summary** — Review new high/critical findings, most frequent finding types, and new content exposures from the past 7 days.
* **Integration health** — Instantly see the status of all your connected SaaS integrations (Healthy, Unhealthy, or Paused) to spot API connection issues.
* **Proactive alerting** — The digest is sent automatically to all subscribed users every Monday morning.
* **Easy to configure** — Users can opt in by enabling the notification in the Cloudflare dashboard under **Manage Account** > **Notifications**.
#### Learn more
* Configure [notification preferences](https://developers.cloudflare.com/notifications/) in Cloudflare.
The CASB Weekly Digest notification is available to all Cloudflare users today.
Nov 13, 2025
1. ### [Fixed custom SQL date picker inconsistencies](https://developers.cloudflare.com/changelog/2025-11-13-fixed-custom-date/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We've resolved a bug in Log Explorer that caused inconsistencies between the custom SQL date field filters and the date picker dropdown. Previously, users attempting to filter logs based on a custom date field via a SQL query sometimes encountered unexpected results or mismatching dates when using the interactive date picker.
This fix ensures that the custom SQL date field filters now align correctly with the selection made in the date picker dropdown, providing a reliable and predictable filtering experience for your log data. This is particularly important for users creating custom log views based on time-sensitive fields.
Nov 13, 2025
1. ### [Log Explorer adds 14 new datasets](https://developers.cloudflare.com/changelog/2025-11-13-new-datasets/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We've significantly enhanced Log Explorer by adding support for 14 additional Cloudflare product datasets.
This expansion enables Operations and Security Engineers to gain deeper visibility and telemetry across a wider range of Cloudflare services. By integrating these new datasets, users can now access full context to efficiently investigate security incidents, troubleshoot application performance issues, and correlate logged events across different layers (like application and network) within a single interface. This capability is crucial for a complete and cohesive understanding of event flows across your Cloudflare environment.
The newly supported datasets include:
#### Zone Level
* `Dns_logs`
* `Nel_reports`
* `Page_shield_events`
* `Spectrum_events`
* `Zaraz_events`
#### Account Level
* `Audit Logs`
* `Audit_logs_v2`
* `Biso_user_actions`
* `DNS firewall logs`
* `Email_security_alerts`
* `Magic Firewall IDS`
* `Network Analytics`
* `Sinkhole HTTP`
* `ipsec_logs`
Note
`Auditlog` and `Auditlog_v2` datasets require `audit-log.read` permission for querying.
The `biso_user_actions` dataset requires either the `Super Admin` or `ZT PII` role for querying.
#### Example: Correlating logs
You can now use Log Explorer to query and filter with each of these datasets. For example, you can identify an IP address exhibiting suspicious behavior in the `FW_event` logs, and then instantly pivot to the `Network Analytics` logs or `Access` logs to see its network-level traffic profile or if it bypassed a corporate policy.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/) and the [Cloudflare Logs documentation](https://developers.cloudflare.com/logs/).
Nov 12, 2025
1. ### [New BOLA Vulnerability Detection for API Shield](https://developers.cloudflare.com/changelog/2025-11-12-bola-attack-detection/)
[API Shield](https://developers.cloudflare.com/api-shield/)
Now, API Shield automatically searches for and highlights **Broken Object Level Authorization (BOLA) attacks** on managed API endpoints. API Shield will highlight both BOLA enumeration attacks and BOLA pollution attacks, telling you what was attacked, by who, and for how long.
You can find these attacks three different ways: Security Overview, Endpoint details, or Security Analytics. If these attacks are not found on your managed API endpoints, there will not be an overview card or security analytics suspicious activity card.
From the endpoint details, you can select **View attack** to find details about the BOLA attacker’s sessions.
From here, select **View in Analytics** to observe attacker traffic over time for the last seven days.
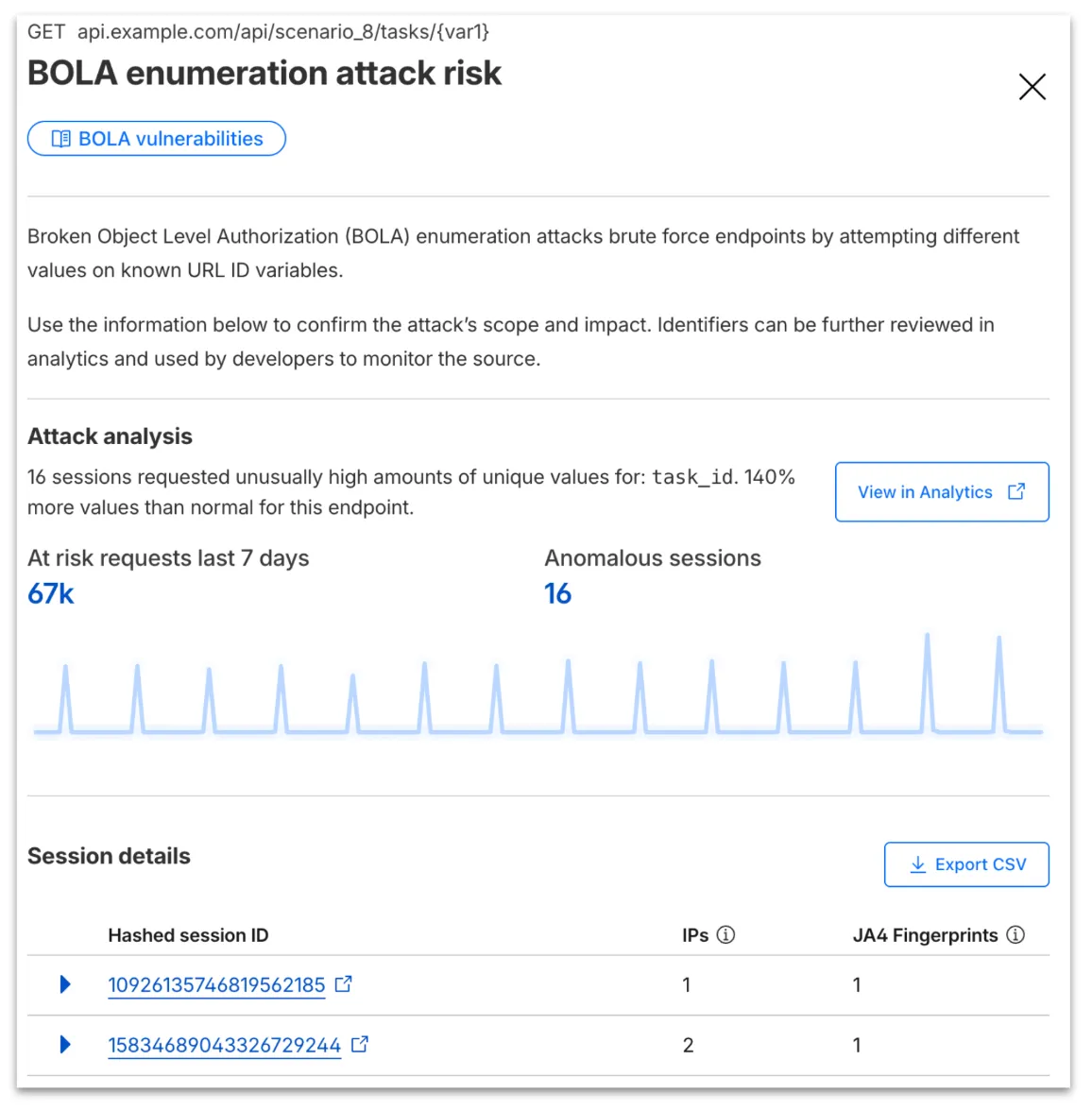
Your search will filter to traffic on that endpoint in the last seven days, along with the malicious session IDs found in the attack. Session IDs are hashed for privacy and will not be found in your origin logs. Refer to IP and JA4 fingerprint to cross-reference behavior at the origin.
At any time, you can also start your investigation into attack traffic from Security Analytics by selecting the suspicious activity card.

We urge you to take all of this client information to your developer team to research the attacker behavior and ensure any broken authorization policies in your API are fixed at the source in your application, preventing further abuse.
In addition, this release marks the end of the beta period for these scans. All Enterprise customers with API Shield subscriptions will see these new attacks if found on their zone.
Nov 12, 2025
1. ### [DEX Logpush jobs](https://developers.cloudflare.com/changelog/2025-11-12-dex-logpush-jobsmdx/)
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into WARP device metrics, connectivity, and network performance across your Cloudflare SASE deployment.
We've released four new WARP and DEX device data sets that can be exported via [Cloudflare Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/). These Logpush data sets can be exported to R2, a cloud bucket, or a SIEM to build a customized logging and analytics experience.
1. [DEX Application Tests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dex_application_tests/)
2. [DEX Device State Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dex_device_state_events/)
3. [WARP Config Changes](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/warp_config_changes/)
4. [WARP Toggle Changes](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/warp_toggle_changes/)
To create a new DEX or WARP Logpush job, customers can go to the account level of the Cloudflare dashboard > Analytics & Logs > Logpush to get started.
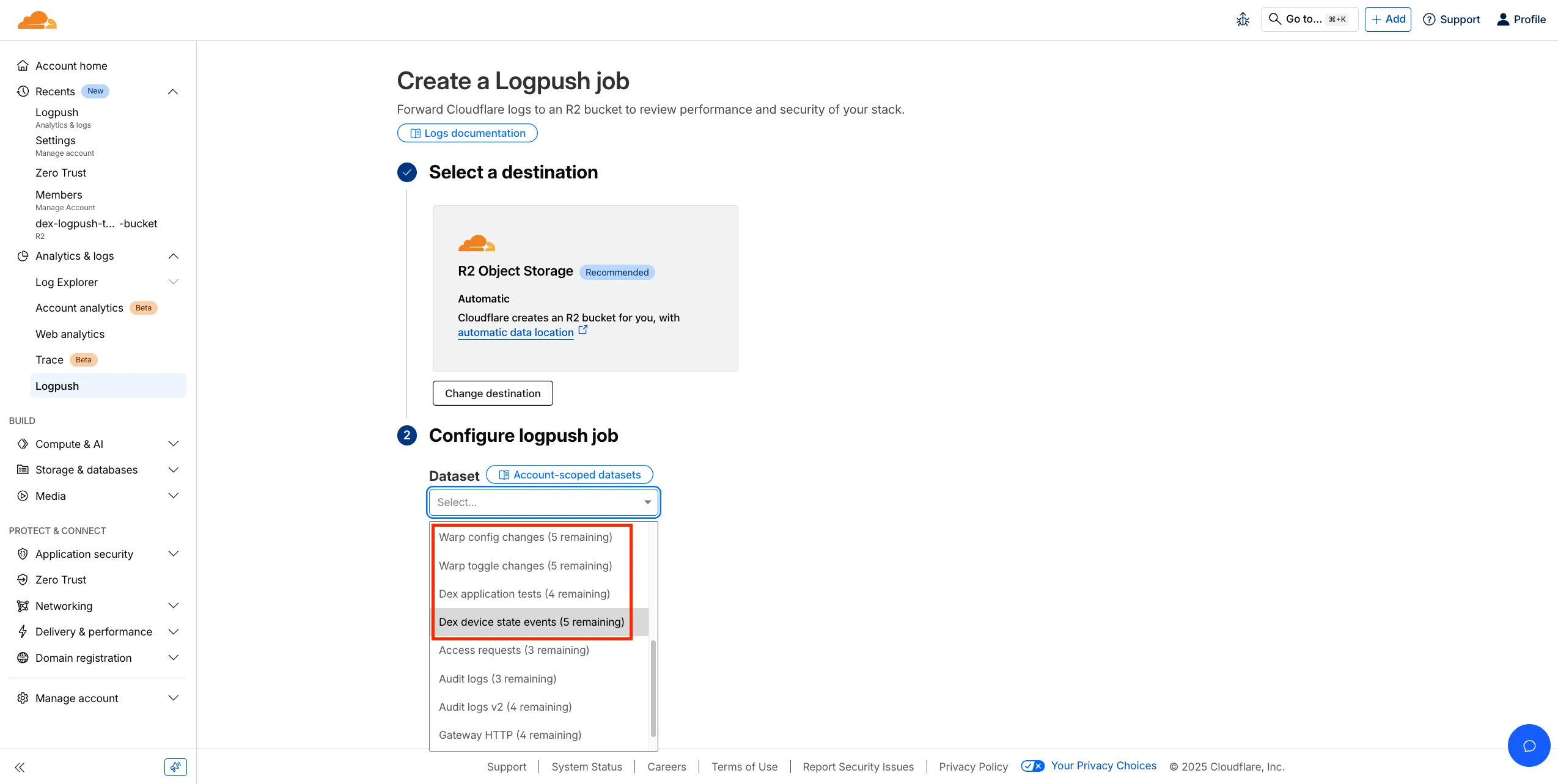
Nov 12, 2025
1. ### [More SQL aggregate, date and time functions available in Workers Analytics Engine](https://developers.cloudflare.com/changelog/2025-11-12-analytics-engine-further-sql-enhancements/)
[Workers Analytics Engine ](https://developers.cloudflare.com/analytics/analytics-engine/)[Workers](https://developers.cloudflare.com/workers/)
You can now perform more powerful queries directly in [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/) with a major expansion of our SQL function library.
Workers Analytics Engine allows you to ingest and store high-cardinality data at scale (such as custom analytics) and query your data through a simple SQL API.
Today, we've expanded Workers Analytics Engine's SQL capabilities with several new functions:
[**New aggregate functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/aggregate-functions/)
* `countIf()` - count the number of rows which satisfy a provided condition
* `sumIf()` - calculate a sum from rows which satisfy a provided condition
* `avgIf()` - calculate an average from rows which satisfy a provided condition
[**New date and time functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/date-time-functions/)
* `toYear()`
* `toMonth()`
* `toDayOfMonth()`
* `toDayOfWeek()`
* `toHour()`
* `toMinute()`
* `toSecond()`
* `toStartOfYear()`
* `toStartOfMonth()`
* `toStartOfWeek()`
* `toStartOfDay()`
* `toStartOfHour()`
* `toStartOfFifteenMinutes()`
* `toStartOfTenMinutes()`
* `toStartOfFiveMinutes()`
* `toStartOfMinute()`
* `today()`
* `toYYYYMM()`
#### Ready to get started?
Whether you're building usage-based billing systems, customer analytics dashboards, or other custom analytics, these functions let you get the most out of your data. [Get started ](https://developers.cloudflare.com/analytics/analytics-engine/get-started/)with Workers Analytics Engine and explore all available functions in our [SQL reference documentation](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/).
Nov 11, 2025
1. ### [cloudflared proxy-dns command will be removed starting February 2, 2026](https://developers.cloudflare.com/changelog/2025-11-11-cloudflared-proxy-dns/)
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
Starting February 2, 2026, the `cloudflared proxy-dns` command will be removed from all new `cloudflared` [releases](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/downloads/).
This change is being made to enhance security and address a potential vulnerability in an underlying DNS library. This vulnerability is specific to the `proxy-dns` command and does not affect any other `cloudflared` features, such as the core [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) service.
The `proxy-dns` command, which runs a client-side [DNS-over-HTTPS (DoH)](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/) proxy, has been an officially undocumented feature for several years. This functionality is fully and securely supported by our actively developed products.
Versions of `cloudflared` released before this date will not be affected and will continue to operate. However, note that our [official support policy](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/downloads/#deprecated-releases) for any `cloudflared` release is one year from its release date.
#### Migration paths
We strongly advise users of this undocumented feature to migrate to one of the following officially supported solutions before February 2, 2026, to continue benefiting from secure [DNS-over-HTTPS](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/).
#### End-user devices
The preferred method for enabling DNS-over-HTTPS on user devices is the [Cloudflare WARP client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/). The WARP client automatically secures and proxies all DNS traffic from your device, integrating it with your organization's [Zero Trust policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) and [posture checks](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/).
#### Servers, routers, and IoT devices
For scenarios where installing a client on every device is not possible (such as servers, routers, or IoT devices), we recommend using the [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/).
Instead of running `cloudflared proxy-dns` on a machine, you can install the WARP Connector on a single Linux host within your private network. This connector will act as a gateway, securely routing all DNS and network traffic from your [entire subnet](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/site-to-internet/) to Cloudflare for [filtering and logging](https://developers.cloudflare.com/cloudflare-one/traffic-policies/).
Nov 11, 2025
1. ### [Resize your custom SQL window in Log Explorer](https://developers.cloudflare.com/changelog/2025-11-11-resize-sql-window/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We're excited to announce a quality-of-life improvement for Log Explorer users. You can now resize the custom SQL query window to accommodate longer and more complex queries.
Previously, if you were writing a long custom SQL query, the fixed-size window required excessive scrolling to view the full query. This update allows you to easily drag the bottom edge of the query window to make it taller. This means you can view your entire custom query at once, improving the efficiency and experience of writing and debugging complex queries.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/).
Nov 11, 2025
1. ### [Logpush Health Dashboards](https://developers.cloudflare.com/changelog/2025-11-11-health-dashboards/)
[Logs](https://developers.cloudflare.com/logs/)
We’re excited to introduce **Logpush Health Dashboards**, giving customers real-time visibility into the status, reliability, and performance of their [Logpush](https://developers.cloudflare.com/logs/logpush/) jobs. Health dashboards make it easier to detect delivery issues, monitor job stability, and track performance across destinations. The dashboards are divided into two sections:
* **Upload Health**: See how much data was successfully uploaded, where drops occurred, and how your jobs are performing overall. This includes data completeness, success rate, and upload volume.
* **Upload Reliability** – Diagnose issues impacting stability, retries, or latency, and monitor key metrics such as retry counts, upload duration, and destination availability.
Health Dashboards can be accessed from the Logpush page in the Cloudflare dashboard at the account or zone level, under the Health tab. For more details, refer to our [**Logpush Health Dashboards**](https://developers.cloudflare.com/logs/logpush/logpush-health) documentation, which includes a comprehensive troubleshooting guide to help interpret and resolve common issues.
Nov 10, 2025
1. ### [Crawler drilldowns with extended actions menu](https://developers.cloudflare.com/changelog/2025-11-10-ai-crawl-control-crawler-info/)
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
AI Crawl Control now supports per-crawler drilldowns with an extended actions menu and status code analytics. Drill down into Metrics, Cloudflare Radar, and Security Analytics, or export crawler data for use in [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/), [Redirect Rules](https://developers.cloudflare.com/rules/url-forwarding/), and robots.txt files.
#### What's new
#### Status code distribution chart
The **Metrics** tab includes a status code distribution chart showing HTTP response codes (2xx, 3xx, 4xx, 5xx) over time. Filter by individual crawler, category, operator, or time range to analyze how specific crawlers interact with your site.

#### Extended actions menu
Each crawler row includes a three-dot menu with per-crawler actions:
* **View Metrics** — Filter the AI Crawl Control Metrics page to the selected crawler.
* **View on Cloudflare Radar** — Access verified crawler details on Cloudflare Radar.
* **Copy User Agent** — Copy user agent strings for use in WAF custom rules, Redirect Rules, or robots.txt files.
* **View in Security Analytics** — Filter Security Analytics by detection IDs (Bot Management customers).
* **Copy Detection ID** — Copy detection IDs for use in WAF custom rules (Bot Management customers).
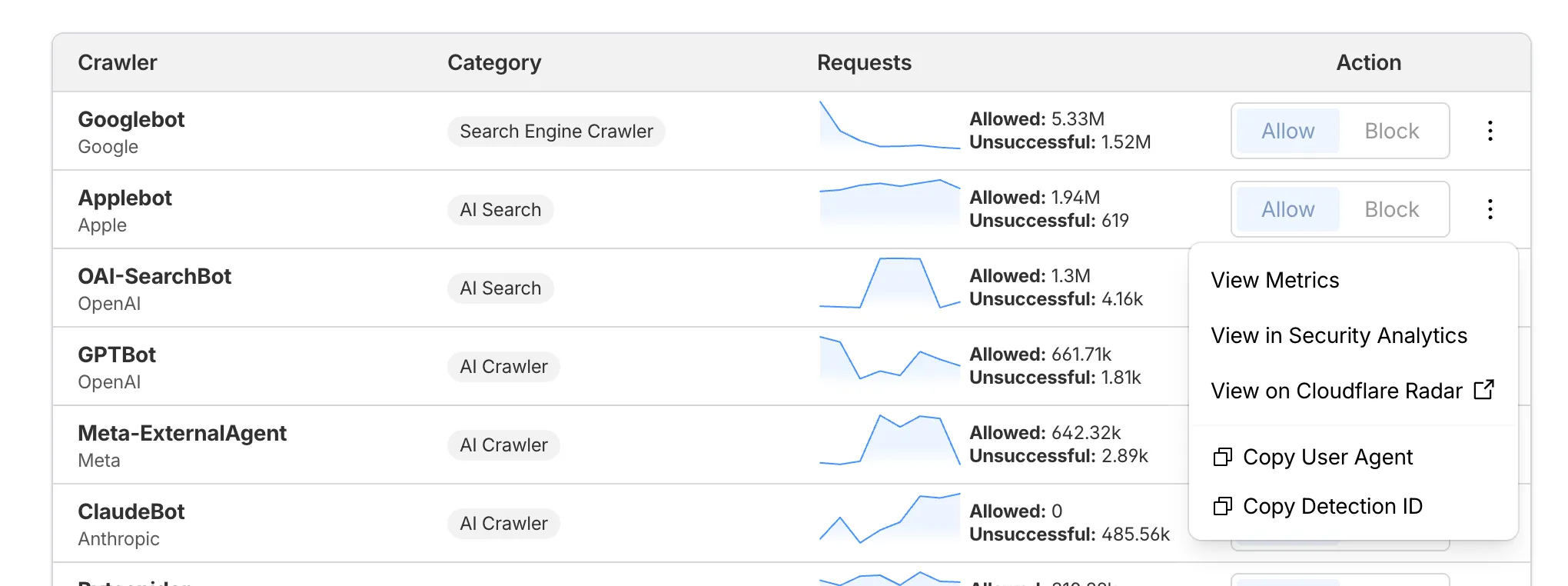
#### Get started
1. Log in to the Cloudflare dashboard, and select your account and domain.
2. Go to **AI Crawl Control** > **Metrics** to access the status code distribution chart.
3. Go to **AI Crawl Control** > **Crawlers** and select the three-dot menu for any crawler to access per-crawler actions.
4. Select multiple crawlers to use bulk copy buttons for user agents or detection IDs.
Learn more about [AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/).
Nov 07, 2025
1. ### [Inspect Cache Keys with Cloudflare Trace](https://developers.cloudflare.com/changelog/2025-11-07-cache-keys-for-cloudflare-trace/)
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now see the exact cache key generated for any request directly in Cloudflare Trace. This visibility helps you troubleshoot cache hits and misses, and verify that your Custom Cache Keys — configured via Cache Rules or Page Rules — are working as intended.
Previously, diagnosing caching behavior required inferring the key from configuration settings. Now, you can confirm that your custom logic for headers, query strings, and device types is correctly applied.
Access Trace via the [dashboard](https://developers.cloudflare.com/rules/trace-request/how-to/#use-trace-in-the-dashboard) or [API](https://developers.cloudflare.com/api/resources/request_tracer/methods/trace/), either manually for ad-hoc debugging or automated as part of your quality-of-service monitoring.
#### Example scenario
If you have a Cache Rule that segments content based on a specific cookie (for example, `user_region`), run a Trace with that cookie present to confirm the `user_region` value appears in the resulting cache key.
The Trace response includes the cache key in the `cache` object:
```json
{
"step_name": "request",
"type": "cache",
"matched": true,
"public_name": "Cache Parameters",
"cache": {
"key": {
"zone_id": "023e105f4ecef8ad9ca31a8372d0c353",
"scheme": "https",
"host": "example.com",
"uri": "/images/hero.jpg"
},
"key_string": "023e105f4ecef8ad9ca31a8372d0c353::::https://example.com/images/hero.jpg:::::"
}
}
```
#### Get started
To learn more, refer to the [Trace documentation](https://developers.cloudflare.com/rules/trace-request/) and our guide on [Custom Cache Keys](https://developers.cloudflare.com/cache/how-to/cache-keys/).
Nov 06, 2025
1. ### [Applications to be remapped to the new categories](https://developers.cloudflare.com/changelog/2025-11-06-applications-recategorised-plan/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
We have previously added new application categories to better reflect their content and improve HTTP traffic management: refer to [Changelog](https://developers.cloudflare.com/cloudflare-one/changelog/gateway/#2025-10-28). While the new categories are live now, we want to ensure you have ample time to review and adjust any existing rules you have configured against old categories. The remapping of existing applications into these new categories will be completed by January 30, 2026. This timeline allows you a dedicated period to:
* Review the new category structure.
* Identify any policies you have that target the older categories.
* Adjust your rules to reference the new, more precise categories before the old mappings change. Once the applications have been fully remapped by January 30, 2026, you might observe some changes in the traffic being mitigated or allowed by your existing policies. We encourage you to use the intervening time to prepare for a smooth transition.
**Applications being remappedd**
| Application Name | Existing Category | New Category |
| - | - | - |
| Google Photos | File Sharing | Photography & Graphic Design |
| Flickr | File Sharing | Photography & Graphic Design |
| ADP | Human Resources | Business |
| Greenhouse | Human Resources | Business |
| myCigna | Human Resources | Health & Fitness |
| UnitedHealthcare | Human Resources | Health & Fitness |
| ZipRecruiter | Human Resources | Business |
| Amazon Business | Human Resources | Business |
| Jobcenter | Human Resources | Business |
| Jobsuche | Human Resources | Business |
| Zenjob | Human Resources | Business |
| DocuSign | Legal | Business |
| Postident | Legal | Business |
| Adobe Creative Cloud | Productivity | Photography & Graphic Design |
| Airtable | Productivity | Development |
| Autodesk Fusion360 | Productivity | IT Management |
| Coursera | Productivity | Education |
| Microsoft Power BI | Productivity | Business |
| Tableau | Productivity | Business |
| Duolingo | Productivity | Education |
| Adobe Reader | Productivity | Business |
| AnpiReport | Productivity | Travel |
| ビズリーチ | Productivity | Business |
| doda (デューダ) | Productivity | Business |
| 求人ボックス | Productivity | Business |
| マイナビ2026 | Productivity | Business |
| Power Apps | Productivity | Business |
| RECRUIT AGENT | Productivity | Business |
| シフトボード | Productivity | Business |
| スタンバイ | Productivity | Business |
| Doctolib | Productivity | Health & Fitness |
| Miro | Productivity | Photography & Graphic Design |
| MyFitnessPal | Productivity | Health & Fitness |
| Sentry Mobile | Productivity | Travel |
| Slido | Productivity | Photography & Graphic Design |
| Arista Networks | Productivity | IT Management |
| Atlassian | Productivity | Business |
| CoderPad | Productivity | Business |
| eAgreements | Productivity | Business |
| Vmware | Productivity | IT Management |
| Vmware Vcenter | Productivity | IT Management |
| AWS Skill Builder | Productivity | Education |
| Microsoft Office 365 (GCC) | Productivity | Business |
| Microsoft Exchange Online (GCC) | Productivity | Business |
| Canva | Sales & Marketing | Photography & Graphic Design |
| Instacart | Shopping | Food & Drink |
| Wawa | Shopping | Food & Drink |
| McDonald's | Shopping | Food & Drink |
| Vrbo | Shopping | Travel |
| American Airlines | Shopping | Travel |
| Booking.com | Shopping | Travel |
| Ticketmaster | Shopping | Entertainment & Events |
| Airbnb | Shopping | Travel |
| DoorDash | Shopping | Food & Drink |
| Expedia | Shopping | Travel |
| EasyPark | Shopping | Travel |
| UEFA Tickets | Shopping | Entertainment & Events |
| DHL Express | Shopping | Business |
| UPS | Shopping | Business |
For more information on creating HTTP policies, refer to [Applications and app types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
Nov 06, 2025
1. ### [Designate WAN link for breakout traffic](https://developers.cloudflare.com/changelog/2025-11-06-connector-designate-wan-link-breakout/)
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Magic WAN Connector now allows you to designate a specific WAN port for breakout traffic, giving you deterministic control over the egress path for latency-sensitive applications.
With this feature, you can:
* Pin breakout traffic for specific applications to a preferred WAN port.
* Ensure critical traffic (such as Zoom or Teams) always uses your fastest or most reliable connection.
* Benefit from automatic failover to standard WAN port priority if the preferred port goes down.
This is useful for organizations with multiple ISP uplinks who need predictable egress behavior for performance-sensitive traffic.
For configuration details, refer to [Designate WAN ports for breakout apps](https://developers.cloudflare.com/magic-wan/configuration/connector/network-options/application-based-policies/breakout-traffic/#designate-wan-ports-for-breakout-apps).
Nov 06, 2025
1. ### [Automatic Return Routing (Beta)](https://developers.cloudflare.com/changelog/2025-11-06-automatic-return-routing-beta/)
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Magic WAN now supports Automatic Return Routing (ARR), allowing customers to configure Magic on-ramps (IPsec/GRE/CNI) to learn the return path for traffic flows without requiring static routes.
Key benefits:
* **Route-less mode**: Static or dynamic routes are optional when using ARR.
* **Overlapping IP space support**: Traffic originating from customer sites can use overlapping private IP ranges.
* **Symmetric routing**: Return traffic is guaranteed to use the same connection as the original on-ramp.
This feature is currently in beta and requires the new Unified Routing mode (beta).
For configuration details, refer to [Configure Automatic Return Routing](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-automatic-return-routing-beta).
Nov 05, 2025
1. ### [D1 can restrict data localization with jurisdictions](https://developers.cloudflare.com/changelog/2025-11-05-d1-jurisdiction/)
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
You can now set a [jurisdiction](https://developers.cloudflare.com/d1/configuration/data-location/) when creating a D1 database to guarantee where your database runs and stores data. Jurisdictions can help you comply with data localization regulations such as GDPR. Supported jurisdictions include `eu` and `fedramp`.
A jurisdiction can only be set at database creation time via wrangler, REST API or the UI and cannot be added/updated after the database already exists.
```sh
npx wrangler@latest d1 create db-with-jurisdiction --jurisdiction eu
```
```plaintext
curl -X POST "https://api.cloudflare.com/client/v4/accounts//d1/database" \
-H "Authorization: Bearer $TOKEN" \
-H "Content-Type: application/json" \
--data '{"name": "db-wth-jurisdiction", "jurisdiction": "eu" }'
```
To learn more, visit D1's data location [documentation](https://developers.cloudflare.com/d1/configuration/data-location/).
Nov 05, 2025
1. ### [Logpush Permission Update for Zero Trust Datasets](https://developers.cloudflare.com/changelog/2025-11-05-logpush-permissions-update/)
[Logs](https://developers.cloudflare.com/logs/)
[Permissions](https://developers.cloudflare.com/logs/logpush/permissions/) for managing Logpush jobs related to [Zero Trust datasets](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/) (Access, Gateway, and DEX) have been updated to improve data security and enforce appropriate access controls.
To view, create, update, or delete Logpush jobs for Zero Trust datasets, users must now have both of the following permissions:
* Logs Edit
* Zero Trust: PII Read
Note
Update your UI, API or Terraform configurations to include the new permissions. Requests to Zero Trust datasets will fail due to insufficient access without the additional permission.
Nov 05, 2025
1. ### [Announcing Workers VPC Services (Beta)](https://developers.cloudflare.com/changelog/2025-09-25-workers-vpc/)
[Workers VPC](https://developers.cloudflare.com/workers-vpc/)
**Workers VPC Services** is now available, enabling your Workers to securely access resources in your private networks, without having to expose them on the public Internet.
#### What's new
* **VPC Services**: Create secure connections to internal APIs, databases, and services using familiar Worker binding syntax
* **Multi-cloud Support**: Connect to resources in private networks in any external cloud (AWS, Azure, GCP, etc.) or on-premise using Cloudflare Tunnels
```js
export default {
async fetch(request, env, ctx) {
// Perform application logic in Workers here
// Sample call to an internal API running on ECS in AWS using the binding
const response = await env.AWS_VPC_ECS_API.fetch("https://internal-host.example.com");
// Additional application logic in Workers
return new Response();
},
};
```
#### Getting started
Set up a Cloudflare Tunnel, create a VPC Service, add service bindings to your Worker, and access private resources securely. [Refer to the documentation](https://developers.cloudflare.com/workers-vpc/) to get started.
Nov 04, 2025
1. ### [Log Explorer now supports query cancellation](https://developers.cloudflare.com/changelog/2025-11-04-query-cancellation/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We're excited to announce that Log Explorer users can now cancel queries that are currently running.
This new feature addresses a common pain point: waiting for a long, unintended, or misconfigured query to complete before you can submit a new, correct one. With query cancellation, you can immediately stop the execution of any undesirable query, allowing you to quickly craft and submit a new query, significantly improving your investigative workflow and productivity within Log Explorer.
Nov 04, 2025
1. ### [Log Explorer now shows query result distribution](https://developers.cloudflare.com/changelog/2025-11-13-query-result-distribution/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We're excited to announce a new feature in Log Explorer that significantly enhances how you analyze query results: the Query results distribution chart.
This new chart provides a graphical distribution of your results over the time window of the query. Immediately after running a query, you will see the distribution chart above your result table. This visualization allows Log Explorer users to quickly spot trends, identify anomalies, and understand the temporal concentration of log events that match their criteria. For example, you can visually confirm if a spike in traffic or errors occurred at a specific time, allowing you to focus your investigation efforts more effectively. This feature makes it faster and easier to extract meaningful insights from your vast log data.
The chart will dynamically update to reflect the logs matching your current query.
Oct 31, 2025
1. ### [Report logo misuse to Cloudflare directly from the Brand Protection dashboard](https://developers.cloudflare.com/changelog/2025-10-31-brand-protection-logo-dashboard-report-abuse/)
[Security Center](https://developers.cloudflare.com/security-center/)
The Brand Protection logo query dashboard now allows you to use the **Report to Cloudflare** button to submit an Abuse report directly from the Brand Protection logo queries dashboard. While you could previously report new domains that were impersonating your brand before, now you can do the same for websites found to be using your logo wihtout your permission. The abuse reports wiull be prefilled and you will only need to validate a few fields before you can click the submit button, after which our team process your request.
Ready to start? Check out the [Brand Protection docs](https://developers.cloudflare.com/security-center/brand-protection/).
Oct 31, 2025
1. ### [Workers WebSocket message size limit increased from 1 MiB to 32 MiB](https://developers.cloudflare.com/changelog/2025-10-31-increased-websocket-message-size-limit/)
[Workers ](https://developers.cloudflare.com/workers/)[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
Workers, including those using [Durable Objects](https://developers.cloudflare.com/durable-objects/) and [Browser Rendering](https://developers.cloudflare.com/browser-rendering/workers-bindings/), may now process WebSocket messages up to 32 MiB in size. Previously, this limit was 1 MiB.
This change allows Workers to handle use cases requiring large message sizes, such as processing Chrome Devtools Protocol messages.
For more information, please see the [Durable Objects startup limits](https://developers.cloudflare.com/durable-objects/platform/limits/#SQLite-backed-Durable-Objects-general-limits).
Oct 31, 2025
1. ### [Increased Workflows instance and concurrency limits](https://developers.cloudflare.com/changelog/2025-10-28-raising-limits/)
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
We've raised the [Cloudflare Workflows](https://developers.cloudflare.com/workflows/) account-level limits for all accounts on the [Workers paid plan](https://developers.cloudflare.com/workers/platform/pricing/):
* **Instance creation rate** increased from 100 workflow instances per 10 seconds to 100 instances per second
* **Concurrency limit** increased from 4,500 to 10,000 workflow instances per account
These increases mean you can create new instances up to 10x faster, and have more workflow instances concurrently executing. To learn more and get started with Workflows, refer to [the getting started guide](https://developers.cloudflare.com/workflows/get-started/guide/).
If your application requires a higher limit, fill out the [Limit Increase Request Form](https://developers.cloudflare.com/workers/platform/limits/) or contact your account team. Please refer to [Workflows pricing](https://developers.cloudflare.com/workflows/reference/pricing/) for more information.
Oct 30, 2025
1. ### [Introducing email two-factor authentication](https://developers.cloudflare.com/changelog/2025-10-30-email-2fa/)
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Two-factor authentication (2FA) is one of the best ways to protect your account from the risk of account takeover. Cloudflare has offered phishing resistant 2FA options including hardware based keys (for example, a Yubikey) and app based TOTP (time-based one-time password) options which use apps like Google or Microsoft's Authenticator app. Unfortunately, while these solutions are very secure, they can be lost if you misplace the hardware based key, or lose the phone which includes that app. The result is that users sometimes get locked out of their accounts and need to contact support.
Today, we are announcing the addition of email as a 2FA factor for all Cloudflare accounts. Email 2FA is in wide use across the industry as a least common denominator for 2FA because it is low friction, loss resistant, and still improves security over username/password login only. We also know that most commercial email providers already require 2FA, so your email address is usually well protected already.
You can now enable email 2FA on the Cloudflare dashboard:
1. Go to **Profile** at the top right corner.
2. Select **Authentication**.
3. Under **Two-Factor Authentication**, select **Set up**.
#### Sign-in security best practices
Cloudflare is critical infrastructure, and you should protect it as such. Review the following best practices and make sure you are doing your part to secure your account:
* Use a unique password for every website, including Cloudflare, and store it in a password manager like 1Password or Keeper. These services are cross-platform and simplify the process of managing secure passwords.
* Use 2FA to make it harder for an attacker to get into your account in the event your password is leaked.
* Store your backup codes securely. A password manager is the best place since it keeps the backup codes encrypted, but you can also print them and put them somewhere safe in your home.
* If you use an app to manage your 2FA keys, enable cloud backup, so that you don't lose your keys in the event you lose your phone.
* If you use a custom email domain to sign in, [configure SSO](https://developers.cloudflare.com/fundamentals/manage-members/dashboard-sso/).
* If you use a public email domain like Gmail or Hotmail, you can also use social login with Apple, GitHub, or Google to sign in.
* If you manage a Cloudflare account for work:
* Have at least two administrators in case one of them unexpectedly leaves your company.
* Use SCIM to automate permissions management for members in your Cloudflare account.
Oct 30, 2025
1. ### [Revamped Member Management UI](https://developers.cloudflare.com/changelog/2025-10-30-member-management-improvements/)
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
As Cloudflare's platform has grown, so has the need for precise, role-based access control. We’ve redesigned the Member Management experience in the Dashboard to help administrators more easily discover, assign, and refine permissions for specific principals.
#### What's New
**Refreshed member invite flow**
We overhauled the Invite Members UI to simplify inviting users and assigning permissions.
**Refreshed Members Overview Page**
We've updated the Members Overview Page to clearly display:
* Member 2FA status
* Which members hold Super Admin privileges
* API access settings per member
* Member onboarding state (accepted vs pending invite)

**New Member Permission Policies Details View**
We've created a new member details screen that shows all permission policies associated with a member; including policies inherited from group associations to make it easier for members to understand the effective permissions they have.

**Improved Member Permission Workflow**
We redesigned the permission management experience to make it faster and easier for administrators to review roles and grant access.

**Account-scoped Policies Restrictions Relaxed**
Previously, customers could only associate a single account-scoped policy with a member. We've relaxed this restriction, and now Administrators can now assign multiple account-scoped policies to the same member; bringing policy assignment behavior in-line with user-groups and providing greater flexibility in managing member permissions.
Oct 30, 2025
1. ### [New TCP-based fields available in Rulesets](https://developers.cloudflare.com/changelog/2025-10-30-tcp-rtt-and-tcp-fields/)
[Rules](https://developers.cloudflare.com/rules/)
#### Build rules based on TCP transport and latency
Cloudflare now provides two new request fields in the Ruleset engine that let you make decisions based on whether a request used TCP and the measured TCP round-trip time between the client and Cloudflare. These fields help you understand protocol usage across your traffic and build policies that respond to network performance. For example, you can distinguish TCP from QUIC traffic or route high latency requests to alternative origins when needed.
***
#### New fields
| Field | Type | Description |
| - | - | - |
| `cf.edge.client_tcp` | Boolean | Indicates whether the request used TCP. A value of true means the client connected using TCP instead of QUIC. |
| `cf.timings.client_tcp_rtt_msec` | Number | Reports the smoothed TCP round-trip time between the client and Cloudflare in milliseconds. For example, a value of 20 indicates roughly twenty milliseconds of RTT. |
Example filter expression:
```plaintext
cf.edge.client_tcp && cf.timings.client_tcp_rtt_msec < 100
```
More information can be found in the Rules language [fields reference](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/).
Oct 28, 2025
1. ### [Access private hostname applications support all ports/protocols](https://developers.cloudflare.com/changelog/2025-10-28-access-application-support-for-all-ports-and-protocols/)
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Cloudflare Access for private hostname applications](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/non-http/self-hosted-private-app/) can now secure traffic on all ports and protocols.
Previously, applying Zero Trust policies to private applications required the application to use HTTPS on port `443` and support Server Name Indicator (SNI).
This update removes that limitation. As long as the application is reachable via a Cloudflare off-ramp, you can now enforce your critical security controls — like single sign-on (SSO), MFA, device posture, and variable session lengths — to any private application. This allows you to extend Zero Trust security to services like SSH, RDP, internal databases, and other non-HTTPS applications.
For example, you can now create a self-hosted application in Access for `ssh.testapp.local` running on port `22`. You can then build a policy that only allows engineers in your organization to connect after they pass an SSO/MFA check and are using a corporate device.
This feature is generally available across all plans.
Oct 28, 2025
1. ### [Reranking and API-based system prompt configuration in AI Search](https://developers.cloudflare.com/changelog/2025-10-27-ai-search-reranking-system-prompt/)
[AI Search](https://developers.cloudflare.com/ai-search/)
[AI Search](https://developers.cloudflare.com/ai-search/) now supports reranking for improved retrieval quality and allows you to set the system prompt directly in your API requests.
#### Rerank for more relevant results
You can now enable [reranking](https://developers.cloudflare.com/ai-search/configuration/reranking/) to reorder retrieved documents based on their semantic relevance to the user’s query. Reranking helps improve accuracy, especially for large or noisy datasets where vector similarity alone may not produce the optimal ordering.
You can enable and configure reranking in the dashboard or directly in your API requests:
```javascript
const answer = await env.AI.autorag("my-autorag").aiSearch({
query: "How do I train a llama to deliver coffee?",
model: "@cf/meta/llama-3.3-70b-instruct-fp8-fast",
reranking: {
enabled: true,
model: "@cf/baai/bge-reranker-base"
}
});
```
#### Set system prompts in API
Previously, [system prompts](https://developers.cloudflare.com/ai-search/configuration/system-prompt/) could only be configured in the dashboard. You can now define them directly in your API requests, giving you per-query control over behavior. For example:
```javascript
// Dynamically set query and system prompt in AI Search
async function getAnswer(query, tone) {
const systemPrompt = `You are a ${tone} assistant.`;
const response = await env.AI.autorag("my-autorag").aiSearch({
query: query,
system_prompt: systemPrompt
});
return response;
}
// Example usage
const query = "What is Cloudflare?";
const tone = "friendly";
const answer = await getAnswer(query, tone);
console.log(answer);
```
Learn more about [Reranking](https://developers.cloudflare.com/ai-search/configuration/reranking/) and [System Prompt](https://developers.cloudflare.com/ai-search/configuration/system-prompt/) in AI Search.
Oct 28, 2025
1. ### [CASB introduces new granular roles](https://developers.cloudflare.com/changelog/2025-10-28-casb-roles/)
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
Cloudflare CASB (Cloud Access Security Broker) now supports two new granular roles to provide more precise access control for your security teams:
* **Cloudflare CASB Read:** Provides read-only access to view CASB findings and dashboards. This role is ideal for security analysts, compliance auditors, or team members who need visibility without modification rights.
* **Cloudflare CASB:** Provides full administrative access to configure and manage all aspects of the CASB product.
These new roles help you better enforce the principle of least privilege. You can now grant specific members access to CASB security findings without assigning them broader permissions, such as the **Super Administrator** or **Administrator** roles.
To enable [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/), scans in CASB, account members will need the **Cloudflare Zero Trust** role.
You can find these new roles when inviting members or creating API tokens in the Cloudflare dashboard under **Manage Account** > **Members**.
To learn more about managing roles and permissions, refer to the [Manage account members and roles documentation](https://developers.cloudflare.com/fundamentals/manage-members/roles/).
Oct 28, 2025
1. ### [New Application Categories added for HTTP Traffic Management](https://developers.cloudflare.com/changelog/gateway-application-categories-added/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
To give you precision and flexibility while creating policies to block unwanted traffic, we are introducing new, more granular application categories in the Gateway product.
We have added the following categories to provide more precise organization and allow for finer-grained policy creation, designed around how users interact with different types of applications:
* Business
* Education
* Entertainment & Events
* Food & Drink
* Health & Fitness
* Lifestyle
* Navigation
* Photography & Graphic Design
* Travel
The new categories are live now, but we are providing a transition period for existing applications to be fully remapped to these new categories.
The full remapping will be completed by January 30, 2026.
We encourage you to use this time to:
* Review the new category structure.
* Identify and adjust any existing HTTP policies that reference older categories to ensure a smooth transition.
For more information on creating HTTP policies, refer to [Applications and app types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
Oct 27, 2025
1. ### [Azure Sentinel Connector](https://developers.cloudflare.com/changelog/2025-10-27-sentinel-connector/)
[Logs](https://developers.cloudflare.com/logs/)
Logpush now supports integration with [Microsoft Sentinel](https://www.microsoft.com/en-us/security/business/siem-and-xdr/microsoft-sentinel).The new Azure Sentinel Connector built on Microsoft’s Codeless Connector Framework (CCF), is now avaialble. This solution replaces the previous Azure Functions-based connector, offering significant improvements in security, data control, and ease of use for customers. Logpush customers can send logs to Azure Blob Storage and configure this new Sentinel Connector to ingest those logs directly into Microsoft Sentinel.
This upgrade significantly streamlines log ingestion, improves security, and provides greater control:
* Simplified Implementation: Easier for engineering teams to set up and maintain.
* Cost Control: New support for Data Collection Rules (DCRs) allows you to filter and transform logs at ingestion time, offering potential cost savings.
* Enhanced Security: CCF provides a higher level of security compared to the older Azure Functions connector.
* ata Lake Integration: Includes native integration with Data Lake.
Find the new solution [here](https://marketplace.microsoft.com/en-us/product/azure-application/cloudflare.azure-sentinel-solution-cloudflare-ccf?tab=Overview) and refer to the [Cloudflare's developer documention](https://developers.cloudflare.com/analytics/analytics-integrations/sentinel/#supported-logs:~:text=WorkBook%20fields,-Analytic%20rules)for more information on the connector, including setup steps, supported logs and Microsfot's resources.
Oct 27, 2025
1. ### [TLD Insights in Cloudflare Radar](https://developers.cloudflare.com/changelog/2025-10-27-radar-tld-insights/)
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) now introduces Top-Level Domain (TLD) insights, providing visibility into popularity based on the DNS magnitude metric, detailed TLD information including its type, manager, DNSSEC support, RDAP support, and WHOIS data, and trends such as DNS query volume and geographic distribution observed by the [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/) DNS resolver.
The following dimensions were added to the Radar DNS API, specifically, to the [`/dns/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/methods/summary_v2/) and [`/dns/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/methods/timeseries_groups_v2/) endpoints:
* `tld`: Top-level domain extracted from DNS queries; can also be used as a filter.
* `tld_dns_magnitude`: Top-level domain ranking by [DNS magnitude](https://developers.cloudflare.com/radar/glossary#dns-magnitude).
And the following endpoints were added:
* [`/tlds`](https://developers.cloudflare.com/api/resources/radar/subresources/tlds/methods/list/) - Lists all TLDs.
* [`/tlds/{tld}`](https://developers.cloudflare.com/api/resources/radar/subresources/tlds/methods/get/) - Retrieves information about a specific TLD.

Learn more about the new Radar DNS insights in our [blog post](https://blog.cloudflare.com/introducing-tld-insights-on-cloudflare-radar/), and check out the [new Radar page](https://radar.cloudflare.com/tlds).
Oct 23, 2025
1. ### [Workers AI Markdown Conversion: New endpoint to list supported formats](https://developers.cloudflare.com/changelog/2025-10-23-new-markdown-conversion-endpoint/)
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Developers can now programmatically retrieve a list of all file formats supported by the [Markdown Conversion utility](https://developers.cloudflare.com/workers-ai/features/markdown-conversion/) in Workers AI.
You can use the [`env.AI`](https://developers.cloudflare.com/workers-ai/configuration/bindings/) binding:
```typescript
await env.AI.toMarkdown().supported()
```
Or call the REST API:
```bash
curl https://api.cloudflare.com/client/v4/accounts/{ACCOUNT_ID}/ai/tomarkdown/supported \
-H 'Authorization: Bearer {API_TOKEN}'
```
Both return a list of file formats that users can convert into Markdown:
```json
[
{
"extension": ".pdf",
"mimeType": "application/pdf",
},
{
"extension": ".jpeg",
"mimeType": "image/jpeg",
},
...
]
```
Learn more about our [Markdown Conversion utility](https://developers.cloudflare.com/workers-ai/features/markdown-conversion/).
Oct 21, 2025
1. ### [New Robots.txt tab for tracking crawler compliance](https://developers.cloudflare.com/changelog/2025-10-21-track-robots-txt/)
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
AI Crawl Control now includes a **Robots.txt** tab that provides insights into how AI crawlers interact with your `robots.txt` files.
#### What's new
The Robots.txt tab allows you to:
* Monitor the health status of `robots.txt` files across all your hostnames, including HTTP status codes, and identify hostnames that need a `robots.txt` file.
* Track the total number of requests to each `robots.txt` file, with breakdowns of successful versus unsuccessful requests.
* Check whether your `robots.txt` files contain [Content Signals](https://contentsignals.org/) directives for AI training, search, and AI input.
* Identify crawlers that request paths explicitly disallowed by your `robots.txt` directives, including the crawler name, operator, violated path, specific directive, and violation count.
* Filter `robots.txt` request data by crawler, operator, category, and custom time ranges.
#### Take action
When you identify non-compliant crawlers, you can:
* Block the crawler in the [Crawlers tab](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/)
* Create custom [WAF rules](https://developers.cloudflare.com/waf/) for path-specific security
* Use [Redirect Rules](https://developers.cloudflare.com/rules/url-forwarding/) to guide crawlers to appropriate areas of your site
To get started, go to **AI Crawl Control** > **Robots.txt** in the Cloudflare dashboard. Learn more in the [Track robots.txt documentation](https://developers.cloudflare.com/ai-crawl-control/features/track-robots-txt/).
Oct 20, 2025
1. ### [Schedule DNS policies from the UI](https://developers.cloudflare.com/changelog/2025-10-20-schedule-dns-policies-from-the-ui/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Admins can now create [scheduled DNS policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/timed-policies/) directly from the Zero Trust dashboard, without using the API. You can configure policies to be active during specific, recurring times, such as blocking social media during business hours or gaming sites on school nights.
* **Preset Schedules**: Use built-in templates for common scenarios like Business Hours, School Days, Weekends, and more.
* **Custom Schedules**: Define your own schedule with specific days and up to three non-overlapping time ranges per day.
* **Timezone Control**: Choose to enforce a schedule in a specific timezone (for example, US Eastern) or based on the local time of each user.
* **Combined with Duration**: Policies can have both a schedule and a duration. If both are set, the duration's expiration takes precedence.
You can see the flow in the demo GIF:
This update makes time-based DNS policies accessible to all Gateway customers, removing the technical barrier of the API.
Oct 17, 2025
1. ### [On-Demand Security Report](https://developers.cloudflare.com/changelog/2025-10-16-on-demand-security-report/)
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You can now generate on-demand security reports directly from the Cloudflare dashboard. This new feature provides a comprehensive overview of your email security posture, making it easier than ever to demonstrate the value of Cloudflare’s Email security to executives and other decision makers.
These reports offer several key benefits:
* **Executive Summary:** Quickly view the performance of Email security with a high-level executive summary.
* **Actionable Insights:** Dive deep into trend data, breakdowns of threat types, and analysis of top targets to identify and address vulnerabilities.
* **Configuration Transparency:** Gain a clear view of your policy, submission, and domain configurations to ensure optimal setup.
* **Account Takeover Risks:** Get a snapshot of your M365 risky users (requires a Microsoft Entra ID P2 license and [M365 SaaS integration](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/microsoft-365/)).
This feature is available across the following Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
Oct 16, 2025
1. ### [View and edit Durable Object data in UI with Data Studio (Beta)](https://developers.cloudflare.com/changelog/2025-10-16-durable-objects-data-studio/)
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
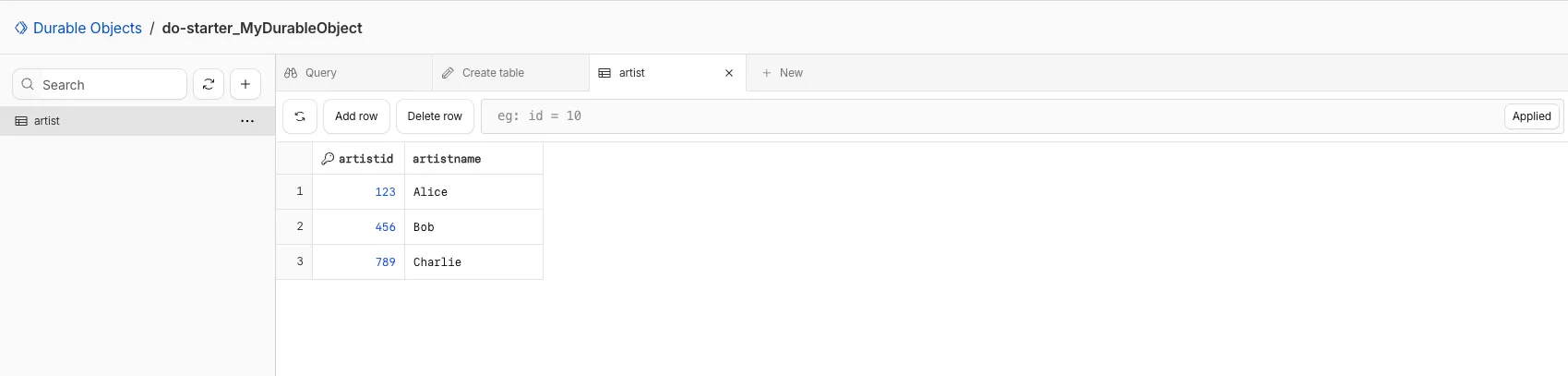
You can now view and write to each Durable Object's storage using a UI editor on the Cloudflare dashboard. Only Durable Objects using [SQLite storage](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#create-sqlite-backed-durable-object-class) can use Data Studio.
[Go to **Durable Objects**](https://dash.cloudflare.com/?to=/:account/workers/durable-objects)
Data Studio unlocks easier data access with Durable Objects for prototyping application data models to debugging production storage usage. Before, querying your Durable Objects data required deploying a Worker.
To access a Durable Object, you can provide an object's unique name or ID generated by Cloudflare. Data Studio requires you to have at least the `Workers Platform Admin` role, and all queries are captured with audit logging for your security and compliance needs. Queries executed by Data Studio send requests to your remote, deployed objects and incur normal usage billing.
To learn more, visit the Data Studio [documentation](https://developers.cloudflare.com/durable-objects/observability/data-studio/). If you have feedback or suggestions for the new Data Studio, please share your experience on [Discord](https://discord.com/channels/595317990191398933/773219443911819284)
Oct 16, 2025
1. ### [Monitor Groups for Advanced Health Checking With Load Balancing](https://developers.cloudflare.com/changelog/2025-08-15-monitor-groups-for-load-balancing/)
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
Cloudflare Load Balancing now supports Monitor Groups, a powerful new way to combine multiple health monitors into a single, logical group. This allows you to create sophisticated health checks that more accurately reflect the true availability of your applications by assessing multiple services at once.
With Monitor Groups, you can ensure that all critical components of an application are healthy before sending traffic to an origin pool, enabling smarter failover decisions and greater resilience. This feature is now available via the API for customers with an Enterprise Load Balancing subscription.
#### What you can do:
* **Combine Multiple Monitors**: Group different health monitors (for example, HTTP, TCP) that check various application components, like a primary API gateway and a specific `/login` service.
* **Isolate Monitors for Observation**: Mark a monitor as "monitoring only" to receive alerts and data without it affecting a pool's health status or traffic steering. This is perfect for testing new checks or observing non-critical dependencies.
* **Improve Steering Intelligence**: Latency for Dynamic Steering is automatically averaged across all active monitors in a group, providing a more holistic view of an origin's performance.
This enhancement is ideal for complex, multi-service applications where the health of one component depends on another. By aggregating health signals, Monitor Groups provide a more accurate and comprehensive assessment of your application's true status.
For detailed information and API configuration guides, please visit our [developer documentation](https://developers.cloudflare.com/load-balancing/monitors/monitor-groups) for Monitor Groups.
Oct 10, 2025
1. ### [New domain categories added](https://developers.cloudflare.com/changelog/2025-10-10-new-domain-categories/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
We have added three new domain categories under the Technology parent category, to better reflect online content and improve DNS filtering.
**New categories added**
| Parent ID | Parent Name | Category ID | Category Name |
| - | - | - | - |
| 26 | Technology | 194 | Keep Awake Software |
| 26 | Technology | 192 | Remote Access |
| 26 | Technology | 193 | Shareware/Freeware |
Refer to [Gateway domain categories](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) to learn more.
Oct 09, 2025
1. ### [Expanded CT log activity insights on Cloudflare Radar](https://developers.cloudflare.com/changelog/2025-10-09-radar-ct-log-activity-insights/)
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) has expanded its Certificate Transparency (CT) log insights with new stats that provide greater visibility into log activity:
* **Log growth rate**: The average throughput of the CT log over the past 7 days, measured in certificates per hour.
* **Included certificate count**: The total number of certificates already included in this CT log.
* **Eligible-for-inclusion certificate count**: The number of certificates eligible for inclusion in this log but not yet included. This metric is based on certificates signed by trusted root CAs within the log’s accepted date range.
* **Last update**: The timestamp of the most recent update to the CT log.
These new statistics have been added to the response of the [Get Certificate Log Details](https://developers.cloudflare.com/api/resources/radar/subresources/ct/subresources/logs/methods/get/) API endpoint, and are displayed on the [CT log information page](https://radar.cloudflare.com/certificate-transparency/log/nimbus2025#log-activity).
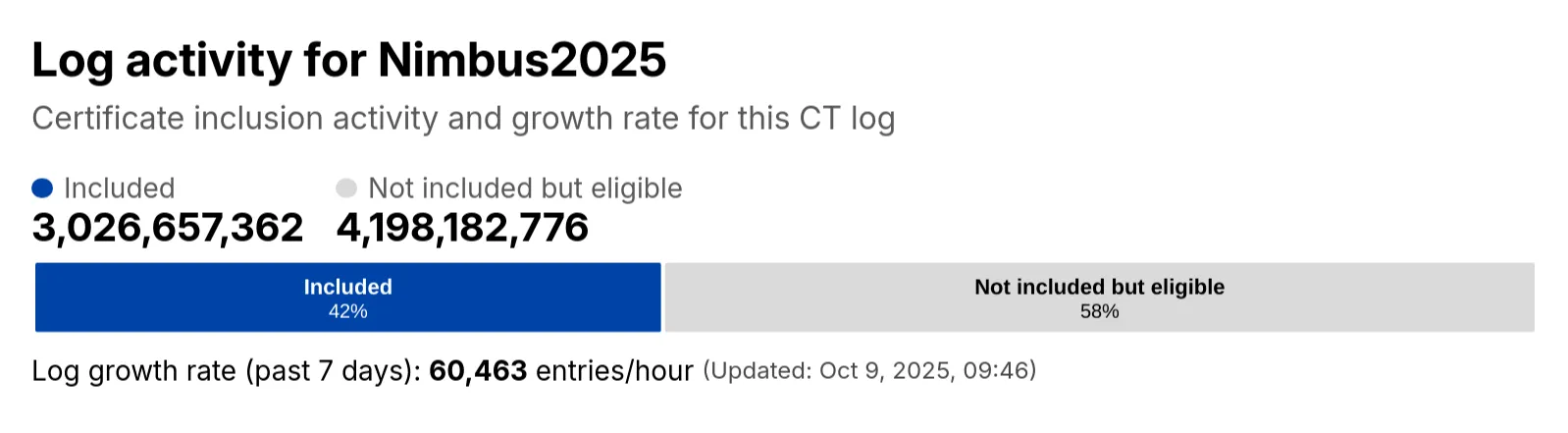
Oct 06, 2025
1. ### [R2 Data Catalog table-level compaction](https://developers.cloudflare.com/changelog/2025-10-06-data-catalog-table-compaction/)
[R2](https://developers.cloudflare.com/r2/)
You can now enable compaction for individual [Apache Iceberg](https://iceberg.apache.org/) tables in [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/), giving you fine-grained control over different workloads.
```bash
# Enable compaction for a specific table (no token required)
npx wrangler r2 bucket catalog compaction enable --target-size 256
```
This allows you to:
* Apply different target file sizes per table
* Disable compaction for specific tables
* Optimize based on table-specific access patterns
Learn more at [Manage catalogs](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/).
Oct 06, 2025
1. ### [Browser Support Detection for PQ Encryption on Cloudflare Radar](https://developers.cloudflare.com/changelog/2025-10-06-radar-pq-encryption-test/)
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) now includes browser detection for Post-quantum (PQ) encryption. The [Post-quantum encryption card](https://radar.cloudflare.com/adoption-and-usage#post-quantum-encryption) now checks whether a user’s browser supports post-quantum encryption. If support is detected, information about the key agreement in use is displayed.
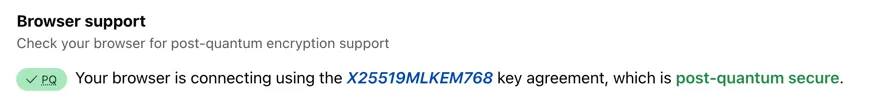
Oct 02, 2025
1. ### [New Deepgram Flux model available on Workers AI](https://developers.cloudflare.com/changelog/2025-10-02-deepgram-flux/)
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Deepgram's newest Flux model [`@cf/deepgram/flux`](https://developers.cloudflare.com/workers-ai/models/flux/) is now available on Workers AI, hosted directly on Cloudflare's infrastructure. We're excited to be a launch partner with Deepgram and offer their new Speech Recognition model built specifically for enabling voice agents. Check out [Deepgram's blog](https://deepgram.com/flux) for more details on the release.
The Flux model can be used in conjunction with Deepgram's speech-to-text model [`@cf/deepgram/nova-3`](https://developers.cloudflare.com/workers-ai/models/nova-3/) and text-to-speech model [`@cf/deepgram/aura-1`](https://developers.cloudflare.com/workers-ai/models/aura-1/) to build end-to-end voice agents. Having Deepgram on Workers AI takes advantage of our edge GPU infrastructure, for ultra low latency voice AI applications.
#### Promotional Pricing
For the month of October 2025, Deepgram's Flux model will be free to use on Workers AI. Official pricing will be announced soon and charged after the promotional pricing period ends on October 31, 2025. Check out the [model page](https://developers.cloudflare.com/workers-ai/models/flux/) for pricing details in the future.
#### Example Usage
The new Flux model is WebSocket only as it requires live bi-directional streaming in order to recognize speech activity.
1. Create a worker that establishes a websocket connection with `@cf/deepgram/flux`
```js
export default {
async fetch(request, env, ctx): Promise {
const resp = await env.AI.run("@cf/deepgram/flux", {
encoding: "linear16",
sample_rate: "16000"
}, {
websocket: true
});
return resp;
},
} satisfies ExportedHandler;
```
1. Deploy your worker
```bash
npx wrangler deploy
```
1. Write a client script to connect to your worker and start sending random audio bytes to it
```js
const ws = new WebSocket('wss://');
ws.onopen = () => {
console.log('Connected to WebSocket');
// Generate and send random audio bytes
// You can replace this part with a function
// that reads from your mic or other audio source
const audioData = generateRandomAudio();
ws.send(audioData);
console.log('Audio data sent');
};
ws.onmessage = (event) => {
// Transcription will be received here
// Add your custom logic to parse the data
console.log('Received:', event.data);
};
ws.onerror = (error) => {
console.error('WebSocket error:', error);
};
ws.onclose = () => {
console.log('WebSocket closed');
};
// Generate random audio data (1 second of noise at 44.1kHz, mono)
function generateRandomAudio() {
const sampleRate = 44100;
const duration = 1;
const numSamples = sampleRate * duration;
const buffer = new ArrayBuffer(numSamples * 2);
const view = new Int16Array(buffer);
for (let i = 0; i < numSamples; i++) {
view[i] = Math.floor(Math.random() * 65536 - 32768);
}
return buffer;
}
```
Oct 02, 2025
1. ### [Workers Analytics Engine adds supports for new SQL functions](https://developers.cloudflare.com/changelog/2025-09-26-analytics-engine-sql-enhancements/)
[Workers Analytics Engine ](https://developers.cloudflare.com/analytics/analytics-engine/)[Workers](https://developers.cloudflare.com/workers/)
You can now perform more powerful queries directly in [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/) with a major expansion of our SQL function library.
Workers Analytics Engine allows you to ingest and store high-cardinality data at scale (such as custom analytics) and query your data through a simple SQL API.
Today, we've expanded Workers Analytics Engine's SQL capabilities with several new functions:
[**New aggregate functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/aggregate-functions/)
* `argMin()` - Returns the value associated with the minimum in a group
* `argMax()` - Returns the value associated with the maximum in a group
* `topK()` - Returns an array of the most frequent values in a group
* `topKWeighted()` - Returns an array of the most frequent values in a group using weights
* `first_value()` - Returns the first value in an ordered set of values within a partition
* `last_value()` - Returns the last value in an ordered set of values within a partition
[**New bit functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/bit-functions/)
* `bitAnd()` - Returns the bitwise AND of two expressions
* `bitCount()` - Returns the number of bits set to one in the binary representation of a number
* `bitHammingDistance()` - Returns the number of bits that differ between two numbers
* `bitNot()` - Returns a number with all bits flipped
* `bitOr()` - Returns the inclusive bitwise OR of two expressions
* `bitRotateLeft()` - Rotates all bits in a number left by specified positions
* `bitRotateRight()` - Rotates all bits in a number right by specified positions
* `bitShiftLeft()` - Shifts all bits in a number left by specified positions
* `bitShiftRight()` - Shifts all bits in a number right by specified positions
* `bitTest()` - Returns the value of a specific bit in a number
* `bitXor()` - Returns the bitwise exclusive-or of two expressions
[**New mathematical functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/mathematical-functions/)
* `abs()` - Returns the absolute value of a number
* `log()` - Computes the natural logarithm of a number
* `round()` - Rounds a number to a specified number of decimal places
* `ceil()` - Rounds a number up to the nearest integer
* `floor()` - Rounds a number down to the nearest integer
* `pow()` - Returns a number raised to the power of another number
[**New string functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/string-functions/)
* `lowerUTF8()` - Converts a string to lowercase using UTF-8 encoding
* `upperUTF8()` - Converts a string to uppercase using UTF-8 encoding
[**New encoding functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/encoding-functions/)
* `hex()` - Converts a number to its hexadecimal representation
* `bin()` - Converts a string to its binary representation
[**New type conversion functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/type-conversion-functions/)
* `toUInt8()` - Converts any numeric expression, or expression resulting in a string representation of a decimal, into an unsigned 8 bit integer
#### Ready to get started?
Whether you're building usage-based billing systems, customer analytics dashboards, or other custom analytics, these functions let you get the most out of your data. [Get started ](https://developers.cloudflare.com/analytics/analytics-engine/get-started/)with Workers Analytics Engine and explore all available functions in our [SQL reference documentation](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/).
Oct 01, 2025
1. ### [New Confidence Intervals in GraphQL Analytics API](https://developers.cloudflare.com/changelog/2025-10-01-confidence-intervals/)
[Analytics](https://developers.cloudflare.com/analytics/)
The GraphQL Analytics API now supports confidence intervals for `sum` and `count` fields on adaptive (sampled) datasets. Confidence intervals provide a statistical range around sampled results, helping verify accuracy and quantify uncertainty.
* **Supported datasets**: Adaptive (sampled) datasets only.
* **Supported fields**: All `sum` and `count` fields.
* **Usage**: The confidence `level` must be provided as a decimal between 0 and 1 (e.g. `0.90`, `0.95`, `0.99`).
* **Default**: If no confidence level is specified, no intervals are returned.
For examples and more details, see the [GraphQL Analytics API documentation](https://developers.cloudflare.com/analytics/graphql-api/features/confidence-intervals/).
Oct 01, 2025
1. ### [Larger Container instance types](https://developers.cloudflare.com/changelog/2025-10-01-new-container-instance-types/)
[Containers](https://developers.cloudflare.com/containers/)
New instance types provide up to 4 vCPU, 12 GiB of memory, and 20 GB of disk per container instance.
| Instance Type | vCPU | Memory | Disk |
| - | - | - | - |
| lite | 1/16 | 256 MiB | 2 GB |
| basic | 1/4 | 1 GiB | 4 GB |
| standard-1 | 1/2 | 4 GiB | 8 GB |
| standard-2 | 1 | 6 GiB | 12 GB |
| standard-3 | 2 | 8 GiB | 16 GB |
| standard-4 | 4 | 12 GiB | 20 GB |
The `dev` and `standard` instance types are preserved for backward compatibility and are aliases for `lite` and `standard-1`, respectively. The `standard-1` instance type now provides up to 8 GB of disk instead of only 4 GB.
See the [getting started guide](https://developers.cloudflare.com/containers/get-started/) to deploy your first Container, and the [limits documentation](https://developers.cloudflare.com/containers/platform-details/limits/) for more details on the available instance types and limits.
Oct 01, 2025
1. ### [Expanded File Type Controls for Executables and Disk Images](https://developers.cloudflare.com/changelog/2025-10-01-new-file-type-support/)
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now enhance your security posture by blocking additional application installer and disk image file types with Cloudflare Gateway. Preventing the download of unauthorized software packages is a critical step in securing endpoints from malware and unwanted applications.
We have expanded Gateway's file type controls to include:
* Apple Disk Image (dmg)
* Microsoft Software Installer (msix, appx)
* Apple Software Package (pkg)
You can find these new options within the [*Upload File Types* and *Download File Types* selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#download-and-upload-file-types) when creating or editing an HTTP policy. The file types are categorized as follows:
* **System**: *Apple Disk Image (dmg)*
* **Executable**: *Microsoft Software Installer (msix)*, *Microsoft Software Installer (appx)*, *Apple Software Package (pkg)*
To ensure these file types are blocked effectively, please note the following behaviors:
* DMG: Due to their file structure, DMG files are blocked at the very end of the transfer. A user's download may appear to progress but will fail at the last moment, preventing the browser from saving the file.
* MSIX: To comprehensively block Microsoft Software Installers, you should also include the file type *Unscannable*. MSIX files larger than 100 MB are identified as Unscannable ZIP files during inspection.
To get started, go to your HTTP policies in Zero Trust. For a full list of file types, refer to [supported file types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#supported-file-types).
Sep 30, 2025
1. ### [Application granular controls for operations in SaaS applications](https://developers.cloudflare.com/changelog/2025-09-25-new-granular-controls-for-saas-applications/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Gateway users can now apply granular controls to their file sharing and AI chat applications through [HTTP policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies).
The new feature offers two methods of controlling SaaS applications:
* **Application Controls** are curated groupings of Operations which provide an easy way for users to achieve a specific outcome. Application Controls may include *Upload*, *Download*, *Prompt*, *Voice*, and *Share* depending on the application.
* **Operations** are controls aligned to the most granular action a user can take. This provides a fine-grained approach to enforcing policy and generally aligns to the SaaS providers API specifications in naming and function.
Get started using [Application Granular Controls](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/granular-controls) and refer to the list of [supported applications](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/granular-controls/#compatible-applications).
Sep 29, 2025
1. ### [Regional Data in Cloudflare Radar](https://developers.cloudflare.com/changelog/2025-09-29-radar-regional-data/)
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) now introduces Regional Data, providing traffic insights that bring a more localized perspective to the traffic trends shown on Radar.
The following API endpoints are now available:
* [`Get Geolocation`](https://developers.cloudflare.com/api/resources/radar/subresources/geolocations/methods/get/) - Retrieves geolocation by `geoId`.
* [`List Geolocations`](https://developers.cloudflare.com/api/resources/radar/subresources/geolocations/methods/list/) - Lists geolocations.
* [`NetFlows Summary By Dimension`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/methods/summary_v2/) - Retrieves NetFlows summary by dimension.
All `summary` and `timeseries_groups` endpoints in [`HTTP`](https://developers.cloudflare.com/api/resources/radar/subresources/http/) and [`NetFlows`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/) now include an `adm1` dimension for grouping data by first level administrative division (for example, state, province, etc.)
A new filter `geoId` was also added to all endpoints in [`HTTP`](https://developers.cloudflare.com/api/resources/radar/subresources/http/) and [`NetFlows`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/), allowing filtering by a specific administrative division.
Check out the new Regional traffic insights on a country specific traffic page [new Radar page](https://radar.cloudflare.com/traffic/pt).
Sep 25, 2025
1. ### [Pipelines now supports SQL transformations and Apache Iceberg](https://developers.cloudflare.com/changelog/2025-09-25-pipelines-sql/)
[Pipelines](https://developers.cloudflare.com/pipelines/)
Today, we're launching the new [Cloudflare Pipelines](https://developers.cloudflare.com/pipelines/): a streaming data platform that ingests events, transforms them with [SQL](https://developers.cloudflare.com/pipelines/sql-reference/select-statements/), and writes to [R2](https://developers.cloudflare.com/r2/) as [Apache Iceberg](https://iceberg.apache.org/) tables or Parquet files.
Pipelines can receive events via [HTTP endpoints](https://developers.cloudflare.com/pipelines/streams/writing-to-streams/#send-via-http) or [Worker bindings](https://developers.cloudflare.com/pipelines/streams/writing-to-streams/#send-via-workers), transform them with SQL, and deliver to R2 with exactly-once guarantees. This makes it easy to build analytics-ready warehouses for server logs, mobile application events, IoT telemetry, or clickstream data without managing streaming infrastructure.
For example, here's a pipeline that ingests clickstream events and filters out bot traffic while extracting domain information:
```sql
INSERT into events_table
SELECT
user_id,
lower(event) AS event_type,
to_timestamp_micros(ts_us) AS event_time,
regexp_match(url, '^https?://([^/]+)')[1] AS domain,
url,
referrer,
user_agent
FROM events_json
WHERE event = 'page_view'
AND NOT regexp_like(user_agent, '(?i)bot|spider');
```
Get started by creating a pipeline in the dashboard or running a single command in [Wrangler](https://developers.cloudflare.com/workers/wrangler/):
```bash
npx wrangler pipelines setup
```
Check out our [getting started guide](https://developers.cloudflare.com/pipelines/getting-started/) to learn how to create a pipeline that delivers events to an [Iceberg table](https://developers.cloudflare.com/r2/data-catalog/) you can query with R2 SQL. Read more about today's announcement in our [blog post](https://blog.cloudflare.com/cloudflare-data-platform).
Sep 25, 2025
1. ### [Announcing R2 SQL](https://developers.cloudflare.com/changelog/2025-09-25-announcing-r2-sql-open-beta/)
[R2 SQL](https://developers.cloudflare.com/r2-sql/)
Today, we're launching the **open beta** for [R2 SQL](https://developers.cloudflare.com/r2-sql/): A serverless, distributed query engine that can efficiently analyze petabytes of data in [Apache Iceberg](https://iceberg.apache.org/) tables managed by [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog).
R2 SQL is ideal for exploring analytical and time-series data stored in R2, such as logs, events from [Pipelines](https://developers.cloudflare.com/pipelines/), or clickstream and user behavior data.
If you already have a table in R2 Data Catalog, running queries is as simple as:
```bash
npx wrangler r2 sql query YOUR_WAREHOUSE "
SELECT
user_id,
event_type,
value
FROM events.user_events
WHERE event_type = 'CHANGELOG' or event_type = 'BLOG'
AND __ingest_ts > '2025-09-24T00:00:00Z'
ORDER BY __ingest_ts DESC
LIMIT 100"
```
To get started with R2 SQL, check out our [getting started guide](https://developers.cloudflare.com/r2-sql/get-started/) or learn more about supported features in the [SQL reference](https://developers.cloudflare.com/r2-sql/sql-reference/). For a technical deep dive into how we built R2 SQL, read our [blog post](https://blog.cloudflare.com/r2-sql-deep-dive/).
Sep 25, 2025
1. ### [Browser Rendering Playwright GA, Stagehand support (Beta), and higher limits](https://developers.cloudflare.com/changelog/2025-09-25-br-playwright-ga-stagehand-limits/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We’re shipping three updates to Browser Rendering:
* Playwright support is now Generally Available and synced with [Playwright v1.55](https://playwright.dev/docs/release-notes#version-155), giving you a stable foundation for critical automation and AI-agent workflows.
* We’re also adding [Stagehand support (Beta)](https://developers.cloudflare.com/browser-rendering/stagehand/) so you can combine code with natural language instructions to build more resilient automations.
* Finally, we’ve tripled [limits](https://developers.cloudflare.com/browser-rendering/limits/#workers-paid) for paid plans across both the [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) and [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/) to help you scale.
To get started with Stagehand, refer to the [Stagehand](https://developers.cloudflare.com/browser-rendering/stagehand/) example that uses Stagehand and [Workers AI](https://developers.cloudflare.com/workers-ai/) to search for a movie on this [example movie directory](https://demo.playwright.dev/movies), extract its details using natural language (title, year, rating, duration, and genre), and return the information along with a screenshot of the webpage.
```ts
const stagehand = new Stagehand({
env: "LOCAL",
localBrowserLaunchOptions: { cdpUrl: endpointURLString(env.BROWSER) },
llmClient: new WorkersAIClient(env.AI),
verbose: 1,
});
await stagehand.init();
const page = stagehand.page;
await page.goto('https://demo.playwright.dev/movies');
// if search is a multi-step action, stagehand will return an array of actions it needs to act on
const actions = await page.observe('Search for "Furiosa"');
for (const action of actions)
await page.act(action);
await page.act('Click the search result');
// normal playwright functions work as expected
await page.waitForSelector('.info-wrapper .cast');
let movieInfo = await page.extract({
instruction: 'Extract movie information',
schema: z.object({
title: z.string(),
year: z.number(),
rating: z.number(),
genres: z.array(z.string()),
duration: z.number().describe("Duration in minutes"),
}),
});
await stagehand.close();
```
Sep 25, 2025
1. ### [AI Search (formerly AutoRAG) now with More Models To Choose From](https://developers.cloudflare.com/changelog/2025-09-25-ai-search-more-models/)
[AI Search](https://developers.cloudflare.com/ai-search/)
AutoRAG is now AI Search! The new name marks a new and bigger mission: to make world-class search infrastructure available to every developer and business.
With AI Search you can now use models from different providers like OpenAI and Anthropic. By attaching your provider keys to the AI Gateway linked to your AI Search instance, you can use many more models for both embedding and inference.
To use AI Search with other [model providers](https://developers.cloudflare.com/ai-search/configuration/models/):
1. **Add provider keys to AI Gateway**
1. Go to AI > AI Gateway in the dashboard.
2. Select or create an AI gateway.
3. In Provider Keys, choose your provider, click Add, and enter the key.
2. **Connect a gateway to AI Search**: When creating a new AI Search, select the AI Gateway with your provider keys. For an existing AI Search, go to Settings and switch to a gateway that has your keys under Resources.
3. **Select models**: Embedding models are only available to be changed when creating a new AI Search. Generation model can be selected when creating a new AI Search and can be changed at any time in Settings.
Once configured, your AI Search instance will be able to reference models available through your AI Gateway when making a `/ai-search` request:
```javascript
export default {
async fetch(request, env) {
// Query your AI Search instance with a natural language question to an OpenAI model
const result = await env.AI.autorag("my-ai-search").aiSearch({
query: "What's new for Cloudflare Birthday Week?",
model: "openai/gpt-5"
});
// Return only the generated answer as plain text
return new Response(result.response, {
headers: { "Content-Type": "text/plain" },
});
},
};
```
In the coming weeks we will also roll out updates to align the APIs with the new name. The existing APIs will continue to be supported for the time being. Stay tuned to the [AI Search Changelog](https://developers.cloudflare.com/changelog/?product=ai-search) and [Discord](https://discord.cloudflare.com/) for more updates!
Sep 25, 2025
1. ### [Run more Containers with higher resource limits](https://developers.cloudflare.com/changelog/2025-09-24-higher-container-resource-limits/)
[Containers](https://developers.cloudflare.com/containers/)
You can now run more Containers concurrently with higher limits on CPU, memory, and disk.
| Limit | New Limit | Previous Limit |
| - | - | - |
| Memory for concurrent live Container instances | 400GiB | 40GiB |
| vCPU for concurrent live Container instances | 100 | 20 |
| Disk for concurrent live Container instances | 2TB | 100GB |
You can now run 1000 instances of the `dev` instance type, 400 instances of `basic`, or 100 instances of `standard` concurrently.
This opens up new possibilities for running larger-scale workloads on Containers.
See the [getting started guide](https://developers.cloudflare.com/containers/get-started/) to deploy your first Container, and the [limits documentation](https://developers.cloudflare.com/containers/platform-details/limits/) for more details on the available instance types and limits.
Sep 25, 2025
1. ### [Refine DLP Scans with New Body Phase Selector](https://developers.cloudflare.com/changelog/2025-09-25-body-phase-selector/)
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now more precisely control your HTTP DLP policies by specifying whether to scan the request or response body, helping to reduce false positives and target specific data flows.
In the Gateway HTTP policy builder, you will find a new selector called *Body Phase*. This allows you to define the direction of traffic the DLP engine will inspect:
* *Request Body*: Scans data sent from a user's machine to an upstream service. This is ideal for monitoring data uploads, form submissions, or other user-initiated data exfiltration attempts.
* *Response Body*: Scans data sent to a user's machine from an upstream service. Use this to inspect file downloads and website content for sensitive data.
For example, consider a policy that blocks Social Security Numbers (SSNs). Previously, this policy might trigger when a user visits a website that contains example SSNs in its content (the response body). Now, by setting the **Body Phase** to *Request Body*, the policy will only trigger if the user attempts to upload or submit an SSN, ignoring the content of the web page itself.
All policies without this selector will continue to scan both request and response bodies to ensure continued protection.
For more information, refer to [Gateway HTTP policy selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#body-phase/).
Sep 25, 2025
1. ### [R2 Data Catalog now supports compaction](https://developers.cloudflare.com/changelog/2025-09-25-data-catalog-compaction/)
[R2](https://developers.cloudflare.com/r2/)
You can now enable automatic compaction for [Apache Iceberg](https://iceberg.apache.org/) tables in [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) to improve query performance.
Compaction is the process of taking a group of small files and combining them into fewer larger files. This is an important maintenance operation as it helps ensure that query performance remains consistent by reducing the number of files that needs to be scanned.
To enable automatic compaction in R2 Data Catalog, find it under **R2 Data Catalog** in your R2 bucket settings in the dashboard.
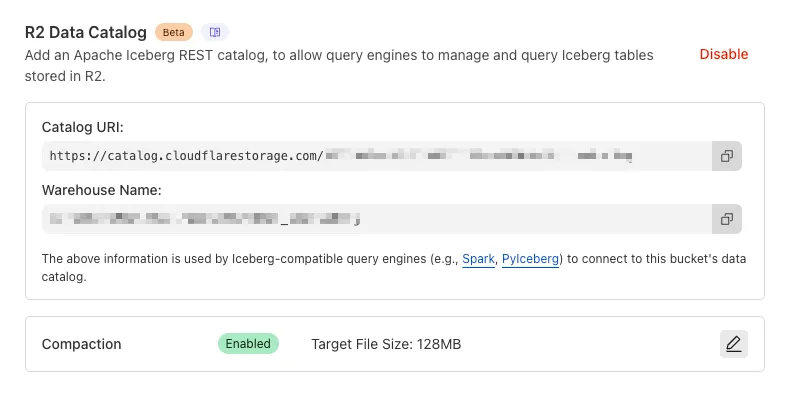
Or with [Wrangler](https://developers.cloudflare.com/workers/wrangler/), run:
```bash
npx wrangler r2 bucket catalog compaction enable --target-size 128 --token
```
To get started with compaction, check out [manage catalogs](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/). For best practices and limitations, refer to [about compaction](https://developers.cloudflare.com/r2/data-catalog/table-maintenance/).
Sep 23, 2025
1. ### [Invalid Submissions Feedback](https://developers.cloudflare.com/changelog/2025-09-23-invalid-submissions/)
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
Email security relies on your submissions to continuously improve our detection models. However, we often receive submissions in formats that cannot be ingested, such as incomplete EMLs, screenshots, or text files.
To ensure all customer feedback is actionable, we have launched two new features to manage invalid submissions sent to our team and user [submission aliases](https://developers.cloudflare.com/cloudflare-one/email-security/settings/phish-submissions/submission-addresses/):
* **Email Notifications:** We now automatically notify users by email when they provide an invalid submission, educating them on the correct format. To disable notifications, go to **[Settings](https://one.dash.cloudflare.com/?to=/:account/email-security/settings)** > **Invalid submission emails** and turn the feature off.
* **Invalid Submission dashboard:** You can quickly identify which users need education to provide valid submissions so Cloudflare can provide continuous protection.
Learn more about this feature on [invalid submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/invalid-submissions/).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
Sep 22, 2025
1. ### [Access Remote Desktop Protocol (RDP) destinations securely from your browser — now generally available!](https://developers.cloudflare.com/changelog/2025-09-22-browser-based-rdp-ga/)
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Browser-based RDP](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/) with [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) is now generally available for all Cloudflare customers. It enables secure, remote Windows server access without VPNs or RDP clients.
Since we announced our [open beta](https://developers.cloudflare.com/changelog/access/#2025-06-30), we've made a few improvements:
* Support for targets with IPv6.
* Support for [Magic WAN](https://developers.cloudflare.com/magic-wan/) and [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) as on-ramps.
* More robust error messaging on the login page to help you if you encounter an issue.
* Worldwide keyboard support. Whether your day-to-day is in Portuguese, Chinese, or something in between, your browser-based RDP experience will look and feel exactly like you are using a desktop RDP client.
* Cleaned up some other miscellaneous issues, including but not limited to enhanced support for Entra ID accounts and support for usernames with spaces, quotes, and special characters.
As a refresher, here are some benefits browser-based RDP provides:
* **Control how users authenticate to internal RDP resources** with single sign-on (SSO), multi-factor authentication (MFA), and granular access policies.
* **Record who is accessing which servers and when** to support regulatory compliance requirements and to gain greater visibility in the event of a security event.
* **Eliminate the need to install and manage software on user devices**. You will only need a web browser.
* **Reduce your attack surface** by keeping your RDP servers off the public Internet and protecting them from common threats like credential stuffing or brute-force attacks.
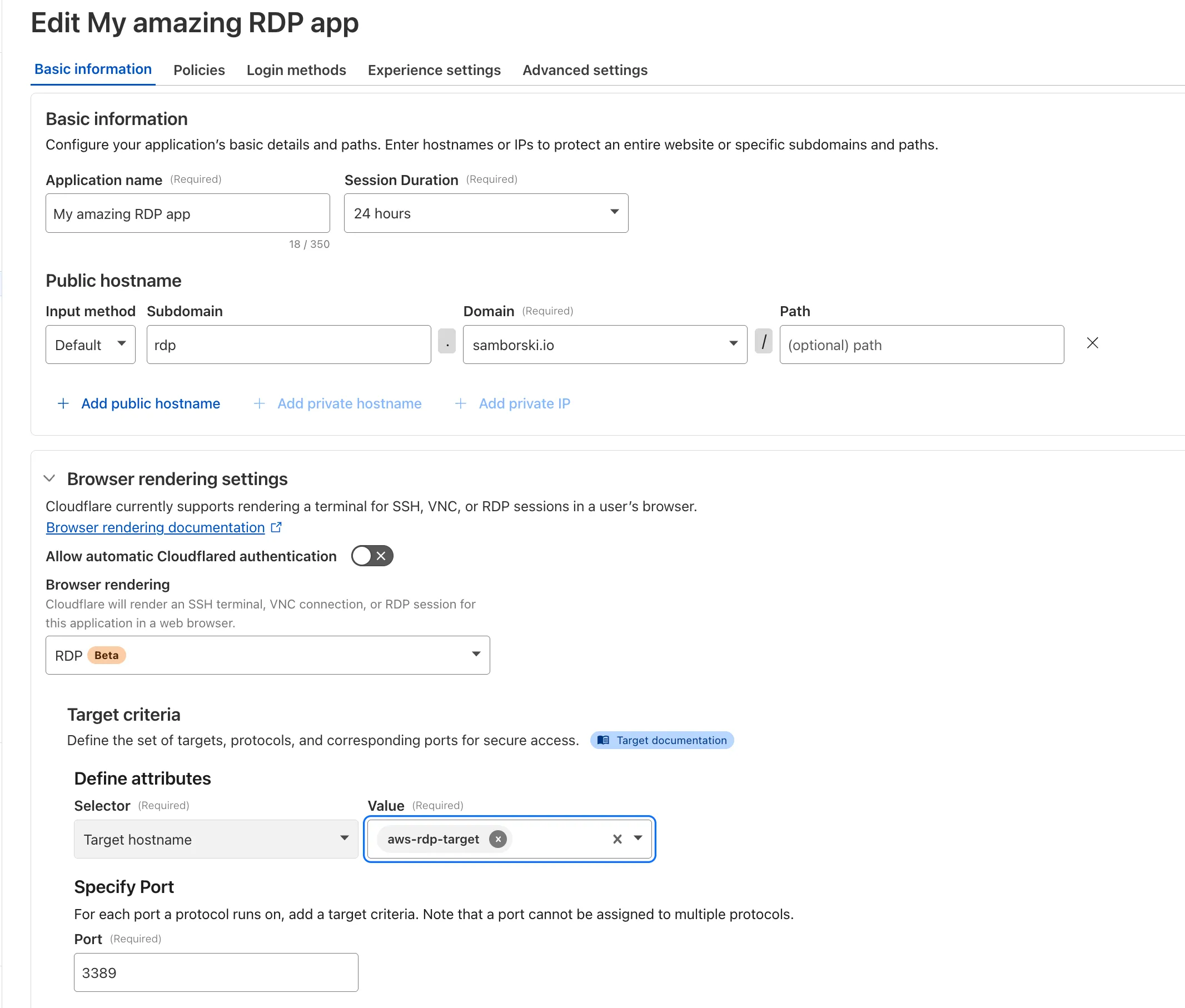
To get started, refer to [Connect to RDP in a browser](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/).
Sep 18, 2025
1. ### [Connect and secure any private or public app by hostname, not IP — with hostname routing for Cloudflare Tunnel](https://developers.cloudflare.com/changelog/2025-09-18-tunnel-hostname-routing/)
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
You can now route private traffic to [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) based on a hostname or domain, moving beyond the limitations of IP-based routing. This new capability is **free for all Cloudflare One customers**.
Previously, Tunnel routes could only be defined by IP address or [CIDR range](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/connect-cidr/). This created a challenge for modern applications with dynamic or ephemeral IP addresses, often forcing administrators to maintain complex and brittle IP lists.
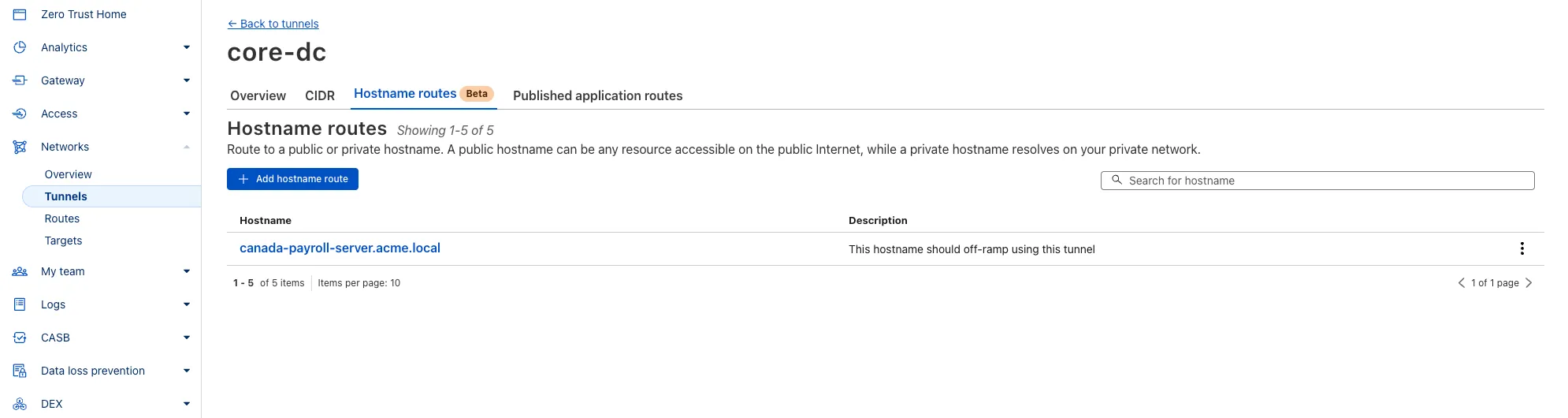
**What’s new:**
* **Hostname & Domain Routing**: Create routes for individual hostnames (e.g., `payroll.acme.local`) or entire domains (e.g., `*.acme.local`) and direct their traffic to a specific Tunnel.
* **Simplified Zero Trust Policies**: Build resilient policies in Cloudflare Access and Gateway using stable hostnames, making it dramatically easier to apply per-resource authorization for your private applications.
* **Precise Egress Control**: Route traffic for public hostnames (e.g., `bank.example.com`) through a specific Tunnel to enforce a dedicated source IP, solving the IP allowlist problem for third-party services.
* **No More IP Lists**: This feature makes the workaround of maintaining dynamic IP Lists for Tunnel connections obsolete.
Get started in the Tunnels section of the Zero Trust dashboard with your first [private hostname](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/connect-private-hostname/) or [public hostname](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/egress-cloudflared/) route.
Learn more in our [blog post](https://blog.cloudflare.com/tunnel-hostname-routing/).
Sep 16, 2025
1. ### [New AI-Enabled Search for Zero Trust Dashboard](https://developers.cloudflare.com/changelog/2025-09-16-new-ai-enabled-search-for-zero-trust-dashboard/)
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust Dashboard has a brand new, AI-powered search functionality. You can search your account by resources (applications, policies, device profiles, settings, etc.), pages, products, and more.
**Ask Cloudy** — You can also ask Cloudy, our AI agent, questions about Cloudflare Zero Trust. Cloudy is trained on our developer documentation and implementation guides, so it can tell you how to configure functionality, best practices, and can make recommendations.
Cloudy can then stay open with you as you move between pages to build configuration or answer more questions.
**Find Recents** — Recent searches and Cloudy questions also have a new tab under Zero Trust Overview.
Sep 16, 2025
1. ### [DNS Firewall Analytics — now in the Cloudflare dashboard](https://developers.cloudflare.com/changelog/2025-09-16-dnsfw-analytics-ui/)
[DNS](https://developers.cloudflare.com/dns/)
#### What's New
Access [GraphQL-powered DNS Firewall analytics](https://developers.cloudflare.com/dns/dns-firewall/analytics/) directly in the Cloudflare dashboard.
#### Explore Four Interactive Panels
* **Query summary**: Describes trends over time, segmented by dimensions.
* **Query statistics**: Describes totals, cached/uncached queries, and processing/response times.
* **DNS queries by data center**: Describes global view and the top 10 data centers.
* **Top query statistics**: Shows a breakdown by key dimensions, with search and expand options (up to top 100 items).
Additional features:
* Apply filters and time ranges once. Changes reflect across all panels.
* Filter by dimensions like query name, query type, cluster, data center, protocol (UDP/TCP), IP version, response code/reason, and more.
* Access up to 62 days of historical data with flexible intervals.
#### Availability
Available to all DNS Firewall customers as part of their existing subscription.
#### Where to Find It
* In the Cloudflare dashboard, go to the **DNS Firewall** page.
[Go to **Analytics**](https://dash.cloudflare.com/?to=/:account/dns-firewall/analytics)
* Refer to the [DNS Firewall Analytics](https://developers.cloudflare.com/dns/dns-firewall/analytics/) to learn more.
Sep 11, 2025
1. ### [D1 automatically retries read-only queries](https://developers.cloudflare.com/changelog/2025-09-11-d1-automatic-read-retries/)
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
D1 now detects read-only queries and automatically attempts up to two retries to execute those queries in the event of failures with retryable errors. You can access the number of execution attempts in the returned [response metadata](https://developers.cloudflare.com/d1/worker-api/return-object/#d1result) property `total_attempts`.
At the moment, only read-only queries are retried, that is, queries containing only the following SQLite keywords: `SELECT`, `EXPLAIN`, `WITH`. Queries containing any [SQLite keyword](https://sqlite.org/lang_keywords.html) that leads to database writes are not retried.
The retry success ratio among read-only retryable errors varies from 5% all the way up to 95%, depending on the underlying error and its duration (like network errors or other internal errors).
The retry success ratio among all retryable errors is lower, indicating that there are write-queries that could be retried. Therefore, we recommend D1 users to continue applying [retries in their own code](https://developers.cloudflare.com/d1/best-practices/retry-queries/) for queries that are not read-only but are idempotent according to the business logic of the application.

D1 ensures that any retry attempt does not cause database writes, making the automatic retries safe from side-effects, even if a query causing changes slips through the read-only detection. D1 achieves this by checking for modifications after every query execution, and if any write occurred due to a retry attempt, the query is rolled back.
The read-only query detection heuristics are simple for now, and there is room for improvement to capture more cases of queries that can be retried, so this is just the beginning.
Sep 11, 2025
1. ### [DNS filtering for private network onramps](https://developers.cloudflare.com/changelog/2025-09-11-dns-filtering-for-private-network-onramps/)
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
[Magic WAN](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-gateway/#dns-filtering) and [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/site-to-internet/#configure-dns-resolver-on-devices) users can now securely route their DNS traffic to the Gateway resolver without exposing traffic to the public Internet.
Routing DNS traffic to the Gateway resolver allows DNS resolution and filtering for traffic coming from private networks while preserving source internal IP visibility. This ensures Magic WAN users have full integration with our Cloudflare One features, including [Internal DNS](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/#internal-dns) and [hostname-based policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/#selector-prerequisites).
To configure DNS filtering, change your Magic WAN or WARP Connector DNS settings to use Cloudflare's shared resolver IPs, `172.64.36.1` and `172.64.36.2`. Once you configure DNS resolution and filtering, you can use *Source Internal IP* as a traffic selector in your [resolver policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/) for routing private DNS traffic to your [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/).
Sep 10, 2025
1. ### [Agents SDK v0.1.0 and workers-ai-provider v2.0.0 with AI SDK v5 support](https://developers.cloudflare.com/changelog/2025-09-03-agents-sdk-beta-v5/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We've shipped a new release for the [Agents SDK](https://github.com/cloudflare/agents) bringing full compatibility with [AI SDK v5](https://ai-sdk.dev/docs/introduction) and introducing automatic message migration that handles all legacy formats transparently.
This release includes improved streaming and tool support, tool confirmation detection (for "human in the loop" systems), enhanced React hooks with automatic tool resolution, improved error handling for streaming responses, and seamless migration utilities that work behind the scenes.
This makes it ideal for building production AI chat interfaces with Cloudflare Workers AI models, agent workflows, human-in-the-loop systems, or any application requiring reliable message handling across SDK versions — all while maintaining backward compatibility.
Additionally, we've updated workers-ai-provider v2.0.0, the official provider for Cloudflare Workers AI models, to be compatible with AI SDK v5.
#### useAgentChat(options)
Creates a new chat interface with enhanced v5 capabilities.
```ts
// Basic chat setup
const { messages, sendMessage, addToolResult } = useAgentChat({
agent,
experimental_automaticToolResolution: true,
tools,
});
// With custom tool confirmation
const chat = useAgentChat({
agent,
experimental_automaticToolResolution: true,
toolsRequiringConfirmation: ["dangerousOperation"],
});
```
#### Automatic Tool Resolution
Tools are automatically categorized based on their configuration:
```ts
const tools = {
// Auto-executes (has execute function)
getLocalTime: {
description: "Get current local time",
inputSchema: z.object({}),
execute: async () => new Date().toLocaleString(),
},
// Requires confirmation (no execute function)
deleteFile: {
description: "Delete a file from the system",
inputSchema: z.object({
filename: z.string(),
}),
},
// Server-executed (no client confirmation)
analyzeData: {
description: "Analyze dataset on server",
inputSchema: z.object({ data: z.array(z.number()) }),
serverExecuted: true,
},
} satisfies Record;
```
#### Message Handling
Send messages using the new v5 format with parts array:
```ts
// Text message
sendMessage({
role: "user",
parts: [{ type: "text", text: "Hello, assistant!" }],
});
// Multi-part message with file
sendMessage({
role: "user",
parts: [
{ type: "text", text: "Analyze this image:" },
{ type: "image", image: imageData },
],
});
```
#### Tool Confirmation Detection
Simplified logic for detecting pending tool confirmations:
```ts
const pendingToolCallConfirmation = messages.some((m) =>
m.parts?.some(
(part) => isToolUIPart(part) && part.state === "input-available",
),
);
// Handle tool confirmation
if (pendingToolCallConfirmation) {
await addToolResult({
toolCallId: part.toolCallId,
tool: getToolName(part),
output: "User approved the action",
});
}
```
#### Automatic Message Migration
Seamlessly handle legacy message formats without code changes.
```ts
// All these formats are automatically converted:
// Legacy v4 string content
const legacyMessage = {
role: "user",
content: "Hello world",
};
// Legacy v4 with tool calls
const legacyWithTools = {
role: "assistant",
content: "",
toolInvocations: [
{
toolCallId: "123",
toolName: "weather",
args: { city: "SF" },
state: "result",
result: "Sunny, 72°F",
},
],
};
// Automatically becomes v5 format:
// {
// role: "assistant",
// parts: [{
// type: "tool-call",
// toolCallId: "123",
// toolName: "weather",
// args: { city: "SF" },
// state: "result",
// result: "Sunny, 72°F"
// }]
// }
```
#### Tool Definition Updates
Migrate tool definitions to use the new `inputSchema` property.
```ts
// Before (AI SDK v4)
const tools = {
weather: {
description: "Get weather information",
parameters: z.object({
city: z.string(),
}),
execute: async (args) => {
return await getWeather(args.city);
},
},
};
// After (AI SDK v5)
const tools = {
weather: {
description: "Get weather information",
inputSchema: z.object({
city: z.string(),
}),
execute: async (args) => {
return await getWeather(args.city);
},
},
};
```
#### Cloudflare Workers AI Integration
Seamless integration with Cloudflare Workers AI models through the updated workers-ai-provider v2.0.0.
#### Model Setup with Workers AI
Use Cloudflare Workers AI models directly in your agent workflows:
```ts
import { createWorkersAI } from "workers-ai-provider";
import { useAgentChat } from "agents/ai-react";
// Create Workers AI model (v2.0.0 - same API, enhanced v5 internals)
const model = createWorkersAI({
binding: env.AI,
})("@cf/meta/llama-3.2-3b-instruct");
```
#### Enhanced File and Image Support
Workers AI models now support v5 file handling with automatic conversion:
```ts
// Send images and files to Workers AI models
sendMessage({
role: "user",
parts: [
{ type: "text", text: "Analyze this image:" },
{
type: "file",
data: imageBuffer,
mediaType: "image/jpeg",
},
],
});
// Workers AI provider automatically converts to proper format
```
#### Streaming with Workers AI
Enhanced streaming support with automatic warning detection:
```ts
// Streaming with Workers AI models
const result = await streamText({
model: createWorkersAI({ binding: env.AI })("@cf/meta/llama-3.2-3b-instruct"),
messages,
onChunk: (chunk) => {
// Enhanced streaming with warning handling
console.log(chunk);
},
});
```
#### Import Updates
Update your imports to use the new v5 types:
```ts
// Before (AI SDK v4)
import type { Message } from "ai";
import { useChat } from "ai/react";
// After (AI SDK v5)
import type { UIMessage } from "ai";
// or alias for compatibility
import type { UIMessage as Message } from "ai";
import { useChat } from "@ai-sdk/react";
```
#### Resources
* [Migration Guide](https://github.com/cloudflare/agents/blob/main/docs/migration-to-ai-sdk-v5.md) - Comprehensive migration documentation
* [AI SDK v5 Documentation](https://ai-sdk.dev/docs/migration-guides/migration-guide-5-0) - Official AI SDK migration guide
* [An Example PR showing the migration from AI SDK v4 to v5](https://github.com/cloudflare/agents-starter/pull/105)
* [GitHub Issues](https://github.com/cloudflare/agents/issues) - Report bugs or request features
#### Feedback Welcome
We'd love your feedback! We're particularly interested in feedback on:
* **Migration experience** - How smooth was the upgrade process?
* **Tool confirmation workflow** - Does the new automatic detection work as expected?
* **Message format handling** - Any edge cases with legacy message conversion?
Sep 08, 2025
1. ### [Custom IKE ID for IPsec Tunnels](https://developers.cloudflare.com/changelog/2025-09-08-custom-ike-id-ipsec-tunnels/)
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Now, Magic WAN customers can configure a custom IKE ID for their IPsec tunnels. Customers that are using Magic WAN and a VeloCloud SD-WAN device together can utilize this new feature to create a high availability configuration.
This feature is available via API only. Customers can read the Magic WAN documentation to learn more about the [Custom IKE ID feature and the API call to configure it](https://developers.cloudflare.com/magic-wan/configuration/common-settings/custom-ike-id-ipsec/).
Sep 05, 2025
1. ### [Bidirectional tunnel health checks are compatible with all Magic on-ramps](https://developers.cloudflare.com/changelog/2025-09-05-bidirectional-health-check-any-on-ramp/)
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
All bidirectional tunnel health check return packets are accepted by any Magic on-ramp.
Previously, when a Magic tunnel had a bidirectional health check configured, the bidirectional health check would pass when the return packets came back to Cloudflare over the same tunnel that was traversed by the forward packets.
There are SD-WAN devices, like VeloCloud, that do not offer controls to steer traffic over one tunnel versus another in a high availability tunnel configuration.
Now, when a Magic tunnel has a bidirectional health check configured, the bidirectional health check will pass when the return packet traverses over any tunnel in a high availability configuration.
Sep 04, 2025
1. ### [Increased static asset limits for Workers](https://developers.cloudflare.com/changelog/2025-09-02-increased-static-asset-limits/)
[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
You can now upload up to **100,000 static assets** per Worker version
* Paid and Workers for Platforms users can now upload up to **100,000 static assets** per Worker version, a 5x increase from the previous limit of 20,000.
* Customers on the free plan still have the same limit as before — 20,000 static assets per version of your Worker
* The individual file size limit of 25 MiB remains unchanged for all customers.
This increase allows you to build larger applications with more static assets without hitting limits.
#### Wrangler
To take advantage of the increased limits, you must use **Wrangler version 4.34.0 or higher**. Earlier versions of Wrangler will continue to enforce the previous 20,000 file limit.
#### Learn more
For more information about Workers static assets, see the [Static Assets documentation](https://developers.cloudflare.com/workers/static-assets/) and [Platform Limits](https://developers.cloudflare.com/workers/platform/limits/#static-assets).
Sep 02, 2025
1. ### [Cloudflare Tunnel and Networks API will no longer return deleted resources by default starting December 1, 2025](https://developers.cloudflare.com/changelog/2025-09-02-tunnel-networks-list-endpoints-new-default/)
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
Starting **December 1, 2025**, list endpoints for the [Cloudflare Tunnel API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/) and [Zero Trust Networks API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/) will no longer return deleted tunnels, routes, subnets and virtual networks by default. This change makes the API behavior more intuitive by only returning active resources unless otherwise specified.
No action is required if you already explicitly set `is_deleted=false` or if you only need to list active resources.
This change affects the following API endpoints:
* List all tunnels: [`GET /accounts/{account_id}/tunnels`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/methods/list/)
* List [Cloudflare Tunnels](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/): [`GET /accounts/{account_id}/cfd_tunnel`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/subresources/cloudflared/methods/list/)
* List [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) tunnels: [`GET /accounts/{account_id}/warp_connector`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/subresources/warp_connector/methods/list/)
* List tunnel routes: [`GET /accounts/{account_id}/teamnet/routes`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/routes/methods/list/)
* List subnets: [`GET /accounts/{account_id}/zerotrust/subnets`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/subnets/methods/list/)
* List virtual networks: [`GET /accounts/{account_id}/teamnet/virtual_networks`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/virtual_networks/methods/list/)
#### What is changing?
The default behavior of the `is_deleted` query parameter will be updated.
| Scenario | Previous behavior (before December 1, 2025) | New behavior (from December 1, 2025) |
| - | - | - |
| `is_deleted` parameter is omitted | Returns **active & deleted** tunnels, routes, subnets and virtual networks | Returns **only active** tunnels, routes, subnets and virtual networks |
#### Action required
If you need to retrieve deleted (or all) resources, please update your API calls to explicitly include the `is_deleted` parameter before **December 1, 2025**.
To get a list of only deleted resources, you must now explicitly add the `is_deleted=true` query parameter to your request:
```bash
# Example: Get ONLY deleted Tunnels
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/tunnels?is_deleted=true" \
-H "Authorization: Bearer $API_TOKEN"
# Example: Get ONLY deleted Virtual Networks
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/teamnet/virtual_networks?is_deleted=true" \
-H "Authorization: Bearer $API_TOKEN"
```
Following this change, retrieving a complete list of both active and deleted resources will require two separate API calls: one to get active items (by omitting the parameter or using `is_deleted=false`) and one to get deleted items (`is_deleted=true`).
#### Why we’re making this change
This update is based on user feedback and aims to:
* **Create a more intuitive default:** Aligning with common API design principles where list operations return only active resources by default.
* **Reduce unexpected results:** Prevents users from accidentally operating on deleted resources that were returned unexpectedly.
* **Improve performance:** For most users, the default query result will now be smaller and more relevant.
To learn more, please visit the [Cloudflare Tunnel API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/) and [Zero Trust Networks API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/) documentation.
Aug 29, 2025
1. ### [Smart Tiered Cache Fallback to Generic](https://developers.cloudflare.com/changelog/2025-08-29-smart-tiered-cache-fallback-to-generic/)
[Cache / CDN](https://developers.cloudflare.com/cache/)
[Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#smart-tiered-cache) now falls back to [Generic Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#generic-global-tiered-cache) when the origin location cannot be determined, improving cache precision for your content.
Previously, when Smart Tiered Cache was unable to select the optimal upper tier (such as when origins are masked by Anycast IPs), latency could be negatively impacted. This fallback now uses Generic Tiered Cache instead, providing better performance and cache efficiency.
#### How it works
When Smart Tiered Cache falls back to Generic Tiered Cache:
1. **Multiple upper-tiers**: Uses all of Cloudflare's global data centers as a network of upper-tiers instead of a single optimal location.
2. **Distributed cache requests**: Lower-tier data centers can query any available upper-tier for cached content.
3. **Improved global coverage**: Provides better cache hit ratios across geographically distributed visitors.
4. **Automatic fallback**: Seamlessly transitions when origin location cannot be determined, such as with Anycast-masked origins.
#### Benefits
* **Preserves high performance during fallback**: Smart Tiered Cache now maintains strong cache efficiency even when optimal upper tier selection is not possible.
* **Minimizes latency impact**: Automatically uses Generic Tiered Cache topology to keep performance high when origin location cannot be determined.
* **Seamless experience**: No configuration changes or intervention required when fallback occurs.
* **Improved resilience**: Smart Tiered Cache remains effective across diverse origin infrastructure, including Anycast-masked origins.
#### Get started
This improvement is automatically applied to all zones using [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/). No action is required on your part.
Aug 29, 2025
1. ### [DEX MCP Server](https://developers.cloudflare.com/changelog/2025-08-29-dex-mcp-server/)
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into device connectivity and performance across your Cloudflare SASE deployment.
We've released an MCP server [(Model Context Protocol)](https://cloudflare.com/learning/ai/what-is-model-context-protocol-mcp/) for DEX.
The DEX MCP server is an AI tool that allows customers to ask a question like, "Show me the connectivity and performance metrics for the device used by carly@acme.com", and receive an answer that contains data from the DEX API.
Any Cloudflare One customer using a Free, PayGo, or Enterprise account can access the DEX MCP Server. This feature is available to everyone.
Customers can test the new DEX MCP server in less than one minute. To learn more, read the [DEX MCP server documentation](https://developers.cloudflare.com/cloudflare-one/insights/dex/dex-mcp-server/).
Aug 29, 2025
1. ### [Terraform v5.9 now available](https://developers.cloudflare.com/changelog/2025-08-29-terrform-v59-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a 2 week cadence to ensure its stability and reliability, including the v5.9 release. We have also pivoted from an issue-to-issue approach to a resource-per-resource approach - we will be focusing on specific resources for every release, stabilizing the release, and closing all associated bugs with that resource before moving onto resolving migration issues.
Thank you for continuing to raise issues. We triage them weekly and they help make our products stronger.
This release includes a new resource, `cloudflare_snippet`, which replaces `cloudflare_snippets`. `cloudflare_snippet` is now considered deprecated but can still be used. Please utilize `cloudflare_snippet` as soon as possible.
#### Changes
* Resources stabilized:
* `cloudflare_zone_setting`
* `cloudflare_worker_script`
* `cloudflare_worker_route`
* `tiered_cache`
* **NEW** resource `cloudflare_snippet` which should be used in place of `cloudflare_snippets`. `cloudflare_snippets` is now deprecated. This enables the management of Cloudflare's snippet functionality through Terraform.
* DNS Record Improvements: Enhanced handling of DNS record drift detection
* Load Balancer Fixes: Resolved `created_on` field inconsistencies and improved pool configuration handling
* Bot Management: Enhanced auto-update model state consistency and fight mode configurations
* Other bug fixes
For a more detailed look at all of the changes, refer to the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.9.0) in GitHub.
#### Issues Closed
* [#5921: In cloudflare\_ruleset removing an existing rule causes recreation of later rules](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5921)
* [#5904: cloudflare\_zero\_trust\_access\_application is not idempotent](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5904)
* [#5898: (cloudflare\_workers\_script) Durable Object migrations not applied](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5898)
* [#5892: cloudflare\_workers\_script secret\_text environment variable gets replaced on every deploy](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5892)
* [#5891: cloudflare\_zone suddenly started showing drift](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5891)
* [#5882: cloudflare\_zero\_trust\_list always marked for change due to read only attributes](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5882)
* [#5879: cloudflare\_zero\_trust\_gateway\_certificate unable to manage resource (cant mark as active/inactive)](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5879)
* [#5858: cloudflare\_dns\_records is always updated in-place](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5858)
* [#5839: Recurring change on cloudflare\_zero\_trust\_gateway\_policy after upgrade to V5 provider & also setting expiration fails](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5839)
* [#5811: Reusable policies are imported as inline type for cloudflare\_zero\_trust\_access\_application](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5811)
* [#5795: cloudflare\_zone\_setting inconsistent value of "editable" upon apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5795)
* [#5789: Pagination issue fetching all policies in "cloudflare\_zero\_trust\_access\_policies" data source](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5789)
* [#5770: cloudflare\_zero\_trust\_access\_application type warp diff on every apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5770)
* [#5765: V5 / cloudflare\_zone\_dnssec fails with HTTP/400 "Malformed request body"](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5765)
* [#5755: Unable to manage Cloudflare managed WAF rules via Terraform](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5755)
* [#5738: v4 to v5 upgrade failing Error: no schema available AND Unable to Read Previously Saved State for UpgradeResourceState](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5738)
* [#5727: cloudflare\_ruleset http\_request\_cache\_settings bypass mismatch between dashboard and terraform](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5727)
* [#5700: cloudflare\_account\_member invalid type 'string' for field 'roles'](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5700)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new issue if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding off on migration to v5 while we work on stabilization. This help will you avoid any blocking issues while the Terraform resources are actively being stabilized.
If you'd like more information on migrating from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition. These do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
* [GitHub Repository](https://github.com/cloudflare/terraform-provider-cloudflare)
Aug 27, 2025
1. ### [Shadow IT - SaaS analytics dashboard](https://developers.cloudflare.com/changelog/2025-08-27-shadow-it-analytics/)
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust has significantly upgraded its **Shadow IT analytics**, providing you with unprecedented visibility into your organizations use of SaaS tools. With this dashboard, you can review who is using an application and volumes of data transfer to the application.
You can review these metrics against application type, such as Artificial Intelligence or Social Media. You can also mark applications with an approval status, including **Unreviewed**, **In Review**, **Approved**, and **Unapproved** designating how they can be used in your organization.

These application statuses can also be used in Gateway HTTP policies, so you can block, isolate, limit uploads and downloads, and more based on the application status.
Both the analytics and policies are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
Aug 26, 2025
1. ### [New CASB integrations for ChatGPT, Claude, and Gemini](https://developers.cloudflare.com/changelog/2025-08-26-casb-ai-integrations/)
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
[Cloudflare CASB](https://www.cloudflare.com/zero-trust/products/casb/) now supports three of the most widely used GenAI platforms — **OpenAI ChatGPT**, **Anthropic Claude**, and **Google Gemini**. These API-based integrations give security teams agentless visibility into posture, data, and compliance risks across their organization’s use of generative AI.
#### Key capabilities
* **Agentless connections** — connect ChatGPT, Claude, and Gemini tenants via API; no endpoint software required
* **Posture management** — detect insecure settings and misconfigurations that could lead to data exposure
* **DLP detection** — identify sensitive data in uploaded chat attachments or files
* **GenAI-specific insights** — surface risks unique to each provider’s capabilities
#### Learn more
* [ChatGPT integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/openai/)
* [Claude integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/anthropic/)
* [Gemini integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/google-workspace/gemini/)
These integrations are available to all Cloudflare One customers today.
Aug 26, 2025
1. ### [Manage and restrict access to internal MCP servers with Cloudflare Access](https://developers.cloudflare.com/changelog/2025-08-26-access-mcp-oauth/)
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
You can now control who within your organization has access to internal MCP servers, by putting internal MCP servers behind [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/).
[Self-hosted applications](https://developers.cloudflare.com/cloudflare-one/access-controls/ai-controls/linked-apps/) in Cloudflare Access now support OAuth for MCP server authentication. This allows Cloudflare to delegate access from any self-hosted application to an MCP server via OAuth. The OAuth access token authorizes the MCP server to make requests to your self-hosted applications on behalf of the authorized user, using that user's specific permissions and scopes.
For example, if you have an MCP server designed for internal use within your organization, you can configure Access policies to ensure that only authorized users can access it, regardless of which MCP client they use. Support for internal, self-hosted MCP servers also works with MCP server portals, allowing you to provide a single MCP endpoint for multiple MCP servers. For more on MCP server portals, read the [blog post](https://blog.cloudflare.com/zero-trust-mcp-server-portals/) on the Cloudflare Blog.
Aug 26, 2025
1. ### [List all vectors in a Vectorize index with the new list-vectors operation](https://developers.cloudflare.com/changelog/2025-08-26-vectorize-list-vectors/)
[Vectorize](https://developers.cloudflare.com/vectorize/)
You can now list all vector identifiers in a Vectorize index using the new `list-vectors` operation. This enables bulk operations, auditing, and data migration workflows through paginated requests that maintain snapshot consistency.
The operation is available via Wrangler CLI and REST API. Refer to the [list-vectors best practices guide](https://developers.cloudflare.com/vectorize/best-practices/list-vectors/) for detailed usage guidance.
Aug 25, 2025
1. ### [Manage and deploy your AI provider keys through Bring Your Own Key (BYOK) with AI Gateway, now powered by Cloudflare Secrets Store](https://developers.cloudflare.com/changelog/2025-08-25-secrets-store-ai-gateway/)
[Secrets Store ](https://developers.cloudflare.com/secrets-store/)[AI Gateway ](https://developers.cloudflare.com/ai-gateway/)[SSL/TLS](https://developers.cloudflare.com/ssl/)
Cloudflare Secrets Store is now integrated with AI Gateway, allowing you to store, manage, and deploy your AI provider keys in a secure and seamless configuration through [Bring Your Own Key](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/). Instead of passing your AI provider keys directly in every request header, you can centrally manage each key with Secrets Store and deploy in your gateway configuration using only a reference, rather than passing the value in plain text.
You can now create a secret directly from your AI Gateway [in the dashboard](http://dash.cloudflare.com/?to=/:account/ai-gateway) by navigating into your gateway -> **Provider Keys** -> **Add**.
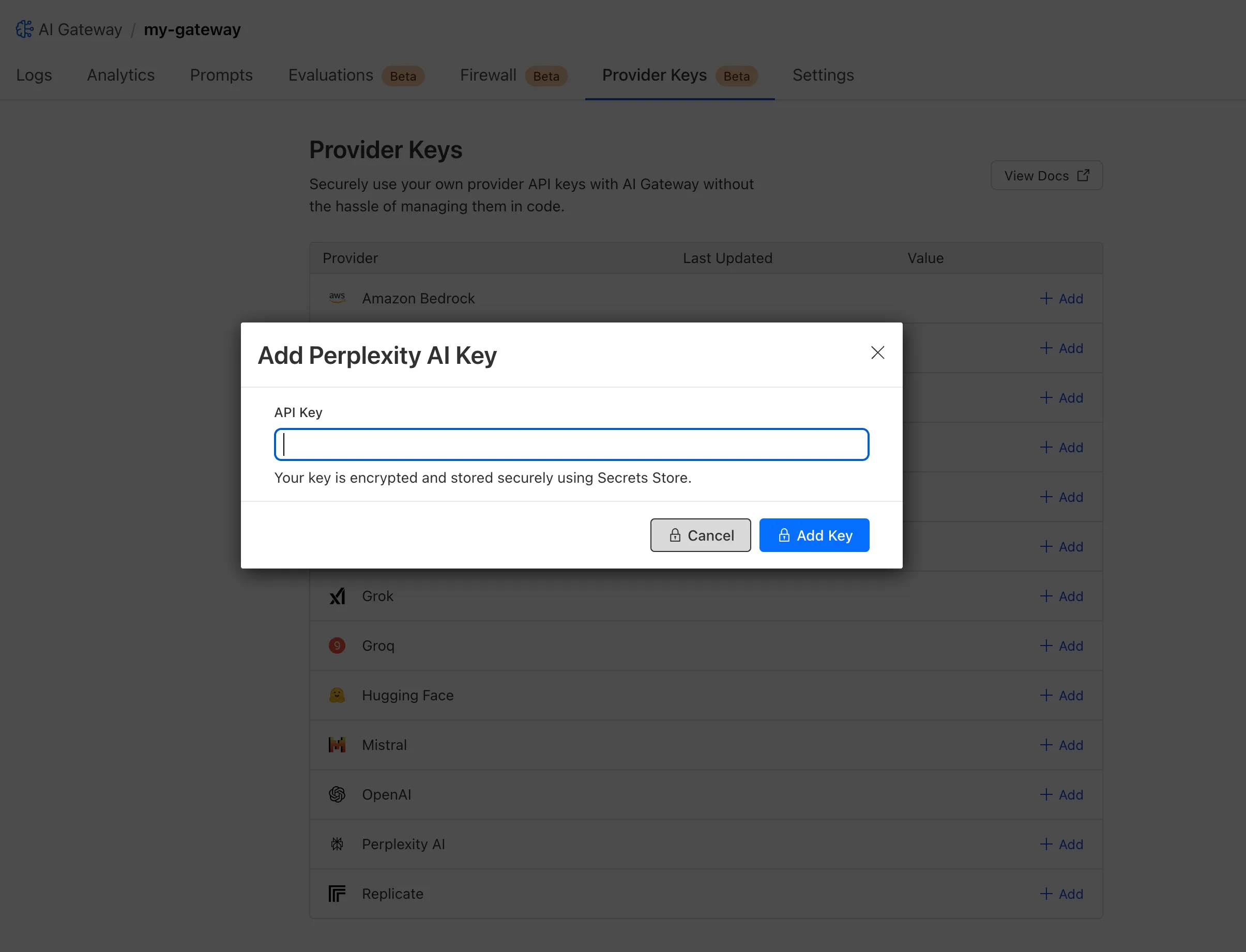
You can also create your secret with the newly available **ai\_gateway** scope via [wrangler](https://developers.cloudflare.com/workers/wrangler/commands/), the [Secrets Store dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store), or the [API](https://developers.cloudflare.com/api/resources/secrets_store/).
Then, pass the key in the request header using its Secrets Store reference:
```plaintext
curl -X POST https://gateway.ai.cloudflare.com/v1//my-gateway/anthropic/v1/messages \
--header 'cf-aig-authorization: ANTHROPIC_KEY_1 \
--header 'anthropic-version: 2023-06-01' \
--header 'Content-Type: application/json' \
--data '{"model": "claude-3-opus-20240229", "messages": [{"role": "user", "content": "What is Cloudflare?"}]}'
```
Or, using Javascript:
```plaintext
import Anthropic from '@anthropic-ai/sdk';
const anthropic = new Anthropic({
apiKey: "ANTHROPIC_KEY_1",
baseURL: "https://gateway.ai.cloudflare.com/v1//my-gateway/anthropic",
});
const message = await anthropic.messages.create({
model: 'claude-3-opus-20240229',
messages: [{role: "user", content: "What is Cloudflare?"}],
max_tokens: 1024
});
```
For more information, check out the [blog](https://blog.cloudflare.com/ai-gateway-aug-2025-refresh)!
Aug 25, 2025
1. ### [New DLP topic based detection entries for AI prompt protection](https://developers.cloudflare.com/changelog/2025-08-25-ai-prompt-protection/)
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You now have access to a comprehensive suite of capabilities to secure your organization's use of generative AI. AI prompt protection introduces four key features that work together to provide deep visibility and granular control.
1. **Prompt Detection for AI Applications**
DLP can now natively detect and inspect user prompts submitted to popular AI applications, including **Google Gemini**, **ChatGPT**, **Claude**, and **Perplexity**.
1. **Prompt Analysis and Topic Classification**
Our DLP engine performs deep analysis on each prompt, applying [topic classification](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics). These topics are grouped into two evaluation categories:
* **Content:** PII, Source Code, Credentials and Secrets, Financial Information, and Customer Data.
* **Intent:** Jailbreak attempts, requests for malicious code, or attempts to extract PII.
To help you apply these topics quickly, we have also released five new predefined profiles (for example, AI Prompt: AI Security, AI Prompt: PII) that bundle these new topics.
1. **Granular Guardrails**
You can now build guardrails using Gateway HTTP policies with [application granular controls](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#application-granular-controls). Apply a DLP profile containing an [AI prompt topic detection](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics) to individual AI applications (for example, `ChatGPT`) and specific user actions (for example, `SendPrompt`) to block sensitive prompts.
2. **Full Prompt Logging**
To aid in incident investigation, an optional setting in your Gateway policy allows you to [capture prompt logs](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#log-generative-ai-prompt-content) to store the full interaction of prompts that trigger a policy match. To make investigations easier, logs can be filtered by `conversation_id`, allowing you to reconstruct the full context of an interaction that led to a policy violation.
AI prompt protection is now available in open beta. To learn more about it, read the [blog](https://blog.cloudflare.com/ai-prompt-protection/#closing-the-loop-logging) or refer to [AI prompt topics](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics).
Aug 22, 2025
1. ### [Workers KV completes hybrid storage provider rollout for improved performance, fault-tolerance](https://developers.cloudflare.com/changelog/2025-08-22-kv-performance-improvements/)
[KV](https://developers.cloudflare.com/kv/)
Workers KV has completed rolling out performance improvements across all KV namespaces, providing a significant latency reduction on read operations for all KV users. This is due to architectural changes to KV's underlying storage infrastructure, which introduces a new metadata later and substantially improves redundancy.
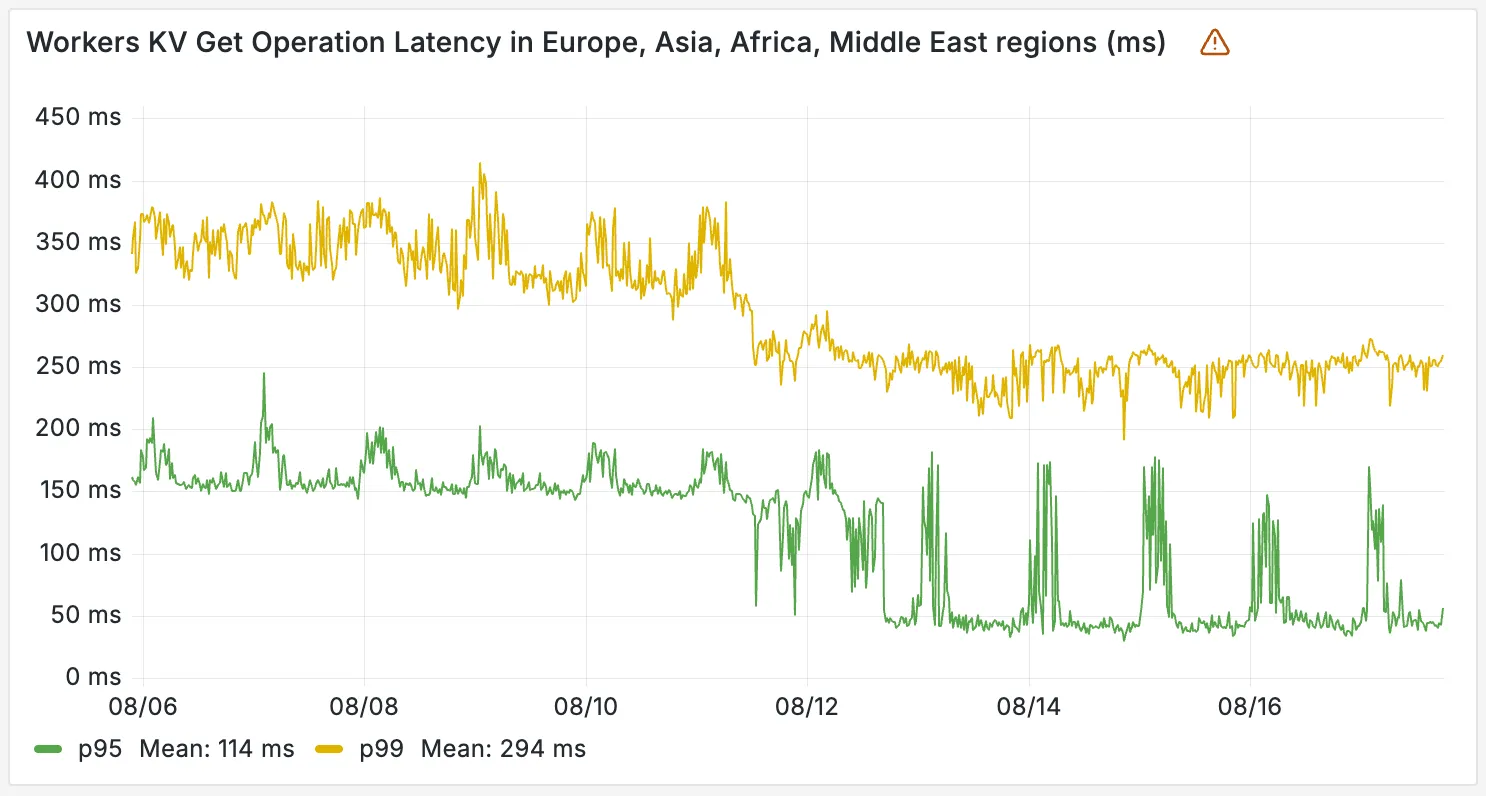
#### Performance improvements
The new hybrid architecture delivers substantial latency reductions throughout Europe, Asia, Middle East, Africa regions. Over the past 2 weeks, we have observed the following:
* **p95 latency**: Reduced from \~150ms to \~50ms (67% decrease)
* **p99 latency**: Reduced from \~350ms to \~250ms (29% decrease)
Aug 22, 2025
1. ### [Audit logs (version 2) - Logpush Beta Release](https://developers.cloudflare.com/changelog/2025-08-22-audit-logs-v2-logpush/)
[Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/)
[Audit Logs v2 dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/audit_logs_v2/) is now available via Logpush.
This expands on earlier releases of Audit Logs v2 in the [API](https://developers.cloudflare.com/changelog/2025-03-27-automatic-audit-logs-beta-release/) and [Dashboard UI](https://developers.cloudflare.com/changelog/2025-07-29-audit-logs-v2-ui-beta/).
We recommend creating a new Logpush job for the Audit Logs v2 dataset.
Timelines for General Availability (GA) of Audit Logs v2 and the retirement of Audit Logs v1 will be shared in upcoming updates.
For more details on Audit Logs v2, refer to the [Audit Logs documentation](https://developers.cloudflare.com/fundamentals/account/account-security/audit-logs/).
Aug 22, 2025
1. ### [Dedicated Egress IP for Logpush](https://developers.cloudflare.com/changelog/2025-08-22-dedicated-egress-ip-logpush/)
[Logs](https://developers.cloudflare.com/logs/)
Cloudflare Logpush can now deliver logs from using fixed, dedicated egress IPs. By routing Logpush traffic through a Cloudflare zone enabled with [Aegis IP](https://developers.cloudflare.com/smart-shield/configuration/dedicated-egress-ips/), your log destination only needs to allow Aegis IPs making setup more secure.
Highlights:
* Fixed egress IPs ensure your destination only accepts traffic from known addresses.
* Works with any supported Logpush destination.
* Recommended to use a dedicated zone as a proxy for easier management.
To get started, work with your Cloudflare account team to provision Aegis IPs, then configure your Logpush job to deliver logs through the proxy zone. For full setup instructions, refer to the [Logpush documentation](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/egress-ip/).
Aug 22, 2025
1. ### [Build durable multi-step applications in Python with Workflows (now in beta)](https://developers.cloudflare.com/changelog/2025-08-22-workflows-python-beta/)
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
You can now build [Workflows](https://developers.cloudflare.com/workflows/) using Python. With Python Workflows, you get automatic retries, state persistence, and the ability to run multi-step operations that can span minutes, hours, or weeks using Python’s familiar syntax and the [Python Workers](https://developers.cloudflare.com/workers/languages/python/) runtime.
Python Workflows use the same step-based execution model as JavaScript Workflows, but with Python syntax and access to Python’s ecosystem. Python Workflows also enable [DAG (Directed Acyclic Graph) workflows](https://developers.cloudflare.com/workflows/python/dag/), where you can define complex dependencies between steps using the depends parameter.
Here’s a simple example:
```python
from workers import Response, WorkflowEntrypoint
class PythonWorkflowStarter(WorkflowEntrypoint):
async def run(self, event, step):
@step.do("my first step")
async def my_first_step():
# do some work
return "Hello Python!"
await my_first_step()
await step.sleep("my-sleep-step", "10 seconds")
@step.do("my second step")
async def my_second_step():
# do some more work
return "Hello again!"
await my_second_step()
class Default(WorkerEntrypoint):
async def fetch(self, request):
await self.env.MY_WORKFLOW.create()
return Response("Hello Workflow creation!")
```
Note
Python Workflows requires a `compatibility_date = "2025-08-01"`, or lower, in your wrangler toml file.
Python Workflows support the same core capabilities as JavaScript Workflows, including sleep scheduling, event-driven workflows, and built-in error handling with configurable retry policies.
To learn more and get started, refer to [Python Workflows documentation](https://developers.cloudflare.com/workflows/python/).
Aug 21, 2025
1. ### [New getByName() API to access Durable Objects](https://developers.cloudflare.com/changelog/2025-08-21-durable-objects-get-by-name/)
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
You can now create a client (a [Durable Object stub](https://developers.cloudflare.com/durable-objects/api/stub/)) to a Durable Object with the new `getByName` method, removing the need to convert Durable Object names to IDs and then create a stub.
```js
// Before: (1) translate name to ID then (2) get a client
const objectId = env.MY_DURABLE_OBJECT.idFromName("foo"); // or .newUniqueId()
const stub = env.MY_DURABLE_OBJECT.get(objectId);
// Now: retrieve client to Durable Object directly via its name
const stub = env.MY_DURABLE_OBJECT.getByName("foo");
// Use client to send request to the remote Durable Object
const rpcResponse = await stub.sayHello();
```
Each Durable Object has a globally-unique name, which allows you to send requests to a specific object from anywhere in the world. Thus, a Durable Object can be used to coordinate between multiple clients who need to work together. You can have billions of Durable Objects, providing isolation between application tenants.
To learn more, visit the Durable Objects [API Documentation](https://developers.cloudflare.com/durable-objects/api/namespace/#getbyname) or the [getting started guide](https://developers.cloudflare.com/durable-objects/get-started/).
Aug 19, 2025
1. ### [Subscribe to events from Cloudflare services with Queues](https://developers.cloudflare.com/changelog/2025-08-19-event-subscriptions/)
[Queues](https://developers.cloudflare.com/queues/)
You can now subscribe to events from other Cloudflare services (for example, [Workers KV](https://developers.cloudflare.com/kv/), [Workers AI](https://developers.cloudflare.com/workers-ai), [Workers](https://developers.cloudflare.com/workers)) and consume those events via [Queues](https://developers.cloudflare.com/queues/), allowing you to build custom workflows, integrations, and logic in response to account activity.

Event subscriptions allow you to receive messages when events occur across your Cloudflare account. Cloudflare products can publish structured events to a queue, which you can then consume with [Workers](https://developers.cloudflare.com/workers/) or [pull via HTTP from anywhere](https://developers.cloudflare.com/queues/configuration/pull-consumers/).
To create a subscription, use the dashboard or [Wrangler](https://developers.cloudflare.com/workers/wrangler/commands/#subscription-create):
```bash
npx wrangler queues subscription create my-queue --source r2 --events bucket.created
```
An event is a structured record of something happening in your Cloudflare account – like a Workers AI batch request being queued, a Worker build completing, or an R2 bucket being created. Events follow a consistent structure:
```json
{
"type": "cf.r2.bucket.created",
"source": {
"type": "r2"
},
"payload": {
"name": "my-bucket",
"location": "WNAM"
},
"metadata": {
"accountId": "f9f79265f388666de8122cfb508d7776",
"eventTimestamp": "2025-07-28T10:30:00Z"
}
}
```
Current [event sources](https://developers.cloudflare.com/queues/event-subscriptions/events-schemas/) include [R2](https://developers.cloudflare.com/r2/), [Workers KV](https://developers.cloudflare.com/kv/), [Workers AI](https://developers.cloudflare.com/workers-ai/), [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/), [Vectorize](https://developers.cloudflare.com/vectorize/), [Super Slurper](https://developers.cloudflare.com/r2/data-migration/super-slurper/), and [Workflows](https://developers.cloudflare.com/workflows/). More sources and events are on the way.
For more information on event subscriptions, available events, and how to get started, refer to our [documentation](https://developers.cloudflare.com/queues/event-subscriptions/).
Aug 15, 2025
1. ### [Steer Traffic by AS Number in Load Balancing Custom Rules](https://developers.cloudflare.com/changelog/2025-08-15-asnum-support-in-custom-rules/)
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
You can now create more granular, network-aware Custom Rules in Cloudflare Load Balancing using the Autonomous System Number (ASN) of an incoming request.
This allows you to steer traffic with greater precision based on the network source of a request. For example, you can route traffic from specific Internet Service Providers (ISPs) or enterprise customers to dedicated infrastructure, optimize performance, or enforce compliance by directing certain networks to preferred data centers.
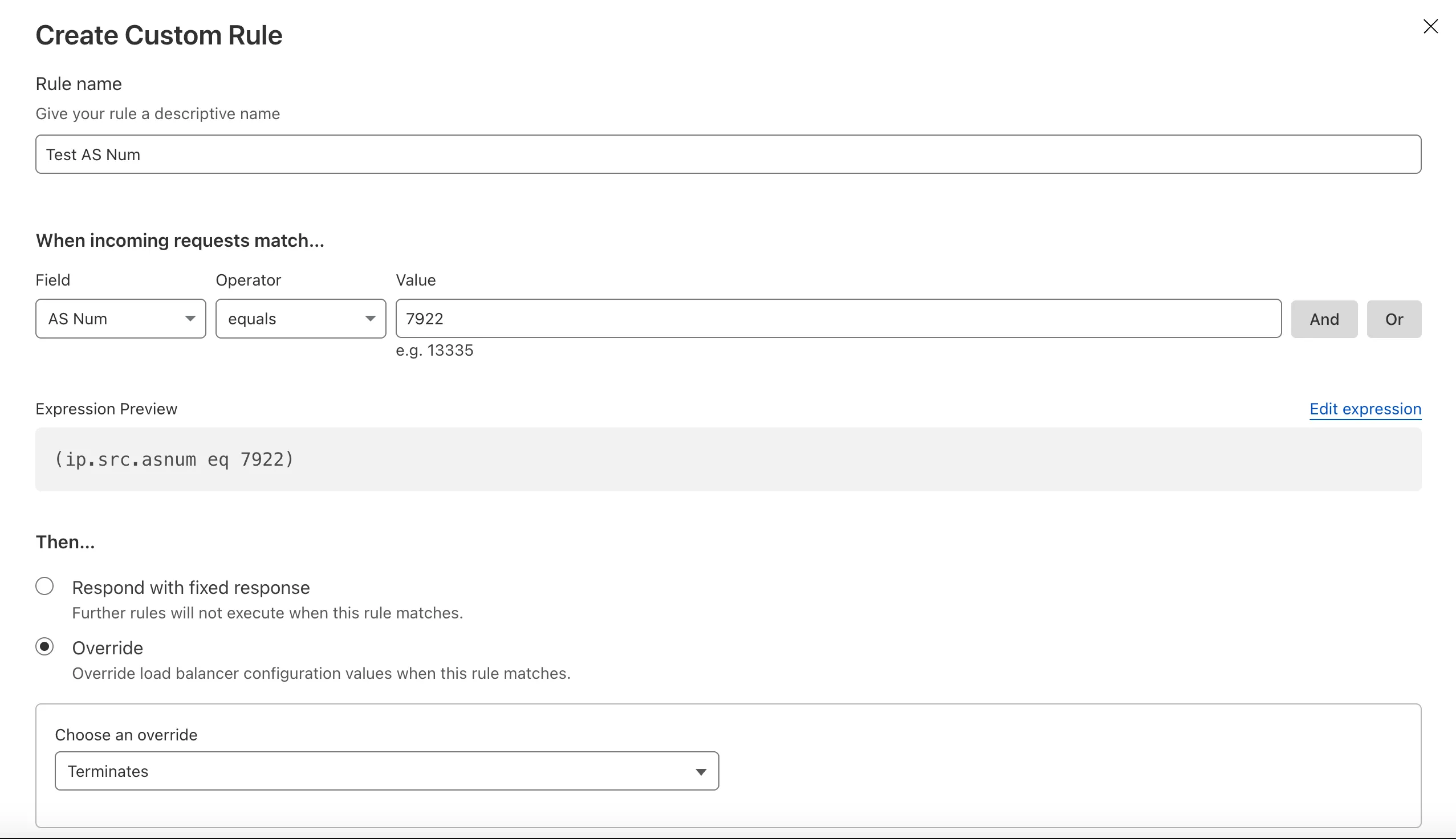
To get started, create a [Custom Rule](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-rules/) in your Load Balancer and select **AS Num** from the **Field** dropdown.
Aug 15, 2025
1. ### [Terraform v5.8.4 now available](https://developers.cloudflare.com/changelog/2025-08-15-terraform-v584-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare Community related to the v5 release. We have committed to releasing improvements on a two week cadence to ensure stability and reliability.
One key change we adopted in recent weeks is a pivot to more comprehensive, test-driven development. We are still evaluating individual issues, but are also investing in much deeper testing to drive our stabilization efforts. We will subsequently be investing in comprehensive migration scripts. As a result, you will see several of the highest traffic APIs have been stabilized in the most recent release, and are supported by comprehensive acceptance tests.
Thank you for continuing to raise issues. We triage them weekly and they help make our products stronger.
#### Changes
* Resources stabilized:
* `cloudflare_argo_smart_routing`
* `cloudflare_bot_management`
* `cloudflare_list`
* `cloudflare_list_item`
* `cloudflare_load_balancer`
* `cloudflare_load_balancer_monitor`
* `cloudflare_load_balancer_pool`
* `cloudflare_spectrum_application`
* `cloudflare_managed_transforms`
* `cloudflare_url_normalization_settings`
* `cloudflare_snippet`
* `cloudflare_snippet_rules`
* `cloudflare_zero_trust_access_application`
* `cloudflare_zero_trust_access_group`
* `cloudflare_zero_trust_access_identity_provider`
* `cloudflare_zero_trust_access_mtls_certificate`
* `cloudflare_zero_trust_access_mtls_hostname_settings`
* `cloudflare_zero_trust_access_policy`
* `cloudflare_zone`
* Multipart handling restored for `cloudflare_snippet`
* `cloudflare_bot_management` diff issues resolves when running `terraform plan` and `terraform apply`
* Other bug fixes
For a more detailed look at all of the changes, refer to the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.8.4) in GitHub.
#### Issues Closed
* [#5017: 'Uncaught Error: No such module' using cloudflare\_snippets](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5017)
* [#5701: cloudflare\_workers\_script migrations for Durable Objects not recorded in tfstate; cannot be upgraded between versions](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5701)
* [#5640: cloudflare\_argo\_smart\_routing importing doesn't read the actual value](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5640)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding off on migration to v5 while we work on stablization. This help will you avoid any blocking issues while the Terraform resources are actively being stablized.
If you'd like more information on migrating to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition. These migration scripts do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Aug 08, 2025
1. ### [Introducing observability and metrics for Stream Live Inputs](https://developers.cloudflare.com/changelog/2025-08-08-stream-live-observability/)
[Stream](https://developers.cloudflare.com/stream/)
New information about broadcast metrics and events is now available in [Cloudflare Stream](https://developers.cloudflare.com/stream/) in the Live Input details of the Dashboard.
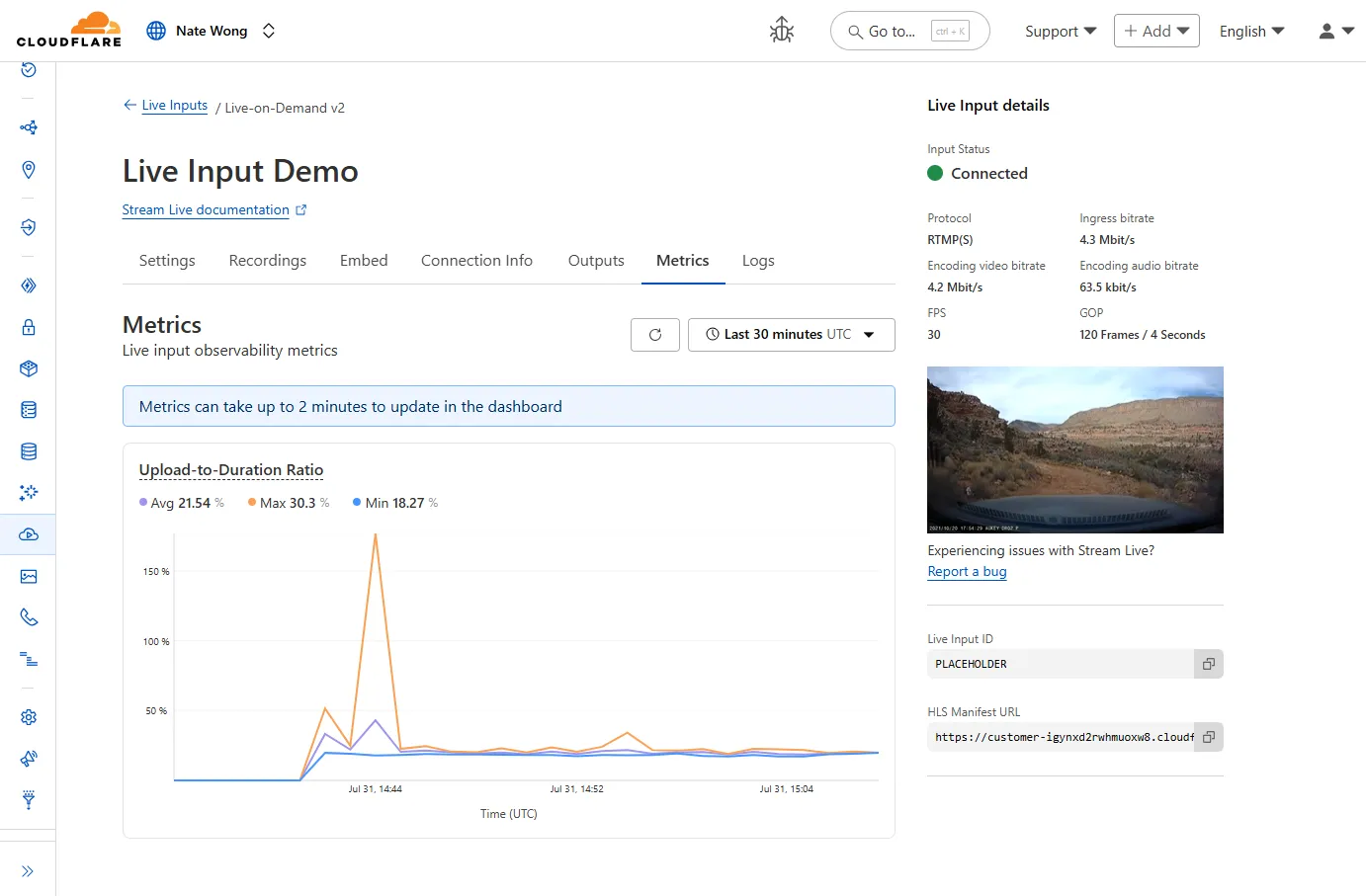
You can now easily understand broadcast-side health and performance with new observability, which can help when troubleshooting common issues, particularly for new customers who are just getting started, and platform customers who may have limited visibility into how their end-users configure their encoders.
To get started, start a live stream ([just getting started?](https://developers.cloudflare.com/stream/examples/obs-from-scratch/)), then visit the Live Input details page in Dash.
See our new live [Troubleshooting](https://developers.cloudflare.com/stream/stream-live/troubleshooting/) guide to learn what these metrics mean and how to use them to address common broadcast issues.
Aug 06, 2025
1. ### [Improvements to Monitoring Using Zone Settings](https://developers.cloudflare.com/changelog/2025-08-06-zone-monitoring-improvements/)
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
Cloudflare Load Balancing Monitors support loading and applying settings for a specific zone to monitoring requests to origin endpoints. This feature has been migrated to new infrastructure to improve reliability, performance, and accuracy.
All zone monitors have been tested against the new infrastructure. There should be no change to health monitoring results of currently healthy and active pools. Newly created or re-enabled pools may need validation of their monitor zone settings before being introduced to service, especially regarding correct application of mTLS.
#### What you can expect:
* More reliable application of zone settings to monitoring requests, including
* Authenticated Origin Pulls
* Aegis Egress IP Pools
* Argo Smart Routing
* HTTP/2 to Origin
* Improved support and bug fixes for retries, redirects, and proxied origin resolution
* Improved performance and reliability of monitoring requests withing the Cloudflare network
* Unrelated CDN or WAF configuration changes should have no risk of impact to pool health
Aug 05, 2025
1. ### [Agents SDK adds MCP Elicitation support, http-streamable suppport, task queues, email integration and more](https://developers.cloudflare.com/changelog/2025-08-05-agents-mcp-update/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
The latest releases of [@cloudflare/agents](https://github.com/cloudflare/agents) brings major improvements to MCP transport protocols support and agents connectivity. Key updates include:
#### MCP elicitation support
MCP servers can now request user input during tool execution, enabling interactive workflows like confirmations, forms, and multi-step processes. This feature uses durable storage to preserve elicitation state even during agent hibernation, ensuring seamless user interactions across agent lifecycle events.
```ts
// Request user confirmation via elicitation
const confirmation = await this.elicitInput({
message: `Are you sure you want to increment the counter by ${amount}?`,
requestedSchema: {
type: "object",
properties: {
confirmed: {
type: "boolean",
title: "Confirm increment",
description: "Check to confirm the increment",
},
},
required: ["confirmed"],
},
});
```
Check out our [demo](https://github.com/whoiskatrin/agents/tree/main/examples/mcp-elicitation-demo) to see elicitation in action.
#### HTTP streamable transport for MCP
MCP now supports HTTP streamable transport which is recommended over SSE. This transport type offers:
* **Better performance**: More efficient data streaming and reduced overhead
* **Improved reliability**: Enhanced connection stability and error recover- **Automatic fallback**: If streamable transport is not available, it gracefully falls back to SSE
```ts
export default MyMCP.serve("/mcp", {
binding: "MyMCP",
});
```
The SDK automatically selects the best available transport method, gracefully falling back from streamable-http to SSE when needed.
#### Enhanced MCP connectivity
Significant improvements to MCP server connections and transport reliability:
* **Auto transport selection**: Automatically determines the best transport method, falling back from streamable-http to SSE as needed
* **Improved error handling**: Better connection state management and error reporting for MCP servers
* **Reliable prop updates**: Centralized agent property updates ensure consistency across different contexts
#### Lightweight .queue for fast task deferral
You can use `.queue()` to enqueue background work — ideal for tasks like processing user messages, sending notifications etc.
```ts
class MyAgent extends Agent {
doSomethingExpensive(payload) {
// a long running process that you want to run in the background
}
queueSomething() {
await this.queue("doSomethingExpensive", somePayload); // this will NOT block further execution, and runs in the background
await this.queue("doSomethingExpensive", someOtherPayload); // the callback will NOT run until the previous callback is complete
// ... call as many times as you want
}
}
```
Want to try it yourself? Just define a method like processMessage in your agent, and you’re ready to scale.
#### New email adapter
Want to build an AI agent that can receive and respond to emails automatically? With the new email adapter and onEmail lifecycle method, now you can.
```ts
export class EmailAgent extends Agent {
async onEmail(email: AgentEmail) {
const raw = await email.getRaw();
const parsed = await PostalMime.parse(raw);
// create a response based on the email contents
// and then send a reply
await this.replyToEmail(email, {
fromName: "Email Agent",
body: `Thanks for your email! You've sent us "${parsed.subject}". We'll process it shortly.`,
});
}
}
```
You route incoming mail like this:
```ts
export default {
async email(email, env) {
await routeAgentEmail(email, env, {
resolver: createAddressBasedEmailResolver("EmailAgent"),
});
},
};
```
You can find a full example [here](https://github.com/cloudflare/agents/tree/main/examples/email-agent).
#### Automatic context wrapping for custom methods
Custom methods are now automatically wrapped with the agent's context, so calling `getCurrentAgent()` should work regardless of where in an agent's lifecycle it's called. Previously this would not work on RPC calls, but now just works out of the box.
```ts
export class MyAgent extends Agent {
async suggestReply(message) {
// getCurrentAgent() now correctly works, even when called inside an RPC method
const { agent } = getCurrentAgent()!;
return generateText({
prompt: `Suggest a reply to: "${message}" from "${agent.name}"`,
tools: [replyWithEmoji],
});
}
}
```
Try it out and tell us what you build!
Aug 05, 2025
1. ### [Cloudflare Sandbox SDK adds streaming, code interpreter, Git support, process control and more](https://developers.cloudflare.com/changelog/2025-08-05-sandbox-sdk-major-update/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We’ve shipped a major release for the [@cloudflare/sandbox](https://github.com/cloudflare/sandbox-sdk) SDK, turning it into a full-featured, container-based execution platform that runs securely on Cloudflare Workers.
This update adds live streaming of output, persistent Python and JavaScript code interpreters with rich output support (charts, tables, HTML, JSON), file system access, Git operations, full background process control, and the ability to expose running services via public URLs.
This makes it ideal for building AI agents, CI runners, cloud REPLs, data analysis pipelines, or full developer tools — all without managing infrastructure.
#### Code interpreter (Python, JS, TS)
Create persistent code contexts with support for rich visual + structured outputs.
#### createCodeContext(options)
Creates a new code execution context with persistent state.
```ts
// Create a Python context
const pythonCtx = await sandbox.createCodeContext({ language: "python" });
// Create a JavaScript context
const jsCtx = await sandbox.createCodeContext({ language: "javascript" });
```
Options:
* language: Programming language ('python' | 'javascript' | 'typescript')
* cwd: Working directory (default: /workspace)
* envVars: Environment variables for the context
#### runCode(code, options)
Executes code with optional streaming callbacks.
```ts
// Simple execution
const execution = await sandbox.runCode('print("Hello World")', {
context: pythonCtx,
});
// With streaming callbacks
await sandbox.runCode(
`
for i in range(5):
print(f"Step {i}")
time.sleep(1)
`,
{
context: pythonCtx,
onStdout: (output) => console.log("Real-time:", output.text),
onResult: (result) => console.log("Result:", result),
},
);
```
Options:
* language: Programming language ('python' | 'javascript' | 'typescript')
* cwd: Working directory (default: /workspace)
* envVars: Environment variables for the context
#### Real-time streaming output
Returns a streaming response for real-time processing.
```ts
const stream = await sandbox.runCodeStream(
"import time; [print(i) for i in range(10)]",
);
// Process the stream as needed
```
#### Rich output handling
Interpreter outputs are auto-formatted and returned in multiple formats:
* text
* html (e.g., Pandas tables)
* png, svg (e.g., Matplotlib charts)
* json (structured data)
* chart (parsed visualizations)
```ts
const result = await sandbox.runCode(
`
import seaborn as sns
import matplotlib.pyplot as plt
data = sns.load_dataset("flights")
pivot = data.pivot("month", "year", "passengers")
sns.heatmap(pivot, annot=True, fmt="d")
plt.title("Flight Passengers")
plt.show()
pivot.to_dict()
`,
{ context: pythonCtx },
);
if (result.png) {
console.log("Chart output:", result.png);
}
```
#### Preview URLs from Exposed Ports
Start background processes and expose them with live URLs.
```ts
await sandbox.startProcess("python -m http.server 8000");
const preview = await sandbox.exposePort(8000);
console.log("Live preview at:", preview.url);
```
#### Full process lifecycle control
Start, inspect, and terminate long-running background processes.
```ts
const process = await sandbox.startProcess("node server.js");
console.log(`Started process ${process.id} with PID ${process.pid}`);
// Monitor the process
const logStream = await sandbox.streamProcessLogs(process.id);
for await (const log of parseSSEStream(logStream)) {
console.log(`Server: ${log.data}`);
}
```
* listProcesses() - List all running processes
* getProcess(id) - Get detailed process status
* killProcess(id, signal) - Terminate specific processes
* killAllProcesses() - Kill all processes
* streamProcessLogs(id, options) - Stream logs from running processes
* getProcessLogs(id) - Get accumulated process output
#### Git integration
Clone Git repositories directly into the sandbox.
```ts
await sandbox.gitCheckout("https://github.com/user/repo", {
branch: "main",
targetDir: "my-project",
});
```
Sandboxes are still experimental. We're using them to explore how isolated, container-like workloads might scale on Cloudflare — and to help define the developer experience around them.
Aug 05, 2025
1. ### [OpenAI open models now available on Workers AI](https://developers.cloudflare.com/changelog/2025-08-05-openai-open-models/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers AI](https://developers.cloudflare.com/workers-ai/)
We're thrilled to be a Day 0 partner with [OpenAI](http://openai.com/index/introducing-gpt-oss) to bring their [latest open models](https://openai.com/index/gpt-oss-model-card/) to Workers AI, including support for Responses API, Code Interpreter, and Web Search (coming soon).
Get started with the new models at `@cf/openai/gpt-oss-120b` and `@cf/openai/gpt-oss-20b`. Check out the [blog](https://blog.cloudflare.com/openai-gpt-oss-on-workers-ai) for more details about the new models, and the [`gpt-oss-120b`](https://developers.cloudflare.com/workers-ai/models/gpt-oss-120b) and [`gpt-oss-20b`](https://developers.cloudflare.com/workers-ai/models/gpt-oss-20b) model pages for more information about pricing and context windows.
#### Responses API
If you call the model through:
* Workers Binding, it will accept/return Responses API – `env.AI.run(“@cf/openai/gpt-oss-120b”)`
* REST API on `/run` endpoint, it will accept/return Responses API – `https://api.cloudflare.com/client/v4/accounts//ai/run/@cf/openai/gpt-oss-120b`
* REST API on new `/responses` endpoint, it will accept/return Responses API – `https://api.cloudflare.com/client/v4/accounts//ai/v1/responses`
* REST API for OpenAI Compatible endpoint, it will return Chat Completions (coming soon) – `https://api.cloudflare.com/client/v4/accounts//ai/v1/chat/completions`
```plaintext
curl https://api.cloudflare.com/client/v4/accounts//ai/v1/responses \
-H "Content-Type: application/json" \
-H "Authorization: Bearer $CLOUDFLARE_API_KEY" \
-d '{
"model": "@cf/openai/gpt-oss-120b",
"reasoning": {"effort": "medium"},
"input": [
{
"role": "user",
"content": "What are the benefits of open-source models?"
}
]
}'
```
#### Code Interpreter
The model is natively trained to support stateful code execution, and we've implemented support for this feature using our [Sandbox SDK](https://github.com/cloudflare/sandbox-sdk) and [Containers](https://blog.cloudflare.com/containers-are-available-in-public-beta-for-simple-global-and-programmable/). Cloudflare's Developer Platform is uniquely positioned to support this feature, so we're very excited to bring our products together to support this new use case.
#### Web Search (coming soon)
We are working to implement Web Search for the model, where users can bring their own Exa API Key so the model can browse the Internet.
Aug 01, 2025
1. ### [Terraform v5.8.2 now available](https://developers.cloudflare.com/changelog/2025-08-01-terraform-v582-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high mumber of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a 2 week cadeance to ensure it's stability and reliability. We have also pivoted from an issue-to-issue approach to a resource-per-resource approach - we will be focusing on specific resources for every release, stablizing the release and closing all associated bugs with that resource before moving onto resolving migration issues.
Thank you for continuing to raise issues. We triage them weekly and they help make our products stronger.
#### Changes
* Resources stablized:
* `cloudflare_custom_pages`
* `cloudflare_page_rule`
* `cloudflare_dns_record`
* `cloudflare_argo_tiered_caching`
* Addressed chronic drift issues in `cloudflare_logpush_job`, `cloudflare_zero_trust_dns_location`, `cloudflare_ruleset` & `cloudflare_api_token`
* `cloudflare_zone_subscripton` returns expected values `rate_plan.id` from former versions
* `cloudflare_workers_script` can now successfully be destroyed with bindings & migration for Durable Objects now recorded in tfstate
* Ability to configure `add_headers` under `cloudflare_zero_trust_gateway_policy`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.8.2) in GitHub.
#### Issues Closed
* [#5666: cloudflare\_ruleset example lists id which is a read-only field](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5666)
* [#5578: cloudflare\_logpush\_job plan always suggests changes](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5578)
* [#5552: 5.4.0: Since provider update, existing cloudflare\_list\_item would be recreated "created" state](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5552)
* [#5670: cloudflare\_zone\_subscription: uses wrong ID field in Read/Update](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5670)
* [#5548: cloudflare\_api\_token resource always shows changes (drift)](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5548)
* [#5634: cloudflare\_workers\_script with bindings fails to be destroyed](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5634)
* [#5616: cloudflare\_workers\_script Unable to deploy worker assets](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5616)
* [#5331: cloudflare\_workers\_script 500 internal server error when uploading python](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5331)
* [#5701: cloudflare\_workers\_script migrations for Durable Objects not recorded in tfstate; cannot be upgraded between versions](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5701)
* [#5704: cloudflare\_workers\_script randomly fails to deploy when changing compatibility\_date](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5704)
* [#5439: cloudflare\_workers\_script (v5.2.0) ignoring content and bindings properties](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5439)
* [#5522: cloudflare\_workers\_script always detects changes after apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5522)
* [#5693: cloudflare\_zero\_trust\_access\_identity\_provider gives recurring change on OTP pin login](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5693)
* [#5567: cloudflare\_r2\_custom\_domain doesn't roundtrip jurisdiction properly](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5567)
* [#5179: Bad request with when creating cloudflare\_api\_shield\_schema resource](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5179)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding off on migration to v5 while we work on stablization. This help will you avoid any blocking issues while the Terraform resources are actively being stablized.
If you'd like more information on migrating from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Jul 30, 2025
1. ### [Magic Transit and Magic WAN health check data is fully compatible with the CMB EU setting.](https://developers.cloudflare.com/changelog/2025-07-30-mt-mwan-health-check-cmb-eu/)
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Today, we are excited to announce that all Magic Transit and Magic WAN customers with CMB EU ([Customer Metadata Boundary - Europe](https://developers.cloudflare.com/data-localization/metadata-boundary/)) enabled in their account will be able to access GRE, IPsec, and CNI health check and traffic volume data in the Cloudflare dashboard and via API.
This ensures that all Magic Transit and Magic WAN customers with CMB EU enabled will be able to access all Magic Transit and Magic WAN features.
Specifically, these two GraphQL endpoints are now compatible with CMB EU:
* `magicTransitTunnelHealthChecksAdaptiveGroups`
* `magicTransitTunnelTrafficAdaptiveGroups`
Jul 29, 2025
1. ### [Deploy to Cloudflare buttons now support Worker environment variables, secrets, and Secrets Store secrets](https://developers.cloudflare.com/changelog/2025-07-01-workers-deploy-button-supports-environment-variables-and-secrets/)
[Workers ](https://developers.cloudflare.com/workers/)[Secrets Store](https://developers.cloudflare.com/secrets-store/)
Any template which uses [Worker environment variables](https://developers.cloudflare.com/workers/configuration/environment-variables/), [secrets](https://developers.cloudflare.com/workers/configuration/secrets/), or [Secrets Store secrets](https://developers.cloudflare.com/secrets-store/) can now be deployed using a [Deploy to Cloudflare button](https://developers.cloudflare.com/workers/platform/deploy-buttons/).
Define environment variables and secrets store bindings in your Wrangler configuration file as normal:
* wrangler.jsonc
```jsonc
{
"name": "my-worker",
"main": "./src/index.ts",
"compatibility_date": "2026-02-07",
"vars": {
"API_HOST": "https://example.com",
},
"secrets_store_secrets": [
{
"binding": "API_KEY",
"store_id": "demo",
"secret_name": "api-key"
}
]
}
```
* wrangler.toml
```toml
name = "my-worker"
main = "./src/index.ts"
compatibility_date = "2026-02-07"
[vars]
API_HOST = "https://example.com"
[[secrets_store_secrets]]
binding = "API_KEY"
store_id = "demo"
secret_name = "api-key"
```
Add secrets to a `.dev.vars.example` or `.env.example` file:
```ini
COOKIE_SIGNING_KEY=my-secret # comment
```
And optionally, you can add a description for these bindings in your template's `package.json` to help users understand how to configure each value:
```json
{
"name": "my-worker",
"private": true,
"cloudflare": {
"bindings": {
"API_KEY": {
"description": "Select your company's API key for connecting to the example service."
},
"COOKIE_SIGNING_KEY": {
"description": "Generate a random string using `openssl rand -hex 32`."
}
}
}
}
```
These secrets and environment variables will be presented to users in the dashboard as they deploy this template, allowing them to configure each value. Additional information about creating templates and Deploy to Cloudflare buttons can be found in [our documentation](https://developers.cloudflare.com/workers/platform/deploy-buttons/).
Jul 29, 2025
1. ### [Audit logs (version 2) - UI Beta Release](https://developers.cloudflare.com/changelog/2025-07-29-audit-logs-v2-ui-beta/)
[Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/)
The Audit Logs v2 UI is now available to all Cloudflare customers in Beta. This release builds on the public [Beta of the Audit Logs v2 API](https://developers.cloudflare.com/changelog/?product=audit-logs) and introduces a redesigned user interface with powerful new capabilities to make it easier to investigate account activity.
**Enabling the new UI**
To try the new user interface, go to **Manage Account > Audit Logs**. The previous version of Audit Logs remains available and can be re-enabled at any time using the **Switch back to old Audit Logs** link in the banner at the top of the page.
**New Features:**
* **Advanced Filtering**: Filter logs by actor, resource, method, and more for faster insights.
* **On-hover filter controls**: Easily include or exclude values in queries by hovering over fields within a log entry.
* **Detailed Log Sidebar**: View rich context for each log entry without leaving the main view.
* **JSON Log View**: Inspect the raw log data in a structured JSON format.
* **Custom Time Ranges**: Define your own time windows to view historical activity.
* **Infinite Scroll**: Seamlessly browse logs without clicking through pages.
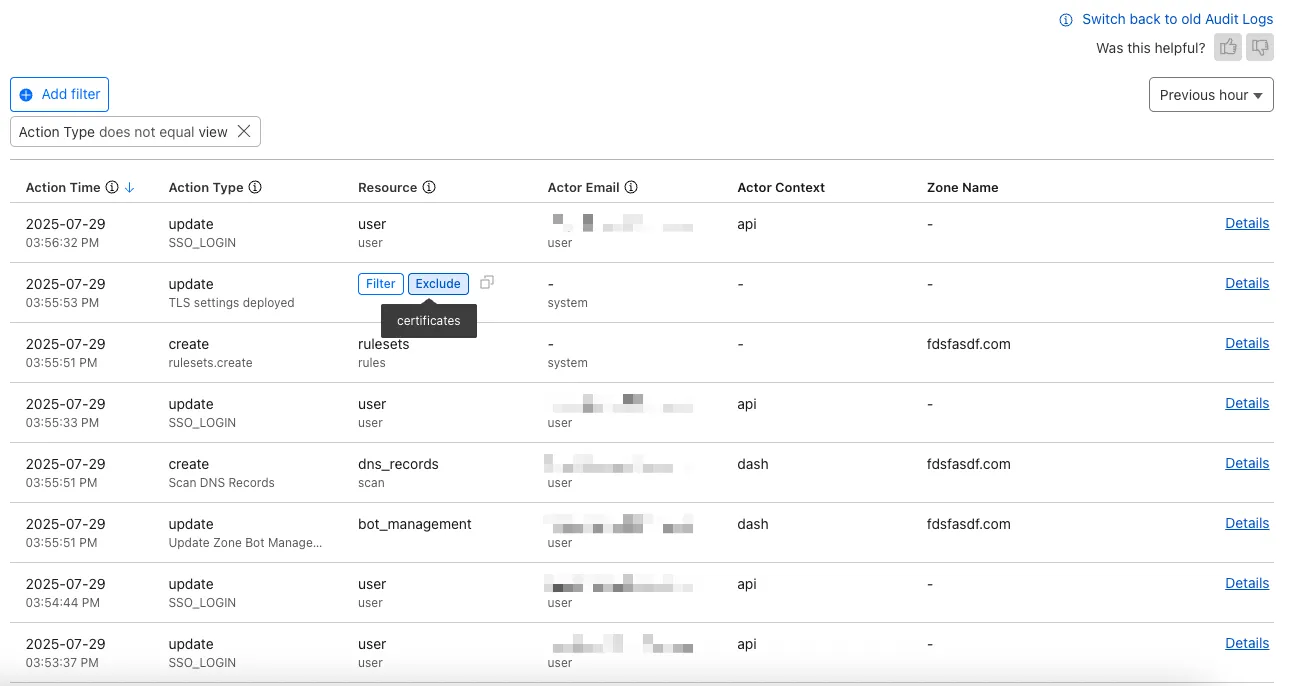
For more details on Audit Logs v2, see the [Audit Logs documentation](https://developers.cloudflare.com/fundamentals/account/account-security/audit-logs/).
**Known issues**
* A small number of audit logs may currently be unavailable in Audit Logs v2. In some cases, certain fields such as actor information may be missing in certain audit logs. We are actively working to improve coverage and completeness for General Availability.
* Export to CSV is not supported in the new UI.
We are actively refining the Audit Logs v2 experience and welcome your feedback. You can share overall feedback by clicking the thumbs up or thumbs down icons at the top of the page, or provide feedback on specific audit log entries using the thumbs icons next to each audit log line or by filling out our [feedback form](https://docs.google.com/forms/d/e/1FAIpQLSfXGkJpOG1jUPEh-flJy9B13icmcdBhveFwe-X0EzQjJQnQfQ/viewform?usp=sharing).
Jul 28, 2025
1. ### [Introducing pricing for the Browser Rendering API — $0.09 per browser hour](https://developers.cloudflare.com/changelog/2025-07-28-br-pricing/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We’ve launched pricing for [Browser Rendering](https://developers.cloudflare.com/browser-rendering/), including a free tier and a pay-as-you-go model that scales with your needs. Starting **August 20, 2025**, Cloudflare will begin billing for Browser Rendering.
There are two ways to use Browser Rendering. Depending on the method you use, here’s how billing will work:
* [**REST API**](https://developers.cloudflare.com/browser-rendering/rest-api/): Charged for **Duration** only ($/browser hour)
* [**Workers Bindings**](https://developers.cloudflare.com/browser-rendering/workers-bindings/): Charged for both **Duration** and **Concurrency** ($/browser hour and # of concurrent browsers)
Included usage and pricing by plan
| Plan | Included duration | Included concurrency | Price (beyond included) |
| - | - | - | - |
| **Workers Free** | 10 minutes per day | 3 concurrent browsers | N/A |
| **Workers Paid** | 10 hours per month | 10 concurrent browsers (averaged monthly) | **1. REST API**: $0.09 per additional browser hour **2. Workers Bindings**: $0.09 per additional browser hour $2.00 per additional concurrent browser |
What you need to know:
* **Workers Free Plan:** 10 minutes of browser usage per day with 3 concurrent browsers at no charge.
* **Workers Paid Plan:** 10 hours of browser usage per month with 10 concurrent browsers (averaged monthly) at no charge. Additional usage is charged as shown above.
You can monitor usage via the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/workers/browser-rendering). Go to **Compute (Workers)** > **Browser Rendering**.

If you've been using Browser Rendering and do not wish to incur charges, ensure your usage stays within your plan's [included usage](https://developers.cloudflare.com/browser-rendering/pricing/). To estimate costs, take a look at these [example pricing scenarios](https://developers.cloudflare.com/browser-rendering/pricing/#examples-of-workers-paid-pricing).
Jul 22, 2025
1. ### [Browser Rendering now supports local development](https://developers.cloudflare.com/changelog/2025-07-22-br-local-dev/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
You can now run your Browser Rendering locally using `npx wrangler dev`, which spins up a browser directly on your machine before deploying to Cloudflare's global network. By running tests locally, you can quickly develop, debug, and test changes without needing to deploy or worry about usage costs.
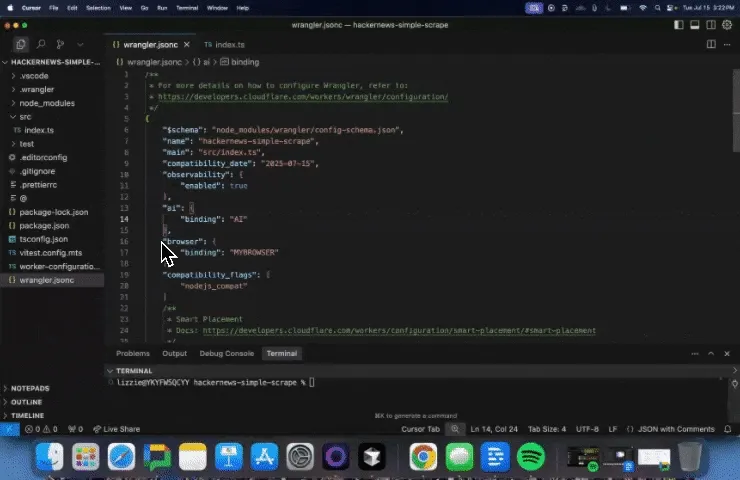
Get started with this [example guide](https://developers.cloudflare.com/browser-rendering/workers-bindings/screenshots/) that shows how to use Cloudflare's [fork of Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/) (you can also use [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/)) to take screenshots of webpages and store the results in [Workers KV](https://developers.cloudflare.com/kv/).
Jul 22, 2025
1. ### [Audio mode for Media Transformations](https://developers.cloudflare.com/changelog/2025-07-22-media-transformations-audio-mode/)
[Stream](https://developers.cloudflare.com/stream/)
We now support `audio` mode! Use this feature to extract audio from a source video, outputting an M4A file to use in downstream workflows like [AI inference](https://developers.cloudflare.com/workers-ai/), content moderation, or transcription.
For example,
```text
https://example.com/cdn-cgi/media//
https://example.com/cdn-cgi/media/mode=audio,time=3s,duration=60s/
```
For more information, learn about [Transforming Videos](https://developers.cloudflare.com/stream/transform-videos/).
Jul 21, 2025
1. ### [Subaddressing support in Email Routing](https://developers.cloudflare.com/changelog/2025-07-21-subaddressing/)
[Email Routing](https://developers.cloudflare.com/email-routing/)
Subaddressing, as defined in [RFC 5233](https://www.rfc-editor.org/rfc/rfc5233), also known as plus addressing, is now supported in Email Routing. This enables using the "+" separator to augment your custom addresses with arbitrary detail information.
Now you can send an email to `user+detail@example.com` and it will be captured by the `user@example.com` custom address. The `+detail` part is ignored by Email Routing, but it can be captured next in the processing chain in the logs, an [Email Worker](https://developers.cloudflare.com/email-routing/email-workers/) or an [Agent application](https://github.com/cloudflare/agents/tree/main/examples/email-agent).
Customers can use this feature to dynamically add context to their emails, such as tracking the source of an email or categorizing emails without needing to create multiple custom addresses.
Check our [Developer Docs](https://developers.cloudflare.com/email-routing/setup/email-routing-addresses/#subaddressing) to learn on to enable subaddressing in Email Routing.
Jul 17, 2025
1. ### [New detection entry type: Document Matching for DLP](https://developers.cloudflare.com/changelog/2025-07-17-document-matching/)
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now create [document-based](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#documents) detection entries in DLP by uploading example documents. Cloudflare will encrypt your documents and create a unique fingerprint of the file. This fingerprint is then used to identify similar documents or snippets within your organization's traffic and stored files.
**Key features and benefits:**
* **Upload documents, forms, or templates:** Easily upload .docx and .txt files (up to 10 MB) that contain sensitive information you want to protect.
* **Granular control with similarity percentage:** Define a minimum similarity percentage (0-100%) that a document must meet to trigger a detection, reducing false positives.
* **Comprehensive coverage:** Apply these document-based detection entries in:
* **Gateway policies:** To inspect network traffic for sensitive documents as they are uploaded or shared.
* **CASB (Cloud Access Security Broker):** To scan files stored in cloud applications for sensitive documents at rest.
* **Identify sensitive data:** This new detection entry type is ideal for identifying sensitive data within completed forms, templates, or even small snippets of a larger document, helping you prevent data exfiltration and ensure compliance.
Once uploaded and processed, you can add this new document entry into a DLP profile and policies to enhance your data protection strategy.
Jul 15, 2025
1. ### [Faster, more reliable UDP traffic for Cloudflare Tunnel](https://developers.cloudflare.com/changelog/2025-07-15-udp-improvements/)
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
Your real-time applications running over [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) are now faster and more reliable. We've completely re-architected the way `cloudflared` proxies UDP traffic in order to isolate it from other traffic, ensuring latency-sensitive applications like private DNS are no longer slowed down by heavy TCP traffic (like file transfers) on the same Tunnel.
This is a foundational improvement to Cloudflare Tunnel, delivered automatically to all customers. There are no settings to configure — your UDP traffic is already flowing faster and more reliably.
**What’s new:**
* **Faster UDP performance**: We've significantly reduced the latency for establishing new UDP sessions, making applications like private DNS much more responsive.
* **Greater reliability for mixed traffic**: UDP packets are no longer affected by heavy TCP traffic, preventing timeouts and connection drops for your real-time services.
Learn more about running [TCP or UDP applications](https://developers.cloudflare.com/reference-architecture/architectures/sase/#connecting-applications) and [private networks](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/) through [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/).
Jul 14, 2025
1. ### [Terraform v5.7.0 now available](https://developers.cloudflare.com/changelog/2025-07-11-terraform-v570-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high mumber of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare community related to the v5 release, with 13.5% of resources impacted. We have committed to releasing improvements on a 2 week cadeance to ensure it's stability and relability, including the v5.7 release.
Thank you for continuing to raise issues and please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Addressed permanent diff bug on Cloudflare Tunnel config
* State is now saved correctly for Zero Trust Access applications
* Exact match is now working as expected within `data.cloudflare_zero_trust_access_applications`
* `cloudflare_zero_trust_access_policy` now supports OIDC claims & diff issues resolved
* Self hosted applications with private IPs no longer require a public domain for `cloudflare_zero_trust_access_application`.
* New resource:
* `cloudflare_zero_trust_tunnel_warp_connector`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.7.0) in GitHub.
#### Issues Closed
* [#5563: cloudflare\_logpull\_retention is missing import](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5563)
* [#5608: cloudflare\_zero\_trust\_access\_policy in 5.5.0 provider gives error upon apply unexpected new value: .app\_count: was cty.NumberIntVal(0), but now cty.NumberIntVal(1)](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5608)
* [#5612: data.cloudflare\_zero\_trust\_access\_applications does not exact match](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5612)
* [#5532: cloudflare\_zero\_trust\_access\_identity\_provider detects changes on every plan](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5532)
* [#5662: cloudflare\_zero\_trust\_access\_policy does not support OIDC claims](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5662)
* [#5565: Running Terraform with the cloudflare\_zero\_trust\_access\_policy resource results in updates on every apply, even when no changes are made - breaks idempotency](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5565)
* [#5529: cloudflare\_zero\_trust\_access\_application: self hosted applications with private ips require public domain](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5529)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding on migration to v5 while we work on stablization of the v5 provider. This will ensure Cloudflare can work ahead and avoid any blocking issues.
If you'd like more information on migrating from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Jul 10, 2025
1. ### [New onboarding guides for Zero Trust](https://developers.cloudflare.com/changelog/2025-07-09-onboarding-resources/)
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Use our brand new onboarding experience for Cloudflare Zero Trust. New and returning users can now engage with a **Get Started** tab with walkthroughs for setting up common use cases end-to-end.
There are eight brand new onboarding guides in total:
* Securely access a private network (sets up device client and Tunnel)
* Device-to-device / mesh networking (sets up and connects multiple device clients)
* Network to network connectivity (sets up and connects multiple WARP Connectors, makes reference to Magic WAN availability for Enterprise)
* Secure web traffic (sets up device client, Gateway, pre-reqs, and initial policies)
* Secure DNS for networks (sets up a new DNS location and Gateway policies)
* Clientless web access (sets up Access to a web app, Tunnel, and public hostname)
* Clientless SSH access (all the same + the web SSH experience)
* Clientless RDP access (all the same + RDP-in-browser)
Each flow walks the user through the steps to configure the essential elements, and provides a “more details” panel with additional contextual information about what the user will accomplish at the end, along with why the steps they take are important.
Try them out now in the [Zero Trust dashboard](https://one.dash.cloudflare.com/?to=/:account/home)!
Jul 08, 2025
1. ### [HEIC support in Cloudflare Images](https://developers.cloudflare.com/changelog/heic-support/)
[Cloudflare Images](https://developers.cloudflare.com/images/)
You can use Images to ingest HEIC images and serve them in supported output formats like AVIF, WebP, JPEG, and PNG.
When inputting a HEIC image, dimension and sizing limits may still apply. Refer to our documentation to see limits for [uploading to Images](https://developers.cloudflare.com/images/upload-images/) or [transforming a remote image](https://developers.cloudflare.com/images/transform-images/).
Jul 07, 2025
1. ### [Cloudy summaries for Access and Gateway Logs](https://developers.cloudflare.com/changelog/2025-07-07-cloudy-summaries-access-gateway/)
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Cloudy, Cloudflare's AI Agent, will now automatically summarize your [Access](https://developers.cloudflare.com/cloudflare-one/insights/logs/audit-logs/) and [Gateway](https://developers.cloudflare.com/cloudflare-one/insights/logs/gateway-logs/) block logs.
In the log itself, Cloudy will summarize what occurred and why. This will be helpful for quick troubleshooting and issue correlation.
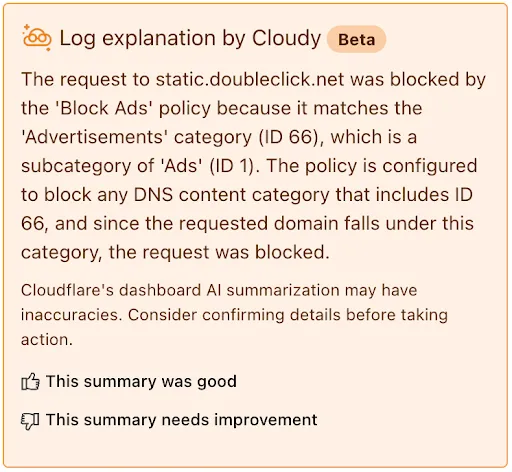
If you have feedback about the Cloudy summary - good or bad - you can provide that right from the summary itself.
Jul 03, 2025
1. ### [Hyperdrive now supports configuring the amount of database connections](https://developers.cloudflare.com/changelog/2025-07-02-hyperdrive-configurable-connection-count/)
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
You can now specify the number of connections your Hyperdrive configuration uses to connect to your origin database.
All configurations have a minimum of 5 connections. The maximum connection count for a Hyperdrive configuration depends on the [Hyperdrive limits of your Workers plan](https://developers.cloudflare.com/hyperdrive/platform/limits/).
This feature allows you to right-size your connection pool based on your database capacity and application requirements. You can configure connection counts through the Cloudflare dashboard or API.
Refer to the [Hyperdrive configuration documentation](https://developers.cloudflare.com/hyperdrive/concepts/connection-pooling/) for more information.
Jun 30, 2025
1. ### [Mail authentication requirements for Email Routing](https://developers.cloudflare.com/changelog/2025-06-30-mail-authentication/)
[Email Routing](https://developers.cloudflare.com/email-routing/)
The Email Routing platform supports [SPF](https://datatracker.ietf.org/doc/html/rfc7208) records and [DKIM (DomainKeys Identified Mail)](https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail) signatures and honors these protocols when the sending domain has them configured. However, if the sending domain doesn't implement them, we still forward the emails to upstream mailbox providers.
Starting on July 3, 2025, we will require all emails to be authenticated using at least one of the protocols, SPF or DKIM, to forward them. We also strongly recommend that all senders implement the DMARC protocol.
If you are using a Worker with an Email trigger to receive email messages and forward them upstream, you will need to handle the case where the forward action may fail due to missing authentication on the incoming email.
SPAM has been a long-standing issue with email. By enforcing mail authentication, we will increase the efficiency of identifying abusive senders and blocking bad emails. If you're an email server delivering emails to large mailbox providers, it's likely you already use these protocols; otherwise, please ensure you have them properly configured.
Jun 25, 2025
1. ### [Run AI-generated code on-demand with Code Sandboxes (new)](https://developers.cloudflare.com/changelog/2025-06-24-announcing-sandboxes/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers ](https://developers.cloudflare.com/workers/)[Workflows](https://developers.cloudflare.com/workflows/)
AI is supercharging app development for everyone, but we need a safe way to run untrusted, LLM-written code. We’re introducing [Sandboxes](https://www.npmjs.com/package/@cloudflare/sandbox), which let your Worker run actual processes in a secure, container-based environment.
```ts
import { getSandbox } from "@cloudflare/sandbox";
export { Sandbox } from "@cloudflare/sandbox";
export default {
async fetch(request: Request, env: Env) {
const sandbox = getSandbox(env.Sandbox, "my-sandbox");
return sandbox.exec("ls", ["-la"]);
},
};
```
#### Methods
* `exec(command: string, args: string[], options?: { stream?: boolean })`:Execute a command in the sandbox.
* `gitCheckout(repoUrl: string, options: { branch?: string; targetDir?: string; stream?: boolean })`: Checkout a git repository in the sandbox.
* `mkdir(path: string, options: { recursive?: boolean; stream?: boolean })`: Create a directory in the sandbox.
* `writeFile(path: string, content: string, options: { encoding?: string; stream?: boolean })`: Write content to a file in the sandbox.
* `readFile(path: string, options: { encoding?: string; stream?: boolean })`: Read content from a file in the sandbox.
* `deleteFile(path: string, options?: { stream?: boolean })`: Delete a file from the sandbox.
* `renameFile(oldPath: string, newPath: string, options?: { stream?: boolean })`: Rename a file in the sandbox.
* `moveFile(sourcePath: string, destinationPath: string, options?: { stream?: boolean })`: Move a file from one location to another in the sandbox.
* `ping()`: Ping the sandbox.
Sandboxes are still experimental. We're using them to explore how isolated, container-like workloads might scale on Cloudflare — and to help define the developer experience around them.
You can try it today from your Worker, with just a few lines of code. Let us know what you build.
Jun 25, 2025
1. ### [@cloudflare/actors library - SDK for Durable Objects in beta](https://developers.cloudflare.com/changelog/2025-06-25-actors-package-alpha/)
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
The new [@cloudflare/actors](https://www.npmjs.com/package/@cloudflare/actors) library is now in beta!
The `@cloudflare/actors` library is a new SDK for Durable Objects and provides a powerful set of abstractions for building real-time, interactive, and multiplayer applications on top of Durable Objects. With beta usage and feedback, `@cloudflare/actors` will become the recommended way to build on Durable Objects and draws upon Cloudflare's experience building products/features on Durable Objects.
The name "actors" originates from the [actor programming model](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/#actor-programming-model), which closely ties to how Durable Objects are modelled.
The `@cloudflare/actors` library includes:
* Storage helpers for querying embeddeded, per-object SQLite storage
* Storage helpers for managing SQL schema migrations
* Alarm helpers for scheduling multiple alarms provided a date, delay in seconds, or cron expression
* `Actor` class for using Durable Objects with a defined pattern
* Durable Objects [Workers API](https://developers.cloudflare.com/durable-objects/api/base/) is always available for your application as needed
Storage and alarm helper methods can be combined with [any Javascript class](https://github.com/cloudflare/actors?tab=readme-ov-file#storage--alarms-with-durableobject-class) that defines your Durable Object, i.e, ones that extend `DurableObject` including the `Actor` class.
```js
import { Storage } from "@cloudflare/actors/storage";
export class ChatRoom extends DurableObject {
storage: Storage;
constructor(ctx: DurableObjectState, env: Env) {
super(ctx, env)
this.storage = new Storage(ctx.storage);
this.storage.migrations = [{
idMonotonicInc: 1,
description: "Create users table",
sql: "CREATE TABLE IF NOT EXISTS users (id INTEGER PRIMARY KEY)"
}]
}
async fetch(request: Request): Promise {
// Run migrations before executing SQL query
await this.storage.runMigrations();
// Query with SQL template
let userId = new URL(request.url).searchParams.get("userId");
const query = this.storage.sql`SELECT * FROM users WHERE id = ${userId};`
return new Response(`${JSON.stringify(query)}`);
}
}
```
`@cloudflare/actors` library introduces the `Actor` class pattern. `Actor` lets you access Durable Objects without writing the Worker that communicates with your Durable Object (the Worker is created for you). By default, requests are routed to a Durable Object named "default".
```js
export class MyActor extends Actor {
async fetch(request: Request): Promise {
return new Response('Hello, World!')
}
}
export default handler(MyActor);
```
You can [route](https://developers.cloudflare.com/durable-objects/get-started/#3-instantiate-and-communicate-with-a-durable-object) to different Durable Objects by name within your `Actor` class using [`nameFromRequest`](https://github.com/cloudflare/actors?tab=readme-ov-file#actor-with-custom-name).
```js
export class MyActor extends Actor {
static nameFromRequest(request: Request): string {
let url = new URL(request.url);
return url.searchParams.get("userId") ?? "foo";
}
async fetch(request: Request): Promise {
return new Response(`Actor identifier (Durable Object name): ${this.identifier}`);
}
}
export default handler(MyActor);
```
For more examples, check out the library [README](https://github.com/cloudflare/actors?tab=readme-ov-file#getting-started). `@cloudflare/actors` library is a place for more helpers and built-in patterns, like retry handling and Websocket-based applications, to reduce development overhead for common Durable Objects functionality. Please share feedback and what more you would like to see on our [Discord channel](https://discord.com/channels/595317990191398933/773219443911819284).
Jun 23, 2025
1. ### [Data Security Analytics in the Zero Trust dashboard](https://developers.cloudflare.com/changelog/cf1-data-security-analytics-v1/)
[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[CASB ](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust now includes **Data security analytics**, providing you with unprecedented visibility into your organization sensitive data.
The new dashboard includes:
* **Sensitive Data Movement Over Time:**
* See patterns and trends in how sensitive data moves across your environment. This helps understand where data is flowing and identify common paths.
* **Sensitive Data at Rest in SaaS & Cloud:**
* View an inventory of sensitive data stored within your corporate SaaS applications (for example, Google Drive, Microsoft 365) and cloud accounts (such as AWS S3).
* **DLP Policy Activity:**
* Identify which of your Data Loss Prevention (DLP) policies are being triggered most often.
* See which specific users are responsible for triggering DLP policies.
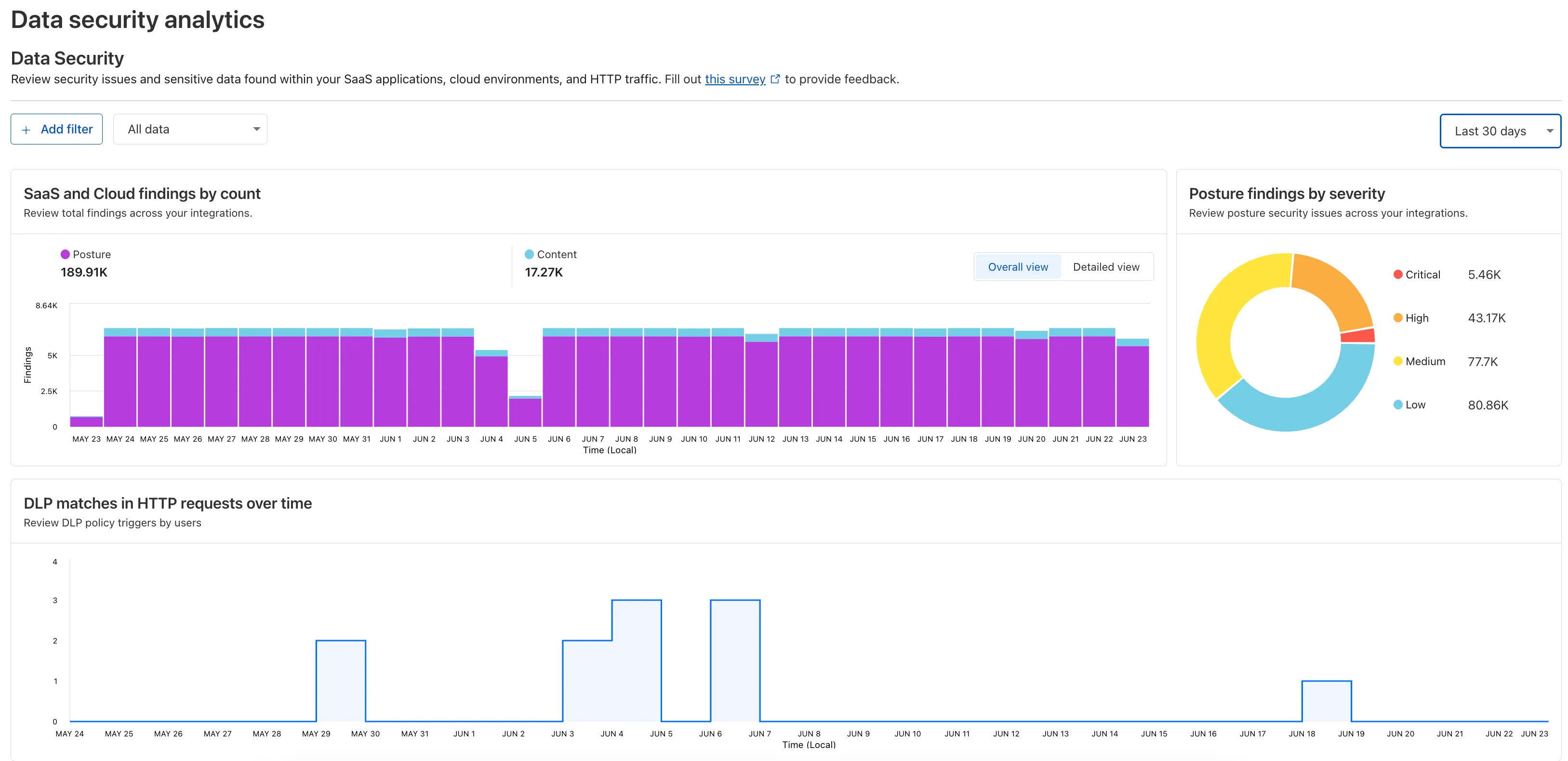
To access the new dashboard, log in to [Cloudflare One](https://one.dash.cloudflare.com/) and go to **Insights** on the sidebar.
Jun 19, 2025
1. ### [Account-level DNS analytics now available via GraphQL Analytics API](https://developers.cloudflare.com/changelog/2025-06-23-account-level-dns-analytics-api/)
[DNS](https://developers.cloudflare.com/dns/)
Authoritative DNS analytics are now available on the **account level** via the [Cloudflare GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/).
This allows users to query DNS analytics across multiple zones in their account, by using the `accounts` filter.
Here is an example to retrieve the most recent DNS queries across all zones in your account that resulted in an `NXDOMAIN` response over a given time frame. Please replace `a30f822fcd7c401984bf85d8f2a5111c` with your actual account ID.
```graphql
query GetLatestNXDOMAINResponses {
viewer {
accounts(filter: { accountTag: "a30f822fcd7c401984bf85d8f2a5111c" }) {
dnsAnalyticsAdaptive(
filter: {
date_geq: "2025-06-16"
date_leq: "2025-06-18"
responseCode: "NXDOMAIN"
}
limit: 10000
orderBy: [datetime_DESC]
) {
zoneTag
queryName
responseCode
queryType
datetime
}
}
}
}
```
[Run in GraphQL API Explorer](https://graphql.cloudflare.com/explorer?query=I4VwpgTgngBA4mALgGQIaLAZ0QOQBoAiA8gLICCAkjgEpYAOA9gHaZYwDeAUDDAG4CWYAO6QO3HjFQBjKQxBNEmABQAzfgBsMEAFwdJMuQoAqqAOa6ARKgDMABhUAOAExOVUgCYB2KQBZbARgBOBx8AI0cAVncHFSdUCP9EqQsYAF8ASjEJCXcWMiZUdShEfilMMndUOhLeMCVxbJ41TUhdLkbGyowAfVMwYEsnWycIgFpbADZR-wmLBo6YLrBu9X7B4bHJ6Yc5hYkIemZWAGEGdzBLfGJyKl2F1Pns9X4AW35EXX9bb9tHiQYIOcIAAhKC6ADaSxKL2WBAAogBlY4AXT+mXaCwAXswwCZTH8eKBIFAcKgYQSYAdMIwWGBTucKUToEYoHQwBSoa92R0HtleWlOKkgA\&variables=N4XyA)
To learn more and get started, refer to the [DNS Analytics documentation](https://developers.cloudflare.com/dns/additional-options/analytics/#analytics).
Jun 19, 2025
1. ### [Automate Worker deployments with a simplified SDK and more reliable Terraform provider](https://developers.cloudflare.com/changelog/2025-06-17-workers-terraform-sdk-api-fixes/)
[D1 ](https://developers.cloudflare.com/d1/)[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
#### Simplified Worker Deployments with our SDKs
We've simplified the programmatic deployment of Workers via our [Cloudflare SDKs](https://developers.cloudflare.com/fundamentals/api/reference/sdks/). This update abstracts away the low-level complexities of the `multipart/form-data` upload process, allowing you to focus on your code while we handle the deployment mechanics.
This new interface is available in:
* [cloudflare-typescript](https://github.com/cloudflare/cloudflare-typescript) (4.4.1)
* [cloudflare-python](https://github.com/cloudflare/cloudflare-python) (4.3.1)
For complete examples, see our guide on [programmatic Worker deployments](https://developers.cloudflare.com/workers/platform/infrastructure-as-code).
#### The Old way: Manual API calls
Previously, deploying a Worker programmatically required manually constructing a `multipart/form-data` HTTP request, packaging your code and a separate `metadata.json` file. This was more complicated and verbose, and prone to formatting errors.
For example, here's how you would upload a Worker script previously with cURL:
```bash
curl https://api.cloudflare.com/client/v4/accounts//workers/scripts/my-hello-world-script \
-X PUT \
-H 'Authorization: Bearer ' \
-F 'metadata={
"main_module": "my-hello-world-script.mjs",
"bindings": [
{
"type": "plain_text",
"name": "MESSAGE",
"text": "Hello World!"
}
],
"compatibility_date": "$today"
};type=application/json' \
-F 'my-hello-world-script.mjs=@-;filename=my-hello-world-script.mjs;type=application/javascript+module' <
#### Terraform provider improvements
We've also made several fixes and enhancements to the [Cloudflare Terraform provider](https://github.com/cloudflare/terraform-provider-cloudflare):
* Fixed the [`cloudflare_workers_script`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_script) resource in Terraform, which previously was producing a diff even when there were no changes. Now, your `terraform plan` outputs will be cleaner and more reliable.
* Fixed the [`cloudflare_workers_for_platforms_dispatch_namespace`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_for_platforms_dispatch_namespace), where the provider would attempt to recreate the namespace on a `terraform apply`. The resource now correctly reads its remote state, ensuring stability for production environments and CI/CD workflows.
* The [`cloudflare_workers_route`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_route) resource now allows for the `script` property to be empty, null, or omitted to indicate that pattern should be negated for all scripts (see routes [docs](https://developers.cloudflare.com/workers/configuration/routing/routes)). You can now reserve a pattern or temporarily disable a Worker on a route without deleting the route definition itself.
* Using `primary_location_hint` in the [`cloudflare_d1_database`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/d1_database) resource will no longer always try to recreate. You can now safely change the location hint for a D1 database without causing a destructive operation.
#### API improvements
We've also properly documented the [Workers Script And Version Settings](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/subresources/script_and_version_settings) in our public OpenAPI spec and SDKs.
Jun 17, 2025
1. ### [Terraform v5.6.0 now available](https://developers.cloudflare.com/changelog/2025-06-17-terraform-v560-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). Unlike the earlier Terraform providers, v5 is automatically generated based on the OpenAPI Schemas for our REST APIs. Since launch, we have seen an unexpectedly high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by customers. These issues currently impact about 15% of resources. We have been working diligently to address these issues across the company, and have released the v5.6.0 release which includes a number of bug fixes. Please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Broad fixes across resources with recurring diffs, including, but not limited to:
* `cloudflare_zero_trust_access_identity_provider`
* `cloudflare_zone`
* `cloudflare_page_rules` runtime panic when setting `cache_level` to `cache_ttl_by_status`
* Failure to serialize requests in `cloudflare_zero_trust_tunnel_cloudflared_config`
* Undocumented field 'priority' on `zone_lockdown` resource
* Missing importability for `cloudflare_zero_trust_device_default_profile_local_domain_fallback` and `cloudflare_account_subscription`
* New resources:
* `cloudflare_schema_validation_operation_settings`
* `cloudflare_schema_validation_schemas`
* `cloudflare_schema_validation_settings`
* `cloudflare_zero_trust_device_settings`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.6.0) in GitHub.
#### Issues Closed
* [#5098: 500 Server Error on updating 'zero\_trust\_tunnel\_cloudflared\_virtual\_network' Terraform resource](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5098)
* [#5148: cloudflare\_user\_agent\_blocking\_rule doesn’t actually support user agents](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5148)
* [#5472: cloudflare\_zone showing changes in plan after following upgrade steps](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5472)
* [#5508: cloudflare\_zero\_trust\_tunnel\_cloudflared\_config failed to serialize http request](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5508)
* [#5509: cloudflare\_zone: Problematic Terraform behaviour with paused zones](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5509)
* [#5520: Resource 'cloudflare\_magic\_wan\_static\_route' is not working](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5520)
* [#5524: Optional fields cause crash in cloudflare\_zero\_trust\_tunnel\_cloudflared(s) when left null](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5524)
* [#5526: Provider v5 migration issue: no import method for cloudflare\_zero\_trust\_device\_default\_profile\_local\_domain\_fallback](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5526)
* [#5532: cloudflare\_zero\_trust\_access\_identity\_provider detects changes on every plan](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5532)
* [#5561: cloudflare\_zero\_trust\_tunnel\_cloudflared: cannot rotate tunnel secret](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5561)
* [#5569: cloudflare\_zero\_trust\_device\_custom\_profile\_local\_domain\_fallback not allowing multiple DNS Server entries](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5569)
* [#5577: Panic modifying page\_rule resource](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5577)
* [#5653: cloudflare\_zone\_setting resource schema confusion in 5.5.0: value vs enabled](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5653)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
If you are evaluating a move from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Jun 16, 2025
1. ### [Internal DNS (beta) now manageable in the Cloudflare dashboard](https://developers.cloudflare.com/changelog/2025-06-16-internal-dns-beta-ui/)
[DNS](https://developers.cloudflare.com/dns/)
Participating beta testers can now fully configure [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/) directly in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/internal-dns).
#### Internal DNS enables customers to:
* Map internal hostnames to private IPs for services, devices, and applications not exposed to the public Internet
* Resolve internal DNS queries securely through [Cloudflare Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
* Use split-horizon DNS to return different responses based on network context
* Consolidate internal and public DNS zones within a single management platform
#### What’s new in this release:
* Beta participants can now create and manage internal zones and views in the Cloudflare dashboard
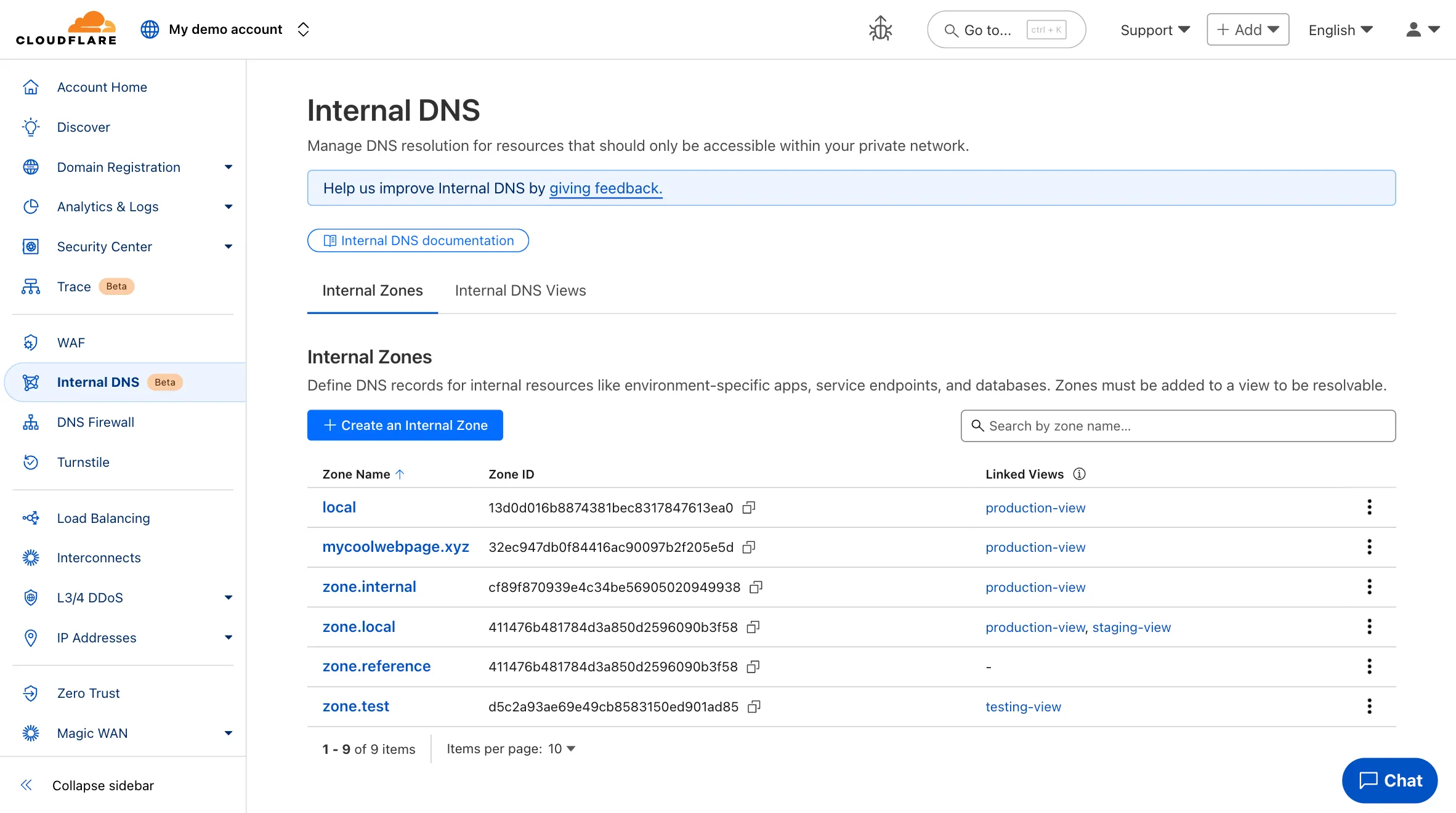
Note
The Internal DNS beta is currently only available to Enterprise customers.
To learn more and get started, refer to the [Internal DNS documentation](https://developers.cloudflare.com/dns/internal-dns/).
Jun 11, 2025
1. ### [NSEC3 support for DNSSEC](https://developers.cloudflare.com/changelog/2025-06-11-nsec3-support/)
[DNS](https://developers.cloudflare.com/dns/)
Enterprise customers can now select NSEC3 as method for proof of non-existence on their zones.
What's new:
* **NSEC3 support for live-signed zones** – For both primary and secondary zones that are configured to be live-signed (also known as "on-the-fly signing"), NSEC3 can now be selected as proof of non-existence.
* **NSEC3 support for pre-signed zones** – Secondary zones that are transferred to Cloudflare in a [pre-signed setup](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/dnssec-for-secondary/#set-up-pre-signed-dnssec) now also support NSEC3 as proof of non-existence.
For more information and how to enable NSEC3, refer to the [NSEC3 documentation](https://developers.cloudflare.com/dns/dnssec/enable-nsec3/).
Jun 10, 2025
1. ### [Increased limits for Media Transformations](https://developers.cloudflare.com/changelog/2025-06-10-media-transformations-limits-increase/)
[Stream](https://developers.cloudflare.com/stream/)
We have increased the limits for [Media Transformations](https://developers.cloudflare.com/stream/transform-videos/):
* Input file size limit is now 100MB (was 40MB)
* Output video duration limit is now 1 minute (was 30 seconds)
Additionally, we have improved caching of the input asset, resulting in fewer requests to origin storage even when transformation options may differ.
For more information, learn about [Transforming Videos](https://developers.cloudflare.com/stream/transform-videos/).
Jun 05, 2025
1. ### [Cloudflare One Analytics Dashboards and Exportable Access Report](https://developers.cloudflare.com/changelog/dashboards-access-report/)
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Cloudflare One now offers powerful new analytics dashboards to help customers easily discover available insights into their application access and network activity. These dashboards provide a centralized, intuitive view for understanding user behavior, application usage, and security posture.
!\[Cloudflare One Analytics Dashboards]\(\~/assets/images/changelog/cloudflare-one/Analytics Dashboards.png)
Additionally, a new exportable access report is available, allowing customers to quickly view high-level metrics and trends in their application access. A **preview** of the report is shown below, with more to be found in the report:
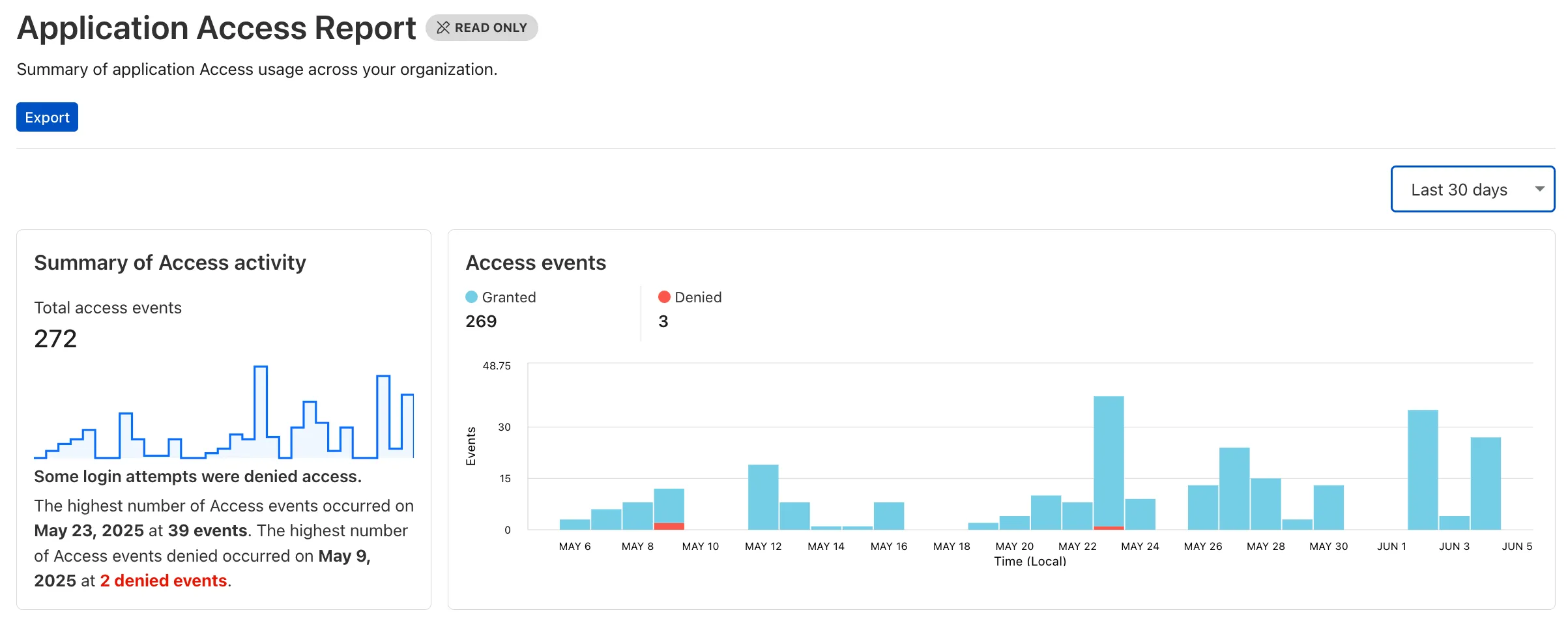
Both features are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
Jun 04, 2025
1. ### [New Account-Level Load Balancing UI and Private Load Balancers](https://developers.cloudflare.com/changelog/2025-06-04-account-load-balancing-ui/)
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
We've made two large changes to load balancing:
* Redesigned the user interface, now centralized at the **account level**.
* Introduced [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to the UI, enabling you to manage traffic for all of your external and internal applications in a single spot.
This update streamlines how you manage load balancers across multiple zones and extends robust traffic management to your private network infrastructure.
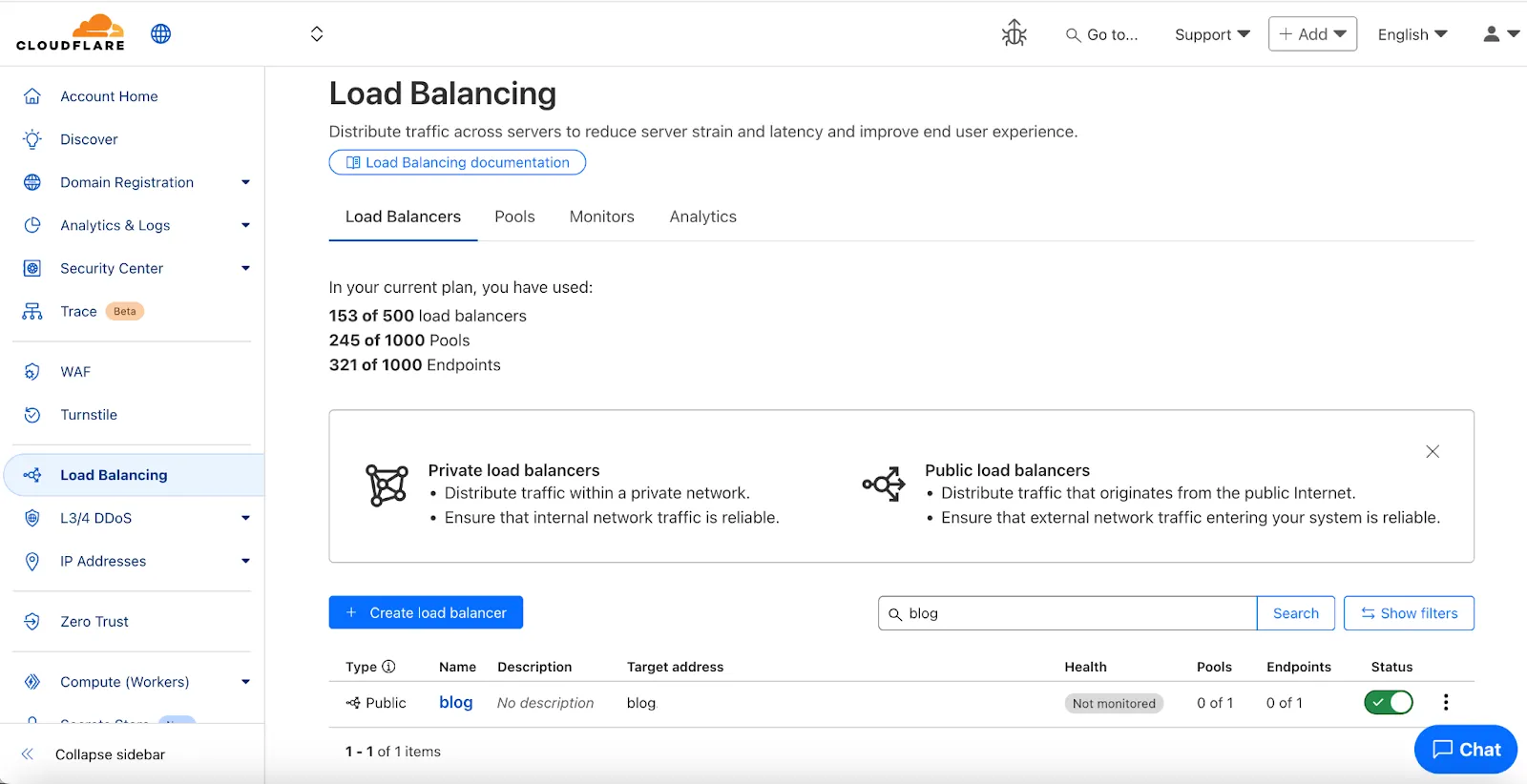
**Key Enhancements:**
* **Account-Level UI Consolidation:**
* **Unified Management:** Say goodbye to navigating individual zones for load balancing tasks. You can now view, configure, and monitor all your load balancers across every zone in your account from a single, intuitive interface at the account level.
* **Improved Efficiency:** This centralized approach provides a more streamlined workflow, making it faster and easier to manage both your public-facing and internal traffic distribution.
* **Private Network Load Balancing:**
* **Secure Internal Application Access:** Create [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to distribute traffic to applications hosted within your private network, ensuring they are not exposed to the public Internet.
* **WARP & Magic WAN Integration:** Effortlessly direct internal traffic from users connected via Cloudflare WARP or through your Magic WAN infrastructure to the appropriate internal endpoint pools.
* **Enhanced Security for Internal Resources:** Combine reliable Load Balancing with Zero Trust access controls to ensure your internal services are both performant and only accessible by verified users.
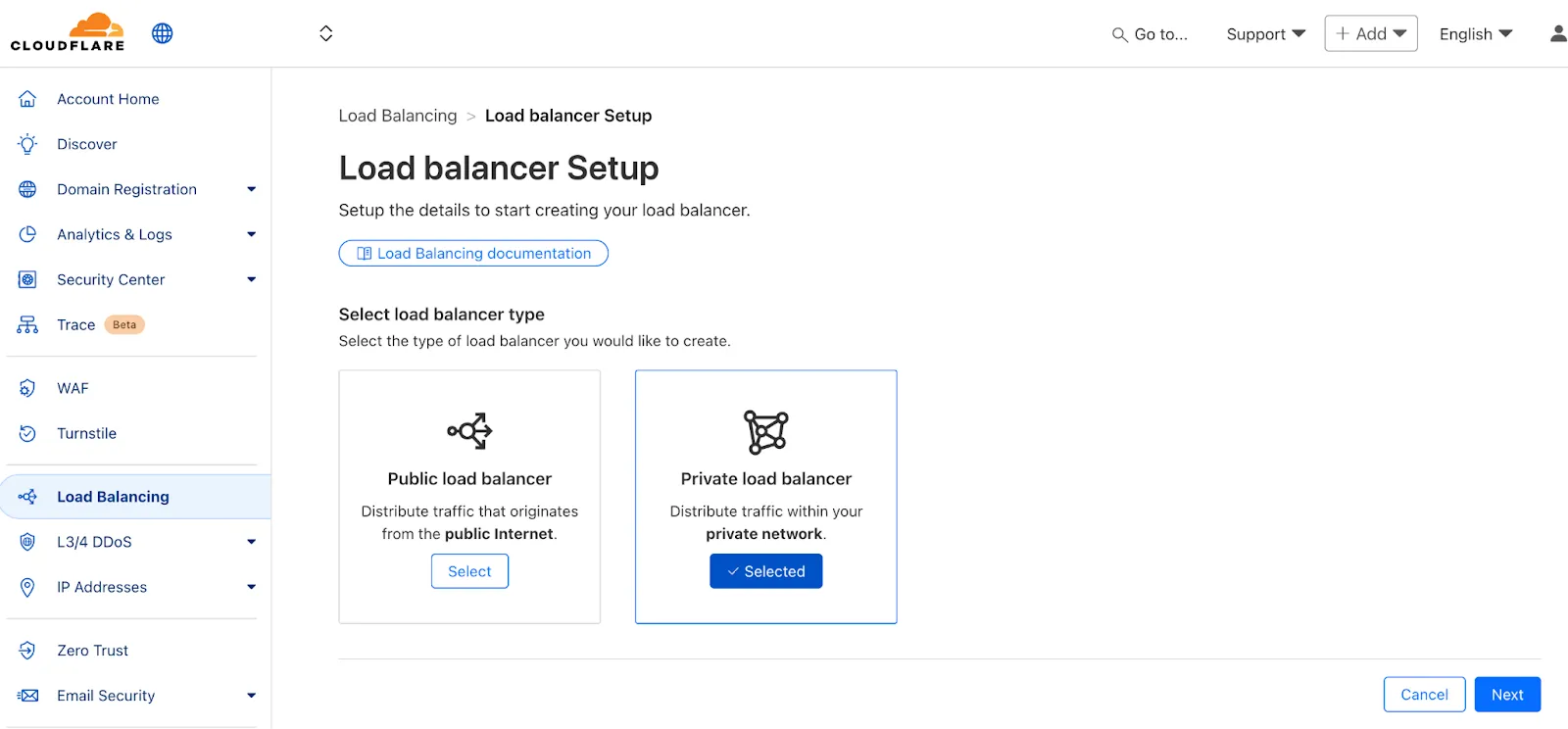
Jun 03, 2025
1. ### [AI Gateway adds OpenAI compatible endpoint](https://developers.cloudflare.com/changelog/2025-06-03-aig-openai-compatible-endpoint/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
Users can now use an [OpenAI Compatible endpoint](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) in AI Gateway to easily switch between providers, while keeping the exact same request and response formats. We're launching now with the chat completions endpoint, with the embeddings endpoint coming up next.
To get started, use the OpenAI compatible chat completions endpoint URL with your own account id and gateway id and switch between providers by changing the `model` and `apiKey` parameters.
```js
import OpenAI from "openai";
const client = new OpenAI({
apiKey: "YOUR_PROVIDER_API_KEY", // Provider API key
baseURL:
"https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/compat",
});
const response = await client.chat.completions.create({
model: "google-ai-studio/gemini-2.0-flash",
messages: [{ role: "user", content: "What is Cloudflare?" }],
});
console.log(response.choices[0].message.content);
```
Additionally, the [OpenAI Compatible endpoint](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) can be combined with our [Universal Endpoint](https://developers.cloudflare.com/ai-gateway/usage/universal/) to add fallbacks across multiple providers. That means AI Gateway will return every response in the same standardized format, no extra parsing logic required!
Learn more in the [OpenAI Compatibility](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) documentation.
Jun 03, 2025
1. ### [Improved onboarding for Shopify merchants](https://developers.cloudflare.com/changelog/2025-06-03-shopify-o2o-improvements/)
[DNS](https://developers.cloudflare.com/dns/)
Shopify merchants can now onboard to **Orange-to-Orange (O2O)** automatically, without needing to contact support or community members.
What's new:
* **Automatic enablement** – O2O is available for all mutual Cloudflare and Shopify customers.
* **Branded record display** – Merchants see a Shopify logo in DNS records, complete with helpful tooltips.
* **Checkout protection** – Workers and Snippets are blocked from running on the checkout path to reduce risk and improve security.
For more information, refer to the [provider guide](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/saas-customers/provider-guides/shopify/).
May 30, 2025
1. ### [Cloudflare Pages builds now provide Node.js v22 by default](https://developers.cloudflare.com/changelog/2025-05-30-pages-build-image-v3/)
[Pages](https://developers.cloudflare.com/pages/)
When you use the built-in build system that is part of [Cloudflare Pages](https://developers.cloudflare.com/pages/), the [Build Image](https://developers.cloudflare.com/pages/configuration/build-image/) now includes Node.js v22. Previously, Node.js v18 was provided by default, and Node.js v18 is now end-of-life (EOL).
If you are creating a new Pages project, the new V3 build image that includes Node.js v22 will be used by default. If you have an existing Pages project, you can update to the latest build image by navigating to Settings > Build & deployments > Build system version in the Cloudflare dashboard for a specific Pages project.
Note that you can always specify a particular version of Node.js or other built-in dependencies by [setting an environment variable](https://developers.cloudflare.com/pages/configuration/build-image/#override-default-versions).
For more, refer to the [developer docs for Cloudflare Pages builds](https://developers.cloudflare.com/pages/configuration/build-image)
May 29, 2025
1. ### [New Gateway Analytics in the Cloudflare One Dashboard](https://developers.cloudflare.com/changelog/gateway-analytics-v2/)
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Users can now access significant enhancements to Cloudflare Gateway analytics, providing you with unprecedented visibility into your organization's DNS queries, HTTP requests, and Network sessions. These powerful new dashboards enable you to go beyond raw logs and gain actionable insights into how your users are interacting with the Internet and your protected resources.
You can now visualize and explore:
* Patterns Over Time: Understand trends in traffic volume and blocked requests, helping you identify anomalies and plan for future capacity.
* Top Users & Destinations: Quickly pinpoint the most active users, enabling better policy enforcement and resource allocation.
* Actions Taken: See a clear breakdown of security actions applied by Gateway policies, such as blocks and allows, offering a comprehensive view of your security posture.
* Geographic Regions: Gain insight into the global distribution of your traffic.
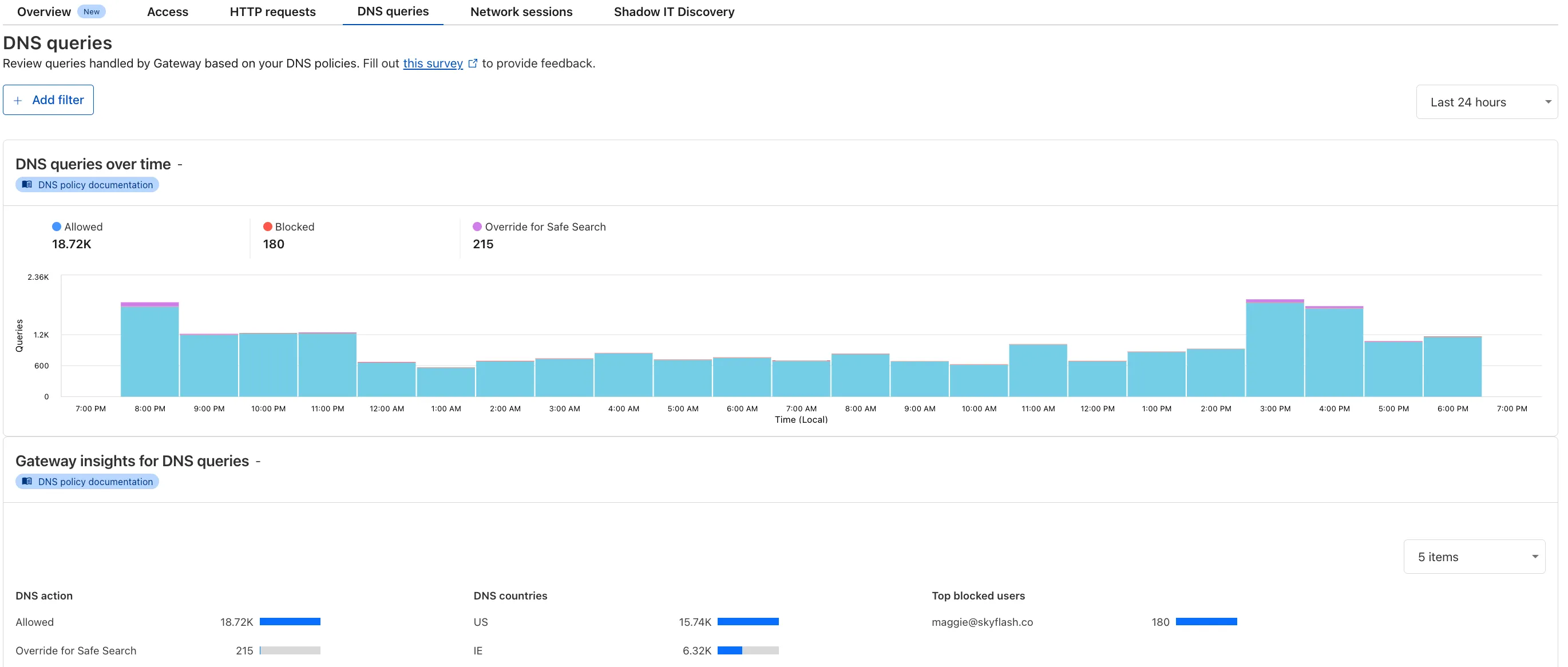
To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and go to Analytics in the side navigation bar.
May 29, 2025
1. ### [50-500ms Faster D1 REST API Requests](https://developers.cloudflare.com/changelog/2025-05-30-d1-rest-api-latency/)
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
Users using Cloudflare's [REST API](https://developers.cloudflare.com/api/resources/d1/) to query their D1 database can see lower end-to-end request latency now that D1 authentication is performed at the closest Cloudflare network data center that received the request. Previously, authentication required D1 REST API requests to proxy to Cloudflare's core, centralized data centers, which added network round trips and latency.
Latency improvements range from 50-500 ms depending on request location and [database location](https://developers.cloudflare.com/d1/configuration/data-location/) and only apply to the REST API. REST API requests and databases outside the United States see a bigger benefit since Cloudflare's primary core data centers reside in the United States.
D1 query endpoints like `/query` and `/raw` have the most noticeable improvements since they no longer access Cloudflare's core data centers. D1 control plane endpoints such as those to create and delete databases see smaller improvements, since they still require access to Cloudflare's core data centers for other control plane metadata.
May 28, 2025
1. ### [Playwright MCP server is now compatible with Browser Rendering](https://developers.cloudflare.com/changelog/2025-05-28-playwright-mcp/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We're excited to share that you can now use the [Playwright MCP](https://github.com/cloudflare/playwright-mcp) server with Browser Rendering.
Once you [deploy the server](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/#deploying), you can use any MCP client with it to interact with Browser Rendering. This allows you to run AI models that can automate browser tasks, such as taking screenshots, filling out forms, or scraping data.
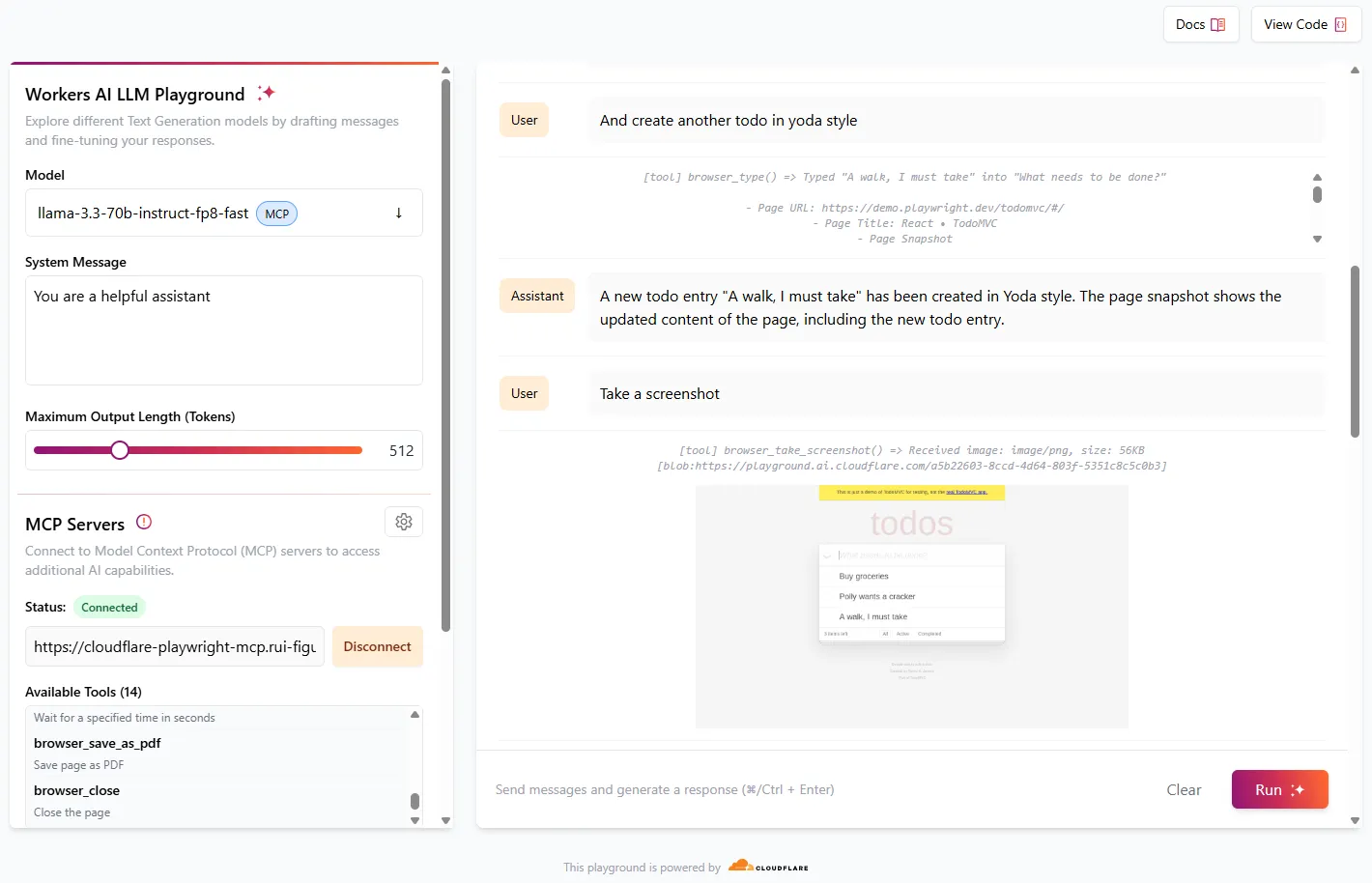
Playwright MCP is available as an npm package at [`@cloudflare/playwright-mcp`](https://www.npmjs.com/package/@cloudflare/playwright-mcp). To install it, type:
* npm
```sh
npm i -D @cloudflare/playwright-mcp
```
* yarn
```sh
yarn add -D @cloudflare/playwright-mcp
```
* pnpm
```sh
pnpm add -D @cloudflare/playwright-mcp
```
Deploying the server is then as easy as:
```ts
import { env } from "cloudflare:workers";
import { createMcpAgent } from "@cloudflare/playwright-mcp";
export const PlaywrightMCP = createMcpAgent(env.BROWSER);
export default PlaywrightMCP.mount("/sse");
```
Check out the full code at [GitHub](https://github.com/cloudflare/playwright-mcp).
Learn more about Playwright MCP in our [documentation](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/).
May 27, 2025
1. ### [Increased limits for Cloudflare for SaaS and Secrets Store free and pay-as-you-go plans](https://developers.cloudflare.com/changelog/2025-05-19-paygo-updates/)
[SSL/TLS ](https://developers.cloudflare.com/ssl/)[Cloudflare for SaaS ](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)[Secrets Store](https://developers.cloudflare.com/secrets-store/)
With upgraded limits to [all free and paid plans](https://www.cloudflare.com/plans/), you can now scale more easily with [Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/) and [Secrets Store](https://developers.cloudflare.com/secrets-store/).
[Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/) allows you to extend the benefits of Cloudflare to your customers via their own custom or vanity domains. Now, the [limit for custom hostnames](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/plans/) on a Cloudflare for SaaS pay-as-you-go plan has been **raised from 5,000 custom hostnames to 50,000 custom hostnames.**
With custom origin server -- previously an enterprise-only feature -- you can route traffic from one or more custom hostnames somewhere other than your default proxy fallback. [Custom origin server](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/advanced-settings/custom-origin/) is now available to Cloudflare for SaaS customers on Free, Pro, and Business plans.
You can enable custom origin server on a per-custom hostname basis [via the API](https://developers.cloudflare.com/api/resources/custom_hostnames/methods/edit/) or the UI:
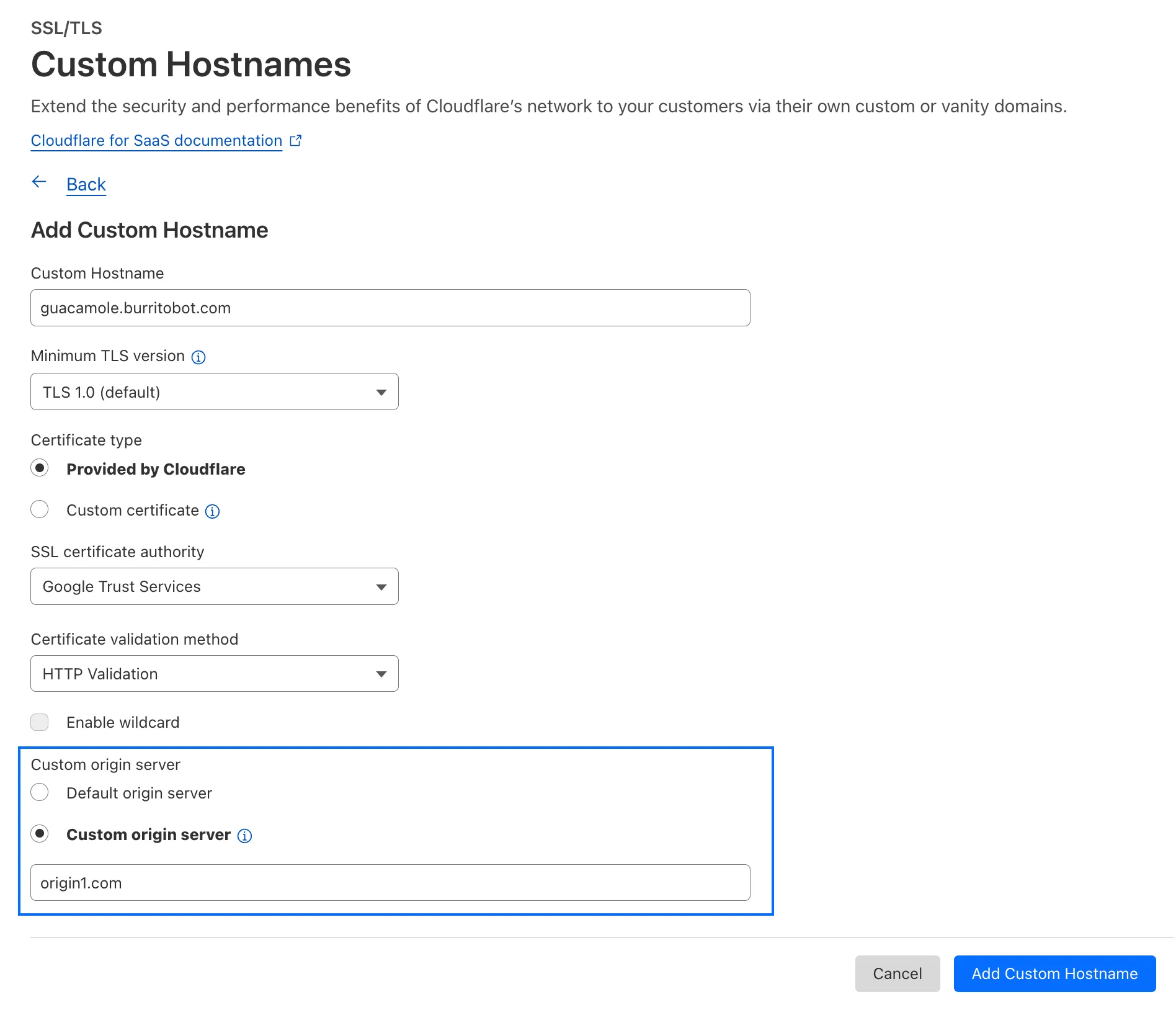
Currently [in beta with a Workers integration](https://blog.cloudflare.com/secrets-store-beta/), [Cloudflare Secrets Store](https://developers.cloudflare.com/secrets-store/) allows you to store, manage, and deploy account level secrets from a secure, centralized platform your [Cloudflare Workers](https://developers.cloudflare.com/workers/). Now, you can create and deploy **100 secrets per account**. Try it out [in the dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store), with [Wrangler](https://developers.cloudflare.com/secrets-store/integrations/workers/), or [via the API](https://developers.cloudflare.com/api/resources/secrets_store/) today.
May 23, 2025
1. ### [New GraphQL Analytics API Explorer and MCP Server](https://developers.cloudflare.com/changelog/2025-05-23-graphql-api-explorer/)
[Analytics](https://developers.cloudflare.com/analytics/)
We’ve launched two powerful new tools to make the GraphQL Analytics API more accessible:
#### GraphQL API Explorer
The new [GraphQL API Explorer](https://graphql.cloudflare.com/explorer) helps you build, test, and run queries directly in your browser. Features include:
* In-browser schema documentation to browse available datasets and fields
* Interactive query editor with autocomplete and inline documentation
* A "Run in GraphQL API Explorer" button to execute example queries from our docs
* Seamless OAuth authentication — no manual setup required
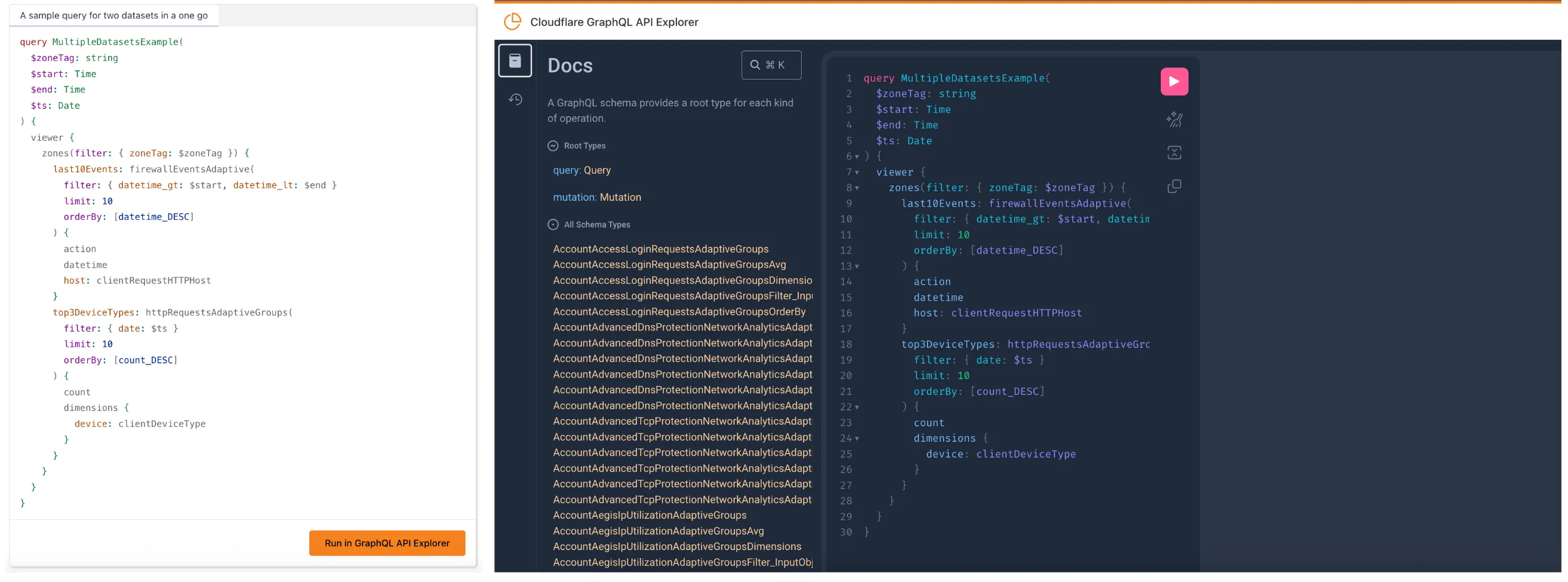
#### GraphQL Model Context Protocol (MCP) Server
MCP Servers let you use natural language tools like Claude to generate structured queries against your data. See our [blog post](https://blog.cloudflare.com/thirteen-new-mcp-servers-from-cloudflare/) for details on how they work and which servers are available. The new [GraphQL MCP server](https://github.com/cloudflare/mcp-server-cloudflare/tree/main/apps/graphql) helps you discover and generate useful queries for the GraphQL Analytics API. With this server, you can:
* Explore what data is available to query
* Generate and refine queries using natural language, with one-click links to run them in the API Explorer
* Build dashboards and visualizations from structured query outputs
Example prompts include:
* “Show me HTTP traffic for the last 7 days for example.com”
* “What GraphQL node returns firewall events?”
* “Can you generate a link to the Cloudflare GraphQL API Explorer with a pre-populated query and variables?”
We’re continuing to expand these tools, and your feedback helps shape what’s next. [Explore the documentation](https://developers.cloudflare.com/analytics/graphql-api/) to learn more and get started.
May 19, 2025
1. ### [Terraform v5.5.0 now available](https://developers.cloudflare.com/changelog/2025-05-19-terraform-v550-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). Unlike the earlier Terraform providers, v5 is automatically generated based on the OpenAPI Schemas for our REST APIs. Since launch, we have seen an unexpectedly high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by customers. These issues currently impact about 15% of resources. We have been working diligently to address these issues across the company, and have released the v5.5.0 release which includes a number of bug fixes. Please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Broad fixes across resources with recurring diffs, including, but not limited to:
* `cloudflare_zero_trust_gateway_policy`
* `cloudflare_zero_trust_access_application`
* `cloudflare_zero_trust_tunnel_cloudflared_route`
* `cloudflare_zone_setting`
* `cloudflare_ruleset`
* `cloudflare_page_rule`
* Zone settings can be re-applied without client errors
* Page rules conversion errors are fixed
* Failure to apply changes to `cloudflare_zero_trust_tunnel_cloudflared_route`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.5.0) in GitHub.
#### Issues Closed
* [#5304: Importing cloudflare\_zero\_trust\_gateway\_policy invalid attribute filter value](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5304)
* [#5303: cloudflare\_page\_rule import does not set values for all of the fields in terraform state](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5303)
* [#5178: cloudflare\_page\_rule Page rule creation with redirect fails](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5178)
* [#5336: cloudflare\_turnstile\_wwidget not able to udpate](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5336)
* [#5418: cloudflare\_cloud\_connector\_rules: Provider returned invalid result object after apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5418)
* [#5423: cloudflare\_zone\_setting: "Invalid value for zone setting always\_use\_https"](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5423)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
If you are evaluating a move from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
May 16, 2025
1. ### [New Access Analytics in the Cloudflare One Dashboard](https://developers.cloudflare.com/changelog/access-analytics-v2/)
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
A new Access Analytics dashboard is now available to all Cloudflare One customers. Customers can apply and combine multiple filters to dive into specific slices of their Access metrics. These filters include:
* Logins granted and denied
* Access events by type (SSO, Login, Logout)
* Application name (Salesforce, Jira, Slack, etc.)
* Identity provider (Okta, Google, Microsoft, onetimepin, etc.)
* Users (`chris@cloudflare.com`, `sally@cloudflare.com`, `rachel@cloudflare.com`, etc.)
* Countries (US, CA, UK, FR, BR, CN, etc.)
* Source IP address
* App type (self-hosted, Infrastructure, RDP, etc.)
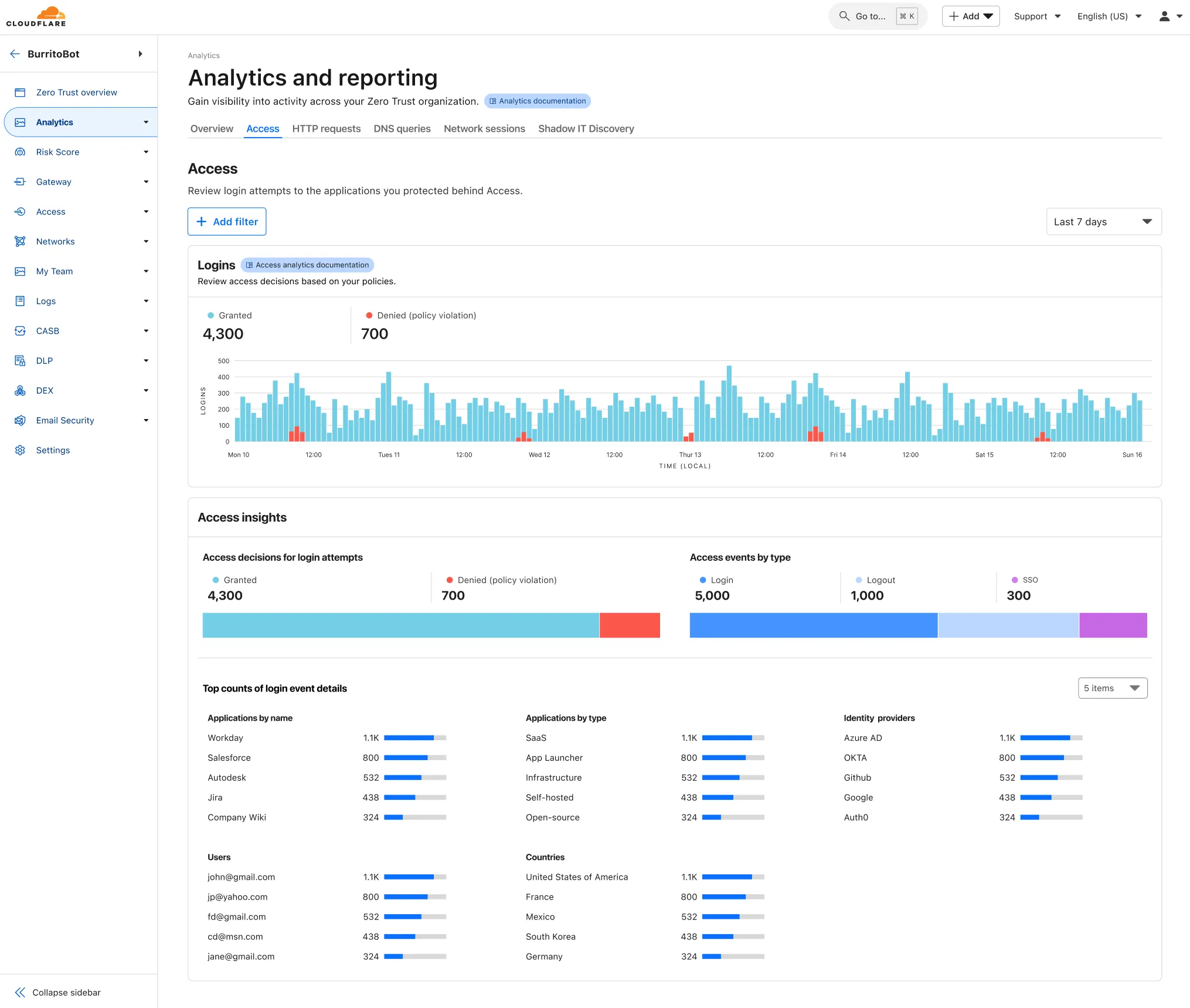
To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and find Analytics in the side navigation bar.
May 16, 2025
1. ### [Durable Objects are now supported in Python Workers](https://developers.cloudflare.com/changelog/2025-05-14-python-worker-durable-object/)
[Workers ](https://developers.cloudflare.com/workers/)[Durable Objects](https://developers.cloudflare.com/durable-objects/)
You can now create [Durable Objects](https://developers.cloudflare.com/durable-objects/) using [Python Workers](https://developers.cloudflare.com/workers/languages/python/). A Durable Object is a special kind of Cloudflare Worker which uniquely combines compute with storage, enabling stateful long-running applications which run close to your users. For more info see [here](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/).
You can define a Durable Object in Python in a similar way to JavaScript:
```python
from workers import DurableObject, Response, WorkerEntrypoint
from urllib.parse import urlparse
class MyDurableObject(DurableObject):
def __init__(self, ctx, env):
self.ctx = ctx
self.env = env
def fetch(self, request):
result = self.ctx.storage.sql.exec("SELECT 'Hello, World!' as greeting").one()
return Response(result.greeting)
class Default(WorkerEntrypoint):
async def fetch(self, request):
url = urlparse(request.url)
id = env.MY_DURABLE_OBJECT.idFromName(url.path)
stub = env.MY_DURABLE_OBJECT.get(id)
greeting = await stub.fetch(request.url)
return greeting
```
Define the Durable Object in your Wrangler configuration file:
* wrangler.jsonc
```jsonc
{
"durable_objects": {
"bindings": [
{
"name": "MY_DURABLE_OBJECT",
"class_name": "MyDurableObject"
}
]
}
}
```
* wrangler.toml
```toml
[[durable_objects.bindings]]
name = "MY_DURABLE_OBJECT"
class_name = "MyDurableObject"
```
Then define the storage backend for your Durable Object:
* wrangler.jsonc
```jsonc
{
"migrations": [
{
"tag": "v1", // Should be unique for each entry
"new_sqlite_classes": [ // Array of new classes
"MyDurableObject"
]
}
]
}
```
* wrangler.toml
```toml
[[migrations]]
tag = "v1"
new_sqlite_classes = [ "MyDurableObject" ]
```
Then test your new Durable Object locally by running `wrangler dev`:
```plaintext
npx wrangler dev
```
Consult the [Durable Objects documentation](https://developers.cloudflare.com/durable-objects/) for more details.
May 14, 2025
1. ### [Hyperdrive achieves FedRAMP Moderate-Impact Authorization](https://developers.cloudflare.com/changelog/2025-05-14-hyperdrive-fedramp/)
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive has been approved for FedRAMP Authorization and is now available in the [FedRAMP Marketplace](https://marketplace.fedramp.gov/products/FR2000863987).
FedRAMP is a U.S. government program that provides standardized assessment and authorization for cloud products and services. As a result of this product update, Hyperdrive has been approved as an authorized service to be used by U.S. federal agencies at the Moderate Impact level.
For detailed information regarding FedRAMP and its implications, please refer to the [official FedRAMP documentation for Cloudflare](https://marketplace.fedramp.gov/products/FR2000863987).
May 14, 2025
1. ### [Introducing Origin Restrictions for Media Transformations](https://developers.cloudflare.com/changelog/2025-05-14-media-transformations-origin-restrictions/)
[Stream](https://developers.cloudflare.com/stream/)
We are adding [source origin restrictions](https://developers.cloudflare.com/stream/transform-videos/sources/) to the Media Transformations beta. This allows customers to restrict what sources can be used to fetch images and video for transformations. This feature is the same as --- and uses the same settings as --- [Image Transformations sources](https://developers.cloudflare.com/images/transform-images/sources/).
When transformations is first enabled, the default setting only allows transformations on images and media from the same website or domain being used to make the transformation request. In other words, by default, requests to `example.com/cdn-cgi/media` can only reference originals on `example.com`.
Adding access to other sources, or allowing any source, [is easy to do](https://developers.cloudflare.com/images/transform-images/sources/) in the **Transformations** tab under **Stream**. Click each domain enabled for Transformations and set its sources list to match the needs of your content. The user making this change will need permission to edit zone settings.
For more information, learn about [Transforming Videos](https://developers.cloudflare.com/stream/transform-videos/).
May 13, 2025
1. ### [SAML HTTP-POST bindings support for RBI](https://developers.cloudflare.com/changelog/2025-05-13-rbi-saml-post-support/)
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
Remote Browser Isolation (RBI) now supports SAML HTTP-POST bindings, enabling seamless authentication for SSO-enabled applications that rely on POST-based SAML responses from Identity Providers (IdPs) within a Remote Browser Isolation session. This update resolves a previous limitation that caused `405` errors during login and improves compatibility with multi-factor authentication (MFA) flows.
With expanded support for major IdPs like Okta and Azure AD, this enhancement delivers a more consistent and user-friendly experience across authentication workflows. Learn how to [set up Remote Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/).
May 12, 2025
1. ### [Case Sensitive Custom Word Lists](https://developers.cloudflare.com/changelog/2025-05-12-case-sensitive-cwl/)
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now configure [custom word lists](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#custom-wordlist) to enforce case sensitivity. This setting supports flexibility where needed and aims to reduce false positives where letter casing is critical.
May 09, 2025
1. ### [Publish messages to Queues directly via HTTP](https://developers.cloudflare.com/changelog/2025-05-09-publish-to-queues-via-http/)
[Queues](https://developers.cloudflare.com/queues/)
You can now publish messages to [Cloudflare Queues](https://developers.cloudflare.com/queues/) directly via HTTP from any service or programming language that supports sending HTTP requests. Previously, publishing to queues was only possible from within [Cloudflare Workers](https://developers.cloudflare.com/workers/). You can already consume from queues via Workers or [HTTP pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/), and now publishing is just as flexible.
Publishing via HTTP requires a [Cloudflare API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with `Queues Edit` permissions for authentication. Here's a simple example:
```bash
curl "https://api.cloudflare.com/client/v4/accounts//queues//messages" \
-X POST \
-H 'Authorization: Bearer ' \
--data '{ "body": { "greeting": "hello", "timestamp": "2025-07-24T12:00:00Z"} }'
```
You can also use our [SDKs](https://developers.cloudflare.com/fundamentals/api/reference/sdks/) for TypeScript, Python, and Go.
To get started with HTTP publishing, check out our [step-by-step example](https://developers.cloudflare.com/queues/examples/publish-to-a-queue-via-http/) and the full API documentation in our [API reference](https://developers.cloudflare.com/api/resources/queues/subresources/messages/methods/push/).
May 07, 2025
1. ### [Send forensic copies to storage without DLP profiles](https://developers.cloudflare.com/changelog/2025-05-07-forensic-copy-update/)
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now [send DLP forensic copies](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#send-http-requests-to-logpush-destination/) to third-party storage for any HTTP policy with an `Allow` or `Block` action, without needing to include a DLP profile. This change increases flexibility for data handling and forensic investigation use cases.
By default, Gateway will send all matched HTTP requests to your configured DLP Forensic Copy jobs.
May 06, 2025
1. ### [UDP and ICMP Monitor Support for Private Load Balancing Endpoints](https://developers.cloudflare.com/changelog/2025-05-06-private-health-monitoring-methods/)
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
Cloudflare Load Balancing now supports **UDP (Layer 4)** and **ICMP (Layer 3)** health monitors for **private endpoints**. This makes it simple to track the health and availability of internal services that don’t respond to HTTP, TCP, or other protocol probes.
#### What you can do:
* Set up **ICMP ping monitors** to check if your private endpoints are reachable.
* Use **UDP monitors** for lightweight health checks on non-TCP workloads, such as DNS, VoIP, or custom UDP-based services.
* Gain better visibility and uptime guarantees for services running behind **Private Network Load Balancing**, without requiring public IP addresses.
This enhancement is ideal for internal applications that rely on low-level protocols, especially when used in conjunction with [**Cloudflare Tunnel**](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/), [**WARP**](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/), and [**Magic WAN**](https://developers.cloudflare.com/magic-wan/) to create a secure and observable private network.
Learn more about [Private Network Load Balancing](https://developers.cloudflare.com/load-balancing/private-network/) or view the full list of [supported health monitor protocols](https://developers.cloudflare.com/load-balancing/monitors/#supported-protocols).
May 06, 2025
1. ### [Terraform v5.4.0 now available](https://developers.cloudflare.com/changelog/2025-05-06-terraform-v540-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). Unlike the earlier Terraform providers, v5 is automatically generated based on the OpenAPI Schemas for our REST APIs. Since launch, we have seen an unexpectedly high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by customers. These issues currently impact about 15% of resources. We have been working diligently to address these issues across the company, and have released the v5.4.0 release which includes a number of bug fixes. Please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Removes the `worker_platforms_script_secret` resource from the provider (see [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade#cloudflare_worker_secret) for alternatives—applicable to both Workers and Workers for Platforms)
* Removes duplicated fields in `cloudflare_cloud_connector_rules` resource
* Fixes `cloudflare_workers_route` id issues [#5134](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5134) [#5501](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5501)
* Fixes issue around refreshing resources that have unsupported response types
Affected resources
* `cloudflare_certificate_pack`
* `cloudflare_registrar_domain`
* `cloudflare_stream_download`
* `cloudflare_stream_webhook`
* `cloudflare_user`
* `cloudflare_workers_kv`
* `cloudflare_workers_script`
* Fixes `cloudflare_workers_kv` state refresh issues
* Fixes issues around configurability of nested properties without computed values for the following resources
Affected resources
* `cloudflare_account`
* `cloudflare_account_dns_settings`
* `cloudflare_account_token`
* `cloudflare_api_token`
* `cloudflare_cloud_connector_rules`
* `cloudflare_custom_ssl`
* `cloudflare_d1_database`
* `cloudflare_dns_record`
* `email_security_trusted_domains`
* `cloudflare_hyperdrive_config`
* `cloudflare_keyless_certificate`
* `cloudflare_list_item`
* `cloudflare_load_balancer`
* `cloudflare_logpush_dataset_job`
* `cloudflare_magic_network_monitoring_configuration`
* `cloudflare_magic_transit_site`
* `cloudflare_magic_transit_site_lan`
* `cloudflare_magic_transit_site_wan`
* `cloudflare_magic_wan_static_route`
* `cloudflare_notification_policy`
* `cloudflare_pages_project`
* `cloudflare_queue`
* `cloudflare_queue_consumer`
* `cloudflare_r2_bucket_cors`
* `cloudflare_r2_bucket_event_notification`
* `cloudflare_r2_bucket_lifecycle`
* `cloudflare_r2_bucket_lock`
* `cloudflare_r2_bucket_sippy`
* `cloudflare_ruleset`
* `cloudflare_snippet_rules`
* `cloudflare_snippets`
* `cloudflare_spectrum_application`
* `cloudflare_workers_deployment`
* `cloudflare_zero_trust_access_application`
* `cloudflare_zero_trust_access_group`
* Fixed defaults that made `cloudflare_workers_script` fail when using Assets
* Fixed Workers Logpush setting in `cloudflare_workers_script` mistakenly being readonly
* Fixed `cloudflare_pages_project` broken when using "source"
The detailed [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.4.0) is available on GitHub.
#### Upgrading
If you are evaluating a move from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues either by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare), or by opening a [support ticket](https://www.support.cloudflare.com/s/?language=en_US).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
May 01, 2025
1. ### [Browser Isolation Overview page for Zero Trust](https://developers.cloudflare.com/changelog/2025-05-01-browser-isolation-overview-page/)
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
A new **Browser Isolation Overview** page is now available in the Cloudflare Zero Trust dashboard. This centralized view simplifies the management of [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/) deployments, providing:
* **Streamlined Onboarding:** Easily set up and manage isolation policies from one location.
* **Quick Testing:** Validate [clientless web application isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/) with ease.
* **Simplified Configuration:** Configure [isolated access applications](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/isolate-application/) and policies efficiently.
* **Centralized Monitoring:** Track aggregate usage and blocked actions.
This update consolidates previously disparate settings, accelerating deployment, improving visibility into isolation activity, and making it easier to ensure your protections are working effectively.
To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and find Browser Isolation in the side navigation bar.
May 01, 2025
1. ### [R2 Dashboard experience gets new updates](https://developers.cloudflare.com/changelog/2025-05-01-r2-dashboard-updates/)
[R2](https://developers.cloudflare.com/r2/)
We're excited to announce several improvements to the [Cloudflare R2](https://developers.cloudflare.com/r2/) dashboard experience that make managing your object storage easier and more intuitive:
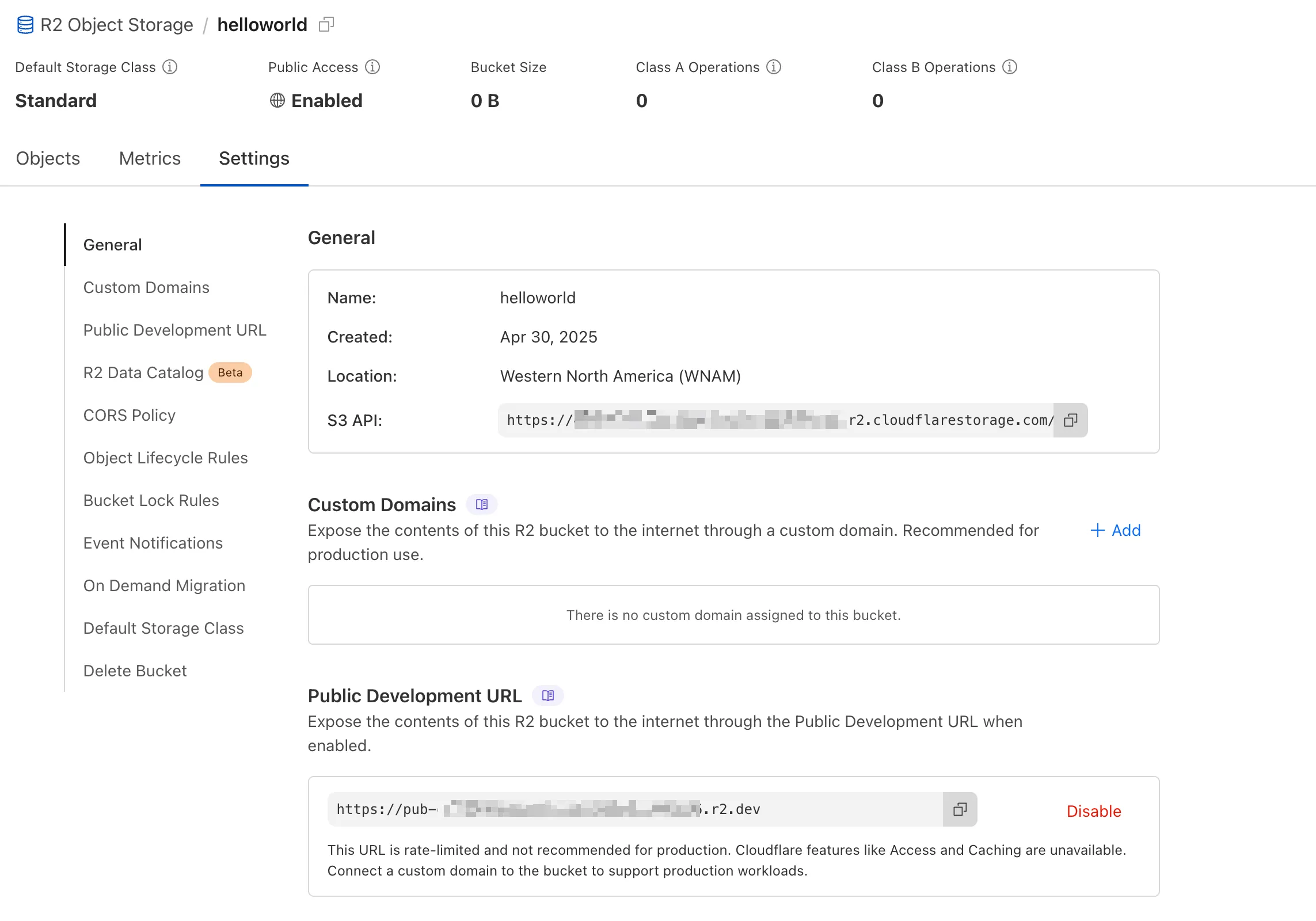
#### All-new settings page
We've redesigned the bucket settings page, giving you a centralized location to manage all your bucket configurations in one place.
#### Improved navigation and sharing
* Deeplink support for prefix directories: Navigate through your bucket hierarchy without losing your state. Your browser's back button now works as expected, and you can share direct links to specific prefix directories with teammates.
* Objects as clickable links: Objects are now proper links that you can copy or `CMD + Click` to open in a new tab.
#### Clearer public access controls
* Renamed "r2.dev domain" to "Public Development URL" for better clarity when exposing bucket contents for non-production workloads.
* Public Access status now clearly displays "Enabled" when your bucket is exposed to the internet (via Public Development URL or Custom Domains).
We've also made numerous other usability improvements across the board to make your R2 experience smoother and more productive.
Apr 17, 2025
1. ### [Increased limits for Queues pull consumers](https://developers.cloudflare.com/changelog/2025-04-17-pull-consumer-limits/)
[Queues](https://developers.cloudflare.com/queues/)
[Queues pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/) can now pull and acknowledge up to **5,000 messages / second per queue**. Previously, pull consumers were rate limited to 1,200 requests / 5 minutes, aggregated across all queues.
Pull consumers allow you to consume messages over HTTP from any environment—including outside of [Cloudflare Workers](https://developers.cloudflare.com/workers). They’re also useful when you need fine-grained control over how quickly messages are consumed.
To setup a new queue with a pull based consumer using [Wrangler](https://developers.cloudflare.com/workers/wrangler/), run:
```sh
npx wrangler queues create my-queue
npx wrangler queues consumer http add my-queue
```
You can also configure a pull consumer using the [REST API](https://developers.cloudflare.com/api/resources/queues/subresources/consumers/methods/create/) or the Queues dashboard.
Once configured, you can pull messages from the queue using any HTTP client. You'll need a [Cloudflare API Token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with `queues_read` and `queues_write` permissions. For example:
```bash
curl "https://api.cloudflare.com/client/v4/accounts/${CF_ACCOUNT_ID}/queues/${QUEUE_ID}/messages/pull" \
--header "Authorization: Bearer ${API_TOKEN}" \
--header "Content-Type: application/json" \
--data '{ "visibility_timeout": 10000, "batch_size": 2 }'
```
To learn more about how to acknowledge messages, pull batches at once, and setup multiple consumers, refer to the [pull consumer documentation](https://developers.cloudflare.com/queues/configuration/pull-consumers).
As always, Queues doesn't charge for data egress. Pull operations continue to be billed at the [existing rate](https://developers.cloudflare.com/queues/platform/pricing), of $0.40 / million operations. The increased limits are available now, on all new and existing queues. If you're new to Queues, [get started with the Cloudflare Queues guide](https://developers.cloudflare.com/queues/get-started).
Apr 17, 2025
1. ### [Read multiple keys from Workers KV with bulk reads](https://developers.cloudflare.com/changelog/2025-04-10-kv-bulk-reads/)
[KV](https://developers.cloudflare.com/kv/)
You can now retrieve up to 100 keys in a single bulk read request made to Workers KV using the binding.
This makes it easier to request multiple KV pairs within a single Worker invocation. Retrieving many key-value pairs using the bulk read operation is more performant than making individual requests since bulk read operations are not affected by [Workers simultaneous connection limits](https://developers.cloudflare.com/workers/platform/limits/#simultaneous-open-connections).
```js
// Read single key
const key = "key-a";
const value = await env.NAMESPACE.get(key);
// Read multiple keys
const keys = ["key-a", "key-b", "key-c", ...] // up to 100 keys
const values : Map = await env.NAMESPACE.get(keys);
// Print the value of "key-a" to the console.
console.log(`The first key is ${values.get("key-a")}.`)
```
Consult the [Workers KV Read key-value pairs API](https://developers.cloudflare.com/kv/api/read-key-value-pairs/) for full details on Workers KV's new bulk reads support.
Apr 15, 2025
1. ### [Fixed and documented Workers Routes and Secrets API](https://developers.cloudflare.com/changelog/2025-04-15-workers-api-fixes/)
[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
#### Workers Routes API
Previously, a request to the Workers [Create Route API](https://developers.cloudflare.com/api/resources/workers/subresources/routes/methods/create/) always returned `null` for "script" and an empty string for "pattern" even if the request was successful.
```bash
curl https://api.cloudflare.com/client/v4/zones/$CF_ACCOUNT_ID/workers/routes \
-X PUT \
-H "Authorization: Bearer $CF_API_TOKEN" \
-H 'Content-Type: application/json' \
--data '{ "pattern": "example.com/*", "script": "hello-world-script" }'
```
```json
{
"result": {
"id": "bf153a27ba2b464bb9f04dcf75de1ef9",
"pattern": "",
"script": null,
"request_limit_fail_open": false
},
"success": true,
"errors": [],
"messages": []
}
```
Now, it properly returns all values!
```json
{
"result": {
"id": "bf153a27ba2b464bb9f04dcf75de1ef9",
"pattern": "example.com/*",
"script": "hello-world-script",
"request_limit_fail_open": false
},
"success": true,
"errors": [],
"messages": []
}
```
#### Workers Secrets API
The [Workers](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/subresources/secrets/) and [Workers for Platforms](https://developers.cloudflare.com/api/resources/workers_for_platforms/subresources/dispatch/subresources/namespaces/subresources/scripts/subresources/secrets/) secrets APIs are now properly documented in the Cloudflare OpenAPI docs. Previously, these endpoints were not publicly documented, leaving users confused on how to directly manage their secrets via the API. Now, you can find the proper endpoints in our public documentation, as well as in our API Library SDKs such as [cloudflare-typescript](https://github.com/cloudflare/cloudflare-typescript) (>4.2.0) and [cloudflare-python](https://github.com/cloudflare/cloudflare-python) (>4.1.0).
Note the `cloudflare_workers_secret` and `cloudflare_workers_for_platforms_script_secret` [Terraform resources](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs) are being removed in a future release. This resource is not recommended for managing secrets. Users should instead use the:
* [Secrets Store](https://developers.cloudflare.com/api/resources/secrets_store/) with the "Secrets Store Secret" binding on Workers and Workers for Platforms Script Upload
* "Secret Text" Binding on [Workers Script Upload](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/methods/update/) and [Workers for Platforms Script Upload](https://developers.cloudflare.com/api/resources/workers_for_platforms/subresources/dispatch/subresources/namespaces/subresources/scripts/methods/update/)
* Workers (and WFP) Secrets API
Apr 11, 2025
1. ### [Signed URLs and Infrastructure Improvements on Stream Live WebRTC Beta](https://developers.cloudflare.com/changelog/2025-04-14-webrtc-beta-signed-urls/)
[Stream](https://developers.cloudflare.com/stream/)
Cloudflare [Stream](https://developers.cloudflare.com/stream/) has completed an infrastructure upgrade for our [Live WebRTC beta](https://developers.cloudflare.com/stream/webrtc-beta/) support which brings increased scalability and improved playback performance to all customers. WebRTC allows broadcasting directly from a browser (or supported WHIP client) with ultra-low latency to tens of thousands of concurrent viewers across the globe.
Additionally, as part of this upgrade, the WebRTC beta now supports Signed URLs to protect playback, just like our standard live stream options (HLS/DASH).
For more information, learn about the [Stream Live WebRTC beta](https://developers.cloudflare.com/stream/webrtc-beta/).
Apr 10, 2025
1. ### [D1 Read Replication Public Beta](https://developers.cloudflare.com/changelog/2025-04-10-d1-read-replication-beta/)
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
D1 read replication is available in public beta to help lower average latency and increase overall throughput for read-heavy applications like e-commerce websites or content management tools.
Workers can leverage read-only database copies, called read replicas, by using D1 [Sessions API](https://developers.cloudflare.com/d1/best-practices/read-replication). A session encapsulates all the queries from one logical session for your application. For example, a session may correspond to all queries coming from a particular web browser session. With Sessions API, D1 queries in a session are guaranteed to be [sequentially consistent](https://developers.cloudflare.com/d1/best-practices/read-replication/#replica-lag-and-consistency-model) to avoid data consistency pitfalls. D1 [bookmarks](https://developers.cloudflare.com/d1/reference/time-travel/#bookmarks) can be used from a previous session to ensure logical consistency between sessions.
```ts
// retrieve bookmark from previous session stored in HTTP header
const bookmark = request.headers.get("x-d1-bookmark") ?? "first-unconstrained";
const session = env.DB.withSession(bookmark);
const result = await session
.prepare(`SELECT * FROM Customers WHERE CompanyName = 'Bs Beverages'`)
.run();
// store bookmark for a future session
response.headers.set("x-d1-bookmark", session.getBookmark() ?? "");
```
Read replicas are automatically created by Cloudflare (currently one in each supported [D1 region](https://developers.cloudflare.com/d1/best-practices/read-replication/#read-replica-locations)), are active/inactive based on query traffic, and are transparently routed to by Cloudflare at no additional cost.
To checkout D1 read replication, deploy the following Worker code using Sessions API, which will prompt you to create a D1 database and enable read replication on said database.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/d1-starter-sessions-api)
To learn more about how read replication was implemented, go to our [blog post](https://blog.cloudflare.com/d1-read-replication-beta).
Apr 10, 2025
1. ### [Cloudflare Pipelines now available in beta](https://developers.cloudflare.com/changelog/2025-04-10-launching-pipelines/)
[Pipelines ](https://developers.cloudflare.com/pipelines/)[R2 ](https://developers.cloudflare.com/r2/)[Workers](https://developers.cloudflare.com/workers/)
[Cloudflare Pipelines](https://developers.cloudflare.com/pipelines) is now available in beta, to all users with a [Workers Paid](https://developers.cloudflare.com/workers/platform/pricing) plan.
Pipelines let you ingest high volumes of real time data, without managing the underlying infrastructure. A single pipeline can ingest up to 100 MB of data per second, via HTTP or from a [Worker](https://developers.cloudflare.com/workers). Ingested data is automatically batched, written to output files, and delivered to an [R2 bucket](https://developers.cloudflare.com/r2) in your account. You can use Pipelines to build a data lake of clickstream data, or to store events from a Worker.
Create your first pipeline with a single command:
```bash
$ npx wrangler@latest pipelines create my-clickstream-pipeline --r2-bucket my-bucket
🌀 Authorizing R2 bucket "my-bucket"
🌀 Creating pipeline named "my-clickstream-pipeline"
✅ Successfully created pipeline my-clickstream-pipeline
Id: 0e00c5ff09b34d018152af98d06f5a1xvc
Name: my-clickstream-pipeline
Sources:
HTTP:
Endpoint: https://0e00c5ff09b34d018152af98d06f5a1xvc.pipelines.cloudflare.com/
Authentication: off
Format: JSON
Worker:
Format: JSON
Destination:
Type: R2
Bucket: my-bucket
Format: newline-delimited JSON
Compression: GZIP
Batch hints:
Max bytes: 100 MB
Max duration: 300 seconds
Max records: 100,000
🎉 You can now send data to your pipeline!
Send data to your pipeline's HTTP endpoint:
curl "https://0e00c5ff09b34d018152af98d06f5a1xvc.pipelines.cloudflare.com/" -d '[{ ...JSON_DATA... }]'
To send data to your pipeline from a Worker, add the following configuration to your config file:
{
"pipelines": [
{
"pipeline": "my-clickstream-pipeline",
"binding": "PIPELINE"
}
]
}
```
Head over to our [getting started guide](https://developers.cloudflare.com/pipelines/getting-started) for an in-depth tutorial to building with Pipelines.
Apr 09, 2025
1. ### [Hyperdrive now supports custom TLS/SSL certificates](https://developers.cloudflare.com/changelog/2025-04-09-hyperdrive-custom-certificate-support/)
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive now supports more SSL/TLS security options for your database connections:
* Configure Hyperdrive to verify server certificates with `verify-ca` or `verify-full` SSL modes and protect against man-in-the-middle attacks
* Configure Hyperdrive to provide client certificates to the database server to authenticate itself (mTLS) for stronger security beyond username and password
Use the new `wrangler cert` commands to create certificate authority (CA) certificate bundles or client certificate pairs:
```bash
# Create CA certificate bundle
npx wrangler cert upload certificate-authority --ca-cert your-ca-cert.pem --name your-custom-ca-name
# Create client certificate pair
npx wrangler cert upload mtls-certificate --cert client-cert.pem --key client-key.pem --name your-client-cert-name
```
Then create a Hyperdrive configuration with the certificates and desired SSL mode:
```bash
npx wrangler hyperdrive create your-hyperdrive-config \
--connection-string="postgres://user:password@hostname:port/database" \
--ca-certificate-id \
--mtls-certificate-id
--sslmode verify-full
```
Learn more about [configuring SSL/TLS certificates for Hyperdrive](https://developers.cloudflare.com/hyperdrive/configuration/tls-ssl-certificates-for-hyperdrive/) to enhance your database security posture.
Apr 09, 2025
1. ### [Cloudflare Secrets Store now available in Beta](https://developers.cloudflare.com/changelog/2025-04-09-secrets-store-beta/)
[Secrets Store ](https://developers.cloudflare.com/secrets-store/)[SSL/TLS](https://developers.cloudflare.com/ssl/)
Cloudflare Secrets Store is available today in Beta. You can now store, manage, and deploy account level secrets from a secure, centralized platform to your Workers.
To spin up your Cloudflare Secrets Store, simply click the new Secrets Store tab [in the dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store) or use this Wrangler command:
```sh
wrangler secrets-store store create --remote
```
The following are supported in the Secrets Store beta:
* Secrets Store UI & API: create your store & create, duplicate, update, scope, and delete a secret
* Workers UI: bind a new or existing account level secret to a Worker and deploy in code
* Wrangler: create your store & create, duplicate, update, scope, and delete a secret
* Account Management UI & API: assign Secrets Store permissions roles & view audit logs for actions taken in Secrets Store core platform
For instructions on how to get started, visit our [developer documentation](https://developers.cloudflare.com/secrets-store/).
Apr 08, 2025
1. ### [Local development support for Email Workers](https://developers.cloudflare.com/changelog/2025-04-08-local-development/)
[Email Routing](https://developers.cloudflare.com/email-routing/)
Email Workers enables developers to programmatically take action on anything that hits their email inbox. If you're building with Email Workers, you can now test the behavior of an Email Worker script, receiving, replying and sending emails in your local environment using `wrangler dev`.
Below is an example that shows you how you can receive messages using the `email()` handler and parse them using [postal-mime](https://www.npmjs.com/package/postal-mime):
```ts
import * as PostalMime from "postal-mime";
export default {
async email(message, env, ctx) {
const parser = new PostalMime.default();
const rawEmail = new Response(message.raw);
const email = await parser.parse(await rawEmail.arrayBuffer());
console.log(email);
},
};
```
Now when you run `npx wrangler dev`, wrangler will expose a local `/cdn-cgi/handler/email` endpoint that you can `POST` email messages to and trigger your Worker's `email()` handler:
```bash
curl -X POST 'http://localhost:8787/cdn-cgi/handler/email' \
--url-query 'from=sender@example.com' \
--url-query 'to=recipient@example.com' \
--header 'Content-Type: application/json' \
--data-raw 'Received: from smtp.example.com (127.0.0.1)
by cloudflare-email.com (unknown) id 4fwwffRXOpyR
for ; Tue, 27 Aug 2024 15:50:20 +0000
From: "John"
Reply-To: sender@example.com
To: recipient@example.com
Subject: Testing Email Workers Local Dev
Content-Type: text/html; charset="windows-1252"
X-Mailer: Curl
Date: Tue, 27 Aug 2024 08:49:44 -0700
Message-ID: <6114391943504294873000@ZSH-GHOSTTY>
Hi there'
```
This is what you get in the console:
```json
{
"headers": [
{
"key": "received",
"value": "from smtp.example.com (127.0.0.1) by cloudflare-email.com (unknown) id 4fwwffRXOpyR for ; Tue, 27 Aug 2024 15:50:20 +0000"
},
{ "key": "from", "value": "\"John\" " },
{ "key": "reply-to", "value": "sender@example.com" },
{ "key": "to", "value": "recipient@example.com" },
{ "key": "subject", "value": "Testing Email Workers Local Dev" },
{ "key": "content-type", "value": "text/html; charset=\"windows-1252\"" },
{ "key": "x-mailer", "value": "Curl" },
{ "key": "date", "value": "Tue, 27 Aug 2024 08:49:44 -0700" },
{
"key": "message-id",
"value": "<6114391943504294873000@ZSH-GHOSTTY>"
}
],
"from": { "address": "sender@example.com", "name": "John" },
"to": [{ "address": "recipient@example.com", "name": "" }],
"replyTo": [{ "address": "sender@example.com", "name": "" }],
"subject": "Testing Email Workers Local Dev",
"messageId": "<6114391943504294873000@ZSH-GHOSTTY>",
"date": "2024-08-27T15:49:44.000Z",
"html": "Hi there\n",
"attachments": []
}
```
Local development is a critical part of the development flow, and also works for sending, replying and forwarding emails. See [our documentation](https://developers.cloudflare.com/email-routing/email-workers/local-development/) for more information.
Apr 08, 2025
1. ### [Hyperdrive Free plan makes fast, global database access available to all](https://developers.cloudflare.com/changelog/2025-04-08-hyperdrive-free-plan/)
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive is now available on the Free plan of Cloudflare Workers, enabling you to build Workers that connect to PostgreSQL or MySQL databases without compromise.
Low-latency access to SQL databases is critical to building full-stack Workers applications. We want you to be able to build on fast, global apps on Workers, regardless of the tools you use. So we made Hyperdrive available for all, to make it easier to build Workers that connect to PostgreSQL and MySQL.
If you want to learn more about how Hyperdrive works, read the [deep dive](https://blog.cloudflare.com/how-hyperdrive-speeds-up-database-access) on how Hyperdrive can make your database queries up to 4x faster.
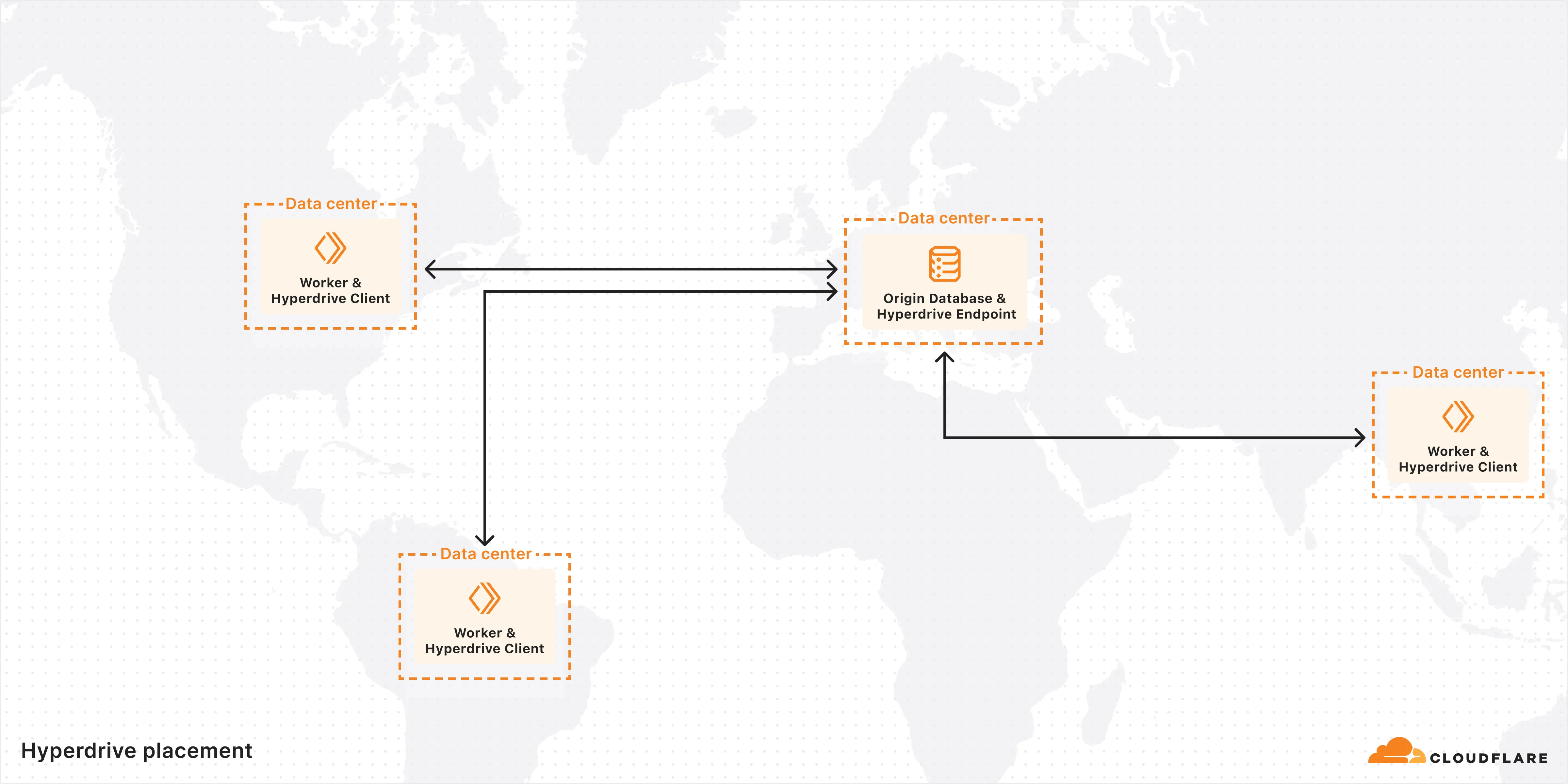
Visit the docs to [get started](https://developers.cloudflare.com/hyperdrive/get-started/) with Hyperdrive for PostgreSQL or MySQL.
Apr 08, 2025
1. ### [Full-stack frameworks are now Generally Available on Cloudflare Workers](https://developers.cloudflare.com/changelog/2025-04-08-fullstack-on-workers/)
[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
The following full-stack frameworks now have Generally Available ("GA") adapters for Cloudflare Workers, and are ready for you to use in production:
* [React Router v7 (Remix)](https://developers.cloudflare.com/workers/framework-guides/web-apps/react-router/)
* [Astro](https://developers.cloudflare.com/workers/framework-guides/web-apps/astro/)
* [Hono](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/hono/)
* [Vue.js](https://developers.cloudflare.com/workers/framework-guides/web-apps/vue/)
* [Nuxt](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/nuxt/)
* [Svelte (SvelteKit)](https://developers.cloudflare.com/workers/framework-guides/web-apps/sveltekit/)
* And [more](https://developers.cloudflare.com/workers/framework-guides/).
The following frameworks are now in **beta**, with GA support coming very soon:
* [Next.js](https://developers.cloudflare.com/workers/framework-guides/web-apps/nextjs/), supported through [@opennextjs/cloudflare](https://opennext.js.org/cloudflare) is now `v1.0-beta`.
* [Angular](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/angular/)
* [SolidJS (SolidStart)](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/solid/)
You can also build complete full-stack apps on Workers **without a framework**:
* You can [“just use Vite"](https://blog.cloudflare.com/introducing-the-cloudflare-vite-plugin) and React together, and build a back-end API in the same Worker. Follow our [React SPA with an API tutorial](https://developers.cloudflare.com/workers/vite-plugin/tutorial/) to learn how.
**Get started building today with our [framework guides](https://developers.cloudflare.com/workers/framework-guides/)**, or read our [Developer Week 2025 blog post](https://blog.cloudflare.com/full-stack-development-on-cloudflare-workers) about all the updates to building full-stack applications on Workers.
Apr 07, 2025
1. ### [Build MCP servers with the Agents SDK](https://developers.cloudflare.com/changelog/2025-04-07-mcp-servers-agents-sdk-updates/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
The Agents SDK now includes built-in support for building remote MCP (Model Context Protocol) servers directly as part of your Agent. This allows you to easily create and manage MCP servers, without the need for additional infrastructure or configuration.
The SDK includes a new `MCPAgent` class that extends the `Agent` class and allows you to expose resources and tools over the MCP protocol, as well as authorization and authentication to enable remote MCP servers.
* JavaScript
```js
export class MyMCP extends McpAgent {
server = new McpServer({
name: "Demo",
version: "1.0.0",
});
async init() {
this.server.resource(`counter`, `mcp://resource/counter`, (uri) => {
// ...
});
this.server.tool(
"add",
"Add two numbers together",
{ a: z.number(), b: z.number() },
async ({ a, b }) => {
// ...
},
);
}
}
```
* TypeScript
```ts
export class MyMCP extends McpAgent {
server = new McpServer({
name: "Demo",
version: "1.0.0",
});
async init() {
this.server.resource(`counter`, `mcp://resource/counter`, (uri) => {
// ...
});
this.server.tool(
"add",
"Add two numbers together",
{ a: z.number(), b: z.number() },
async ({ a, b }) => {
// ...
},
);
}
}
```
See [the example](https://github.com/cloudflare/agents/tree/main/examples/mcp) for the full code and as the basis for building your own MCP servers, and the [client example](https://github.com/cloudflare/agents/tree/main/examples/mcp-client) for how to build an Agent that acts as an MCP client.
To learn more, review the [announcement blog](https://blog.cloudflare.com/building-ai-agents-with-mcp-authn-authz-and-durable-objects) as part of Developer Week 2025.
#### Agents SDK updates
We've made a number of improvements to the [Agents SDK](https://developers.cloudflare.com/agents/), including:
* Support for building MCP servers with the new `MCPAgent` class.
* The ability to export the current agent, request and WebSocket connection context using `import { context } from "agents"`, allowing you to minimize or avoid direct dependency injection when calling tools.
* Fixed a bug that prevented query parameters from being sent to the Agent server from the `useAgent` React hook.
* Automatically converting the `agent` name in `useAgent` or `useAgentChat` to kebab-case to ensure it matches the naming convention expected by [`routeAgentRequest`](https://developers.cloudflare.com/agents/api-reference/routing/).
To install or update the Agents SDK, run `npm i agents@latest` in an existing project, or explore the `agents-starter` project:
```sh
npm create cloudflare@latest -- --template cloudflare/agents-starter
```
See the full release notes and changelog [on the Agents SDK repository](https://github.com/cloudflare/agents/blob/main/packages/agents/CHANGELOG.md) and
Apr 07, 2025
1. ### [Create fully-managed RAG pipelines for your AI applications with AutoRAG](https://developers.cloudflare.com/changelog/2025-04-07-autorag-open-beta/)
[AI Search ](https://developers.cloudflare.com/ai-search/)[Vectorize](https://developers.cloudflare.com/vectorize/)
[AutoRAG](https://developers.cloudflare.com/ai-search/) is now in open beta, making it easy for you to build fully-managed retrieval-augmented generation (RAG) pipelines without managing infrastructure. Just upload your docs to [R2](https://developers.cloudflare.com/r2/get-started/), and AutoRAG handles the rest: embeddings, indexing, retrieval, and response generation via API.
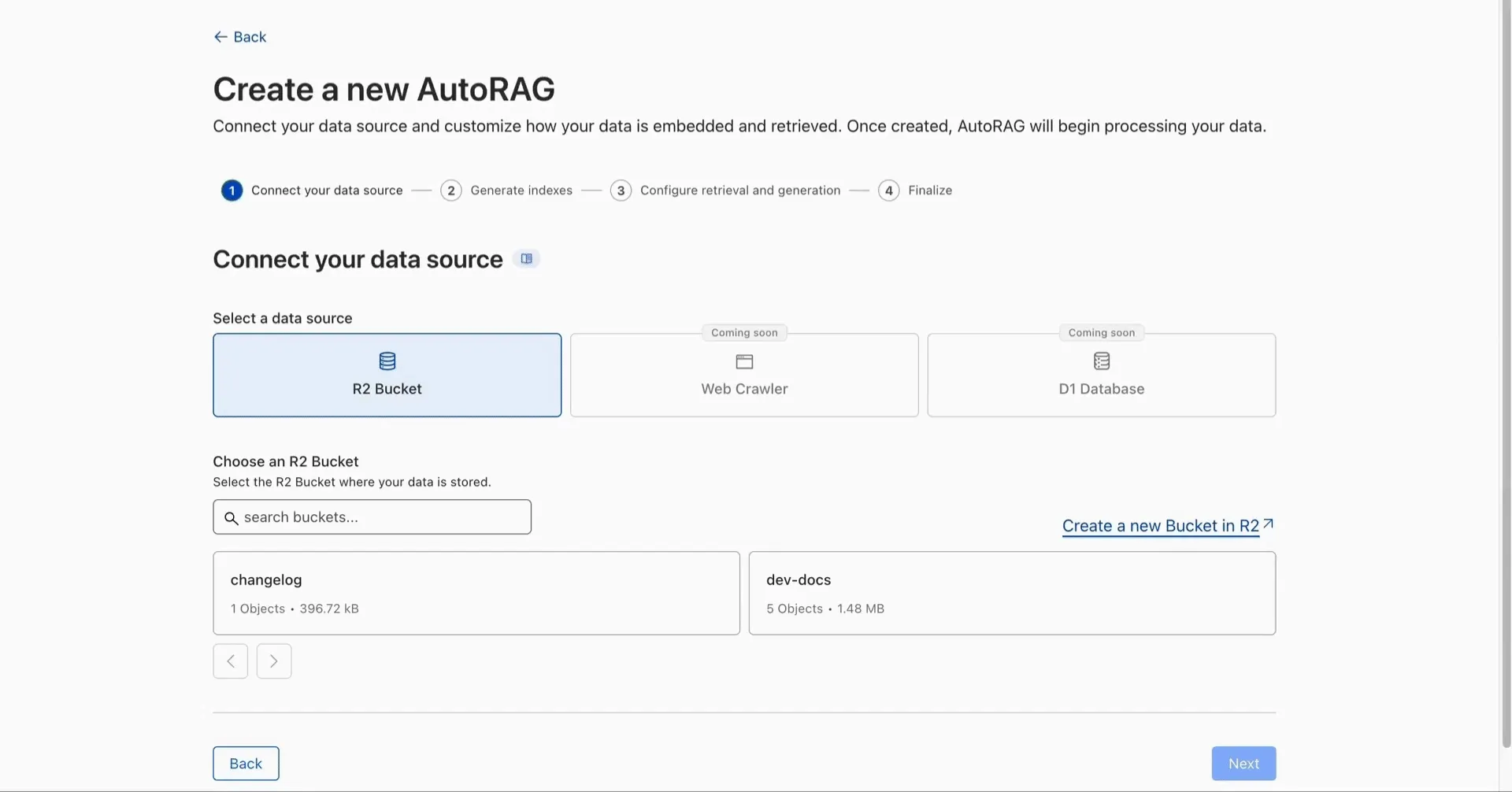
With AutoRAG, you can:
* **Customize your pipeline:** Choose from [Workers AI](https://developers.cloudflare.com/workers-ai) models, configure chunking strategies, edit system prompts, and more.
* **Instant setup:** AutoRAG provisions everything you need from [Vectorize](https://developers.cloudflare.com/vectorize), [AI gateway](https://developers.cloudflare.com/ai-gateway), to pipeline logic for you, so you can go from zero to a working RAG pipeline in seconds.
* **Keep your index fresh:** AutoRAG continuously syncs your index with your data source to ensure responses stay accurate and up to date.
* **Ask questions:** Query your data and receive grounded responses via a [Workers binding](https://developers.cloudflare.com/ai-search/usage/workers-binding/) or [API](https://developers.cloudflare.com/ai-search/usage/rest-api/).
Whether you're building internal tools, AI-powered search, or a support assistant, AutoRAG gets you from idea to deployment in minutes.
Get started in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/ai/autorag) or check out the [guide](https://developers.cloudflare.com/ai-search/get-started/) for instructions on how to build your RAG pipeline today.
Apr 07, 2025
1. ### [Browser Rendering REST API is Generally Available, with new endpoints and a free tier](https://developers.cloudflare.com/changelog/2025-04-07-br-free-ga-playwright/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We’re excited to announce Browser Rendering is now available on the [Workers Free plan](https://www.cloudflare.com/plans/developer-platform/), making it even easier to prototype and experiment with web search and headless browser use-cases when building applications on Workers.
The Browser Rendering **[REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) is now Generally Available**, allowing you to control browser instances from outside of Workers applications. We've added three new endpoints to help automate more browser tasks:
* **Extract structured data** – Use `/json` to retrieve structured data from a webpage.
* **Retrieve links** – Use `/links` to pull all links from a webpage.
* **Convert to Markdown** – Use `/markdown` to convert webpage content into Markdown format.
For example, to fetch the Markdown representation of a webpage:
```bash
curl -X 'POST' 'https://api.cloudflare.com/client/v4/accounts//browser-rendering/markdown' \
-H 'Content-Type: application/json' \
-H 'Authorization: Bearer ' \
-d '{
"url": "https://example.com"
}'
```
For the full list of endpoints, check out our [REST API documentation](https://developers.cloudflare.com/browser-rendering/rest-api/). You can also interact with Browser Rendering via the [Cloudflare TypeScript SDK](https://github.com/cloudflare/cloudflare-typescript).
We also recently landed support for [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) in Browser Rendering for browser automation from Cloudflare [Workers](https://developers.cloudflare.com/workers/), in addition to [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/), giving you more flexibility to test across different browser environments.
Visit the [Browser Rendering docs](https://developers.cloudflare.com/browser-rendering/) to learn more about how to use headless browsers in your applications.
Apr 07, 2025
1. ### [SQLite in Durable Objects GA with 10GB storage per object](https://developers.cloudflare.com/changelog/2025-04-07-sqlite-in-durable-objects-ga/)
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
SQLite in Durable Objects is now generally available (GA) with 10GB SQLite database per Durable Object. Since the [public beta](https://blog.cloudflare.com/sqlite-in-durable-objects/) in September 2024, we've added feature parity and robustness for the SQLite storage backend compared to the preexisting key-value (KV) storage backend for Durable Objects.
SQLite-backed Durable Objects are recommended for all new Durable Object classes, using `new_sqlite_classes` [Wrangler configuration](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#create-sqlite-backed-durable-object-class). Only SQLite-backed Durable Objects have access to Storage API's [SQL](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/#sql-api) and [point-in-time recovery](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/#pitr-point-in-time-recovery-api) methods, which provide relational data modeling, SQL querying, and better data management.
```js
export class MyDurableObject extends DurableObject {
sql: SqlStorage
constructor(ctx: DurableObjectState, env: Env) {
super(ctx, env);
this.sql = ctx.storage.sql;
}
async sayHello() {
let result = this.sql
.exec("SELECT 'Hello, World!' AS greeting")
.one();
return result.greeting;
}
}
```
KV-backed Durable Objects remain for backwards compatibility, and a migration path from key-value storage to SQL storage for existing Durable Object classes will be offered in the future.
For more details on SQLite storage, checkout [Zero-latency SQLite storage in every Durable Object blog](https://blog.cloudflare.com/sqlite-in-durable-objects/).
Apr 07, 2025
1. ### [Durable Objects on Workers Free plan](https://developers.cloudflare.com/changelog/2025-04-07-durable-objects-free-tier/)
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
Durable Objects can now be used with zero commitment on the [Workers Free plan](https://developers.cloudflare.com/workers/platform/pricing/) allowing you to build AI agents with [Agents SDK](https://developers.cloudflare.com/agents/), collaboration tools, and real-time applications like chat or multiplayer games.
Durable Objects let you build stateful, serverless applications with millions of tiny coordination instances that run your application code alongside (in the same thread!) your durable storage. Each Durable Object can access its own SQLite database through a [Storage API](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/). A Durable Object class is defined in a Worker script encapsulating the Durable Object's behavior when accessed from a Worker. To try the code below, click the button:
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/hello-world-do-template)
```js
import { DurableObject } from "cloudflare:workers";
// Durable Object
export class MyDurableObject extends DurableObject {
...
async sayHello(name) {
return `Hello, ${name}!`;
}
}
// Worker
export default {
async fetch(request, env) {
// Every unique ID refers to an individual instance of the Durable Object class
const id = env.MY_DURABLE_OBJECT.idFromName("foo");
// A stub is a client used to invoke methods on the Durable Object
const stub = env.MY_DURABLE_OBJECT.get(id);
// Methods on the Durable Object are invoked via the stub
const response = await stub.sayHello("world");
return response;
},
};
```
Free plan [limits](https://developers.cloudflare.com/durable-objects/platform/pricing/) apply to Durable Objects compute and storage usage. Limits allow developers to build real-world applications, with every Worker request able to call a Durable Object on the free plan.
For more information, checkout:
* [Documentation](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/)
* [Zero-latency SQLite storage in every Durable Object blog](https://blog.cloudflare.com/sqlite-in-durable-objects/)
Apr 07, 2025
1. ### [Workflows is now Generally Available](https://developers.cloudflare.com/changelog/2025-04-07-workflows-ga/)
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
[Workflows](https://developers.cloudflare.com/workflows/) is now *Generally Available* (or "GA"): in short, it's ready for production workloads. Alongside marking Workflows as GA, we've introduced a number of changes during the beta period, including:
* A new `waitForEvent` API that allows a Workflow to wait for an event to occur before continuing execution.
* Increased concurrency: you can [run up to 4,500 Workflow instances](https://developers.cloudflare.com/changelog/2025-02-25-workflows-concurrency-increased/) concurrently — and this will continue to grow.
* Improved observability, including new CPU time metrics that allow you to better understand which Workflow instances are consuming the most resources and/or contributing to your bill.
* Support for `vitest` for testing Workflows locally and in CI/CD pipelines.
Workflows also supports the new [increased CPU limits](https://developers.cloudflare.com/changelog/2025-03-25-higher-cpu-limits/) that apply to Workers, allowing you to run more CPU-intensive tasks (up to 5 minutes of CPU time per instance), not including the time spent waiting on network calls, AI models, or other I/O bound tasks.
#### Human-in-the-loop
The new `step.waitForEvent` API allows a Workflow instance to wait on events and data, enabling human-in-the-the-loop interactions, such as approving or rejecting a request, directly handling webhooks from other systems, or pushing event data to a Workflow while it's running.
Because Workflows are just code, you can conditionally execute code based on the result of a `waitForEvent` call, and/or call `waitForEvent` multiple times in a single Workflow based on what the Workflow needs.
For example, if you wanted to implement a human-in-the-loop approval process, you could use `waitForEvent` to wait for a user to approve or reject a request, and then conditionally execute code based on the result.
* JavaScript
```js
import { Workflow, WorkflowEvent } from "cloudflare:workflows";
export class MyWorkflow extends WorkflowEntrypoint {
async run(event, step) {
// Other steps in your Workflow
let event = await step.waitForEvent(
"receive invoice paid webhook from Stripe",
{ type: "stripe-webhook", timeout: "1 hour" },
);
// Rest of your Workflow
}
}
```
* TypeScript
```ts
import { Workflow, WorkflowEvent } from "cloudflare:workflows";
export class MyWorkflow extends WorkflowEntrypoint {
async run(event: WorkflowEvent, step: WorkflowStep) {
// Other steps in your Workflow
let event = await step.waitForEvent("receive invoice paid webhook from Stripe", { type: "stripe-webhook", timeout: "1 hour" })
// Rest of your Workflow
}
}
```
You can then send a Workflow an event from an external service via HTTP or from within a Worker using the [Workers API](https://developers.cloudflare.com/workflows/build/workers-api/) for Workflows:
* JavaScript
```js
export default {
async fetch(req, env) {
const instanceId = new URL(req.url).searchParams.get("instanceId");
const webhookPayload = await req.json();
let instance = await env.MY_WORKFLOW.get(instanceId);
// Send our event, with `type` matching the event type defined in
// our step.waitForEvent call
await instance.sendEvent({
type: "stripe-webhook",
payload: webhookPayload,
});
return Response.json({
status: await instance.status(),
});
},
};
```
* TypeScript
```ts
export default {
async fetch(req: Request, env: Env) {
const instanceId = new URL(req.url).searchParams.get("instanceId")
const webhookPayload = await req.json()
let instance = await env.MY_WORKFLOW.get(instanceId);
// Send our event, with `type` matching the event type defined in
// our step.waitForEvent call
await instance.sendEvent({type: "stripe-webhook", payload: webhookPayload})
return Response.json({
status: await instance.status(),
});
},
};
```
Read the [GA announcement blog](https://blog.cloudflare.com/workflows-is-now-generally-available/) to learn more about what landed as part of the Workflows GA.
Apr 04, 2025
1. ### [Workers Fetch API can override Cache Rules](https://developers.cloudflare.com/changelog/2025-04-04-workers-fetch-api-override-cache-rules/)
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now programmatically override Cache Rules using the `cf` object in the `fetch()` command. This feature gives you fine-grained control over caching behavior on a per-request basis, allowing Workers to customize cache settings dynamically based on request properties, user context, or business logic.
#### How it works
Using the `cf` object in `fetch()`, you can override specific Cache Rules settings by:
1. **Setting custom cache options**: Pass cache properties in the `cf` object as the second argument to `fetch()` to override default Cache Rules.
2. **Dynamic cache control**: Apply different caching strategies based on request headers, cookies, or other runtime conditions.
3. **Per-request customization**: Bypass or modify Cache Rules for individual requests while maintaining default behavior for others.
4. **Programmatic cache management**: Implement complex caching logic that adapts to your application's needs.
#### What can be configured
Workers can override the following Cache Rules settings through the `cf` object:
* **`cacheEverything`**: Treat all content as static and cache all file types beyond the default cached content.
* **`cacheTtl`**: Set custom time-to-live values in seconds for cached content at the edge, regardless of origin headers.
* **`cacheTtlByStatus`**: Set different TTLs based on the response status code (for example, `{ "200-299": 86400, 404: 1, "500-599": 0 }`).
* **`cacheKey`**: Customize cache keys to control which requests are treated as the same for caching purposes (Enterprise only).
* **`cacheTags`**: Append additional cache tags for targeted cache purging operations.
#### Benefits
* **Enhanced flexibility**: Customize cache behavior without modifying zone-level Cache Rules.
* **Dynamic optimization**: Adjust caching strategies in real-time based on request context.
* **Simplified configuration**: Reduce the number of Cache Rules needed by handling edge cases programmatically.
* **Improved performance**: Fine-tune cache behavior for specific use cases to maximize hit rates.
#### Get started
To get started, refer to the [Workers Fetch API documentation](https://developers.cloudflare.com/workers/runtime-apis/fetch/) and the [cf object properties documentation](https://developers.cloudflare.com/workers/runtime-apis/request/#the-cf-property-requestinitcfproperties).
Apr 03, 2025
1. ### [All cache purge methods now available for all plans](https://developers.cloudflare.com/changelog/2025-04-01-purge-for-all/)
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now access all Cloudflare cache purge methods — no matter which plan you’re on. Whether you need to update a single asset or instantly invalidate large portions of your site’s content, you now have the same powerful tools previously reserved for Enterprise customers.
**Anyone on Cloudflare can now:**
1. [Purge Everything](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-everything/): Clears all cached content associated with a website.
2. [Purge by Prefix](https://developers.cloudflare.com/cache/how-to/purge-cache/purge_by_prefix/): Targets URLs sharing a common prefix.
3. [Purge by Hostname](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-hostname/): Invalidates content by specific hostnames.
4. [Purge by URL (single-file purge)](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-single-file/): Precisely targets individual URLs.
5. [Purge by Tag](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-tags/): Uses Cache-Tag response headers to invalidate grouped assets, offering flexibility for complex cache management scenarios.
Want to learn how each purge method works, when to use them, or what limits apply to your plan? Dive into our [purge cache documentation](https://developers.cloudflare.com/cache/how-to/purge-cache/) and [API reference](https://developers.cloudflare.com/api/resources/cache/methods/purge/) for all the details.
Mar 27, 2025
1. ### [New Pause & Purge APIs for Queues](https://developers.cloudflare.com/changelog/2025-03-25-pause-purge-queues/)
[Queues](https://developers.cloudflare.com/queues/)
[Queues](https://developers.cloudflare.com/queues/) now supports the ability to pause message delivery and/or purge (delete) messages on a queue. These operations can be useful when:
* Your consumer has a bug or downtime, and you want to temporarily stop messages from being processed while you fix the bug
* You have pushed invalid messages to a queue due to a code change during development, and you want to clean up the backlog
* Your queue has a backlog that is stale and you want to clean it up to allow new messages to be consumed
To pause a queue using [Wrangler](https://developers.cloudflare.com/workers/wrangler/), run the `pause-delivery` command. Paused queues continue to receive messages. And you can easily unpause a queue using the `resume-delivery` command.
```bash
$ wrangler queues pause-delivery my-queue
Pausing message delivery for queue my-queue.
Paused message delivery for queue my-queue.
$ wrangler queues resume-delivery my-queue
Resuming message delivery for queue my-queue.
Resumed message delivery for queue my-queue.
```
Purging a queue permanently deletes all messages in the queue. Unlike pausing, purging is an irreversible operation:
```bash
$ wrangler queues purge my-queue
✔ This operation will permanently delete all the messages in queue my-queue. Type my-queue to proceed. … my-queue
Purged queue 'my-queue'
```
You can also do these operations using the [Queues REST API](https://developers.cloudflare.com/api/resources/queues/), or the dashboard page for a queue.
This feature is available on all new and existing queues. Head over to the [pause and purge documentation](https://developers.cloudflare.com/queues/configuration/pause-purge) to learn more. And if you haven't used Cloudflare Queues before, [get started with the Cloudflare Queues guide](https://developers.cloudflare.com/queues/get-started).
Mar 27, 2025
1. ### [Register and renew .ai and .shop domains at cost](https://developers.cloudflare.com/changelog/2025-03-27-ai-domains-available/)
[Registrar](https://developers.cloudflare.com/registrar/)
Cloudflare Registrar now supports `.ai` and `.shop` domains. These are two of our most highly-requested top-level domains (TLDs) and are great additions to the [300+ other TLDs we support](https://domains.cloudflare.com/tlds).
Starting today, customers can:
* Register and renew these domains *at cost* without any markups or add-on fees
* Enjoy best-in-class security and performance with native integrations with Cloudflare DNS, CDN, and SSL services like one-click DNSSEC
* Combat domain hijacking with [Custom Domain Protection](https://www.cloudflare.com/products/registrar/custom-domain-protection/) (available on enterprise plans)
We can't wait to see what AI and e-commerce projects you deploy on Cloudflare. To get started, transfer your domains to Cloudflare or [search for new ones to register](https://domains.cloudflare.com/).
Mar 27, 2025
1. ### [Audit logs (version 2) - Beta Release](https://developers.cloudflare.com/changelog/2025-03-27-automatic-audit-logs-beta-release/)
[Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/)
The latest version of audit logs streamlines audit logging by automatically capturing all user and system actions performed through the Cloudflare Dashboard or public APIs. This update leverages Cloudflare’s existing API Shield to generate audit logs based on OpenAPI schemas, ensuring a more consistent and automated logging process.
Availability: Audit logs (version 2) is now in Beta, with support limited to **API access**.
Use the following API endpoint to retrieve audit logs:
```js
GET https://api.cloudflare.com/client/v4/accounts//logs/audit?since=&before=
```
You can access detailed documentation for audit logs (version 2) Beta API release [here](https://developers.cloudflare.com/api/resources/accounts/subresources/logs/subresources/audit/methods/list/).
**Key Improvements in the Beta Release:**
* **Automated & standardized logging**: Logs are now generated automatically using a standardized system, replacing manual, team-dependent logging. This ensures consistency across all Cloudflare services.
* **Expanded product coverage**: Increased audit log coverage from 75% to 95%. Key API endpoints such as `/accounts`, `/zones`, and `/organizations` are now included.
* **Granular filtering**: Logs now follow a uniform format, enabling precise filtering by actions, users, methods, and resources—allowing for faster and more efficient investigations.
* **Enhanced context and traceability**: Each log entry now includes detailed context, such as the authentication method used, the interface (API or Dashboard) through which the action was performed, and mappings to Cloudflare Ray IDs for better traceability.
* **Comprehensive activity capture**: Expanded logging to include GET requests and failed attempts, ensuring that all critical activities are recorded.
**Known Limitations in Beta**
* Error handling for the API is not implemented.
* There may be gaps or missing entries in the available audit logs.
* UI is unavailable in this Beta release.
* System-level logs and User-Activity logs are not included.
Support for these features is coming as part of the GA release later this year. For more details, including a sample audit log, check out our blog post: [Introducing Automatic Audit Logs](https://blog.cloudflare.com/introducing-automatic-audit-logs/)
Mar 22, 2025
1. ### [New Managed WAF rule for Next.js CVE-2025-29927.](https://developers.cloudflare.com/changelog/2025-03-22-next-js-vulnerability-waf/)
[Workers ](https://developers.cloudflare.com/workers/)[Pages ](https://developers.cloudflare.com/pages/)[WAF](https://developers.cloudflare.com/waf/)
**Update: Mon Mar 24th, 11PM UTC**: Next.js has made further changes to address a smaller vulnerability introduced in the patches made to its middleware handling. Users should upgrade to Next.js versions `15.2.4`, `14.2.26`, `13.5.10` or `12.3.6`. **If you are unable to immediately upgrade or are running an older version of Next.js, you can enable the WAF rule described in this changelog as a mitigation**.
**Update: Mon Mar 24th, 8PM UTC**: Next.js has now [backported the patch for this vulnerability](https://github.com/advisories/GHSA-f82v-jwr5-mffw) to cover Next.js v12 and v13. Users on those versions will need to patch to `13.5.9` and `12.3.5` (respectively) to mitigate the vulnerability.
**Update: Sat Mar 22nd, 4PM UTC**: We have changed this WAF rule to opt-in only, as sites that use auth middleware with third-party auth vendors were observing failing requests.
**We strongly recommend updating your version of Next.js (if eligible)** to the patched versions, as your app will otherwise be vulnerable to an authentication bypass attack regardless of auth provider.
#### Enable the Managed Rule (strongly recommended)
This rule is opt-in only for sites on the Pro plan or above in the [WAF managed ruleset](https://developers.cloudflare.com/waf/managed-rules/).
To enable the rule:
1. Head to Security > WAF > Managed rules in the Cloudflare dashboard for the zone (website) you want to protect.
2. Click the three dots next to **Cloudflare Managed Ruleset** and choose **Edit**
3. Scroll down and choose **Browse Rules**
4. Search for **CVE-2025-29927** (ruleId: `34583778093748cc83ff7b38f472013e`)
5. Change the **Status** to **Enabled** and the **Action** to **Block**. You can optionally set the rule to Log, to validate potential impact before enabling it. Log will not block requests.
6. Click **Next**
7. Scroll down and choose **Save**
This will enable the WAF rule and block requests with the `x-middleware-subrequest` header regardless of Next.js version.
#### Create a WAF rule (manual)
For users on the Free plan, or who want to define a more specific rule, you can create a [Custom WAF rule](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/) to block requests with the `x-middleware-subrequest` header regardless of Next.js version.
To create a custom rule:
1. Head to Security > WAF > Custom rules in the Cloudflare dashboard for the zone (website) you want to protect.
2. Give the rule a name - e.g. `next-js-CVE-2025-29927`
3. Set the matching parameters for the rule match any request where the `x-middleware-subrequest` header `exists` per the rule expression below.
```sh
(len(http.request.headers["x-middleware-subrequest"]) > 0)
```
1. Set the action to 'block'. If you want to observe the impact before blocking requests, set the action to 'log' (and edit the rule later).
2. **Deploy** the rule.
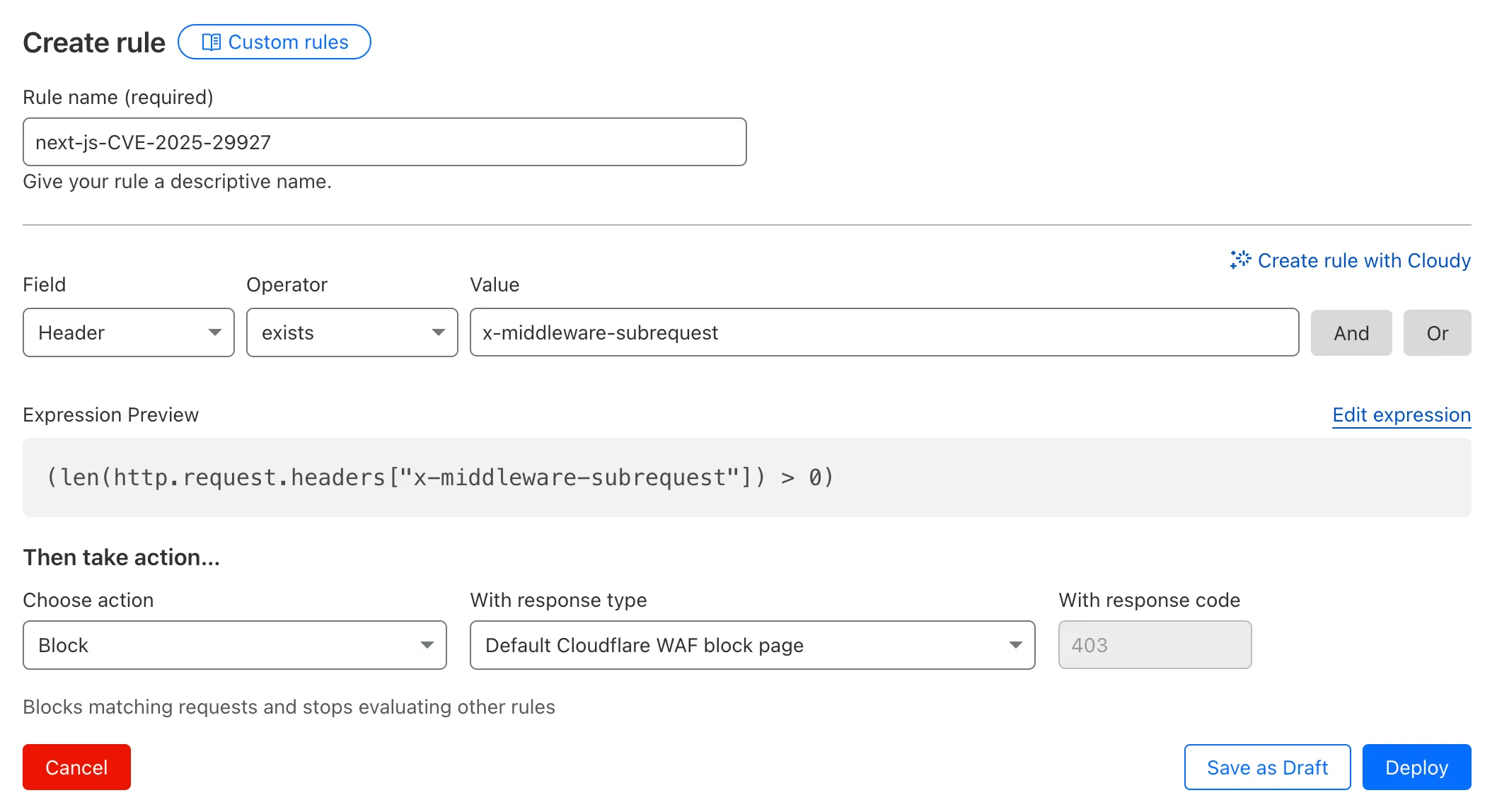
#### Next.js CVE-2025-29927
We've made a WAF (Web Application Firewall) rule available to all sites on Cloudflare to protect against the [Next.js authentication bypass vulnerability](https://github.com/advisories/GHSA-f82v-jwr5-mffw) (`CVE-2025-29927`) published on March 21st, 2025.
**Note**: This rule is not enabled by default as it blocked requests across sites for specific authentication middleware.
* This managed rule protects sites using Next.js on Workers and Pages, as well as sites using Cloudflare to protect Next.js applications hosted elsewhere.
* This rule has been made available (but not enabled by default) to all sites as part of our [WAF Managed Ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/) and blocks requests that attempt to bypass authentication in Next.js applications.
* The vulnerability affects almost all Next.js versions, and has been fully patched in Next.js `14.2.26` and `15.2.4`. Earlier, interim releases did not fully patch this vulnerability.
* **Users on older versions of Next.js (`11.1.4` to `13.5.6`) did not originally have a patch available**, but this the patch for this vulnerability and a subsequent additional patch have been backported to Next.js versions `12.3.6` and `13.5.10` as of Monday, March 24th. Users on Next.js v11 will need to deploy the stated workaround or enable the WAF rule.
The managed WAF rule mitigates this by blocking *external* user requests with the `x-middleware-subrequest` header regardless of Next.js version, but we recommend users using Next.js 14 and 15 upgrade to the patched versions of Next.js as an additional mitigation.
Mar 22, 2025
1. ### [Smart Placement is smarter about running Workers and Pages Functions in the best locations](https://developers.cloudflare.com/changelog/2025-03-22-smart-placement-stablization/)
[Workers ](https://developers.cloudflare.com/workers/)[Pages](https://developers.cloudflare.com/pages/)
[Smart Placement](https://developers.cloudflare.com/workers/configuration/placement/) is a unique Cloudflare feature that can make decisions to move your Worker to run in a more optimal location (such as closer to a database). Instead of always running in the default location (the one closest to where the request is received), Smart Placement uses certain “heuristics” (rules and thresholds) to decide if a different location might be faster or more efficient.
Previously, if these heuristics weren't consistently met, your Worker would revert to running in the default location—even after it had been optimally placed. This meant that if your Worker received minimal traffic for a period of time, the system would reset to the default location, rather than remaining in the optimal one.
Now, once Smart Placement has identified and assigned an optimal location, temporarily dropping below the heuristic thresholds will not force a return to default locations. For example in the previous algorithm, a drop in requests for a few days might return to default locations and heuristics would have to be met again. This was problematic for workloads that made requests to a geographically located resource every few days or longer. In this scenario, your Worker would never get placed optimally. This is no longer the case.
Mar 21, 2025
1. ### [AI Gateway launches Realtime WebSockets API](https://developers.cloudflare.com/changelog/2025-03-20-websockets/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
We are excited to announce that [AI Gateway](https://developers.cloudflare.com/ai-gateway/) now supports real-time AI interactions with the new [Realtime WebSockets API](https://developers.cloudflare.com/ai-gateway/usage/websockets-api/realtime-api/).
This new capability allows developers to establish persistent, low-latency connections between their applications and AI models, enabling natural, real-time conversational AI experiences, including speech-to-speech interactions.
The Realtime WebSockets API works with the [OpenAI Realtime API](https://platform.openai.com/docs/guides/realtime#connect-with-websockets), [Google Gemini Live API](https://ai.google.dev/gemini-api/docs/multimodal-live), and supports real-time text and speech interactions with models from [Cartesia](https://docs.cartesia.ai/api-reference/tts/tts), and [ElevenLabs](https://elevenlabs.io/docs/conversational-ai/api-reference/conversational-ai/websocket).
Here's how you can connect AI Gateway to [OpenAI's Realtime API](https://platform.openai.com/docs/guides/realtime#connect-with-websockets) using WebSockets:
```javascript
import WebSocket from "ws";
const url =
"wss://gateway.ai.cloudflare.com/v1///openai?model=gpt-4o-realtime-preview-2024-12-17";
const ws = new WebSocket(url, {
headers: {
"cf-aig-authorization": process.env.CLOUDFLARE_API_KEY,
Authorization: "Bearer " + process.env.OPENAI_API_KEY,
"OpenAI-Beta": "realtime=v1",
},
});
ws.on("open", () => console.log("Connected to server."));
ws.on("message", (message) => console.log(JSON.parse(message.toString())));
ws.send(
JSON.stringify({
type: "response.create",
response: { modalities: ["text"], instructions: "Tell me a joke" },
}),
);
```
Get started by checking out the [Realtime WebSockets API](https://developers.cloudflare.com/ai-gateway/usage/websockets-api/realtime-api/) documentation.
Mar 21, 2025
1. ### [Dozens of Cloudflare Terraform Provider resources now have proper drift detection](https://developers.cloudflare.com/changelog/2025-03-21-resource-force-replacement-bug/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
In [Cloudflare Terraform Provider](https://github.com/cloudflare/terraform-provider-cloudflare) versions 5.2.0 and above, dozens of resources now have proper drift detection. Before this fix, these resources would indicate they needed to be updated or replaced — even if there was no real change. Now, you can rely on your `terraform plan` to only show what resources are expected to change.
This issue affected [resources](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs) related to these products and features:
* API Shield
* Argo Smart Routing
* Argo Tiered Caching
* Bot Management
* BYOIP
* D1
* DNS
* Email Routing
* Hyperdrive
* Observatory
* Pages
* R2
* Rules
* SSL/TLS
* Waiting Room
* Workers
* Zero Trust
Mar 21, 2025
1. ### [Cloudflare Terraform Provider now properly redacts sensitive values](https://developers.cloudflare.com/changelog/2025-03-21-sensitive-values-redacted/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
In the [Cloudflare Terraform Provider](https://github.com/cloudflare/terraform-provider-cloudflare) versions 5.2.0 and above, sensitive properties of resources are redacted in logs. Sensitive properties in [Cloudflare's OpenAPI Schema](https://raw.githubusercontent.com/cloudflare/api-schemas/refs/heads/main/openapi.yaml) are now annotated with `x-sensitive: true`. This results in proper auto-generation of the corresponding Terraform resources, and prevents sensitive values from being shown when you run Terraform commands.
This issue affected [resources](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs) related to these products and features:
* Alerts and Audit Logs
* Device API
* DLP
* DNS
* Magic Visibility
* Magic WAN
* TLS Certs and Hostnames
* Tunnels
* Turnstile
* Workers
* Zaraz
Mar 18, 2025
1. ### [npm i agents](https://developers.cloudflare.com/changelog/2025-03-18-npm-i-agents/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)

#### `agents-sdk` -> `agents` Updated
📝 **We've renamed the Agents package to `agents`**!
If you've already been building with the Agents SDK, you can update your dependencies to use the new package name, and replace references to `agents-sdk` with `agents`:
```sh
# Install the new package
npm i agents
```
```sh
# Remove the old (deprecated) package
npm uninstall agents-sdk
# Find instances of the old package name in your codebase
grep -r 'agents-sdk' .
# Replace instances of the old package name with the new one
# (or use find-replace in your editor)
sed -i 's/agents-sdk/agents/g' $(grep -rl 'agents-sdk' .)
```
All future updates will be pushed to the new `agents` package, and the older package has been marked as deprecated.
#### Agents SDK updates New
We've added a number of big new features to the Agents SDK over the past few weeks, including:
* You can now set `cors: true` when using `routeAgentRequest` to return permissive default CORS headers to Agent responses.
* The regular client now syncs state on the agent (just like the React version).
* `useAgentChat` bug fixes for passing headers/credentials, including properly clearing cache on unmount.
* Experimental `/schedule` module with a prompt/schema for adding scheduling to your app (with evals!).
* Changed the internal `zod` schema to be compatible with the limitations of Google's Gemini models by removing the discriminated union, allowing you to use Gemini models with the scheduling API.
We've also fixed a number of bugs with state synchronization and the React hooks.
* JavaScript
```js
// via https://github.com/cloudflare/agents/tree/main/examples/cross-domain
export default {
async fetch(request, env) {
return (
// Set { cors: true } to enable CORS headers.
(await routeAgentRequest(request, env, { cors: true })) ||
new Response("Not found", { status: 404 })
);
},
};
```
* TypeScript
```ts
// via https://github.com/cloudflare/agents/tree/main/examples/cross-domain
export default {
async fetch(request: Request, env: Env) {
return (
// Set { cors: true } to enable CORS headers.
(await routeAgentRequest(request, env, { cors: true })) ||
new Response("Not found", { status: 404 })
);
},
} satisfies ExportedHandler;
```
#### Call Agent methods from your client code New
We've added a new [`@unstable_callable()`](https://developers.cloudflare.com/agents/api-reference/agents-api/) decorator for defining methods that can be called directly from clients. This allows you call methods from within your client code: you can call methods (with arguments) and get native JavaScript objects back.
* JavaScript
```js
// server.ts
import { unstable_callable, Agent } from "agents";
export class Rpc extends Agent {
// Use the decorator to define a callable method
@unstable_callable({
description: "rpc test",
})
async getHistory() {
return this.sql`SELECT * FROM history ORDER BY created_at DESC LIMIT 10`;
}
}
```
* TypeScript
```ts
// server.ts
import { unstable_callable, Agent, type StreamingResponse } from "agents";
import type { Env } from "../server";
export class Rpc extends Agent {
// Use the decorator to define a callable method
@unstable_callable({
description: "rpc test",
})
async getHistory() {
return this.sql`SELECT * FROM history ORDER BY created_at DESC LIMIT 10`;
}
}
```
#### agents-starter Updated
We've fixed a number of small bugs in the [`agents-starter`](https://github.com/cloudflare/agents-starter) project — a real-time, chat-based example application with tool-calling & human-in-the-loop built using the Agents SDK. The starter has also been upgraded to use the latest [wrangler v4](https://developers.cloudflare.com/changelog/2025-03-13-wrangler-v4/) release.
If you're new to Agents, you can install and run the `agents-starter` project in two commands:
```sh
# Install it
$ npm create cloudflare@latest agents-starter -- --template="cloudflare/agents-starter"
# Run it
$ npm run start
```
You can use the starter as a template for your own Agents projects: open up `src/server.ts` and `src/client.tsx` to see how the Agents SDK is used.
#### More documentation Updated
We've heard your feedback on the Agents SDK documentation, and we're shipping more API reference material and usage examples, including:
* Expanded [API reference documentation](https://developers.cloudflare.com/agents/api-reference/), covering the methods and properties exposed by the Agents SDK, as well as more usage examples.
* More [Client API](https://developers.cloudflare.com/agents/api-reference/agents-api/#client-api) documentation that documents `useAgent`, `useAgentChat` and the new `@unstable_callable` RPC decorator exposed by the SDK.
* New documentation on how to [route requests to agents](https://developers.cloudflare.com/agents/api-reference/routing/) and (optionally) authenticate clients before they connect to your Agents.
Note that the Agents SDK is continually growing: the type definitions included in the SDK will always include the latest APIs exposed by the `agents` package.
If you're still wondering what Agents are, [read our blog on building AI Agents on Cloudflare](https://blog.cloudflare.com/build-ai-agents-on-cloudflare/) and/or visit the [Agents documentation](https://developers.cloudflare.com/agents/) to learn more.
Mar 18, 2025
1. ### [New API Posture Management for API Shield](https://developers.cloudflare.com/changelog/2025-03-18-api-posture-management/)
[API Shield](https://developers.cloudflare.com/api-shield/)
Now, API Shield **automatically** labels your API inventory with API-specific risks so that you can track and manage risks to your APIs.
View these risks in [Endpoint Management](https://developers.cloudflare.com/api-shield/management-and-monitoring/) by label:

...or in [Security Center Insights](https://developers.cloudflare.com/security-center/security-insights/):
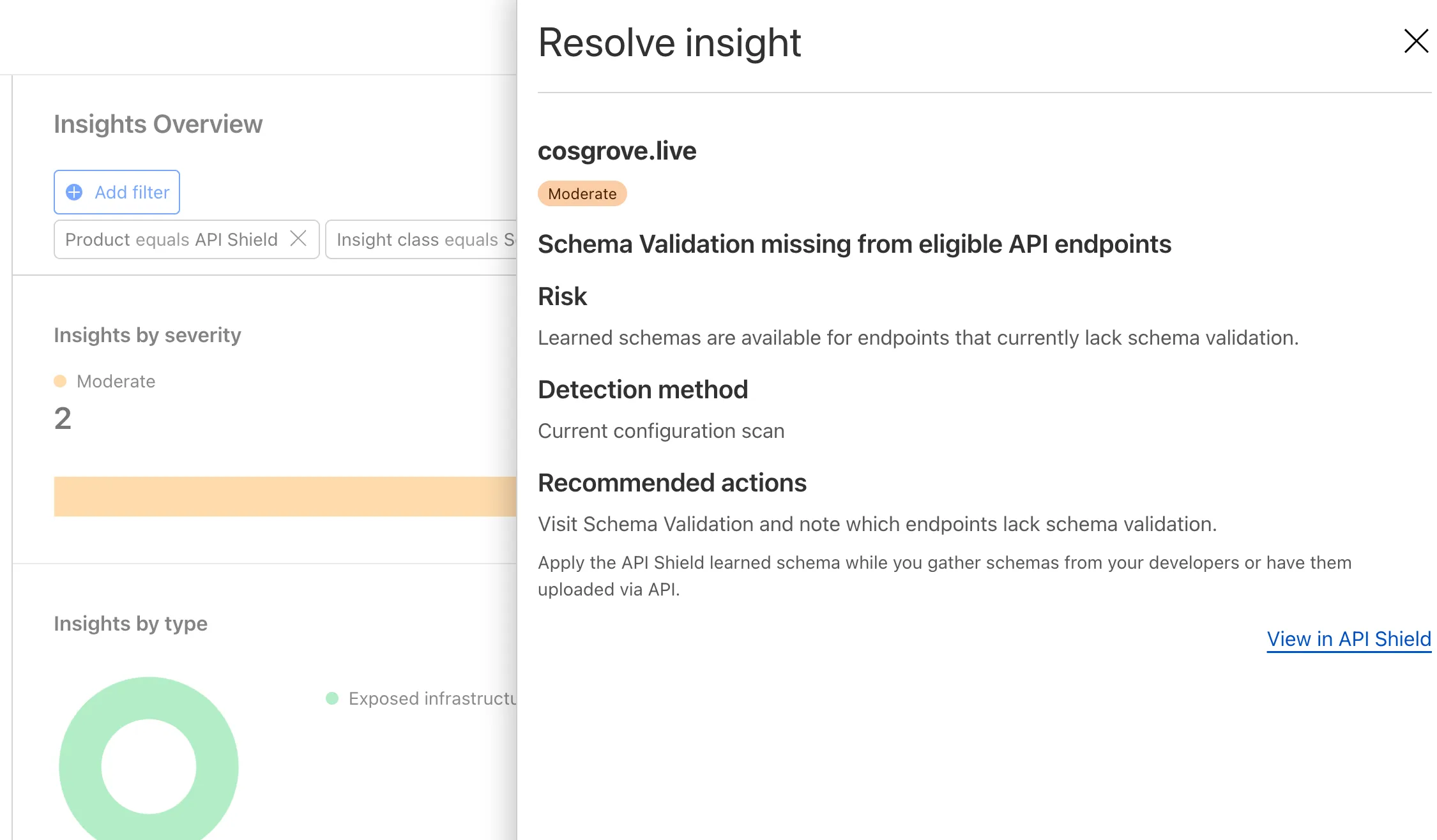
API Shield will scan for risks on your API inventory daily. Here are the new risks we're scanning for and automatically labelling:
* **cf-risk-sensitive**: applied if the customer is subscribed to the [sensitive data detection ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/sensitive-data-detection/) and the WAF detects sensitive data returned on an endpoint in the last seven days.
* **cf-risk-missing-auth**: applied if the customer has configured a session ID and no successful requests to the endpoint contain the session ID.
* **cf-risk-mixed-auth**: applied if the customer has configured a session ID and some successful requests to the endpoint contain the session ID while some lack the session ID.
* **cf-risk-missing-schema**: added when a learned schema is available for an endpoint that has no active schema.
* **cf-risk-error-anomaly**: added when an endpoint experiences a recent increase in response errors over the last 24 hours.
* **cf-risk-latency-anomaly**: added when an endpoint experiences a recent increase in response latency over the last 24 hours.
* **cf-risk-size-anomaly**: added when an endpoint experiences a spike in response body size over the last 24 hours.
In addition, API Shield has two new 'beta' scans for **Broken Object Level Authorization (BOLA) attacks**. If you're in the beta, you will see the following two labels when API Shield suspects an endpoint is suffering from a BOLA vulnerability:
* **cf-risk-bola-enumeration**: added when an endpoint experiences successful responses with drastic differences in the number of unique elements requested by different user sessions.
* **cf-risk-bola-pollution**: added when an endpoint experiences successful responses where parameters are found in multiple places in the request.
We are currently accepting more customers into our beta. Contact your account team if you are interested in BOLA attack detection for your API.
Refer to the [blog post](https://blog.cloudflare.com/cloudflare-security-posture-management/) for more information about Cloudflare's expanded posture management capabilities.
Mar 17, 2025
1. ### [Retry Pages & Workers Builds Directly from GitHub](https://developers.cloudflare.com/changelog/2025-03-17-rerun-build/)
[Workers ](https://developers.cloudflare.com/workers/)[Pages](https://developers.cloudflare.com/pages/)
You can now retry your Cloudflare Pages and Workers builds directly from GitHub. No need to switch to the Cloudflare Dashboard for a simple retry!

Let’s say you push a commit, but your build fails due to a spurious error like a network timeout. Instead of going to the Cloudflare Dashboard to manually retry, you can now rerun the build with just a few clicks inside GitHub, keeping you inside your workflow.
For Pages and Workers projects connected to a GitHub repository:
1. When a build fails, go to your GitHub repository or pull request
2. Select the failed Check Run for the build
3. Select "Details" on the Check Run
4. Select "Rerun" to trigger a retry build for that commit
Learn more about [Pages Builds](https://developers.cloudflare.com/pages/configuration/git-integration/github-integration/) and [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/git-integration/github-integration/).
Mar 13, 2025
1. ### [Cloudflare IP Ranges List](https://developers.cloudflare.com/changelog/2025-03-13-new-managed-iplist/)
[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
Magic Firewall now supports a new managed list of Cloudflare IP ranges. This list is available as an option when creating a Magic Firewall policy based on IP source/destination addresses. When selecting "is in list" or "is not in list", the option "**Cloudflare IP Ranges**" will appear in the dropdown menu.
This list is based on the IPs listed in the Cloudflare [IP ranges](https://www.cloudflare.com/en-gb/ips/). Updates to this managed list are applied automatically.
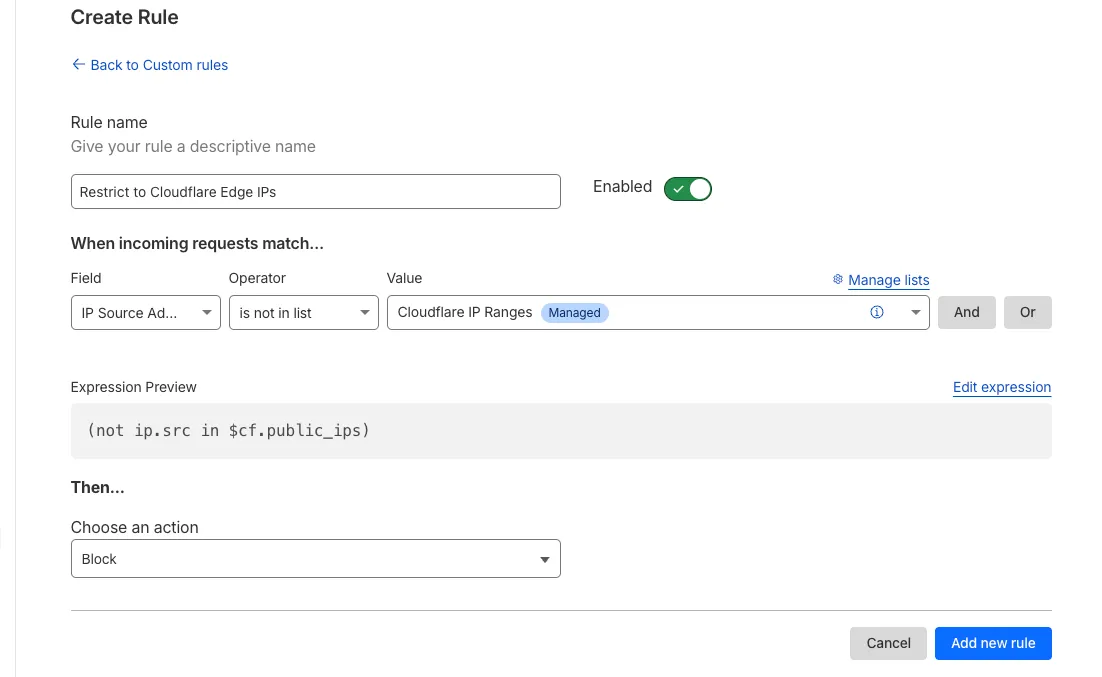
Note: IP Lists require an advanced Magic Firewall subscription. For more details about Magic Firewall plans, refer to [Plans](https://developers.cloudflare.com/magic-firewall/plans).
Mar 12, 2025
1. ### [Threaded replies now possible in Email Workers](https://developers.cloudflare.com/changelog/2025-03-12-reply-limits/)
[Email Routing](https://developers.cloudflare.com/email-routing/)
We’re removing some of the restrictions in Email Routing so that AI Agents and task automation can better handle email workflows, including how Workers can [reply](https://developers.cloudflare.com/email-routing/email-workers/reply-email-workers/) to incoming emails.
It's now possible to keep a threaded email conversation with an [Email Worker](https://developers.cloudflare.com/email-routing/email-workers/) script as long as:
* The incoming email has to have valid [DMARC](https://www.cloudflare.com/learning/dns/dns-records/dns-dmarc-record/).
* The email can only be replied to once in the same `EmailMessage` event.
* The recipient in the reply must match the incoming sender.
* The outgoing sender domain must match the same domain that received the email.
* Every time an email passes through Email Routing or another MTA, an entry is added to the `References` list. We stop accepting replies to emails with more than 100 `References` entries to prevent abuse or accidental loops.
Here's an example of a Worker responding to Emails using a Workers AI model:
```ts
import PostalMime from "postal-mime";
import { createMimeMessage } from "mimetext";
import { EmailMessage } from "cloudflare:email";
export default {
async email(message, env, ctx) {
const email = await PostalMime.parse(message.raw);
const res = await env.AI.run("@cf/meta/llama-2-7b-chat-fp16", {
messages: [
{
role: "user",
content: email.text ?? "",
},
],
});
// message-id is generated by mimetext
const response = createMimeMessage();
response.setHeader("In-Reply-To", message.headers.get("Message-ID")!);
response.setSender("agent@example.com");
response.setRecipient(message.from);
response.setSubject("Llama response");
response.addMessage({
contentType: "text/plain",
data:
res instanceof ReadableStream
? await new Response(res).text()
: res.response!,
});
const replyMessage = new EmailMessage(
"",
message.from,
response.asRaw(),
);
await message.reply(replyMessage);
},
} satisfies ExportedHandler;
```
See [Reply to emails from Workers](https://developers.cloudflare.com/email-routing/email-workers/reply-email-workers/) for more information.
Mar 07, 2025
1. ### [Cloudflare One Agent now supports Endpoint Monitoring](https://developers.cloudflare.com/changelog/2025-03-07-cloudflare-one-device-health-monitoring/)
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into device, network, and application performance across your Cloudflare SASE deployment. The latest release of the Cloudflare One agent (v2025.1.861) now includes device endpoint monitoring capabilities to provide deeper visibility into end-user device performance which can be analyzed directly from the dashboard.
Device health metrics are now automatically collected, allowing administrators to:
* View the last network a user was connected to
* Monitor CPU and RAM utilization on devices
* Identify resource-intensive processes running on endpoints
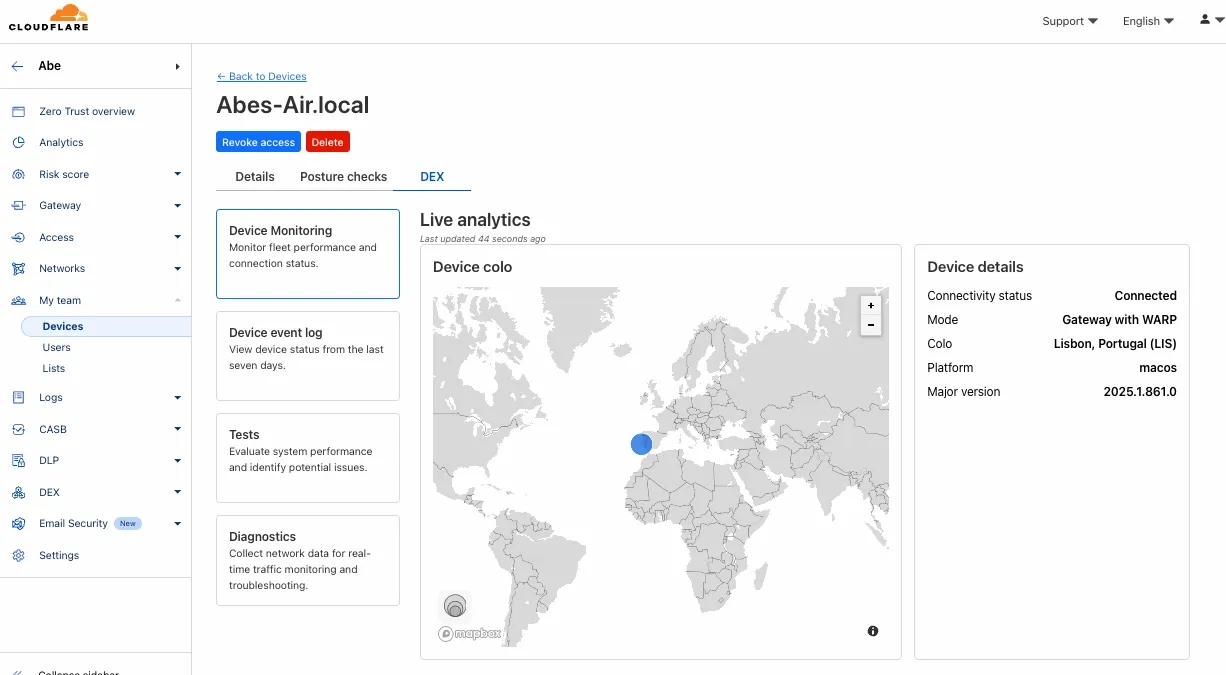
This feature complements existing DEX features like [synthetic application monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/) and [network path visualization](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/traceroute/), creating a comprehensive troubleshooting workflow that connects application performance with device state.
For more details refer to our [DEX](https://developers.cloudflare.com/cloudflare-one/insights/dex/) documentation.
Mar 04, 2025
1. ### [Gain visibility into user actions in Zero Trust Browser Isolation sessions](https://developers.cloudflare.com/changelog/2025-03-03-user-action-logging/)
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
We're excited to announce that new logging capabilities for [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/) through [Logpush](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/) are available in Beta starting today!
With these enhanced logs, administrators can gain visibility into end user behavior in the remote browser and track blocked data extraction attempts, along with the websites that triggered them, in an isolated session.
```json
{
"AccountID": "$ACCOUNT_ID",
"Decision": "block",
"DomainName": "www.example.com",
"Timestamp": "2025-02-27T23:15:06Z",
"Type": "copy",
"UserID": "$USER_ID"
}
```
User Actions available:
* **Copy & Paste**
* **Downloads & Uploads**
* **Printing**
Learn more about how to get started with Logpush in our [documentation](https://developers.cloudflare.com/logs/logpush/).
Feb 26, 2025
1. ### [Introducing Guardrails in AI Gateway](https://developers.cloudflare.com/changelog/2025-02-26-guardrails/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/) now includes [Guardrails](https://developers.cloudflare.com/ai-gateway/features/guardrails/), to help you monitor your AI apps for harmful or inappropriate content and deploy safely.
Within the AI Gateway settings, you can configure:
* **Guardrails**: Enable or disable content moderation as needed.
* **Evaluation scope**: Select whether to moderate user prompts, model responses, or both.
* **Hazard categories**: Specify which categories to monitor and determine whether detected inappropriate content should be blocked or flagged.
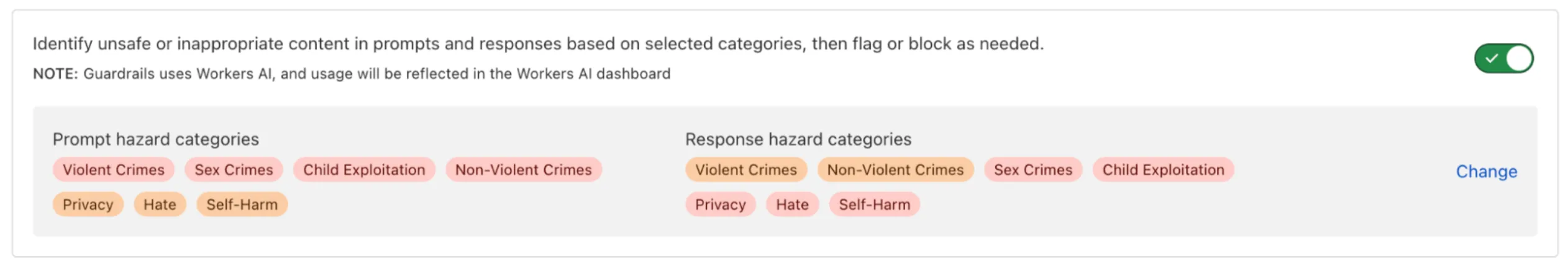
Learn more in the [blog](https://blog.cloudflare.com/guardrails-in-ai-gateway/) or our [documentation](https://developers.cloudflare.com/ai-gateway/features/guardrails/).
Feb 25, 2025
1. ### [Introducing the Agents SDK](https://developers.cloudflare.com/changelog/2025-02-25-agents-sdk/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We've released the [Agents SDK](http://blog.cloudflare.com/build-ai-agents-on-cloudflare/), a package and set of tools that help you build and ship AI Agents.
You can get up and running with a [chat-based AI Agent](https://github.com/cloudflare/agents-starter) (and deploy it to Workers) that uses the Agents SDK, tool calling, and state syncing with a React-based front-end by running the following command:
```sh
npm create cloudflare@latest agents-starter -- --template="cloudflare/agents-starter"
# open up README.md and follow the instructions
```
You can also add an Agent to any existing Workers application by installing the `agents` package directly
```sh
npm i agents
```
... and then define your first Agent:
```ts
import { Agent } from "agents";
export class YourAgent extends Agent {
// Build it out
// Access state on this.state or query the Agent's database via this.sql
// Handle WebSocket events with onConnect and onMessage
// Run tasks on a schedule with this.schedule
// Call AI models
// ... and/or call other Agents.
}
```
Head over to the [Agents documentation](https://developers.cloudflare.com/agents/) to learn more about the Agents SDK, the SDK APIs, as well as how to test and deploying agents to production.
Feb 25, 2025
1. ### [Concurrent Workflow instances limits increased.](https://developers.cloudflare.com/changelog/2025-02-25-workflows-concurrency-increased/)
[Workflows](https://developers.cloudflare.com/workflows/)
[Workflows](https://developers.cloudflare.com/workflows/) now supports up to 4,500 concurrent (running) instances, up from the previous limit of 100. This limit will continue to increase during the Workflows open beta. This increase applies to all users on the Workers Paid plan, and takes effect immediately.
Review the Workflows [limits documentation](https://developers.cloudflare.com/workflows/reference/limits) and/or dive into the [get started guide](https://developers.cloudflare.com/workflows/get-started/guide/) to start building on Workflows.
Feb 24, 2025
1. ### [Bind the Images API to your Worker](https://developers.cloudflare.com/changelog/2025-02-21-images-bindings-in-workers/)
[Cloudflare Images](https://developers.cloudflare.com/images/)
You can now [interact with the Images API](https://developers.cloudflare.com/images/transform-images/bindings/) directly in your Worker.
This allows more fine-grained control over transformation request flows and cache behavior. For example, you can resize, manipulate, and overlay images without requiring them to be accessible through a URL.
The Images binding can be configured in the Cloudflare dashboard for your Worker or in the Wrangler configuration file in your project's directory:
* wrangler.jsonc
```jsonc
{
"images": {
"binding": "IMAGES", // i.e. available in your Worker on env.IMAGES
},
}
```
* wrangler.toml
```toml
[images]
binding = "IMAGES"
```
Within your Worker code, you can interact with this binding by using `env.IMAGES`.
Here's how you can rotate, resize, and blur an image, then output the image as AVIF:
```ts
const info = await env.IMAGES.info(stream);
// stream contains a valid image, and width/height is available on the info object
const response = (
await env.IMAGES.input(stream)
.transform({ rotate: 90 })
.transform({ width: 128 })
.transform({ blur: 20 })
.output({ format: "image/avif" })
).response();
return response;
```
For more information, refer to [Images Bindings](https://developers.cloudflare.com/images/transform-images/bindings/).
Feb 24, 2025
1. ### [Zaraz moves to the “Tag Management” category in the Cloudflare dashboard](https://developers.cloudflare.com/changelog/2025-02-24-zaraz-dash-placement/)
[Zaraz](https://developers.cloudflare.com/zaraz/)
Previously, you could only configure Zaraz by going to each individual zone under your Cloudflare account. Now, if you’d like to get started with Zaraz or manage your existing configuration, you can navigate to the [Tag Management](https://dash.cloudflare.com/?to=/:account/tag-management/zaraz) section on the Cloudflare dashboard – this will make it easier to compare and configure the same settings across multiple zones.
These changes will not alter any existing configuration or entitlements for zones you already have Zaraz enabled on. If you’d like to edit existing configurations, you can go to the [Tag Setup](https://dash.cloudflare.com/?to=/:account/tag-management/zaraz) section of the dashboard, and select the zone you'd like to edit.
Feb 20, 2025
1. ### [Workers for Platforms - Instant dispatch for newly created User Workers](https://developers.cloudflare.com/changelog/2025-02-20-synchronous-uploads/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/) is an architecture wherein a centralized [dispatch Worker](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/#dynamic-dispatch-worker) processes incoming requests and routes them to isolated sub-Workers, called [User Workers](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/#user-workers).
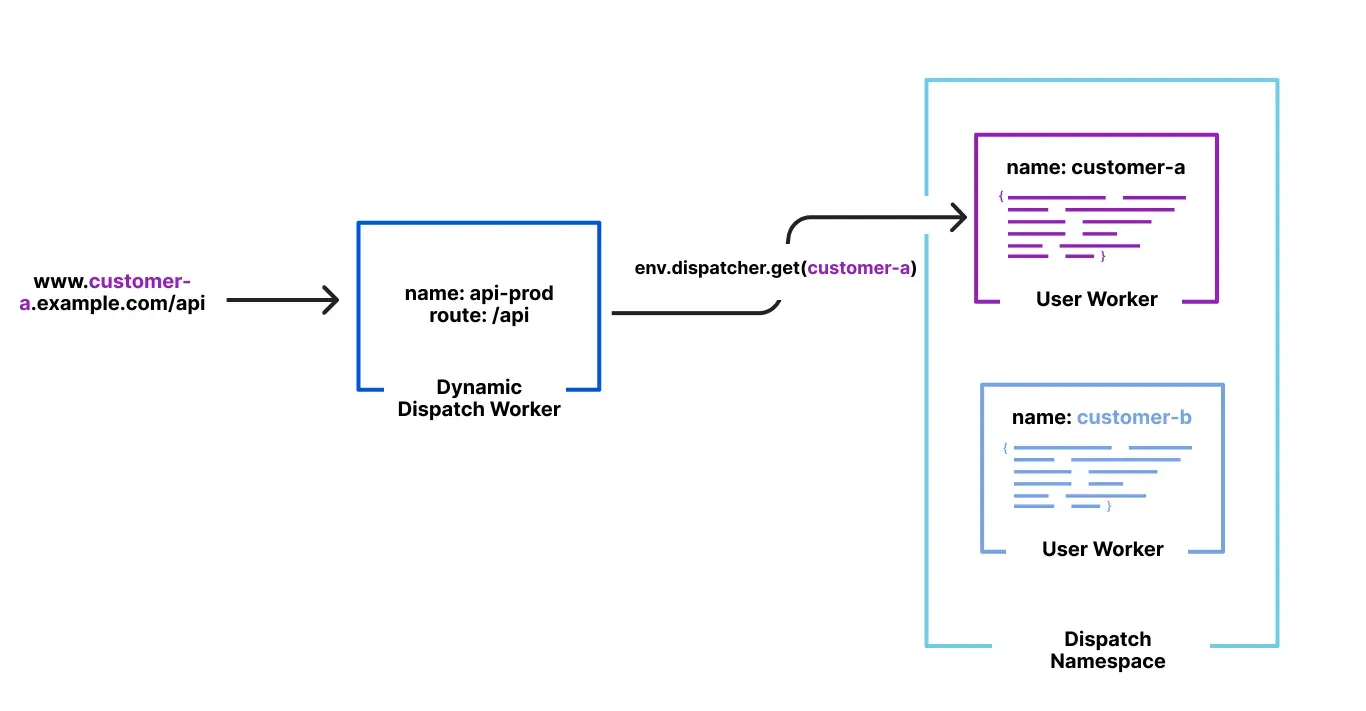
Previously, when a new User Worker was uploaded, there was a short delay before it became available for dispatch. This meant that even though an API request could return a 200 OK response, the script might not yet be ready to handle requests, causing unexpected failures for platforms that immediately dispatch to new Workers.
**With this update, first-time uploads of User Workers are now deployed synchronously**. A 200 OK response guarantees the script is fully provisioned and ready to handle traffic immediately, ensuring more predictable deployments and reducing errors.
Feb 14, 2025
1. ### [Build AI Agents with Example Prompts](https://developers.cloudflare.com/changelog/2025-02-14-example-ai-prompts/)
[Agents ](https://developers.cloudflare.com/agents/)[Workers ](https://developers.cloudflare.com/workers/)[Workflows](https://developers.cloudflare.com/workflows/)
We've added an [example prompt](https://developers.cloudflare.com/workers/get-started/prompting/) to help you get started with building AI agents and applications on Cloudflare [Workers](https://developers.cloudflare.com/workers/), including [Workflows](https://developers.cloudflare.com/workflows/), [Durable Objects](https://developers.cloudflare.com/durable-objects/), and [Workers KV](https://developers.cloudflare.com/kv/).
You can use this prompt with your favorite AI model, including Claude 3.5 Sonnet, OpenAI's o3-mini, Gemini 2.0 Flash, or Llama 3.3 on Workers AI. Models with large context windows will allow you to paste the prompt directly: provide your own prompt within the `` tags.
```sh
{paste_prompt_here}
user: Build an AI agent using Cloudflare Workflows. The Workflow should run when a new GitHub issue is opened on a specific project with the label 'help' or 'bug', and attempt to help the user troubleshoot the issue by calling the OpenAI API with the issue title and description, and a clear, structured prompt that asks the model to suggest 1-3 possible solutions to the issue. Any code snippets should be formatted in Markdown code blocks. Documentation and sources should be referenced at the bottom of the response. The agent should then post the response to the GitHub issue. The agent should run as the provided GitHub bot account.
```
This prompt is still experimental, but we encourage you to try it out and [provide feedback](https://github.com/cloudflare/cloudflare-docs/issues/new?template=content.edit.yml).
Feb 14, 2025
1. ### [Configure your Magic WAN Connector to connect via static IP assigment](https://developers.cloudflare.com/changelog/2025-02-14-local-console-access/)
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
You can now locally configure your [Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/) to work in a static IP configuration.
This local method does not require having access to a DHCP Internet connection. However, it does require being comfortable with using tools to access the serial port on Magic WAN Connector as well as using a serial terminal client to access the Connector's environment.
For more details, refer to [WAN with a static IP address](https://developers.cloudflare.com/magic-wan/configuration/connector/configure-hardware-connector/#bootstrap-via-serial-console).
Feb 14, 2025
1. ### [Upload a certificate bundle with an RSA and ECDSA certificate per custom hostname](https://developers.cloudflare.com/changelog/2025-02-14-cert-bundling-for-custom-hostnames/)
[SSL/TLS](https://developers.cloudflare.com/ssl/)
Cloudflare has supported both RSA and ECDSA certificates across our platform for a number of years. Both certificates offer the same security, but ECDSA is more performant due to a smaller key size. However, RSA is more widely adopted and ensures compatibility with legacy clients. Instead of choosing between them, you may want both – that way, ECDSA is used when clients support it, but RSA is available if not.
Now, you can upload both an RSA and ECDSA certificate on a custom hostname via the API.
```plaintext
curl -X POST https://api.cloudflare.com/client/v4/zones/$ZONE_ID/custom_hostnames \
-H 'Content-Type: application/json' \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY" \
-d '{
"hostname": "hostname",
"ssl": {
"custom_cert_bundle": [
{
"custom_certificate": "RSA Cert",
"custom_key": "RSA Key"
},
{
"custom_certificate": "ECDSA Cert",
"custom_key": "ECDSA Key"
}
],
"bundle_method": "force",
"wildcard": false,
"settings": {
"min_tls_version": "1.0"
}
}
}’
```
You can also:
* [Upload](https://developers.cloudflare.com/api/resources/custom_hostnames/methods/create/) an RSA or ECDSA certificate to a custom hostname with an existing ECDSA or RSA certificate, respectively.
* [Replace](https://developers.cloudflare.com/api/resources/custom_hostnames/subresources/certificate_pack/subresources/certificates/methods/update/) the RSA or ECDSA certificate with a certificate of its same type.
* [Delete](https://developers.cloudflare.com/api/resources/custom_hostnames/subresources/certificate_pack/subresources/certificates/methods/delete/) the RSA or ECDSA certificate (if the custom hostname has both an RSA and ECDSA uploaded).
This feature is available for Business and Enterprise customers who have purchased custom certificates.
Feb 06, 2025
1. ### [Request timeouts and retries with AI Gateway](https://developers.cloudflare.com/changelog/2025-02-05-aig-request-handling/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
AI Gateway adds additional ways to handle requests - [Request Timeouts](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-timeouts) and [Request Retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries), making it easier to keep your applications responsive and reliable.
Timeouts and retries can be used on both the [Universal Endpoint](https://developers.cloudflare.com/ai-gateway/usage/universal/) or directly to a [supported provider](https://developers.cloudflare.com/ai-gateway/usage/providers/).
**Request timeouts** A [request timeout](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-timeouts) allows you to trigger [fallbacks](https://developers.cloudflare.com/ai-gateway/configuration/fallbacks/) or a retry if a provider takes too long to respond.
To set a request timeout directly to a provider, add a `cf-aig-request-timeout` header.
```bash
curl https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/workers-ai/@cf/meta/llama-3.1-8b-instruct \
--header 'Authorization: Bearer {cf_api_token}' \
--header 'Content-Type: application/json' \
--header 'cf-aig-request-timeout: 5000'
--data '{"prompt": "What is Cloudflare?"}'
```
**Request retries** A [request retry](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) automatically retries failed requests, so you can recover from temporary issues without intervening.
To set up request retries directly to a provider, add the following headers:
* cf-aig-max-attempts (number)
* cf-aig-retry-delay (number)
* cf-aig-backoff ("constant" | "linear" | "exponential)
Feb 05, 2025
1. ### [AI Gateway adds Cerebras, ElevenLabs, and Cartesia as new providers](https://developers.cloudflare.com/changelog/2025-02-04-aig-provider-cartesia-eleven-cerebras/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/) has added three new providers: [Cartesia](https://developers.cloudflare.com/ai-gateway/usage/providers/cartesia/), [Cerebras](https://developers.cloudflare.com/ai-gateway/usage/providers/cerebras/), and [ElevenLabs](https://developers.cloudflare.com/ai-gateway/usage/providers/elevenlabs/), giving you more even more options for providers you can use through AI Gateway. Here's a brief overview of each:
* [Cartesia](https://developers.cloudflare.com/ai-gateway/usage/providers/cartesia/) provides text-to-speech models that produce natural-sounding speech with low latency.
* [Cerebras](https://developers.cloudflare.com/ai-gateway/usage/providers/cerebras/) delivers low-latency AI inference to Meta's Llama 3.1 8B and Llama 3.3 70B models.
* [ElevenLabs](https://developers.cloudflare.com/ai-gateway/usage/providers/elevenlabs/) offers text-to-speech models with human-like voices in 32 languages.
To get started with AI Gateway, just update the base URL. Here's how you can send a request to [Cerebras](https://developers.cloudflare.com/ai-gateway/usage/providers/cerebras/) using cURL:
```bash
curl -X POST https://gateway.ai.cloudflare.com/v1/ACCOUNT_TAG/GATEWAY/cerebras/chat/completions \
--header 'content-type: application/json' \
--header 'Authorization: Bearer CEREBRAS_TOKEN' \
--data '{
"model": "llama-3.3-70b",
"messages": [
{
"role": "user",
"content": "What is Cloudflare?"
}
]
}'
```
Feb 03, 2025
1. ### [Block files that are password-protected, compressed, or otherwise unscannable.](https://developers.cloudflare.com/changelog/2025-02-13-improvements-unscannable-files/)
[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Gateway HTTP policies can now block files that are password-protected, compressed, or otherwise unscannable.
These unscannable files are now matched with the [Download and Upload File Types traffic selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#download-and-upload-file-types) for HTTP policies:
* Password-protected Microsoft Office document
* Password-protected PDF
* Password-protected ZIP archive
* Unscannable ZIP archive
To get started inspecting and modifying behavior based on these and other rules, refer to [HTTP filtering](https://developers.cloudflare.com/cloudflare-one/traffic-policies/initial-setup/http/).
Feb 03, 2025
1. ### [Terraform v5 Provider is now generally available](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/)
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Cloudflare's v5 Terraform Provider is now generally available. With this release, Terraform resources are now automatically generated based on OpenAPI Schemas. This change brings alignment across our SDKs, API documentation, and now Terraform Provider. The new provider boosts coverage by increasing support for API properties to 100%, adding 25% more resources, and more than 200 additional data sources. Going forward, this will also reduce the barriers to bringing more resources into Terraform across the broader Cloudflare API. This is a small, but important step to making more of our platform manageable through GitOps, making it easier for you to manage Cloudflare just like you do your other infrastructure.
The Cloudflare Terraform Provider v5 is a ground-up rewrite of the provider and introduces breaking changes for some resource types. Please refer to the [upgrade guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade) for best practices, or the [blog post on automatically generating Cloudflare's Terraform Provider](https://blog.cloudflare.com/automatically-generating-cloudflares-terraform-provider/) for more information about the approach.
For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
Jan 31, 2025
1. ### [Workers for Platforms now supports Static Assets](https://developers.cloudflare.com/changelog/2025-01-31-workers-platforms-static-assets/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
Workers for Platforms customers can now attach static assets (HTML, CSS, JavaScript, images) directly to User Workers, removing the need to host separate infrastructure to serve the assets.
This allows your platform to serve entire front-end applications from Cloudflare's global edge, utilizing caching for fast load times, while supporting dynamic logic within the same Worker. Cloudflare automatically scales its infrastructure to handle high traffic volumes, enabling you to focus on building features without managing servers.
#### What you can build
**Static Sites:** Host and serve HTML, CSS, JavaScript, and media files directly from Cloudflare's network, ensuring fast loading times worldwide. This is ideal for blogs, landing pages, and documentation sites because static assets can be efficiently cached and delivered closer to the user, reducing latency and enhancing the overall user experience.
**Full-Stack Applications:** Combine asset hosting with Cloudflare Workers to power dynamic, interactive applications. If you're an e-commerce platform, you can serve your customers' product pages and run inventory checks from within the same Worker.
* JavaScript
```js
export default {
async fetch(request, env) {
const url = new URL(request.url);
// Check real-time inventory
if (url.pathname === "/api/inventory/check") {
const product = url.searchParams.get("product");
const inventory = await env.INVENTORY_KV.get(product);
return new Response(inventory);
}
// Serve static assets (HTML, CSS, images)
return env.ASSETS.fetch(request);
},
};
```
* TypeScript
```ts
export default {
async fetch(request, env) {
const url = new URL(request.url);
// Check real-time inventory
if (url.pathname === '/api/inventory/check') {
const product = url.searchParams.get('product');
const inventory = await env.INVENTORY_KV.get(product);
return new Response(inventory);
}
// Serve static assets (HTML, CSS, images)
return env.ASSETS.fetch(request);
}
};
```
**Get Started:** Upload static assets using the Workers for Platforms API or Wrangler. For more information, visit our [Workers for Platforms documentation.](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/static-assets/)
Jan 30, 2025
1. ### [Increased Browser Rendering limits!](https://developers.cloudflare.com/changelog/2025-01-30-browser-rendering-more-instances/)
[Workers ](https://developers.cloudflare.com/workers/)[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/) now supports 10 concurrent browser instances per account *and* 10 new instances per minute, up from the previous limits of 2.
This allows you to launch more browser tasks from [Cloudflare Workers](https://developers.cloudflare.com/workers).
To manage concurrent browser sessions, you can use [Queues](https://developers.cloudflare.com/queues/) or [Workflows](https://developers.cloudflare.com/workflows/):
* JavaScript
```js
export default {
async queue(batch, env) {
for (const message of batch.messages) {
const browser = await puppeteer.launch(env.BROWSER);
const page = await browser.newPage();
try {
await page.goto(message.url, {
waitUntil: message.waitUntil,
});
// Process page...
} finally {
await browser.close();
}
}
},
};
```
* TypeScript
```ts
interface QueueMessage {
url: string;
waitUntil: number;
}
export interface Env {
BROWSER_QUEUE: Queue;
BROWSER: Fetcher;
}
export default {
async queue(batch: MessageBatch, env: Env): Promise {
for (const message of batch.messages) {
const browser = await puppeteer.launch(env.BROWSER);
const page = await browser.newPage();
try {
await page.goto(message.url, {
waitUntil: message.waitUntil
});
// Process page...
} finally {
await browser.close();
}
}
}
};
```
Jan 28, 2025
1. ### [Workers KV namespace limits increased to 1000](https://developers.cloudflare.com/changelog/2025-01-27-kv-increased-namespaces-limits/)
[KV](https://developers.cloudflare.com/kv/)
You can now have up to 1000 Workers KV namespaces per account.
Workers KV namespace limits were increased from 200 to 1000 for all accounts. Higher limits for Workers KV namespaces enable better organization of key-value data, such as by category, tenant, or environment.
Consult the [Workers KV limits documentation](https://developers.cloudflare.com/kv/platform/limits/) for the rest of the limits. This increased limit is available for both the Free and Paid [Workers plans](https://developers.cloudflare.com/workers/platform/pricing/).
Jan 15, 2025
1. ### [Increased Workflows limits and improved instance queueing.](https://developers.cloudflare.com/changelog/2025-01-15-workflows-more-steps/)
[Workflows](https://developers.cloudflare.com/workflows/)
[Workflows](https://developers.cloudflare.com/workflows/) (beta) now allows you to define up to 1024 [steps](https://developers.cloudflare.com/workflows/build/workers-api/#workflowstep). `sleep` steps do not count against this limit.
We've also added:
* `instanceId` as property to the [`WorkflowEvent`](https://developers.cloudflare.com/workflows/build/workers-api/#workflowevent) type, allowing you to retrieve the current instance ID from within a running Workflow instance
* Improved queueing logic for Workflow instances beyond the current maximum concurrent instances, reducing the cases where instances are stuck in the queued state.
* Support for [`pause` and `resume`](https://developers.cloudflare.com/workflows/build/workers-api/#pause) for Workflow instances in a queued state.
We're continuing to work on increases to the number of concurrent Workflow instances, steps, and support for a new `waitForEvent` API over the coming weeks.
Jan 07, 2025
1. ### [40-60% Faster D1 Worker API Requests](https://developers.cloudflare.com/changelog/2025-01-07-d1-faster-query/)
[D1](https://developers.cloudflare.com/d1/)
Users making [D1](https://developers.cloudflare.com/d1/) requests via the [Workers API](https://developers.cloudflare.com/d1/worker-api/) can see up to a 60% end-to-end latency improvement due to the removal of redundant network round trips needed for each request to a D1 database.
*p50, p90, and p95 request latency aggregated across entire D1 service. These latencies are a reference point and should not be viewed as your exact workload improvement.*
This performance improvement benefits all D1 Worker API traffic, especially cross-region requests where network latency is an outsized latency factor. For example, a user in Europe talking to a database in North America. D1 [location hints](https://developers.cloudflare.com/d1/configuration/data-location/#provide-a-location-hint) can be used to influence the geographic location of a database.
For more details on how D1 removed redundant round trips, see the D1 specific release note [entry](https://developers.cloudflare.com/d1/platform/release-notes/#2025-01-07).
Dec 19, 2024
1. ### [Troubleshoot tunnels with diagnostic logs](https://developers.cloudflare.com/changelog/2024-12-19-diagnostic-logs/)
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
The latest `cloudflared` build [2024.12.2](https://github.com/cloudflare/cloudflared/releases/tag/2024.12.2) introduces the ability to collect all the diagnostic logs needed to troubleshoot a `cloudflared` instance.
A diagnostic report collects data from a single instance of `cloudflared` running on the local machine and outputs it to a `cloudflared-diag` file.
The `cloudflared-diag-YYYY-MM-DDThh-mm-ss.zip` archive contains the files listed below. The data in a file either applies to the `cloudflared` instance being diagnosed (`diagnosee`) or the instance that triggered the diagnosis (`diagnoser`). For example, if your tunnel is running in a Docker container, the diagnosee is the Docker instance and the diagnoser is the host instance.
| File name | Description | Instance |
| - | - | - |
| `cli-configuration.json` | [Tunnel run parameters](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/configure-tunnels/cloudflared-parameters/run-parameters/) used when starting the tunnel | diagnosee |
| `cloudflared_logs.txt` | [Tunnel log file](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/logs/)[1](#user-content-fn-1) | diagnosee |
| `configuration.json` | Tunnel configuration parameters | diagnosee |
| `goroutine.pprof` | goroutine profile made available by `pprof` | diagnosee |
| `heap.pprof` | heap profile made available by `pprof` | diagnosee |
| `metrics.txt` | Snapshot of [Tunnel metrics](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/metrics/#available-metrics) at the time of diagnosis | diagnosee |
| `network.txt` | JSON traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
| `raw-network.txt` | Raw traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
| `systeminformation.json` | Operating system information and resource usage | diagnosee |
| `task-result.json` | Result of each diagnostic task | diagnoser |
| `tunnelstate.json` | Tunnel connections at the time of diagnosis | diagnosee |
## Footnotes
1. If the log file is blank, you may need to [set `--loglevel` to `debug`](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/logs/#view-logs-on-the-server) when you start the tunnel. The `--loglevel` parameter is only required if you ran the tunnel from the CLI using a `cloudflared tunnel run` command. It is not necessary if the tunnel runs as a Linux/macOS service or runs in Docker/Kubernetes. [↩](#user-content-fnref-1)
For more information, refer to [Diagnostic logs](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/troubleshoot-tunnels/diag-logs/).
Dec 17, 2024
1. ### [Establish BGP peering over Direct CNI circuits](https://developers.cloudflare.com/changelog/2024-12-17-bgp-support-cni/)
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Network Interconnect](https://developers.cloudflare.com/network-interconnect/)
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
Refer to [Magic WAN BGP peering](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes) or [Magic Transit BGP peering](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes) to learn more about this feature and how to set it up.
Dec 05, 2024
1. ### [Generate customized terraform files for building cloud network on-ramps](https://developers.cloudflare.com/changelog/2024-12-05-cloud-onramp-terraform/)
[Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/)
You can now generate customized terraform files for building cloud network on-ramps to [Magic WAN](https://developers.cloudflare.com/magic-wan/).
[Magic Cloud](https://developers.cloudflare.com/magic-cloud-networking/) can scan and discover existing network resources and generate the required terraform files to automate cloud resource deployment using their existing infrastructure-as-code workflows for cloud automation.
You might want to do this to:
* Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
* Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
For more details, refer to [Set up with Terraform](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#set-up-with-terraform).
Nov 22, 2024
1. ### [Find security misconfigurations in your AWS cloud environment](https://developers.cloudflare.com/changelog/2024-11-22-cloud-data-extraction-aws/)
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
You can now use CASB to find security misconfigurations in your AWS cloud environment using [Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/).
You can also [connect your AWS compute account](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/aws-s3/#compute-account) to extract and scan your S3 buckets for sensitive data while avoiding egress fees. CASB will scan any objects that exist in the bucket at the time of configuration.
To connect a compute account to your AWS integration:
1. In [Cloudflare One](https://one.dash.cloudflare.com), go to **Cloud & SaaS findings** > **Integrations**.
2. Find and select your AWS integration.
3. Select **Open connection instructions**.
4. Follow the instructions provided to connect a new compute account.
5. Select **Refresh**.
Nov 21, 2024
1. ### [Improved non-English keyboard support](https://developers.cloudflare.com/changelog/2024-11-21-non-english-keyboard/)
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
You can now type in languages that use diacritics (like á or ç) and character-based scripts (such as Chinese, Japanese, and Korean) directly within the remote browser. The isolated browser now properly recognizes non-English keyboard input, eliminating the need to copy and paste content from a local browser or device.
Oct 24, 2024
1. ### [Workflows is now in open beta](https://developers.cloudflare.com/changelog/2024-10-24-workflows-beta/)
[Workers ](https://developers.cloudflare.com/workers/)[Workflows](https://developers.cloudflare.com/workflows/)
Workflows is now in open beta, and available to any developer a free or paid Workers plan.
Workflows allow you to build multi-step applications that can automatically retry, persist state and run for minutes, hours, days, or weeks. Workflows introduces a programming model that makes it easier to build reliable, long-running tasks, observe as they progress, and programmatically trigger instances based on events across your services.
#### Get started
You can get started with Workflows by [following our get started guide](https://developers.cloudflare.com/workflows/get-started/guide/) and/or using `npm create cloudflare` to pull down the starter project:
```sh
npm create cloudflare@latest workflows-starter -- --template "cloudflare/workflows-starter"
```
You can open the `src/index.ts` file, extend it, and use `wrangler deploy` to deploy your first Workflow. From there, you can:
* Learn the [Workflows API](https://developers.cloudflare.com/workflows/build/workers-api/)
* [Trigger Workflows](https://developers.cloudflare.com/workflows/build/trigger-workflows/) via your Workers apps.
* Understand the [Rules of Workflows](https://developers.cloudflare.com/workflows/build/rules-of-workflows/) and how to adopt best practices
Oct 02, 2024
1. ### [Search for custom rules using rule name and/or ID](https://developers.cloudflare.com/changelog/2024-10-02-custom-rule-search/)
[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
The Magic Firewall dashboard now allows you to search custom rules using the rule name and/or ID.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Analytics & Logs** > **Network Analytics**.
3. Select **Magic Firewall**.
4. Add a filter for **Rule ID**.
Additionally, the rule ID URL link has been added to Network Analytics.
Sep 24, 2024
1. ### [Try out Magic Network Monitoring](https://developers.cloudflare.com/changelog/2024-09-24-magic-network-monitoring/)
[Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/)
The free version of Magic Network Monitoring (MNM) is now available to everyone with a Cloudflare account by default.
1. Log in to your [Cloudflare dashboard](https://dash.cloudflare.com), and select your account.
2. Go to **Analytics & Logs** > **Magic Monitoring**.
For more details, refer to the [Get started guide](https://developers.cloudflare.com/magic-network-monitoring/get-started/).
Jun 17, 2024
1. ### [Exchange user risk scores with Okta](https://developers.cloudflare.com/changelog/2024-06-17-okta-risk-exchange/)
[Risk Score](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)
Beyond the controls in [Zero Trust](https://developers.cloudflare.com/cloudflare-one/), you can now [exchange user risk scores](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/risk-score/#send-risk-score-to-okta) with Okta to inform SSO-level policies.
First, configure Cloudflare One to send user risk scores to Okta.
1. Set up the [Okta SSO integration](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/okta/).
2. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Integrations** > **Identity providers**.
3. In **Your identity providers**, locate your Okta integration and select **Edit**.
4. Turn on **Send risk score to Okta**.
5. Select **Save**.
6. Upon saving, Cloudflare One will display the well-known URL for your organization. Copy the value.
Next, configure Okta to receive your risk scores.
1. On your Okta admin dashboard, go to **Security** > **Device Integrations**.
2. Go to **Receive shared signals**, then select **Create stream**.
3. Name your integration. In **Set up integration with**, choose *Well-known URL*.
4. In **Well-known URL**, enter the well-known URL value provided by Cloudflare One.
5. Select **Create**.
Jun 16, 2024
1. ### [Explore product updates for Cloudflare One](https://developers.cloudflare.com/changelog/2024-06-16-cloudflare-one/)
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Browser Isolation ](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)[CASB ](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)[Cloudflare Tunnel ](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)[Digital Experience Monitoring ](https://developers.cloudflare.com/cloudflare-one/insights/dex/)[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[Email security ](https://developers.cloudflare.com/cloudflare-one/email-security/)[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Magic Cloud Networking ](https://developers.cloudflare.com/magic-cloud-networking/)[Magic Firewall ](https://developers.cloudflare.com/magic-firewall/)[Magic Network Monitoring ](https://developers.cloudflare.com/magic-network-monitoring/)[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Network Interconnect ](https://developers.cloudflare.com/network-interconnect/)[Risk Score ](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
Welcome to your new home for product updates on [Cloudflare One](https://developers.cloudflare.com/cloudflare-one/).
Our [new changelog](https://developers.cloudflare.com/changelog/) lets you read about changes in much more depth, offering in-depth examples, images, code samples, and even gifs.
If you are looking for older product updates, refer to the following locations.
Older product updates
* [Access](https://developers.cloudflare.com/cloudflare-one/changelog/access/)
* [Browser Isolation](https://developers.cloudflare.com/cloudflare-one/changelog/browser-isolation/)
* [CASB](https://developers.cloudflare.com/cloudflare-one/changelog/casb/)
* [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/changelog/tunnel/)
* [Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/changelog/dlp/)
* [Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/changelog/dex/)
* [Email security](https://developers.cloudflare.com/cloudflare-one/changelog/email-security/)
* [Gateway](https://developers.cloudflare.com/cloudflare-one/changelog/gateway/)
* [Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/changelog/)
* [Magic Firewall](https://developers.cloudflare.com/magic-firewall/changelog/)
* [Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/changelog/)
* [Magic Transit](https://developers.cloudflare.com/magic-transit/changelog/)
* [Magic WAN](https://developers.cloudflare.com/magic-wan/changelog/)
* [Network Interconnect](https://developers.cloudflare.com/network-interconnect/changelog/)
* [Risk score](https://developers.cloudflare.com/cloudflare-one/changelog/risk-score/)
* [Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/changelog/warp/)
Feb 26, 2024
1. ### [Easily Exclude EU Visitors from RUM](https://developers.cloudflare.com/changelog/2025-02-25-rum-exclude-eu/)
[Cloudflare Web Analytics](https://developers.cloudflare.com/web-analytics/)
You can now easily enable Real User Monitoring (RUM) monitoring for your hostnames, while safely dropping requests from visitors in the European Union to comply with GDPR and CCPA.
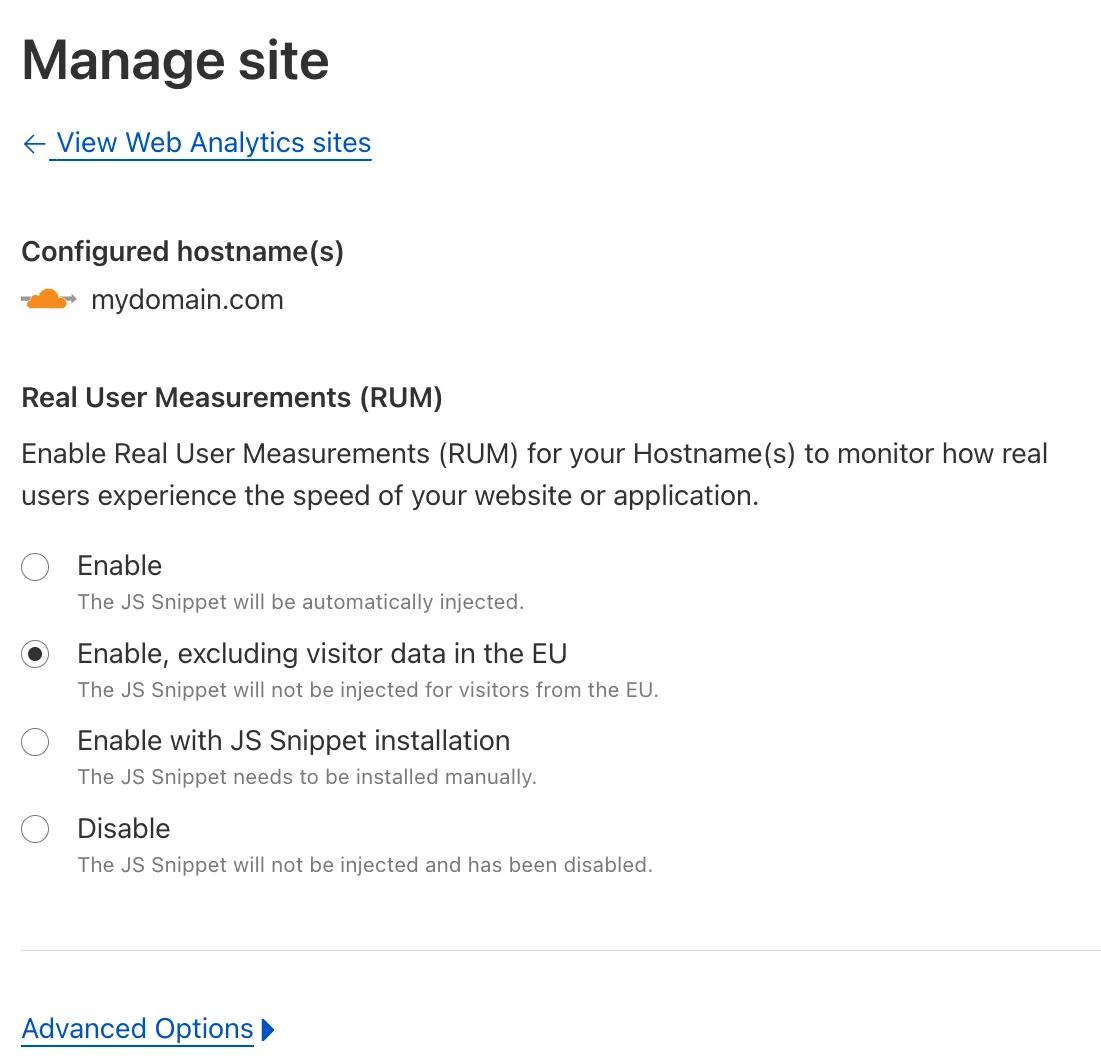
Our Web Analytics product has always been centered on giving you insights into your users' experience that you need to provide the best quality experience, without sacrificing user privacy in the process.
To help with that aim, you can now selectively enable RUM monitoring for your hostname and exclude EU visitor data in a single click. If you opt for this option, we will drop all metrics collected by our EU data centeres automatically.
You can learn more about what metrics are reported by Web Analytics and how it is collected [in the Web Analytics documentation](https://developers.cloudflare.com/web-analytics/data-metrics/). You can enable Web Analytics on any hostname by going to the [Web Analytics](https://dash.cloudflare.com/?to=/:account/web-analytics/sites) section of the dashboard, selecting "Manage Site" for the hostname you want to monitor, and choosing the appropriate enablement option.
[Search for historical entries](https://developers.cloudflare.com/search/?contentType=Changelog+entry)
---
title: Google tag gateway for advertisers · Google tag gateway for advertisers docs
description: Google tag gateway for advertisers allows website owners using
Cloudflare as a CDN to get the most out of ad measurement tools with just a
few clicks. It allows you to deploy Google scripts using your own domain,
enhancing data privacy and improving signal measurement recovery. Unlike
standard setups where tags are requested from a Google domain, Google tag
gateway for advertisers loads the tag from your domain and sends measurement
events to your domain, where they are forwarded to Google.
lastUpdated: 2025-09-05T14:35:13.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/google-tag-gateway/
md: https://developers.cloudflare.com/google-tag-gateway/index.md
---
Google tag gateway for advertisers allows website owners using Cloudflare as a CDN to get the most out of ad measurement tools with just a few clicks. It allows you to deploy Google scripts using your own domain, enhancing data privacy and improving signal measurement recovery. Unlike standard setups where tags are requested from a Google domain, Google tag gateway for advertisers loads the tag from your domain and sends measurement events to your domain, where they are forwarded to Google.
Learn more about why we built it and how it works in our [blog post](https://blog.cloudflare.com/google-tag-gateway-for-advertisers/).
## Get started
Site owners can enable this feature in one of two ways: through the Google tag console, or through the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/tag-management/google-tag-gateway).
### Configure in Google Tag Manager
The fastest way to set up Google tag gateway for advertisers is in Google Tag Manager. [Follow the steps in Google's Help Center](https://support.google.com/analytics/answer/16061641).
### Configure in the Cloudflare dashboard
Note
Your Cloudflare dashboard user must have one of the following [Account Roles](https://developers.cloudflare.com/fundamentals/manage-members/roles/#account-scoped-roles): Super Administrator, Administrator or Zaraz Admin. If you are using Domain Scoped Roles, your [Domain Role](https://developers.cloudflare.com/fundamentals/manage-members/roles/#domain-scoped-roles) must be Domain Administrator.
1. In the Cloudflare dashboard, go to the **Google Tag Gateway** page.
[Go to **Google Tag Gateway**](https://dash.cloudflare.com/?to=/:account/tag-management/google-tag-gateway)
2. Select your domain.
3. Enable the toggle for **Turn on and configure Google tag gateway**.
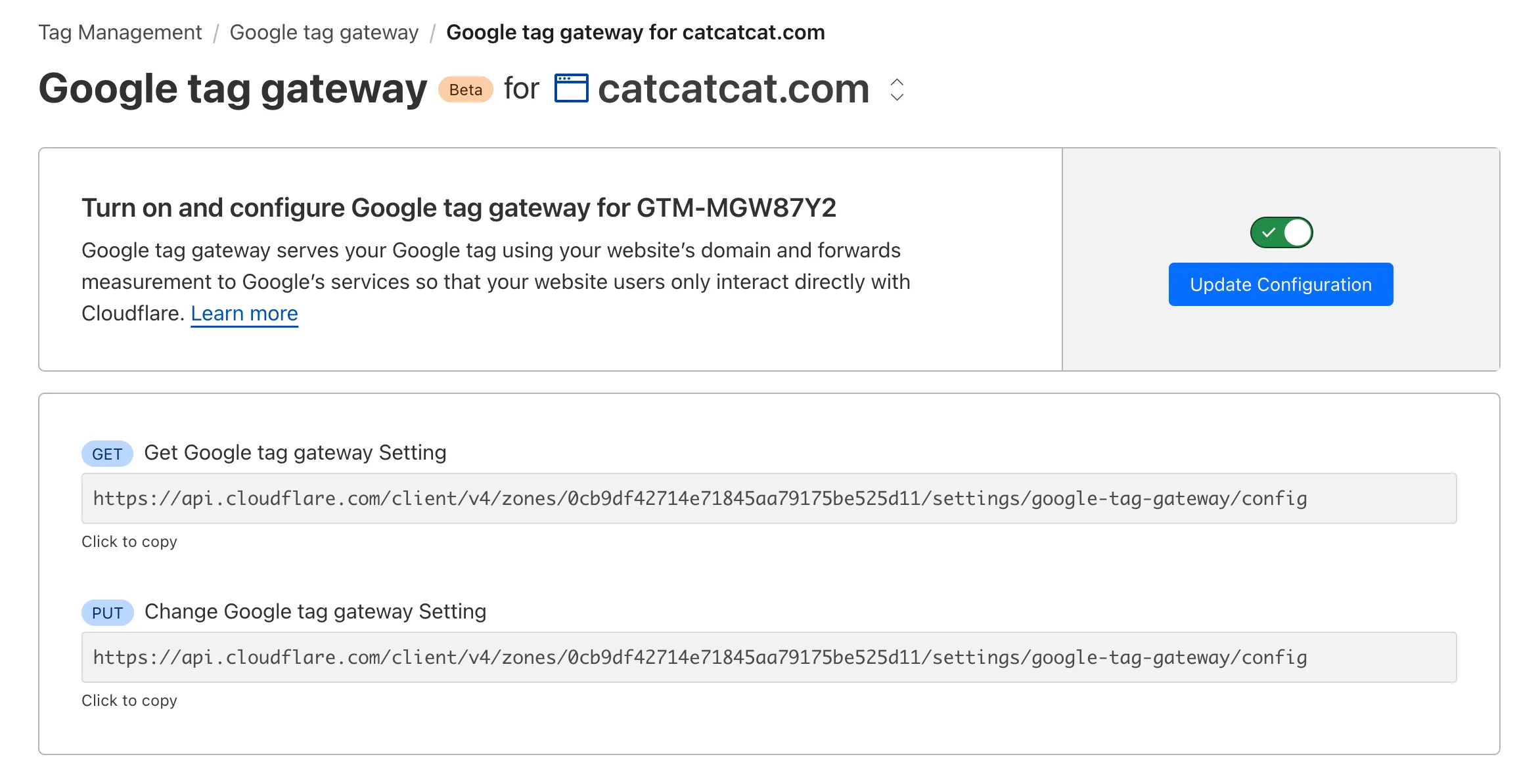
1. Add your Google tag ID and the path on your website reserved for the Google tag. The [Google tag ID](https://support.google.com/analytics/answer/9539598?hl=en) can be found in the Google Tag Experience dashboard. The measurement path is an unused path on your site that will load Google Tag Manager and all subsequent measurement requests.
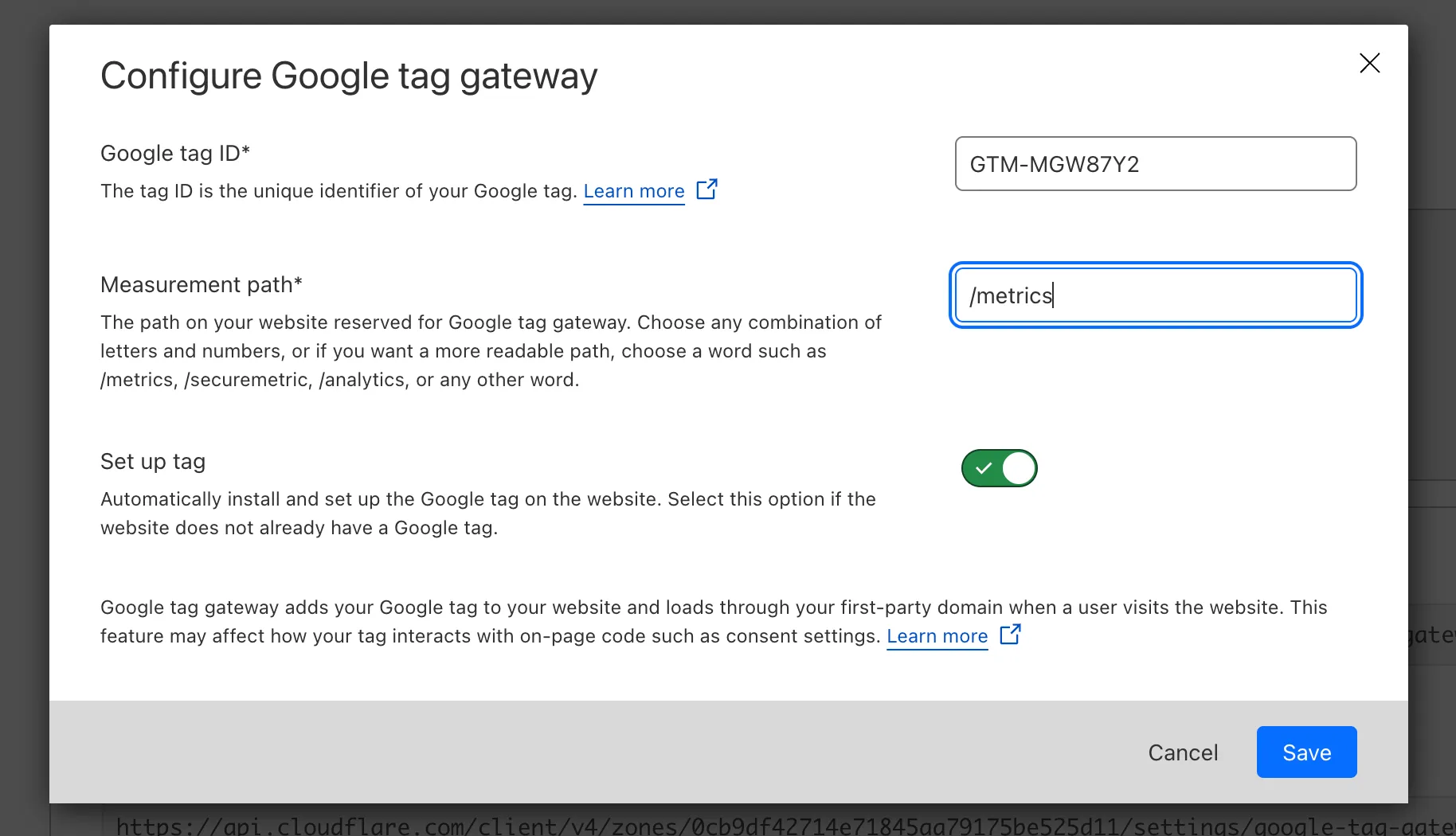
1. Once you click **Save**, Google tag gateway for advertisers will be enabled on your zone. If you already have a GTM script on your website, this First Party Tag will override the existing script.
Now that you have authenticated into your Cloudflare account and configured GTM in first-party mode, your Google Tags will be loaded using `https://your-domain/measurement-path/...`and subsequent measurement requests will be served by Cloudflare.
## Related resources
* [Google Developer Docs: Set up Google tag gateway for advertisers](https://developers.google.com/tag-platform/tag-manager/gateway/setup-guide?setup=auto)
* [Google Help Center: Set up Google tag gateway for advertisers in the Google tag with Cloudflare](https://support.google.com/tagmanager/answer/16061406)
* [Google Help Center: Set up Google tag gateway for advertisers in Google Tag Manager with Cloudflare](https://support.google.com/analytics/answer/16061641)
---
title: Health Checks · Cloudflare Health Checks docs
description: Standalone Health Checks monitors an IP address or hostname for
origin servers or applications and notifies you in near real-time if there
happens to be a problem.
lastUpdated: 2025-10-02T15:01:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/health-checks/
md: https://developers.cloudflare.com/health-checks/index.md
---
Smart Shield
This functionality is now offered as part of Cloudflare's origin server safeguard, Smart Shield. [Learn more](https://developers.cloudflare.com/smart-shield/).
Standalone Health Checks monitors an IP address or hostname for origin servers or applications and notifies you in near real-time if there happens to be a problem.
A health check is a service that runs on Cloudflare's edge network to monitor whether an origin server is online. This allows you to view the health of your origin servers even if there is only one origin or you do not yet need to balance traffic across your infrastructure.
Health Checks support various configurations to hone in on what you can check, including response codes, protocol types, and intervals. You can specify a particular path if an origin server serves multiple applications or check a larger subset of response codes for your staging environment. All of these options allow you to properly target your Health Check, providing a precise picture of what is wrong with an origin server.
Note
Standalone Health Checks are different from health monitors associated with load balancers. For more details about health monitors, refer to the [Load Balancing documentation](https://developers.cloudflare.com/load-balancing/monitors/).
***
## Features
### Health Checks Analytics
You can use Health Checks Analytics to evaluate origin uptime, latency, failure reason, and specific event logs to debug possible origin issues.
[Use Health Checks Analytics](https://developers.cloudflare.com/health-checks/health-checks-analytics/)
***
## Related products
**[Load Balancing](https://developers.cloudflare.com/load-balancing/)**
Cloudflare Load Balancing distributes traffic across your [endpoints](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/), which reduces endpoint strain and latency and improves the experience for end users.
***
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | Yes | Yes | Yes |
| Number of checks | 0 | 10 | 50 | 1,000 |
| Analytics | No | Yes | Yes | Yes |
---
title: Overview · Cloudflare Hyperdrive docs
description: Hyperdrive is a service that accelerates queries you make to
existing databases, making it faster to access your data from across the globe
from Cloudflare Workers, irrespective of your users' location.
lastUpdated: 2026-02-06T18:26:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/hyperdrive/
md: https://developers.cloudflare.com/hyperdrive/index.md
---
Turn your existing regional database into a globally distributed database.
Available on Free and Paid plans
Hyperdrive is a service that accelerates queries you make to existing databases, making it faster to access your data from across the globe from [Cloudflare Workers](https://developers.cloudflare.com/workers/), irrespective of your users' location.
Hyperdrive supports any Postgres or MySQL database, including those hosted on AWS, Google Cloud, Azure, Neon and PlanetScale. Hyperdrive also supports Postgres-compatible databases like CockroachDB and Timescale. You do not need to write new code or replace your favorite tools: Hyperdrive works with your existing code and tools you use.
Use Hyperdrive's connection string from your Cloudflare Workers application with your existing Postgres drivers and object-relational mapping (ORM) libraries:
* PostgreSQL
* index.ts
```ts
import { Client } from "pg";
export default {
async fetch(request, env, ctx): Promise {
// Create a new client instance for each request. Hyperdrive maintains the
// underlying database connection pool, so creating a new client is fast.
const client = new Client({
connectionString: env.HYPERDRIVE.connectionString,
});
try {
// Connect to the database
await client.connect();
// Sample SQL query
const result = await client.query("SELECT * FROM pg_tables");
return Response.json(result.rows);
} catch (e) {
return Response.json({ error: e instanceof Error ? e.message : e }, { status: 500 });
}
},
} satisfies ExportedHandler<{ HYPERDRIVE: Hyperdrive }>;
```
* wrangler.jsonc
```json
{
"$schema": "node_modules/wrangler/config-schema.json",
"name": "WORKER-NAME",
"main": "src/index.ts",
"compatibility_date": "2025-02-04",
"compatibility_flags": [
"nodejs_compat"
],
"observability": {
"enabled": true
},
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "",
"localConnectionString": ""
}
]
}
```
* MySQL
* index.ts
```ts
import { createConnection } from 'mysql2/promise';
export default {
async fetch(request, env, ctx): Promise {
// Create a new connection on each request. Hyperdrive maintains the
// underlying database connection pool, so creating a new client is fast.
const connection = await createConnection({
host: env.HYPERDRIVE.host,
user: env.HYPERDRIVE.user,
password: env.HYPERDRIVE.password,
database: env.HYPERDRIVE.database,
port: env.HYPERDRIVE.port,
// This is needed to use mysql2 with Workers
// This configures mysql2 to use static parsing instead of eval() parsing (not available on Workers)
disableEval: true
});
const [results, fields] = await connection.query('SHOW tables;');
return new Response(JSON.stringify({ results, fields }), {
headers: {
'Content-Type': 'application/json',
'Access-Control-Allow-Origin': '\*',
},
});
}} satisfies ExportedHandler<{ HYPERDRIVE: Hyperdrive }>;
```
* wrangler.jsonc
```json
{
"$schema": "node_modules/wrangler/config-schema.json",
"name": "WORKER-NAME",
"main": "src/index.ts",
"compatibility_date": "2025-02-04",
"compatibility_flags": [
"nodejs_compat"
],
"observability": {
"enabled": true
},
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "",
"localConnectionString": ""
}
]
}
```
* index.ts
```ts
import { Client } from "pg";
export default {
async fetch(request, env, ctx): Promise {
// Create a new client instance for each request. Hyperdrive maintains the
// underlying database connection pool, so creating a new client is fast.
const client = new Client({
connectionString: env.HYPERDRIVE.connectionString,
});
try {
// Connect to the database
await client.connect();
// Sample SQL query
const result = await client.query("SELECT * FROM pg_tables");
return Response.json(result.rows);
} catch (e) {
return Response.json({ error: e instanceof Error ? e.message : e }, { status: 500 });
}
},
} satisfies ExportedHandler<{ HYPERDRIVE: Hyperdrive }>;
```
* wrangler.jsonc
```json
{
"$schema": "node_modules/wrangler/config-schema.json",
"name": "WORKER-NAME",
"main": "src/index.ts",
"compatibility_date": "2025-02-04",
"compatibility_flags": [
"nodejs_compat"
],
"observability": {
"enabled": true
},
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "",
"localConnectionString": ""
}
]
}
```
* index.ts
```ts
import { createConnection } from 'mysql2/promise';
export default {
async fetch(request, env, ctx): Promise {
// Create a new connection on each request. Hyperdrive maintains the
// underlying database connection pool, so creating a new client is fast.
const connection = await createConnection({
host: env.HYPERDRIVE.host,
user: env.HYPERDRIVE.user,
password: env.HYPERDRIVE.password,
database: env.HYPERDRIVE.database,
port: env.HYPERDRIVE.port,
// This is needed to use mysql2 with Workers
// This configures mysql2 to use static parsing instead of eval() parsing (not available on Workers)
disableEval: true
});
const [results, fields] = await connection.query('SHOW tables;');
return new Response(JSON.stringify({ results, fields }), {
headers: {
'Content-Type': 'application/json',
'Access-Control-Allow-Origin': '\*',
},
});
}} satisfies ExportedHandler<{ HYPERDRIVE: Hyperdrive }>;
```
* wrangler.jsonc
```json
{
"$schema": "node_modules/wrangler/config-schema.json",
"name": "WORKER-NAME",
"main": "src/index.ts",
"compatibility_date": "2025-02-04",
"compatibility_flags": [
"nodejs_compat"
],
"observability": {
"enabled": true
},
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "",
"localConnectionString": ""
}
]
}
```
[Get started](https://developers.cloudflare.com/hyperdrive/get-started/)
***
## Features
### Connect your database
Connect Hyperdrive to your existing database and deploy a [Worker](https://developers.cloudflare.com/workers/) that queries it.
[Connect Hyperdrive to your database](https://developers.cloudflare.com/hyperdrive/get-started/)
### PostgreSQL support
Hyperdrive allows you to connect to any PostgreSQL or PostgreSQL-compatible database.
[Connect Hyperdrive to your PostgreSQL database](https://developers.cloudflare.com/hyperdrive/examples/connect-to-postgres/)
### MySQL support
Hyperdrive allows you to connect to any MySQL database.
[Connect Hyperdrive to your MySQL database](https://developers.cloudflare.com/hyperdrive/examples/connect-to-mysql/)
### Query Caching
Default-on caching for your most popular queries executed against your database.
[Learn about Query Caching](https://developers.cloudflare.com/hyperdrive/concepts/query-caching/)
***
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Pages](https://developers.cloudflare.com/pages/)**
Deploy dynamic front-end applications in record time.
***
## More resources
[Pricing](https://developers.cloudflare.com/hyperdrive/platform/pricing/)
Learn about Hyperdrive's pricing.
[Limits](https://developers.cloudflare.com/hyperdrive/platform/limits/)
Learn about Hyperdrive limits.
[Storage options](https://developers.cloudflare.com/workers/platform/storage-options/)
Learn more about the storage and database options you can build on with Workers.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Developer Platform.
---
title: Overview · Cloudflare Images docs
description: Streamline your image infrastructure with Cloudflare Images. Store,
transform, and deliver images efficiently using Cloudflare's global network.
lastUpdated: 2026-02-05T14:19:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/
md: https://developers.cloudflare.com/images/index.md
---
Store, transform, optimize, and deliver images at scale
Available on all plans
Cloudflare Images provides an end-to-end solution designed to help you streamline your image infrastructure from a single API and runs on [Cloudflare's global network](https://www.cloudflare.com/network/).
There are two different ways to use Images:
* **Efficiently store and deliver images.** You can upload images into Cloudflare Images and dynamically deliver multiple variants of the same original image.
* **Optimize images that are stored outside of Images** You can make transformation requests to optimize any publicly available image on the Internet.
Cloudflare Images is available on both [Free and Paid plans](https://developers.cloudflare.com/images/pricing/). By default, all users have access to the Images Free plan, which includes limited usage of the transformations feature to optimize images in remote sources.
Image Resizing is now available as transformations
All Image Resizing features are available as transformations with Images. Each unique transformation is billed only once per calendar month.
If you are using a legacy plan with Image Resizing, visit the [dashboard](https://dash.cloudflare.com/) to switch to an Images plan.
***
## Features
### Storage
Use Cloudflare’s edge network to store your images.
[Use Storage](https://developers.cloudflare.com/images/upload-images/)
### Direct creator upload
Accept uploads directly and securely from your users by generating a one-time token.
[Use Direct creator upload](https://developers.cloudflare.com/images/upload-images/direct-creator-upload/)
### Variants
Add up to 100 variants to specify how images should be resized for various use cases.
[Create variants by transforming images](https://developers.cloudflare.com/images/transform-images)
### Signed URLs
Control access to your images by using signed URL tokens.
[Serve private images](https://developers.cloudflare.com/images/manage-images/serve-images/serve-private-images)
***
## More resources
[Community Forum](https://community.cloudflare.com/c/developers/images/63)
Engage with other users and the Images team on Cloudflare support forum.
---
title: Overview · Cloudflare Key Transparency Auditor docs
description: Cloudflare's Key Transparency Auditor aims to secure the
distribution of public keys for end-to-end encrypted (E2EE) messaging systems
like WhatsApp. It achieves this by building a verifiable append-only data
structure called a Log, similar to Certificate Transparency.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/key-transparency/
md: https://developers.cloudflare.com/key-transparency/index.md
---
Secure the distribution of public keys in your end-to-end encrypted (E2EE) messaging systems
Cloudflare's Key Transparency Auditor aims to secure the distribution of public keys for end-to-end encrypted (E2EE) messaging systems like [WhatsApp](https://engineering.fb.com/2023/04/13/security/whatsapp-key-transparency/). It achieves this by building a verifiable append-only data structure called a Log, similar to [Certificate Transparency](https://developer.mozilla.org/en-US/docs/Web/Security/Certificate_Transparency).
Cloudflare acts as an auditor of Key Transparency Logs to ensure the transparency of end-to-end encrypted messaging public keys. Cloudflare provides an API for anyone to monitor the verification work we perform, and verify the state of its associated Logs locally.
## Related products
**[Certificate Transparency Monitoring](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/certificate-transparency-monitoring/)**
Certificate Transparency (CT) Monitoring is an opt-in feature in public beta that aims to improve security by allowing you to double-check any SSL/TLS certificates issued for your domain.
**[Privacy Gateway](https://developers.cloudflare.com/privacy-gateway/)**
Privacy Gateway is a managed service deployed on Cloudflare's global network that implements part of the [Oblivious HTTP (OHTTP) IETF](https://www.ietf.org/archive/id/draft-thomson-http-oblivious-01.html) standard. The goal of Privacy Gateway and Oblivious HTTP is to hide the client's IP address when interacting with an application backend.
---
title: Cloudflare Workers KV · Cloudflare Workers KV docs
description: Workers KV is a data storage that allows you to store and retrieve
data globally. With Workers KV, you can build dynamic and performant APIs and
websites that support high read volumes with low latency.
lastUpdated: 2025-07-02T08:12:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/
md: https://developers.cloudflare.com/kv/index.md
---
Create a global, low-latency, key-value data storage.
Available on Free and Paid plans
Workers KV is a data storage that allows you to store and retrieve data globally. With Workers KV, you can build dynamic and performant APIs and websites that support high read volumes with low latency.
For example, you can use Workers KV for:
* Caching API responses.
* Storing user configurations / preferences.
* Storing user authentication details.
Access your Workers KV namespace from Cloudflare Workers using [Workers Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) or from your external application using the REST API:
* Workers Binding API
* index.ts
```ts
export default {
async fetch(request, env, ctx): Promise {
// write a key-value pair
await env.KV.put('KEY', 'VALUE');
// read a key-value pair
const value = await env.KV.get('KEY');
// list all key-value pairs
const allKeys = await env.KV.list();
// delete a key-value pair
await env.KV.delete('KEY');
// return a Workers response
return new Response(
JSON.stringify({
value: value,
allKeys: allKeys,
}),
);
},
} satisfies ExportedHandler<{ KV: KVNamespace }>;
```
* wrangler.jsonc
```json
{
"$schema": "node_modules/wrangler/config-schema.json",
"name": "",
"main": "src/index.ts",
"compatibility_date": "2025-02-04",
"observability": {
"enabled": true
},
"kv_namespaces": [
{
"binding": "KV",
"id": ""
}
]
}
```
See the full [Workers KV binding API reference](https://developers.cloudflare.com/kv/api/read-key-value-pairs/).
* REST API
* cURL
```plaintext
curl https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/storage/kv/namespaces/$NAMESPACE_ID/values/$KEY_NAME \
-X PUT \
-H 'Content-Type: multipart/form-data' \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY" \
-d '{
"value": "Some Value"
}'
curl https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/storage/kv/namespaces/$NAMESPACE_ID/values/$KEY_NAME \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY"
```
* TypeScript
```ts
const client = new Cloudflare({
apiEmail: process.env['CLOUDFLARE_EMAIL'], // This is the default and can be omitted
apiKey: process.env['CLOUDFLARE_API_KEY'], // This is the default and can be omitted
});
const value = await client.kv.namespaces.values.update('', 'KEY', {
account_id: '',
value: 'VALUE',
});
const value = await client.kv.namespaces.values.get('', 'KEY', {
account_id: '',
});
const value = await client.kv.namespaces.values.delete('', 'KEY', {
account_id: '',
});
// Automatically fetches more pages as needed.
for await (const namespace of client.kv.namespaces.list({ account_id: '' })) {
console.log(namespace.id);
}
```
See the full Workers KV [REST API and SDK reference](https://developers.cloudflare.com/api/resources/kv/) for details on using REST API from external applications, with pre-generated SDK's for external TypeScript, Python, or Go applications.
* index.ts
```ts
export default {
async fetch(request, env, ctx): Promise {
// write a key-value pair
await env.KV.put('KEY', 'VALUE');
// read a key-value pair
const value = await env.KV.get('KEY');
// list all key-value pairs
const allKeys = await env.KV.list();
// delete a key-value pair
await env.KV.delete('KEY');
// return a Workers response
return new Response(
JSON.stringify({
value: value,
allKeys: allKeys,
}),
);
},
} satisfies ExportedHandler<{ KV: KVNamespace }>;
```
* wrangler.jsonc
```json
{
"$schema": "node_modules/wrangler/config-schema.json",
"name": "",
"main": "src/index.ts",
"compatibility_date": "2025-02-04",
"observability": {
"enabled": true
},
"kv_namespaces": [
{
"binding": "KV",
"id": ""
}
]
}
```
* cURL
```plaintext
curl https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/storage/kv/namespaces/$NAMESPACE_ID/values/$KEY_NAME \
-X PUT \
-H 'Content-Type: multipart/form-data' \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY" \
-d '{
"value": "Some Value"
}'
curl https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/storage/kv/namespaces/$NAMESPACE_ID/values/$KEY_NAME \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY"
```
* TypeScript
```ts
const client = new Cloudflare({
apiEmail: process.env['CLOUDFLARE_EMAIL'], // This is the default and can be omitted
apiKey: process.env['CLOUDFLARE_API_KEY'], // This is the default and can be omitted
});
const value = await client.kv.namespaces.values.update('', 'KEY', {
account_id: '',
value: 'VALUE',
});
const value = await client.kv.namespaces.values.get('', 'KEY', {
account_id: '',
});
const value = await client.kv.namespaces.values.delete('', 'KEY', {
account_id: '',
});
// Automatically fetches more pages as needed.
for await (const namespace of client.kv.namespaces.list({ account_id: '' })) {
console.log(namespace.id);
}
```
[Get started](https://developers.cloudflare.com/kv/get-started/)
***
## Features
### Key-value storage
Learn how Workers KV stores and retrieves data.
[Use Key-value storage](https://developers.cloudflare.com/kv/get-started/)
### Wrangler
The Workers command-line interface, Wrangler, allows you to [create](https://developers.cloudflare.com/workers/wrangler/commands/#init), [test](https://developers.cloudflare.com/workers/wrangler/commands/#dev), and [deploy](https://developers.cloudflare.com/workers/wrangler/commands/#publish) your Workers projects.
[Use Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/)
### Bindings
Bindings allow your Workers to interact with resources on the Cloudflare developer platform, including [R2](https://developers.cloudflare.com/r2/), [Durable Objects](https://developers.cloudflare.com/durable-objects/), and [D1](https://developers.cloudflare.com/d1/).
[Use Bindings](https://developers.cloudflare.com/kv/concepts/kv-bindings/)
***
## Related products
**[R2](https://developers.cloudflare.com/r2/)**
Cloudflare R2 Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
**[Durable Objects](https://developers.cloudflare.com/durable-objects/)**
Cloudflare Durable Objects allows developers to access scalable compute and permanent, consistent storage.
**[D1](https://developers.cloudflare.com/d1/)**
Built on SQLite, D1 is Cloudflare’s first queryable relational database. Create an entire database by importing data or defining your tables and writing your queries within a Worker or through the API.
***
### More resources
[Limits](https://developers.cloudflare.com/kv/platform/limits/)
Learn about KV limits.
[Pricing](https://developers.cloudflare.com/kv/platform/pricing/)
Learn about KV pricing.
[Discord](https://discord.com/channels/595317990191398933/893253103695065128)
Ask questions, show off what you are building, and discuss the platform with other developers.
[Twitter](https://x.com/cloudflaredev)
Learn about product announcements, new tutorials, and what is new in Cloudflare Developer Platform.
---
title: Cloudflare Load Balancing · Cloudflare Load Balancing docs
description: Cloudflare Load Balancing distributes traffic across your
endpoints, which reduces endpoint strain and latency and improves the
experience for end users.
lastUpdated: 2025-02-10T10:26:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/
md: https://developers.cloudflare.com/load-balancing/index.md
---
Maximize application performance and availability
Paid add-on
Cloudflare Load Balancing distributes traffic across your [endpoints](https://developers.cloudflare.com/glossary/?term=endpoint), which reduces endpoint strain and latency and improves the experience for end users.
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
***
## Features
### Load balancing and failover
Distribute traffic evenly across your healthy endpoints, automatically failing over when an endpoint is unhealthy or unresponsive.
[Use Load balancing and failover](https://developers.cloudflare.com/load-balancing/load-balancers/)
### Active monitoring
Monitor your endpoints at configurable intervals and across multiple data centers to look for specific status codes, response text, and timeouts.
[Use Active monitoring](https://developers.cloudflare.com/load-balancing/monitors/)
### Intelligent routing
Choose whether to distribute requests based on endpoint latency, a visitor's geographic region, or even a visitor's GPS coordinates.
[Use Intelligent routing](https://developers.cloudflare.com/load-balancing/understand-basics/traffic-steering/)
### Custom rules
Customize the behavior of your load balancer based on the characteristics of individual requests.
[Use Custom rules](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-rules/)
### Analytics
Review comprehensive analytics to evaluate traffic flow, assess endpoint health status, and review changes in pools and pool health over time.
[Use Analytics](https://developers.cloudflare.com/load-balancing/reference/load-balancing-analytics/)
***
## Related products
**[Standalone Health Checks](https://developers.cloudflare.com/health-checks/)**
Actively monitor whether your origin server is online by sending specific requests at regular intervals.
**[DNS](https://developers.cloudflare.com/dns/)**
Get enterprise-grade authoritative DNS service with the fastest response time, unparalleled redundancy, and advanced security with built-in DDoS mitigation and DNSSEC.
**[Waiting Room](https://developers.cloudflare.com/waiting-room/)**
Route excess users to a custom-branded waiting room, helping preserve customer experience and protect origin servers from being overwhelmed with requests.
***
## More resources
[Plans](https://www.cloudflare.com/plans/#overview)
Compare available Cloudflare plans.
[Pricing](https://dash.cloudflare.com/?to=/:account/:zone/traffic/load-balancing/)
Explore pricing options for Load Balancing in the dashboard.
[Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/load-balancing/)
Learn more about the structure of Cloudflare Load Balancers and their various configurations.
[Learning Paths](https://developers.cloudflare.com/learning-paths/)
Module-based guidance on Cloudflare product workflows.
---
title: Log Explorer · Cloudflare Log Explorer docs
description: Log Explorer is Cloudflare's native observability and forensics
product that enables security teams and developers to analyze, investigate,
and monitor issues directly from the Cloudflare dashboard, without the expense
and complexity of forwarding logs to third-party tools.
lastUpdated: 2025-10-22T13:43:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/
md: https://developers.cloudflare.com/log-explorer/index.md
---
Store and explore your Cloudflare logs directly within the Cloudflare dashboard or API.
Log Explorer is Cloudflare's native observability and forensics product that enables security teams and developers to analyze, investigate, and monitor issues directly from the Cloudflare dashboard, without the expense and complexity of forwarding logs to third-party tools.
Log Explorer provides access to Cloudflare logs with all the context available within the Cloudflare platform. You can monitor security and performance issues with custom dashboards or investigate and troubleshoot issues with log search. Benefits include:
* **Reduced cost and complexity**: Drastically reduce the expense and operational overhead associated with forwarding, storing, and analyzing terabytes of log data in external tools.
* **Faster detection and triage**: Access Cloudflare-native logs directly, eliminating cumbersome data pipelines and the ingest lags that delay critical security insights.
* **Accelerated investigations with full context**: Investigate incidents with Cloudflare's unparalleled contextual data, accelerating your analysis and understanding of "What exactly happened?" and "How did it happen?"
* **Minimal recovery time**: Seamlessly transition from investigation to action with direct mitigation capabilities via the Cloudflare platform.
Contract customers can choose to store their logs in Log Explorer for up to two years, at an additional cost of $0.10 per GB per month. Customers interested in this feature can contact their account team to have it added to their contract.
## Permissions
Access to Log Explorer features is controlled through specific permissions. Each permission grants users the ability to perform certain actions, such as querying logs, managing datasets, or creating dashboards.
| Feature | Required Permission | Description |
| - | - | - |
| **Manage datasets** | `Logs Edit` | Add, enable, or disable datasets. |
| **Log Search** | `Logs Read` | Query logs in the dashboard or via API. |
| **Log Search (save query)** | `Logs Write` | Save log search queries. |
| **Custom dashboards** | `Analytics Read` | Create and view custom dashboards. |
These permissions apply across both the dashboard and the API, and must be granted at either the account or zone level depending on which datasets you need to access.
Authentication with the API can be done via an API token or API key with an email. Refer to [Create API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) for further instructions.
## Features
### Log Search
Explore your Cloudflare logs directly within the Cloudflare dashboard or [API](https://developers.cloudflare.com/log-explorer/api/).
[Use Log Search](https://developers.cloudflare.com/log-explorer/log-search/)
### Custom dashboards
Design customized views for tracking application security, performance, and usage metrics.
[Use Custom dashboards](https://developers.cloudflare.com/log-explorer/custom-dashboards/)
### Manage datasets
Manage the data you want to store within Log Explorer.
[Use Manage datasets](https://developers.cloudflare.com/log-explorer/manage-datasets/)
### API
Manage configuration and perform queries via the API.
[Use API](https://developers.cloudflare.com/log-explorer/api/)
## Related products
**[Logpush](https://developers.cloudflare.com/logs/)**
Forward Cloudflare logs to third-party tools for debugging, identifying configuration adjustments, and creating analytics dashboards.
**[Analytics](https://developers.cloudflare.com/analytics/)**
Visualize the metadata collected by our products in the Cloudflare dashboard.
---
title: Cloudflare Logs · Cloudflare Logs docs
description: These logs are helpful for debugging, identifying configuration
adjustments, and creating analytics, especially when combined with logs from
other sources, such as your application server. For information about the
types of data Cloudflare collects, refer to Cloudflare's Types of analytics.
lastUpdated: 2025-07-30T11:32:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/
md: https://developers.cloudflare.com/logs/index.md
---
Detailed logs that contain metadata generated by our products.
These logs are helpful for debugging, identifying configuration adjustments, and creating analytics, especially when combined with logs from other sources, such as your application server. For information about the types of data Cloudflare collects, refer to [Cloudflare's Types of analytics](https://developers.cloudflare.com/analytics/types-of-analytics/).
***
## Features
### Logpush
Push your request or event logs to your cloud service provider using Logpush, which can be configured via the Cloudflare dashboard or API.
[Use Logpush](https://developers.cloudflare.com/logs/logpush/)
### Instant Logs
View HTTP request logs instantly in the Cloudflare dashboard or the CLI.
[Use Instant Logs](https://developers.cloudflare.com/logs/instant-logs/)
### Logpull (legacy)
Consume request logs over HTTP using Cloudflare Logpull, a REST API designed for log retrieval.
[Use Logpull (legacy)](https://developers.cloudflare.com/logs/logpull/)
***
## Related products
**[Log Explorer](https://developers.cloudflare.com/log-explorer/)**
Store and explore your Cloudflare logs directly within the Cloudflare dashboard or API.
**[Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/)**
Summarize the history of changes made within your Cloudflare account.
**[Web Analytics](https://developers.cloudflare.com/web-analytics/)**
Provides privacy-first analytics without changing your DNS or using Cloudflare's proxy.
***
## More resources
[Plans](https://www.cloudflare.com/products/cloudflare-logs/)
Compare available Cloudflare plans
[Pricing](https://www.cloudflare.com/plans/#overview)
Explore pricing options for Logs
---
title: Magic Cloud Networking · Cloudflare Magic Cloud Networking docs
description: Magic Cloud Networking (beta) simplifies the process of connecting
to your public cloud infrastructure, like Amazon Web Services, Google Cloud
Platform, or Azure. With Magic Cloud Networking you can automatically discover
your cloud resources through Cloudflare's dashboard, and effortlessly combine
your cloud networks with your office and data center networks.
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/
md: https://developers.cloudflare.com/magic-cloud-networking/index.md
---
Automate resource discovery and simplify connectivity when connecting to your public cloud.
Enterprise-only
Magic Cloud Networking (beta) simplifies the process of connecting to your public cloud infrastructure, like Amazon Web Services, Google Cloud Platform, or Azure. With Magic Cloud Networking you can automatically discover your cloud resources through Cloudflare's dashboard, and effortlessly combine your cloud networks with your office and data center networks.
Magic Cloud Networking allows you to connect, accelerate, and manage your virtual private clouds securely through Cloudflare. Grow your multi-cloud network architecture in a consistent and scalable manner, centered on Cloudflare's connectivity cloud services.
Magic Cloud Networking is currently in closed beta. If you would like to be among the first customers to try it out, [fill out this form](https://www.cloudflare.com/lp/cloud-networking/).
Learn how to [get started](https://developers.cloudflare.com/magic-cloud-networking/get-started/).
***
## Features
### Discover your cloud resources automatically
Discover your cloud resources like virtual private clouds (VPCs), subnets, virtual machines (VMs), route tables, and routes automatically, and easily set up your integrations.
[Use cloud resource discovery](https://developers.cloudflare.com/magic-cloud-networking/get-started/)
### Automatically connect a cloud network
Automatically build VPN tunnels between cloud networks and Magic WAN.
[Create cloud on-ramps](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/)
***
## Related products
**[Cloudflare Magic WAN](https://developers.cloudflare.com/magic-wan/)**
Connect and secure your network infrastructure with Cloudflare's global network.
---
title: Overview · Cloudflare Magic Firewall docs
description: Magic Firewall is a firewall-as-a-service (FWaaS) delivered from
the Cloudflare global network to protect office networks and cloud
infrastructure with advanced, scalable protection. With Magic Firewall, you
can apply filter rules on a variety of criteria, such as protocol and packet
length, to filter unwanted traffic before it reaches your network.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/
md: https://developers.cloudflare.com/magic-firewall/index.md
---
Protect your cloud infrastructure or network offices with advanced, scalable firewall-as-a-service protection.
Enterprise-only
Magic Firewall is a firewall-as-a-service (FWaaS) delivered from the Cloudflare global network to protect office networks and cloud infrastructure with advanced, scalable protection. With Magic Firewall, you can apply filter rules on a variety of criteria, such as protocol and packet length, to filter unwanted traffic before it reaches your network.
Magic Firewall uses Wireshark syntax, a domain-specific language (DSL) common in the networking world and the same syntax used across our other products. With this syntax, you can easily craft powerful rules to precisely allow or deny any traffic in or out of your network.
Magic Firewall is available with the purchase of [Magic Transit](https://developers.cloudflare.com/magic-transit/) or [Magic WAN](https://developers.cloudflare.com/magic-wan/).
***
## Features
### Intrusion Detection System (IDS)
Actively monitor for a wide range of known threat signatures in your traffic.
[Use Intrusion Detection System (IDS)](https://developers.cloudflare.com/magic-firewall/how-to/enable-ids/)
***
## Related products
**[Cloudflare Magic Transit](https://developers.cloudflare.com/magic-transit/)**
Secure your network from incoming Internet traffic, and improve performance at Cloudflare scale.
**[Cloudflare Magic WAN](https://developers.cloudflare.com/magic-wan/)**
Improve security and performance for your entire corporate networking, reducing cost and operation complexity.
---
title: Overview · Cloudflare Magic Network Monitoring docs
description: Magic Network Monitoring provides visibility into your network and
cloud traffic by analyzing network flow data that your routers or cloud
environment send. The service supports NetFlow v5, NetFlow v9, IPFIX, and
sFlow. In cloud environments, it supports AWS VPC flow logs through AWS
Firehose.
lastUpdated: 2026-01-22T18:08:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/
md: https://developers.cloudflare.com/magic-network-monitoring/index.md
---
Improve your network and cloud traffic visibility. Customers with public IPs can also detect DDoS attacks based on their traffic flows.
Available on all plans
Magic Network Monitoring provides visibility into your network and cloud traffic by analyzing network flow data that your routers or cloud environment send. The service supports NetFlow v5, NetFlow v9, IPFIX, and sFlow. In cloud environments, it supports AWS VPC flow logs through AWS Firehose.
Magic Network Monitoring is generally available to all users with a Cloudflare account by default. You can log in to your Cloudflare dashboard, select your account, then go to the [Network flow](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics) page to get started.
All users can use the [free version](https://developers.cloudflare.com/magic-network-monitoring/magic-network-monitoring-free/) in a home network, network lab, or business to get end-to-end visibility across their network traffic. Potential enterprise customers are encouraged to use the free version to run a proof of concept.
Enterprise customers can use Magic Network Monitoring with [Magic Transit on-demand](https://developers.cloudflare.com/magic-transit/on-demand/) to monitor their network, identify volumetric DDoS attacks, and activate Magic Transit on-demand to mitigate those attacks.
Refer to [Get started](https://developers.cloudflare.com/magic-network-monitoring/get-started/).
***
## Features
### Rules
Create rules to set thresholds for network traffic volume and receive alerts when thresholds are exceeded.
[Use Rules](https://developers.cloudflare.com/magic-network-monitoring/rules/)
### Magic Transit integration
Magic Transit On Demand customers can automatically enable DDoS mitigation when the service detects a DDoS attack.
[Use Magic Transit integration](https://developers.cloudflare.com/magic-network-monitoring/magic-transit-integration/)
### Rule notifications
Configure email, webhook, or PagerDuty notifications to receive alerts when rule thresholds are exceeded.
[Use Rule notifications](https://developers.cloudflare.com/magic-network-monitoring/rules/rule-notifications/)
***
## Related products
**[Magic Transit](https://developers.cloudflare.com/magic-transit/)**
Mitigates L7, L4, and L3 DDoS attacks when combined with Magic Network Monitoring and Magic Transit on-demand.
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Provides HTTP DDoS attack protection for zones onboarded to Cloudflare in addition to L3 and L4 DDoS attack protection.
**[Cloudflare Network Interconnect](https://developers.cloudflare.com/network-interconnect/)**
Connects your network infrastructure directly with Cloudflare - rather than using the public Internet - for a more reliable and secure experience.
## More resources
[Discord](https://discord.com/invite/cloudflaredev)
Connect with the Magic Network Monitoring community on Discord to ask questions, and share feedback.
---
title: Overview · Cloudflare Magic Transit docs
description: Magic Transit is a network security and performance solution that
offers Distributed Denial of Service (DDoS) protection, traffic acceleration,
and more for on-premises, cloud-hosted, and hybrid networks.
lastUpdated: 2026-02-02T13:59:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/
md: https://developers.cloudflare.com/magic-transit/index.md
---
Secure your network and improve performance at Cloudflare scale.
Enterprise-only
Magic Transit is a network security and performance solution that offers Distributed Denial of Service (DDoS) protection, traffic acceleration, and more for on-premises, cloud-hosted, and hybrid networks.
* **DDoS mitigation and protection**: Instead of relying on local infrastructure that large DDoS attacks can overwhelm, Magic Transit uses the [global Cloudflare Network](https://www.cloudflare.com/network/) to ingest and mitigate attacks close to their source.
* **Traffic acceleration**: Magic Transit takes advantage of the Cloudflare global network to reduce latency and ensure that requests always have a data center nearby.
Learn more [about how Magic Transit works](https://developers.cloudflare.com/magic-transit/about/) and how to [get started](https://developers.cloudflare.com/magic-transit/get-started/).
***
## Features
### Tunnel health checks
Magic Transit sends health check probes to monitor network status and the health of specific network components.
[Learn about health checks](https://developers.cloudflare.com/magic-transit/reference/tunnel-health-checks/)
### Traffic steering
Magic Transit steers traffic along tunnel routes based on priorities you define during the onboarding process.
[Learn about traffic steering](https://developers.cloudflare.com/magic-transit/reference/traffic-steering/)
### Cloudflare IPs
Use Cloudflare-owned IP addresses if you want to protect a smaller network and do not meet Magic Transit's `/24` prefix length requirements.
[Use Cloudflare IPs](https://developers.cloudflare.com/magic-transit/cloudflare-ips/)
### BGP peering (beta)
Use BGP peering between your networks and Cloudflare to automate adding or removing networks and subnets, and take advantage of failure detection and session recovery features.
[Use BGP peering (beta)](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes)
***
## Related products
**[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)**
Magic Firewall is a firewall-as-a-service (FWaaS) delivered from the Cloudflare global network to protect office networks and cloud infrastructure with advanced, scalable protection.
**[Cloudflare Network Interconnect](https://developers.cloudflare.com/network-interconnect/)**
Cloudflare Network Interconnect (CNI) allows you to connect your network infrastructure directly with Cloudflare instead of using the public Internet for a more reliable and secure experience.
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Cloudflare DDoS protection secures websites, applications, and entire networks without compromising legitimate traffic performance.
**[Bring Your Own IP (BYOIP)](https://developers.cloudflare.com/byoip/)**
Get Cloudflare's security and performance while using your own IPs. With Bring Your Own IP (BYOIP), Cloudflare announces your IPs in all Cloudflare locations.
***
## More resources
[Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/magic-transit/)
Deep dive into the key architecture, functionalities, and network deployment options of Cloudflare Magic Transit.
---
title: Overview · Cloudflare Magic WAN docs
description: Magic WAN provides secure, performant connectivity and routing for
your entire corporate network, reducing cost and operational complexity. Magic
Firewall integrates smoothly with Magic WAN, enabling you to enforce network
firewall policies at Cloudflare's global network, across traffic from any
entity within your network.
lastUpdated: 2025-10-27T11:06:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/
md: https://developers.cloudflare.com/magic-wan/index.md
---
Improve security and performance for your entire corporate network, reducing cost and operational complexity.
Enterprise-only
Magic WAN provides secure, performant connectivity and [routing](https://www.cloudflare.com/learning/network-layer/what-is-routing/) for your entire corporate network, reducing cost and operational complexity. [Magic Firewall](https://developers.cloudflare.com/magic-firewall/) integrates smoothly with Magic WAN, enabling you to enforce network firewall policies at Cloudflare's global network, across traffic from any entity within your network.
With Magic WAN, you can securely connect any traffic source - data centers, offices, devices, cloud resources - to Cloudflare's network and configure routing policies to direct traffic where it needs to go, all within one SaaS solution.
Magic WAN supports a variety of on-ramps including any device that supports anycast GRE or IPsec tunnels. To make it easier to onboard your cloud resources, you can use [Magic Cloud Networking](https://developers.cloudflare.com/magic-wan/configuration/magic-cloud-networking/), which automates creating on-ramps from your cloud networks.
Refer to [On-ramps](https://developers.cloudflare.com/magic-wan/on-ramps/) for a full list of supported on-ramps.
Learn how to [get started](https://developers.cloudflare.com/magic-wan/get-started/).
***
## Features
### Connect your network automatically
Use Magic WAN Connector to automatically connect, steer, and shape any IP traffic.
[Use Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/)
### Connect your network manually
Magic WAN is compatible with a host of third-party devices. If you do not have Magic WAN Connector, start here to learn how to set up Magic WAN manually.
[Use a third-party device](https://developers.cloudflare.com/magic-wan/configuration/manually/third-party/)
### Automatic cloud on-ramps
Automate resource discovery, and reduce management burden when connecting to your public cloud.
[Automate your cloud on-ramps](https://developers.cloudflare.com/magic-wan/configuration/magic-cloud-networking/)
### Zero Trust integration
Learn how you can use Magic WAN with other Cloudflare Zero Trust products.
[Integrate with other Zero Trust products](https://developers.cloudflare.com/magic-wan/zero-trust/)
### BGP peering (beta)
Use BGP (Border Gateway Protocol) peering between your networks and Cloudflare to automate adding or removing networks and subnets, and take advantage of failure detection and session recovery features.
[Use BGP peering (beta)](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes)
***
## Related products
**[Cloudflare Zero Trust](https://developers.cloudflare.com/cloudflare-one/) **Cloudflare Zero Trust replaces legacy security perimeters with our global edge, making the Internet faster and safer for teams around the world.
**[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)**
Magic Firewall is a firewall-as-a-service (FWaaS) delivered from the Cloudflare global network to protect office networks and cloud infrastructure with advanced, and scalable protection.
**[Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/) **Simplify and automate cloud resource discovery, and reduce your management burden when connecting to your public cloud.
**[Cloudflare Network Interconnect](https://developers.cloudflare.com/network-interconnect/)**
Cloudflare Network Interconnect (CNI) allows you to connect your network infrastructure directly with Cloudflare - rather than using the public Internet - for a more reliable and secure experience.
**[Load Balancing](https://developers.cloudflare.com/load-balancing/)**
Cloudflare Load Balancing distributes traffic across your endpoints, which reduces endpoint strain and latency and improves the experience for end users.
***
## More resources
[Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/sase/)
Deep dive into key architecture and functionalities aspects of Cloudflare One, and learn more about Magic WAN and its structure.
---
title: Migration guides · Cloudflare Migration Guides
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/migration-guides/
md: https://developers.cloudflare.com/migration-guides/index.md
---
Content designed to help you migrate from another provider to Cloudflare.
This section is still in work. Expect more guides soon.
***
## More resources
[Reference architectures](https://developers.cloudflare.com/reference-architecture/)
High-level overviews of Cloudflare's network and platform.
[Cloudflare blog](https://blog.cloudflare.com/)
Read articles and announcements about the latest Cloudflare products and features.
[Learning Paths](https://developers.cloudflare.com/learning-paths/)
Module-based guidance on Cloudflare product workflows.
---
title: Overview · Cloudflare MoQ docs
description: MoQ (Media over QUIC) is a protocol for delivering live media
content using QUIC transport. It provides efficient, low-latency media
streaming by leveraging QUIC's multiplexing and connection management
capabilities.
lastUpdated: 2025-09-12T21:55:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/moq/
md: https://developers.cloudflare.com/moq/index.md
---
MoQ (Media over QUIC) is a protocol for delivering live media content using QUIC transport. It provides efficient, low-latency media streaming by leveraging QUIC's multiplexing and connection management capabilities.
MoQ is designed to be an Internet infrastructure level service that provides media delivery to applications, similar to how HTTP provides content delivery and WebRTC provides real-time communication.
Cloudflare's implementation of MoQ currently supports a subset of the [draft-07 MoQ Transport specfication](https://datatracker.ietf.org/doc/html/draft-ietf-moq-transport-07).
For the most up-to-date documentation on the protocol, please visit the IETF working group documentation.
## Frequently Asked Questions
* What about Safari?
Safari does not yet have fully functional WebTransport support. Apple never publicly commits to timelines for new features like this. However, Apple has indicated their [intent to support WebTransport](https://github.com/WebKit/standards-positions/issues/18#issuecomment-1495890122). An Apple employee is even a co-author of the [WebTransport over HTTP/3](https://datatracker.ietf.org/doc/draft-ietf-webtrans-http3/) draft. Since Safari 18.4 (2025-03-31), an early (not yet fully functional) implementation of the WebTransport API has been available for testing behind a developer-mode / advanced settings feature flag (including on iOS).
Until Safari has a fully functional WebTransport implementation, some MoQ use cases may require a fallback to WebRTC, or, in some cases, WebSockets.
## Known Issues
* Extra Subgroup header field
The current implementation includes a `subscribe_id` field in Subgroup Headers which [`draft-ietf-moq-transport-07`](https://datatracker.ietf.org/doc/html/draft-ietf-moq-transport-07) omits.
In section 7.3.1, `draft-ietf-moq-transport-07` [specifies](https://www.ietf.org/archive/id/draft-ietf-moq-transport-07.html#section-7.3.1):
```txt
STREAM_HEADER_SUBGROUP Message {
Track Alias (i),
Group ID (i),
Subgroup ID (i),
Publisher Priority (8),
}
```
Whereas our implementation expects and produces:
```txt
STREAM_HEADER_SUBGROUP Message {
Subscribe ID (i),
Track Alias (i),
Group ID (i),
Subgroup ID (i),
Publisher Priority (8),
}
```
This was erroroneously left over from a previous draft version and will be fixed in a future release. Thank you to [@yuki-uchida](https://github.com/yuki-uchida) for reporting.
---
title: Overview · Cloudflare Network settings docs
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/
md: https://developers.cloudflare.com/network/index.md
---
Manage network settings for your website.
Available on all plans
***
## Features
### IP Geolocation
Include the country code of the visitor location with all requests to your website.
[Use IP Geolocation](https://developers.cloudflare.com/network/ip-geolocation/)
### IPv6 Compatibility
Enable IPv6 support and gateway.
[Use IPv6 Compatibility](https://developers.cloudflare.com/network/ipv6-compatibility/)
### WebSockets
Allow WebSockets connections to your origin server.
[Use WebSockets](https://developers.cloudflare.com/network/websockets/)
***
## Related products
**[China Network](https://developers.cloudflare.com/china-network/)**
The Cloudflare China Network is a package of selected Cloudflare’s performance and security products running on data centers located in mainland China and operated by Cloudflare’s partner JD Cloud.
**[Managed Transforms](https://developers.cloudflare.com/rules/transform/managed-transforms/)**
Managed Transforms allow you to perform common adjustments to HTTP request and response headers with the click of a button.
---
title: Overview · Cloudflare Network Error Logging docs
description: Network Error Logging (NEL) is a browser-based reporting system
that allows users to report their own failures to an external endpoint. You
can use Network Error Logging to gain insight into connectivity issues on the
Internet to learn when and where an incident is happening, who is impacted,
and how they are being impacted.
lastUpdated: 2025-06-17T16:28:37.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-error-logging/
md: https://developers.cloudflare.com/network-error-logging/index.md
---
Network Error Logging (NEL) is a browser-based reporting system that allows users to report their own failures to an external endpoint. You can use Network Error Logging to gain insight into connectivity issues on the Internet to learn when and where an incident is happening, who is impacted, and how they are being impacted.
## The last mile
The last mile is the path from a user to the first point of ingress to the resource, whether that be a network like Cloudflare or directly to the origin server. The last mile is important because it is in the critical path of the request for a resource: if the last mile has issues, users cannot connect to their resources. When Network Error Logging is enabled, you can receive alerts about issues in the last mile — which are typically difficult to detect — to learn what the problem is and how to fix it.
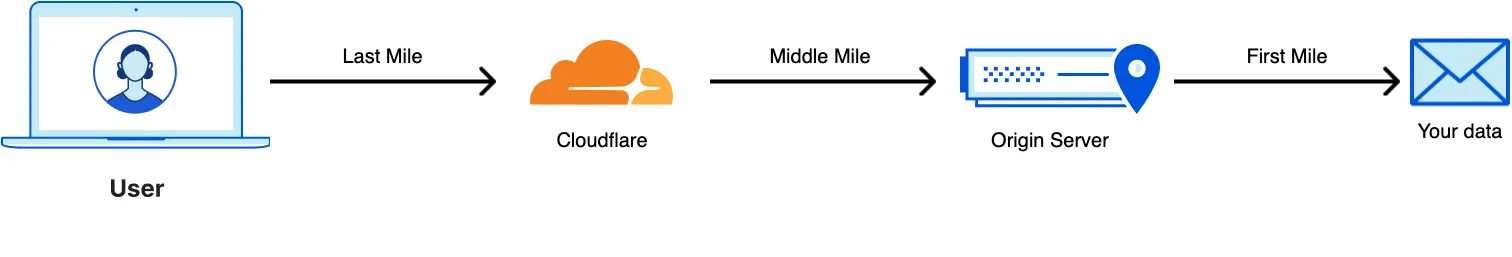
## How NEL affects requests
The Report-To header is present in all requests to Cloudflare zones that have NEL enabled:
```txt
report-to: {"group":"cf-nel","max_age":31536000,"endpoints":[{"url":"`[`https://a.nel.cloudflare.com/report?lkg-colo=lhr&lkg-time=1600338181`](https://gcp.nel.cloudflare.com/report?lkg-colo=lhr&lkg-time=1600338181&lkg-ip=1.1.1.1)`"}]}
```
A sample Network Error Report payload appears as follows:
```json
{
"age": 20,
"type": "network-error",
"url": "https://example.com/previous-page",
"body": {
"elapsed_time": 18,
"method": "POST",
"phase": "dns",
"protocol": "http/1.1",
"referrer": "https://example.com/previous-page",
"sampling_fraction": 1,
"server_ip": "",
"status_code": 0,
"type": "dns.name_not_resolved",
"url": "https://example-host.com/"
}
}
```
## Privacy
Cloudflare uses geolocation lookups to extract the following information from every client IP in a NEL report:
* Client ASN
* Client country
* Client metro area
Cloudflare uses internal lookups to associate the above data with a customer domain and customer account.
Cloudflare does not store any PII or user-specific data, and any IP data is only kept for the duration of the request as it is processed. After the report is processed through the NEL pipeline, all PII data is purged from the system.
The client IP address is only stored in volatile memory for the lifetime of the request to Cloudflare’s NEL endpoint (order of milliseconds) and is dropped immediately after the request completes. Cloudflare does not log the client IP address anywhere in the Network Error Logging pipeline. Customers can opt out of having their end users consume the NEL headers by [contacting Cloudflare support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
---
title: Overview · Cloudflare Network Interconnect docs
description: Cloudflare Network Interconnect (CNI) allows you to connect your
network infrastructure directly to Cloudflare — rather than using the public
Internet — for a more performant and secure experience. With CNI, you can
bring Cloudflare's full suite of network functions to your network edge.
lastUpdated: 2026-02-02T13:59:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-interconnect/
md: https://developers.cloudflare.com/network-interconnect/index.md
---
Connect your network infrastructure directly to Cloudflare
Enterprise-only
Cloudflare Network Interconnect (CNI) allows you to connect your network infrastructure directly to Cloudflare — rather than using the public Internet — for a more performant and secure experience. With CNI, you can bring Cloudflare's full suite of network functions to your network edge.
## Benefits
Enterprises use CNI to achieve:
* **Enhanced Performance**: Gain lower latency and more consistent network throughput.
* **Increased Security**: Reduce your network's attack surface by connecting privately and avoiding the public Internet.
## Connection types
Choose the connection type for your infrastructure and operational needs.
| | Direct Interconnect | Partner Interconnect | Cloud Interconnect |
| - | - | - | - |
| **Port type** | A dedicated physical fiber connection between your network equipment and Cloudflare's hardware in a shared data center. | A virtual connection to Cloudflare established through one of our global connectivity partners. | A private connection between a customer's cloud environments (for example, Amazon Web Services (AWS), Google Cloud) and Cloudflare. |
| **Operations** | You are responsible for procuring and managing the physical cross-connect to Cloudflare's equipment. | Your partner manages the connection logistics, often through a software-defined networking portal. | Cloudflare connects to cloud providers' dedicated services, and customers establish private virtual circuits from their virtual private clouds. |
| **Ideal use case** | For customers collocated with Cloudflare who require maximum control, performance, and reliability. | For customers who are not in the same data center as Cloudflare or prefer a managed connectivity solution. | For customers with workloads in public clouds who need secure, reliable connectivity to Cloudflare services. |
## Dataplane
Cloudflare's data centers may support one or more interconnect dataplanes. The dataplane is the type of equipment that terminates your direct connection:
* **Dataplane v1**: A peering connection to a Cloudflare edge data center that supports Generic Routing Encapsulation (GRE) tunnels for connecting with the Magic Networking overlay, with optional GRE-less delivery for Magic Transit Direct Server Return.
* **Dataplane v2**: Is based on the Customer Connectivity Router (CCR), which is specifically designed for customer connectivity. It provides simplified routing without GRE tunneling and supports a 1,500-byte Maximum Transmission Unit (MTU) bidirectionally.
When you review the [available locations](https://developers.cloudflare.com/network-interconnect/static/cni-locations-21-jan-2026.pdf) (PDF), you can see which dataplane version(s) are available.
## Product use cases
CNI provides a private point-to-point IP connection with Cloudflare. There are two Dataplanes that come with different technical specifications.
| | Dataplane v1 | Dataplane v2 |
| - | - | - |
| **Magic Transit Direct Server Return (DSR)** Distributed Denial of Service (DDoS) protection for all ingress traffic from the Internet to your public network. Send egress traffic via your ISP. | Supported with or without a GRE tunnel established over the interconnect circuit. | Supported. |
| **Magic Transit with Egress** DDoS protection for all ingress traffic from the Internet to your public network. Send egress traffic via Cloudflare. | Supported with or without a GRE tunnel established over the interconnect circuit. | Supported. |
| **Magic WAN and Zero Trust** Build a secure, private network backbone connecting your Zero Trust users and applications with all your sites, data centers, and clouds. | Supported with a GRE tunnel established over the interconnect circuit. | Supported. |
| **Peering** Exchange public routes with a single Cloudflare PoP (Point of Presence). | Supported. All customers connecting with the edge data center will exchange public routes at that PoP with AS13335. Connectivity is established at each individual PoP. Routes for other edge locations in Cloudflare's network may not be available. Routes for customer-advertised prefixes will be available only in the connected PoP. | Not supported. |
| **Application Security and Performance** Improve the performance and security of your web applications | **Supported via peering**: Customers can use Argo Smart Routing to direct origin traffic via the edge peering connection when it is determined to be the lowest latency option. Customers must maintain a direct Internet connection which will always be used for a portion of traffic and during failure scenarios. **Supported Via Magic Transit**: Customers may configure any product with an origin server IP address that is protected by Magic Transit. Magic Transit will direct this traffic via the overlay and customer can control interconnect next-hops using the Magic networking routing table. | When the origin IPs are behind Magic Transit over a CNI v2, all Cloudflare services that work with public origins (like Load Balancer, WAF, Cache) will run over the CNI. |
For more details refer to the [prerequisites section](https://developers.cloudflare.com/network-interconnect/get-started/#prerequisites).
### Designing for high availability
To protect against a single point of failure, it is critical to design your CNI deployment for resilience. For business-critical applications, seek Cloudflare locations that support diversity on the device level. This ensures your connections terminate on physically separate hardware.
Refer to [Service Expectations](https://developers.cloudflare.com/network-interconnect/get-started/#service-expectations) for more information.
***
## Related products
**[Magic Transit](https://developers.cloudflare.com/magic-transit/)**
Magic Transit is a network security and performance solution that offers Distributed Denial of Service (DDoS) protection, traffic acceleration, and more for on-premise, cloud-hosted, and hybrid networks.
**[Magic WAN](https://developers.cloudflare.com/magic-wan/)**
Improve security and performance for your entire corporate network, reducing cost and operation complexity.
---
title: Notifications · Cloudflare Notifications docs
description: Cloudflare Notifications help you stay up to date with your
Cloudflare account. Manage your Notifications to define what you want to be
warned about and how, be it a denial-of-service attack or an issue with your
server.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/notifications/
md: https://developers.cloudflare.com/notifications/index.md
---
Available on all plans
Cloudflare Notifications help you stay up to date with your Cloudflare account. Manage your Notifications to define what you want to be warned about and how, be it a denial-of-service attack or an issue with your server.
The available Notification features vary according to your plan:
* Free plans can set up email-based Notifications.
* Business and higher plans can also [access PagerDuty](https://developers.cloudflare.com/notifications/get-started/configure-pagerduty/).
* Professional and higher plans can also [use webhooks](https://developers.cloudflare.com/notifications/get-started/configure-webhooks/).
The notification service only works on the [proxied](https://developers.cloudflare.com/dns/proxy-status/) domains because Cloudflare needs enough information necessary to decide if we need to trigger a notification or not.
Note
The availability of delivery methods like PagerDuty and webhooks in Free or Professional zones depends on the highest zone plan in your Cloudflare account:
* PagerDuty is available in zones on a Free/Professional plan if your Cloudflare account has at least one zone in a Business plan (or higher).
* Webhooks are available in zones on a Free plan if your Cloudflare account has at least one zone in a Professional plan (or higher).
---
title: Overview · Cloudflare Page Shield docs
description: Page Shield is a comprehensive client-side security and privacy
solution that allows you to ensure the safety of your website visitors'
browsing environment.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/
md: https://developers.cloudflare.com/page-shield/index.md
---
Ensures the safety and privacy of your website visitors' browsing environment.
Available on all plans
Page Shield helps manage resources loaded by your website visitors — including scripts, their connections, and cookies — and triggers alert notifications when resources change or are considered malicious.
Learn how to [get started](https://developers.cloudflare.com/page-shield/get-started/).
***
## Features
### Resource monitoring
Displays information about client-side resources loaded in your domain's pages.
[Monitor client-side resources](https://developers.cloudflare.com/page-shield/detection/monitor-connections-scripts/)
### Page attribution
Find in which page a resource first appeared, and view a list of the latest occurrences of the resource in your pages.
[Find resource occurrences](https://developers.cloudflare.com/page-shield/detection/monitor-connections-scripts/#view-details)
### Malicious script detection
Detects malicious scripts in your pages using threat intelligence and machine learning.
[Review malicious scripts](https://developers.cloudflare.com/page-shield/detection/review-malicious-scripts/)
### Code change detection
Detects any changes in the scripts loaded in your pages.
[Review changed scripts](https://developers.cloudflare.com/page-shield/detection/review-changed-scripts/)
### Alerts
Receive notifications about newly detected scripts, scripts loaded from unknown domains, new scripts considered malicious, or code changes in your existing scripts.
[Use Alerts](https://developers.cloudflare.com/page-shield/alerts/)
### Policies
Policies define allowed resources on your websites. Use policies to enforce an allowlist of resources, effectively blocking resources not included in your policies.
[Use Policies](https://developers.cloudflare.com/page-shield/policies/)
## Availability
| | Free | Pro | Business | Enterprise | Enterprise with add-on |
| - | - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes | Yes |
| Script monitoring | Yes | Yes | Yes | Yes | Yes |
| Connection monitoring | No | No | Yes | Yes | Yes |
| Cookie monitoring | No | No | Yes | Yes | Yes |
| Page attribution | No | No | Yes | Yes | Yes |
| New Resources Alerts and New Domain Alerts | No | No | Yes | Yes | Yes |
| Malicious script detection and alerting | No | No | No | No | Yes |
| Code change detection and alerting | No | No | No | No | Yes |
| Malicious connection detection and alerting | No | No | No | No | Yes |
| Cookie monitoring advanced fields | No | No | No | No | Yes |
| Number of policies (positive blocking) | 0 | 0 | 0 | 0 | 5 |
| Number of Logpush jobs | 0 | 0 | 0 | 0 | 4 |
---
title: Overview · Cloudflare Pages docs
description: Deploy your Pages project by connecting to your Git provider,
uploading prebuilt assets directly to Pages with Direct Upload or using C3
from the command line.
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pages/
md: https://developers.cloudflare.com/pages/index.md
---
Create full-stack applications that are instantly deployed to the Cloudflare global network.
Available on all plans
Deploy your Pages project by connecting to [your Git provider](https://developers.cloudflare.com/pages/get-started/git-integration/), uploading prebuilt assets directly to Pages with [Direct Upload](https://developers.cloudflare.com/pages/get-started/direct-upload/) or using [C3](https://developers.cloudflare.com/pages/get-started/c3/) from the command line.
***
## Features
### Pages Functions
Use Pages Functions to deploy server-side code to enable dynamic functionality without running a dedicated server.
[Use Pages Functions](https://developers.cloudflare.com/pages/functions/)
### Rollbacks
Rollbacks allow you to instantly revert your project to a previous production deployment.
[Use Rollbacks](https://developers.cloudflare.com/pages/configuration/rollbacks/)
### Redirects
Set up redirects for your Cloudflare Pages project.
[Use Redirects](https://developers.cloudflare.com/pages/configuration/redirects/)
***
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Cloudflare Workers provides a serverless execution environment that allows you to create new applications or augment existing ones without configuring or maintaining infrastructure.
**[R2](https://developers.cloudflare.com/r2/)**
Cloudflare R2 Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
**[D1](https://developers.cloudflare.com/d1/)**
D1 is Cloudflare’s native serverless database. Create a database by importing data or defining your tables and writing your queries within a Worker or through the API.
**[Zaraz](https://developers.cloudflare.com/zaraz/)**
Offload third-party tools and services to the cloud and improve the speed and security of your website.
***
## More resources
[Limits](https://developers.cloudflare.com/pages/platform/limits/)
Learn about limits that apply to your Pages project (500 deploys per month on the Free plan).
[Framework guides](https://developers.cloudflare.com/pages/framework-guides/)
Deploy popular frameworks such as React, Hugo, and Next.js on Pages.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
---
title: Pipelines · Cloudflare Pipelines Docs
description: Cloudflare Pipelines ingests events, transforms them with SQL, and
delivers them to R2 as Iceberg tables or as Parquet and JSON files.
lastUpdated: 2026-02-03T18:17:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pipelines/
md: https://developers.cloudflare.com/pipelines/index.md
---
Note
Pipelines is in **open beta**, and any developer with a [Workers Paid plan](https://developers.cloudflare.com/workers/platform/pricing/) can start using it. Currently, outside of standard R2 storage and operations, you will not be billed for your use of Pipelines.
Ingest, transform, and load streaming data into Apache Iceberg or Parquet in R2.
Available on Paid plans
Cloudflare Pipelines ingests events, transforms them with SQL, and delivers them to R2 as [Iceberg tables](https://developers.cloudflare.com/r2/data-catalog/) or as Parquet and JSON files.
Whether you're processing server logs, mobile application events, IoT telemetry, or clickstream data, Pipelines provides durable ingestion via HTTP endpoints or Worker bindings, SQL-based transformations, and exactly-once delivery to R2. This makes it easy to build analytics-ready data warehouses and lakehouses without managing streaming infrastructure.
Create your first pipeline by following the [getting started guide](https://developers.cloudflare.com/pipelines/getting-started) or running this [Wrangler](https://developers.cloudflare.com/workers/wrangler/) command:
```sh
npx wrangler pipelines setup
```
***
## Features
### Create your first pipeline
Build your first pipeline to ingest data via HTTP or Workers, apply SQL transformations, and deliver to R2 as Iceberg tables or Parquet files.
[Get started](https://developers.cloudflare.com/pipelines/getting-started/)
### Streams
Durable, buffered queues that receive events via HTTP endpoints or Worker bindings.
[Learn about Streams](https://developers.cloudflare.com/pipelines/streams/)
### Pipelines
Connect streams to sinks with SQL transformations that validate, filter, transform, and enrich your data at ingestion time.
[Learn about Pipelines](https://developers.cloudflare.com/pipelines/pipelines/)
### Sinks
Configure destinations for your data. Write Apache Iceberg tables to R2 Data Catalog or export as Parquet and JSON files.
[Learn about Sinks](https://developers.cloudflare.com/pipelines/sinks/)
***
## Related products
**[R2](https://developers.cloudflare.com/r2/)**
Cloudflare R2 Object Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
**[Workers](https://developers.cloudflare.com/workers/)**
Cloudflare Workers allows developers to build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
***
## More resources
[Limits](https://developers.cloudflare.com/pipelines/platform/limits/)
Learn about pipelines limits.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
---
title: Plans | Cloudflare Docs
description: View the products and features available to you based on your Cloudflare plan.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/plans/
md: https://developers.cloudflare.com/plans/index.md
---
A feature-level companion to our [Plans and Pricing page](https://www.cloudflare.com/plans/)
(may not include [all features](#missing-features))
## Account
### Cloudflare dashboard single sign-on
**Link:** [Cloudflare dashboard single sign-on](https://developers.cloudflare.com/fundamentals/manage-members/dashboard-sso/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Version Management
**Link:** [Version Management](https://developers.cloudflare.com/version-management/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Zone holds
**Link:** [Zone holds](https://developers.cloudflare.com/fundamentals/account/account-security/zone-holds/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
## Analytics
### GraphQL Analytics API
**Link:** [GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Instant Logs
**Link:** [Instant Logs](https://developers.cloudflare.com/logs/instant-logs/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
### Logpull
**Link:** [Logpull](https://developers.cloudflare.com/logs/instant-logs/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Logpush
**Link:** [Logpush](https://developers.cloudflare.com/logs/logpush/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Traffic analytics
**Link:** [Traffic analytics](https://developers.cloudflare.com/analytics/account-and-zone-analytics/zone-analytics/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Level of detail**
* **Free:** Requests, bandwidth, unique visitors
* **Lite:** Requests, bandwidth, unique visitors
* **Pro:** Same as Free, but able to see historical trends and filter by characteristics
* **Pro Plus:** Same as Free, but able to see historical trends and filter by characteristics
* **Business:** Same as Pro
* **Enterprise:** Same as Pro
**Historical time**
* **Free:** 30 days
* **Lite:** 30 days
* **Pro:** 7 days
* **Pro Plus:** 7 days
* **Business:** 30 days
* **Enterprise:** 30 days
## Cache
### Always Online
**Link:** [Always Online](https://developers.cloudflare.com/cache/how-to/always-online/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Crawl interval**
Available on all plans
* **Free:** Every 30 days
* **Lite:** Every 30 days
* **Pro:** Every 15 days
* **Pro Plus:** Every 15 days
* **Business:** Every 5 days
* **Enterprise:** Every 5 days
### Browser Cache TTL
**Link:** [Browser Cache TTL](https://developers.cloudflare.com/cache/how-to/edge-browser-cache-ttl/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Minimum Browser Cache TTL (Page Rules)**
* **Free:** 2 minutes
* **Lite:** 2 minutes
* **Pro:** 2 minutes
* **Pro Plus:** 2 minutes
* **Business:** 2 minutes
* **Enterprise:** 30 seconds
**Minimum Browser Cache TTL**
* **Free:** 1 second
* **Lite:** 1 second
* **Pro:** 1 second
* **Pro Plus:** 1 second
* **Business:** 1 second
* **Enterprise:** 1 second
**Default Browser Cache TTL**
* **Free:** 4 hours
* **Lite:** 4 hours
* **Pro:** 4 hours
* **Pro Plus:** 4 hours
* **Business:** 4 hours
* **Enterprise:** 4 hours
### Cache analytics
**Link:** [Cache analytics](https://developers.cloudflare.com/cache/performance-review/cache-analytics/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Retention period**
* **Free:** N/A
* **Lite:** N/A
* **Pro:** 7 days
* **Pro Plus:** 7 days
* **Business:** 30 days
* **Enterprise:** 30 days
### Cache keys
**Link:** [Cache keys](https://developers.cloudflare.com/cache/how-to/cache-keys/)
**Cache deception armor**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Cache by device type**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Ignore query string**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Sort query string**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Query string**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Headers**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Cookie**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Host**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**User features**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Set caching level
**Link:** [Set caching level](https://developers.cloudflare.com/cache/how-to/set-caching-levels/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Cache reserve
**Link:** [Cache reserve](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/)
**Feature availability**
* **Free:** Paid add-on
* **Lite:** Paid add-on
* **Pro:** Paid add-on
* **Pro Plus:** Paid add-on
* **Business:** Paid add-on
* **Enterprise:** Paid add-on
### Cache Rules
**Link:** [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Lite:** 10
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
### Cache by status code
**Link:** [Cache by status code](https://developers.cloudflare.com/cache/how-to/configure-cache-status-code/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Crawler Hints
**Link:** [Crawler Hints](https://developers.cloudflare.com/cache/advanced-configuration/crawler-hints/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### CSAM Scanning Tool
**Link:** [CSAM Scanning Tool](https://developers.cloudflare.com/cache/reference/csam-scanning/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Development mode
**Link:** [Development mode](https://developers.cloudflare.com/cache/reference/development-mode/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Edge Cache TTL
**Link:** [Edge Cache TTL](https://developers.cloudflare.com/cache/how-to/edge-browser-cache-ttl/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Minimum Edge Cache TTL**
* **Free:** 2 hours
* **Lite:** 2 hours
* **Pro:** 1 hour
* **Pro Plus:** 1 hour
* **Business:** 1 second
* **Enterprise:** 1 second
### ETag Headers
**Link:** [ETag Headers](https://developers.cloudflare.com/cache/reference/etag-headers/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Purge cache
**Link:** [Purge cache](https://developers.cloudflare.com/cache/how-to/purge-cache/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Purge options**
* **Free:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Lite:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Pro:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Pro Plus:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Business:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Enterprise:** URL, Hostname, Tag, Prefix, and Purge Everything
### Purge limits for hostname, tag, prefix URL, and purge everything.
**Link:** [Purge limits for hostname, tag, prefix URL, and purge everything.](https://developers.cloudflare.com/cache/how-to/purge-cache/)
**Requests**
Available on all plans
* **Free:** 5 requests per minute
* **Lite:** 5 requests per minute
* **Pro:** 5 requests per second
* **Pro Plus:** 5 requests per second
* **Business:** 10 requests per second
* **Enterprise:** 50 requests per second
**Bucket size**
* **Free:** 25
* **Lite:** 25
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 500
**Max operations per request**
* **Free:** 100
* **Lite:** 100
* **Pro:** 100
* **Pro Plus:** 100
* **Business:** 100
* **Enterprise:** 100
### Single file purge
**Link:** [Single file purge](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-single-file/)
**URLs**
Available on all plans
* **Free:** 800 URLs per second
* **Lite:** 800 URLs per second
* **Pro:** 1500 URLs per second
* **Pro Plus:** 1500 URLs per second
* **Business:** 1500 URLs per second
* **Enterprise:** 3000 URLs per second
**Max operations per request**
* **Free:** 100
* **Lite:** 100
* **Pro:** 100
* **Pro Plus:** 100
* **Business:** 100
* **Enterprise:** 500
### Query string sort
**Link:** [Query string sort](https://developers.cloudflare.com/cache/advanced-configuration/query-string-sort/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Tiered cache
**Link:** [Tiered cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/)
**Tiered Cache**
Available on all plans
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Smart Topology**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Generic Global Topology**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Regional Tiered Cache**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Custom Topology**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Vary for images
**Link:** [Vary for images](https://developers.cloudflare.com/cache/advanced-configuration/vary-for-images/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
## DNS
### Advanced nameservers
**Link:** [Advanced nameservers](https://developers.cloudflare.com/dns/foundation-dns/advanced-nameservers/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Included with [Foundation DNS](https://developers.cloudflare.com/dns/foundation-dns/)
### CNAME flattening
**Link:** [CNAME flattening](https://developers.cloudflare.com/dns/cname-flattening/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Can customize**
Pro plans and above can customize
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Custom nameservers
**Link:** [Custom nameservers](https://developers.cloudflare.com/dns/nameservers/custom-nameservers/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
### DNS analytics
**Link:** [DNS analytics](https://developers.cloudflare.com/dns/additional-options/analytics/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Maximum time interval (zone)**
* **Free:** 7 days
* **Lite:** 7 days
* **Pro:** 31 days
* **Pro Plus:** 31 days
* **Business:** 31 days
* **Enterprise:** 62 days
**Maximum time interval (account)**
* **Free:** 7 days
* **Lite:** 7 days
* **Pro:** 7 days
* **Pro Plus:** 7 days
* **Business:** 7 days
* **Enterprise:** 62 days
**Historical data (zone)**
* **Free:** 8 days
* **Lite:** 8 days
* **Pro:** 31 days
* **Pro Plus:** 31 days
* **Business:** 31 days
* **Enterprise:** 62 days
**Historical data (account)**
* **Free:** 8 days
* **Lite:** 8 days
* **Pro:** 8 days
* **Pro Plus:** 8 days
* **Business:** 8 days
* **Enterprise:** 62 days
### DNSSEC
**Link:** [DNSSEC](https://developers.cloudflare.com/dns/dnssec/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### DNS Firewall
**Link:** [DNS Firewall](https://developers.cloudflare.com/dns/dns-firewall/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**Historical data**
* **Free:** N/A
* **Lite:** N/A
* **Pro:** N/A
* **Pro Plus:** N/A
* **Business:** N/A
* **Enterprise:** 62 days
**Maximum time interval**
* **Free:** N/A
* **Lite:** N/A
* **Pro:** N/A
* **Pro Plus:** N/A
* **Business:** N/A
* **Enterprise:** 62 days
### Full zone setup
**Link:** [Full zone setup](https://developers.cloudflare.com/dns/zone-setups/full-setup/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Partial zone setup
**Link:** [Partial zone setup](https://developers.cloudflare.com/dns/zone-setups/partial-setup/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
### DNS records management
**Link:** [DNS records management](https://developers.cloudflare.com/dns/manage-dns-records/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of records per zone**
* **Free:** 1,000 for zones created before `2024-09-01 00:00:00 UTC`\
200 for zones created on or after `2024-09-01 00:00:00 UTC`
* **Lite:** 1,000 for zones created before `2024-09-01 00:00:00 UTC`\
200 for zones created on or after `2024-09-01 00:00:00 UTC`
* **Pro:** 3,500
* **Pro Plus:** 3,500
* **Business:** 3,500
* **Enterprise:** 3,500 (can be increased)
### DNS record comments
**Link:** [DNS record comments](https://developers.cloudflare.com/dns/manage-dns-records/reference/record-attributes/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Character limit**
* **Free:** 100
* **Lite:** 500
* **Pro:** 500
* **Pro Plus:** 500
* **Business:** 500
* **Enterprise:** 500
**Comments per record**
* **Free:** 1
* **Lite:** 1
* **Pro:** 1
* **Pro Plus:** 1
* **Business:** 1
* **Enterprise:** 1
### DNS record tags
**Link:** [DNS record tags](https://developers.cloudflare.com/dns/manage-dns-records/reference/record-attributes/)
**Feature availability**
* **Free:** No
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Name character limit (everything before the colon)**
* **Free:** N/A
* **Lite:** 32
* **Pro:** 32
* **Pro Plus:** 32
* **Business:** 32
* **Enterprise:** 32
**Value character limit (everything after the colon)**
* **Free:** N/A
* **Lite:** 100
* **Pro:** 100
* **Pro Plus:** 100
* **Business:** 100
* **Enterprise:** 100
**Tags per record**
* **Free:** N/A
* **Lite:** 20
* **Pro:** 20
* **Pro Plus:** 20
* **Business:** 20
* **Enterprise:** 20
### DNS zone transfers
**Link:** [DNS zone transfers](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Subdomain zone setup
**Link:** [Subdomain zone setup](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Subdomain delegation
**Link:** [Subdomain delegation](https://developers.cloudflare.com/dns/manage-dns-records/how-to/subdomains-outside-cloudflare/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Reverse zones
**Link:** [Reverse zones](https://developers.cloudflare.com/dns/additional-options/reverse-zones/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
## Email
### Email Routing
**Link:** [Email Routing](https://developers.cloudflare.com/email-routing/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Area 1 Email Security
**Link:** [Area 1 Email Security](https://developers.cloudflare.com/email-security/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
## Global configurations
### Lists
**Link:** [Lists](https://developers.cloudflare.com/waf/tools/lists/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of custom lists (any type)**
* **Free:** 1
* **Lite:** 10
* **Pro:** 10
* **Pro Plus:** 10
* **Business:** 10
* **Enterprise:** 1,000
**Max. number of list items (across all custom lists)**
* **Free:** 10,000
* **Lite:** 10,000
* **Pro:** 10,000
* **Pro Plus:** 10,000
* **Business:** 10,000
* **Enterprise:** 500,000
**IP lists**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Other custom lists (hostnames, ASNs)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Managed IP List: Cloudflare Open Proxies**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**All Managed IP Lists**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** With separate add-on
## Network
### 0-RTT Connection Resumption
**Link:** [0-RTT Connection Resumption](https://developers.cloudflare.com/speed/optimization/protocol/0-rtt-connection-resumption/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### gRPC
**Link:** [gRPC](https://developers.cloudflare.com/network/grpc-connections/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### IP Geolocation
**Link:** [IP Geolocation](https://developers.cloudflare.com/network/ip-geolocation/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### IPv6 Compatibility
**Link:** [IPv6 Compatibility](https://developers.cloudflare.com/network/ipv6-compatibility/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Can customize**
Only Enterprise can customize
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Max upload size
**Link:** [Max upload size](https://developers.cloudflare.com/cache/concepts/default-cache-behavior/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Max upload size**
* **Free:** 100 MB
* **Lite:** 100 MB
* **Pro:** 100 MB
* **Pro Plus:** 200 MB
* **Business:** 200 MB
* **Enterprise:** 500+ MB
### Onion Routing
**Link:** [Onion Routing](https://developers.cloudflare.com/network/onion-routing/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Pseudo IPv4
**Link:** [Pseudo IPv4](https://developers.cloudflare.com/network/pseudo-ipv4/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### True Client IP Header
**Link:** [True Client IP Header](https://developers.cloudflare.com/fundamentals/reference/http-headers/#true-client-ip-enterprise-plan-only)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### WebSockets
**Link:** [WebSockets](https://developers.cloudflare.com/network/websockets/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Volume of concurrent connections**
Varies by plan
* **Free:** Low (hobby projects)
* **Lite:** Low (hobby projects)
* **Pro:** Medium (Small businesses)
* **Pro Plus:** Medium (Small businesses)
* **Business:** High (important applications)
* **Enterprise:** Custom (mission-critical applications)
## Rules
### Bulk Redirects
**Link:** [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Bulk Redirect Rules**
* **Free:** 15
* **Lite:** 15
* **Pro:** 15
* **Pro Plus:** 15
* **Business:** 15
* **Enterprise:** 50
**Bulk Redirect Lists**
* **Free:** 5
* **Lite:** 5
* **Pro:** 5
* **Pro Plus:** 5
* **Business:** 5
* **Enterprise:** 25
**URL redirects across lists**
* **Free:** 10,000
* **Lite:** 10,000
* **Pro:** 25,000
* **Pro Plus:** 25,000
* **Business:** 50,000
* **Enterprise:** 1,000,000
### Cloud Connector (beta)
**Link:** [Cloud Connector (beta)](https://developers.cloudflare.com/rules/cloud-connector/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Lite:** 10
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
### Configuration Rules
**Link:** [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Lite:** 10
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
### Compression Rules
**Link:** [Compression Rules](https://developers.cloudflare.com/rules/compression-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Lite:** 10
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
### Custom Errors
**Link:** [Custom Errors](https://developers.cloudflare.com/rules/custom-errors/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 0
* **Lite:** 0
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
**Number of assets**
* **Free:** 0
* **Lite:** 0
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
**Error Pages**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Origin Error Pages**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Origin Rules
**Link:** [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Lite:** 10
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
**Override Host header**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Override SNI**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Override DNS records**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Override destination port**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Page Rules
**Link:** [Page Rules](https://developers.cloudflare.com/rules/page-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 3
* **Lite:** 3
* **Pro:** 20
* **Pro Plus:** 30
* **Business:** 50
* **Enterprise:** 125
### Snippets
**Link:** [Snippets](https://developers.cloudflare.com/rules/snippets/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of snippets**
* **Free:** 0
* **Lite:** 0
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
**Number of snippet subrequests**
* **Free:** 0
* **Lite:** 0
* **Pro:** 2
* **Pro Plus:** 2
* **Business:** 3
* **Enterprise:** 5
### Single Redirects
**Link:** [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Lite:** 10
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
**Wildcard support**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Regex support**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
### Transform Rules
**Link:** [Transform Rules](https://developers.cloudflare.com/rules/transform/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Active Transform Rules**
* **Free:** 10
* **Lite:** 10
* **Pro:** 25
* **Pro Plus:** 25
* **Business:** 50
* **Enterprise:** 300
**Regex support**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
## Scrape Shield
### Email Address Obfuscation
**Link:** [Email Address Obfuscation](https://developers.cloudflare.com/waf/tools/scrape-shield/email-address-obfuscation/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Hotlink Protection
**Link:** [Hotlink Protection](https://developers.cloudflare.com/waf/tools/scrape-shield/hotlink-protection/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
## Security
### Bot protection
**Link:** [Bot protection](https://developers.cloudflare.com/bots/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Bot analytics**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Bot Management variables**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**Bot Fight Mode**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Super Bot Fight Mode**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### DDoS protection
**Link:** [DDoS protection](https://developers.cloudflare.com/ddos-protection/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Standard, unmetered DDoS protection (layers 3-7)**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**HTTP DDoS attack protection**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Network-layer (L3/4) DDoS attack protection**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Managed rules customization**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes, with Log action
**Proactive false positive detection for new rules**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Adaptive DDoS protection**
* **Free:** Only error adaptive rules
* **Lite:** Only error adaptive rules
* **Pro:** Only error adaptive rules
* **Pro Plus:** Only error adaptive rules
* **Business:** Only error adaptive rules
* **Enterprise:** Only error adaptive rules
**Traffic profiling signals for adaptive DDoS protection**
* **Free:** Error rates only
* **Lite:** Error rates only
* **Pro:** Error rates only
* **Pro Plus:** Error rates only
* **Business:** Error rates & historical trends
* **Enterprise:** Error rates & historical trends
**Advanced TCP Protection**
* **Free:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Lite:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Pro:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Pro Plus:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Business:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Enterprise:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
**Advanced DNS Protection**
* **Free:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Lite:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Pro:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Pro Plus:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Business:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
* **Enterprise:** Available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers
**Number of ruleset overrides allowed**
* **Free:** 1
* **Lite:** 1
* **Pro:** 1
* **Pro Plus:** 1
* **Business:** 1
* **Enterprise:** 1
**Alerts**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Security Events
**Link:** [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Dashboard features**
* **Free:** Sampled logs only
* **Lite:** Sampled logs only
* **Pro:** All
* **Pro Plus:** All
* **Business:** All
* **Enterprise:** All
**Account-level dashboard**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Historical time**
* **Free:** Up to the last 24 hours
* **Lite:** Up to the last 24 hours
* **Pro:** Up to the last 24 hours
* **Pro Plus:** Up to the last 24 hours
* **Business:** Up to the last 72 hours
* **Enterprise:** Up to the last 30 days
**Export report**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Up to 500 events
* **Enterprise:** Up to 500 events
**Print report**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Security Analytics
**Link:** [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Retention**
* **Free:** 7
* **Lite:** 7
* **Pro:** 31
* **Pro Plus:** 31
* **Business:** 31
* **Enterprise:** 90
**Query window**
* **Free:** 1
* **Lite:** 1
* **Pro:** 7
* **Pro Plus:** 7
* **Business:** 31
* **Enterprise:** 31
### Firewall rules (deprecated)
**Link:** [Firewall rules (deprecated)](https://developers.cloudflare.com/firewall/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 5
* **Lite:** 20
* **Pro:** 20
* **Pro Plus:** 40
* **Business:** 100
* **Enterprise:** 1,000
**Supported actions**
* **Free:** All except Log
* **Lite:** All except Log
* **Pro:** All except Log
* **Pro Plus:** All except Log
* **Business:** All except Log
* **Enterprise:** All
**Regex support**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
### IP Access Rules
**Link:** [IP Access Rules](https://developers.cloudflare.com/waf/tools/ip-access-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 50,000
* **Lite:** 50,000
* **Pro:** 50,000
* **Pro Plus:** 50,000
* **Business:** 50,000
* **Enterprise:** 50,000, but can purchase more
**Block by country**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### WAF Managed Rules
**Link:** [WAF Managed Rules](https://developers.cloudflare.com/waf/managed-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Free Managed Ruleset**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Cloudflare Managed Ruleset**
Available on paid plans
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Cloudflare OWASP Core Ruleset**
Available on paid plans
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Cloudflare Exposed Credentials Check**
Available on paid plans
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Cloudflare Sensitive Data Detection**
Enterprise with add-on
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
### WAF detections
**Link:** [WAF detections](https://developers.cloudflare.com/waf/detections/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Malicious uploads detection**
Enterprise with add-on
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**Leaked credentials detection**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Leaked credentials fields**
* **Free:** Password Leaked
* **Lite:** Password Leaked
* **Pro:** Password Leaked, User and Password Leaked
* **Pro Plus:** Password Leaked, User and Password Leaked
* **Business:** Password Leaked, User and Password Leaked
* **Enterprise:** All leaked credentials fields
**Number of custom detection locations**
Enterprise-only
* **Free:** 0
* **Lite:** 0
* **Pro:** 0
* **Pro Plus:** 0
* **Business:** 0
* **Enterprise:** 10
**Attack score**
Business and Enterprise plans
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** One field only
* **Enterprise:** Yes
**Firewall for AI (beta)**
Enterprise-only
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### WAF custom rules
**Link:** [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 5
* **Lite:** 20
* **Pro:** 20
* **Pro Plus:** 40
* **Business:** 100
* **Enterprise:** 1,000
**Supported actions**
* **Free:** All except Log
* **Lite:** All except Log
* **Pro:** All except Log
* **Pro Plus:** All except Log
* **Business:** All except Log
* **Enterprise:** All
**Regex support**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**Number of custom rulesets (zone)**
* **Free:** 1
* **Lite:** 1
* **Pro:** 2
* **Pro Plus:** 2
* **Business:** 5
* **Enterprise:** 10
**Account-level custom rulesets**
Enterprise with add-on
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
### Page Shield
**Link:** [Page Shield](https://developers.cloudflare.com/page-shield/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Script monitoring**
Available on all plans
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Connection monitoring**
Business and above
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**Cookie monitoring**
Business and above
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**Page attribution**
Business and above
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**New Resources Alerts and New Domain Alerts**
Business and above
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**Malicious script detection and alerting**
Enterprise with add-on
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** No
**Code change detection and alerting**
Enterprise with add-on
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** No
**Malicious connection detection and alerting**
Enterprise with add-on
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** No
**Cookie monitoring advanced fields**
Enterprise with add-on
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** No
**Number of policies (positive blocking)**
Enterprise with add-on
* **Free:** 0
* **Lite:** 0
* **Pro:** 0
* **Pro Plus:** 0
* **Business:** 0
* **Enterprise:** 0
**Number of Logpush jobs**
Enterprise with add-on
* **Free:** 0
* **Lite:** 0
* **Pro:** 0
* **Pro Plus:** 0
* **Business:** 0
* **Enterprise:** 0
### Rate limiting rules (new version)
**Link:** [Rate limiting rules (new version)](https://developers.cloudflare.com/waf/rate-limiting-rules/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 1
* **Lite:** 1
* **Pro:** 2
* **Pro Plus:** 2
* **Business:** 5
* **Enterprise:** 5
### Rate Limiting (previous version)
**Link:** [Rate Limiting (previous version)](https://developers.cloudflare.com/waf/reference/legacy/old-rate-limiting/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 1
* **Lite:** 10
* **Pro:** 10
* **Pro Plus:** 15
* **Business:** 15
* **Enterprise:** 100
**Number of header rules**
* **Free:** 1
* **Lite:** 1
* **Pro:** 1
* **Pro Plus:** 10
* **Business:** 10
* **Enterprise:** 10
### User Agent Blocking
**Link:** [User Agent Blocking](https://developers.cloudflare.com/waf/tools/user-agent-blocking/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Lite:** 50
* **Pro:** 50
* **Pro Plus:** 250
* **Business:** 250
* **Enterprise:** 1,000
### Zone Lockdown
**Link:** [Zone Lockdown](https://developers.cloudflare.com/waf/tools/zone-lockdown/)
**Feature availability**
* **Free:** No
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 0
* **Lite:** 3
* **Pro:** 3
* **Pro Plus:** 10
* **Business:** 10
* **Enterprise:** 200
### Turnstile
**Link:** [Turnstile](https://developers.cloudflare.com/turnstile/)
**Pricing**
* **Free:** Free
* **Lite:** Free
* **Enterprise:** Contact Sales
**Number of widgets**
* **Free:** Up to 20 widgets
* **Lite:** Up to 20 widgets
* **Enterprise:** Unlimited
**All widget types**
* **Free:** Yes
* **Lite:** Yes
* **Enterprise:** Yes
**Unlimited challenges (traffic or verification requests)**
* **Free:** Yes
* **Lite:** Yes
* **Enterprise:** Yes
**Hostname management**
* **Free:** 10 hostnames per widget
* **Lite:** 10 hostnames per widget
* **Enterprise:** Maximum of 200 hostnames per widget
**Any hostname widget (no preconfigured hostnames)**
* **Free:** No
* **Lite:** No
* **Enterprise:** Yes
**Analytics lookback**
* **Free:** 7 days maximum
* **Lite:** 7 days maximum
* **Enterprise:** 30 days maximum
**Pre-clearance support**
* **Free:** Yes
* **Lite:** Yes
* **Enterprise:** Yes
**Ephemeral IDs**
* **Free:** No
* **Lite:** No
* **Enterprise:** Yes
**Offlabel (remove Cloudflare branding)**
* **Free:** No
* **Lite:** No
* **Enterprise:** Yes
**WCAG 2.1 AA compliance**
* **Free:** Yes
* **Lite:** Yes
* **Enterprise:** Yes
**Community support**
* **Free:** Yes
* **Lite:** Yes
* **Enterprise:** Yes
## Spectrum
### Spectrum
**Link:** [Spectrum](https://developers.cloudflare.com/spectrum/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Paid add-on
* **Pro Plus:** Paid add-on
* **Business:** Paid add-on
* **Enterprise:** Yes
**TCP**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**UDP**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**HTTP**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**HTTPS**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**Minecraft (one app allowed)**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**SSH (one app allowed)**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**RDP (one app allowed)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
## Speed
### Automatic Platform Optimization
**Link:** [Automatic Platform Optimization](https://developers.cloudflare.com/automatic-platform-optimization/)
**Feature availability**
* **Free:** Paid add-on
* **Lite:** Paid add-on
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Brotli compression
**Link:** [Brotli compression](https://developers.cloudflare.com/speed/optimization/content/compression/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Early Hints
**Link:** [Early Hints](https://developers.cloudflare.com/cache/advanced-configuration/early-hints)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Enhanced HTTP/2 Prioritization
**Link:** [Enhanced HTTP/2 Prioritization](https://developers.cloudflare.com/speed/optimization/protocol/enhanced-http2-prioritization/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### HTTP/2
**Link:** [HTTP/2](https://developers.cloudflare.com/speed/optimization/protocol/http2/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Can customize**
Free customers cannot disable
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### HTTP/2 to Origin
**Link:** [HTTP/2 to Origin](https://developers.cloudflare.com/speed/optimization/protocol/http2-to-origin/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### HTTP/3 (with QUIC)
**Link:** [HTTP/3 (with QUIC)](https://developers.cloudflare.com/speed/optimization/protocol/http3/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Image Optimization
**Link:** [Image Optimization](https://developers.cloudflare.com/images/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Paid add-on
* **Pro Plus:** Paid add-on
* **Business:** Paid add-on
* **Enterprise:** Paid add-on
### Polish
**Link:** [Polish](https://developers.cloudflare.com/images/polish/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Prefetch URLs
**Link:** [Prefetch URLs](https://developers.cloudflare.com/speed/optimization/content/prefetch-urls/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Rocket Loader
**Link:** [Rocket Loader](https://developers.cloudflare.com/speed/optimization/content/rocket-loader/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Speed Brain
**Link:** [Speed Brain](https://developers.cloudflare.com/speed/optimization/content/speed-brain/)
**Feature availability**
* **Free:** Enabled by default
* **Lite:** Enabled by default
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### TCP Turbo
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
## SSL/TLS
### Advanced Certificates
**Link:** [Advanced Certificates](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
**Feature availability**
* **Free:** Paid add-on
* **Lite:** Paid add-on
* **Pro:** Paid add-on
* **Pro Plus:** Paid add-on
* **Business:** Paid add-on
* **Enterprise:** Paid add-on
### Authenticated origin pull
**Link:** [Authenticated origin pull](https://developers.cloudflare.com/ssl/origin-configuration/authenticated-origin-pull/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Backup Certificates
**Link:** [Backup Certificates](https://developers.cloudflare.com/ssl/edge-certificates/backup-certificates/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Can opt out?**
Enterprise-only
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Custom Certificates
**Link:** [Custom Certificates](https://developers.cloudflare.com/ssl/edge-certificates/custom-certificates/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Certificates included**
* **Free:** 0
* **Lite:** 0
* **Pro:** 0
* **Pro Plus:** 1
* **Business:** 1 Modern and 1 Legacy
* **Enterprise:** 1 Modern (can purchase more) and 1 Legacy (can purchase more)
### Always Use HTTPS
**Link:** [Always Use HTTPS](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/always-use-https/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Automatic HTTPS Rewrites
**Link:** [Automatic HTTPS Rewrites](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/automatic-https-rewrites/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Certificate Transparency Monitoring
**Link:** [Certificate Transparency Monitoring](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/certificate-transparency-monitoring/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Email Recipients**
* **Free:** All account members
* **Lite:** All account members
* **Pro:** All account members
* **Pro Plus:** All account members
* **Business:** Specified email addresses
* **Enterprise:** Specified email addresses
### Opportunistic Encryption
**Link:** [Opportunistic Encryption](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/opportunistic-encryption/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### HTTP Strict Transport Security
**Link:** [HTTP Strict Transport Security](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/http-strict-transport-security/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### TLS 1.3
**Link:** [TLS 1.3](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/tls-13/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Minimum TLS Version
**Link:** [Minimum TLS Version](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/minimum-tls/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Per-hostname**
* **Free:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Lite:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro Plus:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Business:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Enterprise:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
### Certificate Signing Requests
**Link:** [Certificate Signing Requests](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/certificate-signing-requests/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
### Custom Hostnames
**Link:** [Custom Hostnames](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/plans/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Contact your account team
**Hostnames included**
Varies
* **Free:** 100
* **Lite:** 100
* **Pro:** 100
* **Pro Plus:** 100
* **Business:** 100
* **Enterprise:** Custom
**Max hostnames**
* **Free:** 50,000
* **Lite:** 50,000
* **Pro:** 50,000
* **Pro Plus:** 50,000
* **Business:** 50,000
* **Enterprise:** Unlimited, but contact sales if using over 50,000.
**Price per additional hostname**
* **Free:** $0.10
* **Lite:** $0.10
* **Pro:** $0.10
* **Pro Plus:** $0.10
* **Business:** $0.10
* **Enterprise:** Custom pricing
**[Custom analytics](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/hostname-analytics/)**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**[Custom origin](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/advanced-settings/custom-origin/)**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**[SNI Rewrite for Custom Origin](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/advanced-settings/custom-origin/#sni-rewrites)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Contact your account team
**[Custom certificates](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/custom-certificates/)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**[CSR support](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/custom-certificates/certificate-signing-requests/)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**[Selectable CA](https://developers.cloudflare.com/ssl/reference/certificate-authorities/)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Wildcard custom hostnames**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**Non-SNI support for SaaS zone**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**[mTLS support](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/enforce-mtls/)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
**[WAF for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/waf-for-saas/)**
* **Free:** WAF rules with current zone plan
* **Lite:** WAF rules with current zone plan
* **Pro:** WAF rules with current zone plan
* **Pro Plus:** WAF rules with current zone plan
* **Business:** WAF rules with current zone plan
* **Enterprise:** Create and apply custom firewall rulesets.
**[Apex proxying/BYOIP](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/advanced-settings/apex-proxying/)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
**[Custom metadata](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/domain-support/custom-metadata/)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
### Custom origin trust store
**Link:** [Custom origin trust store](https://developers.cloudflare.com/ssl/origin-configuration/custom-origin-trust-store/)
**Feature availability**
* **Free:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Lite:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro Plus:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Business:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Enterprise:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
### SSL/TLS encryption mode
**Link:** [SSL/TLS encryption mode](https://developers.cloudflare.com/ssl/origin-configuration/ssl-modes/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Strict (SSL-Only Origin Pull)**
Enterprise-only
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Keyless SSL
**Link:** [Keyless SSL](https://developers.cloudflare.com/ssl/keyless-ssl/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Paid add-on
### Origin certificates
**Link:** [Origin certificates](https://developers.cloudflare.com/ssl/origin-configuration/origin-ca/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Staging environment
**Link:** [Staging environment](https://developers.cloudflare.com/ssl/edge-certificates/staging-environment/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes (open beta)
### SSL/TLS Recommender
**Link:** [SSL/TLS Recommender](https://developers.cloudflare.com/ssl/origin-configuration/ssl-tls-recommender/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Custom cipher suites
**Link:** [Custom cipher suites](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/cipher-suites/customize-cipher-suites/)
**Feature availability**
* **Free:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Lite:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro Plus:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Business:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Enterprise:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
### Total TLS
**Link:** [Total TLS](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/total-tls/)
**Feature availability**
* **Free:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Lite:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro Plus:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Business:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Enterprise:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
### Delegated DCV
**Link:** [Delegated DCV](https://developers.cloudflare.com/ssl/edge-certificates/changing-dcv-method/methods/delegated-dcv/)
**Feature availability**
* **Free:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Lite:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Pro Plus:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Business:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
* **Enterprise:** Included with [Advanced Certificate Manager](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/)
### Universal Certificates
**Link:** [Universal Certificates](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Client Certificates
**Link:** [Client Certificates](https://developers.cloudflare.com/ssl/client-certificates/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Client Certificates included, issued by a Cloudflare Managed CA**
* **Free:** 100
* **Lite:** 100
* **Pro:** 100
* **Pro Plus:** 100
* **Business:** 100
* **Enterprise:** 100 (default), but can allocate more quota.
**[Bring your own CA](https://developers.cloudflare.com/ssl/client-certificates/byo-ca/)**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
## Support
### Ticket Support
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Initial ticket response time**
* **Free:** N/A
* **Lite:** N/A
* **Pro:** N/A
* **Pro Plus:** N/A
* **Business:** 8-72 hrs (P1-P4 issues)
* **Enterprise:** 1hr (urgent issues)
### Chat Support
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
### 24x7x365 Emergency Phone Support
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Yes
### Uptime guarantees
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**SLA**
* **Free:** N/A
* **Lite:** N/A
* **Pro:** N/A
* **Pro Plus:** N/A
* **Business:** 100%
* **Enterprise:** 100%
**Service credits**
* **Free:** N/A
* **Lite:** N/A
* **Pro:** N/A
* **Pro Plus:** N/A
* **Business:** 1x
* **Enterprise:** 10x (Standard) 25x (Premium)
## Traffic
### Argo Smart Routing
**Link:** [Argo Smart Routing](https://developers.cloudflare.com/argo-smart-routing/)
**Feature availability**
* **Free:** Paid add-on
* **Lite:** Paid add-on
* **Pro:** Paid add-on
* **Pro Plus:** Paid add-on
* **Business:** Paid add-on
* **Enterprise:** Paid add-on
### Health checks
**Link:** [Health checks](https://developers.cloudflare.com/health-checks/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of checks**
* **Free:** 0
* **Lite:** 0
* **Pro:** 10
* **Pro Plus:** 10
* **Business:** 50
* **Enterprise:** 1,000
**Analytics**
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Load Balancing
**Link:** [Load Balancing](https://developers.cloudflare.com/load-balancing/)
**Feature availability**
* **Free:** Paid add-on
* **Lite:** Paid add-on
* **Pro:** Paid add-on
* **Pro Plus:** Paid add-on
* **Business:** Paid add-on
* **Enterprise:** Paid add-on
**Analytics**
Pro and above
* **Free:** No
* **Lite:** No
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Custom rules**
* **Free:** 1 per hostname
* **Lite:** 1 per hostname
* **Pro:** 1 per hostname
* **Pro Plus:** 1 per hostname
* **Business:** 1 per hostname
* **Enterprise:** Varies
**Origin servers**
* **Free:** Up to 20
* **Lite:** Up to 20
* **Pro:** Up to 20
* **Pro Plus:** Up to 20
* **Business:** Up to 20
* **Enterprise:** Custom
### Waiting Room
**Link:** [Waiting Room](https://developers.cloudflare.com/waiting-room/)
**Feature availability**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**Number of rooms**
Business and above
* **Free:** 0
* **Lite:** 0
* **Pro:** 0
* **Pro Plus:** 0
* **Business:** 1
* **Enterprise:** 1 (default) *With advanced:* Custom (can purchase more)
**Customized templates**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Advanced add-on
**Queueing methods**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** First In First Out (FIFO)
* **Enterprise:** First In First Out (FIFO) (default) *With advanced:* FIFO, Random, Reject, Passthrough
**Configure multiple hostnames and paths**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Advanced add-on
**Disable session renewal**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Advanced add-on
**JSON-friendly response**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Advanced add-on
**Customize queuing status code**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**Scheduled events**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Advanced add-on
**Waiting Room rules**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Advanced add-on
**Session Revocation**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** No
* **Enterprise:** Advanced add-on
**SEO Crawler Bypassing**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Yes
* **Enterprise:** Yes
**Turnstile Widget Mode**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Invisible only
* **Enterprise:** Invisible (default) *With advanced:* Invisible, Managed, Non Interactive
**Turnstile Fail Action**
* **Free:** No
* **Lite:** No
* **Pro:** No
* **Pro Plus:** No
* **Business:** Log only
* **Enterprise:** Log only (default) *With advanced:* Log only & Infinite queue
## Web3
### IPFS Gateways
**Link:** [IPFS Gateways](https://developers.cloudflare.com/web3/ipfs-gateway/)
**Feature availability**
* **Free:** Yes (Usage-based billing)
* **Lite:** Yes (Usage-based billing)
* **Pro:** Yes (Usage-based billing)
* **Pro Plus:** Yes (Usage-based billing)
* **Business:** Yes (Usage-based billing)
* **Enterprise:** Yes (Usage-based billing)
**Total gateways**
* **Free:** 15
* **Lite:** 15
* **Pro:** 15
* **Pro Plus:** 15
* **Business:** 15
* **Enterprise:** Unlimited
**Gateway types**
* **Free:** [DNSLink](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/dnslink/)
* **Lite:** [DNSLink](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/dnslink/)
* **Pro:** [DNSLink](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/dnslink/)
* **Pro Plus:** [DNSLink](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/dnslink/)
* **Business:** [DNSLink](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/dnslink/)
* **Enterprise:** [DNSLink](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/dnslink/), [Universal Gateway](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/universal-gateway/)
**Included bandwidth (without additional cost)**
* **Free:** 50 GB data transfer
* **Lite:** 50 GB data transfer
* **Pro:** 50 GB data transfer
* **Pro Plus:** 50 GB data transfer
* **Business:** 50 GB data transfer
* **Enterprise:** 100 GB data transfer
**File size limit**
* **Free:** None
* **Lite:** None
* **Pro:** None
* **Pro Plus:** None
* **Business:** None
* **Enterprise:** None
### Ethereum Gateways
**Link:** [Ethereum Gateways](https://developers.cloudflare.com/web3/ethereum-gateway/)
**Feature availability**
* **Free:** Yes (Usage-based billing)
* **Lite:** Yes (Usage-based billing)
* **Pro:** Yes (Usage-based billing)
* **Pro Plus:** Yes (Usage-based billing)
* **Business:** Yes (Usage-based billing)
* **Enterprise:** Yes (Usage-based billing)
**Total gateways**
* **Free:** 15
* **Lite:** 15
* **Pro:** 15
* **Pro Plus:** 15
* **Business:** 15
* **Enterprise:** Unlimited
**Included bandwidth (without additional cost)**
* **Free:** 500,000 HTTP requests
* **Lite:** 500,000 HTTP requests
* **Pro:** 500,000 HTTP requests
* **Pro Plus:** 500,000 HTTP requests
* **Business:** 500,000 HTTP requests
* **Enterprise:** 1,000,000 HTTP requests
## Zaraz
### Zaraz
**Link:** [Zaraz](https://developers.cloudflare.com/zaraz/)
**Feature availability**
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Consent Management**
Available on all plans
* **Free:** Yes
* **Lite:** Yes
* **Pro:** Yes
* **Pro Plus:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Preview mode**
Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Free:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Lite:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Pro:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Pro Plus:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Business:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Enterprise:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
**History**
Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Free:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Lite:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Pro:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Pro Plus:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Business:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
* **Enterprise:** Included with a [Workers Paid Plan](https://developers.cloudflare.com/workers/platform/pricing/)
## Missing features
This page is meant to be a companion to our [Plans and Pricing page](https://www.cloudflare.com/plans/), but is not meant to be comprehensive. In the event of any inconsistency between this page and the Plans and Pricing page, the Plans and Pricing page controls.
Refer to the following locations for more information:
* **Developer products**: Refer to the [Developer Platform pricing page](https://www.cloudflare.com/plans/developer-platform/) or individual [product docs](https://developers.cloudflare.com/directory/) to learn more about plans and pricing.
* **Zero Trust products**: Refer to the [Zero Trust pricing](https://www.cloudflare.com/plans/zero-trust-services/) page.
* **Other products**: Refer to the individual [product docs](https://developers.cloudflare.com/directory/) to learn more about plans and pricing.
---
title: Overview · Cloudflare Privacy Gateway docs
description: Privacy Gateway is a managed service deployed on Cloudflare’s
global network that implements part of the Oblivious HTTP (OHTTP) IETF
standard. The goal of Privacy Gateway and Oblivious HTTP is to hide the
client's IP address when interacting with an application backend.
lastUpdated: 2026-02-03T18:17:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-gateway/
md: https://developers.cloudflare.com/privacy-gateway/index.md
---
Implements the Oblivious HTTP IETF standard to improve client privacy.
Enterprise-only
[Privacy Gateway](https://blog.cloudflare.com/building-privacy-into-internet-standards-and-how-to-make-your-app-more-private-today/) is a managed service deployed on Cloudflare’s global network that implements part of the [Oblivious HTTP (OHTTP) IETF](https://www.ietf.org/archive/id/draft-thomson-http-oblivious-01.html) standard. The goal of Privacy Gateway and Oblivious HTTP is to hide the client's IP address when interacting with an application backend.
OHTTP introduces a trusted third party between client and server, called a relay, whose purpose is to forward encrypted requests and responses between client and server. These messages are encrypted between client and server such that the relay learns nothing of the application data, beyond the length of the encrypted message and the server the client is interacting with.
***
## Availability
Privacy Gateway is currently in closed beta – available to select privacy-oriented companies and partners. If you are interested, [contact us](https://www.cloudflare.com/lp/privacy-edge/).
***
## Features
### Get started
Learn how to set up Privacy Gateway for your application.
[Get started](https://developers.cloudflare.com/privacy-gateway/get-started/)
### Legal
Learn about the different parties and data shared in Privacy Gateway.
[Learn more](https://developers.cloudflare.com/privacy-gateway/reference/legal/)
### Metrics
Learn about how to query Privacy Gateway metrics.
[Learn more](https://developers.cloudflare.com/privacy-gateway/reference/metrics/)
---
title: Privacy Proxy · Cloudflare Privacy Proxy docs
description: Privacy Proxy is a managed proxy service that runs on Cloudflare's
global network. It uses the MASQUE protocol suite to proxy TCP and UDP traffic
via HTTP CONNECT and CONNECT-UDP methods over HTTP/2 and HTTP/3.
lastUpdated: 2026-02-03T18:20:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-proxy/
md: https://developers.cloudflare.com/privacy-proxy/index.md
---
A MASQUE-based forward proxy that protects user privacy while preserving geolocation accuracy.
Enterprise-only
Privacy Proxy is a managed proxy service that runs on Cloudflare's global network. It uses the [MASQUE](https://datatracker.ietf.org/wg/masque/about/) protocol suite to proxy TCP and UDP traffic via HTTP CONNECT and CONNECT-UDP methods over HTTP/2 and HTTP/3.
Privacy Proxy separates user identity from user activity. Users authenticate to the proxy without revealing which destinations they visit, and destination servers see requests from Cloudflare IP addresses without learning who made them.
Privacy Proxy powers services like [Microsoft Edge Secure Network](https://blog.cloudflare.com/cloudflare-now-powering-microsoft-edge-secure-network/) and serves as a second-hop relay for [iCloud Private Relay](https://blog.cloudflare.com/icloud-private-relay/).
***
## Features
### Single-hop deployment
Deploy Privacy Proxy as a standalone proxy where Cloudflare handles authentication, proxying, and egress.
[Use Single-hop deployment](https://developers.cloudflare.com/privacy-proxy/concepts/deployment-models/#single-hop)
### Double-hop deployment
Operate your own first-hop proxy to authenticate users, then relay traffic through Cloudflare for additional privacy separation.
[Use Double-hop deployment](https://developers.cloudflare.com/privacy-proxy/concepts/deployment-models/#double-hop)
### Geolocation preservation
Maintain accurate geolocation for users without exposing their real IP addresses, ensuring location-relevant content and services work correctly.
[Use Geolocation preservation](https://developers.cloudflare.com/privacy-proxy/concepts/geolocation/)
### Privacy Pass authentication
Authenticate users with Privacy Pass tokens for production deployments, ensuring privacy-preserving access control.
[Use Privacy Pass authentication](https://developers.cloudflare.com/privacy-proxy/concepts/authentication/)
***
## Related products
**[Privacy Gateway](https://developers.cloudflare.com/privacy-gateway/)**
Implements the Oblivious HTTP (OHTTP) standard for request-level privacy, hiding client IP addresses from application backends.
**[WARP Client](https://developers.cloudflare.com/warp-client/)**
Cloudflare's consumer VPN application that uses similar privacy-preserving proxy technology.
***
## Availability
Privacy Proxy is available as a managed service for Enterprise customers. [Contact us](https://www.cloudflare.com/lp/privacy-edge/) to discuss your use case and get started.
---
title: Overview · Pulumi docs
description: Provision and manage Cloudflare using infrastructure as code
through Pulumi. With the Pulumi Cloudflare package, you can build, deploy, and
manage Cloudflare resources using standard programming languages (TypeScript,
JavaScript, Python, .NET, Java, Go, and YAML). You can define the desired
state for your infrastructure in code and leverage language features like
loops, functions, classes, and package management.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pulumi/
md: https://developers.cloudflare.com/pulumi/index.md
---
Create, deploy, and manage Cloudflare resources in various programming languages.
Provision and manage Cloudflare using infrastructure as code through [Pulumi](https://www.pulumi.com/). With the [Pulumi Cloudflare package](https://www.pulumi.com/registry/packages/cloudflare/), you can build, deploy, and manage Cloudflare resources using standard programming languages (TypeScript, JavaScript, Python, .NET, Java, Go, and YAML). You can define the desired state for your infrastructure in code and leverage language features like loops, functions, classes, and package management.
***
## Features
### Open Source
[Pulumi](https://github.com/pulumi/pulumi) is open source and uses the Apache 2.0 license.
[View open source commitment](https://www.pulumi.com/blog/pulumi-hearts-opensource/)
### Multiple languages and SDKs
Use TypeScript, JavaScript, Python, Go, .Net, Java, or YAML to write Pulumi programs. Each language is as capable as the other and supports the entire [Pulumi Registry](https://www.pulumi.com/registry/).
[Use Multiple languages and SDKs](https://www.pulumi.com/docs/languages-sdks/)
***
## Related products
**[Pulumi Cloud](https://www.pulumi.com/product/pulumi-cloud/)**
Pulumi Cloud fully manages infrastructure state and secrets, provides rich search capabilities, and more.
**[Pulumi AI](https://www.pulumi.com/ai)**
Pulumi AI is an experimental feature that lets you use natural-language prompts to generate Pulumi infrastructure-as-code programs in any language.
**[Pulumi ESC](https://www.pulumi.com/product/esc/)**
Pulumi ESC provides centralized management of environments, secrets, and configurations.
***
## More resources
[Visit the Pulumi docs](https://www.pulumi.com/docs)
To learn more about Pulumi.
[Report issues](https://github.com/pulumi/pulumi)
Report Pulumi configuration issues via GitHub.
---
title: Overview · Cloudflare Queues docs
description: Cloudflare Queues integrate with Cloudflare Workers and enable you
to build applications that can guarantee delivery, offload work from a
request, send data from Worker to Worker, and buffer or batch data.
lastUpdated: 2026-02-04T18:31:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/
md: https://developers.cloudflare.com/queues/index.md
---
Send and receive messages with guaranteed delivery and no charges for egress bandwidth.
Available on Free and Paid plans
Cloudflare Queues integrate with [Cloudflare Workers](https://developers.cloudflare.com/workers/) and enable you to build applications that can [guarantee delivery](https://developers.cloudflare.com/queues/reference/delivery-guarantees/), [offload work from a request](https://developers.cloudflare.com/queues/reference/how-queues-works/), [send data from Worker to Worker](https://developers.cloudflare.com/queues/configuration/configure-queues/), and [buffer or batch data](https://developers.cloudflare.com/queues/configuration/batching-retries/).
[Get started](https://developers.cloudflare.com/queues/get-started/)
***
## Features
### Batching, Retries and Delays
Cloudflare Queues allows you to batch, retry and delay messages.
[Use Batching, Retries and Delays](https://developers.cloudflare.com/queues/configuration/batching-retries/)
### Dead Letter Queues
Redirect your messages when a delivery failure occurs.
[Use Dead Letter Queues](https://developers.cloudflare.com/queues/configuration/dead-letter-queues/)
### Pull consumers
Configure pull-based consumers to pull from a queue over HTTP from infrastructure outside of Cloudflare Workers.
[Use Pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/)
***
## Related products
**[R2](https://developers.cloudflare.com/r2/)**
Cloudflare R2 Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
**[Workers](https://developers.cloudflare.com/workers/)**
Cloudflare Workers allows developers to build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
***
## More resources
[Pricing](https://developers.cloudflare.com/queues/platform/pricing/)
Learn about pricing.
[Limits](https://developers.cloudflare.com/queues/platform/limits/)
Learn about Queues limits.
[Try the Demo](https://github.com/Electroid/queues-demo#cloudflare-queues-demo)
Try Cloudflare Queues which can run on your local machine.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[Configuration](https://developers.cloudflare.com/queues/configuration/configure-queues/)
Learn how to configure Cloudflare Queues using Wrangler.
[JavaScript APIs](https://developers.cloudflare.com/queues/configuration/javascript-apis/)
Learn how to use JavaScript APIs to send and receive messages to a Cloudflare Queue.
[Event subscriptions](https://developers.cloudflare.com/queues/event-subscriptions/)
Learn how to configure and manage event subscriptions for your queues.
---
title: R2 SQL · R2 SQL docs
description: A distributed SQL engine for R2 Data Catalog
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2-sql/
md: https://developers.cloudflare.com/r2-sql/index.md
---
Note
R2 SQL is in **open beta**, and any developer with an [R2 subscription](https://developers.cloudflare.com/r2/pricing/) can start using it. Currently, outside of standard R2 storage and operations, you will not be billed for your use of R2 SQL. We will update [the pricing page](https://developers.cloudflare.com/r2-sql/platform/pricing) and provide at least 30 days notice before enabling billing.
Query Apache Iceberg tables managed by R2 Data Catalog using SQL.
R2 SQL is Cloudflare's serverless, distributed, analytics query engine for querying [Apache Iceberg](https://iceberg.apache.org/) tables stored in [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/). R2 SQL is designed to efficiently query large amounts of data by automatically utilizing file pruning, Cloudflare's distributed compute, and R2 object storage.
```sh
❯ npx wrangler r2 sql query "3373912de3f5202317188ae01300bd6_data-catalog" \
"SELECT * FROM default.transactions LIMIT 10"
⛅️ wrangler 4.38.0
────────────────────────────────────────────────────────────────────────────
▲ [WARNING] 🚧 `wrangler r2 sql query` is an open-beta command. Please report any issues to https://github.com/cloudflare/workers-sdk/issues/new/choose
┌─────────────────────────────┬──────────────────────────────────────┬─────────┬──────────┬──────────────────────────────────┬───────────────┬───────────────────┬──────────┐
│ __ingest_ts │ transaction_id │ user_id │ amount │ transaction_timestamp │ location │ merchant_category │ is_fraud │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.872554Z │ fdc1beed-157c-4d2d-90cf-630fdea58051 │ 1679 │ 13241.59 │ 2025-09-20T02:23:04.269988+00:00 │ NEW_YORK │ RESTAURANT │ false │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.724378Z │ ea7ef106-8284-4d08-9348-ad33989b6381 │ 1279 │ 17615.79 │ 2025-09-20T02:23:04.271090+00:00 │ MIAMI │ GAS_STATION │ true │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.724330Z │ afcdee4d-5c71-42be-97ec-e282b6937a8c │ 1843 │ 7311.65 │ 2025-09-20T06:23:04.267890+00:00 │ SEATTLE │ GROCERY │ true │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.657007Z │ b99d14e0-dbe0-49bc-a417-0ee57f8bed99 │ 1976 │ 15228.21 │ 2025-09-16T23:23:04.269426+00:00 │ NEW_YORK │ RETAIL │ false │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.656992Z │ 712cd094-ad4c-4d24-819a-0d3daaaceea1 │ 1184 │ 7570.89 │ 2025-09-20T00:23:04.269163+00:00 │ LOS_ANGELES │ RESTAURANT │ true │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.656912Z │ b5a1aab3-676d-4492-92b8-aabcde6db261 │ 1196 │ 46611.25 │ 2025-09-20T16:23:04.268693+00:00 │ NEW_YORK │ RETAIL │ true │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.613740Z │ 432d3976-8d89-4813-9099-ea2afa2c0e70 │ 1720 │ 21547.9 │ 2025-09-20T05:23:04.273681+00:00 │ SAN FRANCISCO │ GROCERY │ true │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.532068Z │ 25e0b851-3092-4ade-842f-e3189e07d4ee │ 1562 │ 29311.54 │ 2025-09-20T05:23:04.277405+00:00 │ NEW_YORK │ RETAIL │ false │
├─────────────────────────────┼──────────────────────────────────────┼─────────┼──────────┼──────────────────────────────────┼───────────────┼───────────────────┼──────────┤
│ 2025-09-20T22:30:11.526037Z │ 8001746d-05fe-42fe-a189-40caf81d7aa2 │ 1817 │ 15976.5 │ 2025-09-15T16:23:04.266632+00:00 │ SEATTLE │ RESTAURANT │ true │
└─────────────────────────────┴──────────────────────────────────────┴─────────┴──────────┴──────────────────────────────────┴───────────────┴───────────────────┴──────────┘
Read 11.3 kB across 4 files from R2
On average, 3.36 kB / s
```
Create an end-to-end data pipeline by following [this step by step guide](https://developers.cloudflare.com/r2-sql/get-started/), which shows you how to stream events into an Apache Iceberg table and query it with R2 SQL.
---
title: Overview · Cloudflare R2 docs
description: Cloudflare R2 is a cost-effective, scalable object storage solution
for cloud-native apps, web content, and data lakes without egress fees.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/
md: https://developers.cloudflare.com/r2/index.md
---
Object storage for all your data.
Cloudflare R2 Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
You can use R2 for multiple scenarios, including but not limited to:
* Storage for cloud-native applications
* Cloud storage for web content
* Storage for podcast episodes
* Data lakes (analytics and big data)
* Cloud storage output for large batch processes, such as machine learning model artifacts or datasets
[Get started](https://developers.cloudflare.com/r2/get-started/)
[Browse the examples](https://developers.cloudflare.com/r2/examples/)
***
## Features
### Location Hints
Location Hints are optional parameters you can provide during bucket creation to indicate the primary geographical location you expect data will be accessed from.
[Use Location Hints](https://developers.cloudflare.com/r2/reference/data-location/#location-hints)
### CORS
Configure CORS to interact with objects in your bucket and configure policies on your bucket.
[Use CORS](https://developers.cloudflare.com/r2/buckets/cors/)
### Public buckets
Public buckets expose the contents of your R2 bucket directly to the Internet.
[Use Public buckets](https://developers.cloudflare.com/r2/buckets/public-buckets/)
### Bucket scoped tokens
Create bucket scoped tokens for granular control over who can access your data.
[Use Bucket scoped tokens](https://developers.cloudflare.com/r2/api/tokens/)
***
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
A [serverless](https://www.cloudflare.com/learning/serverless/what-is-serverless/) execution environment that allows you to create entirely new applications or augment existing ones without configuring or maintaining infrastructure.
**[Stream](https://developers.cloudflare.com/stream/)**
Upload, store, encode, and deliver live and on-demand video with one API, without configuring or maintaining infrastructure.
**[Images](https://developers.cloudflare.com/images/)**
A suite of products tailored to your image-processing needs.
***
## More resources
[Pricing](https://developers.cloudflare.com/r2/pricing)
Understand pricing for free and paid tier rates.
[Discord](https://discord.cloudflare.com)
Ask questions, show off what you are building, and discuss the platform with other developers.
[Twitter](https://x.com/cloudflaredev)
Learn about product announcements, new tutorials, and what is new in Cloudflare Workers.
---
title: Overview · Cloudflare Radar docs
description: Cloudflare Radar is a hub that showcases global Internet traffic,
attacks, and technology trends and insights. It is powered by data from
Cloudflare’s global network, as well as aggregated and anonymized data from
Cloudflare’s 1.1.1.1 public DNS resolver.
lastUpdated: 2025-05-02T13:54:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/
md: https://developers.cloudflare.com/radar/index.md
---
Get access to Cloudflare's data on global Internet traffic.
Available on all plans
[Cloudflare Radar](https://radar.cloudflare.com) is a hub that showcases global Internet traffic, attacks, and technology trends and insights. It is powered by data from [Cloudflare’s global network](https://www.cloudflare.com/network/), as well as aggregated and [anonymized data](https://developers.cloudflare.com/1.1.1.1/privacy/public-dns-resolver/) from Cloudflare’s [1.1.1.1 public DNS resolver](https://developers.cloudflare.com/1.1.1.1/).
Using [Radar's API](https://developers.cloudflare.com/api/resources/radar/) you can access Cloudflare's data on global Internet traffic. Radar's API is free, allowing academics, technology professionals, and other web enthusiasts to investigate Internet usage across the globe.
Data available via Radar API endpoints is made available under the [CC BY-NC 4.0](https://creativecommons.org/licenses/by-nc/4.0/) license.
[Get started](https://developers.cloudflare.com/radar/get-started/)
[Radar website](https://radar.cloudflare.com/)
***
## Features
### Make your first API request
Start learning how to use Radar's API by making your first request.
[Make your first API request](https://developers.cloudflare.com/radar/get-started/first-request/)
### Compare data
What to know before making comparisons between locations, [autonomous systems](https://www.cloudflare.com/en-gb/learning/network-layer/what-is-an-autonomous-system/), and more.
[Compare data](https://developers.cloudflare.com/radar/get-started/making-comparisons/)
### URL Scanner
Understand the security, performance, technology, and network details of a URL with a publicly shareable report.
[Use URL Scanner](https://developers.cloudflare.com/radar/investigate/url-scanner/)
***
## More resources
[Investigate](https://developers.cloudflare.com/radar/investigate/)
Explore the diverse data available in Cloudflare Radar, including NetFlows, HTTP requests, DNS queries, and much more.
[@CloudflareRadar](https://x.com/cloudflareradar)
Follow @CloudflareRadar on X to learn about Internet trends, as seen by the Cloudflare global network.
[@cloudflareradar](https://noc.social/@cloudflareradar)
Follow @cloudflareradar on Mastodon to learn about Internet trends, as seen by the Cloudflare global network.
[@radar.cloudflare.com](https://bsky.app/profile/radar.cloudflare.com)
Follow @radar.cloudflare.com on Bluesky to learn about Internet trends, as seen by the Cloudflare global network.
[Cloudflare blog](https://blog.cloudflare.com/tag/cloudflare-radar/)
Read articles about the latest trends and updates on Cloudflare Radar.
[MCP Server](https://github.com/cloudflare/mcp-server-cloudflare/tree/main/apps/radar#cloudflare-radar-mcp-server-)
Enable any MCP client to access and explore trends and insights on Cloudflare Radar.
---
title: Overview · Cloudflare Randomness Beacon docs
description: drand (pronounced "dee-rand") is a distributed randomness beacon
daemon written in Golang. Servers running drand can be linked to each other to
produce collective, publicly verifiable, unbiased, unpredictable random values
at fixed intervals using bilinear pairings and threshold cryptography.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/randomness-beacon/
md: https://developers.cloudflare.com/randomness-beacon/index.md
---
drand (pronounced "dee-rand") is a distributed randomness beacon daemon written in Golang. Servers running drand can be linked to each other to produce collective, publicly verifiable, unbiased, unpredictable random values at fixed intervals using bilinear pairings and threshold cryptography.
drand is meant to be an Internet infrastructure level service that provides randomness to applications, similar to how NTP provides timing information and Certificate Transparency Logs provide certificate issuance information.
For the most up-to-date documentation on drand, please visit [drand.love](https://drand.love).
---
title: Overview · Cloudflare Realtime docs
description: RealtimeKit is a set of SDKs and APIs that lets you add
customizable live video and voice to web or mobile applications. It is fully
customisable and you sets up in just a few lines of code.
lastUpdated: 2025-12-01T15:18:21.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/realtime/
md: https://developers.cloudflare.com/realtime/index.md
---
Cloudflare Realtime is a comprehensive suite of products designed to help you build powerful, scalable real-time applications.
### RealtimeKit
[RealtimeKit](https://developers.cloudflare.com/realtime/realtimekit/) is a set of SDKs and APIs that lets you add customizable live video and voice to web or mobile applications. It is fully customisable and you sets up in just a few lines of code.
It sits on top of the Realtime SFU, abstracting away the heavy lifting of media routing, peer management, and other complex WebRTC operations.
### Realtime SFU
The [Realtime SFU (Selective Forwarding Unit)](https://developers.cloudflare.com/realtime/sfu/) is a powerful media server that efficiently routes video and audio. The Realtime SFU runs on [Cloudflare's global cloud network](https://www.cloudflare.com/network/) in hundreds of cities worldwide.
For developers with WebRTC expertise, the SFU can be used independently to build highly custom applications that require full control over media streams. This is recommended only for those who want to leverage Cloudflare's network with their own WebRTC logic.
### TURN Service
The [TURN service](https://developers.cloudflare.com/realtime/turn/) is a managed service that acts as a relay for WebRTC traffic. It ensures connectivity for users behind restrictive firewalls or NATs by providing a public relay point for media streams.
## Choose the right Realtime product
Use this comparison table to quickly find the right Realtime product for your needs:
| | **RealtimeKit** | **Realtime SFU** | **TURN Service** |
| - | - | - | - |
| **What is it** | High-level SDKs and APIs with pre-built UI components for video/voice integration. Built on top of Realtime SFU. | Low-level WebRTC media server (Selective Forwarding Unit) that routes audio/video/data streams between participants. | Managed relay service for WebRTC traffic that ensures connectivity through restrictive firewalls and NATs. |
| **Who is it for** | Developers who want to quickly add video/voice features without handling WebRTC complexities. | Developers with WebRTC expertise who need full control over media streams and want to build highly custom applications. | Any WebRTC application needing reliable connectivity in restrictive network environments. |
| **Effort to get started** | Low - Just a few lines of code with UI Kit and Core SDK. | High - Requires deep WebRTC knowledge. No SDK provided (unopinionated). You manage sessions, tracks, and presence protocol. Works with every WebRTC library. | Low - Automatically used by WebRTC libraries (browser WebRTC, Pion, libwebrtc). No additional code needed. |
| **WebRTC expertise required** | None - Abstracts away WebRTC complexities. | Expert - You handle all WebRTC logic yourself. | None - Used transparently by WebRTC libraries. |
| **Primitives** | Meetings, Sessions, Participants, Presets (roles), Stage, Waiting Room | Sessions (PeerConnections), Tracks (MediaStreamTracks), pub/sub model - no rooms concept | TURN allocations, relayed transport addresses, protocols (UDP/TCP/TLS) |
| **Key use cases** | Team meetings, virtual classrooms, webinars, live streaming with interactive features, social video chat | Highly custom real-time apps, unique WebRTC architectures that don't fit standard patterns, leveraging Cloudflare's network with custom logic | Ensuring connectivity for all users regardless of firewall/NAT configuration, used alongside SFU or peer-to-peer WebRTC |
| **Key features** | Pre-built UI components, automatic track management, recording, chat, polls, breakout rooms, virtual backgrounds, transcription | Unopinionated architecture, no lock-in, globally scalable, full control over media routing, programmable "switchboard" | Anycast routing to nearest location, multiple protocol options |
| **Pricing** | Pricing by minute [view details](https://workers.cloudflare.com/pricing#media) | $0.05/GB egress | Free when used with Realtime SFU, otherwise $0.05/GB egress |
| **Free tier** | None | First 1,000 GB free each month | First 1,000 GB free each month |
## Related products
**[Workers AI](https://developers.cloudflare.com/workers-ai/)**
Run machine learning models, powered by serverless GPUs, on Cloudflare’s global network.
**[Stream](https://developers.cloudflare.com/stream/)**
Cloudflare Stream lets you or your end users upload, store, encode, and deliver live and on-demand video with one API, without configuring or maintaining infrastructure.
## More resources
[Developer Discord](https://discord.cloudflare.com)
Connect with the Realtime community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[Use cases](https://developers.cloudflare.com/realtime/realtimekit/introduction#use-cases)
Learn how you can build and deploy ambitious Realtime applications to Cloudflare's global network.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Realtime.
---
title: Reference Architectures · Cloudflare Reference Architecture docs
description: No matter if you know Cloudflare well, or if you are just starting
out. These documents help you understand how our connectivity cloud is
architectured and how the services can be integrated with your own
infrastructure. Read How to use to understand how the documentation is
structured, and either navigate by type from the menu or find by solution
area.
lastUpdated: 2024-12-30T11:27:09.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/reference-architecture/
md: https://developers.cloudflare.com/reference-architecture/index.md
---

All the documents in this section are designed to help you understand how Cloudflare and its products are designed and architected. These documents describe how you can leverage our platform to create solutions based on your business needs.
No matter if you know Cloudflare well, or if you are just starting out. These documents help you understand how our connectivity cloud is architectured and how the services can be integrated with your own infrastructure. Read [How to use](https://developers.cloudflare.com/reference-architecture/how-to-use/) to understand how the documentation is structured, and either navigate by type from the menu or [find by solution](https://developers.cloudflare.com/reference-architecture/by-solution/) area.
* [How to use](https://developers.cloudflare.com/reference-architecture/how-to-use/)
* [Find by solution](https://developers.cloudflare.com/reference-architecture/by-solution/)
* [Reference Architectures](https://developers.cloudflare.com/reference-architecture/architectures/)
* [Reference Architecture Diagrams](https://developers.cloudflare.com/reference-architecture/diagrams/)
* [Design Guides](https://developers.cloudflare.com/reference-architecture/design-guides/)
* [Implementation Guides](https://developers.cloudflare.com/reference-architecture/implementation-guides/)
***
## More resources
[Cloudflare blog](https://blog.cloudflare.com/)
Read articles and announcements about the latest Cloudflare products and features.
[Learning Paths](https://developers.cloudflare.com/learning-paths/)
Module-based guidance on Cloudflare product workflows.
---
title: Overview · Cloudflare Registrar docs
description: Buy and manage your domain with Cloudflare Registrar, and add an
additional layer of security to your DNS records for free. Cloudflare
Registrar also offers redacted WHOIS information by default and will only
charge you what is paid to the registry for your domain. No markup. No
surprise fees.
lastUpdated: 2025-07-08T19:21:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/
md: https://developers.cloudflare.com/registrar/index.md
---
Buy and renew your domain at cost with Cloudflare Registrar.
Available on all plans
Buy and manage your domain with Cloudflare Registrar, and add an additional layer of security to your DNS records for free. Cloudflare Registrar also offers redacted WHOIS information by default and will only charge you what is paid to the registry for your domain. No markup. No surprise fees.
***
## Features
### Buy domains at cost
Buy and renew domains through Cloudflare Registrar at cost, without markup fees. You only pay what is charged by [registries and ICANN](https://www.cloudflare.com/products/registrar/).
[Buy domains at cost](https://developers.cloudflare.com/registrar/get-started/register-domain/)
### Renew your domain
Cloudflare Registrar enrolls your domain to auto-renew by default. Unlike other registrars, your domain will only renew at the list price set by the registry.
[Renew your domain](https://developers.cloudflare.com/registrar/account-options/renew-domains/)
### DNSSEC
Cloudflare Registrar offers one-click DNSSEC activation. DNSSEC secures DNS records with cryptographic signatures, and is free to all Cloudflare customers.
[Use DNSSEC](https://developers.cloudflare.com/registrar/get-started/enable-dnssec/)
***
## Related products
**[DNS](https://developers.cloudflare.com/dns/)**
When you use Cloudflare DNS, all DNS queries for your domain are answered by Cloudflare’s global anycast network. This network delivers performance and global availability.
---
title: Resources | Cloudflare Docs
description: Explore our resources to learn more about Cloudflare products and services
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/resources/
md: https://developers.cloudflare.com/resources/index.md
---
Content Type
Products
[Code interpreter with Workers AI](https://developers.cloudflare.com/sandbox/tutorials/workers-ai-code-interpreter/)
[Build a code interpreter using Workers AI GPT-OSS model with the official workers-ai-provider package.](https://developers.cloudflare.com/sandbox/tutorials/workers-ai-code-interpreter/)
[Add multiple sites via automation](https://developers.cloudflare.com/fundamentals/manage-domains/add-multiple-sites-automation/)
[To add multiple sites to Cloudflare at once and more efficiently, you can do so via the Cloudflare API.](https://developers.cloudflare.com/fundamentals/manage-domains/add-multiple-sites-automation/)
[Fraud detection with Ephemeral IDs](https://developers.cloudflare.com/turnstile/tutorials/fraud-detection-with-ephemeral-ids/)
[Learn how to implement fraud detection using Turnstile's Ephemeral IDs to identify and block bad actors who rotate IP addresses.](https://developers.cloudflare.com/turnstile/tutorials/fraud-detection-with-ephemeral-ids/)
[Platform Starter Kit](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/platform-templates/platform-starter-kit/)
[Deploy an AI vibe coding platform](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/platform-templates/vibesdk/)
[Deploy self-hosted VoIP services for hybrid users](https://developers.cloudflare.com/reference-architecture/diagrams/sase/deploying-self-hosted-voip-services-for-hybrid-users/)
[Learn how Cloudflare improves over traditional VPN solutions by leveraging its global network.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/deploying-self-hosted-voip-services-for-hybrid-users/)
[Understanding Email Security Deployments](https://developers.cloudflare.com/reference-architecture/architectures/email-security-deployments/)
[This reference architecture describes the key architecture of Cloudflare Email security.](https://developers.cloudflare.com/reference-architecture/architectures/email-security-deployments/)
[Implement regional private DNS servers with Gateway resolver policies](https://developers.cloudflare.com/cloudflare-one/tutorials/regional-private-dns-resolver-policies/)
[Configure Gateway resolver policies to route DNS queries to region-specific private DNS servers, enabling geo-steering for internal resources across multiple locations.](https://developers.cloudflare.com/cloudflare-one/tutorials/regional-private-dns-resolver-policies/)
[Data persistence with R2](https://developers.cloudflare.com/sandbox/tutorials/persistent-storage/)
[Mount R2 buckets as local filesystem paths to persist data across sandbox lifecycles.](https://developers.cloudflare.com/sandbox/tutorials/persistent-storage/)
[Build an Interactive ChatGPT App](https://developers.cloudflare.com/agents/guides/chatgpt-app/)
[Connect to an MCP server](https://developers.cloudflare.com/agents/guides/connect-mcp-client/)
[Run Claude Code on a Sandbox](https://developers.cloudflare.com/sandbox/tutorials/claude-code/)
[Use Claude Code to implement a task in your GitHub repository.](https://developers.cloudflare.com/sandbox/tutorials/claude-code/)
[Deploy an Express.js application on Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/deploy-an-express-app/)
[Learn how to deploy an Express.js application on Cloudflare Workers.](https://developers.cloudflare.com/workers/tutorials/deploy-an-express-app/)
[Build an AI code executor](https://developers.cloudflare.com/sandbox/tutorials/ai-code-executor/)
[Use Claude to generate Python code from natural language and execute it securely in sandboxes.](https://developers.cloudflare.com/sandbox/tutorials/ai-code-executor/)
[Automated testing pipeline](https://developers.cloudflare.com/sandbox/tutorials/automated-testing-pipeline/)
[Build a testing pipeline that clones Git repositories, installs dependencies, runs tests, and reports results.](https://developers.cloudflare.com/sandbox/tutorials/automated-testing-pipeline/)
[Analyze data with AI](https://developers.cloudflare.com/sandbox/tutorials/analyze-data-with-ai/)
[Upload CSV files, generate analysis code with Claude, and return visualizations.](https://developers.cloudflare.com/sandbox/tutorials/analyze-data-with-ai/)
[Build a code review bot](https://developers.cloudflare.com/sandbox/tutorials/code-review-bot/)
[Clone repositories, analyze code with Claude, and post review comments to GitHub PRs.](https://developers.cloudflare.com/sandbox/tutorials/code-review-bot/)
[Deploy WARP on headless Linux machines](https://developers.cloudflare.com/cloudflare-one/tutorials/warp-on-headless-linux/)
[This tutorial explains how to deploy the Cloudflare WARP client on headless Linux devices using a service token and an installation script.](https://developers.cloudflare.com/cloudflare-one/tutorials/warp-on-headless-linux/)
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Build an end to end data pipeline](https://developers.cloudflare.com/r2-sql/tutorials/end-to-end-pipeline/)
[This tutorial demonstrates how to build a complete data pipeline using Cloudflare Pipelines, R2 Data Catalog, and R2 SQL.](https://developers.cloudflare.com/r2-sql/tutorials/end-to-end-pipeline/)
[Optimize mobile viewing](https://developers.cloudflare.com/images/tutorials/optimize-mobile-viewing/)
[Lazy loading is an easy way to optimize the images on your webpages for mobile devices, with faster page load times and lower costs.](https://developers.cloudflare.com/images/tutorials/optimize-mobile-viewing/)
[Connect to a PostgreSQL database with Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/postgres/)
[This tutorial explains how to connect to a Postgres database with Cloudflare Workers. The Workers application you create in this tutorial will interact with a product database inside of Postgres.](https://developers.cloudflare.com/workers/tutorials/postgres/)
[Query D1 using Prisma ORM](https://developers.cloudflare.com/d1/tutorials/d1-and-prisma-orm/)
[This tutorial shows you how to set up and deploy a Cloudflare Worker that is accessing a D1 database from scratch.](https://developers.cloudflare.com/d1/tutorials/d1-and-prisma-orm/)
[Protect your forms](https://developers.cloudflare.com/turnstile/tutorials/login-pages/)
[This tutorial will guide you through integrating Cloudflare Turnstile to protect your web forms, such as login, signup, or contact forms.](https://developers.cloudflare.com/turnstile/tutorials/login-pages/)
[Migrate from Netlify to Workers](https://developers.cloudflare.com/workers/static-assets/migration-guides/netlify-to-workers/)
[Migrate your Netlify application to Cloudflare Workers. You should already have an existing project deployed on Netlified that you would like to host on Workers.](https://developers.cloudflare.com/workers/static-assets/migration-guides/netlify-to-workers/)
[Create and secure an AI agent wrapper using AI Gateway and Zero Trust](https://developers.cloudflare.com/cloudflare-one/tutorials/ai-wrapper-tenant-control/)
[This tutorial explains how to use Cloudflare AI Gateway and Zero Trust to create a functional and secure website wrapper for an AI agent.](https://developers.cloudflare.com/cloudflare-one/tutorials/ai-wrapper-tenant-control/)
[Enhancing security posture with SentinelOne and Cloudflare One](https://developers.cloudflare.com/reference-architecture/architectures/cloudflare-sase-with-sentinelone/)
[The integration between Cloudflare One and SentinelOne provides organizations with a comprehensive security solution. The integration works through a service-to-service posture check that identifies devices based on their serial numbers.](https://developers.cloudflare.com/reference-architecture/architectures/cloudflare-sase-with-sentinelone/)
[Migrate from Vercel to Workers](https://developers.cloudflare.com/workers/static-assets/migration-guides/vercel-to-workers/)
[Migrate your Vercel application to Cloudflare Workers. You should already have an existing project deployed on Vercel that you would like to host on Workers.](https://developers.cloudflare.com/workers/static-assets/migration-guides/vercel-to-workers/)
[Point to Pages with a custom domain](https://developers.cloudflare.com/rules/origin-rules/tutorials/point-to-pages-with-custom-domain/)
[This tutorial will instruct you how to configure an origin rule and a DNS record to point to a Pages deployment with a custom domain.](https://developers.cloudflare.com/rules/origin-rules/tutorials/point-to-pages-with-custom-domain/)
[Point to R2 bucket with a custom domain](https://developers.cloudflare.com/rules/origin-rules/tutorials/point-to-r2-bucket-with-custom-domain/)
[This tutorial will instruct you how to configure an origin rule and a DNS record to point to an R2 bucket configured with a custom domain.](https://developers.cloudflare.com/rules/origin-rules/tutorials/point-to-r2-bucket-with-custom-domain/)
[Migrating from Vercel to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-vercel/)
[In this tutorial, you will learn how to deploy your Vercel application to Cloudflare Pages.](https://developers.cloudflare.com/pages/migrations/migrating-from-vercel/)
[Using D1 Read Replication for your e-commerce website](https://developers.cloudflare.com/d1/tutorials/using-read-replication-for-e-com/)
[D1 Read Replication is a feature that allows you to replicate your D1 database to multiple regions. This is useful for your e-commerce website, as it reduces read latencies and improves read throughput.](https://developers.cloudflare.com/d1/tutorials/using-read-replication-for-e-com/)
[Tutorial - React SPA with an API](https://developers.cloudflare.com/workers/vite-plugin/tutorial/)
[Create a React SPA with an API Worker using the Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/tutorial/)
[Transform user-uploaded images before uploading to R2](https://developers.cloudflare.com/images/tutorials/optimize-user-uploaded-image/)
[Set up bindings to connect Images, R2, and Assets to your Worker](https://developers.cloudflare.com/images/tutorials/optimize-user-uploaded-image/)
[Whisper-large-v3-turbo with Cloudflare Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-workers-ai-whisper-with-chunking/)
[Learn how to transcribe large audio files using Workers AI.](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-workers-ai-whisper-with-chunking/)
[Connect to a MySQL database with Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/mysql/)
[This tutorial explains how to connect to a Cloudflare database using TCP Sockets and Hyperdrive. The Workers application you create in this tutorial will interact with a product database inside of MySQL.](https://developers.cloudflare.com/workers/tutorials/mysql/)
[AI Gateway Binding Methods](https://developers.cloudflare.com/ai-gateway/integrations/worker-binding-methods/)
[This guide provides an overview of how to use the latest Cloudflare Workers AI Gateway binding methods. You will learn how to set up an AI Gateway binding, access new methods, and integrate them into your Workers.](https://developers.cloudflare.com/ai-gateway/integrations/worker-binding-methods/)
[Conditionally enforce Turnstile](https://developers.cloudflare.com/turnstile/tutorials/conditionally-enforcing-turnstile/)
[This tutorial explains how to conditionally enforce Turnstile based on the incoming request, such as a pre-shared secret in a header or a specific IP address.](https://developers.cloudflare.com/turnstile/tutorials/conditionally-enforcing-turnstile/)
[Storing user generated content](https://developers.cloudflare.com/reference-architecture/diagrams/storage/storing-user-generated-content/)
[Store user-generated content in R2 for fast, secure, and cost-effective architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/storing-user-generated-content/)
[Programmable Platforms](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[Workers for Platforms provide secure, scalable, cost-effective infrastructure for programmable platforms with global reach.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[Change URI path and Host header](https://developers.cloudflare.com/rules/origin-rules/tutorials/change-uri-path-and-host-header/)
[This tutorial shows you how to modify both the URI path and the Host header of incoming requests using Transform Rules and Origin Rules.](https://developers.cloudflare.com/rules/origin-rules/tutorials/change-uri-path-and-host-header/)
[Set up and use a Prisma Postgres database](https://developers.cloudflare.com/workers/tutorials/using-prisma-postgres-with-workers/)
[This tutorial shows you how to set up a Cloudflare Workers project with Prisma ORM.](https://developers.cloudflare.com/workers/tutorials/using-prisma-postgres-with-workers/)
[FIPS 140 level 3 compliance with Cloudflare Application Services](https://developers.cloudflare.com/reference-architecture/diagrams/security/fips-140-3/)
[This document outlines a reference architecture for achieving Federal Information Processing Standard (FIPS) 140 Level 3 compliance using Cloudflare's Application Services.](https://developers.cloudflare.com/reference-architecture/diagrams/security/fips-140-3/)
[Llama 3.2 11B Vision Instruct model on Cloudflare Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/llama-vision-tutorial/)
[Learn how to use the Llama 3.2 11B Vision Instruct model on Cloudflare Workers AI.](https://developers.cloudflare.com/workers-ai/guides/tutorials/llama-vision-tutorial/)
[Store and Catalog AI Generated Images with R2 (Part 3)](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-store-and-catalog/)
[In the final part of the AI Image Playground series, Kristian teaches how to utilize Cloudflare's R2 object storage.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-store-and-catalog/)
[Exclude Turnstile from E2E tests](https://developers.cloudflare.com/turnstile/tutorials/excluding-turnstile-from-e2e-tests/)
[This tutorial explains how to handle Turnstile in your end-to-end (E2E) tests by using Turnstile's dedicated testing keys.](https://developers.cloudflare.com/turnstile/tutorials/excluding-turnstile-from-e2e-tests/)
[Leveraging Cloudflare for your SaaS applications](https://developers.cloudflare.com/reference-architecture/design-guides/leveraging-cloudflare-for-your-saas-applications/)
[This document provides a reference and guidance for using Cloudflare for Platforms. It is designed for SaaS application owners, engineers, or architects who want to learn how to make their application more scalable and secure.](https://developers.cloudflare.com/reference-architecture/design-guides/leveraging-cloudflare-for-your-saas-applications/)
[Protect data center networks](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-data-center-networks/)
[This document focuses on the reference architecture of using Cloudflare's Magic WAN, Magic Firewall, and Cloudflare Gateway services.](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-data-center-networks/)
[Protective DNS for governments](https://developers.cloudflare.com/reference-architecture/diagrams/sase/gateway-for-protective-dns/)
[Learn how to use Cloudflare Gateway as a Protective DNS service for governments.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/gateway-for-protective-dns/)
[Securing guest wireless networks](https://developers.cloudflare.com/reference-architecture/design-guides/securing-guest-wireless-networks/)
[This guide is designed for IT or security professionals who are looking at Cloudflare to help secure their guest wireless networks.](https://developers.cloudflare.com/reference-architecture/design-guides/securing-guest-wireless-networks/)
[Secure access to SaaS applications with SASE](https://developers.cloudflare.com/reference-architecture/diagrams/sase/secure-access-to-saas-applications-with-sase/)
[Cloudflare's SASE platform offers the ability to bring a more Zero Trust orientated approach to securing SaaS applications. Centralized policies, based on device posture, identity attributes and granular network location can be applied across one or many Saas applications.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/secure-access-to-saas-applications-with-sase/)
[Zero Trust and Virtual Desktop Infrastructure](https://developers.cloudflare.com/reference-architecture/diagrams/sase/zero-trust-and-virtual-desktop-infrastructure/)
[This document provides a reference and guidance for using Cloudflare's Zero Trust services. It offers a vast improvement over remote access to web applications with greater security.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/zero-trust-and-virtual-desktop-infrastructure/)
[Optimizing device roaming experience with geolocated IPs](https://developers.cloudflare.com/reference-architecture/diagrams/network/optimizing-roaming-experience-with-geolocated-ips/)
[Cloudflare can use private mobile networks (APNs) to connect devices roaming across multiple countries through regional Internet breakouts.](https://developers.cloudflare.com/reference-architecture/diagrams/network/optimizing-roaming-experience-with-geolocated-ips/)
[Streamlined WAF deployment across zones and applications](https://developers.cloudflare.com/reference-architecture/design-guides/streamlined-waf-deployment-across-zones-and-applications/)
[Learn how to streamline WAF deployment across different zones and applications.](https://developers.cloudflare.com/reference-architecture/design-guides/streamlined-waf-deployment-across-zones-and-applications/)
[Optimizing and securing connected transportation systems](https://developers.cloudflare.com/reference-architecture/diagrams/iot/optimizing-and-securing-connected-transportation-systems/)
[This diagram showcases Cloudflare components optimizing connected transportation systems. It illustrates how their technologies minimize latency, ensure reliability, and strengthen security for critical data flow.](https://developers.cloudflare.com/reference-architecture/diagrams/iot/optimizing-and-securing-connected-transportation-systems/)
[Designing ZTNA access policies for Cloudflare Access](https://developers.cloudflare.com/reference-architecture/design-guides/designing-ztna-access-policies/)
[This guide is for customers looking to deploy Cloudflare's ZTNA service. It provides best practices and guidelines for how to effectively build the right policies.](https://developers.cloudflare.com/reference-architecture/design-guides/designing-ztna-access-policies/)
[Build a Retrieval Augmented Generation (RAG) AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-retrieval-augmented-generation-ai/)
[Build your first AI app with Cloudflare AI. This guide uses Workers AI, Vectorize, D1, and Cloudflare Workers.](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-retrieval-augmented-generation-ai/)
[Control and data plane architectural pattern for Durable Objects](https://developers.cloudflare.com/reference-architecture/diagrams/storage/durable-object-control-data-plane-pattern/)
[Separate the control plane from the data plane of your application to achieve great performance and reliability without compromising on functionality.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/durable-object-control-data-plane-pattern/)
[Magic WAN Connector deployment options](https://developers.cloudflare.com/reference-architecture/diagrams/sase/magic-wan-connector-deployment/)
[Learn how to deploy Magic WAN Connector and evaluate your various deployment options.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/magic-wan-connector-deployment/)
[Create different resources using Pulumi and Wrangler](https://developers.cloudflare.com/pulumi/tutorial/dynamic-provider-and-wrangler/)
[Pulumi and Wrangler can be used to create different types of resources.](https://developers.cloudflare.com/pulumi/tutorial/dynamic-provider-and-wrangler/)
[Bulk import to D1 using REST API](https://developers.cloudflare.com/d1/tutorials/import-to-d1-with-rest-api/)
[This tutorial uses the REST API to import a database into D1.](https://developers.cloudflare.com/d1/tutorials/import-to-d1-with-rest-api/)
[Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[You can connect a Cloudflare Worker to get data from Google BigQuery and pass it to Workers AI, to run AI Models, powered by serverless GPUs.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[DNS filtering solution for Internet service providers](https://developers.cloudflare.com/reference-architecture/diagrams/sase/gateway-dns-for-isp/)
[Learn how to use Cloudflare Gateway as a DNS filtering solution for Internet service providers.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/gateway-dns-for-isp/)
[Bring your own IP space to Cloudflare](https://developers.cloudflare.com/reference-architecture/diagrams/network/bring-your-own-ip-space-to-cloudflare/)
[Cloudflare allows enterprises to bring their IP space to the Cloudflare network. This allows them to gain the security and performance of the platform while still appearing to the rest of the world via their own public IP space.](https://developers.cloudflare.com/reference-architecture/diagrams/network/bring-your-own-ip-space-to-cloudflare/)
[Using a zero trust framework to secure SaaS applications](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-saas/)
[Learn how to eliminate the trade-off between security and performance by using Cloudflare's global network.](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-saas/)
[Event notifications for storage](https://developers.cloudflare.com/reference-architecture/diagrams/storage/event-notifications-for-storage/)
[Use Cloudflare Workers or an external service to monitor for notifications about data changes and then handle them appropriately.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/event-notifications-for-storage/)
[Using BigQuery with Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/using-bigquery-with-workers-ai/)
[Learn how to ingest data stored outside of Cloudflare as an input to Workers AI models.](https://developers.cloudflare.com/workers-ai/guides/tutorials/using-bigquery-with-workers-ai/)
[Workers AI](https://developers.cloudflare.com/ai-gateway/integrations/aig-workers-ai-binding/)
[This guide will walk you through setting up and deploying a Workers AI project. You will use Workers, an AI Gateway binding, and a large language model (LLM) to deploy your first AI-powered application on the Cloudflare global network.](https://developers.cloudflare.com/ai-gateway/integrations/aig-workers-ai-binding/)
[Add New AI Models to your Playground (Part 2)](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux-newmodels/)
[In part 2, Kristian expands upon the existing environment built in part 1, by showing you how to integrate new AI models and introduce new parameters that allow you to customize how images are generated.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux-newmodels/)
[Build an AI Image Generator Playground (Part 1)](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux/)
[The new flux models on Workers AI are our most powerful text-to-image AI models yet. Using Workers AI, you can get access to the best models in the industry without having to worry about inference, ops, or deployment.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux/)
[How to Build an Image Generator using Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/)
[Learn how to build an image generator using Workers AI.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/)
[Use event notification to summarize PDF files on upload](https://developers.cloudflare.com/r2/tutorials/summarize-pdf/)
[Use event notification to summarize PDF files on upload. Use Workers AI to summarize the PDF and store the summary as a text file.](https://developers.cloudflare.com/r2/tutorials/summarize-pdf/)
[Extend ZTNA with external authorization and serverless computing](https://developers.cloudflare.com/reference-architecture/diagrams/sase/augment-access-with-serverless/)
[Cloudflare's ZTNA enhances access policies using external API calls and Workers for robust security. It verifies user authentication and authorization, ensuring only legitimate access to protected resources.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/augment-access-with-serverless/)
[Bot management](https://developers.cloudflare.com/reference-architecture/diagrams/bots/bot-management/)
[Cloudflare has bot management capabilities to help identify and mitigate automated traffic to protect domains from bad bots.](https://developers.cloudflare.com/reference-architecture/diagrams/bots/bot-management/)
[Magic Network Monitoring encrypt network flow data](https://developers.cloudflare.com/magic-network-monitoring/tutorials/encrypt-network-flow-data/)
[Encrypt the network flowData sent from your router to Cloudflare by routing your network traffic through a device running the WARP client.](https://developers.cloudflare.com/magic-network-monitoring/tutorials/encrypt-network-flow-data/)
[Use Cloudflare Tunnels with Kubernetes client-go plugin](https://developers.cloudflare.com/cloudflare-one/tutorials/tunnel-kubectl/)
[This tutorial explains how to use Cloudflare Tunnels with Kubernetes client-go credential plugins for authentication. By following these steps, you can securely access your Kubernetes cluster through a Cloudflare Tunnel.](https://developers.cloudflare.com/cloudflare-one/tutorials/tunnel-kubectl/)
[Build a Comments API](https://developers.cloudflare.com/d1/tutorials/build-a-comments-api/)
[In this tutorial, you will learn how to use D1 to add comments to a static blog site. You will construct a new D1 database, and build a JSON API that allows the creation and retrieval of comments.](https://developers.cloudflare.com/d1/tutorials/build-a-comments-api/)
[Build an API for your front end using Pages Functions](https://developers.cloudflare.com/pages/tutorials/build-an-api-with-pages-functions/)
[This tutorial builds a full-stack Pages application using the React framework.](https://developers.cloudflare.com/pages/tutorials/build-an-api-with-pages-functions/)
[Send SSO attributes to Access-protected origins with Workers](https://developers.cloudflare.com/cloudflare-one/tutorials/extend-sso-with-workers/)
[This tutorial will walk you through extending the single-sign-on (SSO) capabilities of Cloudflare Access with our serverless computing platform, Cloudflare Workers.](https://developers.cloudflare.com/cloudflare-one/tutorials/extend-sso-with-workers/)
[Protect public networks with Cloudflare](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-public-networks-with-cloudflare/)
[This document explains how Cloudflare Magic Transit, Magic Firewall, and Gateway work. The products offer in-line, automatic, scalable network protection for all Internet-facing networks. The architecture is designed to protect public networks across multiple clouds and on-premises.](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-public-networks-with-cloudflare/)
[Use SSE-C](https://developers.cloudflare.com/r2/examples/ssec/)
[The following tutorial shows some snippets for how to use Server-Side Encryption with Customer-Provided Keys (SSE-C) on Cloudflare R2.](https://developers.cloudflare.com/r2/examples/ssec/)
[Cloudflare Queues - Queues & Rate Limits](https://developers.cloudflare.com/queues/tutorials/handle-rate-limits/)
[Example of how to use Queues to handle rate limits of external APIs.](https://developers.cloudflare.com/queues/tutorials/handle-rate-limits/)
[Build a seat booking app with SQLite in Durable Objects](https://developers.cloudflare.com/durable-objects/tutorials/build-a-seat-booking-app/)
[This tutorial shows you how to build a seat reservation app using Durable Objects.](https://developers.cloudflare.com/durable-objects/tutorials/build-a-seat-booking-app/)
[Build an API to access D1 using a proxy Worker](https://developers.cloudflare.com/d1/tutorials/build-an-api-to-access-d1/)
[This tutorial shows how to create an API that allows you to securely run queries against a D1 database. The API can be used to customize access controls and/or limit what tables can be queried.](https://developers.cloudflare.com/d1/tutorials/build-an-api-to-access-d1/)
[Network-focused migration from VPN concentrators to Zero Trust Network Access](https://developers.cloudflare.com/reference-architecture/design-guides/network-vpn-migration/)
[The traditional approach of installing and maintaining hardware for remote access to private company networks is no longer secure or cost effective. IT teams are recognizing the cost and effort to install and maintain their own hardware can be offset with more modern, and more secure cloud hosted services.](https://developers.cloudflare.com/reference-architecture/design-guides/network-vpn-migration/)
[Integrate Turnstile, WAF, & Bot Management](https://developers.cloudflare.com/turnstile/tutorials/integrating-turnstile-waf-and-bot-management/)
[This tutorial will guide you on how to integrate Cloudflare Turnstile, Web Application Firewall (WAF), and Bot Management. This combination creates a robust defense against various threats, including automated attacks and malicious login attempts.](https://developers.cloudflare.com/turnstile/tutorials/integrating-turnstile-waf-and-bot-management/)
[On-demand Object Storage Data Migration](https://developers.cloudflare.com/reference-architecture/diagrams/storage/on-demand-object-storage-migration/)
[Use Cloudflare migration tools to migrate data between cloud object storage providers.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/on-demand-object-storage-migration/)
[Add a site](https://developers.cloudflare.com/pulumi/tutorial/add-site/)
[This tutorial uses Pulumi infrastructure as code (IaC) to familiarize yourself with the resource management lifecycle.](https://developers.cloudflare.com/pulumi/tutorial/add-site/)
[Deploy a Worker](https://developers.cloudflare.com/pulumi/tutorial/hello-world/)
[In this tutorial, you will follow step-by-step instructions to deploy a Hello World application using Cloudflare Workers and Pulumi infrastructure as code (IaC).](https://developers.cloudflare.com/pulumi/tutorial/hello-world/)
[Protect hybrid cloud networks with Cloudflare Magic Transit](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-hybrid-cloud-networks-with-cloudflare-magic-transit/)
[Cloudflare Magic Transit provides cloud-native, in-line DDoS protection, and traffic acceleration for all Internet-facing networks.](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-hybrid-cloud-networks-with-cloudflare-magic-transit/)
[Evolving to a SASE architecture with Cloudflare](https://developers.cloudflare.com/reference-architecture/architectures/sase/)
[This reference architecture explains how organizations can work towards a SASE architecture using Cloudflare.](https://developers.cloudflare.com/reference-architecture/architectures/sase/)
[Manage secrets with Pulumi ESC](https://developers.cloudflare.com/pulumi/tutorial/manage-secrets/)
[Pulumi ESC (Environments, Secrets, and Configuration) is a secure and robust secrets management solution. The tutorial will walk you through how to develop with Wrangler while following security best practices.](https://developers.cloudflare.com/pulumi/tutorial/manage-secrets/)
[Extend Cloudflare's benefits to SaaS providers' end-customers](https://developers.cloudflare.com/reference-architecture/design-guides/extending-cloudflares-benefits-to-saas-providers-end-customers/)
[Learn how to use Cloudflare to extend performance, security, and data localization to your end users.](https://developers.cloudflare.com/reference-architecture/design-guides/extending-cloudflares-benefits-to-saas-providers-end-customers/)
[Cloudflare Queues - Queues & Browser Rendering](https://developers.cloudflare.com/queues/tutorials/web-crawler-with-browser-rendering/)
[Example of how to use Queues and Browser Rendering to power a web crawler.](https://developers.cloudflare.com/queues/tutorials/web-crawler-with-browser-rendering/)
[Create your first AI Gateway using Workers AI](https://developers.cloudflare.com/ai-gateway/tutorials/create-first-aig-workers/)
[This tutorial guides you through creating your first AI Gateway using Workers AI on the Cloudflare dashboard.](https://developers.cloudflare.com/ai-gateway/tutorials/create-first-aig-workers/)
[Explore Workers AI Models Using a Jupyter Notebook](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-workers-ai-models-using-a-jupyter-notebook/)
[This Jupyter notebook explores various models (including Whisper, Distilled BERT, LLaVA, and Meta Llama 3) using Python and the requests library.](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-workers-ai-models-using-a-jupyter-notebook/)
[Use R2 as static asset storage with Cloudflare Pages](https://developers.cloudflare.com/pages/tutorials/use-r2-as-static-asset-storage-for-pages/)
[This tutorial will teach you how to use R2 as a static asset storage bucket for your Pages app.](https://developers.cloudflare.com/pages/tutorials/use-r2-as-static-asset-storage-for-pages/)
[Protect ISP and telecommunications networks from DDoS attacks](https://developers.cloudflare.com/reference-architecture/diagrams/network/protecting-sp-networks-from-ddos/)
[Learn how Internet service providers (ISPs) and telecommunications companies (such as T-Mobile or British Telecom) can protect themselves from DDoS attacks.](https://developers.cloudflare.com/reference-architecture/diagrams/network/protecting-sp-networks-from-ddos/)
[Use Pages as an origin for Load Balancing](https://developers.cloudflare.com/load-balancing/pools/cloudflare-pages-origin/)
[This tutorial is intended as an introductory example of how you can leverage Cloudflare's global traffic management.](https://developers.cloudflare.com/load-balancing/pools/cloudflare-pages-origin/)
[Cloudflare Security Architecture](https://developers.cloudflare.com/reference-architecture/architectures/security/)
[This document provides insight into how this network and platform are architected from a security perspective, how they are operated, and what services are available for businesses to address their own security challenges.](https://developers.cloudflare.com/reference-architecture/architectures/security/)
[Reference Architecture using Cloudflare SASE with Microsoft](https://developers.cloudflare.com/reference-architecture/architectures/cloudflare-sase-with-microsoft/)
[This reference architecture explains how Microsoft and Cloudflare can be integrated together. By leveraging Cloudflare's secure network access, risky user isolation, and application and data visibility, organizations can consolidate management.](https://developers.cloudflare.com/reference-architecture/architectures/cloudflare-sase-with-microsoft/)
[Optimizing image delivery with Cloudflare image resizing and R2](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/optimizing-image-delivery-with-cloudflare-image-resizing-and-r2/)
[Learn how to get a scalable, high-performance solution to optimizing image delivery.](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/optimizing-image-delivery-with-cloudflare-image-resizing-and-r2/)
[Create a fine-tuned OpenAI model with R2](https://developers.cloudflare.com/workers/tutorials/create-finetuned-chatgpt-ai-models-with-r2/)
[In this tutorial, you will use the OpenAI API and Cloudflare R2 to create a fine-tuned model.](https://developers.cloudflare.com/workers/tutorials/create-finetuned-chatgpt-ai-models-with-r2/)
[Build a Slackbot](https://developers.cloudflare.com/workers/tutorials/build-a-slackbot/)
[Learn how to build a Slackbot with Hono and TypeScript in Cloudflare Workerss](https://developers.cloudflare.com/workers/tutorials/build-a-slackbot/)
[Use Workers KV directly from Rust](https://developers.cloudflare.com/workers/tutorials/workers-kv-from-rust/)
[This tutorial will teach you how to read and write to KV directly from Rust using workers-rs. You will use Workers KV from Rust to build an app to store and retrieve cities.](https://developers.cloudflare.com/workers/tutorials/workers-kv-from-rust/)
[Build a todo list Jamstack application](https://developers.cloudflare.com/workers/tutorials/build-a-jamstack-app/)
[This tutorial explains how to build a todo list application using HTML, CSS, and JavaScript.](https://developers.cloudflare.com/workers/tutorials/build-a-jamstack-app/)
[Localize a website with HTMLRewriter](https://developers.cloudflare.com/pages/tutorials/localize-a-website/)
[This tutorial uses the HTMLRewriter functionality in the Cloudflare Workers platform to overlay an i18n layer, automatically translating the site based on the user’s language.](https://developers.cloudflare.com/pages/tutorials/localize-a-website/)
[Send Emails With Postmark](https://developers.cloudflare.com/workers/tutorials/send-emails-with-postmark/)
[This tutorial explains how to send transactional emails from Workers using Postmark.](https://developers.cloudflare.com/workers/tutorials/send-emails-with-postmark/)
[Securing data at rest](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-at-rest/)
[Learn how Cloudflare's API-driven Cloud Access Security Broker (CASB) works and secures data at rest.](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-at-rest/)
[Reference Architecture Diagram: Securing data in transit](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-in-transit/)
[Data in transit is often considered vulnerable to interception or tampering during transmission. Data Loss Prevention (DLP) technologies can be used to inspect the contents of network traffic and block sensitive data from going to a risky destination.](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-in-transit/)
[Securing data in use](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-in-use/)
[Learn how Cloudflare's Remote Browser Isolation (RBI) works and secures data in use.](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-in-use/)
[Multi-vendor AI observability and control](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-multivendor-observability-control/)
[By shifting features such as rate limiting, caching, and error handling to the proxy layer, organizations can apply unified configurations across services and inference service providers.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-multivendor-observability-control/)
[Composable AI architecture](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[The architecture diagram illustrates how AI applications can be built end-to-end on Cloudflare, or single services can be integrated with external infrastructure and services.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[A/B-testing using Workers](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/a-b-testing-using-workers/)
[Cloudflare's low-latency, fully serverless compute platform, Workers offers powerful capabilities to enable A/B testing using a server-side implementation.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/a-b-testing-using-workers/)
[Serverless global APIs](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[An example architecture of a serverless API on Cloudflare and aims to illustrate how different compute and data products could interact with each other.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[Send Emails With Resend](https://developers.cloudflare.com/workers/tutorials/send-emails-with-resend/)
[This tutorial explains how to send emails from Cloudflare Workers using Resend.](https://developers.cloudflare.com/workers/tutorials/send-emails-with-resend/)
[Building zero trust architecture into your startup](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-startups/)
[Cloudflare Zero Trust is a simple, (sometimes free!) way for startups to develop a comprehensive Zero Trust strategy. This guide explains how to use Cloudflare to establish the foundation for a Zero Trust architecture.](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-startups/)
[Protect an R2 Bucket with Cloudflare Access](https://developers.cloudflare.com/r2/tutorials/cloudflare-access/)
[You can secure access to R2 buckets using Cloudflare Access, which allows you to only allow specific users, groups or applications within your organization to access objects within a bucket.](https://developers.cloudflare.com/r2/tutorials/cloudflare-access/)
[Serverless ETL pipelines](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-etl/)
[Cloudflare enables fully serverless ETL pipelines, significantly reducing complexity, accelerating time to production, and lowering overall costs.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-etl/)
[Egress-free object storage in multi-cloud setups](https://developers.cloudflare.com/reference-architecture/diagrams/storage/egress-free-storage-multi-cloud/)
[Learn how to use R2 to get egress-free object storage in multi-cloud setups.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/egress-free-storage-multi-cloud/)
[Access to private apps without having to deploy client agents](https://developers.cloudflare.com/reference-architecture/diagrams/sase/sase-clientless-access-private-dns/)
[Learn how to provide access to private apps without having to deploy client agents.](https://developers.cloudflare.com/reference-architecture/diagrams/sase/sase-clientless-access-private-dns/)
[Log and store upload events in R2 with event notifications](https://developers.cloudflare.com/r2/tutorials/upload-logs-event-notifications/)
[This example provides a step-by-step guide on using event notifications to capture and store R2 upload logs in a separate bucket.](https://developers.cloudflare.com/r2/tutorials/upload-logs-event-notifications/)
[Fine Tune Models With AutoTrain from HuggingFace](https://developers.cloudflare.com/workers-ai/guides/tutorials/fine-tune-models-with-autotrain/)
[Fine-tuning AI models with LoRA adapters on Workers AI allows adding custom training data, like for LLM finetuning.](https://developers.cloudflare.com/workers-ai/guides/tutorials/fine-tune-models-with-autotrain/)
[Build a Staff Directory Application](https://developers.cloudflare.com/d1/tutorials/build-a-staff-directory-app/)
[Build a staff directory using D1. Users access employee info; admins add new employees within the app.](https://developers.cloudflare.com/d1/tutorials/build-a-staff-directory-app/)
[Use virtual networks to change user egress IPs](https://developers.cloudflare.com/cloudflare-one/tutorials/user-selectable-egress-ips/)
[This tutorial gives administrators an easy way to allow their users to change their egress IP address between any of your assigned dedicated egress IP addresses.](https://developers.cloudflare.com/cloudflare-one/tutorials/user-selectable-egress-ips/)
[Content-based asset creation](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-asset-creation/)
[AI systems combine text-generation and text-to-image models to create visual content from text. They generate prompts, moderate content, and produce images for various applications.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-asset-creation/)
[Retrieval Augmented Generation (RAG)](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
[RAG combines retrieval with generative models for better text. It uses external knowledge to create factual, relevant responses, improving coherence and accuracy in NLP tasks like chatbots.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
[Automatic captioning for video uploads](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-video-caption/)
[By integrating automatic speech recognition technology into video platforms, content creators, publishers, and distributors can reach a broader audience, including individuals with hearing impairments or those who prefer to consume content in different languages.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-video-caption/)
[Serverless image content management](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
[Leverage various components of Cloudflare's ecosystem to construct a scalable image management solution](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
[Access and secure a MySQL database using Cloudflare Tunnel and network policies](https://developers.cloudflare.com/cloudflare-one/tutorials/mysql-network-policy/)
[Using Cloudflare Tunnel's private networks, users can connect to arbitrary non-browser based TCP/UDP applications, like databases. You can set up network policies that implement zero trust controls to define who and what can access those applications using the WARP client.](https://developers.cloudflare.com/cloudflare-one/tutorials/mysql-network-policy/)
[Access a web application via its private hostname without WARP](https://developers.cloudflare.com/cloudflare-one/tutorials/clientless-access-private-dns/)
[With Cloudflare Browser Isolation and resolver policies, users can connect to private web-based applications via their private hostnames.](https://developers.cloudflare.com/cloudflare-one/tutorials/clientless-access-private-dns/)
[Load Balancing Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/load-balancing/)
[This reference architecture is for organizations looking to deploy both global and local traffic management load balancing solutions. It is designed for IT, web hosting, and network professionals with some responsibility over or familiarity with their organization's existing infrastructure.](https://developers.cloudflare.com/reference-architecture/architectures/load-balancing/)
[Explore Code Generation Using DeepSeek Coder Models](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-code-generation-using-deepseek-coder-models/)
[Explore how you can use AI models to generate code and work more efficiently.](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-code-generation-using-deepseek-coder-models/)
[Choose the Right Text Generation Model](https://developers.cloudflare.com/workers-ai/guides/tutorials/how-to-choose-the-right-text-generation-model/)
[There's a wide range of text generation models available through Workers AI. In an effort to aid you in your journey of finding the right model, this notebook will help you get to know your options in a speed dating type of scenario.](https://developers.cloudflare.com/workers-ai/guides/tutorials/how-to-choose-the-right-text-generation-model/)
[Use Microsoft Entra ID Conditional Access policies in Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/tutorials/entra-id-conditional-access/)
[With Conditional Access in Microsoft Entra ID, administrators can enforce policies on applications and users directly in EntraID.](https://developers.cloudflare.com/cloudflare-one/tutorials/entra-id-conditional-access/)
[Securely deliver applications with Cloudflare](https://developers.cloudflare.com/reference-architecture/design-guides/secure-application-delivery/)
[Cloudflare provides a complete suite of services around application performance, security, reliability, development, and Zero Trust.](https://developers.cloudflare.com/reference-architecture/design-guides/secure-application-delivery/)
[Protect access to Microsoft 365 with dedicated egress IPs](https://developers.cloudflare.com/cloudflare-one/tutorials/m365-dedicated-egress-ips/)
[This tutorial covers how to secure access to your Microsoft 365 applications with Cloudflare Gateway dedicated egress IPs.](https://developers.cloudflare.com/cloudflare-one/tutorials/m365-dedicated-egress-ips/)
[Monitor Cloudflare Tunnel with Grafana](https://developers.cloudflare.com/cloudflare-one/tutorials/grafana/)
[This tutorial covers how to create the metrics endpoint and set up the Prometheus server.](https://developers.cloudflare.com/cloudflare-one/tutorials/grafana/)
[Use Cloudflare R2 as a Zero Trust log destination](https://developers.cloudflare.com/cloudflare-one/tutorials/r2-logs/)
[This tutorial covers how to build a Cloudflare R2 bucket to store Zero Trust logs. It also shows how to connect the bucket to the Zero Trust Logpush service.](https://developers.cloudflare.com/cloudflare-one/tutorials/r2-logs/)
[Create custom headers for Cloudflare Access-protected origins with Workers](https://developers.cloudflare.com/cloudflare-one/tutorials/access-workers/)
[This tutorial covers how to use a Cloudflare Worker to add custom headers to traffic. The headers will be sent to origin services protected by Cloudflare Access.](https://developers.cloudflare.com/cloudflare-one/tutorials/access-workers/)
[Create a serverless, globally distributed time-series API with Timescale](https://developers.cloudflare.com/hyperdrive/tutorials/serverless-timeseries-api-with-timescale/)
[In this tutorial, you will learn to build an API on Workers which will ingest and query time-series data stored in Timescale.](https://developers.cloudflare.com/hyperdrive/tutorials/serverless-timeseries-api-with-timescale/)
[Protect access to Amazon S3 buckets with Cloudflare Zero Trust](https://developers.cloudflare.com/cloudflare-one/tutorials/s3-buckets/)
[This tutorial demonstrates how to secure access to Amazon S3 buckets with Cloudflare Zero Trust so that data in these buckets is not publicly exposed on the Internet.](https://developers.cloudflare.com/cloudflare-one/tutorials/s3-buckets/)
[Deploy a Browser Rendering Worker with Durable Objects](https://developers.cloudflare.com/browser-rendering/workers-bindings/browser-rendering-with-do/)
[Use the Browser Rendering API along with Durable Objects to take screenshots from web pages and store them in R2.](https://developers.cloudflare.com/browser-rendering/workers-bindings/browser-rendering-with-do/)
[GitHub SMS notifications using Twilio](https://developers.cloudflare.com/workers/tutorials/github-sms-notifications-using-twilio/)
[This tutorial shows you how to build an SMS notification system on Workers to receive updates on a GitHub repository. Your Worker will send you a text update using Twilio when there is new activity on your repository.](https://developers.cloudflare.com/workers/tutorials/github-sms-notifications-using-twilio/)
[Deploy a Worker that connects to OpenAI via AI Gateway](https://developers.cloudflare.com/ai-gateway/tutorials/deploy-aig-worker/)
[Learn how to deploy a Worker that makes calls to OpenAI through AI Gateway](https://developers.cloudflare.com/ai-gateway/tutorials/deploy-aig-worker/)
[Deploy a real-time chat application](https://developers.cloudflare.com/workers/tutorials/deploy-a-realtime-chat-app/)
[This tutorial shows how to deploy a serverless, real-time chat application. The chat application uses a Durable Object to control each chat room.](https://developers.cloudflare.com/workers/tutorials/deploy-a-realtime-chat-app/)
[Multi-vendor Application Security and Performance Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/multi-vendor/)
[This reference architecture describes how a multi-vendor approach for application security and performance can be accomplished.](https://developers.cloudflare.com/reference-architecture/architectures/multi-vendor/)
[Build a QR code generator](https://developers.cloudflare.com/workers/tutorials/build-a-qr-code-generator/)
[This tutorial shows you how to build and publish a Worker application that generates QR codes. The final version of the codebase is available on GitHub.](https://developers.cloudflare.com/workers/tutorials/build-a-qr-code-generator/)
[Securely access and upload assets with Cloudflare R2](https://developers.cloudflare.com/workers/tutorials/upload-assets-with-r2/)
[This tutorial explains how to create a TypeScript-based Cloudflare Workers project that can securely access files from and upload files to a CloudFlare R2 bucket.](https://developers.cloudflare.com/workers/tutorials/upload-assets-with-r2/)
[OpenAI GPT function calling with JavaScript and Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/openai-function-calls-workers/)
[Build a project that leverages OpenAI's function calling feature, available in OpenAI's latest Chat Completions API models.](https://developers.cloudflare.com/workers/tutorials/openai-function-calls-workers/)
[Handle form submissions with Airtable](https://developers.cloudflare.com/workers/tutorials/handle-form-submissions-with-airtable/)
[Use Cloudflare Workers and Airtable to persist form submissions from a front-end user interface. Workers will handle incoming form submissions and use Airtables REST API to asynchronously persist the data in an Airtable base.](https://developers.cloudflare.com/workers/tutorials/handle-form-submissions-with-airtable/)
[Validate the Access token with FastAPI](https://developers.cloudflare.com/cloudflare-one/tutorials/fastapi/)
[This tutorial covers how to validate that the Access JWT is on requests made to FastAPI apps. The code is written in Python.](https://developers.cloudflare.com/cloudflare-one/tutorials/fastapi/)
[Deploy a static WordPress site](https://developers.cloudflare.com/pages/how-to/deploy-a-wordpress-site/)
[Learn how to deploy a static WordPress site using Cloudflare Pages.](https://developers.cloudflare.com/pages/how-to/deploy-a-wordpress-site/)
[Connect to and query your Turso database using Workers](https://developers.cloudflare.com/workers/tutorials/connect-to-turso-using-workers/)
[This tutorial will guide you on how to build globally distributed applications with Cloudflare Workers, and Turso, an edge-hosted distributed database based on libSQL.](https://developers.cloudflare.com/workers/tutorials/connect-to-turso-using-workers/)
[Generate YouTube thumbnails with Workers and Cloudflare Image Resizing](https://developers.cloudflare.com/workers/tutorials/generate-youtube-thumbnails-with-workers-and-images/)
[This tutorial explains how to programmatically generate a custom YouTube thumbnail using Cloudflare Workers. You may want to customize the thumbnail's design, call-to-actions and images used to encourage more viewers to watch your video.](https://developers.cloudflare.com/workers/tutorials/generate-youtube-thumbnails-with-workers-and-images/)
[Mastodon](https://developers.cloudflare.com/r2/tutorials/mastodon/)
[This guide explains how to configure R2 to be the object storage for a self hosted Mastodon instance. You can set up a self-hosted instance in multiple ways.](https://developers.cloudflare.com/r2/tutorials/mastodon/)
[Isolate risky Entra ID users](https://developers.cloudflare.com/cloudflare-one/tutorials/entra-id-risky-users/)
[Microsoft Entra ID (formerly Azure Active Directory) calculates a user's risk level based on the probability that their account has been compromised. With Cloudflare Zero Trust, you can synchronize the Entra ID risky users list with Cloudflare Access and apply more stringent Zero Trust policies to users at higher risk.](https://developers.cloudflare.com/cloudflare-one/tutorials/entra-id-risky-users/)
[GraphQL Analytics](https://developers.cloudflare.com/magic-network-monitoring/tutorials/graphql-analytics/)
[Use the GraphQL Analytics API to retrieve Magic Network Monitoring flow data.](https://developers.cloudflare.com/magic-network-monitoring/tutorials/graphql-analytics/)
[Content Delivery Network (CDN) Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/cdn/)
[This reference architecture discusses the traditional challenges customers face with web applications, how the Cloudflare CDN resolves these challenges, and CDN architecture and design.](https://developers.cloudflare.com/reference-architecture/architectures/cdn/)
[Magic Transit Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/magic-transit/)
[This reference architecture describes the key architecture, functionalities, and network deployment options of Cloudflare Magic Transit.](https://developers.cloudflare.com/reference-architecture/architectures/magic-transit/)
[Build a blog using Nuxt.js and Sanity.io on Cloudflare Pages](https://developers.cloudflare.com/pages/tutorials/build-a-blog-using-nuxt-and-sanity/)
[Build a blog application using Nuxt.js and Sanity.io and deploy it on Cloudflare Pages.](https://developers.cloudflare.com/pages/tutorials/build-a-blog-using-nuxt-and-sanity/)
[Create a HTML form](https://developers.cloudflare.com/pages/tutorials/forms/)
[This tutorial will briefly touch upon the basics of HTML forms. This tutorial will make heavy use of Cloudflare Pages and its Workers integration.](https://developers.cloudflare.com/pages/tutorials/forms/)
[Migrating from Netlify to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-netlify/)
[Learn how to migrate from Netlify to Cloudflare. This guide includes instructions for migrating redirects and headers.](https://developers.cloudflare.com/pages/migrations/migrating-from-netlify/)
[Connect through Cloudflare Access using kubectl](https://developers.cloudflare.com/cloudflare-one/tutorials/kubectl/)
[Connecting to Cloudflare's network using kubectl. Create a Zero Trust policy for your machine. Create an outbound-only connection between your machine and Cloudflared's network.](https://developers.cloudflare.com/cloudflare-one/tutorials/kubectl/)
[Postman](https://developers.cloudflare.com/r2/tutorials/postman/)
[Learn how to configure Postman to interact with R2.](https://developers.cloudflare.com/r2/tutorials/postman/)
[GraphQL Analytics](https://developers.cloudflare.com/cloudflare-one/tutorials/graphql-analytics/)
[Use the GraphQL Analytics API to review data for Magic Firewall network traffic related to rules matching your traffic.](https://developers.cloudflare.com/cloudflare-one/tutorials/graphql-analytics/)
[GraphQL Analytics](https://developers.cloudflare.com/magic-firewall/tutorials/graphql-analytics/)
[Use the GraphQL Analytics API to review data for Magic Firewall network traffic related to rules matching your traffic.](https://developers.cloudflare.com/magic-firewall/tutorials/graphql-analytics/)
[Add a React form with Formspree](https://developers.cloudflare.com/pages/tutorials/add-a-react-form-with-formspree/)
[Learn how to add a React form with Formspree, a back-end service that handles form processing and storage.](https://developers.cloudflare.com/pages/tutorials/add-a-react-form-with-formspree/)
[Add an HTML form with Formspree](https://developers.cloudflare.com/pages/tutorials/add-an-html-form-with-formspree/)
[Learn how to add an HTML form with Formspree, a back-end service that handles form processing and storage.](https://developers.cloudflare.com/pages/tutorials/add-an-html-form-with-formspree/)
[Integrate Microsoft MCAS with Cloudflare Zero Trust](https://developers.cloudflare.com/cloudflare-one/tutorials/integrate-microsoft-mcas-teams/)
[With an MCAS API call, you can manage a URL category that contains the blocked URLs. Use the output to create a Hostname List that can be used by Gateway HTTP policies to block them.](https://developers.cloudflare.com/cloudflare-one/tutorials/integrate-microsoft-mcas-teams/)
[Migrating a Jekyll-based site from GitHub Pages](https://developers.cloudflare.com/pages/migrations/migrating-jekyll-from-github-pages/)
[Learn how to migrate a Jekyll-based site from GitHub Pages to Cloudflare Pages.](https://developers.cloudflare.com/pages/migrations/migrating-jekyll-from-github-pages/)
[Connect through Cloudflare Access using a CLI](https://developers.cloudflare.com/cloudflare-one/tutorials/cli/)
[Cloudflare's cloudflared command-line tool allows you to interact with endpoints protected by Cloudflare Access.](https://developers.cloudflare.com/cloudflare-one/tutorials/cli/)
[MongoDB SSH](https://developers.cloudflare.com/cloudflare-one/tutorials/mongodb-tunnel/)
[You can build Zero Trust rules to secure connections to MongoDB deployments using Cloudflare Access and Cloudflared Tunnel.](https://developers.cloudflare.com/cloudflare-one/tutorials/mongodb-tunnel/)
[Zero Trust GitLab SSH & HTTP](https://developers.cloudflare.com/cloudflare-one/tutorials/gitlab/)
[Learn how to add Zero Trust rules to a self-hosted instance of GitLab. This tutorial walks you through deploying GitLab in DigitalOcean.](https://developers.cloudflare.com/cloudflare-one/tutorials/gitlab/)
[Require U2F with Okta](https://developers.cloudflare.com/cloudflare-one/tutorials/okta-u2f/)
[This tutorial covers how to Integrate Cloudflare Access with Okta. It also covers the steps to set up Cloudflare Access and integrate Okta with Zero Trust.](https://developers.cloudflare.com/cloudflare-one/tutorials/okta-u2f/)
[Migrating from Firebase](https://developers.cloudflare.com/pages/migrations/migrating-from-firebase/)
[This tutorial explains how to migrate an existing Firebase application to Cloudflare Pages.](https://developers.cloudflare.com/pages/migrations/migrating-from-firebase/)
[Certificate signing requests (CSRs) — Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/custom-certificates/certificate-signing-requests/)
[Cloudflare for SaaS allows you to generate a Certificate Signing Request (CSR) A CSR contains information about your domain, common name, and Subject Alternative Names.](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/custom-certificates/certificate-signing-requests/)
[Migrating from Workers Sites to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-workers/)
[Learn how to migrate from Workers Sites to Cloudflare Pages.](https://developers.cloudflare.com/pages/migrations/migrating-from-workers/)
[Get started](https://developers.cloudflare.com/version-management/get-started/)
```
Learn how to enable Version Management in the Cloudflare dashboard.
```
[DNS over Discord](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-over-discord/)
[1.1. 1.1 works from a Discord server. Invite the bot to your Discord server to start using DNS over Discord. Or, add it to your account to use it anywhere in Discord.](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-over-discord/)
[DNS in Google Sheets](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-in-google-sheets/)
[Cloudflare 1.1.1 works directly inside Google Sheets. To get started, create a Google Function with the following code.](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-in-google-sheets/)
[DNS over Tor](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-over-tor/)
[If you do not want to disclose your IP address to the resolver, you can use our Tor onion service. Resolving DNS queries through the Tor network guarantees a significantly higher level of anonymity than making the requests directly.](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-over-tor/)
[Datadog](https://developers.cloudflare.com/analytics/analytics-integrations/datadog/)
[This tutorial explains how to analyze Cloudflare metrics using the Cloudflare Integration tile for Datadog](https://developers.cloudflare.com/analytics/analytics-integrations/datadog/)
[Graylog](https://developers.cloudflare.com/analytics/analytics-integrations/graylog/)
[This tutorial explains how to analyze Cloudflare Logs using Graylog. The Graylog integration is available on GitHub.](https://developers.cloudflare.com/analytics/analytics-integrations/graylog/)
[New Relic](https://developers.cloudflare.com/analytics/analytics-integrations/new-relic/)
[This tutorial explains how to analyze Cloudflare metrics using the New Relic One Cloudflare Quickstart.](https://developers.cloudflare.com/analytics/analytics-integrations/new-relic/)
[Splunk](https://developers.cloudflare.com/analytics/analytics-integrations/splunk/)
[This tutorial explains how to analyze Cloudflare Logs using the Cloudflare App for Splunk.](https://developers.cloudflare.com/analytics/analytics-integrations/splunk/)
[Activate the Cloudflare WordPress plugin](https://developers.cloudflare.com/automatic-platform-optimization/get-started/activate-cf-wp-plugin/)
[The easiest way to begin using APO is directly from Cloudflare’s WordPress plugin. Before you can use APO, you must first install and activate the plugin and then activate APO.](https://developers.cloudflare.com/automatic-platform-optimization/get-started/activate-cf-wp-plugin/)
[Use BYOIP with CDN and Spectrum](https://developers.cloudflare.com/byoip/service-bindings/cdn-and-spectrum/)
[Cloudflare allows users to use their Cloudflare prefix to route traffic to a different service. Service bindings must be created on the parent account of the prefix.](https://developers.cloudflare.com/byoip/service-bindings/cdn-and-spectrum/)
[Use BYOIP with Magic Transit and CDN](https://developers.cloudflare.com/byoip/service-bindings/magic-transit-with-cdn/)
[Service bindings allow BYOIP customers to selectively route traffic on a per-IP address basis to the CDN pipeline. It is important to note that traffic routed to the CDN pipeline is protected at Layers 3 and 4 by the inherent DDoS protection capabilities.](https://developers.cloudflare.com/byoip/service-bindings/magic-transit-with-cdn/)
[DNSSEC migration tutorial](https://developers.cloudflare.com/dns/dnssec/dnssec-active-migration/)
[Follow this tutorial to migrate an existing DNS zone to Cloudflare without having to disable DNSSEC.](https://developers.cloudflare.com/dns/dnssec/dnssec-active-migration/)
[Onboard a domain](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/)
[Learn how to connect the domain to Cloudflare, even if you purchased your domain name from another provider.](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/)
[Change your domain version](https://developers.cloudflare.com/fundamentals/manage-domains/domain-version/)
[Version Management allows you to safely test, deploy, and roll back changes to your zone configurations. By default, Version Management is not enabled on a zone.](https://developers.cloudflare.com/fundamentals/manage-domains/domain-version/)
[Minimize downtime](https://developers.cloudflare.com/fundamentals/performance/minimize-downtime/)
[Learn how to minimize downtime while onboarding your domain onto Cloudflare.](https://developers.cloudflare.com/fundamentals/performance/minimize-downtime/)
[Load shedding](https://developers.cloudflare.com/load-balancing/additional-options/load-shedding/)
[Use load shedding to prevent an at-risk endpoint from becoming unhealthy and starting the failover process.](https://developers.cloudflare.com/load-balancing/additional-options/load-shedding/)
[Perform planned maintenance](https://developers.cloudflare.com/load-balancing/additional-options/planned-maintenance/)
[When you change application settings or add new assets, you will likely want to make these changes on one endpoint at a time. Going endpoint by endpoint reduces the risk of changes and ensures a more consistent user experience.](https://developers.cloudflare.com/load-balancing/additional-options/planned-maintenance/)
[Kentik](https://developers.cloudflare.com/magic-transit/partners/kentik/)
[Kentik is a network observability company that helps detect attacks on your network and triggers Cloudflare's Magic Transit to begin advertisement. The example scenario includes two mitigations, one which pulls the advertisement from the router and a second mitigation that makes an API call to Cloudflare.](https://developers.cloudflare.com/magic-transit/partners/kentik/)
[Use WARP as an on-ramp](https://developers.cloudflare.com/magic-wan/zero-trust/warp/)
[Use WARP as an on-ramp to Magic WAN and route traffic from user devices with WARP installed to any network connected with Cloudflare Tunnel or Magic IP-layer tunnels (anycast GRE, IPsec, or CNI).](https://developers.cloudflare.com/magic-wan/zero-trust/warp/)
[Transfer your domain to Cloudflare](https://developers.cloudflare.com/registrar/get-started/transfer-domain-to-cloudflare/)
[This page contains generic instructions on how to transfer your domain to Cloudflare.](https://developers.cloudflare.com/registrar/get-started/transfer-domain-to-cloudflare/)
[When to use Snippets vs Workers](https://developers.cloudflare.com/rules/snippets/when-to-use/)
[This guide helps you determine when to use Snippets or Workers on Cloudflare's global network.](https://developers.cloudflare.com/rules/snippets/when-to-use/)
[Workers integration](https://developers.cloudflare.com/secrets-store/integrations/workers/)
[Cloudflare Secrets Store is a secure, centralized location in which account-level secrets are stored and managed. The secrets are securely encrypted and stored across all Cloudflare data centers.](https://developers.cloudflare.com/secrets-store/integrations/workers/)
[Configure your mobile app or IoT device](https://developers.cloudflare.com/ssl/client-certificates/configure-your-mobile-app-or-iot-device/)
[This tutorial demonstrates how to configure your Internet-of-things (IoT) device and mobile application to use client certificates with API Shield.](https://developers.cloudflare.com/ssl/client-certificates/configure-your-mobile-app-or-iot-device/)
[Import Cloudflare resources](https://developers.cloudflare.com/terraform/advanced-topics/import-cloudflare-resources/)
[The Cloudflare Terraform tool is available in the Terraform ME repository. To use it, you must first install the Terraform app on your Mac or Linux system. You must then import Cloudflare resources individually by providing their IDs and names.](https://developers.cloudflare.com/terraform/advanced-topics/import-cloudflare-resources/)
[Add exceptions with Page Rules](https://developers.cloudflare.com/terraform/tutorial/add-page-rules/)
[Page Rules let you override zone settings for specific URL patterns. Redirects old URLs with a 301 permanent redirect.](https://developers.cloudflare.com/terraform/tutorial/add-page-rules/)
[Configure HTTPS settings](https://developers.cloudflare.com/terraform/tutorial/configure-https-settings/)
[This tutorial shows how to enable TLS 1.3, Automatic HTTPS Rewrites, and Strict SSL mode using the updated v5 provider.](https://developers.cloudflare.com/terraform/tutorial/configure-https-settings/)
[Introduction to Terraform init](https://developers.cloudflare.com/terraform/tutorial/initialize-terraform/)
[This tutorial shows you how to get started with Terraform. You will create a DNS record pointing www.example.com to a web server at 203.0.113.10.](https://developers.cloudflare.com/terraform/tutorial/initialize-terraform/)
[Revert configuration](https://developers.cloudflare.com/terraform/tutorial/revert-configuration/)
[Sometimes, you may have to roll back configuration changes. To revert your configuration, check out the desired branch and ask Terraform to move your Cloudflare settings back in time.](https://developers.cloudflare.com/terraform/tutorial/revert-configuration/)
[Track your history](https://developers.cloudflare.com/terraform/tutorial/track-history/)
[Learn how to track history with Cloudflare Terraform.](https://developers.cloudflare.com/terraform/tutorial/track-history/)
[Improve performance and reliability](https://developers.cloudflare.com/terraform/tutorial/use-load-balancing/)
[Learn how to use Terraform with Cloudflare Load Balancing product to fail traffic over as needed.](https://developers.cloudflare.com/terraform/tutorial/use-load-balancing/)
[Test a waiting room](https://developers.cloudflare.com/waiting-room/additional-options/test-waiting-room/)
[Follow this tutorial to test your waiting room behavior in response to load. To accurately simulate traffic, run your test script or planner for a period of time longer than a minute, ideally more than 2-3 minutes.](https://developers.cloudflare.com/waiting-room/additional-options/test-waiting-room/)
[Connect to 1.1.1.1 using DoH clients](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/dns-over-https-client/)
[Learn how to connect to Cloudflare's 1.1.1.1 using DNS over HTTPS (DoH) clients.](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/dns-over-https-client/)
[Convert full setup to partial setup](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-full-to-partial/)
[Convert full setup to secondary setup](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-full-to-secondary/)
[If you initially configured a full setup you can later convert your zone to use incoming zone transfers (Cloudflare as secondary).](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-full-to-secondary/)
[Convert partial setup to full setup](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-partial-to-full/)
[If you initially set up a partial domain on Cloudflare, you can later migrate it to a full setup.](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-partial-to-full/)
[Convert partial setup to secondary setup](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-partial-to-secondary/)
[If you initially set up a partial zone on Cloudflare, you can later convert it to use a secondary setup.](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-partial-to-secondary/)
[Convert secondary setup to full setup](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-secondary-to-full/)
[If you initially set up incoming zone transfers (Cloudflare as secondary), you can later convert your zone to use a full setup.](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-secondary-to-full/)
[Convert secondary setup to partial setup](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-secondary-to-partial/)
[If you initially set up incoming zone transfers (Cloudflare as secondary), you can later convert your zone to use a partial setup.](https://developers.cloudflare.com/dns/zone-setups/conversions/convert-secondary-to-partial/)
[Change your nameservers (Full setup)](https://developers.cloudflare.com/dns/zone-setups/full-setup/setup/)
[If you want to use Cloudflare as your primary DNS provider and manage your DNS records, your domain should be using a full setup.](https://developers.cloudflare.com/dns/zone-setups/full-setup/setup/)
[Set up a partial zone (CNAME setup)](https://developers.cloudflare.com/dns/zone-setups/partial-setup/setup/)
[A CNAME setup (also known as partial) allows you to use Cloudflare's reverse proxy while maintaining your primary and authoritative DNS provider.](https://developers.cloudflare.com/dns/zone-setups/partial-setup/setup/)
[AI Vibe Coding Platform](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/)
[Cloudflare's low-latency, fully serverless compute platform, Workers offers powerful capabilities to enable A/B testing using a server-side implementation.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/)
[AWS cloud HSM](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/aws-cloud-hsm/)
[Learn how to use Keyless SSL with AWS CloudHSM.](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/aws-cloud-hsm/)
[Azure Dedicated HSM](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/azure-dedicated-hsm/)
[Learn how to use Keyless SSL with Azure Dedicated HSM.](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/azure-dedicated-hsm/)
[Azure Managed HSM](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/azure-managed-hsm/)
[This tutorial uses Microsoft Azure’s Managed HSM to deploy a VM with the Keyless SSL daemon. Follow these instructions to deploy your keyless server.](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/azure-managed-hsm/)
[Entrust nShield Connect](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/entrust-nshield-connect/)
[Learn how to use Keyless SSL with Entrust nShield Connect.](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/entrust-nshield-connect/)
[Google Cloud HSM](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/google-cloud-hsm/)
[Learn how to use Keyless SSL with Google Cloud HSM.](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/google-cloud-hsm/)
[IBM Cloud HSM](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/ibm-cloud-hsm/)
[Learn how to use Keyless SSL with IBM Cloud HSM.](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/ibm-cloud-hsm/)
[SoftHSMv2](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/softhsmv2/)
[Learn how to use Keyless SSL with SoftHSMv2.](https://developers.cloudflare.com/ssl/keyless-ssl/hardware-security-modules/softhsmv2/)
[Set up multi-signer DNSSEC with outgoing zone transfers](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-primary/dnssec-for-primary/)
[With outgoing zone transfers, you keep Cloudflare as your primary DNS provider and use one or more secondary providers for increased availability and fault tolerance.](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-primary/dnssec-for-primary/)
[Set up outgoing zone transfers (Cloudflare as Primary)](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-primary/setup/)
[With outgoing zone transfers, you can keep Cloudflare as your primary DNS provider and use one or more secondary providers for increased availability.](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-primary/setup/)
[Set up incoming zone transfers (Cloudflare as Secondary)](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/setup/)
[With incoming zone transfers, you can keep your primary DNS provider and use Cloudflare as a secondary DNS provider.](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/setup/)
[Application Security - Dashboard walkthrough](https://developers.cloudflare.com/videos/app-sec-dashboard/)
[In this video, learn how to navigate the Cloudflare Application Security dashboard and how to use each page to monitor, investigate, and manage security protections.](https://developers.cloudflare.com/videos/app-sec-dashboard/)
[Application Security - Get started guide](https://developers.cloudflare.com/videos/app-sec-get-started/)
[In this video, learn how to get immediate protection against the most common attacks.](https://developers.cloudflare.com/videos/app-sec-get-started/)
[China network - CDN global acceleration for Mainland China](https://developers.cloudflare.com/videos/china-network-acceleration/)
[In this video, Jess Liu discusses Cloudflares CDN Global Acceleration (formerly China Express), including solutions for high latency on dynamic content, accelerating API calls, accessing Cloudflare One services like WARP and Magic WAN from within mainland China, and securely connecting private enterprise networks.](https://developers.cloudflare.com/videos/china-network-acceleration/)
[China network - How to speed up your web traffic inside mainland China](https://developers.cloudflare.com/videos/china-network-inside-china/)
[In this video, Jess Liu walks us through the main features of Cloudflares China Network. They cover how the China Network works, including integrated caching, in-country China name servers, and compliance with ICP regulations. They also briefly discuss Cloudflare's CDN Global Acceleration (formerly China Express), an option for accelerating dynamic content that cannot be cached.](https://developers.cloudflare.com/videos/china-network-inside-china/)
[Create an API token](https://developers.cloudflare.com/videos/create-api-tokens/)
[In this video, learn the difference between account and user API tokens how to create one.](https://developers.cloudflare.com/videos/create-api-tokens/)
[Content compression](https://developers.cloudflare.com/videos/content-compression/)
[In this video, learn how Cloudflare compresses content between Cloudflare and your website visitors and between Cloudflare and your origin server.](https://developers.cloudflare.com/videos/content-compression/)
[Understand how Cloudflare works](https://developers.cloudflare.com/videos/how-cf-works/)
[Learn how Cloudflare makes the Internet safer, faster, and more reliable for everyone through the connectivity cloud.](https://developers.cloudflare.com/videos/how-cf-works/)
[Configure Full encryption mode](https://developers.cloudflare.com/videos/full-ssl-encryption/)
[In this video, learn how to configure your site to use Full encryption mode.](https://developers.cloudflare.com/videos/full-ssl-encryption/)
[Life of a Request: The First Hop - Into the Smart Network](https://developers.cloudflare.com/videos/life-of-a-request-1/)
[Imagine your request is a letter you are trying to send to a friend across the country. Instead of going through the slow, traditional postal service, Cloudflare acts as a hyper-efficient courier company with a fleet of delivery hubs all over the world.](https://developers.cloudflare.com/videos/life-of-a-request-1/)
[Life of a Request: The Fast Lane - Caching and Smart Routing](https://developers.cloudflare.com/videos/life-of-a-request-2/)
[After your request hits Cloudflare's secure network at the nearest data center where it's checked for security threats with a clean bill of health, it's time to get it to its destination at lightning speed.](https://developers.cloudflare.com/videos/life-of-a-request-2/)
[How to set up a load balancer](https://developers.cloudflare.com/videos/load-balancing/)
[Unexpected traffic spikes can crash your website, but Cloudflare Load Balancing helps keep your apps online and fast. In this step-by-step tutorial, learn how to create a public load balancer in just five steps - select a hostname, add an origin pool, attach a health monitor, choose a traffic steering method, and configure custom rules. We'll also explain the difference between public and private load balancers and guide you through using session affinity, fallback pools, and proxy modes.](https://developers.cloudflare.com/videos/load-balancing/)
[Life of a Request: The Finish Line - Serving the Content](https://developers.cloudflare.com/videos/life-of-a-request-3/)
[Once a request is routed to the nearest Cloudflare data center and then intelligently sped along its way, it moves to the final leg of the journey and how we serve content faster than ever.](https://developers.cloudflare.com/videos/life-of-a-request-3/)
[Onboard your domain to Cloudflare](https://developers.cloudflare.com/videos/onboard-domain-cf/)
[Learn how Cloudflare secures and accelerates your website using its global network and reverse proxy technology. In this video, we explain how connecting your domain to Cloudflare protects your origin server, enhances performance, and keeps your site online—even during attacks. You'll see how DNS, nameservers, and proxy status work together to route and safeguard traffic. Whether you're self-hosting or using serverless platforms like Cloudflare Workers, this guide helps you understand the onboarding process and why Cloudflare is essential for modern web infrastructure.](https://developers.cloudflare.com/videos/onboard-domain-cf/)
[Manage account members](https://developers.cloudflare.com/videos/manage-account-members/)
[In this video, learn how to define the roles and permission scope for members associated with an account.](https://developers.cloudflare.com/videos/manage-account-members/)
[SASE - The evolution of corporate networks](https://developers.cloudflare.com/videos/sase-1-evolution-corp-networks/)
[In this video, we discuss Cloudflare One, our Secure Access Service Edge (SASE) platform and how it has been designed to revolutionize the corporate network and enable companies with their Zero Trust strategy. Legacy network design is struggling to address today's challenges of security, performance, and monitoring needs. Many IT teams are trying to evolve their corporate network with point solutions and finding the lack of integration and performance an issue.](https://developers.cloudflare.com/videos/sase-1-evolution-corp-networks/)
[SASE - Stop hosting your VPN service](https://developers.cloudflare.com/videos/sase-2-stop-your-own-vpn/)
[Cloudflare's SASE platform can replace your traditional, expensive VPN appliances, which deliver poor performance for users and create more security risks than solve them. Cloudflare's Zero Trust Network Access (ZTNA) service is a more secure, highly scalable cloud solution. In this video, we look at how easily you can deploy Cloudflare to secure access to internal resources.](https://developers.cloudflare.com/videos/sase-2-stop-your-own-vpn/)
[SASE - Secure remote access to your critical infrastructure](https://developers.cloudflare.com/videos/sase-3-secure-remote-access/)
[In this video, learn how Cloudflare's SASE platform can provide highly secure access to your critical infrastructure by leveraging a modern ZTNA service to implement Zero Trust principles Applications, databases and their servers are running in a variety of locations from on-premises data centers to cloud hyperscalers, making the need to secure administrative access more important than ever.](https://developers.cloudflare.com/videos/sase-3-secure-remote-access/)
[SASE - Connect and secure from any network to anywhere](https://developers.cloudflare.com/videos/sase-4-connect-secure/)
[Build your new corporate network with Cloudflare, connecting any network into our modern SASE platform and secure applications, users, devices and your company data. In this video, you will learn all of the different methods of connecting networks to Cloudflare and what services can be used to improve security and performance.](https://developers.cloudflare.com/videos/sase-4-connect-secure/)
[Manage SSL version or cipher mismatch errors](https://developers.cloudflare.com/videos/ssl-cipher-mismatch/)
[In this video, learn how to manage an SSL version or cipher mismatch error.](https://developers.cloudflare.com/videos/ssl-cipher-mismatch/)
[SASE - Protect your users from Internet risks](https://developers.cloudflare.com/videos/sase-5-protect-users/)
[The Internet has become part of your corporate network; however, browsing the web comes with hidden risks including malware, phishing attacks, and malicious websites. In this video, we will explore how Cloudflare's Secure Web Gateway (SWG) helps keep users safe by filtering and inspecting Internet traffic in real time. Whether you are protecting a remote workforce or securing an entire organization, Cloudflare ensures that users can access the web securely — without sacrificing speed or productivity.](https://developers.cloudflare.com/videos/sase-5-protect-users/)
[SSL/TLS concepts](https://developers.cloudflare.com/videos/strict-ssl-concepts/)
[In this video, learn the key concepts relevant to Cloudflare SSL/TLS.](https://developers.cloudflare.com/videos/strict-ssl-concepts/)
[The Online Address Book](https://developers.cloudflare.com/videos/the-online-address-book/)
[This video focuses on the first prerequisite for using a tunnel, a domain name. It uses the metaphor of an online address book to explain DNS and how Cloudflare manages your domain.](https://developers.cloudflare.com/videos/the-online-address-book/)
[Configure Strict encryption mode](https://developers.cloudflare.com/videos/strict-ssl-encryption/)
[In this video, learn how to configure your site to use Strict (SSL-Only Origin Pull) encryption mode.](https://developers.cloudflare.com/videos/strict-ssl-encryption/)
[WARP - Understand Cloudflare WARP basics](https://developers.cloudflare.com/videos/warp-1-basics/)
[In this episode, we explain the core features of the Cloudflare WARP client and how to troubleshoot common issues. After watching, you will have an understanding of the GUI, the differences between the consumer and corporate WARP, device profiles, the various operating modes of WARP, split tunneling, and more.](https://developers.cloudflare.com/videos/warp-1-basics/)
[What is Cloudflare Tunnel?](https://developers.cloudflare.com/videos/what-is-cf-tunnel/)
[Learn how Cloudflare Tunnel is like a private, secure pathway from your computer to the Internet, so you don't have to leave the front door (your network) wide open.](https://developers.cloudflare.com/videos/what-is-cf-tunnel/)
[WARP - Understand Cloudflare WARP through diagnostic logs](https://developers.cloudflare.com/videos/warp-2-diagnostic-logs/)
[In this more advanced episode, we explain how to use warp-diag files to identify and resolve connection issues with the WARP client. You will learn how to locate and interpret three key files - warp-status, warp-settings, and daemonlog. The video also provides troubleshooting tips, including specific keyword searches and guidance on how to cross-reference logs to identify a bigger picture of the problem.](https://developers.cloudflare.com/videos/warp-2-diagnostic-logs/)
[Application Security](https://developers.cloudflare.com/learning-paths/application-security/account-security//)
[Learn more about the tools Cloudflare offers to protect your website against malicious traffic and bad actors.](https://developers.cloudflare.com/learning-paths/application-security/account-security//)
[Introduction to the China Network](https://developers.cloudflare.com/learning-paths/china-network-overview/series/china-network-main-features-1//)
[Watch to learn how Cloudflare's China Network can help you improve performance, compliance, and connectivity for your users in mainland China.](https://developers.cloudflare.com/learning-paths/china-network-overview/series/china-network-main-features-1//)
[Deploy clientless access](https://developers.cloudflare.com/learning-paths/clientless-access/concepts//)
[Learn how to set up clientless access to internal applications with Cloudflare Zero Trust.](https://developers.cloudflare.com/learning-paths/clientless-access/concepts//)
[Project Cybersafe Schools](https://developers.cloudflare.com/learning-paths/cybersafe/concepts//)
[Prevent children from accessing obscene or harmful content over the Internet.](https://developers.cloudflare.com/learning-paths/cybersafe/concepts//)
[Protect your data center](https://developers.cloudflare.com/learning-paths/data-center-protection/concepts//)
[Learn how to use Magic Transit to protect your data centers from distributed denial-of-service (DDoS) attacks.](https://developers.cloudflare.com/learning-paths/data-center-protection/concepts//)
[Introduction to Durable Objects](https://developers.cloudflare.com/learning-paths/durable-objects-course/series/introduction-to-series-1//)
[Dive into a hands-on Durable Objects project and learn how to build stateful apps using serverless architecture](https://developers.cloudflare.com/learning-paths/durable-objects-course/series/introduction-to-series-1//)
[Holistic AI security with Cloudflare One](https://developers.cloudflare.com/learning-paths/holistic-ai-security/concepts//)
[Address new security challenges and mitigate risks like shadow AI and data loss.](https://developers.cloudflare.com/learning-paths/holistic-ai-security/concepts//)
[Load balancing](https://developers.cloudflare.com/learning-paths/load-balancing/concepts//)
[Maximize application performance and availability.](https://developers.cloudflare.com/learning-paths/load-balancing/concepts//)
[mTLS at Cloudflare](https://developers.cloudflare.com/learning-paths/mtls/concepts//)
[Safeguard APIs and Devices on Cloudflare's network.](https://developers.cloudflare.com/learning-paths/mtls/concepts//)
[Prevent DDoS attacks](https://developers.cloudflare.com/learning-paths/prevent-ddos-attacks/concepts//)
[Protect your application from distributed (DDoS) and regular denial of service (DoS) attacks.](https://developers.cloudflare.com/learning-paths/prevent-ddos-attacks/concepts//)
[Replace your VPN](https://developers.cloudflare.com/learning-paths/replace-vpn/concepts//)
[Learn how to replace your VPN with Cloudflare Zero Trust.](https://developers.cloudflare.com/learning-paths/replace-vpn/concepts//)
[Introduction to R2](https://developers.cloudflare.com/learning-paths/r2-intro/series/r2-1//)
[Learn about Cloudflare R2, an object storage solution designed to handle your data and files efficiently. It is ideal for storing large media files, creating data lakes, or delivering web assets.](https://developers.cloudflare.com/learning-paths/r2-intro/series/r2-1//)
[Build and secure your SASE corporate network](https://developers.cloudflare.com/learning-paths/sase-overview-course/series/evolution-corporate-networks-1//)
[Watch this series and learn all about Cloudflare's Secure Access Service Edge (SASE) platform to learn how it can revolutionize your corporate network.](https://developers.cloudflare.com/learning-paths/sase-overview-course/series/evolution-corporate-networks-1//)
[Secure your Internet traffic and SaaS apps](https://developers.cloudflare.com/learning-paths/secure-internet-traffic/concepts//)
[Provide your users and networks with a secure, performant, and flexible path to the Internet.](https://developers.cloudflare.com/learning-paths/secure-internet-traffic/concepts//)
[Prepare for surges or spikes in web traffic](https://developers.cloudflare.com/learning-paths/surge-readiness/concepts//)
[Learn how to protect your website for potential surges or spikes in web traffic.](https://developers.cloudflare.com/learning-paths/surge-readiness/concepts//)
[Secure your email with Email security](https://developers.cloudflare.com/learning-paths/secure-your-email/concepts//)
[Use Cloudflare's Email security to protect your email inbox from phishing and malware attacks.](https://developers.cloudflare.com/learning-paths/secure-your-email/concepts//)
[Understand and troubleshoot Cloudflare WARP](https://developers.cloudflare.com/learning-paths/warp-overview-course/series/warp-basics-1//)
[In this series, we cover the basics of Cloudflare WARP, share useful troubleshooting tips, and explain the warp-diag logs in detail.](https://developers.cloudflare.com/learning-paths/warp-overview-course/series/warp-basics-1//)
[Build applications with Cloudflare Workers](https://developers.cloudflare.com/learning-paths/workers/concepts//)
[Deploy serverless code, globally with exceptional performance, reliability, and scale.](https://developers.cloudflare.com/learning-paths/workers/concepts//)
[Introduction to Cloudflare Workflows](https://developers.cloudflare.com/learning-paths/workflows-course/series/workflows-1//)
[In this series, we introduce Cloudflare Workflows and the term 'Durable Execution' which comes from the desire to run applications that can resume execution from where they left off, even if the underlying host or compute fails.](https://developers.cloudflare.com/learning-paths/workflows-course/series/workflows-1//)
---
title: Overview · Cloudflare Rules docs
description: Use Cloudflare Rules to adjust requests and responses, configure
settings, and trigger actions for specific requests.
lastUpdated: 2025-08-20T13:33:03.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/
md: https://developers.cloudflare.com/rules/index.md
---
Available on all plans
Cloudflare Rules allows you to make adjustments to requests and responses, configure Cloudflare settings, and trigger specific actions for matching requests.
Rules features require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
***
## Features
### Configuration Rules
Customize Cloudflare configuration settings for matching incoming requests.
[Use Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/)
### Snippets
Customize the behavior of your website or application using short pieces of JavaScript code.
[Use Snippets](https://developers.cloudflare.com/rules/snippets/)
### Transform Rules
Adjust the URI path, query string, and HTTP headers of requests and responses on the Cloudflare global network.
[Use Transform Rules](https://developers.cloudflare.com/rules/transform/)
### Redirects
Redirect visitors from a source URL to a target URL with a specific HTTP status code. Use Single Redirects or Bulk Redirects depending on your use case.
[Use Redirects](https://developers.cloudflare.com/rules/url-forwarding/)
### Origin Rules
Customize where the incoming traffic will go and with which parameters. Override request properties such as `Host` header, destination hostname, and destination port.
[Use Origin Rules](https://developers.cloudflare.com/rules/origin-rules/)
### Cloud Connector
Route matching incoming traffic from your website to a public cloud provider such as AWS, Google Cloud, and Azure.
[Use Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/)
### Compression Rules
Customize the compression applied to responses from Cloudflare's global network to your website visitors, based on the file extension and content type.
[Use Compression Rules](https://developers.cloudflare.com/rules/compression-rules/)
### Page Rules
Trigger certain actions when a request matches a URL pattern.
[Use Page Rules](https://developers.cloudflare.com/rules/page-rules/)
### URL normalization
Modify the URLs of incoming requests so that they conform to a consistent formatting standard.
[Configure URL normalization](https://developers.cloudflare.com/rules/normalization/)
### Custom Errors
Define what custom content to serve for errors returned by an origin server or by a Cloudflare product, including Workers.
[Configure Custom Errors](https://developers.cloudflare.com/rules/custom-errors/)
***
## Related products
**[Custom rules](https://developers.cloudflare.com/waf/custom-rules/)**
Control incoming traffic by filtering requests to a zone. You can block or challenge incoming requests according to rules you define.
**[Rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/)**
Define rate limits for requests matching an expression, and the action to perform when those rate limits are reached.
**[Cache rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)**
Customize the cache properties of your HTTP requests.
**[Workers](https://developers.cloudflare.com/workers/)**
Cloudflare Workers provides a serverless execution environment that allows you to create new applications or augment existing ones without configuring or maintaining infrastructure.
***
## More resources
[Plans](https://www.cloudflare.com/plans/#overview)
Compare available Cloudflare plans
---
title: Overview · Cloudflare Ruleset Engine docs
description: Create and deploy rules and rulesets across Cloudflare products
using the Ruleset Engine's powerful syntax and high-performance evaluation.
lastUpdated: 2025-03-25T12:42:09.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ruleset-engine/
md: https://developers.cloudflare.com/ruleset-engine/index.md
---
The Cloudflare Ruleset Engine allows you to create and deploy rules and rulesets in different Cloudflare products using the same basic syntax.
## Main features
* **Powerful syntax**: Rule expressions use a powerful Rules language similar to the wirefilter syntax that allows you to create complex rules.
* **High-performance rule evaluation**: Allows you to have many rules in different Cloudflare products with almost no impact on performance.
* **Engine powering different Cloudflare products**: Cloudflare keeps building products on top of the Ruleset Engine, which means that you can use the same API methods for configuring different products, with the same customization possibilities. Additionally, the Ruleset Engine supports the different phases of the request life cycle at Cloudflare.
## Availability
The Ruleset Engine supports different Cloudflare products. Refer to [Phases list](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/) and to each product's documentation for details.
---
title: Overview · Cloudflare Sandbox SDK docs
description: The Sandbox SDK enables you to run untrusted code securely in
isolated environments. Built on Containers, Sandbox SDK provides a simple API
for executing commands, managing files, running background processes, and
exposing services — all from your Workers applications.
lastUpdated: 2026-02-06T17:12:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/
md: https://developers.cloudflare.com/sandbox/index.md
---
Build secure, isolated code execution environments
Available on Workers Paid plan
The Sandbox SDK enables you to run untrusted code securely in isolated environments. Built on [Containers](https://developers.cloudflare.com/containers/), Sandbox SDK provides a simple API for executing commands, managing files, running background processes, and exposing services — all from your [Workers](https://developers.cloudflare.com/workers/) applications.
Sandboxes are ideal for building AI agents that need to execute code, interactive development environments, data analysis platforms, CI/CD systems, and any application that needs secure code execution at the edge. Each sandbox runs in its own isolated container with a full Linux environment, providing strong security boundaries while maintaining performance.
With Sandbox, you can execute Python scripts, run Node.js applications, analyze data, compile code, and perform complex computations — all with a simple TypeScript API and no infrastructure to manage.
* Execute Commands
```typescript
import { getSandbox } from '@cloudflare/sandbox';
export { Sandbox } from '@cloudflare/sandbox';
export default {
async fetch(request: Request, env: Env): Promise {
const sandbox = getSandbox(env.Sandbox, 'user-123');
// Execute a command and get the result
const result = await sandbox.exec('python --version');
return Response.json({
output: result.stdout,
exitCode: result.exitCode,
success: result.success
});
}
};
```
* Code Interpreter
```typescript
import { getSandbox } from '@cloudflare/sandbox';
export { Sandbox } from '@cloudflare/sandbox';
export default {
async fetch(request: Request, env: Env): Promise {
const sandbox = getSandbox(env.Sandbox, 'user-123');
// Create a Python execution context
const ctx = await sandbox.createCodeContext({ language: 'python' });
// Execute Python code with automatic result capture
const result = await sandbox.runCode(`
import pandas as pd
data = {'product': ['A', 'B', 'C'], 'sales': [100, 200, 150]}
df = pd.DataFrame(data)
df['sales'].sum() # Last expression is automatically returned
`, { context: ctx });
return Response.json({
result: result.results?.[0]?.text,
logs: result.logs
});
}
};
```
* File Operations
```typescript
import { getSandbox } from '@cloudflare/sandbox';
export { Sandbox } from '@cloudflare/sandbox';
export default {
async fetch(request: Request, env: Env): Promise {
const sandbox = getSandbox(env.Sandbox, 'user-123');
// Create a project structure
await sandbox.mkdir('/workspace/project/src', { recursive: true });
// Write files
await sandbox.writeFile(
'/workspace/project/package.json',
JSON.stringify({ name: 'my-app', version: '1.0.0' })
);
// Read a file back
const content = await sandbox.readFile('/workspace/project/package.json');
return Response.json({ content });
}
};
```
* File Watching
```typescript
import { getSandbox } from '@cloudflare/sandbox';
export { Sandbox } from '@cloudflare/sandbox';
export default {
async fetch(request: Request, env: Env): Promise {
const sandbox = getSandbox(env.Sandbox, 'user-123');
// Watch for file changes in real-time
const watcher = await sandbox.watch('/workspace/src', {
include: ['*.js', '*.ts'],
onEvent: (event) => {
console.log(`${event.type}: ${event.path}`);
if (event.type === 'modify') {
// Trigger rebuild or hot reload
console.log('Code changed, recompiling...');
}
},
onError: (error) => {
console.error('Watch error:', error);
}
});
// Stop watching when done
setTimeout(() => watcher.stop(), 60000);
return Response.json({ message: 'File watcher started' });
}
};
```
* WebSocket Connections
```typescript
import { getSandbox } from '@cloudflare/sandbox';
export { Sandbox } from '@cloudflare/sandbox';
export default {
async fetch(request: Request, env: Env): Promise {
// Connect to WebSocket services in sandbox
if (request.headers.get('Upgrade')?.toLowerCase() === 'websocket') {
const sandbox = getSandbox(env.Sandbox, 'user-123');
return await sandbox.wsConnect(request, 8080);
}
return Response.json({ message: 'WebSocket endpoint' });
}
};
```
Connect to WebSocket servers running in sandboxes. Learn more: [WebSocket Connections](https://developers.cloudflare.com/sandbox/guides/websocket-connections/).
[Get started](https://developers.cloudflare.com/sandbox/get-started/)
[API Reference](https://developers.cloudflare.com/sandbox/api/)
***
## Features
### Execute commands securely
Run shell commands, Python scripts, Node.js applications, and more with streaming output support and automatic timeout handling.
[Learn about command execution](https://developers.cloudflare.com/sandbox/guides/execute-commands/)
### Manage files and processes
Read, write, and manipulate files in the sandbox filesystem. Run background processes, monitor output, and manage long-running operations.
[Learn about file operations](https://developers.cloudflare.com/sandbox/guides/manage-files/)
### Expose services with preview URLs
Expose HTTP services running in your sandbox with automatically generated preview URLs, perfect for interactive development environments and application hosting.
[Learn about preview URLs](https://developers.cloudflare.com/sandbox/guides/expose-services/)
### Execute code directly
Execute Python and JavaScript code with rich outputs including charts, tables, and images. Maintain persistent state between executions for AI-generated code and interactive workflows.
[Learn about code execution](https://developers.cloudflare.com/sandbox/guides/code-execution/)
### Persistent storage with object storage
Mount S3-compatible object storage (R2, S3, GCS, and more) as local filesystems. Access buckets using standard file operations with data that persists across sandbox lifecycles. Production deployment required.
[Learn about bucket mounting](https://developers.cloudflare.com/sandbox/guides/mount-buckets/)
### Watch files for real-time changes
Monitor files and directories for changes using native filesystem events. Perfect for building hot reloading development servers, build automation systems, and configuration monitoring tools.
[Learn about file watching](https://developers.cloudflare.com/sandbox/guides/file-watching/)
***
## Use Cases
Build powerful applications with Sandbox:
### AI Code Execution
Execute code generated by Large Language Models safely and reliably. Native integration with [Workers AI](https://developers.cloudflare.com/workers-ai/) models like GPT-OSS enables function calling with sandbox execution. Perfect for AI agents, code assistants, and autonomous systems that need to run untrusted code.
### Data Analysis & Notebooks
Create interactive data analysis environments with pandas, NumPy, and Matplotlib. Generate charts, tables, and visualizations with automatic rich output formatting.
### Interactive Development Environments
Build cloud IDEs, coding playgrounds, and collaborative development tools with full Linux environments and preview URLs.
### CI/CD & Build Systems
Run tests, compile code, and execute build pipelines in isolated environments with parallel execution and streaming logs.
***
## Related products
**[Containers](https://developers.cloudflare.com/containers/)**
Serverless container runtime that powers Sandbox, enabling you to run any containerized workload on the edge.
**[Workers AI](https://developers.cloudflare.com/workers-ai/)**
Run machine learning models and LLMs on the network. Combine with Sandbox for secure AI code execution workflows.
**[Durable Objects](https://developers.cloudflare.com/durable-objects/)**
Stateful coordination layer that enables Sandbox to maintain persistent environments with strong consistency.
***
## More resources
[Tutorials](https://developers.cloudflare.com/sandbox/tutorials/)
Explore complete examples including AI code execution, data analysis, and interactive environments.
[How-to Guides](https://developers.cloudflare.com/sandbox/guides/)
Learn how to solve specific problems and implement features with the Sandbox SDK.
[API Reference](https://developers.cloudflare.com/sandbox/api/)
Explore the complete API documentation for the Sandbox SDK.
[Concepts](https://developers.cloudflare.com/sandbox/concepts/)
Learn about the key concepts and architecture of the Sandbox SDK.
[Configuration](https://developers.cloudflare.com/sandbox/configuration/)
Learn about the configuration options for the Sandbox SDK.
[GitHub Repository](https://github.com/cloudflare/sandbox-sdk)
View the SDK source code, report issues, and contribute to the project.
[Beta Information](https://developers.cloudflare.com/sandbox/platform/beta-info/)
Learn about the Sandbox Beta, current status, and upcoming features.
[Pricing](https://developers.cloudflare.com/sandbox/platform/pricing/)
Understand Sandbox pricing based on the underlying Containers platform.
[Limits](https://developers.cloudflare.com/sandbox/platform/limits/)
Learn about resource limits, quotas, and best practices for working within them.
[Discord Community](https://discord.cloudflare.com)
Connect with the community on Discord. Ask questions, share what you're building, and get help from other developers.
```plaintext
```
---
title: Search | Cloudflare Docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/search/
md: https://developers.cloudflare.com/search/index.md
---
---
title: Overview · Cloudflare Secrets Store docs
description: Use Secrets Store to encrypt and store sensitive information as
secrets that are securely reusable across your Cloudflare account.
lastUpdated: 2025-09-03T14:48:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/secrets-store/
md: https://developers.cloudflare.com/secrets-store/index.md
---
Encrypt and store sensitive information as secrets that are securely reusable across your account.
Available in open beta
Cloudflare Secrets Store is a secure, centralized location in which account-level secrets are stored and managed. The secrets are securely encrypted and stored across all [Cloudflare data centers](https://www.cloudflare.com/network/).
Secrets Store is currently compatible with [Cloudflare Workers](https://developers.cloudflare.com/secrets-store/integrations/workers/) and [AI Gateway](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/). Integrations with other products will be added in the future.
China availability
Secrets Store is unavailable in the [Cloudflare China Network](https://developers.cloudflare.com/china-network/), operated by Cloudflare's partner JD Cloud.
---
title: Overview · Security dashboard docs
description: The application security dashboard helps you understand the current
security posture of your web applications and allows you configure different
security rules for those applications.
lastUpdated: 2025-10-17T14:13:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security/
md: https://developers.cloudflare.com/security/index.md
---
The application security dashboard is your starting point to better understand the security posture of your web applications, and to configure rules to protect them.
New dashboard experience
Cloudflare is gradually making the new **Security** dashboard available by default to users. Users who do not have the new dashboard by default can still manually opt in:
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com), and select your account and domain.
2. Open any page under **Security**.
3. In the top right-hand corner of the page, select **Try new dashboard**.
To opt out of the new security dashboard:
1. In the Cloudflare dashboard, go to the Security **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
2. Turn off the setting **New application security dashboard**.
The opt-out option will be available for a limited time.
## Features
### Security overview
Get a high-level overview of your domain's security posture.
[Explore Security overview](https://developers.cloudflare.com/security/overview/)
### Security Analytics
Shows information about all incoming HTTP requests or mitigated requests (rule matches). Tailor your security configurations based on sampled logs.
[Explore Security Analytics](https://developers.cloudflare.com/security/analytics/)
### Web assets
Discover your web assets (including API endpoints) and instruct Cloudflare how to best protect them.
[Use Web assets](https://developers.cloudflare.com/security/web-assets/)
### Security rules
Perform security actions on incoming requests that match specified filters.
[Use Security rules](https://developers.cloudflare.com/security/rules/)
***
## More resources
[Plans](https://www.cloudflare.com/plans/#overview)
Compare available Cloudflare plans
---
title: Overview · Cloudflare Security Center docs
description: "Cloudflare Security Center brings together our suite of security
products, our security expertise, and unique Internet intelligence as a
unified security intelligence solution. Security Center enables you to
strengthen your security posture by:"
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/
md: https://developers.cloudflare.com/security-center/index.md
---
Cloudflare Security Center brings together our suite of security products, our security expertise, and unique Internet intelligence as a unified security intelligence solution. Security Center enables you to strengthen your security posture by:
* Mapping your cyber attack surface
* Providing asset inventory and discovery
* Identifying potential security risks, misconfigurations, and vulnerabilities
* Helping you to mitigate these risks through remediation in a few clicks
## Main features
* **Security Insights**: Review and manage potential security risks and vulnerabilities associated with your IT infrastructure.
* **Infrastructure**: Review and manage your IT infrastructure.
* **Investigate**: Investigate threats using data from Cloudflare's global network.
* **Security Reports (beta)**: Gain visibility into requests blocked or challenged by the Cloudflare Application Security suite of products.
* **Brand Protection (beta)**: Search for new domains that may be attempting to impersonate your brand.
[Get started](https://developers.cloudflare.com/security-center/get-started/)
***
## Availability
Cloudflare Security Center is available to customers on all plans. If you have any comments, questions, or bugs to report, create a post in the [Cloudflare Community forum](https://community.cloudflare.com/c/security/security-center/65).
The frequency of security scans depends on your Cloudflare plan. Refer to [Scan frequency](https://developers.cloudflare.com/security-center/security-insights/how-it-works/#scan-frequency) for more information.
## Limitations
* Users with an [Administrator Read Only](https://developers.cloudflare.com/fundamentals/manage-members/roles/#account-scoped-roles) role cannot access the Cloudflare Security Center.
* Only Cloudflare accounts with at least one Business or Enterprise zone, or accounts on the Teams Standard or Teams Enterprise plans, can manually start a new scan.
---
title: Overview · Cloudflare Smart Shield docs
description: Use Smart Shield to protect your origin server, improve content
availability, and reduce network latency.
lastUpdated: 2025-11-19T12:11:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/smart-shield/
md: https://developers.cloudflare.com/smart-shield/index.md
---
Safeguard your origin with just a few clicks.
Smart Shield acts as an intermediate caching layer between Cloudflare's content delivery network and your origin server, consolidating multiple requests from various locations into a single request. Combined with [connection reuse](https://developers.cloudflare.com/smart-shield/concepts/connection-reuse/), this approach significantly reduces origin load while improving website and application performance.
Learn how to [get started](https://developers.cloudflare.com/smart-shield/get-started/).
***
## Related products
**[Cache](https://developers.cloudflare.com/cache/)**
Cache stores copies of frequently accessed content (such as images, videos, or webpages) in geographically distributed data centers that are located closer to end users than origin servers, improving website performance.
**[Observatory](https://developers.cloudflare.com/speed/observatory/)**
Observatory uses synthetic tests and real user data to assess the performance of your website, producing different metrics and insights. Cloudflare then uses this analysis to recommend optimizations that best address your performance issues.
---
title: Cloudflare Spectrum · Cloudflare Spectrum docs
description: Spectrum allows you to route MQTT, email, file transfer, version
control, games, and more over TCP or UDP through Cloudflare to mask the origin
and protect it from DDoS attacks.
lastUpdated: 2025-07-31T21:09:55.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/spectrum/
md: https://developers.cloudflare.com/spectrum/index.md
---
Spectrum provides security and acceleration for any [TCP](https://www.cloudflare.com/learning/ddos/glossary/tcp-ip/) or [UDP](https://www.cloudflare.com/learning/ddos/glossary/user-datagram-protocol-udp/) based application.
Available on Paid plans
Spectrum allows you to route MQTT, email, file transfer, version control, games, and more over TCP or UDP through Cloudflare to mask the origin and protect it from [DDoS attacks](https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/).
***
## Features
### Enable Proxy protocol
Use a proxy protocol for Cloudflare to pass on the client IP to your service.
[Use Enable Proxy protocol](https://developers.cloudflare.com/spectrum/how-to/enable-proxy-protocol/)
### DDoS Protection for Spectrum
Learn more about what L3/4 DDoS Protection is included as part of the Spectrum service.
[Use DDoS Protection for Spectrum](https://developers.cloudflare.com/spectrum/about/ddos-for-spectrum/)
***
## Related products
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Cloudflare DDoS protection secures websites, applications, and entire networks while ensuring the performance of legitimate traffic is not compromised.
**[BYOIP](https://developers.cloudflare.com/byoip/)**
Get Cloudflare's security and performance while using your own IPs. With Bring Your Own IP (BYOIP), Cloudflare announces your IPs in all our locations.
**[Load Balancing](https://developers.cloudflare.com/load-balancing/)**
Cloudflare Load Balancing distributes traffic across your endpoints, which reduces endpoint strain and latency and improves the experience for end users.
**[DNS](https://developers.cloudflare.com/dns/)**
Cloudflare's global DNS platform provides speed and resilience. DNS customers also benefit from free DNSSEC, and protection against route leaks and hijacking.
***
## More resources
[Plans](https://www.cloudflare.com/plans/)
Compare available Cloudflare plans.
---
title: Speed · Cloudflare Speed docs
description: Speed allows you to assess the performance of your website and get
recommendations of Cloudflare products to enhance the website performance.
lastUpdated: 2025-09-26T10:03:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/speed/
md: https://developers.cloudflare.com/speed/index.md
---
Improve the performance of your website or web application.
Available on all plans
Speed allows you to assess the performance of your website and get recommendations of Cloudflare products to enhance the website performance.
***
## Features
### Observatory
Use Observatory to conduct tests with both synthetic and real user data to identify potential website performance enhancements.
[Use Observatory](https://developers.cloudflare.com/speed/observatory/)
### Settings
Get recommendations of Cloudflare products and settings to improve your website’s performance.
[Use Settings](https://developers.cloudflare.com/speed/optimization/)
### Aggregated Internet Measurement
Understand your Internet quality to identify scenarios that your Internet connection is good or bad for.
[Use Aggregated Internet Measurement](https://developers.cloudflare.com/speed/aim/)
***
## Related products
**[Cache rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)**
Customize the cache properties of your HTTP requests.
**[Cloudflare Web Analytics](https://developers.cloudflare.com/web-analytics/)**
Understand the performance of your webpages as experienced by your site visitors.
**[Cloudflare Image Resizing](https://developers.cloudflare.com/images/transform-images/)**
Transform images on Cloudflare's edge platform: resize, adjust quality, and convert images to WebP or AVIF format on demand.
**[Early Hints](https://developers.cloudflare.com/cache/advanced-configuration/early-hints/)**
Take advantage of "server think time" to asynchronously send instructions to the browser to begin loading resources while the origin server is compiling the full response.
***
## More resources
[Quotas](https://developers.cloudflare.com/speed/observatory/run-speed-test/#quotas)
Learn about the quota limits for the number of tests you can run per month.
[Community Forum](https://community.cloudflare.com/c/website-application-performance/88)
Engage with other users and explore more resources on Cloudflare support forum.
---
title: Sponsorships | Cloudflare Docs
description: |-
Cloudflare powers over 20 million Internet properties, including these
world-changing open-source projects.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sponsorships/
md: https://developers.cloudflare.com/sponsorships/index.md
---
Cloudflare powers over 20 million Internet properties, including these world-changing open-source projects.
[](https://yarnpkg.com/en/)
### [Yarn](https://yarnpkg.com/en/)
A package manager for Node that creates a lockfile for dependencies and cache’s packages for future projects.
[Visit site](https://yarnpkg.com/en/) [Code on GitHub](https://github.com/yarnpkg/yarn)
[](https://momentjs.com/)
### [Moment.js](https://momentjs.com/)
A library for Parsing, validating, manipulating, and displaying dates and times in JavaScript.
[Visit site](https://momentjs.com/) [Code on GitHub](https://github.com/moment/moment/)
[](https://d3js.org/)
### [D3](https://d3js.org/)
A way to bind data to the DOM, and then apply data-driven transformations to the document.
[Visit site](https://d3js.org/) [Code on GitHub](https://github.com/d3/d3)
[](https://unpkg.com/)
### [UNPKG](https://unpkg.com/)
A fast, global Content Delivery Network for everything on npm.
[Visit site](https://unpkg.com/) [Code on GitHub](https://github.com/unpkg/unpkg)
[](https://html5boilerplate.com/)
### [HTML5 Boilerplate](https://html5boilerplate.com/)
A fast, robust, and adaptable way to create web apps or sites.
[Visit site](https://html5boilerplate.com/) [Code on GitHub](https://github.com/h5bp/html5-boilerplate)
[](https://cdnjs.com/)
### [cdnjs](https://cdnjs.com/)
A free, public Content Delivery Network for popular libraries.
[Visit site](https://cdnjs.com/) [Code on GitHub](https://github.com/cdnjs/cdnjs)
[](https://webpack.js.org/)
### [Webpack](https://webpack.js.org/)
A module bundler for combining JavaScript files.
[Visit site](https://webpack.js.org/) [Code on GitHub](https://github.com/webpack/webpack)
[](https://nodejs.org/)
### [Node.js](https://nodejs.org/)
A JavaScript runtime built on Chrome’s V8 JavaScript engine.
[Visit site](https://nodejs.org/) [Code on GitHub](https://github.com/nodejs/node)
[](https://reactjs.org/)
### [React](https://reactjs.org/)
A JavaScript library for building user interfaces created by facebook.
[Visit site](https://reactjs.org/) [Code on GitHub](https://github.com/facebook/react/)
[](https://git-scm.com/)
### [git](https://git-scm.com/)
A version control system that allows millions people across the world to collaborate on coding projects.
[Visit site](https://git-scm.com/) [Code on GitHub](https://github.com/git/git)
[](https://www.kali.org/)
### [Kali Linux](https://www.kali.org/)
Kali Linux is an advanced penetration testing Linux distribution.
[Visit site](https://www.kali.org/) [Code on GitHub](https://github.com/offensive-security)
[](https://clickhouse.tech/)
### [ClickHouse](https://clickhouse.tech/)
ClickHouse is a free analytics DBMS for big data
[Visit site](https://clickhouse.tech/) [Code on GitHub](https://github.com/ClickHouse/ClickHouse)
[](https://phalcon.io/)
### [Phalcon](https://phalcon.io/)
Phalcon is a full-stack PHP framework delivered as a C-extension
[Visit site](https://phalcon.io/) [Code on GitHub](https://github.com/phalcon/cphalcon/)
[](https://www.jsdelivr.com/)
### [JsDelivr](https://www.jsdelivr.com/)
JsDelivr is a public, open-source CDN (Content Delivery Network) developed by ProspectOne, focused on performance, reliability, and security.
[Visit site](https://www.jsdelivr.com/) [Code on GitHub](https://github.com/jsdelivr/jsdelivr)
[](https://freecodecamp.org/)
### [freeCodeCamp](https://freecodecamp.org/)
An online coding bootcamp that teaches you to code for free.
[Visit site](https://freecodecamp.org/) [Code on GitHub](https://github.com/freeCodeCamp/freeCodeCamp)
[](https://uppy.io/)
### [Uppy](https://uppy.io/)
A sleek, modular file uploader that integrates seamlessly with any application.
[Visit site](https://uppy.io/) [Code on GitHub](https://github.com/transloadit/uppy)
[](https://redux.js.org/)
### [Redux](https://redux.js.org/)
A predictable state container for JavaScript apps. It’s commonly used with React to make state management simple.
[Visit site](https://redux.js.org/) [Code on GitHub](https://github.com/reactjs/redux/)
[](https://jquery.com)
### [jQuery](https://jquery.com)
The Write Less, Do More, JavaScript Library.
[Visit site](https://jquery.com) [Code on GitHub](https://github.com/jquery/jquery)
[](https://select2.org/)
### [Select2](https://select2.org/)
A jQuery based replacement for select boxes. It supports searching, remote data sets, and infinite scrolling of results.
[Visit site](https://select2.org/) [Code on GitHub](https://github.com/select2/select2)
[](https://gulpjs.com/)
### [Gulp](https://gulpjs.com/)
A toolkit for automating painful or time-consuming tasks in your development workflow, so you can stop messing around and build something.
[Visit site](https://gulpjs.com/) [Code on GitHub](https://github.com/gulpjs/gulp)
[](https://impress.js.org/)
### [impress.js](https://impress.js.org/)
A presentation tool made to leverage the power of css3 transforms and transitions.
[Visit site](https://impress.js.org/) [Code on GitHub](https://github.com/impress/impress.js)
[](https://expressjs.com/)
### [Express](https://expressjs.com/)
A fast, minimalist web framework for Node.js.
[Visit site](https://expressjs.com/) [Code on GitHub](https://github.com/expressjs/express)
[](https://revealjs.com/#/)
### [REVEAL.JS](https://revealjs.com/#/)
A framework for making powerpoint-like presentations using HTML, CSS and JS.
[Visit site](https://revealjs.com/#/) [Code on GitHub](https://github.com/hakimel/reveal.js)
[](https://threejs.org/)
### [three.js](https://threejs.org/)
A JavaScript library used to create and display animated 3D computer graphics in a web browser.
[Visit site](https://threejs.org/) [Code on GitHub](https://github.com/mrdoob/three.js/)
[](https://getbootstrap.com/)
### [Bootstrap](https://getbootstrap.com/)
A responsive, mobile-first HTML, CSS and JS styling library.
[Visit site](https://getbootstrap.com/) [Code on GitHub](https://github.com/twbs/bootstrap)
---
title: Overview · Cloudflare Stream docs
description: Cloudflare Stream lets you or your end users upload, store, encode,
and deliver live and on-demand video with one API, without configuring or
maintaining infrastructure.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/
md: https://developers.cloudflare.com/stream/index.md
---
Serverless live and on-demand video streaming
Cloudflare Stream lets you or your end users upload, store, encode, and deliver live and on-demand video with one API, without configuring or maintaining infrastructure.
You can use Stream to build your own video features in websites and native apps, from simple playback to an entire video platform.
Cloudflare Stream runs on [Cloudflare’s global cloud network](https://www.cloudflare.com/network/) in hundreds of cities worldwide.
[Get started ](https://developers.cloudflare.com/stream/get-started/)[Stream dashboard](https://dash.cloudflare.com/?to=/:account/stream)
***
## Features
### Control access to video content
Restrict access to paid or authenticated content with signed URLs.
[Use Signed URLs](https://developers.cloudflare.com/stream/viewing-videos/securing-your-stream/)
### Let your users upload their own videos
Let users in your app upload videos directly to Stream with a unique, one-time upload URL.
[Direct Creator Uploads](https://developers.cloudflare.com/stream/uploading-videos/direct-creator-uploads/)
### Play video on any device
Play on-demand and live video on websites, in native iOS and Android apps, and dedicated streaming devices like Apple TV.
[Play videos](https://developers.cloudflare.com/stream/viewing-videos/)
### Get detailed analytics
Understand and analyze which videos and live streams are viewed most and break down metrics on a per-creator basis.
[Explore Analytics](https://developers.cloudflare.com/stream/getting-analytics/)
***
## More resources
[Discord](https://discord.cloudflare.com)
Join the Stream developer community
---
title: Overview · Cloudflare SSL/TLS docs
description: Cloudflare SSL/TLS offers free Universal SSL alongside advanced and
enterprise features to meet your encryption and certificate management needs.
lastUpdated: 2025-01-15T09:15:45.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/
md: https://developers.cloudflare.com/ssl/index.md
---
Encrypt your web traffic to prevent data theft and other tampering.
Available on all plans
Through [Universal SSL](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/), Cloudflare is the first Internet performance and security company to offer free SSL/TLS protection. Cloudflare SSL/TLS also provides a number of other features to meet your encryption requirements and certificate management needs. Refer to [Get started](https://developers.cloudflare.com/ssl/get-started/) for more.
***
## Features
### Total TLS
Extending the protection offered by Universal SSL, Total TLS is an easy way to automatically issue certificates for all levels of subdomains that you have.
[Use Total TLS](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/total-tls/)
### Delegated DCV
Even if you use a different provider for authoritative DNS, you can delegate domain control validation (DCV) to Cloudflare, reducing the need of manual intervention.
[Use Delegated DCV](https://developers.cloudflare.com/ssl/edge-certificates/changing-dcv-method/methods/delegated-dcv/)
### Custom TLS settings
Cloudflare also allows you to specify the minimum TLS version that visitors must use to connect to your website or application, and [restrict cipher suites](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/cipher-suites/customize-cipher-suites/) according to your security requirements.
[Use Custom TLS settings](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/minimum-tls/)
Refer to [features and availability](https://developers.cloudflare.com/ssl/reference/all-features/) for a complete list of SSL/TLS features and their availability according to different Cloudflare plans.
***
## Related products
**[Cloudflare DNS](https://developers.cloudflare.com/dns/)**
When you use Cloudflare DNS, all DNS queries for your domain are answered by Cloudflare's global anycast network. This network delivers performance and global availability.
**[Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)**
Cloudflare for SaaS allows you to extend the security and performance benefits of Cloudflare's network to your customers via their own custom or vanity domains.
---
title: Style Guide · Cloudflare Style Guide
description: Improve your contributions to Cloudflare's documentation. Ensure
consistency, professionalism, and clarity in your content across all products.
lastUpdated: 2025-09-11T09:44:45.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/
md: https://developers.cloudflare.com/style-guide/index.md
---
Use this guide when writing any content for product, including the dashboard and documentation.
Understanding Cloudflare style is the first step in being able to write, review, and edit documentation. Adhering to Cloudflare style ensures consistency across the company's documentation and promotes the following benefits:
* A professional and reliable product image
* A seamless customer experience across Cloudflare products
* Minimized customer confusion
* Simplified translation process
To contribute to the documentation, visit the [contributor guide](https://developers.cloudflare.com/style-guide/contributions/).
## Available resources
* [Contributions](https://developers.cloudflare.com/style-guide/contributions/)
* [AI Tooling](https://developers.cloudflare.com/style-guide/ai-tooling/)
* [API docs content strategy](https://developers.cloudflare.com/style-guide/api-content-strategy/)
* [Guidelines for cURL commands](https://developers.cloudflare.com/style-guide/api-content-strategy/guidelines-for-curl-commands/)
* [Method types & common verbs](https://developers.cloudflare.com/style-guide/api-content-strategy/method-types-and-command-verbs/)
* [API content types](https://developers.cloudflare.com/style-guide/api-content-strategy/api-content-types/)
* [Deprecated APIs](https://developers.cloudflare.com/style-guide/api-content-strategy/api-content-types/deprecated-apis/)
* [Get started - API](https://developers.cloudflare.com/style-guide/api-content-strategy/api-content-types/get-started-api/)
* [Resources](https://developers.cloudflare.com/style-guide/api-content-strategy/api-content-types/resources/)
* [Endpoints](https://developers.cloudflare.com/style-guide/api-content-strategy/api-content-types/endpoints/)
* [Parameters](https://developers.cloudflare.com/style-guide/api-content-strategy/api-content-types/parameters/)
* [Components](https://developers.cloudflare.com/style-guide/components/)
* [Anchor heading](https://developers.cloudflare.com/style-guide/components/anchor-heading/)
* [API request](https://developers.cloudflare.com/style-guide/components/api-request/)
* [Available notifications](https://developers.cloudflare.com/style-guide/components/available-notifications/)
* [Badges](https://developers.cloudflare.com/style-guide/components/badges/)
* [Buttons](https://developers.cloudflare.com/style-guide/components/buttons/)
* [Cards](https://developers.cloudflare.com/style-guide/components/cards/)
* [CURL](https://developers.cloudflare.com/style-guide/components/curl/)
* [DashButton](https://developers.cloudflare.com/style-guide/components/dash-button/)
* [Descriptions](https://developers.cloudflare.com/style-guide/components/description/)
* [Details](https://developers.cloudflare.com/style-guide/components/details/)
* [Directory listing](https://developers.cloudflare.com/style-guide/components/directory-listing/)
* [Example](https://developers.cloudflare.com/style-guide/components/example/)
* [External resources](https://developers.cloudflare.com/style-guide/components/external-resources/)
* [Feature](https://developers.cloudflare.com/style-guide/components/feature/)
* [Feature table](https://developers.cloudflare.com/style-guide/components/feature-table/)
* [File tree](https://developers.cloudflare.com/style-guide/components/file-tree/)
* [GitHubCode](https://developers.cloudflare.com/style-guide/components/github-code/)
* [Glossary](https://developers.cloudflare.com/style-guide/components/glossary/)
* [Glossary definition](https://developers.cloudflare.com/style-guide/components/glossary-definition/)
* [Glossary tooltip](https://developers.cloudflare.com/style-guide/components/glossary-tooltip/)
* [Icons](https://developers.cloudflare.com/style-guide/components/icons/)
* [Stream](https://developers.cloudflare.com/style-guide/components/stream/)
* [Tabs](https://developers.cloudflare.com/style-guide/components/tabs/)
* [Type highlighting](https://developers.cloudflare.com/style-guide/components/type-highlighting/)
* [TypeScript example](https://developers.cloudflare.com/style-guide/components/typescript-example/)
* [Usage](https://developers.cloudflare.com/style-guide/components/usage/)
* [Inline badge](https://developers.cloudflare.com/style-guide/components/inline-badge/)
* [Link cards](https://developers.cloudflare.com/style-guide/components/link-cards/)
* [List tutorials](https://developers.cloudflare.com/style-guide/components/list-tutorials/)
* [Markdown](https://developers.cloudflare.com/style-guide/components/markdown/)
* [Package Managers](https://developers.cloudflare.com/style-guide/components/package-managers/)
* [Pages build preset](https://developers.cloudflare.com/style-guide/components/pages-build-preset/)
* [Plan](https://developers.cloudflare.com/style-guide/components/plan/)
* [Product changelog](https://developers.cloudflare.com/style-guide/components/product-changelog/)
* [Product features](https://developers.cloudflare.com/style-guide/components/product-features/)
* [Public stats](https://developers.cloudflare.com/style-guide/components/public-stats/)
* [Related product](https://developers.cloudflare.com/style-guide/components/related-product/)
* [Render](https://developers.cloudflare.com/style-guide/components/render/)
* [Resources by selector](https://developers.cloudflare.com/style-guide/components/resources-by-selector/)
* [RSSButton](https://developers.cloudflare.com/style-guide/components/rss-button/)
* [Rule ID](https://developers.cloudflare.com/style-guide/components/rule-id/)
* [Steps](https://developers.cloudflare.com/style-guide/components/steps/)
* [Subtract IP calculator](https://developers.cloudflare.com/style-guide/components/subtract-ip-calculator/)
* [Width](https://developers.cloudflare.com/style-guide/components/width/)
* [WranglerCLI](https://developers.cloudflare.com/style-guide/components/wrangler-cli/)
* [WranglerCommand](https://developers.cloudflare.com/style-guide/components/wrangler-command/)
* [WranglerConfig](https://developers.cloudflare.com/style-guide/components/wrangler-config/)
* [WranglerNamespace](https://developers.cloudflare.com/style-guide/components/wrangler-namespace/)
* [YouTube](https://developers.cloudflare.com/style-guide/components/youtube/)
* [YouTube Videos](https://developers.cloudflare.com/style-guide/components/youtube-videos/)
* [Fixtures](https://developers.cloudflare.com/style-guide/fixtures/)
* [Markdown](https://developers.cloudflare.com/style-guide/fixtures/markdown/)
* [Grammar](https://developers.cloudflare.com/style-guide/grammar/)
* [Parts of speech](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/)
* [Abbreviations](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/abbreviations/)
* [Acronyms](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/acronyms/)
* [Anthropomorphisms](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/anthropomorphisms/)
* [Capitalization](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/capitalization/)
* [Compound words](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/compound-words/)
* [Contractions](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/contractions/)
* [Nouns and pronouns](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/nouns-and-pronouns/)
* [Possessives](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/possessives/)
* [Prepositions](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/prepositions/)
* [Slang](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/slang/)
* [Punctuation marks and symbols](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/)
* [Ampersands](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/ampersands/)
* [Colons](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/colons/)
* [Commas](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/commas/)
* [Dashes](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/dashes/)
* [Exclamation points](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/exclamation-points/)
* [Percentages](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/percentages/)
* [Periods](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/periods/)
* [Quotation marks](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/quotation-marks/)
* [Semicolons](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/semicolons/)
* [Formatting](https://developers.cloudflare.com/style-guide/formatting/)
* [Code block guidelines](https://developers.cloudflare.com/style-guide/formatting/code-block-guidelines/)
* [Code conventions and format](https://developers.cloudflare.com/style-guide/formatting/code-conventions-and-format/)
* [Dates and times](https://developers.cloudflare.com/style-guide/formatting/dates-and-times/)
* [Example values](https://developers.cloudflare.com/style-guide/formatting/example-values/)
* [External references](https://developers.cloudflare.com/style-guide/formatting/external-references/)
* [File types and extensions](https://developers.cloudflare.com/style-guide/formatting/file-types-and-extensions/)
* [Footnotes](https://developers.cloudflare.com/style-guide/formatting/footnotes/)
* [Keyboard keys](https://developers.cloudflare.com/style-guide/formatting/keyboard-keys/)
* [Notes and other notation types](https://developers.cloudflare.com/style-guide/formatting/notes-and-other-notation-types/)
* [Numbers and units of measurement](https://developers.cloudflare.com/style-guide/formatting/numbers-and-units-of-measurement/)
* [Product name and pluralization](https://developers.cloudflare.com/style-guide/formatting/product-name-and-pluralization/)
* [UI elements](https://developers.cloudflare.com/style-guide/formatting/ui-elements/)
* [URLs and domain names](https://developers.cloudflare.com/style-guide/formatting/urls-and-domain-names/)
* [Structure](https://developers.cloudflare.com/style-guide/formatting/structure/)
* [Links](https://developers.cloudflare.com/style-guide/formatting/structure/links/)
* [Lists](https://developers.cloudflare.com/style-guide/formatting/structure/lists/)
* [Paragraphs and line breaks](https://developers.cloudflare.com/style-guide/formatting/structure/paragraphs-and-line-breaks/)
* [Sentence structure](https://developers.cloudflare.com/style-guide/formatting/structure/sentence-structure/)
* [Tables](https://developers.cloudflare.com/style-guide/formatting/structure/tables/)
* [Frontmatter](https://developers.cloudflare.com/style-guide/frontmatter/)
* [Banner](https://developers.cloudflare.com/style-guide/frontmatter/banner/)
* [Sidebar](https://developers.cloudflare.com/style-guide/frontmatter/sidebar/)
* [Tags](https://developers.cloudflare.com/style-guide/frontmatter/tags/)
* [Custom properties](https://developers.cloudflare.com/style-guide/frontmatter/custom-properties/)
* [Product docs content strategy](https://developers.cloudflare.com/style-guide/documentation-content-strategy/)
* [Component attributes](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/)
* [Context](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/context/)
* [Diagrams](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/diagrams/)
* [Dynamic lists](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/dynamic-lists/)
* [Examples](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/examples/)
* [Glossary entry](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/glossary-entry/)
* [Intended audience](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/intended-audience/)
* [Introduction](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/introduction/)
* [Last updated](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/last-updated/)
* [Links](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/links/)
* [Mathematical operations](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/mathematical-operations/)
* [Next steps](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/next-steps/)
* [Notes/tips/warnings](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/notes-tips-warnings/)
* [Prerequisites](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/prerequisites/)
* [Product descriptions](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/product-descriptions/)
* [Reference diagram](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/reference-diagram/)
* [Screenshots](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/screenshots/)
* [Steps/tasks/procedures](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/steps-tasks-procedures/)
* [Tables](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/tables/)
* [Titles](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/titles/)
* [Information architecture](https://developers.cloudflare.com/style-guide/documentation-content-strategy/information-architecture/)
* [Writing guidelines](https://developers.cloudflare.com/style-guide/documentation-content-strategy/writing-guidelines/)
* [Accessibility guidelines](https://developers.cloudflare.com/style-guide/documentation-content-strategy/accessibility/)
* [File conventions](https://developers.cloudflare.com/style-guide/documentation-content-strategy/file-conventions/)
* [Content types](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/)
* [3rd-party integration guide](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/3rd-party-integration-guide/)
* [Changelog](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/changelog/)
* [Concept](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/concept/)
* [Configuration](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/configuration/)
* [Design guide](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/design-guide/)
* [FAQ](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/faq/)
* [Get started](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/get-started/)
* [How to](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/how-to/)
* [Implementation guide](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/implementation-guide/)
* [Navigation](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/navigation/)
* [Overview](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/overview/)
* [Reference](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/reference/)
* [Reference architecture](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/reference-architecture/)
* [Reference architecture diagram](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/reference-architecture-diagram/)
* [How to select a content type](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/select-content-type/)
* [Troubleshooting](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/troubleshooting/)
* [Tutorial](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/tutorial/)
* [How we docs](https://developers.cloudflare.com/style-guide/how-we-docs/)
* [AI consumability](https://developers.cloudflare.com/style-guide/how-we-docs/ai-consumability/)
* [Content reviews](https://developers.cloudflare.com/style-guide/how-we-docs/reviews/)
* [Our site](https://developers.cloudflare.com/style-guide/how-we-docs/our-site/)
* [Redirects](https://developers.cloudflare.com/style-guide/how-we-docs/redirects/)
* [Image maintenance](https://developers.cloudflare.com/style-guide/how-we-docs/image-maintenance/)
* [Links](https://developers.cloudflare.com/style-guide/how-we-docs/links/)
* [Metadata](https://developers.cloudflare.com/style-guide/how-we-docs/metadata/)
* [How we AI](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/)
* [When we use AI](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/when-we-use-ai/)
* [Prompt templates](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/prompt-templates/)
* [Prompt libraries](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/prompt-libraries/)
* [Control how AI crawls your docs](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/control-ai-crawls/)
* [Examples](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/examples/)
* [CLUE](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/examples/clue/)
* [Cloudspeaker](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/examples/cloudspeaker/)
* [How we video](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-video/)
* [Why and when we use videos](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-video/why-and-when-we-use-videos/)
* [Video production workflow](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-video/video-production-workflow/)
* [Integration in docs](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-video/integration-in-docs/)
* [Maintenance](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-video/maintenance/)
---
title: Support · Cloudflare Support docs
description: Below you will find links to the relevant sections for
support-focused material.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/
md: https://developers.cloudflare.com/support/index.md
---
Below you will find links to the relevant sections for support-focused material.
* [Contacting Cloudflare Support](https://developers.cloudflare.com/support/contacting-cloudflare-support/)
* [Third-Party Software](https://developers.cloudflare.com/support/third-party-software/)
* [Troubleshooting](https://developers.cloudflare.com/support/troubleshooting/)
* [Cloudflare Status](https://developers.cloudflare.com/support/cloudflare-status/)
* [Customer Incident Management Policy](https://developers.cloudflare.com/support/customer-incident-management-policy/)
* [Disruptive Maintenance](https://developers.cloudflare.com/support/disruptive-maintenance/)
---
title: Overview · Cloudflare Tenant docs
description: The Cloudflare Tenant API is a provisioning mechanism to help
Channel and Alliance partners set up and manage Cloudflare accounts and
services for their customers.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/tenant/
md: https://developers.cloudflare.com/tenant/index.md
---
The Cloudflare Tenant API is a provisioning mechanism to help Channel and Alliance partners set up and manage Cloudflare accounts and services for their customers.
These APIs are built into our Client v4 API library to provide a streamlined onboarding and setup experience.
## Available resources
As you dive into the Tenant API, take advantage of the following resources:
* [Tenant structure](https://developers.cloudflare.com/tenant/structure/) explains some basic ideas behind the Tenant API and how it works.
* [Get started](https://developers.cloudflare.com/tenant/get-started/) provides the quickest path to get your customer accounts up and running.
* [How to](https://developers.cloudflare.com/tenant/how-to/) offers step-by-step instructions for specific tasks.
* [Reference topics](https://developers.cloudflare.com/tenant/reference/) contains detailed information about the Tenant API, including a list of available zone and account-level subscriptions.
---
title: Overview · Cloudflare Terraform docs
description: Configure Cloudflare using HashiCorp's “Infrastructure as Code”
tool, Terraform. With Cloudflare’s Terraform provider, you can manage the
Cloudflare global network using the same familiar tools you use to automate
the rest of your infrastructure. Define and store configuration in source code
repositories like GitHub, track and version changes over time, and roll back
when needed — all without needing to use the Cloudflare APIs.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/terraform/
md: https://developers.cloudflare.com/terraform/index.md
---
Configure Cloudflare using HashiCorp's “Infrastructure as Code” tool, Terraform. With [Cloudflare’s Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs), you can manage the Cloudflare global network using the same familiar tools you use to automate the rest of your infrastructure. Define and store configuration in source code repositories like GitHub, track and version changes over time, and roll back when needed — all without needing to use the Cloudflare APIs.
Report Terraform configuration issues via [GitHub](https://github.com/cloudflare/terraform-provider-cloudflare/issues/new/choose).
---
title: Overview · Cloudflare Time Services docs
description: Learn more about Cloudflare’s suite of time services.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/time-services/
md: https://developers.cloudflare.com/time-services/index.md
---
Learn more about Cloudflare’s suite of time services.
* [Network Time Protocol](https://developers.cloudflare.com/time-services/ntp/)
* [Network Time Security](https://developers.cloudflare.com/time-services/nts/)
* [Roughtime](https://developers.cloudflare.com/time-services/roughtime/)
* [Terms of use](https://developers.cloudflare.com/time-services/tos/)
---
title: Overview · Cloudflare Turnstile docs
description: Turnstile can be embedded into any website without sending traffic
through Cloudflare and works without showing visitors a CAPTCHA.
lastUpdated: 2026-01-23T18:32:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/
md: https://developers.cloudflare.com/turnstile/index.md
---
Cloudflare's smart CAPTCHA alternative.
Turnstile can be embedded into any website without sending traffic through Cloudflare and works without showing visitors a CAPTCHA.
Cloudflare issues challenges through the [Challenge Platform](https://developers.cloudflare.com/cloudflare-challenges/), which is the same underlying technology powering [Turnstile](https://developers.cloudflare.com/turnstile/).
In contrast to our Challenge page offerings, Turnstile allows you to run challenges anywhere on your site in a less-intrusive way without requiring the use of Cloudflare's CDN.
## How Turnstile works
Turnstile adapts the challenge outcome to the individual visitor or browser. First, we run a series of small non-interactive JavaScript challenges to gather signals about the visitor or browser environment.
These challenges include proof-of-work, proof-of-space, probing for web APIs, and various other challenges for detecting browser-quirks and human behavior. As a result, we can fine-tune the difficulty of the challenge to the specific request and avoid showing a visual or interactive puzzle to a user.
Note
For detailed information on Turnstile's data privacy practices, refer to the [Turnstile Privacy Addendum](https://www.cloudflare.com/turnstile-privacy-policy/).
### Widget types
Turnstile [widget types](https://developers.cloudflare.com/turnstile/concepts/widget/) include:
* **Non-interactive**: Visitors never need to interact with the widget.
* **Managed**: Visitors are presented with an interactive checkbox if they are a suspected bot.
* **Invisible**: The widget is completely hidden from the visitor.
***
## Accessibility
Turnstile is WCAG 2.1 AA compliant.
***
## Features
### Turnstile Analytics
Assess the number of challenges issued, evaluate the [challenge solve rate](https://developers.cloudflare.com/cloudflare-challenges/reference/challenge-solve-rate/), and view the metrics of issued challenges.
[Use Turnstile Analytics](https://developers.cloudflare.com/turnstile/turnstile-analytics/)
### Pre-clearance
Integrate Cloudflare challenges on single-page applications (SPAs) by allowing Turnstile to issue a Pre-Clearance cookie.
[Use Pre-clearance](< /cloudflare-challenges/concepts/clearance/#pre-clearance-support-in-turnstile>)
***
## Related products
**[Bots](https://developers.cloudflare.com/bots/)**
Cloudflare bot solutions identify and mitigate automated traffic to protect your domain from bad bots.
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Detect and mitigate Distributed Denial of Service (DDoS) attacks using Cloudflare's Autonomous Edge.
**[WAF](https://developers.cloudflare.com/waf/)**
Get automatic protection from vulnerabilities and the flexibility to create custom rules.
***
## More resources
[Plans](https://developers.cloudflare.com/turnstile/plans/)
Learn more about Turnstile's plan availability.
---
title: Use cases · Cloudflare use cases
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/use-cases/
md: https://developers.cloudflare.com/use-cases/index.md
---
* [Build AI Applications](https://developers.cloudflare.com/use-cases/ai/)
---
title: Overview · Cloudflare Vectorize docs
description: Vectorize is a globally distributed vector database that enables
you to build full-stack, AI-powered applications with Cloudflare Workers.
Vectorize makes querying embeddings — representations of values or objects
like text, images, audio that are designed to be consumed by machine learning
models and semantic search algorithms — faster, easier and more affordable.
lastUpdated: 2025-09-24T17:03:07.000Z
chatbotDeprioritize: false
tags: AI
source_url:
html: https://developers.cloudflare.com/vectorize/
md: https://developers.cloudflare.com/vectorize/index.md
---
Build full-stack AI applications with Vectorize, Cloudflare's powerful vector database.
Vectorize is a globally distributed vector database that enables you to build full-stack, AI-powered applications with [Cloudflare Workers](https://developers.cloudflare.com/workers/). Vectorize makes querying embeddings — representations of values or objects like text, images, audio that are designed to be consumed by machine learning models and semantic search algorithms — faster, easier and more affordable.
Vectorize is now Generally Available
To report bugs or give feedback, go to the [#vectorize Discord channel](https://discord.cloudflare.com). If you are having issues with Wrangler, report issues in the [Wrangler GitHub repository](https://github.com/cloudflare/workers-sdk/issues/new/choose).
For example, by storing the embeddings (vectors) generated by a machine learning model, including those built-in to [Workers AI](https://developers.cloudflare.com/workers-ai/) or by bringing your own from platforms like [OpenAI](#), you can build applications with powerful search, similarity, recommendation, classification and/or anomaly detection capabilities based on your own data.
The vectors returned can reference images stored in Cloudflare R2, documents in KV, and/or user profiles stored in D1 — enabling you to go from vector search result to concrete object all within the Workers platform, and without standing up additional infrastructure.
***
## Features
### Vector database
Learn how to create your first Vectorize database, upload vector embeddings, and query those embeddings from [Cloudflare Workers](https://developers.cloudflare.com/workers/).
[Create your Vector database](https://developers.cloudflare.com/vectorize/get-started/intro/)
### Vector embeddings using Workers AI
Learn how to use Vectorize to generate vector embeddings using Workers AI.
[Create vector embeddings using Workers AI](https://developers.cloudflare.com/vectorize/get-started/embeddings/)
### Search using Vectorize and AI Search
Learn how to automatically index your data and store it in Vectorize, then query it to generate context-aware responses using AI Search.
[Build a RAG with Vectorize](https://developers.cloudflare.com/ai-search/)
***
## Related products
**[Workers AI](https://developers.cloudflare.com/workers-ai/)**
Run machine learning models, powered by serverless GPUs, on Cloudflare’s global network.
**[R2 Storage](https://developers.cloudflare.com/r2/)**
Store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
***
## More resources
[Limits](https://developers.cloudflare.com/vectorize/platform/limits/)
Learn about Vectorize limits and how to work within them.
[Use cases](https://developers.cloudflare.com/use-cases/ai/)
Learn how you can build and deploy ambitious AI applications to Cloudflare's global network.
[Storage options](https://developers.cloudflare.com/workers/platform/storage-options/)
Learn more about the storage and database options you can build on with Workers.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, join the `#vectorize` channel to show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Developer Platform.
---
title: Overview · Cloudflare Version Management docs
description: "By using Version Management, you can:"
lastUpdated: 2025-08-20T18:25:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/version-management/
md: https://developers.cloudflare.com/version-management/index.md
---
Safely test, deploy, and roll back changes to your zone configurations using Version Management.
Enterprise-only
## Benefits
By using Version Management, you can:
* Create independent versions to make changes with no risk of impacting live traffic.
* Safely deploy changes to staging environments ahead of deploy to production.
* Quickly roll back deployed changes when issues occur.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | No | Yes |
For access, [enable](https://developers.cloudflare.com/version-management/how-to/enable/) Zone Versioning in the Cloudflare dashboard.
## Limitations
Version Management does not currently support or have limited support for the following products or features:
API Shield
* Some [API Shield](https://developers.cloudflare.com/api-shield/) configurations are not cloned when a new zone version is created.
* Customers are allowed to opt-in to remove the UI block that prevents enabling Version Management.
Authenticated Origin Pull
* [Authenticated Origin Pull](https://developers.cloudflare.com/ssl/origin-configuration/authenticated-origin-pull/) does not work with Zone Versioning.
* Accessing your domain from an allowlisted IP returns a Cloudflare 520 error.
Cache
* [Cache Reserve](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/) is intended for production use only.
* Purging the production environment purges all environments.
Cache Rules when used with Cloudflare Images
* [Image Resizing](https://developers.cloudflare.com/images/) does not work with the `additional_cacheable_ports` [Cache Rule](https://developers.cloudflare.com/cache/how-to/cache-rules/) setting and Zone Versioning.
* If you use `additional_cacheable_ports` with Image Resizing, the image will be resized every time it is requested and will result in low performance.
Workers Cache API
* [Workers Cache API](https://developers.cloudflare.com/workers/runtime-apis/cache/) does not work with Version Management.
* If you use the Workers Cache API with Zone Versioning, you might encounter unexpected caching behaviours.
China Network
* Regardless of the version deployed to production, traffic in China will always target the root zone.
* Other incompatibility issues with Access and ICP licenses.
Cloudflare API
* Version Management does not currently expose a public [API](https://developers.cloudflare.com/api/).
* Customers can only use Version Management through the [Cloudflare dashboard](https://dash.cloudflare.com/).
Domain-scoped Roles
* [Domain-scoped Roles](https://developers.cloudflare.com/fundamentals/manage-members/roles/#domain-scoped-roles) apply only to your root zone.
* Once a new version is created, these roles do not copy over and they lose access to versions.
Image Transformations
* Changes made to [Image Transformations](https://developers.cloudflare.com/images/transform-images/) are not cloned when a new zone version is created.
Network Error Logging
* [Network Error Logging](https://developers.cloudflare.com/network-error-logging/) configurations are not cloned when a new version is created.
Page Shield
* [Page Shield](https://developers.cloudflare.com/page-shield/) is not available for versioning and is only configurable under your Global Configuration.
Rules
* Version Management does not currently support the following:
* [Snippets](https://developers.cloudflare.com/rules/snippets/)
* [Compression Rules](https://developers.cloudflare.com/rules/compression-rules/)
Security Insights
* [Security Insights](https://developers.cloudflare.com/security-center/security-insights/) are not shown when Zone Versioning is enabled and the first version is deployed to production.
Terraform
* Version Management does not currently support [Terraform](https://developers.cloudflare.com/terraform/).
* Customers should either use Terraform or Version Management.
WAF Attack Score
* [WAF Attack Score](https://developers.cloudflare.com/waf/detections/attack-score/) configurations are not cloned when a new zone version is created.
Waiting Room
* [Waiting Room](https://developers.cloudflare.com/waiting-room/) users active on the site may be placed back in the queue.
* Waiting Room users in the queue may lose their place in line.
* Traffic may exceed limits.
Wrangler
* If a version has a Worker route, it might disappear when a Worker is deployed via [Wrangler](https://developers.cloudflare.com/workers/wrangler/).
* If two versions have the same custom domains, the Worker might randomly choose between them.
## Requirements
To use Version Management, the following must all be true:
* Your zone is on an Enterprise plan.
* Your zone is in an [active](https://developers.cloudflare.com/dns/zone-setups/reference/domain-status/) state.
* Your zone uses [WAF managed rules](https://developers.cloudflare.com/waf/managed-rules/).
* Your zone has migrated to use [custom rules](https://developers.cloudflare.com/waf/custom-rules/) instead of Firewall Rules (deprecated).
* Your account uses the [new WAF](https://blog.cloudflare.com/new-cloudflare-waf/) (if not, contact your account team).
* Your user account must have a Super Administrator or Administrator [role](https://developers.cloudflare.com/fundamentals/manage-members/roles/). **Zone Versioning** roles cannot create new versions.
* Your user account must have an API Key provisioned (if not, [view your API Key](https://developers.cloudflare.com/fundamentals/api/get-started/keys/#view-your-global-api-key)).
* Your user account must have API Access enabled. Refer to [control API Access](https://developers.cloudflare.com/fundamentals/api/how-to/control-api-access/) for more information.
* You must use the dashboard to manage versioning.
---
title: Videos | Cloudflare Docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/
md: https://developers.cloudflare.com/videos/index.md
---
[Application Security - Dashboard walkthrough](https://developers.cloudflare.com/videos/app-sec-dashboard/)
[In this video, learn how to navigate the Cloudflare Application Security dashboard and how to use each page to monitor, investigate, and manage security protections.](https://developers.cloudflare.com/videos/app-sec-dashboard/)
[Application Security - Get started guide](https://developers.cloudflare.com/videos/app-sec-get-started/)
[In this video, learn how to get immediate protection against the most common attacks.](https://developers.cloudflare.com/videos/app-sec-get-started/)
[China network - CDN global acceleration for Mainland China](https://developers.cloudflare.com/videos/china-network-acceleration/)
[In this video, Jess Liu discusses Cloudflares CDN Global Acceleration (formerly China Express), including solutions for high latency on dynamic content, accelerating API calls, accessing Cloudflare One services like WARP and Magic WAN from within mainland China, and securely connecting private enterprise networks.](https://developers.cloudflare.com/videos/china-network-acceleration/)
[China network - How to speed up your web traffic inside mainland China](https://developers.cloudflare.com/videos/china-network-inside-china/)
[In this video, Jess Liu walks us through the main features of Cloudflares China Network. They cover how the China Network works, including integrated caching, in-country China name servers, and compliance with ICP regulations. They also briefly discuss Cloudflare's CDN Global Acceleration (formerly China Express), an option for accelerating dynamic content that cannot be cached.](https://developers.cloudflare.com/videos/china-network-inside-china/)
[Create an API token](https://developers.cloudflare.com/videos/create-api-tokens/)
[In this video, learn the difference between account and user API tokens how to create one.](https://developers.cloudflare.com/videos/create-api-tokens/)
[Content compression](https://developers.cloudflare.com/videos/content-compression/)
[In this video, learn how Cloudflare compresses content between Cloudflare and your website visitors and between Cloudflare and your origin server.](https://developers.cloudflare.com/videos/content-compression/)
[Understand how Cloudflare works](https://developers.cloudflare.com/videos/how-cf-works/)
[Learn how Cloudflare makes the Internet safer, faster, and more reliable for everyone through the connectivity cloud.](https://developers.cloudflare.com/videos/how-cf-works/)
[Configure Full encryption mode](https://developers.cloudflare.com/videos/full-ssl-encryption/)
[In this video, learn how to configure your site to use Full encryption mode.](https://developers.cloudflare.com/videos/full-ssl-encryption/)
[Life of a Request: The First Hop - Into the Smart Network](https://developers.cloudflare.com/videos/life-of-a-request-1/)
[Imagine your request is a letter you are trying to send to a friend across the country. Instead of going through the slow, traditional postal service, Cloudflare acts as a hyper-efficient courier company with a fleet of delivery hubs all over the world.](https://developers.cloudflare.com/videos/life-of-a-request-1/)
[Life of a Request: The Fast Lane - Caching and Smart Routing](https://developers.cloudflare.com/videos/life-of-a-request-2/)
[After your request hits Cloudflare's secure network at the nearest data center where it's checked for security threats with a clean bill of health, it's time to get it to its destination at lightning speed.](https://developers.cloudflare.com/videos/life-of-a-request-2/)
[How to set up a load balancer](https://developers.cloudflare.com/videos/load-balancing/)
[Unexpected traffic spikes can crash your website, but Cloudflare Load Balancing helps keep your apps online and fast. In this step-by-step tutorial, learn how to create a public load balancer in just five steps - select a hostname, add an origin pool, attach a health monitor, choose a traffic steering method, and configure custom rules. We'll also explain the difference between public and private load balancers and guide you through using session affinity, fallback pools, and proxy modes.](https://developers.cloudflare.com/videos/load-balancing/)
[Life of a Request: The Finish Line - Serving the Content](https://developers.cloudflare.com/videos/life-of-a-request-3/)
[Once a request is routed to the nearest Cloudflare data center and then intelligently sped along its way, it moves to the final leg of the journey and how we serve content faster than ever.](https://developers.cloudflare.com/videos/life-of-a-request-3/)
[Onboard your domain to Cloudflare](https://developers.cloudflare.com/videos/onboard-domain-cf/)
[Learn how Cloudflare secures and accelerates your website using its global network and reverse proxy technology. In this video, we explain how connecting your domain to Cloudflare protects your origin server, enhances performance, and keeps your site online—even during attacks. You'll see how DNS, nameservers, and proxy status work together to route and safeguard traffic. Whether you're self-hosting or using serverless platforms like Cloudflare Workers, this guide helps you understand the onboarding process and why Cloudflare is essential for modern web infrastructure.](https://developers.cloudflare.com/videos/onboard-domain-cf/)
[Manage account members](https://developers.cloudflare.com/videos/manage-account-members/)
[In this video, learn how to define the roles and permission scope for members associated with an account.](https://developers.cloudflare.com/videos/manage-account-members/)
[SASE - The evolution of corporate networks](https://developers.cloudflare.com/videos/sase-1-evolution-corp-networks/)
[In this video, we discuss Cloudflare One, our Secure Access Service Edge (SASE) platform and how it has been designed to revolutionize the corporate network and enable companies with their Zero Trust strategy. Legacy network design is struggling to address today's challenges of security, performance, and monitoring needs. Many IT teams are trying to evolve their corporate network with point solutions and finding the lack of integration and performance an issue.](https://developers.cloudflare.com/videos/sase-1-evolution-corp-networks/)
[SASE - Stop hosting your VPN service](https://developers.cloudflare.com/videos/sase-2-stop-your-own-vpn/)
[Cloudflare's SASE platform can replace your traditional, expensive VPN appliances, which deliver poor performance for users and create more security risks than solve them. Cloudflare's Zero Trust Network Access (ZTNA) service is a more secure, highly scalable cloud solution. In this video, we look at how easily you can deploy Cloudflare to secure access to internal resources.](https://developers.cloudflare.com/videos/sase-2-stop-your-own-vpn/)
[SASE - Secure remote access to your critical infrastructure](https://developers.cloudflare.com/videos/sase-3-secure-remote-access/)
[In this video, learn how Cloudflare's SASE platform can provide highly secure access to your critical infrastructure by leveraging a modern ZTNA service to implement Zero Trust principles Applications, databases and their servers are running in a variety of locations from on-premises data centers to cloud hyperscalers, making the need to secure administrative access more important than ever.](https://developers.cloudflare.com/videos/sase-3-secure-remote-access/)
[SASE - Connect and secure from any network to anywhere](https://developers.cloudflare.com/videos/sase-4-connect-secure/)
[Build your new corporate network with Cloudflare, connecting any network into our modern SASE platform and secure applications, users, devices and your company data. In this video, you will learn all of the different methods of connecting networks to Cloudflare and what services can be used to improve security and performance.](https://developers.cloudflare.com/videos/sase-4-connect-secure/)
[Manage SSL version or cipher mismatch errors](https://developers.cloudflare.com/videos/ssl-cipher-mismatch/)
[In this video, learn how to manage an SSL version or cipher mismatch error.](https://developers.cloudflare.com/videos/ssl-cipher-mismatch/)
[SASE - Protect your users from Internet risks](https://developers.cloudflare.com/videos/sase-5-protect-users/)
[The Internet has become part of your corporate network; however, browsing the web comes with hidden risks including malware, phishing attacks, and malicious websites. In this video, we will explore how Cloudflare's Secure Web Gateway (SWG) helps keep users safe by filtering and inspecting Internet traffic in real time. Whether you are protecting a remote workforce or securing an entire organization, Cloudflare ensures that users can access the web securely — without sacrificing speed or productivity.](https://developers.cloudflare.com/videos/sase-5-protect-users/)
[SSL/TLS concepts](https://developers.cloudflare.com/videos/strict-ssl-concepts/)
[In this video, learn the key concepts relevant to Cloudflare SSL/TLS.](https://developers.cloudflare.com/videos/strict-ssl-concepts/)
[The Online Address Book](https://developers.cloudflare.com/videos/the-online-address-book/)
[This video focuses on the first prerequisite for using a tunnel, a domain name. It uses the metaphor of an online address book to explain DNS and how Cloudflare manages your domain.](https://developers.cloudflare.com/videos/the-online-address-book/)
[Configure Strict encryption mode](https://developers.cloudflare.com/videos/strict-ssl-encryption/)
[In this video, learn how to configure your site to use Strict (SSL-Only Origin Pull) encryption mode.](https://developers.cloudflare.com/videos/strict-ssl-encryption/)
[WARP - Understand Cloudflare WARP basics](https://developers.cloudflare.com/videos/warp-1-basics/)
[In this episode, we explain the core features of the Cloudflare WARP client and how to troubleshoot common issues. After watching, you will have an understanding of the GUI, the differences between the consumer and corporate WARP, device profiles, the various operating modes of WARP, split tunneling, and more.](https://developers.cloudflare.com/videos/warp-1-basics/)
[What is Cloudflare Tunnel?](https://developers.cloudflare.com/videos/what-is-cf-tunnel/)
[Learn how Cloudflare Tunnel is like a private, secure pathway from your computer to the Internet, so you don't have to leave the front door (your network) wide open.](https://developers.cloudflare.com/videos/what-is-cf-tunnel/)
[WARP - Understand Cloudflare WARP through diagnostic logs](https://developers.cloudflare.com/videos/warp-2-diagnostic-logs/)
[In this more advanced episode, we explain how to use warp-diag files to identify and resolve connection issues with the WARP client. You will learn how to locate and interpret three key files - warp-status, warp-settings, and daemonlog. The video also provides troubleshooting tips, including specific keyword searches and guidance on how to cross-reference logs to identify a bigger picture of the problem.](https://developers.cloudflare.com/videos/warp-2-diagnostic-logs/)
---
title: Overview · Cloudflare Web Application Firewall (WAF) docs
description: The Cloudflare Web Application Firewall (WAF) provides automatic
protection from vulnerabilities and the flexibility to create custom rules.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/
md: https://developers.cloudflare.com/waf/index.md
---
Get automatic protection from vulnerabilities and the flexibility to create custom rules.
Available on all plans
The Cloudflare Web Application Firewall (Cloudflare WAF) checks incoming web and API requests and filters undesired traffic based on sets of rules called rulesets. The matching engine that powers the WAF rules supports the wirefilter syntax using the [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/).
Learn how to [get started](https://developers.cloudflare.com/waf/get-started/).
***
## Features
### Custom rules
Create your own custom rules to protect your website and your APIs from malicious incoming traffic. Use advanced features like [WAF attack score](https://developers.cloudflare.com/waf/detections/attack-score/) and [malicious uploads detection](https://developers.cloudflare.com/waf/detections/malicious-uploads/) in your custom rules.
[Use Custom rules](https://developers.cloudflare.com/waf/custom-rules/)
### Rate limiting rules
Define rate limits for incoming requests matching an expression, and the action to take when those rate limits are reached.
[Use Rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/)
### Managed rules
Enable the pre-configured managed rulesets to get immediate protection. These rulesets are [regularly updated](https://developers.cloudflare.com/waf/change-log/), offering advanced zero-day vulnerability protections, and you can adjust their behavior.
[Use Managed rules](https://developers.cloudflare.com/waf/managed-rules/)
### Account-level configuration
Enterprise-only paid add-on
Create and deploy rulesets to multiple Enterprise zones.
[Use Account-level configuration](https://developers.cloudflare.com/waf/account/)
### Security Events
Review mitigated requests (rule matches) using an intuitive interface. Tailor your security configurations based on sampled logs.
[Explore Security Events](https://developers.cloudflare.com/waf/analytics/security-events/)
### Security Analytics
Displays information about all incoming HTTP requests, including those not affected by security measures.
[Explore Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/)
***
## Related products
**[DDoS Protection](https://developers.cloudflare.com/ddos-protection/)**
Cloudflare DDoS protection secures websites, applications, and entire networks while ensuring the performance of legitimate traffic is not compromised.
**[Page Shield](https://developers.cloudflare.com/page-shield/)**
Page Shield is a comprehensive client-side security solution to ensure the safety of your website visitors' browser environment.
**[Bots](https://developers.cloudflare.com/bots/)**
Cloudflare bot solutions identify and mitigate automated traffic to protect your domain from bad bots.
---
title: Cloudflare Waiting Room · Cloudflare Waiting Room docs
description: Cloudflare Waiting Room allows you to route excess users of your
website to a customized waiting room, helping preserve customer experience and
protect origin servers from being overwhelmed with requests.
lastUpdated: 2024-09-20T15:57:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/
md: https://developers.cloudflare.com/waiting-room/index.md
---
A virtual waiting room to manage peak traffic.
Business and above
Cloudflare Waiting Room allows you to route excess users of your website to a customized waiting room, helping preserve customer experience and protect origin servers from being overwhelmed with requests.
***
## Benefits
Waiting Room protects your origin server by preventing surges in legitimate traffic that may overload your origin.
Waiting Room also benefits your visitors by:
* Keeping your application online and preventing them from reaching error pages.
* Showing estimated wait times that are continuously updated.
* Opening up new spots more quickly by tracking dynamic inflow and [outflow](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/#session-duration).
* Remembering each visitor's status to prevent someone from losing their place in line or having to re-queue if they leave your site.
* Appearing in your own [branding and style](https://developers.cloudflare.com/waiting-room/how-to/customize-waiting-room/), which enhances trust and lets you provide additional information as needed.
***
## Features
### Scheduled Event
Customize the behavior of a waiting room for a specific period of time.
[Use Scheduled Event](https://developers.cloudflare.com/waiting-room/additional-options/create-events/)
### Waiting Room Rules
Create rules to indicate specific traffic or areas of your site or application that you do not want a waiting room to apply to.
[Use Waiting Room Rules](https://developers.cloudflare.com/waiting-room/additional-options/waiting-room-rules/)
### Waiting Room Analytics
Get insights into the traffic going through your waiting room.
[Use Waiting Room Analytics](https://developers.cloudflare.com/waiting-room/waiting-room-analytics/)
### Additional hostname and path coverage
Apply a single waiting room to multiple hostnames and paths within the same zone.
[Use Additional hostname and path coverage](https://developers.cloudflare.com/waiting-room/how-to/place-waiting-room/)
***
## Related products
**[Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)**
Cloudflare for SaaS allows you to extend the security and performance benefits of Cloudflare’s network to your customers via their own custom or vanity domains.
**[Rules](https://developers.cloudflare.com/rules/)**
Cloudflare Rules allows you to make adjustments to requests and responses, configure Cloudflare settings, and trigger specific actions for matching requests.
**[SSL/TLS](https://developers.cloudflare.com/ssl/)**
Cloudflare SSL/TLS encrypts your web traffic to prevent data theft and other tampering.
***
## Availability
The following customers have access to Cloudflare Waiting Room:
* Those qualified under [Project Fair Shot](https://www.cloudflare.com/fair-shot/)
* Customers on a Business or Enterprise plan
Access to certain features depends on a customer's [plan type](https://developers.cloudflare.com/waiting-room/plans/).
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
***
## Prerequisites
* [Cloudflare’s CDN](https://developers.cloudflare.com/cache/) is required to use the Waiting Room feature.
* Configure a [proxied DNS record](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/) or a [proxied load balancer](https://developers.cloudflare.com/load-balancing/understand-basics/proxy-modes/) for the waiting room’s hostname. A DNS record is not auto-configured after a waiting room is created.
* Visitors must enable cookies. Refer to [Waiting Room cookies](https://developers.cloudflare.com/waiting-room/reference/waiting-room-cookie/) for information on how cookies are used in Cloudflare Waiting Room.
***
## More resources
[Pricing](https://www.cloudflare.com/plans/)
Explore pricing options for Waiting Room.
---
title: Overview · Cloudflare WARP client docs
description: The Cloudflare WARP client allows individuals to have a faster,
more secure, and more private experience online. The WARP client sits between
your device and the Internet, and has several connection modes to better suit
different needs.
lastUpdated: 2025-10-21T14:33:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/warp-client/
md: https://developers.cloudflare.com/warp-client/index.md
---
Connect to the Internet faster and in a more secure way.
Available on all plans
The Cloudflare WARP client allows individuals to have a faster, more secure, and more private experience online. The WARP client sits between your device and the Internet, and has several connection modes to better suit different needs.
Consumer WARP
This documentation is for the consumer version of WARP. If you are using WARP with Cloudflare Zero Trust, refer to the [Zero Trust documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/).
## Features
### WARP modes
The WARP client has several modes to better suit your connection needs.
[Use WARP modes](https://developers.cloudflare.com/warp-client/warp-modes/)
### OS clients
WARP is available to several operating systems, including iOS and Android.
[Use OS clients](https://developers.cloudflare.com/warp-client/get-started/)
***
## Related products
**[1.1.1.1](https://developers.cloudflare.com/1.1.1.1/)**
1.1.1.1 is Cloudflare’s public DNS resolver. It offers a fast and private way to browse the Internet.
**[WARP for Zero Trust](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)**
The enterprise version of WARP allows organizations to apply security policies to corporate devices.
---
title: Overview · Cloudflare Web Analytics docs
description: Cloudflare Web Analytics helps you understand the performance of
your web pages as experienced by your site visitors.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/web-analytics/
md: https://developers.cloudflare.com/web-analytics/index.md
---
Get vital web analytics for your website without compromising user privacy.
Available on all plans
Cloudflare Web Analytics helps you understand the performance of your web pages as experienced by your site visitors.
***
## Features
### Filters
Use filters to refine the data displayed in Web Analytics.
[Use Filters](https://developers.cloudflare.com/web-analytics/configuration-options/filters/)
### Rules
Use rules to configure tracking of Web Analytics for specific websites or paths.
[Use Rules](https://developers.cloudflare.com/web-analytics/configuration-options/rules)
### Dimensions
Use dimensions to categorize and organize various metrics or data types effectively.
[Use Dimensions](https://developers.cloudflare.com/web-analytics/data-metrics/dimensions)
***
## Related products
**[Analytics](https://developers.cloudflare.com/analytics/)**
Cloudflare visualizes the metadata collected by our products in the Cloudflare dashboard.
**[Speed](https://developers.cloudflare.com/speed/)**
Speed allows you to assess the performance of your website and get recommendations of Cloudflare products to enhance the website performance.
***
## More resources
[Resource hub](https://www.cloudflare.com/application-services/products/analytics/)
Refer to our latest resources to learn more about security, performance and reliability.
[Cloudflare blog](https://blog.cloudflare.com/privacy-first-web-analytics/)
Read articles about the latest updates about Web Analytics.
---
title: Overview · Cloudflare Web3 docs
description: Cloudflare offers gateways to various networks to help Web3
developers do what they do best, develop applications without having to worry
about running infrastructure.
lastUpdated: 2025-03-14T16:33:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/web3/
md: https://developers.cloudflare.com/web3/index.md
---
Develop Web3 applications without having to worry about running infrastructure
Add-on feature
Web3, or the distributed web, is a set of technologies that enables hosting of content and web applications in a serverless manner by leveraging distributed systems and consensus protocols.
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
***
## Features
### IPFS Gateway
Paid add-on
Provides a read-only, HTTP-accessible interface to the [Interplanetary File System (IPFS)](https://developers.cloudflare.com/web3/ipfs-gateway/concepts/ipfs/).
[Use IPFS Gateway](https://developers.cloudflare.com/web3/ipfs-gateway/)
### Ethereum Gateway
Paid add-on
Gives you read and write access to the [Ethereum network](https://developers.cloudflare.com/web3/ethereum-gateway/concepts/ethereum/) without installing any software on your computer.
[Use Ethereum Gateway](https://developers.cloudflare.com/web3/ethereum-gateway/)
***
## Benefits
Cloudflare's Web3 gateways provide HTTP-accessible interfaces to Web3 networks, providing:
* **Ease of access**: Access content from Web3 networks without installing or running any special software.
* **Security**: Get the protection benefits of Cloudflare's global anycast network for [enhanced security](https://blog.cloudflare.com/cloudflare-thwarts-17-2m-rps-ddos-attack-the-largest-ever-reported/).
* **Reduced maintenance**: Cloudflare — and not your developers — maintains and monitors security, reliability, and performance.
* **Reliability**: Cloudflare's global anycast network provides a high level of [reliability and availability](https://www.cloudflare.com/network/).
* **Performance**: With Cloudflare's edge network of data centers in [hundreds of cities worldwide](https://www.cloudflare.com/network/), content can be cached and served from data centers close to your end users.
***
## More resources
[Plans](https://www.cloudflare.com/plans/#overview)
Compare available Cloudflare plans
[Pricing](https://dash.cloudflare.com/?to=/:account/:zone/web3/)
Explore pricing options for Web3 Gateways in the dashboard
---
title: Overview · Cloudflare Workers docs
description: "With Cloudflare Workers, you can expect to:"
lastUpdated: 2026-01-26T13:23:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/workers/
md: https://developers.cloudflare.com/workers/index.md
---
A serverless platform for building, deploying, and scaling apps across [Cloudflare's global network](https://www.cloudflare.com/network/) with a single command — no infrastructure to manage, no complex configuration
With Cloudflare Workers, you can expect to:
* Deliver fast performance with high reliability anywhere in the world
* Build full-stack apps with your framework of choice, including [React](https://developers.cloudflare.com/workers/framework-guides/web-apps/react/), [Vue](https://developers.cloudflare.com/workers/framework-guides/web-apps/vue/), [Svelte](https://developers.cloudflare.com/workers/framework-guides/web-apps/sveltekit/), [Next](https://developers.cloudflare.com/workers/framework-guides/web-apps/nextjs/), [Astro](https://developers.cloudflare.com/workers/framework-guides/web-apps/astro/), [React Router](https://developers.cloudflare.com/workers/framework-guides/web-apps/react-router/), [and more](https://developers.cloudflare.com/workers/framework-guides/)
* Use your preferred language, including [JavaScript](https://developers.cloudflare.com/workers/languages/javascript/), [TypeScript](https://developers.cloudflare.com/workers/languages/typescript/), [Python](https://developers.cloudflare.com/workers/languages/python/), [Rust](https://developers.cloudflare.com/workers/languages/rust/), [and more](https://developers.cloudflare.com/workers/runtime-apis/webassembly/)
* Gain deep visibility and insight with built-in [observability](https://developers.cloudflare.com/workers/observability/logs/)
* Get started for free and grow with flexible [pricing](https://developers.cloudflare.com/workers/platform/pricing/), affordable at any scale
Get started with your first project:
[Deploy a template](https://dash.cloudflare.com/?to=/:account/workers-and-pages/templates)
[Deploy with Wrangler CLI](https://developers.cloudflare.com/workers/get-started/guide/)
***
## Build with Workers
#### Front-end applications
Deploy [static assets](https://developers.cloudflare.com/workers/static-assets/) to Cloudflare's [CDN & cache](https://developers.cloudflare.com/cache/) for fast rendering
#### Back-end applications
Build APIs and connect to data stores with [Smart Placement](https://developers.cloudflare.com/workers/configuration/placement/) to optimize latency
#### Serverless AI inference
Run LLMs, generate images, and more with [Workers AI](https://developers.cloudflare.com/workers-ai/)
#### Background jobs
Schedule [cron jobs](https://developers.cloudflare.com/workers/configuration/cron-triggers/), run durable [Workflows](https://developers.cloudflare.com/workflows/), and integrate with [Queues](https://developers.cloudflare.com/queues/)
#### Observability & monitoring
Monitor performance, debug issues, and analyze traffic with [real-time logs](https://developers.cloudflare.com/workers/observability/logs/) and [analytics](https://developers.cloudflare.com/workers/observability/metrics-and-analytics/)
***
## Integrate with Workers
Connect to external services like databases, APIs, and storage via [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/), enabling functionality with just a few lines of code:
**Storage**
**[Durable Objects](https://developers.cloudflare.com/durable-objects/)**
Scalable stateful storage for real-time coordination.
**[D1](https://developers.cloudflare.com/d1/)**
Serverless SQL database built for fast, global queries.
**[KV](https://developers.cloudflare.com/kv/)**
Low-latency key-value storage for fast, edge-cached reads.
**[Queues](https://developers.cloudflare.com/queues/)**
Guaranteed delivery with no charges for egress bandwidth.
**[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)**
Connect to your external database with accelerated queries, cached at the edge.
**Compute**
**[Workers AI](https://developers.cloudflare.com/workers-ai/)**
Machine learning models powered by serverless GPUs.
**[Workflows](https://developers.cloudflare.com/workflows/)**
Durable, long-running operations with automatic retries.
**[Vectorize](https://developers.cloudflare.com/vectorize/)**
Vector database for AI-powered semantic search.
**[R2](https://developers.cloudflare.com/r2/)**
Zero-egress object storage for cost-efficient data access.
**[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)**
Programmatic serverless browser instances.
**Media**
**[Cache / CDN](https://developers.cloudflare.com/cache/)**
Global caching for high-performance, low-latency delivery.
**[Images](https://developers.cloudflare.com/images/)**
Streamlined image infrastructure from a single API.
***
Want to connect with the Workers community? [Join our Discord](https://discord.cloudflare.com)
---
title: Overview · Cloudflare Workers AI docs
description: Workers AI allows you to run AI models in a serverless way, without
having to worry about scaling, maintaining, or paying for unused
infrastructure. You can invoke models running on GPUs on Cloudflare's network
from your own code — from Workers, Pages, or anywhere via the Cloudflare API.
lastUpdated: 2025-08-20T18:47:44.000Z
chatbotDeprioritize: false
tags: AI
source_url:
html: https://developers.cloudflare.com/workers-ai/
md: https://developers.cloudflare.com/workers-ai/index.md
---
Run machine learning models, powered by serverless GPUs, on Cloudflare's global network.
Available on Free and Paid plans
Workers AI allows you to run AI models in a serverless way, without having to worry about scaling, maintaining, or paying for unused infrastructure. You can invoke models running on GPUs on Cloudflare's network from your own code — from [Workers](https://developers.cloudflare.com/workers/), [Pages](https://developers.cloudflare.com/pages/), or anywhere via [the Cloudflare API](https://developers.cloudflare.com/api/resources/ai/methods/run/).
Workers AI gives you access to:
* **50+ [open-source models](https://developers.cloudflare.com/workers-ai/models/)**, available as a part of our model catalog
* Serverless, **pay-for-what-you-use** [pricing model](https://developers.cloudflare.com/workers-ai/platform/pricing/)
* All as part of a **fully-featured developer platform**, including [AI Gateway](https://developers.cloudflare.com/ai-gateway/), [Vectorize](https://developers.cloudflare.com/vectorize/), [Workers](https://developers.cloudflare.com/workers/) and more...
[Get started](https://developers.cloudflare.com/workers-ai/get-started)
[Watch a Workers AI demo](https://youtu.be/cK_leoJsBWY?si=4u6BIy_uBOZf9Ve8)
Custom requirements
If you have custom requirements like private custom models or higher limits, complete the [Custom Requirements Form](https://forms.gle/axnnpGDb6xrmR31T6). Cloudflare will contact you with next steps.
Workers AI is now Generally Available
To report bugs or give feedback, go to the [#workers-ai Discord channel](https://discord.cloudflare.com). If you are having issues with Wrangler, report issues in the [Wrangler GitHub repository](https://github.com/cloudflare/workers-sdk/issues/new/choose).
***
## Features
### Models
Workers AI comes with a curated set of popular open-source models that enable you to do tasks such as image classification, text generation, object detection and more.
[Browse models](https://developers.cloudflare.com/workers-ai/models/)
***
## Related products
**[AI Gateway](https://developers.cloudflare.com/ai-gateway/)**
Observe and control your AI applications with caching, rate limiting, request retries, model fallback, and more.
**[Vectorize](https://developers.cloudflare.com/vectorize/)**
Build full-stack AI applications with Vectorize, Cloudflare’s vector database. Adding Vectorize enables you to perform tasks such as semantic search, recommendations, anomaly detection or can be used to provide context and memory to an LLM.
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Pages](https://developers.cloudflare.com/pages/)**
Create full-stack applications that are instantly deployed to the Cloudflare global network.
**[R2](https://developers.cloudflare.com/r2/)**
Store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
**[D1](https://developers.cloudflare.com/d1/)**
Create new serverless SQL databases to query from your Workers and Pages projects.
**[Durable Objects](https://developers.cloudflare.com/durable-objects/)**
A globally distributed coordination API with strongly consistent storage.
**[KV](https://developers.cloudflare.com/kv/)**
Create a global, low-latency, key-value data storage.
***
## More resources
[Get started](https://developers.cloudflare.com/workers-ai/get-started/workers-wrangler/)
Build and deploy your first Workers AI application.
[Plans](https://developers.cloudflare.com/workers-ai/platform/pricing/)
Learn about Free and Paid plans.
[Limits](https://developers.cloudflare.com/workers-ai/platform/limits/)
Learn about Workers AI limits.
[Use cases](https://developers.cloudflare.com/use-cases/ai/)
Learn how you can build and deploy ambitious AI applications to Cloudflare's global network.
[Storage options](https://developers.cloudflare.com/workers/platform/storage-options/)
Learn which storage option is best for your project.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, share what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Workers.
---
title: Overview · Cloudflare Workers VPC
description: Securely connect your private cloud to Cloudflare to build cross-cloud apps.
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/workers-vpc/
md: https://developers.cloudflare.com/workers-vpc/index.md
---
Securely connect your private cloud to Cloudflare to build cross-cloud apps.
Available on Free and Paid plans
Workers VPC allows you to connect your Workers to your private APIs and services in external clouds (AWS, Azure, GCP, on-premise, etc.) that are not accessible from the public Internet.
With Workers VPC, you can configure a [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) to establish secure, private connections from your private networks to Cloudflare. Then, you can configure a [VPC Service](https://developers.cloudflare.com/workers-vpc/configuration/vpc-services/) for each service in the external private network you need to connect to, and use [VPC Service bindings](https://developers.cloudflare.com/workers-vpc/api/) to connect from Workers.
Note
Workers VPC is currently in beta. Features and APIs may change before general availability. While in beta, Workers VPC is available for free to all Workers plans.
* index.ts
```ts
export default {
async fetch(request, env, ctx) {
// Access your private API through the service binding
const response = await env.PRIVATE_API.fetch(
"http://internal-api.company.local/data",
);
// Process the response from your private network
const data = await response.json();
return new Response(JSON.stringify(data), {
headers: { "content-type": "application/json" },
});
},
};
```
* wrangler.jsonc
```json
{
"$schema": "node_modules/wrangler/config-schema.json",
"name": "WORKER-NAME",
"main": "src/index.ts",
"compatibility_date": "2025-02-04",
"vpc_services": [
{
"binding": "PRIVATE_API",
"service_id": "ENTER_SERVICE_ID",
"remote": true
}
]
}
```
## Use cases
### Access private APIs from Workers applications
Deploy APIs or full-stack applications to Workers that connect to private authentication services, CMS systems, internals APIs, and more. Your Workers applications run globally with optimized access to the backend services of your private network.
### API gateway
Route requests to internal microservices in your private network based on URL paths. Centralize access control and load balancing for multiple private services on Workers.
### Internal tooling, agents, dashboards
Build employee-facing applications and MCP servers that aggregate data from multiple private services. Create unified dashboards, admin panels, and internal tools without exposing backend systems.
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)**
Connect to PostgreSQL and MySQL databases from Workers with connection pooling and caching built-in, available to all Workers plans.
---
title: Overview · Cloudflare Workflows docs
description: >-
With Workflows, you can build applications that chain together multiple steps,
automatically retry failed tasks,
and persist state for minutes, hours, or even weeks - with no infrastructure
to manage.
lastUpdated: 2025-12-11T17:16:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/workflows/
md: https://developers.cloudflare.com/workflows/index.md
---
Build durable multi-step applications on Cloudflare Workers with Workflows.
Available on Free and Paid plans
With Workflows, you can build applications that chain together multiple steps, automatically retry failed tasks, and persist state for minutes, hours, or even weeks - with no infrastructure to manage.
Use Workflows to build reliable AI applications, process data pipelines, manage user lifecycle with automated emails and trial expirations, and implement human-in-the-loop approval systems.
**Workflows give you:**
* Durable multi-step execution without timeouts
* The ability to pause for external events or approvals
* Automatic retries and error handling
* Built-in observability and debugging
## Example
An image processing workflow that fetches from R2, generates an AI description, waits for approval, then publishes:
```ts
export class ImageProcessingWorkflow extends WorkflowEntrypoint {
async run(event: WorkflowEvent, step: WorkflowStep) {
const imageData = await step.do('fetch image', async () => {
const object = await this.env.BUCKET.get(event.params.imageKey);
return await object.arrayBuffer();
});
const description = await step.do('generate description', async () => {
const imageArray = Array.from(new Uint8Array(imageData));
return await this.env.AI.run('@cf/llava-hf/llava-1.5-7b-hf', {
image: imageArray,
prompt: 'Describe this image in one sentence',
max_tokens: 50,
});
});
await step.waitForEvent('await approval', {
event: 'approved',
timeout: '24 hours',
});
await step.do('publish', async () => {
await this.env.BUCKET.put(`public/${event.params.imageKey}`, imageData);
});
}
}
```
[Get started](https://developers.cloudflare.com/workflows/get-started/guide/)
[Browse the examples](https://developers.cloudflare.com/workflows/examples/)
***
## Features
### Durable step execution
Break complex operations into durable steps with automatic retries and error handling.
[Learn about steps](https://developers.cloudflare.com/workflows/build/workers-api/)
### Sleep and scheduling
Pause workflows for seconds, hours, or days with `step.sleep()` and `step.sleepUntil()`.
[Add delays](https://developers.cloudflare.com/workflows/build/sleeping-and-retrying/)
### Wait for external events
Wait for webhooks, user input, or external system responses before continuing execution.
[Handle events](https://developers.cloudflare.com/workflows/build/events-and-parameters/)
### Workflow lifecycle management
Trigger, pause, resume, and terminate workflow instances programmatically or via API.
[Manage instances](https://developers.cloudflare.com/workflows/build/trigger-workflows/)
***
## Related products
**[Workers](https://developers.cloudflare.com/workers/)**
Build serverless applications and deploy instantly across the globe for exceptional performance, reliability, and scale.
**[Pages](https://developers.cloudflare.com/pages/)**
Deploy dynamic front-end applications in record time.
***
## More resources
[Pricing](https://developers.cloudflare.com/workflows/reference/pricing/)
Learn more about how Workflows is priced.
[Limits](https://developers.cloudflare.com/workflows/reference/limits/)
Learn more about Workflow limits, and how to work within them.
[Storage options](https://developers.cloudflare.com/workers/platform/storage-options/)
Learn more about the storage and database options you can build on with Workers.
[Developer Discord](https://discord.cloudflare.com)
Connect with the Workers community on Discord to ask questions, show what you are building, and discuss the platform with other developers.
[@CloudflareDev](https://x.com/cloudflaredev)
Follow @CloudflareDev on Twitter to learn about product announcements, and what is new in Cloudflare Developer Platform.
---
title: Overview · Cloudflare Zaraz docs
description: Cloudflare Zaraz gives you complete control over third-party tools
and services for your website, and allows you to offload them to Cloudflare's
edge, improving the speed and security of your website. With Cloudflare Zaraz
you can load tools such as analytics tools, advertising pixels and scripts,
chatbots, marketing automation tools, and more, in the most optimized way.
lastUpdated: 2025-08-20T18:47:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/zaraz/
md: https://developers.cloudflare.com/zaraz/index.md
---
Offload third-party tools and services to the cloud and improve the speed and security of your website.
Available on all plans
Cloudflare Zaraz gives you complete control over third-party tools and services for your website, and allows you to offload them to Cloudflare's edge, improving the speed and security of your website. With Cloudflare Zaraz you can load tools such as analytics tools, advertising pixels and scripts, chatbots, marketing automation tools, and more, in the most optimized way.
Cloudflare Zaraz is built for speed, privacy, and security, and you can use it to load as many tools as you need, with a near-zero performance hit.
***
## Features
### Third-party tools
You can add many third-party tools to Zaraz, and offload them from your website.
[Use Third-party tools](https://developers.cloudflare.com/zaraz/get-started/)
### Custom Managed Components
You can add Custom Managed Components to Zaraz and run them as a tool.
[Use Custom Managed Components](https://developers.cloudflare.com/zaraz/advanced/load-custom-managed-component/)
### Web API
Zaraz provides a client-side web API that you can use anywhere inside the `` tag of a page.
[Use Web API](https://developers.cloudflare.com/zaraz/web-api/)
### Consent management
Zaraz provides a Consent Management platform to help you address and manage required consents.
[Use Consent management](https://developers.cloudflare.com/zaraz/consent-management/)
***
## More resources
[Discord Channel](https://discord.cloudflare.com)
If you have any comments, questions, or bugs to report, contact the Zaraz team on their Discord channel.
[Community Forum](https://community.cloudflare.com/c/developers/zaraz/67)
Engage with other users and the Zaraz team on Cloudflare support forum.
---
title: 404 - Page Not Found · Cloudflare 1.1.1.1 docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/404/
md: https://developers.cloudflare.com/1.1.1.1/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Other ways to use 1.1.1.1 · Cloudflare 1.1.1.1 docs
description: There are many other ways to use 1.1.1.1 beyond the traditional set
up in operating systems and routers.
lastUpdated: 2025-08-13T12:32:09.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/1.1.1.1/additional-options/
md: https://developers.cloudflare.com/1.1.1.1/additional-options/index.md
---
There are many other ways to use 1.1.1.1 beyond the traditional set up in operating systems and routers.
* [DNS in Google Sheets](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-in-google-sheets/)
* [DNS over Discord](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-over-discord/)
* [DNS over Tor](https://developers.cloudflare.com/1.1.1.1/additional-options/dns-over-tor/)
---
title: Verify connection · Cloudflare 1.1.1.1 docs
description: After setting up 1.1.1.1, you can check if you are correctly
connected to Cloudflare's resolver.
lastUpdated: 2026-01-29T12:03:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/check/
md: https://developers.cloudflare.com/1.1.1.1/check/index.md
---
After setting up `1.1.1.1`, you can check if you are correctly connected to Cloudflare's resolver.
1. Open a web browser on a configured device (smartphone or computer) or on a device connected to your configured router.
2. Enter [https://1.1.1.1/help](https://one.one.one.one/help) on the browser address bar.
Wait for the page to load and run its tests. The page will present you a summary of the type of connection you have to `1.1.1.1`, as well as the Cloudflare data center you are connected to.
---
title: Encrypt DNS traffic · Cloudflare 1.1.1.1 docs
description: Traditionally, DNS queries and replies are performed over
plaintext. They are sent over the Internet without any kind of encryption or
protection, even when you are accessing a secured website. This has a great
impact on security and privacy, as these queries might be subject to
surveillance, spoofing and tracking by malicious actors, advertisers, ISPs,
and others.
lastUpdated: 2024-11-19T17:02:12.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/encryption/
md: https://developers.cloudflare.com/1.1.1.1/encryption/index.md
---
Traditionally, DNS queries and replies are performed over plaintext. They are sent over the Internet without any kind of encryption or protection, even when you are accessing a secured website. This has a great impact on security and privacy, as these queries might be subject to surveillance, spoofing and tracking by malicious actors, advertisers, ISPs, and others.
To prevent untrustworthy entities from interpreting and manipulating your queries, 1.1.1.1 supports different standards to encrypt plaintext DNS traffic and improve DNS privacy:
* [DNS over TLS (DoT)](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-tls/)
* [DNS over HTTPS (DoH)](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/)
* [Oblivious DNS over HTTPS (ODoH)](https://developers.cloudflare.com/1.1.1.1/encryption/oblivious-dns-over-https/)
You can also [configure your browser](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/encrypted-dns-browsers/) to secure your DNS queries.
If you need to secure connections in your smartphone, refer to 1.1.1.1 [iOS](https://developers.cloudflare.com/1.1.1.1/setup/ios/) or [Android](https://developers.cloudflare.com/1.1.1.1/setup/android/) apps.
---
title: FAQ · Cloudflare 1.1.1.1 docs
description: Find answers to common questions about Cloudflare's 1.1.1.1 DNS
resolver, including setup, privacy features, IPv6 support, and troubleshooting
tips.
lastUpdated: 2025-05-14T18:16:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/faq/
md: https://developers.cloudflare.com/1.1.1.1/faq/index.md
---
Below you will find answers to our most commonly asked questions. If you cannot find the answer you are looking for, refer to the [community page](https://community.cloudflare.com/) to explore more resources.
## What is 1.1.1.1?
1.1.1.1 is Cloudflare's fast and secure DNS resolver. When you request to visit an application like `cloudflare.com`, your computer needs to know which server to connect you to so that it can load the application. Computers do not know how to do this name to address translation, so they ask a specialized server to do it for them.
This specialized server is called a DNS recursive resolver. The resolver's job is to find the address for a given name, like `2400:cb00:2048:1::c629:d7a2` for `cloudflare.com`, and return it to the computer that asked for it.
Computers are configured to talk to specific DNS resolvers, identified by IP address. Usually the configuration is managed by your ISP (like Comcast or AT\&T) if you are on your home or wireless Internet, and by your network administrator if you are connected to the office Internet. You can also change the configured DNS resolver your computer talks to yourself.
## How can I check if my computer / smartphone / tablet is connected to 1.1.1.1?
Visit [1.1.1.1/help](https://one.one.one.one/help) to make sure your system is connected to 1.1.1.1 and that it is working.
## What do DNS resolvers do?
DNS resolvers are like address books for the Internet. They translate the name of places to addresses so that your browser can figure out how to get there. DNS resolvers do this by working backwards from the top until they find the website you are looking for.
Every resolver knows how to find the invisible `.` at the end of domain names (for example, `cloudflare.com.`). There are [hundreds of root servers](http://www.root-servers.org/) all over the world that host the `.` file, and resolvers are [hard coded to know the IP addresses](http://www.internic.net/domain/named.root) of those servers. Cloudflare itself hosts [that file](http://www.internic.net/domain/root.zone) on all of its servers around the world through a [partnership with ISC](https://blog.cloudflare.com/f-root/).
The resolver asks one of the root servers where to find the next link in the chain — the top-level domain (abbreviated to TLD) or domain ending. An example of a TLD is `.com` or `.org`. Luckily, the root servers store the locations of all the TLD servers, so they can return which IP address the DNS resolver should go ask next.
The resolver then asks the TLD's servers where it can find the domain it is looking for. For example, a resolver might ask `.com` where to find `cloudflare.com`. TLDs host a file containing the location of every domain using the TLD.
Once the resolver has the final IP address, it returns the answer to the computer that asked.
This whole system is called the [Domain Name System (DNS)](https://www.cloudflare.com/learning/dns/what-is-dns/). This system includes the servers that host the information (called [authoritative DNS](https://www.cloudflare.com/learning/dns/dns-server-types/)) and the servers that seek the information (the DNS resolvers).
## Does 1.1.1.1 support ANY?
Cloudflare [stopped supporting the ANY query](https://blog.cloudflare.com/deprecating-dns-any-meta-query-type/) in 2015 as ANY queries are more often used to perpetuate large volumetric attacks against the DNS system than valid use. 1.1.1.1 returns `NOTIMPL` when asked for `qtype==ANY`.
## How does 1.1.1.1 work with DNSSEC?
1.1.1.1 is a DNSSEC validating resolver. 1.1.1.1 sends the `DO` (`DNSSEC OK`) bit on every query to convey to the authoritative server that it wishes to receive signed answers if available. 1.1.1.1 supports the signature algorithms specified in [Supported DNSKEY signature algorithms](https://developers.cloudflare.com/1.1.1.1/encryption/dnskey/).
## Does 1.1.1.1 send EDNS Client Subnet header?
1.1.1.1 is a privacy centric resolver so it does not send any client IP information and does not send the EDNS Client Subnet (ECS) header to authoritative servers. The exception is the single Akamai debug domain `whoami.ds.akahelp.net` to aid in cross-provider debugging. However, Cloudflare does not send ECS to any of Akamai's production domains, such as `akamaihd.net` or similar.
## Does 1.1.1.1 support IPv6?
1.1.1.1 has full IPv6 support.
## What is Purge Cache?
1.1.1.1's Purge Cache tool allows you to refresh 1.1.1.1's DNS cache for domain names. To refresh the cache for a domain name, visit the [Purge Cache page](https://one.one.one.one/purge-cache/).
## What is query name minimization?
Cloudflare minimizes privacy leakage by only sending minimal query name to authoritative DNS servers. For example, if a client is looking for foo.bar.example.com, the only part of the query 1.1.1.1 discloses to .com is that we want to know who's responsible for example.com and the zone internals stay hidden.
## What are root hints?
For decreased latency, reduced privacy leakage of queries and lower load on the DNS system, 1.1.1.1 upstreams to [locally hosted root zone files](https://blog.cloudflare.com/f-root/).
## Can IPs used by 1.1.1.1 be allowlisted?
Authoritative DNS providers may want to allowlist IP's 1.1.1.1 uses to query upstream DNS providers. The comprehensive list of IP's to allowlist is available at .
---
title: Infrastructure · Cloudflare 1.1.1.1 docs
lastUpdated: 2024-09-18T09:24:54.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/1.1.1.1/infrastructure/
md: https://developers.cloudflare.com/1.1.1.1/infrastructure/index.md
---
* [Network operators](https://developers.cloudflare.com/1.1.1.1/infrastructure/network-operators/)
* [Support for IPv6-only networks](https://developers.cloudflare.com/1.1.1.1/infrastructure/ipv6-networks/)
* [Extended DNS error codes](https://developers.cloudflare.com/1.1.1.1/infrastructure/extended-dns-error-codes/)
* [SLA and technical support](https://developers.cloudflare.com/1.1.1.1/infrastructure/sla-and-support/)
---
title: IP addresses · Cloudflare 1.1.1.1 docs
description: Get IPv4 and IPv6 addresses for Cloudflare DNS resolvers, 1.1.1.1
and 1.1.1.1 for Families.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/ip-addresses/
md: https://developers.cloudflare.com/1.1.1.1/ip-addresses/index.md
---
Consider the tables below to know which IPv4 or IPv6 addresses are used by the different Cloudflare DNS resolver offerings.
For detailed guidance refer to [Set up](https://developers.cloudflare.com/1.1.1.1/setup/).
***
## 1.1.1.1
1.1.1.1 is Cloudflare’s public DNS resolver. It offers a fast and private way to browse the Internet.
| IPv4 | IPv6 |
| - | - |
| `1.1.1.1` `1.0.0.1` | `2606:4700:4700::1111` `2606:4700:4700::1001` |
Refer to [Encryption](https://developers.cloudflare.com/1.1.1.1/encryption/) to learn how to use 1.1.1.1 in an encrypted way.
***
## 1.1.1.1 for Families
1.1.1.1 for Families categorizes destinations on the Internet based on the potential threat they pose regarding malware, phishing, or other types of security risks.
For more information, refer to [1.1.1.1 for Families set up](https://developers.cloudflare.com/1.1.1.1/setup/#1111-for-families).
### Block malware
| IPv4 | IPv6 |
| - | - |
| `1.1.1.2` `1.0.0.2` | `2606:4700:4700::1112` `2606:4700:4700::1002` |
### Block malware and adult content
| IPv4 | IPv6 |
| - | - |
| `1.1.1.3` `1.0.0.3` | `2606:4700:4700::1113` `2606:4700:4700::1003` |
---
title: Privacy · Cloudflare 1.1.1.1 docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/privacy/
md: https://developers.cloudflare.com/1.1.1.1/privacy/index.md
---
* [1.1.1.1 Public DNS Resolver](https://developers.cloudflare.com/1.1.1.1/privacy/public-dns-resolver/): This document provides details on our collection, use, and disclosure of the information processed by the 1.1.1.1 public DNS resolver. The 1.1.1.1 public DNS resolver service is governed by our [Privacy Policy](https://www.cloudflare.com/privacypolicy/).
* [Resolver for Firefox](https://developers.cloudflare.com/1.1.1.1/privacy/cloudflare-resolver-firefox/): This document outlines our collection, use, and disclosure of the information processed by the Cloudflare Resolver for Firefox. Any data Cloudflare processes in connection with the Cloudflare Resolver for Firefox is as a data processor acting pursuant to Mozilla’s data processing instructions. Cloudflare Resolver for Firefox is not covered by our main Privacy Policy and is separate from the 1.1.1.1 public DNS resolver.
* [1.1.1.1 Application](https://www.cloudflare.com/application/privacypolicy/): This policy applies to our collection, use, and disclosure of the information from Cloudflare’s consumer-facing 1.1.1.1 Applications, such as our 1.1.1.1 Application for iOS and Android.
---
title: Terms of use · Cloudflare 1.1.1.1 docs
description: By using 1.1.1.1 Public DNS Resolver or 1.1.1.1 for Families, you
consent to be bound by the Cloudflare Website and Online Services Terms of
Use.
lastUpdated: 2025-02-13T09:12:51.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/terms-of-use/
md: https://developers.cloudflare.com/1.1.1.1/terms-of-use/index.md
---
By using 1.1.1.1 Public DNS Resolver or 1.1.1.1 for Families, you consent to be bound by the [Cloudflare Website and Online Services Terms of Use](https://www.cloudflare.com/website-terms/).
If you are an [Internet Service Provider (ISP) or network equipment provider](https://developers.cloudflare.com/1.1.1.1/infrastructure/network-operators/), you agree to provide proper attribution to Cloudflare in accordance with our Trademark Guidelines using our Public DNS Resolver. Please reach out to `resolver@cloudflare.com` for such logo requests.
---
title: Set up Cloudflare 1.1.1.1 resolver · Cloudflare 1.1.1.1 docs
description: Learn how to set up Cloudflare's 1.1.1.1 DNS resolver for enhanced
security and privacy. Protect against malware and adult content with easy
configuration.
lastUpdated: 2025-06-19T13:27:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/setup/
md: https://developers.cloudflare.com/1.1.1.1/setup/index.md
---
By default, the [DNS server](https://www.cloudflare.com/learning/dns/what-is-dns/) your devices use is provided by your Internet service provider (ISP). Some [ISPs and network equipment providers](https://developers.cloudflare.com/1.1.1.1/infrastructure/network-operators/) partner with Cloudflare to add safer browsing to their offerings.
If your providers are not currently using Cloudflare, you can change the DNS settings on your device or router as detailed in the following instructions.
Device or router specific guides
* [Android](https://developers.cloudflare.com/1.1.1.1/setup/android/)
* [Azure](https://developers.cloudflare.com/1.1.1.1/setup/azure/)
* [Gaming consoles](https://developers.cloudflare.com/1.1.1.1/setup/gaming-consoles/)
* [Google Cloud](https://developers.cloudflare.com/1.1.1.1/setup/google-cloud/)
* [iOS](https://developers.cloudflare.com/1.1.1.1/setup/ios/)
* [Linux](https://developers.cloudflare.com/1.1.1.1/setup/linux/)
* [macOS](https://developers.cloudflare.com/1.1.1.1/setup/macos/)
* [Router](https://developers.cloudflare.com/1.1.1.1/setup/router/)
* [Windows](https://developers.cloudflare.com/1.1.1.1/setup/windows/)
You can also set up [1.1.1.1 for Families](#1111-for-families) for an added layer of protection on your home network against malware and adult content. 1.1.1.1 for Families leverages Cloudflare's global network to ensure that it is fast and secure around the world, and includes the same [strong privacy guarantees](https://developers.cloudflare.com/1.1.1.1/privacy/public-dns-resolver/) that Cloudflare committed to when launching 1.1.1.1.
***
## 1.1.1.1 for Families
1.1.1.1 for Families categorizes destinations on the Internet based on the potential threat they pose regarding malware, phishing, or other types of security risks.
1.1.1.1 for Families has two default options:
Block malware
Use the following DNS resolvers to block malicious content:
* `1.1.1.2`
* `1.0.0.2`
* `2606:4700:4700::1112`
* `2606:4700:4700::1002`
Block malware and adult content
Use the following DNS resolvers to block malware and adult content:
* `1.1.1.3`
* `1.0.0.3`
* `2606:4700:4700::1113`
* `2606:4700:4700::1003`
Cloudflare returns `0.0.0.0` if the [fully qualified domain name (FQDN)](https://en.wikipedia.org/wiki/Fully_qualified_domain_name) or IP in a DNS query is classified as malicious.
Domain miscategorization
If you are using 1.1.1.1 for Families and see a domain that you believe is miscategorized, [fill in this form](https://radar.cloudflare.com/categorization-feedback/) to bring it to our attention. Your submission will remain anonymous.
We review these submissions to improve Cloudflare’s categorization.
### Test 1.1.1.1 for Families
After configuring 1.1.1.1 for Families, you can test if it is working as intended with the following URLs:
* : Use this to test if 1.1.1.1 for Families is blocking known malware addresses correctly.
* : Use this to test if 1.1.1.1 for Families is blocking known adult content and malware addresses correctly.
### DNS over HTTPS (DoH)
If you have a DoH-compliant client, such as a compatible router, you can set up 1.1.1.1 for Families to encrypt your DNS queries over HTTPS. This prevents spoofing and tracking by malicious actors, advertisers, ISPs, and others. For more information on DoH, refer to the [Learning Center article on DNS encryption](https://www.cloudflare.com/learning/dns/dns-over-tls/).
To configure an encrypted DoH connection to 1.1.1.1 for Families, type one of the following URLs into the appropriate field of your DoH-compliant client:
Block malware
```txt
https://security.cloudflare-dns.com/dns-query
```
Block malware and adult content
```txt
https://family.cloudflare-dns.com/dns-query
```
### DNS over TLS (DoT)
1.1.1.1 for Families also supports DoT if you have a compliant client, such as a compatible DoT router. DoT allows you to encrypt your DNS queries, protecting you from spoofing, malicious actors, and others. You can learn more about DoT in the [Learning Center article on DNS encryption](https://www.cloudflare.com/learning/dns/dns-over-tls/).
To configure an encrypted DoT connection to 1.1.1.1 for Families, type one of the following URLs into the appropriate field of your DoT-compliant client:
Block malware
```txt
security.cloudflare-dns.com
```
Block malware and adult content
```txt
family.cloudflare-dns.com
```
---
title: Troubleshooting DNS Resolver · Cloudflare 1.1.1.1 docs
description: Learn how to diagnose and report issues with Cloudflare's DNS Resolver
lastUpdated: 2025-09-10T12:25:16.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/1.1.1.1/troubleshooting/
md: https://developers.cloudflare.com/1.1.1.1/troubleshooting/index.md
---
This guide will help you diagnose and resolve common issues with Cloudflare's DNS Resolver. Before proceeding with manual troubleshooting steps, you can [verify your connection](https://developers.cloudflare.com/1.1.1.1/check/) to automatically gather relevant information.
## Name resolution issues
### Linux/macOS
```sh
# Test DNS resolution
dig example.com @1.1.1.1
dig example.com @1.0.0.1
dig example.com @8.8.8.8
# Check connected nameserver
dig +short CHAOS TXT id.server @1.1.1.1
dig +short CHAOS TXT id.server @1.0.0.1
# Optional: Network information
dig @ns3.cloudflare.com whoami.cloudflare.com txt +short
```
### Windows
```sh
# Test DNS resolution
nslookup example.com 1.1.1.1
nslookup example.com 1.0.0.1
nslookup example.com 8.8.8.8
# Check connected nameserver
nslookup -class=chaos -type=txt id.server 1.1.1.1
nslookup -class=chaos -type=txt id.server 1.0.0.1
# Optional: Network information
nslookup -type=txt whoami.cloudflare.com ns3.cloudflare.com
```
**Note:** The network information command reveals your IP address. Only include this in reports to Cloudflare if you are comfortable sharing this information.
For additional analysis, you can generate a [DNSViz](http://dnsviz.net/) report for the domain in question.
## Connectivity and routing issues
Before reporting connectivity issues:
1. Search for existing reports from your country and ISP.
2. Run traceroutes to both Cloudflare DNS resolvers.
### Linux/macOS
```sh
# Basic connectivity tests
traceroute 1.1.1.1
traceroute 1.0.0.1
# If reachable, check nameserver identity
dig +short CHAOS TXT id.server @1.1.1.1
dig +short CHAOS TXT id.server @1.0.0.1
# TCP connection tests
dig +tcp @1.1.1.1 id.server CH TXT
dig +tcp @1.0.0.1 id.server CH TXT
```
### Windows
```sh
# Basic connectivity tests
tracert 1.1.1.1
tracert 1.0.0.1
# If reachable, check nameserver identity
nslookup -class=chaos -type=txt id.server 1.1.1.1
nslookup -class=chaos -type=txt id.server 1.0.0.1
# TCP connection tests
nslookup -vc -class=chaos -type=txt id.server 1.1.1.1
nslookup -vc -class=chaos -type=txt id.server 1.0.0.1
```
## DNS-over-TLS (DoT) troubleshooting
### Linux/macOS
```sh
# Test TLS connectivity
openssl s_client -connect 1.1.1.1:853
openssl s_client -connect 1.0.0.1:853
# Test DNS resolution over TLS
kdig +tls @1.1.1.1 id.server CH TXT
kdig +tls @1.0.0.1 id.server CH TXT
```
### Windows
Windows does not include a standalone DoT client. You can test TLS connectivity using OpenSSL after installing it manually.
## DNS-over-HTTPS (DoH) troubleshooting
### Linux/macOS
```sh
curl -H 'accept: application/dns-json' 'https://cloudflare-dns.com/dns-query?name=cloudflare.com&type=AAAA'
```
### Windows
```powershell
(Invoke-WebRequest -Uri 'https://cloudflare-dns.com/dns-query?name=cloudflare.com&type=AAAA').RawContent
```
## Common issues
### First hop failures
If your traceroute fails at the first hop, the issue is likely hardware-related. Your router may have a hardcoded route for 1.1.1.1. When reporting this issue, include:
* Router make and model
* ISP name
* Any relevant router configuration details
## Additional resources
* [1.1.1.1 DNS Resolver homepage](https://1.1.1.1)
* [DNS over TLS documentation](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-tls/)
* [Diagnostic tool](https://one.one.one.one/help/)
---
title: 404 - Page Not Found · Cloudflare AI Gateway docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/404/
md: https://developers.cloudflare.com/ai-gateway/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: AI Assistant · Cloudflare AI Gateway docs
lastUpdated: 2024-10-30T16:07:34.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/ai/
md: https://developers.cloudflare.com/ai-gateway/ai/index.md
---
---
title: Changelog · Cloudflare AI Gateway docs
description: Subscribe to RSS
lastUpdated: 2025-05-09T15:42:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/changelog/
md: https://developers.cloudflare.com/ai-gateway/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/ai-gateway/changelog/index.xml)
## 2025-11-21
Unified Billing now supports opt-in Zero Data Retention. This ensures supported upstream AI providers (eg [OpenAI ZDR](https://platform.openai.com/docs/guides/your-data#zero-data-retention)) do not retain request and response data.
## 2025-11-14
* Supports adding OpenAI compatible [Custom Providers](https://developers.cloudflare.com/ai-gateway/configuration/custom-providers/) for inferencing with AI providers that are not natively supported by AI Gateway
* Cost and usage tracking for voice models
* You can now use Workers AI via AI Gateway with no additional configuration. Previously, this required generating / passing additional Workers AI tokens.
## 2025-11-06
**Unified Billing**
* [Unified Billing](https://developers.cloudflare.com/ai-gateway/features/unified-billing/) is now in open beta. Connect multiple AI providers (e.g. OpenAI, Anthropic) without any additional setup and pay through a single Cloudflare invoice. To use it, purchase credits in the Cloudflare Dashboard and spend them across providers via AI Gateway.
## 2025-11-03
New supported providers
* [Baseten](https://developers.cloudflare.com/ai-gateway/usage/providers/baseten/)
* [Ideogram](https://developers.cloudflare.com/ai-gateway/usage/providers/ideogram/)
* [Deepgram](https://developers.cloudflare.com/ai-gateway/usage/providers/deepgram/)
## 2025-10-29
* Add support for pipecat model on Workers AI
* Fix OpenAI realtime websocket authentication.
## 2025-10-24
* Added cost tracking and observability support for async video generation requests for OpenAI Sora 2 and Google AI Studio Veo 3.
* `cf-aig-eventId` and `cf-aig-log-id` headers are now returned on all requests including failed requests
## 2025-10-14
The Model playground is now available in the AI Gateway Cloudflare Dashboard, allowing you to request and compare model behaviour across all models supported by AI Gateway.
## 2025-10-07
* Add support for [Deepgram on Workers AI](https://developers.cloudflare.com/ai-gateway/usage/websockets-api/realtime-api/#deepgram-workers-ai) using Websocket transport.
* Added [Parallel](https://developers.cloudflare.com/ai-gateway/usage/providers/parallel/) as a provider.
## 2025-09-24
**OTEL Tracing**
Added OpenTelemetry (OTEL) tracing export for better observability and debugging of AI Gateway requests.
## 2025-09-21
* Added support for [Fal AI](https://developers.cloudflare.com/ai-gateway/usage/providers/fal/) provider.
* You can now set up custom Stripe usage reporting, and report usage and costs for your users directly to Stripe from AI Gateway.
* Fixed incorrectly geoblocked requests for certain regions.
## 2025-09-19
* New API endpoint (`/compat/v1/models`) for listing available models along with their costs.
* Unified API now supports Google Vertex AI providers and all their models.
* BYOK support for requests using WebSocket transport.
## 2025-08-28
**Data Loss Prevention**
[Data loss prevention](https://developers.cloudflare.com/ai-gateway/features/dlp/) capabilities are now available to scan both incoming prompts and outgoing AI responses for sensitive information, ensuring your AI applications maintain security and compliance standards.
## 2025-08-25
**Dynamic routing**
Introduced [Dynamic routing](https://developers.cloudflare.com/ai-gateway/features/dynamic-routing/) that lets you visually or via JSON define flexible request flows that segment users, enforce quotas, and choose models with fallbacks—without changing application code.
## 2025-08-21
**Bring your own keys (BYOK)**
Introduced [Bring your own keys (BYOK)](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/) allowing you to save your AI provider keys securely with Cloudflare Secret Store and manage them through the Cloudflare dashboard.
## 2025-06-18
**New GA providers**
We have moved the following providers out of beta and into GA:
* [Cartesia](https://developers.cloudflare.com/ai-gateway/usage/providers/cartesia/)
* [Cerebras](https://developers.cloudflare.com/ai-gateway/usage/providers/cerebras/)
* [DeepSeek](https://developers.cloudflare.com/ai-gateway/usage/providers/deepseek/)
* [ElevenLabs](https://developers.cloudflare.com/ai-gateway/usage/providers/elevenlabs/)
* [OpenRouter](https://developers.cloudflare.com/ai-gateway/usage/providers/openrouter/)
## 2025-05-28
**OpenAI Compatibility**
* Introduced a new [OpenAI-compatible chat completions endpoint](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) to simplify switching between different AI providers without major code modifications.
## 2025-04-22
* Increased Max Number of Gateways per account: Raised the maximum number of gateways per account from 10 to 20 for paid users. This gives you greater flexibility in managing your applications as you build and scale.
* Streaming WebSocket Bug Fix: Resolved an issue affecting streaming responses over [WebSockets](https://developers.cloudflare.com/ai-gateway/configuration/websockets-api/). This fix ensures more reliable and consistent streaming behavior across all supported AI providers.
* Increased Timeout Limits: Extended the default timeout for AI Gateway requests beyond the previous 100-second limit. This enhancement improves support for long-running requests.
## 2025-04-02
**Cache Key Calculation Changes**
* We have updated how [cache](https://developers.cloudflare.com/ai-gateway/features/caching/) keys are calculated. As a result, new cache entries will be created, and you may experience more cache misses than usual during this transition. Please monitor your traffic and performance, and let us know if you encounter any issues.
## 2025-03-18
**WebSockets**
* Added [WebSockets API](https://developers.cloudflare.com/ai-gateway/configuration/websockets-api/) to provide a persistent connection for AI interactions, eliminating repeated handshakes and reducing latency.
## 2025-02-26
**Guardrails**
* Added [Guardrails](https://developers.cloudflare.com/ai-gateway/features/guardrails/) help deploy AI applications safely by intercepting and evaluating both user prompts and model responses for harmful content.
## 2025-02-19
**Updated Log Storage Settings**
* Introduced customizable log storage settings, enabling users to:
* Define the maximum number of logs stored per gateway.
* Choose how logs are handled when the storage limit is reached:
* **On** - Automatically delete the oldest logs to ensure new logs are always saved.
* **Off** - Stop saving new logs when the storage limit is reached.
## 2025-02-06
**Added request handling**
* Added [request handling options](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/) to help manage AI provider interactions effectively, ensuring your applications remain responsive and reliable.
## 2025-02-05
**New AI Gateway providers**
* **Configuration**: Added [ElevenLabs](https://elevenlabs.io/), [Cartesia](https://docs.cartesia.ai/), and [Cerebras](https://inference-docs.cerebras.ai/) as new providers.
## 2025-01-02
**DeepSeek**
* **Configuration**: Added [DeepSeek](https://developers.cloudflare.com/ai-gateway/usage/providers/deepseek/) as a new provider.
## 2024-12-17
**AI Gateway Dashboard**
* Updated dashboard to view performance, costs, and stats across all gateways.
## 2024-12-13
**Bug Fixes**
* **Bug Fixes**: Fixed Anthropic errors being cached.
* **Bug Fixes**: Fixed `env.AI.run()` requests using authenticated gateways returning authentication error.
## 2024-11-28
**OpenRouter**
* **Configuration**: Added [OpenRouter](https://developers.cloudflare.com/ai-gateway/usage/providers/openrouter/) as a new provider.
## 2024-11-19
**WebSockets API**
* **Configuration**: Added [WebSockets API](https://developers.cloudflare.com/ai-gateway/configuration/websockets-api/) which provides a single persistent connection, enabling continuous communication.
## 2024-11-19
**Authentication**
* **Configuration**: Added [Authentication](https://developers.cloudflare.com/ai-gateway/configuration/authentication/) which adds security by requiring a valid authorization token for each request.
## 2024-10-28
**Grok**
* **Providers**: Added [Grok](https://developers.cloudflare.com/ai-gateway/usage/providers/grok/) as a new provider.
## 2024-10-17
**Vercel SDK**
Added [Vercel AI SDK](https://sdk.vercel.ai/). The SDK supports many different AI providers, tools for streaming completions, and more.
## 2024-09-26
**Persistent logs**
* **Logs**: AI Gateway now has [logs that persist](https://developers.cloudflare.com/ai-gateway/observability/logging/index), giving you the flexibility to store them for your preferred duration.
## 2024-09-26
**Logpush**
* **Logs**: Securely export logs to an external storage location using [Logpush](https://developers.cloudflare.com/ai-gateway/observability/logging/logpush).
## 2024-09-26
**Pricing**
* **Pricing**: Added [pricing](https://developers.cloudflare.com/ai-gateway/reference/pricing/) for storing logs persistently.
## 2024-09-26
**Evaluations**
* **Configurations**: Use AI Gateway’s [Evaluations](https://developers.cloudflare.com/ai-gateway/evaluations) to make informed decisions on how to optimize your AI application.
## 2024-09-10
**Custom costs**
* **Configuration**: AI Gateway now allows you to set custom costs at the request level [custom costs](https://developers.cloudflare.com/ai-gateway/configuration/custom-costs/) to requests, accurately reflect your unique pricing, overriding the default or public model costs.
## 2024-08-02
**Mistral AI**
* **Providers**: Added [Mistral AI](https://developers.cloudflare.com/ai-gateway/usage/providers/mistral/) as a new provider.
## 2024-07-23
**Google AI Studio**
* **Providers**: Added [Google AI Studio](https://developers.cloudflare.com/ai-gateway/usage/providers/google-ai-studio/) as a new provider.
## 2024-07-10
**Custom metadata**
AI Gateway now supports adding [custom metadata](https://developers.cloudflare.com/ai-gateway/configuration/custom-metadata/) to requests, improving tracking and analysis of incoming requests.
## 2024-07-09
**Logs**
[Logs](https://developers.cloudflare.com/ai-gateway/observability/analytics/#logging) are now available for the last 24 hours.
## 2024-06-24
**Custom cache key headers**
AI Gateway now supports [custom cache key headers](https://developers.cloudflare.com/ai-gateway/features/caching/#custom-cache-key-cf-aig-cache-key).
## 2024-06-18
**Access an AI Gateway through a Worker**
Workers AI now natively supports [AI Gateway](https://developers.cloudflare.com/ai-gateway/usage/providers/workersai/#worker).
## 2024-05-22
**AI Gateway is now GA**
AI Gateway is moving from beta to GA.
## 2024-05-16
* **Providers**: Added [Cohere](https://developers.cloudflare.com/ai-gateway/usage/providers/cohere/) and [Groq](https://developers.cloudflare.com/ai-gateway/usage/providers/groq/) as new providers.
## 2024-05-09
* Added new endpoints to the [REST API](https://developers.cloudflare.com/api/resources/ai_gateway/methods/create/).
## 2024-03-26
* [LLM Side Channel vulnerability fixed](https://blog.cloudflare.com/ai-side-channel-attack-mitigated)
* **Providers**: Added Anthropic, Google Vertex, Perplexity as providers.
## 2023-10-26
* **Real-time Logs**: Logs are now real-time, showing logs for the last hour. If you have a need for persistent logs, please let the team know on Discord. We are building out a persistent logs feature for those who want to store their logs for longer.
* **Providers**: Azure OpenAI is now supported as a provider!
* **Docs**: Added Azure OpenAI example.
* **Bug Fixes**: Errors with costs and tokens should be fixed.
## 2023-10-09
* **Logs**: Logs will now be limited to the last 24h. If you have a use case that requires more logging, please reach out to the team on Discord.
* **Dashboard**: Logs now refresh automatically.
* **Docs**: Fixed Workers AI example in docs and dash.
* **Caching**: Embedding requests are now cacheable. Rate limit will not apply for cached requests.
* **Bug Fixes**: Identical requests to different providers are not wrongly served from cache anymore. Streaming now works as expected, including for the Universal endpoint.
* **Known Issues**: There's currently a bug with costs that we are investigating.
---
title: REST API reference · Cloudflare AI Gateway docs
lastUpdated: 2024-12-18T13:12:05.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/api-reference/
md: https://developers.cloudflare.com/ai-gateway/api-reference/index.md
---
---
title: Configuration · Cloudflare AI Gateway docs
description: Configure your AI Gateway with multiple options and customizations.
lastUpdated: 2025-05-28T19:49:34.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-gateway/configuration/
md: https://developers.cloudflare.com/ai-gateway/configuration/index.md
---
Configure your AI Gateway with multiple options and customizations.
* [BYOK (Store Keys)](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/)
* [Custom costs](https://developers.cloudflare.com/ai-gateway/configuration/custom-costs/)
* [Custom Providers](https://developers.cloudflare.com/ai-gateway/configuration/custom-providers/)
* [Manage gateways](https://developers.cloudflare.com/ai-gateway/configuration/manage-gateway/)
* [Request handling](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/)
* [Fallbacks](https://developers.cloudflare.com/ai-gateway/configuration/fallbacks/)
* [Authenticated Gateway](https://developers.cloudflare.com/ai-gateway/configuration/authentication/)
---
title: Architectures · Cloudflare AI Gateway docs
description: Learn how you can use AI Gateway within your existing architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-gateway/demos/
md: https://developers.cloudflare.com/ai-gateway/demos/index.md
---
Learn how you can use AI Gateway within your existing architecture.
## Reference architectures
Explore the following reference architectures that use AI Gateway:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Multi-vendor AI observability and control](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-multivendor-observability-control/)
[By shifting features such as rate limiting, caching, and error handling to the proxy layer, organizations can apply unified configurations across services and inference service providers.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-multivendor-observability-control/)
[AI Vibe Coding Platform](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/)
[Cloudflare's low-latency, fully serverless compute platform, Workers offers powerful capabilities to enable A/B testing using a server-side implementation.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/)
---
title: Evaluations · Cloudflare AI Gateway docs
description: Understanding your application's performance is essential for
optimization. Developers often have different priorities, and finding the
optimal solution involves balancing key factors such as cost, latency, and
accuracy. Some prioritize low-latency responses, while others focus on
accuracy or cost-efficiency.
lastUpdated: 2025-08-19T11:42:14.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-gateway/evaluations/
md: https://developers.cloudflare.com/ai-gateway/evaluations/index.md
---
Understanding your application's performance is essential for optimization. Developers often have different priorities, and finding the optimal solution involves balancing key factors such as cost, latency, and accuracy. Some prioritize low-latency responses, while others focus on accuracy or cost-efficiency.
AI Gateway's Evaluations provide the data needed to make informed decisions on how to optimize your AI application. Whether it is adjusting the model, provider, or prompt, this feature delivers insights into key metrics around performance, speed, and cost. It empowers developers to better understand their application's behavior, ensuring improved accuracy, reliability, and customer satisfaction.
Evaluations use datasets which are collections of logs stored for analysis. You can create datasets by applying filters in the Logs tab, which help narrow down specific logs for evaluation.
Our first step toward comprehensive AI evaluations starts with human feedback (currently in open beta). We will continue to build and expand AI Gateway with additional evaluators.
[Learn how to set up an evaluation](https://developers.cloudflare.com/ai-gateway/evaluations/set-up-evaluations/) including creating datasets, selecting evaluators, and running the evaluation process.
---
title: Features · Cloudflare AI Gateway docs
description: AI Gateway provides a comprehensive set of features to help you
build, deploy, and manage AI applications with confidence. From performance
optimization to security and observability, these features work together to
create a robust AI infrastructure.
lastUpdated: 2025-09-02T18:45:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/features/
md: https://developers.cloudflare.com/ai-gateway/features/index.md
---
AI Gateway provides a comprehensive set of features to help you build, deploy, and manage AI applications with confidence. From performance optimization to security and observability, these features work together to create a robust AI infrastructure.
## Core Features
### Performance & Cost Optimization
### Caching
Serve identical requests directly from Cloudflare's global cache, reducing latency by up to 90% and significantly cutting costs by avoiding repeated API calls to AI providers.
**Key benefits:**
* Reduced response times for repeated queries
* Lower API costs through cache hits
* Configurable TTL and per-request cache control
* Works across all supported AI providers
[Use Caching](https://developers.cloudflare.com/ai-gateway/features/caching/)
### Rate Limiting
Control application scaling and protect against abuse with flexible rate limiting options. Set limits based on requests per time window with sliding or fixed window techniques.
**Key benefits:**
* Prevent API quota exhaustion
* Control costs and usage patterns
* Configurable per gateway or per request
* Multiple rate limiting techniques available
[Use Rate Limiting](https://developers.cloudflare.com/ai-gateway/features/rate-limiting/)
### Dynamic Routing
Create sophisticated request routing flows without code changes. Route requests based on user segments, geography, content analysis, or A/B testing requirements through a visual interface.
**Key benefits:**
* Visual flow-based configuration
* User-based and geographic routing
* A/B testing and fractional traffic splitting
* Context-aware routing based on request content
* Dynamic rate limiting with automatic fallbacks
[Use Dynamic Routing](https://developers.cloudflare.com/ai-gateway/features/dynamic-routing/)
### Security & Safety
### Guardrails
Deploy AI applications safely with real-time content moderation. Automatically detect and block harmful content in both user prompts and model responses across all providers.
**Key benefits:**
* Consistent moderation across all AI providers
* Real-time prompt and response evaluation
* Configurable content categories and actions
* Compliance and audit capabilities
* Enhanced user safety and trust
[Use Guardrails](https://developers.cloudflare.com/ai-gateway/features/guardrails/)
### Data Loss Prevention (DLP)
Protect your organization from inadvertent exposure of sensitive data through AI interactions. Scan prompts and responses for PII, financial data, and other sensitive information.
**Key benefits:**
* Real-time scanning of AI prompts and responses
* Detection of PII, financial, healthcare, and custom data patterns
* Configurable actions: flag or block sensitive content
* Integration with Cloudflare's enterprise DLP solution
* Compliance support for GDPR, HIPAA, and PCI DSS
[Use Data Loss Prevention (DLP)](https://developers.cloudflare.com/ai-gateway/features/dlp/)
### Authentication
Secure your AI Gateway with token-based authentication. Control access to your gateways and protect against unauthorized usage.
**Key benefits:**
* Token-based access control
* Configurable per gateway
* Integration with Cloudflare's security infrastructure
* Audit trail for access attempts
[Use Authentication](https://developers.cloudflare.com/ai-gateway/configuration/authentication/)
### Bring Your Own Keys (BYOK)
Securely store and manage AI provider API keys in Cloudflare's encrypted infrastructure. Remove hardcoded keys from your applications while maintaining full control.
**Key benefits:**
* Encrypted key storage at rest and in transit
* Centralized key management across providers
* Easy key rotation without code changes
* Support for 20+ AI providers
* Enhanced security and compliance
[Use Bring Your Own Keys (BYOK)](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/)
### Observability & Analytics
### Analytics
Gain deep insights into your AI application usage with comprehensive analytics. Track requests, tokens, costs, errors, and performance across all providers.
**Key benefits:**
* Real-time usage metrics and trends
* Cost tracking and estimation across providers
* Error monitoring and troubleshooting
* Cache hit rates and performance insights
* GraphQL API for custom dashboards
[Use Analytics](https://developers.cloudflare.com/ai-gateway/observability/analytics/)
### Logging
Capture detailed logs of all AI requests and responses for debugging, compliance, and analysis. Configure log retention and export options.
**Key benefits:**
* Complete request/response logging
* Configurable log retention policies
* Export capabilities via Logpush
* Custom metadata support
* Compliance and audit support
[Use Logging](https://developers.cloudflare.com/ai-gateway/observability/logging/)
### Custom Metadata
Enrich your logs and analytics with custom metadata. Tag requests with user IDs, team information, or any custom data for enhanced filtering and analysis.
**Key benefits:**
* Enhanced request tracking and filtering
* User and team-based analytics
* Custom business logic integration
* Improved debugging and troubleshooting
[Use Custom Metadata](https://developers.cloudflare.com/ai-gateway/observability/custom-metadata/)
### Advanced Configuration
### Custom Costs
Override default pricing with your negotiated rates or custom cost models. Apply custom costs at the request level for accurate cost tracking.
**Key benefits:**
* Accurate cost tracking with negotiated rates
* Per-request cost customization
* Better budget planning and forecasting
* Support for enterprise pricing agreements
[Use Custom Costs](https://developers.cloudflare.com/ai-gateway/configuration/custom-costs/)
## Feature Comparison by Use Case
| Use Case | Recommended Features |
| - | - |
| **Cost Optimization** | Caching, Rate Limiting, Custom Costs |
| **High Availability** | Fallbacks using Dynamic Routing |
| **Security & Compliance** | Guardrails, DLP, Authentication, BYOK, Logging |
| **Performance Monitoring** | Analytics, Logging, Custom Metadata |
| **A/B Testing** | Dynamic Routing, Custom Metadata, Analytics |
## Getting Started with Features
1. **Start with the basics**: Enable [Caching](https://developers.cloudflare.com/ai-gateway/features/caching/) and [Analytics](https://developers.cloudflare.com/ai-gateway/observability/analytics/) for immediate benefits
2. **Add reliability**: Configure Fallbacks and Rate Limiting using [Dynamic routing](https://developers.cloudflare.com/ai-gateway/features/dynamic-routing/)
3. **Enhance security**: Implement [Guardrails](https://developers.cloudflare.com/ai-gateway/features/guardrails/), [DLP](https://developers.cloudflare.com/ai-gateway/features/dlp/), and [Authentication](https://developers.cloudflare.com/ai-gateway/configuration/authentication/)
***
*All features work seamlessly together and across all 20+ supported AI providers. Get started with [AI Gateway](https://developers.cloudflare.com/ai-gateway/get-started/) to begin using these features in your applications.*
---
title: Getting started · Cloudflare AI Gateway docs
description: In this guide, you will learn how to create and use your first AI Gateway.
lastUpdated: 2026-01-21T09:55:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/get-started/
md: https://developers.cloudflare.com/ai-gateway/get-started/index.md
---
In this guide, you will learn how to create and use your first AI Gateway.
* Dashboard
[Go to **AI Gateway**](https://dash.cloudflare.com/?to=/:account/ai/ai-gateway)
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com/) and select your account.
2. Go to **AI** > **AI Gateway**.
3. Select **Create Gateway**.
4. Enter your **Gateway name**. Note: Gateway name has a 64 character limit.
5. Select **Create**.
* API
To set up an AI Gateway using the API:
1. [Create an API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with the following permissions:
* `AI Gateway - Read`
* `AI Gateway - Edit`
2. Get your [Account ID](https://developers.cloudflare.com/fundamentals/account/find-account-and-zone-ids/).
3. Using that API token and Account ID, send a [`POST` request](https://developers.cloudflare.com/api/resources/ai_gateway/methods/create/) to the Cloudflare API.
### Authenticated gateway 🔒
When you enable authentication on a gateway, each request is required to include a valid Cloudflare API token, adding an extra layer of security. We recommend using an authenticated gateway to prevent unauthorized access. [Learn more](https://developers.cloudflare.com/ai-gateway/configuration/authentication/).
## Provider Authentication
Authenticate with your upstream AI provider using one of the following options:
* **Unified Billing:** Use the AI Gateway billing to pay for and authenticate your inference requests. Refer to [Unified Billing](https://developers.cloudflare.com/ai-gateway/features/unified-billing/).
* **BYOK (Store Keys):** Store your own provider API Keys with Cloudflare, and AI Gateway will include them at runtime. Refer to [BYOK](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/).
* **Request headers:** Include your provider API Key in the request headers as you normally would (for example, `Authorization: Bearer `).
## Integration Options
### Unified API Endpoint
OpenAI Compatible Recommended
The easiest way to get started with AI Gateway is through our OpenAI-compatible `/chat/completions` endpoint. This allows you to use existing OpenAI SDKs and tools with minimal code changes while gaining access to multiple AI providers.
`https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_name}/compat/chat/completions`
**Key benefits:**
* Drop-in replacement for OpenAI API, works with existing OpenAI SDKs and other OpenAI compliant clients
* Switch between providers by changing the `model` parameter
* Dynamic Routing - Define complex routing scenarios requiring conditional logic, conduct A/B tests, set rate / budget limits, etc
#### Example:
Make a request to
 OpenAI
using
OpenAI JS SDK
with
Stored Key (BYOK)
Refer to [Unified API](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) to learn more about OpenAI compatibility.
### Provider-specific endpoints
For direct integration with specific AI providers, use dedicated endpoints that maintain the original provider's API schema while adding AI Gateway features.
```txt
https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/{provider}
```
**Available providers:**
* [OpenAI](https://developers.cloudflare.com/ai-gateway/usage/providers/openai/) - GPT models and embeddings
* [Anthropic](https://developers.cloudflare.com/ai-gateway/usage/providers/anthropic/) - Claude models
* [Google AI Studio](https://developers.cloudflare.com/ai-gateway/usage/providers/google-ai-studio/) - Gemini models
* [Workers AI](https://developers.cloudflare.com/ai-gateway/usage/providers/workersai/) - Cloudflare's inference platform
* [AWS Bedrock](https://developers.cloudflare.com/ai-gateway/usage/providers/bedrock/) - Amazon's managed AI service
* [Azure OpenAI](https://developers.cloudflare.com/ai-gateway/usage/providers/azureopenai/) - Microsoft's OpenAI service
* [and more...](https://developers.cloudflare.com/ai-gateway/usage/providers/)
## Next steps
* Learn more about [caching](https://developers.cloudflare.com/ai-gateway/features/caching/) for faster requests and cost savings and [rate limiting](https://developers.cloudflare.com/ai-gateway/features/rate-limiting/) to control how your application scales.
* Explore how to specify model or provider [fallbacks, ratelimits, A/B tests](https://developers.cloudflare.com/ai-gateway/features/dynamic-routing/) for resiliency.
* Learn how to use low-cost, open source models on [Workers AI](https://developers.cloudflare.com/ai-gateway/usage/providers/workersai/) - our AI inference service.
---
title: Header Glossary · Cloudflare AI Gateway docs
description: AI Gateway supports a variety of headers to help you configure,
customize, and manage your API requests. This page provides a complete list of
all supported headers, along with a short description
lastUpdated: 2025-08-19T11:42:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/glossary/
md: https://developers.cloudflare.com/ai-gateway/glossary/index.md
---
AI Gateway supports a variety of headers to help you configure, customize, and manage your API requests. This page provides a complete list of all supported headers, along with a short description
| Term | Definition |
| - | - |
| cf-aig-backoff | Header to customize the backoff type for [request retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) of a request. |
| cf-aig-cache-key | The [cf-aig-cache-key-aig-cache-key](https://developers.cloudflare.com/ai-gateway/features/caching/#custom-cache-key-cf-aig-cache-key) let you override the default cache key in order to precisely set the cacheability setting for any resource. |
| cf-aig-cache-status | [Status indicator for caching](https://developers.cloudflare.com/ai-gateway/features/caching/#default-configuration), showing if a request was served from cache. |
| cf-aig-cache-ttl | Specifies the [cache time-to-live for responses](https://developers.cloudflare.com/ai-gateway/features/caching/#cache-ttl-cf-aig-cache-ttl). |
| cf-aig-collect-log | The [cf-aig-collect-log](https://developers.cloudflare.com/ai-gateway/observability/logging/#collect-logs-cf-aig-collect-log) header allows you to bypass the default log setting for the gateway. |
| cf-aig-custom-cost | Allows the [customization of request cost](https://developers.cloudflare.com/ai-gateway/configuration/custom-costs/#custom-cost) to reflect user-defined parameters. |
| cf-aig-event-id | [cf-aig-event-id](https://developers.cloudflare.com/ai-gateway/evaluations/add-human-feedback-api/#3-retrieve-the-cf-aig-log-id) is a unique identifier for an event, used to trace specific events through the system. |
| cf-aig-log-id | The [cf-aig-log-id](https://developers.cloudflare.com/ai-gateway/evaluations/add-human-feedback-api/#3-retrieve-the-cf-aig-log-id) is a unique identifier for the specific log entry to which you want to add feedback. |
| cf-aig-max-attempts | Header to customize the number of max attempts for [request retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) of a request. |
| cf-aig-metadata | [Custom metadata](https://developers.cloudflare.com/ai-gateway/configuration/custom-metadata/)allows you to tag requests with user IDs or other identifiers, enabling better tracking and analysis of your requests. |
| cf-aig-request-timeout | Header to trigger a fallback provider based on a [predetermined response time](https://developers.cloudflare.com/ai-gateway/configuration/fallbacks/#request-timeouts) (measured in milliseconds). |
| cf-aig-retry-delay | Header to customize the retry delay for [request retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) of a request. |
| cf-aig-skip-cache | Header to [bypass caching for a specific request](https://developers.cloudflare.com/ai-gateway/features/caching/#skip-cache-cf-aig-skip-cache). |
| cf-aig-step | [cf-aig-step](https://developers.cloudflare.com/ai-gateway/configuration/fallbacks/#response-headercf-aig-step) identifies the processing step in the AI Gateway flow for better tracking and debugging. |
| cf-cache-ttl | Deprecated: This header is replaced by `cf-aig-cache-ttl`. It specifies cache time-to-live. |
| cf-skip-cache | Deprecated: This header is replaced by `cf-aig-skip-cache`. It bypasses caching for a specific request. |
## Configuration hierarchy
Settings in AI Gateway can be configured at three levels: **Provider**, **Request**, and **Gateway**. Since the same settings can be configured in multiple locations, the following hierarchy determines which value is applied:
1. **Provider-level headers**: Relevant only when using the [Universal Endpoint](https://developers.cloudflare.com/ai-gateway/usage/universal/), these headers take precedence over all other configurations.
2. **Request-level headers**: Apply if no provider-level headers are set.
3. **Gateway-level settings**: Act as the default if no headers are set at the provider or request levels.
This hierarchy ensures consistent behavior, prioritizing the most specific configurations. Use provider-level and request-level headers for more fine-tuned control, and gateway settings for general defaults.
---
title: Integrations · Cloudflare AI Gateway docs
lastUpdated: 2025-05-09T15:42:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-gateway/integrations/
md: https://developers.cloudflare.com/ai-gateway/integrations/index.md
---
---
title: MCP server · Cloudflare AI Gateway docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/mcp-server/
md: https://developers.cloudflare.com/ai-gateway/mcp-server/index.md
---
---
title: Observability · Cloudflare AI Gateway docs
description: Observability is the practice of instrumenting systems to collect
metrics, and logs enabling better monitoring, troubleshooting, and
optimization of applications.
lastUpdated: 2025-05-09T15:42:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-gateway/observability/
md: https://developers.cloudflare.com/ai-gateway/observability/index.md
---
Observability is the practice of instrumenting systems to collect metrics, and logs enabling better monitoring, troubleshooting, and optimization of applications.
* [Analytics](https://developers.cloudflare.com/ai-gateway/observability/analytics/)
* [Costs](https://developers.cloudflare.com/ai-gateway/observability/costs/)
* [Custom metadata](https://developers.cloudflare.com/ai-gateway/observability/custom-metadata/)
* [OpenTelemetry](https://developers.cloudflare.com/ai-gateway/observability/otel-integration/)
* [Logging](https://developers.cloudflare.com/ai-gateway/observability/logging/)
---
title: Platform · Cloudflare AI Gateway docs
lastUpdated: 2025-05-09T15:42:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/reference/
md: https://developers.cloudflare.com/ai-gateway/reference/index.md
---
* [Audit logs](https://developers.cloudflare.com/ai-gateway/reference/audit-logs/)
* [Limits](https://developers.cloudflare.com/ai-gateway/reference/limits/)
* [Pricing](https://developers.cloudflare.com/ai-gateway/reference/pricing/)
---
title: Tutorials · Cloudflare AI Gateway docs
description: View tutorials to help you get started with AI Gateway.
lastUpdated: 2025-05-09T15:42:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-gateway/tutorials/
md: https://developers.cloudflare.com/ai-gateway/tutorials/index.md
---
View tutorials to help you get started with AI Gateway.
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [AI Gateway Binding Methods](https://developers.cloudflare.com/ai-gateway/integrations/worker-binding-methods/) | 10 months ago | |
| [Workers AI](https://developers.cloudflare.com/ai-gateway/integrations/aig-workers-ai-binding/) | over 1 year ago | |
| [Create your first AI Gateway using Workers AI](https://developers.cloudflare.com/ai-gateway/tutorials/create-first-aig-workers/) | over 1 year ago | Beginner |
| [Deploy a Worker that connects to OpenAI via AI Gateway](https://developers.cloudflare.com/ai-gateway/tutorials/deploy-aig-worker/) | over 2 years ago | Beginner |
## Videos
Cloudflare Workflows | Introduction (Part 1 of 3)
In this video, we introduce Cloudflare Workflows, the Newest Developer Platform Primitive at Cloudflare.
Cloudflare Workflows | Batching and Monitoring Your Durable Execution (Part 2 of 3)
Workflows exposes metrics such as execution, error rates, steps, and total duration!
Welcome to the Cloudflare Developer Channel
Welcome to the Cloudflare Developers YouTube channel. We've got tutorials and working demos and everything you need to level up your projects. Whether you're working on your next big thing or just dorking around with some side projects, we've got you covered! So why don't you come hang out, subscribe to our developer channel and together we'll build something awesome. You're gonna love it.
Optimize your AI App & fine-tune models (AI Gateway, R2)
In this workshop, Kristian Freeman, Cloudflare Developer Advocate, shows how to optimize your existing AI applications with Cloudflare AI Gateway, and how to finetune OpenAI models using R2.
How to use Cloudflare AI models and inference in Python with Jupyter Notebooks
Cloudflare Workers AI provides a ton of AI models and inference capabilities. In this video, we will explore how to make use of Cloudflare’s AI model catalog using a Python Jupyter Notebook.
---
title: Using AI Gateway · Cloudflare AI Gateway docs
lastUpdated: 2025-08-19T11:42:14.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-gateway/usage/
md: https://developers.cloudflare.com/ai-gateway/usage/index.md
---
##
---
title: 404 - Page Not Found · Cloudflare AI Crawl Control docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-crawl-control/404/
md: https://developers.cloudflare.com/ai-crawl-control/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Changelog · Cloudflare AI Crawl Control docs
description: Account administrators can now assign the AI Crawl Control Read
Only role to provide read-only access to AI Crawl Control at the domain level.
lastUpdated: 2025-08-27T16:00:59.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-crawl-control/changelog/
md: https://developers.cloudflare.com/ai-crawl-control/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/ai-crawl-control.xml)
## 2026-01-13
**AI Crawl Control Read Only role now available**
Account administrators can now assign the **AI Crawl Control Read Only** role to provide read-only access to AI Crawl Control at the domain level.
Users with this role can view the **Overview**, **Crawlers**, **Metrics**, **Robots.txt**, and **Settings** tabs but cannot modify crawler actions or settings.
This role is specific for AI Crawl Control. You still require correct permissions to access other areas / features of the dashboard.
To assign, go to **Manage Account** > **Members** and add a policy with the **AI Crawl Control Read Only** role scoped to the desired domain.
## 2025-12-18
**New AI Crawl Control Overview tab**
The **Overview** tab is now the default view in AI Crawl Control. The previous default view with controls for individual AI crawlers is available in the **Crawlers** tab.
#### What's new
* **Executive summary** — Monitor total requests, volume change, most common status code, most popular path, and high-volume activity
* **Operator grouping** — Track crawlers by their operating companies (OpenAI, Microsoft, Google, ByteDance, Anthropic, Meta)
* **Customizable filters** — Filter your snapshot by date range, crawler, operator, hostname, or path

#### Get started
1. Log in to the Cloudflare dashboard and select your account and domain.
2. Go to **AI Crawl Control**, where the **Overview** tab opens by default with your activity snapshot.
3. Use filters to customize your view by date range, crawler, operator, hostname, or path.
4. Navigate to the **Crawlers** tab to manage controls for individual crawlers.
Learn more about [analyzing AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/) and [managing AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/).
## 2025-12-10
**Pay Per Crawl (Private beta) - Discovery API, custom pricing, and advanced configuration**
Pay Per Crawl is introducing enhancements for both AI crawler operators and site owners, focusing on programmatic discovery, flexible pricing models, and granular configuration control.
#### For AI crawler operators
#### Discovery API
A new authenticated API endpoint allows verified crawlers to programmatically discover domains participating in Pay Per Crawl. Crawlers can use this to build optimized crawl queues, cache domain lists, and identify new participating sites. This eliminates the need to discover payable content through trial requests.
The API endpoint is `GET https://crawlers-api.ai-audit.cfdata.org/charged_zones` and requires Web Bot Auth authentication. Refer to [Discover payable content](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/discover-payable-content/) for authentication steps, request parameters, and response schema.
#### Payment header signature requirement
Payment headers (`crawler-exact-price` or `crawler-max-price`) must now be included in the Web Bot Auth `signature-input` header components. This security enhancement prevents payment header tampering, ensures authenticated payment intent, validates crawler identity with payment commitment, and protects against replay attacks with modified pricing. Crawlers must add their payment header to the list of signed components when [constructing the signature-input header](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/#22-sign-your-request-with-web-bot-auth).
#### New `crawler-error` header
Pay Per Crawl error responses now include a new `crawler-error` header with 11 specific [error codes](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/#error-code-reference) for programmatic handling. Error response bodies remain unchanged for compatibility. These codes enable robust error handling, automated retry logic, and accurate spending tracking.
#### For site owners
#### Configure free pages
Site owners can now offer free access to specific pages like homepages, navigation, or discovery pages while charging for other content. Create a [Configuration Rule](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-site-owner/advanced-configuration/#disable-pay-per-crawl-by-uri-pattern) in **Rules** > **Configuration Rules**, set your URI pattern using wildcard, exact, or prefix matching on the **URI Full** field, and enable the **Disable Pay Per Crawl** setting. When disabled for a URI pattern, crawler requests pass through without blocking or charging.
Some paths are always free to crawl. These paths are: `/robots.txt`, `/sitemap.xml`, `/security.txt`, `/.well-known/security.txt`, `/crawlers.json`.
#### Get started
**AI crawler operators**: [Discover payable content](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/discover-payable-content/) | [Crawl pages](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/)
**Site owners**: [Advanced configuration](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-site-owner/advanced-configuration/)
## 2025-11-10
**Crawler drilldowns with extended actions menu**
AI Crawl Control now supports per-crawler drilldowns with an extended actions menu and status code analytics. Drill down into Metrics, Cloudflare Radar, and Security Analytics, or export crawler data for use in [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/), [Redirect Rules](https://developers.cloudflare.com/rules/url-forwarding/), and robots.txt files.
#### What's new
#### Status code distribution chart
The **Metrics** tab includes a status code distribution chart showing HTTP response codes (2xx, 3xx, 4xx, 5xx) over time. Filter by individual crawler, category, operator, or time range to analyze how specific crawlers interact with your site.

#### Extended actions menu
Each crawler row includes a three-dot menu with per-crawler actions:
* **View Metrics** — Filter the AI Crawl Control Metrics page to the selected crawler.
* **View on Cloudflare Radar** — Access verified crawler details on Cloudflare Radar.
* **Copy User Agent** — Copy user agent strings for use in WAF custom rules, Redirect Rules, or robots.txt files.
* **View in Security Analytics** — Filter Security Analytics by detection IDs (Bot Management customers).
* **Copy Detection ID** — Copy detection IDs for use in WAF custom rules (Bot Management customers).

#### Get started
1. Log in to the Cloudflare dashboard, and select your account and domain.
2. Go to **AI Crawl Control** > **Metrics** to access the status code distribution chart.
3. Go to **AI Crawl Control** > **Crawlers** and select the three-dot menu for any crawler to access per-crawler actions.
4. Select multiple crawlers to use bulk copy buttons for user agents or detection IDs.
Learn more about [AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/).
## 2025-10-21
**New Robots.txt tab for tracking crawler compliance**
AI Crawl Control now includes a **Robots.txt** tab that provides insights into how AI crawlers interact with your `robots.txt` files.
#### What's new
The Robots.txt tab allows you to:
* Monitor the health status of `robots.txt` files across all your hostnames, including HTTP status codes, and identify hostnames that need a `robots.txt` file.
* Track the total number of requests to each `robots.txt` file, with breakdowns of successful versus unsuccessful requests.
* Check whether your `robots.txt` files contain [Content Signals](https://contentsignals.org/) directives for AI training, search, and AI input.
* Identify crawlers that request paths explicitly disallowed by your `robots.txt` directives, including the crawler name, operator, violated path, specific directive, and violation count.
* Filter `robots.txt` request data by crawler, operator, category, and custom time ranges.
#### Take action
When you identify non-compliant crawlers, you can:
* Block the crawler in the [Crawlers tab](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/)
* Create custom [WAF rules](https://developers.cloudflare.com/waf/) for path-specific security
* Use [Redirect Rules](https://developers.cloudflare.com/rules/url-forwarding/) to guide crawlers to appropriate areas of your site
To get started, go to **AI Crawl Control** > **Robots.txt** in the Cloudflare dashboard. Learn more in the [Track robots.txt documentation](https://developers.cloudflare.com/ai-crawl-control/features/track-robots-txt/).
## 2025-10-14
**Enhanced AI Crawl Control metrics with new drilldowns and filters**
AI Crawl Control now provides enhanced metrics and CSV data exports to help you better understand AI crawler activity across your sites.
#### What's new
#### Track crawler requests over time
Visualize crawler activity patterns over time, and group data by different dimensions:
* **By Crawler** — Track activity from individual AI crawlers (GPTBot, ClaudeBot, Bytespider)
* **By Category** — Analyze crawler purpose or type
* **By Operator** — Discover which companies (OpenAI, Anthropic, ByteDance) are crawling your site
* **By Host** — Break down activity across multiple subdomains
* **By Status Code** — Monitor HTTP response codes to crawlers (200s, 300s, 400s, 500s)
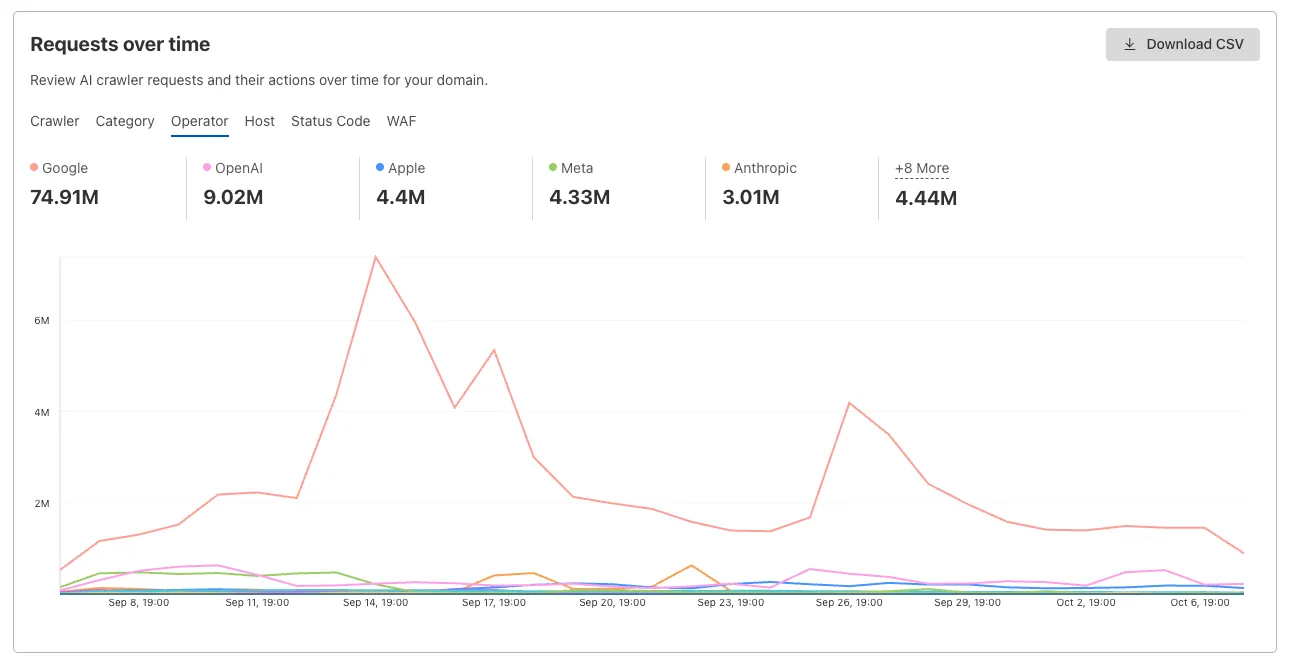
#### Analyze referrer data (Paid plans)
Identify traffic sources with referrer analytics:
* View top referrers driving traffic to your site
* Understand discovery patterns and content popularity from AI operators
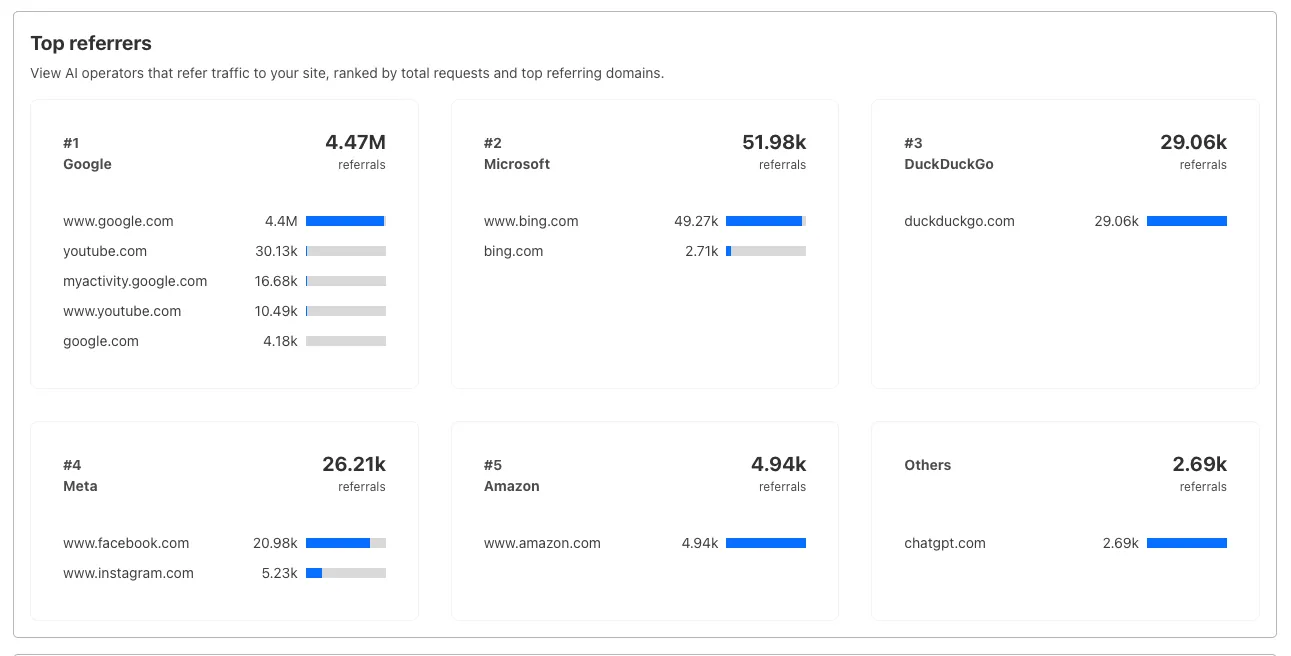
#### Export data
Download your filtered view as a CSV:
* Includes all applied filters and groupings
* Useful for custom reporting and deeper analysis
#### Get started
1. Log in to the Cloudflare dashboard, and select your account and domain.
2. Go to **AI Crawl Control** > **Metrics**.
3. Use the grouping tabs to explore different views of your data.
4. Apply filters to focus on specific crawlers, time ranges, or response codes.
5. Select **Download CSV** to export your filtered data for further analysis.
Learn more about [AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control).
## 2025-08-27
**Enhanced crawler insights and custom 402 responses**
We improved AI crawler management with detailed analytics and introduced custom HTTP 402 responses for blocked crawlers. AI Audit has been renamed to AI Crawl Control and is now generally available.
**Enhanced Crawlers tab:**
* View total allowed and blocked requests for each AI crawler
* Trend charts show crawler activity over your selected time range per crawler

**Custom block responses (paid plans):** You can now return HTTP 402 "Payment Required" responses when blocking AI crawlers, enabling direct communication with crawler operators about licensing terms.
For users on paid plans, when blocking AI crawlers you can configure:
* **Response code:** Choose between 403 Forbidden or 402 Payment Required
* **Response body:** Add a custom message with your licensing contact information

Example 402 response:
```http
HTTP 402 Payment Required
Date: Mon, 24 Aug 2025 12:56:49 GMT
Content-type: application/json
Server: cloudflare
Cf-Ray: 967e8da599d0c3fa-EWR
Cf-Team: 2902f6db750000c3fa1e2ef400000001
{
"message": "Please contact the site owner for access."
}
```
## 2025-07-01
**Introducing Pay Per Crawl (private beta)**
We are introducing a new feature of [AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/) — Pay Per Crawl. [Pay Per Crawl](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/) enables site owners to require payment from AI crawlers every time the crawlers access their content, thereby fostering a fairer Internet by enabling site owners to control and monetize how their content gets used by AI.
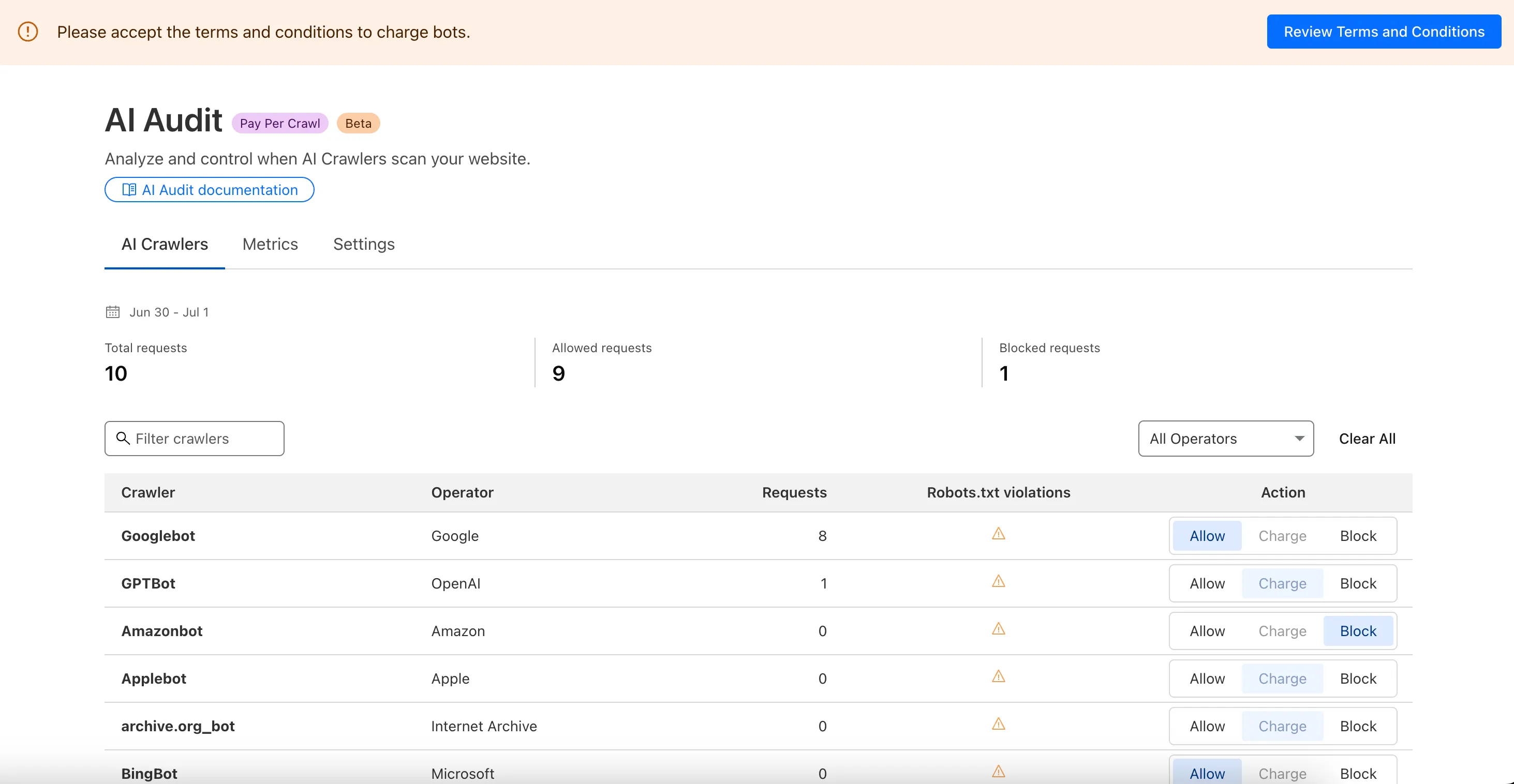
**For Site Owners:**
* Set pricing and select which crawlers to charge for content access
* Manage payments via Stripe
* Monitor analytics on successful content deliveries
**For AI Crawler Owners:**
* Use HTTP headers to request and accept pricing
* Receive clear confirmations on charges for accessed content
Learn more in the [Pay Per Crawl documentation](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/).
## 2025-07-01
**AI Crawl Control refresh**
We redesigned the AI Crawl Control dashboard to provide more intuitive and granular control over AI crawlers.
* From the new **AI Crawlers** tab: block specific AI crawlers.
* From the new **Metrics** tab: view AI Crawl Control metrics.
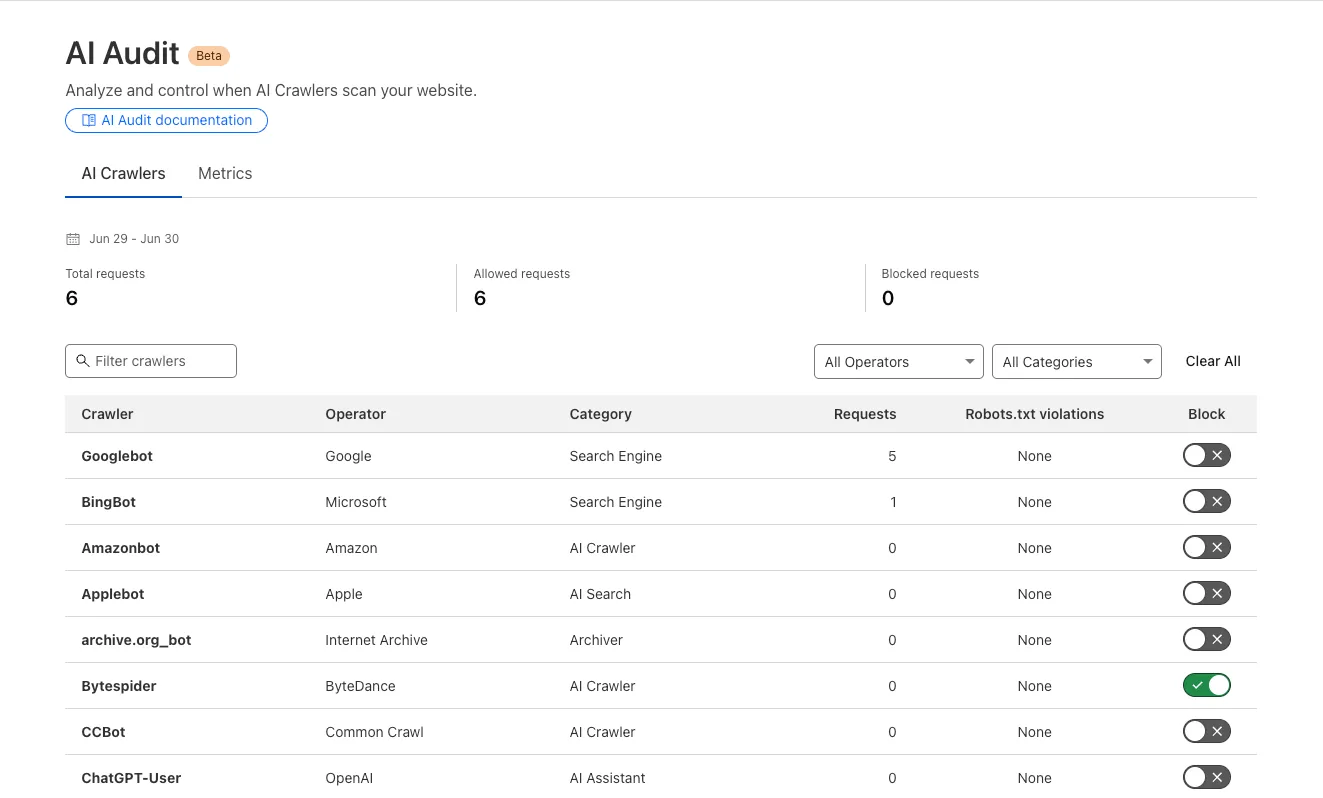 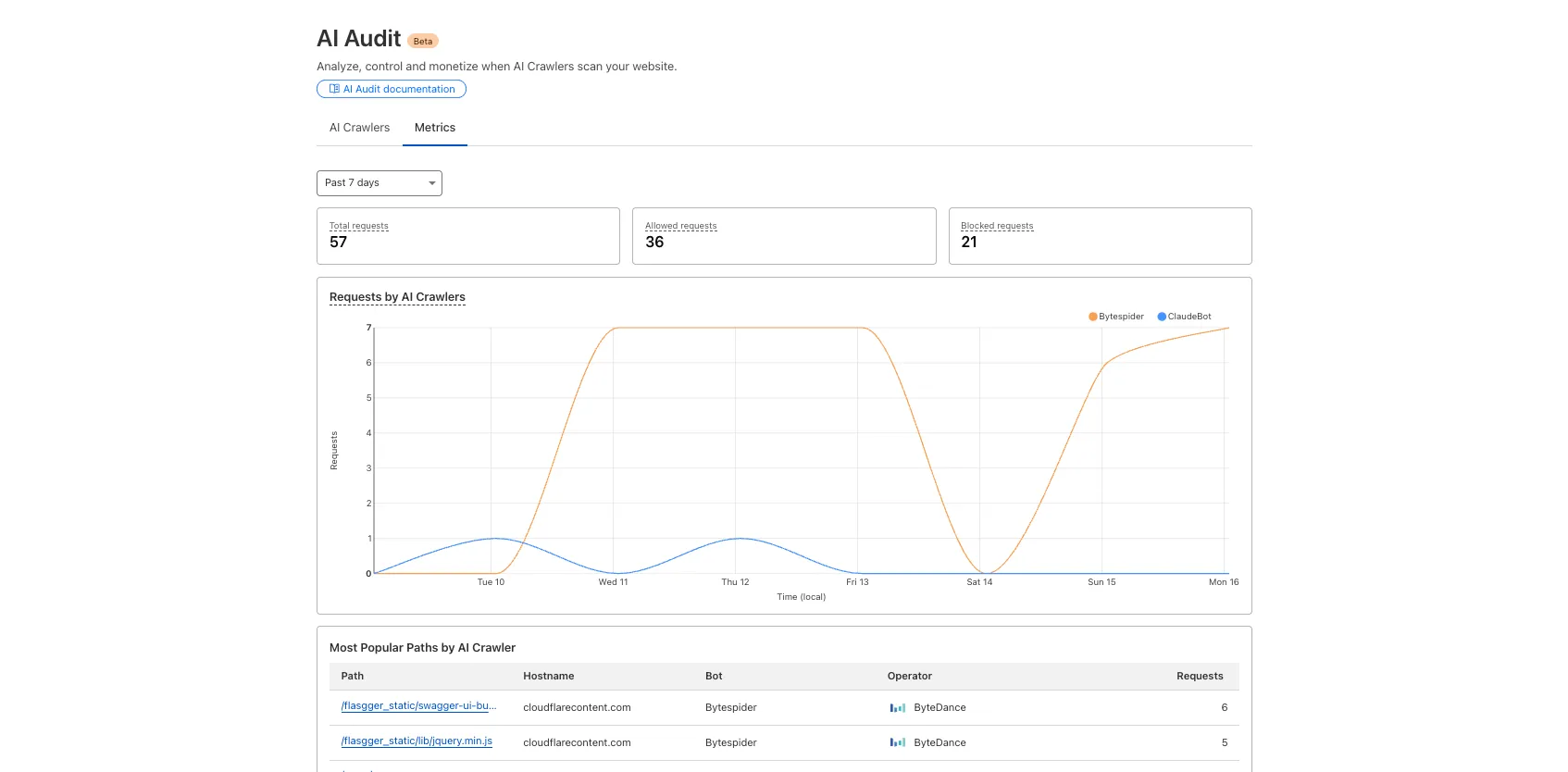
To get started, explore:
* [Manage AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/).
* [Analyze AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/).
## 2024-09-23
**AI Crawl Control**
Every site on Cloudflare now has access to [**AI Audit**](https://developers.cloudflare.com/ai-crawl-control/), which summarizes the crawling behavior of popular and known AI services.
You can use this data to:
* Understand how and how often crawlers access your site (and which content is the most popular).
* Block specific AI bots accessing your site.
* Use Cloudflare to enforce your `robots.txt` policy via an automatic WAF rule.
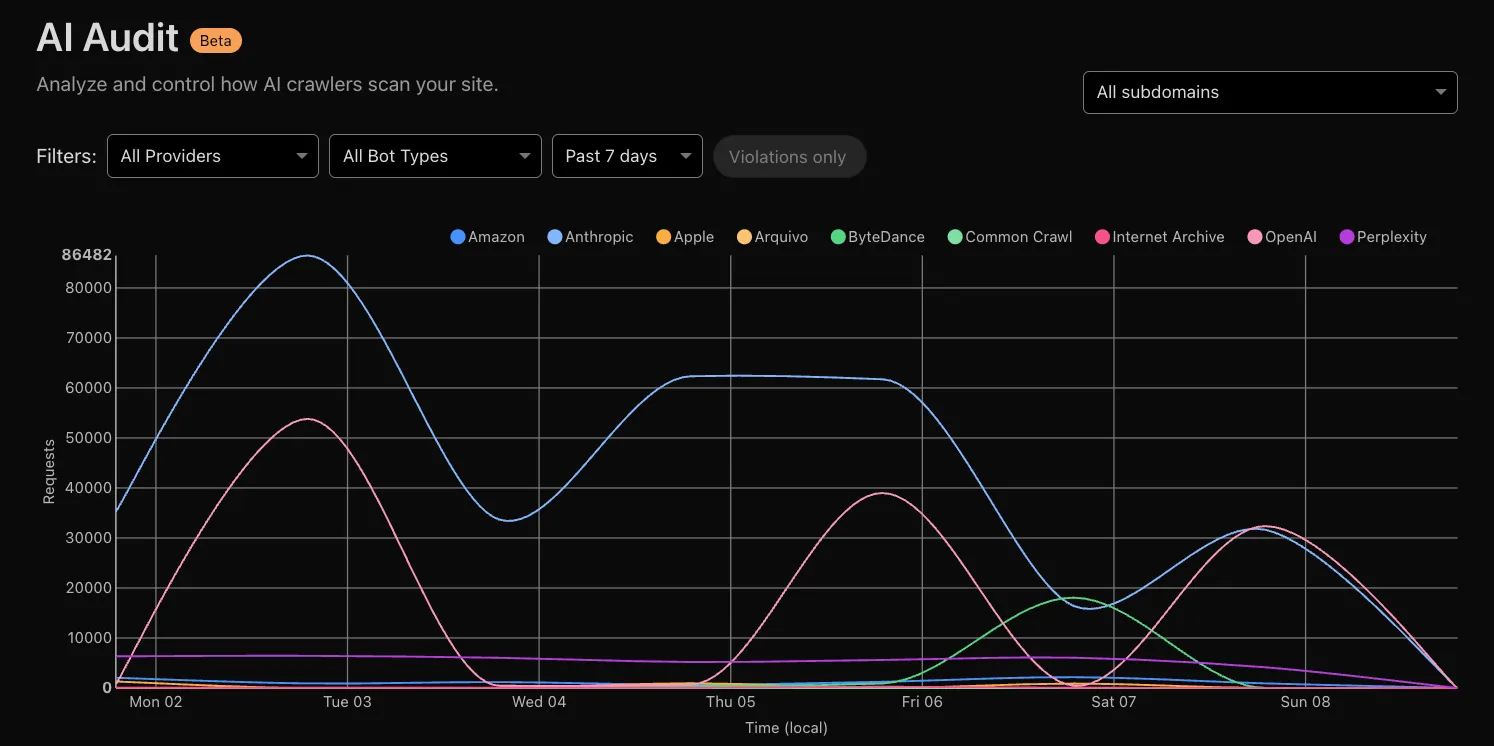
To get started, explore [AI audit](https://developers.cloudflare.com/ai-crawl-control/).
---
title: Configuration · Cloudflare AI Crawl Control docs
lastUpdated: 2025-08-27T16:00:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-crawl-control/configuration/
md: https://developers.cloudflare.com/ai-crawl-control/configuration/index.md
---
* [AI Crawl Control with Cloudflare WAF](https://developers.cloudflare.com/ai-crawl-control/configuration/ai-crawl-control-with-waf/)
* [AI Crawl Control with Cloudflare Bots](https://developers.cloudflare.com/ai-crawl-control/configuration/ai-crawl-control-with-bots/)
---
title: Features · Cloudflare AI Crawl Control docs
lastUpdated: 2025-08-27T16:00:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-crawl-control/features/
md: https://developers.cloudflare.com/ai-crawl-control/features/index.md
---
* [Analyze AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/)
* [Manage AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/)
* [Track robots.txt](https://developers.cloudflare.com/ai-crawl-control/features/track-robots-txt/)
* [Pay Per Crawl](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/)
---
title: Get started with Cloudflare AI Crawl Control · Cloudflare AI Crawl Control docs
description: Learn how to set up AI Crawl Control.
lastUpdated: 2025-12-18T09:52:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-crawl-control/get-started/
md: https://developers.cloudflare.com/ai-crawl-control/get-started/index.md
---
This guide instructs you on how to:
* View AI crawlers that are interacting with pages in your domain (a [Cloudflare zone](https://developers.cloudflare.com/fundamentals/concepts/accounts-and-zones/#zones)).
* Use AI Crawl Control to block individual crawlers from accessing your content.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/).
2. [Connect your domain to Cloudflare](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/).
3. Make sure your domain is [proxying traffic through Cloudflare](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/#cloudflare-as-a-reverse-proxy).
## 1. Monitor AI crawler activity at a glance
1. Go to **AI Crawl Control**.
[Go to **AI Crawl Control**](https://dash.cloudflare.com/?to=/:account/:zone/ai)
2. Review the snapshot of your AI crawler activity in the **Overview** tab.
3. Use the filters to view activity by specific date ranges, crawlers, operators, hostnames, or paths.
## 2. Block specific AI crawlers
* All plans
To block specific AI crawlers:
1. Go to **AI Crawl Control**.
[Go to **AI Crawl Control**](https://dash.cloudflare.com/?to=/:account/:zone/ai)
2. Review which AI crawlers are accessing your domain in the **Crawlers** tab.
3. In the **Action** column, select **Block**.
Quality of AI crawler detection
On the free plan, AI Crawl Control identifies AI crawlers based on their [user agent strings](https://developer.mozilla.org/en-US/docs/Web/HTTP/Reference/Headers/User-Agent). This enables AI Crawl Control to detect well-known, self-identifying AI crawlers.
Upgrade your plan to enable a more thorough detection using Cloudflare's [Bot Management detection ID](https://developers.cloudflare.com/bots/reference/bot-management-variables/#ruleset-engine-fields) field.
* Paid plans
To block specific AI crawlers:
1. Go to **AI Crawl Control**.
[Go to **AI Crawl Control**](https://dash.cloudflare.com/?to=/:account/:zone/ai)
2. Review which AI crawlers are accessing your domain in the **Crawlers** tab.
3. In the **Action** column, select **Block**.
For more information, refer to [Manage AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/).
You can also create more complex rules when taking action on AI crawlers, using [Cloudflare WAF](https://developers.cloudflare.com/waf/). For more information on creating more specific rules, refer to [Create a custom rule in the dashboard](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/).
## 3. Explore detailed metrics
* All plans
For more detailed analytics, use the **Metrics** tab.
1. Go to **AI Crawl Control**.
[Go to **AI Crawl Control**](https://dash.cloudflare.com/?to=/:account/:zone/ai)
2. Review detailed breakdowns by date range, crawler, operator, status code, hostname, or path in the **Metrics** tab.
Note that on free plans, the **Metrics** tab only displays metrics for the past 24 hours.
## Plan comparison
| All plans | Enterprise plans with Bot Management |
| - | - |
| AI crawler detection via [user agent strings](https://developer.mozilla.org/en-US/docs/Web/HTTP/Reference/Headers/User-Agent) | Advanced AI crawler detection via [Bot Management detection ID](https://developers.cloudflare.com/bots/reference/bot-management-variables/#ruleset-engine-fields) |
| Maximum 24-hour analytics window | Configurable analytics timeframes |
| Allow/block controls | Allow/block controls, and the ability to charge AI crawlers using [pay per crawl](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/) |
## Next steps
* [Manage AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/) with granular allow/block controls.
* [Analyze AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/) to understand crawler patterns and content popularity.
* [Explore pay per crawl](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/) to test content monetization options (private beta).
## Related resources
Refer to the following related resources:
* Cloudflare blog: [Start auditing and controlling the AI models accessing your content](https://blog.cloudflare.com/nl-nl/cloudflare-ai-audit-control-ai-content-crawlers/)
* Block AI crawlers that do not adhere to recommended guidelines using [Cloudflare AI Labyrinth](https://developers.cloudflare.com/bots/additional-configurations/ai-labyrinth/).
* [Direct AI crawlers with managed robots.txt](https://developers.cloudflare.com/bots/additional-configurations/managed-robots-txt/).
---
title: Reference · Cloudflare AI Crawl Control docs
lastUpdated: 2025-08-27T16:00:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-crawl-control/reference/
md: https://developers.cloudflare.com/ai-crawl-control/reference/index.md
---
* [Glossary](https://developers.cloudflare.com/ai-crawl-control/reference/glossary/)
---
title: 404 - Page Not Found · Cloudflare Agents docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/agents/404/
md: https://developers.cloudflare.com/agents/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Concepts · Cloudflare Agents docs
lastUpdated: 2025-02-25T13:55:21.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/agents/concepts/
md: https://developers.cloudflare.com/agents/concepts/index.md
---
* [What are agents?](https://developers.cloudflare.com/agents/concepts/what-are-agents/)
* [Workflows](https://developers.cloudflare.com/agents/concepts/workflows/)
* [Tools](https://developers.cloudflare.com/agents/concepts/tools/)
* [Agent class internals](https://developers.cloudflare.com/agents/concepts/agent-class/)
* [Human in the Loop](https://developers.cloudflare.com/agents/concepts/human-in-the-loop/)
* [Calling LLMs](https://developers.cloudflare.com/agents/concepts/calling-llms/)
---
title: Getting started · Cloudflare Agents docs
lastUpdated: 2026-02-05T16:44:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/agents/getting-started/
md: https://developers.cloudflare.com/agents/getting-started/index.md
---
* [Quick start](https://developers.cloudflare.com/agents/getting-started/quick-start/)
* [Add to existing project](https://developers.cloudflare.com/agents/getting-started/add-to-existing-project/)
* [Testing your Agents](https://developers.cloudflare.com/agents/getting-started/testing-your-agent/)
* [Build a Chat Agent](https://github.com/cloudflare/agents-starter)
* [Prompt an AI model](https://developers.cloudflare.com/workers/get-started/prompting/)
---
title: API Reference · Cloudflare Agents docs
description: "Learn more about what Agents can do, the Agent class, and the APIs
that Agents expose:"
lastUpdated: 2026-02-05T16:44:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/agents/api-reference/
md: https://developers.cloudflare.com/agents/api-reference/index.md
---
Learn more about what Agents can do, the `Agent` class, and the APIs that Agents expose:
* [Agents API](https://developers.cloudflare.com/agents/api-reference/agents-api/)
* [Routing](https://developers.cloudflare.com/agents/api-reference/routing/)
* [Configuration](https://developers.cloudflare.com/agents/api-reference/configuration/)
* [Client SDK](https://developers.cloudflare.com/agents/api-reference/client-sdk/)
* [Callable methods](https://developers.cloudflare.com/agents/api-reference/callable-methods/)
* [Store and sync state](https://developers.cloudflare.com/agents/api-reference/store-and-sync-state/)
* [WebSockets](https://developers.cloudflare.com/agents/api-reference/websockets/)
* [HTTP and Server-Sent Events](https://developers.cloudflare.com/agents/api-reference/http-sse/)
* [Schedule tasks](https://developers.cloudflare.com/agents/api-reference/schedule-tasks/)
* [Queue tasks](https://developers.cloudflare.com/agents/api-reference/queue-tasks/)
* [Run Workflows](https://developers.cloudflare.com/agents/api-reference/run-workflows/)
* [Using AI Models](https://developers.cloudflare.com/agents/api-reference/using-ai-models/)
* [Retrieval Augmented Generation](https://developers.cloudflare.com/agents/api-reference/rag/)
* [Browse the web](https://developers.cloudflare.com/agents/api-reference/browse-the-web/)
* [Email routing](https://developers.cloudflare.com/agents/api-reference/email/)
* [getCurrentAgent()](https://developers.cloudflare.com/agents/api-reference/get-current-agent/)
* [Observability](https://developers.cloudflare.com/agents/api-reference/observability/)
---
title: Guides · Cloudflare Agents docs
lastUpdated: 2026-02-05T16:44:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/agents/guides/
md: https://developers.cloudflare.com/agents/guides/index.md
---
* [Implement Effective Agent Patterns](https://github.com/cloudflare/agents/tree/main/guides/anthropic-patterns)
* [Human-in-the-loop patterns](https://developers.cloudflare.com/agents/guides/human-in-the-loop/)
* [Webhooks](https://developers.cloudflare.com/agents/guides/webhooks/)
* [Build a Slack Agent](https://developers.cloudflare.com/agents/guides/slack-agent/)
* [Build an Interactive ChatGPT App](https://developers.cloudflare.com/agents/guides/chatgpt-app/)
* [Build a Remote MCP server](https://developers.cloudflare.com/agents/guides/remote-mcp-server/)
* [Test a Remote MCP Server](https://developers.cloudflare.com/agents/guides/test-remote-mcp-server/)
* [Securing MCP servers](https://developers.cloudflare.com/agents/guides/securing-mcp-server/)
* [Connect to an MCP server](https://developers.cloudflare.com/agents/guides/connect-mcp-client/)
* [Build a Remote MCP Client](https://github.com/cloudflare/ai/tree/main/demos/mcp-client)
* [Handle OAuth with MCP servers](https://developers.cloudflare.com/agents/guides/oauth-mcp-client/)
* [Cross-domain authentication](https://developers.cloudflare.com/agents/guides/cross-domain-authentication/)
---
title: Model Context Protocol (MCP) · Cloudflare Agents docs
description: You can build and deploy Model Context Protocol (MCP) servers on Cloudflare.
lastUpdated: 2026-02-05T16:44:57.000Z
chatbotDeprioritize: false
tags: MCP
source_url:
html: https://developers.cloudflare.com/agents/model-context-protocol/
md: https://developers.cloudflare.com/agents/model-context-protocol/index.md
---
You can build and deploy [Model Context Protocol (MCP)](https://modelcontextprotocol.io/) servers on Cloudflare.
## What is the Model Context Protocol (MCP)?
[Model Context Protocol (MCP)](https://modelcontextprotocol.io) is an open standard that connects AI systems with external applications. Think of MCP like a USB-C port for AI applications. Just as USB-C provides a standardized way to connect your devices to various accessories, MCP provides a standardized way to connect AI agents to different services.
### MCP Terminology
* **MCP Hosts**: AI assistants (like [Claude](http://claude.ai) or [Cursor](http://cursor.com)), AI agents, or applications that need to access external capabilities.
* **MCP Clients**: Clients embedded within the MCP hosts that connect to MCP servers and invoke tools. Each MCP client instance has a single connection to an MCP server.
* **MCP Servers**: Applications that expose [tools](https://developers.cloudflare.com/agents/model-context-protocol/tools/), [prompts](https://modelcontextprotocol.io/docs/concepts/prompts), and [resources](https://modelcontextprotocol.io/docs/concepts/resources) that MCP clients can use.
### Remote vs. local MCP connections
The MCP standard supports two modes of operation:
* **Remote MCP connections**: MCP clients connect to MCP servers over the Internet, establishing a connection using [Streamable HTTP](https://developers.cloudflare.com/agents/model-context-protocol/transport/), and authorizing the MCP client access to resources on the user's account using [OAuth](https://developers.cloudflare.com/agents/model-context-protocol/authorization/).
* **Local MCP connections**: MCP clients connect to MCP servers on the same machine, using [stdio](https://spec.modelcontextprotocol.io/specification/draft/basic/transports/#stdio) as a local transport method.
### Best Practices
* **Tool design**: Do not treat your MCP server as a wrapper around your full API schema. Instead, build tools that are optimized for specific user goals and reliable outcomes. Fewer, well-designed tools often outperform many granular ones, especially for agents with small context windows or tight latency budgets.
* **Scoped permissions**: Deploying several focused MCP servers, each with narrowly scoped permissions, reduces the risk of over-privileged access and makes it easier to manage and audit what each server is allowed to do.
* **Tool descriptions**: Detailed parameter descriptions help agents understand how to use your tools correctly — including what values are expected, how they affect behavior, and any important constraints. This reduces errors and improves reliability.
* **Evaluation tests**: Use evaluation tests ('evals') to measure the agent’s ability to use your tools correctly. Run these after any updates to your server or tool descriptions to catch regressions early and track improvements over time.
### Get Started
Go to the [Getting Started](https://developers.cloudflare.com/agents/guides/remote-mcp-server/) guide to learn how to build and deploy your first remote MCP server to Cloudflare.
---
title: Patterns · Cloudflare Agents docs
description: This page lists and defines common patterns for implementing AI
agents, based on Anthropic's patterns for building effective agents.
lastUpdated: 2026-02-05T16:44:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/agents/patterns/
md: https://developers.cloudflare.com/agents/patterns/index.md
---
This page lists and defines common patterns for implementing AI agents, based on [Anthropic's patterns for building effective agents](https://www.anthropic.com/research/building-effective-agents).
Code samples use the [AI SDK](https://sdk.vercel.ai/docs/foundations/agents), running in [Durable Objects](https://developers.cloudflare.com/durable-objects).
## Prompt Chaining
Decomposes tasks into a sequence of steps, where each LLM call processes the output of the previous one.
```ts
import { openai } from "@ai-sdk/openai";
import { generateText, generateObject } from "ai";
import { z } from "zod";
export default async function generateMarketingCopy(input: string) {
const model = openai("gpt-4o");
// First step: Generate marketing copy
const { text: copy } = await generateText({
model,
prompt: `Write persuasive marketing copy for: ${input}. Focus on benefits and emotional appeal.`,
});
// Perform quality check on copy
const { object: qualityMetrics } = await generateObject({
model,
schema: z.object({
hasCallToAction: z.boolean(),
emotionalAppeal: z.number().min(1).max(10),
clarity: z.number().min(1).max(10),
}),
prompt: `Evaluate this marketing copy for:
1. Presence of call to action (true/false)
2. Emotional appeal (1-10)
3. Clarity (1-10)
Copy to evaluate: ${copy}`,
});
// If quality check fails, regenerate with more specific instructions
if (
!qualityMetrics.hasCallToAction ||
qualityMetrics.emotionalAppeal < 7 ||
qualityMetrics.clarity < 7
) {
const { text: improvedCopy } = await generateText({
model,
prompt: `Rewrite this marketing copy with:
${!qualityMetrics.hasCallToAction ? "- A clear call to action" : ""}
${qualityMetrics.emotionalAppeal < 7 ? "- Stronger emotional appeal" : ""}
${qualityMetrics.clarity < 7 ? "- Improved clarity and directness" : ""}
Original copy: ${copy}`,
});
return { copy: improvedCopy, qualityMetrics };
}
return { copy, qualityMetrics };
}
```
## Routing
Classifies input and directs it to specialized followup tasks, allowing for separation of concerns.

```ts
import { openai } from '@ai-sdk/openai';
import { generateObject, generateText } from 'ai';
import { z } from 'zod';
async function handleCustomerQuery(query: string) {
const model = openai('gpt-4o');
// First step: Classify the query type
const { object: classification } = await generateObject({
model,
schema: z.object({
reasoning: z.string(),
type: z.enum(['general', 'refund', 'technical']),
complexity: z.enum(['simple', 'complex']),
}),
prompt: `Classify this customer query:
${query}
Determine:
1. Query type (general, refund, or technical)
2. Complexity (simple or complex)
3. Brief reasoning for classification`,
});
// Route based on classification
// Set model and system prompt based on query type and complexity
const { text: response } = await generateText({
model:
classification.complexity === 'simple'
? openai('gpt-4o-mini')
: openai('o1-mini'),
system: {
general:
'You are an expert customer service agent handling general inquiries.',
refund:
'You are a customer service agent specializing in refund requests. Follow company policy and collect necessary information.',
technical:
'You are a technical support specialist with deep product knowledge. Focus on clear step-by-step troubleshooting.',
}[classification.type],
prompt: query,
});
return { response, classification };
}
```
## Parallelization
Enables simultaneous task processing through sectioning or voting mechanisms.
```ts
import { openai } from '@ai-sdk/openai';
import { generateText, generateObject } from 'ai';
import { z } from 'zod';
// Example: Parallel code review with multiple specialized reviewers
async function parallelCodeReview(code: string) {
const model = openai('gpt-4o');
// Run parallel reviews
const [securityReview, performanceReview, maintainabilityReview] =
await Promise.all([
generateObject({
model,
system:
'You are an expert in code security. Focus on identifying security vulnerabilities, injection risks, and authentication issues.',
schema: z.object({
vulnerabilities: z.array(z.string()),
riskLevel: z.enum(['low', 'medium', 'high']),
suggestions: z.array(z.string()),
}),
prompt: `Review this code:
${code}`,
}),
generateObject({
model,
system:
'You are an expert in code performance. Focus on identifying performance bottlenecks, memory leaks, and optimization opportunities.',
schema: z.object({
issues: z.array(z.string()),
impact: z.enum(['low', 'medium', 'high']),
optimizations: z.array(z.string()),
}),
prompt: `Review this code:
${code}`,
}),
generateObject({
model,
system:
'You are an expert in code quality. Focus on code structure, readability, and adherence to best practices.',
schema: z.object({
concerns: z.array(z.string()),
qualityScore: z.number().min(1).max(10),
recommendations: z.array(z.string()),
}),
prompt: `Review this code:
${code}`,
}),
]);
const reviews = [
{ ...securityReview.object, type: 'security' },
{ ...performanceReview.object, type: 'performance' },
{ ...maintainabilityReview.object, type: 'maintainability' },
];
// Aggregate results using another model instance
const { text: summary } = await generateText({
model,
system: 'You are a technical lead summarizing multiple code reviews.',
prompt: `Synthesize these code review results into a concise summary with key actions:
${JSON.stringify(reviews, null, 2)}`,
});
return { reviews, summary };
}
```
## Orchestrator-Workers
A central LLM dynamically breaks down tasks, delegates to Worker LLMs, and synthesizes results.

```ts
import { openai } from '@ai-sdk/openai';
import { generateObject } from 'ai';
import { z } from 'zod';
async function implementFeature(featureRequest: string) {
// Orchestrator: Plan the implementation
const { object: implementationPlan } = await generateObject({
model: openai('o1'),
schema: z.object({
files: z.array(
z.object({
purpose: z.string(),
filePath: z.string(),
changeType: z.enum(['create', 'modify', 'delete']),
}),
),
estimatedComplexity: z.enum(['low', 'medium', 'high']),
}),
system:
'You are a senior software architect planning feature implementations.',
prompt: `Analyze this feature request and create an implementation plan:
${featureRequest}`,
});
// Workers: Execute the planned changes
const fileChanges = await Promise.all(
implementationPlan.files.map(async file => {
// Each worker is specialized for the type of change
const workerSystemPrompt = {
create:
'You are an expert at implementing new files following best practices and project patterns.',
modify:
'You are an expert at modifying existing code while maintaining consistency and avoiding regressions.',
delete:
'You are an expert at safely removing code while ensuring no breaking changes.',
}[file.changeType];
const { object: change } = await generateObject({
model: openai('gpt-4o'),
schema: z.object({
explanation: z.string(),
code: z.string(),
}),
system: workerSystemPrompt,
prompt: `Implement the changes for ${file.filePath} to support:
${file.purpose}
Consider the overall feature context:
${featureRequest}`,
});
return {
file,
implementation: change,
};
}),
);
return {
plan: implementationPlan,
changes: fileChanges,
};
}
```
## Evaluator-Optimizer
One LLM generates responses while another provides evaluation and feedback in a loop.
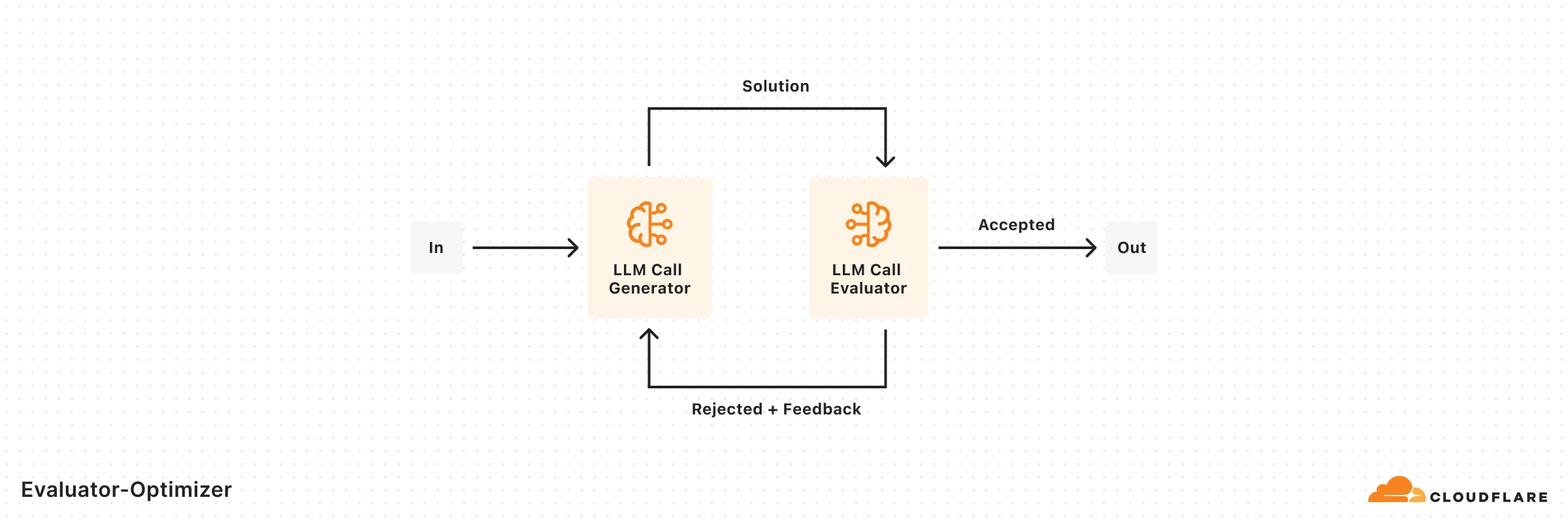
```ts
import { openai } from '@ai-sdk/openai';
import { generateText, generateObject } from 'ai';
import { z } from 'zod';
async function translateWithFeedback(text: string, targetLanguage: string) {
let currentTranslation = '';
let iterations = 0;
const MAX_ITERATIONS = 3;
// Initial translation
const { text: translation } = await generateText({
model: openai('gpt-4o-mini'), // use small model for first attempt
system: 'You are an expert literary translator.',
prompt: `Translate this text to ${targetLanguage}, preserving tone and cultural nuances:
${text}`,
});
currentTranslation = translation;
// Evaluation-optimization loop
while (iterations < MAX_ITERATIONS) {
// Evaluate current translation
const { object: evaluation } = await generateObject({
model: openai('gpt-4o'), // use a larger model to evaluate
schema: z.object({
qualityScore: z.number().min(1).max(10),
preservesTone: z.boolean(),
preservesNuance: z.boolean(),
culturallyAccurate: z.boolean(),
specificIssues: z.array(z.string()),
improvementSuggestions: z.array(z.string()),
}),
system: 'You are an expert in evaluating literary translations.',
prompt: `Evaluate this translation:
Original: ${text}
Translation: ${currentTranslation}
Consider:
1. Overall quality
2. Preservation of tone
3. Preservation of nuance
4. Cultural accuracy`,
});
// Check if quality meets threshold
if (
evaluation.qualityScore >= 8 &&
evaluation.preservesTone &&
evaluation.preservesNuance &&
evaluation.culturallyAccurate
) {
break;
}
// Generate improved translation based on feedback
const { text: improvedTranslation } = await generateText({
model: openai('gpt-4o'), // use a larger model
system: 'You are an expert literary translator.',
prompt: `Improve this translation based on the following feedback:
${evaluation.specificIssues.join('\n')}
${evaluation.improvementSuggestions.join('\n')}
Original: ${text}
Current Translation: ${currentTranslation}`,
});
currentTranslation = improvedTranslation;
iterations++;
}
return {
finalTranslation: currentTranslation,
iterationsRequired: iterations,
};
}
```
---
title: Platform · Cloudflare Agents docs
lastUpdated: 2026-02-05T16:44:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/agents/platform/
md: https://developers.cloudflare.com/agents/platform/index.md
---
* [Limits](https://developers.cloudflare.com/agents/platform/limits/)
* [Prompt Engineering](https://developers.cloudflare.com/workers/get-started/prompting/)
* [prompt.txt](https://developers.cloudflare.com/workers/prompt.txt)
---
title: x402 · Cloudflare Agents docs
description: x402 is an open payment standard that enables services to charge
for access to their APIs and content directly over HTTP. It is built around
the HTTP 402 Payment Required status code and allows clients to
programmatically pay for resources without accounts, sessions, or credential
management.
lastUpdated: 2026-02-05T16:44:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/agents/x402/
md: https://developers.cloudflare.com/agents/x402/index.md
---
## What is x402?
[x402](https://www.x402.org/) is an open payment standard that enables services to charge for access to their APIs and content directly over HTTP. It is built around the HTTP 402 Payment Required status code and allows clients to programmatically pay for resources without accounts, sessions, or credential management.
## x402 Workers and Agents
You can create paywalled endpoints in your Workers and query any x402 server from your agent by wrapping the `fetch` with x402 and your account.
```ts
import { Hono } from "hono";
import { Agent, getAgentByName } from "agents";
import { wrapFetchWithPayment } from "x402-fetch";
import { paymentMiddleware } from "x402-hono";
// This allows us to derive an account from just the private key
import { privateKeyToAccount } from "viem/accounts";
// The code below creates an Agent that can fetch the protected route and automatically pay.
// The agent's account must not be empty! You can get test credits
// for base-sepolia here: https://faucet.circle.com/
export class PayAgent extends Agent {
fetchWithPay!: ReturnType;
onStart() {
// We derive the account from which the agent will pay
const privateKey = process.env.CLIENT_TEST_PK as `0x${string}`;
const account = privateKeyToAccount(privateKey);
console.log("Agent will pay from this address:", account.address);
this.fetchWithPay = wrapFetchWithPayment(fetch, account);
}
async onRequest(req: Request) {
const url = new URL(req.url);
console.log("Trying to fetch paid API");
// Use the x402 compatible fetch (fetchWithPay) to access the paid endpoint
// Note: this could be any paid endpoint, on any server
const paidUrl = new URL("/protected-route", url.origin).toString();
return this.fetchWithPay(paidUrl, {});
}
}
const app = new Hono<{ Bindings: Env }>();
// Configure the middleware.
// Only gate the `protected-route` endpoint, everything else we keep free.
app.use(
paymentMiddleware(
process.env.SERVER_ADDRESS as `0x${string}`, // our server's public address
{
"/protected-route": {
price: "$0.10",
network: "base-sepolia",
config: {
description: "Access to premium content",
},
},
},
{ url: "https://x402.org/facilitator" }, // Payment facilitator URL
// To learn more about facilitators https://x402.gitbook.io/x402/core-concepts/facilitator
),
);
// Our paid endpoint will return some premium content.
app.get("/protected-route", (c) => {
return c.json({
message: "This content is behind a paywall. Thanks for paying!",
});
});
// The agent will fetch our own protected route and automatically pay.
app.get("/agent", async (c) => {
const agent = await getAgentByName(c.env.PAY_AGENT, "1234");
return agent.fetch(c.req.raw);
});
export default app;
```
Check out the [complete example](https://github.com/cloudflare/agents/tree/main/examples/x402).
## MCP servers with paid tools
x402 supercharges your MCP servers so they can include paid tools.
```ts
import { McpServer } from "@modelcontextprotocol/sdk/server/mcp.js";
import { McpAgent } from "agents/mcp";
import { withX402, type X402Config } from "agents/x402";
import { z } from "zod";
const X402_CONFIG: X402Config = {
network: "base",
recipient: env.MCP_ADDRESS,
facilitator: { url: "https://x402.org/facilitator" }, // Payment facilitator URL
// To learn more about facilitators https://x402.gitbook.io/x402/core-concepts/facilitator
};
export class PaidMCP extends McpAgent {
server = withX402(
new McpServer({ name: "PaidMCP", version: "1.0.0" }),
X402_CONFIG,
); // That's it!
async init() {
// Paid tool
this.server.paidTool(
"square",
"Squares a number",
0.01, // USD
{ number: z.number() },
{},
async ({ number }) => {
return { content: [{ type: "text", text: String(number ** 2) }] };
},
);
// Free tool
this.server.tool(
"echo",
"Echo a message",
{ message: z.string() },
async ({ message }) => {
return { content: [{ type: "text", text: message }] };
},
);
}
}
```
We also include an MCP client that you can use from anywhere (not just your Agents!) to pay for these tools.
```ts
import { Agent } from "agents";
import { withX402Client } from "agents/x402";
import { privateKeyToAccount } from "viem/accounts";
export class MyAgent extends Agent {
// Your Agent definitions...
onStart() {
const { id } = await this.mcp.connect(`${env.WORKER_URL}/mcp`);
const account = privateKeyToAccount(this.env.MY_PRIVATE_KEY);
this.x402Client = withX402Client(this.mcp.mcpConnections[id].client, {
network: "base-sepolia",
account,
});
}
onPaymentRequired(paymentRequirements): Promise {
// Your human-in-the-loop confirmation flow...
}
async onToolCall(toolName: string, toolArgs: unknown) {
// The first parameter becomes the confirmation callback.
// We can set it to `null` if we want the agent to pay automatically.
return await this.x402Client.callTool(this.onPaymentRequired, {
name: toolName,
arguments: toolArgs,
});
}
}
```
Check out the [complete example](https://github.com/cloudflare/agents/tree/main/examples/x402-mcp).
---
title: 404 - Page Not Found · Cloudflare AI Search docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-search/404/
md: https://developers.cloudflare.com/ai-search/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: REST API · Cloudflare AI Search docs
lastUpdated: 2026-01-19T17:29:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-search/ai-search-api/
md: https://developers.cloudflare.com/ai-search/ai-search-api/index.md
---
---
title: Concepts · Cloudflare AI Search docs
lastUpdated: 2025-09-24T17:03:07.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-search/concepts/
md: https://developers.cloudflare.com/ai-search/concepts/index.md
---
* [What is RAG](https://developers.cloudflare.com/ai-search/concepts/what-is-rag/)
* [How AI Search works](https://developers.cloudflare.com/ai-search/concepts/how-ai-search-works/)
---
title: Configuration · Cloudflare AI Search docs
description: You can customize how your AI Search instance indexes your data,
and retrieves and generates responses for queries. Some settings can be
updated after the instance is created, while others are fixed at creation
time.
lastUpdated: 2026-01-19T17:29:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-search/configuration/
md: https://developers.cloudflare.com/ai-search/configuration/index.md
---
You can customize how your AI Search instance indexes your data, and retrieves and generates responses for queries. Some settings can be updated after the instance is created, while others are fixed at creation time.
The table below lists all available configuration options:
| Configuration | Editable after creation | Description |
| - | - | - |
| [Data source](https://developers.cloudflare.com/ai-search/configuration/data-source/) | no | The source where your knowledge base is stored |
| [Path filtering](https://developers.cloudflare.com/ai-search/configuration/path-filtering/) | yes | Include or exclude specific paths from indexing |
| [Chunk size](https://developers.cloudflare.com/ai-search/configuration/chunking/) | yes | Number of tokens per chunk |
| [Chunk overlap](https://developers.cloudflare.com/ai-search/configuration/chunking/) | yes | Number of overlapping tokens between chunks |
| [Embedding model](https://developers.cloudflare.com/ai-search/configuration/models/) | no | Model used to generate vector embeddings |
| [Query rewrite](https://developers.cloudflare.com/ai-search/configuration/query-rewriting/) | yes | Enable or disable query rewriting before retrieval |
| [Query rewrite model](https://developers.cloudflare.com/ai-search/configuration/models/) | yes | Model used for query rewriting |
| [Query rewrite system prompt](https://developers.cloudflare.com/ai-search/configuration/system-prompt/) | yes | Custom system prompt to guide query rewriting behavior |
| [Match threshold](https://developers.cloudflare.com/ai-search/configuration/retrieval-configuration/) | yes | Minimum similarity score required for a vector match |
| [Maximum number of results](https://developers.cloudflare.com/ai-search/configuration/retrieval-configuration/) | yes | Maximum number of vector matches returned (`top_k`) |
| [Reranking](https://developers.cloudflare.com/ai-search/configuration/reranking/) | yes | Rerank to reorder retrieved results by semantic relevance using a reranking model after initial retrieval |
| [Generation model](https://developers.cloudflare.com/ai-search/configuration/models/) | yes | Model used to generate the final response |
| [Generation system prompt](https://developers.cloudflare.com/ai-search/configuration/system-prompt/) | yes | Custom system prompt to guide response generation |
| [Similarity caching](https://developers.cloudflare.com/ai-search/configuration/cache/) | yes | Enable or disable caching of responses for similar (not just exact) prompts |
| [Similarity caching threshold](https://developers.cloudflare.com/ai-search/configuration/cache/) | yes | Controls how similar a new prompt must be to a previous one to reuse its cached response |
| [AI Gateway](https://developers.cloudflare.com/ai-gateway) | yes | AI Gateway for monitoring and controlling model usage |
| AI Search name | no | Name of your AI Search instance |
| [Service API token](https://developers.cloudflare.com/ai-search/configuration/service-api-token/) | yes | API token that grants AI Search permission to configure resources on your account |
---
title: Get started with AI Search · Cloudflare AI Search docs
description: Create fully-managed, retrieval-augmented generation pipelines with
Cloudflare AI Search.
lastUpdated: 2026-01-19T17:29:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-search/get-started/
md: https://developers.cloudflare.com/ai-search/get-started/index.md
---
AI Search is Cloudflare's managed search service. Connect your data such as websites or an R2 bucket, and it automatically creates a continuously updating index that you can query with natural language in your applications or AI agents.
## Prerequisites
AI Search integrates with R2 for storing your data. You must have an active R2 subscription before creating your first AI Search instance.
[Go to **R2 Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
## Choose your setup method
[Dashboard ](https://developers.cloudflare.com/ai-search/get-started/dashboard/)Create and configure AI Search using the Cloudflare dashboard.
[API ](https://developers.cloudflare.com/ai-search/get-started/api/)Create AI Search instances programmatically using the REST API.
---
title: How to · Cloudflare AI Search docs
lastUpdated: 2026-01-19T17:29:33.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-search/how-to/
md: https://developers.cloudflare.com/ai-search/how-to/index.md
---
* [NLWeb](https://developers.cloudflare.com/ai-search/how-to/nlweb/)
* [Bring your own generation model](https://developers.cloudflare.com/ai-search/how-to/bring-your-own-generation-model/)
* [Create a simple search engine](https://developers.cloudflare.com/ai-search/how-to/simple-search-engine/)
* [Create multitenancy](https://developers.cloudflare.com/ai-search/how-to/multitenancy/)
* [Build a RAG from your website](https://developers.cloudflare.com/ai-search/how-to/brower-rendering-autorag-tutorial/)
---
title: MCP server · Cloudflare AI Search docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ai-search/mcp-server/
md: https://developers.cloudflare.com/ai-search/mcp-server/index.md
---
---
title: Platform · Cloudflare AI Search docs
lastUpdated: 2025-09-24T17:03:07.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-search/platform/
md: https://developers.cloudflare.com/ai-search/platform/index.md
---
* [Limits & pricing](https://developers.cloudflare.com/ai-search/platform/limits-pricing/)
* [Release note](https://developers.cloudflare.com/ai-search/platform/release-note/)
---
title: Search API · Cloudflare AI Search docs
lastUpdated: 2026-01-19T17:29:33.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ai-search/usage/
md: https://developers.cloudflare.com/ai-search/usage/index.md
---
* [Workers Binding](https://developers.cloudflare.com/ai-search/usage/workers-binding/)
* [REST API](https://developers.cloudflare.com/ai-search/usage/rest-api/)
---
title: 404 - Page Not Found · Cloudflare Analytics docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/404/
md: https://developers.cloudflare.com/analytics/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Account and zone analytics · Cloudflare Analytics docs
description: "Visit the following pages to learn more about account and zone analytics:"
lastUpdated: 2025-03-24T16:14:30.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/analytics/account-and-zone-analytics/
md: https://developers.cloudflare.com/analytics/account-and-zone-analytics/index.md
---
Visit the following pages to learn more about account and zone analytics:
* [Cloudflare analytics with Workers](https://developers.cloudflare.com/analytics/account-and-zone-analytics/analytics-with-workers/)
* [Account analytics (beta)](https://developers.cloudflare.com/analytics/account-and-zone-analytics/account-analytics/)
* [Status codes](https://developers.cloudflare.com/analytics/account-and-zone-analytics/status-codes/)
* [Total threats stopped](https://developers.cloudflare.com/analytics/account-and-zone-analytics/total-threats-stopped/)
* [Zone Analytics](https://developers.cloudflare.com/analytics/account-and-zone-analytics/zone-analytics/)
* [Threat types](https://developers.cloudflare.com/analytics/account-and-zone-analytics/threat-types/)
---
title: Analytics integrations · Cloudflare Analytics docs
description: Cloudflare Enterprise customers can use Cloudflare integrations
with their preferred analytics provider and configure ready-to-use Cloudflare
Dashboards. Most analytics integrations are built on Cloudflare Logs by using
Logpush with either Amazon S3 bucket or GCP Storage bucket.
lastUpdated: 2025-03-24T16:14:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/analytics-integrations/
md: https://developers.cloudflare.com/analytics/analytics-integrations/index.md
---
Cloudflare Enterprise customers can use Cloudflare integrations with their preferred analytics provider and configure ready-to-use Cloudflare Dashboards. Most analytics integrations are built on Cloudflare Logs by using Logpush with either Amazon S3 bucket or GCP Storage bucket.
Analyze [Cloudflare Logs](https://developers.cloudflare.com/logs/) data with the following analytics platforms:
* [Datadog](https://developers.cloudflare.com/analytics/analytics-integrations/datadog/)
* [Graylog](https://developers.cloudflare.com/analytics/analytics-integrations/graylog/)
* [New Relic](https://developers.cloudflare.com/analytics/analytics-integrations/new-relic/)
* [Splunk](https://developers.cloudflare.com/analytics/analytics-integrations/splunk/)
* [Sentinel](https://developers.cloudflare.com/analytics/analytics-integrations/sentinel/)
---
title: Workers Analytics Engine · Cloudflare Analytics docs
description: Workers Analytics Engine provides unlimited-cardinality analytics
at scale, via a built-in API to write data points from Workers, and a SQL API
to query that data.
lastUpdated: 2025-03-24T16:14:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/analytics-engine/
md: https://developers.cloudflare.com/analytics/analytics-engine/index.md
---
Workers Analytics Engine provides unlimited-cardinality analytics at scale, via [a built-in API](https://developers.cloudflare.com/analytics/analytics-engine/get-started/) to write data points from Workers, and a [SQL API](https://developers.cloudflare.com/analytics/analytics-engine/sql-api/) to query that data.
You can use Workers Analytics Engine to:
* Expose custom analytics to your own customers
* Build usage-based billing systems
* Understand the health of your service on a per-customer or per-user basis
* Add instrumentation to frequently called code paths, without impacting performance or overwhelming external analytics systems with events
[Get started](https://developers.cloudflare.com/analytics/analytics-engine/get-started/)
---
title: FAQs · Cloudflare Analytics docs
description: "Visit the following pages for commonly asked questions:"
lastUpdated: 2025-03-24T16:14:30.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/analytics/faq/
md: https://developers.cloudflare.com/analytics/faq/index.md
---
Visit the following pages for commonly asked questions:
* [About Cloudflare Analytics](https://developers.cloudflare.com/analytics/faq/about-analytics/)
* [GraphQL API inconsistent results](https://developers.cloudflare.com/analytics/faq/graphql-api-inconsistent-results/)
* [Workers Analytics Engine FAQs](https://developers.cloudflare.com/analytics/faq/wae-faqs/)
* [Other FAQs](https://developers.cloudflare.com/analytics/faq/other-faqs/)
---
title: GraphQL Analytics API · Cloudflare Analytics docs
description: The GraphQL Analytics API provides data regarding HTTP requests
passing through Cloudflare's network, as well as data from specific products,
such as Firewall or Load Balancing. Network Analytics users also have access
to packet-level data. Use the GraphQL Analytics API to select specific
datasets and metrics of interest, filter and aggregate the data along various
dimensions, and integrate the results with other applications.
lastUpdated: 2025-05-26T13:47:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/graphql-api/
md: https://developers.cloudflare.com/analytics/graphql-api/index.md
---
The GraphQL Analytics API provides data regarding HTTP requests passing through Cloudflare's network, as well as data from specific products, such as Firewall or Load Balancing. Network Analytics users also have access to packet-level data. Use the GraphQL Analytics API to select specific datasets and metrics of interest, filter and aggregate the data along various dimensions, and integrate the results with other applications.
The basis of the API is the [GraphQL framework](https://graphql.org/), created and open-sourced by Facebook. There is an active developer community for GraphQL and powerful clients for running queries, which makes it easy to get started. GraphQL is especially useful for building visualizations and powers the analytics in the Cloudflare dashboard.
GraphQL models a business domain as a graph using a schema. In the schema, there are logical definitions for different types of nodes and their connections (edges). These nodes are the datasets you use for your analytics. You write queries in GraphQL much like in SQL: you specify the dataset (table), the metrics to retrieve (such as requests and bytes), and filter or group by dimensions (for example, a time period).
GraphQL differs from a traditional API: it has one single endpoint:
```txt
https://api.cloudflare.com/client/v4/graphql
```
You pass the query parameters as a JSON object in the payload of a `POST` request to this endpoint.
You can use `curl` to make requests to the GraphQL Analytics API. Alternatively, you can use a GraphQL client to construct queries and pass requests to the GraphQL Analytics API.
## Clients
We are using [GraphiQL](https://github.com/skevy/graphiql-app) for our example GraphQL queries. There are many other popular open-source clients that you can find online, such as [Altair](https://altairgraphql.dev) and [Insomnia](https://insomnia.rest).
## Limitations
The purpose of the GraphQL API is to provide aggregated analytics about various Cloudflare products. These datasets should not be used as a measure for usage that Cloudflare uses for billing purposes. Billable traffic [excludes things like DDoS traffic](https://blog.cloudflare.com/unmetered-mitigation), while GraphQL is a measure of overall consumption/usage, so it will include all measurable traffic.
---
title: Cloudflare Network Analytics · Cloudflare Analytics docs
description: Cloudflare Network Analytics (version 2) provides near real-time
visibility into network and transport-layer traffic patterns and DDoS attacks.
Network Analytics visualizes packet and bit-level data, the same data
available via the Network Analytics dataset of the GraphQL Analytics API.
lastUpdated: 2025-09-09T13:48:51.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/network-analytics/
md: https://developers.cloudflare.com/analytics/network-analytics/index.md
---
Cloudflare Network Analytics (version 2) provides near real-time visibility into network and transport-layer traffic patterns and DDoS attacks. Network Analytics visualizes packet and bit-level data, the same data available via the Network Analytics dataset of the GraphQL Analytics API.
Requirements
Network Analytics requires the following:
* A Cloudflare Enterprise plan.
* Cloudflare Magic Transit or Spectrum.
* Cloudflare Magic WAN.
For a technical deep-dive into Network Analytics, refer to our [blog post](https://blog.cloudflare.com/building-network-analytics-v2/).
## Remarks
* The Network Analytics logs refer to IP traffic of Magic Transit customer prefixes/leased IP addresses or Spectrum applications. These logs are not directly associated with the [zones](https://developers.cloudflare.com/fundamentals/concepts/accounts-and-zones/#zones) in your Cloudflare account.
* The data retention for Network Analytics is 16 weeks. Additionally, data older than eight weeks might have lower resolution when using narrow time frames.
## Related resources
* [Cloudflare GraphQL API](https://developers.cloudflare.com/analytics/graphql-api/)
* [Cloudflare Logpush](https://developers.cloudflare.com/logs/logpush/)
* [Migrating from Network Analytics v1 to Network Analytics v2](https://developers.cloudflare.com/analytics/graphql-api/migration-guides/network-analytics-v2/)
---
title: Understanding sampling in Cloudflare Analytics · Cloudflare Analytics docs
description: Sampling is a technique used in analytics to analyze a subset of
data rather than processing every individual data point. In Cloudflare
Analytics, sampling ensures efficient performance and scalability while
maintaining high accuracy and reliability. This document provides a
comprehensive overview of how sampling works, why it is used, and its impact
on analytics across different Cloudflare tools.
lastUpdated: 2025-03-24T16:14:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/sampling/
md: https://developers.cloudflare.com/analytics/sampling/index.md
---
[Sampling](https://en.wikipedia.org/wiki/Sampling_\(statistics\)) is a technique used in analytics to analyze a subset of data rather than processing every individual data point. In Cloudflare Analytics, sampling ensures efficient performance and scalability while maintaining high accuracy and reliability. This document provides a comprehensive overview of how sampling works, why it is used, and its impact on analytics across different Cloudflare tools.
## How sampling works
We use a sampling method called [Adaptive Bit Rate (ABR)](https://blog.cloudflare.com/explaining-cloudflares-abr-analytics/) to ensure that queries complete quickly, even when working with large datasets. ABR dynamically adjusts the level of detail in the data retrieved based on query complexity and duration. This approach ensures fairness by preventing large or complex queries from consuming a disproportionate amount of computing resources, which could otherwise slow down or block smaller queries. By distributing resources more equitably, ABR allows the system to maintain consistent performance for all users, regardless of the dataset size.
To make this possible, data is stored at multiple resolutions (100%, 10%, 1%), each representing different sampling percentages. When a query is run, ABR selects the best resolution based on the query's complexity and number of rows to retrieve. By dynamically adjusting the data resolution, ABR optimizes performance and prevents delays. This sets it apart from systems that struggle with timeouts, errors, or high costs when dealing with large datasets.
## Why sampling is applied
Cloudflare's data pipeline handles [over 700 million events per second](https://blog.cloudflare.com/how-we-make-sense-of-too-much-data) (and growing) across its global network. Processing and storing all this data in real-time would be prohibitively expensive and time-consuming. By leveraging carefully designed sampling methods, Cloudflare Analytics delivers accurate and actionable data, balancing precision with performance.
Sampling enables:
* **Scalability**: Reduces the volume of data processed without compromising insights.
* **Performance**: Speeds up query execution for analytics.
* **Cost-Efficiency**: Minimizes resource usage and storage needs.
## Can I trust sampled data?
Sampled data is highly reliable, and can provide insights that are as dependable as those derived from full datasets. Cloudflare designs sampling techniques to ensure we capture the essential characteristics of the entire dataset, delivering results you can trust.
Sampling is an approach similarly used in other domains, for instance:
* Google Maps: Just as online maps display lower-resolution images when zoomed out and higher-resolution images when zoomed in — keeping the total number of pixels relatively constant — Cloudflare Analytics dynamically adjusts sampling rates to efficiently provide insights, ensuring queries return consistent and accurate results regardless of dataset size.
* Opinion Polls: Similar to how pollsters sample a subset of the population to predict election outcomes, Cloudflare samples a portion of your data to provide accurate, system-wide insights.
* Movie Frames: Watching a movie at 30 frames per second (fps) instead of 60 fps does not change the overall experience, much like how analyzing fewer data points still reveals the same patterns and trends in your analytics dataset.
We acknowledge it can be challenging to verify the exact resolution of ABR query results at this time. However, as a general rule, you can check the number of rows read. A higher number of rows read will result in higher resolution results. For example, results based on thousands of rows are highly likely to be representative, while those based on just a few rows may not be as reliable.
In the near future, we plan to expose confidence intervals along with query results, so you can see precisely how accurate your results are.
## Additional considerations
**When sampling occurs**
* Sampling is typically applied to very high-traffic datasets where full data analysis would be impractical.
* For smaller datasets, full data analysis is often performed without sampling.
**Sampling rates**
* Sampling rates vary depending on the dataset and product.
* Cloudflare ensures that sampling rates are consistent within a single dataset to maintain accuracy across queries.
**Impact on metrics**
* While sampling reduces the volume of processed data, aggregated metrics like totals, averages, and percentiles are extrapolated based on the sample size. This ensures the reported metrics represent the entire dataset accurately.
**Limitations**
* Sampling may not capture extremely rare events with very low occurrence rates.
**Sampling in analytics interfaces**
* GraphQL API: Sampling metadata is included in the query response. For more information, refer to the sampling [GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/sampling/) documentation.
* Workers Analytics Engine: For more information, refer to the [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/sampling/) documentation.
* Dashboard Analytics: Displays an icon with the sampled percentage of data, if sampled data was used for the visualization.
---
title: Types of analytics · Cloudflare Analytics docs
description: Cloudflare Analytics is a comprehensive product that encompasses
all metadata generated by the Cloudflare network. You can access these
insights through the Cloudflare dashboard. Depending on where in the dashboard
you are, it will show you different aspects from the collected metadata.
lastUpdated: 2025-03-25T09:41:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/analytics/types-of-analytics/
md: https://developers.cloudflare.com/analytics/types-of-analytics/index.md
---
Cloudflare Analytics is a comprehensive product that encompasses all metadata generated by the Cloudflare network. You can access these insights through the Cloudflare dashboard. Depending on where in the dashboard you are, it will show you different aspects from the collected metadata.
## Account-level analytics
### Account Analytics (beta)
Available under **Analytics & Logs** in your Cloudflare dashboard when you log in, Account Analytics (beta) shows you an [overview of traffic for all domains](https://developers.cloudflare.com/analytics/account-and-zone-analytics/account-analytics/) under your Cloudflare account, such as requests and bandwidth by country, information related to security, cache, and errors, among others. To access Account Analytics, [log in to the Cloudflare dashboard](https://dash.cloudflare.com/login), select the appropriate account, and go to **Analytics & Logs** > **Account Analytics**.
### Network Analytics
Network Analytics provides [visibility into network and transport-layer traffic patterns, and DDoS attacks](https://developers.cloudflare.com/analytics/network-analytics/).
The Network Analytics dashboard is only available for customers with an Enterprise domain plan who use [Spectrum](https://developers.cloudflare.com/spectrum/), [Magic Transit](https://developers.cloudflare.com/magic-transit/), or [Bring Your Own IP (BYOIP)](https://developers.cloudflare.com/byoip/).
### Web Analytics
Web Analytics (formerly known as Browser Insights) [provides free, privacy-first analytics for your website](https://developers.cloudflare.com/web-analytics/). Web Analytics does not collect your visitor's personal data, and allows you to have a detailed view into the performance of web pages as experienced by your visitors.
### Carbon Impact Report
Carbon Impact Report gives you a [report on carbon savings](https://blog.cloudflare.com/understand-and-reduce-your-carbon-impact-with-cloudflare/) from using Cloudflare services versus Internet averages for your usage volume.
Cloudflare is committed to use 100% renewable energy sources, but also to [remove all greenhouse gases emitted](https://blog.cloudflare.com/cloudflare-committed-to-building-a-greener-internet/) as a result of powering our network since 2010.
## Analytics related to specific properties
Access aggregated traffic, security, and performance metrics for each domain proxied through Cloudflare. To access these analytics, [log in to the Cloudflare dashboard](https://dash.cloudflare.com/login), select your account and domain, and go to the **Analytics & Logs** section.
Data available under the **Analytics & Logs** section includes:
* **HTTP Traffic** - Requests, Data transfer, Page views, Visits, and API requests.
* **Security** - Total Threats, Top Crawlers/Bots, Rate Limiting, Total Threats Stopped.
* **Performance** - Origin Performance, Bandwidth Saved.
* **Edge Reachability** - [Last mile insights](https://developers.cloudflare.com/network-error-logging/) for Enterprise customers.
* **Workers** - [Detailed information](https://developers.cloudflare.com/workers/observability/metrics-and-analytics/) related to your Workers per zone, and Workers KV per account.
* **Logs** - [Detailed logs](https://developers.cloudflare.com/logs/) of the metadata generated by Cloudflare products for Enterprise customers.
* **Instant logs** - [Live stream of traffic](https://developers.cloudflare.com/logs/instant-logs/) for your domain. Enterprise customers can access this live stream from the Cloudflare dashboard or from a command-line interface (CLI).
## Product analytics
Beyond the analytics provided for your properties, you can also access analytics related to specific products:
* [Bot Analytics](https://developers.cloudflare.com/bots/bot-analytics/) - Shows which requests are associated with known bots, likely automated traffic, likely human traffic, and more.
* [Cache Analytics](https://developers.cloudflare.com/cache/performance-review/cache-analytics/) - Insights to that help determine if resources are missing from cache, expired, or ineligible for caching.
* [DNS Analytics](https://developers.cloudflare.com/dns/additional-options/analytics/) - Provides insights about DNS queries to your zone.
* [Load Balancing Analytics](https://developers.cloudflare.com/load-balancing/reference/load-balancing-analytics/) - Features metrics to help gain insights into traffic load balancer steering decisions.
* [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/) - Highlights attack and mitigation metrics detected by the Cloudflare WAF and HTTP DDoS protection systems.
* [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) - Displays information about all incoming HTTP requests, including those not affected by security measures (for example, from the WAF and DDoS protection systems).
## GraphQL APIs
If you would like to have more control over how you visualize the analytic and log information available on the Cloudflare dashboard, use the [GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/) to build customized views. This API replaces and expands on the previous Zone Analytics API.
---
title: 404 - Page Not Found · Cloudflare API Shield docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/404/
md: https://developers.cloudflare.com/api-shield/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API Gateway · Cloudflare API Shield docs
description: Cloudflare API Shield empowers you to use Cloudflare as your API
Gateway, providing robust security features, streamlined management tools, and
integration with the Cloudflare Developer Platform for building new APIs.
lastUpdated: 2025-08-20T16:33:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/api-gateway/
md: https://developers.cloudflare.com/api-shield/api-gateway/index.md
---
Cloudflare API Shield empowers you to use Cloudflare as your API Gateway, providing robust security features, streamlined management tools, and integration with the Cloudflare Developer Platform for building new APIs.
APIs are fundamental to modern applications but are increasingly targeted by malicious actors. Cloudflare API Shield offers a comprehensive solution to protect, manage, and build your APIs.
* **Enhanced security**: Implement robust runtime protection such as JWT validation, mutual TLS (mTLS) authentication, Schema validation, and protection against the [OWASP Top 10 API Security risks](https://owasp.org/www-project-api-security/).
* **Efficient management and monitoring**: Utilize tools for endpoint management, analytics, and routing to streamline API operations. Highlight risks with Posture Management, and gain visibility with Security Analytics and Security Center Insights.
* **Integrated development**: Leverage the Cloudflare Developer Platform to build and deploy new APIs with ease, taking advantage of scalable infrastructure and a suite of developer tools.
## Cloudflare as your API Gateway
### API security features
* **Protection Against OWASP Top 10 API Security risks**: Mitigate common API vulnerabilities, including injection attacks and improper asset management.
### Management and Monitoring tools
* **[Endpoint management](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/)**: Gain visibility into your API endpoints, including discovery of shadow APIs and monitoring of active endpoints.
* **[Analytics and logging](https://developers.cloudflare.com/api-shield/security/sequence-analytics/)**: Access detailed analytics and logs to monitor API usage, performance, and security events.
* **[API Routing](https://developers.cloudflare.com/api-shield/management-and-monitoring/api-routing/)**: Optimize API performance and reliability with secure routing.
* **[Posture Management](https://developers.cloudflare.com/api-shield/security/authentication-posture/)**: Monitor API Authentication status and receive alerts for common API risks.
### Build APIs with Cloudflare’s Developer Platform
The [Cloudflare Developer Platform](https://www.cloudflare.com/developer-platform/) offers a serverless execution environment, allowing you to build and deploy new APIs without the need to manage infrastructure. Its benefits include:
* **Global scalability**: Deploy your APIs across Cloudflare's extensive global network, ensuring low latency and high availability.
* **Integrated services**: Access a suite of services, including storage, databases, and AI tools, to enhance your API functionality.
* **Developer-friendly tools**: Utilize modern development tools and frameworks to streamline the API development process.
## Get started
To begin using Cloudflare API Shield, refer to our [Get started](https://developers.cloudflare.com/api-shield/get-started/) guide.
For detailed instructions and additional resources, refer to the Cloudflare [API Shield documentation](https://developers.cloudflare.com/api-shield/).
By integrating API security, management, and development into a single platform, Cloudflare API Shield provides a comprehensive solution to protect, manage, and build APIs.
---
title: Changelog · Cloudflare API Shield docs
description: Now, API Shield automatically searches for and highlights Broken
Object Level Authorization (BOLA) attacks on managed API endpoints. API Shield
will highlight both BOLA enumeration attacks and BOLA pollution attacks,
telling you what was attacked, by who, and for how long.
lastUpdated: 2025-10-31T10:10:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/changelog/
md: https://developers.cloudflare.com/api-shield/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/api-shield.xml)
## 2025-11-12
**New BOLA Vulnerability Detection for API Shield**
Now, API Shield automatically searches for and highlights **Broken Object Level Authorization (BOLA) attacks** on managed API endpoints. API Shield will highlight both BOLA enumeration attacks and BOLA pollution attacks, telling you what was attacked, by who, and for how long.
You can find these attacks three different ways: Security Overview, Endpoint details, or Security Analytics. If these attacks are not found on your managed API endpoints, there will not be an overview card or security analytics suspicious activity card.

From the endpoint details, you can select **View attack** to find details about the BOLA attacker’s sessions.

From here, select **View in Analytics** to observe attacker traffic over time for the last seven days.

Your search will filter to traffic on that endpoint in the last seven days, along with the malicious session IDs found in the attack. Session IDs are hashed for privacy and will not be found in your origin logs. Refer to IP and JA4 fingerprint to cross-reference behavior at the origin.
At any time, you can also start your investigation into attack traffic from Security Analytics by selecting the suspicious activity card.

We urge you to take all of this client information to your developer team to research the attacker behavior and ensure any broken authorization policies in your API are fixed at the source in your application, preventing further abuse.
In addition, this release marks the end of the beta period for these scans. All Enterprise customers with API Shield subscriptions will see these new attacks if found on their zone.
## 2025-03-18
**New API Posture Management for API Shield**
Now, API Shield **automatically** labels your API inventory with API-specific risks so that you can track and manage risks to your APIs.
View these risks in [Endpoint Management](https://developers.cloudflare.com/api-shield/management-and-monitoring/) by label:

...or in [Security Center Insights](https://developers.cloudflare.com/security-center/security-insights/):

API Shield will scan for risks on your API inventory daily. Here are the new risks we're scanning for and automatically labelling:
* **cf-risk-sensitive**: applied if the customer is subscribed to the [sensitive data detection ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/sensitive-data-detection/) and the WAF detects sensitive data returned on an endpoint in the last seven days.
* **cf-risk-missing-auth**: applied if the customer has configured a session ID and no successful requests to the endpoint contain the session ID.
* **cf-risk-mixed-auth**: applied if the customer has configured a session ID and some successful requests to the endpoint contain the session ID while some lack the session ID.
* **cf-risk-missing-schema**: added when a learned schema is available for an endpoint that has no active schema.
* **cf-risk-error-anomaly**: added when an endpoint experiences a recent increase in response errors over the last 24 hours.
* **cf-risk-latency-anomaly**: added when an endpoint experiences a recent increase in response latency over the last 24 hours.
* **cf-risk-size-anomaly**: added when an endpoint experiences a spike in response body size over the last 24 hours.
In addition, API Shield has two new 'beta' scans for **Broken Object Level Authorization (BOLA) attacks**. If you're in the beta, you will see the following two labels when API Shield suspects an endpoint is suffering from a BOLA vulnerability:
* **cf-risk-bola-enumeration**: added when an endpoint experiences successful responses with drastic differences in the number of unique elements requested by different user sessions.
* **cf-risk-bola-pollution**: added when an endpoint experiences successful responses where parameters are found in multiple places in the request.
We are currently accepting more customers into our beta. Contact your account team if you are interested in BOLA attack detection for your API.
Refer to the [blog post](https://blog.cloudflare.com/cloudflare-security-posture-management/) for more information about Cloudflare's expanded posture management capabilities.
## 2025-02-17
**New automatically applied risk labels**
API Shield now automatically labels endpoints with risks due to missing schemas and performance anomalies (spikes in error rates, latency, and body response sizes).
## 2025-01-16
**API Authentication Posture**
Customers will see per-endpoint authentication details inside [Endpoints](https://developers.cloudflare.com/api-shield/management-and-monitoring/) for zones with configured session identifiers.
## 2024-12-19
**Automatically applied endpoint risk labels**
API Shield now automatically labels endpoints with risks due to authentication status and sensitive data detection.
## 2024-11-04
**Endpoint labels**
Customers can now organize their endpoints by use case and custom labels using the [Endpoint labeling service](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/) for easy reference and future machine learning (ML) model training.
## 2024-10-18
**API Shield fields in Custom Rules**
Customers can now use API Shield product feature fields in [custom rules](https://developers.cloudflare.com/waf/custom-rules/), referencing features such as [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/), [session identifiers](https://developers.cloudflare.com/api-shield/get-started/#session-identifiers), and [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/).
## 2024-09-25
**Fallthrough rule for Schema validation 2.0**
Customers can now enable the [Fallthrough Action](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-adding-a-fallthrough-rule) for Schema validation 2.0 to block or log requests that do not match the endpoints listed in schemas protected by Schema validation 2.0.
## 2024-08-28
**Increased capacity for Endpoint management and Schema validation**
Endpoint management and Schema validation now support up to 10,000 saved and validated API endpoints.
## 2024-07-08
**API Discovery's hostname variables**
Customers can now see when [API Discovery](https://developers.cloudflare.com/api-shield/security/api-discovery/) groups similar subdomains with the same methods and paths, making it easy to discover and manage APIs that share many vanity domains or subdomains.
## 2024-07-02
**Route API requests using API Routing**
Customers can now route requests to different back-end services through [API Routing](https://developers.cloudflare.com/api-shield/management-and-monitoring/api-routing/), creating a unified front for their APIs distributed across otherwise disparate systems.
## 2024-05-13
**Use JWT claims in Advanced Rate Limiting, Transform Rules, and as session IDs**
Customers can now use the fields inside [JSON Web Tokens (known as claims)](https://developers.cloudflare.com/api-shield/security/jwt-validation/transform-rules/#enhance-transform-rules-with-jwt-claims) as [session identifiers in API Shield](https://developers.cloudflare.com/api-shield/get-started/#session-identifiers), to count values in [Advanced Rate Limiting](https://developers.cloudflare.com/waf/rate-limiting-rules/), and to send on useful information in [Transform Rules](https://developers.cloudflare.com/rules/transform/).
## 2024-04-30
**Build sequence mitigation rules via the Cloudflare dashboard**
Customers can now build [Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/) rules with a new user interface inside the API Shield section of the [Cloudflare dashboard](https://dash.cloudflare.com/).
## 2024-02-23
**Endpoint management supports hostname variables**
Customers can now save endpoints in [Endpoint management](https://developers.cloudflare.com/api-shield/management-and-monitoring/) that contain variables in the hostname. Hostname variables are supported across all product features.
---
title: Get started with API Shield · Cloudflare API Shield docs
description: This guide will help you set up API Shield to identify and address
API security best practices.
lastUpdated: 2025-10-08T09:32:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/get-started/
md: https://developers.cloudflare.com/api-shield/get-started/index.md
---
This guide will help you set up API Shield to identify and address API security best practices.
Note
Enabling API Shield features will have no impact on your traffic until you choose to move a setting from `log` to `block` mode.
## Session identifiers
While not strictly required, it is recommended that you configure your session identifiers when getting started with API Shield. When Cloudflare inspects your API traffic for individual sessions, we can offer more tools for visibility, management, and control.
If you are unsure of the session identifiers that your API uses, consult with your development team.
Session identifiers should uniquely identify API clients. A common session identifier for API traffic is the `Authorization` header. When a [JSON Web Token (JWT)](https://developers.cloudflare.com/api-shield/security/jwt-validation/) is used by the API for client authentication, its value may change over time. You can use a claim value inside the JWT such as `sub` or `email` as a session ID to uniquely identify the session over time.
If your API uses the `Authorization` header on more than 1% of successful requests to your zone, Cloudflare will automatically set it as the API Shield session identifier.
You must have specific entitlements to configure session identifiers or cookies as a form of identifiers, such as an Enterprise subscription, for features such as [API Discovery](https://developers.cloudflare.com/api-shield/security/api-discovery/), [Sequence Mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/) or [rate limiting recommendations](https://developers.cloudflare.com/api-shield/security/volumetric-abuse-detection/), and to see results in [Sequence Analytics](https://developers.cloudflare.com/api-shield/security/sequence-analytics/) and [Authentication Posture](https://developers.cloudflare.com/api-shield/security/authentication-posture/).
### To set up session identifiers
* New dashboard
1. In the Cloudflare dashboard, go to the **Security Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
2. Filter by **API abuse**.
3. On **Session identifiers**, select **Configure session identifiers**.
4. Select **Manage identifiers**.
5. Choose the type of session identifier (cookie, HTTP header, or JWT claim).
Note
The session identifier cookie must comply with RFC 6265. Otherwise, it will be rejected.
If you are using a JWT claim, choose the [Token Configuration](https://developers.cloudflare.com/api-shield/security/jwt-validation/api/#token-configurations) that will verify the JWT. Token Configurations are required to use JWT claims as session identifiers. Refer to [JWT Validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/) for more information.
6. Enter the name of the session identifier.
7. Select **Save**.
* Old dashboard
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/login), and select your account and domain.
2. Go to **Security** > **API Shield**.
3. Select **Settings**.
4. On **Endpoint settings**, select **Manage identifiers**.
5. Choose the type of session identifier (cookie, HTTP header, or JWT claim).
Note
The session identifier cookie must comply with RFC 6265. Otherwise, it will be rejected.
If you are using a JWT claim, choose the [Token Configuration](https://developers.cloudflare.com/api-shield/security/jwt-validation/api/#token-configurations) that will verify the JWT. Token Configurations are required to use JWT claims as session identifiers. Refer to [JWT Validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/) for more information.
6. Enter the name of the session identifier.
7. Select **Save**.
After setting up session identifiers and allowing some time for Cloudflare to learn your traffic patterns, you can view your per endpoint and per session rate limiting recommendations, as well as enforce per endpoint and per session rate limits by creating new rules. Session identifiers will allow you to view API Discovery results from session ID-based discovery and session traffic patterns in Sequence Analytics.
## Upload a schema using Schema validation (optional)
Schema validation protects your APIs by ensuring only requests matching your API schema are allowed to communicate with your origin.
While not strictly required, uploading a pre-existing schema will offer the chance to automatically add endpoints to Endpoint Management. If you already have a schema, you can upload it to [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/).
Note
It is recommended to start with Schema validation rules set to `log` to review logged requests in [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/). When you are confident that only the correct requests are logged, you should switch the rule to `block`.
If you do not have a schema to upload, continue reading this guide to learn how to generate a schema with API Shield.
## Enable the Sensitive Data Detection ruleset and accompanying rules
API Shield works with Cloudflare WAF’s [Sensitive Data Detection](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#sensitive-data-detection) ruleset to identify API endpoints that return sensitive data such as social security or credit card numbers in their HTTP responses. Monitoring these endpoints can be critical to ensuring sensitive data is returned only when expected.
Note
A subscription is required for Sensitive Data Detection. Contact your account team if you are not entitled for Sensitive Data Detection.
You can identify endpoints returning sensitive data by selecting the icon next to the path in a row. Expand the endpoint to see details on which rules were triggered and view more information by exploring events in **Firewall Events**.
## Add your discovered endpoints to Endpoint Management
Cloudflare’s machine learning models have already inspected your existing traffic for the presence of API endpoints. By adding endpoints from API Discovery to Endpoint Management, you can unlock further security, visibility, and management features of the platform. Endpoint Management monitors the health of your API endpoints by saving, updating, and monitoring performance metrics.
Note
Schema validation, schema learning, JWT validation, Sequence Analytics, sequence mitigation, and rate limit recommendations only run on endpoints saved to Endpoint Management.
You can save your endpoints directly from [API Discovery](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#add-endpoints-from-api-discovery), [Schema validation](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#add-endpoints-from-schema-validation), or [manually](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#add-endpoints-manually) by method, path, and host.
This will add the specified endpoints to your list of managed endpoints. You can view your list of saved endpoints in the **Endpoint Management** page.
Cloudflare will aggregate [performance data](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#endpoint-analysis) and security data on your endpoint once it is saved.
### Allow the system to learn your traffic patterns
Cloudflare will inspect your API traffic and begin to learn its schema over the next 24 hours after adding an endpoint. Depending on how much traffic an individual endpoint sees, our confidence in the resulting schema may differ.
Cloudflare will also use the configured session identifiers to suggest rate limits per endpoint.
For best results, allow at least 24 hours after adding endpoints before proceeding to the following steps.
We recommend proceeding with [additional configurations](https://developers.cloudflare.com/api-shield/get-started/#additional-configuration) if this is your first time setting up API Shield and have added your first API endpoints to Endpoint Management.
## Add rate limits to your most sensitive endpoints
[Rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/) allow you to define rate limits for requests matching an expression, and choose the action to perform when those rate limits are reached.
You can observe Cloudflare suggested rate limits in Endpoint Management for endpoints using session identifiers. Unlike many security tools, these recommended rate limits are per-endpoint and per-session, not site-wide and not based on IP address. When creating a rule, it will be based on only traffic to that specific endpoint from unique visitors during their session. This feature allows you to be very specific and targeted with your rate limit enforcement, both lowering abusive traffic and false positives due to broadly scoped rules.
## Import a learned schema to Schema validation
Cloudflare learns schema parameters via traffic inspection for all endpoints stored in Endpoint Management. You can export OpenAPI schemas in OpenAPI v3.0.0 format by hostname.
By importing the learned schema, you can protect API endpoints found via API Discovery that were never previously possible to protect due to not knowing about their presence or schema.
You can import the learned schema of an entire hostname using the [Cloudflare dashboard](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-applying-a-learned-schema-to-an-entire-hostname). Alternatively, you can [apply learned schemas to individual endpoints](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-applying-a-learned-schema-to-a-single-endpoint). Before applying the learned schema, Cloudflare suggests exporting the schema to review what will validate your traffic.
## Export a learned schema from Endpoint Management
Learned schemas will always include the listed hostname in the servers section, all endpoints by host, method, and path, and detected path variables. They can also potentially include detected query parameters and their format. You can optionally include API Shield's rate limit threshold recommendations.
You can export your learned schemas in the [Cloudflare dashboard](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/schema-learning/#export-a-schema) or via the [API](https://developers.cloudflare.com/api/resources/api_gateway/subresources/schemas/methods/list/).
## View and configure Sequence Analytics
[Sequence Analytics](https://developers.cloudflare.com/api-shield/security/sequence-analytics/) surfaces a subset of important API request sequences found in your API traffic over time.
You can observe the top sequences in your API traffic that contain endpoints stored in Endpoint Management. We rank sequences by Correlation Score. High-scoring sequences contain API requests which are likely to occur together in order.
[Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/) allows you to enforce request patterns for authenticated clients communicating with your API. Use Sequence Analytics to better understand the request sequences used by your API clients.
You should apply all possible API Shield protections (rate limiting suggestions, Schema validation, JWT validation, and mTLS) to API endpoints found in high correlation score sequences that make up the critical request flows in your application. You should also check their specific endpoint order with your development team.
For more information, refer to [Detecting API abuse automatically using sequence analysis](https://blog.cloudflare.com/api-sequence-analytics) blog post.
## Additional configuration
### Set up JSON Web Tokens (JWT) validation
Use the Cloudflare API to configure [JSON Web Tokens validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/), which validates the integrity and validity of JWTs sent by clients to your API or web application.
### Set up GraphQL Malicious Query Protection
If your origin uses GraphQL, you may consider setting limits on GraphQL query size and depth.
[GraphQL malicious query protection](https://developers.cloudflare.com/api-shield/security/graphql-protection/api/) scans your GraphQL traffic for queries that could overload your origin and result in a denial of service. Customers can build rules that limit the query depth and size of incoming GraphQL queries in order to block suspiciously large or complex queries.
For more information, refer to the [blog post](https://blog.cloudflare.com/protecting-graphql-apis-from-malicious-queries/).
### Mutual TLS (mTLS) authentication
If you operate an API that requires or would benefit from an extra layer of protection, you may consider using Mutual TLS (mTLS).
[Mutual TLS (mTLS) authentication](https://developers.cloudflare.com/api-shield/security/mtls/) uses client certificates to ensure traffic between client and server is bidirectionally secure and trusted. mTLS also allows requests that do not authenticate via an identity provider, such as Internet-of-things (IoT) devices, to demonstrate they can reach a given resource.
---
title: Glossary · Cloudflare API Shield docs
description: Review the definitions for terms used across Cloudflare's API
Shield documentation.
lastUpdated: 2024-09-24T14:19:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/glossary/
md: https://developers.cloudflare.com/api-shield/glossary/index.md
---
Review the definitions for terms used across Cloudflare's API Shield documentation.
| Term | Definition |
| - | - |
| API call | Also known as an API request. An API call is a message sent to a server asking an API to provide a service or information. |
| API endpoint | The API endpoint is the location where API calls or requests are fulfilled. API Shield defines endpoints as a host, method, and path tuple. |
| API schema | The API schema defines which API requests are valid based on several request properties like target endpoint, path or query variable format, and HTTP method. |
| session identifier | A session identifier is a unique identifier that a website assigns to identify a specific user for the duration of their visit. |
| source endpoint | The source endpoint is the endpoint managed by API Shield in Endpoint Management by its routing feature. |
| target endpoint | The target endpoint is the ultimate destination that a request is sent to by API Shield's routing feature. |
---
title: Management and Monitoring · Cloudflare API Shield docs
lastUpdated: 2025-05-30T21:42:40.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/api-shield/management-and-monitoring/
md: https://developers.cloudflare.com/api-shield/management-and-monitoring/index.md
---
* [Endpoint Management](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/)
* [Endpoint labeling service](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/)
* [Session identifiers](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/)
* [API Routing](https://developers.cloudflare.com/api-shield/management-and-monitoring/api-routing/)
* [Build developer portals](https://developers.cloudflare.com/api-shield/management-and-monitoring/developer-portal/)
---
title: Plans · Cloudflare API Shield docs
description: Free, Pro, Business, and Enterprise customers without an API Shield
subscription can access Endpoint Management and Schema validation, but no
other API Shield features.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/plans/
md: https://developers.cloudflare.com/api-shield/plans/index.md
---
Free, Pro, Business, and Enterprise customers without an API Shield subscription can access [Endpoint Management](https://developers.cloudflare.com/api-shield/management-and-monitoring/) and [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/), but no other [API Shield](https://developers.cloudflare.com/api-shield/) features.
To subscribe to API Shield, upgrade to an Enterprise plan and contact your account team.
Limits to endpoints apply to Endpoint Management and Schema validation. Refer to the table below for limits based on your zone plan.
| Plan type | Saved endpoints | Uploaded schemas | Total uploaded schema size | Rule action |
| - | - | - | - | - |
| **Free** | 100 | 5 | 200 kB | `Block` only |
| **Pro** | 250 | 5 | 500 kB | `Block` only |
| **Business** | 500 | 10 | 2 MB | `Block` only |
| **Enterprise without API Shield** | 500 | 10 | 5 MB | `Log` or `Block` |
| **Enterprise with API Shield** | 10,000 | 10+ | 10+ MB | `Log` or `Block` |
---
title: Reference · Cloudflare API Shield docs
description: "Refer to the following pages for more information about API Shield:"
lastUpdated: 2025-05-30T21:42:40.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/api-shield/reference/
md: https://developers.cloudflare.com/api-shield/reference/index.md
---
Refer to the following pages for more information about API Shield:
* [Classic Schema validation (deprecated)](https://developers.cloudflare.com/api-shield/reference/classic-schema-validation/)
* [Terraform](https://developers.cloudflare.com/api-shield/reference/terraform/)
---
title: Security · Cloudflare API Shield docs
description: "Cloudflare offers the following features to help secure your APIs:"
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/api-shield/security/
md: https://developers.cloudflare.com/api-shield/security/index.md
---
Cloudflare offers the following features to help secure your APIs:
| Discovery & management | Posture management | Runtime protection |
| - | - | - |
| [API Discovery](https://developers.cloudflare.com/api-shield/security/api-discovery/) | [Volumetric Abuse Detection](https://developers.cloudflare.com/api-shield/security/volumetric-abuse-detection/) | [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/) |
| [Schema learning](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/schema-learning/) | [Authentication Posture](https://developers.cloudflare.com/api-shield/security/authentication-posture/) | [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/) |
| [Sequence Analytics](https://developers.cloudflare.com/api-shield/security/sequence-analytics/) | [BOLA vulnerability detection](https://developers.cloudflare.com/api-shield/security/bola-vulnerability-detection/) | [Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/) |
| | [Risk labels](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/#risk-labels) | [Mutual TLS (mTLS)](https://developers.cloudflare.com/api-shield/security/mtls/) |
| | | [GraphQL query protection](https://developers.cloudflare.com/api-shield/security/graphql-protection/) |
## Example Cloudflare solutions
Cloudflare's API Shield — together with other compatible Cloudflare products — helps protect your API from the issues detailed in the [OWASP® API Security Top 10](https://owasp.org/www-project-api-security/).
The following table provides examples of how you might match Cloudflare products to OWASP vulnerabilities:
| OWASP issue | Example Cloudflare solution |
| - | - |
| Broken Object Level Authorization | [BOLA vulnerability detection](https://developers.cloudflare.com/api-shield/security/bola-vulnerability-detection/), [Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/), [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/), [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/), [Rate Limiting](https://developers.cloudflare.com/waf/rate-limiting-rules/) |
| Broken Authentication | [Authentication Posture](https://developers.cloudflare.com/api-shield/security/authentication-posture/), [mTLS](https://developers.cloudflare.com/api-shield/security/mtls/), [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/), [Exposed Credential Checks](https://developers.cloudflare.com/waf/managed-rules/check-for-exposed-credentials/), [Bot Management](https://developers.cloudflare.com/bots/) |
| Broken Object Property Level Authorization | [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/), [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/) |
| Unrestricted Resource Consumption | [Rate Limiting](https://developers.cloudflare.com/waf/rate-limiting-rules/), [Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/), [Bot Management](https://developers.cloudflare.com/bots/), [GraphQL Query Protection](https://developers.cloudflare.com/api-shield/security/graphql-protection/) |
| Broken Function Level Authorization | [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/), [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/) |
| Unrestricted Access to Sensitive Business Flows | [Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/), [Bot Management](https://developers.cloudflare.com/bots/), [GraphQL Query Protection](https://developers.cloudflare.com/api-shield/security/graphql-protection/) |
| Server Side Request Forgery | [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/), [WAF managed rules](https://developers.cloudflare.com/waf/managed-rules/), [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/) |
| Security Misconfiguration | [Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/), [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/), [WAF managed rules](https://developers.cloudflare.com/waf/managed-rules/), [GraphQL Query Protection](https://developers.cloudflare.com/api-shield/security/graphql-protection/) |
| Improper Inventory Management | [Discovery](https://developers.cloudflare.com/api-shield/security/api-discovery/), [Schema learning](https://developers.cloudflare.com/api-shield/management-and-monitoring/#endpoint-schema-learning) |
| Unsafe Consumption of APIs | [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/), [WAF managed rules](https://developers.cloudflare.com/waf/managed-rules/) |
---
title: 404 - Page Not Found · Cloudflare Argo Smart Routing docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/argo-smart-routing/404/
md: https://developers.cloudflare.com/argo-smart-routing/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Analytics · Cloudflare Argo Smart Routing docs
description: Cloudflare provides analytics to show the performance benefits of
Argo Smart Routing.
lastUpdated: 2025-09-17T12:18:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/argo-smart-routing/analytics/
md: https://developers.cloudflare.com/argo-smart-routing/analytics/index.md
---
Cloudflare provides analytics to show the performance benefits of Argo Smart Routing.
You can access Argo analytics for your domain in the [Cloudflare dashboard](https://dash.cloudflare.com/) at **Analytics** > **Performance**. For information on all analytics in the dashboard, refer to [Analytics](https://developers.cloudflare.com/analytics/).
## How it works
Analytics collects data based on the time-to-first-byte (TTFB) from your origin to the Cloudflare network. TTFB is the delay between when Cloudflare sends a request to your server and when it receives the first byte in response. Argo Smart Routing optimizes your server's network transit time to minimize this delay.
Note
Detailed performance data within **Origin Performance (Argo)** will only display if Argo has routed at least 500 origin requests within the last 48 hours.
## Types of analytics
The dashboard displays two different views for performance data:
* **Origin Response Time**: A histogram shows response time from your origin to the Cloudflare network. The blue bars show TTFB without Argo, while the orange bars show TTFB where Argo found a Smart Route.
* **Geography**: A map shows the improvement in response time at each Cloudflare data center.
* A negative value indicates that requests from that location would not have benefited from Argo Smart Routing, so instead would have been routed directly.
---
title: Argo for Packets · Cloudflare Argo Smart Routing docs
description: Argo for Packets provides IP layer network optimizations to
supercharge your Cloudflare network services products like Magic Transit,
Magic WAN, and Cloudflare for Offices.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/argo-smart-routing/argo-for-packets/
md: https://developers.cloudflare.com/argo-smart-routing/argo-for-packets/index.md
---
Argo for Packets provides IP layer network optimizations to supercharge your Cloudflare network services products like [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Cloudflare for Offices](https://blog.cloudflare.com/cloudflare-for-offices/).
Argo for Packets dynamically chooses the best possible path through Cloudflare's network and looks at every path back from every Cloudflare data center back to your origin, down to the individual network path. Argo compares existing Layer 4 traffic and network analytics across all of these unique paths to determine the fastest, most available path.
Customers with multiple locations will especially benefit from Argo for Packets because it optimizes complex paths on the Internet and makes them just as fast as the other paths.
To begin using Argo for Packets, contact your account manager.
---
title: Get started · Cloudflare Argo Smart Routing docs
description: Learn how to enable Argo Smart Routing in the Cloudflare dashboard.
lastUpdated: 2025-10-09T07:47:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/argo-smart-routing/get-started/
md: https://developers.cloudflare.com/argo-smart-routing/get-started/index.md
---
Smart Shield
This functionality is now offered as part of Cloudflare's origin server safeguard, Smart Shield. [Learn more](https://developers.cloudflare.com/smart-shield/).
Argo Smart Routing is a one-click solution to speed up your global traffic.
* Dashboard
To enable [Argo Smart Routing](https://dash.cloudflare.com/?to=/:account/:zone/traffic) in the dashboard:
1. In the Cloudflare dashboard, go to the **Argo Smart Routing** page.
[Go to **Argo Smart Routing**](https://dash.cloudflare.com/?to=/:account/:zone/traffic)
2. For **Argo Smart Routing**, switch the toggle to **On**.
3. Provide your billing information.
* If you do not have a [billing profile](https://developers.cloudflare.com/billing/create-billing-profile/), enter your billing information.
* If you have a billing profile, confirm your billing information.
* API
To enable or disable Argo Smart Routing with the API, send a [`PATCH`](https://developers.cloudflare.com/api/resources/argo/subresources/smart_routing/methods/edit/) request with the `value` parameter set to your desired setting (`"on"` or `"off"`).
You will need to already have a [billing profile](https://developers.cloudflare.com/billing/create-billing-profile/) on your account to enable Argo Smart Routing.
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
## Billing
If Cloudflare mitigates attacks on your site - whether through DDoS protection, the WAF, or other mechanisms - that traffic will not be included in any charges for Argo Smart Routing.
Since this is a service with [usage-based billing](https://developers.cloudflare.com/billing/usage-based-billing/), Cloudflare recommends that you set up usage-based billing notifications to avoid unexpected bills.
To set up those notifications:
1. In the Cloudflare dashboard, go to the **Notifications** page.
[Go to **Notifications**](https://dash.cloudflare.com/?to=/:account/notifications)
2. On **Alert Type** of **Usage Based Billing**, click **Select**.
3. Fill out the following information:
* **Name**
* **Product**
* **Notification limit** (exact metric will vary based on product)
* **Notification email**
Note
Some plans also have access to alerts through [PagerDuty](https://developers.cloudflare.com/notifications/get-started/configure-pagerduty/) and [Webhooks](https://developers.cloudflare.com/notifications/get-started/configure-webhooks/).
4. Select **Save**.
## Enable Tiered Cache
[Cache](https://developers.cloudflare.com/cache/) works by storing a copy of website content at Cloudflare's data centers. [Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) divides these data centers into a hierarchy based on location. This behavior allows Cloudflare to deliver content from data centers closest to your visitor.
Argo Smart Routing and Tiered Cache work together to provide the most efficient connection for visitors to your site. For more information, go to [Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/).
---
title: 404 - Page Not Found · Cloudflare Automatic Platform Optimization docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/automatic-platform-optimization/404/
md: https://developers.cloudflare.com/automatic-platform-optimization/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About · Cloudflare Automatic Platform Optimization docs
description: With Automatic Platform Optimization (APO), Cloudflare serves your
entire site from our edge network, ensuring customers see improved performance
when visiting your site. Cloudflare typically only caches static content, but
with APO, we can also cache dynamic content — like HTML — to serve the entire
site from the cache. This process removes round trips from the origin to
drastically improve time to first byte (TTFB) along with other site
performance metrics. In addition to caching dynamic content, APO caches
third-party scripts to further reduce the number of requests that leave
Cloudflare's edge network.
lastUpdated: 2025-05-02T13:58:18.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/automatic-platform-optimization/about/
md: https://developers.cloudflare.com/automatic-platform-optimization/about/index.md
---
With Automatic Platform Optimization (APO), Cloudflare serves your entire site from our edge network, ensuring customers see improved performance when visiting your site. Cloudflare typically only caches static content, but with APO, we can also cache dynamic content — like HTML — to serve the entire site from the cache. This process removes round trips from the origin to drastically improve time to first byte (TTFB) along with other site performance metrics. In addition to caching dynamic content, APO caches third-party scripts to further reduce the number of requests that leave Cloudflare's edge network.
With APO, you can manage your WordPress site as normal. Whenever you update content in WordPress, Cloudflare updates content on our edge to prevent serving stale content when you use Cloudflare's WordPress plugin. Additionally, for logged-in or administrator users, we bypass the cache to ensure that private content is not cached and served to other visitors. Find more about [what APO can do for you.](https://www.youtube.com/watch?v=DWANhxoDxFI?feature=youtu.be)
## Limitations
Automatic Platform Optimization is not compatible with Enterprise [subdomain setup](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/) when a subdomain, for example, `www` is in a different zone to the apex domain.
---
title: Get started with APO · Cloudflare Automatic Platform Optimization docs
description: Before you configure APO for your WordPress site, complete the following tasks.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/automatic-platform-optimization/get-started/
md: https://developers.cloudflare.com/automatic-platform-optimization/get-started/index.md
---
Before you configure APO for your WordPress site, complete the following tasks.
* [Confirm DNS records](https://developers.cloudflare.com/automatic-platform-optimization/get-started/confirm-dns-records/)
* [Change nameservers](https://developers.cloudflare.com/automatic-platform-optimization/get-started/change-nameservers/)
* [Activate the Cloudflare WordPress plugin](https://developers.cloudflare.com/automatic-platform-optimization/get-started/activate-cf-wp-plugin/)
* [Verify APO works](https://developers.cloudflare.com/automatic-platform-optimization/get-started/verify-apo-works/)
---
title: Reference · Cloudflare Automatic Platform Optimization docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/automatic-platform-optimization/reference/
md: https://developers.cloudflare.com/automatic-platform-optimization/reference/index.md
---
* [Query parameters and cached responses](https://developers.cloudflare.com/automatic-platform-optimization/reference/query-parameters/)
* [Page Rule integration with APO](https://developers.cloudflare.com/automatic-platform-optimization/reference/page-rule-integration/)
* [Cache by device type](https://developers.cloudflare.com/automatic-platform-optimization/reference/cache-device-type/)
* [Subdomains and subdirectories](https://developers.cloudflare.com/automatic-platform-optimization/reference/subdomain-subdirectories/)
---
title: Troubleshooting · Cloudflare Automatic Platform Optimization docs
description: The WordPress plugin may go undetected on your Cloudflare dashboard
for a few reasons.
lastUpdated: 2025-05-08T20:05:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/automatic-platform-optimization/troubleshooting/
md: https://developers.cloudflare.com/automatic-platform-optimization/troubleshooting/index.md
---
## WordPress plugin is undetected on Cloudflare dashboard
The WordPress plugin may go undetected on your Cloudflare dashboard for a few reasons.
* Versions older than 3.8.2 of the WordPress plugin are installed.
* **Solution:** Install version 4.4.0 of the WordPress plugin.
* Version 3.8.2 of the plugin is installed but existing cache plugins return stale responses, for example, without `cf-edge-cache` header.
* **Solution:** Enable APO from the WordPress plugin and purge the cache in the existing cache plugins.
* WordPress only runs on a subdomain, but WordPress and the WordPress plugin check against the apex domain.
* **Solution:** For additional information, see [Subdomains and subdirectories](https://developers.cloudflare.com/automatic-platform-optimization/reference/subdomain-subdirectories/)
If your Cloudflare dashboard cannot detect the WordPress plugin after trying the solutions above, ensure you completed all of the steps listed in [Activate the Cloudflare WordPress plugin](https://developers.cloudflare.com/automatic-platform-optimization/get-started/activate-cf-wp-plugin/).
Note
The Cloudflare APO WordPress plugin does not support multisite WordPress installation.
## WordPress returns stale content
If WordPress is returning stale content, [purge the cache](https://developers.cloudflare.com/cache/how-to/purge-cache/) when APO is enabled.
---
title: 404 - Page Not Found · Cloudflare Billing docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/404/
md: https://developers.cloudflare.com/billing/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Billing policy · Cloudflare Billing docs
description: The terms subscription and add-on service are used interchangeably
in this support guide.
lastUpdated: 2025-11-05T16:12:03.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/billing-policy/
md: https://developers.cloudflare.com/billing/billing-policy/index.md
---
**The terms subscription and add-on service are used interchangeably in this support guide.**
Cloudflare plans and add-on services are billed every 30 days for each domain in your account.
Cloudflare plans are billed monthly and annually for each domain on the account. Monthly plans are billed every 30 days for each domain in your account, and annual plans are billed yearly for each domain in your account.
Add-on services are only billed monthly and cannot be billed annually.
Cloudflare also collects sales tax as governed by local laws. Sales taxes are computed based on the nine (9) digit postal code of either the shipping or billing address on file for your Cloudflare account where applicable.
Note
If you are a US-based customer, you can [file for sales tax exemption](https://developers.cloudflare.com/billing/sales-tax/#filing-for-us-sales-tax-exemption/).
Cloudflare issues a separate invoice for plans and subscriptions (or add-on services) for every domain added to a Cloudflare account.
Cloudflare issues a monthly or annual invoice based on the plans you purchase. You will receive a $0 invoice even if your domain is on a Free plan.
Note
Subdomains do not count as billable domains.
For example, if test1.com and test2.com are added to the same Cloudflare account and upgraded to the Pro plan, you will receive an invoice with two charges. Subdomains such as blog.test1.com or blog.test2.com will not be included as billable domains.
The date you initiate a paid plan or add-on service will be both the start of your billing period and your [invoice date](https://developers.cloudflare.com/billing/invoices/). For example, if you upgrade your plan on January 10, all future plan charges will be billed on the 10th of every month. Both dates are initialized using the UTC (Coordinated Universal Time) time zone, and not your local time zone.
If your account is dunned (downgraded and banned for non payment of dues), the new start date changes to the day of the upgrade and applies to monthly, yearly, and add-on plans.
When ordering a paid plan, subscription, or add-on service, you must agree to the following:
*By clicking "Enable" you agree that you are purchasing a continuous month-to-month subscription which will automatically renew, and that the price of your selected subscription plan level and/or add on(s) will be billed to your designated payment method monthly as a recurring charge, unless you cancel your subscription(s), through your account dashboard,* ***before*** *the beginning of your next monthly billing period.*
***You will be billed for the full monthly period in which you cancel and no refunds will be given. By purchasing a subscription, you agree to a minimum one month purchase obligation.***
Note
For more information on renewal terms and cancellation, refer to the [Terms of Use](https://www.cloudflare.com/terms/).
## Upgrade or downgrade Cloudflare paid plans
If your domain is on a paid plan (for example, Pro) and you upgrade to a higher-priced plan (for example, Business),
* Your invoice will reflect the prorated cost of the higher-tiered plan, until the end of your billing cycle.
* Cloudflare credits the prorated cost of the lower-priced plan, until the end of the billing cycle.
* At the beginning of the next billing cycle, your invoice will reflect the full cost of the higher-priced plan.
* Your bill cycle start and end dates are calculated using the UTC (Coordinated Universal Time) time zone, and not your local time zone.
For example, if your billing date is January 1, but you upgrade from Pro to Business, on January 15,
* Your invoice will reflect the prorated Business plan rate for the period of use January 15 - January 30.
* Cloudflare credits the prorated Pro plan cost from January 1 - January 15.
* Your invoice for the billing period of January 1 - January 30 will appear in the Cloudflare dashboard on January 31.
Note
Account credits are automatically added to your account and can only be used on recurring monthly charges for Cloudflare plans or add-on services. Your monthly invoice lists any credits.
All credits are added on the backend of your account and are not visible from the invoice. The invoice will, however, reflect any uses of applied account credits. Account credits can be used for any future Cloudflare transactions except Registrar transactions.
If your domain is on a paid plan (for example, Business) and you downgrade to a lower-priced plan (for example, Pro),
* Your plan type and higher-tiered Cloudflare plan features are downgraded at the end of the current billing service period.
* You are billed at the lower-tiered plan and feature rate for the next billing service period.
For example, if your billing date is February 1, but you downgrade to Pro from the Business plan on February 15,
* You can access Business plan features and services until March 1.
* Your March plan charges will reflect the downgraded cost.
## Billing and payment for Enterprise plans
Enterprise customers work with the Cloudflare account team to customize a plan and service contract to best suit their needs. The Cloudflare accounting team receives and processes Enterprise plan charges.
Enterprise account owners receive invoices directly from the Cloudflare accounting team.
## Approved payment methods
Cloudflare only accepts Visa, Mastercard, American Express, Discover, PayPal, Link, and UnionPay. No other payment methods (for example, Maestro) are possible at this time.
Note
Enterprise customers can use ACH payments for Cloudflare plans and subscriptions.
Please ensure that you're using a valid payment method before changing your plan type or enabling subscriptions.
Note
Gift cards and pre-payment cards may not be accepted for payment as they are not associated with a billing address.
## Account Payment Method Preauthorization
For services subject to usage-based billing, Cloudflare may preauthorize your credit card at any point in a billing period to confirm the payment method on file can cover accrued fees. This is a temporary hold and you will not be charged until the end of your billing period. If your payment method is validated, service will continue normally.
If your payment method fails, we may suspend your access to the usage-based billing services for which we conducted the preauthorization. In the case of [R2](https://developers.cloudflare.com/r2/), you will not be able to access your R2 buckets and requests will return errors, but your data will remain secure. If you do not update your payment method within 30 days, the data related to any usage-based billing service(s) may be deleted.
To regain access, you must settle any outstanding balances and pass preauthorization with a valid payment method. To update your primary payment method, navigate to the **Manage Account** > **Billing** > **Payment** section of your account. Upon validation of your updated payment details, we will promptly reactivate your subscription(s), which will restore access to the relevant data and services.
For assistance, visit our [Support Portal](https://support.cloudflare.com/hc/en-us) and submit a Billing request (category: “Payment issue”) to our Support team. They will assist you in verifying your updated payment information.
## Non-refundable occurrences
The following occurences cannot be refunded:
* Billing or renewal issues: Often involves charges for renewals, unexpected billing, or issues related to subscription payments.
* Accidental purchases of services and subscriptions: Includes instances where users bought the wrong service, made a mistake during the purchase process, or unintentionally upgraded their plan.
* Domain issues: Incorrect domain registration, issues with domain transfers, or accidental domain purchases.
* Service or plan issues: Issues with a service or plan itself, such as attempts to downgrade, cancel unused services, or problems with specific features.
* Support issues: Unresolved support issues.
## Related resources
* [Cloudflare Self-Serve Subscription Agreement](https://www.cloudflare.com/terms/)
* [Understanding Cloudflare Invoices](https://developers.cloudflare.com/billing/invoices/)
* [Understanding Cloudflare sales tax](https://developers.cloudflare.com/billing/sales-tax/)
---
title: Cancel Cloudflare subscriptions · Cloudflare Billing docs
description: Cancel Cloudflare subscriptions
lastUpdated: 2025-09-03T18:47:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/cancel-subscription/
md: https://developers.cloudflare.com/billing/cancel-subscription/index.md
---
Cancellations are not processed until the end of the billing period, so you can continue using the add-on or subscription until the new billing period begins. To avoid unwanted charges, start the cancellation process before the end of your billing period.
If you are making a subscription downgrade including a change from a yearly plan to a monthly plan or a change from a paid plan to a free plan, be aware that downgrades and cancellations do not take immediate effect and that you will continue to be billed and have access to your service for the remainder of your contracted service period. You should not contact Cloudflare to ask for exceptions to this policy or refunds for early downgrades and cancellations.
In addition, you may not always see a cancel button present for each subscription and often it is a switch from a paid plan to a free plan that will act as the cancellation of your paid subscription.
Note
All billing period dates on invoices and the dashboard are in UTC/GMT timezone, not your local timezone. We recommend any downgrades or changes to subscriptions be made at least 24 hours before stated billing date to avoid any timezone confusion.
***
## Step 1: Disable the Cloudflare subscription
To disable a subscription:
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Subscriptions**.
3. Select the feature you want to disable under **Active Subscriptions** (Free or Pro customers) or **Plan Extensions** (Enterprise customers).
4. Follow the instructions to disable the feature. Each feature has a different process which could include toggling a switch, clicking a button, or choosing *Disable* from a drop-down list.
## Step 2: Cancel the subscription in your billing profile
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Subscriptions**.
3. Find the subscription you want to disable and select **Cancel**.
4. You will be asked to share feedback with us. Choose all that apply.
5. Select **Confirm** to finish.
Note
To alter your plan, select **Change** under **Active Subscriptions** and choose a new plan type. If you would like to cancel your paid plan, select **Free**.
FEES ARE NONREFUNDABLE. YOU WILL BE BILLED IN FULL FOR THE SUBSCRIPTION TERM IN WHICH YOU CANCEL AND NO REFUNDS WILL BE PROVIDED FOR THE UNUSED PORTION OF SUCH SUBSCRIPTION TERM. Following any cancellation, however, you will continue to have access to the Paid Services through the end of your current Subscription Term (except with respect to Services subject to usage-based billing). We may, in our sole discretion, provide a refund, discount, or credit ("Credits") to you in a specific instance, however the provision of Credits in a specific instance does not entitle you to Credits in the future for similar instances or obligate us to provide additional Credits.
---
title: Change domain plan · Cloudflare Billing docs
description: Occasionally, you may want to upgrade or downgrade the plan
associated with a specific Cloudflare domain.
lastUpdated: 2025-05-22T15:53:35.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/change-plan/
md: https://developers.cloudflare.com/billing/change-plan/index.md
---
Occasionally, you may want to upgrade or downgrade the plan associated with a specific Cloudflare domain.
## Limitations
Only Super Administrators can manage changes to domain plans.
If you decide to downgrade or remove a domain, Cloudflare does not issue refunds. Refer to our [billing policy](https://developers.cloudflare.com/billing/billing-policy/) for more information.
Upgrades are processed immediately, but downgrades are not processed until the end of the billing period. You will not be able to upgrade if you have an unpaid invoice. When downgrading, you are allowed to continue using the higher plans' products until the new billing period begins.
If you downgrade your plan, your plan may have access to [fewer Page Rules](https://developers.cloudflare.com/rules/page-rules/). If you continue to use more page rules than is allowed by your plan limit, you may be charged for additional rules. Remove excess rules and [cancel additional subscriptions](https://developers.cloudflare.com/billing/cancel-subscription/) if you do not want to be charged.
The Enterprise App Sec Advanced and Enterprise App Sec Core plans cannot be downgraded without [contacting Cloudflare](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
For additional help, refer to [this Community thread](https://community.cloudflare.com/t/communitytip-page-rules-best-practices-when-downgrading-pro-to-free/305725).
## Change plan type
* Dashboard
To change the Cloudflare plan for a domain in the dashboard:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account and domain.
2. Go to **Overview**.
3. For Plan Extensions, select **Change**.
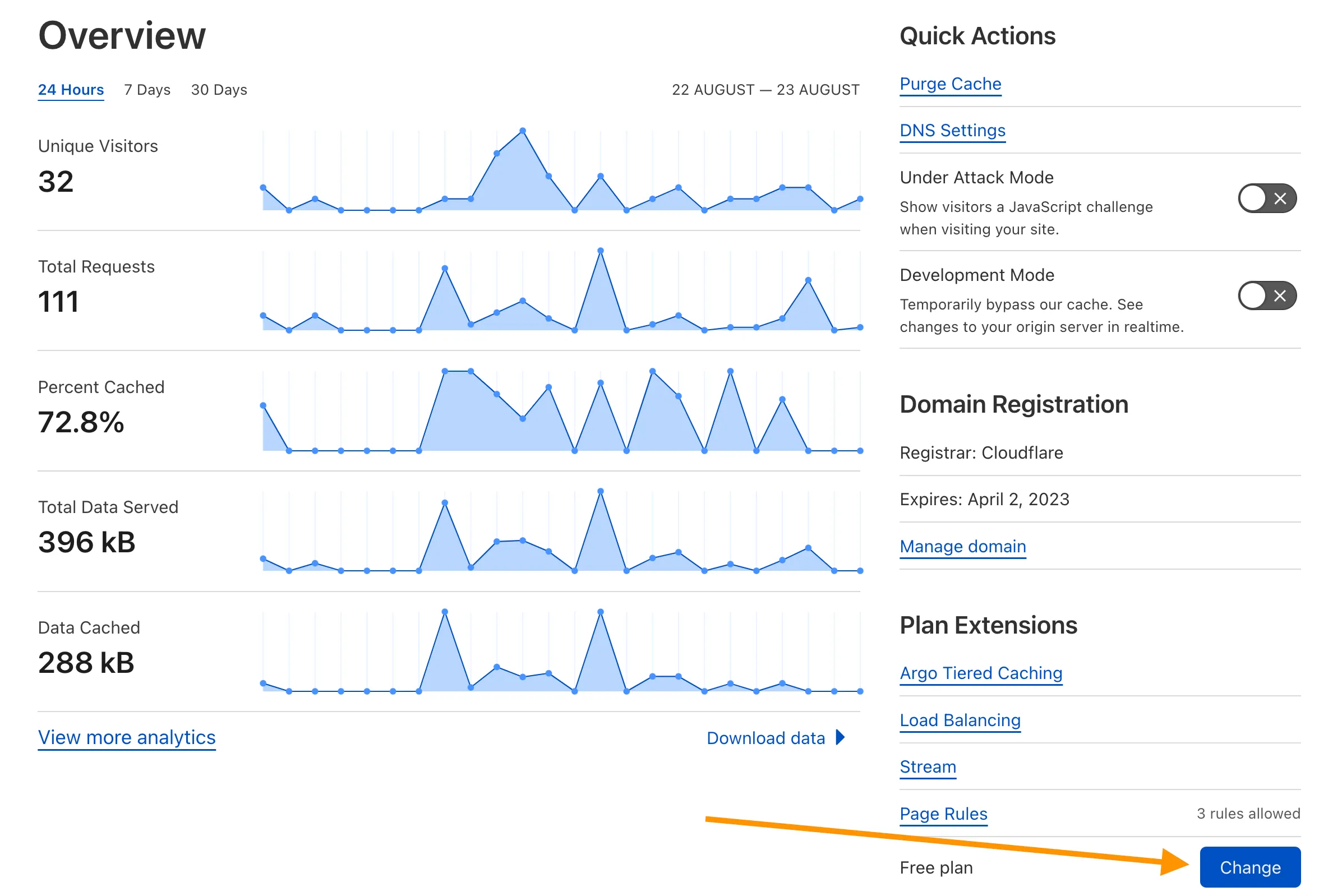
4. Choose the appropriate plan type, then select **Continue**.
5. Select **Confirm**.
* API
To change the Cloudflare plan for a domain using the API, first send a [`GET`](https://developers.cloudflare.com/api/resources/zones/subresources/plans/methods/list/) request to review available subscriptions.
Then, send a [`PUT`](https://developers.cloudflare.com/api/resources/zones/subresources/subscriptions/methods/update/) request with your desired plan type in the `rate_plan` object.
Note
If you are an Enterprise customer and cannot change your plan type, contact your Customer Success Manager.
## Change plan duration
* Dashboard
To change the duration of your Cloudflare plan in the dashboard:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account and domain.
2. Go to **Overview**.
3. For Plan Extensions, select **Change**.

4. Switch the toggle between **Monthly** or **Annual**.
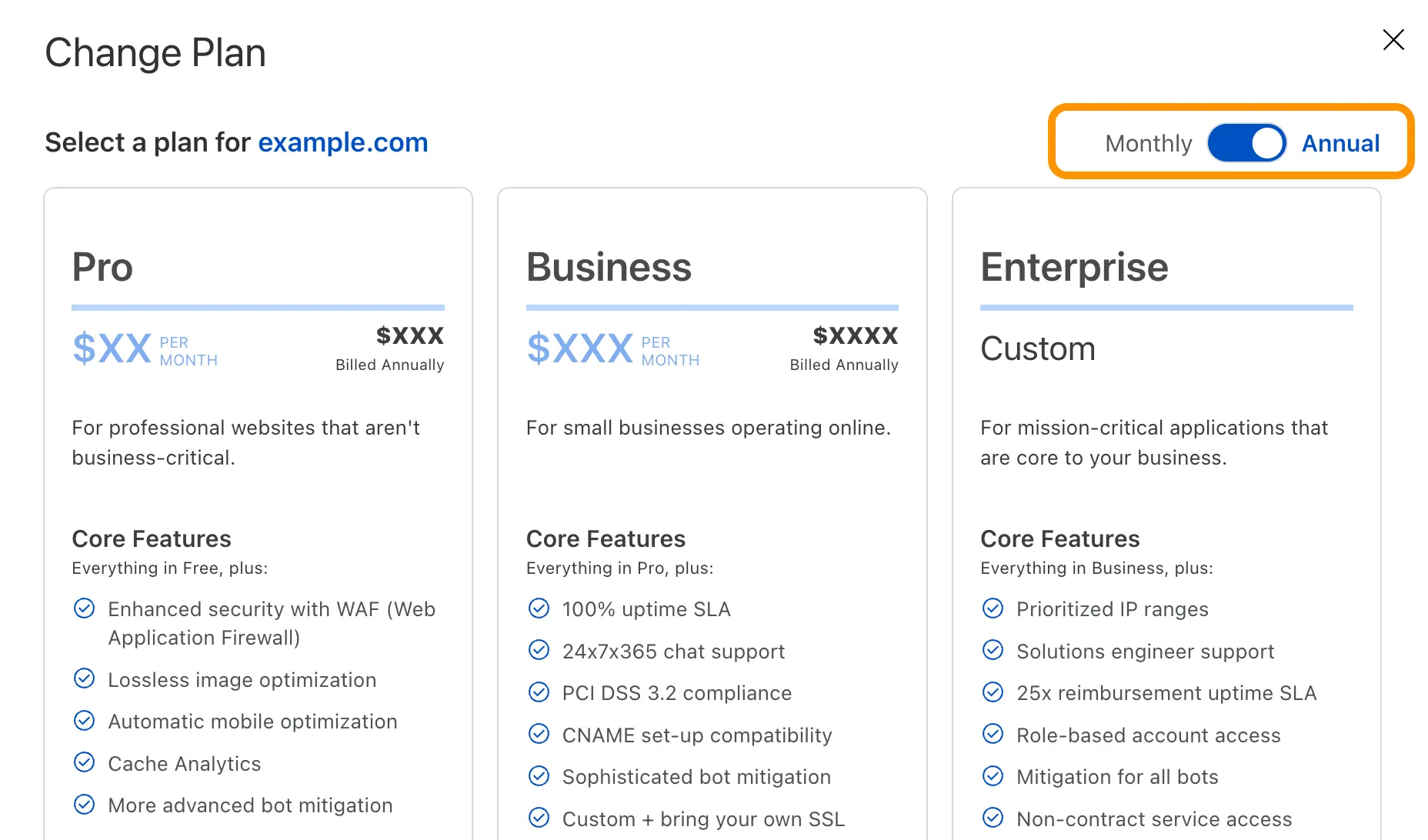
5. Choose the appropriate plan type, then select **Continue**.
6. Select **Confirm**.
* API
To change the duration of a Cloudflare plan for a domain using the API, send a [`PUT`](https://developers.cloudflare.com/api/resources/zones/subresources/subscriptions/methods/update/) request with an updated value for the `frequency` parameter.
---
title: Create billing profile · Cloudflare Billing docs
description: A primary payment method is required to process payment for
Cloudflare products and services. We value your confidentiality and privacy -
Cloudflare does not have access to your bank, credit card, pin, or PayPal
account password details.
lastUpdated: 2025-09-03T18:47:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/create-billing-profile/
md: https://developers.cloudflare.com/billing/create-billing-profile/index.md
---
## Add a primary payment method
A primary payment method is required to process payment for Cloudflare products and services. We value your confidentiality and privacy - Cloudflare does not have access to your bank, credit card, pin, or PayPal account password details.
Note
Customers on an [Enterprise plan](https://www.cloudflare.com/plans/enterprise/contact/) have [additional payment options](https://developers.cloudflare.com/billing/create-billing-profile/#payment-options) such as wire and ACH, as well as yearly or quarterly billing.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Payment**. If no payment method is on file, the **Payment methods** dialog opens automatically.
3. Select **Manage** next to your current payment method. The **Manage payment methods** dialog opens.
4. Enter the required information based on the payment options below: **Credit card**:
1. Enter the required information under the **Credit Card Details** form.
2. If applicable, add your business information to your invoice, including your **Company** and **VAT/GST Number**.
**PayPal** (Your credit card will be charged if you have insufficient funds in your PayPal account):
1. Select the **PayPal**.
2. Follow the online instructions until PayPal returns you to the Cloudflare **Payment Method** to continue your set-up.
3. Verify your **PayPal username** now appears next to the PayPal logo.
4. Add your account contact information as well as **Company** and **VAT/GST Number**, if applicable.
Note
Because some countries tax goods and services on personal accounts, you may be asked to indicate whether your Cloudflare account is personal or business to determine tax eligibility.
1. Review the payment method and contact information to ensure it is accurate.
2. To finish, select **Confirm**.
3. Ensure your new payment method appears in the **Payment Method** section.
Enterprise customers must email with the last four digits of the credit card and its expiration date.
## Add a backup payment method
Optionally, add a backup payment method to use if the primary payment method fails.
Note
You may receive the error message "Your account is limited to 2 payment methods, and you've reached that limit. Please remove an existing payment method before adding a new one." when trying to add additional methods.
If you are unable to add or edit a payment method, [delete a payment method](https://developers.cloudflare.com/billing/update-billing-info/#delete-a-payment-method) and try again.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Payment**.
3. From **Payment methods**, select **Manage**.
4. From **Backup**, select **Add** to enter a backup payment method.
5. Enter the required information based on your preferred payment method (credit card or PayPal) and select **Confirm**.
6. To make the backup payment method the primary method, select **Make primary payment method**.
## Payment options
Enterprise customers can submit payments via the following payment options:
### ACH
(preferred method)
* **Bank**: Citibank, One Penn's Way, New Castle, DE 19720 USA
* **Account name**: CLOUDFLARE INC
* **Account number**: 31460181
* **ABA/Routing number**: 031100209
### Wire transfer
* **Bank**: Citibank, One Penn's Way, New Castle, DE 19720 USA
* **Account name**: CLOUDFLARE INC
* **Account number**: 31460181
* **ABA/Routing number**: 031100209
* **SWIFT**: CITIUS33
### PayPal
Log in to your PayPal account and send your payment to . The payment must include the invoice number and customer name.
### International payments
* **Bank**: Citibank, One Penn's Way, New Castle, DE 19720 USA
* **Account name**: CLOUDFLARE INC
* **Account number**: 31460181
* **SWIFT**: CITIUS33
Note
US banks do not participate in International Bank Account Numbers (IBAN).
---
title: Invoices · Cloudflare Billing docs
description: "You will receive an invoice in the Billing section of your
Cloudflare account when you:"
lastUpdated: 2025-09-03T18:47:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/invoices/
md: https://developers.cloudflare.com/billing/invoices/index.md
---
You will receive an invoice in the **Billing** section of your Cloudflare account when you:
* Change your Cloudflare plan type.
* Upgrade or downgrade to or from a paid plan.
* Add a new domain to a Cloudflare account.
* Enable or renew a subscription or add-on service.
For any historical invoices not included in the **Billing** section, [contact Cloudflare support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
Note
Enterprise customers receive invoices directly from the Cloudflare accounting team.
## Enable email invoices from Cloudflare
To enable Cloudflare invoice emails which are sent when you add or remove subscriptions from your account:
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Invoices & Documents**.
3. From **Billing email preferences**, toggle the notification switch to **On**.
After you enable email invoices, you will receive invoices via email:
* Within one business day of initial set-up.
* Every month at the end of your billing period.
* Within one business day for all new purchases.
## Download invoice
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Invoices & Documents**.
3. Find the invoice you want to download and select the icon next to the invoice number.
Note
Invoices cannot be regenerated after they are issued. Any pending billing updates or changes will appear in the next month's invoice.
## Billing cycles
Monthly and annual billing subscriptions run on different billing cycles.
The first monthly purchase on a Cloudflare account sets the billing date for the following monthly subscriptions. The same behaviour occurs for annual subscriptions.
You can have two different billing cycles on your account, one for a monthly subscription and another for an annual subscription.
---
title: Pay an outstanding balance · Cloudflare Billing docs
description: "If the automatic retry attempts to take payment fails, and you
have not manually paid the invoice, your account will have an overdue balance.
An overdue balance will block you from purchasing new products or
subscriptions, upgrading existing ones, and you won’t be able to update your
billing profile until you have successfully paid the balance. Attempts to
purchase or upgrade subscriptions will return an error mentioning this:"
lastUpdated: 2026-01-05T16:15:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/pay-invoices-overdue-balances/
md: https://developers.cloudflare.com/billing/pay-invoices-overdue-balances/index.md
---
If the automatic retry attempts to take payment fails, and you have not manually paid the invoice, your account will have an overdue balance. An overdue balance will block you from purchasing new products or subscriptions, upgrading existing ones, and you won’t be able to update your billing profile until you have successfully paid the balance. Attempts to purchase or upgrade subscriptions will return an error mentioning this:
**You cannot add or modify subscriptions or services until the outstanding balance is paid.**
The full range of error messages you may see are:
* "You cannot add or modify subscriptions/services until your outstanding balance is paid. Please visit the Billing section to proceed."
The simplest way to pay your balance is to click **Pay Now** from your Billing homepage in the Cloudflare dashboard. To see these steps in more detail, refer to [Pay an outstanding balance](#pay-an-outstanding-balance).
You can pay your entire balance in one transaction, or if you have multiple invoices with unpaid amounts, you can choose to pay them individually by following [pay unpaid invoices](#manually-pay-invoices).
## Understand why you have an outstanding balance
Warning
Please note that some unpaid invoices may not be visible. These unpaid invoices will still prevent account modifications. In these cases you should [contact Cloudflare Support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
When an outstanding balance is due, a new invoice will be created in your account for that amount. When you view that new invoice, it will show the original invoice number that the outstanding balance relates to. You can look up this original invoice to understand which product(s) were not fully paid for.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Invoices and documents**.
3. Select the most recent invoice - the amount shown should match your outstanding balance
4. On the invoice PDF, look for the section below the **Pay Online** link: **Invoice that pays the following outstanding balance:** and note the invoice number
5. Go back to the **Invoices and documents** section and click to view the invoice number
## Pay an outstanding balance
Note
Allow up to 24 hours for your payment to be recognized and for your account to be in good standing. After that time has passed, you will be able to manage your subscriptions and order more services.
To pay the total outstanding balance:
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Go to the **Pay overdue balances** section.
3. Select **Pay now** next to the balance you want to pay.
You will be redirected to our payment system to proceed.
## Manually pay invoices
If an automatic subscription renewal payment fails, Cloudflare automatically retries the payment using your default payment method five times over five days. During this period, you can log into the dashboard and attempt to manually pay the invoices.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Invoices and documents**.
3. Select **Pay now** next to the invoice you want to pay.
You will be redirected to our payment system to proceed.
---
title: Preview services · Cloudflare Billing docs
description: Contracted customers can try certain products and features for 30 days.
lastUpdated: 2025-05-22T15:53:35.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/preview-services/
md: https://developers.cloudflare.com/billing/preview-services/index.md
---
Contracted customers can try certain products and features for 30 days.
Once you enable the product or feature, it will not be an officially contracted service until you purchase it. Cloudflare will reach out in case you have any questions or feedback, and provide you with a sales quote if you are enjoying the product.
You may cancel at any time before the 30 days ends by reaching out to your sales team for assistance.
## Available features and products
To enable a preview service, use the **Dashboard link** in the following table. Then, select **Enable**. And that is it. You will have instant access to the product or feature you selected so you can begin determining if it is right for your business' needs.
| Name | Dashboard link | Docs | Community |
| - | - | - | - |
| Advanced Certificate Manager (ACM) | [ACM dashboard](https://dash.cloudflare.com/?to=/:account/:zone/ssl-tls/edge-certificates) | [ACM docs](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/) | [ACM community](https://community.cloudflare.com/c/security/6) |
| API Shield | [API Shield dashboard](https://dash.cloudflare.com/?to=/:account/:zone/security/api-shield) | [API Shield docs](https://developers.cloudflare.com/api-shield/) | [API Shield community](https://community.cloudflare.com/) |
| Argo Smart Routing | [Argo dashboard](https://dash.cloudflare.com/?to=/:account/:zone/traffic) | [Argo docs](https://developers.cloudflare.com/argo-smart-routing/) | [Argo community](https://community.cloudflare.com/c/performance/argo/45) |
| Bot Management | [Bot Management dashboard](https://dash.cloudflare.com/?to=/:account/:zone/security/bots) | [Bot Management docs](https://developers.cloudflare.com/bots/plans/bm-subscription/) | [Bot Management community](https://community.cloudflare.com/c/security/6) |
| Cloudflare for SaaS | [Cloudflare for SaaS dashboard](https://dash.cloudflare.com/?to=/:account/:zone/ssl-tls/custom-hostnames) | [Cloudflare for SaaS docs](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/) | [Cloudflare for SaaS community](https://discord.cloudflare.com) |
| Images | [Images dashboard](https://dash.cloudflare.com/?to=/:account/images) | [Images docs](https://developers.cloudflare.com/images/) | [Images community](https://community.cloudflare.com/c/developers/images/63) |
| Load Balancing | [Load Balancing dashboard](https://dash.cloudflare.com/?to=/:account/:zone/traffic/load-balancing) | [Load Balancing docs](https://developers.cloudflare.com/load-balancing/) | [Load Balancing community](https://community.cloudflare.com/tag/loadbalancing) |
| Advanced Rate Limiting | [Rate Limiting dashboard](https://dash.cloudflare.com/?to=/:account/:zone/security/waf/rate-limiting-rules) | [Rate Limiting docs](https://developers.cloudflare.com/waf/rate-limiting-rules/) | [Rate Limiting community](https://community.cloudflare.com/c/security/6) |
| Stream | [Stream dashboard](https://dash.cloudflare.com/?to=/:account/stream) | [Stream docs](https://developers.cloudflare.com/stream/) | [Stream community](https://community.cloudflare.com/tag/cloudflarestream) |
| Waiting Room | [Waiting Room dashboard](https://dash.cloudflare.com/?to=/:account/:zone/traffic/waiting-rooms) | [Waiting Room docs](https://developers.cloudflare.com/waiting-room/) | [Waiting Room community](https://community.cloudflare.com/) |
| Web3 | [Web3 dashboard](https://dash.cloudflare.com/?to=/:account/:zone/web3) | [Web3 docs](https://developers.cloudflare.com/web3/) | [Web3 discord](https://discord.cloudflare.com) |
| Workers | [Workers dashboard](https://dash.cloudflare.com/?to=/:account/workers) | [Workers docs](https://developers.cloudflare.com/workers/) | [Workers discord](https://discord.com/invite/cloudflaredev) |
| Zero Trust | [Zero Trust dashboard](https://one.dash.cloudflare.com/) | [Zero Trust docs](https://developers.cloudflare.com/cloudflare-one/) | [Zero Trust community](https://community.cloudflare.com/c/security/access/51) |
## Recommendations
Since these services are not yet part of your contract, we recommend that you use them on staging or other, non-production environments.
## View enabled products
To view which products you have previously enabled, go to your [Account Subscriptions](https://dash.cloudflare.com/?to=/:account/billing/subscriptions) page and look for items that with **Terms** of **NOT IN CONTRACT**.
---
title: Resolve "cannot remove payment method" · Cloudflare Billing docs
description: "This article will help if you are receiving an error that mentions
one of the following errors when attempting to remove a payment method:"
lastUpdated: 2026-01-05T16:15:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/resolve-cannot-remove-payment-method/
md: https://developers.cloudflare.com/billing/resolve-cannot-remove-payment-method/index.md
---
This article will help if you are receiving an error that mentions one of the following errors when attempting to remove a payment method:
* "You can't remove this payment method while it's linked to active subscriptions. Go to Billing to manage subscriptions."
* "You can't remove a payment method while there are transactions in progress. Make sure all transactions are completed and all subscriptions are cancelled."
## Causes
* You still have active paid subscriptions
* You have cancelled your paid subscriptions, but a usage-based charge is still scheduled
* You have an upcoming Registrar domain registration renewal within the next 24 hours
## Solutions
You can resolve this by checking your account for each of the potential causes.
### Check for active paid subscriptions
You can only remove your payment method once all your paid subscriptions and outstanding charges have been completed. To check your paid subscriptions are cancelled follow this:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Manage Account > Billing**.
3. Go to **Subscriptions**.
4. Check **Service status** for any which are marked “Active”
5. Click the “Cancel” button
You must complete this for all active paid subscriptions before you will be able to remove your card.
### Check for Usage Based products
If you have cancelled all of your paid products & subscriptions, any usage based products cancelled within the last 30 days may still generate charges. We require that your payment method remains on file until those potential usage charges have been processed. As such, if you recently cancelled any of the following products, you will need to wait 30 days before you can remove your payment method:
* Images
* Stream
* Workers
* Argo
* Spectrum
* R2
* Cache Reserve
* Load Balancing
* Rate Limiting
* Log Explorer
* Zero Trust
* Vectorize
* Analytics
Once your next monthly invoice has been produced you should be able to remove your card.
### Check for an upcoming Registrar renewal
For Registrar domains scheduled for auto-renewal, we will attempt to renew approximately 30 days before your renewal date. In the 24 hours prior to that, we will automatically process a payment hold using your payment method. During this time you will be unable to remove your payment method.
To check if any of your domains are in the process of renewal:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Domain Registration > Manage Domains**.
3. Under the **Expires** column, look for any domains expiring within the next 31 days which have Auto-renew enabled.
If you have any domains with auto-renew enabled that are expiring in 31 days or less, you will need to wait for them to renew before you can remove your payment method. To understand more about this process, refer to [renew domains](https://developers.cloudflare.com/registrar/account-options/renew-domains/).
### If none of the above apply
If you have confirmed all of the above do not apply in your case and you still receive an error message when attempting to remove your payment method, please [contact support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
---
title: Resolve "you cannot modify this subscription" · Cloudflare Billing docs
description: 'This article will help if you are receiving an error that mentions
"You cannot modify this subscription since it is currently scheduled to be
cancelled" when attempting to cancel or modify a subscription. For reference,
the full message you receive may be one of the following:'
lastUpdated: 2026-01-05T16:15:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/resolve-you-cannot-modify-this-subscription/
md: https://developers.cloudflare.com/billing/resolve-you-cannot-modify-this-subscription/index.md
---
This article will help if you are receiving an error that mentions "You cannot modify this subscription since it is currently scheduled to be cancelled" when attempting to cancel or modify a subscription. For reference, the full message you receive may be one of the following:
* "This subscription is scheduled to be cancelled at the end of the billing period. To make changes or purchase more, please click 'Cancel Downgrade' on the Subscriptions page."
## Causes
* You are attempting to cancel a subscription which you have already requested cancellation for
* You are attempting to upgrade a subscription for which a cancellation is already scheduled
## Solutions
If your intent is to cancel a subscription, this request has already been scheduled and your subscription will be cancelled at the end of the current billing period. See “When will my subscription be cancelled” below to understand the exact date this will take effect.
### When will my subscription be cancelled?
Once you have requested cancellation, you will see the date your subscription will be cancelled on the subscriptions page underneath the text “Ending On”.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Manage Account > Billing**.
3. Go to **Subscriptions**.
4. Locate the **Product** you have cancelled
5. Under the **Service status** column, the status should say **ENDING ON** with the date cancellation will take effect
If you previously cancelled the subscription and have changed your decision, you need to cancel the downgrade.
### Can I receive a refund for my cancelled subscription?
No refund will be issued for a cancelled subscription - instead, your subscription will remain active until the end of the current billing period.
If you do not wish to pay for the coming billing period, then you should cancel your subscription no later than on the last day of the billing period. You can discover this date by visiting the **Subscriptions** page and checking the renew date, for example “RENEWS ON Aug 29, 2025”.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Manage Account > Billing**.
3. Go to **Subscriptions**.
4. Locate the **Product** you have cancelled
5. Under the **Service status** column, the status should say **RENEWS ON** with the date of the next renewal
### Can I stop the cancellation?
If the cancellation hasn’t taken effect yet, you can click **Cancel Downgrade** next to the appropriate subscription in the **Billing > Subscriptions** page.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Manage Account > Billing**.
3. Go to **Subscriptions**.
4. Locate the **Product** you have cancelled
5. Under the **Action** column, click **Cancel Downgrade**
---
title: Resolve the zone cannot be upgraded error · Cloudflare Billing docs
description: "When trying to upgrade a domain or purchase a subscription, you
may see an error that contains one of the following phrases:"
lastUpdated: 2026-01-05T16:15:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/resolve-zone-cannot-be-ugpraded/
md: https://developers.cloudflare.com/billing/resolve-zone-cannot-be-ugpraded/index.md
---
When trying to upgrade a domain or purchase a subscription, you may see an error that contains one of the following phrases:
* "this zone cannot be upgraded"
* "there is a problem with your billing profile"
## Causes
* Your account may have an outstanding unpaid balance
* Another account previously associated with the domain / zone your purchase relates to has an outstanding unpaid balance
## Solution
This message appears when the account or domain involved has an outstanding unpaid balance. In the case of a domain, this may also be triggered by a previous account that owned the domain. To resolve this you will need to:
1. Check each Cloudflare account you have access to for an outstanding balance. Refer to [Email address and password](https://developers.cloudflare.com/fundamentals/user-profiles/change-password-or-email/) if you have forgotten these details.
2. Refer to [Pay an overdue balance](https://developers.cloudflare.com/billing/pay-invoices-overdue-balances/#pay-an-overdue-balance) to pay this balance
3. Wait 24 hours after paying this balance
4. Attempt to upgrade again
As a reference, the full error messages you may see are:
* "Due to a Billing related issue, the zone cannot be upgraded at this time. Please visit the Billing section to ensure there is no outstanding balance."
* "Refer to for assistance. For security reasons, there is a problem with your billing profile."
---
title: Sales tax · Cloudflare Billing docs
description: To adhere to tax laws in specific geographies, Cloudflare collects
sales tax on sales of our services based on your billing address.
lastUpdated: 2025-09-12T21:09:09.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/sales-tax/
md: https://developers.cloudflare.com/billing/sales-tax/index.md
---
To adhere to tax laws in specific geographies, Cloudflare collects sales tax on sales of our services based on your billing address.
To avoid unwanted charges, ensure your billing address and payment method are accurate within your Cloudflare account.
Note
Cloudflare customers in a sponsorship program (i.e. [Project Athenian](https://www.cloudflare.com/athenian/), [Project Galileo](https://www.cloudflare.com/galileo/), [Cloudflare for Campaigns](https://www.cloudflare.com/campaigns/)) are not charged sales tax.
## US State sales tax
In the US, sales tax requirements are computed based on the 9-digit postal code of the address on file for your Cloudflare account. Note to customers in Maryland: On July 1, 2025, Maryland began charging a tax on some technology services, including some provided by Cloudflare.
### Filing for US sales tax exemption
Cloudflare is required by law to maintain documentation of tax-exempt sales. If you or your company are exempt from paying sales tax, email from an email address associated with your Cloudflare account and provide one of the following forms of tax-exempt documentation:
* Resale certificate
* Multi-state tax exemption certificate
* State sales tax exemption certificate
* Partial sales tax exemption certificate
After your exemption is validated, tax-exempt status is added to your Cloudflare account information. Cloudflare invoices do not contain sales tax for the duration your exemption is valid.
## Russia (VAT)
Foreign e-services suppliers are required by law to collect taxes on the supply of e-services to Russian customers. Cloudflare customers with Russian billing addresses are charged a 20% flat tax rate based on their billing address on file.
[Update your billing information](https://developers.cloudflare.com/billing/update-billing-info/) with your Russian VAT ID to include it in your Cloudflare invoices.
Note
There is no tax exemption for Russian customers.
## Singapore (GST)
Cloudflare adds 9% sales tax for individuals and non-GST registered business customers within Singapore. GST-registered customers are required to self access GST. Refunds are not issued for taxed customers that were missing the GST Registration Number within their Cloudflare account.
Contact with any questions.
## Taiwan (VAT)
Cloudflare collects VAT on all pay-as-you-go customers in Taiwan. The eGUI Invoice ID and eGUI Code are shown in the Cloudflare dashboard and are required to retrieve an invoice from the Taiwan government.
## Japan (CT)
Cloudflare Inc. is currently registered in Japan as of October 1st, 2023. Due to some constraints, Cloudflare will be only able to start collecting tax from PAYGO customers on April 1st, 2024.
## Canada
All **NON-GST Registered** Customers who are located in Canada are required by law to pay tax.
Note
Anyone who provides a GST ID is exempt, no other exceptions.
## Malaysia (VAT)
All customers who are located in Malaysia are required to pay tax. This includes companies located or whose management is located in Malaysia. **Non-Residents of Malaysia are exempt.**
If there is no invoice, there is no VAT. VAT is calculated on the amount billed.
## South Africa (VAT)
All customers who are located in South Africa are required to pay tax. This includes companies located or whose management is located in South Africa. **Non-Residents of South Africa are exempt.**
If there is no invoice, there is no VAT. VAT is calculated on the amount billed.
## India (GST)
Cloudflare Inc. is registered for Goods and Services Tax (GST) purposes in India as of October 1st, 2023.
An email communication, in both English and Hindi, was shared at the end of October and the beginning of November with all Indian customers to inform and request them to update addresses and GST IDs accordingly.
Make sure that your complete address and GST ID is properly updated on your account to avoid additional charges.
## Kenya (VAT)
Cloudflare will issue tax invoices and add VAT at the 16% standard rate on top of the amounts charged beginning on October 1st, 2023.
You may update your VAT registration number in your account profile.
Reach out to Cloudflare via email if you have any tax related concerns or questions.
---
title: Resolve a payment failure · Cloudflare Billing docs
description: "This article will help if you are receiving errors about your
payment failing when attempting to purchase something, change an existing
subscription, pay an invoice or an outstanding balance. You may see one of the
following error messages:"
lastUpdated: 2026-01-05T16:15:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/troubleshoot-failed-payments/
md: https://developers.cloudflare.com/billing/troubleshoot-failed-payments/index.md
---
This article will help if you are receiving errors about your payment failing when attempting to purchase something, change an existing subscription, pay an invoice or an outstanding balance. You may see one of the following error messages:
* "The payment has failed. Please contact your bank or use a different payment method."
* "Payment error: authorization failed for \[“example.com”]"
Alternatively, you may receive an email from us about a subscription renewal payment failure with the subject: “\[Cloudflare]: We couldn't process your renewal payment” which states “We were unable to process your renewal payment”.
## Automatic retries and product removal
If the failed payment relates to a recurring charge for a Cloudflare plan, add-on, or subscription then after a five (5) day grace period, your account is automatically downgraded to a Free plan. Downgrading to a Free plan does not suspend your website, but you will lose any subscriptions or add-on services associated with the Pro, Business, or Enterprise plan.
To avoid this, follow the Causes & Solution sections below to resolve the failing payment and retry. If you are unable to resolve the issue within the 5 day grace period, you’ll need to manually re-subscribe to these products. You may need to [pay an overdue balance](https://developers.cloudflare.com/billing/pay-invoices-overdue-balances/#pay-an-overdue-balance) relating to the five day grace period, if applicable.
## Causes
* Your card details are incorrect
* There are not enough funds in your account
* You did not pass 3D Secure (3DS) correctly
* Your bank is rate limiting payments from us
* Your bank is declining the payment
## Solution
### Check your details & contact your bank
#### Check your card details
* Check your address is valid and matches the one registered with your bank for the payment method you are using
* Check that the Card Verification Value (CVC) you entered is correct for your card
* If you are using PayPal, check for a verification email to your PayPal email address and follow the instructions to authorize
#### Check you have enough funds
Double check your payment method’s balance to ensure that your account has enough funds.
#### Correctly authorise your transaction with 3D Secure (3DS)
You may be using a bank that mandates the use of 3D Secure (3DS) for online card transactions. For one off or first time subscription payments, you need to be prepared to pass 3DS authentication when you attempt the payment in the Cloudflare dashboard. Your bank will contact you to authorise the transaction in real time. This contact typically comes via an SMS or push notification from your bank’s mobile application.
Please note that for customers of Indian banks, 3DS is mandatory for all transactions as per the mandate from the Reserve Bank of India (RBI).
#### Contact your bank if purchasing / renewing Registrar domains
If you were purchasing or renewing multiple domains via [Cloudflare Registrar](https://developers.cloudflare.com/registrar) each domain will be charged as a separate transaction. This may be flagged as fraud by your credit card company. You will need to contact your bank in order to confirm and resolve this.
#### Contact your bank to understand & fix the declined payment
Cloudflare’s payment system does not know why a payment was declined, so you should contact your bank to confirm specifically why they declined the payment.
### Try your payment again
Once you have checked the items above, you should try your transaction again by visiting the Cloudflare dashboard. If the payment that failed was a renewal payment, we will retry automatically 5 times in 5 days. However, we recommend you retry the payment manually in the dashboard to receive instant feedback. To do this:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Manage Account > Billing**.
3. Go to **Invoices and documents**.
4. Click **Pay Now** next to your invoice OR from the Invoice PDF, click the payment link.
5. Follow the on screen instructions to try again.
### Try a new payment method
If you cannot resolve this using your current payment method, you may wish to try an alternative payment method. We support multiple different credit card types and PayPal. To try this, refer [add a new payment method](https://developers.cloudflare.com/billing/update-billing-info/#update-payment-methods).
---
title: Troubleshoot invoices · Cloudflare Billing docs
description: If your billing contact information has changed, update your
Cloudflare email address as soon as possible.
lastUpdated: 2025-08-21T17:26:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/troubleshoot-invoices/
md: https://developers.cloudflare.com/billing/troubleshoot-invoices/index.md
---
## Change in billing contact information
If your billing contact information has changed, [update your Cloudflare email address](https://developers.cloudflare.com/billing/update-billing-info/#update-billing-email-address) as soon as possible.
## Change in Cloudflare subscription or account
The invoice data corresponds to the date your Cloudflare account changed. You are charged immediately for the plan, additional domain, or add-on service. An invoice will be available on the Cloudflare dashboard within 24 hours of the account change.
Billing periods are 30 days. Payments for all recurring monthly costs are processed on the last day of the billing period. Invoices are generated the same day and will appear in the **Billing** section of the [Cloudflare dashboard](https://dash.cloudflare.com) within 24 hours.
## Cloudflare invoice without company name
To add your business or company name, VAT ID, or Tax ID/EIN on an invoice, add the company name when [updating billing information](https://developers.cloudflare.com/billing/update-billing-info/).
## Inconsistent invoice and payment amounts
If your Cloudflare payment is past due and you order additional services, the past due amount will be added to your invoice. This may cause inconsistencies between the invoice and what you see in the [Cloudflare dashboard](https://dash.cloudflare.com). Once the account is current, the amounts in the Cloudflare dashboard will update.
Note
You may have to wait up to one billing period for updates to appear in your Cloudflare invoice.
---
title: Update billing information · Cloudflare Billing docs
description: To avoid potential disruptions in your Cloudflare services, make
sure your billing information is current and accurate.
lastUpdated: 2025-09-03T18:47:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/update-billing-info/
md: https://developers.cloudflare.com/billing/update-billing-info/index.md
---
To avoid potential disruptions in your Cloudflare services, make sure your billing information is current and accurate.
If Cloudflare is unable to process your payment, review [Troubleshooting failed payments](https://developers.cloudflare.com/billing/troubleshoot-failed-payments/).
## Update payment methods
Note
You may receive the error message "Your account is limited to 2 payment methods, and you've reached that limit. Please remove an existing payment method before adding a new one." when trying to add additional methods.
If you are unable to add or edit a payment method, [delete a payment method](https://developers.cloudflare.com/billing/update-billing-info/#delete-a-payment-method) and try again.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Payment**.
3. Select **Manage** next to your current payment method. The **Manage payment methods** dialog opens.
4. Select **Edit** next to the payment method you would like to edit.
5. Enter the required information and select **Save Payment Information**.
## Delete a payment method
Before removing your payment method from file, you must cancel all Cloudflare paid services.
Warning
If you currently subscribe to any [add-on services](https://developers.cloudflare.com/billing/usage-based-billing/), Cloudflare must always have a payment method on file. If you need to remove a payment method, you must enter a new one to replace it.
You cannot delete a payment method if a payment fails or if there is an outstanding balance. Until Cloudflare processes payment, you can only add or edit your payment method.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Select **Payment**.
3. From **Payment methods**, select **Manage**.
4. Next to your current payment method, select **Delete**.
5. Select **Confirm** to finish.
## Update your billing address
The billing address is associated with your payment method and is used to calculate your sales tax. If you need to update your billing address, you must also enter your payment method. The process for updating your billing address depends on the payment method.
If paying by credit card:
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. From **Billing Address**, select **Edit** and enter your information.
3. Review the suggested address in the pop-up window. If the information is correct, select **Confirm**.
If paying by PayPal, refer to PayPal's [billing address documentation](https://www.paypal.com/ai/smarthelp/article/how-do-i-edit-the-billing-address-linked-to-my-credit-card-faq680).
## Update billing email address
Your billing email address is particularly important if you have [opted into email invoices](https://developers.cloudflare.com/billing/invoices/#enable-email-invoices-from-cloudflare).
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Go to **Invoices and documents**.
3. From **Billing email preference**, select **Change email address**.
4. Enter and confirm your new email address, then select **Save**.
## Add or change a Tax ID, VAT, or GST number
If you added a payment method but did not include a Tax ID, VAT or GST number, you can add or change the Tax ID, VAT or GST number associated with the payment method afterwards.
Note
You cannot apply a VAT or GST number to past invoices. Adding a VAT or GST number will only apply to future invoices issued in the account.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Go to **Payment**.
3. From **Billing Address**, select **Edit**.
4. In the **VAT/GST** field, enter your VAT or GST number.
5. Select **Confirm**.
## Remove a Tax ID, VAT, or GST number
Note
You cannot remove a VAT or GST number from past invoices. Removing a VAT or GST number will only apply to future invoices issued in the account.
1. In the Cloudflare dashboard, go to the **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Go to **Payment**.
3. From **Billing Address**, select **Edit**.
4. In the **VAT/GST** field, delete the VAT or GST number.
5. Select **Confirm**.
---
title: Usage based billing · Cloudflare Billing docs
description: For some Cloudflare subscriptions and services, you will be charged
based on how much a feature was used during your previous billing period. This
differs from other services, which are a prepaid flat fee for the upcoming
month (e.g. plans, page rules, etc.).
lastUpdated: 2025-06-16T14:59:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/billing/usage-based-billing/
md: https://developers.cloudflare.com/billing/usage-based-billing/index.md
---
For some Cloudflare subscriptions and services, you will be charged based on how much a feature was used during your previous billing period. This differs from other services, which are a prepaid flat fee for the upcoming month (e.g. plans, page rules, etc.).
For example, if your billing date is March 15 and you enabled Cloudflare Workers in the dashboard on March 1, your March 15 invoice will include the Workers charges from March 1-15. The next invoice on April 15 will include charges for Workers usage between March 16 and April 15.
Note
The pricing structure varies based on the service being used.
## Usage-Based billing notifications
For customers on Professional plans or higher, you can monitor the usage of Cloudflare add-ons by enabling email notifications. When enabled, you will receive a notification to the billing email address on file when the traffic, queries, requests, or minutes-watched exceed your desired threshold.
Note
The email notifications are for informational purposes only. Actual usage and billing may vary. Your monthly invoice is the most reliable source for billing information.
You can choose both the product that you want to be notified about, and the threshold that triggers the notification. Thresholds depend on the product chosen.
For example, Argo Smart Routing has **Notify when total bytes of traffic exceeds** as a threshold, and Load Balancing has **Notify when total number of DNS Queries exceeds** as a threshold.
To set up an alert, refer to [Configure Cloudflare notifications](https://developers.cloudflare.com/notifications/get-started/).
---
title: 404 - Page Not Found · Cloudflare bot solutions docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/bots/404/
md: https://developers.cloudflare.com/bots/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Additional Bots configurations · Cloudflare bot solutions docs
description: "Refer to the following pages for more information on additional
bot management configurations:"
lastUpdated: 2025-09-23T18:13:26.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/bots/additional-configurations/
md: https://developers.cloudflare.com/bots/additional-configurations/index.md
---
Refer to the following pages for more information on additional bot management configurations:
* [JA3/JA4 fingerprint](https://developers.cloudflare.com/bots/additional-configurations/ja3-ja4-fingerprint/)
* [Detection IDs](https://developers.cloudflare.com/bots/additional-configurations/detection-ids/)
* [JavaScript detections](https://developers.cloudflare.com/cloudflare-challenges/challenge-types/javascript-detections/)
* [Sequence rules](https://developers.cloudflare.com/bots/additional-configurations/sequence-rules/)
* [AI Labyrinth](https://developers.cloudflare.com/bots/additional-configurations/ai-labyrinth/)
* [Block AI Bots](https://developers.cloudflare.com/bots/additional-configurations/block-ai-bots/)
* [robots.txt setting](https://developers.cloudflare.com/bots/additional-configurations/managed-robots-txt/)
* [Static resource protection](https://developers.cloudflare.com/bots/additional-configurations/static-resources/)
---
title: Cloudflare Bot Analytics · Cloudflare bot solutions docs
description: Business and Enterprise customers without Bot Management can use
Bot Analytics to dynamically examine bot traffic. These dashboards offer less
functionality than Bot Management for Enterprise but still help you understand
bot traffic on your domain.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/bots/bot-analytics/
md: https://developers.cloudflare.com/bots/bot-analytics/index.md
---
## Business and Enterprise
Business and Enterprise customers without Bot Management can use **Bot Analytics** to dynamically examine bot traffic. These dashboards offer less functionality than Bot Management for Enterprise but still help you understand bot traffic on your domain.
### Access
You can access Bot Analytics by going to the [Cloudflare dashboard](https://dash.cloudflare.com/login), and selecting your account and domain.
Old dashboard: **Security** > **Bots**.
New dashboard: **Security** > **Analytics** > **Bot analysis**.

### Features
For a full tour of Bot Analytics, see [our blog post](https://blog.cloudflare.com/introducing-bot-analytics/). At a high level, the tool includes:
* **Requests by traffic type**: View your total domain traffic segmented vertically by traffic type. Keep an eye on *automated* and *likely automated* traffic.
* **Requests by detection source**: Identify the most common detection engines used to score your traffic. Hover over a tooltip to learn more about each engine.
* **Top requests by attribute**: View more detailed information on specific IP addresses and other characteristics.
Bot Analytics shows up to 72 hours of data at a time and can display data up to 30 days old. Bot Analytics displays data in real time in most cases.
Cloudflare uses adaptive bitrate technology to show sampled data — most customers will see a 1-10% sample depending on how much information they are trying to view. Tooltips on the page will display the current sample rate.
### Common uses
Business and Enterprise customers without Bot Management can use Bot Analytics to:
* Understand bot traffic
* Study recent attacks to find trends and detailed information
* Learn more about Cloudflare’s detection engines with real data
For more details and granular control over bot traffic, consider upgrading to [Bot Management for Enterprise](https://developers.cloudflare.com/bots/bot-analytics/#enterprise-bot-management).
## Enterprise Bot Management
Enterprise customers with Bot Management can use **Bot Analytics** to dynamically examine bot traffic.
### Access
You can access Bot Analytics by going to the [Cloudflare dashboard](https://dash.cloudflare.com/login), and selecting your account and domain.
Old dashboard: **Security** > **Bots**.
New dashboard: **Security** > **Analytics** > **Bot analysis**.

### Features
For a full tour of Bot Analytics, see [our blog post](https://blog.cloudflare.com/introducing-bot-analytics/). At a high level, the tool includes:
* **Requests by bot score**: View your total domain traffic and segment it vertically by traffic type. Keep an eye on *automated* and *likely automated* traffic.
* **Bot score distribution**: View the number of requests assigned a bot score 1 through 99.
* **Bot score source**: Identify the most common detection engines used to score your traffic. Hover over a tooltip to learn more about each engine.
* **Top requests by attribute**: View more detailed information on specific IP addresses and other characteristics.
Bot Analytics shows up to one week of data at a time and can display data up to 30 days old. Bot Analytics displays data in real time in most cases.
Cloudflare uses adaptive bitrate technology to show sampled data — most customers will see a 1-10% sample depending on how much information they are trying to view. Tooltips on the page will display the current sample rate.
### Common uses
Bot Management customers can use Bot Analytics to:
* Understand traffic during [your onboarding phase](https://developers.cloudflare.com/bots/get-started/bot-management/).
* Tune WAF custom rules to be effective but not overly aggressive.
* Study recent attacks to find trends and detailed information.
* Learn more about Cloudflare’s detection engines with real data.
### API
Data from Bot Analytics is also available via the GraphQL API. You can access bot scores, bot sources, [bot tags](https://developers.cloudflare.com/bots/concepts/bot-tags/), and bot *decisions* (*automated*, *likely automated*, etc.), and more.
Read the [GraphQL Analytics API documentation](https://developers.cloudflare.com/analytics/graphql-api/) for more information about GraphQL and basic querying.
---
title: Changelog · Cloudflare bot solutions docs
description: Subscribe to RSS
lastUpdated: 2025-10-15T15:50:02.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/bots/changelog/
md: https://developers.cloudflare.com/bots/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/bots/changelog/index.xml)
## 2025-07-02
**Managed robots.txt will prepend existing files**
Cloudflare will prepend our managed `robots.txt` before your existing `robots.txt`, combining both into a single response.
## 2025-06-26
**Web Bot Auth is now available for bot verification**
Web Bot Auth is an authentication method that leverages cryptographic signatures in HTTP messages to verify that a request comes from an automated bot. This provides a more robust way of verifying bots.
## 2025-05-14
**Anomaly detection events now receive a bot score of 2**
Events detected by the [anomaly detection engine](https://developers.cloudflare.com/bots/concepts/bot-detection-engines/#anomaly-detection-enterprise) are now given a bot score of 2.
## 2025-05-08
**Machine Learning model v9 is now the default model**
[Machine Learning model v9](https://developers.cloudflare.com/bots/reference/machine-learning-models/#model-versions-and-release-notes) is now the default model for all new zones and existing zones set to use the latest machine learning model.
## 2025-04-28
**Managed robots.txt is now available**
Direct AI crawlers on what they can and cannot scrape from your website or application by [implementing a `robots.txt` file](https://developers.cloudflare.com/bots/additional-configurations/managed-robots-txt/) to your domain.
## 2025-04-24
**Bot Detection Alerts are now available**
You can now create a [Bot Detection Alert](https://developers.cloudflare.com/bots/reference/alerts/) to notify you when Cloudflare detects a spike in Bot traffic on your website.
## 2024-08-19
**AI bots is now a managed rule**
[AI bots protection](https://developers.cloudflare.com/bots/concepts/bot/#ai-bots) has been upgraded from a custom rule to a managed rule.
---
title: Concepts · Cloudflare bot solutions docs
description: "Refer to the following pages for more information on bot concepts:"
lastUpdated: 2025-06-03T17:37:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/bots/concepts/
md: https://developers.cloudflare.com/bots/concepts/index.md
---
Refer to the following pages for more information on bot concepts:
* [Bots](https://developers.cloudflare.com/bots/concepts/bot/)
* [Bot scores](https://developers.cloudflare.com/bots/concepts/bot-score/)
* [Bot tags](https://developers.cloudflare.com/bots/concepts/bot-tags/)
* [Bot Feedback Loop](https://developers.cloudflare.com/bots/concepts/feedback-loop/)
* [Bot detection engines](https://developers.cloudflare.com/bots/concepts/bot-detection-engines/)
---
title: Get started with Cloudflare bot solutions · Cloudflare bot solutions docs
description: "Refer to the following pages to get started with Cloudflare's bot
solutions based on your plan type:"
lastUpdated: 2025-06-03T17:37:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/bots/get-started/
md: https://developers.cloudflare.com/bots/get-started/index.md
---
Refer to the following pages to get started with Cloudflare's bot solutions based on your plan type:
* [Bot Fight Mode](https://developers.cloudflare.com/bots/get-started/bot-fight-mode/)
* [Super Bot Fight Mode](https://developers.cloudflare.com/bots/get-started/super-bot-fight-mode/)
* [Bot Management](https://developers.cloudflare.com/bots/get-started/bot-management/)
---
title: Glossary · Cloudflare bot solutions docs
description: Review the definitions for terms used across Cloudflare's Bots documentation.
lastUpdated: 2025-10-15T15:50:02.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/bots/glossary/
md: https://developers.cloudflare.com/bots/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Bots documentation.
| Term | Definition |
| - | - |
| bot | A software application programmed to do tasks that can be used for good (chatbots, search engine crawlers) or for evil (inventory hoarding, credential stuffing). |
| bot score | A score from 1 to 99 that indicates how likely that request came from a bot, in which 1 to 29 is likely automated and 30 to 99 is likely human. |
| bot tags | Additional information about a bot request, such as why Cloudflare has given it a bot score and whether the request came from a verified bot or a category of verified bots. |
| Challenge solve rate (CSR) | The percentage of issued challenges that were solved. |
| detection ID | Static rules that are used to detect predictable bot behavior with no overlap with human traffic. |
| JA3 fingerprint | JA3 and JA4 fingerprints profile specific SSL/TLS clients across different destination IPs, Ports, and X509 certificates. |
| verified bot | Bots that are transparent about who they are and what they do. |
---
title: Cloudflare bot plans · Cloudflare bot solutions docs
description: To learn more about features and functionality, select a plan.
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/bots/plans/
md: https://developers.cloudflare.com/bots/plans/index.md
---
To learn more about features and functionality, select a plan.
[Free](https://developers.cloudflare.com/bots/plans/free/)
[Pro](https://developers.cloudflare.com/bots/plans/pro/)
[Business](https://developers.cloudflare.com/bots/plans/biz-and-ent/)
[Bot Management for Enterprise](https://developers.cloudflare.com/bots/plans/bm-subscription/)
## How do I get started?
To get started, review our [setup guides](https://developers.cloudflare.com/bots/get-started/). If you have any questions, visit the [community](https://community.cloudflare.com/) to engage with other Cloudflare users.
---
title: Reference · Cloudflare bot solutions docs
description: "Refer to the following pages for more information on Cloudflare's
bot solutions:"
lastUpdated: 2025-06-03T17:37:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/bots/reference/
md: https://developers.cloudflare.com/bots/reference/index.md
---
Refer to the following pages for more information on Cloudflare's bot solutions:
* [Bot verification methods](https://developers.cloudflare.com/bots/reference/bot-verification/)
* [Bot Management variables](https://developers.cloudflare.com/bots/reference/bot-management-variables/)
* [Machine Learning models](https://developers.cloudflare.com/bots/reference/machine-learning-models/)
* [Bot Detection Alerts](https://developers.cloudflare.com/bots/reference/alerts/)
* [Sample terms](https://developers.cloudflare.com/bots/reference/sample-terms/)
---
title: Troubleshoot issues with Bots · Cloudflare bot solutions docs
description: "Refer to the following pages to troubleshoot issues with
Cloudflare's bot solutions:"
lastUpdated: 2025-06-03T17:37:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/bots/troubleshooting/
md: https://developers.cloudflare.com/bots/troubleshooting/index.md
---
Refer to the following pages to troubleshoot issues with Cloudflare's bot solutions:
* [Bot Management skips](https://developers.cloudflare.com/bots/troubleshooting/bot-management-skips/)
* [Super Bot Fight Mode for WordPress](https://developers.cloudflare.com/bots/troubleshooting/wordpress-loopback-issue/)
* [Handle False Positives from Bot Fight Mode or Super Bot Fight Mode](https://developers.cloudflare.com/bots/troubleshooting/false-positives/)
---
title: Workers templates · Cloudflare bot solutions docs
description: "Refer to the templates below to integrate Bot Management with
Cloudflare Workers:"
lastUpdated: 2025-06-03T17:37:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/bots/workers-templates/
md: https://developers.cloudflare.com/bots/workers-templates/index.md
---
Refer to the templates below to integrate Bot Management with [Cloudflare Workers](https://developers.cloudflare.com/workers/):
* [Delay action](https://developers.cloudflare.com/bots/workers-templates/delay-action/)
---
title: 404 - Page Not Found · Cloudflare Browser Rendering docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/404/
md: https://developers.cloudflare.com/browser-rendering/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Changelog · Cloudflare Browser Rendering docs
description: Review recent changes to Worker Browser Rendering.
lastUpdated: 2025-11-06T19:11:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/changelog/
md: https://developers.cloudflare.com/browser-rendering/changelog/index.md
---
This is a detailed changelog of every update to Browser Rendering. For a higher-level summary of major updates to every Cloudflare product, including Browser Rendering, visit [developers.cloudflare.com/changelog](https://developers.cloudflare.com/changelog/).
[Subscribe to RSS](https://developers.cloudflare.com/browser-rendering/changelog/index.xml)
## 2026-02-03
**@cloudflare/puppeteer v1.0.6 released**
* Released version 1.0.6 of [`@cloudflare/puppeteer`](https://github.com/cloudflare/puppeteer/releases/tag/v1.0.6), which includes a fix for rendering large text PDFs.
## 2026-01-21
**@cloudflare/puppeteer v1.0.5 released**
* Released version 1.0.5 of [`@cloudflare/puppeteer`](https://www.npmjs.com/package/@cloudflare/puppeteer/v/1.0.5), which includes a performance optimization for base64 decoding.
## 2026-01-08
**@cloudflare/playwright v1.1.0 released**
* Released version 1.1.0 of [`@cloudflare/playwright`](https://github.com/cloudflare/playwright), now upgraded to [Playwright v1.57.0](https://playwright.dev/docs/release-notes#version-157).
## 2026-01-07
**Bug fixes for JSON endpoint, waitForSelector timeout, and WebSocket rendering**
* Updated the [`/json` endpoint](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/) fallback model and improved error handling for when plan limits of Workers Free plan users are reached.
* REST API requests using `waitForSelector` will now correctly fail if the specified selector is not found within the time limit.
* Fixed an issue where pages using WebSockets were not rendering correctly.
## 2025-12-04
**Added guidance on allowlisting Browser Rendering in Bot Management**
* Added [FAQ guidance](https://developers.cloudflare.com/browser-rendering/faq/#how-do-i-allowlist-browser-rendering) on how to create a WAF skip rule to allowlist Browser Rendering requests when using Bot Management on your zone.
## 2025-12-03
**Improved AI JSON response parsing and debugging**
* Added `rawAiResponse` field to [`/json` endpoint](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/) error responses, allowing you to inspect the unparsed AI output when JSON parsing fails for easier debugging.
* Improved AI response handling to better distinguish between valid JSON objects, arrays, and invalid payloads, increasing type safety and reliability.
## 2025-10-21
**Added guidance on REST API timeouts and custom fonts**
* Added [REST API timeouts](https://developers.cloudflare.com/browser-rendering/reference/timeouts/) page explaining how Browser Rendering uses independent timers (for page load, selectors, and actions) and how to configure them.
* Updated [Supported fonts](https://developers.cloudflare.com/browser-rendering/reference/supported-fonts/) guide with instructions on using your own custom fonts via `addStyleTag()` in [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) or [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/).
## 2025-09-25
**Updates to Playwright, new support for Stagehand, and increased limits**
* [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) support in Browser Rendering is now GA. We've upgraded to [Playwright v1.55](https://playwright.dev/docs/release-notes#version-155).
* Added support for [Stagehand](https://developers.cloudflare.com/browser-rendering/stagehand/), an open source browser automation framework, powered by [Workers AI](https://developers.cloudflare.com/workers-ai). Stagehand enables developers to build more reliably and flexibly by combining code with natural-language instructions.
* Increased [limits](https://developers.cloudflare.com/browser-rendering/limits/#workers-paid) for paid plans on both the [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) and [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/).
## 2025-09-22
**Added \`excludeExternalLinks\` parameter to \`/links\` REST endpoint**
* Added `excludeExternalLinks` parameter when using the [`/links` endpoint](https://developers.cloudflare.com/browser-rendering/rest-api/links-endpoint/). When set to `true`, links pointing to outside the domain of the requested URL are excluded.
## 2025-09-02
**Added \`X-Browser-Ms-Used\` response header**
* Each REST API response now includes the `X-Browser-Ms-Used` response header, which reports the browser time (in milliseconds) used by the request.
## 2025-08-20
**Browser Rendering billing goes live**
* Billing for Browser Rendering begins today, August 20th, 2025. See [pricing page](https://developers.cloudflare.com/browser-rendering/pricing/) for full details. You can monitor usage via the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/workers/browser-rendering).
## 2025-08-18
**Wrangler updates to local dev**
* Improved the local development experience by updating the method for downloading the dev mode browser and added support for [`/v1/sessions` endpoint](https://developers.cloudflare.com/platform/puppeteer/#list-open-sessions), allowing you to list open browser rendering sessions. Upgrade to `wrangler@4.31.0` to get started.
## 2025-07-29
**Updates to Playwright, local dev support, and REST API**
* [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) upgraded to [Playwright v1.54.1](https://github.com/microsoft/playwright/releases/tag/v1.54.1) and [Playwright MCP](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/) upgraded to be in sync with upstream Playwright MCP v0.0.30.
* Local development with `npx wrangler dev` now supports [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) when using Browser Rendering. Upgrade to the latest version of wrangler to get started.
* The [`/content` endpoint](https://developers.cloudflare.com/browser-rendering/rest-api/content-endpoint/) now returns the page's title, making it easier to identify pages.
* The [`/json` endpoint](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/) now allows you to specify your own AI model for the extraction, using the `custom_ai` parameter.
* The default viewport size on the [`/screenshot` endpoint](https://developers.cloudflare.com/browser-rendering/rest-api/screenshot-endpoint/) has been increased from 800x600 to 1920x1080. You can still override the viewport via request options.
## 2025-07-25
**@cloudflare/puppeteer 1.0.4 released**
* We have released version 1.0.4 of [`@cloudflare/puppeteer`](https://github.com/cloudflare/puppeteer), now in sync with Puppeteer v22.13.1.
## 2025-07-24
**Playwright now supported in local development**
* You can now use Playwright with local development. Upgrade to to get started.
## 2025-07-16
**Pricing update to Browser Rendering**
* Billing for Browser Rendering starts on August 20, 2025, with usage beyond the included [limits](https://developers.cloudflare.com/browser-rendering/limits/) charged according to the new [pricing rates](https://developers.cloudflare.com/browser-rendering/pricing/).
## 2025-07-03
**Local development support**
* We added local development support to Browser Rendering, making it simpler than ever to test and iterate before deploying.
## 2025-06-30
**New Web Bot Auth headers**
* Browser Rendering now supports [Web Bot Auth](https://developers.cloudflare.com/reference/automatic-request-headers/) by automatically attaching `Signature-agent`, `Signature`, and `Signature-input `headers to verify that a request originates from Cloudflare Browser Rendering.
## 2025-06-27
**Bug fix to debug log noise in Workers**
* Fixed an issue where all debug logging was on by default and would flood logs. Debug logs is now off by default but can be re-enabled by setting [`process.env.DEBUG`](https://pptr.dev/guides/debugging#log-devtools-protocol-traffic) when needed.
## 2025-05-26
**Playwright MCP**
* You can now deploy [Playwright MCP](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/) and use any MCP client to get AI models to interact with Browser Rendering.
## 2025-04-30
**Automatic Request Headers**
* [Clarified Automatic Request headers](https://developers.cloudflare.com/browser-rendering/reference/automatic-request-headers/) in Browser Rendering. These headers are unique to Browser Rendering, and are automatically included and cannot be removed or overridden.
## 2025-04-07
**New free tier and REST API GA with additional endpoints**
* Browser Rendering now has a new free tier.
* The [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) is Generally Available.
* Released new endpoints [`/json`](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/), [`/links`](https://developers.cloudflare.com/browser-rendering/rest-api/links-endpoint/), and [`/markdown`](https://developers.cloudflare.com/browser-rendering/rest-api/markdown-endpoint/).
## 2025-04-04
**Playwright support**
* You can now use [Playwright's](https://developers.cloudflare.com/browser-rendering/playwright/) browser automation capabilities from Cloudflare Workers.
## 2025-02-27
**New Browser Rendering REST API**
* Released a new [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) in open beta. Available to all customers with a Workers Paid Plan.
## 2025-01-31
**Increased limits**
* Increased the limits on the number of concurrent browsers, and browsers per minute from 2 to 10.
## 2024-08-08
**Update puppeteer to 21.1.0**
* Rebased the fork on the original implementation up till version 21.1.0
## 2024-04-02
**Browser Rendering Available for everyone**
* Browser Rendering is now out of beta and available to all customers with Workers Paid Plan. Analytics and logs are available in Cloudflare's dashboard, under "Worker & Pages".
## 2023-05-19
**Browser Rendering Beta**
* Beta Launch
---
title: Examples · Cloudflare Browser Rendering docs
description: Use these REST API examples to perform quick, common tasks.
lastUpdated: 2026-01-22T00:58:28.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/examples/
md: https://developers.cloudflare.com/browser-rendering/examples/index.md
---
## REST API examples
Use these [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) examples to perform quick, common tasks.
[Fetch rendered HTML from a URL ](https://developers.cloudflare.com/browser-rendering/rest-api/content-endpoint/#fetch-rendered-html-from-a-url)Capture fully rendered HTML from a webpage after JavaScript execution.
[Take a screenshot of the visible viewport ](https://developers.cloudflare.com/browser-rendering/rest-api/screenshot-endpoint/#basic-usage)Capture a screenshot of a fully rendered webpage from a URL or custom HTML.
[Take a screenshot of the full page ](https://developers.cloudflare.com/browser-rendering/rest-api/screenshot-endpoint/#navigate-and-capture-a-full-page-screenshot)Capture a screenshot of an entire scrollable webpage, not just the visible viewport.
[Take a screenshot of an authenticated page ](https://developers.cloudflare.com/browser-rendering/rest-api/screenshot-endpoint/#capture-a-screenshot-of-an-authenticated-page)Capture a screenshot of a webpage that requires login by providing session cookies.
[Generate a PDF ](https://developers.cloudflare.com/browser-rendering/rest-api/pdf-endpoint/#basic-usage)Generate a PDF from a URL or custom HTML and CSS.
[Extract Markdown from a URL ](https://developers.cloudflare.com/browser-rendering/rest-api/markdown-endpoint/#convert-a-url-to-markdown)Convert a webpage's content into Markdown format.
[Capture a snapshot from a URL ](https://developers.cloudflare.com/browser-rendering/rest-api/snapshot/#capture-a-snapshot-from-a-url)Capture both the rendered HTML and a screenshot from a webpage in a single request.
[Scrape headings and links from a URL ](https://developers.cloudflare.com/browser-rendering/rest-api/scrape-endpoint/#extract-headings-and-links-from-a-url)Extract structured data from specific elements on a webpage using CSS selectors.
[Capture structured data with an AI prompt and JSON schema ](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/#with-a-prompt-and-json-schema)Extract structured data from a webpage using AI using a prompt or JSON schema.
[Retrieve links from a URL ](https://developers.cloudflare.com/browser-rendering/rest-api/links-endpoint/#get-all-links-on-a-page)Retrieve all links from a webpage, including hidden ones.
## Workers Bindings examples
Use [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/) for dynamic, multi-step browser automation with [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/), [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/), or [Stagehand](https://developers.cloudflare.com/browser-rendering/stagehand/).
[Get page metrics with Puppeteer ](https://developers.cloudflare.com/browser-rendering/puppeteer/#use-puppeteer-in-a-worker)Use Puppeteer to navigate to a page and retrieve performance metrics in a Worker.
[Take a screenshot with Playwright ](https://developers.cloudflare.com/browser-rendering/playwright/#take-a-screenshot)Use Playwright to navigate to a page, interact with elements, and capture a screenshot.
[Run test assertions with Playwright ](https://developers.cloudflare.com/browser-rendering/playwright/#assertions)Use Playwright assertions to test web applications in a Worker.
[Generate a trace with Playwright ](https://developers.cloudflare.com/browser-rendering/playwright/#trace)Capture detailed execution logs for debugging with Playwright tracing.
[Reuse browser sessions ](https://developers.cloudflare.com/browser-rendering/workers-bindings/reuse-sessions/)Improve performance by reusing browser sessions across requests.
[Persist sessions with Durable Objects ](https://developers.cloudflare.com/browser-rendering/workers-bindings/browser-rendering-with-do/)Use Durable Objects to maintain long-running browser sessions.
[AI-powered browser automation with Stagehand ](https://developers.cloudflare.com/browser-rendering/stagehand/#use-stagehand-in-a-worker-with-workers-ai)Use natural language instructions to automate browser tasks with AI.
---
title: Frequently asked questions about Cloudflare Browser Rendering ·
Cloudflare Browser Rendering docs
description: Below you will find answers to our most commonly asked questions
about Browser Rendering.
lastUpdated: 2026-02-03T18:59:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/faq/
md: https://developers.cloudflare.com/browser-rendering/faq/index.md
---
Below you will find answers to our most commonly asked questions about Browser Rendering.
For pricing questions, visit the [pricing FAQ](https://developers.cloudflare.com/browser-rendering/pricing/#faq). For usage limits questions, visit the [limits FAQ](https://developers.cloudflare.com/browser-rendering/limits/#faq). If you cannot find the answer you are looking for, join us on [Discord](https://discord.cloudflare.com).
***
## Errors & Troubleshooting
### Error: Cannot read properties of undefined (reading 'fetch')
This error typically occurs because your Puppeteer launch is not receiving the browser binding. To resolve this error, pass your browser binding into `puppeteer.launch`.
### Error: 429 browser time limit exceeded
This error (`Unable to create new browser: code: 429: message: Browser time limit exceeded for today`) indicates you have hit the daily browser-instance limit on the Workers Free plan. [Workers Free plan accounts are capped at 10 minutes of browser use a day](https://developers.cloudflare.com/browser-rendering/limits/#workers-free). Once you exceed that limit, further creation attempts return a 429 error until the next UTC day.
To resolve this error, [upgrade to a Workers Paid plan](https://developers.cloudflare.com/workers/platform/pricing/) which allows for more than 10 minutes of usage a day and has higher [limits](https://developers.cloudflare.com/browser-rendering/limits/#workers-paid). If you recently upgraded but still see this error, try redeploying your Worker to ensure your usage is correctly associated with your new plan.
### Error: 422 unprocessable entity
A `422 Unprocessable Entity` error usually means that Browser Rendering wasn't able to complete an action because of an issue with the site.
This can happen if:
* The website consumes too much memory during rendering.
* The page itself crashed or returned an error before the action completed.
* The request exceeded one of the [timeout limits](https://developers.cloudflare.com/browser-rendering/reference/timeouts/) for page load, element load, or an action.
Most often, this error is caused by a timeout. You can review the different timers and their limits in the [REST API timeouts reference](https://developers.cloudflare.com/browser-rendering/reference/timeouts/).
### Why is my page content missing or incomplete?
If your screenshots, PDFs, or scraped content are missing elements that appear when viewing the page in a browser, the page likely has not finished loading before Browser Rendering captures the output.
JavaScript-heavy pages and Single Page Applications (SPAs) often load content dynamically after the initial HTML is parsed. By default, Browser Rendering waits for `domcontentloaded`, which fires before JavaScript has finished rendering the page.
To fix this, use the `goToOptions.waitUntil` parameter with one of these values:
| Value | Use when |
| - | - |
| `networkidle0` | The page must be completely idle (no network requests for 500 ms). Best for pages that load all content upfront. |
| `networkidle2` | The page can have up to 2 ongoing connections (like analytics or websockets). Best for most dynamic pages. |
REST API example:
```json
{
"url": "https://example.com",
"goToOptions": {
"waitUntil": "networkidle2"
}
}
```
If content is still missing:
* Use `waitForSelector` to wait for a specific element to appear before capturing.
* Increase `goToOptions.timeout` (up to 60 seconds) for slow-loading pages.
* Check if the page requires authentication or returns different content to bots.
For a complete reference, see [REST API timeouts](https://developers.cloudflare.com/browser-rendering/reference/timeouts/).
***
## Getting started & Development
### Does local development support all Browser Rendering features?
Not yet. Local development currently has the following limitation(s):
* Requests larger than 1 MB are not supported.
Use real headless browser during local development
To interact with a real headless browser during local development, set `"remote" : true` in the Browser binding configuration. Learn more in our [remote bindings documentation](https://developers.cloudflare.com/workers/development-testing/#remote-bindings).
### Will Browser Rendering be detected by Bot Management?
Yes, Browser Rendering requests are always identified as bot traffic by Cloudflare. Cloudflare does not enforce bot protection by default — that is the customer's choice.
If you are attempting to scan your own zone and want Browser Rendering to access your website freely without your bot protection configuration interfering, you can create a WAF skip rule to [allowlist Browser Rendering](https://developers.cloudflare.com/browser-rendering/faq/#how-do-i-allowlist-browser-rendering).
### Can I allowlist Browser Rendering on my own website?
You must be on an Enterprise plan to allowlist Browser Rendering on your own website because WAF custom rules require access to [Bot Management](https://developers.cloudflare.com/bots/get-started/bot-management/) fields.
1. In the Cloudflare dashboard, go to the **Security rules** page of your account and domain.
[Go to **Security rules**](https://dash.cloudflare.com/?to=/:account/:zone/security/security-rules)
2. To create a new empty rule, select **Create rule** > **Custom rules**.
3. Enter a descriptive name for the rule in **Rule name**, such as `Allow Browser Rendering`.
4. Under **When incoming requests match**, use the **Field** dropdown to choose *Bot Detection ID*. For **Operator**, select *equals*. For **Value**, enter `128292352`.
5. Under **Then take action**, in the **Choose action** dropdown, select **Skip**.
6. Under **Place at**, select the order of the rule in the **Select order** dropdown to be **First**. Setting the order as **First** allows this rule to be applied before subsequent rules.
7. To save and deploy your rule, select **Deploy**.
### Does Browser Rendering rotate IP addresses for outbound requests?
No. Browser Rendering requests originate from Cloudflare's global network and you cannot configure per-request IP rotation. All rendering traffic comes from Cloudflare IP ranges and requests include [automatic headers](https://developers.cloudflare.com/browser-rendering/reference/automatic-request-headers/), such as `cf-biso-request-id` and `cf-biso-devtools` so origin servers can identify them.
### Is there a limit to how many requests a single browser session can handle?
There is no fixed limit on the number of requests per browser session. A single browser can handle multiple requests as long as it stays within available compute and memory limits.
### Can I use custom fonts in Browser Rendering?
Yes. If your webpage or PDF requires a font that is not pre-installed, you can load custom fonts at render time using `addStyleTag`. This works with both the [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) and [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/). For instructions and examples, refer to [Use your own custom font](https://developers.cloudflare.com/browser-rendering/reference/supported-fonts/#use-your-own-custom-font).
### How can I manage concurrency and session isolation with Browser Rendering?
If you are hitting concurrency [limits](https://developers.cloudflare.com/browser-rendering/limits/#workers-paid), or want to optimize concurrent browser usage with the [Workers Binding method](https://developers.cloudflare.com/browser-rendering/workers-bindings/), here are a few tips:
* Optimize with tabs or shared browsers: Instead of launching a new browser for each task, consider opening multiple tabs or running multiple actions within the same browser instance.
* [Reuse sessions](https://developers.cloudflare.com/browser-rendering/workers-bindings/reuse-sessions/): You can optimize your setup and decrease startup time by reusing sessions instead of launching a new browser every time. If you are concerned about maintaining test isolation (for example, for tests that depend on a clean environment), we recommend using [incognito browser contexts](https://pptr.dev/api/puppeteer.browser.createbrowsercontext), which isolate cookies and cache with other sessions.
If you are still running into concurrency limits you can [request a higher limit](https://forms.gle/CdueDKvb26mTaepa9).
***
## Security & Data Handling
### Does Cloudflare store or retain the HTML content I submit for rendering?
No. Cloudflare processes content ephemerally and does not retain customer-submitted HTML or generated output (such as PDFs or screenshots) beyond what is required to perform the rendering operation. Once the response is returned, the content is immediately discarded from the rendering environment.
This applies to both the [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) and [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/) (using `@cloudflare/puppeteer` or `@cloudflare/playwright`).
### Is there any temporary caching of submitted content?
For the [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/), generated content is cached by default for five seconds (configurable up to one day via the `cacheTTL` parameter, or set to `0` to disable caching). This cache protects against repeated requests for the same URL by the same account. Customer-submitted HTML content itself is not cached.
For [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/), no caching is used. Content exists only in memory for the duration of the rendering operation and is discarded immediately after the response is returned.
---
title: Get started · Cloudflare Browser Rendering docs
description: Cloudflare Browser Rendering allows you to programmatically control
a headless browser, enabling you to do things like take screenshots, generate
PDFs, and perform automated browser tasks.
lastUpdated: 2025-11-06T19:11:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/get-started/
md: https://developers.cloudflare.com/browser-rendering/get-started/index.md
---
Cloudflare Browser Rendering allows you to programmatically control a headless browser, enabling you to do things like take screenshots, generate PDFs, and perform automated browser tasks.
There are two ways to use Browser Rendering:
* [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) for simple, one-off actions, like taking a screenshot, fetching HTML, or generating a PDF.
* [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/) for more complex, multi-step browser automation using [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/) and [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/).
This guide will help you choose the right path for your needs and get you started with your first Browser Rendering project.
## REST API
The REST API is best for situations where you have an existing application and want to perform simple, stateless browser actions.
### Prerequisites
* Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
* Create a [Cloudflare API Token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with `Browser Rendering - Edit` permissions.
### Example: Take a screenshot of the Cloudflare homepage
```bash
curl -X POST 'https://api.cloudflare.com/client/v4/accounts//browser-rendering/screenshot' \
-H 'Authorization: Bearer ' \
-H 'Content-Type: application/json' \
-d '{
"url": "https://example.com"
}' \
--output "screenshot.png"
```
The REST API can also be used to:
* [Fetch HTML](https://developers.cloudflare.com/browser-rendering/rest-api/content-endpoint/)
* [Generate a PDF](https://developers.cloudflare.com/browser-rendering/rest-api/pdf-endpoint/)
* [and more...](https://developers.cloudflare.com/browser-rendering/rest-api/)
## Workers Bindings
Workers Bindings are best for situations where you need to build more complex, multi-step browser automation workflows. You can use familiar tools like [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/) and [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/).
### Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
### Example: Navigate to a URL, take a screenshot, and store in KV
#### 1. Create a Worker project
[Cloudflare Workers](https://developers.cloudflare.com/workers/) provides a serverless execution environment that allows you to create new applications or augment existing ones without configuring or maintaining infrastructure. Your Worker application is a container to interact with a headless browser to do actions, such as taking screenshots.
Create a new Worker project named `browser-worker` by running:
* npm
```sh
npm create cloudflare@latest -- browser-worker
```
* yarn
```sh
yarn create cloudflare browser-worker
```
* pnpm
```sh
pnpm create cloudflare@latest browser-worker
```
For setup, select the following options:
* For *What would you like to start with?*, choose `Hello World example`.
* For *Which template would you like to use?*, choose `Worker only`.
* For *Which language do you want to use?*, choose `JavaScript / TypeScript`.
* For *Do you want to use git for version control?*, choose `Yes`.
* For *Do you want to deploy your application?*, choose `No` (we will be making some changes before deploying).
#### 2. Install Puppeteer
In your `browser-worker` directory, install Cloudflare’s [fork of Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/):
* npm
```sh
npm i -D @cloudflare/puppeteer
```
* yarn
```sh
yarn add -D @cloudflare/puppeteer
```
* pnpm
```sh
pnpm add -D @cloudflare/puppeteer
```
#### 3. Create a KV namespace
Browser Rendering can be used with other developer products. You might need a [relational database](https://developers.cloudflare.com/d1/), an [R2 bucket](https://developers.cloudflare.com/r2/) to archive your crawled pages and assets, a [Durable Object](https://developers.cloudflare.com/durable-objects/) to keep your browser instance alive and share it with multiple requests, or [Queues](https://developers.cloudflare.com/queues/) to handle your jobs asynchronously.
For the purpose of this example, we will use a [KV store](https://developers.cloudflare.com/kv/concepts/kv-namespaces/) to cache your screenshots.
Create two namespaces, one for production and one for development.
```sh
npx wrangler kv namespace create BROWSER_KV_DEMO
npx wrangler kv namespace create BROWSER_KV_DEMO --preview
```
Take note of the IDs for the next step.
#### 4. Configure the Wrangler configuration file
Configure your `browser-worker` project's [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/) by adding a browser [binding](https://developers.cloudflare.com/workers/runtime-apis/bindings/) and a [Node.js compatibility flag](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#nodejs-compatibility-flag). Bindings allow your Workers to interact with resources on the Cloudflare developer platform. Your browser `binding` name is set by you, this guide uses the name `MYBROWSER`. Browser bindings allow for communication between a Worker and a headless browser which allows you to do actions such as taking a screenshot, generating a PDF, and more.
Update your [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/) with the Browser Rendering API binding and the KV namespaces you created:
* wrangler.jsonc
```jsonc
{
"$schema": "./node_modules/wrangler/config-schema.json",
"name": "browser-worker",
"main": "src/index.js",
"compatibility_date": "2026-02-07",
"compatibility_flags": [
"nodejs_compat"
],
"browser": {
"binding": "MYBROWSER"
},
"kv_namespaces": [
{
"binding": "BROWSER_KV_DEMO",
"id": "22cf855786094a88a6906f8edac425cd",
"preview_id": "e1f8b68b68d24381b57071445f96e623"
}
]
}
```
* wrangler.toml
```toml
"$schema" = "./node_modules/wrangler/config-schema.json"
name = "browser-worker"
main = "src/index.js"
compatibility_date = "2026-02-07"
compatibility_flags = [ "nodejs_compat" ]
[browser]
binding = "MYBROWSER"
[[kv_namespaces]]
binding = "BROWSER_KV_DEMO"
id = "22cf855786094a88a6906f8edac425cd"
preview_id = "e1f8b68b68d24381b57071445f96e623"
```
#### 5. Code
* JavaScript
Update `src/index.js` with your Worker code:
```js
import puppeteer from "@cloudflare/puppeteer";
export default {
async fetch(request, env) {
const { searchParams } = new URL(request.url);
let url = searchParams.get("url");
let img;
if (url) {
url = new URL(url).toString(); // normalize
img = await env.BROWSER_KV_DEMO.get(url, { type: "arrayBuffer" });
if (img === null) {
const browser = await puppeteer.launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto(url);
img = await page.screenshot();
await env.BROWSER_KV_DEMO.put(url, img, {
expirationTtl: 60 * 60 * 24,
});
await browser.close();
}
return new Response(img, {
headers: {
"content-type": "image/jpeg",
},
});
} else {
return new Response("Please add an ?url=https://example.com/ parameter");
}
},
};
```
* TypeScript
Update `src/index.ts` with your Worker code:
```ts
import puppeteer from "@cloudflare/puppeteer";
interface Env {
MYBROWSER: Fetcher;
BROWSER_KV_DEMO: KVNamespace;
}
export default {
async fetch(request, env): Promise {
const { searchParams } = new URL(request.url);
let url = searchParams.get("url");
let img: Buffer;
if (url) {
url = new URL(url).toString(); // normalize
img = await env.BROWSER_KV_DEMO.get(url, { type: "arrayBuffer" });
if (img === null) {
const browser = await puppeteer.launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto(url);
img = (await page.screenshot()) as Buffer;
await env.BROWSER_KV_DEMO.put(url, img, {
expirationTtl: 60 * 60 * 24,
});
await browser.close();
}
return new Response(img, {
headers: {
"content-type": "image/jpeg",
},
});
} else {
return new Response("Please add an ?url=https://example.com/ parameter");
}
},
} satisfies ExportedHandler;
```
This Worker instantiates a browser using Puppeteer, opens a new page, navigates to the location of the 'url' parameter, takes a screenshot of the page, stores the screenshot in KV, closes the browser, and responds with the JPEG image of the screenshot.
If your Worker is running in production, it will store the screenshot to the production KV namespace. If you are running `wrangler dev`, it will store the screenshot to the dev KV namespace.
If the same `url` is requested again, it will use the cached version in KV instead, unless it expired.
#### 6. Test
Run `npx wrangler dev` to test your Worker locally.
Use real headless browser during local development
To interact with a real headless browser during local development, set `"remote" : true` in the Browser binding configuration. Learn more in our [remote bindings documentation](https://developers.cloudflare.com/workers/development-testing/#remote-bindings).
To test taking your first screenshot, go to the following URL:
`/?url=https://example.com`
#### 7. Deploy
Run `npx wrangler deploy` to deploy your Worker to the Cloudflare global network.
To take your first screenshot, go to the following URL:
`..workers.dev/?url=https://example.com`
## Next Steps
If you have any feature requests or notice any bugs, share your feedback directly with the Cloudflare team by joining the [Cloudflare Developers community on Discord](https://discord.cloudflare.com/).
* Check out all the [REST API endpoints](https://developers.cloudflare.com/browser-rendering/rest-api/)
* Try out the [Playwright MCP](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/)
* Learn more about Browser Rendering [limits](https://developers.cloudflare.com/browser-rendering/limits/) and [pricing](https://developers.cloudflare.com/browser-rendering/pricing/).
---
title: Tutorials · Cloudflare Browser Rendering docs
lastUpdated: 2025-11-06T19:11:47.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/browser-rendering/how-to/
md: https://developers.cloudflare.com/browser-rendering/how-to/index.md
---
* [Generate PDFs Using HTML and CSS](https://developers.cloudflare.com/browser-rendering/how-to/pdf-generation/)
* [Build a web crawler with Queues and Browser Rendering](https://developers.cloudflare.com/queues/tutorials/web-crawler-with-browser-rendering/)
* [Use browser rendering with AI](https://developers.cloudflare.com/browser-rendering/how-to/ai/)
---
title: Limits · Cloudflare Browser Rendering docs
description: Learn about the limits associated with Browser Rendering.
lastUpdated: 2026-01-29T17:42:12.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/limits/
md: https://developers.cloudflare.com/browser-rendering/limits/index.md
---
Available on Free and Paid plans
## Workers Free
Users on the [Workers Free plan](https://developers.cloudflare.com/workers/platform/pricing/) are limited to **10 minutes of Browser Rendering usage per day**.
To increase this limit, go to the **Compute (Workers) > Workers plans** page in the Cloudflare dashboard:
[Go to **Workers plans**](https://dash.cloudflare.com/?to=/:account/workers/plans)
[Learn more about Workers Plans](https://developers.cloudflare.com/workers/platform/pricing).
| Feature | Limit |
| - | - |
| Concurrent browsers per account (Workers Bindings only) | 3 per account |
| New browser instances per minute (Workers Bindings only) | 3 per minute |
| Browser timeout | 60 seconds [1](#user-content-fn-1) |
| Total requests per min (REST API only) | 6 per minute |
## Workers Paid
Need higher limits?
If you are on the Workers Free plan, [upgrade to Workers Paid](https://developers.cloudflare.com/workers/platform/pricing/) for higher limits. If you are already on Workers Paid and need limits beyond those listed below, Cloudflare will grant [requests for higher limits](https://forms.gle/CdueDKvb26mTaepa9) on a case-by-case basis.
| Feature | Limit |
| - | - |
| Concurrent browsers per account (Workers Bindings only) | 30 per account |
| New browser instances per minute (Workers Bindings only) | 30 per minute |
| Browser timeout | 60 seconds [1](#user-content-fn-1) |
| Total requests per min (REST API only) | 180 per minute |
About concurrent browsers
The Workers Paid plan includes 10 concurrent browsers at no additional cost. You can use up to 30 concurrent browsers per account, but usage beyond the included 10 browsers is billed at $2.00 per additional browser (averaged monthly).
For full pricing details and billing examples, refer to [Pricing](https://developers.cloudflare.com/browser-rendering/pricing/).
### Note on concurrency
While the limits above define the maximum number of concurrent browser sessions per account, in practice you may not need to hit these limits. Browser sessions close automatically—by default, after 60 seconds of inactivity or upon task completion—so if each session finishes its work before a new request comes in, the effective concurrency is lower. This means that most workflows do not require very high concurrent browser limits.
## Limits FAQ & troubleshooting
### How can I manage concurrency and session isolation with Browser Rendering?
If you are hitting concurrency [limits](https://developers.cloudflare.com/browser-rendering/limits/#workers-paid), or want to optimize concurrent browser usage with the [Workers Binding method](https://developers.cloudflare.com/browser-rendering/workers-bindings/), here are a few tips:
* Optimize with tabs or shared browsers: Instead of launching a new browser for each task, consider opening multiple tabs or running multiple actions within the same browser instance.
* [Reuse sessions](https://developers.cloudflare.com/browser-rendering/workers-bindings/reuse-sessions/): You can optimize your setup and decrease startup time by reusing sessions instead of launching a new browser every time. If you are concerned about maintaining test isolation (for example, for tests that depend on a clean environment), we recommend using [incognito browser contexts](https://pptr.dev/api/puppeteer.browser.createbrowsercontext), which isolate cookies and cache with other sessions.
If you are still running into concurrency limits you can [request a higher limit](https://forms.gle/CdueDKvb26mTaepa9).
### Can I increase the browser timeout?
By default, a browser instance will time out after 60 seconds of inactivity. If you want to keep the browser open longer, you can use the [`keep_alive` option](https://developers.cloudflare.com/browser-rendering/puppeteer/#keep-alive), which allows you to extend the timeout to up to 10 minutes.
### Is there a maximum session duration?
There is no fixed maximum lifetime for a browser session as long as it remains active. By default, Browser Rendering closes sessions after one minute of inactivity to prevent unintended usage. You can [increase this inactivity timeout](https://developers.cloudflare.com/browser-rendering/puppeteer/#keep-alive) to up to 10 minutes.
If you need sessions to remain open longer, keep them active by sending a command at least once within your configured inactivity window (for example, every 10 minutes). Sessions also close when Browser Rendering rolls out a new release.
### I upgraded from the Workers Free plan, but I'm still hitting the 10-minute per day limit. What should I do?
If you recently upgraded to the [Workers Paid plan](https://developers.cloudflare.com/workers/platform/pricing/) but still encounter the 10-minute per day limit, redeploy your Worker to ensure your usage is correctly associated with the new plan.
### Why is my browser usage higher than expected?
If you are hitting the daily limit or seeing higher usage than expected, the most common cause is browser sessions that are not being closed properly. When a browser session is not explicitly closed with `browser.close()`, it remains open and continues to consume browser time until it times out (60 seconds by default, or up to 10 minutes if you use the `keep_alive` option).
To minimize usage:
* Always call `browser.close()` when you are finished with a browser session.
* Wrap your browser code in a `try/finally` block to ensure `browser.close()` is called even if an error occurs.
* Use [`puppeteer.history()`](https://developers.cloudflare.com/browser-rendering/puppeteer/#list-recent-sessions) or [`playwright.history()`](https://developers.cloudflare.com/browser-rendering/playwright/#list-recent-sessions) to review recent sessions and identify any that closed due to `BrowserIdle` instead of `NormalClosure`. Sessions that close due to idle timeout indicate the browser was not closed explicitly.
You can monitor your usage and view session close reasons in the Cloudflare dashboard on the **Browser Rendering** page:
[Go to **Browser Rendering**](https://dash.cloudflare.com/?to=/:account/workers/browser-rendering)
Refer to [Browser close reasons](https://developers.cloudflare.com/browser-rendering/reference/browser-close-reasons/) for more information.
## Rate limits and errors
### Understanding rate limits
Rate limits are enforced with a fixed per-second fill rate, not as a burst allowance. This means you cannot send all your requests at once — the API expects them to be spread evenly over the minute.
| Plan | Rate limit | Per-second equivalent |
| - | - | - |
| Workers Free | 6 requests/min | 1 request every 10 seconds |
| Workers Paid | 180 requests/min | 3 requests/second |
If you exceed the rate limit, the API responds with HTTP status code `429 Too many requests` and includes a `Retry-After` header specifying how many seconds to wait before retrying.
### Error: `429 Too many requests`
When you make too many requests in a short period of time, Browser Rendering will respond with HTTP status code `429 Too many requests`. You can view your account's rate limits in the [Workers Free](#workers-free) and [Workers Paid](#workers-paid) sections above.
The example below demonstrates how to handle rate limiting gracefully by reading the `Retry-After` value and retrying the request after that delay.
* REST API
```js
const response = await fetch('https://api.cloudflare.com/client/v4/accounts//browser-rendering/content', {
method: 'POST',
headers: {
'Content-Type': 'application/json',
'Authorization': 'Bearer ',
},
body: JSON.stringify({ url: 'https://example.com' })
});
if (response.status === 429) {
const retryAfter = response.headers.get('Retry-After');
console.log(`Rate limited. Waiting ${retryAfter} seconds...`);
await new Promise(resolve => setTimeout(resolve, retryAfter \* 1000));
// Retry the request
const retryResponse = await fetch(/* same request as above */);
}
```
* Workers Bindings
```js
import puppeteer from "@cloudflare/puppeteer";
try {
const browser = await puppeteer.launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto("https://example.com");
const content = await page.content();
await browser.close();
} catch (error) {
if (error.status === 429) {
const retryAfter = error.headers.get("Retry-After");
console.log(
`Browser instance limit reached. Waiting ${retryAfter} seconds...`,
);
await new Promise((resolve) => setTimeout(resolve, retryAfter * 1000));
// Retry launching browser
const browser = await puppeteer.launch(env.MYBROWSER);
}
}
```
### Error: `429 Browser time limit exceeded for today`
This `Error processing the request: Unable to create new browser: code: 429: message: Browser time limit exceeded for today` error indicates you have hit the daily browser limit on the Workers Free plan. [Workers Free plan accounts are limited](#workers-free) to 10 minutes of Browser Rendering usage per day. If you exceed that limit, you will receive a `429` error until the next UTC day.
You can [increase your limits](#workers-paid) by upgrading to a Workers Paid plan on the **Workers plans** page of the Cloudflare dashboard:
[Go to **Workers plans**](https://dash.cloudflare.com/?to=/:account/workers/plans)
If you recently upgraded but still encounter the 10-minute per day limit, redeploy your Worker to ensure your usage is correctly associated with the new plan.
## Footnotes
1. By default, a browser will time out after 60 seconds of inactivity. You can extend this to up to 10 minutes using the [`keep_alive` option](https://developers.cloudflare.com/browser-rendering/puppeteer/#keep-alive). Call `browser.close()` to release the browser instance immediately. [↩](#user-content-fnref-1) [↩2](#user-content-fnref-1-2)
---
title: MCP server · Cloudflare Browser Rendering docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/mcp-server/
md: https://developers.cloudflare.com/browser-rendering/mcp-server/index.md
---
---
title: Playwright · Cloudflare Browser Rendering docs
description: Learn how to use Playwright with Cloudflare Workers for browser
automation. Access Playwright API, manage sessions, and optimize browser
rendering.
lastUpdated: 2026-02-02T18:38:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/playwright/
md: https://developers.cloudflare.com/browser-rendering/playwright/index.md
---
[Playwright](https://playwright.dev/) is an open-source package developed by Microsoft that can do browser automation tasks; it is commonly used to write frontend tests, create screenshots, or crawl pages.
The Workers team forked a [version of Playwright](https://github.com/cloudflare/playwright) that was modified to be compatible with [Cloudflare Workers](https://developers.cloudflare.com/workers/) and [Browser Rendering](https://developers.cloudflare.com/browser-rendering/).
Our version is open sourced and can be found in [Cloudflare's fork of Playwright](https://github.com/cloudflare/playwright). The npm package can be installed from [npmjs](https://www.npmjs.com/) as [@cloudflare/playwright](https://www.npmjs.com/package/@cloudflare/playwright):
* npm
```sh
npm i -D @cloudflare/playwright
```
* yarn
```sh
yarn add -D @cloudflare/playwright
```
* pnpm
```sh
pnpm add -D @cloudflare/playwright
```
Note
The current version is [`@cloudflare/playwright` v1.1.0](https://github.com/cloudflare/playwright/releases/tag/v1.1.0), based on [Playwright v1.57.0](https://playwright.dev/docs/release-notes#version-157).
## Use Playwright in a Worker
In this [example](https://github.com/cloudflare/playwright/tree/main/packages/playwright-cloudflare/examples/todomvc), you will run Playwright tests in a Cloudflare Worker using the [todomvc](https://demo.playwright.dev/todomvc) application.
If you want to skip the steps and get started quickly, select **Deploy to Cloudflare** below.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/playwright/tree/main/packages/playwright-cloudflare/examples/todomvc)
Make sure you have the [browser binding](https://developers.cloudflare.com/browser-rendering/reference/wrangler/#bindings) configured in your Wrangler configuration file:
Note
To use the latest version of `@cloudflare/playwright`, your Worker configuration must include the `nodejs_compat` compatibility flag and a `compatibility_date` of 2025-09-15 or later. This change is necessary because the library's functionality requires the native `node.fs` API.
* wrangler.jsonc
```jsonc
{
"$schema": "./node_modules/wrangler/config-schema.json",
"name": "cloudflare-playwright-example",
"main": "src/index.ts",
"workers_dev": true,
"compatibility_flags": [
"nodejs_compat"
],
"compatibility_date": "2026-02-07",
"upload_source_maps": true,
"browser": {
"binding": "MYBROWSER"
}
}
```
* wrangler.toml
```toml
"$schema" = "./node_modules/wrangler/config-schema.json"
name = "cloudflare-playwright-example"
main = "src/index.ts"
workers_dev = true
compatibility_flags = [ "nodejs_compat" ]
compatibility_date = "2026-02-07"
upload_source_maps = true
[browser]
binding = "MYBROWSER"
```
Install the npm package:
* npm
```sh
npm i -D @cloudflare/playwright
```
* yarn
```sh
yarn add -D @cloudflare/playwright
```
* pnpm
```sh
pnpm add -D @cloudflare/playwright
```
Let's look at some examples of how to use Playwright:
### Take a screenshot
Using browser automation to take screenshots of web pages is a common use case. This script tells the browser to navigate to , create some items, take a screenshot of the page, and return the image in the response.
```ts
import { launch } from "@cloudflare/playwright";
export default {
async fetch(request: Request, env: Env) {
const browser = await launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto("https://demo.playwright.dev/todomvc");
const TODO_ITEMS = [
"buy some cheese",
"feed the cat",
"book a doctors appointment",
];
const newTodo = page.getByPlaceholder("What needs to be done?");
for (const item of TODO_ITEMS) {
await newTodo.fill(item);
await newTodo.press("Enter");
}
const img = await page.screenshot();
await browser.close();
return new Response(img, {
headers: {
"Content-Type": "image/png",
},
});
},
};
```
### Trace
A Playwright trace is a detailed log of your workflow execution that captures information like user clicks and navigation actions, screenshots of the page, and any console messages generated and used for debugging. Developers can take a `trace.zip` file and either open it [locally](https://playwright.dev/docs/trace-viewer#opening-the-trace) or upload it to the [Playwright Trace Viewer](https://trace.playwright.dev/), a GUI tool that helps you explore the data.
Here's an example of a worker generating a trace file:
```ts
import fs from "fs";
import { launch } from "@cloudflare/playwright";
export default {
async fetch(request: Request, env: Env) {
const browser = await launch(env.MYBROWSER);
const page = await browser.newPage();
// Start tracing before navigating to the page
await page.context().tracing.start({ screenshots: true, snapshots: true });
await page.goto("https://demo.playwright.dev/todomvc");
const TODO_ITEMS = [
"buy some cheese",
"feed the cat",
"book a doctors appointment",
];
const newTodo = page.getByPlaceholder("What needs to be done?");
for (const item of TODO_ITEMS) {
await newTodo.fill(item);
await newTodo.press("Enter");
}
// Stop tracing and save the trace to a zip file
await page.context().tracing.stop({ path: "trace.zip" });
await browser.close();
const file = await fs.promises.readFile("trace.zip");
return new Response(file, {
status: 200,
headers: {
"Content-Type": "application/zip",
},
});
},
};
```
### Assertions
One of the most common use cases for using Playwright is software testing. Playwright includes test assertion features in its APIs; refer to [Assertions](https://playwright.dev/docs/test-assertions) in the Playwright documentation for details. Here's an example of a Worker doing `expect()` test assertions of the [todomvc](https://demo.playwright.dev/todomvc) demo page:
```ts
import { launch } from "@cloudflare/playwright";
import { expect } from "@cloudflare/playwright/test";
export default {
async fetch(request: Request, env: Env) {
const browser = await launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto("https://demo.playwright.dev/todomvc");
const TODO_ITEMS = [
"buy some cheese",
"feed the cat",
"book a doctors appointment",
];
const newTodo = page.getByPlaceholder("What needs to be done?");
for (const item of TODO_ITEMS) {
await newTodo.fill(item);
await newTodo.press("Enter");
}
await expect(page.getByTestId("todo-title")).toHaveCount(TODO_ITEMS.length);
await Promise.all(
TODO_ITEMS.map((value, index) =>
expect(page.getByTestId("todo-title").nth(index)).toHaveText(value),
),
);
},
};
```
### Storage state
Playwright supports [storage state](https://playwright.dev/docs/api/class-browsercontext#browsercontext-storage-state) to obtain and persist cookies and other storage data. In this example, you will use storage state to persist cookies and other storage data in [Workers KV](https://developers.cloudflare.com/kv).
First, ensure you have a KV namespace. You can create a new one with:
```bash
npx wrangler kv namespace create KV
```
Then, add the KV namespace to your Wrangler configuration file:
* wrangler.jsonc
```jsonc
{
"name": "storage-state-examples",
"main": "src/index.ts",
"compatibility_flags": ["nodejs_compat"],
"compatibility_date": "2026-02-07",
"browser": {
"binding": "MYBROWSER"
},
"kv_namespaces": [
{
"binding": "KV",
"id": ""
}
]
}
```
* wrangler.toml
```toml
name = "storage-state-examples"
main = "src/index.ts"
compatibility_flags = [ "nodejs_compat" ]
compatibility_date = "2026-02-07"
[browser]
binding = "MYBROWSER"
[[kv_namespaces]]
binding = "KV"
id = ""
```
Now, you can use the storage state to persist cookies and other storage data in KV:
```ts
// gets persisted storage state from KV or undefined if it does not exist
const storageStateJson = await env.KV.get('storageState');
const storageState = storageStateJson ? await JSON.parse(storageStateJson) as BrowserContextOptions['storageState'] : undefined;
await using browser = await launch(env.MYBROWSER);
// creates a new context with storage state persisted in KV
await using context = await browser.newContext({ storageState });
await using page = await context.newPage();
// do some actions on the page that may update client-side storage
// gets updated storage state: cookies, localStorage, and IndexedDB
const updatedStorageState = await context.storageState({ indexedDB: true });
// persists updated storage state in KV
await env.KV.put('storageState', JSON.stringify(updatedStorageState));
```
### Keep Alive
If users omit the `browser.close()` statement, the browser instance will stay open, ready to be connected to again and [re-used](https://developers.cloudflare.com/browser-rendering/workers-bindings/reuse-sessions/) but it will, by default, close automatically after 1 minute of inactivity. Users can optionally extend this idle time up to 10 minutes, by using the `keep_alive` option, set in milliseconds:
```js
const browser = await playwright.launch(env.MYBROWSER, { keep_alive: 600000 });
```
Using the above, the browser will stay open for up to 10 minutes, even if inactive.
Note
This is an inactivity timeout, not a maximum session duration. Sessions can remain open longer than 10 minutes as long as they stay active. To keep a session open beyond the inactivity timeout, send a command at least once within your configured window (for example, every 10 minutes). Refer to [session duration limits](https://developers.cloudflare.com/browser-rendering/limits/#is-there-a-maximum-session-duration) for more information.
### Session Reuse
The best way to improve the performance of your browser rendering Worker is to reuse sessions by keeping the browser open after you've finished with it, and connecting to that session each time you have a new request. Playwright handles [`browser.close`](https://playwright.dev/docs/api/class-browser#browser-close) differently from Puppeteer. In Playwright, if the browser was obtained using a `connect` session, the session will disconnect. If the browser was obtained using a `launch` session, the session will close.
```js
import { env } from "cloudflare:workers";
import { acquire, connect } from "@cloudflare/playwright";
async function reuseSameSession() {
// acquires a new session
const { sessionId } = await acquire(env.BROWSER);
for (let i = 0; i < 5; i++) {
// connects to the session that was previously acquired
const browser = await connect(env.BROWSER, sessionId);
// ...
// this will disconnect the browser from the session, but the session will be kept alive
await browser.close();
}
}
```
### Set a custom user agent
To specify a custom user agent in Playwright, set it in the options when creating a new browser context with `browser.newContext()`. All pages subsequently created from this context will use the new user agent. This is useful if the target website serves different content based on the user agent.
```js
const context = await browser.newContext({
userAgent:
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36",
});
```
Note
The `userAgent` parameter does not bypass bot protection. Requests from Browser Rendering will always be identified as a bot.
## Session management
In order to facilitate browser session management, we have extended the Playwright API with new methods:
### List open sessions
`playwright.sessions()` lists the current running sessions. It will return an output similar to this:
```json
[
{
"connectionId": "2a2246fa-e234-4dc1-8433-87e6cee80145",
"connectionStartTime": 1711621704607,
"sessionId": "478f4d7d-e943-40f6-a414-837d3736a1dc",
"startTime": 1711621703708
},
{
"sessionId": "565e05fb-4d2a-402b-869b-5b65b1381db7",
"startTime": 1711621703808
}
]
```
Notice that the session `478f4d7d-e943-40f6-a414-837d3736a1dc` has an active worker connection (`connectionId=2a2246fa-e234-4dc1-8433-87e6cee80145`), while session `565e05fb-4d2a-402b-869b-5b65b1381db7` is free. While a connection is active, no other workers may connect to that session.
### List recent sessions
`playwright.history()` lists recent sessions, both open and closed. It is useful to get a sense of your current usage.
```json
[
{
"closeReason": 2,
"closeReasonText": "BrowserIdle",
"endTime": 1711621769485,
"sessionId": "478f4d7d-e943-40f6-a414-837d3736a1dc",
"startTime": 1711621703708
},
{
"closeReason": 1,
"closeReasonText": "NormalClosure",
"endTime": 1711123501771,
"sessionId": "2be00a21-9fb6-4bb2-9861-8cd48e40e771",
"startTime": 1711123430918
}
]
```
Session `2be00a21-9fb6-4bb2-9861-8cd48e40e771` was closed explicitly with `browser.close()` by the client, while session `478f4d7d-e943-40f6-a414-837d3736a1dc` was closed due to reaching the maximum idle time (check [limits](https://developers.cloudflare.com/browser-rendering/limits/)).
You should also be able to access this information in the dashboard, albeit with a slight delay.
### Active limits
`playwright.limits()` lists your active limits:
```json
{
"activeSessions": [
{ "id": "478f4d7d-e943-40f6-a414-837d3736a1dc" },
{ "id": "565e05fb-4d2a-402b-869b-5b65b1381db7" }
],
"allowedBrowserAcquisitions": 1,
"maxConcurrentSessions": 2,
"timeUntilNextAllowedBrowserAcquisition": 0
}
```
* `activeSessions` lists the IDs of the current open sessions
* `maxConcurrentSessions` defines how many browsers can be open at the same time
* `allowedBrowserAcquisitions` specifies if a new browser session can be opened according to the rate [limits](https://developers.cloudflare.com/browser-rendering/limits/) in place
* `timeUntilNextAllowedBrowserAcquisition` defines the waiting period before a new browser can be launched.
## Playwright API
The full Playwright API can be found at the [Playwright API documentation](https://playwright.dev/docs/api/class-playwright).
The following capabilities are not yet fully supported, but we’re actively working on them:
* [Playwright Test](https://playwright.dev/docs/test-configuration) except [Assertions](https://playwright.dev/docs/test-assertions)
* [Components](https://playwright.dev/docs/test-components)
* [Firefox](https://playwright.dev/docs/api/class-playwright#playwright-firefox), [Android](https://playwright.dev/docs/api/class-android) and [Electron](https://playwright.dev/docs/api/class-electron), as well as different versions of Chrome
* [Videos](https://playwright.dev/docs/next/videos)
This is **not an exhaustive list** — expect rapid changes as we work toward broader parity with the original feature set. You can also check [latest test results](https://playwright-full-test-report.pages.dev/) for a granular up to date list of the features that are fully supported.
---
title: Pricing · Cloudflare Browser Rendering docs
description: "There are two ways to use Browser Rendering. Depending on the
method you use, here is how billing works:"
lastUpdated: 2025-12-09T17:41:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/pricing/
md: https://developers.cloudflare.com/browser-rendering/pricing/index.md
---
Available on Free and Paid plans
There are two ways to use Browser Rendering. Depending on the method you use, here is how billing works:
* [**REST API**](https://developers.cloudflare.com/browser-rendering/rest-api/): Charged for browser hours only
* [**Workers Bindings**](https://developers.cloudflare.com/browser-rendering/workers-bindings/): Charged for both browser hours and concurrent browsers
Browser hours are shared across both methods (REST API and Workers Bindings).
| | Workers Free | Workers Paid |
| - | - | - |
| Browser hours | 10 minutes per day | 10 hours per month, then $0.09 per additional hour |
| Concurrent browsers (Workers Bindings only) | 3 browsers | 10 browsers ([averaged monthly](#how-is-the-number-of-concurrent-browsers-calculated)), then $2.00 per additional browser |
## Examples of Workers Paid pricing
#### Example: REST API pricing
If a Workers Paid user uses the REST API for 50 hours during the month, the estimated cost for the month is as follows.
For browser hours:\
50 hours - 10 hours (included in plan) = 40 hours\
40 hours × $0.09 per hour = $3.60
#### Example: Workers Bindings pricing
If a Workers Paid plan user uses the Workers Bindings method for 50 hours during the month, and uses 10 concurrent browsers for the first 15 days and 20 concurrent browsers the last 15 days, the estimated cost for the month is as follows.
For browser hours:\
50 hours - 10 hours (included in plan) = 40 hours\
40 hours × $0.09 per hour = $3.60
For concurrent browsers:\
((10 browsers × 15 days) + (20 browsers × 15 days)) = 450 total browsers used in month\
450 browsers used in month ÷ 30 days in month = 15 browsers (averaged monthly)\
15 browsers (averaged monthly) − 10 (included in plan) = 5 browsers\
5 browsers × $2.00 per browser = $10.00
For browser hours and concurrent browsers:\
$3.60 + $10.00 = $13.60
## Pricing FAQ
### How do I estimate my Browser Rendering costs?
You can monitor Browser Rendering usage in two ways:
* To monitor your Browser Rendering usage in the Cloudflare dashboard, go to the **Browser Rendering** page.
[Go to **Browser Rendering**](https://dash.cloudflare.com/?to=/:account/workers/browser-rendering)
* The `X-Browser-Ms-Used` header, which is returned in every REST API response, reports browser time used for the request (in milliseconds). You can also access this header using the Typescript SDK with the .asResponse() method:
```ts
const contentRes = await client.browserRendering.content.create({
account_id: 'account_id',
}).asResponse();
const browserMsUsed = parseInt(contentRes.headers.get('X-Browser-Ms-Used') || '');
```
You can then use the tables above to estimate your costs based on your usage.
### Do failed API calls, such as those that time out, add to billable browser hours?
No. If a request to the Browser Rendering REST API fails with a `waitForTimeout` error, the browser session is not charged.
### How is the number of concurrent browsers calculated?
Cloudflare calculates concurrent browsers as the monthly average of your daily peak usage. In other words, we record the peak number of concurrent browsers each day and then average those values over the month. This approach reflects your typical traffic and ensures you are not disproportionately charged for brief spikes in browser concurrency.
### How is billing time calculated?
At the end of each day, Cloudflare totals all of your browser usage for that day in seconds. At the end of each billing cycle, we add up all of the daily totals to find the monthly total of browser hours, rounded to the nearest hour.
For example, if you only use 1 minute of browser time in a day, that day counts as 1 minute. If you do that every day for a 30-day month, your total would be 30 minutes. For billing, we round that up to 1 browser hour.
---
title: Puppeteer · Cloudflare Browser Rendering docs
description: Learn how to use Puppeteer with Cloudflare Workers for browser
automation. Access Puppeteer API, manage sessions, and optimize browser
rendering.
lastUpdated: 2026-01-22T12:20:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/puppeteer/
md: https://developers.cloudflare.com/browser-rendering/puppeteer/index.md
---
[Puppeteer](https://pptr.dev/) is one of the most popular libraries that abstract the lower-level DevTools protocol from developers and provides a high-level API that you can use to easily instrument Chrome/Chromium and automate browsing sessions. Puppeteer is used for tasks like creating screenshots, crawling pages, and testing web applications.
Puppeteer typically connects to a local Chrome or Chromium browser using the DevTools port. Refer to the [Puppeteer API documentation on the `Puppeteer.connect()` method](https://pptr.dev/api/puppeteer.puppeteer.connect) for more information.
The Workers team forked a version of Puppeteer and patched it to connect to the Workers Browser Rendering API instead. After connecting, the developers can then use the full [Puppeteer API](https://github.com/cloudflare/puppeteer/blob/main/docs/api/index.md) as they would on a standard setup.
Our version is open sourced and can be found in [Cloudflare's fork of Puppeteer](https://github.com/cloudflare/puppeteer). The npm can be installed from [npmjs](https://www.npmjs.com/) as [@cloudflare/puppeteer](https://www.npmjs.com/package/@cloudflare/puppeteer):
* npm
```sh
npm i -D @cloudflare/puppeteer
```
* yarn
```sh
yarn add -D @cloudflare/puppeteer
```
* pnpm
```sh
pnpm add -D @cloudflare/puppeteer
```
Note
The current version is [`@cloudflare/puppeteer` v1.0.4](https://github.com/cloudflare/puppeteer/releases/tag/v1.0.4), based on [Puppeteer v22.13.1](https://pptr.dev/chromium-support).
## Use Puppeteer in a Worker
Once the [browser binding](https://developers.cloudflare.com/browser-rendering/reference/wrangler/#bindings) is configured and the `@cloudflare/puppeteer` library is installed, Puppeteer can be used in a Worker:
* JavaScript
```js
import puppeteer from "@cloudflare/puppeteer";
export default {
async fetch(request, env) {
const browser = await puppeteer.launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto("https://example.com");
const metrics = await page.metrics();
await browser.close();
return Response.json(metrics);
},
};
```
* TypeScript
```ts
import puppeteer from "@cloudflare/puppeteer";
interface Env {
MYBROWSER: Fetcher;
}
export default {
async fetch(request, env): Promise {
const browser = await puppeteer.launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto("https://example.com");
const metrics = await page.metrics();
await browser.close();
return Response.json(metrics);
},
} satisfies ExportedHandler;
```
This script [launches](https://pptr.dev/api/puppeteer.puppeteernode.launch) the `env.MYBROWSER` browser, opens a [new page](https://pptr.dev/api/puppeteer.browser.newpage), [goes to](https://pptr.dev/api/puppeteer.page.goto) , gets the page load [metrics](https://pptr.dev/api/puppeteer.page.metrics), [closes](https://pptr.dev/api/puppeteer.browser.close) the browser and prints metrics in JSON.
### Keep Alive
If users omit the `browser.close()` statement, it will stay open, ready to be connected to again and [re-used](https://developers.cloudflare.com/browser-rendering/workers-bindings/reuse-sessions/) but it will, by default, close automatically after 1 minute of inactivity. Users can optionally extend this idle time up to 10 minutes, by using the `keep_alive` option, set in milliseconds:
```js
const browser = await puppeteer.launch(env.MYBROWSER, { keep_alive: 600000 });
```
Using the above, the browser will stay open for up to 10 minutes, even if inactive.
Note
This is an inactivity timeout, not a maximum session duration. Sessions can remain open longer than 10 minutes as long as they stay active. To keep a session open beyond the inactivity timeout, send a command at least once within your configured window (for example, every 10 minutes). Refer to [session duration limits](https://developers.cloudflare.com/browser-rendering/limits/#is-there-a-maximum-session-duration) for more information.
### Set a custom user agent
To specify a custom user agent in Puppeteer, use the `page.setUserAgent()` method. This is useful if the target website serves different content based on the user agent.
```js
await page.setUserAgent(
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36"
);
```
Note
The `userAgent` parameter does not bypass bot protection. Requests from Browser Rendering will always be identified as a bot.
## Element selection
Puppeteer provides multiple methods for selecting elements on a page. While CSS selectors work as expected, XPath selectors are not supported due to security constraints in the Workers runtime.
Instead of using Xpath selectors, you can use CSS selectors or `page.evaluate()` to run XPath queries in the browser context:
```ts
const innerHtml = await page.evaluate(() => {
return (
// @ts-ignore this runs on browser context
new XPathEvaluator()
.createExpression("/html/body/div/h1")
// @ts-ignore this runs on browser context
.evaluate(document, XPathResult.FIRST_ORDERED_NODE_TYPE).singleNodeValue
.innerHTML
);
});
```
Note
`page.evaluate()` can only return primitive types like strings, numbers, and booleans. Returning complex objects like `HTMLElement` will not work.
## Session management
In order to facilitate browser session management, we've added new methods to `puppeteer`:
### List open sessions
`puppeteer.sessions()` lists the current running sessions. It will return an output similar to this:
```json
[
{
"connectionId": "2a2246fa-e234-4dc1-8433-87e6cee80145",
"connectionStartTime": 1711621704607,
"sessionId": "478f4d7d-e943-40f6-a414-837d3736a1dc",
"startTime": 1711621703708
},
{
"sessionId": "565e05fb-4d2a-402b-869b-5b65b1381db7",
"startTime": 1711621703808
}
]
```
Notice that the session `478f4d7d-e943-40f6-a414-837d3736a1dc` has an active worker connection (`connectionId=2a2246fa-e234-4dc1-8433-87e6cee80145`), while session `565e05fb-4d2a-402b-869b-5b65b1381db7` is free. While a connection is active, no other workers may connect to that session.
### List recent sessions
`puppeteer.history()` lists recent sessions, both open and closed. It's useful to get a sense of your current usage.
```json
[
{
"closeReason": 2,
"closeReasonText": "BrowserIdle",
"endTime": 1711621769485,
"sessionId": "478f4d7d-e943-40f6-a414-837d3736a1dc",
"startTime": 1711621703708
},
{
"closeReason": 1,
"closeReasonText": "NormalClosure",
"endTime": 1711123501771,
"sessionId": "2be00a21-9fb6-4bb2-9861-8cd48e40e771",
"startTime": 1711123430918
}
]
```
Session `2be00a21-9fb6-4bb2-9861-8cd48e40e771` was closed explicitly with `browser.close()` by the client, while session `478f4d7d-e943-40f6-a414-837d3736a1dc` was closed due to reaching the maximum idle time (check [limits](https://developers.cloudflare.com/browser-rendering/limits/)).
You should also be able to access this information in the dashboard, albeit with a slight delay.
### Active limits
`puppeteer.limits()` lists your active limits:
```json
{
"activeSessions": [
{ "id": "478f4d7d-e943-40f6-a414-837d3736a1dc" },
{ "id": "565e05fb-4d2a-402b-869b-5b65b1381db7" }
],
"allowedBrowserAcquisitions": 1,
"maxConcurrentSessions": 2,
"timeUntilNextAllowedBrowserAcquisition": 0
}
```
* `activeSessions` lists the IDs of the current open sessions
* `maxConcurrentSessions` defines how many browsers can be open at the same time
* `allowedBrowserAcquisitions` specifies if a new browser session can be opened according to the rate [limits](https://developers.cloudflare.com/browser-rendering/limits/) in place
* `timeUntilNextAllowedBrowserAcquisition` defines the waiting period before a new browser can be launched.
## Puppeteer API
The full Puppeteer API can be found in the [Cloudflare's fork of Puppeteer](https://github.com/cloudflare/puppeteer/blob/main/docs/api/index.md).
---
title: Reference · Cloudflare Browser Rendering docs
lastUpdated: 2025-11-06T19:11:47.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/browser-rendering/reference/
md: https://developers.cloudflare.com/browser-rendering/reference/index.md
---
* [Automatic request headers](https://developers.cloudflare.com/browser-rendering/reference/automatic-request-headers/)
* [Supported fonts](https://developers.cloudflare.com/browser-rendering/reference/supported-fonts/)
* [REST API timeouts](https://developers.cloudflare.com/browser-rendering/reference/timeouts/)
* [Browser close reasons](https://developers.cloudflare.com/browser-rendering/reference/browser-close-reasons/)
* [Wrangler](https://developers.cloudflare.com/browser-rendering/reference/wrangler/)
---
title: REST API · Cloudflare Browser Rendering docs
description: >-
The REST API is a RESTful interface that provides endpoints for common browser
actions such as capturing screenshots, extracting HTML content, generating
PDFs, and more.
The following are the available options:
lastUpdated: 2026-02-03T12:27:00.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/rest-api/
md: https://developers.cloudflare.com/browser-rendering/rest-api/index.md
---
The REST API is a RESTful interface that provides endpoints for common browser actions such as capturing screenshots, extracting HTML content, generating PDFs, and more. The following are the available options:
* [/content - Fetch HTML](https://developers.cloudflare.com/browser-rendering/rest-api/content-endpoint/)
* [/screenshot - Capture screenshot](https://developers.cloudflare.com/browser-rendering/rest-api/screenshot-endpoint/)
* [/pdf - Render PDF](https://developers.cloudflare.com/browser-rendering/rest-api/pdf-endpoint/)
* [/markdown - Extract Markdown from a webpage](https://developers.cloudflare.com/browser-rendering/rest-api/markdown-endpoint/)
* [/snapshot - Take a webpage snapshot](https://developers.cloudflare.com/browser-rendering/rest-api/snapshot/)
* [/scrape - Scrape HTML elements](https://developers.cloudflare.com/browser-rendering/rest-api/scrape-endpoint/)
* [/json - Capture structured data using AI](https://developers.cloudflare.com/browser-rendering/rest-api/json-endpoint/)
* [/links - Retrieve links from a webpage](https://developers.cloudflare.com/browser-rendering/rest-api/links-endpoint/)
* [Reference](https://developers.cloudflare.com/api/resources/browser_rendering/)
Use the REST API when you need a fast, simple way to perform common browser tasks such as capturing screenshots, extracting HTML, or generating PDFs without writing complex scripts. If you require more advanced automation, custom workflows, or persistent browser sessions, [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/) are the better choice.
## Before you begin
Before you begin, make sure you [create a custom API Token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with the following permissions:
* `Browser Rendering - Edit`
Note
You can monitor Browser Rendering usage in two ways:
* In the Cloudflare dashboard, go to the **Browser Rendering** page to view aggregate metrics, including total REST API requests and total browser hours used. [Go to **Browser Rendering**](https://dash.cloudflare.com/?to=/:account/workers/browser-rendering)
* `X-Browser-Ms-Used` header: Returned in every REST API response, reporting browser time used for that request (in milliseconds).
---
title: Stagehand · Cloudflare Browser Rendering docs
description: Deploy a Stagehand server that uses Browser Rendering to provide
browser automation capabilities to your agents.
lastUpdated: 2026-02-02T18:38:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/browser-rendering/stagehand/
md: https://developers.cloudflare.com/browser-rendering/stagehand/index.md
---
[Stagehand](https://www.stagehand.dev/) is an open-source, AI-powered browser automation library. Stagehand lets you combine code with natural-language instructions powered by AI, eliminating the need to dictate exact steps or specify selectors. With Stagehand, your agents are more resilient to website changes and easier to maintain, helping you build more reliably and flexibly.
This guide shows you how to deploy a [Worker](https://developers.cloudflare.com/workers/) that uses Stagehand, Browser Rendering, and [Workers AI](https://developers.cloudflare.com/workers-ai/) to automate a web task.
Note
Browser Rendering currently supports `@browserbasehq/stagehand` `v2.5.x` only. Stagehand `v3` and later are not supported because they are not Playwright-based.
## Use Stagehand in a Worker with Workers AI
In this example, you will use Stagehand to search for a movie on this [example movie directory](https://demo.playwright.dev/movies), extract its details (title, year, rating, duration, and genre), and return the information along with a screenshot of the webpage.
See a video of this example
 Output: 
If instead you want to skip the steps and get started right away, select **Deploy to Cloudflare** below.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/playwright/tree/main/packages/playwright-cloudflare/examples/stagehand)
After you deploy, you can interact with the Worker using this URL pattern:
```plaintext
https://.workers.dev
```
### 1. Set up your project
Install the necessary dependencies:
```bash
npm ci
```
### 2. Configure your Worker
Update your Wrangler configuration file to include the bindings for Browser Rendering and [Workers AI](https://developers.cloudflare.com/workers-ai/):
Note
Your Worker configuration must include the `nodejs_compat` compatibility flag and a `compatibility_date` of 2025-09-15 or later.
* wrangler.jsonc
```jsonc
{
"name": "stagehand-example",
"main": "src/index.ts",
"compatibility_flags": ["nodejs_compat"],
"compatibility_date": "2026-02-07",
"observability": {
"enabled": true
},
"browser": {
"binding": "BROWSER"
},
"ai": {
"binding": "AI"
}
}
```
* wrangler.toml
```toml
name = "stagehand-example"
main = "src/index.ts"
compatibility_flags = [ "nodejs_compat" ]
compatibility_date = "2026-02-07"
[observability]
enabled = true
[browser]
binding = "BROWSER"
[ai]
binding = "AI"
```
If you are using the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/), you need to include the following [alias](https://vite.dev/config/shared-options.html#resolve-alias) in `vite.config.ts`:
```ts
export default defineConfig({
// ...
resolve: {
alias: {
'playwright': '@cloudflare/playwright',
},
},
});
```
If you are not using the Cloudflare Vite plugin, you need to include the following [module alias](https://developers.cloudflare.com/workers/wrangler/configuration/#module-aliasing) to the wrangler configuration:
```jsonc
{
// ...
"alias": {
"playwright": "@cloudflare/playwright"
}
}
```
### 3. Write the Worker code
Copy [workersAIClient.ts](https://github.com/cloudflare/playwright/blob/main/packages/playwright-cloudflare/examples/stagehand/src/worker/workersAIClient.ts) to your project.
Then, in your Worker code, import the `workersAIClient.ts` file and use it to configure a new `Stagehand` instance:
```ts
import { Stagehand } from "@browserbasehq/stagehand";
import { z } from "zod";
import { endpointURLString } from "@cloudflare/playwright";
import { WorkersAIClient } from "./workersAIClient";
export default {
async fetch(request: Request, env: Env) {
if (new URL(request.url).pathname !== "/")
return new Response("Not found", { status: 404 });
const stagehand = new Stagehand({
env: "LOCAL",
localBrowserLaunchOptions: { cdpUrl: endpointURLString(env.BROWSER) },
llmClient: new WorkersAIClient(env.AI),
verbose: 1,
});
await stagehand.init();
const page = stagehand.page;
await page.goto('https://demo.playwright.dev/movies');
// if search is a multi-step action, stagehand will return an array of actions it needs to act on
const actions = await page.observe('Search for "Furiosa"');
for (const action of actions)
await page.act(action);
await page.act('Click the search result');
// normal playwright functions work as expected
await page.waitForSelector('.info-wrapper .cast');
let movieInfo = await page.extract({
instruction: 'Extract movie information',
schema: z.object({
title: z.string(),
year: z.number(),
rating: z.number(),
genres: z.array(z.string()),
duration: z.number().describe("Duration in minutes"),
}),
});
await stagehand.close();
return Response.json(movieInfo);
},
};
```
Note
The snippet above requires [Zod v3](https://v3.zod.dev/) and is currently not compatible with Zod v4.
Ensure your `package.json` has the following dependencies:
```json
{
// ...
"dependencies": {
"@browserbasehq/stagehand": "2.5.x",
"@cloudflare/playwright": "^1.0.0",
"zod": "^3.25.76",
"zod-to-json-schema": "^3.24.6"
// ...
}
}
```
### 4. Build the project
```bash
npm run build
```
### 5. Deploy to Cloudflare Workers
After you deploy, you can interact with the Worker using this URL pattern:
```plaintext
https://.workers.dev
```
```bash
npm run deploy
```
## Use Cloudflare AI Gateway with Workers AI
[AI Gateway](https://developers.cloudflare.com/ai-gateway/) is a service that adds observability to your AI applications. By routing your requests through AI Gateway, you can monitor and debug your AI applications.
To use AI Gateway with a third-party model, first create a gateway in the **AI Gateway** page of the Cloudflare dashboard.
[Go to **AI Gateway**](https://dash.cloudflare.com/?to=/:account/ai/ai-gateway)
In this example, we've named the gateway `stagehand-example-gateway`.
```typescript
const stagehand = new Stagehand({
env: "LOCAL",
localBrowserLaunchOptions: { cdpUrl },
llmClient: new WorkersAIClient(env.AI, {
gateway: {
id: "stagehand-example-gateway"
}
}),
});
```
## Use a third-party model
If you want to use a model outside of Workers AI, you can configure Stagehand to use models from supported [third-party providers](https://docs.stagehand.dev/configuration/models#supported-providers), including OpenAI and Anthropic, by providing your own credentials.
In this example, you will configure Stagehand to use [OpenAI](https://openai.com/). You will need an OpenAI API key. Cloudflare recommends storing your API key as a [secret](https://developers.cloudflare.com/workers/configuration/secrets/).
```bash
npx wrangler secret put OPENAI_API_KEY
```
Then, configure Stagehand with your provider, model, and API key.
```typescript
const stagehand = new Stagehand({
env: "LOCAL",
localBrowserLaunchOptions: { cdpUrl: endpointURLString(env.BROWSER) },
modelName: "openai/gpt-4.1",
modelClientOptions: {
apiKey: env.OPENAI_API_KEY,
},
});
```
## Use Cloudflare AI Gateway with a third-party model
[AI Gateway](https://developers.cloudflare.com/ai-gateway/) is a service that adds observability to your AI applications. By routing your requests through AI Gateway, you can monitor and debug your AI applications.
To use AI Gateway with a third-party model, first create a gateway in the **AI Gateway** page of the Cloudflare dashboard.
[Go to **AI Gateway**](https://dash.cloudflare.com/?to=/:account/ai/ai-gateway)
In this example, we are using [OpenAI with AI Gateway](https://developers.cloudflare.com/ai-gateway/usage/providers/openai/). Make sure to add the `baseURL` as shown below, with your own Account ID and Gateway ID.
You must specify the `apiKey` in the `modelClientOptions`:
```typescript
const stagehand = new Stagehand({
env: "LOCAL",
localBrowserLaunchOptions: { cdpUrl: endpointURLString(env.BROWSER) },
modelName: "openai/gpt-4.1",
modelClientOptions: {
apiKey: env.OPENAI_API_KEY,
baseURL: `https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/openai`,
},
});
```
If you are using an authenticated AI Gateway, follow the instructions in [AI Gateway authentication](https://developers.cloudflare.com/ai-gateway/configuration/authentication/) and include `cf-aig-authorization` as a header.
## Stagehand API
For the full list of Stagehand methods and capabilities, refer to the official [Stagehand API documentation](https://docs.stagehand.dev/first-steps/introduction).
---
title: Workers Bindings · Cloudflare Browser Rendering docs
description: "Workers Bindings allow you to execute advanced browser rendering
scripts within Cloudflare Workers. They provide developers the flexibility to
automate and control complex workflows and browser interactions. The following
options are available for browser rendering tasks:"
lastUpdated: 2025-11-06T19:11:47.000Z
chatbotDeprioritize: false
tags: Bindings
source_url:
html: https://developers.cloudflare.com/browser-rendering/workers-bindings/
md: https://developers.cloudflare.com/browser-rendering/workers-bindings/index.md
---
Workers Bindings allow you to execute advanced browser rendering scripts within Cloudflare Workers. They provide developers the flexibility to automate and control complex workflows and browser interactions. The following options are available for browser rendering tasks:
* [Deploy a Browser Rendering Worker](https://developers.cloudflare.com/browser-rendering/workers-bindings/screenshots/)
* [Deploy a Browser Rendering Worker with Durable Objects](https://developers.cloudflare.com/browser-rendering/workers-bindings/browser-rendering-with-do/)
* [Reuse sessions](https://developers.cloudflare.com/browser-rendering/workers-bindings/reuse-sessions/)
Use Workers Bindings when you need advanced browser automation, custom workflows, or complex interactions beyond basic rendering. For quick, one-off tasks like capturing screenshots or extracting HTML, the [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) is the simpler choice.
---
title: 404 - Page Not Found · Cloudflare BYOIP docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/404/
md: https://developers.cloudflare.com/byoip/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About address maps · Cloudflare BYOIP docs
description: Address map is a data structure enabling customers with BYOIP
prefixes or account-level static IPs to specify which IP addresses should be
mapped to DNS records when they are proxied through Cloudflare.
lastUpdated: 2025-10-30T14:41:37.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/address-maps/
md: https://developers.cloudflare.com/byoip/address-maps/index.md
---
Address map is a data structure enabling customers with BYOIP prefixes or account-level static IPs to specify which IP addresses should be mapped to DNS records when they are proxied through Cloudflare.
If you do not have BYOIP or static IPs and you want to use Address Maps, contact your account manager. You can [customize the IPs Cloudflare uses](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/#customize-cloudflare-ip-addresses) by bringing your own IP addresses to Cloudflare (BYOIP) or by leasing static Cloudflare IPs.
Note
Both IPv4 and IPv6 addresses are supported.
***
## How Address Maps works
For zones using [Cloudflare's authoritative DNS](https://developers.cloudflare.com/dns/), Cloudflare typically responds to DNS queries for proxied hostnames with [anycast IPs](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/). However, if you [customize the IPs Cloudflare uses](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/#customize-cloudflare-ip-addresses) and use Address Maps, Cloudflare will respond with the IP address(es) on the address map.
Address maps do not change [how Cloudflare reaches the configured origin](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/#how-cloudflare-works-as-a-reverse-proxy). The IP addresses defined on your zone's [DNS Records](https://dash.cloudflare.com/?to=/:account/:zone/dns/records) continue to instruct Cloudflare how to reach the origin.
Warning
Depending on whether you use static IPs or BYOIP, the process to [create an address map](https://developers.cloudflare.com/byoip/address-maps/setup/) is different.
### Static IPs or BYOIP
Leased static IPs allow you to use a set of specifically assigned Cloudflare IPs to ensure they do not change. Cloudflare creates an address map with your static IPs that you may edit. You cannot create another map using your static IPs.
With BYOIP, you use your IPs by bringing an address space that you lease or own and creating an address map.
***
## Immutable address maps
Some customers may only proxy zones through BYOIP addresses, and are prohibited from using Cloudflare IP addresses for proxied DNS names. In this case, Cloudflare will create an immutable, account-wide address map to ensure all zones in your account receive BYOIP addresses as a fallback. These address maps cannot be deleted.
It is still possible to create more specific zone-level address maps with specific BYOIPs, but DNS will fall back to the account-wide address map without one.
To specify different addresses for certain zones, [create a new address map](https://developers.cloudflare.com/byoip/address-maps/setup/).
***
## Spectrum compatibility
You can use address maps to set up [non-SNI support](https://developers.cloudflare.com/byoip/address-maps/setup/#spectrum-https-applications) for Spectrum HTTPS applications.
However, to control what IP address Cloudflare will use when responding to requests for your Spectrum applications, you should first refer to their respective configuration and set the `edge_ips` field as `static`. For details, refer to the [Spectrum API](https://developers.cloudflare.com/api/resources/spectrum/models/edge_ips/).
---
title: Changelog · Cloudflare BYOIP docs
description: Subscribe to RSS
lastUpdated: 2025-02-13T19:35:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/changelog/
md: https://developers.cloudflare.com/byoip/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/byoip/changelog/index.xml)
## 2024-07-02
**Address Maps for BYOIP and Static IPs**
Address Maps is available via [API](https://developers.cloudflare.com/api/resources/addressing/subresources/address_maps/methods/list/) and via [dashboard](https://dash.cloudflare.com/?to=/:account/ip-addresses/proxy-ips). Address Maps allows customers with BYOIP prefixes or account-level Static IPs to specify which IP addresses should be mapped to DNS records when they are proxied through Cloudflare. Refer to the [documentation](https://developers.cloudflare.com/byoip/address-maps/) for details.
---
title: Concepts · Cloudflare BYOIP docs
description: Review the topics below for more information about concepts related to BYOIP.
lastUpdated: 2024-09-19T15:40:35.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/byoip/concepts/
md: https://developers.cloudflare.com/byoip/concepts/index.md
---
Review the topics below for more information about concepts related to BYOIP.
* [Dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/)
* [Internet Routing Registry (IRR)](https://developers.cloudflare.com/byoip/concepts/irr-entries/)
* [Route filtering and RPKI](https://developers.cloudflare.com/byoip/concepts/route-filtering-rpki/)
* [Letter of Agency](https://developers.cloudflare.com/byoip/concepts/loa/)
* [Prefix delegations](https://developers.cloudflare.com/byoip/concepts/prefix-delegations/)
* [Static IPs](https://developers.cloudflare.com/byoip/concepts/static-ips/)
---
title: Get started · Cloudflare BYOIP docs
description: To use your own IP addresses with Cloudflare, please check with
your account team to confirm your contract covers this functionality. You will
need to configure settings specific to the services you want to use, as well
as meet some standard requirements for all BYOIP customers.
lastUpdated: 2026-01-21T10:23:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/get-started/
md: https://developers.cloudflare.com/byoip/get-started/index.md
---
To use your own IP addresses with Cloudflare, please check with your account team to confirm your contract covers this functionality. You will need to configure settings specific to the services you want to use, as well as meet some standard requirements for all BYOIP customers.
Once your account configurations are in place, consider the sections below to learn how to set up your BYOIP prefixes. Also make sure to review the [BYOIP Service-Specific Terms](https://www.cloudflare.com/service-specific-terms-network-services/#bring-your-own-ip-terms).
Magic Transit
The process described on this page does not support onboarding IP prefixes for use with [Cloudflare Magic Transit](https://developers.cloudflare.com/magic-transit/). For further guidance, refer to the [Magic Transit get started](https://developers.cloudflare.com/magic-transit/get-started/).
## Before you begin
* Your prefix must be registered under one of the Regional Internet Registries (RIRs):
* [AFRINIC](https://afrinic.net/)
* [APNIC](https://www.apnic.net/)
* [ARIN](https://www.arin.net/)
* [LACNIC](https://lacnic.net/)
* [RIPE](https://www.ripe.net/)
* Also verify that your [Internet Routing Registry (IRR)](https://developers.cloudflare.com/byoip/concepts/irr-entries/) records are are up to date and contain:
* `route` or `route6` objects matching the exact prefixes you want to onboard
* `origin` matching the correct ASN you want to onboard
Use Cloudflare's ASN
The process described on this page only supports using Cloudflare's ASN (AS13335). If you must announce the prefixes under your own ASN, contact your account team.
* You must use [Resource Public Key Infrastructure (RPKI) validation](https://developers.cloudflare.com/byoip/concepts/route-filtering-rpki/) and make sure your ROAs are accurate. You can use [Cloudflare's RPKI Portal](https://rpki.cloudflare.com/?view=validator) and a second source such as [Routinator](https://rpki-validator.ripe.net/ui/) to double-check your prefixes.
* If you are not familiar with how Cloudflare API works, refer to [Fundamentals](https://developers.cloudflare.com/fundamentals/api/). Make sure you have the necessary permissions and that you have your account ID.
***
## 1. Set up your prefixes
### Add your prefix
1. Use the [Add Prefix endpoint](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/methods/create/) to create a prefix in the Cloudflare account that should own the BYOIP prefix.
Use Cloudflare's ASN
The process described on this page only supports using Cloudflare's ASN (AS13335). If you must announce the prefixes under your own ASN, contact your account team.
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/addressing/prefixes" \
--request POST \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY" \
--json '{
"cidr": "203.0.113.0/24",
"asn": 13335,
"delegate_loa_creation": true
}'
```
```json
"result": {
"id": "72823e95d6c64d48a8111fec81179816",
"created_at": "2025-02-25T00:34:11.423722Z",
"modified_at": "2025-02-25T00:34:11.423722Z",
"cidr": "203.0.113.0/24",
"account_id": "654c5f71c324478cc9f68d60065d4620",
"description": "",
"approved": "P",
"on_demand_enabled": false,
"on_demand_locked": false,
"advertised": null,
"advertised_modified_at": null,
"loa_document_id": "b9ff4afe312246a8b2e7324d98f40b23",
"asn": 13335,
"ownership_validation_token": "",
"delegate_loa_creation" : true,
"irr_validation_state": "pending",
"rpki_validation_state": "pending",
"ownership_validation_state": "pending",
}
```
1. Take note of the `id` assigned to the prefix you added. It will be used in future steps.
Letter of Agency (LOA)
The process described on this page leverages automated [LOA](https://developers.cloudflare.com/byoip/concepts/loa/) generation. If you set `delegate_loa_creation` to `false`, you have to manually upload your LOA, make a [PATCH request](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/methods/edit/) once the prefix is approved, and contact your account team - which is more prone to error and increases the onboarding time.
### Validate prefix ownership
1. Validate prefix ownership using one of the following methods:
* IRR record
1. Copy the `ownership_validation_token` returned by the API call.
2. On the IRR record of the prefix you are onboarding, add the following string in either a `description` or `remarks` field. Replace `` by the actual token you copied in the previous step.
```plaintext
cf-validation:
```
Note
The exact steps to update your IRR record will depend on the registry you are using. Refer to [Internet Routing Registry (IRR)](https://developers.cloudflare.com/byoip/concepts/irr-entries/best-practices/) for details.
* Reverse DNS zone and TXT record
1. Consider the size of the prefix you are bringing to Cloudflare. Since the standard `in-addr.arpa` tree assumes delegations on octet or nibble boundaries, if you onboard prefixes that are not aligned with those, you will have to split up the prefix into subnets and create the corresponding reverse DNS zones for each.
Example
To calculate how many smaller subnets you need, use the following formula:
```plaintext
2^(next boundary - current netmask)
```
For `1.1.0.0/23`, you would setup two (`2^(24-23)`) reverse DNS zones, one for `1.1.0.0/24` and another for `1.1.1.0/24`.
For `2001:0db8::/34`, you would setup four (`2^(36-34)`) reverse DNS zones, for `2001:0db8::/36`, `2001:0db8:1:/36`, `2001:0db8:2::/36`, and `2001:0db8:3::/36`.
1. Set up a reverse DNS zone. If you use Cloudflare for DNS, refer to [Reverse DNS zones](https://developers.cloudflare.com/dns/additional-options/reverse-zones/#set-up-a-reverse-zone). If you use a different DNS provider, follow their instructions.
2. Create TXT records using `cf-validation` as their `name`. They should look like the following example:
```plaintext
cf-validation. IN TXT
```
1. Update nameservers at your Regional Internet Registry (RIR). The exact steps to update your nameservers will depend on the registry you are using.
2. After applying the necessary changes, use the Validate Prefix endpoint to trigger the validation checks.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Magic Transit Write`
* `IP Prefixes: Write`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/addressing/prefixes/$PREFIX_ID/validate" \
--request POST \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY"
```
Once the ownership validation is successful, you can remove the token.
When all validations pass - RPKI, IRR, and ownership - the `approved` field in your prefix will return `"V"`. This means you can proceed to create IP address service bindings[1](#user-content-fn-1).
If needed, you can use the [Prefix Details endpoint](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/methods/get/) to check if any issues were found during validation. If so, proceed with the necessary changes and make a request to restart validation. Refer to [Prefix validation checks](https://developers.cloudflare.com/byoip/troubleshooting/prefix-validation/) for details.
### (Optional) Delegate your BYOIP prefixes
You can allow other accounts to use part or all of your BYOIP prefix. Refer to [Prefix delegations](https://developers.cloudflare.com/byoip/concepts/prefix-delegations/) for details.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `IP Prefixes: Write`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/addressing/prefixes/$PREFIX_ID/delegations" \
--request POST \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY" \
--json '{
"cidr": "",
"delegated_account_id": ""
}'
```
Note
Although you can delegate IPs to other accounts, the IP address service bindings are still created and managed on the parent account - meaning the Cloudflare account where you added the prefix in step 1.
***
## 2. Create service bindings
In IP address management, service bindings map the traffic destined for a given IP address to the Cloudflare service that it should be routed through.
### Default service binding
When you onboard your IP prefixes to Cloudflare, there must be one service binding that spans across your entire prefix. Traffic destined for a given IP address will be routed to this service by default. You can also configure [additional service bindings](#optional-additional-bindings) as described in the next step.
1. Make a `GET` request to the [List Services](https://developers.cloudflare.com/api/resources/addressing/subresources/services/methods/list/) endpoint and take note of the `id` associated with the service you want to use.
CDN egress
[Dedicated CDN Egress IPs](https://developers.cloudflare.com/smart-shield/configuration/dedicated-egress-ips/) (formerly known as Aegis) is only available for Enterprise. If you are interested, reach out to your account team. Also note that a single BYOIP prefix can be used for either CDN ingress or CDN egress, but not both.
1. (Optional) If needed, use the [List Prefixes](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/methods/list/) endpoint to get or confirm the `id` associated with your prefix.
2. Make a `POST` request to the [Create service binding](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/service_bindings/methods/create/) endpoint, indicating the entire BYOIP prefix that you are onboarding and the service that should be used for your default binding.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `IP Prefixes: Write`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/addressing/prefixes/$PREFIX_ID/bindings" \
--request POST \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY" \
--json '{
"cidr": "203.0.113.0/24",
"service_id": ""
}'
```
A corresponding BGP prefix will be created automatically. Allow five hours before you advertise the prefix.
### (Optional) Additional bindings
If you want to selectively route traffic on a per-IP address basis to CDN or Spectrum, you can create additional service bindings.
Note
The steps below only cover assigning specific IPs to additional services. For guidance that includes CDN or Spectrum setup steps, refer to [Service bindings](https://developers.cloudflare.com/byoip/service-bindings/).
1. Plan for what IP(s) will get the additional binding. Cloudflare **strongly** recommends implementing service bindings through an **aggregated** CIDR block, as it is more efficient than adding discrete bindings for non-contiguous CIDR blocks.
Example
**Spectrum protected prefix:** `203.0.113.0/24`
**IPs to upgrade to CDN:**
`203.0.113.16`\
`203.0.113.17`\
`203.0.113.18`\
`203.0.113.19`\
`203.0.113.20`\
`203.0.113.21`\
`203.0.113.22`\
`203.0.113.23`
Add one discrete CDN service binding for `203.0.113.16` with a `/29` netmask.
1. Make a `POST` request to the [Create service binding](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/service_bindings/methods/create/) endpoint, indicating the IP address you want to bind to the CDN or Spectrum. Specify the **corresponding network mask** as needed.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `IP Prefixes: Write`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/addressing/prefixes/$PREFIX_ID/bindings" \
--request POST \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY" \
--json '{
"cidr": "203.0.113.16/29",
"service_id": ""
}'
```
In the response body, the initial provisioning state should be `provisioning`.
```json
{
"errors": [],
"messages": [],
"success": true,
"result": {
"cidr": "203.0.113.16/29",
"id": "",
"provisioning": {
"state": "provisioning"
},
"service_id": "",
"service_name": ""
}
}
```
Once a service binding is created (or deleted), it will take **four to six hours** to propagate across Cloudflare's global network.
Note
Magic Transit can only be used as default binding, spanning across your entire prefix. For more details, refer to [Service bindings scope](https://developers.cloudflare.com/byoip/service-bindings/#scope).
***
## 3. Advertise the BGP prefix
Once automatically created (following [step 2](#2-create-service-bindings)), BGP prefixes are initially withdrawn. After all your configurations are in place - including [address maps](https://developers.cloudflare.com/byoip/address-maps/)[2](#user-content-fn-2) if you will use CDN service -, proceed to advertise the BGP route for your prefix.
1. Use the [Update BGP prefix](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/bgp_prefixes/methods/edit/) endpoint to start the advertisement.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Magic Transit Write`
* `IP Prefixes: Write`
* `IP Prefixes: BGP On Demand Write`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/addressing/prefixes/$PREFIX_ID/bgp/prefixes/$BGP_PREFIX_ID" \
--request PATCH \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY" \
--json '{
"on_demand": {
"advertised": true
}
}'
```
## Footnotes
1. Mappings that control through which pipeline traffic destined for a given IP address will be routed. [↩](#user-content-fnref-1)
2. Mappings that specify which IP addresses should be used when Cloudflare responds to DNS queries for proxied hostnames. [↩](#user-content-fnref-2)
---
title: Route Leak Detection · Cloudflare BYOIP docs
description: Route Leak Detection protects your routes on the Internet by
notifying you when your traffic is routed somewhere it should not go, which
could indicate a possible attack. Route Leak Detection also reduces the amount
of time needed to mitigate leaks by providing you with timely notifications.
lastUpdated: 2025-09-04T17:04:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/route-leak-detection/
md: https://developers.cloudflare.com/byoip/route-leak-detection/index.md
---
Route Leak Detection protects your routes on the Internet by notifying you when your traffic is routed somewhere it should not go, which could indicate a possible attack. Route Leak Detection also reduces the amount of time needed to mitigate leaks by providing you with timely notifications.
Cloudflare detects route leaks by using several sources of routing data to create a synthesis of how the Internet sees routes to BYOIP users. Cloudflare then watches these views to track any sudden changes that occur on the Internet. If the changes can be correlated to actions Cloudflare has taken, no further action is required. However, if changes have not been made, Cloudflare notifies you to inform you that your routes and users may be at risk.
## Enable Route Leak Detection
Route Leak Detection Alert
**Who is it for?**
[BYOIP customers](https://developers.cloudflare.com/byoip/) who want to receive a notification when their prefixes are advertised in places they should not be.
**Other options / filters**
None.
**Included with**
Purchase of BYOIP.
**What should you do if you receive one?**
Confirm your traffic is healthy. Reach out to your transit providers to ensure you are behaving as expected and ask them to follow up with any providers accepting the unauthorized routes.
You must be a user who has brought your own IP address to Cloudflare, which includes Magic Transit, Spectrum, and WAF users. Only prefixes advertised by Cloudflare qualify for Route Leak Detection.
1. In the Cloudflare dashboard, go to the **Notifications** page.
[Go to **Notifications**](https://dash.cloudflare.com/?to=/:account/notifications)
2. Select **Add**.
3. Locate **Route Leak Detection** from the list > **Select**.
4. Enter a name and description for the notification.
5. Enter one or more email addresses to receive the notifications.
6. Select **Save**.
---
title: Glossary · Cloudflare BYOIP docs
description: Review the definitions for terms used across Cloudflare's BYOIP documentation.
lastUpdated: 2024-10-30T13:44:50.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/glossary/
md: https://developers.cloudflare.com/byoip/glossary/index.md
---
Review the definitions for terms used across Cloudflare's BYOIP documentation.
| Term | Definition |
| - | - |
| address map | A data structure enabling customers with BYOIP prefixes or account-level static IPs to specify which IP addresses should be mapped to DNS records when they are proxied through Cloudflare. |
| autonomous system numbers (ASNs) | A large network or group of networks that has a unified routing policy. Every computer or device that connects to the Internet is connected to an autonomous system. |
| Border Gateway Protocol (BGP) | The routing protocol for the Internet, which is responsible for picking the most efficient routes to deliver Internet traffic. |
| Internet Routing Registry (IRR) | A globally distributed database of routing information which contains announced routes and routing policies in a common format. Network operators use this information, as well as [RPKI](https://developers.cloudflare.com/byoip/concepts/route-filtering-rpki/), to configure backbone routers. |
| Resource Public Key Infrastructure (RPKI) | A cryptographic method of signing records that associate a route with an originating autonomous system number. |
| Route Origin Authorization (ROA) | The RPKI-signed object that states an autonomous system is authorized to originate a particular IP address prefix or set of prefixes. |
| Unicast Reverse Path Forwarding (uRPF) | A security feature that can prevent spoofing attacks. |
---
title: IP address service bindings · Cloudflare BYOIP docs
description: In IP address management, service binding refers to the association
of IPs to specific Cloudflare services. Review the available options and the
API endpoints to set up service bindings.
lastUpdated: 2026-01-21T10:23:58.000Z
chatbotDeprioritize: false
tags: Bindings
source_url:
html: https://developers.cloudflare.com/byoip/service-bindings/
md: https://developers.cloudflare.com/byoip/service-bindings/index.md
---
In IP address management, service bindings map the traffic destined for a given IP address to the Cloudflare service that it should be routed through.
Service binding operations are currently only available via API. You can find all endpoints and their specifications in the [Cloudflare API documentation](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/service_bindings/). For detailed guidance, refer to the sections and tutorials linked below.
Note
Service bindings take four to six hours to propagate across Cloudflare's global network after being created or deleted. Services for the IP addresses in scope are likely disrupted during this window.
## Scope
Customers using BYOIP with Magic Transit, [CDN services](https://developers.cloudflare.com/cache/), or [Spectrum](https://developers.cloudflare.com/spectrum/) can leverage the [service binding API endpoints](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/service_bindings/) to selectively route traffic through the CDN \[^1] or Spectrum \[^2] pipelines on a per-IP address basis. This means:
* You can upgrade individual IPs within a Magic Transit prefix to either a CDN IP or a Spectrum IP. For example, if you have a Magic Transit prefix `203.0.113.0/24`, you can upgrade `203.0.113.1` to CDN and `203.0.113.2` to Spectrum.
* You can upgrade individual IPs within a CDN prefix to a Spectrum IP. For example, if you have a CDN prefix `203.0.113.0/24`, you can upgrade `203.0.113.1` to Spectrum.
* You can upgrade individual IPs within a Spectrum prefix to a CDN IP. For example, if you have a Spectrum prefix `203.0.113.0/24`, you can upgrade `203.0.113.1` to CDN.
Refer to [Magic Transit with CDN](https://developers.cloudflare.com/byoip/service-bindings/magic-transit-with-cdn/) or [CDN and Spectrum](https://developers.cloudflare.com/byoip/service-bindings/cdn-and-spectrum/) for detailed guidance.
Warning
Magic Transit customers must ensure that their contract includes CDN and/or Spectrum according to their needs.
### CDN (Cache)
When a service binding of type `CDN` is applied, once the change has propagated across Cloudflare's global network (four to six hours), any HTTP requests are directed into the CDN pipeline for Layer 7 processing.
### Spectrum
When a service binding of type `Spectrum` is applied, once the change has propagated across Cloudflare's global network (four to six hours), any TCP/HTTP requests are directed into the Spectrum pipeline for Layer 4 or Layer 7 processing.
UDP applications
Spectrum UDP applications are [not supported](https://developers.cloudflare.com/spectrum/reference/limitations/#udp) when using Spectrum with BYOIP.
### Magic Transit
Note
Magic Transit can only be used as default binding, spanning across your entire prefix. You can then add CDN or Spectrum for smaller subnets but not the other way around.
The entire BYOIP prefix is primarily announced for Magic Transit, providing layer 3 DDoS protection and acceleration. Traffic not explicitly bound to CDN will flow through Magic Transit.
Also, traffic egressing to an IP in the prefix will always go to Magic Transit, even if there is an overlapping binding for CDN or Spectrum. This allows customers who want to use the same IP as ingress IP and as origin IP to do so.
```mermaid
flowchart LR
accTitle: Cloudflare as a reverse proxy
accDescr: Diagram showing Cloudflare's network between clients and the origin server.
A[Client] --ingress--> B((Cloudflare))--egress--> C[(Origin server)]
```
When adding a service binding for a given IP address, it must be either a CDN service binding or a Spectrum service binding. It is not possible (or necessary) to bind both services.
### CDN egress
[Dedicated CDN Egress IPs](https://developers.cloudflare.com/smart-shield/configuration/dedicated-egress-ips/) (formerly known as Aegis) is only available for Enterprise. If you are interested, reach out to your account team. Also note that a single BYOIP prefix can be used for either CDN ingress or CDN egress, but not both.
## Tutorials
* [Use BYOIP with Magic Transit and CDN](https://developers.cloudflare.com/byoip/service-bindings/magic-transit-with-cdn/)
* [Use BYOIP with CDN and Spectrum](https://developers.cloudflare.com/byoip/service-bindings/cdn-and-spectrum/)
---
title: Troubleshooting · Cloudflare BYOIP docs
description: Review common troubleshooting scenarios for BYOIP.
lastUpdated: 2025-10-30T18:03:49.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/byoip/troubleshooting/
md: https://developers.cloudflare.com/byoip/troubleshooting/index.md
---
The following topics are useful for troubleshooting BYOIP issues.
## uRPF filtering and packet loss
Routers receive IP packets and forward the packets to the destination IP address. Unicast Reverse Path Forwarding (uRPF) is a security feature that can prevent spoofing attacks. uRPF operates under two modes: strict and loose mode.
Under **strict mode**, the router performs two checks on incoming packets to look for a matching entry in the source routing table and to determine whether the interface that received the packet can be used to reach the source. If the incoming IP packets pass both checks, the packets are forwarded; if the checks do not pass, the packets are dropped.
When uRPF is set to loose mode, the router performs a single check when it receives an IP packet to look for a source's matching entry in the routing table.
If you are experiencing packet loss as a result of an upstream ISP implementing uRPF filtering, contact your ISP and request the link be set to **loose mode**.
## Non-SNI support
Currently, BYOIP cannot be used with [legacy custom certificates](https://developers.cloudflare.com/ssl/edge-certificates/custom-certificates/uploading/) to support [non-SNI](https://developers.cloudflare.com/ssl/reference/browser-compatibility/#non-sni-support) requests.
Instead, you can use Address Maps to set a default SNI for IPs on your account or zone. Refer to [Setup](https://developers.cloudflare.com/byoip/address-maps/setup/#non-sni-support) for further guidance.
---
title: 404 - Page Not Found · Cloudflare Cache (CDN) docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cache/404/
md: https://developers.cloudflare.com/cache/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Advanced configuration · Cloudflare Cache (CDN) docs
description: Learn how to complete different configuration options to customize
your cache behavior.
lastUpdated: 2024-09-10T14:21:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/advanced-configuration/
md: https://developers.cloudflare.com/cache/advanced-configuration/index.md
---
Learn how to complete different configuration options to customize your cache behavior.
* [Cache Reserve](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/)
* [Crawler Hints](https://developers.cloudflare.com/cache/advanced-configuration/crawler-hints/)
* [Early Hints](https://developers.cloudflare.com/cache/advanced-configuration/early-hints/)
* [Query String Sort](https://developers.cloudflare.com/cache/advanced-configuration/query-string-sort/)
* [Serving tailored content with Cloudflare](https://developers.cloudflare.com/cache/advanced-configuration/serve-tailored-content/)
* [Vary for images](https://developers.cloudflare.com/cache/advanced-configuration/vary-for-images/)
---
title: Cache security · Cloudflare Cache (CDN) docs
description: Review the following content to learn more about cache security.
lastUpdated: 2024-09-10T14:21:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/cache-security/
md: https://developers.cloudflare.com/cache/cache-security/index.md
---
Review the following content to learn more about cache security.
* [Avoid web cache poisoning](https://developers.cloudflare.com/cache/cache-security/avoid-web-poisoning/)
* [Cache Deception Armor](https://developers.cloudflare.com/cache/cache-security/cache-deception-armor/)
* [Cross-Origin Resource Sharing (CORS)](https://developers.cloudflare.com/cache/cache-security/cors/)
---
title: Changelog · Cloudflare Cache (CDN) docs
description: "You can now review detailed audit logs for cache purge events,
giving you visibility into what purge requests were sent, what they contained,
and by whom. Audit your purge requests via the Dashboard or API for all purge
methods:"
lastUpdated: 2026-01-08T10:45:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cache/changelog/
md: https://developers.cloudflare.com/cache/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/cache.xml)
## 2025-11-25
**Audit Logs for Cache Purge Events**
You can now review detailed audit logs for cache purge events, giving you visibility into what purge requests were sent, what they contained, and by whom. Audit your purge requests via the Dashboard or API for all purge methods:
* Purge everything
* List of prefixes
* List of tags
* List of hosts
* List of files
#### Example
The detailed audit payload is visible within the Cloudflare Dashboard (under **Manage Account** > **Audit Logs**) and via the API. Below is an example of the Audit Logs v2 payload structure:
```json
{
"action": {
"result": "success",
"type": "create"
},
"actor": {
"id": "1234567890abcdef",
"email": "user@example.com",
"type": "user"
},
"resource": {
"product": "purge_cache",
"request": {
"files": [
"https://example.com/images/logo.png",
"https://example.com/css/styles.css"
]
}
},
"zone": {
"id": "023e105f4ecef8ad9ca31a8372d0c353",
"name": "example.com"
}
}
```
#### Get started
To get started, refer to the [Audit Logs documentation](https://developers.cloudflare.com/fundamentals/account/account-security/audit-logs/).
## 2025-11-07
**Inspect Cache Keys with Cloudflare Trace**
You can now see the exact cache key generated for any request directly in Cloudflare Trace. This visibility helps you troubleshoot cache hits and misses, and verify that your Custom Cache Keys — configured via Cache Rules or Page Rules — are working as intended.
Previously, diagnosing caching behavior required inferring the key from configuration settings. Now, you can confirm that your custom logic for headers, query strings, and device types is correctly applied.
Access Trace via the [dashboard](https://developers.cloudflare.com/rules/trace-request/how-to/#use-trace-in-the-dashboard) or [API](https://developers.cloudflare.com/api/resources/request_tracer/methods/trace/), either manually for ad-hoc debugging or automated as part of your quality-of-service monitoring.
#### Example scenario
If you have a Cache Rule that segments content based on a specific cookie (for example, `user_region`), run a Trace with that cookie present to confirm the `user_region` value appears in the resulting cache key.
The Trace response includes the cache key in the `cache` object:
```json
{
"step_name": "request",
"type": "cache",
"matched": true,
"public_name": "Cache Parameters",
"cache": {
"key": {
"zone_id": "023e105f4ecef8ad9ca31a8372d0c353",
"scheme": "https",
"host": "example.com",
"uri": "/images/hero.jpg"
},
"key_string": "023e105f4ecef8ad9ca31a8372d0c353::::https://example.com/images/hero.jpg:::::"
}
}
```
#### Get started
To learn more, refer to the [Trace documentation](https://developers.cloudflare.com/rules/trace-request/) and our guide on [Custom Cache Keys](https://developers.cloudflare.com/cache/how-to/cache-keys/).
## 2025-08-29
**Smart Tiered Cache Fallback to Generic**
[Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#smart-tiered-cache) now falls back to [Generic Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#generic-global-tiered-cache) when the origin location cannot be determined, improving cache precision for your content.
Previously, when Smart Tiered Cache was unable to select the optimal upper tier (such as when origins are masked by Anycast IPs), latency could be negatively impacted. This fallback now uses Generic Tiered Cache instead, providing better performance and cache efficiency.
#### How it works
When Smart Tiered Cache falls back to Generic Tiered Cache:
1. **Multiple upper-tiers**: Uses all of Cloudflare's global data centers as a network of upper-tiers instead of a single optimal location.
2. **Distributed cache requests**: Lower-tier data centers can query any available upper-tier for cached content.
3. **Improved global coverage**: Provides better cache hit ratios across geographically distributed visitors.
4. **Automatic fallback**: Seamlessly transitions when origin location cannot be determined, such as with Anycast-masked origins.
#### Benefits
* **Preserves high performance during fallback**: Smart Tiered Cache now maintains strong cache efficiency even when optimal upper tier selection is not possible.
* **Minimizes latency impact**: Automatically uses Generic Tiered Cache topology to keep performance high when origin location cannot be determined.
* **Seamless experience**: No configuration changes or intervention required when fallback occurs.
* **Improved resilience**: Smart Tiered Cache remains effective across diverse origin infrastructure, including Anycast-masked origins.
#### Get started
This improvement is automatically applied to all zones using [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/). No action is required on your part.
## 2025-04-04
**Workers Fetch API can override Cache Rules**
You can now programmatically override Cache Rules using the `cf` object in the `fetch()` command. This feature gives you fine-grained control over caching behavior on a per-request basis, allowing Workers to customize cache settings dynamically based on request properties, user context, or business logic.
#### How it works
Using the `cf` object in `fetch()`, you can override specific Cache Rules settings by:
1. **Setting custom cache options**: Pass cache properties in the `cf` object as the second argument to `fetch()` to override default Cache Rules.
2. **Dynamic cache control**: Apply different caching strategies based on request headers, cookies, or other runtime conditions.
3. **Per-request customization**: Bypass or modify Cache Rules for individual requests while maintaining default behavior for others.
4. **Programmatic cache management**: Implement complex caching logic that adapts to your application's needs.
#### What can be configured
Workers can override the following Cache Rules settings through the `cf` object:
* **`cacheEverything`**: Treat all content as static and cache all file types beyond the default cached content.
* **`cacheTtl`**: Set custom time-to-live values in seconds for cached content at the edge, regardless of origin headers.
* **`cacheTtlByStatus`**: Set different TTLs based on the response status code (for example, `{ "200-299": 86400, 404: 1, "500-599": 0 }`).
* **`cacheKey`**: Customize cache keys to control which requests are treated as the same for caching purposes (Enterprise only).
* **`cacheTags`**: Append additional cache tags for targeted cache purging operations.
#### Benefits
* **Enhanced flexibility**: Customize cache behavior without modifying zone-level Cache Rules.
* **Dynamic optimization**: Adjust caching strategies in real-time based on request context.
* **Simplified configuration**: Reduce the number of Cache Rules needed by handling edge cases programmatically.
* **Improved performance**: Fine-tune cache behavior for specific use cases to maximize hit rates.
#### Get started
To get started, refer to the [Workers Fetch API documentation](https://developers.cloudflare.com/workers/runtime-apis/fetch/) and the [cf object properties documentation](https://developers.cloudflare.com/workers/runtime-apis/request/#the-cf-property-requestinitcfproperties).
## 2025-04-03
**All cache purge methods now available for all plans**
You can now access all Cloudflare cache purge methods — no matter which plan you’re on. Whether you need to update a single asset or instantly invalidate large portions of your site’s content, you now have the same powerful tools previously reserved for Enterprise customers.
**Anyone on Cloudflare can now:**
1. [Purge Everything](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-everything/): Clears all cached content associated with a website.
2. [Purge by Prefix](https://developers.cloudflare.com/cache/how-to/purge-cache/purge_by_prefix/): Targets URLs sharing a common prefix.
3. [Purge by Hostname](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-hostname/): Invalidates content by specific hostnames.
4. [Purge by URL (single-file purge)](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-single-file/): Precisely targets individual URLs.
5. [Purge by Tag](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-tags/): Uses Cache-Tag response headers to invalidate grouped assets, offering flexibility for complex cache management scenarios.
Want to learn how each purge method works, when to use them, or what limits apply to your plan? Dive into our [purge cache documentation](https://developers.cloudflare.com/cache/how-to/purge-cache/) and [API reference](https://developers.cloudflare.com/api/resources/cache/methods/purge/) for all the details.
## 2025-02-12
**Configurable multiplexing HTTP/2 to Origin**
You can now configure HTTP/2 multiplexing settings for origin connections on Enterprise plans. This feature allows you to optimize how Cloudflare manages concurrent requests over HTTP/2 connections to your origin servers, improving cache efficiency and reducing connection overhead.
#### How it works
HTTP/2 multiplexing allows multiple requests to be sent over a single TCP connection. With this configuration option, you can:
1. **Control concurrent streams**: Adjust the maximum number of concurrent streams per connection.
2. **Optimize connection reuse**: Fine-tune connection pooling behavior for your origin infrastructure.
3. **Reduce connection overhead**: Minimize the number of TCP connections required between Cloudflare and your origin.
4. **Improve cache performance**: Better connection management can enhance cache fetch efficiency.
#### Benefits
* **Customizable performance**: Tailor multiplexing settings to your origin's capabilities.
* **Reduced latency**: Fewer connection handshakes improve response times.
* **Lower origin load**: More efficient connection usage reduces server resource consumption.
* **Enhanced scalability**: Better connection management supports higher traffic volumes.
#### Get started
Enterprise customers can configure HTTP/2 multiplexing settings in the [Cloudflare Dashboard](https://dash.cloudflare.com/) or through our [API](https://developers.cloudflare.com/api/).
Important consideration
This setting needs to be tuned carefully for your origin infrastructure. Setting the concurrent stream limit too high can negatively impact performance by saturating the shared TCP connection and overwhelming server processing capacity, leading to increased latency for individual requests.
## 2025-02-04
**Fight CSAM More Easily Than Ever**
You can now implement our **child safety tooling**, the **[CSAM Scanning Tool](https://developers.cloudflare.com/cache/reference/csam-scanning/)**, more easily. Instead of requiring external reporting credentials, you only need a verified email address for notifications to onboard. This change makes the tool more accessible to a wider range of customers.
**How It Works**
When enabled, the tool automatically [hashes images for enabled websites as they enter the Cloudflare cache](https://blog.cloudflare.com/the-csam-scanning-tool/). These hashes are then checked against a database of **known abusive images**.
* **Potential match detected?**
* The **content URL is blocked**, and
* **Cloudflare will notify you** about the found matches via the provided email address.
**Updated Service-Specific Terms**
We have also made updates to our **[Service-Specific Terms](https://www.cloudflare.com/service-specific-terms-application-services/#csam-scanning-tool-terms)** to reflect these changes.
## 2025-01-08
**Smart Tiered Cache optimizes Load Balancing Pools**
You can now achieve higher cache hit rates and reduce origin load when using [Load Balancing](https://developers.cloudflare.com/load-balancing/) with [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/). Cloudflare automatically selects a single, optimal tiered data center for all origins in your Load Balancing Pool.
#### How it works
When you use [Load Balancing](https://developers.cloudflare.com/load-balancing/) with [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/), Cloudflare analyzes performance metrics across your pool's origins and automatically selects the optimal Upper Tier data center for the entire pool. This means:
* **Consistent cache location**: All origins in the pool share the same Upper Tier cache.
* **Higher HIT rates**: Requests for the same content hit the cache more frequently.
* **Reduced origin requests**: Fewer requests reach your origin servers.
* **Improved performance**: Faster response times for cache HITs.
#### Example workflow
```txt
Load Balancing Pool: api-pool
├── Origin 1: api-1.example.com
├── Origin 2: api-2.example.com
└── Origin 3: api-3.example.com
↓
Selected Upper Tier: [Optimal data center based on pool performance]
```
#### Get started
To get started, enable [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) on your zone and configure your [Load Balancing Pool](https://developers.cloudflare.com/load-balancing/).
## 2024-11-20
**Smart Tiered Cache automatically optimizes R2 caching**
You can now reduce latency and lower R2 egress costs automatically when using [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) with [R2](https://developers.cloudflare.com/r2/). Cloudflare intelligently selects a tiered data center close to your R2 bucket location, creating an efficient caching topology without additional configuration.
#### How it works
When you enable [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) for zones using [R2](https://developers.cloudflare.com/r2/) as an origin, Cloudflare automatically:
1. **Identifies your R2 bucket location**: Determines the geographical region where your R2 bucket is stored.
2. **Selects an optimal Upper Tier**: Chooses a data center close to your bucket as the common Upper Tier cache.
3. **Routes requests efficiently**: All cache misses in edge locations route through this Upper Tier before reaching R2.
#### Benefits
* **Automatic optimization**: No manual configuration required.
* **Lower egress costs**: Fewer requests to R2 reduce egress charges.
* **Improved hit ratio**: Common Upper Tier increases cache efficiency.
* **Reduced latency**: Upper Tier proximity to R2 minimizes fetch times.
#### Get started
To get started, enable [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) on your zone using R2 as an origin.
## 2024-11-07
**Stage and test cache configurations safely**
You can now stage and test cache configurations before deploying them to production. Versioned environments let you safely validate cache rules, purge operations, and configuration changes without affecting live traffic.
#### How it works
With versioned environments, you can:
1. **Create staging versions** of your cache configuration.
2. **Test cache rules** in a non-production environment.
3. **Purge staged content** independently from production.
4. **Validate changes** before promoting to production.
This capability integrates with Cloudflare's broader [versioning system](https://developers.cloudflare.com/version-management/), allowing you to manage cache configurations alongside other zone settings.
#### Benefits
* **Risk-free testing**: Validate configuration changes without impacting production.
* **Independent purging**: Clear staging cache without affecting live content.
* **Deployment confidence**: Catch issues before they reach end users.
* **Team collaboration**: Multiple team members can work on different versions.
#### Get started
To get started, refer to the [version management documentation](https://developers.cloudflare.com/version-management/).
Important limitation
Cache Reserve is only supported for your production environment. Staged environments can use standard cache functionality, but Cache Reserve persistence is limited to production deployments.
## 2024-11-07
**Shard cache using custom cache key values**
Enterprise customers can now optimize cache hit ratios for content that varies by device, language, or referrer by **sharding cache** using up to ten values from previously restricted headers with [custom cache keys](https://developers.cloudflare.com/cache/how-to/cache-keys/).
#### How it works
When configuring [custom cache keys](https://developers.cloudflare.com/cache/how-to/cache-keys/), you can now include values from these headers to create distinct cache entries:
* **`accept*` headers** (for example, `accept`, `accept-encoding`, `accept-language`): Serve different cached versions based on content negotiation.
* **`referer` header**: Cache content differently based on the referring page or site.
* **`user-agent` header**: Maintain separate caches for different browsers, devices, or bots.
#### When to use cache sharding
* Content varies significantly by device type (mobile vs desktop).
* Different language or encoding preferences require distinct responses.
* Referrer-specific content optimization is needed.
#### Example configuration
```json
{
"cache_key": {
"custom_key": {
"header": {
"include": ["accept-language", "user-agent"],
"check_presence": ["referer"]
}
}
}
}
```
This configuration creates separate cache entries based on the `accept-language` and `user-agent` headers, while also considering whether the `referer` header is present.
#### Get started
To get started, refer to the [custom cache keys documentation](https://developers.cloudflare.com/cache/how-to/cache-keys/).
Note
While cache sharding can improve hit ratios for specific use cases, overly sharding your cache can reduce overall cache efficiency and negatively impact performance. Carefully evaluate whether sharding benefits your specific traffic patterns.
## 2024-09-05
**One-click Cache Rules templates now available**
You can now create optimized cache rules instantly with **one-click templates**, eliminating the complexity of manual rule configuration.
#### How it works
1. Navigate to **Rules** > **Templates** in your Cloudflare dashboard.
2. Select a template for your use case.
3. Click to apply the template with sensible defaults.
4. Customize as needed for your specific requirements.
#### Available cache templates
* **Cache everything**: Adjust the cache level for all requests.
* **Bypass cache for everything**: Bypass cache for all requests.
* **Cache default file extensions**: Replicate Page Rules caching behavior by making only default extensions eligible for cache.
* **Bypass cache on cookie**: Bypass cache for requests containing specific cookies.
* **Set edge cache time**: Cache responses with status code between 200 and 599 on the Cloudflare edge.
* **Set browser cache time**: Adjust how long a browser should cache a resource.
#### Get started
To get started, go to [**Rules > Templates**](https://dash.cloudflare.com/?to=/:account/:zone/caching/cache-rules) in the dashboard. For more information, refer to the [Cache Rules documentation](https://developers.cloudflare.com/cache/how-to/cache-rules/).
## 2024-07-19
**Regionalized Generic Tiered Cache for higher hit ratios**
You can now achieve higher cache hit ratios with [Generic Global Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#generic-global-tiered-cache). Regional content hashing routes content consistently to the same upper-tier data centers, eliminating redundant caching and reducing origin load.
#### How it works
Regional content hashing groups data centers by region and uses consistent hashing to route content to designated upper-tier caches:
* Same content always routes to the same upper-tier data center within a region.
* Eliminates redundant copies across multiple upper-tier caches.
* Increases the likelihood of cache HITs for the same content.
#### Example
A popular image requested from multiple edge locations in a region:
* **Before**: Cached at 3-4 different upper-tier data centers
* **After**: Cached at 1 designated upper-tier data center
* **Result**: 3-4x fewer cache MISSes, reducing origin load and improving performance
#### Get started
To get started, enable [Generic Global Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#generic-global-tiered-cache) on your zone.
---
title: Get started with Cache · Cloudflare Cache (CDN) docs
description: "Cloudflare makes customer websites faster by storing a copy of the
website's content on the servers of our globally distributed data centers.
Content can be either static or dynamic: static content is “cacheable” or
eligible for caching, and dynamic content is “uncacheable” or ineligible for
caching. The cached copies of content are stored physically closer to users,
optimized to be fast, and do not require recomputing."
lastUpdated: 2026-01-14T11:41:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cache/get-started/
md: https://developers.cloudflare.com/cache/get-started/index.md
---
Cloudflare makes customer websites faster by storing a copy of the website's content on the servers of our globally distributed data centers. Content can be either static or dynamic: static content is “cacheable” or eligible for caching, and dynamic content is “uncacheable” or ineligible for caching. The cached copies of content are stored physically closer to users, optimized to be fast, and do not require recomputing.
Cloudflare caches static content based on the following factors:
* [Caching levels](https://developers.cloudflare.com/cache/how-to/set-caching-levels/)
* [File extension](https://developers.cloudflare.com/cache/concepts/default-cache-behavior/#default-cached-file-extensions)
* Presence of [query strings](https://developers.cloudflare.com/cache/advanced-configuration/query-string-sort/)
* [Origin cache-control headers](https://developers.cloudflare.com/cache/concepts/cache-control/)
* Origin headers that indicate dynamic content
* Cache rules that bypass cache on cookie
Cloudflare only caches resources within the Cloudflare data center that serve the request. Cloudflare does not cache off-site or third-party resources, such as Facebook or Flickr, or content hosted on [unproxied (grey-clouded)](https://developers.cloudflare.com/dns/proxy-status/) DNS records.
## Learn the basics
Discover the benefits of caching with Cloudflare's CDN and understand the default cache behavior.
* [Understand what is a CDN](https://www.cloudflare.com/learning/cdn/what-is-a-cdn/)
* [Understand default cache behavior](https://developers.cloudflare.com/cache/concepts/default-cache-behavior/)
* [Understand the default file types Cloudflare caches](https://developers.cloudflare.com/cache/concepts/default-cache-behavior/#default-cached-file-extensions)
## Make more resources cacheable
Configure your settings to cache static HTML or cache anonymous page views of dynamic content.
* [Customize Caching with Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
* [Specify which resources to cache](https://developers.cloudflare.com/cache/concepts/customize-cache/)
* [Understand Origin Cache Control](https://developers.cloudflare.com/cache/concepts/cache-control/)
* [Cache by device type (Enterprise only)](https://developers.cloudflare.com/cache/how-to/cache-rules/examples/cache-device-type/)
## Improve cache HIT rates
Include or exclude query strings, optimize cache keys, or enable [Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) to improve HIT rates and reduce traffic to your origin.
* [Choose a cache level](https://developers.cloudflare.com/cache/how-to/set-caching-levels/)
* [Enable Tiered Cache with Argo](https://developers.cloudflare.com/cache/how-to/tiered-cache/#enable-tiered-cache)
* [Configure custom cache keys (Enterprise only)](https://developers.cloudflare.com/cache/how-to/cache-keys/)
* [Enable Prefetch URLs (Enterprise only)](https://developers.cloudflare.com/speed/optimization/content/prefetch-urls/)
## Secure your cache configuration
Control resources a client is allowed to load and set access permissions to allow different origins to access your origin’s resources. Protect your site from web cache deception attacks while still caching static assets.
* [Avoid web cache poisoning attacks](https://developers.cloudflare.com/cache/cache-security/avoid-web-poisoning/)
* [Configure Cross-Origin Resource Sharing (CORS)](https://developers.cloudflare.com/cache/cache-security/cors/)
* [Enable Cache Deception Armor](https://developers.cloudflare.com/cache/cache-security/cache-deception-armor/#enable-cache-deception-armor)
## Cloudflare features that can alter your HTML and cacheable objects
To provide Cloudflare services to our customers, we may need to alter your HTML or cached objects to enable the feature or provide optimization.
These code alterations only occur on the cacheable objects found at Cloudflare's edge and do not affect the original source. The changes will also be removed if the specific feature is disabled and the cache is purged.
Review the list of Cloudflare features that function in this manner:
* [Rocket Loader](https://developers.cloudflare.com/speed/optimization/content/rocket-loader/)
* [Polish](https://developers.cloudflare.com/images/polish/)
* [Hotlink Protection](https://developers.cloudflare.com/waf/tools/scrape-shield/hotlink-protection/)
* [Email address obfuscation](https://developers.cloudflare.com/waf/tools/scrape-shield/email-address-obfuscation/)
* [Bot Management JavaScript Detections](https://developers.cloudflare.com/bots/additional-configurations/javascript-detections/)
## Troubleshoot
Resolve common caching concerns.
* [Learn about Cloudflare's cache response statuses](https://developers.cloudflare.com/cache/concepts/cache-responses/)
* [Investigate Cloudflare's cache response with cURL](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/gathering-information-for-troubleshooting-sites/#troubleshoot-requests-with-curl)
* [Diagnose Always Online issues](https://developers.cloudflare.com/cache/troubleshooting/always-online/)
---
title: Concepts · Cloudflare Cache (CDN) docs
description: Review the following topics to learn more about the basic concepts
and components of Cloudflare Cache.
lastUpdated: 2024-09-10T14:21:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/concepts/
md: https://developers.cloudflare.com/cache/concepts/index.md
---
Review the following topics to learn more about the basic concepts and components of Cloudflare Cache.
* [CDN-Cache-Control](https://developers.cloudflare.com/cache/concepts/cdn-cache-control/)
* [Cloudflare cache responses](https://developers.cloudflare.com/cache/concepts/cache-responses/)
* [Customize cache](https://developers.cloudflare.com/cache/concepts/customize-cache/)
* [Default cache behavior](https://developers.cloudflare.com/cache/concepts/default-cache-behavior/)
* [Head Requests and Set-Cookie Headers](https://developers.cloudflare.com/cache/concepts/cache-behavior/)
* [Origin Cache Control](https://developers.cloudflare.com/cache/concepts/cache-control/)
* [Retention vs Freshness (TTL)](https://developers.cloudflare.com/cache/concepts/retention-vs-freshness/)
* [Revalidation and request collapsing](https://developers.cloudflare.com/cache/concepts/revalidation/)
---
title: Glossary · Cloudflare Cache (CDN) docs
description: Review the definitions for terms used across Cloudflare's Cache documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cache/glossary/
md: https://developers.cloudflare.com/cache/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Cache documentation.
| Term | Definition |
| - | - |
| cache | A temporary storage area where frequently accessed data is stored for quick retrieval. |
| cache hit | When a requested piece of content is found in the cache, reducing the need to fetch it from the origin server. |
| cache lock | Cache lock (or mutex) is a mechanism employed by CDN data centers, comprising numerous servers, to prevent the overloading of origin servers. This mechanism ensures that only one server can request a specific file from the origin at any given time, facilitating efficient coordination among the servers. |
| cache miss | When a requested piece of content is not found in the cache, requiring the server to fetch it from the origin server. |
| cached bandwidth (cached egress bandwidth) | The amount of bandwidth served from Cloudflare without hitting the origin server. Cached bandwidth is the sum of all `EdgeResponseBytes` where `CacheCacheStatus` equals `hit`, `stale`, `updating`, `ignored`, or `revalidated`. |
| cached requests | The number of requests served from Cloudflare without having to hit the origin server. Cached requests are the sum of all requests where `CacheCacheStatus` equals `hit`, `stale`, `updating`, `ignored`. This does not include `revalidated` since the request had to be sent to the origin server. |
| caching | The process of storing copies of files or data in a cache to accelerate future requests. |
| dynamic content | Dynamic content refers to website content that changes based on factors specific to the user such as time of visit, location, and device. News websites or social media are examples of this type of content. For this type of website, content has to be fetched from the origin server every time it is requested. |
| edge server | A server located at the edge of a network, typically within a CDN, that serves content to end-users. |
| origin bandwidth (origin egress bandwidth) | The amount of data transferred from the origin server to Cloudflare within a certain period of time. Origin bandwidth is the sum of all `EdgeResponseBytes` where `OriginResponseStatus` does not equal `0`. |
| origin server | The original server where the web content is hosted before it is distributed to edge servers in a CDN. |
| purge | The process of removing outdated content from the cache to make room for updated content and ensure the delivery of the latest content. |
| saved bandwidth (saved egress bandwidth) | The percentage of bandwidth saved by caching on the Cloudflare network. |
| static content | Static content, like images, stylesheets, and JavaScript, remains the same for all users. It can be directly served from the cache without fetching from the origin server because it does not change without manual intervention. |
| time-to-live (TTL) | The duration for which a cached copy of a resource is considered valid before it needs to be refreshed or revalidated. |
| total bandwidth (total egress bandwidth, edge bandwidth) | Total bandwidth is the amount of data transferred from Cloudflare to end users within a certain period of time. Total bandwidth equals the sum of all `EdgeResponseBytes` for a certain period of time. |
| uncached bandwidth (uncached egress bandwidth) | Uncached bandwidth is the amount of bandwidth that is not cached and therefore is served from the origin. Uncached bandwidth is the sum of all `EdgeResponseBytes` where `CacheCacheStatus` does not equal `hit`, `stale`, `updating`, `ignored`, or `revalidated`. |
| uncached requests | Uncached requests are requests that are not cached and therefore are served from the origin server. Uncached requests are the sum of all requests where `CacheCacheStatus` does not equal to `hit`, `stale`, `updating`, or `ignored`. |
---
title: Cache configuration · Cloudflare Cache (CDN) docs
description: Learn how to complete different configuration options to customize
your cache behavior.
lastUpdated: 2024-09-10T14:21:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/how-to/
md: https://developers.cloudflare.com/cache/how-to/index.md
---
Learn how to complete different configuration options to customize your cache behavior.
* [Always Online](https://developers.cloudflare.com/cache/how-to/always-online/)
* [Cache by status code](https://developers.cloudflare.com/cache/how-to/configure-cache-status-code/)
* [Cache keys](https://developers.cloudflare.com/cache/how-to/cache-keys/)
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
* [Caching levels](https://developers.cloudflare.com/cache/how-to/set-caching-levels/)
* [Edge and Browser Cache TTL](https://developers.cloudflare.com/cache/how-to/edge-browser-cache-ttl/)
* [Purge cache](https://developers.cloudflare.com/cache/how-to/purge-cache/)
* [Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/)
---
title: Interaction with Cloudflare products · Cloudflare Cache (CDN) docs
description: Review the following topics to learn more about how Cache interacts
with other Cloudflare products.
lastUpdated: 2024-10-17T18:33:04.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/interaction-cloudflare-products/
md: https://developers.cloudflare.com/cache/interaction-cloudflare-products/index.md
---
Review the following topics to learn more about how Cache interacts with other Cloudflare products.
* [Customize cache behavior with Workers](https://developers.cloudflare.com/cache/interaction-cloudflare-products/workers/)
* [How Workers interact with Cache Rules](https://developers.cloudflare.com/cache/interaction-cloudflare-products/workers-cache-rules/)
* [Enable cache in an R2 bucket](https://developers.cloudflare.com/cache/interaction-cloudflare-products/r2/)
* [Control cache access with WAF and Snippets](https://developers.cloudflare.com/cache/interaction-cloudflare-products/waf-snippets/)
---
title: Performance review · Cloudflare Cache (CDN) docs
description: Review the following content to learn more about cache performance.
lastUpdated: 2024-09-10T14:21:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/performance-review/
md: https://developers.cloudflare.com/cache/performance-review/index.md
---
Review the following content to learn more about cache performance.
* [Cache Analytics](https://developers.cloudflare.com/cache/performance-review/cache-analytics/)
* [Cache performance](https://developers.cloudflare.com/cache/performance-review/cache-performance/)
---
title: Features by plan type · Cloudflare Cache (CDN) docs
description: Cloudflare provides the following features for different plans.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cache/plans/
md: https://developers.cloudflare.com/cache/plans/index.md
---
Cloudflare provides the following features for different [plans](https://www.cloudflare.com/plans/).
## Features
### Always Online
**Link:** [Always Online](https://developers.cloudflare.com/cache/how-to/always-online/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Crawl interval**
Available on all plans
* **Free:** Every 30 days
* **Pro:** Every 15 days
* **Business:** Every 5 days
* **Enterprise:** Every 5 days
### Browser Cache TTL
**Link:** [Browser Cache TTL](https://developers.cloudflare.com/cache/how-to/edge-browser-cache-ttl/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Minimum Browser Cache TTL (Page Rules)**
* **Free:** 2 minutes
* **Pro:** 2 minutes
* **Business:** 2 minutes
* **Enterprise:** 30 seconds
**Minimum Browser Cache TTL**
* **Free:** 1 second
* **Pro:** 1 second
* **Business:** 1 second
* **Enterprise:** 1 second
**Default Browser Cache TTL**
* **Free:** 4 hours
* **Pro:** 4 hours
* **Business:** 4 hours
* **Enterprise:** 4 hours
### Cache analytics
**Link:** [Cache analytics](https://developers.cloudflare.com/cache/performance-review/cache-analytics/)
**Feature availability**
* **Free:** No
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Retention period**
* **Free:** N/A
* **Pro:** 7 days
* **Business:** 30 days
* **Enterprise:** 30 days
### Cache keys
**Link:** [Cache keys](https://developers.cloudflare.com/cache/how-to/cache-keys/)
**Cache deception armor**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Cache by device type**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Ignore query string**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Sort query string**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Query string**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
**Headers**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
**Cookie**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
**Host**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
**User features**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
### Set caching level
**Link:** [Set caching level](https://developers.cloudflare.com/cache/how-to/set-caching-levels/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Cache reserve
**Link:** [Cache reserve](https://developers.cloudflare.com/cache/advanced-configuration/cache-reserve/)
**Feature availability**
* **Free:** Paid add-on
* **Pro:** Paid add-on
* **Business:** Paid add-on
* **Enterprise:** Paid add-on
### Cache Rules
**Link:** [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Number of rules**
* **Free:** 10
* **Pro:** 25
* **Business:** 50
* **Enterprise:** 300
### Cache by status code
**Link:** [Cache by status code](https://developers.cloudflare.com/cache/how-to/configure-cache-status-code/)
**Feature availability**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
### Crawler Hints
**Link:** [Crawler Hints](https://developers.cloudflare.com/cache/advanced-configuration/crawler-hints/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### CSAM Scanning Tool
**Link:** [CSAM Scanning Tool](https://developers.cloudflare.com/cache/reference/csam-scanning/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Development mode
**Link:** [Development mode](https://developers.cloudflare.com/cache/reference/development-mode/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Edge Cache TTL
**Link:** [Edge Cache TTL](https://developers.cloudflare.com/cache/how-to/edge-browser-cache-ttl/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Minimum Edge Cache TTL**
* **Free:** 2 hours
* **Pro:** 1 hour
* **Business:** 1 second
* **Enterprise:** 1 second
### ETag Headers
**Link:** [ETag Headers](https://developers.cloudflare.com/cache/reference/etag-headers/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
### Purge cache
**Link:** [Purge cache](https://developers.cloudflare.com/cache/how-to/purge-cache/)
**Feature availability**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Purge options**
* **Free:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Pro:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Business:** URL, Hostname, Tag, Prefix, and Purge Everything
* **Enterprise:** URL, Hostname, Tag, Prefix, and Purge Everything
### Purge limits for hostname, tag, prefix URL, and purge everything.
**Link:** [Purge limits for hostname, tag, prefix URL, and purge everything.](https://developers.cloudflare.com/cache/how-to/purge-cache/)
**Requests**
Available on all plans
* **Free:** 5 requests per minute
* **Pro:** 5 requests per second
* **Business:** 10 requests per second
* **Enterprise:** 50 requests per second
**Bucket size**
* **Free:** 25
* **Pro:** 25
* **Business:** 50
* **Enterprise:** 500
**Max operations per request**
* **Free:** 100
* **Pro:** 100
* **Business:** 100
* **Enterprise:** 100
### Single file purge
**Link:** [Single file purge](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-single-file/)
**URLs**
Available on all plans
* **Free:** 800 URLs per second
* **Pro:** 1500 URLs per second
* **Business:** 1500 URLs per second
* **Enterprise:** 3000 URLs per second
**Max operations per request**
* **Free:** 100
* **Pro:** 100
* **Business:** 100
* **Enterprise:** 500
### Query string sort
**Link:** [Query string sort](https://developers.cloudflare.com/cache/advanced-configuration/query-string-sort/)
**Feature availability**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
### Tiered cache
**Link:** [Tiered cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/)
**Tiered Cache**
Available on all plans
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Smart Topology**
* **Free:** Yes
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
**Generic Global Topology**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
**Regional Tiered Cache**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
**Custom Topology**
* **Free:** No
* **Pro:** No
* **Business:** No
* **Enterprise:** Yes
### Vary for images
**Link:** [Vary for images](https://developers.cloudflare.com/cache/advanced-configuration/vary-for-images/)
**Feature availability**
* **Free:** No
* **Pro:** Yes
* **Business:** Yes
* **Enterprise:** Yes
---
title: Reference · Cloudflare Cache (CDN) docs
description: Review the reference content to learn more about specific caching
functionality.
lastUpdated: 2024-09-10T14:21:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/reference/
md: https://developers.cloudflare.com/cache/reference/index.md
---
Review the reference content to learn more about specific caching functionality.
* [CDN Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/cdn/)
* [CSAM Scanning Tool](https://developers.cloudflare.com/cache/reference/csam-scanning/)
* [Development Mode](https://developers.cloudflare.com/cache/reference/development-mode/)
* [Using ETag Headers with Cloudflare](https://developers.cloudflare.com/cache/reference/etag-headers/)
---
title: Troubleshooting · Cloudflare Cache (CDN) docs
description: The following topics are useful for troubleshooting Cache issues.
lastUpdated: 2024-09-10T14:21:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cache/troubleshooting/
md: https://developers.cloudflare.com/cache/troubleshooting/index.md
---
The following topics are useful for troubleshooting Cache issues.
* [Always Online](https://developers.cloudflare.com/cache/troubleshooting/always-online/)
---
title: 404 - Page Not Found · Cloudflare China Network docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/china-network/404/
md: https://developers.cloudflare.com/china-network/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Concepts · Cloudflare China Network docs
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/china-network/concepts/
md: https://developers.cloudflare.com/china-network/concepts/index.md
---
* [China Authoritative DNS](https://developers.cloudflare.com/china-network/concepts/china-dns/)
* [Global Acceleration](https://developers.cloudflare.com/china-network/concepts/global-acceleration/)
* [Internet Content Provider (ICP)](https://developers.cloudflare.com/china-network/concepts/icp/)
---
title: FAQ · Cloudflare China Network docs
description: Review FAQs for Cloudflare's China Network.
lastUpdated: 2025-10-24T08:58:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/china-network/faq/
md: https://developers.cloudflare.com/china-network/faq/index.md
---
## Prerequisites and onboarding
### What are the requirements to enable Cloudflare China Network service from Cloudflare?
Refer to [Get started](https://developers.cloudflare.com/china-network/get-started/) for more information.
### Can I use my current account to access Cloudflare China Network service?
Yes, you can use your current Cloudflare account and dashboard.
### What are the requirements for requesting a Cloudflare China Network PoC?
Cloudflare requires that you have a valid [ICP (Internet Content Provider)](https://developers.cloudflare.com/china-network/concepts/icp/) number and content vetting approval from JD Cloud to provide you with a Cloudflare China Network PoC (Proof of Concept). If you are interested in a PoC, please contact your sales team.
## Data storage
### Will my Cloudflare account or configuration information be stored in China?
Cloudflare has taken numerous steps to ensure your security and the integrity of your data in China. Your identification information such as email addresses, password hashes, and billing information are never stored on Cloudflare China Network or shared with the Cloudflare partner except for Zone configuration information and bindings with Cloudflare’s Developer Suite which are stored on the China Network operated by our partners in China upon your enabling the China Service for a particular Zone.
## Compliance
### Does Cloudflare have an MIIT license to provide CDN services in China?
As a US company, Cloudflare does not have a license from China's Ministry of Industry and Information Technology (MIIT). However, Cloudflare's partner JD Cloud has all the licenses required by the MIIT to operate and provide CDN services in China.
### Can Cloudflare or JD Cloud help me to get the ICP?
No, neither Cloudflare nor JD Cloud is responsible for [ICP (Internet Content Provider)](https://developers.cloudflare.com/china-network/concepts/icp/) applications. However, Cloudflare can help provide referrals to ICP partners specialized in ICP applications. For more information, refer to [Obtain an ICP number](https://developers.cloudflare.com/china-network/concepts/icp/#obtain-an-icp-number).
### Why is my ICP filing/license revoked?
The application and revocation of ICP filings or licenses is managed by China's local authorities. Usually, either the customer or the agency processing the ICP application will receive a notification with more details. Cloudflare cannot provide the ICP revocation reasons.
### What would happen if my ICP filing/license got revoked?
Cloudflare's partner JD Cloud and the local authorities continuously track the status of the ICP. If your ICP gets revoked, JD Cloud may terminate or suspend your access to the China Service at any time and without liability, in accordance with China local regulations. To mitigate the impact on your Internet properties, Cloudflare will reroute the traffic for the affected domains to the nearest data centers outside of China.
### What is content vetting and why do I need JD Cloud to vet my domain's content before onboarding?
The JD Cloud network is proxying content inside of China for customers who have purchased Cloudflare China Network. To ensure compliance with China’s Internet regulations and with [JD Cloud's service terms](https://docs.jdcloud.com/cn/product-service-agreement/starshield-terms-of-service), JD Cloud must review the content of all the domains before onboarding those domains to their network. They can approve or reject any domain based on the nature of its content. For more information, contact your sales team.
## Products and features
### How does IPv6 work on China Network?
All sites hosted in Mainland China must have IPv6 enabled. China Network automatically enables IPv6 for domains to fulfill this requirement and it is not possible to disable it. According to internal testing, IPv6 connections in Mainland China are more reliable and offer better latency.
### Is Turnstile available in Mainland China?
[Turnstile](https://developers.cloudflare.com/turnstile/) is not supported in Mainland China. Therefore, both China Network zones and [global zones](https://developers.cloudflare.com/fundamentals/concepts/accounts-and-zones/#zones) with users visiting your content from Mainland China may experience issues with Turnstile.
### Is Pages available in Mainland China?
[Pages](https://developers.cloudflare.com/pages/) is not available in Mainland China due to pages.dev certificate not residing within Mainland China. However, Pages from a global zone may potentially be extended into Mainland China.
---
title: Get started · Cloudflare China Network docs
description: Contact your sales team for more information on these steps.
lastUpdated: 2025-10-23T09:44:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/china-network/get-started/
md: https://developers.cloudflare.com/china-network/get-started/index.md
---
## 1. Contract required services and agree to supplemental terms
1. Ensure that you have a Cloudflare Enterprise plan. If you do not have an Enterprise plan yet, you must upgrade.
2. Add the Cloudflare China Network package (a separate subscription) to your Enterprise plan.
3. Agree to the [China Service Supplemental Terms](https://www.cloudflare.com/supplemental-terms/#china-service).
Contact your sales team for more information on these steps.
## 2. Obtain ICP and vet domain content
1. Obtain [Internet Content Provider filings or licenses](https://developers.cloudflare.com/china-network/concepts/icp/#obtain-an-icp-number) for all the apex domains you wish to onboard.
2. Present valid ICP filings or licenses for the zones you are onboarding.
3. Ensure that your websites [display their ICP number in the page footer](https://developers.cloudflare.com/china-network/concepts/icp/#display-your-icp-number).
4. Prepare the required information for JD Cloud to review your domains' content. JD Cloud, our partner, is required to review and vet the content of all domains on their network before China Network is enabled. You will need to provide the following information:
* Customer and company name
* Domain name
* ICP license/filing number
* A general description of the content of each domain (for example, Marketing website)
* A signed Self Attestation letter (provided by your sales team)
## 3. Onboard your domains to the Cloudflare China Network
After content vetting is complete, [add your domains to Cloudflare](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/).
For first-time enablement of a zone, it will take approximately 24-48 hours to fully onboard to China Network. Afterwards, you can enable and disable China Network within your Cloudflare dashboard.
---
title: Reference · Cloudflare China Network docs
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/china-network/reference/
md: https://developers.cloudflare.com/china-network/reference/index.md
---
* [Available products and features](https://developers.cloudflare.com/china-network/reference/available-products/)
* [Infrastructure](https://developers.cloudflare.com/china-network/reference/infrastructure/)
---
title: Videos · Cloudflare China Network docs
lastUpdated: 2025-08-27T13:31:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/china-network/videos/
md: https://developers.cloudflare.com/china-network/videos/index.md
---
[Introduction to the China Network ](https://developers.cloudflare.com/learning-paths/china-network-overview/series/china-network-main-features-1/)Watch to learn how Cloudflare's China Network can help you improve performance, compliance, and connectivity for your users in Mainland China.
[Accelerate dynamic traffic outside of Mainland China ](https://developers.cloudflare.com/learning-paths/china-network-overview/series/china-express-overview-2/)Watch to learn more about Cloudflare's CDN Global Acceleration (formerly China Express).
---
title: 404 - Page Not Found · Cloudflare Client IP Geolocation docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/client-ip-geolocation/404/
md: https://developers.cloudflare.com/client-ip-geolocation/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About · Cloudflare Client IP Geolocation docs
description: Cloudflare Client IP Geolocation helps you understand where in the
world a given client is located, even if their true client IP address is
obscured by Cloudflare's proxy systems. We offer this service to ensure
customers have high-quality experiences interacting with origins that rely on
geolocation — such as mapping providers — and origin operators can deliver the
right content to the right users. Ensuring origins know where clients are
located avoids problems associated with traditional VPNs that obscure a
consumer’s geolocation and allow circumvention of geographic restrictions on
content.
lastUpdated: 2025-05-19T16:42:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/client-ip-geolocation/about/
md: https://developers.cloudflare.com/client-ip-geolocation/about/index.md
---
Note
Client IP Geolocation is currently in closed Beta testing.
Cloudflare Client IP Geolocation helps you understand where in the world a given client is located, even if their true client IP address is obscured by Cloudflare's proxy systems. We offer this service to ensure customers have high-quality experiences interacting with origins that rely on geolocation — such as mapping providers — and origin operators can deliver the right content to the right users. Ensuring origins know where clients are located avoids problems associated with traditional VPNs that obscure a consumer’s geolocation and allow circumvention of geographic restrictions on content.
**Users cannot opt out of this geolocation support and Cloudflare will always make a best effort to convey geolocation.**
## Simple explanation
When Cloudflare connects to your origin over **IPv4**, we geolocate our VPN users to 1 of 1,000 egress locations (a `cell`). The list of cells is a super set of all the countries in the world and all US Designated Market Areas and includes multiple cells for large metropolitan areas. For all supported cell locations, download [our list](https://api.cloudflare.com/local-ip-ranges.csv).
When Cloudflare connects to your origin over **IPv6**, we geolocate our VPN users to one of thousands of locations distributed across the globe.
If a VPN user tries to use an interposed VPN or proxy system that attempts to hide their location, we share that information with downstream entities.
## Technical explanation
We map our egress IP addresses for our forward-proxy offerings to specific geolocations and continuously share this information with major geolocation database providers like *MaxMind*, *IP 2 Location*, and *Neustar*.
When Cloudflare receives an inbound request from a WARP or 1.1.1.1 user, we first geolocate the IP address that made the connection to Cloudflare. Then, we select an egress IP that maps to the client geolocation. We then discard Client IP information to preserve user privacy but return their true geographic location.
If the Client IP is a known proxy or VPN service without strong commitments to preserving client location, we return an unmapped/unknown location.
Because our cell list includes Designated Market Areas in the United States, you can use the returned geolocation information — or lack of it — to enforce content restrictions when delivering linear or on-demand video content subject to common licensing requirements.
## Example scenario
Jane is a Cloudflare WARP user in Glendive, Montana, USA. She is interested in the privacy benefits of using a VPN. Her client IP address is `108.59.112.0`, which is owned by [Mid-Rivers Telephone Cooperative](https://bgp.he.net/AS11961) and geolocates to 47.0984,-104.7275, approximately.

Jane connects to Cloudflare’s edge using a secure tunnel. Cloudflare operates an anycast network and dictates VPN ingress by anycast. Jane’s VPN traffic lands in the Cloudflare Minneapolis data center, [930km from Glendive](http://www.gcmap.com/mapui?P=GDV-MSP).
A naive geolocation implementation would provide unacceptably inaccurate information. It would have Jane geolocated to Minneapolis, which is in a totally different state — Minnesota instead of Montana — and Designated Marketing Area — Glendive, MT, the [country’s smallest DMA](https://mediatracks.com/resources/nielsen-dma-rankings-2020/), instead of Minneapolis, MN — from her true location. From a content distribution perspective, this level of geolocation is **not acceptable**.
Instead, Cloudflare uses its [own geolocation mapping](#technical-explanation) to provide much more accurate information. Cloudflare’s edge would geolocate Jane’s client IP (`108.59.112.0`) to Glendive and select an egress IP address of `a.b.c.d` from its list of available egress IP addresses based on this geolocation result.
Jane attempts to watch live television via an over-the-top (OTT) video provider. The video provider’s origin sees a connection from `a.b.c.d`. A geolocation lookup on `a.b.c.d` returns Glendale, MT, and Jane is able to access the linear video content because the OTT provider is able to geolocate the VPN traffic to the true client location.
---
title: FAQ · Cloudflare Client IP Geolocation docs
description: If you operate a website or ISP that needs to use IP address
geolocation information for geographic content restriction, consider allowing
IP addresses associated with a VPN.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/client-ip-geolocation/faq/
md: https://developers.cloudflare.com/client-ip-geolocation/faq/index.md
---
Note
Client IP Geolocation is currently in closed Beta testing.
## Website operators
### What does this functionality mean for me as a website operator?
If you operate a website or ISP that needs to use IP address geolocation information for geographic content restriction, consider allowing IP addresses associated with a VPN.
You can now restrict content delivery to Cloudflare VPN users using the same client IP geolocation mechanisms used for non-VPN users.
### How does the above scenario change if I use Cloudflare to secure my infrastructure?
There is significant cross pollination between Cloudflare forward- and reverse-proxy services. When a user connects through Cloudflare proxies to origin infrastructure protected by Cloudflare security tools, our origin-facing tools automatically consume information from our user-facing systems about client geography, IP reputation, and other client metadata. This process happens in a privacy-preserving manner that reduces unnecessary collection of personally identifiable information while ensuring customers can maintain their desired security posture.
WAF custom rules specifying country- or region-level match criteria will match correctly on users passing through our VPN and forward-proxy systems with no action needed from you.
### In the example, what happens when Cloudflare’s Minneapolis data center is removed from service for maintenance?
The [example scenario](https://developers.cloudflare.com/client-ip-geolocation/about/#example-scenario) still provides accurate geolocation data.
Geography-specific egress IPs are not tightly coupled to physical Cloudflare network locations. We continue using geography-specific egress IPs even if the geographically closest network location or locations are rerouted.
### What happens when a user nests or chains VPNs and connects to Cloudflare through a downstream proxy service?
Cloudflare will make best efforts to identify such circumstances and communicate this information upstream to origins. Client IPs will geolocate as `unknown` when the entity that made the initial connection to Cloudflare appears to have originated from an open-proxy service or we are unsure of the location of the user.
### I want greater geographic detail on egress locations. Can you provide it?
Yes! We can provide much finer granularity for origins reachable over IPv6. We encourage adoption of IPv6 for the good of the Internet, as well as for providing much finer detail on user locations to origin operators.
### What incentives does Cloudflare have to ensure location information is accurate?
Cloudflare wants those using our consumer VPN and corporate forward-proxy services to have as smooth an experience as possible. We want our users to have uninterrupted browsing experiences. At the same time, we also want to give origin operators the information they need to distribute the right content to the right users at the right times.
## Cloudflare VPN users
### What does this mean for me as a Cloudflare VPN user?
If you use [Cloudflare WARP](https://developers.cloudflare.com/warp-client/) or [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/), geolocation improves your user experience. Because we communicate your geographic location accurately (but still in a non-identifiable way), you should have accurate, geography-specific experiences and uninterrupted access to the content you are licensed to consume in your local geography.
We also maintain all of our [privacy commitments](https://www.cloudflare.com/trust-hub/privacy-and-data-protection/) regarding your use of our consumer application and will keep your Internet browsing private and secure.
### What if I am a user and want to spoof my location?
Cloudflare does not permit or support the spoofing of location and will never offer such functionality in the future.
---
title: Get started · Cloudflare Client IP Geolocation docs
description: "There are several things you can do to best handle traffic from
Cloudflare VPN and forward-proxy users:"
lastUpdated: 2024-08-16T19:06:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/client-ip-geolocation/get-started/
md: https://developers.cloudflare.com/client-ip-geolocation/get-started/index.md
---
Note
Client IP Geolocation is currently in closed Beta testing.
There are several things you can do to best handle traffic from Cloudflare VPN and forward-proxy users:
* **Origin operators**:
* Do not block IP addresses associated with our VPN and proxy products (see the [About section](https://developers.cloudflare.com/client-ip-geolocation/about/) for more details)
* To get even more accurate geolocation data, ensure your origin is [reachable via IPv6](https://developers.cloudflare.com/client-ip-geolocation/faq/)
* **Geolocation data providers**:
* Regularly pull updated geolocation data from the [Cloudflare API](https://api.cloudflare.com/local-ip-ranges.csv)
* **Users of WARP and 1.1.1.1**:
* Review the [FAQs](https://developers.cloudflare.com/client-ip-geolocation/faq/#cloudflare-vpn-users) and [About section](https://developers.cloudflare.com/client-ip-geolocation/about/) to learn exactly how, how much, and why we share geolocation data
---
title: 404 - Page Not Found · Cloudflare challenges docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-challenges/404/
md: https://developers.cloudflare.com/cloudflare-challenges/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Available Challenges · Cloudflare challenges docs
description: "Refer to the following pages for more information on available
Challenge types:"
lastUpdated: 2025-06-24T17:41:46.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cloudflare-challenges/challenge-types/
md: https://developers.cloudflare.com/cloudflare-challenges/challenge-types/index.md
---
Refer to the following pages for more information on available Challenge types:
* [Interstitial Challenge Pages](https://developers.cloudflare.com/cloudflare-challenges/challenge-types/challenge-pages/)
* [Turnstile](https://developers.cloudflare.com/cloudflare-challenges/challenge-types/turnstile/)
* [JavaScript Detections](https://developers.cloudflare.com/cloudflare-challenges/challenge-types/javascript-detections/)
---
title: Concepts · Cloudflare challenges docs
description: "Refer to the following pages for more information on how Challenges work:"
lastUpdated: 2025-06-24T17:41:46.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cloudflare-challenges/concepts/
md: https://developers.cloudflare.com/cloudflare-challenges/concepts/index.md
---
Refer to the following pages for more information on how Challenges work:
* [How Challenges work](https://developers.cloudflare.com/cloudflare-challenges/concepts/how-challenges-work/)
* [Clearance](https://developers.cloudflare.com/cloudflare-challenges/concepts/clearance/)
---
title: Reference · Cloudflare challenges docs
description: "Refer to the following pages for more information about Cloudflare
Challenges:"
lastUpdated: 2025-10-13T17:48:00.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cloudflare-challenges/reference/
md: https://developers.cloudflare.com/cloudflare-challenges/reference/index.md
---
Refer to the following pages for more information about Cloudflare Challenges:
* [Challenge solve rate (CSR)](https://developers.cloudflare.com/cloudflare-challenges/reference/challenge-solve-rate/)
* [Private Access Tokens (PAT)](https://developers.cloudflare.com/cloudflare-challenges/reference/private-access-tokens/)
* [Supported browsers](https://developers.cloudflare.com/cloudflare-challenges/reference/supported-browsers/)
* [Supported languages](https://developers.cloudflare.com/cloudflare-challenges/reference/supported-languages/)
---
title: Troubleshooting · Cloudflare challenges docs
description: If your hostname is proxied through Cloudflare, visitors may
experience challenges on your webpages.
lastUpdated: 2025-11-05T15:18:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-challenges/troubleshooting/
md: https://developers.cloudflare.com/cloudflare-challenges/troubleshooting/index.md
---
## Common issues
### Proxied hostnames
If your hostname is proxied through Cloudflare, visitors may experience challenges on your webpages.
Cloudflare issues challenges through the [Challenge Platform](https://developers.cloudflare.com/cloudflare-challenges/), which is the same underlying technology powering [Turnstile](https://developers.cloudflare.com/turnstile/).
In contrast to our Challenge page offerings, Turnstile allows you to run challenges anywhere on your site in a less-intrusive way without requiring the use of Cloudflare's CDN.
### Deprecated browser support
Challenges are not supported by Microsoft Internet Explorer. If you are currently using Internet Explorer, try using another modern web browser (Chrome, Safari, Firefox). If you are already using a modern web browser, make sure it is using the latest version.
### Referer header
Your visitor's HTTP request contains a referer header set to the website that they came from. When they encounter and solve a Challenge Page, the request with the referer is sent to the origin, and the response to the request is served to the user. The JavaScript on the response page may read the value of `document.referer`, but it will not be accurate.
For example, a visitor coming from a given website is challenged by a [WAF rule](https://developers.cloudflare.com/waf/custom-rules/) via an interstitial Challenge Page served by your domain. Once the visitor loads the website's home page, the `document.referer` value is your domain, not the origin website.
This affects tools like Google Analytics, which reads the referer from JavaScript, since it replaces the previous website that visitors came from.
You can add tracking scripts, such as the Google Tag Manager Javascript, within an existing [Challenge Page](https://developers.cloudflare.com/rules/custom-errors/) to capture the correct referer header on the initial request.
```js
```
### Cross-origin resource sharing (CORS) preflight requests
Cross-origin resource sharing (CORS) preflight requests, or `OPTIONS`, exclude user credentials that include cookies. As a result, the `cf_clearance` cookie will not be sent with the request, causing it to fail to bypass a Challenge Page (Non-interactive, Managed, or Interactive Challenge).
### Challenges on Cloudflare-protected sites
Cloudflare issues Challenges to website visitors to protect against malicious activity, such as bot attacks and DDoS attempts. If a legitimate human visitor is unexpectedly challenged, the reason typically stems from a security feature flagging their request.
| Source | Description |
| - | - |
| High threat score | IP addresses with a high-risk score trigger Challenges. |
| IP reputation | If your IP has a history of suspicious activity, it may be flagged. |
| Bot detection | Automated traffic resembling bots is filtered by Cloudflare. |
| Web Application Firewall (WAF) custom rules | Site owners may set rules targeting specific regions or user agents. |
| Browser Integrity Check | Cloudflare verifies that browsers meet certain standards. |
| Challenge Passage | Technologies like Privacy Pass reduce the frequency of repeated Challenges. |
To avoid repeated Challenges, visitors can take the following steps to ensure their environment does not trigger security checks:
* Ensure your web browser is updated to the latest stable version for full compatibility with modern challenge technologies.
* Temporarily disable browser extensions, such as ad blockers or privacy tools, that may block standard browser headers or the necessary Challenge scripts.
* If your IP address has a poor reputation (often seen with shared VPNs or corporate proxies), try switching to a different, trusted network connection.
### Allowlist traffic from mitigation actions
If you need to prevent a **Block** or **Challenge** action from being applied to specific requests, such as known search engine crawlers, monitoring services, or internal APIs, you must configure an exclusion using [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/).
Cloudflare supports two primary methods for creating these exclusions:
#### 1. Use a Skip rule (recommended)
The most robust method for creating an exception is to create a custom rule with the **Skip** action. This allows matching requests to bypass certain security features, including Bot Management and other WAF rules.
Note
Due to the evaluation order, **Skip** rules must be positioned before the **Block** or **Challenge** rule they are designed to bypass.
Example
Block Amazon Web Services (AWS) and Google Cloud Platform (GCP) because of large volumes of undesired traffic, but allow Googlebot and other known bots that Cloudflare validates.
* Basic rule, no exclusion:
* **Expression**: `(ip.src.asnum in {16509 15169} and not cf.client.bot)`
* **Action**: Block (or a challenge action)
* Rule that excludes IP addresses from being blocked or challenged:
* **Expression**: `(ip.src.asnum in {16509 15169} and not cf.client.bot) and not (ip.src in {192.0.2.1 198.51.100.42 203.0.113.0/24})`
* **Action**: Block (or a challenge action)
* Two rules to skip remaining custom rules for specific IPs and block the rest.
1. Rule 1:
* Expression: `ip.src in {192.0.2.1 198.51.100.42 203.0.113.0/24}`
* Action: Skip > All remaining custom rules
2. Rule 2:
* Expression: `(ip.src.asnum in {16509 15169} and not cf.client.bot)`
* Action: Block (or a challenge action)
#### 2. Modify the Rule Expression
You can refine the expression of a **Block** or **Challenge** rule to directly exclude known good traffic by using the logical not operator with an exclusion list, such as an IP list, country code, or ASN.
This approach is useful for simple exclusions but can make complex rules more difficult to maintain than separate **Skip** rules.
Example
Exclude multiple IP addresses from a **Block** or **Challenge** rule that assesses attack score.
* Basic rule, no exclusion:
* **Expression**: `(http.host eq "example.com" and cf.waf.score lt 20)`
* **Action**: Block (or a challenge action)
* Rule that excludes IP addresses from being blocked/challenged:
* **Expression**: `(http.host eq "example.com" and cf.waf.score lt 20) and not (ip.src in {192.0.2.1 198.51.100.42 203.0.113.0/24})`
* **Action**: Block (or a challenge action)
* Two rules to skip remaining custom rules for specific IPs and block the rest.
1. Rule 1:
* Expression: `ip.src in {192.0.2.1 198.51.100.42 203.0.113.0/24}`
* Action: Skip > All remaining custom rules
2. Rule 2:
* Expression: `(http.host eq "example.com" and cf.waf.score lt 20)`
* Action: Block (or a challenge action)
---
title: 404 - Page Not Found · Cloudflare for Platforms docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-for-platforms/404/
md: https://developers.cloudflare.com/cloudflare-for-platforms/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Cloudflare for SaaS · Cloudflare for Platforms docs
description: Cloudflare for SaaS allows you to extend the security and
performance benefits of Cloudflare's network to your customers via their own
custom or vanity domains.
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/
md: https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/index.md
---
Cloudflare for SaaS allows you to extend the security and performance benefits of Cloudflare's network to your customers via their own custom or vanity domains.
As a SaaS provider, you may want to support subdomains under your own zone in addition to letting your customers use their own domain names with your services. For example, a customer may want to use their vanity domain `app.customer.com` to point to an application hosted on your Cloudflare zone `service.saas.com`. Cloudflare for SaaS allows you to increase security, performance, and reliability of your customers' domains.
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
## Benefits
When you use Cloudflare for SaaS, it helps you to:
* Provide custom domain support.
* Keep your customers' traffic encrypted.
* Keep your customers online.
* Facilitate fast load times of your customers' domains.
* Gain insight through traffic analytics.
## Limitations
If your customers already have their applications on Cloudflare, they cannot control some Cloudflare features for hostnames managed by your Custom Hostnames configuration, including:
* Argo
* Early Hints
* Page Shield
* Spectrum
* Wildcard DNS
## How it works
As the SaaS provider, you can extend Cloudflare's products to customer-owned custom domains by adding them to your zone [as custom hostnames](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/domain-support/). Through a suite of easy-to-use products, Cloudflare for SaaS routes traffic from custom hostnames to an origin, set up on your domain. Cloudflare for SaaS is highly customizable. Three possible configurations are shown below.
### Standard Cloudflare for SaaS configuration:
Custom hostnames are routed to a default origin server called fallback origin. This configuration is available on all plans.
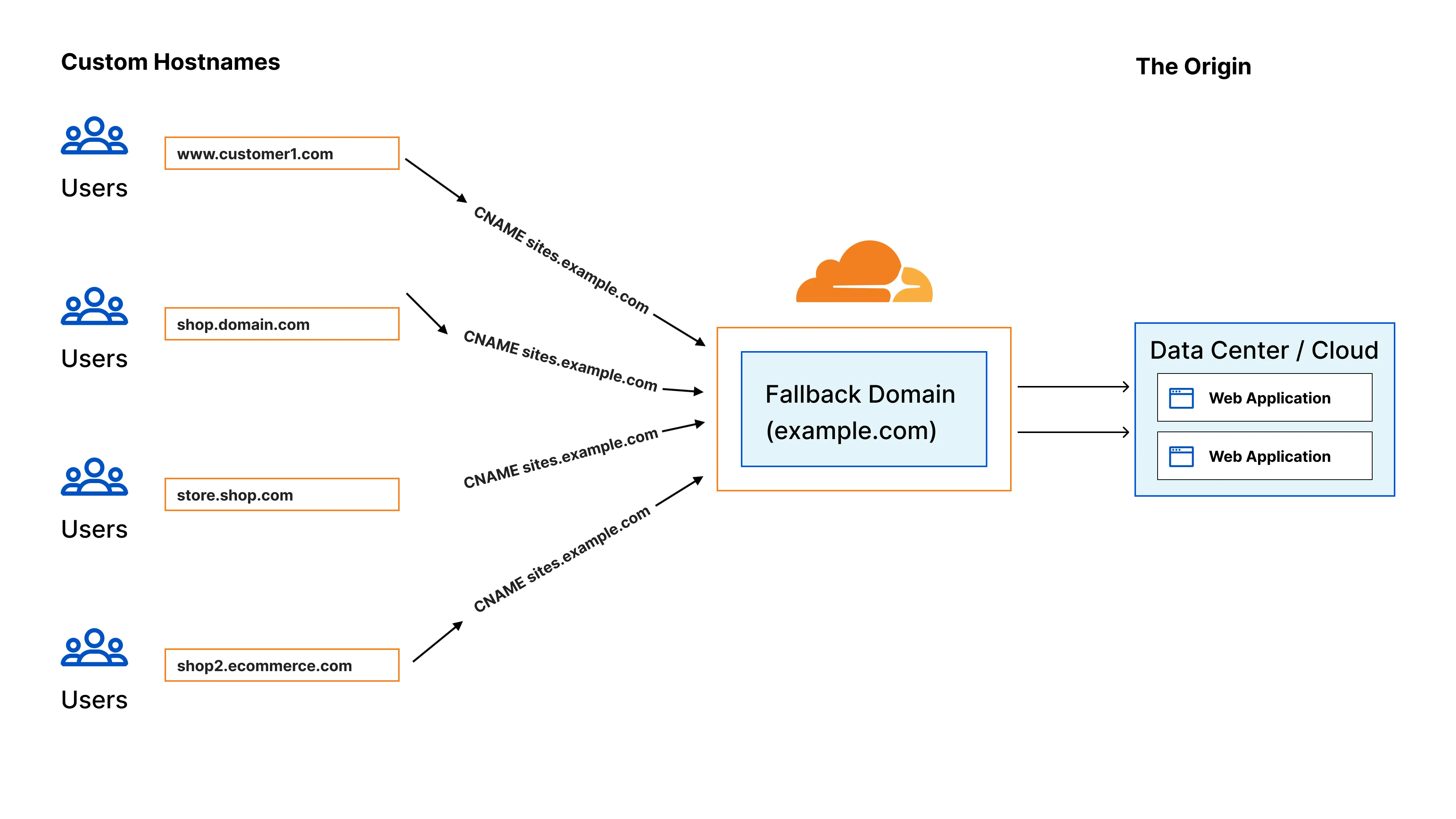
### Cloudflare for SaaS with Apex Proxying:
This allows you to support apex domains even if your customers are using a DNS provider that does not allow a CNAME at the apex. This is available as an add-on for Enterprise plans. For more details, refer to [Apex Proxying](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/advanced-settings/apex-proxying/).
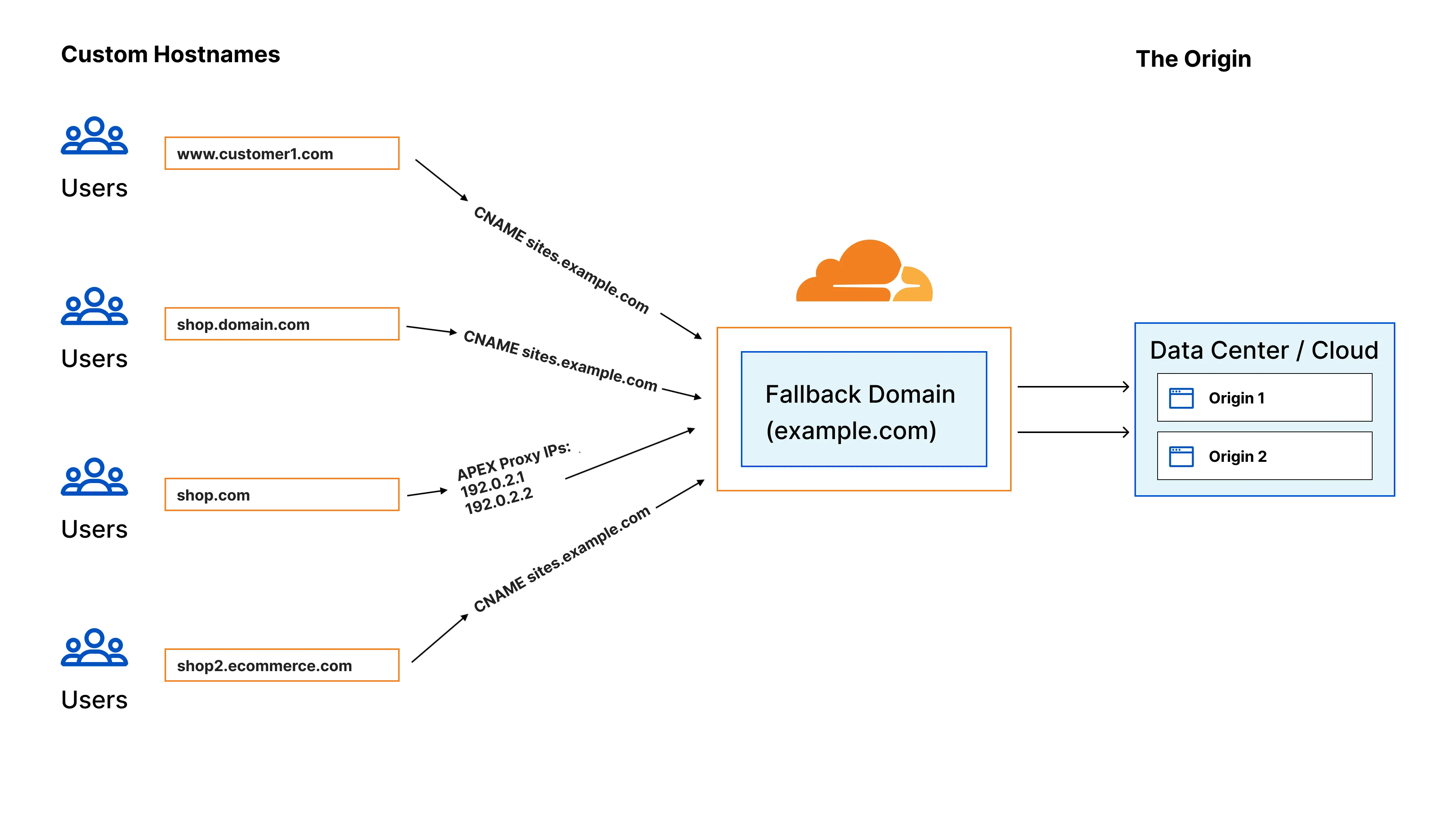
### Cloudflare for SaaS with BYOIP:
This allows you to support apex domains even if your customers are using a DNS provider that does not allow a CNAME at the apex. Also, you can point to your own IPs if you want to bring an IP range to Cloudflare (instead of Cloudflare provided IPs). This is available as an add-on for Enterprise plans.
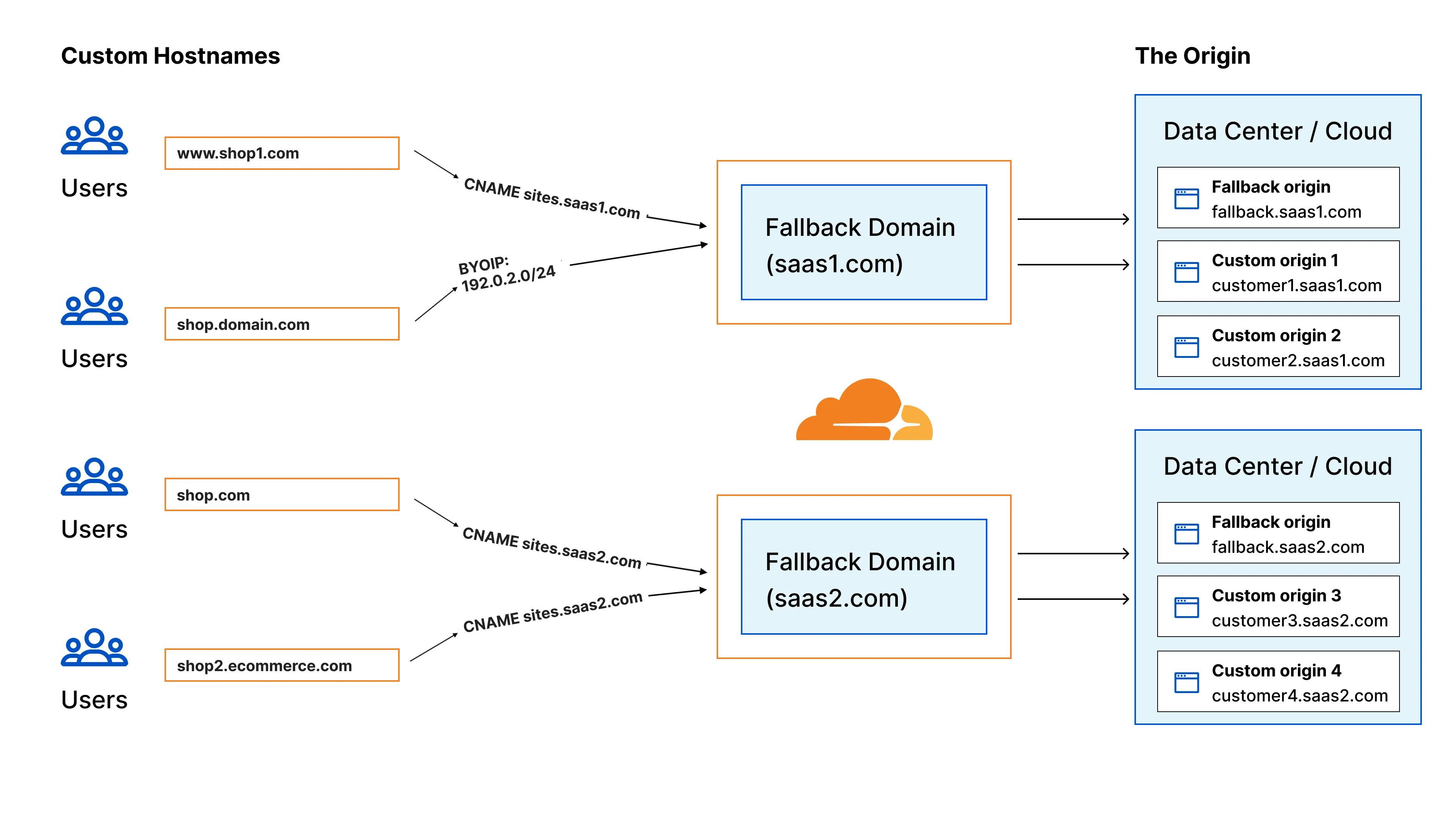
## Availability
Cloudflare for SaaS is bundled with non-Enterprise plans and available as an add-on for Enterprise plans. For more details, refer to [Plans](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/plans/).
## Next steps
[Get started](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/getting-started/)
[Learn more](https://blog.cloudflare.com/introducing-ssl-for-saas/)
---
title: Workers for Platforms · Cloudflare for Platforms docs
description: Workers for Platforms lets you run untrusted code written by your
customers, or by AI, in a secure hosted sandbox. Each customer runs code in
their own Worker, a secure and isolated environment.
lastUpdated: 2025-12-29T17:29:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/
md: https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/index.md
---
Build a multi-tenant platform that runs untrusted code in secure, isolated sandboxes.
Workers for Platforms lets you run untrusted code written by your customers, or by AI, in a secure hosted sandbox. Each customer runs code in their own Worker, a secure and isolated environment.
## When to use Workers for Platforms
Use Workers for Platforms when you need to:
* **Run untrusted code at scale** - Execute code written by your customers or generated by AI in a secure sandbox, with the ability to deploy an unlimited number of applications.
* **Build multi-tenant platforms** - Give each customer their own isolated compute environment with complete separation between tenants.
* **Extend Cloudflare's developer platform to your customers** - Use [bindings](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/bindings/) to give each customer access to KV stores, D1 databases, R2 storage, and more. Your customers get the same powerful tools, managed through your platform.
* **Give each application its own domain** - Host applications under a subdomain of your domain (for example, `customer-name.myplatform.com`) or integrate with [custom hostnames](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/domain-support/) to allow customers to use their own domains.
## Features
Workers for Platforms provides tools to manage and control your customers' code:
* **[Custom limits](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/custom-limits/)** - Set per-customer limits on CPU time and subrequests.
* **[Observability](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/observability/)** - Collect logs and metrics across all user Workers in your namespace. Export to third-party platforms like Datadog, Splunk, and Grafana.
* **[Tags](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/tags/)** - Organize, search, and filter user Workers by custom tags like customer ID, plan type, or environment.
***
## Reference architectures
Explore reference architectures that use Workers for Platforms:
[Programmable Platforms](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[Workers for Platforms provide secure, scalable, cost-effective infrastructure for programmable platforms with global reach.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[AI Vibe Coding Platform](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/)
[Cloudflare's low-latency, fully serverless compute platform, Workers offers powerful capabilities to enable A/B testing using a server-side implementation.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/)
***
## Get started
[Get started](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/get-started/)
Set up a dispatch namespace, dynamic dispatch Worker, and user Worker.
[How Workers for Platforms works](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/)
Understand the architecture: dispatch namespaces, dynamic dispatch Workers, user Workers, and outbound Workers.
---
title: 404 - Page Not Found · Cloudflare One docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/404/
md: https://developers.cloudflare.com/cloudflare-one/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Access controls · Cloudflare One docs
description: Learn how to secure your self-hosted and SaaS applications with
Zero Trust policies.
lastUpdated: 2025-10-23T19:01:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/access-controls/
md: https://developers.cloudflare.com/cloudflare-one/access-controls/index.md
---
Learn how to secure your self-hosted and SaaS applications with Zero Trust policies.
* [Applications](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/)
* [Policies](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
* [AI controls](https://developers.cloudflare.com/cloudflare-one/access-controls/ai-controls/)
* [Service credentials](https://developers.cloudflare.com/cloudflare-one/access-controls/service-credentials/)
* [Access settings](https://developers.cloudflare.com/cloudflare-one/access-controls/access-settings/)
* [Event subscriptions](https://developers.cloudflare.com/cloudflare-one/access-controls/event-subscriptions/)
Refer to our [reference architecture](https://developers.cloudflare.com/reference-architecture/architectures/sase/) for an understanding on how to architect a Zero Trust and SASE solution.
---
title: Account limits · Cloudflare One docs
description: This page lists the default account limits for rules, applications,
fields, and other features. These limits may be increased on Enterprise
accounts. To request a limit increase, contact your account team.
lastUpdated: 2026-01-30T22:09:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/account-limits/
md: https://developers.cloudflare.com/cloudflare-one/account-limits/index.md
---
This page lists the default account limits for rules, applications, fields, and other features. These limits may be increased on Enterprise accounts. To request a limit increase, contact your account team.
## Access
| Feature | Limit |
| - | - |
| Applications | 500 |
| Audit Logpush jobs | 5 |
| Email addresses per rule | 1,000 |
| Rule groups | 300 |
| Rules per rule group | 1,000 |
| IP addresses per rule | 1,000 |
| mTLS root certificates | 50 |
| Service tokens | 50 |
| Identity providers | 50 |
| Reusable policies | 500 |
| Rules per application | 1,000 |
| Domains per application | 5 |
| Infrastructure targets | 5,000 |
| MCP portals | 20 |
| MCP servers per portal | 10 |
## Gateway
| Feature | Limit |
| - | - |
| DNS policies per account | 500 |
| Network policies per account | 500 |
| HTTP policies per account | 500 |
| Egress policies per account | 500 |
| Resolver policies per account | 500 |
| DNS locations | 250 |
| Source IP CIDRs per DNS location | 1,500 |
| Concurrent streams for HTTP/2 connections | 256 |
| Proxy endpoints | 500 |
| Source IP CIDRs per proxy endpoint | 2,000 |
| Lists | 100 |
| Entries per list (Standard users) | 1,000 |
| Entries per list (Enterprise users) | 5,000 |
| List API requests per minute | 600 |
| DNS Logpush jobs | 5 |
| HTTP Logpush jobs | 5 |
## Data Loss Prevention (DLP)
| Feature | Limit |
| - | - |
| Custom entries | 25 |
| Exact Data Match cells per spreadsheet | 100,000 |
| Custom Wordlist keywords per spreadsheet | 200 |
| Custom Wordlist keywords per account | 1,000 |
| Dataset cells per account | 1,000,000 |
## Cloudflare Tunnel
| Feature | Limit |
| - | - |
| `cloudflared` tunnels per account | 1,000 |
| WARP Connectors per account | 10 |
| Routes (CIDR routes + Hostname routes) per account | 1,000 |
| Active `cloudflared` replicas per tunnel | 25 |
| Virtual networks per account | 1,000 |
## Digital Experience Monitoring (DEX)
| Feature | Limit |
| - | - |
| DEX Tests per account | Zero Trust Free: 10 Zero Trust Standard: 30 Zero Trust Enterprise: 50 |
| Remote captures per day | Zero Trust Free: 100 Zero Trust Standard: 200 Zero Trust Enterprise: 800 |
## Certificates
| Feature | Limit |
| - | - |
| Active certificates | 10 |
| Certificates generated per day | 3 |
| Custom certificates | 5 |
## Maximum number of characters
| Feature | Character limit |
| - | - |
| Application name | 350 |
| Group name | 350 |
| mTLS certificates name | 350 |
| Service token name | 350 |
| IdP name | 350 |
| Target name | 255 |
| Application URL | 63 |
| Team domain | 63 |
| Gateway API policy expression | 140,000 |
## WARP
| Feature | Limit |
| - | - |
| Characters per device profile expression | 10,000 |
| Combined Split Tunnel and Local Domain Fallback entries per device profile | 1,000 |
| Device IP assignments per account | 30 |
---
title: API and Terraform · Cloudflare One docs
description: "You can manage your Cloudflare Zero Trust configuration using the
API or Terraform. For more information, refer to the following links:"
lastUpdated: 2025-11-21T23:11:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/api-terraform/
md: https://developers.cloudflare.com/cloudflare-one/api-terraform/index.md
---
You can manage your Cloudflare Zero Trust configuration using the API or Terraform. For more information, refer to the following links:
* [API reference](https://developers.cloudflare.com/api/)
* [Terraform provider reference](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Terraform how-to documentation](https://developers.cloudflare.com/terraform/)
Detailed API and Terraform examples for Cloudflare Zero Trust are available in our [implementation guides](https://developers.cloudflare.com/cloudflare-one/implementation-guides/) and throughout the Cloudflare Zero Trust documentation.
## Set dashboard to read-only
Super Administrators can lock all settings as read-only in the Cloudflare One dashboard. Read-only mode ensures that all updates for the account are made through the API or Terraform.
To enable read-only mode:
1. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Settings** > **Admin controls**.
2. Enable **Set dashboard to read-only**.
All users, regardless of [user permissions](https://developers.cloudflare.com/cloudflare-one/roles-permissions/), will be prevented from making configuration changes through the UI.
## Scoped API tokens
The administrators managing policies and groups in Cloudflare Zero Trust might be different from those responsible for configuring WAF custom rules or other Cloudflare settings. You can configure scoped API tokens so that team members and automated systems can manage Cloudflare Zero Trust settings without having permission to modify other configurations in Cloudflare.
You can create a scoped API token [via the dashboard](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) or [via the API](https://developers.cloudflare.com/fundamentals/api/how-to/create-via-api/). For a list of available token permissions, refer to [API token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/).
---
title: Changelog · Cloudflare One docs
description: Review recent changes to Cloudflare One.
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/changelog/
md: https://developers.cloudflare.com/cloudflare-one/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/cloudflare-one.xml)
## 2026-01-30
[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**BGP over GRE and IPsec tunnels**
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using IPsec and GRE tunnel on-ramps (beta).
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via IPsec and GRE tunnel on-ramps.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
For configuration details, refer to:
* [Configure BGP routes for Magic WAN](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes)
* [Configure BGP routes for Magic Transit](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes)
## 2026-01-27
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2026.1.89.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes, improvements, and new features.
**Changes and improvements**
* Improvements to [multi-user mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/). Fixed an issue where when switching from a pre-login registration to a user registration, Mobile Device Management (MDM) configuration association could be lost.
* Added a new feature to [manage NetBIOS over TCP/IP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#netbios-over-tcpip) functionality on the Windows client. NetBIOS over TCP/IP on the Windows client is now disabled by default and can be enabled in [device profile settings](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/device-profiles/).
* Fixed an issue causing failure of the [local network exclusion](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#allow-users-to-enable-local-network-exclusion) feature when configured with a timeout of `0`.
* Improvement for the Windows [client certificate posture check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/) to ensure logged results are from checks that run once users log in.
* Improvement for more accurate reporting of device colocation information in the Cloudflare One dashboard.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2026-01-27
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2026.1.89.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue causing failure of the [local network exclusion](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#allow-users-to-enable-local-network-exclusion) feature when configured with a timeout of `0`.
* Improvement for more accurate reporting of device colocation information in the Cloudflare One dashboard.
## 2026-01-27
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Configure Cloudflare source IPs (beta)**
Cloudflare source IPs are the IP addresses used by Cloudflare services (such as Load Balancing, Gateway, and Browser Isolation) when sending traffic to your private networks.
For customers using legacy mode routing, traffic to private networks is sourced from public Cloudflare IPs, which may cause IP conflicts. For customers using Unified Routing mode (beta), traffic to private networks is sourced from dedicated, non-Internet-routable private IPv4 range to ensure:
* Symmetric routing over private network connections
* Proper firewall state preservation
* Private traffic stays on secure paths
Key details:
* **IPv4**: Sourced from `100.64.0.0/12` by default, configurable to any `/12` CIDR
* **IPv6**: Sourced from `2606:4700:cf1:5000::/64` (not configurable)
* **Affected connectors**: GRE, IPsec, CNI, WARP Connector, and WARP Client (Cloudflare Tunnel is not affected)
Configuring Cloudflare source IPs requires Unified Routing (beta) and the `Cloudflare One Networks Write` permission.
For configuration details, refer to [Configure Cloudflare source IPs](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-cloudflare-source-ips/).
## 2026-01-15
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
**Verify WARP Connector connectivity with a simple ping**
We have made it easier to validate connectivity when deploying [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) as part of your [software-defined private network](https://developers.cloudflare.com/reference-architecture/architectures/sase/#connecting-networks).
You can now `ping` the WARP Connector host directly on its LAN IP address immediately after installation. This provides a fast, familiar way to confirm that the Connector is online and reachable within your network before testing access to downstream services.
Starting with [version 2025.10.186.0](https://developers.cloudflare.com/changelog/2026-01-13-warp-linux-ga/), WARP Connector responds to traffic addressed to its own LAN IP, giving you immediate visibility into Connector reachability.
Learn more about deploying [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) and building private network connectivity with [Cloudflare One](https://developers.cloudflare.com/cloudflare-one/).
## 2026-01-15
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic Firewall ](https://developers.cloudflare.com/magic-firewall/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/)
**Network Services navigation update**
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

## 2026-01-15
[Risk Score](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)
**Support for CrowdStrike device scores in User Risk Scoring**
Cloudflare One has expanded its \[User Risk Scoring] (/cloudflare-one/insights/risk-score/) capabilities by introducing two new behaviors for organizations using the \[CrowdStrike integration] (/cloudflare-one/integrations/service-providers/crowdstrike/).
Administrators can now automatically escalate the risk score of a user if their device matches specific CrowdStrike Zero Trust Assessment (ZTA) score ranges. This allows for more granular security policies that respond dynamically to the health of the endpoint.
New risk behaviors The following risk scoring behaviors are now available:
* CrowdStrike low device score: Automatically increases a user's risk score when the connected device reports a "Low" score from CrowdStrike.
* CrowdStrike medium device score: Automatically increases a user's risk score when the connected device reports a "Medium" score from CrowdStrike.
These scores are derived from \[CrowdStrike device posture attributes] (/cloudflare-one/integrations/service-providers/crowdstrike/#device-posture-attributes), including OS signals and sensor configurations.
## 2026-01-13
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.10.186.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features. New features include the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/), and a new WARP client device posture check for [Antivirus](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/antivirus/).
**Changes and improvements**
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
* Fixed an issue that caused occasional audio degradation and increased CPU usage on Windows by optimizing route configurations for large [domain-based split tunnel rules](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/split-tunnels/#domain-based-split-tunnels).
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where sending large messages to the daemon by Inter-Process Communication (IPC) could cause the daemon to fail and result in service interruptions.
* Added support for a new WARP client device posture check for [Antivirus](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/antivirus/). The check confirms the presence of an antivirus program on a Windows device with the option to check if the antivirus is up to date.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2026-01-13
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.10.186.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features, including the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/).
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
## 2026-01-13
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.10.186.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features, including the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/).
WARP client version 2025.8.779.0 introduced an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com).
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* Linux [disk encryption posture check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/disk-encryption/) now supports non-filesystem encryption types like `dm-crypt`.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where the GUI becomes unresponsive when the **Re-Authenticate in browser** button is clicked.
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
## 2026-01-12
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Enhanced visibility for post-delivery actions**
The Action Log now provides enriched data for post-delivery actions to improve troubleshooting. In addition to success confirmations, failed actions now display the targeted Destination folder and a specific failure reason within the Activity field.
Note
Error messages will vary depending on whether you are using Google Workspace or Microsoft 365.

This update allows you to see the full lifecycle of a failed action. For instance, if an administrator tries to move an email that has already been deleted or moved manually, the log will now show the multiple retry attempts and the specific destination error.
This applies to all Email Security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
## 2026-01-08
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Cloudflare admin activity logs capture creation of DNS over HTTP (DoH) users**
Cloudflare [admin activity logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) now capture each time a [DNS over HTTP (DoH) user](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/dns-over-https/) is created.
These logs can be viewed from the [Cloudflare One dashboard](https://one.dash.cloudflare.com/), pulled via the [Cloudflare API](https://developers.cloudflare.com/api/), and exported through [Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/).
## 2025-12-31
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Breakout traffic visibility via NetFlow**
Magic WAN Connector now exports NetFlow data for breakout traffic to Magic Network Monitoring (MNM), providing visibility into traffic that bypasses Cloudflare's security filtering.
This feature allows you to:
* Monitor breakout traffic statistics in the Cloudflare dashboard.
* View traffic patterns for applications configured to bypass Cloudflare.
* Maintain visibility across all traffic passing through your Magic WAN Connector.
For more information, refer to [NetFlow statistics](https://developers.cloudflare.com/magic-wan/analytics/netflow-analytics/).
## 2025-12-17
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**Shadow IT - domain level SaaS analytics**
Zero Trust has again upgraded its **Shadow IT analytics**, providing you with unprecedented visibility into your organizations use of SaaS tools. With this dashboard, you can review who is using an application and volumes of data transfer to the application.
With this update, you can review data transfer metrics at the domain level, rather than just the application level, providing more granular insight into your data transfer patterns.

These metrics can be filtered by all available filters on the dashboard, including user, application, or content category.
Both the analytics and policies are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
## 2025-12-16
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New duplicate action for supported Cloudflare One resources**
You can now duplicate specific Cloudflare One resources with a single click from the dashboard.
Initially supported resources:
* Access Applications
* Access Policies
* Gateway Policies
To try this out, simply click on the overflow menu (⋮) from the resource table and click *Duplicate*. We will continue to add the Duplicate action for resources throughout 2026.
## 2025-12-09
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.10.118.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where sending large messages to the WARP daemon by Inter-Process Communication (IPC) could cause WARP to crash and result in service interruptions.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-12-09
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.10.118.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
## 2025-12-03
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Reclassifications to Submissions**
We have updated the terminology “Reclassify” and “Reclassifications” to “Submit” and “Submissions” respectively. This update more accurately reflects the outcome of providing these items to Cloudflare.
Submissions are leveraged to tune future variants of campaigns. To respect data sanctity, providing a submission does not change the original disposition of the emails submitted.

This applies to all Email Security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-11-18
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Adjustment to Final Disposition Column**
#### Adjustment to Final Disposition column
#### The **Final Disposition** column in **Submissions** > **Team Submissions** tab is changing for non-Phishguard customers.
#### What's Changing
* Column will be called **Status** instead of **Final Disposition**
* Column status values will now be: **Submitted**, **Accepted** or **Rejected**.
#### Next Steps
We will listen carefully to your feedback and continue to find comprehensive ways to communicate updates on your submissions. Your submissions will continue to be addressed at an even greater rate than before, fuelling faster and more accurate email security improvement.
## 2025-11-17
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New Cloudflare One Navigation and Product Experience**
The Zero Trust dashboard and navigation is receiving significant and exciting updates. The dashboard is being restructured to better support common tasks and workflows, and various pages have been moved and consolidated.
There is a new guided experience on login detailing the changes, and you can use the Zero Trust dashboard search to find product pages by both their new and old names, as well as your created resources. To replay the guided experience, you can find it in Overview > Get Started.

Notable changes
* Product names have been removed from many top-level navigation items to help bring clarity to what they help you accomplish. For example, you can find Gateway policies under ‘Traffic policies' and CASB findings under ‘Cloud & SaaS findings.'
* You can view all analytics, logs, and real-time monitoring tools from ‘Insights.'
* ‘Networks' better maps the ways that your corporate network interacts with Cloudflare. Some pages like Tunnels, are now a tab rather than a full page as part of these changes. You can find them at Networks > Connectors.
* Settings are now located closer to the tools and resources they impact. For example, this means you'll find your WARP configurations at Team & Resources > Devices.

No changes to our API endpoint structure or to any backend services have been made as part of this effort.
## 2025-11-14
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Generate Cloudflare Access SSH certificate authority (CA) directly from the Cloudflare dashboard**
SSH with [Cloudflare Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/) allows you to use short-lived SSH certificates to eliminate SSH key management and reduce security risks associated with lost or stolen keys.
Previously, users had to generate this certificate by using the [Cloudflare API](https://developers.cloudflare.com/api/) directly. With this update, you can now create and manage this certificate in the [Cloudflare One dashboard](https://one.dash.cloudflare.com) from the **Access controls** > **Service credentials** page.

For more details, refer to [Generate a Cloudflare SSH CA](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/#generate-a-cloudflare-ssh-ca).
## 2025-11-14
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
**New SaaS Security weekly digests with API CASB**
You can now stay on top of your SaaS security posture with the new **CASB Weekly Digest** notification. This opt-in email digest is delivered to your inbox every Monday morning and provides a high-level summary of your organization's Cloudflare API CASB findings from the previous week.
This allows security teams and IT administrators to get proactive, at-a-glance visibility into new risks and integration health without having to log in to the dashboard.
To opt in, navigate to **Manage Account** > **Notifications** in the Cloudflare dashboard to configure the **CASB Weekly Digest** alert type.
#### Key capabilities
* **At-a-glance summary** — Review new high/critical findings, most frequent finding types, and new content exposures from the past 7 days.
* **Integration health** — Instantly see the status of all your connected SaaS integrations (Healthy, Unhealthy, or Paused) to spot API connection issues.
* **Proactive alerting** — The digest is sent automatically to all subscribed users every Monday morning.
* **Easy to configure** — Users can opt in by enabling the notification in the Cloudflare dashboard under **Manage Account** > **Notifications**.
#### Learn more
* Configure [notification preferences](https://developers.cloudflare.com/notifications/) in Cloudflare.
The CASB Weekly Digest notification is available to all Cloudflare users today.
## 2025-11-12
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
**DEX Logpush jobs**
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into WARP device metrics, connectivity, and network performance across your Cloudflare SASE deployment.
We've released four new WARP and DEX device data sets that can be exported via [Cloudflare Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/). These Logpush data sets can be exported to R2, a cloud bucket, or a SIEM to build a customized logging and analytics experience.
1. [DEX Application Tests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dex_application_tests/)
2. [DEX Device State Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dex_device_state_events/)
3. [WARP Config Changes](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/warp_config_changes/)
4. [WARP Toggle Changes](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/warp_toggle_changes/)
To create a new DEX or WARP Logpush job, customers can go to the account level of the Cloudflare dashboard > Analytics & Logs > Logpush to get started.

## 2025-11-11
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.9.558.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features including [Path Maximum Transmission Unit Discovery (PMTUD)](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery). When PMTUD is enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to diagnose connectivity issues.
**Changes and improvements**
* Fixed an inconsistency with [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings in multi-user environments when switching between users.
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to diagnose connectivity issues.
* Fixed an issue where deleting a registration was erroneously reported as having failed.
* Path Maximum Transmission Unit Discovery (PMTUD) may now be used to discover the effective MTU of the connection. This allows the WARP client to improve connectivity optimized for each network. PMTUD is disabled by default. To enable it, refer to the [PMTUD documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery).
* Improvements for the [OS version](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/os-version/) WARP client check. Windows Updated Build Revision (UBR) numbers can now be checked by the client to ensure devices have required security patches and features installed.
* The WARP client now supports Windows 11 ARM-based machines. For information on known limitations, refer to the [Known limitations page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/troubleshooting/known-limitations/#warp-disconnected-on-windows-arm).
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-11-11
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.9.558.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features including [Path Maximum Transmission Unit Discovery (PMTUD)](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery). When PMTUD is enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to diagnose connectivity issues.
**Changes and improvements**
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to diagnose connectivity issues.
* Fixed an issue where deleting a registration was erroneously reported as having failed.
* Path Maximum Transmission Unit Discovery (PMTUD) may now be used to discover the effective MTU of the connection. This allows the WARP client to improve connectivity optimized for each network. PMTUD is disabled by default. To enable it, refer to the [PMTUD documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery).
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-11-11
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.9.558.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features including [Path Maximum Transmission Unit Discovery (PMTUD)](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery). When PMTUD is enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to diagnose connectivity issues.
WARP client version 2025.8.779.0 introduced an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com/).
**Changes and improvements**
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to diagnose connectivity issues.
* Fixed an issue where deleting a registration was erroneously reported as having failed.
* Path Maximum Transmission Unit Discovery (PMTUD) may now be used to discover the effective MTU of the connection. This allows the WARP client to improve connectivity optimized for each network. PMTUD is disabled by default. To enable it, refer to the [PMTUD documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery).
## 2025-11-11
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
**cloudflared proxy-dns command will be removed starting February 2, 2026**
Starting February 2, 2026, the `cloudflared proxy-dns` command will be removed from all new `cloudflared` [releases](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/downloads/).
This change is being made to enhance security and address a potential vulnerability in an underlying DNS library. This vulnerability is specific to the `proxy-dns` command and does not affect any other `cloudflared` features, such as the core [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) service.
The `proxy-dns` command, which runs a client-side [DNS-over-HTTPS (DoH)](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/) proxy, has been an officially undocumented feature for several years. This functionality is fully and securely supported by our actively developed products.
Versions of `cloudflared` released before this date will not be affected and will continue to operate. However, note that our [official support policy](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/downloads/#deprecated-releases) for any `cloudflared` release is one year from its release date.
#### Migration paths
We strongly advise users of this undocumented feature to migrate to one of the following officially supported solutions before February 2, 2026, to continue benefiting from secure [DNS-over-HTTPS](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/).
#### End-user devices
The preferred method for enabling DNS-over-HTTPS on user devices is the [Cloudflare WARP client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/). The WARP client automatically secures and proxies all DNS traffic from your device, integrating it with your organization's [Zero Trust policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) and [posture checks](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/).
#### Servers, routers, and IoT devices
For scenarios where installing a client on every device is not possible (such as servers, routers, or IoT devices), we recommend using the [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/).
Instead of running `cloudflared proxy-dns` on a machine, you can install the WARP Connector on a single Linux host within your private network. This connector will act as a gateway, securely routing all DNS and network traffic from your [entire subnet](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/site-to-internet/) to Cloudflare for [filtering and logging](https://developers.cloudflare.com/cloudflare-one/traffic-policies/).
## 2025-11-06
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Applications to be remapped to the new categories**
We have previously added new application categories to better reflect their content and improve HTTP traffic management: refer to [Changelog](https://developers.cloudflare.com/cloudflare-one/changelog/gateway/#2025-10-28). While the new categories are live now, we want to ensure you have ample time to review and adjust any existing rules you have configured against old categories. The remapping of existing applications into these new categories will be completed by January 30, 2026. This timeline allows you a dedicated period to:
* Review the new category structure.
* Identify any policies you have that target the older categories.
* Adjust your rules to reference the new, more precise categories before the old mappings change. Once the applications have been fully remapped by January 30, 2026, you might observe some changes in the traffic being mitigated or allowed by your existing policies. We encourage you to use the intervening time to prepare for a smooth transition.
**Applications being remappedd**
| Application Name | Existing Category | New Category |
| - | - | - |
| Google Photos | File Sharing | Photography & Graphic Design |
| Flickr | File Sharing | Photography & Graphic Design |
| ADP | Human Resources | Business |
| Greenhouse | Human Resources | Business |
| myCigna | Human Resources | Health & Fitness |
| UnitedHealthcare | Human Resources | Health & Fitness |
| ZipRecruiter | Human Resources | Business |
| Amazon Business | Human Resources | Business |
| Jobcenter | Human Resources | Business |
| Jobsuche | Human Resources | Business |
| Zenjob | Human Resources | Business |
| DocuSign | Legal | Business |
| Postident | Legal | Business |
| Adobe Creative Cloud | Productivity | Photography & Graphic Design |
| Airtable | Productivity | Development |
| Autodesk Fusion360 | Productivity | IT Management |
| Coursera | Productivity | Education |
| Microsoft Power BI | Productivity | Business |
| Tableau | Productivity | Business |
| Duolingo | Productivity | Education |
| Adobe Reader | Productivity | Business |
| AnpiReport | Productivity | Travel |
| ビズリーチ | Productivity | Business |
| doda (デューダ) | Productivity | Business |
| 求人ボックス | Productivity | Business |
| マイナビ2026 | Productivity | Business |
| Power Apps | Productivity | Business |
| RECRUIT AGENT | Productivity | Business |
| シフトボード | Productivity | Business |
| スタンバイ | Productivity | Business |
| Doctolib | Productivity | Health & Fitness |
| Miro | Productivity | Photography & Graphic Design |
| MyFitnessPal | Productivity | Health & Fitness |
| Sentry Mobile | Productivity | Travel |
| Slido | Productivity | Photography & Graphic Design |
| Arista Networks | Productivity | IT Management |
| Atlassian | Productivity | Business |
| CoderPad | Productivity | Business |
| eAgreements | Productivity | Business |
| Vmware | Productivity | IT Management |
| Vmware Vcenter | Productivity | IT Management |
| AWS Skill Builder | Productivity | Education |
| Microsoft Office 365 (GCC) | Productivity | Business |
| Microsoft Exchange Online (GCC) | Productivity | Business |
| Canva | Sales & Marketing | Photography & Graphic Design |
| Instacart | Shopping | Food & Drink |
| Wawa | Shopping | Food & Drink |
| McDonald's | Shopping | Food & Drink |
| Vrbo | Shopping | Travel |
| American Airlines | Shopping | Travel |
| Booking.com | Shopping | Travel |
| Ticketmaster | Shopping | Entertainment & Events |
| Airbnb | Shopping | Travel |
| DoorDash | Shopping | Food & Drink |
| Expedia | Shopping | Travel |
| EasyPark | Shopping | Travel |
| UEFA Tickets | Shopping | Entertainment & Events |
| DHL Express | Shopping | Business |
| UPS | Shopping | Business |
For more information on creating HTTP policies, refer to [Applications and app types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
## 2025-11-06
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Designate WAN link for breakout traffic**
Magic WAN Connector now allows you to designate a specific WAN port for breakout traffic, giving you deterministic control over the egress path for latency-sensitive applications.
With this feature, you can:
* Pin breakout traffic for specific applications to a preferred WAN port.
* Ensure critical traffic (such as Zoom or Teams) always uses your fastest or most reliable connection.
* Benefit from automatic failover to standard WAN port priority if the preferred port goes down.
This is useful for organizations with multiple ISP uplinks who need predictable egress behavior for performance-sensitive traffic.
For configuration details, refer to [Designate WAN ports for breakout apps](https://developers.cloudflare.com/magic-wan/configuration/connector/network-options/application-based-policies/breakout-traffic/#designate-wan-ports-for-breakout-apps).
## 2025-11-06
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Automatic Return Routing (Beta)**
Magic WAN now supports Automatic Return Routing (ARR), allowing customers to configure Magic on-ramps (IPsec/GRE/CNI) to learn the return path for traffic flows without requiring static routes.
Key benefits:
* **Route-less mode**: Static or dynamic routes are optional when using ARR.
* **Overlapping IP space support**: Traffic originating from customer sites can use overlapping private IP ranges.
* **Symmetric routing**: Return traffic is guaranteed to use the same connection as the original on-ramp.
This feature is currently in beta and requires the new Unified Routing mode (beta).
For configuration details, refer to [Configure Automatic Return Routing](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-automatic-return-routing-beta).
## 2025-10-28
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Access private hostname applications support all ports/protocols**
[Cloudflare Access for private hostname applications](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/non-http/self-hosted-private-app/) can now secure traffic on all ports and protocols.
Previously, applying Zero Trust policies to private applications required the application to use HTTPS on port `443` and support Server Name Indicator (SNI).
This update removes that limitation. As long as the application is reachable via a Cloudflare off-ramp, you can now enforce your critical security controls — like single sign-on (SSO), MFA, device posture, and variable session lengths — to any private application. This allows you to extend Zero Trust security to services like SSH, RDP, internal databases, and other non-HTTPS applications.

For example, you can now create a self-hosted application in Access for `ssh.testapp.local` running on port `22`. You can then build a policy that only allows engineers in your organization to connect after they pass an SSO/MFA check and are using a corporate device.
This feature is generally available across all plans.
## 2025-10-28
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
**CASB introduces new granular roles**
Cloudflare CASB (Cloud Access Security Broker) now supports two new granular roles to provide more precise access control for your security teams:
* **Cloudflare CASB Read:** Provides read-only access to view CASB findings and dashboards. This role is ideal for security analysts, compliance auditors, or team members who need visibility without modification rights.
* **Cloudflare CASB:** Provides full administrative access to configure and manage all aspects of the CASB product.
These new roles help you better enforce the principle of least privilege. You can now grant specific members access to CASB security findings without assigning them broader permissions, such as the **Super Administrator** or **Administrator** roles.
To enable [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/), scans in CASB, account members will need the **Cloudflare Zero Trust** role.
You can find these new roles when inviting members or creating API tokens in the Cloudflare dashboard under **Manage Account** > **Members**.
To learn more about managing roles and permissions, refer to the [Manage account members and roles documentation](https://developers.cloudflare.com/fundamentals/manage-members/roles/).
## 2025-10-28
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**New Application Categories added for HTTP Traffic Management**
To give you precision and flexibility while creating policies to block unwanted traffic, we are introducing new, more granular application categories in the Gateway product.
We have added the following categories to provide more precise organization and allow for finer-grained policy creation, designed around how users interact with different types of applications:
* Business
* Education
* Entertainment & Events
* Food & Drink
* Health & Fitness
* Lifestyle
* Navigation
* Photography & Graphic Design
* Travel
The new categories are live now, but we are providing a transition period for existing applications to be fully remapped to these new categories.
The full remapping will be completed by January 30, 2026.
We encourage you to use this time to:
* Review the new category structure.
* Identify and adjust any existing HTTP policies that reference older categories to ensure a smooth transition.
For more information on creating HTTP policies, refer to [Applications and app types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
## 2025-10-20
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Schedule DNS policies from the UI**
Admins can now create [scheduled DNS policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/timed-policies/) directly from the Zero Trust dashboard, without using the API. You can configure policies to be active during specific, recurring times, such as blocking social media during business hours or gaming sites on school nights.
* **Preset Schedules**: Use built-in templates for common scenarios like Business Hours, School Days, Weekends, and more.
* **Custom Schedules**: Define your own schedule with specific days and up to three non-overlapping time ranges per day.
* **Timezone Control**: Choose to enforce a schedule in a specific timezone (for example, US Eastern) or based on the local time of each user.
* **Combined with Duration**: Policies can have both a schedule and a duration. If both are set, the duration's expiration takes precedence.
You can see the flow in the demo GIF:

This update makes time-based DNS policies accessible to all Gateway customers, removing the technical barrier of the API.
## 2025-10-17
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**On-Demand Security Report**
You can now generate on-demand security reports directly from the Cloudflare dashboard. This new feature provides a comprehensive overview of your email security posture, making it easier than ever to demonstrate the value of Cloudflare’s Email security to executives and other decision makers.
These reports offer several key benefits:
* **Executive Summary:** Quickly view the performance of Email security with a high-level executive summary.
* **Actionable Insights:** Dive deep into trend data, breakdowns of threat types, and analysis of top targets to identify and address vulnerabilities.
* **Configuration Transparency:** Gain a clear view of your policy, submission, and domain configurations to ensure optimal setup.
* **Account Takeover Risks:** Get a snapshot of your M365 risky users (requires a Microsoft Entra ID P2 license and [M365 SaaS integration](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/microsoft-365/)).

This feature is available across the following Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-10-16
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.9.173.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes, improvements, and new features including Path Maximum Transmission Unit Discovery (PMTUD). With PMTUD enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to debug connectivity issues.
**Changes and improvements**
* Improvements for [Windows multi-user](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/) to maintain the [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) state when switching between users.
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to debug connectivity issues.
* Deleting registrations no longer returns an error when succeeding.
* Path Maximum Transmission Unit Discovery (PMTUD) is now used to discover the effective MTU of the connection. This allows the client to improve connection performance optimized for the current network.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-10-16
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.9.173.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes, improvements, and new features including Path Maximum Transmission Unit Discovery (PMTUD). With PMTUD enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to debug connectivity issues.
**Changes and improvements**
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to debug connectivity issues.
* Deleting registrations no longer returns an error when succeeding.
* Path Maximum Transmission Unit Discovery (PMTUD) is now used to discover the effective MTU of the connection. This allows the client to improve connection performance optimized for the current network.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-10-10
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**New domain categories added**
We have added three new domain categories under the Technology parent category, to better reflect online content and improve DNS filtering.
**New categories added**
| Parent ID | Parent Name | Category ID | Category Name |
| - | - | - | - |
| 26 | Technology | 194 | Keep Awake Software |
| 26 | Technology | 192 | Remote Access |
| 26 | Technology | 193 | Shareware/Freeware |
Refer to [Gateway domain categories](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) to learn more.
## 2025-10-07
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.8.779.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains significant fixes and improvements including an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com/).
**Changes and improvements**
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) has been enhanced for even faster resolution. Proxy mode now supports SOCKS4, SOCK5, and HTTP CONNECT over an L4 tunnel with custom congestion control optimizations instead of the previous L3 tunnel to Cloudflare's network. This has more than doubled Proxy mode throughput in lab speed testing, by an order of magnitude in some cases.
* The MASQUE protocol is now the only protocol that can use [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode). If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new WARP mode or switch to the MASQUE protocol. Otherwise, all devices matching the profile will lose connectivity.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-10-07
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.8.779.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains significant fixes and improvements.
**Changes and improvements**
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) has been enhanced for even faster resolution. Proxy mode now supports SOCKS4, SOCK5, and HTTP CONNECT over an L4 tunnel with custom congestion control optimizations instead of the previous L3 tunnel to Cloudflare's network. This has more than doubled Proxy mode throughput in lab speed testing, by an order of magnitude in some cases.
* The MASQUE protocol is now the only protocol that can use [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode). If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new WARP mode or switch to the MASQUE protocol. Otherwise, all devices matching the profile will lose connectivity.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-10-07
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.8.779.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains significant fixes and improvements.
**Changes and improvements**
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) has been enhanced for even faster resolution. Proxy mode now supports SOCKS4, SOCK5, and HTTP CONNECT over an L4 tunnel with custom congestion control optimizations instead of the previous L3 tunnel to Cloudflare's network. This has more than doubled Proxy mode throughput in lab speed testing, by an order of magnitude in some cases.
* The MASQUE protocol is now the only protocol that can use [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode). If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new WARP mode or switch to the MASQUE protocol. Otherwise, all devices matching the profile will lose connectivity.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-10-01
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**Expanded File Type Controls for Executables and Disk Images**
You can now enhance your security posture by blocking additional application installer and disk image file types with Cloudflare Gateway. Preventing the download of unauthorized software packages is a critical step in securing endpoints from malware and unwanted applications.
We have expanded Gateway's file type controls to include:
* Apple Disk Image (dmg)
* Microsoft Software Installer (msix, appx)
* Apple Software Package (pkg)
You can find these new options within the [*Upload File Types* and *Download File Types* selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#download-and-upload-file-types) when creating or editing an HTTP policy. The file types are categorized as follows:
* **System**: *Apple Disk Image (dmg)*
* **Executable**: *Microsoft Software Installer (msix)*, *Microsoft Software Installer (appx)*, *Apple Software Package (pkg)*
To ensure these file types are blocked effectively, please note the following behaviors:
* DMG: Due to their file structure, DMG files are blocked at the very end of the transfer. A user's download may appear to progress but will fail at the last moment, preventing the browser from saving the file.
* MSIX: To comprehensively block Microsoft Software Installers, you should also include the file type *Unscannable*. MSIX files larger than 100 MB are identified as Unscannable ZIP files during inspection.
To get started, go to your HTTP policies in Zero Trust. For a full list of file types, refer to [supported file types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#supported-file-types).
## 2025-09-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.7.176.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* MASQUE is now the default [tunnel protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) for all new WARP device profiles.
* Improvement to limit idle connections in [Gateway with DoH mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#gateway-with-doh) to avoid unnecessary resource usage that can lead to DoH requests not resolving.
* Improvement to maintain TCP connections to reduce interruptions in long-lived connections such as RDP or SSH.
* Improvements to maintain [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings when [switching between organizations](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/switch-organizations/#switch-organizations-in-warp).
* Improvements to maintain client connectivity during network changes.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-09-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.7.176.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed a bug preventing the `warp-diag captive-portal` command from running successfully due to the client not parsing SSID on macOS.
* Improvements to maintain [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings when [switching between organizations](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/switch-organizations/#switch-organizations-in-warp).
* MASQUE is now the default [tunnel protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) for all new WARP device profiles.
* Improvement to limit idle connections in [Gateway with DoH mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#gateway-with-doh) to avoid unnecessary resource usage that can lead to DoH requests not resolving.
* Improvements to maintain client connectivity during network changes.
* The WARP client now supports macOS Tahoe (version 26.0).
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-09-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.7.176.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements including an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com/).
**Changes and improvements**
* MASQUE is now the default [tunnel protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) for all new WARP device profiles.
* Improvement to limit idle connections in [Gateway with DoH mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#gateway-with-doh) to avoid unnecessary resource usage that can lead to DoH requests not resolving.
* Improvements to maintain [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings when [switching between organizations](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/switch-organizations/#switch-organizations-in-warp).
* Improvements to maintain client connectivity during network changes.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-09-30
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Application granular controls for operations in SaaS applications**
Gateway users can now apply granular controls to their file sharing and AI chat applications through [HTTP policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies).
The new feature offers two methods of controlling SaaS applications:
* **Application Controls** are curated groupings of Operations which provide an easy way for users to achieve a specific outcome. Application Controls may include *Upload*, *Download*, *Prompt*, *Voice*, and *Share* depending on the application.
* **Operations** are controls aligned to the most granular action a user can take. This provides a fine-grained approach to enforcing policy and generally aligns to the SaaS providers API specifications in naming and function.
Get started using [Application Granular Controls](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/granular-controls) and refer to the list of [supported applications](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/granular-controls/#compatible-applications).
## 2025-09-25
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**Refine DLP Scans with New Body Phase Selector**
You can now more precisely control your HTTP DLP policies by specifying whether to scan the request or response body, helping to reduce false positives and target specific data flows.
In the Gateway HTTP policy builder, you will find a new selector called *Body Phase*. This allows you to define the direction of traffic the DLP engine will inspect:
* *Request Body*: Scans data sent from a user's machine to an upstream service. This is ideal for monitoring data uploads, form submissions, or other user-initiated data exfiltration attempts.
* *Response Body*: Scans data sent to a user's machine from an upstream service. Use this to inspect file downloads and website content for sensitive data.
For example, consider a policy that blocks Social Security Numbers (SSNs). Previously, this policy might trigger when a user visits a website that contains example SSNs in its content (the response body). Now, by setting the **Body Phase** to *Request Body*, the policy will only trigger if the user attempts to upload or submit an SSN, ignoring the content of the web page itself.
All policies without this selector will continue to scan both request and response bodies to ensure continued protection.
For more information, refer to [Gateway HTTP policy selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#body-phase/).
## 2025-09-23
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Invalid Submissions Feedback**
Email security relies on your submissions to continuously improve our detection models. However, we often receive submissions in formats that cannot be ingested, such as incomplete EMLs, screenshots, or text files.
To ensure all customer feedback is actionable, we have launched two new features to manage invalid submissions sent to our team and user [submission aliases](https://developers.cloudflare.com/cloudflare-one/email-security/settings/phish-submissions/submission-addresses/):
* **Email Notifications:** We now automatically notify users by email when they provide an invalid submission, educating them on the correct format. To disable notifications, go to **[Settings](https://one.dash.cloudflare.com/?to=/:account/email-security/settings)** > **Invalid submission emails** and turn the feature off.

* **Invalid Submission dashboard:** You can quickly identify which users need education to provide valid submissions so Cloudflare can provide continuous protection.

Learn more about this feature on [invalid submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/invalid-submissions/).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-09-22
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Access Remote Desktop Protocol (RDP) destinations securely from your browser — now generally available!**
[Browser-based RDP](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/) with [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) is now generally available for all Cloudflare customers. It enables secure, remote Windows server access without VPNs or RDP clients.
Since we announced our [open beta](https://developers.cloudflare.com/changelog/access/#2025-06-30), we've made a few improvements:
* Support for targets with IPv6.
* Support for [Magic WAN](https://developers.cloudflare.com/magic-wan/) and [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) as on-ramps.
* More robust error messaging on the login page to help you if you encounter an issue.
* Worldwide keyboard support. Whether your day-to-day is in Portuguese, Chinese, or something in between, your browser-based RDP experience will look and feel exactly like you are using a desktop RDP client.
* Cleaned up some other miscellaneous issues, including but not limited to enhanced support for Entra ID accounts and support for usernames with spaces, quotes, and special characters.
As a refresher, here are some benefits browser-based RDP provides:
* **Control how users authenticate to internal RDP resources** with single sign-on (SSO), multi-factor authentication (MFA), and granular access policies.
* **Record who is accessing which servers and when** to support regulatory compliance requirements and to gain greater visibility in the event of a security event.
* **Eliminate the need to install and manage software on user devices**. You will only need a web browser.
* **Reduce your attack surface** by keeping your RDP servers off the public Internet and protecting them from common threats like credential stuffing or brute-force attacks.

To get started, refer to [Connect to RDP in a browser](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/).
## 2025-09-18
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
**Connect and secure any private or public app by hostname, not IP — with hostname routing for Cloudflare Tunnel**
You can now route private traffic to [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) based on a hostname or domain, moving beyond the limitations of IP-based routing. This new capability is **free for all Cloudflare One customers**.
Previously, Tunnel routes could only be defined by IP address or [CIDR range](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/connect-cidr/). This created a challenge for modern applications with dynamic or ephemeral IP addresses, often forcing administrators to maintain complex and brittle IP lists.

**What’s new:**
* **Hostname & Domain Routing**: Create routes for individual hostnames (e.g., `payroll.acme.local`) or entire domains (e.g., `*.acme.local`) and direct their traffic to a specific Tunnel.
* **Simplified Zero Trust Policies**: Build resilient policies in Cloudflare Access and Gateway using stable hostnames, making it dramatically easier to apply per-resource authorization for your private applications.
* **Precise Egress Control**: Route traffic for public hostnames (e.g., `bank.example.com`) through a specific Tunnel to enforce a dedicated source IP, solving the IP allowlist problem for third-party services.
* **No More IP Lists**: This feature makes the workaround of maintaining dynamic IP Lists for Tunnel connections obsolete.
Get started in the Tunnels section of the Zero Trust dashboard with your first [private hostname](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/connect-private-hostname/) or [public hostname](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/egress-cloudflared/) route.
Learn more in our [blog post](https://blog.cloudflare.com/tunnel-hostname-routing/).
## 2025-09-16
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New AI-Enabled Search for Zero Trust Dashboard**
Zero Trust Dashboard has a brand new, AI-powered search functionality. You can search your account by resources (applications, policies, device profiles, settings, etc.), pages, products, and more.

**Ask Cloudy** — You can also ask Cloudy, our AI agent, questions about Cloudflare Zero Trust. Cloudy is trained on our developer documentation and implementation guides, so it can tell you how to configure functionality, best practices, and can make recommendations.
Cloudy can then stay open with you as you move between pages to build configuration or answer more questions.
**Find Recents** — Recent searches and Cloudy questions also have a new tab under Zero Trust Overview.
## 2025-09-11
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Regional Email Processing for Germany, India, or Australia**
We’re excited to announce that Email security customers can now choose their preferred mail processing location directly from the UI when onboarding a domain. This feature is available for the following onboarding methods: **MX**, **BCC**, and **Journaling**.
#### What’s new
Customers can now select where their email is processed. The following regions are supported:
* **Germany**
* **India**
* **Australia**
Global processing remains the default option, providing flexibility to meet both compliance requirements or operational preferences.
#### How to use it
When onboarding a domain with MX, BCC, or Journaling:
1. Select the desired processing location (Germany, India, or Australia).
2. The UI will display updated processing addresses specific to that region.
3. For MX onboarding, if your domain is managed by Cloudflare, you can automatically update MX records directly from the UI.
#### Availability
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
#### What’s next
We’re expanding the list of processing locations to match our [Data Localization Suite (DLS)](https://developers.cloudflare.com/data-localization/) footprint, giving customers the broadest set of regional options in the market without the complexity of self-hosting.
## 2025-09-11
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
**DNS filtering for private network onramps**
[Magic WAN](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-gateway/#dns-filtering) and [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/site-to-internet/#configure-dns-resolver-on-devices) users can now securely route their DNS traffic to the Gateway resolver without exposing traffic to the public Internet.
Routing DNS traffic to the Gateway resolver allows DNS resolution and filtering for traffic coming from private networks while preserving source internal IP visibility. This ensures Magic WAN users have full integration with our Cloudflare One features, including [Internal DNS](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/#internal-dns) and [hostname-based policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/#selector-prerequisites).
To configure DNS filtering, change your Magic WAN or WARP Connector DNS settings to use Cloudflare's shared resolver IPs, `172.64.36.1` and `172.64.36.2`. Once you configure DNS resolution and filtering, you can use *Source Internal IP* as a traffic selector in your [resolver policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/) for routing private DNS traffic to your [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/).
## 2025-09-10
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.7.106.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements including enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
**Changes and improvements**
* Enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
* Improvement to keep TCP connections up the first time WARP connects on devices so that remote desktop sessions (such as RDP or SSH) continue to work.
* Improvements to maintain Global WARP Override settings when switching between organization configurations.
* The [MASQUE protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) is now the default protocol for all new WARP device profiles.
* Improvement to limit idle connections in DoH mode to avoid unnecessary resource usage that can lead to DoH requests not resolving.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about Win32/ClickFix.ABA being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-09-10
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.7.106.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements including enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
**Changes and improvements**
* Enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
* Fixed a bug preventing the `warp-diag captive-portal` command from running successfully due to the client not parsing SSID on macOS.
* Improvements to maintain Global WARP Override settings when switching between organization configurations.
* The [MASQUE protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) is now the default protocol for all new WARP device profiles.
* Improvement to limit idle connections in DoH mode to avoid unnecessary resource usage that can lead to DoH requests not resolving.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-09-08
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Custom IKE ID for IPsec Tunnels**
Now, Magic WAN customers can configure a custom IKE ID for their IPsec tunnels. Customers that are using Magic WAN and a VeloCloud SD-WAN device together can utilize this new feature to create a high availability configuration.
This feature is available via API only. Customers can read the Magic WAN documentation to learn more about the [Custom IKE ID feature and the API call to configure it](https://developers.cloudflare.com/magic-wan/configuration/common-settings/custom-ike-id-ipsec/).
## 2025-09-05
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Bidirectional tunnel health checks are compatible with all Magic on-ramps**
All bidirectional tunnel health check return packets are accepted by any Magic on-ramp.
Previously, when a Magic tunnel had a bidirectional health check configured, the bidirectional health check would pass when the return packets came back to Cloudflare over the same tunnel that was traversed by the forward packets.
There are SD-WAN devices, like VeloCloud, that do not offer controls to steer traffic over one tunnel versus another in a high availability tunnel configuration.
Now, when a Magic tunnel has a bidirectional health check configured, the bidirectional health check will pass when the return packet traverses over any tunnel in a high availability configuration.
## 2025-09-02
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
**Cloudflare Tunnel and Networks API will no longer return deleted resources by default starting December 1, 2025**
Starting **December 1, 2025**, list endpoints for the [Cloudflare Tunnel API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/) and [Zero Trust Networks API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/) will no longer return deleted tunnels, routes, subnets and virtual networks by default. This change makes the API behavior more intuitive by only returning active resources unless otherwise specified.
No action is required if you already explicitly set `is_deleted=false` or if you only need to list active resources.
This change affects the following API endpoints:
* List all tunnels: [`GET /accounts/{account_id}/tunnels`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/methods/list/)
* List [Cloudflare Tunnels](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/): [`GET /accounts/{account_id}/cfd_tunnel`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/subresources/cloudflared/methods/list/)
* List [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) tunnels: [`GET /accounts/{account_id}/warp_connector`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/subresources/warp_connector/methods/list/)
* List tunnel routes: [`GET /accounts/{account_id}/teamnet/routes`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/routes/methods/list/)
* List subnets: [`GET /accounts/{account_id}/zerotrust/subnets`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/subnets/methods/list/)
* List virtual networks: [`GET /accounts/{account_id}/teamnet/virtual_networks`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/virtual_networks/methods/list/)
#### What is changing?
The default behavior of the `is_deleted` query parameter will be updated.
| Scenario | Previous behavior (before December 1, 2025) | New behavior (from December 1, 2025) |
| - | - | - |
| `is_deleted` parameter is omitted | Returns **active & deleted** tunnels, routes, subnets and virtual networks | Returns **only active** tunnels, routes, subnets and virtual networks |
#### Action required
If you need to retrieve deleted (or all) resources, please update your API calls to explicitly include the `is_deleted` parameter before **December 1, 2025**.
To get a list of only deleted resources, you must now explicitly add the `is_deleted=true` query parameter to your request:
```bash
# Example: Get ONLY deleted Tunnels
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/tunnels?is_deleted=true" \
-H "Authorization: Bearer $API_TOKEN"
# Example: Get ONLY deleted Virtual Networks
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/teamnet/virtual_networks?is_deleted=true" \
-H "Authorization: Bearer $API_TOKEN"
```
Following this change, retrieving a complete list of both active and deleted resources will require two separate API calls: one to get active items (by omitting the parameter or using `is_deleted=false`) and one to get deleted items (`is_deleted=true`).
#### Why we’re making this change
This update is based on user feedback and aims to:
* **Create a more intuitive default:** Aligning with common API design principles where list operations return only active resources by default.
* **Reduce unexpected results:** Prevents users from accidentally operating on deleted resources that were returned unexpectedly.
* **Improve performance:** For most users, the default query result will now be smaller and more relevant.
To learn more, please visit the [Cloudflare Tunnel API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/) and [Zero Trust Networks API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/) documentation.
## 2025-09-01
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Updated Email security roles**
To provide more granular controls, we refined the [existing roles](https://developers.cloudflare.com/cloudflare-one/roles-permissions/#email-security-roles) for Email security and launched a new Email security role as well.
All Email security roles no longer have read or write access to any of the other Zero Trust products:
* **Email Configuration Admin**
* **Email Integration Admin**
* **Email security Read Only**
* **Email security Analyst**
* **Email security Policy Admin**
* **Email security Reporting**
To configure [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/email-security/outbound-dlp/) or [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/#set-up-clientless-web-isolation), you now need to be an admin for the Zero Trust dashboard with the **Cloudflare Zero Trust** role.
Also through customer feedback, we have created a new additive role to allow **Email security Analyst** to create, edit, and delete Email security policies, without needing to provide access via the **Email Configuration Admin** role. This role is called **Email security Policy Admin**, which can read all settings, but has write access to [allow policies](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/allow-policies/), [trusted domains](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/trusted-domains/), and [blocked senders](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/blocked-senders/).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-08-29
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
**DEX MCP Server**
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into device connectivity and performance across your Cloudflare SASE deployment.
We've released an MCP server [(Model Context Protocol)](https://cloudflare.com/learning/ai/what-is-model-context-protocol-mcp/) for DEX.
The DEX MCP server is an AI tool that allows customers to ask a question like, "Show me the connectivity and performance metrics for the device used by carly@acme.com", and receive an answer that contains data from the DEX API.
Any Cloudflare One customer using a Free, PayGo, or Enterprise account can access the DEX MCP Server. This feature is available to everyone.
Customers can test the new DEX MCP server in less than one minute. To learn more, read the [DEX MCP server documentation](https://developers.cloudflare.com/cloudflare-one/insights/dex/dex-mcp-server/).
## 2025-08-29
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**Cloudflare One WARP Diagnostic AI Analyzer**
We're excited to share a new AI feature, the [WARP diagnostic analyzer](https://blog.cloudflare.com/AI-troubleshoot-warp-and-network-connectivity-issues/), to help you troubleshoot and resolve WARP connectivity issues faster. This beta feature is now available in the [Zero Trust dashboard](https://one.dash.cloudflare.com/) to all users. The AI analyzer makes it easier for you to identify the root cause of client connectivity issues by parsing [remote captures](https://developers.cloudflare.com/cloudflare-one/insights/dex/remote-captures/#start-a-remote-capture) of [WARP diagnostic logs](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/troubleshooting/warp-logs/#warp-diag-logs). The WARP diagnostic analyzer provides a summary of impact that may be experienced on the device, lists notable events that may contribute to performance issues, and recommended troubleshooting steps and articles to help you resolve these issues. Refer to [WARP diagnostics analyzer (beta)](https://developers.cloudflare.com/cloudflare-one/insights/dex/remote-captures/#warp-diagnostics-analyzer-beta) to learn more about how to maximize using the WARP diagnostic analyzer to troubleshoot the WARP client.
## 2025-08-27
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**Shadow IT - SaaS analytics dashboard**
Zero Trust has significantly upgraded its **Shadow IT analytics**, providing you with unprecedented visibility into your organizations use of SaaS tools. With this dashboard, you can review who is using an application and volumes of data transfer to the application.
You can review these metrics against application type, such as Artificial Intelligence or Social Media. You can also mark applications with an approval status, including **Unreviewed**, **In Review**, **Approved**, and **Unapproved** designating how they can be used in your organization.

These application statuses can also be used in Gateway HTTP policies, so you can block, isolate, limit uploads and downloads, and more based on the application status.
Both the analytics and policies are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
## 2025-08-26
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
**New CASB integrations for ChatGPT, Claude, and Gemini**
[Cloudflare CASB](https://www.cloudflare.com/zero-trust/products/casb/) now supports three of the most widely used GenAI platforms — **OpenAI ChatGPT**, **Anthropic Claude**, and **Google Gemini**. These API-based integrations give security teams agentless visibility into posture, data, and compliance risks across their organization’s use of generative AI.

#### Key capabilities
* **Agentless connections** — connect ChatGPT, Claude, and Gemini tenants via API; no endpoint software required
* **Posture management** — detect insecure settings and misconfigurations that could lead to data exposure
* **DLP detection** — identify sensitive data in uploaded chat attachments or files
* **GenAI-specific insights** — surface risks unique to each provider’s capabilities
#### Learn more
* [ChatGPT integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/openai/)
* [Claude integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/anthropic/)
* [Gemini integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/google-workspace/gemini/)
These integrations are available to all Cloudflare One customers today.
## 2025-08-26
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Manage and restrict access to internal MCP servers with Cloudflare Access**
You can now control who within your organization has access to internal MCP servers, by putting internal MCP servers behind [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/).
[Self-hosted applications](https://developers.cloudflare.com/cloudflare-one/access-controls/ai-controls/linked-apps/) in Cloudflare Access now support OAuth for MCP server authentication. This allows Cloudflare to delegate access from any self-hosted application to an MCP server via OAuth. The OAuth access token authorizes the MCP server to make requests to your self-hosted applications on behalf of the authorized user, using that user's specific permissions and scopes.
For example, if you have an MCP server designed for internal use within your organization, you can configure Access policies to ensure that only authorized users can access it, regardless of which MCP client they use. Support for internal, self-hosted MCP servers also works with MCP server portals, allowing you to provide a single MCP endpoint for multiple MCP servers. For more on MCP server portals, read the [blog post](https://blog.cloudflare.com/zero-trust-mcp-server-portals/) on the Cloudflare Blog.
## 2025-08-26
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**MCP server portals**\

An [MCP server portal](https://developers.cloudflare.com/cloudflare-one/access-controls/ai-controls/mcp-portals/) centralizes multiple Model Context Protocol (MCP) servers onto a single HTTP endpoint. Key benefits include:
* **Streamlined access to multiple MCP servers**: MCP server portals support both unauthenticated MCP servers as well as MCP servers secured using any third-party or custom OAuth provider. Users log in to the portal URL through Cloudflare Access and are prompted to authenticate separately to each server that requires OAuth.
* **Customized tools per portal**: Admins can tailor an MCP portal to a particular use case by choosing the specific tools and prompt templates that they want to make available to users through the portal. This allows users to access a curated set of tools and prompts — the less external context exposed to the AI model, the better the AI responses tend to be.
* **Observability**: Once the user's AI agent is connected to the portal, Cloudflare Access logs the indiviudal requests made using the tools in the portal.
This is available in an open beta for all customers across all plans! For more information check out our [blog](https://blog.cloudflare.com/zero-trust-mcp-server-portals/) for this release.
## 2025-08-25
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**New DLP topic based detection entries for AI prompt protection**
You now have access to a comprehensive suite of capabilities to secure your organization's use of generative AI. AI prompt protection introduces four key features that work together to provide deep visibility and granular control.
1. **Prompt Detection for AI Applications**
DLP can now natively detect and inspect user prompts submitted to popular AI applications, including **Google Gemini**, **ChatGPT**, **Claude**, and **Perplexity**.
1. **Prompt Analysis and Topic Classification**
Our DLP engine performs deep analysis on each prompt, applying [topic classification](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics). These topics are grouped into two evaluation categories:
* **Content:** PII, Source Code, Credentials and Secrets, Financial Information, and Customer Data.
* **Intent:** Jailbreak attempts, requests for malicious code, or attempts to extract PII.
To help you apply these topics quickly, we have also released five new predefined profiles (for example, AI Prompt: AI Security, AI Prompt: PII) that bundle these new topics.

1. **Granular Guardrails**
You can now build guardrails using Gateway HTTP policies with [application granular controls](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#application-granular-controls). Apply a DLP profile containing an [AI prompt topic detection](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics) to individual AI applications (for example, `ChatGPT`) and specific user actions (for example, `SendPrompt`) to block sensitive prompts.

2. **Full Prompt Logging**
To aid in incident investigation, an optional setting in your Gateway policy allows you to [capture prompt logs](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#log-generative-ai-prompt-content) to store the full interaction of prompts that trigger a policy match. To make investigations easier, logs can be filtered by `conversation_id`, allowing you to reconstruct the full context of an interaction that led to a policy violation.

AI prompt protection is now available in open beta. To learn more about it, read the [blog](https://blog.cloudflare.com/ai-prompt-protection/#closing-the-loop-logging) or refer to [AI prompt topics](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics).
## 2025-08-21
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.6.1400.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for pre-login for multi-user for the 2025.6.1135.0 release.
**Changes and improvements**
* Fixes an issue where new pre-login registrations were not being properly created.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about Win32/ClickFix.ABA being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, please reconnect the WARP client by toggling off and back on.
## 2025-08-21
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Gateway BYOIP Dedicated Egress IPs now available.**
Enterprise Gateway users can now use Bring Your Own IP (BYOIP) for dedicated egress IPs.
Admins can now onboard and use their own IPv4 or IPv6 prefixes to egress traffic from Cloudflare, delivering greater control, flexibility, and compliance for network traffic.
Get started by following the [BYOIP onboarding process](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/dedicated-egress-ips/#bring-your-own-ip-address-byoip). Once your IPs are onboarded, go to **Gateway** > **Egress policies** and select or create an egress policy. In **Select an egress IP**, choose *Use dedicated egress IPs (Cloudflare or BYOIP)*, then select your BYOIP address from the dropdown menu.

For more information, refer to [BYOIP for dedicated egress IPs](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/dedicated-egress-ips/#bring-your-own-ip-address-byoip).
## 2025-08-19
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.6.1335.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Improvements to better manage multi-user pre-login registrations.
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement for faster client connectivity on high-latency captive portal networks.
* Fixed an issue where recursive CNAME records could cause intermittent WARP connectivity issues.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-08-19
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.6.1335.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement for faster client connectivity on high-latency captive portal networks.
* Fixed an issue where recursive CNAME records could cause intermittent WARP connectivity issues.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-08-19
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.6.1335.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement for faster client connectivity on high-latency captive portal networks.
* Fixed an issue where recursive CNAME records could cause intermittent WARP connectivity issues.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-08-15
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**SFTP support for SSH with Cloudflare Access for Infrastructure**
[SSH with Cloudflare Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/) now supports SFTP. It is compatible with SFTP clients, such as Cyberduck.
## 2025-08-14
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Cloudflare Access Logging supports the Customer Metadata Boundary (CMB)**
Cloudflare Access logs now support the [Customer Metadata Boundary (CMB)](https://developers.cloudflare.com/data-localization/metadata-boundary/). If you have configured the CMB for your account, all Access logging will respect that configuration.
Note
For EU CMB customers, the logs will not be stored by Access and will appear as empty in the dashboard. EU CMB customers should utilize [Logpush](https://developers.cloudflare.com/logs/logpush/) to retain their Access logging, if desired.
## 2025-08-07
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Expanded Email Link Isolation**
When you deploy MX or Inline, not only can you apply email link isolation to suspicious links in all emails (including benign), you can now also apply email link isolation to all links of a specified disposition. This provides more flexibility in controlling user actions within emails.
For example, you may want to deliver suspicious messages but isolate the links found within them so that users who choose to interact with the links will not accidentally expose your organization to threats. This means your end users are more secure than ever before.
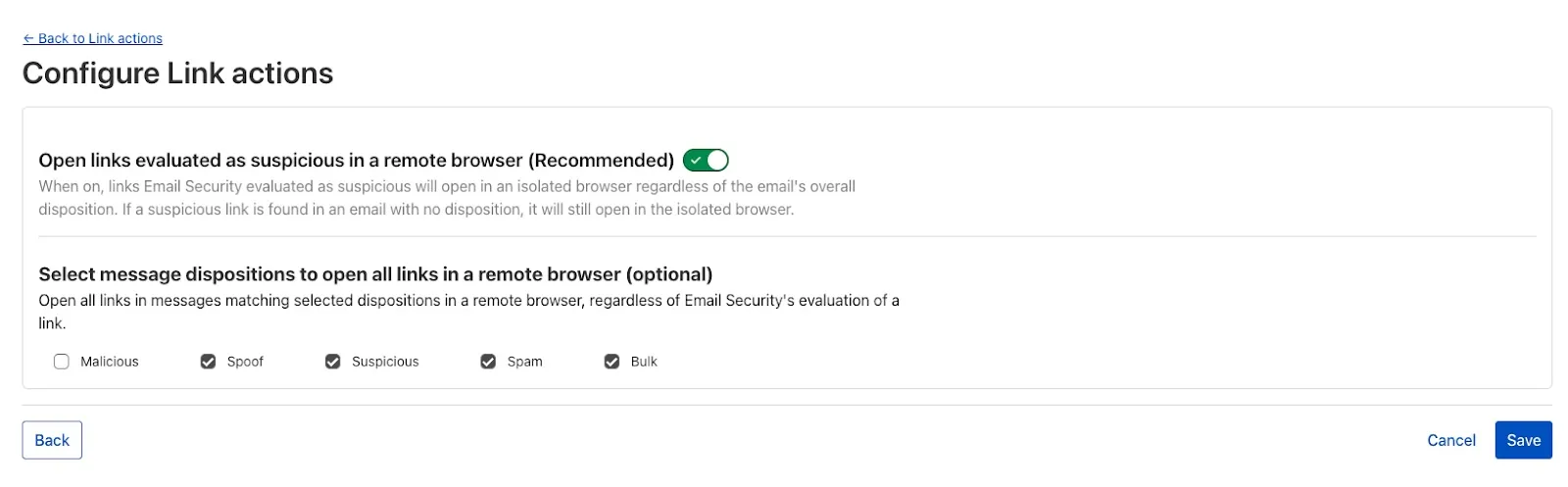
To isolate all links within a message based on the disposition, select **Settings** > **Link Actions** > **View** and select **Configure**. As with other other links you isolate, an interstitial will be provided to warn users that this site has been isolated and the link will be recrawled live to evaluate if there are any changes in our threat intel. Learn more about this feature on [Configure link actions](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/configure-link-actions/).
This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-07-30
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Magic Transit and Magic WAN health check data is fully compatible with the CMB EU setting.**
Today, we are excited to announce that all Magic Transit and Magic WAN customers with CMB EU ([Customer Metadata Boundary - Europe](https://developers.cloudflare.com/data-localization/metadata-boundary/)) enabled in their account will be able to access GRE, IPsec, and CNI health check and traffic volume data in the Cloudflare dashboard and via API.
This ensures that all Magic Transit and Magic WAN customers with CMB EU enabled will be able to access all Magic Transit and Magic WAN features.
Specifically, these two GraphQL endpoints are now compatible with CMB EU:
* `magicTransitTunnelHealthChecksAdaptiveGroups`
* `magicTransitTunnelTrafficAdaptiveGroups`
## 2025-07-28
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Scam domain category introduced under Security Threats**
We have introduced a new Security Threat category called **Scam**. Relevant domains are marked with the Scam category. Scam typically refers to fraudulent websites and schemes designed to trick victims into giving away money or personal information.
**New category added**
| Parent ID | Parent Name | Category ID | Category Name |
| - | - | - | - |
| 21 | Security Threats | 191 | Scam |
Refer to [Gateway domain categories](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) to learn more.
## 2025-07-24
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.6.824.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Improvements to better manage multi-user pre-login registrations.
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement to managed network detection checks for faster switching between managed networks.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-07-24
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.6.824.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement to managed network detection checks for faster switching between managed networks.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-07-24
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Gateway HTTP Filtering on all ports available in open BETA**
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) can now apply [HTTP filtering](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/) to all proxied HTTP requests, not just traffic on standard HTTP (`80`) and HTTPS (`443`) ports. This means all requests can now be filtered by [A/V scanning](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/antivirus-scanning/), [file sandboxing](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/file-sandboxing/), [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/#data-in-transit), and more.
You can turn this [setting](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/protocol-detection/#inspect-on-all-ports) on by going to **Settings** > **Network** > **Firewall** and choosing *Inspect on all ports*.

To learn more, refer to [Inspect on all ports (Beta)](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/protocol-detection/#inspect-on-all-ports).
## 2025-07-23
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.5.943.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* WARP proxy mode now uses the operating system's DNS settings. Changes made to system DNS settings while in proxy mode require the client to be turned off then back on to take effect.
* Changes to the [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) feature to no longer restart the SMS Agent Host (`ccmexec.exe`) service.
* Fixed an issue affecting clients in Split Tunnel Include mode, where access to split-tunneled traffic was blocked after reconnecting the client.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-07-23
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.5.943.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* WARP proxy mode now uses the operating system's DNS settings. Changes made to system DNS settings while in proxy mode require the client to be turned off then back on to take effect.
* Fixed an issue affecting clients in Split Tunnel Include mode, where access to split-tunneled traffic was blocked after reconnecting the client.
* For macOS deployments, the WARP client can now be managed using an `mdm.xml` file placed in `/Library/Application Support/Cloudflare/mdm.xml`. This new configuration option offers an alternative to the still supported method of deploying a managed plist through an MDM solution.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-07-23
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.5.943.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* WARP proxy mode now uses the operating system's DNS settings. Changes made to system DNS settings while in proxy mode require the client to be turned off then back on to take effect.
* Fixed an issue affecting clients in Split Tunnel Include mode, where access to split-tunneled traffic was blocked after reconnecting the client.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-07-22
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Google Bard Application replaced by Gemini**
The **Google Bard** application (ID: 1198) has been deprecated and fully removed from the system. It has been replaced by the **Gemini** application (ID: 1340). Any existing Gateway policies that reference the old Google Bard application will no longer function. To ensure your policies continue to work as intended, you should update them to use the new Gemini application. We recommend replacing all instances of the deprecated Bard application with the new Gemini application in your Gateway policies. For more information about application policies, please see the [Cloudflare Gateway documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
## 2025-07-17
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**New detection entry type: Document Matching for DLP**
You can now create [document-based](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#documents) detection entries in DLP by uploading example documents. Cloudflare will encrypt your documents and create a unique fingerprint of the file. This fingerprint is then used to identify similar documents or snippets within your organization's traffic and stored files.

**Key features and benefits:**
* **Upload documents, forms, or templates:** Easily upload .docx and .txt files (up to 10 MB) that contain sensitive information you want to protect.
* **Granular control with similarity percentage:** Define a minimum similarity percentage (0-100%) that a document must meet to trigger a detection, reducing false positives.
* **Comprehensive coverage:** Apply these document-based detection entries in:
* **Gateway policies:** To inspect network traffic for sensitive documents as they are uploaded or shared.
* **CASB (Cloud Access Security Broker):** To scan files stored in cloud applications for sensitive documents at rest.
* **Identify sensitive data:** This new detection entry type is ideal for identifying sensitive data within completed forms, templates, or even small snippets of a larger document, helping you prevent data exfiltration and ensure compliance.
Once uploaded and processed, you can add this new document entry into a DLP profile and policies to enhance your data protection strategy.
## 2025-07-15
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
**Faster, more reliable UDP traffic for Cloudflare Tunnel**
Your real-time applications running over [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) are now faster and more reliable. We've completely re-architected the way `cloudflared` proxies UDP traffic in order to isolate it from other traffic, ensuring latency-sensitive applications like private DNS are no longer slowed down by heavy TCP traffic (like file transfers) on the same Tunnel.
This is a foundational improvement to Cloudflare Tunnel, delivered automatically to all customers. There are no settings to configure — your UDP traffic is already flowing faster and more reliably.
**What’s new:**
* **Faster UDP performance**: We've significantly reduced the latency for establishing new UDP sessions, making applications like private DNS much more responsive.
* **Greater reliability for mixed traffic**: UDP packets are no longer affected by heavy TCP traffic, preventing timeouts and connection drops for your real-time services.
Learn more about running [TCP or UDP applications](https://developers.cloudflare.com/reference-architecture/architectures/sase/#connecting-applications) and [private networks](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/) through [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/).
## 2025-07-10
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New onboarding guides for Zero Trust**
Use our brand new onboarding experience for Cloudflare Zero Trust. New and returning users can now engage with a **Get Started** tab with walkthroughs for setting up common use cases end-to-end.

There are eight brand new onboarding guides in total:
* Securely access a private network (sets up device client and Tunnel)
* Device-to-device / mesh networking (sets up and connects multiple device clients)
* Network to network connectivity (sets up and connects multiple WARP Connectors, makes reference to Magic WAN availability for Enterprise)
* Secure web traffic (sets up device client, Gateway, pre-reqs, and initial policies)
* Secure DNS for networks (sets up a new DNS location and Gateway policies)
* Clientless web access (sets up Access to a web app, Tunnel, and public hostname)
* Clientless SSH access (all the same + the web SSH experience)
* Clientless RDP access (all the same + RDP-in-browser)
Each flow walks the user through the steps to configure the essential elements, and provides a “more details” panel with additional contextual information about what the user will accomplish at the end, along with why the steps they take are important.
Try them out now in the [Zero Trust dashboard](https://one.dash.cloudflare.com/?to=/:account/home)!
## 2025-07-07
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**Cloudy summaries for Access and Gateway Logs**
Cloudy, Cloudflare's AI Agent, will now automatically summarize your [Access](https://developers.cloudflare.com/cloudflare-one/insights/logs/audit-logs/) and [Gateway](https://developers.cloudflare.com/cloudflare-one/insights/logs/gateway-logs/) block logs.
In the log itself, Cloudy will summarize what occurred and why. This will be helpful for quick troubleshooting and issue correlation.

If you have feedback about the Cloudy summary - good or bad - you can provide that right from the summary itself.
## 2025-07-07
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New App Library for Zero Trust Dashboard**
Cloudflare Zero Trust customers can use the App Library to get full visibility over the SaaS applications that they use in their Gateway policies, CASB integrations, and Access for SaaS applications.
**App Library**, found under **My Team**, makes information available about all Applications that can be used across the Zero Trust product suite.
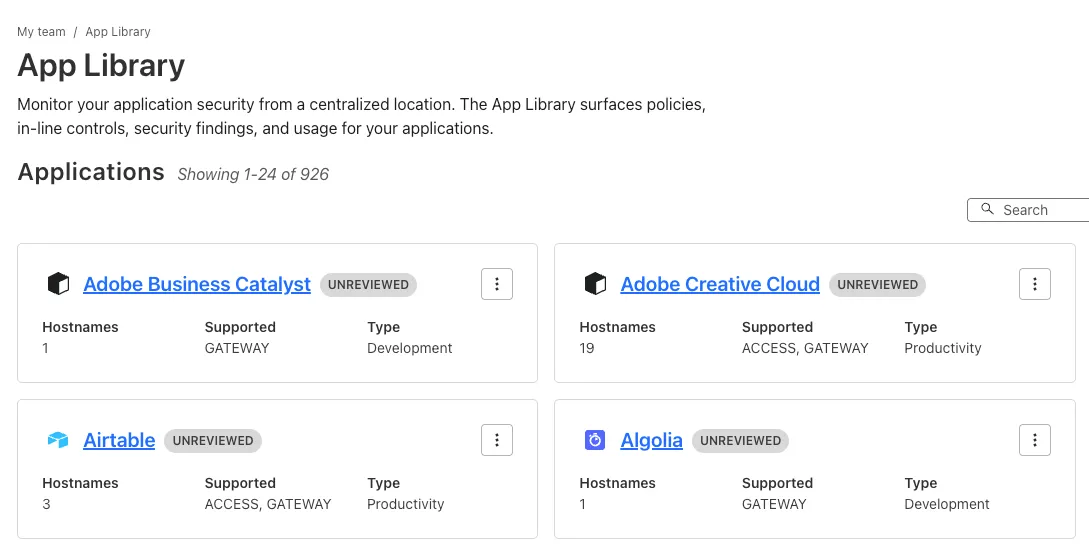
You can use the App Library to see:
* How Applications are defined
* Where they are referenced in policies
* Whether they have Access for SaaS configured
* Review their CASB findings and integration status.
Within individual Applications, you can also track their usage across your organization, and better understand user behavior.
## 2025-07-01
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Access RDP securely from your browser — now in open beta**
[Browser-based RDP](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/) with [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) is now available in open beta for all Cloudflare customers. It enables secure, remote Windows server access without VPNs or RDP clients.
With browser-based RDP, you can:
* **Control how users authenticate to internal RDP resources** with single sign-on (SSO), multi-factor authentication (MFA), and granular access policies.
* **Record who is accessing which servers and when** to support regulatory compliance requirements and to gain greater visibility in the event of a security event.
* **Eliminate the need to install and manage software on user devices**. You will only need a web browser.
* **Reduce your attack surface** by keeping your RDP servers off the public Internet and protecting them from common threats like credential stuffing or brute-force attacks.

To get started, see [Connect to RDP in a browser](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/).
## 2025-06-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.5.893.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains improvements and new exciting features, including [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) and [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed a device registration issue that caused WARP connection failures when changing networks.
* Captive portal improvements and fixes:
* Captive portal sign in notifications will now be sent through operating system notification services.
* Fix for firewall configuration issue affecting clients in DoH only mode.
* Improved the connectivity status message in the client GUI.
* Fixed a bug affecting clients in Gateway with DoH mode where the original DNS servers were not restored after disabling WARP.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to handle client configuration changes made by an MDM while WARP is not running.
* Improvements for multi-user experience to better handle fast user switching and transitions from a pre-login to a logged-in state.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Added [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) to device profile settings. With SCCM VPN boundary support enabled, operating systems will register WARP's local interface IP with the on-premise DNS server when reachable.
* Fix for an issue causing WARP connectivity to fail without full system reboot.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5060829](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-06-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.5.893.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed an issue where WARP sometimes failed to automatically relaunch after updating.
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements and fixes:
* Captive portal sign in notifications will now be sent through operating system notification services.
* Fix for firewall configuration issue affecting clients in DoH only mode.
* Improved the connectivity status message in the client GUI.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to handle client configuration changes made by an MDM while WARP is not running.
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Improvement for WARP connectivity issues on macOS due to the operating system not accepting DNS server configurations.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
## 2025-06-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.5.893.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements and fixes:
* Captive portal sign in notifications will now be sent through operating system notification services.
* Fix for firewall configuration issue affecting clients in DoH only mode.
* Improved the connectivity status message in the client GUI.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to handle client configuration changes made by MDM while WARP is not running.
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-06-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**Cloudflare One Agent for Android (version 2.4.2)**
A new GA release for the Android Cloudflare One Agent is now available in the [Google Play Store](https://play.google.com/store/apps/details?id=com.cloudflare.cloudflareoneagent). This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate [protection of post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* QLogs are now disabled by default and can be enabled in the app by turning on **Enable qlogs** under **Settings** > **Advanced** > **Diagnostics** > **Debug Logs**. The QLog setting from previous releases will no longer be respected.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* The WARP client now applies [post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be enabled by [MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Fixed an issue that caused WARP connection failures on ChromeOS devices.
## 2025-06-30
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**Cloudflare One Agent for iOS (version 1.11)**
A new GA release for the iOS Cloudflare One Agent is now available in the [iOS App Store](https://apps.apple.com/us/app/cloudflare-one-agent/id6443476492). This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate [protection of post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* QLogs are now disabled by default and can be enabled in the app by turning on **Enable qlogs** under **Settings** > **Advanced** > **Diagnostics** > **Debug Logs**. The QLog setting from previous releases will no longer be respected.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* The WARP client now applies [post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be enabled by [MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
## 2025-06-23
[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[CASB ](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**Data Security Analytics in the Zero Trust dashboard**
Zero Trust now includes **Data security analytics**, providing you with unprecedented visibility into your organization sensitive data.
The new dashboard includes:
* **Sensitive Data Movement Over Time:**
* See patterns and trends in how sensitive data moves across your environment. This helps understand where data is flowing and identify common paths.
* **Sensitive Data at Rest in SaaS & Cloud:**
* View an inventory of sensitive data stored within your corporate SaaS applications (for example, Google Drive, Microsoft 365) and cloud accounts (such as AWS S3).
* **DLP Policy Activity:**
* Identify which of your Data Loss Prevention (DLP) policies are being triggered most often.
* See which specific users are responsible for triggering DLP policies.

To access the new dashboard, log in to [Cloudflare One](https://one.dash.cloudflare.com/) and go to **Insights** on the sidebar.
## 2025-06-18
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Gateway will now evaluate Network policies before HTTP policies from July 14th, 2025**
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) will now evaluate [Network (Layer 4) policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/) **before** [HTTP (Layer 7) policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/). This change preserves your existing security posture and does not affect which traffic is filtered — but it may impact how notifications are displayed to end users.
This change will roll out progressively between **July 14–18, 2025**. If you use HTTP policies, we recommend reviewing your configuration ahead of rollout to ensure the user experience remains consistent.
#### Updated order of enforcement
**Previous order:**
1. DNS policies
2. HTTP policies
3. Network policies
**New order:**
1. DNS policies
2. **Network policies**
3. **HTTP policies**
#### Action required: Review your Gateway HTTP policies
This change may affect block notifications. For example:
* You have an **HTTP policy** to block `example.com` and display a block page.
* You also have a **Network policy** to block `example.com` silently (no client notification).
With the new order, the Network policy will trigger first — and the user will no longer see the HTTP block page.
To ensure users still receive a block notification, you can:
* Add a client notification to your Network policy, or
* Use only the HTTP policy for that domain.
***
#### Why we’re making this change
This update is based on user feedback and aims to:
* Create a more intuitive model by evaluating network-level policies before application-level policies.
* Minimize [526 connection errors](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/cloudflare-5xx-errors/error-526/#error-526-in-the-zero-trust-context) by verifying the network path to an origin before attempting to establish a decrypted TLS connection.
***
To learn more, visit the [Gateway order of enforcement documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/order-of-enforcement/).
## 2025-06-17
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.5.828.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains new improvements in addition to the features and improvements introduced in Beta client version 2025.5.735.1.
**Changes and improvements**
* Improvement to better handle multi-user fast user switching.
* Fix for an issue causing WARP connectivity to fail without full system reboot.
**Known issues**
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected. To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-06-17
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.5.828.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains new improvements in addition to the features and improvements introduced in Beta client version 2025.5.735.1.
**Changes and improvements**
* Improvement for WARP connectivity issues on macOS due to the operating system not accepting DNS server configurations.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
## 2025-06-05
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.5.735.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains improvements and new exciting features, including [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) and [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements including showing connectivity status in the client and sending system notifications for captive portal sign in.
* Fixed a bug where in Gateway with DoH mode, connection to DNS servers was not automatically restored after reconnecting WARP.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to gracefully handle changes made by MDM while WARP is not running.
* Improvement for multi-user mode to avoid unnecessary key rotations when transitioning from a pre-login to a logged-in state.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Added [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) to device profile settings. With SCCM VPN boundary support enabled, operating systems will register WARP's local interface IP with the on-premise DNS server when reachable.
**Known issues**
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected. To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-06-05
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.5.735.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed an issue where the Cloudflare WARP application may not have automatically relaunched after an update.
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements including showing connectivity status in the client and sending system notifications for captive portal sign in.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to gracefully handle changes made by MDM while WARP is not running.
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
## 2025-06-05
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**Cloudflare One Analytics Dashboards and Exportable Access Report**
Cloudflare One now offers powerful new analytics dashboards to help customers easily discover available insights into their application access and network activity. These dashboards provide a centralized, intuitive view for understanding user behavior, application usage, and security posture.
!\[Cloudflare One Analytics Dashboards]\(\~/assets/images/changelog/cloudflare-one/Analytics Dashboards.png)
Additionally, a new exportable access report is available, allowing customers to quickly view high-level metrics and trends in their application access. A **preview** of the report is shown below, with more to be found in the report:

Both features are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
## 2025-05-29
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New Gateway Analytics in the Cloudflare One Dashboard**
Users can now access significant enhancements to Cloudflare Gateway analytics, providing you with unprecedented visibility into your organization's DNS queries, HTTP requests, and Network sessions. These powerful new dashboards enable you to go beyond raw logs and gain actionable insights into how your users are interacting with the Internet and your protected resources.
You can now visualize and explore:
* Patterns Over Time: Understand trends in traffic volume and blocked requests, helping you identify anomalies and plan for future capacity.
* Top Users & Destinations: Quickly pinpoint the most active users, enabling better policy enforcement and resource allocation.
* Actions Taken: See a clear breakdown of security actions applied by Gateway policies, such as blocks and allows, offering a comprehensive view of your security posture.
* Geographic Regions: Gain insight into the global distribution of your traffic.

To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and go to Analytics in the side navigation bar.
## 2025-05-27
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Gateway Protocol Detection Now Available for PAYGO and Free Plans**
All Cloudflare One Gateway users can now use Protocol detection logging and filtering, including those on Pay-as-you-go and Free plans.
With Protocol Detection, admins can identify and enforce policies on traffic proxied through Gateway based on the underlying network protocol (for example, HTTP, TLS, or SSH), enabling more granular traffic control and security visibility no matter your plan tier.
This feature is available to enable in your account network settings for all accounts. For more information on using Protocol Detection, refer to the [Protocol detection documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/protocol-detection/).
## 2025-05-22
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.4.943.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for [managed networks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/managed-networks/) for the 2025.4.929.0 release.
**Changes and improvements**
* Fixed an issue where it could take up to 3 minutes for the correct device profile to be applied in some circumstances. In the worst case, it should now only take up to 40 seconds. This will be improved further in a future release.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
## 2025-05-22
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.4.943.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for [managed networks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/managed-networks/) for the 2025.4.929.0 release.
**Changes and improvements**
* Fixed an issue where it could take up to 3 minutes for the correct device profile to be applied in some circumstances. In the worst case, it should now only take up to 40 seconds. This will be improved further in a future release.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
## 2025-05-22
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.4.943.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for [managed networks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/managed-networks/) for the 2025.4.929.0 release.
**Changes and improvements**
* Fixed an issue where it could take up to 3 minutes for the correct device profile to be applied in some circumstances. In the worst case, it should now only take up to 40 seconds. This will be improved further in a future release.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-05-18
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New Applications Added to Zero Trust**
42 new applications have been added for Zero Trust support within the Application Library and Gateway policy enforcement, giving you the ability to investigate or apply inline policies to these applications.
33 of the 42 applications are Artificial Intelligence applications. The others are Human Resources (2 applications), Development (2 applications), Productivity (2 applications), Sales & Marketing, Public Cloud, and Security.
To view all available applications, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), navigate to the **App Library** under **My Team**.
For more information on creating Gateway policies, see our [Gateway policy documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/).
## 2025-05-16
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**New Access Analytics in the Cloudflare One Dashboard**
A new Access Analytics dashboard is now available to all Cloudflare One customers. Customers can apply and combine multiple filters to dive into specific slices of their Access metrics. These filters include:
* Logins granted and denied
* Access events by type (SSO, Login, Logout)
* Application name (Salesforce, Jira, Slack, etc.)
* Identity provider (Okta, Google, Microsoft, onetimepin, etc.)
* Users (`chris@cloudflare.com`, `sally@cloudflare.com`, `rachel@cloudflare.com`, etc.)
* Countries (US, CA, UK, FR, BR, CN, etc.)
* Source IP address
* App type (self-hosted, Infrastructure, RDP, etc.)

To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and find Analytics in the side navigation bar.
## 2025-05-15
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Open email attachments with Browser Isolation**
You can now safely open email attachments to view and investigate them.
What this means is that messages now have a **Attachments** section. Here, you can view processed attachments and their classifications (for example, *Malicious*, *Suspicious*, *Encrypted*). Next to each attachment, a **Browser Isolation** icon allows your team to safely open the file in a **clientless, isolated browser** with no risk to the analyst or your environment.
To use this feature, you must:
* Enable **Clientless Web Isolation** in your Zero Trust settings.
* Have **Browser Isolation (BISO)** seats assigned.
For more details, refer to our [setup guide](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/).
Some attachment types may not render in Browser Isolation. If there is a file type that you would like to be opened with Browser Isolation, reach out to your Cloudflare contact.
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-05-14
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.4.929.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains two significant changes all customers should be aware of:
1. All DNS traffic now flows inside the WARP tunnel. Customers are no longer required to configure their local firewall rules to allow our [DoH IP addresses and domains](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#doh-ip).
2. When using MASQUE, the connection will fall back to HTTP/2 (TCP) when we detect that HTTP/3 traffic is blocked. This allows for a much more reliable connection on some public WiFi networks.
**Changes and improvements**
* Fixed an issue causing reconnection loops when captive portals are detected.
* Fixed an issue that caused WARP client disk encryption posture checks to fail due to missing drive names.
* Fixed an issue where managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue where some parts of the WARP Client UI were missing in high contrast mode.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Added a TCP fallback for the MASQUE tunnel protocol to improve connectivity on networks that block UDP or HTTP/3 specifically.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
* Improvement for WARP to check if tunnel connectivity fails or times out at device wake before attempting to reconnect.
* Fixed an issue causing WARP connection disruptions after network changes.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
## 2025-05-14
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Domain Categories improvements**
**New categories added**
| Parent ID | Parent Name | Category ID | Category Name |
| - | - | - | - |
| 1 | Ads | 66 | Advertisements |
| 3 | Business & Economy | 185 | Personal Finance |
| 3 | Business & Economy | 186 | Brokerage & Investing |
| 21 | Security Threats | 187 | Compromised Domain |
| 21 | Security Threats | 188 | Potentially Unwanted Software |
| 6 | Education | 189 | Reference |
| 9 | Government & Politics | 190 | Charity and Non-profit |
**Changes to existing categories**
| Original Name | New Name |
| - | - |
| Religion | Religion & Spirituality |
| Government | Government/Legal |
| Redirect | URL Alias/Redirect |
Refer to [Gateway domain categories](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) to learn more.
## 2025-05-13
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
**SAML HTTP-POST bindings support for RBI**
Remote Browser Isolation (RBI) now supports SAML HTTP-POST bindings, enabling seamless authentication for SSO-enabled applications that rely on POST-based SAML responses from Identity Providers (IdPs) within a Remote Browser Isolation session. This update resolves a previous limitation that caused `405` errors during login and improves compatibility with multi-factor authentication (MFA) flows.
With expanded support for major IdPs like Okta and Azure AD, this enhancement delivers a more consistent and user-friendly experience across authentication workflows. Learn how to [set up Remote Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/).
## 2025-05-13
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**New Applications Added for DNS Filtering**
You can now create DNS policies to manage outbound traffic for an expanded list of applications. This update adds support for 273 new applications, giving you more control over your organization's outbound traffic.
With this update, you can:
* Create DNS policies for a wider range of applications
* Manage outbound traffic more effectively
* Improve your organization's security and compliance posture
For more information on creating DNS policies, see our [DNS policy documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/).
## 2025-05-12
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.4.929.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains two significant changes all customers should be aware of:
1. All DNS traffic now flows inside the WARP tunnel. Customers are no longer required to configure their local firewall rules to allow our [DoH IP addresses and domains](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#doh-ip).
2. When using MASQUE, the connection will fall back to HTTP/2 (TCP) when we detect that HTTP/3 traffic is blocked. This allows for a much more reliable connection on some public WiFi networks.
**Changes and improvements**
* Fixed an issue where the managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Added a TCP fallback for the MASQUE tunnel protocol to improve connectivity on networks that block UDP or HTTP/3 specifically.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improvement for WARP to check if tunnel connectivity fails or times out at device wake before attempting to reconnect.
* Fixed an issue causing WARP connection disruptions after network changes.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
## 2025-05-12
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.4.929.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains two significant changes all customers should be aware of:
1. All DNS traffic now flows inside the WARP tunnel. Customers are no longer required to configure their local firewall rules to allow our [DoH IP addresses and domains](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#doh-ip).
2. When using MASQUE, the connection will fall back to HTTP/2 (TCP) when we detect that HTTP/3 traffic is blocked. This allows for a much more reliable connection on some public WiFi networks.
**Changes and improvements**
* Fixed an issue where the managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Improved captive portal detection.
* Added a TCP fallback for the MASQUE tunnel protocol to improve connectivity on networks that block UDP or HTTP/3 specifically.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
* Improvement for WARP to check if tunnel connectivity fails or times out at device wake before attempting to reconnect.
* Fixed an issue causing WARP connection disruptions after network changes.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
## 2025-05-12
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**Case Sensitive Custom Word Lists**
You can now configure [custom word lists](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#custom-wordlist) to enforce case sensitivity. This setting supports flexibility where needed and aims to reduce false positives where letter casing is critical.

## 2025-05-08
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Open email links with Browser Isolation**
You can now safely open links in emails to view and investigate them.
From **Investigation**, go to **View details**, and look for the **Links identified** section. Next to each link, the Cloudflare dashboard will display an **Open in Browser Isolation** icon which allows your team to safely open the link in a clientless, isolated browser with no risk to the analyst or your environment. Refer to [Open links](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#open-links) to learn more about this feature.
To use this feature, you must:
* Enable **Clientless Web Isolation** in your Zero Trust settings.
* Have **Browser Isolation (RBI)** seats assigned.
For more details, refer to our [setup guide](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-05-07
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**Send forensic copies to storage without DLP profiles**
You can now [send DLP forensic copies](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#send-http-requests-to-logpush-destination/) to third-party storage for any HTTP policy with an `Allow` or `Block` action, without needing to include a DLP profile. This change increases flexibility for data handling and forensic investigation use cases.
By default, Gateway will send all matched HTTP requests to your configured DLP Forensic Copy jobs.

## 2025-05-01
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
**Browser Isolation Overview page for Zero Trust**
A new **Browser Isolation Overview** page is now available in the Cloudflare Zero Trust dashboard. This centralized view simplifies the management of [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/) deployments, providing:
* **Streamlined Onboarding:** Easily set up and manage isolation policies from one location.
* **Quick Testing:** Validate [clientless web application isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/) with ease.
* **Simplified Configuration:** Configure [isolated access applications](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/isolate-application/) and policies efficiently.
* **Centralized Monitoring:** Track aggregate usage and blocked actions.
This update consolidates previously disparate settings, accelerating deployment, improving visibility into isolation activity, and making it easier to ensure your protections are working effectively.

To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and find Browser Isolation in the side navigation bar.
## 2025-04-30
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
**Dark Mode for Zero Trust Dashboard**
The [Cloudflare Zero Trust dashboard](https://one.dash.cloudflare.com/) now supports Cloudflare's native dark mode for all accounts and plan types.
Zero Trust Dashboard will automatically accept your user-level preferences for system settings, so if your Dashboard appearance is set to 'system' or 'dark', the Zero Trust dashboard will enter dark mode whenever the rest of your Cloudflare account does.
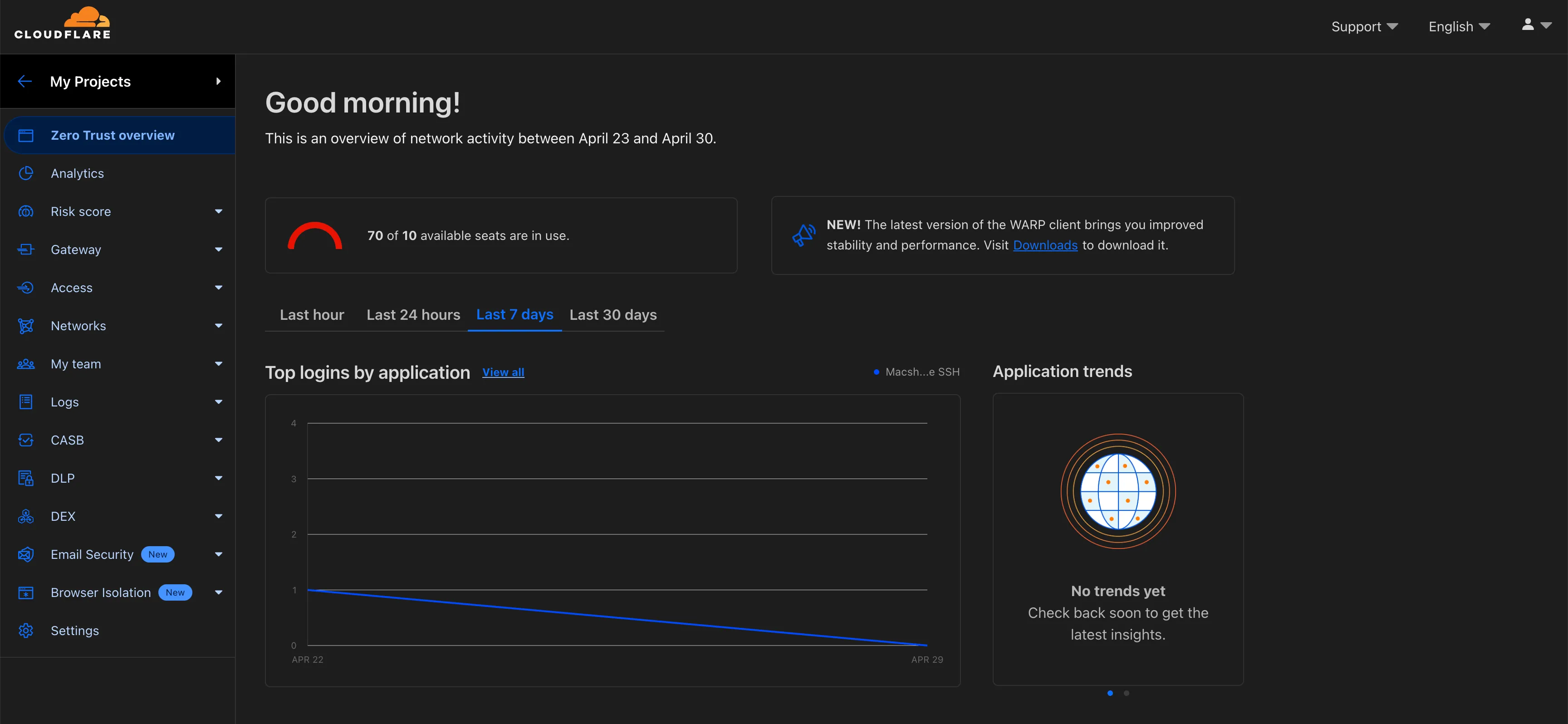
* Zero Trust Dashboard
To update your view preference in the Zero Trust dashboard:
1. Log into the [Zero Trust dashboard](https://one.dash.cloudflare.com/).
2. Select your user icon.
3. Select **Dark Mode**.
* Core Dashboard
To update your view preference in the Core dashboard:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com).
2. Go to **My Profile**
3. For **Appearance**, choose **Dark**.
## 2025-04-28
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**FQDN Filtering For Gateway Egress Policies**
Cloudflare One administrators can now control which egress IP is used based on a destination's fully qualified domain name (FDQN) within Gateway Egress policies.
* Host, Domain, Content Categories, and Application selectors are now available in the Gateway Egress policy builder in beta.
* During the beta period, you can use these selectors with traffic on-ramped to Gateway with the WARP client, proxy endpoints (commonly deployed with PAC files), or Cloudflare Browser Isolation.
* For WARP client support, additional configuration is required. For more information, refer to the [WARP client configuration documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/#limitations).
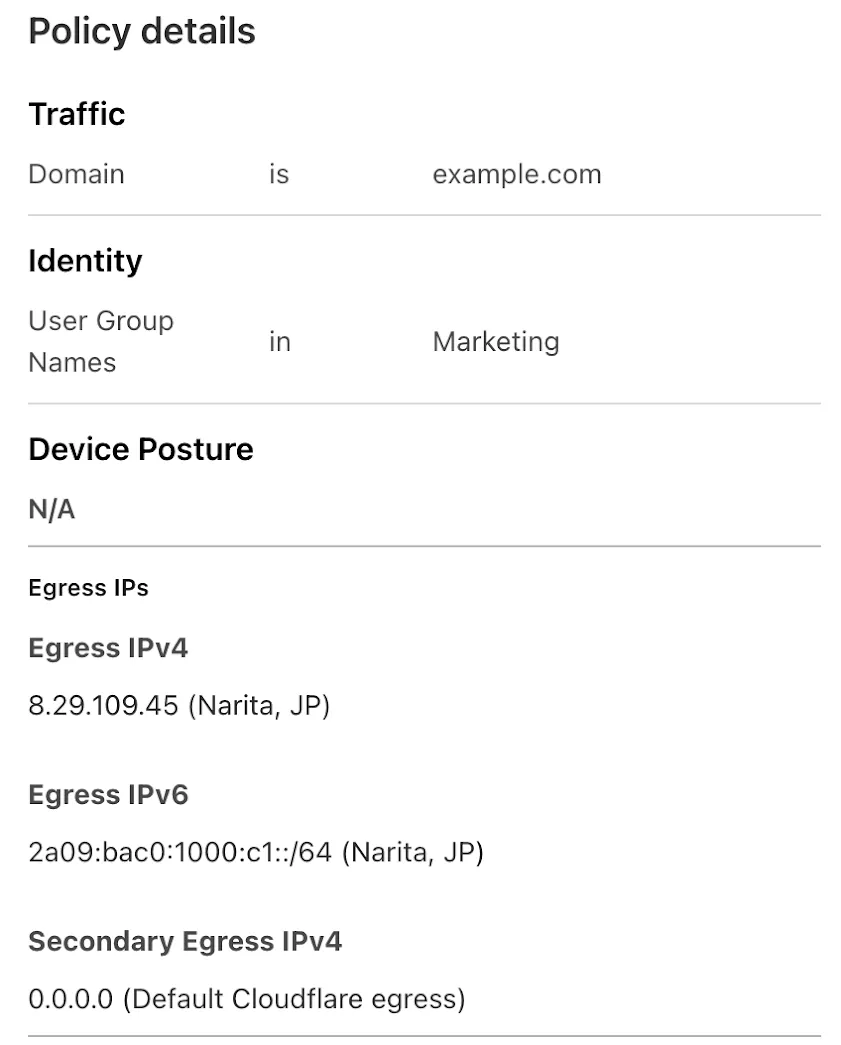
This will help apply egress IPs to your users' traffic when an upstream application or network requires it, while the rest of their traffic can take the most performant egress path.
## 2025-04-22
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.4.589.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
**Changes and improvements**
* Fixed an issue causing reconnection loops when captive portals are detected.
* Fixed an issue that caused WARP client disk encryption posture checks to fail due to missing drive names.
* Fixed an issue where managed network policies could incorrectly report network location beacons as missing.
* Improved error reporting for DEX tests.
* Improved WARP client UI high contrast mode.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Added a TCP fallback for the MASQUE tunnel protocol to improve compatibility with networks on MASQUE.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Added a [Collect Captive Portal Diag](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/#get-captive-portal-logs) button in the client GUI to make it easier for users to collect captive portal debugging diagnostics.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-04-22
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.4.589.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
**Changes and improvements**
* Fixed an issue where managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Improved captive portal detection.
* Added a TCP fallback for the MASQUE tunnel protocol to improve compatibility with networks on MASQUE.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Added a [Collect Captive Portal Diag](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/#get-captive-portal-logs) button in the client GUI to make it easier for users to collect captive portal debugging diagnostics.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
## 2025-04-21
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Access bulk policy tester**
The [Access bulk policy tester](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/policy-management/#test-all-policies-in-an-application) is now available in the Cloudflare Zero Trust dashboard. The bulk policy tester allows you to simulate Access policies against your entire user base before and after deploying any changes. The policy tester will simulate the configured policy against each user's last seen identity and device posture (if applicable).
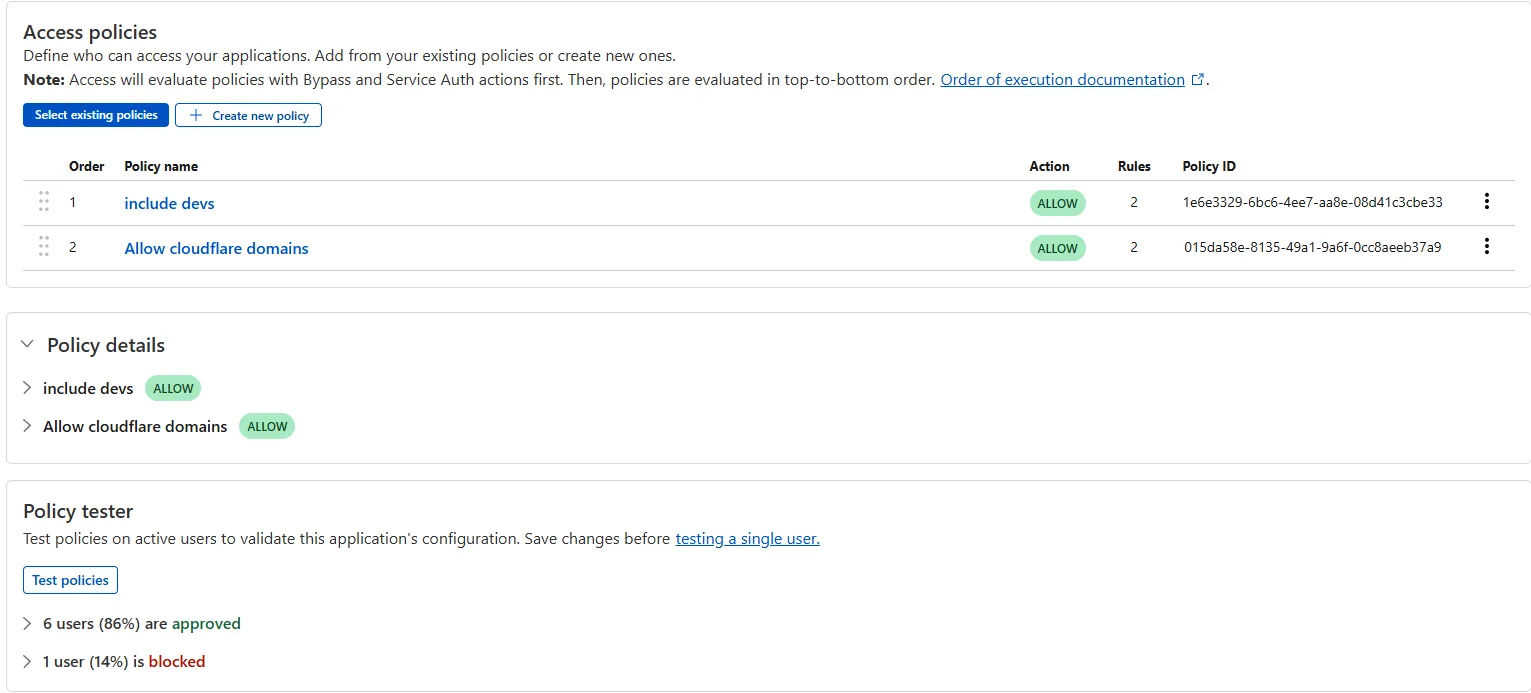
## 2025-04-14
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**New predefined detection entry for ICD-11**
You now have access to the World Health Organization (WHO) 2025 edition of the [International Classification of Diseases 11th Revision (ICD-11)](https://www.who.int/news/item/14-02-2025-who-releases-2025-update-to-the-international-classification-of-diseases-%28icd-11%29) as a predefined detection entry. The new dataset can be found in the [Health Information](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/predefined-profiles/#health-information) predefined profile.
ICD-10 dataset remains available for use.
## 2025-04-11
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**HTTP redirect and custom block page redirect**
You can now use more flexible redirect capabilities in Cloudflare One with Gateway.
* A new **Redirect** action is available in the HTTP policy builder, allowing admins to redirect users to any URL when their request matches a policy. You can choose to preserve the original URL and query string, and optionally include policy context via query parameters.
* For **Block** actions, admins can now configure a custom URL to display when access is denied. This block page redirect is set at the account level and can be overridden in DNS or HTTP policies. Policy context can also be passed along in the URL.
Learn more in our documentation for [HTTP Redirect](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#redirect) and [Block page redirect](https://developers.cloudflare.com/cloudflare-one/reusable-components/custom-pages/gateway-block-page/#redirect-to-a-block-page).
## 2025-04-09
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Cloudflare Zero Trust SCIM User and Group Provisioning Logs**
[Cloudflare Zero Trust SCIM provisioning](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/scim) now has a full audit log of all create, update and delete event from any SCIM Enabled IdP. The [SCIM logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/scim-logs/) support filtering by IdP, Event type, Result and many more fields. This will help with debugging user and group update issues and questions.
SCIM logs can be found on the Zero Trust Dashboard under **Logs** -> **SCIM provisioning**.
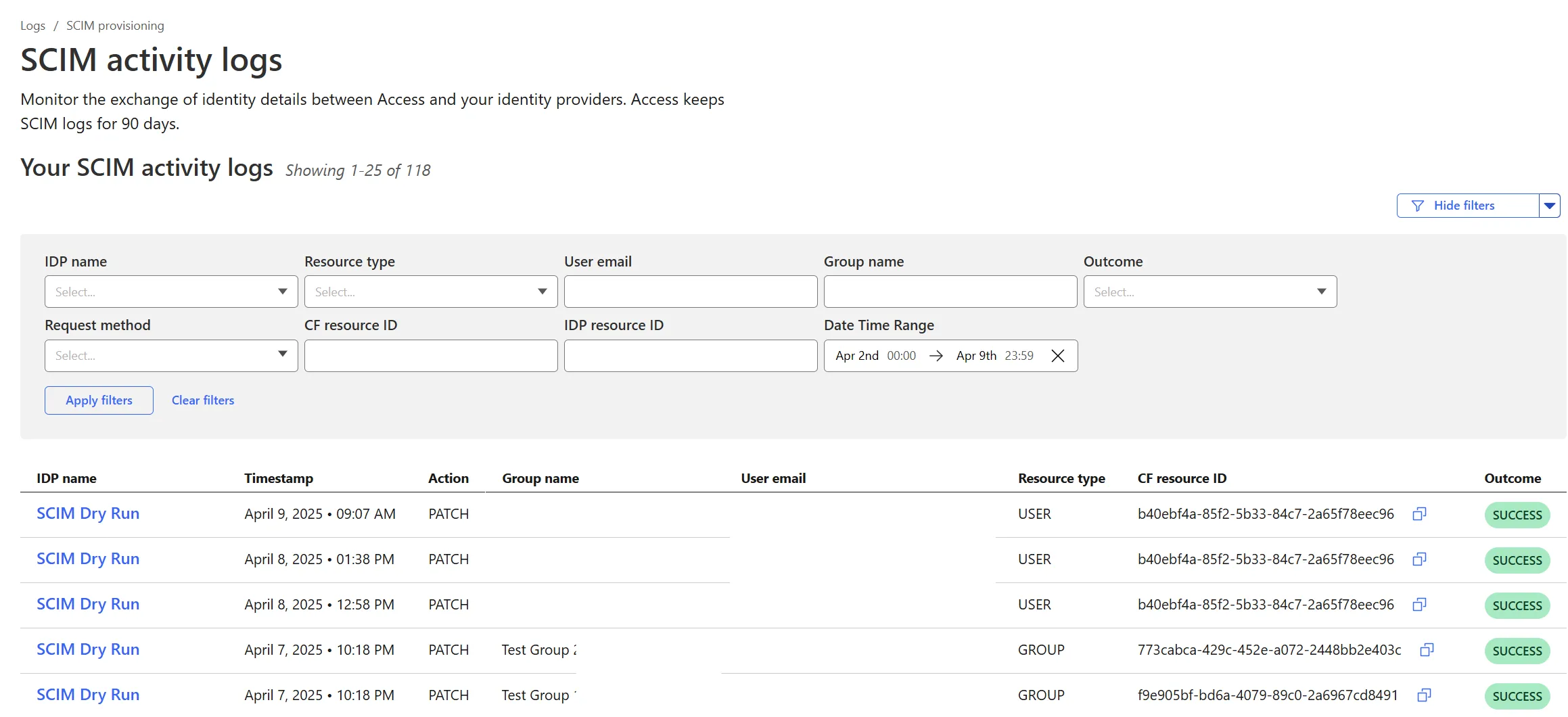
## 2025-04-08
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.2.664.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for captive portal detection for the 2025.2.600.0 release.
**Changes and improvements**
* Fix to reduce the number of browser tabs opened during captive portal logins.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-04-08
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.2.664.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for captive portal detection and PF state tables for the 2025.2.600.0 release.
**Changes and improvements**
* Fix to reduce the number of browser tabs opened during captive portal logins.
* Improvement to exclude local DNS traffic entries from PF state table to reduce risk of connectivity issues from exceeding table capacity.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
## 2025-04-01
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**CASB and Email security**
With Email security, you get two free CASB integrations.
Use one SaaS integration for Email security to sync with your directory of users, take actions on delivered emails, automatically provide EMLs for reclassification requests for clean emails, discover CASB findings and more.
With the other integration, you can have a separate SaaS integration for CASB findings for another SaaS provider.
Refer to [Add an integration](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/#add-an-integration) to learn more about this feature.
This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-03-31
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.2.600.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains support for a new WARP setting, [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices). It also includes significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Fixed an issue with device revocation and re-registration when switching configurations.
* Added a new [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
## 2025-03-31
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.2.600.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains support for a new WARP setting, [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices). It also includes significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* Added the ability to control if the WARP interface IPs are [registered with DNS servers](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#warp-interface-ip-dns-registration) or not.
* Removed DNS logs view from the Windows client GUI. DNS logs can be viewed as part of `warp-diag` or by viewing the log file on the user's local directory.
* Fixed an issue that would result in a user receiving multiple re-authentication requests when waking their device from sleep.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Improvements to [Windows multi-user](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/) including support for fast user switching. If you are interested in testing this feature, reach out to your Cloudflare account team.
* Fixed an issue with device revocation and re-registration when switching configurations.
* Fixed an issue where DEX tests would run during certain sleep states where the networking stack was not fully up. This would result in failures that would be ignored.
* Added a new [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-03-31
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.2.600.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains support for a new WARP setting, [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices). It also includes significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Fixed an issue with device revocation and re-registration when switching configurations.
* Added a new [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
## 2025-03-21
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Secure DNS Locations Management User Role**
We're excited to introduce the [**Cloudflare Zero Trust Secure DNS Locations Write role**](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/#secure-dns-locations), designed to provide DNS filtering customers with granular control over third-party access when configuring their Protective DNS (PDNS) solutions.
Many DNS filtering customers rely on external service partners to manage their DNS location endpoints. This role allows you to grant access to external parties to administer DNS locations without overprovisioning their permissions.
**Secure DNS Location Requirements:**
* Mandate usage of [Bring your own DNS resolver IP addresses](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/dns-resolver-ips/#bring-your-own-dns-resolver-ip) if available on the account.
* Require source network filtering for IPv4/IPv6/DoT endpoints; token authentication or source network filtering for the DoH endpoint.
You can assign the new role via Cloudflare Dashboard (`Manage Accounts > Members`) or via API. For more information, refer to the [Secure DNS Locations documentation](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/#secure-dns-locations).
## 2025-03-17
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**Cloudflare One Agent for Android (version 2.4)**
A new GA release for the Android Cloudflare One Agent is now available in the [Google Play Store](https://play.google.com/store/apps/details?id=com.cloudflare.cloudflareoneagent). This release includes a new feature allowing [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url) during enrollment, as well as fixes and minor improvements.
**Changes and improvements**
* Improved in-app error messages.
* Improved mobile client login with support for [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url).
* Fixed an issue preventing admin split tunnel settings taking priority for traffic from certain applications.
## 2025-03-17
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**Cloudflare One Agent for iOS (version 1.10)**
A new GA release for the iOS Cloudflare One Agent is now available in the [iOS App Store](https://apps.apple.com/us/app/cloudflare-one-agent/id6443476492). This release includes a new feature allowing [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url) during enrollment, as well as fixes and minor improvements.
**Changes and improvements**
* Improved in-app error messages.
* Improved mobile client login with support for [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url).
* Bug fixes and performance improvements.
## 2025-03-13
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.2.460.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Fixed issue with device revocation and re-registration when switching configurations.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
## 2025-03-13
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.2.460.1)**
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* Added the ability to control if the WARP interface IPs are [registered with DNS servers](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#warp-interface-ip-dns-registration) or not.
* Removed DNS logs view from the Windows client GUI. DNS logs can be viewed as part of `warp-diag` or by viewing the log file on the user's local directory.
* Fixed issue that would result in a user receiving multiple re-authentication requests when waking their device from sleep.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Improvements to [Windows multi-user](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/) including support for fast user switching. If you are interested in testing this feature, reach out to your Cloudflare account team.
* Fixed issue with device revocation and re-registration when switching configurations.
* Fixed issue where DEX tests would run during certain sleep states where the networking stack was not fully up. This would result in failures that would be ignored.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-03-13
[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
**Cloudflare IP Ranges List**
Magic Firewall now supports a new managed list of Cloudflare IP ranges. This list is available as an option when creating a Magic Firewall policy based on IP source/destination addresses. When selecting "is in list" or "is not in list", the option "**Cloudflare IP Ranges**" will appear in the dropdown menu.
This list is based on the IPs listed in the Cloudflare [IP ranges](https://www.cloudflare.com/en-gb/ips/). Updates to this managed list are applied automatically.

Note: IP Lists require an advanced Magic Firewall subscription. For more details about Magic Firewall plans, refer to [Plans](https://developers.cloudflare.com/magic-firewall/plans).
## 2025-03-07
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
**Cloudflare One Agent now supports Endpoint Monitoring**
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into device, network, and application performance across your Cloudflare SASE deployment. The latest release of the Cloudflare One agent (v2025.1.861) now includes device endpoint monitoring capabilities to provide deeper visibility into end-user device performance which can be analyzed directly from the dashboard.
Device health metrics are now automatically collected, allowing administrators to:
* View the last network a user was connected to
* Monitor CPU and RAM utilization on devices
* Identify resource-intensive processes running on endpoints

This feature complements existing DEX features like [synthetic application monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/) and [network path visualization](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/traceroute/), creating a comprehensive troubleshooting workflow that connects application performance with device state.
For more details refer to our [DEX](https://developers.cloudflare.com/cloudflare-one/insights/dex/) documentation.
## 2025-03-04
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
**Gain visibility into user actions in Zero Trust Browser Isolation sessions**
We're excited to announce that new logging capabilities for [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/) through [Logpush](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/) are available in Beta starting today!
With these enhanced logs, administrators can gain visibility into end user behavior in the remote browser and track blocked data extraction attempts, along with the websites that triggered them, in an isolated session.
```json
{
"AccountID": "$ACCOUNT_ID",
"Decision": "block",
"DomainName": "www.example.com",
"Timestamp": "2025-02-27T23:15:06Z",
"Type": "copy",
"UserID": "$USER_ID"
}
```
User Actions available:
* **Copy & Paste**
* **Downloads & Uploads**
* **Printing**
Learn more about how to get started with Logpush in our [documentation](https://developers.cloudflare.com/logs/logpush/).
## 2025-03-03
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**New SAML and OIDC Fields and SAML transforms for Access for SaaS**
[Access for SaaS applications](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/http-apps/saas-apps/) now include more configuration options to support a wider array of SaaS applications.
**SAML and OIDC Field Additions**
OIDC apps now include:
* Group Filtering via RegEx
* OIDC Claim mapping from an IdP
* OIDC token lifetime control
* Advanced OIDC auth flows including hybrid and implicit flows
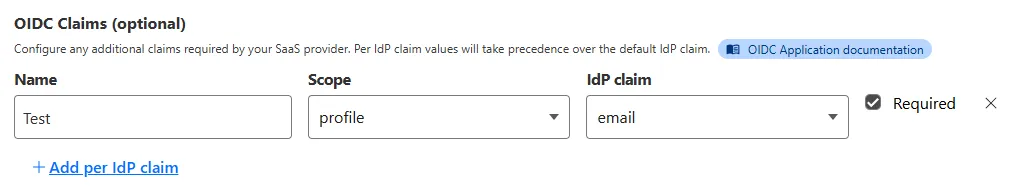
SAML apps now include improved SAML attribute mapping from an IdP.
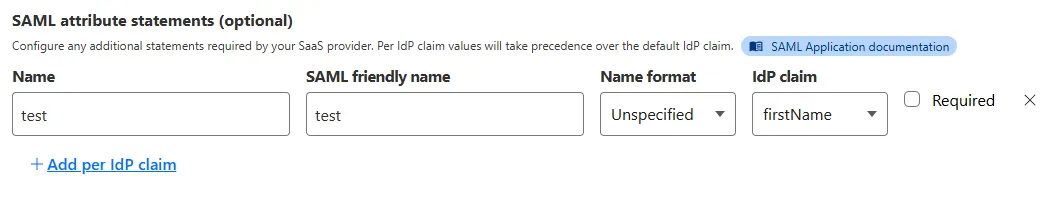
**SAML transformations**
SAML identities sent to Access applications can be fully customized using JSONata expressions. This allows admins to configure the precise identity SAML statement sent to a SaaS application.
## 2025-03-01
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Use Logpush for Email security detections**
You can now send detection logs to an endpoint of your choice with Cloudflare Logpush.
Filter logs matching specific criteria you have set and select from over 25 fields you want to send. When creating a new Logpush job, remember to select **Email security alerts** as the dataset.
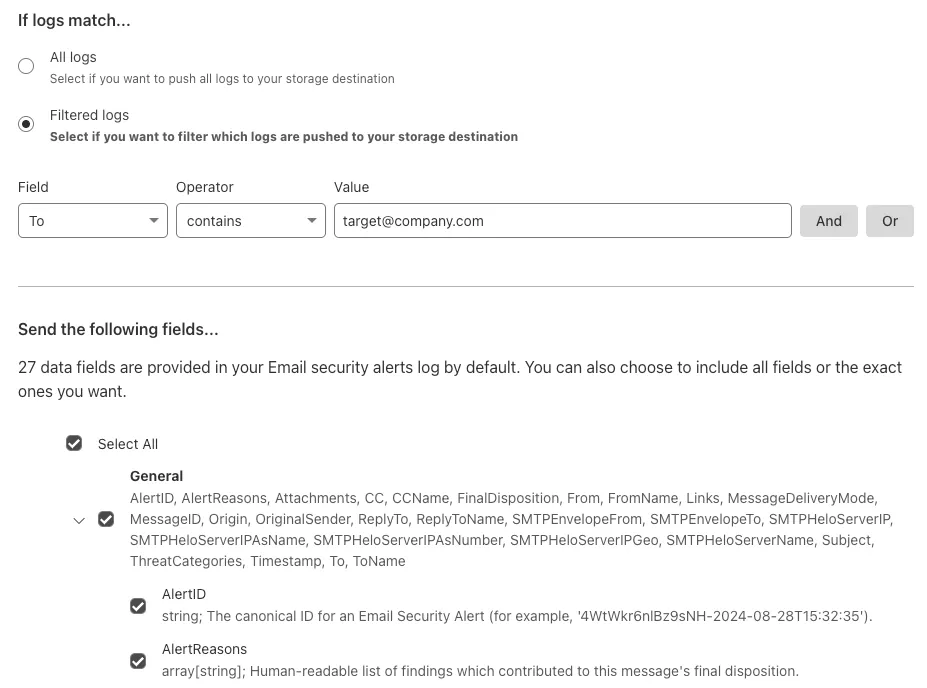
For more information, refer to [Enable detection logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-detection-logs).
This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-02-27
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Check status of Email security or Area 1**
Concerns about performance for Email security or Area 1? You can now check the operational status of both on the [Cloudflare Status page](https://www.cloudflarestatus.com/).
For Email security, look under **Cloudflare Sites and Services**.
* **Dashboard** is the dashboard for Cloudflare, including Email security
* **Email security (Zero Trust)** is the processing of email
* **API** are the Cloudflare endpoints, including the ones for Email security
For Area 1, under **Cloudflare Sites and Services**:
* **Area 1 - Dash** is the dashboard for Cloudflare, including Email security
* **Email security (Area1)** is the processing of email
* **Area 1 - API** are the Area 1 endpoints

This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-02-25
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Use DLP Assist for M365**
Cloudflare Email security customers who have Microsoft 365 environments can quickly deploy an Email DLP (Data Loss Prevention) solution for free.
Simply deploy our add-in, create a DLP policy in Cloudflare, and configure Outlook to trigger behaviors like displaying a banner, alerting end users before sending, or preventing delivery entirely.
Refer to [Outbound Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/email-security/outbound-dlp/) to learn more about this feature.
In GUI alert:
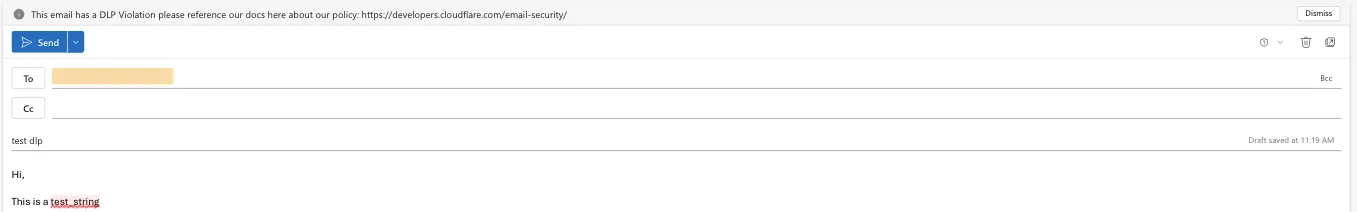
Alert before sending:
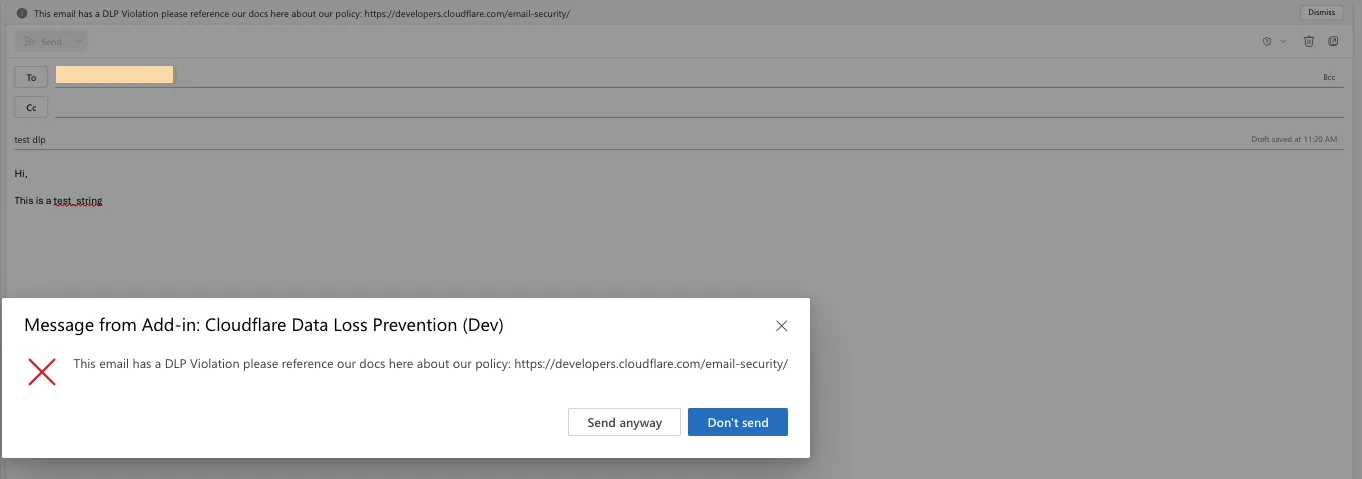
Prevent delivery:
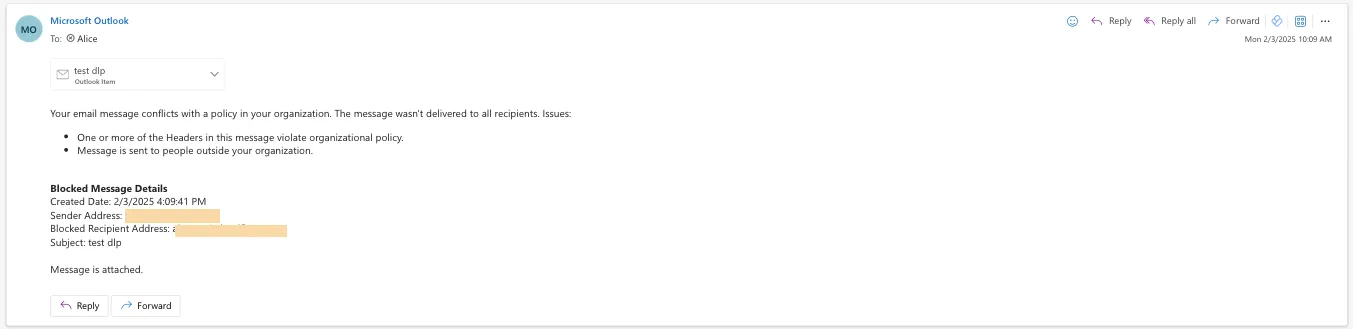
This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-02-19
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Windows (version 2025.1.861.0)**
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains only improvements.
**Changes and improvements**
* Improved command line interface for Access for Infrastructure with added function for filtering and ordering.
* Fixed client connectivity issues when switching between managed network profiles that use different WARP protocols.
* Added support for WARP desktop to use additional DoH endpoints to help reduce NAT congestion.
* Improved connectivity check reliability in certain split tunnel configurations.
* Improved reading of device DNS settings at connection restart.
* Improved WARP connectivity in environments with virtual machine interfaces.
* Improved Wireguard connection stability on reconnections.
* Improved reliability of device posture checks for OS Version, Unique Client ID, Domain Joined, Disk Encryption, and Firewall attributes.
* Added additional HTTP/3 QUIC connectivity test to warp-diag.
* Added support for collection of system health metrics for enhanced device Digital Experience Monitoring.
* Automated the removal of active registrations for devices with multiple registrations with the same Zero Trust organization.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
## 2025-02-19
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.1.861.0)**
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
Note: If using macOS Sequoia, Cloudflare recommends the use of macOS 15.3 or later. With macOS 15.3, Apple addressed several issues that may have caused the WARP client to not behave as expected when used with macOS 15.0.x.
**Changes and improvements**
* Improved command line interface for Access for Infrastructure with added function for filtering and ordering.
* Fixed client connectivity issues when switching between managed network profiles that use different WARP protocols.
* Improved OS version posture checks on macOS for greater reliability and availability.
* Added support for WARP desktop to use additional DoH endpoints to help reduce NAT congestion.
* Improved Wireguard connection stability on reconnections.
* Added additional HTTP/3 QUIC connectivity test to `warp-diag`.
* Added support for collection of system health metrics for enhanced device Digital Experience Monitoring.
* Automated the removal of active registrations for devices with multiple registrations with the same Zero Trust organization.
* Fixes issues with deleted registration at start up.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
## 2025-02-19
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for Linux (version 2025.1.861.0)**
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release includes fixes and minor improvements.
**Changes and improvements**
* Improved command line interface for Access for Infrastructure with added function for filtering and ordering.
* Fixed client connectivity issues when switching between managed network profiles that use different WARP protocols.
* Added support for WARP desktop to use additional DoH endpoints to help reduce NAT congestion.
* Improved Wireguard connection stability on reconnections.
* Added additional HTTP/3 QUIC connectivity test to `warp-diag`.
* Added support for collection of system health metrics for enhanced device Digital Experience Monitoring.
* Automated the removal of active registrations for devices with multiple registrations with the same Zero Trust organization.
## 2025-02-14
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
**Configure your Magic WAN Connector to connect via static IP assigment**
You can now locally configure your [Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/) to work in a static IP configuration.
This local method does not require having access to a DHCP Internet connection. However, it does require being comfortable with using tools to access the serial port on Magic WAN Connector as well as using a serial terminal client to access the Connector's environment.
For more details, refer to [WAN with a static IP address](https://developers.cloudflare.com/magic-wan/configuration/connector/configure-hardware-connector/#bootstrap-via-serial-console).
## 2025-02-07
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Open email links with Security Center**
You can now investigate links in emails with Cloudflare Security Center to generate a report containing a myriad of technical details: a phishing scan, SSL certificate data, HTTP request and response data, page performance data, DNS records, what technologies and libraries the page uses, and more.
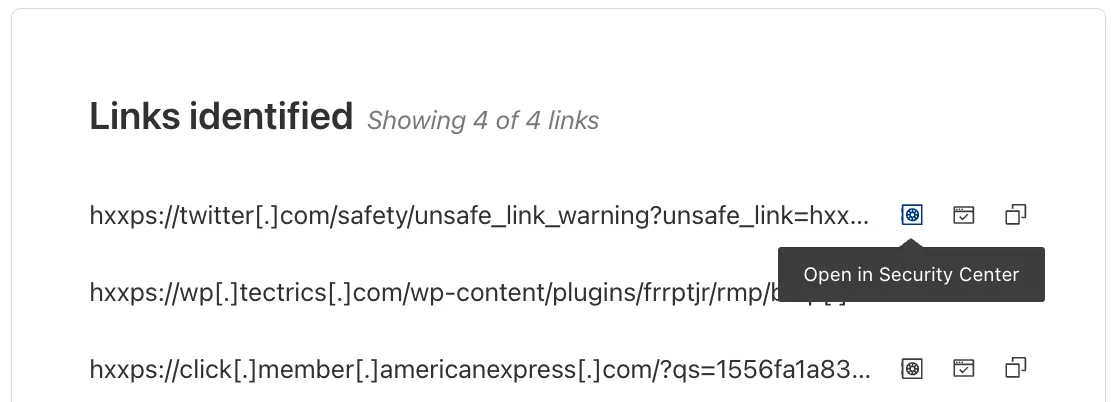
From **Investigation**, go to **View details**, and look for the **Links identified** section. Select **Open in Security Center** next to each link. **Open in Security Center** allows your team to quickly generate a detailed report about the link with no risk to the analyst or your environment.
For more details, refer to [Open links](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#open-links).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2025-02-07
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**WARP client for macOS (version 2025.1.634.1)**
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains only a hotfix from the 2025.1.447.1 release. Note: If using macOS Sequoia, Cloudflare recommends the use of macOS 15.2 or later. With macOS 15.2, Apple addressed several issues that may have caused the WARP client to not behave as expected when used with macOS 15.0.x. **Changes and improvements** - Improved device registration retrieval for graceful restarts **Known issues** - macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.2 or later.
## 2025-02-03
[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**Block files that are password-protected, compressed, or otherwise unscannable.**
Gateway HTTP policies can now block files that are password-protected, compressed, or otherwise unscannable.
These unscannable files are now matched with the [Download and Upload File Types traffic selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#download-and-upload-file-types) for HTTP policies:
* Password-protected Microsoft Office document
* Password-protected PDF
* Password-protected ZIP archive
* Unscannable ZIP archive
To get started inspecting and modifying behavior based on these and other rules, refer to [HTTP filtering](https://developers.cloudflare.com/cloudflare-one/traffic-policies/initial-setup/http/).
## 2025-01-20
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
**Detect source code leaks with Data Loss Prevention**
You can now detect source code leaks with Data Loss Prevention (DLP) with predefined checks against common programming languages.
The following programming languages are validated with natural language processing (NLP).
* C
* C++
* C#
* Go
* Haskell
* Java
* JavaScript
* Lua
* Python
* R
* Rust
* Swift
DLP also supports confidence level for [source code profiles](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/predefined-profiles/#source-code).
For more details, refer to [DLP profiles](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/).
## 2025-01-15
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Export SSH command logs with Access for Infrastructure using Logpush**
Availability
Only available on Enterprise plans.
Cloudflare now allows you to send SSH command logs to storage destinations configured in [Logpush](https://developers.cloudflare.com/logs/logpush/), including third-party destinations. Once exported, analyze and audit the data as best fits your organization! For a list of available data fields, refer to the [SSH logs dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/ssh_logs/).
To set up a Logpush job, refer to [Logpush integration](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/).
## 2024-12-19
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Escalate user submissions**
After you triage your users' submissions (that are machine reviewed), you can now escalate them to our team for reclassification (which are instead human reviewed). User submissions from the submission alias, PhishNet, and our API can all be escalated.
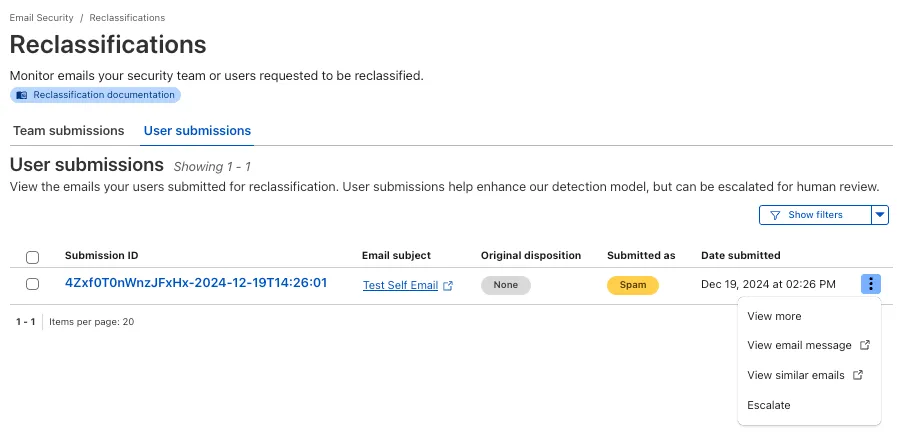
From **Reclassifications**, go to **User submissions**. Select the three dots next to any of the user submissions, then select **Escalate** to create a team request for reclassification. The Cloudflare dashboard will then show you the submissions on the **Team Submissions** tab.
Refer to [User submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/user-submissions/) to learn more about this feature.
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
## 2024-12-19
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
**Troubleshoot tunnels with diagnostic logs**
The latest `cloudflared` build [2024.12.2](https://github.com/cloudflare/cloudflared/releases/tag/2024.12.2) introduces the ability to collect all the diagnostic logs needed to troubleshoot a `cloudflared` instance.
A diagnostic report collects data from a single instance of `cloudflared` running on the local machine and outputs it to a `cloudflared-diag` file.
The `cloudflared-diag-YYYY-MM-DDThh-mm-ss.zip` archive contains the files listed below. The data in a file either applies to the `cloudflared` instance being diagnosed (`diagnosee`) or the instance that triggered the diagnosis (`diagnoser`). For example, if your tunnel is running in a Docker container, the diagnosee is the Docker instance and the diagnoser is the host instance.
| File name | Description | Instance |
| - | - | - |
| `cli-configuration.json` | [Tunnel run parameters](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/configure-tunnels/cloudflared-parameters/run-parameters/) used when starting the tunnel | diagnosee |
| `cloudflared_logs.txt` | [Tunnel log file](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/logs/)[1](#user-content-fn-1) | diagnosee |
| `configuration.json` | Tunnel configuration parameters | diagnosee |
| `goroutine.pprof` | goroutine profile made available by `pprof` | diagnosee |
| `heap.pprof` | heap profile made available by `pprof` | diagnosee |
| `metrics.txt` | Snapshot of [Tunnel metrics](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/metrics/#available-metrics) at the time of diagnosis | diagnosee |
| `network.txt` | JSON traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
| `raw-network.txt` | Raw traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
| `systeminformation.json` | Operating system information and resource usage | diagnosee |
| `task-result.json` | Result of each diagnostic task | diagnoser |
| `tunnelstate.json` | Tunnel connections at the time of diagnosis | diagnosee |
## Footnotes
1. If the log file is blank, you may need to [set `--loglevel` to `debug`](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/logs/#view-logs-on-the-server) when you start the tunnel. The `--loglevel` parameter is only required if you ran the tunnel from the CLI using a `cloudflared tunnel run` command. It is not necessary if the tunnel runs as a Linux/macOS service or runs in Docker/Kubernetes. [↩](#user-content-fnref-1)
For more information, refer to [Diagnostic logs](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/troubleshoot-tunnels/diag-logs/).
## 2024-12-19
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Increased transparency for phishing email submissions**
You now have more transparency about team and user submissions for phishing emails through a **Reclassification** tab in the Zero Trust dashboard.
Reclassifications happen when users or admins [submit a phish](https://developers.cloudflare.com/cloudflare-one/email-security/settings/phish-submissions/) to Email security. Cloudflare reviews and - in some cases - reclassifies these emails based on improvements to our machine learning models.
This new tab increases your visibility into this process, allowing you to view what submissions you have made and what the outcomes of those submissions are.
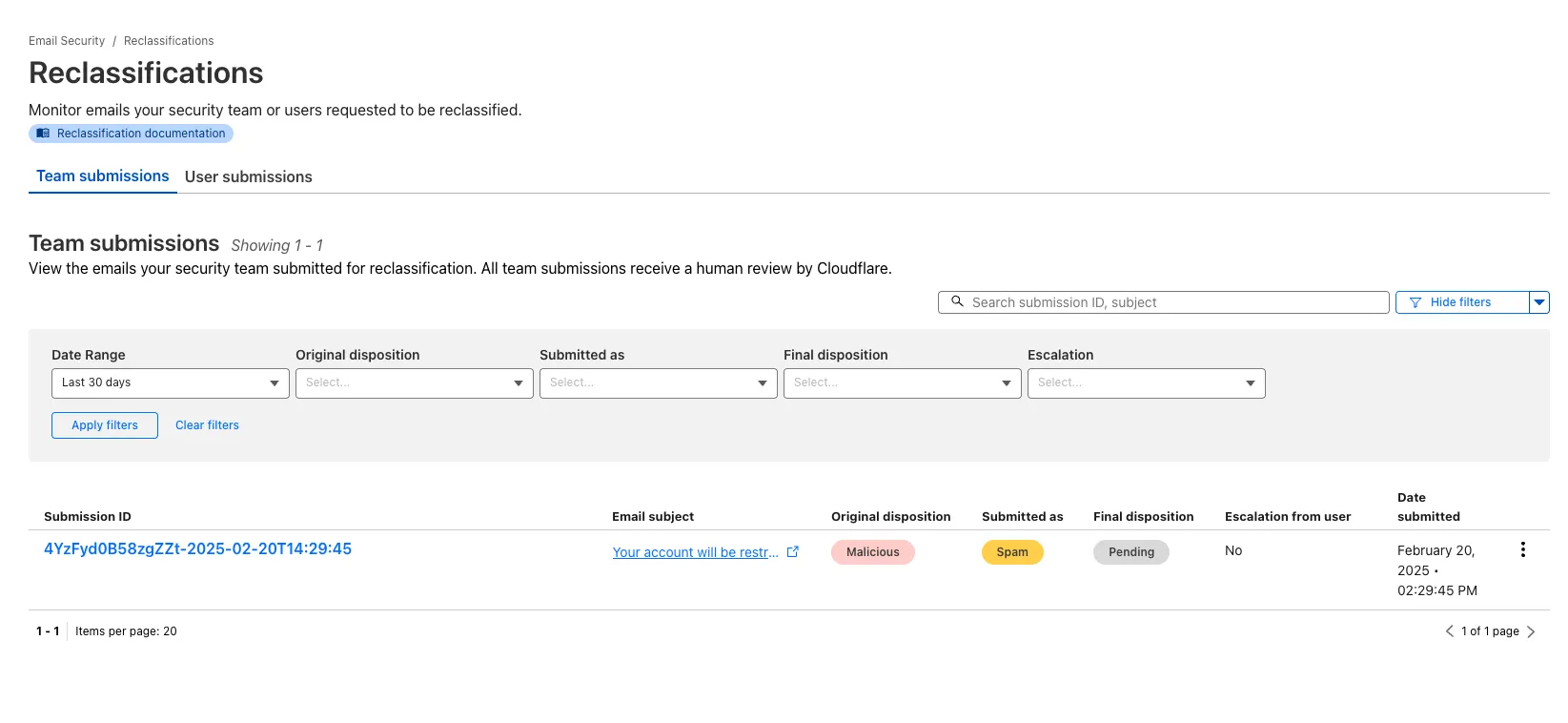
## 2024-12-17
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Network Interconnect](https://developers.cloudflare.com/network-interconnect/)
**Establish BGP peering over Direct CNI circuits**
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
Refer to [Magic WAN BGP peering](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes) or [Magic Transit BGP peering](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes) to learn more about this feature and how to set it up.
## 2024-12-05
[Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/)
**Generate customized terraform files for building cloud network on-ramps**
You can now generate customized terraform files for building cloud network on-ramps to [Magic WAN](https://developers.cloudflare.com/magic-wan/).
[Magic Cloud](https://developers.cloudflare.com/magic-cloud-networking/) can scan and discover existing network resources and generate the required terraform files to automate cloud resource deployment using their existing infrastructure-as-code workflows for cloud automation.
You might want to do this to:
* Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
* Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
For more details, refer to [Set up with Terraform](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#set-up-with-terraform).
## 2024-11-22
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
**Find security misconfigurations in your AWS cloud environment**
You can now use CASB to find security misconfigurations in your AWS cloud environment using [Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/).
You can also [connect your AWS compute account](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/aws-s3/#compute-account) to extract and scan your S3 buckets for sensitive data while avoiding egress fees. CASB will scan any objects that exist in the bucket at the time of configuration.
To connect a compute account to your AWS integration:
1. In [Cloudflare One](https://one.dash.cloudflare.com), go to **Cloud & SaaS findings** > **Integrations**.
2. Find and select your AWS integration.
3. Select **Open connection instructions**.
4. Follow the instructions provided to connect a new compute account.
5. Select **Refresh**.
## 2024-11-21
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
**Improved non-English keyboard support**
You can now type in languages that use diacritics (like á or ç) and character-based scripts (such as Chinese, Japanese, and Korean) directly within the remote browser. The isolated browser now properly recognizes non-English keyboard input, eliminating the need to copy and paste content from a local browser or device.
## 2024-11-07
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
**Use Logpush for Email security user actions**
You can now send user action logs for Email security to an endpoint of your choice with Cloudflare Logpush.
Filter logs matching specific criteria you have set or select from multiple fields you want to send. For all users, we will log the date and time, user ID, IP address, details about the message they accessed, and what actions they took.
When creating a new Logpush job, remember to select **Audit logs** as the dataset and filter by:
* **Field**: `"ResourceType"`
* **Operator**: `"starts with"`
* **Value**: `"email_security"`.
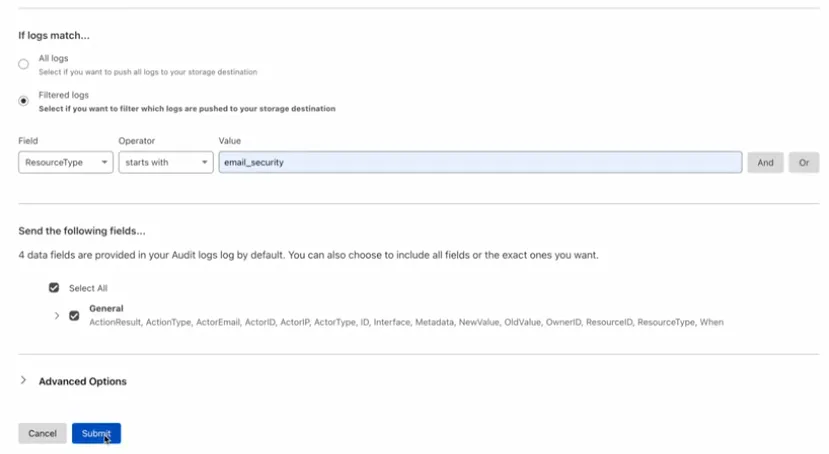
For more information, refer to [Enable user action logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-user-action-logs).
This feature is available across all Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
## 2024-10-02
[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
**Search for custom rules using rule name and/or ID**
The Magic Firewall dashboard now allows you to search custom rules using the rule name and/or ID.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Analytics & Logs** > **Network Analytics**.
3. Select **Magic Firewall**.
4. Add a filter for **Rule ID**.

Additionally, the rule ID URL link has been added to Network Analytics.
## 2024-10-01
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
**Eliminate long-lived credentials and enhance SSH security with Cloudflare Access for Infrastructure**
Organizations can now eliminate long-lived credentials from their SSH setup and enable strong multi-factor authentication for SSH access, similar to other Access applications, all while generating access and command logs.
SSH with [Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/non-http/infrastructure-apps/) uses short-lived SSH certificates from Cloudflare, eliminating SSH key management and reducing the security risks associated with lost or stolen keys. It also leverages a common deployment model for Cloudflare One customers: [WARP-to-Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-warp-to-tunnel/).
SSH with Access for Infrastructure enables you to:
* **Author fine-grained policy** to control who may access your SSH servers, including specific ports, protocols, and SSH users.
* **Monitor infrastructure access** with Access and SSH command logs, supporting regulatory compliance and providing visibility in case of security breach.
* **Preserve your end users' workflows.** SSH with Access for Infrastructure supports native SSH clients and does not require any modifications to users’ SSH configs.
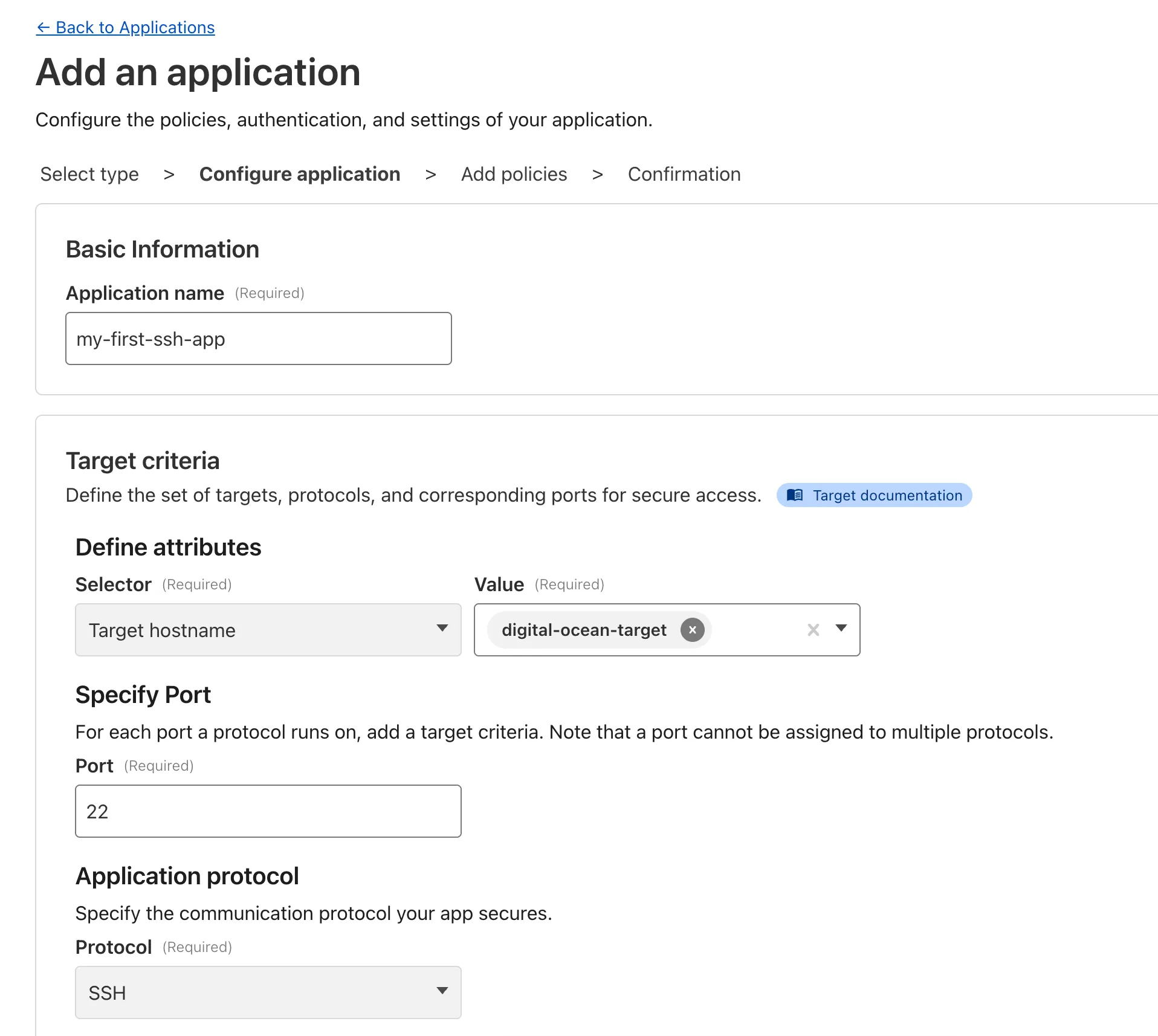
To get started, refer to [SSH with Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/).
## 2024-06-17
[Risk Score](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)
**Exchange user risk scores with Okta**
Beyond the controls in [Zero Trust](https://developers.cloudflare.com/cloudflare-one/), you can now [exchange user risk scores](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/risk-score/#send-risk-score-to-okta) with Okta to inform SSO-level policies.
First, configure Cloudflare One to send user risk scores to Okta.
1. Set up the [Okta SSO integration](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/okta/).
2. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Integrations** > **Identity providers**.
3. In **Your identity providers**, locate your Okta integration and select **Edit**.
4. Turn on **Send risk score to Okta**.
5. Select **Save**.
6. Upon saving, Cloudflare One will display the well-known URL for your organization. Copy the value.
Next, configure Okta to receive your risk scores.
1. On your Okta admin dashboard, go to **Security** > **Device Integrations**.
2. Go to **Receive shared signals**, then select **Create stream**.
3. Name your integration. In **Set up integration with**, choose *Well-known URL*.
4. In **Well-known URL**, enter the well-known URL value provided by Cloudflare One.
5. Select **Create**.
## 2024-06-16
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Browser Isolation ](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)[CASB ](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)[Cloudflare Tunnel ](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)[Digital Experience Monitoring ](https://developers.cloudflare.com/cloudflare-one/insights/dex/)[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[Email security ](https://developers.cloudflare.com/cloudflare-one/email-security/)[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Magic Cloud Networking ](https://developers.cloudflare.com/magic-cloud-networking/)[Magic Firewall ](https://developers.cloudflare.com/magic-firewall/)[Magic Network Monitoring ](https://developers.cloudflare.com/magic-network-monitoring/)[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Network Interconnect ](https://developers.cloudflare.com/network-interconnect/)[Risk Score ](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
**Explore product updates for Cloudflare One**
Welcome to your new home for product updates on [Cloudflare One](https://developers.cloudflare.com/cloudflare-one/).
Our [new changelog](https://developers.cloudflare.com/changelog/) lets you read about changes in much more depth, offering in-depth examples, images, code samples, and even gifs.
If you are looking for older product updates, refer to the following locations.
Older product updates
* [Access](https://developers.cloudflare.com/cloudflare-one/changelog/access/)
* [Browser Isolation](https://developers.cloudflare.com/cloudflare-one/changelog/browser-isolation/)
* [CASB](https://developers.cloudflare.com/cloudflare-one/changelog/casb/)
* [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/changelog/tunnel/)
* [Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/changelog/dlp/)
* [Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/changelog/dex/)
* [Email security](https://developers.cloudflare.com/cloudflare-one/changelog/email-security/)
* [Gateway](https://developers.cloudflare.com/cloudflare-one/changelog/gateway/)
* [Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/changelog/)
* [Magic Firewall](https://developers.cloudflare.com/magic-firewall/changelog/)
* [Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/changelog/)
* [Magic Transit](https://developers.cloudflare.com/magic-transit/changelog/)
* [Magic WAN](https://developers.cloudflare.com/magic-wan/changelog/)
* [Network Interconnect](https://developers.cloudflare.com/network-interconnect/changelog/)
* [Risk score](https://developers.cloudflare.com/cloudflare-one/changelog/risk-score/)
* [Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/changelog/warp/)
---
title: Cloud and SaaS findings · Cloudflare One docs
description: Cloudflare's API-driven Cloud Access Security Broker (CASB)
integrates with SaaS applications and cloud environments to scan for
misconfigurations, unauthorized user activity, shadow IT, and other data
security issues that can occur after a user has successfully logged in.
lastUpdated: 2025-10-24T15:44:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/cloud-and-saas-findings/
md: https://developers.cloudflare.com/cloudflare-one/cloud-and-saas-findings/index.md
---
Availability
Available for all Zero Trust users.
Free users can configure up to two CASB integrations. You must upgrade to an Enterprise plan to view the details of a finding instance.
Cloudflare's API-driven [Cloud Access Security Broker](https://www.cloudflare.com/learning/access-management/what-is-a-casb/) (CASB) integrates with SaaS applications and cloud environments to scan for misconfigurations, unauthorized user activity, [shadow IT](https://www.cloudflare.com/learning/access-management/what-is-shadow-it/), and other data security issues that can occur after a user has successfully logged in.
For a list of available findings, refer to [Cloud and SaaS integrations](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/).
## Manage CASB integrations
When you integrate a third-party SaaS application or cloud environment with Cloudflare CASB, you allow CASB to make API calls to its endpoint and read relevant data on your behalf. The CASB integration permissions are read-only and follow the least privileged model. In other words, only the minimum access required to perform a scan is granted.
### Prerequisites
Before you can integrate a SaaS application or cloud environment with CASB, your account with that integration must meet certain requirements. Refer to the SaaS application or cloud environment's [integration guide](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/) to learn more about the prerequisites and permissions.
### Add an integration
1. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Cloud & SaaS findings** > **Integrations**.
2. Select **Connect an integration** or **Add integration**.
3. Browse the available integrations and select the application you would like to add.
4. Follow the step-by-step integration instructions in the UI.
5. To run your first scan, select **Save integration**.
After the first scan, CASB will automatically scan your SaaS application or cloud environment on a frequent basis to keep up with any changes. Scan intervals will vary due to each application having their own set of requirements, but the frequency is typically between every 1 hour and every 24 hours.
Once CASB detects at least one finding, you can [view and manage your findings](https://developers.cloudflare.com/cloudflare-one/cloud-and-saas-findings/manage-findings/).
### Pause an integration
1. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Cloud & SaaS findings** > **Integrations**.
2. Find the integration you would like to pause and select **Configure**.
3. To stop scanning the application, turn off **Scan for findings**.
4. Select **Save integration**.
You can resume CASB scanning at any time by turning on **Scan for findings**.
### Delete an integration
Warning
When you delete an integration, all keys and OAuth data will be deleted. This means you cannot restore a deleted integration or its scanned data.
1. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Cloud & SaaS findings** > **Integrations**.
2. Find the integration you would like to delete and select **Configure**.
3. Select **Disenroll**.
To resume scanning the integration for findings, you will need to [add the integration](#add-an-integration) again.
---
title: Data loss prevention · Cloudflare One docs
description: Cloudflare Data Loss Prevention (DLP) allows you to scan your web
traffic and SaaS applications for the presence of sensitive data such as
social security numbers, financial information, secret keys, and source code.
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/
md: https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/index.md
---
Availability
Available as an add-on to Zero Trust Enterprise plans.
Users on Zero Trust Free and Pay-as-you-go plans can use the [Financial Information](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/predefined-profiles/#financial-information) and [Social Security, Insurance, Tax, and Identifier Numbers](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/predefined-profiles/#social-security-insurance-tax-and-identifier-numbers) predefined profiles, [payload logging](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#log-the-payload-of-matched-rules), and [false positive reporting](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/#report-false-positives).
Cloudflare [Data Loss Prevention](https://www.cloudflare.com/learning/access-management/what-is-dlp/) (DLP) allows you to scan your web traffic and SaaS applications for the presence of sensitive data such as social security numbers, financial information, secret keys, and source code.
To prevent interference, Cloudflare does not write scanned content to disk. Instead, DLP only encrypts and temporarily stores content in memory. Optionally, you can configure [payload logging](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#log-the-payload-of-matched-rules) to store encrypted copies of payloads from matching HTTP requests or a [Logpush destination](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#send-http-requests-to-logpush-destination) to export entire matching HTTP requests.
## Data in transit
Data Loss Prevention complements [Secure Web Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) to detect sensitive data transferred in HTTP requests. DLP scans the entire HTTP body, which may include uploaded or downloaded files, chat messages, forms, and other web content. You can also use DLP with [Email security](https://developers.cloudflare.com/cloudflare-one/email-security/) to scan [outbound emails](https://developers.cloudflare.com/cloudflare-one/email-security/outbound-dlp/).
DLP requires [Gateway HTTP filtering](https://developers.cloudflare.com/cloudflare-one/traffic-policies/initial-setup/http/) with [TLS decryption](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/tls-decryption/) for visibility into data in transit. The depth of visibility varies for each site or application. DLP does not scan any traffic that bypasses Cloudflare Gateway (such as traffic that matches a [Do Not Inspect](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#do-not-inspect) policy).
To get started, refer to [Scan HTTP traffic with DLP](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/).
## Data at rest
Data Loss Prevention complements [Cloudflare CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/) to detect sensitive data stored in your SaaS applications. Unlike data in transit scans which read files sent through Cloudflare Gateway, CASB retrieves files directly via the API. Therefore, Gateway and WARP settings (such as [Do Not Inspect](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#do-not-inspect) policies and [Split Tunnel](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/split-tunnels/) configurations) will not affect data at rest scans.
To get started, refer to [Scan SaaS applications with DLP](https://developers.cloudflare.com/cloudflare-one/cloud-and-saas-findings/casb-dlp/).
## Supported file types
### Formats
DLP supports reporting and scanning the following file types:
* Text and CSV
* Microsoft Office 2007 and later (`.docx`, `.xlsx,` `.pptx`), including Microsoft 365
* PDF
* ZIP files containing the above
DLP will scan the text contained in text, Microsoft Office, and PDF files.
### Size
DLP can scan files less than or equal to 100 MB in size. ZIP files can be recursively compressed a maximum of 10 times, and each content file within the ZIP file must be less than or equal to 200 MB in uncompressed size.
---
title: Email security · Cloudflare One docs
description: Email security is the practice of protecting your email inbox from
cyber attacks and unwanted communication sent via email.
lastUpdated: 2025-12-04T22:38:54.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/email-security/
md: https://developers.cloudflare.com/cloudflare-one/email-security/index.md
---
Important
Refer to [Area 1](https://developers.cloudflare.com/email-security/) if you are looking for the Area 1 documentation.
Note
If you have not yet purchased Email security, you can try Email security with Retro Scan. Refer to [Retro Scan](https://developers.cloudflare.com/cloudflare-one/email-security/retro-scan/) to learn more.
Protect your email inbox with Email security.
Email security is the practice of protecting your email inbox from cyber attacks and unwanted communication sent via email.
Cloudflare's Email security uses Artificial Intelligence (AI), threat intelligence, and expert security rules to analyze every incoming email.
Email security protects your email inbox from phishing attacks, malware, [Business Email Compromise](https://www.cloudflare.com/en-gb/learning/email-security/business-email-compromise-bec/) attacks, and vendor email fraud.
Cloudflare's Email security integrates with your existing email provider (such as Microsoft 365 or Gmail), and reduces the amount of spam and phishing emails landing in your inbox. You can configure Email security via [API](https://developers.cloudflare.com/cloudflare-one/email-security/setup/post-delivery-deployment/api/), [BCC](https://developers.cloudflare.com/cloudflare-one/email-security/setup/post-delivery-deployment/bcc-journaling/bcc-setup/gmail-bcc-setup/gmail-bcc-setup/)/[Journaling](https://developers.cloudflare.com/cloudflare-one/email-security/setup/post-delivery-deployment/bcc-journaling/journaling-setup/m365-journaling/), or [MX/Inline](https://developers.cloudflare.com/cloudflare-one/email-security/setup/pre-delivery-deployment/mx-inline-deployment-setup/) deployment. All three deployments aim at protecting your organization from malicious activities.
When you complete the [setup process](https://developers.cloudflare.com/cloudflare-one/email-security/setup/), the Cloudflare dashboard will display the Email security overview page.
The Email security overview provides you with:
* **Quick actions**, where you can:
* View [submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/)
* Manage detection settings: manage [allow policies](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/allow-policies/), [blocked senders](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/blocked-senders/), [trusted domains](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/trusted-domains/), [impersonation registry](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/impersonation-registry/) and [additional detections](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/additional-detections/).
* [Run screens](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#screen-criteria)
* **Recommendations**: A series of recommendations. For example, you may be recommended to learn how to submit emails for submission, create policies, or protect users at risk of [impersonation](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/impersonation-registry/)
* **Email security metrics**: Activity from the last seven days.
* **Recently modified policies** A list of modified policies.
* **Education and resources**: Links to [implementation guides](https://developers.cloudflare.com/cloudflare-one/implementation-guides/), [Email security changelogs](https://developers.cloudflare.com/cloudflare-one/changelog/email-security/), and [API documentation](https://developers.cloudflare.com/api/resources/email_security/subresources/investigate/methods/get/)
To access the Email security overview:
1. Log in to [Cloudflare One](https://one.dash.cloudflare.com/).
2. Go to **Email security** > **Overview**.
---
title: FAQ · Cloudflare One docs
description: Review answers to the most commonly asked questions on Cloudflare
Zero Trust, as well as a troubleshooting section to help you solve common
issues and errors you may come across.
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/faq/
md: https://developers.cloudflare.com/cloudflare-one/faq/index.md
---
Review answers to the most commonly asked questions on Cloudflare Zero Trust, as well as a troubleshooting section to help you solve common issues and errors you may come across.
If you cannot find the answer you are looking for, go to our [community page](https://community.cloudflare.com/) and post your question there.
***
## Getting started with Cloudflare Zero Trust
For extra guidance on experiencing Cloudflare Zero Trust for the first time.
[Getting started ❯](https://developers.cloudflare.com/cloudflare-one/faq/getting-started-faq/)
## General
For general questions on Cloudflare Zero Trust and how it works.
[General ❯](https://developers.cloudflare.com/cloudflare-one/faq/general-faq/)
## Identity
For questions on identity providers and accessing applications behind Cloudflare Zero Trust.
[Identity ❯](https://developers.cloudflare.com/cloudflare-one/faq/authentication-faq/)
## Policies
For questions on how policies work, and how to create and test them.
[Policies ❯](https://developers.cloudflare.com/cloudflare-one/faq/policies-faq/)
## Devices
For questions on device connectivity and the WARP client.
[Devices ❯](https://developers.cloudflare.com/cloudflare-one/faq/devices-faq/)
## Tunnels
For questions on connecting applications with Tunnels.
[Tunnels ❯](https://developers.cloudflare.com/cloudflare-one/faq/cloudflare-tunnels-faq/)
## Troubleshooting
Got an unexpected error? Check if it is covered in our troubleshooting section.
[Troubleshooting ❯](https://developers.cloudflare.com/cloudflare-one/faq/troubleshooting/)
---
title: Glossary · Cloudflare One docs
description: Review definitions for Cloudflare One terms.
lastUpdated: 2025-11-21T23:11:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/glossary/
md: https://developers.cloudflare.com/cloudflare-one/glossary/index.md
---
Review definitions for Cloudflare One terms.
| Term | Definition |
| - | - |
| App Launcher | The App Launcher portal provides end users with a single dashboard to open applications secured by Cloudflare One. |
| application | The resource protected by Cloudflare One, which can be a subdomain, a path, or a SaaS application. |
| application token | A piece of data that grants a user access to a specific Access application for a period of time. Can be stored in a browser cookie or passed to the application in place of a normal password. |
| captive portal | A login screen shown to users when they connect to a public Wi-Fi. Captive portals typically occur in places such as airports, cafes, and hotels. |
| Cloudflare Access | Cloudflare Access replaces corporate VPNs with Cloudflare's network. It verifies attributes such as identity and device posture to grant users secure access to internal tools. |
| Cloudflare Browser Isolation | Cloudflare Browser Isolation seamlessly executes active webpage content in a secure isolated browser to protect users from zero-day attacks, malware, and phishing. |
| Cloudflare CASB | Cloudflare CASB provides comprehensive visibility and control over SaaS apps to prevent data leaks and compliance violations. It helps detect insider threats, shadow IT, risky data sharing, and bad actors. |
| Cloudflare Data Loss Prevention (DLP) | Cloudflare [Data Loss Prevention](https://www.cloudflare.com/learning/access-management/what-is-dlp/) (DLP) allows you to scan your web traffic and SaaS applications for the presence of sensitive data such as social security numbers, financial information, secret keys, and source code. |
| Cloudflare DEX | Cloudflare Digital Experience Monitoring (DEX) provides visibility into device, network, and application performance across your Zero Trust Organization. |
| Cloudflare Gateway | Cloudflare Gateway is a modern next-generation firewall between your user, device, or network and the public Internet. It includes DNS filtering to inspect and apply policies to all Internet-bound DNS queries. |
| Cloudflare One | The name for Cloudflare's Secure Access Service Edge (SASE) platform, which includes Zero Trust and network services. |
| Cloudflare One Agent | The name of the Cloudflare WARP client app on iOS and Android devices. |
| Cloudflare Tunnel | Cloudflare Tunnel uses software agents (`cloudflared` or WARP Connector) to establish a secure connection between a private network and Cloudflare. |
| Cloudflare Zero Trust | Cloudflare Zero Trust provides the power of Cloudflare's global network to your internal teams and infrastructure. It empowers users with secure, fast, and seamless access to any device on the Internet. |
| cloudflared | The software powering Cloudflare Tunnel. It runs on origin servers to connect applications or private networks to Cloudflare. |
| cloudflared replica | An additional instance of `cloudflared` that points to the same Cloudflare Tunnel. It ensures that your network remains online in case a single host running `cloudflared` goes down. |
| daemon | A program that performs tasks without active management or maintenance. |
| device posture | A way to evaluate the security of a user's device, for example by verifying its serial number or checking if it has the latest software updates. |
| device profile | A collection of WARP client settings applied to a specific set of devices in your organization. |
| device registration | An individual session of the WARP client on a physical device, with associated configuration including a unique public key, device profile, and virtual IP addresses (one IPv4 and one IPv6). |
| DNS filtering | DNS filtering uses the Domain Name System to block malicious websites and filter out harmful content, enhancing security and access control. |
| DNS location | DNS locations are a collection of DNS endpoints which can be mapped to physical entities such as offices, homes, or data centers. |
| DoH subdomain | A unique DoH subdomain for each DNS location in Cloudflare One used in WARP client settings. |
| fleet | A fleet is a collection of user devices. All devices in a fleet have WARP installed and are connected to a [Zero Trust Organization](https://developers.cloudflare.com/cloudflare-one/setup/#create-a-zero-trust-organization). |
| Hops | Hops refer to the stops an email makes as it travels from the sender to the recipient. |
| identity provider | An identity provider (IdP) stores and manages users' digital identities, enabling single sign-on and authentication for multiple applications. |
| initial resolved IP | A unique, ephemeral IP address that Gateway assigns to DNS queries when filtering network traffic by hostname. The IP is randomly selected from the `100.80.0.0/16` (IPv4) or `2606:4700:0cf1:4000::/64` (IPv6) range. |
| JSON web token | A compact way to securely transmit information between parties as a JSON object, often used for authentication. |
| locally-managed tunnel | A Cloudflare Tunnel that was created by running `cloudflared tunnel create ` on the command line. Tunnel configuration is stored in your local `cloudflared` directory. |
| managed network | A network location, such as an office, that is associated with a specific WARP client device profile. |
| MCP client | A Model Context Protocol (MCP) client is an AI program that can request information and receive responses from an MCP server. Examples of MCP clients include Claude Desktop, Cursor AI, and Windsurf. |
| MCP server | A web application that allows AI agents to access third-party data sources and APIs using the Model Context Protocol (MCP). For example, you can use an MCP server to connect an AI assistant to your Google Drive account. |
| MCP server portal | A web application in Cloudflare One that serves as a gateway to multiple MCP servers. |
| MCP server tool | An integration provided by an MCP server which allows an AI agent to perform a limited set of actions on a third-party system. |
| MDM file | A Mobile Device Management (MDM) file is a configuration file that allows organizations to manage the software, settings, and certificates installed on their devices. |
| MFA | Multi-factor authentication (MFA) checks multiple aspects of a user's identity, not only their username and password, before allowing them access to an application. |
| OAuth | A protocol for authorizing users, allowing them to perform actions and view data on different platforms without sharing credentials. |
| OIDC | OpenID Connect (OIDC) is an identity authentication protocol built on top of OAuth 2.0. It is used verifying user identity and obtaining basic profile information. |
| on-ramp | Refers to a way of connecting a business network to Cloudflare. Examples of on-ramps, or ways to connect to Cloudflare, are Anycast GRE tunnels, Anycast IPsec tunnels, Cloudflare Network Interconnect (CNI), Cloudflare Tunnel, and WARP. |
| PAC file | A file containing a JavaScript function which can instruct a browser to forward traffic to a proxy server instead of directly to the destination server. |
| policy | A set of rules that regulate network activity, such as login access and website reachability. |
| Quarantine policies | Policies that block specific types of emails (usually malicious and suspicious emails), preventing emails from reaching the end-user or the next mail service provider. Emails that are quarantined are reviewed by administrators and potentially released if falsely flagged. |
| RDP | Remote Desktop Protocol (RDP) allows remote desktop connections to a computer, often used on Windows and Mac operating systems. |
| remotely-managed tunnel | A Cloudflare Tunnel whose configuration is stored on Cloudflare rather than on your local machine. You can manage the tunnel in the dashboard under **Networks** > **Connectors** or by using the API. |
| Rule group | A set of Access rules that can be configured once and then quickly applied across many Access policies. |
| SafeSearch | SafeSearch is a feature of search engines that filters explicit or offensive content from search results. |
| SAML | Security Assertion Markup Language (SAML) enables single sign-on and authentication for multiple applications. |
| SASE | Secure Access Service Edge (SASE) is a cloud-based security model bundling networking and security functions. |
| SCIM | System for Cross-domain Identity Management (SCIM) is an open standard protocol that allows identity providers (such as Okta or Microsoft Entra ID) to synchronize user identity information with cloud applications and services. |
| seat | A unique, billable user within your Zero Trust organization who has performed [an authentication event](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/seat-management/#authentication-events). Service tokens do not consume seats. |
| service provider (SP) | A service provider (SP) provides federated access to an application for a user from an identity provider (IdP). |
| service token | Authentication credentials generated by Cloudflare Access which enable automated systems to access protected applications. |
| session | An event generated when a user logs in to an Access application. |
| shadow IT | Shadow IT is the unsanctioned use of software, hardware, or other systems and services within an organization, often without the knowledge of that organization's information technology (IT) department.For more information, refer to the [Cloudflare Learning Center](https://www.cloudflare.com/learning/access-management/what-is-shadow-it/). |
| SMB | Secure Messaging Block (SMB) is a network file sharing protocol used for accessing files and services on a network. |
| SSH | Secure Shell (SSH) protocol allows users to connect to infrastructure remotely and execute commands. |
| SSO | Single Sign-On (SSO) is a technology that combines multiple application logins into one, requiring users to enter credentials only once. |
| target | A resource with an IP address or hostname that is reachable by Cloudflare, such as a server or web application. |
| target hostname | A label used to identify a set of targets in an Access for Infrastructure application. |
| team domain | A unique subdomain assigned to your Cloudflare account (for example, `.cloudflareaccess.com`), where users will find the apps you have secured behind Cloudflare One. |
| team name | The customizable portion of your team domain (`.cloudflareaccess.com`). You can view your team name in Cloudflare One under **Settings**. |
| Terraform | An infrastructure as code software tool that allows you to deploy services from different providers using a standardized configuration syntax. |
| tunnel | A secure pathway for network traffic to flow between a device and Cloudflare's global network. |
| User risk score | Ranks the likelihood of a user to introduce risk to your organization's systems and data based on the detection of security risk behaviors. Risk scores add user and entity behavior analytics (UEBA) to the Cloudflare One platform. |
| User risk score level | Cloudflare One assigns a risk score of Low, Medium or High based on detections of users' activities, posture, and settings. A user's risk score is equal to the highest-level risk behavior they trigger. |
| Virtual network | A software abstraction that allows you to logically segregate resources on a private network. Virtual networks are especially useful for exposing resources which have overlapping IP routes. |
| Virtual Private Cloud (VPC) | A secure, isolated private network hosted on public cloud infrastructure. Examples of public cloud providers include Google Cloud, AWS, and Microsoft Azure. |
| Virtual Private Network (VPN) | A tool that allows users to send and receive data across shared or public networks as if their devices were directly connected to the private network. For example, employees working from home can use a VPN to access files on the corporate network. |
| WARP CGNAT IP | A unique, virtual IP address assigned to each WARP device from the `100.96.0.0/12` range. |
| WARP client | An application that connects corporate devices to Cloudflare for private network access, advanced web filtering, and other security functions. |
| WARP Connector | An extension of the WARP client used to establish site-to-site, bidirectional, and mesh networking connectivity. WARP Connector software installs on a Linux server within a private network, which then becomes a gateway for other local networks that need to on-ramp traffic to Cloudflare. |
| Zero Trust Security | Zero Trust Security is an IT security model that requires strict identity verification for every person and device accessing resources on a network. |
---
title: Implementation guides · Cloudflare One docs
description: View implementation guides for Cloudflare Zero Trust.
lastUpdated: 2026-01-19T14:05:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/implementation-guides/
md: https://developers.cloudflare.com/cloudflare-one/implementation-guides/index.md
---
Implementation guides cover deployment steps and best practices for specific Cloudflare One use cases.
[Secure your Internet Traffic and SaaS apps](https://developers.cloudflare.com/learning-paths/secure-internet-traffic/concepts/)
Provide your users and networks with a secure, performant, and flexible path to the Internet.
[Replace your VPN](https://developers.cloudflare.com/learning-paths/replace-vpn/concepts/)
Give users secure, auditable network and application access.
[Deploy clientless access](https://developers.cloudflare.com/learning-paths/clientless-access/concepts/)
Secure access to internal web applications without a device client.
[Secure your email with Email security](https://developers.cloudflare.com/learning-paths/secure-your-email/concepts/)
Use Cloudflare's Email security to protect your Microsoft 365 email inbox from phishing and malware attacks.
[Holistic AI security with Cloudflare One](https://developers.cloudflare.com/learning-paths/holistic-ai-security/concepts/)
Monitor and secure generative AI usage within your organization.
---
title: Insights · Cloudflare One docs
description: "Cloudflare One offers observability tools to monitor and
troubleshoot your environment:"
lastUpdated: 2026-01-30T15:54:45.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/insights/
md: https://developers.cloudflare.com/cloudflare-one/insights/index.md
---
Cloudflare One offers observability tools to monitor and troubleshoot your environment:
* [Analytics Overview](https://developers.cloudflare.com/cloudflare-one/insights/analytics-overview/) to monitor overall Cloudflare One usage.
* [Analytics Dashboards](https://developers.cloudflare.com/cloudflare-one/insights/analytics/) to review organizational traffic trends and policy insights.
* [Logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) for event-level investigation.
* [Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) for device, network, and application performance.
## Troubleshooting workflow example
A user reports they cannot reach an internal application behind [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/). To address the issue:
1. The admin checks the [Access Event Analytics dashboard](https://developers.cloudflare.com/cloudflare-one/insights/analytics-overview/) to review if other users are experiencing similar issues.
2. The admin then reviews [Logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) to examine the user's authentication attempts and blocked requests.
3. Finally, the admin uses [DEX](https://developers.cloudflare.com/cloudflare-one/insights/dex/) to evaluate the user's device health and network performance.
## How to use these tools together
### Onboarding
After onboarding your devices and users, use these tools to confirm everything is set up correctly and to monitor your organization's activity.
1. Start with [Logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) to validate initial configuration and confirm that authentication is successful.
2. Use [Analytics Overview](https://developers.cloudflare.com/cloudflare-one/insights/analytics-overview/) to confirm expected patterns and policy activity.
If your device is experiencing connectivity issues, Cloudflare recommends starting with [troubleshooting WARP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/troubleshooting/troubleshooting-guide/) as WARP misconfiguration is the most common cause of connectivity issues.
### Daily monitoring
1. Use [Analytics Dashboards](https://developers.cloudflare.com/cloudflare-one/insights/analytics/) to understand trends and for visualizations of your log data.
Administrators typically start with Analytics Dashboards because they offer:
* A high-level view of activity across your products, like Access, or security use cases, such as AI and shadow IT.
* Visibility into trends, provided through time-series graphs, to track the evolution of key metrics (such as [DNS queries](https://developers.cloudflare.com/cloudflare-one/insights/analytics/gateway/#dns-query-analytics), [network sessions](https://developers.cloudflare.com/cloudflare-one/insights/analytics/gateway/#network-session-analytics), [HTTP requests](https://developers.cloudflare.com/cloudflare-one/insights/analytics/gateway/#http-request-analytics), and [CASB posture/content findings](https://developers.cloudflare.com/cloudflare-one/insights/analytics/data-analytics/)) over time.
2. Use [Logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) as needed for event-level verification.
Use Logs when you need to:
* Investigate a specific event; for example, a user's [failed authentication attempt](https://developers.cloudflare.com/cloudflare-one/insights/logs/audit-logs/) when trying to log into an application.
* Validate identity or device details; for example, confirming which user made the request, how they authenticated, and whether their device met required [posture conditions](https://developers.cloudflare.com/cloudflare-one/insights/logs/posture-logs/).
* Confirm policy matches; for example, verifying which [specific rule](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/#rule-types) allowed, blocked, or challenged a user's request and why it was applied.
### User-reported issues
Users may report problems like slow or failing connections to internal apps.
1. Start with [Analytics Dashboards](https://developers.cloudflare.com/cloudflare-one/insights/analytics/) to review whether the issue impacts others.
2. Check [Logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) for failed authentication attempts, blocked requests, or unexpected policy matches.
3. Use [DEX](https://developers.cloudflare.com/cloudflare-one/insights/dex/) to diagnose device- or network-level causes with [synthetic tests](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/) and [device monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/monitoring/).
---
title: Integrations · Cloudflare One docs
description: Integrate third-party applications and services with Cloudflare One.
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cloudflare-one/integrations/
md: https://developers.cloudflare.com/cloudflare-one/integrations/index.md
---
Integrate third-party applications and services with Cloudflare One.
* [Cloud and SaaS integrations](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
* [Identity providers](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/)
* [Service providers](https://developers.cloudflare.com/cloudflare-one/integrations/service-providers/)
---
title: Networks · Cloudflare One docs
description: Learn how to connect your private networks to Cloudflare.
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cloudflare-one/networks/
md: https://developers.cloudflare.com/cloudflare-one/networks/index.md
---
Learn how to connect your private networks to Cloudflare.
* [Connectors](https://developers.cloudflare.com/cloudflare-one/networks/connectors/)
* [Add routes](https://developers.cloudflare.com/cloudflare-one/networks/routes/)
* [Resolvers and proxies](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/)
---
title: Reference architecture · Cloudflare One docs
lastUpdated: 2025-11-21T23:11:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/reference-architecture/
md: https://developers.cloudflare.com/cloudflare-one/reference-architecture/index.md
---
---
title: Remote browser isolation · Cloudflare One docs
description: Cloudflare Browser Isolation complements the Secure Web Gateway and
Zero Trust Network Access solutions by executing active webpage content in a
secure isolated browser. Executing active content remotely from the endpoint
protects users from zero-day attacks and malware. In addition to protecting
endpoints, Browser Isolation also protects users from phishing attacks by
preventing user input on risky websites and controlling data transmission to
sensitive web applications. You can further filter isolated traffic with
Gateway HTTP and DNS policies.
lastUpdated: 2025-10-30T19:21:21.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/
md: https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/index.md
---
Cloudflare Browser Isolation complements the [Secure Web Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) and [Zero Trust Network Access](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) solutions by executing active webpage content in a secure isolated browser. Executing active content remotely from the endpoint protects users from zero-day attacks and malware. In addition to protecting endpoints, Browser Isolation also protects users from phishing attacks by preventing user input on risky websites and controlling data transmission to sensitive web applications. You can further filter isolated traffic with Gateway [HTTP](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/) and [DNS](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/) policies.
Remote browsing is invisible to the user who continues to use their browser normally without changing their preferred browser and habits. Every open tab and window is automatically isolated. When the user closes the isolated browser, their session is automatically deleted.
Note
Available as an add-on to Zero Trust Pay-as-you-go and Enterprise plans.
## Privacy
Cloudflare Browser Isolation is a security product. In order to serve transparent isolated browsing and block web based threats our network decrypts Internet traffic using the [Cloudflare root CA](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/user-side-certificates/). Traffic logs are retained as per the [Zero Trust](https://developers.cloudflare.com/cloudflare-one/insights/logs/) documentation.
---
title: Reusable components · Cloudflare One docs
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cloudflare-one/reusable-components/
md: https://developers.cloudflare.com/cloudflare-one/reusable-components/index.md
---
* [Lists](https://developers.cloudflare.com/cloudflare-one/reusable-components/lists/)
* [Packet filtering (Magic Firewall) fields](https://developers.cloudflare.com/cloudflare-one/reusable-components/packet-filtering-fields/)
* [Tags](https://developers.cloudflare.com/cloudflare-one/reusable-components/tags/)
* [Use IP lists](https://developers.cloudflare.com/cloudflare-one/reusable-components/use-rules-list/)
* [Custom pages](https://developers.cloudflare.com/cloudflare-one/reusable-components/custom-pages/)
* [Posture checks](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/)
---
title: Roles and permissions · Cloudflare One docs
description: When creating a Cloudflare Zero Trust account, you will be given
the Super Administrator role. As a Super Administrator, you can invite members
to join your Zero Trust account and assign them different roles. There is no
limit to the number of members which can be added to a given account. Any
members with the proper permissions will be able to make configuration changes
while actively logged into Zero Trust (unless read-only mode is enabled).
lastUpdated: 2026-01-20T15:40:05.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/roles-permissions/
md: https://developers.cloudflare.com/cloudflare-one/roles-permissions/index.md
---
When creating a Cloudflare Zero Trust account, you will be given the Super Administrator role. As a Super Administrator, you can invite members to join your Zero Trust account and assign them different roles. There is no limit to the number of members which can be added to a given account. Any members with the proper permissions will be able to make configuration changes while actively logged into Zero Trust (unless [read-only mode](https://developers.cloudflare.com/cloudflare-one/api-terraform/#set-dashboard-to-read-only) is enabled).
To check the list of members in your account, or to manage roles and permissions, refer to our [Account setup](https://developers.cloudflare.com/fundamentals/manage-members/) documentation.
## Zero Trust roles
Only Super Administrators will be able to assign or remove the following roles from users in their account. Scroll to the right to see a full list of permissions for each role.
| | Access Read | Access Edit | Gateway Read | Gateway Edit | Gateway Report | DNS Location Read | DNS Location Edit | Billing Read | Billing Edit | DEX Read | DEX Edit | CASB Read | CASB Edit |
| - | - | - | - | - | - | - | - | - | - | - | - | - | - |
| Super Administrator | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Cloudflare Zero Trust[1](#user-content-fn-1) | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ❌ | ✅ | ✅ | ✅ | ✅ |
| Cloudflare Access | ✅ | ✅ | ✅ | ❌ | ✅ | ❌ | ❌ | ✅ | ❌ | ❌ | ❌ | ❌ | ❌ |
| Cloudflare Gateway | ✅ | ❌ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ❌ | ❌ | ❌ | ❌ | ❌ |
| Cloudflare Zero Trust Read Only | ✅ | ❌ | ✅ | ❌ | ✅ | ✅ | ❌ | ✅ | ❌ | ✅ | ❌ | ✅ | ❌ |
| Cloudflare Zero Trust Reporting | ❌ | ❌ | ❌ | ❌ | ✅ | ❌ | ❌ | ✅ | ❌ | ✅ | ❌ | ❌ | ❌ |
| Cloudflare Zero Trust DNS Locations Write[2](#user-content-fn-2) | ❌ | ❌ | ❌ | ❌ | ❌ | ✅ | ✅ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ |
| Cloudflare DEX | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ✅ | ✅ | ❌ | ❌ |
| Cloudflare CASB Read | ❌ | ❌ | ✅ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ✅ | ❌ |
| Cloudflare CASB | ❌ | ❌ | ✅ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ✅ | ✅ |
### Cloudflare Zero Trust PII
By default, only Super Administrators can view end users' PII in the Gateway activity logs, such as Device IDs, Source IPs, or user emails. No other roles will have the ability to read PII unless Super Administrators explicitly assign the **Cloudflare Zero Trust PII** role to them.
The Cloudflare Zero Trust PII role should be considered an add-on role, to be combined with any role from the table above. For example, Super Administrators may decide to assign the Cloudflare Gateway role to a user, and add the Cloudflare Zero Trust PII role to allow that user to access PII in the Gateway logs.
Note
The Cloudflare Zero Trust PII role does not apply to Access authentication logs. PII is always visible in Access logs.
## Email security roles
For more information on Email security roles, refer to [Account-scoped roles](https://developers.cloudflare.com/fundamentals/manage-members/roles/#account-scoped-roles).
* **Cloudflare Zero Trust**: Can edit Cloudflare [Zero Trust](https://developers.cloudflare.com/cloudflare-one/). Grants administrator access to all Zero Trust products including Access, Gateway, WARP, Tunnel, Browser Isolation, CASB, DLP, DEX, and Email security.
* **Cloudflare Zero Trust PII**: Can read PII in Zero Trust. This includes Email security.
* **Email security Analyst** and **Email security Configuration Admin**: Has full access to all admin features in Email security.
* **Email security Integration Admin**: Can read and set up integrations only.
* **Email security Configuration Admin**: Has administrator access. Cannot take actions on emails, or read emails.
* **Email security Analyst**: Has analyst access. Can take action on emails and read emails.
* **Email security Reporting**: Can read metrics.
* **Email security Read Only**: Can read all information, but cannot take action on anything.
* **Email security Policy Admin**: Can read all settings, but only write [allow policies](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/allow-policies/), [trusted domains](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/trusted-domains/), and [blocked senders](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/blocked-senders/).
## Footnotes
1. The **Cloudflare Zero Trust** role grants administrator access to all Zero Trust products including Access, Gateway, WARP, Tunnel, Browser Isolation, CASB, DLP, DEX, and Email security. [↩](#user-content-fnref-1)
2. Users with the **Cloudflare Zero Trust DNS Locations Write** role can view all DNS locations for an organization but can only create and edit [secure DNS locations](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/#secure-dns-locations). [↩](#user-content-fnref-2)
---
title: Get started · Cloudflare One docs
description: This guide covers the recommended steps to start securing your
users and devices with Cloudflare Zero Trust.
lastUpdated: 2025-10-30T21:17:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/setup/
md: https://developers.cloudflare.com/cloudflare-one/setup/index.md
---
This guide covers the recommended steps to start securing your users and devices with Cloudflare Zero Trust.
Note
To get started with a specific use case, refer to our [implementation guides](https://developers.cloudflare.com/cloudflare-one/implementation-guides/).
## Prerequisites
Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up).
## Create a Zero Trust Organization
1. In the [Cloudflare dashboard](https://dash.cloudflare.com/), select **Zero Trust**.
[Go to **Zero Trust**](https://one.dash.cloudflare.com/)
2. On the onboarding screen, choose a team name. The team name is a unique, internal identifier for your Zero Trust organization. Users will enter this team name when they enroll their device manually, and it will be the subdomain for your App Launcher (as relevant). Your business name is the typical entry.
You can find your team name in [Cloudflare One](https://one.dash.cloudflare.com) by going to **Settings**.
3. Complete your onboarding by selecting a subscription plan and entering your payment details. If you chose the **Zero Trust Free plan**, this step is still needed but you will not be charged.
Welcome to Cloudflare Zero Trust! You can now explore a list of one-click actions we have designed to help you kickstart your experience.
## Install the WARP client on your devices
If you want to enable security features such as Browser Isolation, HTTP filtering, AV scanning, and device posture, or connect networks to Cloudflare, here are the next steps you need to take:
1. **Set up a login method.** Configure [One-time PIN](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/one-time-pin/) or connect a [third-party identity provider](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/) in Cloudflare Zero Trust. This is the login method your users will utilize when authenticating to add a new device to your Cloudflare Zero Trust setup.
2. **Next, define [device enrollment permissions](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/device-enrollment/)**. Create device enrollment rules to define which users in your organization should be able to connect devices to your organization's Cloudflare Zero Trust setup. As you create your rule, you will be asked to select which login method you would like users to authenticate with.
3. **Install the [Cloudflare root certificate](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/user-side-certificates/) on your devices.** Advanced security features including HTTP traffic inspection require users to install and trust the Cloudflare root certificate on their machine or device. If you are installing certificates manually on all your devices, these steps will need to be performed on each new device that is to be subject to HTTP filtering.
4. **[Download](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/) and deploy the WARP client to your devices**. Choose one of the [different ways](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/) to deploy the WARP client, depending on what works best for your organization.
5. **Log in to your organization's Cloudflare Zero Trust instance from your devices**. On your device, go to the Settings section in the WARP client and insert your organization's team name.
Your devices are now connected to Cloudflare Zero Trust through the WARP client. You can go to **Team & Resources** > **Devices** to find a list of your enrolled devices, when they were last seen, and the WARP client version they are running.
Next, [enforce security policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) on your traffic and access requests.
---
title: Team and resources · Cloudflare One docs
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/cloudflare-one/team-and-resources/
md: https://developers.cloudflare.com/cloudflare-one/team-and-resources/index.md
---
* [Application Library](https://developers.cloudflare.com/cloudflare-one/team-and-resources/app-library/)
* [Devices](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/)
* [Users](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/)
---
title: Traffic policies · Cloudflare One docs
description: Cloudflare Gateway, our comprehensive Secure Web Gateway, allows
you to set up policies to inspect DNS, Network, HTTP, and Egress traffic.
lastUpdated: 2025-12-05T17:26:05.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/traffic-policies/
md: https://developers.cloudflare.com/cloudflare-one/traffic-policies/index.md
---
Cloudflare Gateway, our comprehensive [Secure Web Gateway](https://www.cloudflare.com/learning/access-management/what-is-a-secure-web-gateway/), allows you to set up policies to inspect DNS, Network, HTTP, and Egress traffic.
* **Packet filtering** inspects and filters unwanted traffic based on packet attributes. Packet filtering policies block threats regardless of user or session context.
* **DNS policies** inspect DNS queries. You can block domains and IP addresses from resolving on your devices. For more information on DNS filtering, refer to our [Learning Center article](https://www.cloudflare.com/learning/access-management/what-is-dns-filtering/).
* **Network policies** inspect individual TCP/UDP/GRE packets. You can block access to specific ports on your origin server, including non-HTTP resources.
* **HTTP policies** inspect HTTP requests. You can block specific URLs from loading, not just the domain itself. For more information on URL filtering, refer to our [Learning Center article](https://www.cloudflare.com/learning/access-management/what-is-url-filtering/).
* **Egress policies** inspect traffic to assign egress IP addresses unique to your organization.
* **Resolver policies** inspect DNS queries to enable resolution by custom authoritative nameservers.
Note
When creating or editing policies, it may take up to 60 seconds for that policy to be updated across all of Cloudflare's data centers.
## Best practices
For each type of policy, we recommend the following workflow:
1. Connect the devices and/or networks that you want to apply policies to.
2. Verify that Gateway is successfully proxying traffic from your devices.
3. Set up basic security and compatibility policies (recommended for most use cases).
4. Customize your configuration to the unique needs of your organization.
To get started with specific Gateway filtering types, refer to the initial setup for [DNS](https://developers.cloudflare.com/cloudflare-one/traffic-policies/initial-setup/dns/), [Network](https://developers.cloudflare.com/cloudflare-one/traffic-policies/initial-setup/network/), and [HTTP](https://developers.cloudflare.com/cloudflare-one/traffic-policies/initial-setup/http/) policies.
### Select a policy type
The recommended policy type depends on what kind of traffic you are trying to filter. For example:
* To block websites, create an HTTP policy.
* To block non-HTTP traffic such as SSH and RDP, create a Network policy.
* To block malware and other security threats, create both DNS and HTTP policies.
* To assign static IP addresses to your organization's egress traffic, create an egress policy.
Refer to the [Packet filtering](https://developers.cloudflare.com/cloudflare-one/traffic-policies/packet-filtering/magic-firewall-overview/), [DNS](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/), [Network](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/), [HTTP](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/), and [egress](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/) configuration pages to see the available filtering options within each policy builder.
---
title: Tutorials · Cloudflare One docs
description: View tutorials for Cloudflare Zero Trust.
lastUpdated: 2025-11-18T20:09:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/tutorials/
md: https://developers.cloudflare.com/cloudflare-one/tutorials/index.md
---
| Name | Last Updated | Difficulty |
| - | - | - |
| [Implement regional private DNS servers with Gateway resolver policies](https://developers.cloudflare.com/cloudflare-one/tutorials/regional-private-dns-resolver-policies/) | 3 months ago | Advanced |
| [Deploy WARP on headless Linux machines](https://developers.cloudflare.com/cloudflare-one/tutorials/warp-on-headless-linux/) | 4 months ago | Beginner |
| [Create and secure an AI agent wrapper using AI Gateway and Zero Trust](https://developers.cloudflare.com/cloudflare-one/tutorials/ai-wrapper-tenant-control/) | 9 months ago | Advanced |
| [Use Cloudflare Tunnels with Kubernetes client-go plugin](https://developers.cloudflare.com/cloudflare-one/tutorials/tunnel-kubectl/) | over 1 year ago | Intermediate |
| [Send SSO attributes to Access-protected origins with Workers](https://developers.cloudflare.com/cloudflare-one/tutorials/extend-sso-with-workers/) | over 1 year ago | Advanced |
| [Use virtual networks to change user egress IPs](https://developers.cloudflare.com/cloudflare-one/tutorials/user-selectable-egress-ips/) | almost 2 years ago | Intermediate |
| [Access and secure a MySQL database using Cloudflare Tunnel and network policies](https://developers.cloudflare.com/cloudflare-one/tutorials/mysql-network-policy/) | almost 2 years ago | Intermediate |
| [Access a web application via its private hostname without WARP](https://developers.cloudflare.com/cloudflare-one/tutorials/clientless-access-private-dns/) | almost 2 years ago | Intermediate |
| [Use Microsoft Entra ID Conditional Access policies in Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/tutorials/entra-id-conditional-access/) | about 2 years ago | Intermediate |
| [Protect access to Microsoft 365 with dedicated egress IPs](https://developers.cloudflare.com/cloudflare-one/tutorials/m365-dedicated-egress-ips/) | about 2 years ago | Intermediate |
| [Monitor Cloudflare Tunnel with Grafana](https://developers.cloudflare.com/cloudflare-one/tutorials/grafana/) | about 2 years ago | Intermediate |
| [Use Cloudflare R2 as a Zero Trust log destination](https://developers.cloudflare.com/cloudflare-one/tutorials/r2-logs/) | about 2 years ago | Beginner |
| [Create custom headers for Cloudflare Access-protected origins with Workers](https://developers.cloudflare.com/cloudflare-one/tutorials/access-workers/) | about 2 years ago | Intermediate |
| [Protect access to Amazon S3 buckets with Cloudflare Zero Trust](https://developers.cloudflare.com/cloudflare-one/tutorials/s3-buckets/) | over 2 years ago | Advanced |
| [Validate the Access token with FastAPI](https://developers.cloudflare.com/cloudflare-one/tutorials/fastapi/) | over 2 years ago | Beginner |
| [Isolate risky Entra ID users](https://developers.cloudflare.com/cloudflare-one/tutorials/entra-id-risky-users/) | about 3 years ago | Advanced |
| [Connect through Cloudflare Access using kubectl](https://developers.cloudflare.com/cloudflare-one/tutorials/kubectl/) | over 3 years ago | Advanced |
| [GraphQL Analytics](https://developers.cloudflare.com/cloudflare-one/tutorials/graphql-analytics/) | almost 4 years ago | Intermediate |
| [Integrate Microsoft MCAS with Cloudflare Zero Trust](https://developers.cloudflare.com/cloudflare-one/tutorials/integrate-microsoft-mcas-teams/) | over 4 years ago | Intermediate |
| [Connect through Cloudflare Access using a CLI](https://developers.cloudflare.com/cloudflare-one/tutorials/cli/) | almost 5 years ago | Intermediate |
| [MongoDB SSH](https://developers.cloudflare.com/cloudflare-one/tutorials/mongodb-tunnel/) | about 5 years ago | Advanced |
| [Zero Trust GitLab SSH & HTTP](https://developers.cloudflare.com/cloudflare-one/tutorials/gitlab/) | about 5 years ago | Advanced |
| [Require U2F with Okta](https://developers.cloudflare.com/cloudflare-one/tutorials/okta-u2f/) | about 5 years ago | Intermediate |
---
title: Videos · Cloudflare One docs
lastUpdated: 2025-11-21T23:11:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/cloudflare-one/video-tutorials/
md: https://developers.cloudflare.com/cloudflare-one/video-tutorials/index.md
---
[Build and secure your SASE corporate network ](https://developers.cloudflare.com/learning-paths/sase-overview-course/series/evolution-corporate-networks-1/)Dive into Cloudflare's Secure Access Service Edge (SASE) platform and learn how it's been designed to revolutionize the idea of the corporate network.
[Understand and troubleshoot Cloudflare WARP ](https://developers.cloudflare.com/learning-paths/warp-overview-course/series/warp-basics-1/)In this series, we cover the basics of Cloudflare WARP, share useful troubleshooting tips, and explain the warp-diag logs in detail.
---
title: 404 - Page Not Found · Constellation docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/constellation/404/
md: https://developers.cloudflare.com/constellation/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Platform · Constellation docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/constellation/platform/
md: https://developers.cloudflare.com/constellation/platform/index.md
---
* [Client API](https://developers.cloudflare.com/constellation/platform/client-api/)
---
title: 404 - Page Not Found · Cloudflare Containers docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/404/
md: https://developers.cloudflare.com/containers/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Beta Info & Roadmap · Cloudflare Containers docs
description: "Currently, Containers are in beta. There are several changes we
plan to make prior to GA:"
lastUpdated: 2025-09-22T15:52:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/beta-info/
md: https://developers.cloudflare.com/containers/beta-info/index.md
---
Currently, Containers are in beta. There are several changes we plan to make prior to GA:
## Upcoming Changes and Known Gaps
### Limits
Container limits will be raised in the future. We plan to increase both maximum instance size and maximum number of instances in an account.
See the [Limits documentation](https://developers.cloudflare.com/containers/platform-details/#limits) for more information.
### Autoscaling and load balancing
Currently, Containers are not autoscaled or load balanced. Containers can be scaled manually by calling `get()` on their binding with a unique ID.
We plan to add official support for utilization-based autoscaling and latency-aware load balancing in the future.
See the [Autoscaling documentation](https://developers.cloudflare.com/containers/platform-details/scaling-and-routing) for more information.
### Reduction of log noise
Currently, the `Container` class uses Durable Object alarms to help manage Container shutdown. This results in unnecessary log noise in the Worker logs. You can filter these logs out in the dashboard by adding a Query, but this is not ideal.
We plan to automatically reduce log noise in the future.
### Dashboard Updates
The dashboard will be updated to show:
* links from Workers to their associated Containers
### Co-locating Durable Objects and Containers
Currently, Durable Objects are not co-located with their associated Container. When requesting a container, the Durable Object will find one close to it, but not on the same machine.
We plan to co-locate Durable Objects with their Container in the future.
### More advanced Container placement
We currently prewarm servers across our global network with container images to ensure quick start times. There are times in which you may request a new container and it will be started in a location that farther from the end user than is desired. We are optimizing this process to ensure that this happens as little as possible, but it may still occur.
### Atomic code updates across Workers and Containers
When deploying a Container with `wrangler deploy`, the Worker code will be immediately updated while the Container code will slowly be updated using a rolling deploy.
This means that you must ensure Worker code is backwards compatible with the old Container code.
In the future, Worker code in the Durable Object will only update when associated Container code updates.
## Feedback wanted
There are several areas where we wish to gather feedback from users:
* Do you want to integrate Containers with any other Cloudflare services? If so, which ones and how?
* Do you want more ways to interact with a Container via Workers? If so, how?
* Do you need different mechanisms for routing requests to containers?
* Do you need different mechanisms for scaling containers? (see [scaling documentation](https://developers.cloudflare.com/containers/platform-details/scaling-and-routing) for information on autoscaling plans)
At any point during the Beta, feel free to [give feedback using this form](https://forms.gle/CscdaEGuw5Hb6H2s7).
---
title: Examples · Cloudflare Containers docs
description: "Explore the following examples of Container functionality:"
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/examples/
md: https://developers.cloudflare.com/containers/examples/index.md
---
Explore the following examples of Container functionality:
[Mount R2 buckets with FUSE](https://developers.cloudflare.com/containers/examples/r2-fuse-mount/)
[Mount R2 buckets as filesystems using FUSE in Containers](https://developers.cloudflare.com/containers/examples/r2-fuse-mount/)
[Static Frontend, Container Backend](https://developers.cloudflare.com/containers/examples/container-backend/)
[A simple frontend app with a containerized backend](https://developers.cloudflare.com/containers/examples/container-backend/)
[Cron Container](https://developers.cloudflare.com/containers/examples/cron/)
[Running a container on a schedule using Cron Triggers](https://developers.cloudflare.com/containers/examples/cron/)
[Using Durable Objects Directly](https://developers.cloudflare.com/containers/examples/durable-object-interface/)
[Various examples calling Containers directly from Durable Objects](https://developers.cloudflare.com/containers/examples/durable-object-interface/)
[Env Vars and Secrets](https://developers.cloudflare.com/containers/examples/env-vars-and-secrets/)
[Pass in environment variables and secrets to your container](https://developers.cloudflare.com/containers/examples/env-vars-and-secrets/)
[Stateless Instances](https://developers.cloudflare.com/containers/examples/stateless/)
[Run multiple instances across Cloudflare's network](https://developers.cloudflare.com/containers/examples/stateless/)
[Status Hooks](https://developers.cloudflare.com/containers/examples/status-hooks/)
[Execute Workers code in reaction to Container status changes](https://developers.cloudflare.com/containers/examples/status-hooks/)
[Websocket to Container](https://developers.cloudflare.com/containers/examples/websocket/)
[Forwarding a Websocket request to a Container](https://developers.cloudflare.com/containers/examples/websocket/)
---
title: Frequently Asked Questions · Cloudflare Containers docs
description: "Frequently Asked Questions:"
lastUpdated: 2025-09-22T15:52:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/faq/
md: https://developers.cloudflare.com/containers/faq/index.md
---
Frequently Asked Questions:
## How do Container logs work?
To get logs in the Dashboard, including live tailing of logs, toggle `observability` to true in your Worker's wrangler config:
* wrangler.jsonc
```jsonc
{
"observability": {
"enabled": true
}
}
```
* wrangler.toml
```toml
[observability]
enabled = true
```
Logs are subject to the same [limits as Worker logs](https://developers.cloudflare.com/workers/observability/logs/workers-logs/#limits), which means that they are retained for 3 days on Free plans and 7 days on Paid plans.
See [Workers Logs Pricing](https://developers.cloudflare.com/workers/observability/logs/workers-logs/#pricing) for details on cost.
If you are an Enterprise user, you are able to export container logs via [Logpush](https://developers.cloudflare.com/logs/logpush/) to your preferred destination.
## How are container instance locations selected?
When initially deploying a Container, Cloudflare will select various locations across our network to deploy instances to. These locations will span multiple regions.
When a Container instance is requested with `this.ctx.container.start`, the nearest free container instance will be selected from the pre-initialized locations. This will likely be in the same region as the external request, but may not be. Once the container instance is running, any future requests will be routed to the initial location.
An Example:
* A user deploys a Container. Cloudflare automatically readies instances across its Network.
* A request is made from a client in Bariloche, Argentia. It reaches the Worker in Cloudflare's location in Neuquen, Argentina.
* This Worker request calls `MY_CONTAINER.get("session-1337")` which brings up a Durable Object, which then calls `this.ctx.container.start`.
* This requests the nearest free Container instance.
* Cloudflare recognizes that an instance is free in Buenos Aires, Argentina, and starts it there.
* A different user needs to route to the same container. This user's request reaches the Worker running in Cloudflare's location in San Diego.
* The Worker again calls `MY_CONTAINER.get("session-1337")`.
* If the initial container instance is still running, the request is routed to the location in Buenos Aires. If the initial container has gone to sleep, Cloudflare will once again try to find the nearest "free" instance of the Container, likely one in North America, and start an instance there.
## How do container updates and rollouts work?
See [rollout documentation](https://developers.cloudflare.com/containers/platform-details/rollouts/) for details.
## How does scaling work?
See [scaling & routing documentation](https://developers.cloudflare.com/containers/platform-details/scaling-and-routing/) for details.
## What are cold starts? How fast are they?
A cold start is when a container instance is started from a completely stopped state.
If you call `env.MY_CONTAINER.get(id)` with a completely novel ID and launch this instance for the first time, it will result in a cold start.
This will start the container image from its entrypoint for the first time. Depending on what this entrypoint does, it will take a variable amount of time to start.
Container cold starts can often be the 2-3 second range, but this is dependent on image size and code execution time, among other factors.
## How do I use an existing container image?
See [image management documentation](https://developers.cloudflare.com/containers/platform-details/image-management/#using-existing-images) for details.
## Is disk persistent? What happens to my disk when my container sleeps?
All disk is ephemeral. When a Container instance goes to sleep, the next time it is started, it will have a fresh disk as defined by its container image.
Persistent disk is something the Cloudflare team is exploring in the future, but is not slated for the near term.
## What happens if I run out of memory?
If you run out of memory, your instance will throw an Out of Memory (OOM) error and will be restarted.
Containers do not use swap memory.
## How long can instances run for? What happens when a host server is shutdown?
Cloudflare will not actively shut off a container instance after a specific amount of time. If you do not set `sleepAfter` on your Container class, or stop the instance manually, it will continue to run unless its host server is restarted. This happens on an irregular cadence, but frequently enough where Cloudflare does not guarantee that any instance will run for any set period of time.
When a container instance is going to be shut down, it is sent a `SIGTERM` signal, and then a `SIGKILL` signal after 15 minutes. You should perform any necessary cleanup to ensure a graceful shutdown in this time. The container instance will be rebooted elsewhere shortly after this.
## How can I pass secrets to my container?
You can use [Worker Secrets](https://developers.cloudflare.com/workers/configuration/secrets/) or the [Secrets Store](https://developers.cloudflare.com/secrets-store/integrations/workers/) to define secrets for your Workers.
Then you can pass these secrets to your Container using the `envVars` property:
```javascript
class MyContainer extends Container {
defaultPort = 5000;
envVars = {
MY_SECRET: this.env.MY_SECRET,
};
}
```
Or when starting a Container instance on a Durable Object:
```javascript
this.ctx.container.start({
env: {
MY_SECRET: this.env.MY_SECRET,
},
});
```
See [the Env Vars and Secrets Example](https://developers.cloudflare.com/containers/examples/env-vars-and-secrets/) for details.
## How do I allow or disallow egress from my container?
When booting a Container, you can specify `enableInternet`, which will toggle internet access on or off.
To disable it, configure it on your Container class:
```javascript
class MyContainer extends Container {
defaultPort = 7000;
enableInternet = false;
}
```
or when starting a Container instance on a Durable Object:
```javascript
this.ctx.container.start({
enableInternet: false,
});
```
---
title: Container Package · Cloudflare Containers docs
description: >-
When writing code that interacts with a container instance, you can either use
a
Durable Object directly or use the Container class
importable from @cloudflare/containers.
lastUpdated: 2025-09-22T15:52:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/container-package/
md: https://developers.cloudflare.com/containers/container-package/index.md
---
When writing code that interacts with a container instance, you can either use a [Durable Object directly](https://developers.cloudflare.com/containers/platform-details/durable-object-methods) or use the [`Container` class](https://github.com/cloudflare/containers) importable from [`@cloudflare/containers`](https://www.npmjs.com/package/@cloudflare/containers).
We recommend using the `Container` class for most use cases.
* npm
```sh
npm i @cloudflare/containers
```
* yarn
```sh
yarn add @cloudflare/containers
```
* pnpm
```sh
pnpm add @cloudflare/containers
```
Then, you can define a class that extends `Container`, and use it in your Worker:
```javascript
import { Container } from "@cloudflare/containers";
class MyContainer extends Container {
defaultPort = 8080;
sleepAfter = "5m";
}
export default {
async fetch(request, env) {
// gets default instance and forwards request from outside Worker
return env.MY_CONTAINER.getByName("hello").fetch(request);
},
};
```
The `Container` class extends `DurableObject` so all [Durable Object](https://developers.cloudflare.com/durable-objects) functionality is available. It also provides additional functionality and a nice interface for common container behaviors, such as:
* sleeping instances after an inactivity timeout
* making requests to specific ports
* running status hooks on startup, stop, or error
* awaiting specific ports before making requests
* setting environment variables and secrets
See the [Containers GitHub repo](https://github.com/cloudflare/containers) for more details and the complete API.
---
title: Getting started · Cloudflare Containers docs
description: >-
In this guide, you will deploy a Worker that can make requests to one or more
Containers in response to end-user requests.
In this example, each container runs a small webserver written in Go.
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/get-started/
md: https://developers.cloudflare.com/containers/get-started/index.md
---
In this guide, you will deploy a Worker that can make requests to one or more Containers in response to end-user requests. In this example, each container runs a small webserver written in Go.
This example Worker should give you a sense for simple Container use, and provide a starting point for more complex use cases.
## Prerequisites
### Ensure Docker is running locally
In this guide, we will build and push a container image alongside your Worker code. By default, this process uses [Docker](https://www.docker.com/) to do so.
You must have Docker running locally when you run `wrangler deploy`. For most people, the best way to install Docker is to follow the [docs for installing Docker Desktop](https://docs.docker.com/desktop/). Other tools like [Colima](https://github.com/abiosoft/colima) may also work.
You can check that Docker is running properly by running the `docker info` command in your terminal. If Docker is running, the command will succeed. If Docker is not running, the `docker info` command will hang or return an error including the message "Cannot connect to the Docker daemon".
## Deploy your first Container
Run the following command to create and deploy a new Worker with a container, from the starter template:
* npm
```sh
npm create cloudflare@latest -- --template=cloudflare/templates/containers-template
```
* yarn
```sh
yarn create cloudflare --template=cloudflare/templates/containers-template
```
* pnpm
```sh
pnpm create cloudflare@latest --template=cloudflare/templates/containers-template
```
When you want to deploy a code change to either the Worker or Container code, you can run the following command using [Wrangler CLI](https://developers.cloudflare.com/workers/wrangler/):
* npm
```sh
npx wrangler deploy
```
* yarn
```sh
yarn wrangler deploy
```
* pnpm
```sh
pnpm wrangler deploy
```
When you run `wrangler deploy`, the following things happen:
* Wrangler builds your container image using Docker.
* Wrangler pushes your image to a [Container Image Registry](https://developers.cloudflare.com/containers/platform-details/image-management/) that is automatically integrated with your Cloudflare account.
* Wrangler deploys your Worker, and configures Cloudflare's network to be ready to spawn instances of your container
The build and push usually take the longest on the first deploy. Subsequent deploys are faster, because they [reuse cached image layers](https://docs.docker.com/build/cache/).
Note
After you deploy your Worker for the first time, you will need to wait several minutes until it is ready to receive requests. Unlike Workers, Containers take a few minutes to be provisioned. During this time, requests are sent to the Worker, but calls to the Container will error.
### Check deployment status
After deploying, run the following command to show a list of containers containers in your Cloudflare account, and their deployment status:
* npm
```sh
npx wrangler containers list
```
* yarn
```sh
yarn wrangler containers list
```
* pnpm
```sh
pnpm wrangler containers list
```
And see images deployed to the Cloudflare Registry with the following command:
* npm
```sh
npx wrangler containers images list
```
* yarn
```sh
yarn wrangler containers images list
```
* pnpm
```sh
pnpm wrangler containers images list
```
### Make requests to Containers
Now, open the URL for your Worker. It should look something like `https://hello-containers.YOUR_ACCOUNT_NAME.workers.dev`.
If you make requests to the paths `/container/1` or `/container/2`, your Worker routes requests to specific containers. Each different path after "/container/" routes to a unique container.
If you make requests to `/lb`, you will load balanace requests to one of 3 containers chosen at random.
You can confirm this behavior by reading the output of each request.
## Understanding the Code
Now that you've deployed your first container, let's explain what is happening in your Worker's code, in your configuration file, in your container's code, and how requests are routed.
## Each Container is backed by its own Durable Object
Incoming requests are initially handled by the Worker, then passed to a container-enabled [Durable Object](https://developers.cloudflare.com/durable-objects). To simplify and reduce boilerplate code, Cloudflare provides a [`Container` class](https://github.com/cloudflare/containers) as part of the `@cloudflare/containers` NPM package.
You don't have to be familiar with Durable Objects to use Containers, but it may be helpful to understand the basics.
Each Durable Object runs alongside an individual container instance, manages starting and stopping it, and can interact with the container through its ports. Containers will likely run near the Worker instance requesting them, but not necessarily. Refer to ["How Locations are Selected"](https://developers.cloudflare.com/containers/platform-details/#how-are-locations-are-selected) for details.
In a simple app, the Durable Object may just boot the container and proxy requests to it.
In a more complex app, having container-enabled Durable Objects allows you to route requests to individual stateful container instances, manage the container lifecycle, pass in custom starting commands and environment variables to containers, run hooks on container status changes, and more.
See the [documentation for Durable Object container methods](https://developers.cloudflare.com/durable-objects/api/container/) and the [`Container` class repository](https://github.com/cloudflare/containers) for more details.
### Configuration
Your [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/) defines the configuration for both your Worker and your container:
* wrangler.jsonc
```jsonc
{
"containers": [
{
"max_instances": 10,
"class_name": "MyContainer",
"image": "./Dockerfile"
}
],
"durable_objects": {
"bindings": [
{
"name": "MY_CONTAINER",
"class_name": "MyContainer"
}
]
},
"migrations": [
{
"tag": "v1",
"new_sqlite_classes": [
"MyContainer"
]
}
]
}
```
* wrangler.toml
```toml
[[containers]]
max_instances = 10
class_name = "MyContainer"
image = "./Dockerfile"
[[durable_objects.bindings]]
name = "MY_CONTAINER"
class_name = "MyContainer"
[[migrations]]
tag = "v1"
new_sqlite_classes = [ "MyContainer" ]
```
Important points about this config:
* `image` points to a Dockerfile or to a directory containing a Dockerfile.
* `class_name` must be a [Durable Object class name](https://developers.cloudflare.com/durable-objects/api/base/).
* `max_instances` declares the maximum number of simultaneously running container instances that will run.
* The Durable Object must use [`new_sqlite_classes`](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#create-sqlite-backed-durable-object-class) not `new_classes`.
### The Container Image
Your container image must be able to run on the `linux/amd64` architecture, but aside from that, has few limitations.
In the example you just deployed, it is a simple Golang server that responds to requests on port 8080 using the `MESSAGE` environment variable that will be set in the Worker and an [auto-generated environment variable](https://developers.cloudflare.com/containers/platform-details/#environment-variables) `CLOUDFLARE_DEPLOYMENT_ID.`
```go
func handler(w http.ResponseWriter, r *http.Request) {
message := os.Getenv("MESSAGE")
instanceId := os.Getenv("CLOUDFLARE_DEPLOYMENT_ID")
fmt.Fprintf(w, "Hi, I'm a container and this is my message: %s, and my instance ID is: %s", message, instanceId)
}
```
Note
After deploying the example code, to deploy a different image, you can replace the provided image with one of your own.
### Worker code
#### Container Configuration
First note `MyContainer` which extends the [`Container`](https://github.com/cloudflare/containers) class:
```js
export class MyContainer extends Container {
defaultPort = 8080;
sleepAfter = '10s';
envVars = {
MESSAGE: 'I was passed in via the container class!',
};
override onStart() {
console.log('Container successfully started');
}
override onStop() {
console.log('Container successfully shut down');
}
override onError(error: unknown) {
console.log('Container error:', error);
}
}
```
This defines basic configuration for the container:
* `defaultPort` sets the port that the `fetch` and `containerFetch` methods will use to communicate with the container. It also blocks requests until the container is listening on this port.
* `sleepAfter` sets the timeout for the container to sleep after it has been idle for a certain amount of time.
* `envVars` sets environment variables that will be passed to the container when it starts.
* `onStart`, `onStop`, and `onError` are hooks that run when the container starts, stops, or errors, respectively.
See the [Container class documentation](https://developers.cloudflare.com/containers/container-package) for more details and configuration options.
#### Routing to Containers
When a request enters Cloudflare, your Worker's [`fetch` handler](https://developers.cloudflare.com/workers/runtime-apis/handlers/fetch/) is invoked. This is the code that handles the incoming request. The fetch handler in the example code, launches containers in two ways, on different routes:
* Making requests to `/container/` passes requests to a new container for each path. This is done by spinning up a new Container instance. You may note that the first request to a new path takes longer than subsequent requests, this is because a new container is booting.
```js
if (pathname.startsWith("/container")) {
const container = env.MY_CONTAINER.getByName(pathname);
return await container.fetch(request);
}
```
* Making requests to `/lb` will load balance requests across several containers. This uses a simple `getRandom` helper method, which picks an ID at random from a set number (in this case 3), then routes to that Container instance. You can replace this with any routing or load balancing logic you choose to implement:
```js
if (pathname.startsWith("/lb")) {
const container = await getRandom(env.MY_CONTAINER, 3);
return await container.fetch(request);
}
```
This allows for multiple ways of using Containers:
* If you simply want to send requests to many stateless and interchangeable containers, you should load balance.
* If you have stateful services or need individually addressable containers, you should request specific Container instances.
* If you are running short-lived jobs, want fine-grained control over the container lifecycle, want to parameterize container entrypoint or env vars, or want to chain together multiple container calls, you should request specific Container instances.
Note
Currently, routing requests to one of many interchangeable Container instances is accomplished with the `getRandom` helper.
This is temporary — we plan to add native support for latency-aware autoscaling and load balancing in the coming months.
## View Containers in your Dashboard
The [Containers Dashboard](http://dash.cloudflare.com/?to=/:account/workers/containers) shows you helpful information about your Containers, including:
* Status and Health
* Metrics
* Logs
* A link to associated Workers and Durable Objects
After launching your Worker, navigate to the Containers Dashboard by clicking on "Containers" under "Workers & Pages" in your sidebar.
## Next Steps
To do more:
* Modify the image by changing the Dockerfile and calling `wrangler deploy`
* Review our [examples](https://developers.cloudflare.com/containers/examples) for more inspiration
* Get [more information on the Containers Beta](https://developers.cloudflare.com/containers/beta-info)
---
title: Local Development · Cloudflare Containers docs
description: You can run both your container and your Worker locally by simply
running npx wrangler dev (or vite dev for Vite projects using the Cloudflare
Vite plugin) in your project's directory.
lastUpdated: 2025-09-22T15:52:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/local-dev/
md: https://developers.cloudflare.com/containers/local-dev/index.md
---
You can run both your container and your Worker locally by simply running [`npx wrangler dev`](https://developers.cloudflare.com/workers/wrangler/commands/#dev) (or `vite dev` for Vite projects using the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/)) in your project's directory.
To develop Container-enabled Workers locally, you will need to first ensure that a Docker compatible CLI tool and Engine are installed. For instance, you could use [Docker Desktop](https://docs.docker.com/desktop/) or [Colima](https://github.com/abiosoft/colima).
When you start a dev session, your container image will be built or downloaded. If your [Wrangler configuration](https://developers.cloudflare.com/workers/wrangler/configuration/#containers) sets the `image` attribute to a local path, the image will be built using the local Dockerfile. If the `image` attribute is set to a URL, the image will be pulled from the Cloudflare registry.
Note
Currently, the Cloudflare Vite-plugin does not support registry links in local development, unlike `wrangler dev`. As a workaround, you can create a minimal Dockerfile that uses `FROM `. Make sure to `EXPOSE` a port for local dev as well.
Container instances will be launched locally when your Worker code calls to create a new container. Requests will then automatically be routed to the correct locally-running container.
When the dev session ends, all associated container instances should be stopped, but local images are not removed, so that they can be reused in subsequent builds.
Note
If your Worker app creates many container instances, your local machine may not be able to run as many containers concurrently as is possible when you deploy to Cloudflare.
Also, `max_instances` configuration option does not apply during local development.
Additionally, if you regularly rebuild containers locally, you may want to clear out old container images (using `docker image prune` or similar) to reduce disk used.
## Iterating on Container code
When you develop with Wrangler or Vite, your Worker's code is automatically reloaded each time you save a change, but code running within the container is not.
To rebuild your container with new code changes, you can hit the `[r]` key on your keyboard, which triggers a rebuild. Container instances will then be restarted with the newly built images.
You may prefer to set up your own code watchers and reloading mechanisms, or mount a local directory into the local container images to sync code changes. This can be done, but there is no built-in mechanism for doing so, and best-practices will depend on the languages and frameworks you are using in your container code.
## Troubleshooting
### Exposing Ports
In production, all of your container's ports will be accessible by your Worker, so you do not need to specifically expose ports using the [`EXPOSE` instruction](https://docs.docker.com/reference/dockerfile/#expose) in your Dockerfile.
But for local development you will need to declare any ports you need to access in your Dockerfile with the EXPOSE instruction; for example: `EXPOSE 4000`, if you will be accessing port 4000.
If you have not exposed any ports, you will see the following error in local development:
```txt
The container "MyContainer" does not expose any ports. In your Dockerfile, please expose any ports you intend to connect to.
```
And if you try to connect to any port that you have not exposed in your `Dockerfile` you will see the following error:
```txt
connect(): Connection refused: container port not found. Make sure you exposed the port in your container definition.
```
You may also see this while the container is starting up and no ports are available yet. You should retry until the ports become available. This retry logic should be handled for you if you are using the [containers package](https://github.com/cloudflare/containers/tree/main/src).
### Socket configuration - `internal error`
If you see an opaque `internal error` when attempting to connect to your container, you may need to set the `DOCKER_HOST` environment variable to the socket path your container engine is listening on. Wrangler or Vite will attempt to automatically find the correct socket to use to communicate with your container engine, but if that does not work, you may have to set this environment variable to the appropriate socket path.
---
title: Pricing · Cloudflare Containers docs
description: "Containers are billed for every 10ms that they are actively
running at the following rates, with included monthly usage as part of the $5
USD per month Workers Paid plan:"
lastUpdated: 2025-11-21T16:40:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/pricing/
md: https://developers.cloudflare.com/containers/pricing/index.md
---
## vCPU, Memory and Disk
Containers are billed for every 10ms that they are actively running at the following rates, with included monthly usage as part of the $5 USD per month [Workers Paid plan](https://developers.cloudflare.com/workers/platform/pricing/):
| | Memory | CPU | Disk |
| - | - | - | - |
| **Free** | N/A | N/A | |
| **Workers Paid** | 25 GiB-hours/month included +$0.0000025 per additional GiB-second | 375 vCPU-minutes/month + $0.000020 per additional vCPU-second | 200 GB-hours/month +$0.00000007 per additional GB-second |
You only pay for what you use — charges start when a request is sent to the container or when it is manually started. Charges stop after the container instance goes to sleep, which can happen automatically after a timeout. This makes it easy to scale to zero, and allows you to get high utilization even with bursty traffic.
Memory and disk usage are based on the *provisioned resources* for the instance type you select, while CPU usage is based on *active usage* only.
#### Instance Types
When you deploy a container, you specify an [instance type](https://developers.cloudflare.com/containers/platform-details/#instance-types).
The instance type you select will impact your bill — larger instances include more memory and disk, incurring additional costs, and higher CPU capacity, which allows you to incur higher CPU costs based on active usage.
The following instance types are currently available:
| Instance Type | vCPU | Memory | Disk |
| - | - | - | - |
| lite | 1/16 | 256 MiB | 2 GB |
| basic | 1/4 | 1 GiB | 4 GB |
| standard-1 | 1/2 | 4 GiB | 8 GB |
| standard-2 | 1 | 6 GiB | 12 GB |
| standard-3 | 2 | 8 GiB | 16 GB |
| standard-4 | 4 | 12 GiB | 20 GB |
## Network Egress
Egress from Containers is priced at the following rates:
| Region | Price per GB | Included Allotment per month |
| - | - | - |
| North America & Europe | $0.025 | 1 TB |
| Oceania, Korea, Taiwan | $0.05 | 500 GB |
| Everywhere Else | $0.04 | 500 GB |
## Workers and Durable Objects Pricing
When you use Containers, incoming requests to your containers are handled by your [Worker](https://developers.cloudflare.com/workers/platform/pricing/), and each container has its own [Durable Object](https://developers.cloudflare.com/durable-objects/platform/pricing/). You are billed for your usage of both Workers and Durable Objects.
## Logs and Observability
Containers are integrated with the [Workers Logs](https://developers.cloudflare.com/workers/observability/logs/workers-logs/) platform, and billed at the same rate. Refer to [Workers Logs pricing](https://developers.cloudflare.com/workers/observability/logs/workers-logs/#pricing) for details.
When you [enable observability for your Worker](https://developers.cloudflare.com/workers/observability/logs/workers-logs/#enable-workers-logs) with a binding to a container, logs from your container will show in both the Containers and Observability sections of the Cloudflare dashboard.
---
title: Platform Reference · Cloudflare Containers docs
lastUpdated: 2025-09-22T15:52:17.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/containers/platform-details/
md: https://developers.cloudflare.com/containers/platform-details/index.md
---
---
title: Wrangler Commands · Cloudflare Containers docs
lastUpdated: 2025-09-22T15:52:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/wrangler-commands/
md: https://developers.cloudflare.com/containers/wrangler-commands/index.md
---
---
title: Wrangler Configuration · Cloudflare Containers docs
lastUpdated: 2025-09-22T15:52:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/containers/wrangler-configuration/
md: https://developers.cloudflare.com/containers/wrangler-configuration/index.md
---
---
title: 404 - Page Not Found · Cloudflare D1 docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/404/
md: https://developers.cloudflare.com/d1/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Best practices · Cloudflare D1 docs
lastUpdated: 2024-12-11T09:43:45.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/d1/best-practices/
md: https://developers.cloudflare.com/d1/best-practices/index.md
---
* [Import and export data](https://developers.cloudflare.com/d1/best-practices/import-export-data/)
* [Query a database](https://developers.cloudflare.com/d1/best-practices/query-d1/)
* [Retry queries](https://developers.cloudflare.com/d1/best-practices/retry-queries/)
* [Use indexes](https://developers.cloudflare.com/d1/best-practices/use-indexes/)
* [Local development](https://developers.cloudflare.com/d1/best-practices/local-development/)
* [Remote development](https://developers.cloudflare.com/d1/best-practices/remote-development/)
* [Use D1 from Pages](https://developers.cloudflare.com/pages/functions/bindings/#d1-databases)
* [Global read replication](https://developers.cloudflare.com/d1/best-practices/read-replication/)
---
title: Configuration · Cloudflare D1 docs
lastUpdated: 2025-04-09T22:35:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/d1/configuration/
md: https://developers.cloudflare.com/d1/configuration/index.md
---
* [Data location](https://developers.cloudflare.com/d1/configuration/data-location/)
* [Environments](https://developers.cloudflare.com/d1/configuration/environments/)
---
title: REST API · Cloudflare D1 docs
lastUpdated: 2025-04-09T22:35:27.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/d1-api/
md: https://developers.cloudflare.com/d1/d1-api/index.md
---
---
title: Demos and architectures · Cloudflare D1 docs
description: Learn how you can use D1 within your existing application and architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/demos/
md: https://developers.cloudflare.com/d1/demos/index.md
---
Learn how you can use D1 within your existing application and architecture.
## Featured Demos
* [Starter code for D1 Sessions API](https://github.com/cloudflare/templates/tree/main/d1-starter-sessions-api-template): An introduction to D1 Sessions API. This demo simulates purchase orders administration.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/d1-starter-sessions-api-template)
Tip: Place your database further away for the read replication demo
To simulate how read replication can improve a worst case latency scenario, select your primary database location to be in a farther away region (one of the deployment steps).
You can find this in the **Database location hint** dropdown.
## Demos
Explore the following demo applications for D1.
* [Starter code for D1 Sessions API:](https://github.com/cloudflare/templates/tree/main/d1-starter-sessions-api-template) An introduction to D1 Sessions API. This demo simulates purchase orders administration.
* [Jobs At Conf:](https://github.com/harshil1712/jobs-at-conf-demo) A job lisiting website to add jobs you find at in-person conferences. Built with Cloudflare Pages, R2, D1, Queues, and Workers AI.
* [Remix Authentication Starter:](https://github.com/harshil1712/remix-d1-auth-template) Implement authenticating to a Remix app and store user data in Cloudflare D1.
* [JavaScript-native RPC on Cloudflare Workers <> Named Entrypoints:](https://github.com/cloudflare/js-rpc-and-entrypoints-demo) This is a collection of examples of communicating between multiple Cloudflare Workers using the remote-procedure call (RPC) system that is built into the Workers runtime.
* [Workers for Platforms Example Project:](https://github.com/cloudflare/workers-for-platforms-example) Explore how you could manage thousands of Workers with a single Cloudflare Workers account.
* [Staff Directory demo:](https://github.com/lauragift21/staff-directory) Built using the powerful combination of HonoX for backend logic, Cloudflare Pages for fast and secure hosting, and Cloudflare D1 for seamless database management.
* [Wildebeest:](https://github.com/cloudflare/wildebeest) Wildebeest is an ActivityPub and Mastodon-compatible server whose goal is to allow anyone to operate their Fediverse server and identity on their domain without needing to keep infrastructure, with minimal setup and maintenance, and running in minutes.
* [D1 Northwind Demo:](https://github.com/cloudflare/d1-northwind) This is a demo of the Northwind dataset, running on Cloudflare Workers, and D1 - Cloudflare's SQL database, running on SQLite.
## Reference architectures
Explore the following reference architectures that use D1:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[You can connect a Cloudflare Worker to get data from Google BigQuery and pass it to Workers AI, to run AI Models, powered by serverless GPUs.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[Composable AI architecture](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[The architecture diagram illustrates how AI applications can be built end-to-end on Cloudflare, or single services can be integrated with external infrastructure and services.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[Serverless global APIs](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[An example architecture of a serverless API on Cloudflare and aims to illustrate how different compute and data products could interact with each other.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[Retrieval Augmented Generation (RAG)](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
[RAG combines retrieval with generative models for better text. It uses external knowledge to create factual, relevant responses, improving coherence and accuracy in NLP tasks like chatbots.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
---
title: Examples · Cloudflare D1 docs
description: Explore the following examples for D1.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/d1/examples/
md: https://developers.cloudflare.com/d1/examples/index.md
---
Explore the following examples for D1.
[Query D1 from Python Workers](https://developers.cloudflare.com/d1/examples/query-d1-from-python-workers/)
[Learn how to query D1 from a Python Worker](https://developers.cloudflare.com/d1/examples/query-d1-from-python-workers/)
[Query D1 from Hono](https://developers.cloudflare.com/d1/examples/d1-and-hono/)
[Query D1 from the Hono web framework](https://developers.cloudflare.com/d1/examples/d1-and-hono/)
[Query D1 from Remix](https://developers.cloudflare.com/d1/examples/d1-and-remix/)
[Query your D1 database from a Remix application.](https://developers.cloudflare.com/d1/examples/d1-and-remix/)
[Query D1 from SvelteKit](https://developers.cloudflare.com/d1/examples/d1-and-sveltekit/)
[Query a D1 database from a SvelteKit application.](https://developers.cloudflare.com/d1/examples/d1-and-sveltekit/)
---
title: Getting started · Cloudflare D1 docs
description: "This guide instructs you through:"
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/get-started/
md: https://developers.cloudflare.com/d1/get-started/index.md
---
This guide instructs you through:
* Creating your first database using D1, Cloudflare's native serverless SQL database.
* Creating a schema and querying your database via the command-line.
* Connecting a [Cloudflare Worker](https://developers.cloudflare.com/workers/) to your D1 database using bindings, and querying your D1 database programmatically.
You can perform these tasks through the CLI or through the Cloudflare dashboard.
Note
If you already have an existing Worker and an existing D1 database, follow this tutorial from [3. Bind your Worker to your D1 database](https://developers.cloudflare.com/d1/get-started/#3-bind-your-worker-to-your-d1-database).
## Quick start
If you want to skip the steps and get started quickly, click on the button below.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/docs-examples/tree/d1-get-started/d1/d1-get-started)
This creates a repository in your GitHub account and deploys the application to Cloudflare Workers. Use this option if you are familiar with Cloudflare Workers, and wish to skip the step-by-step guidance.
You may wish to manually follow the steps if you are new to Cloudflare Workers.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
## 1. Create a Worker
Create a new Worker as the means to query your database.
* CLI
1. Create a new project named `d1-tutorial` by running:
* npm
```sh
npm create cloudflare@latest -- d1-tutorial
```
* yarn
```sh
yarn create cloudflare d1-tutorial
```
* pnpm
```sh
pnpm create cloudflare@latest d1-tutorial
```
For setup, select the following options:
* For *What would you like to start with?*, choose `Hello World example`.
* For *Which template would you like to use?*, choose `Worker only`.
* For *Which language do you want to use?*, choose `TypeScript`.
* For *Do you want to use git for version control?*, choose `Yes`.
* For *Do you want to deploy your application?*, choose `No` (we will be making some changes before deploying).
This creates a new `d1-tutorial` directory as illustrated below.
Your new `d1-tutorial` directory includes:
* A `"Hello World"` [Worker](https://developers.cloudflare.com/workers/get-started/guide/#3-write-code) in `index.ts`.
* A [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/). This file is how your `d1-tutorial` Worker accesses your D1 database.
Note
If you are familiar with Cloudflare Workers, or initializing projects in a Continuous Integration (CI) environment, initialize a new project non-interactively by setting `CI=true` as an [environmental variable](https://developers.cloudflare.com/workers/configuration/environment-variables/) when running `create cloudflare@latest`.
For example: `CI=true npm create cloudflare@latest d1-tutorial --type=simple --git --ts --deploy=false` creates a basic "Hello World" project ready to build on.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page. [Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select **Create application**.
3. Select **Start with Hello World!** > **Get started**.
4. Name your Worker. For this tutorial, name your Worker `d1-tutorial`.
5. Select **Deploy**.
* npm
```sh
npm create cloudflare@latest -- d1-tutorial
```
* yarn
```sh
yarn create cloudflare d1-tutorial
```
* pnpm
```sh
pnpm create cloudflare@latest d1-tutorial
```
## 2. Create a database
A D1 database is conceptually similar to many other SQL databases: a database may contain one or more tables, the ability to query those tables, and optional indexes. D1 uses the familiar [SQL query language](https://www.sqlite.org/lang.html) (as used by SQLite).
To create your first D1 database:
* CLI
1. Change into the directory you just created for your Workers project:
```sh
cd d1-tutorial
```
2. Run the following `wrangler@latest d1` command and give your database a name. In this tutorial, the database is named `prod-d1-tutorial`:
Note
The [Wrangler command-line interface](https://developers.cloudflare.com/workers/wrangler/) is Cloudflare's tool for managing and deploying Workers applications and D1 databases in your terminal. It was installed when you used `npm create cloudflare@latest` to initialize your new project.
While Wrangler gets installed locally to your project, you can use it outside the project by using the command `npx wrangler`.
```sh
npx wrangler@latest d1 create prod-d1-tutorial
```
```txt
✅ Successfully created DB 'prod-d1-tutorial' in region WEUR
Created your new D1 database.
{
"d1_databases": [
{
"binding": "prod_d1_tutorial",
"database_name": "prod-d1-tutorial",
"database_id": ""
}
]
}
```
3. When prompted: `Would you like Wrangler to add it on your behalf?`, select `Yes`. This will automatically add the binding to your Wrangler configuration file.
This creates a new D1 database and outputs the [binding](https://developers.cloudflare.com/workers/runtime-apis/bindings/) configuration needed in the next step.
* Dashboard
1. In the Cloudflare dashboard, go to the **D1 SQL database** page.
[Go to **D1 SQL database**](https://dash.cloudflare.com/?to=/:account/workers/d1)
2. Select **Create Database**.
3. Name your database. For this tutorial, name your D1 database `prod-d1-tutorial`.
4. (Optional) Provide a location hint. Location hint is an optional parameter you can provide to indicate your desired geographical location for your database. Refer to [Provide a location hint](https://developers.cloudflare.com/d1/configuration/data-location/#provide-a-location-hint) for more information.
5. Select **Create**.
Note
For reference, a good database name:
* Uses a combination of ASCII characters, shorter than 32 characters, and uses dashes (-) instead of spaces.
* Is descriptive of the use-case and environment. For example, "staging-db-web" or "production-db-backend".
* Only describes the database, and is not directly referenced in code.
## 3. Bind your Worker to your D1 database
You must create a binding for your Worker to connect to your D1 database. [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) allow your Workers to access resources, like D1, on the Cloudflare developer platform.
To bind your D1 database to your Worker:
* CLI
You can automatically add the binding to your Wrangler configuration file when you run the `wrangler d1 create` command (step 3 of [2. Create a database](https://developers.cloudflare.com/d1/get-started/#2-create-a-database)).
But if you wish to add the binding manually, follow the steps below:
1. Copy the lines obtained from step 2 of [2. Create a database](https://developers.cloudflare.com/d1/get-started/#2-create-a-database) from your terminal.
2. Add them to the end of your Wrangler file.
* wrangler.jsonc
```jsonc
{
"d1_databases": [
{
"binding": "prod_d1_tutorial", // available in your Worker on env.DB
"database_name": "prod-d1-tutorial",
"database_id": ""
}
]
}
```
* wrangler.toml
```toml
[[d1_databases]]
binding = "prod_d1_tutorial"
database_name = "prod-d1-tutorial"
database_id = ""
```
Specifically:
* The value (string) you set for `binding` is the **binding name**, and is used to reference this database in your Worker. In this tutorial, name your binding `prod_d1_tutorial`.
* The binding name must be [a valid JavaScript variable name](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Guide/Grammar_and_types#variables). For example, `binding = "MY_DB"` or `binding = "productionDB"` would both be valid names for the binding.
* Your binding is available in your Worker at `env.` and the D1 [Workers Binding API](https://developers.cloudflare.com/d1/worker-api/) is exposed on this binding.
Note
When you execute the `wrangler d1 create` command, the client API package (which implements the D1 API and database class) is automatically installed. For more information on the D1 Workers Binding API, refer to [Workers Binding API](https://developers.cloudflare.com/d1/worker-api/).
You can also bind your D1 database to a [Pages Function](https://developers.cloudflare.com/pages/functions/). For more information, refer to [Functions Bindings for D1](https://developers.cloudflare.com/pages/functions/bindings/#d1-databases).
* Dashboard
You create bindings by adding them to the Worker you have created.
1. In the Cloudflare dashboard, go to the **Workers & Pages** page. [Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select the `d1-tutorial` Worker you created in [step 1](https://developers.cloudflare.com/d1/get-started/#1-create-a-worker).
3. Go to the **Bindings** tab.
4. Select **Add binding**.
5. Select **D1 database** > **Add binding**.
6. Name your binding in **Variable name**, then select the `prod-d1-tutorial` D1 database you created in [step 2](https://developers.cloudflare.com/d1/get-started/#2-create-a-database) from the dropdown menu. For this tutorial, name your binding `prod_d1_tutorial`.
7. Select **Add binding**.
* wrangler.jsonc
```jsonc
{
"d1_databases": [
{
"binding": "prod_d1_tutorial", // available in your Worker on env.DB
"database_name": "prod-d1-tutorial",
"database_id": ""
}
]
}
```
* wrangler.toml
```toml
[[d1_databases]]
binding = "prod_d1_tutorial"
database_name = "prod-d1-tutorial"
database_id = ""
```
## 4. Run a query against your D1 database
### Populate your D1 database
* CLI
After correctly preparing your [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/), set up your database. Create a `schema.sql` file using the SQL syntax below to initialize your database.
1. Copy the following code and save it as a `schema.sql` file in the `d1-tutorial` Worker directory you created in step 1:
```sql
DROP TABLE IF EXISTS Customers;
CREATE TABLE IF NOT EXISTS Customers (CustomerId INTEGER PRIMARY KEY, CompanyName TEXT, ContactName TEXT);
INSERT INTO Customers (CustomerID, CompanyName, ContactName) VALUES (1, 'Alfreds Futterkiste', 'Maria Anders'), (4, 'Around the Horn', 'Thomas Hardy'), (11, 'Bs Beverages', 'Victoria Ashworth'), (13, 'Bs Beverages', 'Random Name');
```
2. Initialize your database to run and test locally first. Bootstrap your new D1 database by running:
```sh
npx wrangler d1 execute prod-d1-tutorial --local --file=./schema.sql
```
```txt
⛅️ wrangler 4.13.2
-------------------
🌀 Executing on local database prod-d1-tutorial () from .wrangler/state/v3/d1:
🌀 To execute on your remote database, add a --remote flag to your wrangler command.
🚣 3 commands executed successfully.
```
Note
The command `npx wrangler d1 execute` initializes your database locally, not on the remote database.
3. Validate that your data is in the database by running:
```sh
npx wrangler d1 execute prod-d1-tutorial --local --command="SELECT * FROM Customers"
```
```txt
🌀 Executing on local database jun-d1-db-gs-2025 (cf91ec5c-fa77-4d49-ad8e-e22921b996b2) from .wrangler/state/v3/d1:
🌀 To execute on your remote database, add a --remote flag to your wrangler command.
🚣 1 command executed successfully.
┌────────────┬─────────────────────┬───────────────────┐
│ CustomerId │ CompanyName │ ContactName │
├────────────┼─────────────────────┼───────────────────┤
│ 1 │ Alfreds Futterkiste │ Maria Anders │
├────────────┼─────────────────────┼───────────────────┤
│ 4 │ Around the Horn │ Thomas Hardy │
├────────────┼─────────────────────┼───────────────────┤
│ 11 │ Bs Beverages │ Victoria Ashworth │
├────────────┼─────────────────────┼───────────────────┤
│ 13 │ Bs Beverages │ Random Name │
└────────────┴─────────────────────┴───────────────────┘
```
* Dashboard
Use the Dashboard to create a table and populate it with data.
1. In the Cloudflare dashboard, go to the **D1 SQL database** page.
[Go to **D1 SQL database**](https://dash.cloudflare.com/?to=/:account/workers/d1)
2. Select the `prod-d1-tutorial` database you created in [step 2](https://developers.cloudflare.com/d1/get-started/#2-create-a-database).
3. Select **Console**.
4. Paste the following SQL snippet.
```sql
DROP TABLE IF EXISTS Customers;
CREATE TABLE IF NOT EXISTS Customers (CustomerId INTEGER PRIMARY KEY, CompanyName TEXT, ContactName TEXT);
INSERT INTO Customers (CustomerID, CompanyName, ContactName) VALUES (1, 'Alfreds Futterkiste', 'Maria Anders'), (4, 'Around the Horn', 'Thomas Hardy'), (11, 'Bs Beverages', 'Victoria Ashworth'), (13, 'Bs Beverages', 'Random Name');
```
5. Select **Execute**. This creates a table called `Customers` in your `prod-d1-tutorial` database.
6. Select **Tables**, then select the `Customers` table to view the contents of the table.
### Write queries within your Worker
After you have set up your database, run an SQL query from within your Worker.
* CLI
1. Navigate to your `d1-tutorial` Worker and open the `index.ts` file. The `index.ts` file is where you configure your Worker's interactions with D1.
2. Clear the content of `index.ts`.
3. Paste the following code snippet into your `index.ts` file:
* JavaScript
```js
export default {
async fetch(request, env) {
const { pathname } = new URL(request.url);
if (pathname === "/api/beverages") {
// If you did not use `DB` as your binding name, change it here
const { results } = await env.prod_d1_tutorial
.prepare("SELECT * FROM Customers WHERE CompanyName = ?")
.bind("Bs Beverages")
.run();
return Response.json(results);
}
return new Response(
"Call /api/beverages to see everyone who works at Bs Beverages",
);
},
};
```
* TypeScript
```ts
export interface Env {
// If you set another name in the Wrangler config file for the value for 'binding',
// replace "DB" with the variable name you defined.
prod_d1_tutorial: D1Database;
}
export default {
async fetch(request, env): Promise {
const { pathname } = new URL(request.url);
if (pathname === "/api/beverages") {
// If you did not use `DB` as your binding name, change it here
const { results } = await env.prod_d1_tutorial.prepare(
"SELECT * FROM Customers WHERE CompanyName = ?",
)
.bind("Bs Beverages")
.run();
return Response.json(results);
}
return new Response(
"Call /api/beverages to see everyone who works at Bs Beverages",
);
},
} satisfies ExportedHandler;
```
* Python
```python
from workers import Response, WorkerEntrypoint
from urllib.parse import urlparse
class Default(WorkerEntrypoint):
async def fetch(self, request):
pathname = urlparse(request.url).path
if pathname == "/api/beverages":
query = (
await self.env.prod_d1_tutorial.prepare(
"SELECT * FROM Customers WHERE CompanyName = ?",
)
.bind("Bs Beverages")
.run()
)
return Response.json(query.results)
return Response(
"Call /api/beverages to see everyone who works at Bs Beverages"
)
```
In the code above, you:
1. Define a binding to your D1 database in your code. This binding matches the `binding` value you set in the [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/) under `d1_databases`.
2. Query your database using `env.prod_d1_tutorial.prepare` to issue a [prepared query](https://developers.cloudflare.com/d1/worker-api/d1-database/#prepare) with a placeholder (the `?` in the query).
3. Call `bind()` to safely and securely bind a value to that placeholder. In a real application, you would allow a user to pass the `CompanyName` they want to list results for. Using `bind()` prevents users from executing arbitrary SQL (known as "SQL injection") against your application and deleting or otherwise modifying your database.
4. Execute the query by calling [`run()`](https://developers.cloudflare.com/d1/worker-api/prepared-statements/#run) to return all rows (or none, if the query returns none).
5. Return your query results, if any, in JSON format with `Response.json(results)`.
After configuring your Worker, you can test your project locally before you deploy globally.
* Dashboard
You can query your D1 database using your Worker.
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select the `d1-tutorial` Worker you created.
3. Select the **Edit code** icon (**\**).
4. Clear the contents of the `worker.js` file, then paste the following code:
```js
export default {
async fetch(request, env) {
const { pathname } = new URL(request.url);
if (pathname === "/api/beverages") {
// If you did not use `DB` as your binding name, change it here
const { results } = await env.prod_d1_tutorial.prepare(
"SELECT * FROM Customers WHERE CompanyName = ?"
)
.bind("Bs Beverages")
.run();
return new Response(JSON.stringify(results), {
headers: { 'Content-Type': 'application/json' }
});
}
return new Response(
"Call /api/beverages to see everyone who works at Bs Beverages"
);
},
};
```
5. Select **Save**.
* JavaScript
```js
export default {
async fetch(request, env) {
const { pathname } = new URL(request.url);
if (pathname === "/api/beverages") {
// If you did not use `DB` as your binding name, change it here
const { results } = await env.prod_d1_tutorial
.prepare("SELECT * FROM Customers WHERE CompanyName = ?")
.bind("Bs Beverages")
.run();
return Response.json(results);
}
return new Response(
"Call /api/beverages to see everyone who works at Bs Beverages",
);
},
};
```
* TypeScript
```ts
export interface Env {
// If you set another name in the Wrangler config file for the value for 'binding',
// replace "DB" with the variable name you defined.
prod_d1_tutorial: D1Database;
}
export default {
async fetch(request, env): Promise {
const { pathname } = new URL(request.url);
if (pathname === "/api/beverages") {
// If you did not use `DB` as your binding name, change it here
const { results } = await env.prod_d1_tutorial.prepare(
"SELECT * FROM Customers WHERE CompanyName = ?",
)
.bind("Bs Beverages")
.run();
return Response.json(results);
}
return new Response(
"Call /api/beverages to see everyone who works at Bs Beverages",
);
},
} satisfies ExportedHandler;
```
* Python
```python
from workers import Response, WorkerEntrypoint
from urllib.parse import urlparse
class Default(WorkerEntrypoint):
async def fetch(self, request):
pathname = urlparse(request.url).path
if pathname == "/api/beverages":
query = (
await self.env.prod_d1_tutorial.prepare(
"SELECT * FROM Customers WHERE CompanyName = ?",
)
.bind("Bs Beverages")
.run()
)
return Response.json(query.results)
return Response(
"Call /api/beverages to see everyone who works at Bs Beverages"
)
```
## 5. Deploy your application
Deploy your application on Cloudflare's global network.
* CLI
To deploy your Worker to production using Wrangler, you must first repeat the [database configuration](https://developers.cloudflare.com/d1/get-started/#populate-your-d1-database) steps after replacing the `--local` flag with the `--remote` flag to give your Worker data to read. This creates the database tables and imports the data into the production version of your database.
1. Create tables and add entries to your remote database with the `schema.sql` file you created in step 4. Enter `y` to confirm your decision.
```sh
npx wrangler d1 execute prod-d1-tutorial --remote --file=./schema.sql
```
```txt
🌀 Executing on remote database prod-d1-tutorial ():
🌀 To execute on your local development database, remove the --remote flag from your wrangler command.
Note: if the execution fails to complete, your DB will return to its original state and you can safely retry.
├ 🌀 Uploading .a7f10c4651cc3a26.sql
│ 🌀 Uploading complete.
│
🌀 Starting import...
🌀 Processed 3 queries.
🚣 Executed 3 queries in 0.00 seconds (5 rows read, 6 rows written)
Database is currently at bookmark 00000000-0000000a-00004f6d-b85c16a3dbcf077cb8f258b4d4eb965e.
┌────────────────────────┬───────────┬──────────────┬────────────────────┐
│ Total queries executed │ Rows read │ Rows written │ Database size (MB) │
├────────────────────────┼───────────┼──────────────┼────────────────────┤
│ 3 │ 5 │ 6 │ 0.02 │
└────────────────────────┴───────────┴──────────────┴────────────────────┘
```
2. Validate the data is in production by running:
```sh
npx wrangler d1 execute prod-d1-tutorial --remote --command="SELECT * FROM Customers"
```
```txt
⛅️ wrangler 4.33.1
───────────────────
🌀 Executing on remote database jun-d1-db-gs-2025 (cf91ec5c-fa77-4d49-ad8e-e22921b996b2):
🌀 To execute on your local development database, remove the --remote flag from your wrangler command.
🚣 Executed 1 command in 0.1797ms
┌────────────┬─────────────────────┬───────────────────┐
│ CustomerId │ CompanyName │ ContactName │
├────────────┼─────────────────────┼───────────────────┤
│ 1 │ Alfreds Futterkiste │ Maria Anders │
├────────────┼─────────────────────┼───────────────────┤
│ 4 │ Around the Horn │ Thomas Hardy │
├────────────┼─────────────────────┼───────────────────┤
│ 11 │ Bs Beverages │ Victoria Ashworth │
├────────────┼─────────────────────┼───────────────────┤
│ 13 │ Bs Beverages │ Random Name │
└────────────┴─────────────────────┴───────────────────┘
```
3. Deploy your Worker to make your project accessible on the Internet. Run:
```sh
npx wrangler deploy
```
```txt
⛅️ wrangler 4.33.1
────────────────────
Total Upload: 0.52 KiB / gzip: 0.33 KiB
Your Worker has access to the following bindings:
Binding Resource
env.prod_d1_tutorial (prod-d1-tutorial) D1 Database
Uploaded prod-d1-tutorial (4.17 sec)
Deployed prod-d1-tutorial triggers (3.49 sec)
https://prod-d1-tutorial.pcx-team.workers.dev
Current Version ID: 42c82f1c-ff2b-4dce-9ea2-265adcccd0d5
```
You can now visit the URL for your newly created project to query your live database.
For example, if the URL of your new Worker is `d1-tutorial..workers.dev`, accessing `https://d1-tutorial..workers.dev/api/beverages` sends a request to your Worker that queries your live database directly.
4. Test your database is running successfully. Add `/api/beverages` to the provided Wrangler URL. For example, `https://d1-tutorial..workers.dev/api/beverages`.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page. [Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select your `d1-tutorial` Worker.
3. Select **Deployments**.
4. From the **Version History** table, select **Deploy version**.
5. From the **Deploy version** page, select **Deploy**.
This deploys the latest version of the Worker code to production.
## 6. (Optional) Develop locally with Wrangler
If you are using D1 with Wrangler, you can test your database locally. While in your project directory:
1. Run `wrangler dev`:
```sh
npx wrangler dev
```
When you run `wrangler dev`, Wrangler provides a URL (most likely `localhost:8787`) to review your Worker.
2. Go to the URL.
The page displays `Call /api/beverages to see everyone who works at Bs Beverages`.
3. Test your database is running successfully. Add `/api/beverages` to the provided Wrangler URL. For example, `localhost:8787/api/beverages`.
If successful, the browser displays your data.
Note
You can only develop locally if you are using Wrangler. You cannot develop locally through the Cloudflare dashboard.
## 7. (Optional) Delete your database
To delete your database:
* CLI
Run:
```sh
npx wrangler d1 delete prod-d1-tutorial
```
* Dashboard
1. In the Cloudflare dashboard, go to the **D1 SQL database** page.
[Go to **D1 SQL database**](https://dash.cloudflare.com/?to=/:account/workers/d1)
2. Select your `prod-d1-tutorial` D1 database.
3. Select **Settings**.
4. Select **Delete**.
5. Type the name of the database (`prod-d1-tutorial`) to confirm the deletion.
Warning
Note that deleting your D1 database will stop your application from functioning as before.
If you want to delete your Worker:
* CLI
Run:
```sh
npx wrangler delete d1-tutorial
```
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select your `d1-tutorial` Worker.
3. Select **Settings**.
4. Scroll to the bottom of the page, then select **Delete**.
5. Type the name of the Worker (`d1-tutorial`) to confirm the deletion.
## Summary
In this tutorial, you have:
* Created a D1 database
* Created a Worker to access that database
* Deployed your project globally
## Next steps
If you have any feature requests or notice any bugs, share your feedback directly with the Cloudflare team by joining the [Cloudflare Developers community on Discord](https://discord.cloudflare.com).
* See supported [Wrangler commands for D1](https://developers.cloudflare.com/workers/wrangler/commands/#d1).
* Learn how to use [D1 Worker Binding APIs](https://developers.cloudflare.com/d1/worker-api/) within your Worker, and test them from the [API playground](https://developers.cloudflare.com/d1/worker-api/#api-playground).
* Explore [community projects built on D1](https://developers.cloudflare.com/d1/reference/community-projects/).
---
title: Observability · Cloudflare D1 docs
lastUpdated: 2025-04-09T22:35:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/d1/observability/
md: https://developers.cloudflare.com/d1/observability/index.md
---
* [Audit Logs](https://developers.cloudflare.com/d1/observability/audit-logs/)
* [Debug D1](https://developers.cloudflare.com/d1/observability/debug-d1/)
* [Metrics and analytics](https://developers.cloudflare.com/d1/observability/metrics-analytics/)
* [Billing](https://developers.cloudflare.com/d1/observability/billing/)
---
title: Platform · Cloudflare D1 docs
lastUpdated: 2025-04-09T22:35:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/d1/platform/
md: https://developers.cloudflare.com/d1/platform/index.md
---
* [Pricing](https://developers.cloudflare.com/d1/platform/pricing/)
* [Limits](https://developers.cloudflare.com/d1/platform/limits/)
* [Alpha database migration guide](https://developers.cloudflare.com/d1/platform/alpha-migration/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
* [Release notes](https://developers.cloudflare.com/d1/platform/release-notes/)
---
title: Reference · Cloudflare D1 docs
lastUpdated: 2025-04-09T22:35:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/d1/reference/
md: https://developers.cloudflare.com/d1/reference/index.md
---
* [Migrations](https://developers.cloudflare.com/d1/reference/migrations/)
* [Time Travel and backups](https://developers.cloudflare.com/d1/reference/time-travel/)
* [Community projects](https://developers.cloudflare.com/d1/reference/community-projects/)
* [Generated columns](https://developers.cloudflare.com/d1/reference/generated-columns/)
* [Data security](https://developers.cloudflare.com/d1/reference/data-security/)
* [Backups (Legacy)](https://developers.cloudflare.com/d1/reference/backups/)
* [FAQs](https://developers.cloudflare.com/d1/reference/faq/)
* [Glossary](https://developers.cloudflare.com/d1/reference/glossary/)
---
title: SQL API · Cloudflare D1 docs
lastUpdated: 2025-04-09T22:35:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/d1/sql-api/
md: https://developers.cloudflare.com/d1/sql-api/index.md
---
* [SQL statements](https://developers.cloudflare.com/d1/sql-api/sql-statements/)
* [Define foreign keys](https://developers.cloudflare.com/d1/sql-api/foreign-keys/)
* [Query JSON](https://developers.cloudflare.com/d1/sql-api/query-json/)
---
title: Tutorials · Cloudflare D1 docs
description: View tutorials to help you get started with D1.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/tutorials/
md: https://developers.cloudflare.com/d1/tutorials/index.md
---
View tutorials to help you get started with D1.
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [Deploy an Express.js application on Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/deploy-an-express-app/) | 4 months ago | Beginner |
| [Query D1 using Prisma ORM](https://developers.cloudflare.com/d1/tutorials/d1-and-prisma-orm/) | 8 months ago | Beginner |
| [Using D1 Read Replication for your e-commerce website](https://developers.cloudflare.com/d1/tutorials/using-read-replication-for-e-com/) | 10 months ago | Beginner |
| [Build a Retrieval Augmented Generation (RAG) AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-retrieval-augmented-generation-ai/) | about 1 year ago | Beginner |
| [Bulk import to D1 using REST API](https://developers.cloudflare.com/d1/tutorials/import-to-d1-with-rest-api/) | over 1 year ago | Beginner |
| [Build a Comments API](https://developers.cloudflare.com/d1/tutorials/build-a-comments-api/) | over 1 year ago | Intermediate |
| [Build an API to access D1 using a proxy Worker](https://developers.cloudflare.com/d1/tutorials/build-an-api-to-access-d1/) | over 1 year ago | Intermediate |
| [Build a Staff Directory Application](https://developers.cloudflare.com/d1/tutorials/build-a-staff-directory-app/) | almost 2 years ago | Intermediate |
## Videos
Cloudflare Workflows | Introduction (Part 1 of 3)
In this video, we introduce Cloudflare Workflows, the Newest Developer Platform Primitive at Cloudflare.
Cloudflare Workflows | Batching and Monitoring Your Durable Execution (Part 2 of 3)
Workflows exposes metrics such as execution, error rates, steps, and total duration!
Welcome to the Cloudflare Developer Channel
Welcome to the Cloudflare Developers YouTube channel. We've got tutorials and working demos and everything you need to level up your projects. Whether you're working on your next big thing or just dorking around with some side projects, we've got you covered! So why don't you come hang out, subscribe to our developer channel and together we'll build something awesome. You're gonna love it.
Stateful Apps with Cloudflare Workers
Learn how to access external APIs, cache and retrieve data using Workers KV, and create SQL-driven applications with Cloudflare D1.
---
title: Workers Binding API · Cloudflare D1 docs
description: "You can execute SQL queries on your D1 database from a Worker
using the Worker Binding API. To do this, you can perform the following
steps:"
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/worker-api/
md: https://developers.cloudflare.com/d1/worker-api/index.md
---
You can execute SQL queries on your D1 database from a Worker using the Worker Binding API. To do this, you can perform the following steps:
1. [Bind the D1 Database](https://developers.cloudflare.com/d1/get-started/#3-bind-your-worker-to-your-d1-database).
2. [Prepare a statement](https://developers.cloudflare.com/d1/worker-api/d1-database/#prepare).
3. [Run the prepared statement](https://developers.cloudflare.com/d1/worker-api/prepared-statements).
4. Analyze the [return object](https://developers.cloudflare.com/d1/worker-api/return-object) (if necessary).
Refer to the relevant sections for the API documentation.
## TypeScript support
D1 Worker Bindings API is fully-typed via the runtime types generated by running [`wrangler types`](https://developers.cloudflare.com/workers/languages/typescript/#typescript) package, and also supports [generic types](https://www.typescriptlang.org/docs/handbook/2/generics.html#generic-types) as part of its TypeScript API. A generic type allows you to provide an optional `type parameter` so that a function understands the type of the data it is handling.
When using the query statement methods [`D1PreparedStatement::run`](https://developers.cloudflare.com/d1/worker-api/prepared-statements/#run), [`D1PreparedStatement::raw`](https://developers.cloudflare.com/d1/worker-api/prepared-statements/#raw) and [`D1PreparedStatement::first`](https://developers.cloudflare.com/d1/worker-api/prepared-statements/#first), you can provide a type representing each database row. D1's API will [return the result object](https://developers.cloudflare.com/d1/worker-api/return-object/#d1result) with the correct type.
For example, providing an `OrderRow` type as a type parameter to [`D1PreparedStatement::run`](https://developers.cloudflare.com/d1/worker-api/prepared-statements/#run) will return a typed `Array` object instead of the default `Record` type:
```ts
// Row definition
type OrderRow = {
Id: string;
CustomerName: string;
OrderDate: number;
};
// Elsewhere in your application
// env.MY_DB is the D1 database binding from your Wrangler configuration file
const result = await env.MY_DB.prepare(
"SELECT Id, CustomerName, OrderDate FROM [Order] ORDER BY ShippedDate DESC LIMIT 100",
).run();
```
## Type conversion
D1 automatically converts supported JavaScript (including TypeScript) types passed as parameters via the Workers Binding API to their associated D1 types 1. This conversion is permanent and one-way only. This means that when reading the written values back in your code, you will get the converted values rather than the originally inserted values.
Note
We recommend using [STRICT tables](https://www.sqlite.org/stricttables.html) in your SQL schema to avoid issues with mismatched types between values that are actually stored in your database compared to values defined by your schema.
The type conversion during writes is as follows:
| JavaScript (write) | D1 | JavaScript (read) |
| - | - | - |
| null | `NULL` | null |
| Number | `REAL` | Number |
| Number 2 | `INTEGER` | Number |
| String | `TEXT` | String |
| Boolean 3 | `INTEGER` | Number (`0`,`1`) |
| ArrayBuffer | `BLOB` | Array 4 |
| ArrayBuffer View | `BLOB` | Array 4 |
| undefined | Not supported. 5 | - |
1 D1 types correspond to the underlying [SQLite types](https://www.sqlite.org/datatype3.html).
2 D1 supports 64-bit signed `INTEGER` values internally, however [BigInts](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/BigInt) are not currently supported in the API yet. JavaScript integers are safe up to [`Number.MAX_SAFE_INTEGER`](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/Number/MAX_SAFE_INTEGER).
3 Booleans will be cast to an `INTEGER` type where `1` is `TRUE` and `0` is `FALSE`.
4 `ArrayBuffer` and [`ArrayBuffer` views](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/ArrayBuffer/isView) are converted using [`Array.from`](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/Array/from).
5 Queries with `undefined` values will return a `D1_TYPE_ERROR`.
## API playground
The D1 Worker Binding API playground is an `index.js` file where you can test each of the documented Worker Binding APIs for D1. The file builds from the end-state of the [Get started](https://developers.cloudflare.com/d1/get-started/#write-queries-within-your-worker) code.
You can use this alongside the API documentation to better understand how each API works.
Follow the steps to setup your API playground.
### 1. Complete the Get started tutorial
Complete the [Get started](https://developers.cloudflare.com/d1/get-started/#write-queries-within-your-worker) tutorial. Ensure you use JavaScript instead of TypeScript.
### 2. Modify the content of `index.js`
Replace the contents of your `index.js` file with the code below to view the effect of each API.
index.js
```js
// D1 API Playground - Test each D1 Worker Binding API method
// Change the URL pathname to test different methods (e.g., /RUN, /RAW, /FIRST)
export default {
async fetch(request, env) {
const { pathname } = new URL(request.url);
// Sample data for testing
const companyName1 = `Bs Beverages`;
const companyName2 = `Around the Horn`;
// Prepare reusable statements
const stmt = env.DB.prepare(`SELECT * FROM Customers WHERE CompanyName = ?`);
const stmtMulti = env.DB.prepare(`SELECT * FROM Customers; SELECT * FROM Customers WHERE CompanyName = ?`);
const session = env.DB.withSession("first-primary")
const sessionStmt = session.prepare(`SELECT * FROM Customers WHERE CompanyName = ?`);
// Test D1PreparedStatement::run - returns full D1Result object
if (pathname === `/RUN`){
const returnValue = await stmt.bind(companyName1).run();
return Response.json(returnValue);
// Test D1PreparedStatement::raw - returns array of arrays
} else if (pathname === `/RAW`){
const returnValue = await stmt.bind(companyName1).raw();
return Response.json(returnValue);
// Test D1PreparedStatement::first - returns first row only
} else if (pathname === `/FIRST`){
const returnValue = await stmt.bind(companyName1).first();
return Response.json(returnValue);
// Test D1Database::batch - execute multiple statements
} else if (pathname === `/BATCH`) {
const batchResult = await env.DB.batch([
stmt.bind(companyName1),
stmt.bind(companyName2)
]);
return Response.json(batchResult);
// Test D1Database::exec - execute raw SQL without parameters
} else if (pathname === `/EXEC`){
const returnValue = await env.DB.exec(`SELECT * FROM Customers WHERE CompanyName = "Bs Beverages"`);
return Response.json(returnValue);
// Test D1 Sessions API with read replication
} else if (pathname === `/WITHSESSION`){
const returnValue = await sessionStmt.bind(companyName1).run();
console.log("You're now using D1 Sessions!")
return Response.json(returnValue);
}
// Default response with instructions
return new Response(
`Welcome to the D1 API Playground!
\nChange the URL to test the various methods inside your index.js file.`,
);
},
};
```
### 3. Deploy the Worker
1. Navigate to your tutorial directory you created by following step 1.
2. Run `npx wrangler deploy`.
```sh
npx wrangler deploy
```
```sh
⛅️ wrangler 3.112.0
--------------------
Total Upload: 1.90 KiB / gzip: 0.59 KiB
Your worker has access to the following bindings:
- D1 Databases:
- DB: DATABASE_NAME ()
Uploaded WORKER_NAME (7.01 sec)
Deployed WORKER_NAME triggers (1.25 sec)
https://jun-d1-rr.d1-sandbox.workers.dev
Current Version ID: VERSION_ID
```
3. Open a browser at the specified address.
### 4. Test the APIs
Change the URL to test the various D1 Worker Binding APIs.
```plaintext
```
---
title: Wrangler commands · Cloudflare D1 docs
description: D1 Wrangler commands use REST APIs to interact with the control
plane. This page lists the Wrangler commands for D1.
lastUpdated: 2025-12-09T14:15:41.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/d1/wrangler-commands/
md: https://developers.cloudflare.com/d1/wrangler-commands/index.md
---
D1 Wrangler commands use REST APIs to interact with the control plane. This page lists the Wrangler commands for D1.
## `d1 create`
Creates a new D1 database, and provides the binding and UUID that you will put in your config file
This command acts on remote D1 Databases.
* npm
```sh
npx wrangler d1 create [NAME]
```
* pnpm
```sh
pnpm wrangler d1 create [NAME]
```
* yarn
```sh
yarn wrangler d1 create [NAME]
```
- `[NAME]` string required
The name of the new D1 database
- `--location` string
A hint for the primary location of the new DB. Options: weur: Western Europe eeur: Eastern Europe apac: Asia Pacific oc: Oceania wnam: Western North America enam: Eastern North America
- `--jurisdiction` string
The location to restrict the D1 database to run and store data within to comply with local regulations. Note that if jurisdictions are set, the location hint is ignored. Options: eu: The European Union fedramp: FedRAMP-compliant data centers
- `--use-remote` boolean
Use a remote binding when adding the newly created resource to your config
- `--update-config` boolean
Automatically update your config file with the newly added resource
- `--binding` string
The binding name of this resource in your Worker
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 info`
Get information about a D1 database, including the current database size and state
This command acts on remote D1 Databases.
* npm
```sh
npx wrangler d1 info [NAME]
```
* pnpm
```sh
pnpm wrangler d1 info [NAME]
```
* yarn
```sh
yarn wrangler d1 info [NAME]
```
- `[NAME]` string required
The name of the DB
- `--json` boolean default: false
Return output as clean JSON
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 list`
List all D1 databases in your account
This command acts on remote D1 Databases.
* npm
```sh
npx wrangler d1 list
```
* pnpm
```sh
pnpm wrangler d1 list
```
* yarn
```sh
yarn wrangler d1 list
```
- `--json` boolean default: false
Return output as clean JSON
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 delete`
Delete a D1 database
This command acts on remote D1 Databases.
* npm
```sh
npx wrangler d1 delete [NAME]
```
* pnpm
```sh
pnpm wrangler d1 delete [NAME]
```
* yarn
```sh
yarn wrangler d1 delete [NAME]
```
- `[NAME]` string required
The name or binding of the DB
- `--skip-confirmation` boolean alias: --y default: false
Skip confirmation
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 execute`
Execute a command or SQL file
You must provide either --command or --file for this command to run successfully.
* npm
```sh
npx wrangler d1 execute [DATABASE]
```
* pnpm
```sh
pnpm wrangler d1 execute [DATABASE]
```
* yarn
```sh
yarn wrangler d1 execute [DATABASE]
```
- `[DATABASE]` string required
The name or binding of the DB
- `--command` string
The SQL query you wish to execute, or multiple queries separated by ';'
- `--file` string
A .sql file to ingest
- `--yes` boolean alias: --y
Answer "yes" to any prompts
- `--local` boolean
Execute commands/files against a local DB for use with wrangler dev
- `--remote` boolean
Execute commands/files against a remote D1 database for use with remote bindings or your deployed Worker
- `--persist-to` string
Specify directory to use for local persistence (for use with --local)
- `--json` boolean default: false
Return output as clean JSON
- `--preview` boolean default: false
Execute commands/files against a preview D1 database
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 export`
Export the contents or schema of your database as a .sql file
* npm
```sh
npx wrangler d1 export [NAME]
```
* pnpm
```sh
pnpm wrangler d1 export [NAME]
```
* yarn
```sh
yarn wrangler d1 export [NAME]
```
- `[NAME]` string required
The name of the D1 database to export
- `--local` boolean
Export from your local DB you use with wrangler dev
- `--remote` boolean
Export from a remote D1 database
- `--output` string required
Path to the SQL file for your export
- `--table` string
Specify which tables to include in export
- `--no-schema` boolean
Only output table contents, not the DB schema
- `--no-data` boolean
Only output table schema, not the contents of the DBs themselves
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 time-travel info`
Retrieve information about a database at a specific point-in-time using Time Travel
This command acts on remote D1 Databases.
For more information about Time Travel, see
* npm
```sh
npx wrangler d1 time-travel info [DATABASE]
```
* pnpm
```sh
pnpm wrangler d1 time-travel info [DATABASE]
```
* yarn
```sh
yarn wrangler d1 time-travel info [DATABASE]
```
- `[DATABASE]` string required
The name or binding of the DB
- `--timestamp` string
Accepts a Unix (seconds from epoch) or RFC3339 timestamp (e.g. 2023-07-13T08:46:42.228Z) to retrieve a bookmark for
- `--json` boolean default: false
Return output as clean JSON
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 time-travel restore`
Restore a database back to a specific point-in-time
This command acts on remote D1 Databases.
For more information about Time Travel, see
* npm
```sh
npx wrangler d1 time-travel restore [DATABASE]
```
* pnpm
```sh
pnpm wrangler d1 time-travel restore [DATABASE]
```
* yarn
```sh
yarn wrangler d1 time-travel restore [DATABASE]
```
- `[DATABASE]` string required
The name or binding of the DB
- `--bookmark` string
Bookmark to use for time travel
- `--timestamp` string
Accepts a Unix (seconds from epoch) or RFC3339 timestamp (e.g. 2023-07-13T08:46:42.228Z) to retrieve a bookmark for (within the last 30 days)
- `--json` boolean default: false
Return output as clean JSON
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 migrations create`
Create a new migration
This will generate a new versioned file inside the 'migrations' folder. Name your migration file as a description of your change. This will make it easier for you to find your migration in the 'migrations' folder. An example filename looks like:
```
0000_create_user_table.sql
```
The filename will include a version number and the migration name you specify.
* npm
```sh
npx wrangler d1 migrations create [DATABASE] [MESSAGE]
```
* pnpm
```sh
pnpm wrangler d1 migrations create [DATABASE] [MESSAGE]
```
* yarn
```sh
yarn wrangler d1 migrations create [DATABASE] [MESSAGE]
```
- `[DATABASE]` string required
The name or binding of the DB
- `[MESSAGE]` string required
The Migration message
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 migrations list`
View a list of unapplied migration files
* npm
```sh
npx wrangler d1 migrations list [DATABASE]
```
* pnpm
```sh
pnpm wrangler d1 migrations list [DATABASE]
```
* yarn
```sh
yarn wrangler d1 migrations list [DATABASE]
```
- `[DATABASE]` string required
The name or binding of the DB
- `--local` boolean
Check migrations against a local DB for use with wrangler dev
- `--remote` boolean
Check migrations against a remote DB for use with wrangler dev --remote
- `--preview` boolean default: false
Check migrations against a preview D1 DB
- `--persist-to` string
Specify directory to use for local persistence (you must use --local with this flag)
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 migrations apply`
Apply any unapplied D1 migrations
This command will prompt you to confirm the migrations you are about to apply. Confirm that you would like to proceed. After applying, a backup will be captured.
The progress of each migration will be printed in the console.
When running the apply command in a CI/CD environment or another non-interactive command line, the confirmation step will be skipped, but the backup will still be captured.
If applying a migration results in an error, this migration will be rolled back, and the previous successful migration will remain applied.
* npm
```sh
npx wrangler d1 migrations apply [DATABASE]
```
* pnpm
```sh
pnpm wrangler d1 migrations apply [DATABASE]
```
* yarn
```sh
yarn wrangler d1 migrations apply [DATABASE]
```
- `[DATABASE]` string required
The name or binding of the DB
- `--local` boolean
Execute commands/files against a local DB for use with wrangler dev
- `--remote` boolean
Execute commands/files against a remote DB for use with wrangler dev --remote
- `--preview` boolean default: false
Execute commands/files against a preview D1 DB
- `--persist-to` string
Specify directory to use for local persistence (you must use --local with this flag)
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
## `d1 insights`
Experimental
Get information about the queries run on a D1 database
This command acts on remote D1 Databases.
* npm
```sh
npx wrangler d1 insights [NAME]
```
* pnpm
```sh
pnpm wrangler d1 insights [NAME]
```
* yarn
```sh
yarn wrangler d1 insights [NAME]
```
- `[NAME]` string required
The name of the DB
- `--timePeriod` string default: 1d
Fetch data from now to the provided time period
- `--sort-type` string default: sum
Choose the operation you want to sort insights by
- `--sort-by` string default: time
Choose the field you want to sort insights by
- `--sort-direction` string default: DESC
Choose a sort direction
- `--limit` number default: 5
fetch insights about the first X queries
- `--json` boolean default: false
return output as clean JSON
Global flags
* `--v` boolean alias: --version
Show version number
* `--cwd` string
Run as if Wrangler was started in the specified directory instead of the current working directory
* `--config` string alias: --c
Path to Wrangler configuration file
* `--env` string alias: --e
Environment to use for operations, and for selecting .env and .dev.vars files
* `--env-file` string
Path to an .env file to load - can be specified multiple times - values from earlier files are overridden by values in later files
* `--experimental-provision` boolean aliases: --x-provision default: true
Experimental: Enable automatic resource provisioning
* `--experimental-auto-create` boolean alias: --x-auto-create default: true
Automatically provision draft bindings with new resources
---
title: 404 - Page Not Found · Cloudflare Data Localization Suite docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/404/
md: https://developers.cloudflare.com/data-localization/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Changelog · Cloudflare Data Localization Suite docs
description: Subscribe to RSS
lastUpdated: 2025-02-13T19:35:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/changelog/
md: https://developers.cloudflare.com/data-localization/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/data-localization/changelog/index.xml)
## 2024-05-22
**Expanded Regional Services for more precise data localization.**
* Added Austria, Brazil, France, Hong Kong, Italy, NATO, the Netherlands, Russia, Saudi Arabia, South Africa, Spain, Switzerland, and Taiwan. Some regions may not appear in the dropdown as they require Cloudflare approval. Contact your account team for more information.
* Introduced Exclusive of Hong Kong and Macau, and Exclusive of Russia and Belarus options.
* Launched the Cloudflare Green Energy region, using renewable-powered data centers.
---
title: Cloudflare product compatibility · Cloudflare Data Localization Suite docs
description: The table below provides a summary of the Data Localization Suite
product's behavior with Cloudflare products. Refer to the table legend for
guidance on interpreting the table.
lastUpdated: 2025-12-11T11:16:37.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/compatibility/
md: https://developers.cloudflare.com/data-localization/compatibility/index.md
---
The table below provides a summary of the Data Localization Suite product's behavior with Cloudflare products. Refer to the table legend for guidance on interpreting the table.
✅ Product works with no caveats\
🚧 Product can be used with some caveats\
✘ Product cannot be used\
⚫️ Not applicable
## Application Performance
| Product | Geo Key Manager | Regional Services | Customer Metadata Boundary |
| - | - | - | - |
| Caching/CDN | ✅ | ✅ | ✅ |
| Cache Reserve | ⚫️ | 🚧 | ✅ [1](#user-content-fn-29) |
| DNS | ⚫️ | 🚧 [2](#user-content-fn-33) | 🚧 [3](#user-content-fn-32) |
| HTTP/3 (with QUIC) | ⚫️ | ✘ | ⚫️ |
| Image Resizing | ✅ | ✅ [4](#user-content-fn-6) | 🚧 [5](#user-content-fn-1) |
| Load Balancing | ✅ | ✅ | 🚧 [5](#user-content-fn-1) |
| Network Error Logging (NEL) | ⚫️ | ⚫️ | ✘ |
| Onion Routing | ✘ | ✘ | ✘ |
| Orange-to-Orange (O2O) | ✘ | ✘ | ✘ |
| Stream Delivery | ✅ | ✅ | ✅ |
| Tiered Caching | ✅ | 🚧 [6](#user-content-fn-2) | 🚧 [7](#user-content-fn-30) |
| Trace | ✘ | ✘ | ✘ |
| Waiting Room | ⚫️ | ✅ | ✅ |
| Web Analytics / Real User Monitoring (RUM) | ⚫️ | ⚫️ | ✘ [8](#user-content-fn-43) |
| Zaraz | ✅ | ✅ | ✅ |
***
## Application Security
| Product | Geo Key Manager | Regional Services | Customer Metadata Boundary |
| - | - | - | - |
| Advanced Certificate Manager | ⚫️ | ⚫️ | ⚫️ |
| Advanced DDoS Protection | ✅ | ✅ | 🚧 [9](#user-content-fn-3) |
| API Shield | ✅ | ✅ | 🚧 [10](#user-content-fn-4) |
| Bot Management | ✅ | ✅ | ✅ |
| DNS Firewall | ⚫️ | ⚫️ | 🚧 [11](#user-content-fn-22) |
| Page Shield | ✅ | ✅ | ✅ |
| Rate Limiting | ✅ | ✅ | ✅ [12](#user-content-fn-37) |
| SSL | ✅ | ✅ | ✅ |
| Cloudflare for SaaS | ✘ | ✅ | ✅ |
| Turnstile | ⚫️ | ✘ | ✅ [13](#user-content-fn-38) |
| WAF/L7 Firewall | ✅ | ✅ | ✅ |
| DMARC Management | ⚫️ | ⚫️ | ✅ |
***
## Developer Platform
| Product | Geo Key Manager | Regional Services | Customer Metadata Boundary |
| - | - | - | - |
| Cloudflare Images | ⚫️ | ✅ [14](#user-content-fn-36) | 🚧 [15](#user-content-fn-35) |
| AI Gateway | ✘ | ✘ | 🚧 [16](#user-content-fn-39) |
| AI Search | ✘ [17](#user-content-fn-46) | ✘ [18](#user-content-fn-47) | 🚧 [19](#user-content-fn-48) |
| Cloudflare Pages | ✅ [20](#user-content-fn-11) | ✅ [20](#user-content-fn-11) | 🚧 [5](#user-content-fn-1) |
| Cloudflare D1 | ⚫️ | ⚫️ | 🚧 [21](#user-content-fn-40) |
| Durable Objects | ⚫️ | ✅ [22](#user-content-fn-7) | 🚧 [5](#user-content-fn-1) |
| Email Routing | ⚫️ | ⚫️ | ✅ |
| Firewall for AI | ✘ | ✘ | ✘ |
| Remote MCP Server | ✅ [23](#user-content-fn-44) | ✅ [24](#user-content-fn-45) | 🚧 [5](#user-content-fn-1) |
| R2 | ✅ [25](#user-content-fn-27) | ✅ [26](#user-content-fn-8) | ✅ [27](#user-content-fn-28) |
| Smart Placement | ⚫️ | ✘ | ✘ |
| Stream | ⚫️ | ✘ | 🚧 [5](#user-content-fn-1) |
| Vectorize | ⚫️ | ✘ | ✘ |
| Workers (deployed on a Zone) | ✅ | ✅ | 🚧 [28](#user-content-fn-41) |
| Workers AI | ⚫️ | ✘ | ✅ |
| Workers KV | ⚫️ | ✘ | ✅ [29](#user-content-fn-34) |
| Workers.dev | ✘ | ✘ | ✘ |
| Workers Analytics Engine (WAE) | ⚫️ | ⚫️ | 🚧 [5](#user-content-fn-1) |
***
## Network Services
| Product | Geo Key Manager | Regional Services | Customer Metadata Boundary |
| - | - | - | - |
| Argo Smart Routing | ✅ | ✘ [30](#user-content-fn-9) | ✘ [31](#user-content-fn-10) |
| Static IP/BYOIP | ⚫️ | ✅ [32](#user-content-fn-26) | ⚫️ |
| Magic Firewall | ⚫️ | ⚫️ | ✅ |
| Magic Network Monitoring | ⚫️ | ⚫️ | 🚧 [5](#user-content-fn-1) |
| Magic Transit | ⚫️ | ⚫️ | ✅ |
| Magic WAN | ⚫️ | ⚫️ | ✅ |
| Spectrum | ✅ | ✅ [33](#user-content-fn-42) | ✅ |
***
## Platform
| Product | Geo Key Manager | Regional Services | Customer Metadata Boundary |
| - | - | - | - |
| Logpull | ⚫️ | ⚫️ | 🚧 [34](#user-content-fn-12) |
| Logpush | ⚫️ | ✅ | 🚧 [35](#user-content-fn-13) |
| Log Explorer | ⚫️ | ⚫️ | ✘ [36](#user-content-fn-23) |
***
## Zero Trust
| Product | Geo Key Manager | Regional Services | Customer Metadata Boundary |
| - | - | - | - |
| Access | 🚧 [37](#user-content-fn-14) | 🚧 [38](#user-content-fn-15) | ✅ [39](#user-content-fn-16) |
| Browser Isolation | ⚫️ | 🚧 [40](#user-content-fn-17) | ✅ |
| CASB | ⚫️ | ⚫️ | ✘ |
| Cloudflare Tunnel | ⚫️ | 🚧 [41](#user-content-fn-18) | ⚫️ |
| DLP | ⚫️ [42](#user-content-fn-19) | ⚫️ [42](#user-content-fn-19) | 🚧 [43](#user-content-fn-31) |
| Gateway | 🚧 [44](#user-content-fn-20) | 🚧 [45](#user-content-fn-21) | 🚧 [11](#user-content-fn-22) |
| WARP | ⚫️ | ⚫️ | 🚧 [5](#user-content-fn-1) |
## Footnotes
1. You cannot yet specify region location for object storage itself. [↩](#user-content-fnref-29)
2. [Outgoing zone transfers](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-primary/) will carry Earth region proxy IPs, thus making regional service dysfunctional when non-Cloudflare nameservers respond to the DNS queries. [↩](#user-content-fnref-33)
3. Dashboard Analytics are empty when using CMB outside the US region. Use Logpush instead. [↩](#user-content-fnref-32)
4. Only when using a Custom Domain set to a region, either through Workers or [Transform Rules](https://developers.cloudflare.com/images/transform-images/serve-images-custom-paths/) within the same zone. [↩](#user-content-fnref-6)
5. Logs / Analytics not available outside US region when using Customer Metadata Boundary. [↩](#user-content-fnref-1) [↩2](#user-content-fnref-1-2) [↩3](#user-content-fnref-1-3) [↩4](#user-content-fnref-1-4) [↩5](#user-content-fnref-1-5) [↩6](#user-content-fnref-1-6) [↩7](#user-content-fnref-1-7) [↩8](#user-content-fnref-1-8) [↩9](#user-content-fnref-1-9)
6. Regular and Custom Tiered Cache works; Smart Tiered Caching not available with Regional Services. [↩](#user-content-fnref-2)
7. Regular/Generic and Custom Tiered Cache works; Smart Tiered Caching does not work with Customer Metadata Boundary (CMB).\
With CMB set to EU, the Zone Dashboard **Caching** > **Tiered Cache** > **Smart Tiered Caching** option will not populate the Dashboard Analytics. [↩](#user-content-fnref-30)
8. Web Analytics collects the [minimum amount of information](https://developers.cloudflare.com/web-analytics/data-metrics/data-origin-and-collection/). Alternatively, you can [exclude EU Visitors from RUM](https://developers.cloudflare.com/speed/observatory/rum-beacon/#rum-excluding-eeaeu). [↩](#user-content-fnref-43)
9. [Adaptive DDoS Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/adaptive-protection/) is only supported for CMB = US. All other features are available to all CMB regions. [↩](#user-content-fnref-3)
10. API Discovery, Volumetric Abuse Detection and [Sequence Analytics and Mitigation](https://developers.cloudflare.com/api-shield/security/sequence-analytics/) will not work with CMB = EU. All other features are available to all CMB regions. [↩](#user-content-fnref-4)
11. Dashboard Analytics and Logs are empty when using CMB outside the US region. Use Logpush instead. [↩](#user-content-fnref-22) [↩2](#user-content-fnref-22-2)
12. Legacy Zone Analytics & Logs section not available outside US region when using CMB. Use [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) instead. [↩](#user-content-fnref-37)
13. [Turnstile Analytics](https://developers.cloudflare.com/turnstile/turnstile-analytics/) are available. However, there are no regionalization guarantees for the Siteverify API yet. [↩](#user-content-fnref-38)
14. Only when using a [Custom Domain](https://developers.cloudflare.com/images/manage-images/serve-images/serve-from-custom-domains/) set to a region. [↩](#user-content-fnref-36)
15. Logs / Analytics not supported for CMB = EU. Jurisdictional Restrictions ([storage](https://developers.cloudflare.com/images/upload-images/)) options are not supported today. All other features are available to all CMB regions. Note that beta or future features may not be in scope and could be subject to change. [↩](#user-content-fnref-35)
16. Jurisdictional Restrictions (storage) options for [Logs](https://developers.cloudflare.com/ai-gateway/observability/logging/) are not supported today. All other features are available to all CMB regions. [↩](#user-content-fnref-39)
17. Only R2 Custom Domains and Custom Certificate are supported. [↩](#user-content-fnref-46)
18. Only R2 Custom Domains are supported. [↩](#user-content-fnref-47)
19. The following are exceptions and are supported: AI Gateway Analytics (GraphQL Analytics datasets) and Logs (Logpush), R2 Dashboard Metrics & Analytics, Workers AI GraphQL Analytics datasets like aiInferenceAdaptive. [↩](#user-content-fnref-48)
20. Only when using [Custom Domain](https://developers.cloudflare.com/pages/configuration/custom-domains/) set to a region. [↩](#user-content-fnref-11) [↩2](#user-content-fnref-11-2)
21. Jurisdictional Restrictions ([data location](https://developers.cloudflare.com/d1/configuration/data-location/) / storage) options are not supported today. All other features are available to all CMB regions. Note that beta or future features may not be in scope and could be subject to change. [↩](#user-content-fnref-40)
22. [Jurisdiction restrictions for Durable Objects](https://developers.cloudflare.com/durable-objects/reference/data-location/#restrict-durable-objects-to-a-jurisdiction). [↩](#user-content-fnref-7)
23. Only when using Workers Routes & Domains and Custom Certificate. [↩](#user-content-fnref-44)
24. Only when using Workers Routes & Domains. [↩](#user-content-fnref-45)
25. Only when using a Custom Domain and a [Custom Certificate](https://developers.cloudflare.com/r2/reference/data-security/#encryption-in-transit) or [Keyless SSL](https://developers.cloudflare.com/ssl/keyless-ssl/). [↩](#user-content-fnref-27)
26. Only when using a [Custom Domain](https://developers.cloudflare.com/r2/buckets/public-buckets/#connect-a-bucket-to-a-custom-domain) set to a region and using [jurisdictions with the S3 API](https://developers.cloudflare.com/r2/reference/data-location/#using-jurisdictions-with-the-s3-api). [↩](#user-content-fnref-8)
27. R2 Dashboard [Metrics and Analytics](https://developers.cloudflare.com/r2/platform/metrics-analytics/) are populated. [Jurisdictional Restrictions](https://developers.cloudflare.com/r2/reference/data-location/#jurisdictional-restrictions) guarantee objects in a bucket are stored within a specific jurisdiction. [↩](#user-content-fnref-28)
28. Logs / Analytics not available outside US region when using Customer Metadata Boundary. Use Logpush instead. [↩](#user-content-fnref-41)
29. Jurisdictional Restrictions (storage) for Workers KV pairs is not supported today. [↩](#user-content-fnref-34)
30. Argo cannot be used with Regional Services. [↩](#user-content-fnref-9)
31. Argo cannot be used with Customer Metadata Boundary. [↩](#user-content-fnref-10)
32. Static IP/BYOIP can be used with the legacy Spectrum setup. [↩](#user-content-fnref-26)
33. Only applies to HTTP/S Spectrum applications. [↩](#user-content-fnref-42)
34. Logpull available when using CMB = US only. Logpull is a legacy feature, consider using [Logpush](https://developers.cloudflare.com/data-localization/metadata-boundary/logpush-datasets/) or [Log Explorer](https://developers.cloudflare.com/log-explorer/) instead. [↩](#user-content-fnref-12)
35. Logpush available with Customer Metadata Boundary for [these datasets](https://developers.cloudflare.com/data-localization/metadata-boundary/logpush-datasets/). Contact your account team if you need another dataset. [↩](#user-content-fnref-13)
36. Currently, customers do not have the ability to choose the location of the Cloudflare-managed R2 bucket for Log Explorer. [↩](#user-content-fnref-23)
37. Access App SSL keys can use Geo Key Manager. [Access JWT](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/http-apps/authorization-cookie/validating-json/) is not yet localized. [↩](#user-content-fnref-14)
38. Can be localized to US FedRAMP Moderate Domestic region only. [↩](#user-content-fnref-15)
39. Customer Metadata Boundary can be used to limit data transfer outside region, but Access User Logs will not be available outside US region. EU customers must use Logpush to retain logs. [↩](#user-content-fnref-16)
40. Currently may only be used with US FedRAMP region. [↩](#user-content-fnref-17)
41. When Cloudflare Tunnel connects to Cloudflare, the connectivity options available are the Global Region (default) and [US FedRAMP Moderate Domestic region](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/configure-tunnels/cloudflared-parameters/run-parameters/#region). For incoming requests to the Cloudflare Edge, Regional Services only applies when using [published applications](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/routing-to-tunnel/). In this case, the region associated with the DNS record will apply. [↩](#user-content-fnref-18)
42. Uses Gateway HTTP and CASB. [↩](#user-content-fnref-19) [↩2](#user-content-fnref-19-2)
43. DLP is part of Gateway HTTP, however, [DLP detection entries](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/) are not available outside US region when using Customer Metadata Boundary. [↩](#user-content-fnref-31)
44. You can [bring your own certificate](https://blog.cloudflare.com/bring-your-certificates-cloudflare-gateway/) to Gateway but these cannot yet be restricted to a specific region. [↩](#user-content-fnref-20)
45. Gateway HTTP supports Regional Services. Gateway DNS does not yet support regionalization.\
ICMP proxy and WARP-to-WARP proxy are not available to Regional Services users. [File Sandboxing](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/file-sandboxing/) (add-on) is incompatible with DLS. [↩](#user-content-fnref-21)
---
title: FAQs · Cloudflare Data Localization Suite docs
description: No, they are not. DLP stands for Data Loss Prevention, and it is
part of Cloudflare’s Zero Trust offering (requiring Gateway). It allows
customers to scan web traffic and SaaS apps for sensitive data like secret
keys, financial information (credit card numbers), and other keywords.
lastUpdated: 2025-10-22T21:11:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/faq/
md: https://developers.cloudflare.com/data-localization/faq/index.md
---
## Are DLP and DLS the same?
No, they are not. DLP stands for [Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/), and it is part of Cloudflare’s Zero Trust offering (requiring Gateway). It allows customers to scan web traffic and SaaS apps for sensitive data like secret keys, financial information (credit card numbers), and other keywords.
[Data Localization Suite](https://developers.cloudflare.com/data-localization/) (DLS) is a suite of features that can provide localization and data residency features.
## Are Cloudflare’s services GDPR compliant?
Yes, even without DLS, Cloudflare services are designed to satisfy the GDPR’s requirements. Cloudflare services are also verified compliant with the EU Cloud CoC, Verification-ID: 2023LVL02SCOPE4316. For further information, visit EU Cloud CoC [public register](https://eucoc.cloud/en/public-register).
## How can I use DLS?
Once you have purchased DLS, the post-sales team will entitle DLS for you, and you will be able to configure all features by yourself via dashboard or API. You can find more specific information under the [Configuration guides](https://developers.cloudflare.com/data-localization/how-to/) section.
## Does Regional Services work with HTTP/3 / QUIC?
Not yet.
## Are there other options if I prefer not to have Cloudflare handle TLS termination (decryption)?
Yes, you have these options available:
* [Spectrum TCP/UDP Apps](https://developers.cloudflare.com/spectrum/) (without TLS Termination)
* [Magic Transit](https://developers.cloudflare.com/magic-transit/)
* [Privacy Gateway](https://developers.cloudflare.com/privacy-gateway/)
These options only offer L3/L4 DDoS protection and using them imply that no application / L7 security or performance services can be applied.
## I have configured [Customer Metadata Boundary](https://developers.cloudflare.com/data-localization/metadata-boundary/) for EU region, I'm accessing the Cloudflare Dashboard from Europe, why am I getting an error `Data not available due to your account's Customer Metadata Boundary configuration`?
Based on Internet conditions that vary over time, users may be dynamically steered to a data center that is physically further away. This can be based on a variety of factors, including latency and network congestion. [Out of region access](https://developers.cloudflare.com/data-localization/metadata-boundary/out-of-region-access/) allows requests arriving in the United States to pull Customer Logs from the European Union and vice-versa. The analytics are still exclusively stored in the CMB configured region.
---
title: Geo Key Manager · Cloudflare Data Localization Suite docs
description: Geo Key Manager offers enhanced control over the storage location
of private SSL/TLS keys, ensuring compliance with regional data regulations
and security requirements.
lastUpdated: 2025-01-07T10:59:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/geo-key-manager/
md: https://developers.cloudflare.com/data-localization/geo-key-manager/index.md
---
Geo Key Manager offers enhanced control over the storage location of private SSL/TLS keys, ensuring compliance with regional data regulations and security requirements.
## Customize key storage
By default, private keys will be encrypted and securely distributed to each data center, where they can be utilized for local SSL/TLS termination. Geo Key Manager allows you to choose where you want to store your private keys.
Geo Key Manager was restricted to the US, EU, and high-security data centers, but with the new version of Geo Key Manager, available in [Closed Beta](https://blog.cloudflare.com/configurable-and-scalable-geo-key-manager-closed-beta/), you can now create `allowlists` and `blocklists` of countries in which your private keys will be stored. That means that you will be able define specific geographic locations where to store keys, for instance you can store your private keys exclusively in Australia or limit private keys storage to the EU and the UK.
## Cloudflare data center flow example
The following diagram is a high-level example of the flow of the Cloudflare data centers without private TLS key. In this process, data centers have to request and create temporary Session Keys to perform TLS termination by reaching out to Cloudflare data centers which hold the private TLS keys:
```mermaid
sequenceDiagram
participant User as End user
participant CloudflarePoP as Closest data center without TLS Key
participant CloudflarePoPwTLS as Data center with TLS Key
User->>CloudflarePoP: Initial request
Note right of CloudflarePoP: Closest data center cannot decrypt
CloudflarePoP-->>CloudflarePoPwTLS: Requests TLS Signature
CloudflarePoPwTLS-->>CloudflarePoP: Sends TLS Signature in order to establish Session Key
Note right of CloudflarePoP: Decrypts and performs business logic (for example, WAF, Configuration Rules, Load Balancing)
CloudflarePoP-->>User: Subsequent requests use the Session Key
User-->>CloudflarePoP: Subsequent requests use the Session Key
```
For detailed information on setup and supported options, refer to [Geo Key Manager documentation](https://developers.cloudflare.com/ssl/edge-certificates/geokey-manager/).
---
title: Configuration guides · Cloudflare Data Localization Suite docs
description: Learn how to use Cloudflare products with the Data Localization Suite.
lastUpdated: 2025-01-28T15:34:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/how-to/
md: https://developers.cloudflare.com/data-localization/how-to/index.md
---
Learn how to use Cloudflare products with the Data Localization Suite.
* [Zero Trust](https://developers.cloudflare.com/data-localization/how-to/zero-trust/)
* [Pages](https://developers.cloudflare.com/data-localization/how-to/pages/)
* [Cache](https://developers.cloudflare.com/data-localization/how-to/cache/)
* [Load Balancing](https://developers.cloudflare.com/data-localization/how-to/load-balancing/)
* [Cloudflare for SaaS](https://developers.cloudflare.com/data-localization/how-to/cloudflare-for-saas/)
* [R2 Object Storage](https://developers.cloudflare.com/data-localization/how-to/r2/)
* [Durable Objects](https://developers.cloudflare.com/data-localization/how-to/durable-objects/)
* [Workers](https://developers.cloudflare.com/data-localization/how-to/workers/)
## Verify Regional Services behavior
In order to verify that Regional Services is working, customers can confirm the behavior by executing one of the following `curl` commands on a regionalized hostname:
```bash
curl -X GET -I https:/// 2>&1 | grep cf-ray
```
```bash
curl -s https:///cdn-cgi/trace | grep "colo="
```
The first command will return a three-letter IATA code in the [Cf-Ray](https://developers.cloudflare.com/fundamentals/reference/http-headers/#cf-ray) header, indicating the Cloudflare data center location of processing and/or TLS termination. The second command will directly return the three-letter IATA code.
For example, when a hostname is configured to use the region European Union (EU), the three-letter IATA code will always return a data center inside of the EU.
---
title: Limitations · Cloudflare Data Localization Suite docs
description: There are some caveats and limitations when deploying Data
Localization Suite features.
lastUpdated: 2025-07-25T16:42:51.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/limitations/
md: https://developers.cloudflare.com/data-localization/limitations/index.md
---
There are some caveats and limitations when deploying Data Localization Suite features.
Cloudflare is working hard to improve this offering and fill the gaps. If you have a specific feature request, please contact your [Account Team](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
## Key Management
When using Geo Key Manager or Keyless SSL, some caveats may apply.
The remote procedure call from the server to the key server can add latency to the handshake, slowing down connection establishment. The additional latency cost corresponds to the round-trip time from the server to the key server, which can be as much as a second if the key server is on the other side of the world. Luckily, this latency cost only applies to the first time you connect to a server. Once the handshake is complete, the key server is not involved. Furthermore, if you reconnect to a site you do not have to pay the latency cost either because resuming a connection with TLS Session Resumption does not require the private key. Hence, latency is only added for the initial connection.
Learn more about how it works in our [blog post](https://blog.cloudflare.com/geo-key-manager-how-it-works/).
## Regional Services
When using Regional Services, some caveats and limitations may apply.
For product-specific caveats, refer to [Cloudflare product compatibility](https://developers.cloudflare.com/data-localization/compatibility/) page.
The following features and protocols are not supported by Regional Services and might not work on regionalized hostnames:
* [ICMP](https://www.cloudflare.com/learning/ddos/glossary/internet-control-message-protocol-icmp/)
* [Encrypted Client Hello (ECH)](https://developers.cloudflare.com/ssl/edge-certificates/ech/)
* [Orange-to-Orange (O2O)](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/saas-customers/how-it-works/)
* [Onion Routing (Tor)](https://developers.cloudflare.com/network/onion-routing/)
Since Regional Services leverages Spectrum in the background, [Spectrum limitations](https://developers.cloudflare.com/spectrum/reference/limitations/) apply.
Regional Services does not apply to [Subrequests](https://developers.cloudflare.com/workers/platform/limits/#subrequests). Regional Services operates on your hostname's IPs. We recommend using [DNSSEC](https://developers.cloudflare.com/learning-paths/application-security/default-traffic-security/dnssec/) and/or [DNS over HTTPS](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/) to ensure that DNS responses are secure and correct.
## Customer Metadata Boundary
There are certain limitations and caveats when using Customer Metadata Boundary.
Specifically most of the Zone Analytics & Logs UI Tabs will be showing up as empty, when configuring Customer Metadata Boundary to EU only. It is recommended to use the UI [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) instead, or the [HTTP request](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) logs via [Logpush](https://developers.cloudflare.com/logs/logpush/).
To configure Customer Metadata Boundary to EU only, you must disable Log Retention for all zones within your account. Log Retention is a legacy feature of [Logpull](https://developers.cloudflare.com/logs/logpull/).
For product-specific caveats, refer to [Cloudflare product compatibility](https://developers.cloudflare.com/data-localization/compatibility/) page.
### Data unavailability
If you encounter a message on the dashboard indicating that your data is unavailable due to your account's Metadata Boundary configuration, this is because you are trying to access data that is not stored in your region (that is, you are in the US and trying to access data that is only stored in the EU, or vice versa). If you receive this error message while being in the region where your data is stored, there are two potential reasons why you might get this message:
* Your account has Customer Metadata Boundary (CMB) enabled, and your request is being directed to an incorrect region. For example, if you are in the EU and CMB is configured to store your data in the US.
* If you are trying to access your data from the correct region, such as being in the EU with CMB configured to save your data in the EU, the issue may be caused by network congestion. Typically, this problem resolves within a few minutes.
### Dashboard UI Analytics
In some cases, when using Customer Metadata Boundary set to the EU, some Dashboard UI Analytics might show up empty.
---
title: Customer Metadata Boundary · Cloudflare Data Localization Suite docs
description: As part of the Data Localization Suite, the Customer Metadata
Boundary (CMB) ensures that Customer Logs — any traffic metadata that can
identify a customer’s end user (that is, contains the customer's Account ID) —
will stay in the EU (European Union) or in the US (United States), depending
on the region the customer selects. For example, if a customer selects the EU
Customer Metadata Boundary, metadata will only be sent to our core data center
located in the European Union.
lastUpdated: 2025-07-16T14:37:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/metadata-boundary/
md: https://developers.cloudflare.com/data-localization/metadata-boundary/index.md
---
As part of the Data Localization Suite, the Customer Metadata Boundary (CMB) ensures that Customer Logs — any traffic metadata that can identify a customer’s end user (that is, contains the customer's [Account ID](https://developers.cloudflare.com/fundamentals/account/find-account-and-zone-ids/)) — will stay in the `EU` (European Union) or in the `US` (United States), depending on the region the customer selects. For example, if a customer selects the `EU` Customer Metadata Boundary, metadata will **only** be sent to our core data center located in the European Union.
An exception is made if "Allow out-of-region access" is enabled. When enabled, Customer Logs will still be stored in the configured regions but will be accessible to authorized end users, regardless of physical location. Refer to [Out of region access](https://developers.cloudflare.com/data-localization/metadata-boundary/out-of-region-access/) for more details.
## Customer traffic metadata flow
The following diagram is a high-level example of the flow of how metadata about a customer's traffic is generated on a Cloudflare data center. Logs are exclusively sent to the EU core data center for Cloudflare customers and their authorized users to access and view.
```mermaid
sequenceDiagram
participant UserEU as End user
participant CloudflarePoP as Closest data center
participant EUCoreDC as Core data center in EU
participant CloudflareSuperAdmin as Admin
UserEU->>CloudflarePoP: Connects
Note right of CloudflarePoP: Customer Logs generated
(for example, HTTP requests and Firewall events)
CloudflarePoP-->>EUCoreDC: Forwards encrypted Customer Logs
Note right of EUCoreDC: Authorized users can view Logs & Analytics
on the UI or via API
CloudflareSuperAdmin->>EUCoreDC: Authenticated access
EUCoreDC->>CloudflareSuperAdmin: Logs & Analytics
CloudflarePoP->>UserEU: Response
```
## Log management
Additionally, customers have the option to configure [Logpush](https://developers.cloudflare.com/logs/logpush/) to push their Customer Logs to various storage services, SIEMs, and log management providers.
## Product specific-behavior
For detailed information about product-specific behavior regarding Metadata Boundary, refer to the [Cloudflare product compatibility](https://developers.cloudflare.com/data-localization/compatibility/) page.
---
title: Region support · Cloudflare Data Localization Suite docs
description: "Support by product and region is summarized in the following table:"
lastUpdated: 2025-12-11T16:55:02.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/region-support/
md: https://developers.cloudflare.com/data-localization/region-support/index.md
---
Support by product and region is summarized in the following table:
| Region | Geo Key Manager | Regional Services | Customer Metadata Boundary |
| - | - | - | - |
| Australia | ✅ [1](#user-content-fn-1) | ✅ | ✘ |
| Austria | ✘ | ✅ | Can use EU metadata boundary. |
| Brazil | ✘ | ✅ | ✘ |
| Canada | ✅ [1](#user-content-fn-1) | ✅ | ✘ |
| Cloudflare Green Energy | ✘ | ✅ | ✘ |
| European Union | ✅ | ✅ | ✅ |
| Exclusive of Hong Kong and Macau | ✘ | ✅ | ✘ |
| Exclusive of Russia and Belarus | ✘ | ✅ | ✘ |
| FedRAMP Moderate Compliant (Domestic) | ✅ [1](#user-content-fn-1) | ✅ | ✅ |
| FedRAMP Moderate Compliant (International) | ✘ | ✅ | ✅ |
| France | ✘ | ✅ | Can use EU metadata boundary. |
| Germany | ✅ [1](#user-content-fn-1) | ✅ | Can use EU metadata boundary. |
| Hong Kong | ✘ | ✅ | ✘ |
| India | ✅ [1](#user-content-fn-1) | ✅ | ✘ |
| [IRAP](https://www.cloudflare.com/cloudflare-for-government/australia/irap/) Protected | ✘ | ✅ | ✘ |
| ISO 27001 Certified European Union | ✘ | ✅ | Can use EU metadata boundary. |
| Italy | ✘ | ✅ | Can use EU metadata boundary. |
| Japan | ✅ [1](#user-content-fn-1) | ✅ | ✘ |
| NATO | ✘ | ✅ | ✘ |
| Netherlands | ✘ | ✅ | Can use EU metadata boundary. |
| Russia | ✘ | ✅ | ✘ |
| Saudi Arabia | ✘ | ✅ | ✘ |
| Singapore | ✅ [1](#user-content-fn-1) | ✅ | ✘ |
| South Africa | ✘ | ✅ | ✘ |
| South Korea | ✅ [1](#user-content-fn-1) | ✅ | ✘ |
| Spain | ✘ | ✅ | Can use EU metadata boundary. |
| Switzerland | ✘ | ✅ | ✘ |
| Taiwan | ✘ | ✅ | ✘ |
| Turkey | ✘ | ✅ | ✘ |
| United Arab Emirates | ✘ | ✅ | ✘ |
| United Kingdom | ✅ [1](#user-content-fn-1) | ✅ | Can use EU metadata boundary. |
| United States of America | ✅ | ✅ | ✅ |
| US State of California | ✘ | ✅ | ✘ |
| US State of Florida | ✘ | ✅ | ✘ |
| US State of Texas | ✘ | ✅ | ✘ |
Refer to the table below for the complete list of available regions and their definitions.
| Region | Definition |
| - | - |
| Australia | Cloudflare will only use data centers that are physically located within Australia to decrypt and service HTTPS traffic. |
| Austria | Cloudflare will only use data centers that are physically located within Austria to decrypt and service HTTPS traffic. |
| Brazil | Cloudflare will only use data centers that are physically located within Brazil to decrypt and service HTTPS traffic. |
| Canada | Cloudflare will only use data centers that are physically located within Canada to decrypt and service HTTPS traffic. |
| Cloudflare Green Energy | Cloudflare will only use data centers that are committed to powering their operations with [renewable energy](https://www.cloudflare.com/impact/). |
| European Union | Cloudflare will only use data centers that are physically located within the European Union. For more details, refer to the [list of European Union countries](https://european-union.europa.eu/principles-countries-history/country-profiles_en). |
| Exclusive of Hong Kong and Macau | Cloudflare will only use data centers that are NOT physically located within Hong Kong and Macau to decrypt and service HTTPS traffic. |
| Exclusive of Russia and Belarus | Cloudflare will only use data centers that are NOT physically located within Russia and Belarus to decrypt and service HTTPS traffic. |
| FedRAMP Moderate Compliant (Domestic) | Cloudflare will only use data centers that are FedRAMP Moderate certified and located within the United States. |
| FedRAMP Moderate Compliant (International) | Cloudflare will only use data centers that are FedRAMP Moderate certified, including certified locations outside the United States. |
| France | Cloudflare will only use data centers that are physically located within Metropolitan France (the European territory of France) to decrypt and service HTTPS traffic. |
| Germany | Cloudflare will only use data centers that are physically located within Germany to decrypt and service HTTPS traffic. |
| Hong Kong | Cloudflare will only use data centers that are physically located within Hong Kong to decrypt and service HTTPS traffic. |
| India | Cloudflare will only use data centers that are physically located within India to decrypt and service HTTPS traffic. |
| ISO 27001 Certified European Union | Cloudflare will only use data centers that are physically located within the [European Union](https://european-union.europa.eu/principles-countries-history/country-profiles_en) and that adhere to the ISO 27001 certification. |
| IRAP Protected | Cloudflare will only use data centers that are IRAP protected, including certified locations outside Australia. |
| Italy | Cloudflare will only use data centers that are physically located within Italy to decrypt and service HTTPS traffic. |
| Japan | Cloudflare will only use data centers that are physically located within Japan to decrypt and service HTTPS traffic. |
| NATO | Cloudflare will only use data centers that are physically located within North Atlantic Treaty Organization (NATO) countries. For more details, refer to the [list of NATO countries](https://www.nato.int/nato-welcome/). |
| Netherlands | Cloudflare will only use data centers that are physically located within the Netherlands to decrypt and service HTTPS traffic. |
| Russia | Cloudflare will only use data centers that are physically located within Russia to decrypt and service HTTPS traffic. |
| Saudi Arabia | Cloudflare will only use data centers that are physically located within Saudi Arabia to decrypt and service HTTPS traffic. |
| Singapore | Cloudflare will only use data centers that are physically located within Singapore to decrypt and service HTTPS traffic. |
| South Africa | Cloudflare will only use data centers that are physically located within South Africa to decrypt and service HTTPS traffic. |
| South Korea | Cloudflare will only use data centers that are physically located within South Korea to decrypt and service HTTPS traffic. |
| Spain | Cloudflare will only use data centers that are physically located within Spain to decrypt and service HTTPS traffic. |
| Switzerland | Cloudflare will only use data centers that are physically located within Switzerland to decrypt and service HTTPS traffic. |
| Taiwan | Cloudflare will only use data centers that are physically located within Taiwan to decrypt and service HTTPS traffic. |
| Turkey | Cloudflare will only use data centers that are physically located within Turkey to decrypt and service HTTPS traffic. |
| United Arab Emirates | Cloudflare will only use data centers that are physically located within United Arab Emirates to decrypt and service HTTPS traffic. |
| United Kingdom | Cloudflare will only use data centers that are physically located within the United Kingdom to decrypt and service HTTPS traffic. |
| United States of America | Cloudflare will only use data centers that are physically located within the United States of America to decrypt and service HTTPS traffic. |
| US State of California | Cloudflare will only use data centers that are physically located within the US State of California to decrypt and service HTTPS traffic. |
| US State of Florida | Cloudflare will only use data centers that are physically located within the US State of Florida to decrypt and service HTTPS traffic. |
| US State of Texas | Cloudflare will only use data centers that are physically located within the US State of Texas to decrypt and service HTTPS traffic. |
## Footnotes
1. Only supported in [Geo Key Manager v2](https://developers.cloudflare.com/ssl/edge-certificates/geokey-manager/). [↩](#user-content-fnref-1) [↩2](#user-content-fnref-1-2) [↩3](#user-content-fnref-1-3) [↩4](#user-content-fnref-1-4) [↩5](#user-content-fnref-1-5) [↩6](#user-content-fnref-1-6) [↩7](#user-content-fnref-1-7) [↩8](#user-content-fnref-1-8) [↩9](#user-content-fnref-1-9)
---
title: Regional Services · Cloudflare Data Localization Suite docs
description: Regional Services gives you the ability to accommodate regional
restrictions by choosing which subset of data centers decrypt and service
HTTPS traffic.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/data-localization/regional-services/
md: https://developers.cloudflare.com/data-localization/regional-services/index.md
---
Regional Services gives you the ability to accommodate regional restrictions by choosing which subset of data centers decrypt and service HTTPS traffic.
Regional Services proceeds and processes traffic within certain regions for customers who have to meet regional compliance or have preferences for maintaining regional control over their data. Examples of use cases could be a customer that needs to accommodate regional restrictions like [GDPR](https://www.cloudflare.com/trust-hub/gdpr/) (General Data Protection Regulation), or customers that are bound by agreement with their own customers that include geographic restrictions on data flows or data processing.
With Regional Services, TLS is only terminated inside the configured region. For example, if a hostname is configured to regionalize to the European Union (EU), any HTTPS request from the United States (US) will route to the EU.
## Global traffic management
Regional Services globally ingests traffic, implementing [L3/L4 DDoS mitigations](https://developers.cloudflare.com/ddos-protection/about/attack-coverage/). Meanwhile, security, performance, and reliability functions are serviced at only in-region Cloudflare locations.
Regional Services ensures that all edge application services operate within the selected region. This includes (the following list is not exhaustive):
* Storing and retrieving content from Cache.
* Blocking malicious HTTP payloads with the Web Application Firewall (WAF).
* Detecting and blocking suspicious activity with Bot Management.
* Running Cloudflare Workers scripts.
* Load Balancing traffic to the best origin servers (or other endpoints).
## Request flow example
The following diagram is a high-level example of the flow of a request coming from an end user located within the US connecting to a website using Cloudflare Regional Services set to EU.
```mermaid
sequenceDiagram
participant User in US as End user in US
participant CloudflarePoPNYC as Closest data center
in US
participant CloudflarePoPDUB as Data center in EU
participant EUOriginServer as Origin Server
User in US->>CloudflarePoPNYC: TCP connection
Note right of User in US: TLS encryption
Note left of CloudflarePoPNYC: TCP connection
(no TLS unwrapping)
Note right of CloudflarePoPNYC: L3 DDoS protection
CloudflarePoPNYC-->>CloudflarePoPDUB: Forwards
encrypted request
Note right of CloudflarePoPDUB: TLS termination (decryption)
Note right of CloudflarePoPDUB: Applies security
and performance features
(for example, WAF, Configuration Rules,
Load Balancing)
Note right of CloudflarePoPDUB: TLS encryption
CloudflarePoPDUB-->>EUOriginServer: Requests content
EUOriginServer-->>CloudflarePoPDUB: Response content
Note right of CloudflarePoPDUB: TLS termination (decryption)
Note right of CloudflarePoPDUB: Caches eligible static content
(on encrypted disks)
Note right of CloudflarePoPDUB: TLS encryption
CloudflarePoPDUB->>User in US: Forwards response with content
```
## Additional information
For more details about the products that are compatible with Regional Services, refer to the [Cloudflare product compatibility](https://developers.cloudflare.com/data-localization/compatibility/) page. If you have purchased these products as part of your Enterprise subscription plan, Cloudflare will only terminate TLS connections for these products in the geographic region you have configured for Regional Services.
---
title: 404 - Page Not Found · Cloudflare DDoS Protection docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/404/
md: https://developers.cloudflare.com/ddos-protection/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About Cloudflare DDoS protection · Cloudflare DDoS Protection docs
description: Cloudflare provides unmetered and unlimited distributed
denial-of-service (DDoS) protection at layers 3, 4, and 7 to all customers on
all plans and services.
lastUpdated: 2025-08-19T15:06:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/about/
md: https://developers.cloudflare.com/ddos-protection/about/index.md
---
Cloudflare provides unmetered and unlimited [distributed denial-of-service (DDoS)](https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/) protection at layers 3, 4, and 7 to all customers on all plans and services.
The protection is enabled by Cloudflare's [Autonomous DDoS Protection Edge](https://developers.cloudflare.com/ddos-protection/about/components/#autonomous-edge), which automatically detects and mitigates DDoS attacks.
The Autonomous Edge includes multiple dynamic mitigation rules exposed as [managed rulesets](https://developers.cloudflare.com/ddos-protection/managed-rulesets/), which provide comprehensive protection against a variety of DDoS attacks across layers 3/4 and layer 7 of the OSI model.
[Adaptive DDoS Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/adaptive-protection/) also learns your unique traffic patterns and adapts to them to provide better protection against sophisticated DDoS attacks on layer 7 and layers 3/4. Your Internet properties can be secured from sophisticated TCP and DNS DDoS attacks using [Advanced DDoS Protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/) that leverages stateful inspection and traffic profiling.
---
title: Advanced DDoS systems · Cloudflare DDoS Protection docs
description: "Refer to the following pages for more information on Cloudflare's
Advanced DDoS systems:"
lastUpdated: 2025-06-03T17:37:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/
md: https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/index.md
---
Refer to the following pages for more information on Cloudflare's Advanced DDoS systems:
* [General settings](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/)
* [Concepts](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/concepts/)
* [How to](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/how-to/)
* [API configuration](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/api/)
---
title: Best practices · Cloudflare DDoS Protection docs
description: Learn about best practices for configuring Cloudflare's DDoS protection.
lastUpdated: 2024-08-27T14:57:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ddos-protection/best-practices/
md: https://developers.cloudflare.com/ddos-protection/best-practices/index.md
---
Refer to the following pages for more information on DDoS protection best practices:
* [Third-party services and DDoS protection](https://developers.cloudflare.com/ddos-protection/best-practices/third-party/)
* [Proactive DDoS defense](https://developers.cloudflare.com/ddos-protection/best-practices/proactive-defense/)
* [Prevent DDoS attacks](https://developers.cloudflare.com/learning-paths/prevent-ddos-attacks/concepts/)
---
title: DDoS Botnet Threat Feed for service providers · Cloudflare DDoS Protection docs
description: The Cloudflare DDoS Botnet Threat Feed is a threat intelligence
feed for service providers (SPs) such as hosting providers and Internet
service providers (ISPs) that provides information about their own IP
addresses that have participated in HTTP DDoS attacks as observed from
Cloudflare's global network. The feed aims to help service providers stop the
abuse and reduce DDoS attacks originating from within their networks.
lastUpdated: 2025-09-03T18:12:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/botnet-threat-feed/
md: https://developers.cloudflare.com/ddos-protection/botnet-threat-feed/index.md
---
The Cloudflare DDoS Botnet Threat Feed is a threat intelligence feed for service providers (SPs) such as hosting providers and Internet service providers (ISPs) that provides information about their own IP addresses that have participated in HTTP DDoS attacks as observed from Cloudflare's global network. The feed aims to help service providers stop the abuse and reduce DDoS attacks originating from within their networks.
Each offense is a mitigated HTTP request from the specific IP address. For example, if an IP has 3,000 offenses, it means that Cloudflare has mitigated 3,000 HTTP requests from that IP.
A service provider can only get information about IP addresses associated with their autonomous system numbers (ASNs). The affiliation of a service provider with their ASNs will be checked against [PeeringDB](https://www.peeringdb.com/), a reliable and globally recognized interconnection database.
To ensure the feed's accuracy, Cloudflare will only include IP addresses that have participated in multiple HTTP DDoS attacks and have triggered high-confidence rules.
## Context
A single DDoS attack consisting of thousands of bots can involve as little as one single IP per service provider. Service providers usually only see a small fraction of the attack traffic leaving their network, and it can be hard to correlate it to malicious activity, while trying to identify abusers.
In the case of HTTPS DDoS attacks, service providers only see encrypted payloads leaving their network without any possibility to decrypt or understand if it is malicious or legitimate traffic. However, Cloudflare can see an entire attack and all of its sources if the attack targets an Internet property that uses Cloudflare's services. This global view can help service providers stop the abusers.
For more details, refer to [How DDoS protection works](https://developers.cloudflare.com/ddos-protection/about/how-ddos-protection-works/).
## Availability
The Cloudflare DDoS Botnet Threat Feed is available for free to service providers. For more information, refer to the [Terms of Use](https://www.cloudflare.com/en-gb/service-specific-terms-application-services/#ddos-botnet-threat-feed).
***
## Before you begin
Make sure that:
* You have [created a Cloudflare account](https://developers.cloudflare.com/fundamentals/account/).
## Get started
### 1. Authenticate your ASN via PeeringDB
1. In the Cloudflare dashboard, go to your account settings page.
[Go to **Configurations**](https://dash.cloudflare.com/?to=/:account/configurations)
2. Select **DDoS Threat Feed ASNs**.
3. On the list of ASNs configured for your threat feed, select **Add ASN**.
4. You will be redirected to the PeeringDB authentication page, where you can log in and consent to share the affiliation data with us. You will be redirected back to the configuration page once it is successful.
Note
You can add multiple ASNs to your threat feed.
### 2. Obtain Cloudflare API token
You must [obtain a Cloudflare API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with at least the following account-level permission:
* *DDoS Botnet Feed* > *Read*
### 3. Call Botnet Threat Feed API
Invoke one of the Botnet Threat Feed API endpoints:
* [Get full report](#get-full-report)
* [Get day report](#get-day-report)
***
## Available API endpoints
Important notes
* The API URI path is planned to change from `.../botnet_feed/...` to `.../ddos_botnet_feed/...` in the future.
* Responses with no IP addresses in the results (empty state) will return an `HTTP 200` status code (success), with an empty list in the `result` property.
* When the response is a success but the result is `0` or `null`, this means that there are no detected offenses.
To invoke an API endpoint, append the operation endpoint to the Cloudflare API base URL:
```txt
https://api.cloudflare.com/client/v4
```
### Get full report
Retrieves all the data in the botnet tracking database for a given ASN (currently two weeks worth of data).
* HTTP verb: `GET`
* Operation endpoint: `/accounts/{account_id}/botnet_feed/asn/{asn}/full_report`
The provided `{asn}` must be affiliated with your account.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `DDoS Botnet Feed Write`
* `DDoS Botnet Feed Read`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/botnet_feed/asn/$ASN_ID/full_report" \
--request GET \
--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN"
```
```json
{
"result": [
{
"cidr": "127.0.0.1/32",
"date": "1970-01-01T00:00:00Z",
"offense_count": 10000
},
// ... other entries ...
],
"success": true,
"errors": [],
"messages": []
}
```
### Get day report
Retrieves all the data the botnet tracking database has for a given ASN on a given date. This operation currently allows dates greater than two weeks prior, but in this case it will return an empty dataset (the database currently stores two-weeks worth of data).
* HTTP verb: `GET`
* Operation endpoint: `/accounts/{account_id}/botnet_feed/asn/{asn}/day_report?date={date}`
The provided `{asn}` must be affiliated with your account.
`{date}` must be an ISO 8601-formatted date: `YYYY-MM-DD`. If no date is specified, the API responds with the data from the day before.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `DDoS Botnet Feed Write`
* `DDoS Botnet Feed Read`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/botnet_feed/asn/$ASN_ID/day_report" \
--request GET \
--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN"
```
```json
{
"result": [
{
"cidr": "127.0.0.1/32",
"date": "2024-05-05T00:00:00Z",
"offense_count": 10000
},
// ... other entries ...
],
"success": true,
"errors": [],
"messages": []
}
```
---
title: Changelog for global changes to DDoS protection · Cloudflare DDoS
Protection docs
description: Stay updated with Cloudflare's DDoS protection. Discover the latest
rule updates, accuracy improvements, and threat landscape adaptations.
lastUpdated: 2025-06-30T19:31:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/change-log/
md: https://developers.cloudflare.com/ddos-protection/change-log/index.md
---
Cloudflare has a regular cadence of releasing updates and new rules to the DDoS managed rulesets. The updates either improve a rule's accuracy, lower false positives rates, or increase the protection due to a change in the threat landscape.
The release cycle for a new rule within the regular cadence follows this process:
* Cloudflare adds a new rule configured with the *Log* action, and announces the rule in the "Scheduled changes" section of each managed ruleset.
* From that point on, if this rule matches any traffic, the matched traffic will be visible in one of the [analytics dashboards](https://developers.cloudflare.com/ddos-protection/reference/analytics/). If you suspect this might be a false positive, you can lower the sensitivity for that rule. Refer to [override examples](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/override-examples/#legitimate-traffic-is-incorrectly-identified-as-an-attack-and-causes-a-false-positive) for details.
* Cloudflare updates the rule action to mitigate traffic (for example, using the *Block* action) after a period of at least seven days, usually on a Monday. The exact date is shown in the scheduled changes list.
Changes to existing rules follow the same process, except that Cloudflare will create a temporary updated rule (denoted as `BETA` in rule description) before updating the original rule on the next release cycle.
Cloudflare is very proactive in responding to new attack vectors, which may need to be released outside of the 7-day cycle, defined as an Emergency Release. This emergency release is only used to respond to new high priority threats with a low false positive probability.
## RSS feeds
* [General updates](https://developers.cloudflare.com/ddos-protection/change-log/general-updates/) - [Subscribe to RSS](https://developers.cloudflare.com/ddos-protection/change-log/general-updates/index.xml)
* [Network-layer DDoS managed ruleset](https://developers.cloudflare.com/ddos-protection/change-log/network/) - [Subscribe to RSS](https://developers.cloudflare.com/ddos-protection/change-log/network/index.xml)
* [HTTP DDoS managed ruleset](https://developers.cloudflare.com/ddos-protection/change-log/http/) - [Subscribe to RSS](https://developers.cloudflare.com/ddos-protection/change-log/http/index.xml)
---
title: Frequently asked questions for DDoS Protection · Cloudflare DDoS
Protection docs
description: When Cloudflare's DDoS systems detect and mitigate attacks, they
drop, rate-limit, or challenge (as applicable) packets, DNS queries, or HTTP
requests, based on the type of attack.
lastUpdated: 2026-01-27T18:50:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/frequently-asked-questions/
md: https://developers.cloudflare.com/ddos-protection/frequently-asked-questions/index.md
---
## What is a DDoS attack event?
When Cloudflare's DDoS systems detect and mitigate attacks, they drop, rate-limit, or challenge (as applicable) packets, DNS queries, or HTTP requests, based on the type of attack.
There are three main DDoS mitigation systems:
1. [DDoS managed rulesets](https://developers.cloudflare.com/ddos-protection/managed-rulesets/)
a. [Network-layer DDoS managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/)
b. [HTTP DDoS managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/)
2. [Advanced TCP Protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-tcp-protection/)
3. [Advanced DNS Protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-dns-protection/)
The DDoS managed ruleset includes many individual rules. Each rule provides the heuristics that instructs the system how to identify DDoS attack traffic. When the DDoS managed ruleset identifies an attack, it will generate a real-time fingerprint to match against the attack traffic, and install an ephemeral mitigation rule to mitigate the attack using that fingerprint.
The start time of the attack is when the mitigation rule is installed. The attack ends when there is no more traffic matching the rule. This is a single DDoS attack event.
A DDoS attack has a start time, end time, and additional attack metadata such as:
* Attack ID
* Attack vector
* Mitigating rule
* Total bytes and packets
* Attack target
* Mitigation action
This information is used to populate the [Executive Summary](https://developers.cloudflare.com/analytics/network-analytics/understand/main-dashboard/#executive-summary) section in the [Network Analytics](https://developers.cloudflare.com/analytics/network-analytics/) dashboard.
It can also be retrieved via GraphQL API using the `dosdAttackAnalyticsGroups` node.
Currently, the concept of a DDoS attack event only exists for the [Network-layer DDoS managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/). There is no such grouping of individual packets, queries, or HTTP requests for the other systems yet.
***
## How does Cloudflare protect against "low and slow" DDoS attacks?
A [low and slow DDoS attack](https://www.cloudflare.com/learning/ddos/ddos-low-and-slow-attack/) is most commonly a non-volumetric attack. The attacker will send a low volume of HTTP requests, and do so slowly. This type of attack aims to be less detectable and slowly exhausts resources.
[Slowloris](https://www.cloudflare.com/learning/ddos/ddos-attack-tools/slowloris/) is a type of low and slow attack where the attacker establishes [TCP connections](https://developers.cloudflare.com/fundamentals/reference/tcp-connections/) to the target server, often using HTTP or HTTPS protocols.
In the case of a Slowloris attack, the attacker sends incomplete HTTP header lines, thus never completing the HTTP request. The server waits for the complete request, holding the connection open. The attacker periodically sends additional HTTP header fields or partial lines to keep the connection alive. This can be achieved by sending partial HTTP headers, or using the `content-length` header to declare a message body size larger than what is actually sent.
The best practice to defend against low and slow attacks is by using an HTTP reverse proxy, such as Cloudflare's [CDN](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/) or [WAF](https://developers.cloudflare.com/waf/) service. The reverse proxy acts as a shield. It waits for a full HTTP request before forwarding it to the origin, serving from cache, or applying other actions based on user configuration. You can configure your zone so that requests are buffered by Cloudflare, which will absorb low and slow attacks. Our proxy waits for the full HTTP request before passing it on. To enable buffered requests, refer to [Request Body Buffering](https://developers.cloudflare.com/rules/configuration-rules/settings/#request-body-buffering).
The request will be served from Cloudflare's [Cache](https://developers.cloudflare.com/cache/) or [Workers](https://developers.cloudflare.com/workers/), if applicable. If not, it will only be sent to the origin — assuming it was fully completed and has passed WAF checks. So the attack does not exist, similar to TCP Slowloris attacks protection.
Additionally, the reverse proxy will timeout incomplete HTTP requests after a series of [keepalive probes](https://developers.cloudflare.com/fundamentals/reference/tcp-connections/#tcp-connections-and-keepalives).
There is not a minimum threshold for activation. However, to provide additional security, custom firewall rules check for payload sizes and conducts basic sanity checks to ensure the content looks like what is expected.
The RUDY (R-U-Dead-Yet?) DDoS attack is another type of denial-of-service (DoS) tool that performs slow-rate attacks on targeted servers.
Unlike conventional DDoS attacks that overwhelm servers with a high volume of requests in a short period, RUDY focuses on creating a few prolonged requests. It does this by submitting form data at an extremely slow pace to keep the web server tied up and unavailable to legitimate traffic. This approach makes RUDY attacks difficult to detect, because the traffic can appear legitimate and does not flood the server with requests that would typically trigger conventional DDoS protection mechanisms.
RUDY specifically targets the application layer (Layer 7) of web servers by exploiting the way web forms handle data submission. The attack works by injecting one byte of information into an application `POST` field at a time, then waiting. This process causes application threads to await the completion of the form submission indefinitely, effectively exhausting the server's resources and preventing it from processing legitimate requests.
Refer to the [learning center](https://www.cloudflare.com/learning/ddos/ddos-attack-tools/r-u-dead-yet-rudy/) for more information on RUDY attacks.
***
## How does Cloudflare deal with SSL/TLS negotiation attacks or floods?
SSL/TLS based attacks such as BEAST, Poodle, and CRIME are mitigated by Cloudflare's TLS settings, configuration, and cipher limitations. Because Cloudflare serves as the HTTP reverse proxy, TLS exhaustion style attacks are mitigated by terminating TLS sessions before passing HTTP requests to origin servers. TLS traffic is not proxied to origin servers without completing a proper TLS handshake. Additionally, our automated DDoS detection and mitigation systems leverage cipher suites, packet fields, HTTP request attributes and metadata, origin health, traffic profiling, Machine Learning models, and threat intelligence to detect and mitigate additional SSL-based attacks.
***
## Does Cloudflare use BGP Flowspec for upstream mitigation?
Yes. Using our anycast network, along with Traffic Manager, Unimog, and Plurimog, we conduct automated traffic engineering to spread the load of traffic (legitimate and attack) to ensure our network is performant, especially during mitigation of large attacks.
***
## Where can I see latest DDoS trends?
Cloudflare publishes quarterly DDoS reports and coverage of significant DDoS attacks. The publications are available on our [blog website](https://blog.cloudflare.com/tag/ddos-reports/) and as interactive reports on the [Cloudflare Radar Reports website](https://radar.cloudflare.com/reports?q=DDoS).
Learn more about the [methodologies](https://developers.cloudflare.com/radar/reference/quarterly-ddos-reports/) behind these reports.
You can also view [Cloudflare Radar](https://radar.cloudflare.com/) for near real-time insights and trends.
***
## What is the Ping of Death DDoS attacks?
The Ping of Death (PoD) attack involves sending malformed or oversized packets to another computer or server, which can cause the system to freeze, crash, or reboot. Packets are pieces of data sent over the Internet, and the Ping of Death takes advantage of the fact that the IP protocol requires packets to be a maximum of 65,535 bytes in size. By sending a packet larger than this size, the attacker can exploit vulnerabilities in the target's TCP/IP stack, causing a buffer overflow and leading to unpredictable behavior, including system crashes. This type of attack is less common nowadays, as most modern systems and networking equipment have been patched to handle such anomalies.
***
## What are LOIC and HOIC?
LOIC is a popular network stress testing and DoS attack application that is used to flood a server with TCP, UDP, or HTTP requests with the intention of disrupting the service. It is known for its simplicity and ability to be used by individuals with minimal hacking experience. LOIC can be directed by the user to attack a small server, which can cause the server to slow down or crash from the overload of requests. It became famous around 2010 for its use by the hacker group Anonymous in attacks against major companies and organizations.
HOIC is an upgrade from LOIC, designed to overcome some of its limitations, especially in terms of detection and mitigation. It allows users to launch a more powerful DoS attack by enabling attacks on multiple websites at the same time with a higher volume of requests. HOIC also incorporates a feature that makes it more difficult for defense mechanisms to identify and mitigate the attack traffic, partly because it uses a technique that allows the traffic to mimic legitimate HTTP traffic, which is more challenging for traditional network security tools to detect. HOIC supports the use of "booster" scripts that enable it to target various websites simultaneously, significantly increasing its potency as a tool for conducting broad-scale DoS attacks.
These tools and attacks exploit different aspects of network protocols and behaviors to overwhelm targets with unwanted traffic, leading to denial of service. Due to their potential for abuse, their use is illegal and unethical outside of controlled environments for testing purposes.
***
## Can I exclude specific user agents from HTTP DDoS protection?
Yes, you can create an [override](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/override-expressions/) and use the expression fields to match against HTTP requests with the user agent. There are a variety of [fields](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/override-expressions/#available-expression-fields) that you can use.
You can then adjust the [sensitivity level](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/override-parameters/#sensitivity-level) or [mitigation action](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/override-parameters/#action).
Refer to the guide on how to [create an override](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/configure-dashboard/#create-a-ddos-override).
The use of expression fields is subject to [availability](https://developers.cloudflare.com/ddos-protection/#availability).
***
## Does Cloudflare charge for DDoS attack traffic?
No. Since 2017, Cloudflare offers [free, unmetered, and unlimited DDoS protection](https://blog.cloudflare.com/unmetered-mitigation/). There is no limit to the number of DDoS attacks, their duration, or their size. Cloudflare's billing systems automatically exclude DDoS attack traffic from your usage.
***
## How does DDoS Protection determine whether a SYN flood attack is mitigated by `dosd` or Advanced TCP Protection?
DDoS [managed rules](https://developers.cloudflare.com/ddos-protection/managed-rulesets/) detect and mitigate attacks by finding commonality between attack packets and generating a real-time fingerprint to mitigate the attack.
When the attacks are highly randomized and DDoS managed rules are unable to detect a common pattern among the attack packets, [Advanced TCP Protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-tcp-protection/) uses its stateful TCP flowtracking capabilities to determine whether or not packets are legitimate. Advanced TCP Protection also mitigates simpler TCP-based attacks.
Advanced TCP Protection is only necessary and available to [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers. For [Spectrum](https://developers.cloudflare.com/spectrum/) and our HTTP services, we leverage the reverse proxy to mitigate sophisticated randomized TCP-based DDoS attacks.
***
## How does Cloudflare handle hyper-localized DDoS attacks that may aim to overwhelm a specific Point of Presence (PoP)?
Hyper-localized DDoS attacks are attacks that target specific PoPs or data centers from botnet nodes that are close to those locations in an attempt to overwhelm them and cause an outage or service disruptions.
However, Cloudflare's defense approach is resilient to these attacks and uses a combination of intelligent traffic engineering, global Anycast, and real-time, autonomous DDoS mitigation to handle hyper-localized DDoS attacks — even those that may temporarily exceed the capacity of a specific Point of Presence (PoP).
### Global Anycast Network
Anycast allows multiple servers (PoPs) to share the same IP address, and the Border Gateway Protocol (BGP) routing system ensures user traffic is routed to the nearest or lowest-cost node.
#### Process
When one PoP is overwhelmed due to a local DDoS flood or as a result of limited capacity, BGP route propagation can be adjusted to shift traffic away from that PoP. Cloudflare can also withdraw BGP announcements from specific peers or upstreams to force traffic to reroute through better-equipped PoPs. Because DDoS traffic originates from multiple geographic regions, Anycast and traffic engineering distributes the attack across [Cloudflare's full capacity Anycast network](https://www.cloudflare.com/network/) to reduce the burden on a single PoP.
### Intelligent Traffic Engineering
Cloudflare uses real-time data and intelligence systems to make decisions about traffic routing, load balancing, and congestion management.
#### Process
If a specific PoP becomes saturated or experiences attack traffic, Cloudflare's internal traffic engineering systems dynamically steer traffic across alternative paths using traffic shaping, path-aware routing, and dynamic DNS responses.
The system monitors CPU load, network congestion, and traffic type to make smart decisions about whether to reroute or throttle connections.
For Layer 7 (application-level) attacks, Cloudflare can challenge or rate-limit traffic before it reaches application servers. This scenario is similar to some extent to when we take down certain PoPs for maintenance. This can be done automatically via Traffic Manager, and if needed, by our Site Reliability Engineers (SRE).
### Real-Time DDoS Mitigation
DDoS managed rules and Advanced DDoS Protection are autonomous and run on every single server independently, while also coordinating locally and globally, contributing to the resilience of each server and PoP. These systems run close to the network edge in every PoP, meaning detection and mitigation happen rapidly, often before any noticeable impact. If traffic exceeds the capacity of one PoP, mitigation rules are replicated to other PoPs to help absorb overflow.
* **DDoS managed rules**: Detects and mitigates DDoS attacks in real-time. When it detects an attack, it deploys rules within seconds to mitigate the malicious traffic.
* **Advanced TCP Protection**: Identifies and drops abnormal TCP/IP behavior before it hits application servers.
* **Advanced DNS Protection**: Identifies and drops abnormal DNS queries behavior before it hits DNS servers.
***
## What is Advanced TCP Protection's Protected Learning functionality?
The Protected Learning functionality enables the [Advanced TCP Protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-tcp-protection/) system to overcome Internet routing chaos while allowing your legitimate traffic through and blocking DDoS attacks at the edge.
Anycast and BGP are protocols that help route Internet traffic by sending it to the nearest or most optimal data center. Occasional network events—such as a data center being taken offline for maintenance or changes in Internet routing—can cause an established connection to be rerouted to a different data center.
Cloudflare's flow inference functionality, also known as Protected Learning, is specifically designed to handle this. When a TCP connection, such as a flow, shifts to a new data center, our system observes that it is an existing connection that does not appear in the local flow table. Instead of immediately blocking the flow as an unknown connection that may be part of a DDoS attack, our system uses a proprietary process to verify if the connection is legitimate. It might challenge the acknowledgment (ACK) packets of the flow to ensure it is not part of a DDoS attack. Once the flow passes our checks, we allow it to continue without interruption. This ensures that even rare, legitimate shifts in traffic do not break your long-running connections while keeping your network protected against DDoS attacks.
---
title: Get started · Cloudflare DDoS Protection docs
description: The DDoS Attack Protection managed rulesets provided by Cloudflare
are enabled by default on zones onboarded to Cloudflare, IP applications
onboarded to Spectrum, and IP Prefixes onboarded to Magic Transit.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/get-started/
md: https://developers.cloudflare.com/ddos-protection/get-started/index.md
---
## Free, Pro, and Business plans
The DDoS Attack Protection managed rulesets provided by Cloudflare are enabled by default on zones onboarded to Cloudflare, IP applications onboarded to Spectrum, and IP Prefixes onboarded to Magic Transit.
In some situations, the default protection offered by DDoS rules may need to be fine-tuned to your specific situation. You may also want to configure additional protection using other Cloudflare products.
### Adjust the provided DDoS rules
If one or more DDoS rules provided by Cloudflare affects legitimate traffic, you can adjust them so that they do not perform any mitigation action against this kind of traffic. Follow the steps in [handling a false positive](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/override-examples/#legitimate-traffic-is-incorrectly-identified-as-an-attack-and-causes-a-false-positive) to reduce the sensitivity level of one or more DDoS rules and allow incoming legitimate traffic.
### Configure additional protection
To configure additional protection against DDoS attacks, refer to the related Cloudflare products listed in [Network-layer DDoS Attack Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/#related-cloudflare-products) and [HTTP DDoS Attack Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/#related-cloudflare-products).
## Enterprise plan
Cloudflare's DDoS protection systems automatically detect and mitigate DDoS attacks. Additionally, the systems may flag suspiciously-looking incoming traffic from legacy applications, Internet services, or faulty client applications as malicious and apply mitigation actions. If the traffic is in fact legitimate, the mitigation actions can cause service disruptions and outages in your Internet properties.
To prevent this situation, Cloudflare recommends that you perform these steps to get started:
1. Set the ruleset actions for all the [DDoS Attack Protection managed rulesets](https://developers.cloudflare.com/ddos-protection/managed-rulesets/) to *Log*.
2. Analyze the flagged traffic.
3. Adjust the sensitivity or action of individual managed ruleset rules, if required.
4. Switch ruleset actions from *Log* back to the default.
### Prerequisites
You must have one of the following:
* [A zone onboarded to Cloudflare](https://developers.cloudflare.com/dns/zone-setups/full-setup/) but without updated DNS records.
* [An IP application onboarded to Spectrum](https://developers.cloudflare.com/spectrum/get-started/).
* [An IP Prefix onboarded to Magic Transit](https://developers.cloudflare.com/magic-transit/get-started/).
### 1. Configure ruleset actions to Log
Note
The *Log* action is only available to Enterprise customers.
1. [Configure all the rules in the HTTP DDoS Attack Protection managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/configure-dashboard/#access), setting their action to *Log*.
2. [Configure all the rules in the Network-layer DDoS Attack Protection managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/network-overrides/configure-dashboard/#create-a-ddos-override), setting the action to *Log*.
Alternatively, if you are using the API, define an override at the ruleset level to set the action of all managed ruleset rules to `log` by following these instructions:
* [Configure an override for the HTTP DDoS Attack Protection managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/configure-api/#configure-an-override-for-the-http-ddos-attack-protection-managed-ruleset)
* [Configure an override for the Network-layer DDoS Attack Protection managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/network-overrides/configure-api/#configure-an-override-for-the-network-layer-ddos-attack-protection-managed-ruleset)
### 2. Review flagged traffic
1. Go to your [analytics dashboard](https://developers.cloudflare.com/ddos-protection/reference/analytics/) (the exact dashboard depends on your Cloudflare services).
2. Apply one or more filters, if required, and identify any rules that would have blocked legitimate traffic if *Log* mode were disabled. Take note of the rule IDs.
### 3. Customize managed ruleset rules
Customize the specific managed ruleset rules you identified, changing their sensitivity or their action, using the Cloudflare dashboard or using the API.
If you are using the Cloudflare dashboard, refer to:
* [Configure HTTP DDoS Attack Protection in the dashboard](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/configure-dashboard/)
* [Configure Network-layer DDoS Attack Protection in the dashboard](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/network-overrides/configure-dashboard/)
If you are using the API, refer to:
* [Configure HTTP DDoS Attack Protection via API](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/configure-api/)
* [Configure Network-layer DDoS Attack Protection via API](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/network-overrides/configure-api/)
When using the API, ensure that you add any required rule overrides without removing the ruleset override you configured in [Step 1](#1-configure-ruleset-actions-to-log).
### 4. Switch ruleset actions back to the default
Revert the change you did in [Step 1](#1-configure-ruleset-actions-to-log), changing the action of each managed ruleset rule back to *Default* in **Ruleset action**.
Alternatively, if you are using the API, [remove the override](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/configure-api/#configure-an-override-for-the-http-ddos-attack-protection-managed-ruleset) you previously configured at the ruleset level for each managed ruleset. Ensure that you only remove the ruleset override and not any of the rule overrides you may have configured in [Step 3](#3-customize-managed-ruleset-rules).
---
title: Managed rulesets · Cloudflare DDoS Protection docs
description: The DDoS Attack Protection managed rulesets provide comprehensive
protection against a variety of DDoS attacks across L3/4 (network layer) and
L7 (application layer) of the OSI model.
lastUpdated: 2025-06-30T19:31:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ddos-protection/managed-rulesets/
md: https://developers.cloudflare.com/ddos-protection/managed-rulesets/index.md
---
The DDoS Attack Protection managed rulesets provide comprehensive protection against a [variety of DDoS attacks](https://developers.cloudflare.com/ddos-protection/about/attack-coverage/) across L3/4 (network layer) and L7 (application layer) of the [OSI model](https://www.cloudflare.com/learning/ddos/glossary/open-systems-interconnection-model-osi/).
The available managed rulesets are:
* **[HTTP DDoS Attack Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/)**
* This ruleset includes rules to detect and mitigate DDoS attacks over HTTP and HTTPS.
* **[Network-layer DDoS Attack Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/)**
* This ruleset includes rules to detect and mitigate DDoS attacks on L3/4 of the OSI model such as UDP floods, SYN-ACK reflection attacks, SYN Floods, and DNS floods.
***
## Proactive false positive detection for new rules
Note
Only available on Business and Enterprise plans.
When Cloudflare creates a new managed rule, we check the rule impact against the traffic of Business and Enterprise zones while the rule is not blocking traffic yet.
If a [false positive](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/override-examples/#legitimate-traffic-is-incorrectly-identified-as-an-attack-and-causes-a-false-positive) is detected, we proactively reach out to the affected customers and help them make configuration changes (for example, to lower the sensitivity level of the new rule) before the rule starts mitigating traffic. This prevents the new rule from causing service disruptions and outages to your Internet properties.
---
title: Reference · Cloudflare DDoS Protection docs
description: Reference information for Cloudflare's DDoS protection.
lastUpdated: 2024-08-27T14:57:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ddos-protection/reference/
md: https://developers.cloudflare.com/ddos-protection/reference/index.md
---
Refer to the following pages for more information about Cloudflare DDoS protection:
* [Analytics](https://developers.cloudflare.com/ddos-protection/reference/analytics/)
* [Reports](https://developers.cloudflare.com/ddos-protection/reference/reports/)
* [Alerts](https://developers.cloudflare.com/ddos-protection/reference/alerts/)
* [Logs](https://developers.cloudflare.com/ddos-protection/reference/logs/)
* [Simulating test DDoS attacks](https://developers.cloudflare.com/ddos-protection/reference/simulate-ddos-attack/)
---
title: 404 - Page Not Found · Cloudflare DMARC Management docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dmarc-management/404/
md: https://developers.cloudflare.com/dmarc-management/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: DNS lookup limit · Cloudflare DMARC Management docs
description: Review number of DNS lookups on your SPF records
lastUpdated: 2025-08-11T15:20:54.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dmarc-management/dns-lookup-limits/
md: https://developers.cloudflare.com/dmarc-management/dns-lookup-limits/index.md
---
The [Sender Policy Framework (SPF)](https://datatracker.ietf.org/doc/rfc4408/) specification has a limit on the number of DNS lookups required to fully resolve an SPF record. According to the specification, SPF must limit the number of DNS lookups to 10 per SPF check. If your SPF records exceed this number, your emails might not reach their destination.
To check if your SPF records are compliant with the SPF specification:
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Email** > **DMARC Management**.
3. In **Email record overview**, select **View records**.
4. Find your SPF record, and select the three dots next to it > **Edit**.
5. DMARC Management will inspect your records and check for the total number of DNS lookups. If the record exceeds the maximum number of DNS lookups, DMARC Management will warn you about this. You should edit and remove unnecessary records in the DNS page. Refer to [Manage DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/#delete-dns-records) for more information on how to delete DNS records.
---
title: Enable DMARC Management · Cloudflare DMARC Management docs
description: You need to enable DMARC Management to allow Cloudflare to process
DMARC reports on your behalf. DMARC Management only works with apex domains
and not domains in subdomain setups.
lastUpdated: 2025-10-15T15:48:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dmarc-management/enable/
md: https://developers.cloudflare.com/dmarc-management/enable/index.md
---
You need to enable DMARC Management to allow Cloudflare to process DMARC reports on your behalf. DMARC Management only works with apex domains and not domains in [subdomain setups](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/).
A warning on DMARC Management and SPF records
DMARC Management does not support modifications to SPF records when a CNAME record in your zone points to an external domain. Any changes to the SPF record could invalidate your DMARC policy, as Cloudflare cannot update the associated external DNS records. We recommend managing SPF updates directly through the external domain's DNS provider.
To enable DMARC Management:
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Email** > **DMARC Management**.
3. Select **Enable DMARC Management**.
4. DMARC Management will scan your zone for DMARC records, and will present you with two outcomes:
* If no DMARC record is found, Cloudflare will automatically invite you to add one that you can edit later. Select **Add** to continue.
* If a DMARC record is found in your zone, Cloudflare will add another `rua` entry to it. This additional `rua` tag has a Cloudflare email address and is needed for Cloudflare to be able to start processing DMARC reports on your behalf. Select **Next** to continue.
DMARC Management (beta) is now active. However, it may take up to 24 hours to receive your first DMARC report and to display this information in DMARC Management.
---
title: Configure email security records · Cloudflare DMARC Management docs
description: Learn how to configure SPF records, DKIM records, and DMARC records
in your Cloudflare account to help improve email security.
lastUpdated: 2025-09-26T12:15:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dmarc-management/security-records/
md: https://developers.cloudflare.com/dmarc-management/security-records/index.md
---
There are several DNS mechanisms to prevent others from sending emails on behalf of your domain. These all work as TXT records that need to be added on your domain:
* [Sender Policy Framework (SPF)](https://www.cloudflare.com/learning/dns/dns-records/dns-spf-record/): List authorized IP addresses and domains that can send email on behalf of your domain.
* [DomainKeys Identified Mail (DKIM)](https://www.cloudflare.com/learning/dns/dns-records/dns-dkim-record/): Ensure email authenticity by cryptographically signing emails.
* [Domain-based Message Authentication Reporting and Conformance (DMARC)](https://www.cloudflare.com/learning/dns/dns-records/dns-dmarc-record/): Receive aggregate reports about your email traffic and provide clear instructions for how email receivers should treat non-conforming emails.
Note
For additional background on email security records, refer to the [introductory blog post](https://blog.cloudflare.com/tackling-email-spoofing/).
## Create security records
To set up email security records:
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Email** > **DMARC Management**.
3. In **Email record overview**, select **View records**.
4. Use the available options to set up [SPF](https://www.cloudflare.com/en-gb/learning/dns/dns-records/dns-spf-record/), [DKIM](https://www.cloudflare.com/en-gb/learning/dns/dns-records/dns-dkim-record/), and [DMARC records](https://www.cloudflare.com/en-gb/learning/dns/dns-records/dns-dmarc-record/). This page will also list any previous records you might already have in your account.
## Edit or delete records
Refer to [Manage DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/) for more information.
---
title: Review DMARC statistics · Cloudflare DMARC Management docs
description: DMARC Management (beta) allows you to review how emails sent on
your behalf have fared regarding security policies such as DMARC, SFP, and
DKIM.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dmarc-management/statistics/
md: https://developers.cloudflare.com/dmarc-management/statistics/index.md
---
DMARC Management (beta) allows you to review how emails sent on your behalf have fared regarding security policies such as DMARC, SFP, and DKIM.
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Email** > **DMARC Management**.
3. The graph shows you the volume of emails during a certain period of time. Select the dropdown to select a period of time up to 30 days.
4. Moving your mouse through the graph gives you details for a particular day. Select **View reports** for a list of DMARC reports by date.
5. Select one of the dates shown to open a window with more details.
## Source details
The Top 10 sources section shows you details about the top sources sending emails on your behalf, with information such as total volume of emails and how these sources fared regarding security policies.
You also have access to information about all third parties, and can drill down for further details on each of them:
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Email** > **DMARC Management**.
3. Select **View all**.
4. The next page shows you a list of all sources sending email on your behalf. You can filter this list by time period.
5. Find a source you want to inspect further, and select the three dots in front of it > **Details** to learn more about that third party.
---
title: 404 - Page Not Found · Cloudflare DNS docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/404/
md: https://developers.cloudflare.com/dns/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Additional options · Cloudflare DNS docs
description: "Beyond setting up your zone and updating your DNS records, you may
want to customize the following settings in Cloudflare DNS:"
lastUpdated: 2025-02-11T10:50:09.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/dns/additional-options/
md: https://developers.cloudflare.com/dns/additional-options/index.md
---
Beyond [setting up your zone](https://developers.cloudflare.com/dns/zone-setups/) and [updating your DNS records](https://developers.cloudflare.com/dns/manage-dns-records/), you may want to customize the following settings in Cloudflare DNS:
* [Configure DNS zone defaults](https://developers.cloudflare.com/dns/additional-options/dns-zone-defaults/)
* [Analytics and logs](https://developers.cloudflare.com/dns/additional-options/analytics/)
* [Reverse zones and PTR records](https://developers.cloudflare.com/dns/additional-options/reverse-zones/)
---
title: Changelog · Cloudflare DNS docs
description: Access GraphQL-powered DNS Firewall analytics directly in the
Cloudflare dashboard.
lastUpdated: 2025-04-23T17:56:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/changelog/
md: https://developers.cloudflare.com/dns/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/dns.xml)
## 2025-09-16
**DNS Firewall Analytics — now in the Cloudflare dashboard**
#### What's New
Access [GraphQL-powered DNS Firewall analytics](https://developers.cloudflare.com/dns/dns-firewall/analytics/) directly in the Cloudflare dashboard.

#### Explore Four Interactive Panels
* **Query summary**: Describes trends over time, segmented by dimensions.
* **Query statistics**: Describes totals, cached/uncached queries, and processing/response times.
* **DNS queries by data center**: Describes global view and the top 10 data centers.
* **Top query statistics**: Shows a breakdown by key dimensions, with search and expand options (up to top 100 items).
Additional features:
* Apply filters and time ranges once. Changes reflect across all panels.
* Filter by dimensions like query name, query type, cluster, data center, protocol (UDP/TCP), IP version, response code/reason, and more.
* Access up to 62 days of historical data with flexible intervals.
#### Availability
Available to all DNS Firewall customers as part of their existing subscription.
#### Where to Find It
* In the Cloudflare dashboard, go to the **DNS Firewall** page.
[Go to **Analytics**](https://dash.cloudflare.com/?to=/:account/dns-firewall/analytics)
* Refer to the [DNS Firewall Analytics](https://developers.cloudflare.com/dns/dns-firewall/analytics/) to learn more.
## 2025-06-19
**Account-level DNS analytics now available via GraphQL Analytics API**
Authoritative DNS analytics are now available on the **account level** via the [Cloudflare GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/).
This allows users to query DNS analytics across multiple zones in their account, by using the `accounts` filter.
Here is an example to retrieve the most recent DNS queries across all zones in your account that resulted in an `NXDOMAIN` response over a given time frame. Please replace `a30f822fcd7c401984bf85d8f2a5111c` with your actual account ID.
```graphql
query GetLatestNXDOMAINResponses {
viewer {
accounts(filter: { accountTag: "a30f822fcd7c401984bf85d8f2a5111c" }) {
dnsAnalyticsAdaptive(
filter: {
date_geq: "2025-06-16"
date_leq: "2025-06-18"
responseCode: "NXDOMAIN"
}
limit: 10000
orderBy: [datetime_DESC]
) {
zoneTag
queryName
responseCode
queryType
datetime
}
}
}
}
```
[Run in GraphQL API Explorer](https://graphql.cloudflare.com/explorer?query=I4VwpgTgngBA4mALgGQIaLAZ0QOQBoAiA8gLICCAkjgEpYAOA9gHaZYwDeAUDDAG4CWYAO6QO3HjFQBjKQxBNEmABQAzfgBsMEAFwdJMuQoAqqAOa6ARKgDMABhUAOAExOVUgCYB2KQBZbARgBOBx8AI0cAVncHFSdUCP9EqQsYAF8ASjEJCXcWMiZUdShEfilMMndUOhLeMCVxbJ41TUhdLkbGyowAfVMwYEsnWycIgFpbADZR-wmLBo6YLrBu9X7B4bHJ6Yc5hYkIemZWAGEGdzBLfGJyKl2F1Pns9X4AW35EXX9bb9tHiQYIOcIAAhKC6ADaSxKL2WBAAogBlY4AXT+mXaCwAXswwCZTH8eKBIFAcKgYQSYAdMIwWGBTucKUToEYoHQwBSoa92R0HtleWlOKkgA\&variables=N4XyA)
To learn more and get started, refer to the [DNS Analytics documentation](https://developers.cloudflare.com/dns/additional-options/analytics/#analytics).
## 2025-06-16
**Internal DNS (beta) now manageable in the Cloudflare dashboard**
Participating beta testers can now fully configure [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/) directly in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/internal-dns).
#### Internal DNS enables customers to:
* Map internal hostnames to private IPs for services, devices, and applications not exposed to the public Internet
* Resolve internal DNS queries securely through [Cloudflare Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
* Use split-horizon DNS to return different responses based on network context
* Consolidate internal and public DNS zones within a single management platform
#### What’s new in this release:
* Beta participants can now create and manage internal zones and views in the Cloudflare dashboard

Note
The Internal DNS beta is currently only available to Enterprise customers.
To learn more and get started, refer to the [Internal DNS documentation](https://developers.cloudflare.com/dns/internal-dns/).
## 2025-06-11
**NSEC3 support for DNSSEC**
Enterprise customers can now select NSEC3 as method for proof of non-existence on their zones.
What's new:
* **NSEC3 support for live-signed zones** – For both primary and secondary zones that are configured to be live-signed (also known as "on-the-fly signing"), NSEC3 can now be selected as proof of non-existence.
* **NSEC3 support for pre-signed zones** – Secondary zones that are transferred to Cloudflare in a [pre-signed setup](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/dnssec-for-secondary/#set-up-pre-signed-dnssec) now also support NSEC3 as proof of non-existence.
For more information and how to enable NSEC3, refer to the [NSEC3 documentation](https://developers.cloudflare.com/dns/dnssec/enable-nsec3/).
## 2025-06-03
**Improved onboarding for Shopify merchants**
Shopify merchants can now onboard to **Orange-to-Orange (O2O)** automatically, without needing to contact support or community members.
What's new:
* **Automatic enablement** – O2O is available for all mutual Cloudflare and Shopify customers.
* **Branded record display** – Merchants see a Shopify logo in DNS records, complete with helpful tooltips.

* **Checkout protection** – Workers and Snippets are blocked from running on the checkout path to reduce risk and improve security.
For more information, refer to the [provider guide](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/saas-customers/provider-guides/shopify/).
## 2025-02-02
**Removed unused meta fields from DNS records**
Cloudflare is removing five fields from the `meta` object of DNS records. These fields have been unused for more than a year and are no longer set on new records. This change may take up to four weeks to fully roll out.
The affected fields are:
* the `auto_added` boolean
* the `managed_by_apps` boolean and corresponding `apps_install_id`
* the `managed_by_argo_tunnel` boolean and corresponding `argo_tunnel_id`
An example record returned from the API would now look like the following:
```json
{
"result": {
"id": "",
"zone_id": "",
"zone_name": "example.com",
"name": "www.example.com",
"type": "A",
"content": "192.0.2.1",
"proxiable": true,
"proxied": false,
"ttl": 1,
"locked": false,
"meta": {
"auto_added": false,
"managed_by_apps": false,
"managed_by_argo_tunnel": false,
"source": "primary"
},
"comment": null,
"tags": [],
"created_on": "2025-03-17T20:37:05.368097Z",
"modified_on": "2025-03-17T20:37:05.368097Z"
},
"success": true,
"errors": [],
"messages": []
}
```
For more guidance, refer to [Manage DNS records](https://developers.cloudflare.com/dns/manage-dns-records/).
## 2025-01-27
**Zone IDs and names on individual DNS records**
Records returned by the API will no longer contain the `zone_id` and `zone_name` fields. This change may take up to four weeks to fully roll out. The affected fields were deprecated with an End of Life (EOL) date of November 30, 2024.
## 2024-10-15
**Quote validation for TXT records added via dashboard**
When creating [TXT records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#txt) via the dashboard you will now find:
* Field validation errors if double quotes `"` are added inconsistently.
* Automatically quoted TXT content upon save if no quotes exist in the record content field.
## 2024-10-07
**API support for per-record CNAME flattening**
Paid zones now have the option to flatten specific CNAME records. When using the API, specify the setting `cname_flatten` as `true` or `false`. Refer to the [documentation](https://developers.cloudflare.com/dns/cname-flattening/set-up-cname-flattening/#per-record) for details.
---
title: CNAME flattening · Cloudflare DNS docs
description: CNAME flattening speeds up CNAME resolution and allows you to use a
CNAME record at your zone apex (example.com).
lastUpdated: 2025-12-12T11:59:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/cname-flattening/
md: https://developers.cloudflare.com/dns/cname-flattening/index.md
---
CNAME flattening speeds up CNAME resolution and allows you to use a [CNAME record](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#cname) at your [zone apex](https://developers.cloudflare.com/dns/concepts/#zone-apex) (`example.com`).
Note
This functionality is also what allows you to use a [root custom domain](https://developers.cloudflare.com/pages/configuration/custom-domains/) with a Cloudflare Pages site.
## How it works
With CNAME flattening, Cloudflare finds the IP address that a CNAME points to. This process could involve a single lookup or multiple (if your CNAME points to another CNAME). Cloudflare then returns the final IP address instead of a CNAME record, helping DNS queries resolve faster.
For more details on the steps involved in CNAME flattening, review the [CNAME flattening diagram](https://developers.cloudflare.com/dns/cname-flattening/cname-flattening-diagram/) and refer to the [Cloudflare blog post](https://blog.cloudflare.com/introducing-cname-flattening-rfc-compliant-cnames-at-a-domains-root/).
Note
For information about CNAME flattening in [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/), refer to [internal DNS records](https://developers.cloudflare.com/dns/internal-dns/internal-zones/internal-dns-records/).
## Aspects to keep in mind
* CNAME flattening happens by default in some cases. Refer to [Setup](https://developers.cloudflare.com/dns/cname-flattening/set-up-cname-flattening/) for details.
* CNAME to a different Cloudflare account is prohibited and will result in [Error 1014: CNAME Cross-User Banned](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/cloudflare-1xxx-errors/error-1014/)
* If a CNAME target is being used to verify a domain for a third-party service, turning on [CNAME flattening for all CNAME records](https://developers.cloudflare.com/dns/cname-flattening/set-up-cname-flattening/#for-all-cname-records) may cause the verification to fail since the CNAME record itself will not be returned directly.
---
title: DNS concepts · Cloudflare DNS docs
description: Understand key DNS concepts with Cloudflare's technical
documentation. Learn about nameservers, DNS records, DNSSEC, and more.
lastUpdated: 2026-01-27T10:57:35.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/concepts/
md: https://developers.cloudflare.com/dns/concepts/index.md
---
This page defines and articulates key concepts that are relevant to the Cloudflare DNS service and are used in this documentation. For more concepts and broader descriptions, refer to the [Cloudflare Learning Center](https://www.cloudflare.com/learning/dns/what-is-dns/).
## Domain
Also known as domain name, a domain is the string of text that identifies a specific website, such as `google.com` or `facebook.com`. Every time you access a website from your web browser, a DNS query takes place and the DNS service maps the domain to the actual IP address where the website is [hosted](https://developers.cloudflare.com/fundamentals/manage-domains/).
## Registrar
Before you can start using the Cloudflare DNS service, you must first have a domain. This is achieved by using a service called registrar. As explained in our [Learning Center](https://www.cloudflare.com/learning/dns/glossary/what-is-a-domain-name-registrar/), a registrar handles the reservation of domain names.
Very often the same company that offers domain registration also offers web hosting and DNS management.
You can register a domain name at cost through [Cloudflare Registrar](https://developers.cloudflare.com/registrar/). Every domain acquired through Cloudflare Registrar must also use Cloudflare as their [primary authoritative DNS](#authoritative-dns).
## Nameserver
Although the resolution of a DNS query involves a number of different servers, in this documentation nameserver usually refers to the Cloudflare authoritative nameservers. As explained in the [article about DNS server types](https://www.cloudflare.com/learning/dns/dns-server-types/), the authoritative nameserver is the last stop in the resolution of a DNS query.
Refer to [Nameservers](https://developers.cloudflare.com/dns/nameservers/) for details on the different nameserver offerings.
## Authoritative DNS
Authoritative DNS refers to the service whose nameservers provide the final information mapping a hostname (such as `example.com` or `blog.example.com`) to the IP address that hosts the corresponding content or resources.
This is important because the performance of such authoritative DNS services determine how available, resilient, and performant your website or application is. Cloudflare DNS is an authoritative DNS service leveraging Cloudflare's global network. Refer to [How Cloudflare works](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/) for details.
## DNS setups
It is also possible that one same company will use more than one DNS provider. Usually, this relates to making a domain more resilient - if one provider faces an outage, the nameservers operated by the other DNS provider will most likely still be available.
In this context, you can have a primary DNS setup, when you use Cloudflare to manage your [DNS records](#dns-records), or a [secondary DNS setup](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/), when your DNS records are managed on a different provider and Cloudflare simply receives zone transfers containing your DNS records.
When you have a primary DNS setup, you can either use only Cloudflare (also known as [Full setup](https://developers.cloudflare.com/dns/zone-setups/full-setup/)), or you can use Cloudflare and another provider, where the other provider is the one to receive [outgoing zone transfers](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-primary/) from Cloudflare.
Finally, as Cloudflare also works as a [reverse proxy](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/#cloudflare-as-a-reverse-proxy), you can use a [CNAME setup](https://developers.cloudflare.com/dns/zone-setups/partial-setup/) (also known as partial) when you do not want Cloudflare to be [authoritative](#authoritative-dns) for your domain but you still want to proxy individual subdomains through Cloudflare.
## DNS records
DNS records are instructions that live in the authoritative DNS servers and provide information about a [zone](#zone). This includes what IP address is associated with a particular domain, but can also cover many other use cases, such as directing emails to a mail server or validating ownership of a domain.
For more details about using DNS records within Cloudflare, refer to [Manage DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/) and [DNS record types](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/).
## Zone
DNS zone is an administrative concept used for delegating control over a given domain and its subdomains. Read more in the ["What is a DNS zone?" Learning Center article](https://www.cloudflare.com/learning/dns/glossary/dns-zone/).
For the purpose of this documentation, keep in mind that each domain added to a Cloudflare account is listed in the account home page as a zone. The exact properties and behaviors of your zone depend on its [DNS setup](https://developers.cloudflare.com/dns/zone-setups/).
Also, different Cloudflare products and features are configurable at the zone level. Refer to [Fundamentals](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/) for details.
### Zone apex
Zone apex refers to the domain or subdomain on which the control of DNS records starts.
Example 1
DNS management for **example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| A | `blog` | `192.0.2.1` | Proxied | Auto |
Zone apex: `example.com`
Full record name: `blog.example.com`
Example 2
DNS management for **sub.example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| A | `blog` | `192.0.2.1` | Proxied | Auto |
Zone apex: `sub.example.com`
Full record name: `blog.sub.example.com`
Usually, the zone apex coincides with the apex domain, as shown in Example 1. Example 2 refers to [subdomain delegation](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/), which is only available to Enterprise plans.
To create a DNS record at the zone apex, use `@` for the record **Name**. For details, refer to [How to](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-zone-apex/).
Record at the zone apex
DNS management for **example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| A | `@` | `192.0.2.1` | Proxied | Auto |
Zone apex: `example.com`
Full record name: `example.com`
DNS management for **sub.example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| A | `@` | `192.0.2.1` | Proxied | Auto |
Zone apex: `sub.example.com`
Full record name: `sub.example.com`
## DNSSEC
DNSSEC stands for DNS Security Extensions. It increases security by adding cryptographic signatures to DNS records. These signatures can then be checked to verify that a record came from the correct DNS server, preventing anyone else from issuing false DNS records on your behalf and redirecting traffic intended for your domain. You can read more about it in the [article about DNS security](https://www.cloudflare.com/learning/dns/dns-security/).
For help setting up DNSSEC in Cloudflare, refer to [Enable DNSSEC](https://developers.cloudflare.com/dns/dnssec/).
---
title: DNS Firewall · Cloudflare DNS docs
description: Cloudflare DNS Firewall proxies all DNS queries to your nameservers
through Cloudflare’s global network. This action protects upstream nameservers
from DDoS attacks and reduces load by caching DNS responses.
lastUpdated: 2025-02-11T10:50:09.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/dns-firewall/
md: https://developers.cloudflare.com/dns/dns-firewall/index.md
---
Speed up and protect entire authoritative nameservers
Enterprise-only paid add-on
Cloudflare DNS Firewall proxies all DNS queries to your nameservers through Cloudflare’s global network. This action protects upstream nameservers from DDoS attacks and reduces load by caching DNS responses.
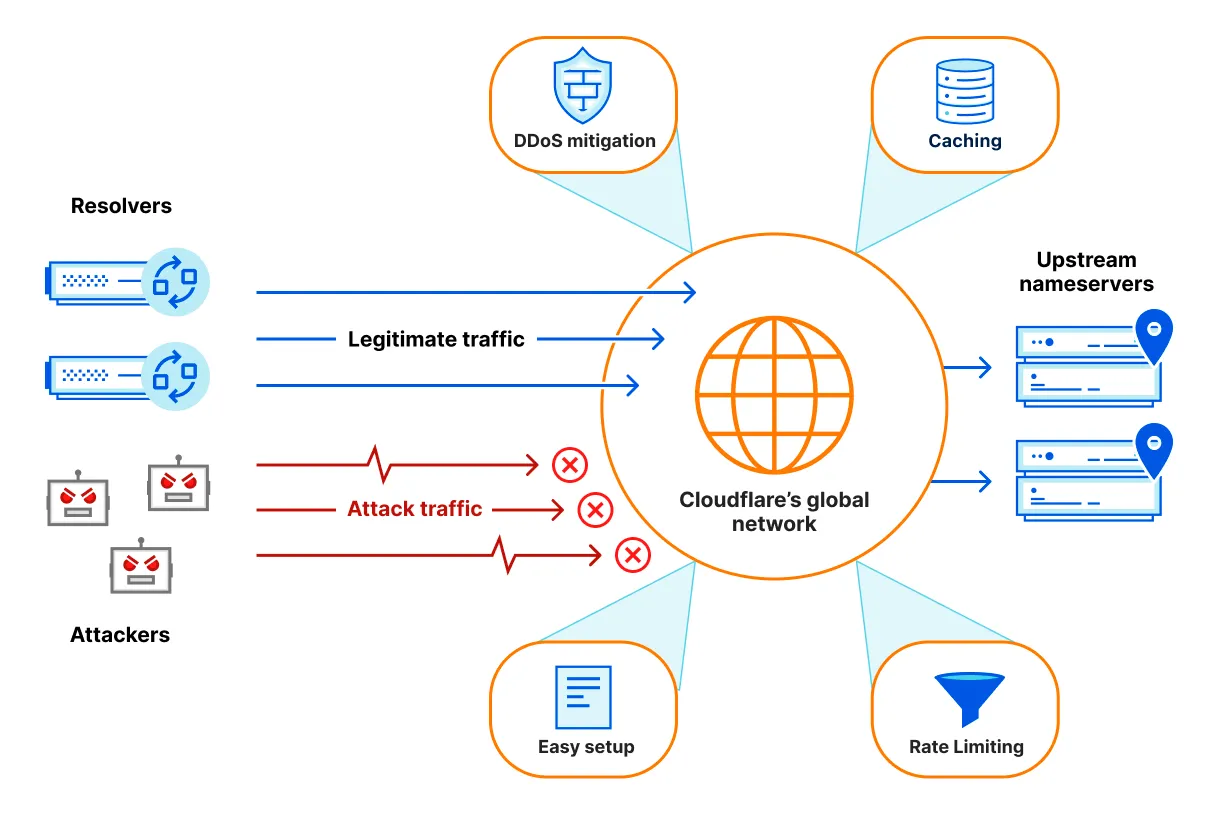
DNS Firewall is for customers who need to speed up and protect entire authoritative nameservers. If you need to speed up and protect individual zones, refer to Cloudflare DNS [Setups](https://developers.cloudflare.com/dns/zone-setups/).
***
## How DNS Firewall works
When a DNS query for your domain takes place:
1. Queries go to the Cloudflare data center that is closest to the website visitor. This is determined by the location of the DNS resolver.
2. Cloudflare tries to return a DNS response from cache.
3. If the response is not available in cache, Cloudflare queries the upstream authoritative nameservers.
4. After returning the response from the nameservers, Cloudflare temporarily caches it for subsequent DNS queries.
***
## Benefits
DNS Firewall provides the following benefits while allowing your organization total control over your authoritative nameservers:
* DDoS mitigation
* High availability
* Global distribution
* Enhanced performance
* Bandwidth savings
* [Rate limiting per data center](https://developers.cloudflare.com/dns/dns-firewall/setup/#additional-options)
* Minimum and maximum cache TTL specification
* DNS [ANY](https://datatracker.ietf.org/doc/html/rfc8482) query type block
---
title: DNSSEC · Cloudflare DNS docs
description: DNS Security Extensions (DNSSEC) adds an extra layer of
authentication to DNS, ensuring requests are not routed to a spoofed domain.
lastUpdated: 2026-02-06T09:34:00.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/dnssec/
md: https://developers.cloudflare.com/dns/dnssec/index.md
---
DNS Security Extensions (DNSSEC) adds an extra layer of authentication to DNS, ensuring requests are not routed to a spoofed domain.
For additional background on DNSSEC, visit the [Cloudflare Learning Center](https://www.cloudflare.com/learning/dns/dns-security/).
***
## Disable DNSSEC
If you are onboarding an existing domain to Cloudflare, make sure DNSSEC **is disabled** at your registrar (where you purchased your domain name). Otherwise, your domain will experience connectivity errors when you change your nameservers.
Provider-specific instructions
This is not an exhaustive list of how to update DS records in other providers, but the following links may be helpful:
* [DNSimple](https://support.dnsimple.com/articles/cloudflare-ds-record/)
* [Domaindiscount24](https://support.domaindiscount24.com/hc/articles/4409759478161)
* [DreamHost](https://help.dreamhost.com/hc/en-us/articles/219539467)
* [Dynadot](https://www.dynadot.com/help/question/set-DNSSEC)
* [Enom](https://support.enom.com/support/solutions/articles/201000065386)
* [Gandi](https://docs.gandi.net/en/domain_names/advanced_users/dnssec.html)
* [GoDaddy](https://www.godaddy.com/help/add-a-ds-record-23865)
* [Hostinger](https://www.hostinger.com/support/3667267-how-to-use-dnssec-records-at-hostinger/)
* [Hover](https://support.hover.com/support/solutions/articles/201000064716)
* [Infomaniak](https://faq.infomaniak.com/2187)
* [InMotion Hosting](https://www.inmotionhosting.com/support/edu/cpanel/enable-dnssec-cloudflare/)
* [INWX](https://kb.inwx.com/en-us/3-nameserver/131)
* [Joker.com](https://joker.com/faq/books/jokercom-faq-en/page/dnssec)
* [Name.com](https://www.name.com/support/articles/205439058-managing-dnssec)
* [Namecheap](https://www.namecheap.com/support/knowledgebase/article.aspx/9722/2232/managing-dnssec-for-domains-pointed-to-custom-dns/)
* [NameISP](https://support.nameisp.com/knowledgebase/dns)
* [Namesilo](https://www.namesilo.com/support/v2/articles/domain-manager/ds-records)
* [OVH](https://help.ovhcloud.com/csm/en-dns-secure-domain-dnssec?id=kb_article_view\&sysparm_article=KB0051637)
* [Squarespace](https://support.squarespace.com/hc/articles/4404183898125-Nameservers-and-DNSSEC-for-Squarespace-managed-domains#toc-dnssec)
* [Registro.br](https://registro.br/tecnologia/dnssec/?secao=tutoriais-dns)
* [Porkbun](https://kb.porkbun.com/article/93-how-to-install-dnssec) (do not fill out **keyData**)
* [TransIP](https://www.transip.eu/knowledgebase/150-secure-domains-custom-nameservers-dnssec/)
Why you have to disable DNSSEC
When your domain has [DNSSEC enabled](https://www.cloudflare.com/learning/dns/dns-security/#what-is-dnssec), your DNS provider digitally signs all your DNS records. This action prevents anyone else from issuing false DNS records on your behalf and redirecting traffic intended for your domain.
However, having a single set of signed records also prevents Cloudflare from issuing new DNS records on your behalf (which is part of using Cloudflare for your authoritative nameservers). So if you change your nameservers without disabling DNSSEC, DNSSEC will prevent Cloudflare's DNS records from resolving properly.
Note
If your previous provider allows you to add DNSKEY records on the zone apex and use these records in responses to DNS queries, refer to this [migration tutorial](https://developers.cloudflare.com/dns/dnssec/dnssec-active-migration/) to learn how to migrate a zone with DNSSEC enabled.
***
## Enable DNSSEC
When you enable DNSSEC, Cloudflare signs your zone, publishes your public signing keys, and generates your **DS** record.
### 1. Activate DNSSEC in Cloudflare
1. In the Cloudflare dashboard, go to the **DNS Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/dns/settings)
2. For **DNSSEC**, click **Enable DNSSEC**.
3. In the dialog, you have access to several necessary values to help you create a **DS** record at your registrar. Once you close the dialog, you can access this information by clicking **DS record** on the **DNSSEC** card.
### 2. Add DS record to your registrar
Add the **DS** record to your registrar. If Algorithm 13 - Cloudflare's preferred cipher choice - is not listed by your registrar, it may also be called *ECDSA Curve P-256 with SHA-256*.
Provider-specific instructions
This is not an exhaustive list of how to update DS records in other providers, but the following links may be helpful:
* [DNSimple](https://support.dnsimple.com/articles/cloudflare-ds-record/)
* [Domaindiscount24](https://support.domaindiscount24.com/hc/articles/4409759478161)
* [DreamHost](https://help.dreamhost.com/hc/en-us/articles/219539467)
* [Dynadot](https://www.dynadot.com/help/question/set-DNSSEC)
* [Enom](https://support.enom.com/support/solutions/articles/201000065386)
* [Gandi](https://docs.gandi.net/en/domain_names/advanced_users/dnssec.html)
* [GoDaddy](https://www.godaddy.com/help/add-a-ds-record-23865)
* [Hostinger](https://www.hostinger.com/support/3667267-how-to-use-dnssec-records-at-hostinger/)
* [Hover](https://support.hover.com/support/solutions/articles/201000064716)
* [Infomaniak](https://faq.infomaniak.com/2187)
* [InMotion Hosting](https://www.inmotionhosting.com/support/edu/cpanel/enable-dnssec-cloudflare/)
* [INWX](https://kb.inwx.com/en-us/3-nameserver/131)
* [Joker.com](https://joker.com/faq/books/jokercom-faq-en/page/dnssec)
* [Name.com](https://www.name.com/support/articles/205439058-managing-dnssec)
* [Namecheap](https://www.namecheap.com/support/knowledgebase/article.aspx/9722/2232/managing-dnssec-for-domains-pointed-to-custom-dns/)
* [NameISP](https://support.nameisp.com/knowledgebase/dns)
* [Namesilo](https://www.namesilo.com/support/v2/articles/domain-manager/ds-records)
* [OVH](https://help.ovhcloud.com/csm/en-dns-secure-domain-dnssec?id=kb_article_view\&sysparm_article=KB0051637)
* [Squarespace](https://support.squarespace.com/hc/articles/4404183898125-Nameservers-and-DNSSEC-for-Squarespace-managed-domains#toc-dnssec)
* [Registro.br](https://registro.br/tecnologia/dnssec/?secao=tutoriais-dns)
* [Porkbun](https://kb.porkbun.com/article/93-how-to-install-dnssec) (do not fill out **keyData**)
* [TransIP](https://www.transip.eu/knowledgebase/150-secure-domains-custom-nameservers-dnssec/)
Note:
Cloudflare automatically adds **DS** records for domains using Cloudflare Registrar or those using `.ch` and `.cz` top-level domains.
***
## Other DNSSEC setup options
If you are using Cloudflare as your Secondary DNS provider and want to configure DNSSEC on your secondary zone(s), you have [three options](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/dnssec-for-secondary/) depending on your setup.
If you want to set up DNSSEC on a subdomain zone, refer to [Subdomain DNSSEC](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/dnssec/).
***
## Limitations
If your registrar does not support DNSSEC with Cloudflare's preferred cipher choice (Algorithm 13), you have several options:
* Contact your registrar to ask for DNSSEC with modern encryption.
* Transfer your domain to a different registrar that supports DNSSEC with Algorithm 13
* File a [complaint with ICANN](https://www.icann.org/compliance/complaint), citing your registrar's lack of compliance.
If your top-level domain does not support DNSSEC with Algorithm 13 (also known as *ECDSA Curve P-256 with SHA-256*), [contact that top-level domain](https://www.iana.org/domains/root/db).
---
title: FAQ · Cloudflare DNS docs
description: Find answers to common questions about Cloudflare's authoritative DNS.
lastUpdated: 2026-01-26T13:01:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/faq/
md: https://developers.cloudflare.com/dns/faq/index.md
---
The sections below cover frequently asked questions about Cloudflare authoritative DNS. For DNS Firewall, refer to [DNS Firewall FAQ](https://developers.cloudflare.com/dns/dns-firewall/faq/).
***
## Cloudflare offerings
### Is Cloudflare a free DNS (domain nameserver) provider?
Yes. Cloudflare offers [free DNS services](https://www.cloudflare.com/dns) to customers on all plans. Note that:
* You do not need to change your hosting provider to use Cloudflare.
* You do not need to move away from your registrar. The only change you make with your registrar is to point the authoritative nameservers to the Cloudflare nameservers.
### Does Cloudflare charge for or limit DNS queries?
Cloudflare never limits or caps DNS queries, but the pricing depends on your plan level.
For customers on Free, Pro, or Business plans, Cloudflare does not charge for DNS queries. For customers on Enterprise plans, Cloudflare uses the number of monthly DNS queries as a pricing input to generate a custom quote.
### Does Cloudflare offer domain masking?
No. Cloudflare does not offer domain masking or DNS redirect services (your hosting provider might). However, we do offer URL forwarding through [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/).
### Can subdomains be added directly to Cloudflare?
Yes. Enterprise customers can add subdomains directly to Cloudflare via [subdomain support](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/).
### Does Cloudflare support EDNS0 (extension mechanisms for DNS)?
Yes, EDNS0 is a building block for modern DNS implementations and is enabled for all Cloudflare customers. EDNS0 adds support for signaling if the DNS Resolver (recursive DNS provider) supports larger message sizes and DNSSEC.
EDNS0 is the first approved set of mechanisms for [DNS extensions](http://en.wikipedia.org/wiki/Extension_mechanisms_for_DNS), originally published as [RFC 2671](https://www.rfc-editor.org/rfc/rfc2671.html).
***
## Nameservers
### Where can I find my Cloudflare nameservers?
On the **DNS Records** page, locate the **Cloudflare Nameservers** card.
[Go to **Records**](https://dash.cloudflare.com/?to=/:account/:zone/dns/records)
Also, the IP address associated with a specific Cloudflare nameserver can be retrieved via a dig command or a third-party DNS lookup tool hosted online such as [whatsmydns.net](https://www.whatsmydns.net/):
```sh
dig kate.ns.cloudflare.com
```
```sh
kate.ns.cloudflare.com. 68675 IN A 173.245.58.124.
```
### Where do I change my nameservers to point to Cloudflare?
Make the change at your registrar, which is where you registered your domain. This may or may not be your hosting provider - refer to [Update nameservers](https://developers.cloudflare.com/dns/nameservers/update-nameservers/) for further context.
If you do not know who your registrar is for the domain, a WHOIS search can help. You can use [ICANN Lookup](https://lookup.icann.org/), for example.
Warning
Some country code TLDs may not be supported by ICANN Lookup. If that is the case, use a different WHOIS search tool.
Once you identify your registrar, follow their instructions.
Provider-specific instructions
This is not an exhaustive list of provider-specific instructions, but the following links may be helpful:
* [Ionos](https://www.ionos.com/help/domains/using-your-own-name-servers/using-your-own-name-servers-for-a-domain/)
* [101Domain](https://help.101domain.com/kb/managing-name-server-records)
* [Amazon](https://docs.aws.amazon.com/Route53/latest/DeveloperGuide/domain-name-servers-glue-records.html#domain-name-servers-glue-records-adding-changing)
* [Blacknight](https://help.blacknight.com/hc/en-us/articles/212512229-Changing-nameservers-in-cp-blacknight-com)
* [BlueHost](https://www.bluehost.com/help/article/custom-nameservers)
* [DirectNIC](https://directnic.com/knowledge/article/33:how%2Bdo%2Bi%2Bmodify%2Bname%2Bservers%2Bfor%2Bmy%2Bdomain%2Bname%253F)
* [DNSMadeEasy](http://www.dnsmadeeasy.com/support/faq/)
* [Domain.com](https://www.domain.com/help/article/domain-management-how-to-update-nameservers)
* [Dotster](https://www.dotster.com/help/article/domain-management-how-to-update-nameservers)
* [DreamHost](https://help.dreamhost.com/hc/en-us/articles/360038897151)
* [EasyDNS](https://kb.easydns.com/knowledge/settingchanging-nameservers/)
* [Enom](https://help.enom.com/hc/en-us/articles/115000486451-Nameservers-NS)
* [Fast Domain](https://www.fastdomain.com/hosting/help/transfer_client_start)
* [FlokiNET](https://billing.flokinet.is/index.php?rp=/knowledgebase/57/Nameserver-and-DNS-records.html)
* [Gandi](https://docs.gandi.net/en/domain_names/common_operations/changing_nameservers.html)
* [GoDaddy](https://www.godaddy.com/help/change-nameservers-for-your-domain-names-664)
* [HostGator](https://www.hostgator.com/help/article/changing-name-servers)
* [Hostico](https://hostico.ro/docs/setarea-nameserverelor-din-contul-de-client-hostico/)
* [HostMonster](https://my.hostmonster.com/cgi/help/222)
* [Hover](https://support.hover.com/support/solutions/articles/201000064742-changing-your-domain-nameservers)
* [Internetdbs](https://faq.internetbs.net/hc/en-gb/articles/4516921367837-How-to-update-Nameservers-for-a-domain)
* [iPage](https://www.ipage.com/help/article/domain-management-how-to-update-nameservers)
* [MelbourneIT](https://support.melbourneit.au/docs/how-do-i-manage-my-dns-on-cpanel)
* [Moniker](https://support.moniker.com/hc/en-gb/articles/10101271418653-How-to-update-Nameservers-for-a-domain)
* [Name.com](https://www.name.com/support/articles/205934457-registering-custom-nameservers)
* [Namecheap](https://www.namecheap.com/support/knowledgebase/article.aspx/767/10/how-can-i-change-the-nameservers-for-my-domain)
* [Network Solutions](https://www.networksolutions.com/manage-it/edit-nameservers.jsp)
* [OVH](https://docs.ovh.com/gb/en/domains/web_hosting_general_information_about_dns_servers/#step-2-edit-your-domains-dns-servers)
* [Porkbun](https://kb.porkbun.com/article/22-how-to-change-your-nameservers)
* [Rackspace](https://support.rackspace.com/how-to/rackspace-name-servers/)
* [Register](https://www.register.com/knowledge)
* [Squarespace](https://support.squarespace.com/hc/articles/4404183898125-Nameservers-and-DNSSEC-for-Squarespace-managed-domains#toc-open-the-domain-s-advanced-settings)
* [Site5](https://kb.site5.com/dns-2/custom-nameservers/)
* [Softlayer](https://cloud.ibm.com/docs/dns?topic=dns-add-edit-or-delete-custom-name-servers-for-a-domain)
* [Yola](https://helpcenter.yola.com/hc/articles/360012492660-Changing-your-name-servers)
### Why have I received an email: (mydomain) stopped using Cloudflare's nameservers?
For domains where Cloudflare hosts the DNS, Cloudflare continuously checks whether the domain uses Cloudflare's nameservers for DNS resolution. If Cloudflare's nameservers are not used, the [domain status](https://developers.cloudflare.com/dns/zone-setups/reference/domain-status/) is updated from **Active** to **Moved** and an email is sent to the customer.
This is important because, if a domain is in a **Moved** state for a [long enough period of time](https://developers.cloudflare.com/dns/zone-setups/reference/domain-status/), it will be deleted from Cloudflare.
To recover a deleted domain, [re-add it in Cloudflare](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/) just like you would for a new domain.
Warning
Cloudflare support is unable to restore DNS or settings for deleted domains.
***
## DNS records
### Does Cloudflare limit the number of DNS records a domain can have?
Yes. All customers have a limit on the number of DNS records they can create.
* Free: 200
* Pro: 3,500
* Business: 3,500
* Enterprise: 3,500
Free zones created before 2024-09-01 00:00:00 UTC have an increased limit of 1,000.
For more DNS records
If you are an Enterprise customer and require more DNS records, contact your account team. Cloudflare can support millions of DNS records on a single zone.
### How long does it take for a DNS change I made to push out?
By default, any changes or additions you make to your Cloudflare zone file will take effect globally within 5 minutes, usually much less.
Depending on the Time-to-Live (TTL) set on the previous [DNS record](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/), old data may still remain cached until the TTL expires. Proxied records expire after 5 minutes ("Automatic"), but the TTL for unproxied records can be customized.
If changes to records with large TTLs are anticipated, it may make sense to reduce the TTL ahead of time so that the change takes effect as quickly as possible.
### Why can't I make ANY queries to Cloudflare DNS servers?
`ANY` queries are special and often misunderstood. They are usually used to get all record types available on a DNS name, but what they return is just any type in the cache of recursive resolvers. This can cause confusion when they are used for debugging.
Because of Cloudflare's many advanced DNS features like CNAME flattening, it can be complex and even impossible to give correct answers to `ANY` queries. For example, when DNS records dynamically come and go or are stored remotely, it can be taxing or even impossible to get all the results at the same time.
Refer to [Deprecating the DNS ANY meta-query type](https://blog.cloudflare.com/deprecating-dns-any-meta-query-type/) for details. The decision to block `ANY` does not affect DNS Firewall customers.
### How do I add ANAME records on Cloudflare?
ANAME or ALIAS are DNS records used by specific DNS providers. If your previous provider was using ANAME or ALIAS, you can recreate these records on Cloudflare as CNAME records. Cloudflare's [CNAME flattening](https://developers.cloudflare.com/dns/cname-flattening/)[1](#user-content-fn-1) allows you to create CNAME records at your [zone apex](https://developers.cloudflare.com/dns/concepts/#zone-apex), removing the need for those other record types.
## Footnotes
1. A process in which Cloudflare returns an IP address instead of the target hostname that a CNAME record points to. [↩](#user-content-fnref-1)
### Why are Cloudflare's A or AAAA records / IP addresses for my domain's DNS responses appearing?
For DNS records proxied to Cloudflare, Cloudflare's IP addresses are returned in DNS queries instead of your original server IP address. This allows Cloudflare to optimize, cache, and protect all requests for your website.
---
title: Foundation DNS · Cloudflare DNS docs
description: Foundation DNS is the Cloudflare DNS offering for enterprise customers.
lastUpdated: 2025-08-01T07:41:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/foundation-dns/
md: https://developers.cloudflare.com/dns/foundation-dns/index.md
---
Foundation DNS is the Cloudflare DNS offering for enterprise customers.
With Foundation DNS, you get access to increased reliability, security, and insights. Features include the following:
* [Advanced nameservers](https://developers.cloudflare.com/dns/foundation-dns/advanced-nameservers/) that provide:
* Strategically distributed IPs to enhance resiliency
* Reduced exposure to incidents or software regression
* More consistent nameserver assignment
* [DNSSEC keys](https://developers.cloudflare.com/dns/foundation-dns/dnssec-keys/) unique to your account
* Additional DNS settings, including:
* [Zone defaults](https://developers.cloudflare.com/dns/additional-options/dns-zone-defaults/)
* [Account custom nameservers](https://developers.cloudflare.com/dns/nameservers/custom-nameservers/account-custom-nameservers/)
* Custom [SOA record](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#soa) and [Nameserver TTL](https://developers.cloudflare.com/dns/nameservers/nameserver-options/#nameserver-ttl)
## Availability
Foundation DNS is only available to Enterprise customers.
Note
Both advanced nameservers and unique ZSK/KSK are opt-in configurations. Refer to [set up advanced nameservers](https://developers.cloudflare.com/dns/foundation-dns/setup/) and [DNSSEC keys](https://developers.cloudflare.com/dns/foundation-dns/dnssec-keys/) for details.
## Related resources
* [Release blog post](https://blog.cloudflare.com/foundation-dns-launch)
* [Product page](https://www.cloudflare.com/dns/foundation-dns/)
---
title: Get started with Cloudflare DNS · Cloudflare DNS docs
description: You can use Cloudflare DNS with a variety of setups. For an
overview of what these setups are and an introduction to specific DNS
terminology, refer to Concepts.
lastUpdated: 2025-08-15T13:12:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/get-started/
md: https://developers.cloudflare.com/dns/get-started/index.md
---
You can use Cloudflare DNS with a variety of [setups](https://developers.cloudflare.com/dns/zone-setups/). For an overview of what these setups are and an introduction to specific DNS terminology, refer to [Concepts](https://developers.cloudflare.com/dns/concepts/).
In the most common setup (full), you [add your domain](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/), import your [DNS records](https://developers.cloudflare.com/dns/manage-dns-records/), and [update your nameservers](https://developers.cloudflare.com/dns/nameservers/update-nameservers/) to make Cloudflare your primary authoritative DNS provider.
Note
Make sure to [review your DNS records](https://developers.cloudflare.com/dns/zone-setups/full-setup/setup/#review-dns-records) before updating your nameservers. If you activate your domain on Cloudflare *without* setting up the correct DNS records, your domain may not be reachable.
Once the setup is completed:
* You [manage DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/) through the Cloudflare dashboard or API. This is how you control which resources are available on the apex domain (`example.com`) or specific subdomains (`blog.example.com`) of your website, as well as control other configurations.
* Cloudflare [responds to all DNS queries](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/) for your hostnames and your DNS records are propagated across the [Cloudflare global network](https://www.cloudflare.com/network/), speeding up your domain.
## Resources
The following links introduce important concepts and will guide you through actions you may need to take while having your website or application on Cloudflare.
* [DNS records](https://developers.cloudflare.com/dns/manage-dns-records/): DNS records contain information about your domain and are used to make your website or application available to visitors and other web services.
* [Nameservers](https://developers.cloudflare.com/dns/nameservers/): In the context of Cloudflare DNS, nameservers refer to authoritative nameservers. When a nameserver is authoritative for `example.com`, it means that DNS resolvers will consider responses from this nameserver when a user tries to access `example.com`.
* [Proxy status](https://developers.cloudflare.com/dns/proxy-status/): Proxy status affects how Cloudflare treats incoming HTTP/S requests to A, AAAA, and CNAME records. When a record is proxied, Cloudflare responds with [anycast IPs](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/), which speeds up and protects HTTP/S traffic with our [cache](https://developers.cloudflare.com/cache/)/[CDN](https://www.cloudflare.com/learning/cdn/what-is-a-cdn/), [DDoS protection](https://developers.cloudflare.com/ddos-protection/), [WAF](https://developers.cloudflare.com/waf/), and [more](https://developers.cloudflare.com/directory/?product-group=Application+performance%2CApplication+security).
## Further reading
* [How Cloudflare works](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/): An overview of how Cloudflare works as a DNS provider and as a reverse proxy.
* [DNS analytics](https://developers.cloudflare.com/dns/additional-options/analytics/): An overview of the different data sources and insights you can get when using Cloudflare DNS.
* [Troubleshooting](https://developers.cloudflare.com/dns/troubleshooting/): A full resources list for when something is not working.
---
title: Glossary · Cloudflare DNS docs
description: Review the definitions for terms used across Cloudflare's DNS documentation.
lastUpdated: 2024-10-30T14:03:50.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/glossary/
md: https://developers.cloudflare.com/dns/glossary/index.md
---
Review the definitions for terms used across Cloudflare's DNS documentation.
| Term | Definition |
| - | - |
| active zone | A DNS zone that is active on Cloudflare requires changing its nameservers to Cloudflare's for management. |
| apex domain | Apex domain is used to refer to a domain that does not contain a subdomain part, such as `example.com` (without `www.`). It is also known as "root domain" or "naked domain". |
| CNAME setup | Also known as partial setup, a CNAME setup allows you to use Cloudflare's reverse proxy without using Cloudflare for your authoritative nameservers. |
| DNS over HTTPS | DNS over HTTPS (DoH) is a standard for encrypting DNS traffic via the HTTPS protocol, preventing tracking and spoofing of DNS queries. |
| DNS over TLS | DNS over TLS (DoT) is a standard for encrypting DNS traffic using its own port (`853`) and TLS encryption. |
| DNS record | DNS records are instructions that live in authoritative DNS servers and provide information about a domain, including what IP address is associated with that domain and how to handle requests for that domain. |
| DNS server | DNS servers translate human-readable domain names into IP addresses, eliminating the need to remember complex IP addresses. |
| DNS zone | A portion of the DNS namespace that is managed by a specific organization or administrator. |
| Domain Name System (DNS) | The Domain Name System (DNS) is the phonebook of the Internet. DNS translates domain names to IP addresses. |
| EDNS Client Subnet (ECS) | ECS is a DNS extension that enables recursive DNS resolvers to include client IP address information in their DNS queries.Not all resolvers use ECS but, if they do, usually a part of the IP address is omitted. Sending ECS headers is generally intended to reduce latency and speed up content delivery in connection to [CDNs](https://developers.cloudflare.com/glossary/?term=cdn) and [load balancers](https://www.cloudflare.com/learning/performance/what-is-load-balancing/). The ECS mechanism is specified in [RFC 7871](https://www.rfc-editor.org/rfc/rfc7871.html). |
| hostname | The name given to a server or node on a network, often the public DNS name of a server. |
| nameserver | A nameserver is a dedicated server that translates human readable hostnames (`www.example.com`) into IP addresses.Nameservers like root servers, TLD servers, and [authoritative nameservers](https://developers.cloudflare.com/dns/nameservers/) are fundamental components of the Domain Name System (DNS). |
| proxy status | The proxy status of a DNS record defines whether requests for your domain will route through Cloudflare (`proxied`) or not (`DNS-only`).When a [DNS record is proxied](https://developers.cloudflare.com/dns/proxy-status/), requests are processed according to your configurations, and Cloudflare can optimize, cache, and protect your domain. Refer to [How Cloudflare works](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/) for details. |
| zone apex | Zone apex refers to the domain or subdomain on which the control of DNS records starts. |
---
title: Internal DNS · Cloudflare DNS docs
description: Manage DNS records that should only be accessible within your
private network. Internal DNS zones and views pair up with Gateway resolver
policies so that you can control how a DNS query should be responded to
according to query context, such as query source IP.
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/internal-dns/
md: https://developers.cloudflare.com/dns/internal-dns/index.md
---
Simplify private network management with Cloudflare DNS for your internal resources.
Enterprise-only
Manage DNS records that should only be accessible within your private network. Internal DNS [zones](https://developers.cloudflare.com/dns/internal-dns/internal-zones/) and [views](https://developers.cloudflare.com/dns/internal-dns/dns-views/) pair up with [Gateway resolver policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/) so that you can control how a DNS query should be responded to according to query context, such as query source IP.
Note
Internal DNS is currently in closed beta. Using it on production traffic is at your own risk. If you are interested in this product, contact your account team.
## Architecture overview
You can use different [connectivity options](https://developers.cloudflare.com/dns/internal-dns/connectivity/) to on-ramp your traffic to Cloudflare. Then, Cloudflare Gateway resolver acts as an interface between the DNS client and internal DNS zones.
Internal DNS zones do not get assigned Cloudflare nameservers and can only be queried via Cloudflare Gateway resolver.
```mermaid
flowchart LR
accTitle: Internal DNS query overview
accDescr: Diagram comparing internal DNS query with public DNS
A[Client]
subgraph Cloudflare account
subgraph Gateway
B[Default 1.1.1.1 resolver]
X[Resolver policy selecting an internal DNS view]
end
subgraph Authoritative DNS
Y[(Public DNS)]
Z[(Internal DNS)]
end
end
C[Public resolver]
B --Query--> Y
X --Query + View ID--> Z
A --Query--> B
A --Query--> X
C --Query--> Y
```
Internal DNS zones are grouped into DNS views, which are selected by the resolver policy you define. Views are usually logical groupings relevant to your organization, such as different geographical locations.
```mermaid
flowchart LR
accTitle: Internal DNS views and zones
accDescr: Diagram exemplifying Internal DNS views and zones relationship
subgraph Internal DNS
subgraph View 111 - London
Y[Zone 600
example.local]
Z[Zone 601
local]
end
subgraph View 110 - San Francisco
X[Zone 101
example.com]
B[Zone 100
example.local]
S[Zone 102
com]
end
W[Zone 701
net]
end
```
Internal DNS zones contain the [DNS records](https://developers.cloudflare.com/dns/internal-dns/internal-zones/internal-dns-records/) that should be used to resolve an internal DNS query. Also, if no internal record is found within a matching internal zone, Cloudflare will check if the matching internal zone is [referencing another internal zone](https://developers.cloudflare.com/dns/internal-dns/internal-zones/reference-zones/).
```mermaid
flowchart LR
accTitle: Internal DNS zones and internal records
accDescr: Diagram exemplifying Internal DNS zones and records relationship
subgraph View 111 - London
subgraph Zone 601 - local
S["@ A 192.0.2.10"]
T["ghi.example A 192.0.2.15"]
end
subgraph Zone 600 - example.local
X["@ A 192.0.2.1"]
Y["abc A 192.0.2.6"]
Z["def A 192.0.2.9"]
end
end
```
In this example, a query for `ghi.example.local` routed to view ID 111 would go to zone 600, which presents the longest matching zone name (`example.local`). Zone 600 does not contain a record for `ghi` but, if it is referencing zone 601, Cloudflare will then look for the queried record within the reference zone.
## Resources
* [Get started](https://developers.cloudflare.com/dns/internal-dns/get-started/)
* [Internal zones](https://developers.cloudflare.com/dns/internal-dns/internal-zones/)
* [Manage DNS views](https://developers.cloudflare.com/dns/internal-dns/dns-views/)
* [Connect to Gateway resolver](https://developers.cloudflare.com/dns/internal-dns/connectivity/)
* [Analytics and logs](https://developers.cloudflare.com/dns/internal-dns/analytics/)
## Related products
**[Cloudflare Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)**
Set up policies to inspect DNS, Network, HTTP, and Egress traffic.
**[Cloudflare Magic WAN](https://developers.cloudflare.com/magic-wan/)**
Improve security and performance for your entire corporate networking, reducing cost and operation complexity.
---
title: DNS records · Cloudflare DNS docs
description: DNS records contain information about your domain and are used to
make your website or application available to visitors and other web services.
lastUpdated: 2026-01-12T14:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/manage-dns-records/
md: https://developers.cloudflare.com/dns/manage-dns-records/index.md
---
DNS records contain information about your domain and are used to make your website or application available to visitors and other web services.
Each DNS record belongs to a different type, and each type serves a different purpose. For background about the different types of DNS records, refer to the [Learning Center](https://www.cloudflare.com/learning/dns/dns-records/). To quickly find reference information about a specific type, refer to [DNS record types](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/).
Depending on the providers you used to [get your domain name](https://developers.cloudflare.com/fundamentals/manage-domains/#get-a-domain-name) and [host your website or application](https://developers.cloudflare.com/fundamentals/manage-domains/#host-your-domain), it is expected that DNS records were automatically created on your behalf. According to your [setup](https://developers.cloudflare.com/dns/zone-setups/), you can use Cloudflare to manage your DNS records.
## DNS records table
When managing your records at Cloudflare, besides the common record fields described below, you may also find an option for [Proxy status](https://developers.cloudflare.com/dns/proxy-status/) and [CNAME flattening](https://developers.cloudflare.com/dns/cname-flattening/). These are specific features offered by Cloudflare.
Record fields
* **Type**: Defines the purpose of a record. Different types of record require different information in their corresponding `Content` field.
* **Name**: Identifies the resource that the record resolves to. Depending on the purpose of the record, the value you want to add to this field will also change.
* **Content**: Contains the core value of a record, depending on the record type.
* **TTL**: Controls how long each record is cached by DNS resolvers.
Example
DNS management for **example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| A | `blog` | `192.0.2.1` | Proxied | Auto |
In this example, an IP address resolution record of type `A` is indicating that the resources that correspond to the subdomain `blog.example.com` can be reached on the IPv4 address `192.0.2.1`.
Also, as this record is [proxied](https://developers.cloudflare.com/dns/proxy-status/), Cloudflare automatically defines for how long this information should be cached by DNS resolvers.
## DNS records quota
There is a limit to the number of records you can create on a single zone.
* Free zones created before `2024-09-01 00:00:00 UTC`: 1,000
* Free zones created on or after `2024-09-01 00:00:00 UTC`: 200
* Pro: 3,500
* Business: 3,500
* Enterprise: 3,500
For more DNS records
If you are an Enterprise customer and require more DNS records, contact your account team. Cloudflare can support millions of DNS records on a single zone.
## Resources
### How to
* [Manage DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/)
* [Create zone apex record](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-zone-apex/)
* [Create subdomain records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-subdomain/)
* [Set up email records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/email-records/)
* [Import and export records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/import-and-export/)
* [Batch record changes](https://developers.cloudflare.com/dns/manage-dns-records/how-to/batch-record-changes/)
* [Dynamically update DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/managing-dynamic-ip-addresses/)
* [Round-robin DNS](https://developers.cloudflare.com/dns/manage-dns-records/how-to/round-robin-dns/)
* [Delegate subdomains](https://developers.cloudflare.com/dns/manage-dns-records/how-to/subdomains-outside-cloudflare/)
### Reference
* [DNS record types](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/)
* [Time to Live (TTL)](https://developers.cloudflare.com/dns/manage-dns-records/reference/ttl/)
* [Record attributes](https://developers.cloudflare.com/dns/manage-dns-records/reference/record-attributes/)
* [Vendor-specific DNS records](https://developers.cloudflare.com/dns/manage-dns-records/reference/vendor-specific-records/)
* [Wildcard DNS records](https://developers.cloudflare.com/dns/manage-dns-records/reference/wildcard-dns-records/)
### Troubleshooting
* [Records with the same name](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/records-with-same-name/)
* [Unexpected DNS records](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/unexpected-dns-records/)
* [Exposed IP addresses](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/exposed-ip-address/)
* [Verify a domain with CNAME](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/cname-domain-verification/)
* [NS records already exist](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/existing-ns-record/)
* [Stale response for upstream DNS resolution](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/stale-response/)
---
title: Nameservers · Cloudflare DNS docs
description: As explained in How DNS works, from the moment a user types an
address (www.example.com) into their web browser, the resolution of a DNS
query takes place. Also, the process behind DNS resolution involves different
computers (or servers).
lastUpdated: 2026-01-22T11:57:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/nameservers/
md: https://developers.cloudflare.com/dns/nameservers/index.md
---
As explained in [How DNS works](https://www.cloudflare.com/learning/dns/what-is-dns/), from the moment a user types an address (`www.example.com`) into their web browser, the resolution of a DNS query takes place. Also, the process behind DNS resolution involves different computers (or servers).
In the context of Cloudflare DNS, nameservers refer to authoritative nameservers, which are the last stop in the DNS query resolution. When a nameserver is authoritative for `example.com`, it means that DNS resolvers will consider responses from this nameserver when a user tries to access `example.com`.
Note
The IPs assigned to each nameserver are static, meaning they will not change without notification.
## Authoritative nameservers offering
Within Cloudflare, and depending on your plan, you can choose between using Cloudflare-branded nameservers or setting up your own custom nameservers. The names for Cloudflare-branded nameservers are automatically assigned and cannot be changed.
Regardless of the type you choose, for these nameservers to be authoritative for your domain, you need to [update your domain nameservers](https://developers.cloudflare.com/dns/nameservers/update-nameservers/). Updating your nameservers is required to activate your domain on Cloudflare and use most of our [application services](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/).
Cloudflare Registrar
If you acquired your domain from [Cloudflare Registrar](https://developers.cloudflare.com/registrar/), your domain already uses Cloudflare nameservers, automatically protecting and speeding up your content or services. If you need to update your nameservers to use a different DNS provider, you will have to [transfer your domain from Cloudflare](https://developers.cloudflare.com/registrar/account-options/transfer-out-from-cloudflare/).
### Standard nameservers
Unless your account has a specific [DNS zone defaults](https://developers.cloudflare.com/dns/additional-options/dns-zone-defaults/) configuration, when you add a domain on a [primary (full)](https://developers.cloudflare.com/dns/zone-setups/full-setup/) or [secondary](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/) DNS setup, Cloudflare automatically assigns two standard nameservers for your zone.
Standard nameservers are hosted on `ns.cloudflare.com` and follow the pattern `.ns.cloudflare.com`.
To know the reason behind these nameserver names, refer to [our blog](https://blog.cloudflare.com/whats-the-story-behind-the-names-of-cloudflares-name-servers/).
### Advanced nameservers
Enterprise accounts on [Foundation DNS](https://developers.cloudflare.com/dns/foundation-dns/) have access to advanced nameservers.
[Advanced nameservers](https://developers.cloudflare.com/dns/foundation-dns/advanced-nameservers/) are hosted on `foundationdns.com`, `foundationdns.net`, and `foundationdns.org`.
Each zone that uses advanced nameservers is assigned a set of three nameservers names: `.foundationdns.com`, `.foundationdns.net`, and `.foundationdns.org`.
### Custom nameservers
With [custom nameservers](https://developers.cloudflare.com/dns/nameservers/custom-nameservers/), your nameservers are hosted on your own domain (or domains) and, in this sense, are not Cloudflare branded.
You provide fully qualified domain names (`ns1.mydomain.com`) for your nameservers, and Cloudflare assigns one IPv4 and one IPv6 to each of your custom nameservers.
Warning
The advantages that come with Foundation DNS [advanced nameservers](https://developers.cloudflare.com/dns/foundation-dns/advanced-nameservers/) are currently not available for [custom nameservers](https://developers.cloudflare.com/dns/nameservers/custom-nameservers/). Make sure you only use one at a time.
---
title: Proxy status · Cloudflare DNS docs
description: While your DNS records make your website or application available
to visitors and other web services, the proxy status of a DNS record defines
how Cloudflare treats incoming DNS queries for that record.
lastUpdated: 2026-01-26T13:01:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/proxy-status/
md: https://developers.cloudflare.com/dns/proxy-status/index.md
---
While your [DNS records](https://developers.cloudflare.com/dns/manage-dns-records/) make your website or application available to visitors and other web services, the proxy status of a DNS record defines how Cloudflare treats incoming DNS queries for that record.
The records you can proxy through Cloudflare are [records used for IP address resolution](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#ip-address-resolution) — meaning A, AAAA, or CNAME records.
Cloudflare recommends setting to proxied all A, AAAA, and CNAME records that are used for serving web traffic. For example, CNAME records being used to verify your domain for a third-party service should not be proxied.
Note
Proxying is on by default when you onboard a domain via the dashboard.
### Benefits
When you set a DNS record to **Proxied** (also known as orange-clouded), Cloudflare can:
* Protect your origin server from [DDoS attacks](https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/).
* [Optimize, cache, and protect](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/) all requests to your application.
* Apply your configurations for a variety of Cloudflare products.
Warning
When you [add a domain](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/) to Cloudflare, Cloudflare protection will be in a [pending state](https://developers.cloudflare.com/dns/zone-setups/reference/domain-status/) until we can verify ownership. This could take up to 24 hours to complete. Refer to [Limitations](https://developers.cloudflare.com/dns/proxy-status/limitations/#pending-domains) for further guidance.
### Example
DNS management for **example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| A | `blog` | `192.0.2.1` | Proxied | Auto |
| A | `shop` | `192.0.2.2` | DNS only | Auto |
In the example DNS table above, there are two DNS records. The record with the name `blog` has proxy on, while the record named `shop` has the proxy off (that is, **DNS only**).
This means that:
* A DNS query to the proxied record `blog.example.com` will be answered with a Cloudflare [anycast IP address](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/) instead of `192.0.2.1`. This ensures that HTTP/HTTPS requests for this name will be sent to Cloudflare's network and can be proxied, which allows the [benefits listed above](#benefits).
* A DNS query to the DNS-only record `shop.example.com` will be answered with the actual origin IP address, `192.0.2.2`. In addition to exposing your origin IP address and not benefitting from several features, Cloudflare cannot provide HTTP/HTTPS analytics on those requests (only DNS analytics).
For further context, refer to [How Cloudflare works](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/).
***
## Proxied records
The sections below describe specific behaviors and expected outcomes when you have DNS records set to proxied. There may also be some [limitations](https://developers.cloudflare.com/dns/proxy-status/limitations/) in specific scenarios.
### Predefined time to live
By default, all proxied records have a time to live (TTL) of **Auto**, which is set to 300 seconds. This value cannot be edited.
Since only [records used for IP address resolution](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#ip-address-resolution) can be proxied, this setting ensures that potential changes to the assigned [anycast IP address](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/) will take effect quickly, as recursive resolvers will not cache them for longer than 300 seconds (five minutes).
Note
It may take longer than five minutes for you to actually experience record changes, as your local DNS cache may take longer to update.
### Mix proxied and unproxied
If you have multiple A or AAAA records on the same name and at least one of them is proxied, Cloudflare will treat all A or AAAA records on this name as being proxied.
Example
DNS management for **example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| A | `blog` | `192.0.2.1` | Proxied | Auto |
| A | `blog` | `192.0.2.5` | DNS only | Auto |
In this example, all traffic intended for `blog.example.com` will be treated as if both records were **Proxied**.
Cloudflare will also proxy a request if a hostname on a CNAME chain is proxied.
Example
Consider that the same Cloudflare account has two different zones, `example.com` and `example.net`.
DNS management for **example.com**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| CNAME | `example.com` | `origin.example.net` | DNS only | Auto |
DNS management for **example.net**:
| Type | Name | Content | Proxy status | TTL |
| - | - | - | - | - |
| CNAME | `origin.example.net` | `` | Proxied | Auto |
In this example, all traffic intended for `example.com` will be treated as **Proxied**.
Note
CNAME to a different Cloudflare account is prohibited and will result in a [Error 1014 (CNAME Cross-User Banned)](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/cloudflare-1xxx-errors/error-1014/)
### CNAME records
Proxied [CNAME records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#cname) are flattened by default, as they return Cloudflare anycast IPs. With CNAME flattening, Cloudflare finds the IP address that a CNAME points to, helping DNS queries resolve faster. Refer to [CNAME flattening](https://developers.cloudflare.com/dns/cname-flattening/) for details.
In some cases, Cloudflare will show a warning message or [prevent](https://developers.cloudflare.com/dns/proxy-status/limitations/#proxy-eligibility) you from proxying a CNAME record. This happens to avoid misconfigurations and is generally related to other CDN providers or to specific records used for DKIM validation.
Note
Specific CNAME record values with traffic proxied through Cloudflare will enable Orange-to-Orange (O2O) routing for the Shopify SaaS provider. Refer to the [Shopify provider guide](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/saas-customers/provider-guides/shopify/) for more information.
### Protocol optimization
For proxied records, if your domain has [HTTP/2 or HTTP/3 enabled](https://developers.cloudflare.com/speed/optimization/protocol/) and is also using [Universal SSL](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/), Cloudflare automatically generates corresponding [HTTPS Service (HTTPS) records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#svcb-and-https) on the fly. HTTPS records allow you to provide a client with information about how it should connect to a server upfront, without the need of an initial plaintext HTTP connection.
Note
Both HTTP/2 and HTTP/3 configurations also require that you have an SSL/TLS certificate served by Cloudflare. This means that disabling [Universal SSL](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/), for example, could impact this behavior.
***
## DNS-only records
When an A, AAAA, or CNAME record is **DNS-only** — also known as being gray-clouded — DNS queries for these will resolve to the record's origin IP address, as described in the [example](#example).
In addition to potentially exposing your origin IP addresses to bad actors and [DDoS attacks](https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/), leaving your records as **DNS-only** means that Cloudflare cannot [optimize, cache, and protect](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/) requests to your application or provide analytics on those requests.
Note
If you have multiple `A/AAAA` records on the same name and at least one of them is proxied, Cloudflare will treat all `A/AAAA` records on this name as being proxied.
---
title: Reference · Cloudflare DNS docs
lastUpdated: 2025-02-11T10:50:09.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/dns/reference/
md: https://developers.cloudflare.com/dns/reference/index.md
---
* [Analytics API properties](https://developers.cloudflare.com/dns/reference/analytics-api-properties/)
* [Recommended third-party tools](https://developers.cloudflare.com/dns/reference/recommended-third-party-tools/)
* [Features and plans](https://developers.cloudflare.com/dns/reference/all-features/)
* [Domain Connect](https://developers.cloudflare.com/dns/reference/domain-connect/)
* [Analytics MCP server](https://github.com/cloudflare/mcp-server-cloudflare/tree/main/apps/dns-analytics)
---
title: Troubleshooting · Cloudflare DNS docs
description: The following topics are useful for troubleshooting DNS issues.
lastUpdated: 2025-08-12T17:54:27.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/troubleshooting/
md: https://developers.cloudflare.com/dns/troubleshooting/index.md
---
The following topics are useful for troubleshooting DNS issues.
Filter resources...
[FAQ](https://developers.cloudflare.com/dns/faq/)
[FAQs — DNS Firewall](https://developers.cloudflare.com/dns/dns-firewall/faq/)
[Troubleshooting DNSSEC](https://developers.cloudflare.com/dns/dnssec/troubleshooting/)
[Available debug endpoints](https://developers.cloudflare.com/dns/troubleshooting/dns-debug-endpoints/)
[General DNS issues](https://developers.cloudflare.com/dns/troubleshooting/dns-issues/)
[Fix DNS\_PROBE\_FINISHED\_NXDOMAIN](https://developers.cloudflare.com/dns/troubleshooting/dns-probe-finished-nxdomain/)
[Fix DNS\_PROBE\_POSSIBLE error](https://developers.cloudflare.com/dns/troubleshooting/dns-probe-possible/)
[Troubleshooting email issues](https://developers.cloudflare.com/dns/troubleshooting/email-issues/)
[Cannot verify a domain with CNAME](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/cname-domain-verification/)
[Existing NS records block new record creation](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/existing-ns-record/)
[Exposed IP addresses](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/exposed-ip-address/)
[Stale response for upstream DNS resolution](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/stale-response/)
[Cannot add DNS records with the same name](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/records-with-same-name/)
[Unexpected DNS records](https://developers.cloudflare.com/dns/manage-dns-records/troubleshooting/unexpected-dns-records/)
[Troubleshooting primary setup (full)](https://developers.cloudflare.com/dns/zone-setups/full-setup/troubleshooting/)
[Cannot add domain to Cloudflare](https://developers.cloudflare.com/dns/zone-setups/troubleshooting/cannot-add-domain/)
[Delete all DNS records](https://developers.cloudflare.com/dns/zone-setups/troubleshooting/delete-all-records/)
[Domain deleted from Cloudflare](https://developers.cloudflare.com/dns/zone-setups/troubleshooting/domain-deleted/)
[Troubleshooting secondary nameservers](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/troubleshooting/)
---
title: DNS setups · Cloudflare DNS docs
description: "When using Cloudflare DNS, you have a few options for your DNS zone setup:"
lastUpdated: 2026-01-27T10:57:35.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/dns/zone-setups/
md: https://developers.cloudflare.com/dns/zone-setups/index.md
---
When using Cloudflare DNS, you have a few options for your DNS zone setup:
* [Primary setup (Full)](https://developers.cloudflare.com/dns/zone-setups/full-setup/) (most common): Use Cloudflare as your primary DNS provider and manage your DNS records on Cloudflare.
* [CNAME setup (Partial)](https://developers.cloudflare.com/dns/zone-setups/partial-setup/): Keep your primary DNS provider and only use Cloudflare's reverse proxy for individual subdomains.
* [Zone transfers](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/): Use Cloudflare and another DNS provider together across your entire zone to increase availability and fault tolerance. DNS records will be transferred between providers using [AXFR](https://datatracker.ietf.org/doc/html/rfc5936) or [IXFR](https://datatracker.ietf.org/doc/html/rfc1995).
* [Subdomain setup](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/): With your apex domain (`example.com`) on a CNAME setup (partial) or primary setup (full), independently manage the settings for a delegated subdomain (`blog.example.com`) within a separate zone and, potentially, a separate account.
When configuring a subdomain setup, its availability will depend on both the parent zone setup and the setup used for the child zone. A child zone holds DNS management for a delegated subdomain.
| Parent zone | Child zone | Available |
| - | - | - |
| [Full](https://developers.cloudflare.com/dns/zone-setups/full-setup/) or [Secondary](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/) | [Full](https://developers.cloudflare.com/dns/zone-setups/full-setup/) | Yes |
| [Full](https://developers.cloudflare.com/dns/zone-setups/full-setup/) or [Secondary](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/) | [Secondary](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/) | Yes |
| [Full](https://developers.cloudflare.com/dns/zone-setups/full-setup/) or [Secondary](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/) | [Partial](https://developers.cloudflare.com/dns/zone-setups/partial-setup/) | No |
| [Partial](https://developers.cloudflare.com/dns/zone-setups/partial-setup/) | [Full](https://developers.cloudflare.com/dns/zone-setups/full-setup/) | Yes |
| [Partial](https://developers.cloudflare.com/dns/zone-setups/partial-setup/) | [Secondary](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/) | Yes |
| [Partial](https://developers.cloudflare.com/dns/zone-setups/partial-setup/) | [Partial](https://developers.cloudflare.com/dns/zone-setups/partial-setup/) | Yes |
For details, refer to [setup](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/setup/).
***
## Zone status
The possible statuses for a zone are the following:
* Initializing
* Pending
* Active
* Moved
* Deleted
* Purged
For details on each status and how a zone can transition from one status to the other, consider the [Reference page](https://developers.cloudflare.com/dns/zone-setups/reference/domain-status/).
Do not use pending zones in production
If you have a paid plan, make sure not to use pending zones for production traffic. Cloudflare responds to DNS queries for pending zones on the assigned Cloudflare nameserver IPs but there are associated risks, especially if you do not use [zone holds](https://developers.cloudflare.com/fundamentals/account/account-security/zone-holds/).
***
## Common use cases and availability
If you are unsure of which setup to use, consider the questions below for an overview of common use cases and their correspondence to each setup and [different pricing plans](https://www.cloudflare.com/plans/#overview).
Are you on a Free or Pro plan?
If you are on a Free or Pro plan, [primary setup (full)](https://developers.cloudflare.com/dns/zone-setups/full-setup/) is the only one available. This is the recommended and most common option.
Will you be using Cloudflare with other DNS providers?
If you are on a Business or Enterprise plan, you can use [CNAME setup (partial)](https://developers.cloudflare.com/dns/zone-setups/partial-setup/) to keep your primary DNS provider and only proxy individual subdomains through Cloudflare.
If you are on an Enterprise plan, you also have the option to use [zone transfers](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/) to set up Cloudflare as either a primary or a secondary DNS provider.
Do you need to manage subdomains separately?
If you are on an Enterprise plan, you can use [subdomain setup](https://developers.cloudflare.com/dns/zone-setups/subdomain-setup/) to manage the Cloudflare settings for one or more subdomains separately from your domain apex.
Note
If you run your own authoritative nameservers but still want to benefit from Cloudflare's global anycast network, check out [DNS Firewall](https://developers.cloudflare.com/dns/dns-firewall/).
---
title: 404 - Page Not Found · Cloudflare Durable Objects docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/404/
md: https://developers.cloudflare.com/durable-objects/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Workers Binding API · Cloudflare Durable Objects docs
lastUpdated: 2025-01-31T11:01:46.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/durable-objects/api/
md: https://developers.cloudflare.com/durable-objects/api/index.md
---
* [Durable Object Base Class](https://developers.cloudflare.com/durable-objects/api/base/)
* [Durable Object Container](https://developers.cloudflare.com/durable-objects/api/container/)
* [Durable Object Namespace](https://developers.cloudflare.com/durable-objects/api/namespace/)
* [Durable Object ID](https://developers.cloudflare.com/durable-objects/api/id/)
* [Durable Object Stub](https://developers.cloudflare.com/durable-objects/api/stub/)
* [Durable Object State](https://developers.cloudflare.com/durable-objects/api/state/)
* [SQLite-backed Durable Object Storage](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/)
* [KV-backed Durable Object Storage (Legacy)](https://developers.cloudflare.com/durable-objects/api/legacy-kv-storage-api/)
* [Alarms](https://developers.cloudflare.com/durable-objects/api/alarms/)
* [WebGPU](https://developers.cloudflare.com/durable-objects/api/webgpu/)
* [Rust API](https://github.com/cloudflare/workers-rs?tab=readme-ov-file#durable-objects)
---
title: Best practices · Cloudflare Durable Objects docs
lastUpdated: 2025-01-31T11:01:46.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/durable-objects/best-practices/
md: https://developers.cloudflare.com/durable-objects/best-practices/index.md
---
* [Rules of Durable Objects](https://developers.cloudflare.com/durable-objects/best-practices/rules-of-durable-objects/)
* [Invoke methods](https://developers.cloudflare.com/durable-objects/best-practices/create-durable-object-stubs-and-send-requests/)
* [Access Durable Objects Storage](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/)
* [Use WebSockets](https://developers.cloudflare.com/durable-objects/best-practices/websockets/)
* [Error handling](https://developers.cloudflare.com/durable-objects/best-practices/error-handling/)
---
title: Demos and architectures · Cloudflare Durable Objects docs
description: Learn how you can use a Durable Object within your existing
application and architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/demos/
md: https://developers.cloudflare.com/durable-objects/demos/index.md
---
Learn how you can use a Durable Object within your existing application and architecture.
## Demos
Explore the following demo applications for Durable Objects.
* [Cloudflare Workers Chat Demo:](https://github.com/cloudflare/workers-chat-demo) This is a demo app written on Cloudflare Workers utilizing Durable Objects to implement real-time chat with stored history.
* [Wildebeest:](https://github.com/cloudflare/wildebeest) Wildebeest is an ActivityPub and Mastodon-compatible server whose goal is to allow anyone to operate their Fediverse server and identity on their domain without needing to keep infrastructure, with minimal setup and maintenance, and running in minutes.
* [Multiplayer Doom Workers:](https://github.com/cloudflare/doom-workers) A WebAssembly Doom port with multiplayer support running on top of Cloudflare's global network using Workers, WebSockets, Pages, and Durable Objects.
## Reference architectures
Explore the following reference architectures that use Durable Objects:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Control and data plane architectural pattern for Durable Objects](https://developers.cloudflare.com/reference-architecture/diagrams/storage/durable-object-control-data-plane-pattern/)
[Separate the control plane from the data plane of your application to achieve great performance and reliability without compromising on functionality.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/durable-object-control-data-plane-pattern/)
---
title: REST API · Cloudflare Durable Objects docs
lastUpdated: 2025-01-31T11:01:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/durable-objects-rest-api/
md: https://developers.cloudflare.com/durable-objects/durable-objects-rest-api/index.md
---
---
title: Examples · Cloudflare Durable Objects docs
description: Explore the following examples for Durable Objects.
lastUpdated: 2025-08-14T13:46:41.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/durable-objects/examples/
md: https://developers.cloudflare.com/durable-objects/examples/index.md
---
Explore the following examples for Durable Objects.
[Use ReadableStream with Durable Object and Workers](https://developers.cloudflare.com/durable-objects/examples/readable-stream/)
[Stream ReadableStream from Durable Objects.](https://developers.cloudflare.com/durable-objects/examples/readable-stream/)
[Use RpcTarget class to handle Durable Object metadata](https://developers.cloudflare.com/durable-objects/examples/reference-do-name-using-init/)
[Access the name from within a Durable Object using RpcTarget.](https://developers.cloudflare.com/durable-objects/examples/reference-do-name-using-init/)
[Durable Object Time To Live](https://developers.cloudflare.com/durable-objects/examples/durable-object-ttl/)
[Use the Durable Objects Alarms API to implement a Time To Live (TTL) for Durable Object instances.](https://developers.cloudflare.com/durable-objects/examples/durable-object-ttl/)
[Build a WebSocket server with WebSocket Hibernation](https://developers.cloudflare.com/durable-objects/examples/websocket-hibernation-server/)
[Build a WebSocket server using WebSocket Hibernation on Durable Objects and Workers.](https://developers.cloudflare.com/durable-objects/examples/websocket-hibernation-server/)
[Build a WebSocket server](https://developers.cloudflare.com/durable-objects/examples/websocket-server/)
[Build a WebSocket server using Durable Objects and Workers.](https://developers.cloudflare.com/durable-objects/examples/websocket-server/)
[Use the Alarms API](https://developers.cloudflare.com/durable-objects/examples/alarms-api/)
[Use the Durable Objects Alarms API to batch requests to a Durable Object.](https://developers.cloudflare.com/durable-objects/examples/alarms-api/)
[Durable Objects - Use KV within Durable Objects](https://developers.cloudflare.com/durable-objects/examples/use-kv-from-durable-objects/)
[Read and write to/from KV within a Durable Object](https://developers.cloudflare.com/durable-objects/examples/use-kv-from-durable-objects/)
[Testing Durable Objects](https://developers.cloudflare.com/durable-objects/examples/testing-with-durable-objects/)
[Write tests for Durable Objects using the Workers Vitest integration.](https://developers.cloudflare.com/durable-objects/examples/testing-with-durable-objects/)
[Build a counter](https://developers.cloudflare.com/durable-objects/examples/build-a-counter/)
[Build a counter using Durable Objects and Workers with RPC methods.](https://developers.cloudflare.com/durable-objects/examples/build-a-counter/)
[Durable Object in-memory state](https://developers.cloudflare.com/durable-objects/examples/durable-object-in-memory-state/)
[Create a Durable Object that stores the last location it was accessed from in-memory.](https://developers.cloudflare.com/durable-objects/examples/durable-object-in-memory-state/)
---
title: Concepts · Cloudflare Durable Objects docs
lastUpdated: 2025-07-30T08:17:23.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/durable-objects/concepts/
md: https://developers.cloudflare.com/durable-objects/concepts/index.md
---
* [What are Durable Objects?](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/)
* [Lifecycle of a Durable Object](https://developers.cloudflare.com/durable-objects/concepts/durable-object-lifecycle/)
---
title: Observability · Cloudflare Durable Objects docs
lastUpdated: 2025-01-31T11:01:46.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/durable-objects/observability/
md: https://developers.cloudflare.com/durable-objects/observability/index.md
---
* [Troubleshooting](https://developers.cloudflare.com/durable-objects/observability/troubleshooting/)
* [Metrics and analytics](https://developers.cloudflare.com/durable-objects/observability/metrics-and-analytics/)
* [Data Studio](https://developers.cloudflare.com/durable-objects/observability/data-studio/)
---
title: Platform · Cloudflare Durable Objects docs
lastUpdated: 2025-03-14T10:22:37.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/durable-objects/platform/
md: https://developers.cloudflare.com/durable-objects/platform/index.md
---
* [Known issues](https://developers.cloudflare.com/durable-objects/platform/known-issues/)
* [Pricing](https://developers.cloudflare.com/durable-objects/platform/pricing/)
* [Limits](https://developers.cloudflare.com/durable-objects/platform/limits/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
---
title: Getting started · Cloudflare Durable Objects docs
description: "This guide will instruct you through:"
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/get-started/
md: https://developers.cloudflare.com/durable-objects/get-started/index.md
---
This guide will instruct you through:
* Writing a JavaScript class that defines a Durable Object.
* Using Durable Objects SQL API to query a Durable Object's private, embedded SQLite database.
* Instantiating and communicating with a Durable Object from another Worker.
* Deploying a Durable Object and a Worker that communicates with a Durable Object.
If you wish to learn more about Durable Objects, refer to [What are Durable Objects?](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/).
## Quick start
If you want to skip the steps and get started quickly, click on the button below.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/hello-world-do-template)
This creates a repository in your GitHub account and deploys the application to Cloudflare Workers. Use this option if you are familiar with Cloudflare Workers, and wish to skip the step-by-step guidance.
You may wish to manually follow the steps if you are new to Cloudflare Workers.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
## 1. Create a Worker project
You will access your Durable Object from a [Worker](https://developers.cloudflare.com/workers/). Your Worker application is an interface to interact with your Durable Object.
To create a Worker project, run:
* npm
```sh
npm create cloudflare@latest -- durable-object-starter
```
* yarn
```sh
yarn create cloudflare durable-object-starter
```
* pnpm
```sh
pnpm create cloudflare@latest durable-object-starter
```
Running `create cloudflare@latest` will install [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), the Workers CLI. You will use Wrangler to test and deploy your project.
For setup, select the following options:
* For *What would you like to start with?*, choose `Hello World example`.
* For *Which template would you like to use?*, choose `Worker + Durable Objects`.
* For *Which language do you want to use?*, choose `TypeScript`.
* For *Do you want to use git for version control?*, choose `Yes`.
* For *Do you want to deploy your application?*, choose `No` (we will be making some changes before deploying).
This will create a new directory, which will include either a `src/index.js` or `src/index.ts` file to write your code and a [`wrangler.jsonc`](https://developers.cloudflare.com/workers/wrangler/configuration/) configuration file.
Move into your new directory:
```sh
cd durable-object-starter
```
Adding a Durable Object to an existing Worker
To add a Durable Object to an existing Worker, you need to:
* Modify the code of the existing Worker to include the following:
```ts
export class MyDurableObject extends DurableObject {
constructor(ctx: DurableObjectState, env: Env) {
// Required, as we're extending the base class.
super(ctx, env)
}
{/* Define your Durable Object methods here */}
}
export default {
async fetch(request, env, ctx): Promise {
const stub = env.MY_DURABLE_OBJECT.getByName(new URL(request.url).pathname);
{/* Access your Durable Object methods here */}
},
} satisfies ExportedHandler;
```
* Update the Wrangler configuration file of your existing Worker to bind the Durable Object to the Worker.
## 2. Write a Durable Object class using SQL API
Before you create and access a Durable Object, its behavior must be defined by an ordinary exported JavaScript class.
Note
If you do not use JavaScript or TypeScript, you will need a [shim](https://developer.mozilla.org/en-US/docs/Glossary/Shim) to translate your class definition to a JavaScript class.
Your `MyDurableObject` class will have a constructor with two parameters. The first parameter, `ctx`, passed to the class constructor contains state specific to the Durable Object, including methods for accessing storage. The second parameter, `env`, contains any bindings you have associated with the Worker when you uploaded it.
* JavaScript
```js
export class MyDurableObject extends DurableObject {
constructor(ctx, env) {
// Required, as we're extending the base class.
super(ctx, env);
}
}
```
* TypeScript
```ts
export class MyDurableObject extends DurableObject {
constructor(ctx: DurableObjectState, env: Env) {
// Required, as we're extending the base class.
super(ctx, env)
}
}
```
* Python
```python
from workers import DurableObject
class MyDurableObject(DurableObject):
def __init__(self, ctx, env):
super().__init__(ctx, env)
```
Workers communicate with a Durable Object using [remote-procedure call](https://developers.cloudflare.com/workers/runtime-apis/rpc/#_top). Public methods on a Durable Object class are exposed as [RPC methods](https://developers.cloudflare.com/durable-objects/best-practices/create-durable-object-stubs-and-send-requests/) to be called by another Worker.
Your file should now look like:
* JavaScript
```js
export class MyDurableObject extends DurableObject {
constructor(ctx, env) {
// Required, as we're extending the base class.
super(ctx, env);
}
async sayHello() {
let result = this.ctx.storage.sql
.exec("SELECT 'Hello, World!' as greeting")
.one();
return result.greeting;
}
}
```
* TypeScript
```ts
export class MyDurableObject extends DurableObject {
constructor(ctx: DurableObjectState, env: Env) {
// Required, as we're extending the base class.
super(ctx, env)
}
async sayHello(): Promise {
let result = this.ctx.storage.sql
.exec("SELECT 'Hello, World!' as greeting")
.one();
return result.greeting;
}
}
```
* Python
```python
from workers import DurableObject
class MyDurableObject(DurableObject):
async def say_hello(self):
result = self.ctx.storage.sql.exec(
"SELECT 'Hello, World!' as greeting"
).one()
return result.greeting
```
In the code above, you have:
1. Defined a RPC method, `sayHello()`, that can be called by a Worker to communicate with a Durable Object.
2. Accessed a Durable Object's attached storage, which is a private SQLite database only accessible to the object, using [SQL API](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/#exec) methods (`sql.exec()`) available on `ctx.storage` .
3. Returned an object representing the single row query result using `one()`, which checks that the query result has exactly one row.
4. Return the `greeting` column from the row object result.
## 3. Instantiate and communicate with a Durable Object
Note
Durable Objects do not receive requests directly from the Internet. Durable Objects receive requests from Workers or other Durable Objects. This is achieved by configuring a binding in the calling Worker for each Durable Object class that you would like it to be able to talk to. These bindings must be configured at upload time. Methods exposed by the binding can be used to communicate with particular Durable Objects.
A Worker is used to [access Durable Objects](https://developers.cloudflare.com/durable-objects/best-practices/create-durable-object-stubs-and-send-requests/).
To communicate with a Durable Object, the Worker's fetch handler should look like the following:
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
const stub = env.MY_DURABLE_OBJECT.getByName(new URL(request.url).pathname);
const greeting = await stub.sayHello();
return new Response(greeting);
},
};
```
* TypeScript
```ts
export default {
async fetch(request, env, ctx): Promise {
const stub = env.MY_DURABLE_OBJECT.getByName(new URL(request.url).pathname);
const greeting = await stub.sayHello();
return new Response(greeting);
},
} satisfies ExportedHandler;
```
* Python
```python
from workers import handler, Response, WorkerEntrypoint
from urllib.parse import urlparse
class Default(WorkerEntrypoint):
async def fetch(request):
url = urlparse(request.url)
stub = self.env.MY_DURABLE_OBJECT.getByName(url.path)
greeting = await stub.say_hello()
return Response(greeting)
```
In the code above, you have:
1. Exported your Worker's main event handlers, such as the `fetch()` handler for receiving HTTP requests.
2. Passed `env` into the `fetch()` handler. Bindings are delivered as a property of the environment object passed as the second parameter when an event handler or class constructor is invoked.
3. Constructed a stub for a Durable Object instance based on the provided name. A stub is a client object used to send messages to the Durable Object.
4. Called a Durable Object by invoking a RPC method, `sayHello()`, on the Durable Object, which returns a `Hello, World!` string greeting.
5. Received an HTTP response back to the client by constructing a HTTP Response with `return new Response()`.
Refer to [Access a Durable Object from a Worker](https://developers.cloudflare.com/durable-objects/best-practices/create-durable-object-stubs-and-send-requests/) to learn more about communicating with a Durable Object.
## 4. Configure Durable Object bindings
[Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) allow your Workers to interact with resources on the Cloudflare developer platform. The Durable Object bindings in your Worker project's [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/) will include a binding name (for this guide, use `MY_DURABLE_OBJECT`) and the class name (`MyDurableObject`).
* wrangler.jsonc
```jsonc
{
"durable_objects": {
"bindings": [
{
"name": "MY_DURABLE_OBJECT",
"class_name": "MyDurableObject"
}
]
}
}
```
* wrangler.toml
```toml
[[durable_objects.bindings]]
name = "MY_DURABLE_OBJECT"
class_name = "MyDurableObject"
```
The `bindings` section contains the following fields:
* `name` - Required. The binding name to use within your Worker.
* `class_name` - Required. The class name you wish to bind to.
* `script_name` - Optional. Defaults to the current [environment's](https://developers.cloudflare.com/durable-objects/reference/environments/) Worker code.
## 5. Configure Durable Object class with SQLite storage backend
A migration is a mapping process from a class name to a runtime state. You perform a migration when creating a new Durable Object class, or when renaming, deleting or transferring an existing Durable Object class.
Migrations are performed through the `[[migrations]]` configurations key in your Wrangler file.
The Durable Object migration to create a new Durable Object class with SQLite storage backend will look like the following in your Worker's Wrangler file:
* wrangler.jsonc
```jsonc
{
"migrations": [
{
"tag": "v1", // Should be unique for each entry
"new_sqlite_classes": [ // Array of new classes
"MyDurableObject"
]
}
]
}
```
* wrangler.toml
```toml
[[migrations]]
tag = "v1"
new_sqlite_classes = [ "MyDurableObject" ]
```
Refer to [Durable Objects migrations](https://developers.cloudflare.com/durable-objects/reference/durable-objects-migrations/) to learn more about the migration process.
## 6. Develop a Durable Object Worker locally
To test your Durable Object locally, run [`wrangler dev`](https://developers.cloudflare.com/workers/wrangler/commands/#dev):
```sh
npx wrangler dev
```
In your console, you should see a`Hello world` string returned by the Durable Object.
## 7. Deploy your Durable Object Worker
To deploy your Durable Object Worker:
```sh
npx wrangler deploy
```
Once deployed, you should be able to see your newly created Durable Object Worker on the Cloudflare dashboard.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
Preview your Durable Object Worker at `..workers.dev`.
## Summary and final code
Your final code should look like this:
* JavaScript
```js
import { DurableObject } from "cloudflare:workers";
export class MyDurableObject extends DurableObject {
constructor(ctx, env) {
// Required, as we are extending the base class.
super(ctx, env);
}
async sayHello() {
let result = this.ctx.storage.sql
.exec("SELECT 'Hello, World!' as greeting")
.one();
return result.greeting;
}
}
export default {
async fetch(request, env, ctx) {
const stub = env.MY_DURABLE_OBJECT.getByName(new URL(request.url).pathname);
const greeting = await stub.sayHello();
return new Response(greeting);
},
};
```
* TypeScript
```ts
import { DurableObject } from "cloudflare:workers";
export class MyDurableObject extends DurableObject {
constructor(ctx: DurableObjectState, env: Env) {
// Required, as we are extending the base class.
super(ctx, env)
}
async sayHello():Promise {
let result = this.ctx.storage.sql
.exec("SELECT 'Hello, World!' as greeting")
.one();
return result.greeting;
}
}
export default {
async fetch(request, env, ctx): Promise {
const stub = env.MY_DURABLE_OBJECT.getByName(new URL(request.url).pathname);
const greeting = await stub.sayHello();
return new Response(greeting);
},
} satisfies ExportedHandler;
```
* Python
```python
from workers import DurableObject, handler, Response
from urllib.parse import urlparse
class MyDurableObject(DurableObject):
async def say_hello(self):
result = self.ctx.storage.sql.exec(
"SELECT 'Hello, World!' as greeting"
).one()
return result.greeting
class Default(WorkerEntrypoint):
async def fetch(self, request):
url = urlparse(request.url)
stub = self.env.MY_DURABLE_OBJECT.getByName(url.path)
greeting = await stub.say_hello()
return Response(greeting)
```
By finishing this tutorial, you have:
* Successfully created a Durable Object
* Called the Durable Object by invoking a [RPC method](https://developers.cloudflare.com/workers/runtime-apis/rpc/)
* Deployed the Durable Object globally
## Related resources
* [Create Durable Object stubs](https://developers.cloudflare.com/durable-objects/best-practices/create-durable-object-stubs-and-send-requests/)
* [Access Durable Objects Storage](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/)
* [Miniflare](https://github.com/cloudflare/workers-sdk/tree/main/packages/miniflare) - Helpful tools for mocking and testing your Durable Objects.
---
title: Reference · Cloudflare Durable Objects docs
lastUpdated: 2025-03-14T10:22:37.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/durable-objects/reference/
md: https://developers.cloudflare.com/durable-objects/reference/index.md
---
* [In-memory state in a Durable Object](https://developers.cloudflare.com/durable-objects/reference/in-memory-state/)
* [Durable Objects migrations](https://developers.cloudflare.com/durable-objects/reference/durable-objects-migrations/)
* [Data security](https://developers.cloudflare.com/durable-objects/reference/data-security/)
* [Data location](https://developers.cloudflare.com/durable-objects/reference/data-location/)
* [Environments](https://developers.cloudflare.com/durable-objects/reference/environments/)
* [Gradual Deployments](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/gradual-deployments/#gradual-deployments-for-durable-objects)
* [FAQs](https://developers.cloudflare.com/durable-objects/reference/faq/)
* [Glossary](https://developers.cloudflare.com/durable-objects/reference/glossary/)
---
title: Release notes · Cloudflare Durable Objects docs
description: Subscribe to RSS
lastUpdated: 2025-03-14T10:22:37.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/release-notes/
md: https://developers.cloudflare.com/durable-objects/release-notes/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/durable-objects/release-notes/index.xml)
## 2026-01-07
**Billing for SQLite Storage**
Storage billing for SQLite-backed Durable Objects will be enabled in January 2026, with a target date of January 7, 2026 (no earlier). For more details, refer to the [Billing for SQLite Storage](https://developers.cloudflare.com/changelog/durable-objects/2026-01-07-durable-objects-sqlite-storage-billing/).
## 2025-10-25
* The maximum WebSocket message size limit has been increased from 1 MiB to 32 MiB.
## 2025-10-16
**Durable Objects can access stored data with UI editor**
Durable Objects stored data can be viewed and written using [Data Studio](https://developers.cloudflare.com/durable-objects/observability/data-studio/) on the Cloudflare dashboard. Only Durable Objects using [SQLite storage](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#create-sqlite-backed-durable-object-class) can use Data Studio.
## 2025-08-21
**Durable Objects stubs can now be directly constructed by name**
A [`DurableObjectStub`](https://developers.cloudflare.com/durable-objects/api/stub) can now be directly constructed by created directly with [`DurableObjectNamespace::getByName`](https://developers.cloudflare.com/durable-objects/api/namespace/#getbyname).
## 2025-04-07
**Durable Objects on Workers Free plan**
[SQLite-backed Durable Objects](https://developers.cloudflare.com/durable-objects/get-started/) are now available on the Workers Free plan with these [limits](https://developers.cloudflare.com/durable-objects/platform/pricing/).
## 2025-04-07
**SQLite in Durable Objects GA**
[SQLite-backed Durable Objects](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#create-sqlite-backed-durable-object-class) and corresponding [Storage API](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/) methods like `sql.exec` have moved from beta to general availability. New Durable Object classes should use wrangler configuration for SQLite storage over key-value storage.
SQLite storage per Durable Object has increased to 10GB for all existing and new objects.
## 2025-02-19
SQLite-backed Durable Objects now support `PRAGMA optimize` command, which can improve database query performance. It is recommended to run this command after a schema change (for example, after creating an index). Refer to [`PRAGMA optimize`](https://developers.cloudflare.com/d1/sql-api/sql-statements/#pragma-optimize) for more information.
## 2025-02-11
When Durable Objects generate an "internal error" exception in response to certain failures, the exception message may provide a reference ID that customers can include in support communication for easier error identification. For example, an exception with the new message might look like: `internal error; reference = 0123456789abcdefghijklmn`.
## 2024-10-07
**Alarms re-enabled in (beta) SQLite-backed Durable Object classes**
The issue identified with [alarms](https://developers.cloudflare.com/durable-objects/api/alarms/) in [beta Durable Object classes with a SQLite storage backend](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#sqlite-storage-backend) has been resolved and alarms have been re-enabled.
## 2024-09-27
**Alarms disabled in (beta) SQLite-backed Durable Object classes**
An issue was identified with [alarms](https://developers.cloudflare.com/durable-objects/api/alarms/) in [beta Durable Object classes with a SQLite storage backend](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#sqlite-storage-backend). Alarms have been temporarily disabled for only SQLite-backed Durable Objects while a fix is implemented. Alarms in Durable Objects with default, key-value storage backend are unaffected and continue to operate.
## 2024-09-26
**(Beta) SQLite storage backend & SQL API available on new Durable Object classes**
The new beta version of Durable Objects is available where each Durable Object has a private, embedded SQLite database. When deploying a new Durable Object class, users can [opt-in to a SQLite storage backend](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#sqlite-storage-backend) in order to access new [SQL API](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/#sql-api) and [point-in-time-recovery API](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/#pitr-point-in-time-recovery-api), part of Durable Objects Storage API.
You cannot enable a SQLite storage backend on an existing, deployed Durable Object class. Automatic migration of deployed classes from their key-value storage backend to SQLite storage backend will be available in the future.
During the initial beta, Storage API billing is not enabled for Durable Object classes using SQLite storage backend. SQLite-backed Durable Objects will incur [charges for requests and duration](https://developers.cloudflare.com/durable-objects/platform/pricing/#billing-metrics). We plan to enable Storage API billing for Durable Objects using SQLite storage backend in the first half of 2025 after advance notice with the following [pricing](https://developers.cloudflare.com/durable-objects/platform/pricing/#sqlite-storage-backend).
## 2024-09-07
**New error message for overloaded Durable Objects**
Introduced a new overloaded error message for Durable Objects: "Durable Object is overloaded. Too many requests for the same object within a 10 second window."
This error message does not replace other types of overload messages that you may encounter for your Durable Object, and is only returned at more extreme levels of overload.
## 2024-06-24
[Exceptions](https://developers.cloudflare.com/durable-objects/best-practices/error-handling) thrown from Durable Object internal operations and tunneled to the caller may now be populated with a `.retryable: true` property if the exception was likely due to a transient failure, or populated with an `.overloaded: true` property if the exception was due to [overload](https://developers.cloudflare.com/durable-objects/observability/troubleshooting/#durable-object-is-overloaded).
## 2024-04-03
**Durable Objects support for Oceania region**
Durable Objects can reside in Oceania, lowering Durable Objects request latency for eyeball Workers in Oceania locations.
Refer to [Durable Objects](https://developers.cloudflare.com/durable-objects/reference/data-location/#provide-a-location-hint) to provide location hints to objects.
## 2024-04-01
**Billing reduction for WebSocket messages**
Durable Objects [request billing](https://developers.cloudflare.com/durable-objects/platform/pricing/#billing-metrics) applies a 20:1 ratio for incoming WebSocket messages. For example, 1 million Websocket received messages across connections would be charged as 50,000 Durable Objects requests.
This is a billing-only calculation and does not impact Durable Objects [metrics and analytics](https://developers.cloudflare.com/durable-objects/observability/metrics-and-analytics/).
## 2024-02-15
**Optional \`alarmInfo\` parameter for Durable Object Alarms**
Durable Objects [Alarms](https://developers.cloudflare.com/durable-objects/api/alarms/) now have a new `alarmInfo` argument that provides more details about an alarm invocation, including the `retryCount` and `isRetry` to signal if the alarm was retried.
---
title: Tutorials · Cloudflare Durable Objects docs
description: View tutorials to help you get started with Durable Objects.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/tutorials/
md: https://developers.cloudflare.com/durable-objects/tutorials/index.md
---
View tutorials to help you get started with Durable Objects.
| Name | Last Updated | Difficulty |
| - | - | - |
| [Build a seat booking app with SQLite in Durable Objects](https://developers.cloudflare.com/durable-objects/tutorials/build-a-seat-booking-app/) | over 1 year ago | Intermediate |
| [Deploy a Browser Rendering Worker with Durable Objects](https://developers.cloudflare.com/browser-rendering/workers-bindings/browser-rendering-with-do/) | over 2 years ago | Beginner |
| [Deploy a real-time chat application](https://developers.cloudflare.com/workers/tutorials/deploy-a-realtime-chat-app/) | over 2 years ago | Intermediate |
---
title: Videos · Cloudflare Durable Objects docs
lastUpdated: 2025-03-12T13:36:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/durable-objects/video-tutorials/
md: https://developers.cloudflare.com/durable-objects/video-tutorials/index.md
---
[Introduction to Durable Objects ](https://developers.cloudflare.com/learning-paths/durable-objects-course/series/introduction-to-series-1/)Dive into a hands-on Durable Objects project and learn how to build stateful apps using serverless architecture
---
title: 404 - Page Not Found · Cloudflare Email Routing docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/404/
md: https://developers.cloudflare.com/email-routing/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API reference · Cloudflare Email Routing docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/api-reference/
md: https://developers.cloudflare.com/email-routing/api-reference/index.md
---
---
title: Email Workers · Cloudflare Email Routing docs
description: With Email Workers you can leverage the power of Cloudflare Workers
to implement any logic you need to process your emails and create complex
rules. These rules determine what happens when you receive an email.
lastUpdated: 2025-05-05T15:05:59.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/email-workers/
md: https://developers.cloudflare.com/email-routing/email-workers/index.md
---
With Email Workers you can leverage the power of Cloudflare Workers to implement any logic you need to process your emails and create complex rules. These rules determine what happens when you receive an email.
Creating your own rules with Email Workers is as easy or complex as you want. You can begin using one of the starter templates that are pre-populated with code for popular use-cases. These templates allow you to create a blocklist, allowlist, or send notifications to Slack.
If you prefer, you can skip the templates and use custom code. You can, for example, create logic that only accepts messages from a specific address, and then forwards them to one or more of your verified email addresses, while also alerting you on Slack.
The following is an example of an allowlist Email Worker:
```js
export default {
async email(message, env, ctx) {
const allowList = ["friend@example.com", "coworker@example.com"];
if (allowList.indexOf(message.from) == -1) {
message.setReject("Address not allowed");
} else {
await message.forward("inbox@corp");
}
},
};
```
Refer to the [Workers Languages](https://developers.cloudflare.com/workers/languages/) for more information regarding the languages you can use with Workers.
## How to use Email Workers
To use Email Routing with Email Workers there are three steps involved:
1. Creating the Email Worker.
2. Adding the logic to your Email Worker (like email addresses allowed or blocked from sending you emails).
3. Binding the Email Worker to a route. This is the email address that forwards emails to the Worker.
The route, or email address, bound to the Worker forwards emails to your Email Worker. The logic in the Worker will then decide if the email is forwarded to its final destination or dropped, and what further actions (if any) will be applied.
For example, say that you create an allowlist Email Worker and bind it to a `hello@my-company.com` route. This route will be the email address you share with the world, to make sure that only email addresses on your allowlist are forwarded to your destination address. All other emails will be dropped.
## Resources
* [Limits](https://developers.cloudflare.com/email-routing/limits/#email-workers-size-limits)
* [Runtime API](https://developers.cloudflare.com/email-routing/email-workers/runtime-api/)
* [Local development](https://developers.cloudflare.com/email-routing/email-workers/local-development/)
---
title: Get started · Cloudflare Email Routing docs
description: To enable Email Routing, start by creating a custom email address
linked to a destination address or Email Worker. This forms an email rule. You
can enable or disable rules from the Cloudflare dashboard. Refer to Enable
Email Routing for more details.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/get-started/
md: https://developers.cloudflare.com/email-routing/get-started/index.md
---
To enable Email Routing, start by creating a custom email address linked to a destination address or Email Worker. This forms an **email rule**. You can enable or disable rules from the Cloudflare dashboard. Refer to [Enable Email Routing](https://developers.cloudflare.com/email-routing/get-started/enable-email-routing) for more details.
Custom addresses you create with Email Routing work as forward addresses only. Emails sent to custom addresses are forwarded by Email Routing to your destination inbox. Cloudflare does not process outbound email, and does not have an SMTP server.
The first time you access Email Routing, you will see a wizard guiding you through the process of creating email rules. You can skip the wizard and add rules manually.
If you need to pause Email Routing or offboard to another service, refer to [Disable Email Routing](https://developers.cloudflare.com/email-routing/setup/disable-email-routing/).
* [Enable Email Routing](https://developers.cloudflare.com/email-routing/get-started/enable-email-routing/)
* [Test Email Routing](https://developers.cloudflare.com/email-routing/get-started/test-email-routing/)
* [Analytics](https://developers.cloudflare.com/email-routing/get-started/email-routing-analytics/)
* [Audit logs](https://developers.cloudflare.com/email-routing/get-started/audit-logs/)
---
title: GraphQL examples · Cloudflare Email Routing docs
lastUpdated: 2026-01-20T12:56:28.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/graphql-example/
md: https://developers.cloudflare.com/email-routing/graphql-example/index.md
---
---
title: Limits · Cloudflare Email Routing docs
description: When you process emails with Email Workers and you are on Workers’
free pricing tier you might encounter an allocation error. This may happen due
to the size of the emails you are processing and/or the complexity of your
Email Worker. Refer to Worker limits for more information.
lastUpdated: 2024-09-29T02:03:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/limits/
md: https://developers.cloudflare.com/email-routing/limits/index.md
---
## Email Workers size limits
When you process emails with Email Workers and you are on [Workers’ free pricing tier](https://developers.cloudflare.com/workers/platform/pricing/) you might encounter an allocation error. This may happen due to the size of the emails you are processing and/or the complexity of your Email Worker. Refer to [Worker limits](https://developers.cloudflare.com/workers/platform/limits/#worker-limits) for more information.
You can use the [log functionality for Workers](https://developers.cloudflare.com/workers/observability/logs/) to look for messages related to CPU limits (such as `EXCEEDED_CPU`) and troubleshoot any issues regarding allocation errors.
If you encounter these error messages frequently, consider upgrading to the [Workers Paid plan](https://developers.cloudflare.com/workers/platform/pricing/) for higher usage limits.
## Message size
Currently, Email Routing does not support messages bigger than 25 MiB.
## Rules and addresses
| Feature | Limit |
| - | - |
| [Rules](https://developers.cloudflare.com/email-routing/setup/email-routing-addresses/) | 200 |
| [Addresses](https://developers.cloudflare.com/email-routing/setup/email-routing-addresses/#destination-addresses) | 200 |
Need a higher limit?
To request an adjustment to a limit, complete the [Limit Increase Request Form](https://forms.gle/ukpeZVLWLnKeixDu7). If the limit can be increased, Cloudflare will contact you with next steps.
## Email Routing summary for emails sent through Workers
Emails sent through Workers will show up in the Email Routing summary page as dropped even if they were successfully delivered.
---
title: Postmaster · Cloudflare Email Routing docs
description: Reference page with postmaster information for professionals, as
well as a known limitations section.
lastUpdated: 2025-07-21T21:33:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/postmaster/
md: https://developers.cloudflare.com/email-routing/postmaster/index.md
---
This page provides technical information about Email Routing to professionals who administer email systems, and other email providers.
Here you will find information regarding Email Routing, along with best practices, rules, guidelines, troubleshooting tools, as well as known limitations for Email Routing.
## Postmaster
### Authenticated Received Chain (ARC)
Email Routing supports [Authenticated Received Chain (ARC)](http://arc-spec.org/). ARC is an email authentication system designed to allow an intermediate email server (such as Email Routing) to preserve email authentication results. Google also supports ARC.
### Contact information
The best way to contact us is using our [community forum](https://community.cloudflare.com/new-topic?category=Feedback/Previews%20%26%20Betas\&tags=email) or our [Discord server](https://discord.com/invite/cloudflaredev).
### DKIM signature
[DKIM (DomainKeys Identified Mail)](https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail) ensures that email messages are not altered in transit between the sender and the recipient's SMTP servers through public-key cryptography.
Through this standard, the sender publishes its public key to a domain's DNS once, and then signs the body of each message before it leaves the server. The recipient server reads the message, gets the domain public key from the domain's DNS, and validates the signature to ensure the message was not altered in transit.
Email Routing adds two new signatures to the emails in transit, one on behalf of the Cloudflare domain used for sender rewriting `email.cloudflare.net`, and another one on behalf of the customer's recipient domain.
Below is the DKIM key for `email.cloudflare.net`:
```sh
dig TXT cf2024-1._domainkey.email.cloudflare.net +short
```
```sh
"v=DKIM1; h=sha256; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAiweykoi+o48IOGuP7GR3X0MOExCUDY/BCRHoWBnh3rChl7WhdyCxW3jgq1daEjPPqoi7sJvdg5hEQVsgVRQP4DcnQDVjGMbASQtrY4WmB1VebF+RPJB2ECPsEDTpeiI5ZyUAwJaVX7r6bznU67g7LvFq35yIo4sdlmtZGV+i0H4cpYH9+3JJ78k" "m4KXwaf9xUJCWF6nxeD+qG6Fyruw1Qlbds2r85U9dkNDVAS3gioCvELryh1TxKGiVTkg4wqHTyHfWsp7KD3WQHYJn0RyfJJu6YEmL77zonn7p2SRMvTMP3ZEXibnC9gz3nnhR6wcYL8Q7zXypKTMD58bTixDSJwIDAQAB"
```
You can find the DKIM key for the customer's `example.com` domain by querying the following:
```sh
dig TXT cf2024-1._domainkey.example.com +short
```
### DMARC enforcing
Email Routing enforces Domain-based Message Authentication, Reporting & Conformance (DMARC). Depending on the sender's DMARC policy, Email Routing will reject emails when there is an authentication failure. Refer to [dmarc.org](https://dmarc.org/) for more information on this protocol. It is recommended that all senders implement the DMARC protocol in order to successfully deliver email to Cloudflare.
### Mail authentication requirement
Cloudflare requires emails to [pass some form of authentication](https://developers.cloudflare.com/changelog/2025-06-30-mail-authentication/), either pass SPF verification or be correctly DKIM-signed to forward them. Having DMARC configured will also have a positive impact and is recommended.
### IPv6 support
Currently, Email Routing will connect to the upstream SMTP servers using IPv6 if they provide AAAA records for their MX servers, and fall back to IPv4 if that is not possible.
Below is an example of a popular provider that supports IPv6:
```sh
dig mx gmail.com
```
```sh
gmail.com. 3084 IN MX 5 gmail-smtp-in.l.google.com.
gmail.com. 3084 IN MX 20 alt2.gmail-smtp-in.l.google.com.
gmail.com. 3084 IN MX 40 alt4.gmail-smtp-in.l.google.com.
gmail.com. 3084 IN MX 10 alt1.gmail-smtp-in.l.google.com.
gmail.com. 3084 IN MX 30 alt3.gmail-smtp-in.l.google.com.
```
```sh
dig AAAA gmail-smtp-in.l.google.com
```
```sh
gmail-smtp-in.l.google.com. 17 IN AAAA 2a00:1450:400c:c09::1b
```
Email Routing also supports IPv6 through Cloudflare’s inbound MX servers.
### MX, SPF, and DKIM records
Email Routing automatically adds a few DNS records to the zone when our customers enable Email Routing. If we take `example.com` as an example:
```txt
example.com. 300 IN MX 13 amir.mx.cloudflare.net.
example.com. 300 IN MX 86 linda.mx.cloudflare.net.
example.com. 300 IN MX 24 isaac.mx.cloudflare.net.
example.com. 300 IN TXT "v=spf1 include:_spf.mx.cloudflare.net ~all"
```
[The MX (mail exchange) records](https://www.cloudflare.com/learning/dns/dns-records/dns-mx-record/) tell the Internet where the inbound servers receiving email messages for the zone are. In this case, anyone who wants to send an email to `example.com` can use the `amir.mx.cloudflare.net`, `linda.mx.cloudflare.net`, or `isaac.mx.cloudflare.net` SMTP servers.
### Outbound prefixes
Email Routing sends its traffic using both IPv4 and IPv6 prefixes, when supported by the upstream SMTP server.
If you are a postmaster and are having trouble receiving Email Routing's emails, allow the following outbound IP addresses in your server configuration:
**IPv4**
`104.30.0.0/19`
**IPv6**
`2405:8100:c000::/38`
*Ranges last updated: December 13th, 2023*
### Outbound hostnames
In addition to the outbound prefixes, Email Routing will use the following outbound domains for the `HELO/EHLO` command:
* `cloudflare-email.net`
* `cloudflare-email.org`
* `cloudflare-email.com`
PTR records (reverse DNS) ensure that each hostname has an corresponding IP. For example:
```sh
dig a-h.cloudflare-email.net +short
```
```sh
104.30.0.7
```
```sh
dig -x 104.30.0.7 +short
```
```sh
a-h.cloudflare-email.net.
```
### Sender rewriting
Email Routing rewrites the SMTP envelope sender (`MAIL FROM`) to the forwarding domain to avoid issues with [SPF](#spf-record). Email Routing uses the [Sender Rewriting Scheme](https://en.wikipedia.org/wiki/Sender_Rewriting_Scheme) to achieve this.
This has no effect to the end user's experience, though. The message headers will still report the original sender's `From:` address.
### SMTP errors
In most cases, Email Routing forwards the upstream SMTP errors back to the sender client in-session.
### Realtime Block Lists
Email Routing uses an internal Domain Name System Blocklists (DNSBL) service to check if the sender's IP is present in one or more Realtime Block Lists (RBL) lists. When the system detects an abusive IP, it blocks the email and returns an SMTP error:
```txt
554 found on one or more RBLs (abusixip). Refer to https://developers.cloudflare.com/email-routing/postmaster/#spam-and-abusive-traffic/
```
We update our RBLs regularly. You can use combined block list lookup services like [MxToolbox](https://mxtoolbox.com/blacklists.aspx) to check if your IP matches other RBLs. IP reputation blocks are usually temporary, but if you feel your IP should be removed immediately, please contact the RBL's maintainer mentioned in the SMTP error directly.
### Anti-spam
In addition to DNSBL, Email Routing uses advanced heuristic and statistical analysis of the email's headers and text to calculate a spam score. We inject the score in the custom `X-Cf-Spamh-Score` header:
```plaintext
X-Cf-Spamh-Score: 2
```
This header is visible in the forwarded email. The higher the score, 5 being the maximum, the more likely the email is spam. Currently, this system is experimental and passive; we do not act on it and suggest that upstream servers and email clients don't act on it either.
We will update this page with more information as we fine-tune the system.
### SPF record
A SPF DNS record is an anti-spoofing mechanism that is used to specify which IP addresses and domains are allowed to send emails on behalf of your zone.
The Internet Engineering Task Force (IETF) tracks the SPFv1 specification [in RFC 7208](https://datatracker.ietf.org/doc/html/rfc7208). Refer to the [SPF Record Syntax](http://www.open-spf.org/SPF_Record_Syntax/) to learn the SPF syntax.
Email Routing's SPF record contains the following:
```txt
v=spf1 include:_spf.mx.cloudflare.net ~all
```
In the example above:
* `spf1`: Refers to SPF version 1, the most common and more widely adopted version of SPF.
* `include`: Include a second query to `_spf.mx.cloudflare.net` and allow its contents.
* `~all`: Otherwise [`SoftFail`](http://www.open-spf.org/SPF_Record_Syntax/) on all other origins. `SoftFail` means NOT allowed to send, but in transition. This instructs the upstream server to accept the email but mark it as suspicious if it came from any IP addresses outside of those defined in the SPF records.
If we do a TXT query to `_spf.mx.cloudflare.net`, we get:
```txt
_spf.mx.cloudflare.net. 300 IN TXT "v=spf1 ip4:104.30.0.0/20 ~all"
```
This response means:
* Allow all IPv4 IPs coming from the `104.30.0.0/20` subnet.
* Otherwise, `SoftFail`.
You can read more about SPF, DKIM, and DMARC in our [Tackling Email Spoofing and Phishing](https://blog.cloudflare.com/tackling-email-spoofing/) blog.
***
## Known limitations
Below, you will find information regarding known limitations for Email Routing.
### Email address internationalization (EAI)
Email Routing does not support [internationalized email addresses](https://en.wikipedia.org/wiki/International_email). Email Routing only supports [internationalized domain names](https://en.wikipedia.org/wiki/Internationalized_domain_name).
This means that you can have email addresses with an internationalized domain, but not an internationalized local-part (the first part of your email address, before the `@` symbol). Refer to the following examples:
* `info@piñata.es` - Supported.
* `piñata@piñata.es` - Not supported.
### Non-delivery reports (NDRs)
Email Routing does not forward non-delivery reports to the original sender. This means the sender will not receive a notification indicating that the email did not reach the intended destination.
### Restrictive DMARC policies can make forwarded emails fail
Due to the nature of email forwarding, restrictive DMARC policies might make forwarded emails fail to be delivered. Refer to [dmarc.org](https://dmarc.org/wiki/FAQ#My_users_often_forward_their_emails_to_another_mailbox.2C_how_do_I_keep_DMARC_valid.3F) for more information.
### Sending or replying to an email from your Cloudflare domain
Email Routing does not support sending or replying from your Cloudflare domain. When you reply to emails forwarded by Email Routing, the reply will be sent from your destination address (like `my-name@gmail.com`), not your custom address (like `info@my-company.com`).
### "`.`" is treated as normal characters for custom addresses
The `.` character, which perform special actions in email providers like Gmail, is treated as a normal character on custom addresses.
---
title: Setup · Cloudflare Email Routing docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/setup/
md: https://developers.cloudflare.com/email-routing/setup/index.md
---
* [Configure rules and addresses](https://developers.cloudflare.com/email-routing/setup/email-routing-addresses/)
* [DNS records](https://developers.cloudflare.com/email-routing/setup/email-routing-dns-records/)
* [Disable Email Routing](https://developers.cloudflare.com/email-routing/setup/disable-email-routing/)
* [Configure MTA-STS](https://developers.cloudflare.com/email-routing/setup/mta-sts/)
* [Subdomains](https://developers.cloudflare.com/email-routing/setup/subdomains/)
---
title: Troubleshooting · Cloudflare Email Routing docs
description: Email Routing warns you when your DNS records are not properly
configured. In Email Routing's Overview page, you will see a message
explaining what type of problem your account's DNS records have.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-routing/troubleshooting/
md: https://developers.cloudflare.com/email-routing/troubleshooting/index.md
---
Email Routing warns you when your DNS records are not properly configured. In Email Routing's **Overview** page, you will see a message explaining what type of problem your account's DNS records have.
Refer to Email Routing's **Settings** tab on the dashboard for more information. Email Routing will list missing DNS records or warn you about duplicate sender policy framework (SPF) records, for example.
* [DNS records](https://developers.cloudflare.com/email-routing/troubleshooting/email-routing-dns-records/)
* [SPF records](https://developers.cloudflare.com/email-routing/troubleshooting/email-routing-spf-records/)
---
title: 404 - Page Not Found · Cloudflare Email security (formerly Area 1) docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/404/
md: https://developers.cloudflare.com/email-security/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Account setup · Cloudflare Email security (formerly Area 1) docs
lastUpdated: 2024-12-17T15:27:22.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/email-security/account-setup/
md: https://developers.cloudflare.com/email-security/account-setup/index.md
---
* [Manage account members](https://developers.cloudflare.com/email-security/account-setup/manage-account-members/)
* [Escalation contacts](https://developers.cloudflare.com/email-security/account-setup/escalation-contacts/)
* [Manage parent permissions](https://developers.cloudflare.com/email-security/account-setup/manage-parent-permissions/)
* [SSO integration](https://developers.cloudflare.com/email-security/account-setup/sso/)
* [Permissions](https://developers.cloudflare.com/email-security/account-setup/permissions/)
---
title: API · Cloudflare Email security (formerly Area 1) docs
description: Email security offers Application Programming Interfaces (APIs) to
expose our phishing campaign rulesets. These APIs both aid research and
provide a set of indicators to block using network security edge devices.
lastUpdated: 2025-10-27T15:00:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/api/
md: https://developers.cloudflare.com/email-security/api/index.md
---
Area 1 has been renamed
Area 1 is now **Email Security (formerly Area 1)**.
Access to Area 1
Beginning October 1, 2025, access and support for Email Security (formerly Area 1) will only be available through the Cloudflare dashboard. Your Email Security protection will not change, but you will no longer be able to access the Area 1 dashboard or send support requests to `@area1security.com` email addresses. For help accessing the Cloudflare dashboard, reach out to .
Email security offers Application Programming Interfaces (APIs) to expose our phishing campaign rulesets. These APIs both aid research and provide a set of indicators to block using network security edge devices.
All API requests are initiated using normal HTTP requests (`GET`/`POST`/`DELETE`) and responses are returned in JSON. Authentication to the APIs uses HTTP Basic Authentication over HTTPS.
For more details, refer to our [API documentation (PDF)](https://developers.cloudflare.com/email-security/static/api_documentation_1.38.1.pdf).
---
title: Setup · Cloudflare Email security (formerly Area 1) docs
description: "When you configure Email Security (formerly Area 1) Email Security
to protect your organization, you can choose between two main setup
architectures: Inline and API."
lastUpdated: 2025-08-29T19:00:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/deployment/
md: https://developers.cloudflare.com/email-security/deployment/index.md
---
Access to Area 1
Beginning October 1, 2025, access and support for Email Security (formerly Area 1) will only be available through the Cloudflare dashboard. Your Email Security protection will not change, but you will no longer be able to access the Area 1 dashboard or send support requests to `@area1security.com` email addresses. For help accessing the Cloudflare dashboard, reach out to .
When you configure Email Security (formerly Area 1) Email Security to protect your organization, you can choose between two main setup architectures: Inline and API.
With an Inline deployment, Email Security evaluates email messages before they reach a user’s inbox. When you choose an API deployment, email messages only reach Email Security after they have already reached a user’s inbox.
Select a deployment method to get started.
* [Inline](https://developers.cloudflare.com/email-security/deployment/inline/)
* [API](https://developers.cloudflare.com/email-security/deployment/api/)
---
title: Email configuration · Cloudflare Email security (formerly Area 1) docs
description: Once you have set up Email security, you have several options to
customize and fine-tune email behavior.
lastUpdated: 2025-10-27T15:00:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/email-configuration/
md: https://developers.cloudflare.com/email-security/email-configuration/index.md
---
Area 1 has been renamed
Area 1 is now **Email Security (formerly Area 1)**.
Access to Area 1
Beginning October 1, 2025, access and support for Email Security (formerly Area 1) will only be available through the Cloudflare dashboard. Your Email Security protection will not change, but you will no longer be able to access the Area 1 dashboard or send support requests to `@area1security.com` email addresses. For help accessing the Cloudflare dashboard, reach out to .
Once you have [set up Email security](https://developers.cloudflare.com/email-security/deployment/), you have several options to customize and fine-tune email behavior.
* [Domains and routing](https://developers.cloudflare.com/email-security/email-configuration/domains-and-routing/)
* [Email policies](https://developers.cloudflare.com/email-security/email-configuration/email-policies/)
* [Allow and block lists](https://developers.cloudflare.com/email-security/email-configuration/lists/)
* [Enhanced detections](https://developers.cloudflare.com/email-security/email-configuration/enhanced-detections/)
* [Retract settings](https://developers.cloudflare.com/email-security/email-configuration/retract-settings/)
* [Phish submissions](https://developers.cloudflare.com/email-security/email-configuration/phish-submissions/)
* [Admin Quarantine](https://developers.cloudflare.com/email-security/email-configuration/admin-quarantine/)
---
title: Glossary · Cloudflare Email security (formerly Area 1) docs
description: Review the definitions for terms used across Email security
(formerly Area 1) documentation.
lastUpdated: 2025-10-27T15:00:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/glossary/
md: https://developers.cloudflare.com/email-security/glossary/index.md
---
Review the definitions for terms used across Email security (formerly Area 1) documentation.
| Term | Definition |
| - | - |
| attribute | Traffic that flows through Area 1 can receive one or more attributes, which indicate that a specific condition has been met. |
| disposition | Represents Area 1's evaluation of a specific message. For example, after evaluating an email it may get a disposition of `malicious`. Email messages with this disposition exhibit characteristics typical of malicious emails. |
| phishing | The practice of trying to acquire sensitive data through fraudulent emails or other means. Usually, the perpetrators try to pass for a legitimate company when asking for sensitive data. |
| SMTP | Stands for Simple Mail Transfer Protocol. It is an Internet standard based on TCP/IP to send and receive email. |
---
title: Migrate to Email security · Cloudflare Email security (formerly Area 1) docs
description: This page aims at showing you how to perform Area 1 actions in Zero
Trust Email security, and new terminology introduced in Email security.
lastUpdated: 2025-12-15T12:02:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/migrate-to-email-security/
md: https://developers.cloudflare.com/email-security/migrate-to-email-security/index.md
---
This page aims at showing you how to perform Area 1 actions in [Zero Trust Email security](https://developers.cloudflare.com/cloudflare-one/email-security/), and new terminology introduced in Email security.
Note
Your Area 1 data and configuration settings are available in Email security.
Access to Area 1
Beginning October 1, 2025, access and support for Email Security (formerly Area 1) will only be available through the Cloudflare dashboard. Your Email Security protection will not change, but you will no longer be able to access the Area 1 dashboard or send support requests to `@area1security.com` email addresses. For help accessing the Cloudflare dashboard, reach out to .
## Contact support
In Area 1, you can reach out to support via the following email addresses:
*
* (for PhishGuard customers only)
In Email security, you can raise a ticket by contacting [technical support](https://dash.cloudflare.com/?to=/:account/support) on the Cloudflare dashboard:
1. Select your account and choose **Technical support**.
2. In **Solve your issue**, answer the following questions:
* What type of question do you have? Select **Technical - Other Products**
* In what area can we help you? Select **Email security**
* What feature, service or problem is this related to? Choose among **Configuration**, **Detections** or **PhishGuard**.
## Invite users
In Area 1, you [invite users](https://developers.cloudflare.com/email-security/account-setup/manage-account-members/#add-user) by logging in to the Area 1 portal and inviting members.
To invite users in Zero Trust Email security:
1. Log in to [Cloudflare One](https://one.dash.cloudflare.com/).
2. Go to **Manage Account**.
3. Select **Members** > **Invite** > [Add account members](https://developers.cloudflare.com/fundamentals/manage-members/manage/#add-account-members).
Once you have added new account members, you will have to assign each member an [Email security role](https://developers.cloudflare.com/cloudflare-one/roles-permissions/#email-security-roles).
| Area 1 | Email security | Description |
| - | - | - |
| N/A | Cloudflare Zero Trust | Can edit Cloudflare [Zero Trust](https://developers.cloudflare.com/cloudflare-one/). Has administrator access to all Zero Trust products including Access, Gateway, WARP, Tunnel, Browser Isolation, CASB, DLP, DEX, and Email security. |
| Super Admin | Email security Analyst + Email security Configuration Admin = Super Admin | Has full access to all admin features in Email security |
| Configuration Admin | Email security Configuration Admin | Has administrator access. Cannot take actions on emails, or read emails |
| SOC Analyst | Email security Analyst | Has analyst access. Can take action on emails and read emails. |
| Viewer | Email security Reporting | Can read metrics |
| N/A | Cloudflare Zero Trust PII | Can read PII in Zero Trust (this includes Email security) |
| N/A | Email security Policy Admin | Can read all settings, but only write allow policies, trusted domains, and blocked senders |
## Create webhooks
Note
Starting from October 1, 2025, Area 1 webhooks will be visible in Zero Trust Email security, but non-configurable. Use [Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-user-action-logs) to create new webhooks or configure webhooks.
In Area 1, you can [create alert webhooks](https://developers.cloudflare.com/email-security/email-configuration/domains-and-routing/alert-webhooks/#create-an-alert-webhook).
In Zero Trust Email security, webhooks are instead referred to as logs. You can enable [detection logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-detection-logs) and/or [user action logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-user-action-logs). Additionally, you can enable [Outbound Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/email-security/outbound-dlp/) to protect sensitive information in outbound emails.
## Set up system alerts
You can check the Area 1 and Email security status in the [Cloudflare System Status](https://www.cloudflarestatus.com/).
To view Area 1 status:
* Search for **Email security (Area1)** and check that the status is set to **Operational**. This means that emails are being processed.
* Search for **Area 1 - Dash** to check the status of the Area 1 dashboard.
* Search for **Area 1 - API** to check the status of the API endpoints.
To view Email security status:
* Search for **Email security (Zero Trust)** and check that the status is set to **Operational**. This means that emails are being processed.
* Search for **Zero Trust Dashboard** to check the status of the Zero Trust dashboard.
* Search for **API** to check the status of the API endpoints.
You can also check the status of APIs through the [Cloudflare Status API](https://www.cloudflarestatus.com/api) and configure [Cloudflare Notifications](https://developers.cloudflare.com/notifications/get-started/#configure-notifications).
## Email reports
Note
Starting from October 1, 2025, weekly and daily email reports will no longer be available. Go to [Monitoring](https://developers.cloudflare.com/cloudflare-one/email-security/monitoring/) in Email security to monitor your inbox.
In Area 1, you receive daily or weekly updates of the number of emails dispositioned.
In Email security, you can view [email monitoring](https://developers.cloudflare.com/cloudflare-one/email-security/monitoring/) over the last 90, 30, 7, 3, 1 day(s).
## Email alerts for detections
Note
Starting from October 1, 2025, emails alerts for detections will no longer be available. As an alternative, use [Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-detection-logs).
In Area 1, you receive an email when an email is assigned a disposition.
In Email security, you enable [Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-detection-logs) to enable detection logs.
## Search emails
In Area 1, you can perform two types of search: [Fielded Search](https://developers.cloudflare.com/email-security/reporting/search/#fielded-search) and [Freeform Search](https://developers.cloudflare.com/email-security/reporting/search/#freeform-search).
In Email security, the ability to search emails has been expanded. You can use three different [screen criteria](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#screen-criteria) to search emails:
* [Advanced screen](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#advanced-screen)
* [Regular screen](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#regular-screen)
* [Popular screen](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#popular-screen)
## Check metrics
In Area 1, you can check [statistics](https://developers.cloudflare.com/email-security/reporting/statistics-overview/) in your Home section.
In Email security, you can check your metrics in the [Monitoring](https://developers.cloudflare.com/cloudflare-one/email-security/monitoring/) section in the dashboard.
## Move messages to a specific folder
Area 1 allows you to set up [message retraction](https://developers.cloudflare.com/email-security/email-configuration/retract-settings/) to move messages to specific folders. This is known as **retraction**.
Moving messages to a specific folder is known as [auto-moves](https://developers.cloudflare.com/cloudflare-one/email-security/settings/auto-moves/) in Zero Trust Email security.
## Create policies
This table displays the difference in terminology used when creating policies:
| Area 1 | Email security |
| - | - |
| [Allowed patterns](https://developers.cloudflare.com/email-security/email-configuration/lists/allowed-patterns/) | [Allow policies](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/allow-policies/) |
| [Block lists](https://developers.cloudflare.com/email-security/email-configuration/lists/block-list/) | [Blocked senders](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/blocked-senders/) |
| [Trusted domains](https://developers.cloudflare.com/email-security/email-configuration/lists/trusted-domains/) | [Trusted domains](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/trusted-domains/) |
| [Text add-ons](https://developers.cloudflare.com/email-security/email-configuration/email-policies/text-addons/) | [Text add-ons](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/configure-text-add-ons/) |
| [Link actions](https://developers.cloudflare.com/email-security/email-configuration/email-policies/link-actions/) | [Link actions](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/configure-link-actions/) |
| [Added detections](https://developers.cloudflare.com/email-security/email-configuration/enhanced-detections/added-detections/) | [Additional detections](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/additional-detections/) |
## Submissions
This table displays the difference in terminology used when finding emails whose disposition is incorrect:
| Area 1 | Email security |
| - | - |
| Report [false negative](https://developers.cloudflare.com/email-security/email-configuration/phish-submissions/#false-negatives)/[false positive](https://developers.cloudflare.com/email-security/email-configuration/phish-submissions/#false-positives) | [Submit messages for review](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/#submit-messages-for-review) |
| N/A | Escalate user submissions |
| [Team submission](https://developers.cloudflare.com/email-security/email-configuration/phish-submissions/#how-to-submit-phish) | [Team submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/team-submissions/) |
| [User submission](https://developers.cloudflare.com/email-security/email-configuration/phish-submissions/#how-to-submit-phish) | [User submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/user-submissions/) |
## Business Email Compromise
In Area 1, you can set up a [Business email compromise (BEC)](https://developers.cloudflare.com/email-security/email-configuration/enhanced-detections/business-email-compromise/) list to protect against attackers who try to impersonate executives.
In Email security, this feature is known as [impersonation registry](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/impersonation-registry/).
## Synchronize directories
In Area 1, you can [integrate directories](https://developers.cloudflare.com/email-security/email-configuration/enhanced-detections/business-email-compromise/#integrating-a-directory) in your email provider.
In Email security, you can add and sync [directories](https://developers.cloudflare.com/cloudflare-one/email-security/directories/).
## API
Note
Area 1 API endpoints will deprecate on December 18, 2025. Use the [Email security API](https://developers.cloudflare.com/api/resources/email_security/) endpoints to prevent interruption to your normal operations.
To access Area 1 API, go to the [API Documentation](https://developers.cloudflare.com/email-security/static/api_documentation_1.38.1.pdf). You can set up a [service account](https://developers.cloudflare.com/email-security/api/service-accounts/) to configure API tokens.
To access Email security API, go to [Email security API](https://developers.cloudflare.com/api/resources/email_security/). You can set up an [API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) to use the Email security API.
---
title: Channel and Alliance Partners · Cloudflare Email security (formerly Area
1) docs
description: Email security Channel and Alliance partners have the option to set
up accounts for themselves and their customers.
lastUpdated: 2025-10-27T15:00:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/partners/
md: https://developers.cloudflare.com/email-security/partners/index.md
---
Area 1 has been renamed
Area 1 is now **Email Security (formerly Area 1)**.
Access to Area 1
Beginning October 1, 2025, access and support for Email Security (formerly Area 1) will only be available through the Cloudflare dashboard. Your Email Security protection will not change, but you will no longer be able to access the Area 1 dashboard or send support requests to `@area1security.com` email addresses. For help accessing the Cloudflare dashboard, reach out to .
Email security Channel and Alliance partners have the option to set up accounts for themselves and their customers.
## Create accounts
Start by creating parent and child accounts.
### Create a parent account
Parent accounts are treated as containers with no services provisioned. User accounts created at the parent level will allow them to access any child account.
Note
This is only required for administrators that manage multiple accounts. For example, Managed Security Service Providers (MSSP) managing multiple customer accounts.
1. Log in to the [Email security dashboard](https://horizon.area1security.com/).
2. Go to **Settings** (the gear icon).
3. In **Delegated Accounts** > **Accounts**, select **Create new customer**.
4. Enter their information, and make sure you select *Parent* in **Account Type**.
5. Select **Save**.
Your newly created account should show up in the list. If not, refresh the page.
### Create a child account
1. Log in to the [Email security dashboard](https://horizon.area1security.com/).
2. Go to **Settings** (the gear icon).
3. In **Delegated Accounts** > **Accounts**, select the parent account where you want to create a child account.
4. Select **Create New customer**.
5. Enter their information, and make sure you select *Advantage* in **Account Type**.
6. Scroll down to the **Email Traffic Related Information** section, and enter the information related to your email provider. The number to enter in **Loopback Hops** will depend on your email configuration and where Email security is in the chain of events. Refer to [Inline deployment](https://developers.cloudflare.com/email-security/deployment/inline/) and [API deployment](https://developers.cloudflare.com/email-security/deployment/api/) for more information.
7. For **Daily Email Volume** and **Number of Email Users** make sure you enter the appropriate values for your organization.
8. Select **Save**.
## Create users and assign permissions
You can create users at both the parent and child account level. Users created at parent level will have access to all its child accounts. Users created at child level will only have access to the assigned child account.
Child accounts can [limit or disable](https://developers.cloudflare.com/email-security/account-setup/manage-parent-permissions/) the level of access allowed from their parent account.
If you modify the Delegated Access controls, make sure you create an administrator account in the child first.
To create an account at parent level or child level:
1. Log in to the [Email Security (formerly Area 1) dashboard](https://horizon.area1security.com/) with a parent account or child account depending on what you are trying to create.
2. Go to **Settings** (the gear icon).
3. Go to **Users and Actions**.
4. Select **Add User**.
5. Enter their information, as well as their [**Permission** level](https://developers.cloudflare.com/email-security/account-setup/permissions/).
6. Select **Send Invitation**.
## Escalation contacts
You should add escalation contacts so Email security can send notifications regarding detection events and critical service related issues. Email security highly recommends that these contacts have both phone and email contacts.
Refer to [Escalation contacts](https://developers.cloudflare.com/email-security/account-setup/escalation-contacts/) for more information.
## Status alerts
Subscribe to incident status alerts [from Email security](https://status.area1security.com/).
## Domains setup (inline/API)
Refer to the [setup options](https://developers.cloudflare.com/email-security/deployment/) for Email security to learn about the best way of deploying Email security in your organization. You can choose between two main setup architectures:
* Inline deployment
* API deployment
With an [inline deployment](https://developers.cloudflare.com/email-security/deployment/inline/), Email security evaluates email messages before they reach a user’s inbox. When you choose an [API deployment](https://developers.cloudflare.com/email-security/deployment/api/), email messages only reach Email security after they have already reached a user’s inbox.
## Classification actions
Email security recommends that you quarantine `MALICIOUS` and `SPAM` dispositions. You can configure this directly in [Office 365](https://developers.cloudflare.com/email-security/deployment/inline/setup/office-365-area1-mx/) and [Gsuite](https://developers.cloudflare.com/email-security/deployment/inline/setup/gsuite-area1-mx/), as well as [Email security](https://developers.cloudflare.com/email-security/email-configuration/domains-and-routing/domains/).
## Message retraction
You can configure message retraction to take post-delivery actions against suspicious email messages. You can retract messages manually or automatically. Refer to [Retract settings](https://developers.cloudflare.com/email-security/email-configuration/retract-settings/) for more information.
## TLS enforcement for domains
To add additional TLS requirements for emails coming from certain domains, you can enforce higher levels of SSL/TLS inspection. Refer to [Partner Domains TLS](https://developers.cloudflare.com/email-security/email-configuration/domains-and-routing/partner-domains-tls/) for more information.
## Reports
You can subscribe to [daily and weekly email reports](https://horizon.area1security.com/settings/subscriptions/email-subscriptions), as well as [SIEM events](https://horizon.area1security.com/settings/email/routing/webhooks). For SIEM events, you will need to [configure your SIEM tool](https://developers.cloudflare.com/email-security/reporting/siem-integration/) into Email security first.
## Whitelisting and blocklisting senders
If you need to whitelist of blocklist senders, refer to [Allow and block lists](https://developers.cloudflare.com/email-security/email-configuration/lists/).
## Submitting false positives and false negatives
There are several ways of dealing with missed phish or messages flagged as such that are not. Refer to [Phish submissions](https://developers.cloudflare.com/email-security/email-configuration/phish-submissions/) to learn more.
## Best practices
Refer to the following pages to learn more:
1. [Business Email compromise (BEC)](https://developers.cloudflare.com/email-security/email-configuration/enhanced-detections/business-email-compromise/)
2. [Text add-ons](https://developers.cloudflare.com/email-security/email-configuration/email-policies/text-addons/)
3. [Search and reports](https://developers.cloudflare.com/email-security/reporting/)
---
title: Reference · Cloudflare Email security (formerly Area 1) docs
lastUpdated: 2024-12-17T15:27:22.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/email-security/reference/
md: https://developers.cloudflare.com/email-security/reference/index.md
---
* [How we detect phish](https://developers.cloudflare.com/email-security/reference/how-we-detect-phish/)
* [Dispositions and attributes](https://developers.cloudflare.com/email-security/reference/dispositions-and-attributes/)
* [Timestamps](https://developers.cloudflare.com/email-security/reference/timestamps/)
* [MS Office 365 GCC](https://developers.cloudflare.com/email-security/reference/office365-gcc/)
* [Cloudflare SSO](https://developers.cloudflare.com/email-security/reference/cloudflare-sso/)
* [Language support](https://developers.cloudflare.com/email-security/reference/language-support/)
---
title: Reporting · Cloudflare Email security (formerly Area 1) docs
description: "Email security offers a variety of ways for you to better examine
and understand your message traffic:"
lastUpdated: 2025-10-27T15:00:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/email-security/reporting/
md: https://developers.cloudflare.com/email-security/reporting/index.md
---
Area 1 has been renamed
Area 1 is now **Email Security (formerly Area 1)**.
Access to Area 1
Beginning October 1, 2025, access and support for Email Security (formerly Area 1) will only be available through the Cloudflare dashboard. Your Email Security protection will not change, but you will no longer be able to access the Area 1 dashboard or send support requests to `@area1security.com` email addresses. For help accessing the Cloudflare dashboard, reach out to .
Email security offers a variety of ways for you to better examine and understand your message traffic:
* [Phish reports](https://developers.cloudflare.com/email-security/reporting/phish-reports/)
* [Audit Logs](https://developers.cloudflare.com/email-security/reporting/audit-logs/)
* [Statistics overview](https://developers.cloudflare.com/email-security/reporting/statistics-overview/)
* [Types of malicious detections](https://developers.cloudflare.com/email-security/reporting/types-malicious-detections/)
* [Search](https://developers.cloudflare.com/email-security/reporting/search/)
* [SIEM integration](https://developers.cloudflare.com/email-security/reporting/siem-integration/)
- The [Email security API](https://developers.cloudflare.com/email-security/api/) also allows you to download historical records as needed.
Note
Timestamps in the dashboard of Email security (formerly Area 1) are localized to your timezone. Email security reads this information from the clock of your computer when you log in.
---
title: 404 - Page Not Found · Cloudflare Firewall Rules (deprecated) docs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/firewall/404/
md: https://developers.cloudflare.com/firewall/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Manage firewall rules via the APIs · Cloudflare Firewall Rules
(deprecated) docs
description: Cloudflare offers APIs that work together to achieve the same
effect as the UI-based Firewall rules feature under Security > WAF.
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/firewall/api/
md: https://developers.cloudflare.com/firewall/api/index.md
---
Cloudflare offers APIs that work together to achieve the same effect as the UI-based **Firewall rules** feature under **Security** > **WAF**.
Deprecation notice
Cloudflare Firewall Rules has been deprecated. Cloudflare has moved existing firewall rules to [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/). For more information on this change, refer to the [upgrade guide](https://developers.cloudflare.com/waf/reference/legacy/firewall-rules-upgrade/).
These APIs are the following:
* [**Firewall Rules API**](https://developers.cloudflare.com/firewall/api/cf-firewall-rules/): Manage firewall rules and their actions, based on criteria separately defined through filters.
* [**Filters API**](https://developers.cloudflare.com/firewall/api/cf-filters/): Manage the filters that enable rule matching.
* [**Lists API**](https://developers.cloudflare.com/waf/tools/lists/lists-api/): Manage named lists of items (such as IP addresses) that you can use in the rules of different Cloudflare products.
---
title: Manage firewall rules in the Cloudflare dashboard · Cloudflare Firewall
Rules (deprecated) docs
description: To configure firewall rules in the Cloudflare dashboard, open
Firewall rules in Security > WAF.
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/firewall/cf-dashboard/
md: https://developers.cloudflare.com/firewall/cf-dashboard/index.md
---
To configure firewall rules in the Cloudflare dashboard, open **Firewall rules** in **Security** > **WAF**.
Deprecation notice
Cloudflare Firewall Rules has been deprecated. Cloudflare has moved existing firewall rules to [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/). For more information on this change, refer to the [upgrade guide](https://developers.cloudflare.com/waf/reference/legacy/firewall-rules-upgrade/).
As depicted in the image below, the **Firewall rules** dashboard interface lets you:
* View the list of existing rules, both enabled and disabled.
* [Create, edit, and delete](https://developers.cloudflare.com/firewall/cf-dashboard/create-edit-delete-rules/) firewall rules.
* Enable or disable rules.
* Search and filter the list of existing rules.
* Reorder firewall rules when using [list ordering](https://developers.cloudflare.com/firewall/cf-firewall-rules/order-priority/#managing-rule-evaluation-by-list-order).

---
title: About Cloudflare Firewall Rules · Cloudflare Firewall Rules (deprecated) docs
description: Cloudflare Firewall Rules is a flexible and intuitive framework for
filtering HTTP requests. It gives you fine-grained control over which requests
reach your applications, proactively inspecting incoming site traffic and
automatically responding to threats.
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/firewall/cf-firewall-rules/
md: https://developers.cloudflare.com/firewall/cf-firewall-rules/index.md
---
Cloudflare Firewall Rules is a flexible and intuitive framework for filtering HTTP requests. It gives you fine-grained control over which requests reach your applications, proactively inspecting incoming site traffic and automatically responding to threats.
Deprecation notice
Cloudflare Firewall Rules has been deprecated. Cloudflare has moved existing firewall rules to [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/). For more information on this change, refer to the [upgrade guide](https://developers.cloudflare.com/waf/reference/legacy/firewall-rules-upgrade/).
In a firewall rule you define an [expression](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/) that tells Cloudflare what to look for in a request, and specify the appropriate [action](https://developers.cloudflare.com/firewall/cf-firewall-rules/actions/) to take when those conditions are met. Expressions can reference [IP lists](https://developers.cloudflare.com/waf/tools/lists/custom-lists/#ip-lists) - groups of IP addresses that you can reference collectively by name.
To write firewall rule expressions, use the [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/), a powerful expression language inspired in the Wireshark Display Filter language.
---
title: Troubleshooting · Cloudflare Firewall Rules (deprecated) docs
description: The following topics are useful for troubleshooting firewall issues.
lastUpdated: 2024-12-12T14:55:48.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/firewall/troubleshooting/
md: https://developers.cloudflare.com/firewall/troubleshooting/index.md
---
The following topics are useful for troubleshooting firewall issues.
* [Required firewall rule changes to enable URL normalization](https://developers.cloudflare.com/firewall/troubleshooting/required-changes-to-enable-url-normalization/)
---
title: 404 - Page Not Found · Cloudflare Fundamentals docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/fundamentals/404/
md: https://developers.cloudflare.com/fundamentals/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Accounts · Cloudflare Fundamentals docs
description: "If you need help setting up a new Cloudflare account, refer to the
following resources:"
lastUpdated: 2025-05-29T18:16:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/fundamentals/account/
md: https://developers.cloudflare.com/fundamentals/account/index.md
---
If you need help setting up a new Cloudflare account, refer to the following resources:
* [Change Super Administrator](https://developers.cloudflare.com/fundamentals/account/change-super-admin/)
* [Create account](https://developers.cloudflare.com/fundamentals/account/create-account/)
* [Account security](https://developers.cloudflare.com/fundamentals/account/account-security/)
* [Find account and zone IDs](https://developers.cloudflare.com/fundamentals/account/find-account-and-zone-ids/)
---
title: Cloudflare's API · Cloudflare Fundamentals docs
description: "Use the following resources to learn more about Cloudflare's REST API:"
lastUpdated: 2025-07-11T20:30:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/fundamentals/api/
md: https://developers.cloudflare.com/fundamentals/api/index.md
---
Use the following resources to learn more about Cloudflare's REST API:
* [Get started](https://developers.cloudflare.com/fundamentals/api/get-started/)
* [How to](https://developers.cloudflare.com/fundamentals/api/how-to/)
* [Reference](https://developers.cloudflare.com/fundamentals/api/reference/)
* [Troubleshooting](https://developers.cloudflare.com/fundamentals/api/troubleshooting/)
---
title: Concepts · Cloudflare Fundamentals docs
lastUpdated: 2024-10-31T11:42:05.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/fundamentals/concepts/
md: https://developers.cloudflare.com/fundamentals/concepts/index.md
---
* [How Cloudflare DNS works](https://developers.cloudflare.com/fundamentals/concepts/how-cloudflare-works/)
* [Traffic flow through Cloudflare](https://developers.cloudflare.com/fundamentals/concepts/traffic-flow-cloudflare/)
* [Accounts, zones, and profiles](https://developers.cloudflare.com/fundamentals/concepts/accounts-and-zones/)
* [Cloudflare IP addresses](https://developers.cloudflare.com/fundamentals/concepts/cloudflare-ip-addresses/)
---
title: Get started · Cloudflare Fundamentals docs
description: Before you can begin using Cloudflare products, first create an account.
lastUpdated: 2025-09-08T19:30:16.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/fundamentals/get-started/
md: https://developers.cloudflare.com/fundamentals/get-started/index.md
---
Before you can begin using Cloudflare products, first [create an account](https://developers.cloudflare.com/fundamentals/account/create-account/).
## Learn about Cloudflare's offerings
### Build
**Build** is where developers create and deploy simple sites and full-stack applications on the [Workers compute platform](https://developers.cloudflare.com/workers/), and connect them to storage and database primitives like [KV](https://developers.cloudflare.com/kv/) (key-value data store), [D1](https://developers.cloudflare.com/d1/) (SQL database), [R2](https://developers.cloudflare.com/r2/) (object storage), [Queues](https://developers.cloudflare.com/queues/) (asynchronous messaging), [Durable Objects](https://developers.cloudflare.com/durable-objects/) (stateful coordination), and more.
Our compute, orchestration, AI, storage, media, and security services are integrated, so you can quickly extend existing apps or launch new ones while Cloudflare's global network takes care of infrastructure, scaling, and performance for you.
### Protect & Connect
**Protect & Connect** is where you establish fast and reliable connections between your websites, apps, and users, while protecting them from attackers and unwanted traffic.
Application security and performance focuses on resources available on the public Internet. Manage delivery performance by controlling and speeding up primarily [Layer 7 (Application) traffic](https://developers.cloudflare.com/fundamentals/reference/network-layers/), in addition to managing media such as video and images. Get started by [onboarding a domain](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/).
Zero Trust protects private, internal users/devices and the resources they access. [Get started with Zero Trust](https://developers.cloudflare.com/cloudflare-one/setup/).
Network services extend protection and acceleration to cloud, on-premise, or hybrid networks, and you can also manage network connections and optimize Layer 3 (Network) and 4 (Transport) traffic. Get started with [Magic Transit](https://developers.cloudflare.com/magic-transit/) or [Magic WAN](https://developers.cloudflare.com/magic-wan/).
---
title: Domains · Cloudflare Fundamentals docs
description: A domain or domain name (also known as a zone) is the location of a
website or application, or what an end user types into their browser to get to
your website (example.com).
lastUpdated: 2025-09-11T15:54:36.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/fundamentals/manage-domains/
md: https://developers.cloudflare.com/fundamentals/manage-domains/index.md
---
A *domain* or *domain name* (also known as a *zone*) is the location of a website or application, or what an end user types into their browser to get to your website (`example.com`).
## Get a domain name
You can purchase domain names for your website from a variety of places. Cloudflare offers an at-cost registrar service to [purchase new domain names](https://developers.cloudflare.com/registrar/get-started/register-domain/) or [transfer existing domain names](https://developers.cloudflare.com/registrar/get-started/transfer-domain-to-cloudflare/).
Refer to [Account and domain management best practices](https://developers.cloudflare.com/fundamentals/reference/best-practices/) for a detailed list of ways to protect your account and domain.
## Host your domain
A web host keeps your website online so visitors can reach it via the domain name.
Cloudflare does not offer web hosting for most websites, though you can deploy and host JAMstack sites with [Cloudflare Pages](https://developers.cloudflare.com/pages/).
## Add a domain to Cloudflare
For help onboarding a domain to Cloudflare's CDN, refer to our [setup guide](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/).
You will need to [update your domain's nameservers](https://developers.cloudflare.com/dns/zone-setups/full-setup/) and [proxy](https://developers.cloudflare.com/dns/proxy-status/) your web traffic to benefit from caching, DDoS protection, Argo Smart Routing, and other [application security and performance products](https://developers.cloudflare.com/directory/?product-group=Application+performance%2CApplication+security).
## Get free SSL certificates
Cloudflare offers free, unshared, publicy trusted [Universal SSL certificates](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/) to all Cloudflare domains.
## Manage subdomains
For more details about subdomains (`www.example.com` or `blog.example.com`), refer to [Manage subdomains](https://developers.cloudflare.com/fundamentals/manage-domains/manage-subdomains/).
---
title: Account members · Cloudflare Fundamentals docs
description: On any Cloudflare account, you can collaborate by adding members to
your account and assigning them access via one or several policies.
lastUpdated: 2025-09-16T14:55:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/fundamentals/manage-members/
md: https://developers.cloudflare.com/fundamentals/manage-members/index.md
---
On any Cloudflare account, you can collaborate by adding members to your account and assigning them access via one or several policies.
Every policy has three parts:
1. The actor
2. The role
3. The scope
Refer to the resources below to configure policies to ensure that you can assign only the necessary access permissions to your account members.
## Resources
* [Set up dashboard SSO](https://developers.cloudflare.com/fundamentals/manage-members/dashboard-sso/)
* [Manage](https://developers.cloudflare.com/fundamentals/manage-members/manage/)
* [Policies](https://developers.cloudflare.com/fundamentals/manage-members/policies/)
* [Roles](https://developers.cloudflare.com/fundamentals/manage-members/roles/)
* [Role scopes](https://developers.cloudflare.com/fundamentals/manage-members/scope/)
* [User Groups](https://developers.cloudflare.com/fundamentals/manage-members/user-groups/)
---
title: RSS Feeds · Cloudflare Fundamentals docs
description: Cloudflare offers several RSS feeds to help you consume content
programatically.
lastUpdated: 2025-07-22T13:55:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/fundamentals/new-features/
md: https://developers.cloudflare.com/fundamentals/new-features/index.md
---
Cloudflare offers several RSS feeds to help you consume content programatically.
* [Available RSS Feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)
* [Consuming RSS Feeds](https://developers.cloudflare.com/fundamentals/new-features/consuming-rss-feeds/)
---
title: Organizations · Cloudflare Fundamentals docs
description: Cloudflare Organizations simplify the way you manage multiple
accounts, domains (also known as zones), and teams by centralizing this
information in one location. You can also share configurations between
accounts and view aggregate analytics.
lastUpdated: 2025-10-22T21:11:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/fundamentals/organizations/
md: https://developers.cloudflare.com/fundamentals/organizations/index.md
---
Cloudflare Organizations simplify the way you manage multiple accounts, domains (also known as zones), and teams by centralizing this information in one location. You can also share configurations between accounts and view aggregate analytics.
Note
Cloudflare Organizations is currently in closed beta.
## Create an Organization
1. Log in to the [Cloudflare dashboard.](https://dash.cloudflare.com)
2. Select **Organizations**.
3. From the **Organizations** page, select **Create organization**.
4. Enter a name for the organization and select **Create**. The organization overview page displays.
Note
Users can only create one organization.
## Organization Overview
From the Organization overview, you can view which accounts are assigned to your organization. After you assign an account, you can view the account, copy an account's ID, or rename the account.
### Assign an account to an organization
After you create an organization, determine which accounts will be assigned to the organization.
1. From **Organization Overview**, select **Assign an account**. The list displays Enterprise accounts where you are listed as a Super Administrator.
2. In the text field, search for the account name and select it.
3. When you are done, select **Assign to organization**. The organization overview page displays with the newly assigned account.
Note
To remove an account from your organization, contact your Cloudflare account team.
## Analytics & Logs
Review incoming HTTP traffic for all domains connected to Cloudflare through your organization. The data includes traffic for proxied hostnames, does not reflect your billable usage, and may be based on an adaptive sample.
You can also view specific data associated with your HTTP traffic by adding optional filters. You can also choose to print a report of your data or download the data.
## Shared Configurations
Create and enforce global policies across your organization or sub-organization with [WAF Custom Rulesets](https://developers.cloudflare.com/waf/custom-rules/) and [Gateway policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/).
By utilizing shared configurations, you can define a WAF custom ruleset that can apply to one or more accounts to be managed in a single place.
## Manage Organization
Rename your organization and add or edit customer identification data related to the organization.
### Rename an organization
1. Select **Organizations** > **Manage Organization**.
2. From **Organization name**, select **Rename**.
3. Enter the new name for the organization and select **Rename**.
### Edit customer identification data
1. Select **Organizations** > **Manage Organization**.
2. From **Customer identification data**, select **Edit**.
3. Enter the information in the text fields and select **Save**.
---
title: Performance · Cloudflare Fundamentals docs
lastUpdated: 2025-05-29T18:16:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/fundamentals/performance/
md: https://developers.cloudflare.com/fundamentals/performance/index.md
---
* [Improve SEO](https://developers.cloudflare.com/fundamentals/performance/improve-seo/)
* [Maintenance mode](https://developers.cloudflare.com/fundamentals/performance/maintenance-mode/)
* [Minimize downtime](https://developers.cloudflare.com/fundamentals/performance/minimize-downtime/)
* [Optimize site speed](https://developers.cloudflare.com/speed/)
* [Prepare for surges or spikes in web traffic](https://developers.cloudflare.com/learning-paths/surge-readiness/concepts/)
* [Test speed](https://developers.cloudflare.com/fundamentals/performance/test-speed/)
---
title: Reference - Get started · Cloudflare Fundamentals docs
lastUpdated: 2025-05-29T18:16:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/fundamentals/reference/
md: https://developers.cloudflare.com/fundamentals/reference/index.md
---
* [/cdn-cgi/ endpoint](https://developers.cloudflare.com/fundamentals/reference/cdn-cgi-endpoint/)
* [Account and domain management best practices](https://developers.cloudflare.com/fundamentals/reference/best-practices/)
* [Cloudflare and Google Analytics](https://developers.cloudflare.com/fundamentals/reference/google-analytics/)
* [Cloudflare crawlers](https://developers.cloudflare.com/fundamentals/reference/cloudflare-site-crawling/)
* [Cloudflare HTTP headers](https://developers.cloudflare.com/fundamentals/reference/http-headers/)
* [Cloudflare Ray ID](https://developers.cloudflare.com/fundamentals/reference/cloudflare-ray-id/)
* [Cloudy AI agent (beta)](https://developers.cloudflare.com/fundamentals/reference/cloudy-ai-agent/)
* [Connection limits](https://developers.cloudflare.com/fundamentals/reference/connection-limits/)
* [Cryptographic Attestation of Personhood](https://developers.cloudflare.com/fundamentals/reference/cryptographic-personhood/)
* [Glossary](https://developers.cloudflare.com/fundamentals/reference/glossary/)
* [Network Layers](https://developers.cloudflare.com/fundamentals/reference/network-layers/)
* [Network ports](https://developers.cloudflare.com/fundamentals/reference/network-ports/)
* [Partners](https://developers.cloudflare.com/fundamentals/reference/partners/)
* [Redirects](https://developers.cloudflare.com/fundamentals/reference/redirects/)
* [Scans and penetration testing policy](https://developers.cloudflare.com/fundamentals/reference/scans-penetration/)
* [Policies](https://developers.cloudflare.com/fundamentals/reference/policies-compliances/)
* [Abuse](https://developers.cloudflare.com/fundamentals/reference/report-abuse/)
* [SDK ecosystem support policy](https://developers.cloudflare.com/fundamentals/reference/sdk-ecosystem-support-policy/)
* [TCP connections](https://developers.cloudflare.com/fundamentals/reference/tcp-connections/)
* [Migration guides](https://developers.cloudflare.com/fundamentals/reference/migration-guides/)
* [Troubleshooting](https://developers.cloudflare.com/fundamentals/reference/troubleshooting/)
* [Under Attack mode](https://developers.cloudflare.com/fundamentals/reference/under-attack-mode/)
---
title: Security · Cloudflare Fundamentals docs
lastUpdated: 2025-05-29T18:16:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/fundamentals/security/
md: https://developers.cloudflare.com/fundamentals/security/index.md
---
* [Prevent DDoS attacks](https://developers.cloudflare.com/learning-paths/prevent-ddos-attacks/concepts/)
* [Protect your origin server](https://developers.cloudflare.com/fundamentals/security/protect-your-origin-server/)
* [Recovering from a hacked site](https://developers.cloudflare.com/fundamentals/security/recovering-from-hacked-site/)
* [Scan for PCI compliance](https://developers.cloudflare.com/fundamentals/security/pci-scans/)
* [Secure your website](https://developers.cloudflare.com/learning-paths/application-security/account-security/)
* [Under a DDoS attack?](https://developers.cloudflare.com/fundamentals/security/under-ddos-attack/)
---
title: User profiles · Cloudflare Fundamentals docs
description: Each user has a profile that contains several settings, such as
Communication preferences and Language preferences.
lastUpdated: 2025-08-20T18:47:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/fundamentals/user-profiles/
md: https://developers.cloudflare.com/fundamentals/user-profiles/index.md
---
Each user has a profile that contains several settings, such as [Communication preferences](https://developers.cloudflare.com/fundamentals/user-profiles/customize-account/#notifications) and [Language preferences](https://developers.cloudflare.com/fundamentals/user-profiles/customize-account/#language).
To access your profile, select the user icon and then **My Profile** from any page within the [Cloudflare dashboard](https://dash.cloudflare.com).
---
title: Improved detection capabilities · Changelog
description: WAF attack score now detects Base64 and Unicode escapes.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-05-23-improved-detection-capabilities/
md: https://developers.cloudflare.com/changelog/2024-05-23-improved-detection-capabilities/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved detection capabilities
May 23, 2024
[WAF](https://developers.cloudflare.com/waf/)
[WAF attack score](https://developers.cloudflare.com/waf/detections/attack-score/) now automatically detects and decodes Base64 and JavaScript (Unicode escape sequences) in HTTP requests. This update is available for all customers with access to WAF attack score (Business customers with access to a single field and Enterprise customers).
---
title: Explore product updates for Cloudflare One · Changelog
description: New changelog format for Cloudflare One
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-06-16-cloudflare-one/
md: https://developers.cloudflare.com/changelog/2024-06-16-cloudflare-one/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Explore product updates for Cloudflare One
Jun 16, 2024
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Browser Isolation ](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)[CASB ](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)[Cloudflare Tunnel ](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)[Digital Experience Monitoring ](https://developers.cloudflare.com/cloudflare-one/insights/dex/)[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[Email security ](https://developers.cloudflare.com/cloudflare-one/email-security/)[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Magic Cloud Networking ](https://developers.cloudflare.com/magic-cloud-networking/)[Magic Firewall ](https://developers.cloudflare.com/magic-firewall/)[Magic Network Monitoring ](https://developers.cloudflare.com/magic-network-monitoring/)[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Network Interconnect ](https://developers.cloudflare.com/network-interconnect/)[Risk Score ](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
Welcome to your new home for product updates on [Cloudflare One](https://developers.cloudflare.com/cloudflare-one/).
Our [new changelog](https://developers.cloudflare.com/changelog/) lets you read about changes in much more depth, offering in-depth examples, images, code samples, and even gifs.
If you are looking for older product updates, refer to the following locations.
Older product updates
* [Access](https://developers.cloudflare.com/cloudflare-one/changelog/access/)
* [Browser Isolation](https://developers.cloudflare.com/cloudflare-one/changelog/browser-isolation/)
* [CASB](https://developers.cloudflare.com/cloudflare-one/changelog/casb/)
* [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/changelog/tunnel/)
* [Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/changelog/dlp/)
* [Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/changelog/dex/)
* [Email security](https://developers.cloudflare.com/cloudflare-one/changelog/email-security/)
* [Gateway](https://developers.cloudflare.com/cloudflare-one/changelog/gateway/)
* [Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/changelog/)
* [Magic Firewall](https://developers.cloudflare.com/magic-firewall/changelog/)
* [Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/changelog/)
* [Magic Transit](https://developers.cloudflare.com/magic-transit/changelog/)
* [Magic WAN](https://developers.cloudflare.com/magic-wan/changelog/)
* [Network Interconnect](https://developers.cloudflare.com/network-interconnect/changelog/)
* [Risk score](https://developers.cloudflare.com/cloudflare-one/changelog/risk-score/)
* [Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/changelog/warp/)
---
title: Exchange user risk scores with Okta · Changelog
description: Okta risk exchange
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-06-17-okta-risk-exchange/
md: https://developers.cloudflare.com/changelog/2024-06-17-okta-risk-exchange/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Exchange user risk scores with Okta
Jun 17, 2024
[Risk Score](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)
Beyond the controls in [Zero Trust](https://developers.cloudflare.com/cloudflare-one/), you can now [exchange user risk scores](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/risk-score/#send-risk-score-to-okta) with Okta to inform SSO-level policies.
First, configure Cloudflare One to send user risk scores to Okta.
1. Set up the [Okta SSO integration](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/okta/).
2. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Integrations** > **Identity providers**.
3. In **Your identity providers**, locate your Okta integration and select **Edit**.
4. Turn on **Send risk score to Okta**.
5. Select **Save**.
6. Upon saving, Cloudflare One will display the well-known URL for your organization. Copy the value.
Next, configure Okta to receive your risk scores.
1. On your Okta admin dashboard, go to **Security** > **Device Integrations**.
2. Go to **Receive shared signals**, then select **Create stream**.
3. Name your integration. In **Set up integration with**, choose *Well-known URL*.
4. In **Well-known URL**, enter the well-known URL value provided by Cloudflare One.
5. Select **Create**.
---
title: Regionalized Generic Tiered Cache for higher hit ratios · Changelog
description: Generic Global Tiered Cache now hashes content within a region's
data centers to reduce duplication and increase cache efficiency.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-07-19-regionalized-generic-tiered-cache/
md: https://developers.cloudflare.com/changelog/2024-07-19-regionalized-generic-tiered-cache/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Regionalized Generic Tiered Cache for higher hit ratios
Jul 19, 2024
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now achieve higher cache hit ratios with [Generic Global Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#generic-global-tiered-cache). Regional content hashing routes content consistently to the same upper-tier data centers, eliminating redundant caching and reducing origin load.
#### How it works
Regional content hashing groups data centers by region and uses consistent hashing to route content to designated upper-tier caches:
* Same content always routes to the same upper-tier data center within a region.
* Eliminates redundant copies across multiple upper-tier caches.
* Increases the likelihood of cache HITs for the same content.
#### Example
A popular image requested from multiple edge locations in a region:
* **Before**: Cached at 3-4 different upper-tier data centers
* **After**: Cached at 1 designated upper-tier data center
* **Result**: 3-4x fewer cache MISSes, reducing origin load and improving performance
#### Get started
To get started, enable [Generic Global Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#generic-global-tiered-cache) on your zone.
---
title: Fixed occasional attack score mismatches · Changelog
description: Fixed mismatches between WAF attack score and subscores.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-08-29-fixed-occasional-attack-score-mismatches/
md: https://developers.cloudflare.com/changelog/2024-08-29-fixed-occasional-attack-score-mismatches/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Fixed occasional attack score mismatches
Aug 29, 2024
[WAF](https://developers.cloudflare.com/waf/)
Fixed an issue causing score mismatches between the global [WAF attack score](https://developers.cloudflare.com/waf/detections/attack-score/) and subscores. In certain cases, subscores were higher (not an attack) than expected while the global attack score was lower than expected (attack), leading to false positives.
---
title: One-click Cache Rules templates now available · Changelog
description: Pre-built templates in the Cloudflare dashboard make it easy to
create optimized cache rules instantly.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-09-05-cache-rules-templates/
md: https://developers.cloudflare.com/changelog/2024-09-05-cache-rules-templates/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## One-click Cache Rules templates now available
Sep 05, 2024
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now create optimized cache rules instantly with **one-click templates**, eliminating the complexity of manual rule configuration.
#### How it works
1. Navigate to **Rules** > **Templates** in your Cloudflare dashboard.
2. Select a template for your use case.
3. Click to apply the template with sensible defaults.
4. Customize as needed for your specific requirements.
#### Available cache templates
* **Cache everything**: Adjust the cache level for all requests.
* **Bypass cache for everything**: Bypass cache for all requests.
* **Cache default file extensions**: Replicate Page Rules caching behavior by making only default extensions eligible for cache.
* **Bypass cache on cookie**: Bypass cache for requests containing specific cookies.
* **Set edge cache time**: Cache responses with status code between 200 and 599 on the Cloudflare edge.
* **Set browser cache time**: Adjust how long a browser should cache a resource.
#### Get started
To get started, go to [**Rules > Templates**](https://dash.cloudflare.com/?to=/:account/:zone/caching/cache-rules) in the dashboard. For more information, refer to the [Cache Rules documentation](https://developers.cloudflare.com/cache/how-to/cache-rules/).
---
title: New Rules Templates for One-Click Rule Creation · Changelog
description: Quickly set up common rules with pre-built templates.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-09-05-rules-templates/
md: https://developers.cloudflare.com/changelog/2024-09-05-rules-templates/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Rules Templates for One-Click Rule Creation
Sep 05, 2024
[Rules](https://developers.cloudflare.com/rules/)
Now, you can create **common rule configurations** in just **one click** using Rules Templates.
What you can do:
* **Pick a pre-built rule** – Choose from a library of templates.
* **One-click setup** – Deploy best practices instantly.
* **Customize as needed** – Adjust templates to fit your setup.
Template cards are now also available directly in the rule builder for each product.
Need more ideas? Check out the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in our documentation.
---
title: AI Crawl Control · Changelog
description: AI Audit is available to all customers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-09-23-ai-audit-launch/
md: https://developers.cloudflare.com/changelog/2024-09-23-ai-audit-launch/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Crawl Control
Sep 23, 2024
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
Every site on Cloudflare now has access to [**AI Audit**](https://developers.cloudflare.com/ai-crawl-control/), which summarizes the crawling behavior of popular and known AI services.
You can use this data to:
* Understand how and how often crawlers access your site (and which content is the most popular).
* Block specific AI bots accessing your site.
* Use Cloudflare to enforce your `robots.txt` policy via an automatic WAF rule.

To get started, explore [AI audit](https://developers.cloudflare.com/ai-crawl-control/).
---
title: Try out Magic Network Monitoring · Changelog
description: The free version of Magic Network Monitoring is available to all customers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-09-24-magic-network-monitoring/
md: https://developers.cloudflare.com/changelog/2024-09-24-magic-network-monitoring/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Try out Magic Network Monitoring
Sep 24, 2024
[Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/)
The free version of Magic Network Monitoring (MNM) is now available to everyone with a Cloudflare account by default.
1. Log in to your [Cloudflare dashboard](https://dash.cloudflare.com), and select your account.
2. Go to **Analytics & Logs** > **Magic Monitoring**.

For more details, refer to the [Get started guide](https://developers.cloudflare.com/magic-network-monitoring/get-started/).
---
title: Eliminate long-lived credentials and enhance SSH security with Cloudflare
Access for Infrastructure · Changelog
description: Use short-lived SSH certificates and fine-grained policy to secure
access to your SSH servers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-10-01-ssh-with-access-for-infrastructure/
md: https://developers.cloudflare.com/changelog/2024-10-01-ssh-with-access-for-infrastructure/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Eliminate long-lived credentials and enhance SSH security with Cloudflare Access for Infrastructure
Oct 01, 2024
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
Organizations can now eliminate long-lived credentials from their SSH setup and enable strong multi-factor authentication for SSH access, similar to other Access applications, all while generating access and command logs.
SSH with [Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/non-http/infrastructure-apps/) uses short-lived SSH certificates from Cloudflare, eliminating SSH key management and reducing the security risks associated with lost or stolen keys. It also leverages a common deployment model for Cloudflare One customers: [WARP-to-Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-warp-to-tunnel/).
SSH with Access for Infrastructure enables you to:
* **Author fine-grained policy** to control who may access your SSH servers, including specific ports, protocols, and SSH users.
* **Monitor infrastructure access** with Access and SSH command logs, supporting regulatory compliance and providing visibility in case of security breach.
* **Preserve your end users' workflows.** SSH with Access for Infrastructure supports native SSH clients and does not require any modifications to users’ SSH configs.

To get started, refer to [SSH with Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/).
---
title: Search for custom rules using rule name and/or ID · Changelog
description: New UI improvements for Magic Firewall
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-10-02-custom-rule-search/
md: https://developers.cloudflare.com/changelog/2024-10-02-custom-rule-search/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Search for custom rules using rule name and/or ID
Oct 02, 2024
[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
The Magic Firewall dashboard now allows you to search custom rules using the rule name and/or ID.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Analytics & Logs** > **Network Analytics**.
3. Select **Magic Firewall**.
4. Add a filter for **Rule ID**.

Additionally, the rule ID URL link has been added to Network Analytics.
---
title: New fields added to Gateway-related datasets in Cloudflare Logs · Changelog
description: Cloudflare has introduced new fields to Gateway-related datasets in
Cloudflare Logs.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-10-08-new-gateway-fields/
md: https://developers.cloudflare.com/changelog/2024-10-08-new-gateway-fields/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New fields added to Gateway-related datasets in Cloudflare Logs
Oct 08, 2024
[Logs](https://developers.cloudflare.com/logs/)
Cloudflare has introduced new fields to two Gateway-related datasets in Cloudflare Logs:
* **Gateway HTTP**: `ApplicationIDs`, `ApplicationNames`, `CategoryIDs`, `CategoryNames`, `DestinationIPContinentCode`, `DestinationIPCountryCode`, `ProxyEndpoint`, `SourceIPContinentCode`, `SourceIPCountryCode`, `VirtualNetworkID`, and `VirtualNetworkName`.
* **Gateway Network**: `ApplicationIDs`, `ApplicationNames`, `DestinationIPContinentCode`, `DestinationIPCountryCode`, `ProxyEndpoint`, `SourceIPContinentCode`, `SourceIPCountryCode`, `TransportProtocol`, `VirtualNetworkID`, and `VirtualNetworkName`.
---
title: Simplified UI for URL Rewrites · Changelog
description: Set up wildcard-based URL rewrites faster with a new streamlined UI.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-10-23-url-rewrites-wildcard/
md: https://developers.cloudflare.com/changelog/2024-10-23-url-rewrites-wildcard/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Simplified UI for URL Rewrites
Oct 23, 2024
[Rules](https://developers.cloudflare.com/rules/)
It’s now easy to create **wildcard-based [URL Rewrites](https://developers.cloudflare.com/rules/transform/url-rewrite/)**. No need for complex functions—just define your patterns and go.

What’s improved:
* **Full wildcard support** – Create rewrite patterns using intuitive interface.
* **Simplified rule creation** – No need for complex functions.
Try it via [creating a Rewrite URL rule in the dashboard](https://developers.cloudflare.com/rules/transform/url-rewrite/create-dashboard/#wildcard-pattern-parameters).
---
title: Workflows is now in open beta · Changelog
description: Build long-running, reliable and durable applications on Cloudflare Workers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-10-24-workflows-beta/
md: https://developers.cloudflare.com/changelog/2024-10-24-workflows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workflows is now in open beta
Oct 24, 2024
[Workers ](https://developers.cloudflare.com/workers/)[Workflows](https://developers.cloudflare.com/workflows/)
Workflows is now in open beta, and available to any developer a free or paid Workers plan.
Workflows allow you to build multi-step applications that can automatically retry, persist state and run for minutes, hours, days, or weeks. Workflows introduces a programming model that makes it easier to build reliable, long-running tasks, observe as they progress, and programmatically trigger instances based on events across your services.
#### Get started
You can get started with Workflows by [following our get started guide](https://developers.cloudflare.com/workflows/get-started/guide/) and/or using `npm create cloudflare` to pull down the starter project:
```sh
npm create cloudflare@latest workflows-starter -- --template "cloudflare/workflows-starter"
```
You can open the `src/index.ts` file, extend it, and use `wrangler deploy` to deploy your first Workflow. From there, you can:
* Learn the [Workflows API](https://developers.cloudflare.com/workflows/build/workers-api/)
* [Trigger Workflows](https://developers.cloudflare.com/workflows/build/trigger-workflows/) via your Workers apps.
* Understand the [Rules of Workflows](https://developers.cloudflare.com/workflows/build/rules-of-workflows/) and how to adopt best practices
---
title: New table in Security Analytics and Security Events · Changelog
description: New responsive table in Security Analytics and Events.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-04-new-table-in-security-analytics-and-security-events/
md: https://developers.cloudflare.com/changelog/2024-11-04-new-table-in-security-analytics-and-security-events/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New table in Security Analytics and Security Events
Nov 04, 2024
[WAF](https://developers.cloudflare.com/waf/)
Switched to a new, more responsive table in Security Analytics and Security Events.
---
title: Stage and test cache configurations safely · Changelog
description: Cache now supports versioned environments for staging
configurations and purging staged content independently.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-07-cache-versioning/
md: https://developers.cloudflare.com/changelog/2024-11-07-cache-versioning/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Stage and test cache configurations safely
Nov 07, 2024
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now stage and test cache configurations before deploying them to production. Versioned environments let you safely validate cache rules, purge operations, and configuration changes without affecting live traffic.
#### How it works
With versioned environments, you can:
1. **Create staging versions** of your cache configuration.
2. **Test cache rules** in a non-production environment.
3. **Purge staged content** independently from production.
4. **Validate changes** before promoting to production.
This capability integrates with Cloudflare's broader [versioning system](https://developers.cloudflare.com/version-management/), allowing you to manage cache configurations alongside other zone settings.
#### Benefits
* **Risk-free testing**: Validate configuration changes without impacting production.
* **Independent purging**: Clear staging cache without affecting live content.
* **Deployment confidence**: Catch issues before they reach end users.
* **Team collaboration**: Multiple team members can work on different versions.
#### Get started
To get started, refer to the [version management documentation](https://developers.cloudflare.com/version-management/).
Important limitation
Cache Reserve is only supported for your production environment. Staged environments can use standard cache functionality, but Cache Reserve persistence is limited to production deployments.
---
title: Use Logpush for Email security user actions · Changelog
description: Send user action logs for Email security to an endpoint of your
choice with Cloudflare Logpush.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-07-logpush-user-actions/
md: https://developers.cloudflare.com/changelog/2024-11-07-logpush-user-actions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Use Logpush for Email security user actions
Nov 07, 2024
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You can now send user action logs for Email security to an endpoint of your choice with Cloudflare Logpush.
Filter logs matching specific criteria you have set or select from multiple fields you want to send. For all users, we will log the date and time, user ID, IP address, details about the message they accessed, and what actions they took.
When creating a new Logpush job, remember to select **Audit logs** as the dataset and filter by:
* **Field**: `"ResourceType"`
* **Operator**: `"starts with"`
* **Value**: `"email_security"`.

For more information, refer to [Enable user action logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-user-action-logs).
This feature is available across all Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Shard cache using custom cache key values · Changelog
description: Enterprise customers can now shard cache using previously
restricted accept*, referer, and user-agent headers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-07-shard-cache-by-cache-key/
md: https://developers.cloudflare.com/changelog/2024-11-07-shard-cache-by-cache-key/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Shard cache using custom cache key values
Nov 07, 2024
[Cache / CDN](https://developers.cloudflare.com/cache/)
Enterprise customers can now optimize cache hit ratios for content that varies by device, language, or referrer by **sharding cache** using up to ten values from previously restricted headers with [custom cache keys](https://developers.cloudflare.com/cache/how-to/cache-keys/).
#### How it works
When configuring [custom cache keys](https://developers.cloudflare.com/cache/how-to/cache-keys/), you can now include values from these headers to create distinct cache entries:
* **`accept*` headers** (for example, `accept`, `accept-encoding`, `accept-language`): Serve different cached versions based on content negotiation.
* **`referer` header**: Cache content differently based on the referring page or site.
* **`user-agent` header**: Maintain separate caches for different browsers, devices, or bots.
#### When to use cache sharding
* Content varies significantly by device type (mobile vs desktop).
* Different language or encoding preferences require distinct responses.
* Referrer-specific content optimization is needed.
#### Example configuration
```json
{
"cache_key": {
"custom_key": {
"header": {
"include": ["accept-language", "user-agent"],
"check_presence": ["referer"]
}
}
}
}
```
This configuration creates separate cache entries based on the `accept-language` and `user-agent` headers, while also considering whether the `referer` header is present.
#### Get started
To get started, refer to the [custom cache keys documentation](https://developers.cloudflare.com/cache/how-to/cache-keys/).
Note
While cache sharding can improve hit ratios for specific use cases, overly sharding your cache can reduce overall cache efficiency and negatively impact performance. Carefully evaluate whether sharding benefits your specific traffic patterns.
---
title: Bypass caching for subrequests made from Cloudflare Workers, with
Request.cache · Changelog
description: New runtime APIs allow you to control when subrequests are cached,
increasing compatibility with popular NPM packages
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-11-cache-no-store/
md: https://developers.cloudflare.com/changelog/2024-11-11-cache-no-store/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Bypass caching for subrequests made from Cloudflare Workers, with Request.cache
Nov 11, 2024
[Workers](https://developers.cloudflare.com/workers/)
You can now use the [`cache`](https://developers.cloudflare.com/workers/runtime-apis/request/#options) property of the [`Request`](https://developers.cloudflare.com/workers/runtime-apis/request/) interface to bypass [Cloudflare's cache](https://developers.cloudflare.com/workers/reference/how-the-cache-works/) when making subrequests from [Cloudflare Workers](https://developers.cloudflare.com/workers), by setting its value to `no-store`.
* JavaScript
```js
export default {
async fetch(req, env, ctx) {
const request = new Request("https://cloudflare.com", {
cache: "no-store",
});
const response = await fetch(request);
return response;
},
};
```
* TypeScript
```ts
export default {
async fetch(req, env, ctx): Promise {
const request = new Request("https://cloudflare.com", { cache: 'no-store'});
const response = await fetch(request);
return response;
}
} satisfies ExportedHandler
```
When you set the value to `no-store` on a subrequest made from a Worker, the Cloudflare Workers runtime will not check whether a match exists in the cache, and not add the response to the cache, even if the response includes directives in the `Cache-Control` HTTP header that otherwise indicate that the response is cacheable.
This increases compatibility with NPM packages and JavaScript frameworks that rely on setting the [`cache`](https://developers.cloudflare.com/workers/runtime-apis/request/#options) property, which is a cross-platform standard part of the [`Request`](https://developers.cloudflare.com/workers/runtime-apis/request/) interface. Previously, if you set the `cache` property on `Request`, the Workers runtime threw an exception.
If you've tried to use `@planetscale/database`, `redis-js`, `stytch-node`, `supabase`, `axiom-js` or have seen the error message `The cache field on RequestInitializerDict is not implemented in fetch` — you should try again, making sure that the [Compatibility Date](https://developers.cloudflare.com/workers/configuration/compatibility-dates/) of your Worker is set to on or after `2024-11-11`, or the [`cache_option_enabled` compatibility flag](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#enable-cache-no-store-http-standard-api) is enabled for your Worker.
* Learn [how the Cache works with Cloudflare Workers](https://developers.cloudflare.com/workers/reference/how-the-cache-works/)
* Enable [Node.js compatibility](https://developers.cloudflare.com/workers/runtime-apis/nodejs/) for your Cloudflare Worker
* Explore [Runtime APIs](https://developers.cloudflare.com/workers/runtime-apis/) and [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) available in Cloudflare Workers
---
title: Security Events pagination · Changelog
description: Fixed pagination and log count issues in Security Events.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-14-security-events-pagination/
md: https://developers.cloudflare.com/changelog/2024-11-14-security-events-pagination/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Security Events pagination
Nov 14, 2024
[WAF](https://developers.cloudflare.com/waf/)
Fixed an issue with pagination in Security Events' sampled logs where some pages were missing data. Also removed the total count from the events log as these are only sampled logs.
---
title: Smart Tiered Cache automatically optimizes R2 caching · Changelog
description: R2 storage buckets now automatically benefit from Smart Tiered
Cache with intelligent Upper Tier selection.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-20-smart-tiered-cache-for-r2/
md: https://developers.cloudflare.com/changelog/2024-11-20-smart-tiered-cache-for-r2/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Smart Tiered Cache automatically optimizes R2 caching
Nov 20, 2024
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now reduce latency and lower R2 egress costs automatically when using [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) with [R2](https://developers.cloudflare.com/r2/). Cloudflare intelligently selects a tiered data center close to your R2 bucket location, creating an efficient caching topology without additional configuration.
#### How it works
When you enable [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) for zones using [R2](https://developers.cloudflare.com/r2/) as an origin, Cloudflare automatically:
1. **Identifies your R2 bucket location**: Determines the geographical region where your R2 bucket is stored.
2. **Selects an optimal Upper Tier**: Chooses a data center close to your bucket as the common Upper Tier cache.
3. **Routes requests efficiently**: All cache misses in edge locations route through this Upper Tier before reaching R2.
#### Benefits
* **Automatic optimization**: No manual configuration required.
* **Lower egress costs**: Fewer requests to R2 reduce egress charges.
* **Improved hit ratio**: Common Upper Tier increases cache efficiency.
* **Reduced latency**: Upper Tier proximity to R2 minimizes fetch times.
#### Get started
To get started, enable [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) on your zone using R2 as an origin.
---
title: Improved non-English keyboard support · Changelog
description: Introduced support for non-English keyboard configurations in the
remote browser, enhancing the global user experience.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-21-non-english-keyboard/
md: https://developers.cloudflare.com/changelog/2024-11-21-non-english-keyboard/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved non-English keyboard support
Nov 21, 2024
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
You can now type in languages that use diacritics (like á or ç) and character-based scripts (such as Chinese, Japanese, and Korean) directly within the remote browser. The isolated browser now properly recognizes non-English keyboard input, eliminating the need to copy and paste content from a local browser or device.
---
title: Cloud Connector Now Supports R2 · Changelog
description: Cloud Connector now integrates with Cloudflare R2 for object storage.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-22-cloud-connector-r2/
md: https://developers.cloudflare.com/changelog/2024-11-22-cloud-connector-r2/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloud Connector Now Supports R2
Nov 22, 2024
[Rules](https://developers.cloudflare.com/rules/)
Now, you can use [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/) to route traffic to your [R2 buckets](https://developers.cloudflare.com/r2/) based on URLs, headers, geolocation, and more.
Example setup:
```bash
curl --request PUT \
"https://api.cloudflare.com/client/v4/zones/{zone_id}/cloud_connector/rules" \
--header "Authorization: Bearer " \
--header "Content-Type: application/json" \
--data '[
{
"expression": "http.request.uri.path wildcard \"/images/*\"",
"provider": "cloudflare_r2",
"description": "Connect to R2 bucket containing images",
"parameters": {
"host": "mybucketcustomdomain.example.com"
}
}
]'
```
Get started using [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/) documentation.
---
title: Find security misconfigurations in your AWS cloud environment · Changelog
description: CASB and DLP with Cloud Data Extraction for AWS cloud environments
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-11-22-cloud-data-extraction-aws/
md: https://developers.cloudflare.com/changelog/2024-11-22-cloud-data-extraction-aws/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Find security misconfigurations in your AWS cloud environment
Nov 22, 2024
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
You can now use CASB to find security misconfigurations in your AWS cloud environment using [Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/).
You can also [connect your AWS compute account](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/aws-s3/#compute-account) to extract and scan your S3 buckets for sensitive data while avoiding egress fees. CASB will scan any objects that exist in the bucket at the time of configuration.
To connect a compute account to your AWS integration:
1. In [Cloudflare One](https://one.dash.cloudflare.com), go to **Cloud & SaaS findings** > **Integrations**.
2. Find and select your AWS integration.
3. Select **Open connection instructions**.
4. Follow the instructions provided to connect a new compute account.
5. Select **Refresh**.
---
title: Generate customized terraform files for building cloud network on-ramps ·
Changelog
description: Download cloud onramp terraform
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-05-cloud-onramp-terraform/
md: https://developers.cloudflare.com/changelog/2024-12-05-cloud-onramp-terraform/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Generate customized terraform files for building cloud network on-ramps
Dec 05, 2024
[Magic Cloud Networking](https://developers.cloudflare.com/magic-cloud-networking/)
You can now generate customized terraform files for building cloud network on-ramps to [Magic WAN](https://developers.cloudflare.com/magic-wan/).
[Magic Cloud](https://developers.cloudflare.com/magic-cloud-networking/) can scan and discover existing network resources and generate the required terraform files to automate cloud resource deployment using their existing infrastructure-as-code workflows for cloud automation.
You might want to do this to:
* Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
* Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
For more details, refer to [Set up with Terraform](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#set-up-with-terraform).
---
title: Change the order of list items in IP Lists (for API and Terraform users)
· Changelog
description: API and Terraform users may see changes in IP list item order.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-10-change-order-of-list-items-in-ip-lists/
md: https://developers.cloudflare.com/changelog/2024-12-10-change-order-of-list-items-in-ip-lists/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Change the order of list items in IP Lists (for API and Terraform users)
Dec 10, 2024
[WAF](https://developers.cloudflare.com/waf/)
Due to changes in the API implementation, the order of list items in an IP list obtained via API or Terraform may change, which may cause Terraform to detect a change in Terraform state. To fix this issue, resync the Terraform state or upgrade the version of your Terraform Cloudflare provider to [version 4.44.0](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v4.44.0) or later.
---
title: Up to 10x faster cached queries for Hyperdrive · Changelog
description: Hyperdrive now caches queries in all Cloudflare locations
decreasing cache hit latency by up to 90%
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-11-hyperdrive-caching-at-edge/
md: https://developers.cloudflare.com/changelog/2024-12-11-hyperdrive-caching-at-edge/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Up to 10x faster cached queries for Hyperdrive
Dec 11, 2024
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive now caches queries in all Cloudflare locations, decreasing cache hit latency by up to 90%.
When you make a query to your database and Hyperdrive has cached the query results, Hyperdrive will now return the results from the nearest cache. By caching data closer to your users, the latency for cache hits reduces by up to 90%.
This reduction in cache hit latency is reflected in a reduction of the session duration for all queries (cached and uncached) from Cloudflare Workers to Hyperdrive, as illustrated below.
*P50, P75, and P90 Hyperdrive session latency for all client connection sessions (both cached and uncached queries) for Hyperdrive configurations with caching enabled during the rollout period.*
This performance improvement is applied to all new and existing Hyperdrive configurations that have caching enabled.
For more details on how Hyperdrive performs query caching, refer to the [Hyperdrive documentation](https://developers.cloudflare.com/hyperdrive/concepts/how-hyperdrive-works/#query-caching).
---
title: Terraform Support for Snippets · Changelog
description: Automate Snippet deployments with Terraform.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-11-terraform-snippets/
md: https://developers.cloudflare.com/changelog/2024-12-11-terraform-snippets/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform Support for Snippets
Dec 11, 2024
[Rules](https://developers.cloudflare.com/rules/)
Now, you can manage [Cloudflare Snippets](https://developers.cloudflare.com/rules/snippets/) with [Terraform](https://developers.cloudflare.com/terraform/). Use infrastructure-as-code to deploy and update Snippet code and rules without manual changes in the dashboard.
Example Terraform configuration:
```tf
resource "cloudflare_snippet" "my_snippet" {
zone_id = ""
name = "my_test_snippet_1"
main_module = "file1.js"
files {
name = "file1.js"
content = file("file1.js")
}
}
resource "cloudflare_snippet_rules" "cookie_snippet_rule" {
zone_id = ""
rules {
enabled = true
expression = "http.cookie eq \"a=b\""
description = "Trigger snippet on specific cookie"
snippet_name = "my_test_snippet_1"
}
depends_on = [cloudflare_snippet.my_snippet]
}
```
Learn more in the [Configure Snippets using Terraform](https://developers.cloudflare.com/rules/snippets/create-terraform/) documentation.
---
title: Establish BGP peering over Direct CNI circuits · Changelog
description: BGP support for Cloudflare Network Interconnect (CNI)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-17-bgp-support-cni/
md: https://developers.cloudflare.com/changelog/2024-12-17-bgp-support-cni/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Establish BGP peering over Direct CNI circuits
Dec 17, 2024
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Network Interconnect](https://developers.cloudflare.com/network-interconnect/)
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
Refer to [Magic WAN BGP peering](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes) or [Magic Transit BGP peering](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes) to learn more about this feature and how to set it up.
---
title: Improved VPN Managed List · Changelog
description: Improved management of VPN IP traffic.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-18-improved-vpn-managed-list/
md: https://developers.cloudflare.com/changelog/2024-12-18-improved-vpn-managed-list/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved VPN Managed List
Dec 18, 2024
[WAF](https://developers.cloudflare.com/waf/)
Customers can now effectively manage incoming traffic identified as originating from VPN IPs. Customers with compliance restrictions can now ensure compliance with local laws and regulations. Customers with CDN restrictions can use the improved VPN Managed List to prevent unauthorized access from users attempting to bypass geographical restrictions. With the new VPN Managed List enhancements, customers can improve their overall security posture to reduce exposure to unwanted or malicious traffic.
---
title: Troubleshoot tunnels with diagnostic logs · Changelog
description: View tunnel diagnostic logs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-19-diagnostic-logs/
md: https://developers.cloudflare.com/changelog/2024-12-19-diagnostic-logs/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Troubleshoot tunnels with diagnostic logs
Dec 19, 2024
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
The latest `cloudflared` build [2024.12.2](https://github.com/cloudflare/cloudflared/releases/tag/2024.12.2) introduces the ability to collect all the diagnostic logs needed to troubleshoot a `cloudflared` instance.
A diagnostic report collects data from a single instance of `cloudflared` running on the local machine and outputs it to a `cloudflared-diag` file.
The `cloudflared-diag-YYYY-MM-DDThh-mm-ss.zip` archive contains the files listed below. The data in a file either applies to the `cloudflared` instance being diagnosed (`diagnosee`) or the instance that triggered the diagnosis (`diagnoser`). For example, if your tunnel is running in a Docker container, the diagnosee is the Docker instance and the diagnoser is the host instance.
| File name | Description | Instance |
| - | - | - |
| `cli-configuration.json` | [Tunnel run parameters](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/configure-tunnels/cloudflared-parameters/run-parameters/) used when starting the tunnel | diagnosee |
| `cloudflared_logs.txt` | [Tunnel log file](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/logs/)[1](#user-content-fn-1) | diagnosee |
| `configuration.json` | Tunnel configuration parameters | diagnosee |
| `goroutine.pprof` | goroutine profile made available by `pprof` | diagnosee |
| `heap.pprof` | heap profile made available by `pprof` | diagnosee |
| `metrics.txt` | Snapshot of [Tunnel metrics](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/metrics/#available-metrics) at the time of diagnosis | diagnosee |
| `network.txt` | JSON traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
| `raw-network.txt` | Raw traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
| `systeminformation.json` | Operating system information and resource usage | diagnosee |
| `task-result.json` | Result of each diagnostic task | diagnoser |
| `tunnelstate.json` | Tunnel connections at the time of diagnosis | diagnosee |
## Footnotes
1. If the log file is blank, you may need to [set `--loglevel` to `debug`](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/monitor-tunnels/logs/#view-logs-on-the-server) when you start the tunnel. The `--loglevel` parameter is only required if you ran the tunnel from the CLI using a `cloudflared tunnel run` command. It is not necessary if the tunnel runs as a Linux/macOS service or runs in Docker/Kubernetes. [↩](#user-content-fnref-1)
For more information, refer to [Diagnostic logs](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/troubleshoot-tunnels/diag-logs/).
---
title: Escalate user submissions · Changelog
description: Escalate user-submitted messages for reclassification by the Cloudflare team.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-19-escalate-user-submissions/
md: https://developers.cloudflare.com/changelog/2024-12-19-escalate-user-submissions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Escalate user submissions
Dec 19, 2024
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
After you triage your users' submissions (that are machine reviewed), you can now escalate them to our team for reclassification (which are instead human reviewed). User submissions from the submission alias, PhishNet, and our API can all be escalated.

From **Reclassifications**, go to **User submissions**. Select the three dots next to any of the user submissions, then select **Escalate** to create a team request for reclassification. The Cloudflare dashboard will then show you the submissions on the **Team Submissions** tab.
Refer to [User submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/user-submissions/) to learn more about this feature.
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Increased transparency for phishing email submissions · Changelog
description: New Email reclassifications tab
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-19-reclassification-tab/
md: https://developers.cloudflare.com/changelog/2024-12-19-reclassification-tab/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased transparency for phishing email submissions
Dec 19, 2024
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You now have more transparency about team and user submissions for phishing emails through a **Reclassification** tab in the Zero Trust dashboard.
Reclassifications happen when users or admins [submit a phish](https://developers.cloudflare.com/cloudflare-one/email-security/settings/phish-submissions/) to Email security. Cloudflare reviews and - in some cases - reclassifies these emails based on improvements to our machine learning models.
This new tab increases your visibility into this process, allowing you to view what submissions you have made and what the outcomes of those submissions are.

---
title: Faster Workers Builds with Build Caching and Watch Paths · Changelog
description: Speed up your builds with build caching and build watch paths in
Workers Builds (beta).
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2024-12-29-faster-builds/
md: https://developers.cloudflare.com/changelog/2024-12-29-faster-builds/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Faster Workers Builds with Build Caching and Watch Paths
Dec 29, 2024
[Workers](https://developers.cloudflare.com/workers/)
[**Workers Builds**](https://developers.cloudflare.com/workers/ci-cd/builds/), the integrated CI/CD system for Workers (currently in beta), now lets you cache artifacts across builds, speeding up build jobs by eliminating repeated work, such as downloading dependencies at the start of each build.
* **[Build Caching](https://developers.cloudflare.com/workers/ci-cd/builds/build-caching/)**: Cache dependencies and build outputs between builds with a shared project-wide cache, ensuring faster builds for the entire team.
* **[Build Watch Paths](https://developers.cloudflare.com/workers/ci-cd/builds/build-watch-paths/)**: Define paths to include or exclude from the build process, ideal for [monorepos](https://developers.cloudflare.com/workers/ci-cd/builds/advanced-setups/#monorepos) to target only the files that need to be rebuilt per Workers project.
To get started, select your Worker on the [Cloudflare dashboard](https://dash.cloudflare.com) then go to **Settings** > **Builds**, and connect a GitHub or GitLab repository. Once connected, you'll see options to configure Build Caching and Build Watch Paths.
---
title: Detect source code leaks with Data Loss Prevention · Changelog
description: Added source code confidence levels to Data Loss Prevention
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-03-source-code-confidence-level/
md: https://developers.cloudflare.com/changelog/2025-01-03-source-code-confidence-level/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Detect source code leaks with Data Loss Prevention
Jan 20, 2025
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now detect source code leaks with Data Loss Prevention (DLP) with predefined checks against common programming languages.
The following programming languages are validated with natural language processing (NLP).
* C
* C++
* C#
* Go
* Haskell
* Java
* JavaScript
* Lua
* Python
* R
* Rust
* Swift
DLP also supports confidence level for [source code profiles](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/predefined-profiles/#source-code).
For more details, refer to [DLP profiles](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/).
---
title: WAF Release - 2025-01-06 · Changelog
description: Cloudflare WAF managed rulesets 2025-01-06 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-06-waf-release/
md: https://developers.cloudflare.com/changelog/2025-01-06-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-01-06
Jan 06, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Specials | 3a321b10270b42549ac201009da08beb | 100678 | Pandora FMS - Remote Code Execution - CVE:CVE-2024-11320 | Log | Block | New Detection |
| Cloudflare Specials | 1fe510368b4a47dda90363c2ecdf3d02 | 100679 | Palo Alto Networks - Remote Code Execution - CVE:CVE-2024-0012, CVE:CVE-2024-9474 | Log | Block | New Detection |
| Cloudflare Specials | b7ba636927b44ee288b9a697a40f2a35 | 100680 | Ivanti - Command Injection - CVE:CVE-2024-37397 | Log | Block | New Detection |
| Cloudflare Specials | 6bd9b07c8acc4beeb17c8bee58ae3c89 | 100681 | Really Simple Security - Auth Bypass - CVE:CVE-2024-10924 | Log | Block | New Detection |
| Cloudflare Specials | c86e79e15a4a4307870f6f77e37f2da6 | 100682 | Magento - XXE - CVE:CVE-2024-34102 | Log | Block | New Detection |
| Cloudflare Specials | 945f41b48be9485f953116015054c752 | 100683 | CyberPanel - Remote Code Execution - CVE:CVE-2024-51567 | Log | Block | New Detection |
| Cloudflare Specials | aec9a2e554a34a8fa547d069dfe93d7b | 100684 | Microsoft SharePoint - Remote Code Execution - CVE:CVE-2024-38094, CVE:CVE-2024-38024, CVE:CVE-2024-38023 | Log | Block | New Detection |
| Cloudflare Specials | e614dd46c1ce404da1909e841454c856 | 100685 | CyberPanel - Remote Code Execution - CVE:CVE-2024-51568 | Log | Block | New Detection |
| Cloudflare Specials | 685a4edf68f740b4a2c80d45e92362e5 | 100686 | Seeyon - Remote Code Execution | Log | Block | New Detection |
| Cloudflare Specials | 204f9d948a124829acb86555b9f1c9f8 | 100687 | WordPress - Remote Code Execution - CVE:CVE-2024-10781, CVE:CVE-2024-10542 | Log | Block | New Detection |
| Cloudflare Specials | 19587024724e49329d5b482d0d7ca374 | 100688 | ProjectSend - Remote Code Execution - CVE:CVE-2024-11680 | Log | Block | New Detection |
| Cloudflare Specials | fa49213e55484f6c824e0682a5260b70 | 100689 | Palo Alto GlobalProtect - Remote Code Execution - CVE:CVE-2024-5921 | Log | Block | New Detection |
| Cloudflare Specials | 11b5fc23e85b41ca90316bddd007118b | 100690 | Ivanti - Remote Code Execution - CVE:CVE-2024-37404 | Log | Block | New Detection |
| Cloudflare Specials | aaeada52bcc840598515de6cc3e49f64 | 100691 | Array Networks - Remote Code Execution - CVE:CVE-2023-28461 | Log | Block | New Detection |
| Cloudflare Specials | e2c7ce1ecd6847219f8d9aedfcc6f5bb | 100692 | CyberPanel - Remote Code Execution - CVE:CVE-2024-51378 | Log | Block | New Detection |
| Cloudflare Specials | 84d481b1f49c4735afa2fb2bb615335e | 100693 | Symfony Profiler - Auth Bypass - CVE:CVE-2024-50340 | Log | Block | New Detection |
| Cloudflare Specials | 9f258f463f9f4b26ad07e3c209d08c8a | 100694 | Citrix Virtual Apps - Remote Code Execution - CVE:CVE-2024-8069 | Log | Block | New Detection |
| Cloudflare Specials | b490d6edcfec4028aef45cf08aafb2f5 | 100695 | MSMQ Service - Remote Code Execution - CVE:CVE-2023-21554 | Log | Block | New Detection |
| Cloudflare Specials | c8f65bc9eeef4665820ecfe411b7a8c7 | 100696 | Nginxui - Remote Code Execution - CVE:CVE-2024-49368 | Log | Block | New Detection |
| Cloudflare Specials | d5f2e133e34640198d06d7b345954c7e | 100697 | Apache ShardingSphere - Remote Code Execution - CVE:CVE-2022-22733 | Log | Block | New Detection |
| Cloudflare Specials | c34432e257074cffa9fa15f3f5311209 | 100698 | Mitel MiCollab - Auth Bypass - CVE:CVE-2024-41713 | Log | Block | New Detection |
| Cloudflare Specials | 3bda15acd73a4b55a5f60cd2b3e5e46e | 100699 | Apache Solr - Auth Bypass - CVE:CVE-2024-45216 | Log | Block | New Detection |
---
title: AI Gateway adds DeepSeek as a Provider · Changelog
description: AI Gateway has added DeepSeek as a new provider.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-07-aig-provider-deepseek/
md: https://developers.cloudflare.com/changelog/2025-01-07-aig-provider-deepseek/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Gateway adds DeepSeek as a Provider
Jan 02, 2025
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
[**AI Gateway**](https://developers.cloudflare.com/ai-gateway/) now supports [**DeepSeek**](https://developers.cloudflare.com/ai-gateway/usage/providers/deepseek/), including their cutting-edge DeepSeek-V3 model. With this addition, you have even more flexibility to manage and optimize your AI workloads using AI Gateway. Whether you're leveraging DeepSeek or other providers, like OpenAI, Anthropic, or [Workers AI](https://developers.cloudflare.com/workers-ai/), AI Gateway empowers you to:
* **Monitor**: Gain actionable insights with analytics and logs.
* **Control**: Implement caching, rate limiting, and fallbacks.
* **Optimize**: Improve performance with feedback and evaluations.

To get started, simply update the base URL of your DeepSeek API calls to route through AI Gateway. Here's how you can send a request using cURL:
```bash
curl https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/deepseek/chat/completions \
--header 'content-type: application/json' \
--header 'Authorization: Bearer DEEPSEEK_TOKEN' \
--data '{
"model": "deepseek-chat",
"messages": [
{
"role": "user",
"content": "What is Cloudflare?"
}
]
}'
```
For detailed setup instructions, see our [DeepSeek provider documentation](https://developers.cloudflare.com/ai-gateway/usage/providers/deepseek/).
---
title: Smart Tiered Cache optimizes Load Balancing Pools · Changelog
description: Smart Tiered Cache now selects a common tiered data center for Load
Balancing Pools to increase cache hit ratio.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-08-smart-tiered-cache-for-load-balancing/
md: https://developers.cloudflare.com/changelog/2025-01-08-smart-tiered-cache-for-load-balancing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Smart Tiered Cache optimizes Load Balancing Pools
Jan 08, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now achieve higher cache hit rates and reduce origin load when using [Load Balancing](https://developers.cloudflare.com/load-balancing/) with [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/). Cloudflare automatically selects a single, optimal tiered data center for all origins in your Load Balancing Pool.
#### How it works
When you use [Load Balancing](https://developers.cloudflare.com/load-balancing/) with [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/), Cloudflare analyzes performance metrics across your pool's origins and automatically selects the optimal Upper Tier data center for the entire pool. This means:
* **Consistent cache location**: All origins in the pool share the same Upper Tier cache.
* **Higher HIT rates**: Requests for the same content hit the cache more frequently.
* **Reduced origin requests**: Fewer requests reach your origin servers.
* **Improved performance**: Faster response times for cache HITs.
#### Example workflow
```txt
Load Balancing Pool: api-pool
├── Origin 1: api-1.example.com
├── Origin 2: api-2.example.com
└── Origin 3: api-3.example.com
↓
Selected Upper Tier: [Optimal data center based on pool performance]
```
#### Get started
To get started, enable [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) on your zone and configure your [Load Balancing Pool](https://developers.cloudflare.com/load-balancing/).
---
title: 40-60% Faster D1 Worker API Requests · Changelog
description: D1's Worker API request latency decreases by 40-60%.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-07-d1-faster-query/
md: https://developers.cloudflare.com/changelog/2025-01-07-d1-faster-query/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## 40-60% Faster D1 Worker API Requests
Jan 07, 2025
[D1](https://developers.cloudflare.com/d1/)
Users making [D1](https://developers.cloudflare.com/d1/) requests via the [Workers API](https://developers.cloudflare.com/d1/worker-api/) can see up to a 60% end-to-end latency improvement due to the removal of redundant network round trips needed for each request to a D1 database.

*p50, p90, and p95 request latency aggregated across entire D1 service. These latencies are a reference point and should not be viewed as your exact workload improvement.*
This performance improvement benefits all D1 Worker API traffic, especially cross-region requests where network latency is an outsized latency factor. For example, a user in Europe talking to a database in North America. D1 [location hints](https://developers.cloudflare.com/d1/configuration/data-location/#provide-a-location-hint) can be used to influence the geographic location of a database.
For more details on how D1 removed redundant round trips, see the D1 specific release note [entry](https://developers.cloudflare.com/d1/platform/release-notes/#2025-01-07).
---
title: New Rules Overview Interface · Changelog
description: Manage all your rules in one place with the new Rules Overview.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-09-rules-overview/
md: https://developers.cloudflare.com/changelog/2025-01-09-rules-overview/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Rules Overview Interface
Jan 09, 2025
[Rules](https://developers.cloudflare.com/rules/)
**Rules Overview** gives you a single page to manage all your [Cloudflare Rules](https://developers.cloudflare.com/rules/).
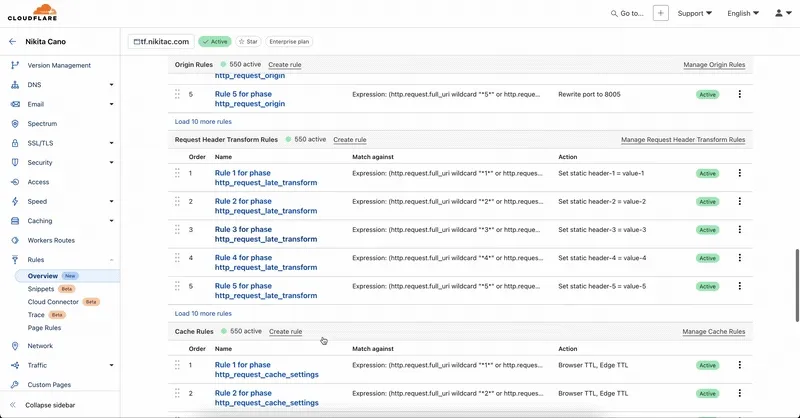
What you can do:
* **See all your rules in one place** – No more clicking around.
* **Find rules faster** – Search by name.
* **Understand execution order** – See how rules run in sequence.
* **Debug easily** – Use [Trace](https://developers.cloudflare.com/rules/trace-request/) without switching tabs.
Check it out in [Rules > Overview](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview).
---
title: WAF Release - 2025-01-13 · Changelog
description: Cloudflare WAF managed rulesets 2025-01-13 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-13-waf-release/
md: https://developers.cloudflare.com/changelog/2025-01-13-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-01-13
Jan 13, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 6e0bfbe4b9c6454c8bd7bd24f49e5840 | 100704 | Cleo Harmony - Auth Bypass - CVE:CVE-2024-55956, CVE:CVE-2024-55953 | Log | Block | New Detection |
| Cloudflare Managed Ruleset | c993997b7d904a9e89448fe6a6d43bc2 | 100705 | Sentry - SSRF | Log | Block | New Detection |
| Cloudflare Managed Ruleset | f40ce742be534ba19d610961ce6311bb | 100706 | Apache Struts - Remote Code Execution - CVE:CVE-2024-53677 | Log | Block | New Detection |
| Cloudflare Managed Ruleset | 67ac639a845c482d948b465b2233da1f | 100707 | FortiWLM - Remote Code Execution - CVE:CVE-2023-48782, CVE:CVE-2023-34993, CVE:CVE-2023-34990 | Log | Block | New Detection |
| Cloudflare Managed Ruleset | 870cca2b874d41738019d4c3e31d972a | 100007C\_BETA | Command Injection - Common Attack Commands | | Disabled | |
---
title: Export SSH command logs with Access for Infrastructure using Logpush ·
Changelog
description: Easily configure automatic export of SSH command logs to
third-party storage destinations or to security information and event
management (SIEM) tools.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-15-ssh-logs-and-logpush/
md: https://developers.cloudflare.com/changelog/2025-01-15-ssh-logs-and-logpush/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Export SSH command logs with Access for Infrastructure using Logpush
Jan 15, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
Availability
Only available on Enterprise plans.
Cloudflare now allows you to send SSH command logs to storage destinations configured in [Logpush](https://developers.cloudflare.com/logs/logpush/), including third-party destinations. Once exported, analyze and audit the data as best fits your organization! For a list of available data fields, refer to the [SSH logs dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/ssh_logs/).
To set up a Logpush job, refer to [Logpush integration](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/).
---
title: Increased Workflows limits and improved instance queueing. · Changelog
description: More steps per Workflow + pause/resume now supported
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-15-workflows-more-steps/
md: https://developers.cloudflare.com/changelog/2025-01-15-workflows-more-steps/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased Workflows limits and improved instance queueing.
Jan 15, 2025
[Workflows](https://developers.cloudflare.com/workflows/)
[Workflows](https://developers.cloudflare.com/workflows/) (beta) now allows you to define up to 1024 [steps](https://developers.cloudflare.com/workflows/build/workers-api/#workflowstep). `sleep` steps do not count against this limit.
We've also added:
* `instanceId` as property to the [`WorkflowEvent`](https://developers.cloudflare.com/workflows/build/workers-api/#workflowevent) type, allowing you to retrieve the current instance ID from within a running Workflow instance
* Improved queueing logic for Workflow instances beyond the current maximum concurrent instances, reducing the cases where instances are stuck in the queued state.
* Support for [`pause` and `resume`](https://developers.cloudflare.com/workflows/build/workers-api/#pause) for Workflow instances in a queued state.
We're continuing to work on increases to the number of concurrent Workflow instances, steps, and support for a new `waitForEvent` API over the coming weeks.
---
title: WAF Release - 2025-01-21 · Changelog
description: Cloudflare WAF managed rulesets 2025-01-21 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-21-waf-release/
md: https://developers.cloudflare.com/changelog/2025-01-21-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-01-21
Jan 21, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | f4a310393c564d50bd585601b090ba9a | 100303 | Command Injection - Nslookup | Log | Block | This was released as aad6f9f85e034022b6a8dee4b8d152f4 |
| Cloudflare Managed Ruleset | fd5d5678ce594ea898aa9bf149e6b538 | 100534 | Web Shell Activity | Log | Block | This was released as 39c8f6066c19466ea084e51e82fe4e7f |
---
title: AI Gateway Introduces New Worker Binding Methods · Changelog
description: New Worker binding methods, enhancing integration capabilities for developers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-26-worker-binding-methods/
md: https://developers.cloudflare.com/changelog/2025-01-26-worker-binding-methods/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Gateway Introduces New Worker Binding Methods
Jan 30, 2025
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
We have released new [Workers bindings API methods](https://developers.cloudflare.com/ai-gateway/integrations/worker-binding-methods/), allowing you to connect Workers applications to AI Gateway directly. These methods simplify how Workers calls AI services behind your AI Gateway configurations, removing the need to use the REST API and manually authenticate.
To add an AI binding to your Worker, include the following in your [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/):
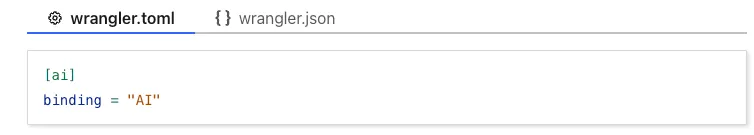
With the new AI Gateway binding methods, you can now:
* Send feedback and update metadata with `patchLog`.
* Retrieve detailed log information using `getLog`.
* Execute [universal requests](https://developers.cloudflare.com/ai-gateway/usage/universal/) to any AI Gateway provider with `run`.
For example, to send feedback and update metadata using `patchLog`:
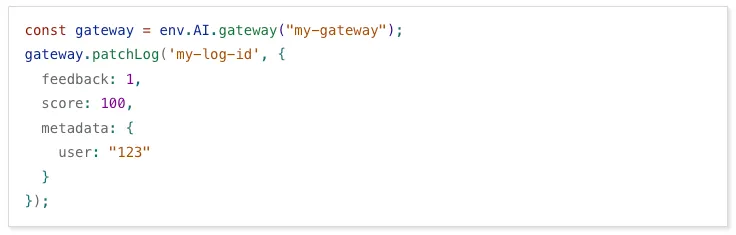
---
title: Workers KV namespace limits increased to 1000 · Changelog
description: You can now have up to 1000 Workers KV namespaces per account.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-27-kv-increased-namespaces-limits/
md: https://developers.cloudflare.com/changelog/2025-01-27-kv-increased-namespaces-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers KV namespace limits increased to 1000
Jan 28, 2025
[KV](https://developers.cloudflare.com/kv/)
You can now have up to 1000 Workers KV namespaces per account.
Workers KV namespace limits were increased from 200 to 1000 for all accounts. Higher limits for Workers KV namespaces enable better organization of key-value data, such as by category, tenant, or environment.
Consult the [Workers KV limits documentation](https://developers.cloudflare.com/kv/platform/limits/) for the rest of the limits. This increased limit is available for both the Free and Paid [Workers plans](https://developers.cloudflare.com/workers/platform/pricing/).
---
title: Automatic configuration for private databases on Hyperdrive · Changelog
description: Hyperdrive now automatically configures your Cloudflare Tunnel to
connect to your private database.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-28-hyperdrive-automated-private-database-configuration/
md: https://developers.cloudflare.com/changelog/2025-01-28-hyperdrive-automated-private-database-configuration/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Automatic configuration for private databases on Hyperdrive
Jan 28, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive now automatically configures your Cloudflare Tunnel to connect to your private database.
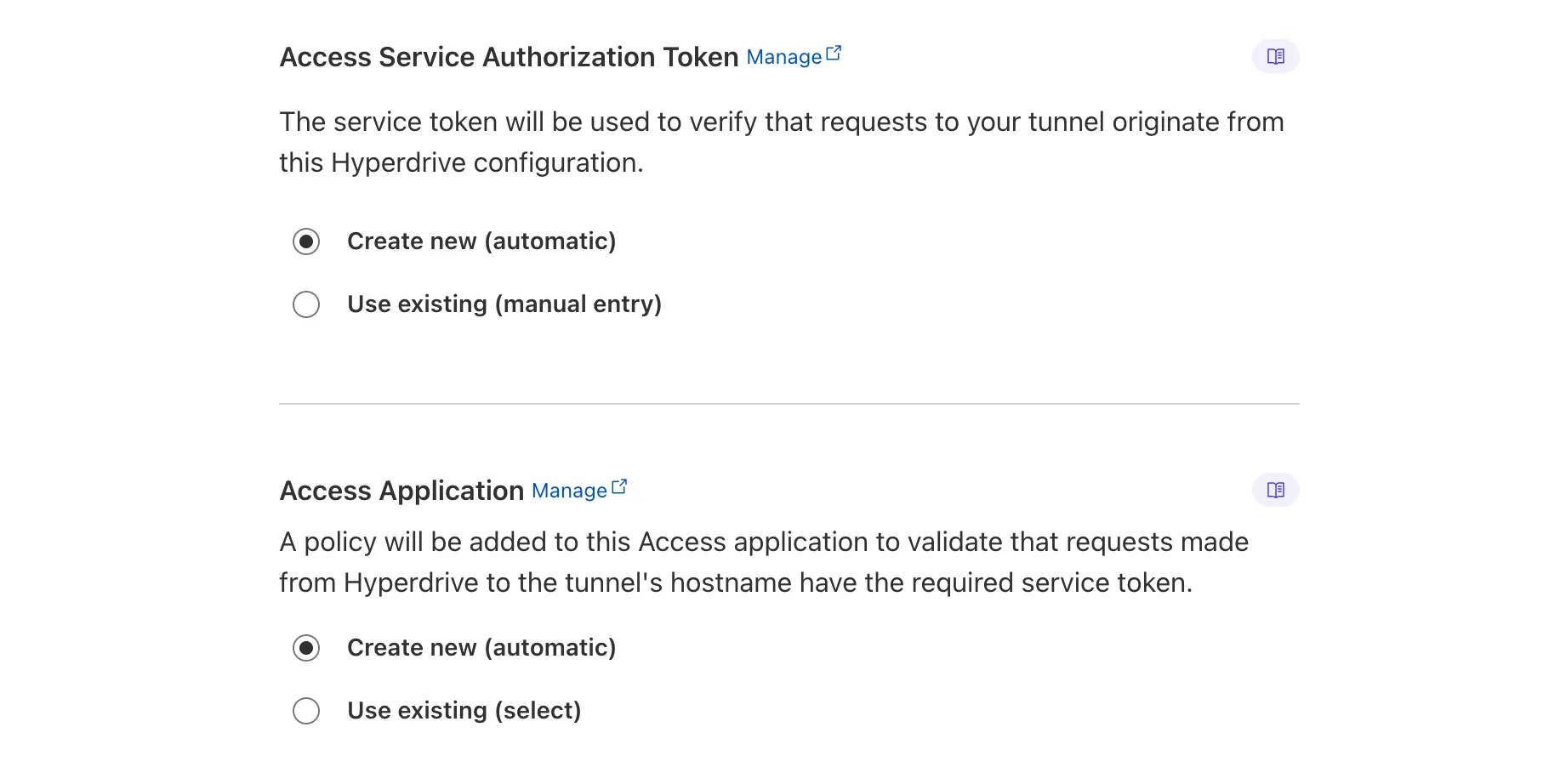
When creating a Hyperdrive configuration for a private database, you only need to provide your database credentials and set up a Cloudflare Tunnel within the private network where your database is accessible. Hyperdrive will automatically create the Cloudflare Access, Service Token, and Policies needed to secure and restrict your Cloudflare Tunnel to the Hyperdrive configuration.
To create a Hyperdrive for a private database, you can follow the [Hyperdrive documentation](https://developers.cloudflare.com/hyperdrive/configuration/connect-to-private-database/). You can still manually create the Cloudflare Access, Service Token, and Policies if you prefer.
This feature is available from the Cloudflare dashboard.
---
title: Support for Node.js DNS, Net, and Timer APIs in Workers · Changelog
description: Node.js APIs from the node:dns, node:net, and node:timers modules
are now available when using nodejs_compat.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-28-nodejs-compat-improvements/
md: https://developers.cloudflare.com/changelog/2025-01-28-nodejs-compat-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Support for Node.js DNS, Net, and Timer APIs in Workers
Jan 28, 2025
[Workers](https://developers.cloudflare.com/workers/)
When using a Worker with the [`nodejs_compat`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/) compatibility flag enabled, you can now use the following Node.js APIs:
* [`node:net`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/net/)
* [`node:dns`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/dns/)
* [`node:timers`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/timers/)
#### node:net
You can use [`node:net`](https://nodejs.org/api/net.html) to create a direct connection to servers via a TCP sockets with [`net.Socket`](https://nodejs.org/api/net.html#class-netsocket).
* JavaScript
```js
import net from "node:net";
const exampleIP = "127.0.0.1";
export default {
async fetch(req) {
const socket = new net.Socket();
socket.connect(4000, exampleIP, function () {
console.log("Connected");
});
socket.write("Hello, Server!");
socket.end();
return new Response("Wrote to server", { status: 200 });
},
};
```
* TypeScript
```ts
import net from "node:net";
const exampleIP = "127.0.0.1";
export default {
async fetch(req): Promise {
const socket = new net.Socket();
socket.connect(4000, exampleIP, function () {
console.log("Connected");
});
socket.write("Hello, Server!");
socket.end();
return new Response("Wrote to server", { status: 200 });
},
} satisfies ExportedHandler;
```
Additionally, you can now use other APIs including [`net.BlockList`](https://nodejs.org/api/net.html#class-netblocklist) and [`net.SocketAddress`](https://nodejs.org/api/net.html#class-netsocketaddress).
Note that [`net.Server`](https://nodejs.org/api/net.html#class-netserver) is not supported.
#### node:dns
You can use [`node:dns`](https://nodejs.org/api/dns.html) for name resolution via [DNS over HTTPS](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/) using [Cloudflare DNS](https://www.cloudflare.com/application-services/products/dns/) at 1.1.1.1.
* JavaScript
```js
import dns from "node:dns";
let response = await dns.promises.resolve4("cloudflare.com", "NS");
```
* TypeScript
```ts
import dns from 'node:dns';
let response = await dns.promises.resolve4('cloudflare.com', 'NS');
```
All `node:dns` functions are available, except `lookup`, `lookupService`, and `resolve` which throw "Not implemented" errors when called.
#### node:timers
You can use [`node:timers`](https://nodejs.org/api/timers.html) to schedule functions to be called at some future period of time.
This includes [`setTimeout`](https://nodejs.org/api/timers.html#settimeoutcallback-delay-args) for calling a function after a delay, [`setInterval`](https://nodejs.org/api/timers.html#setintervalcallback-delay-args) for calling a function repeatedly, and [`setImmediate`](https://nodejs.org/api/timers.html#setimmediatecallback-args) for calling a function in the next iteration of the event loop.
* JavaScript
```js
import timers from "node:timers";
console.log("first");
timers.setTimeout(() => {
console.log("last");
}, 10);
timers.setTimeout(() => {
console.log("next");
});
```
* TypeScript
```ts
import timers from "node:timers";
console.log("first");
timers.setTimeout(() => {
console.log("last");
}, 10);
timers.setTimeout(() => {
console.log("next");
});
```
---
title: New Snippets Code Editor · Changelog
description: Edit Snippets and rules in one place with the new built-in code editor.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-29-snippets-code-editor/
md: https://developers.cloudflare.com/changelog/2025-01-29-snippets-code-editor/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Snippets Code Editor
Jan 29, 2025
[Rules](https://developers.cloudflare.com/rules/)
The new [Snippets](https://developers.cloudflare.com/rules/snippets/) code editor lets you edit Snippet code and rule in one place, making it easier to test and deploy changes without switching between pages.
What’s new:
* **Single-page editing for code and rule** – No need to jump between screens.
* **Auto-complete & syntax highlighting** – Get suggestions and avoid mistakes.
* **Code formatting & refactoring** – Write cleaner, more readable code.
Try it now in [Rules > Snippets](https://dash.cloudflare.com/?to=/:account/:zone/rules/snippets).
---
title: Increased Browser Rendering limits! · Changelog
description: Browser Rendering now supports more concurrent browser sessions.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-30-browser-rendering-more-instances/
md: https://developers.cloudflare.com/changelog/2025-01-30-browser-rendering-more-instances/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased Browser Rendering limits!
Jan 30, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/) now supports 10 concurrent browser instances per account *and* 10 new instances per minute, up from the previous limits of 2.
This allows you to launch more browser tasks from [Cloudflare Workers](https://developers.cloudflare.com/workers).
To manage concurrent browser sessions, you can use [Queues](https://developers.cloudflare.com/queues/) or [Workflows](https://developers.cloudflare.com/workflows/):
* JavaScript
```js
export default {
async queue(batch, env) {
for (const message of batch.messages) {
const browser = await puppeteer.launch(env.BROWSER);
const page = await browser.newPage();
try {
await page.goto(message.url, {
waitUntil: message.waitUntil,
});
// Process page...
} finally {
await browser.close();
}
}
},
};
```
* TypeScript
```ts
interface QueueMessage {
url: string;
waitUntil: number;
}
export interface Env {
BROWSER_QUEUE: Queue;
BROWSER: Fetcher;
}
export default {
async queue(batch: MessageBatch, env: Env): Promise {
for (const message of batch.messages) {
const browser = await puppeteer.launch(env.BROWSER);
const page = await browser.newPage();
try {
await page.goto(message.url, {
waitUntil: message.waitUntil
});
// Process page...
} finally {
await browser.close();
}
}
}
};
```
---
title: Expanded language support for Stream AI Generated Captions · Changelog
description: Captions can now be generated for 11 additional spoken languages at no cost!
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-30-stream-generated-captions-new-languages/
md: https://developers.cloudflare.com/changelog/2025-01-30-stream-generated-captions-new-languages/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Expanded language support for Stream AI Generated Captions
Jan 30, 2025
[Stream](https://developers.cloudflare.com/stream/)
Stream's [generated captions](https://developers.cloudflare.com/stream/edit-videos/adding-captions/#generate-a-caption) leverage Workers AI to automatically transcribe audio and provide captions to the player experience. We have added support for these languages:
* `cs` - Czech
* `nl` - Dutch
* `fr` - French
* `de` - German
* `it` - Italian
* `ja` - Japanese
* `ko` - Korean
* `pl` - Polish
* `pt` - Portuguese
* `ru` - Russian
* `es` - Spanish
For more information, learn about [adding captions to videos](https://developers.cloudflare.com/stream/edit-videos/adding-captions/).
---
title: Transform HTML quickly with streaming content · Changelog
description: HTMLRewriter now supports streamed content for more efficient
replacement of HTML elements
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-31-html-rewriter-streaming/
md: https://developers.cloudflare.com/changelog/2025-01-31-html-rewriter-streaming/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Transform HTML quickly with streaming content
Jan 31, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now transform HTML elements with streamed content using [`HTMLRewriter`](https://developers.cloudflare.com/workers/runtime-apis/html-rewriter).
Methods like `replace`, `append`, and `prepend` now accept [`Response`](https://developers.cloudflare.com/workers/runtime-apis/response/) and [`ReadableStream`](https://developers.cloudflare.com/workers/runtime-apis/streams/readablestream/) values as [`Content`](https://developers.cloudflare.com/workers/runtime-apis/html-rewriter/#global-types).
This can be helpful in a variety of situations. For instance, you may have a Worker in front of an origin, and want to replace an element with content from a different source. Prior to this change, you would have to load all of the content from the upstream URL and convert it into a string before replacing the element. This slowed down overall response times.
Now, you can pass the `Response` object directly into the `replace` method, and HTMLRewriter will immediately start replacing the content as it is streamed in. This makes responses faster.
* JavaScript
```js
class ElementRewriter {
async element(element) {
// able to replace elements while streaming content
// the fetched body is not buffered into memory as part
// of the replace
let res = await fetch("https://upstream-content-provider.example");
element.replace(res);
}
}
export default {
async fetch(request, env, ctx) {
let response = await fetch("https://site-to-replace.com");
return new HTMLRewriter()
.on("[data-to-replace]", new ElementRewriter())
.transform(response);
},
};
```
* TypeScript
```ts
class ElementRewriter {
async element(element: any) {
// able to replace elements while streaming content
// the fetched body is not buffered into memory as part
// of the replace
let res = await fetch('https://upstream-content-provider.example');
element.replace(res);
}
}
export default {
async fetch(request, env, ctx): Promise {
let response = await fetch('https://site-to-replace.com');
return new HTMLRewriter().on('[data-to-replace]', new ElementRewriter()).transform(response);
},
} satisfies ExportedHandler;
```
For more information, see the [`HTMLRewriter` documentation](https://developers.cloudflare.com/workers/runtime-apis/html-rewriter).
---
title: Workers for Platforms now supports Static Assets · Changelog
description: Workers for Platforms customers can now serve static assets for
User Workers directly from Cloudflare's global edge
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-01-31-workers-platforms-static-assets/
md: https://developers.cloudflare.com/changelog/2025-01-31-workers-platforms-static-assets/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers for Platforms now supports Static Assets
Jan 31, 2025
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
Workers for Platforms customers can now attach static assets (HTML, CSS, JavaScript, images) directly to User Workers, removing the need to host separate infrastructure to serve the assets.
This allows your platform to serve entire front-end applications from Cloudflare's global edge, utilizing caching for fast load times, while supporting dynamic logic within the same Worker. Cloudflare automatically scales its infrastructure to handle high traffic volumes, enabling you to focus on building features without managing servers.
#### What you can build
**Static Sites:** Host and serve HTML, CSS, JavaScript, and media files directly from Cloudflare's network, ensuring fast loading times worldwide. This is ideal for blogs, landing pages, and documentation sites because static assets can be efficiently cached and delivered closer to the user, reducing latency and enhancing the overall user experience.
**Full-Stack Applications:** Combine asset hosting with Cloudflare Workers to power dynamic, interactive applications. If you're an e-commerce platform, you can serve your customers' product pages and run inventory checks from within the same Worker.
* JavaScript
```js
export default {
async fetch(request, env) {
const url = new URL(request.url);
// Check real-time inventory
if (url.pathname === "/api/inventory/check") {
const product = url.searchParams.get("product");
const inventory = await env.INVENTORY_KV.get(product);
return new Response(inventory);
}
// Serve static assets (HTML, CSS, images)
return env.ASSETS.fetch(request);
},
};
```
* TypeScript
```ts
export default {
async fetch(request, env) {
const url = new URL(request.url);
// Check real-time inventory
if (url.pathname === '/api/inventory/check') {
const product = url.searchParams.get('product');
const inventory = await env.INVENTORY_KV.get(product);
return new Response(inventory);
}
// Serve static assets (HTML, CSS, images)
return env.ASSETS.fetch(request);
}
};
```
**Get Started:** Upload static assets using the Workers for Platforms API or Wrangler. For more information, visit our [Workers for Platforms documentation.](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/static-assets/)
---
title: Removed unused meta fields from DNS records · Changelog
description: Cloudflare is removing five fields from the meta object of DNS records.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-02-removed-meta-fields/
md: https://developers.cloudflare.com/changelog/2025-02-02-removed-meta-fields/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Removed unused meta fields from DNS records
Feb 02, 2025
[DNS](https://developers.cloudflare.com/dns/)
Cloudflare is removing five fields from the `meta` object of DNS records. These fields have been unused for more than a year and are no longer set on new records. This change may take up to four weeks to fully roll out.
The affected fields are:
* the `auto_added` boolean
* the `managed_by_apps` boolean and corresponding `apps_install_id`
* the `managed_by_argo_tunnel` boolean and corresponding `argo_tunnel_id`
An example record returned from the API would now look like the following:
```json
{
"result": {
"id": "",
"zone_id": "",
"zone_name": "example.com",
"name": "www.example.com",
"type": "A",
"content": "192.0.2.1",
"proxiable": true,
"proxied": false,
"ttl": 1,
"locked": false,
"meta": {
"auto_added": false,
"managed_by_apps": false,
"managed_by_argo_tunnel": false,
"source": "primary"
},
"comment": null,
"tags": [],
"created_on": "2025-03-17T20:37:05.368097Z",
"modified_on": "2025-03-17T20:37:05.368097Z"
},
"success": true,
"errors": [],
"messages": []
}
```
For more guidance, refer to [Manage DNS records](https://developers.cloudflare.com/dns/manage-dns-records/).
---
title: Terraform v5 Provider is now generally available · Changelog
description: Cloudflare's new automatically generated Terraform provider is now
available as v5.0.0
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/
md: https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5 Provider is now generally available
Feb 03, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)

Cloudflare's v5 Terraform Provider is now generally available. With this release, Terraform resources are now automatically generated based on OpenAPI Schemas. This change brings alignment across our SDKs, API documentation, and now Terraform Provider. The new provider boosts coverage by increasing support for API properties to 100%, adding 25% more resources, and more than 200 additional data sources. Going forward, this will also reduce the barriers to bringing more resources into Terraform across the broader Cloudflare API. This is a small, but important step to making more of our platform manageable through GitOps, making it easier for you to manage Cloudflare just like you do your other infrastructure.
The Cloudflare Terraform Provider v5 is a ground-up rewrite of the provider and introduces breaking changes for some resource types. Please refer to the [upgrade guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade) for best practices, or the [blog post on automatically generating Cloudflare's Terraform Provider](https://blog.cloudflare.com/automatically-generating-cloudflares-terraform-provider/) for more information about the approach.
For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: Revamped Workers Metrics · Changelog
description: Monitor your Worker's performance with a default set of
automatically enabled metrics.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-03-workers-metrics-revamp/
md: https://developers.cloudflare.com/changelog/2025-02-03-workers-metrics-revamp/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Revamped Workers Metrics
Feb 03, 2025
[Workers](https://developers.cloudflare.com/workers/)
We've revamped the [Workers Metrics dashboard](https://dash.cloudflare.com/?to=/:account/workers/services/view/:worker/production/metrics/).
Now you can easily compare metrics across Worker versions, understand the current state of a [gradual deployment](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/gradual-deployments/), and review key Workers metrics in a single view. This new interface enables you to:
* Drag-and-select using a graphical timepicker for precise metric selection.
* Use histograms to visualize cumulative metrics, allowing you to bucket and compare rates over time.
* Focus on Worker versions by directly interacting with the version numbers in the legend.
* Monitor and compare active gradual deployments.
* Track error rates across versions with grouping both by version and by invocation status.
* Measure how [Smart Placement](https://developers.cloudflare.com/workers/configuration/placement/) improves request duration.
Learn more about [metrics](https://developers.cloudflare.com/workers/observability/metrics-and-analytics).
---
title: AI Gateway adds Cerebras, ElevenLabs, and Cartesia as new providers · Changelog
description: AI Gateway has added Cerebras, ElevenLabs, and Cartesia as new providers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-04-aig-provider-cartesia-eleven-cerebras/
md: https://developers.cloudflare.com/changelog/2025-02-04-aig-provider-cartesia-eleven-cerebras/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Gateway adds Cerebras, ElevenLabs, and Cartesia as new providers
Feb 05, 2025
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/) has added three new providers: [Cartesia](https://developers.cloudflare.com/ai-gateway/usage/providers/cartesia/), [Cerebras](https://developers.cloudflare.com/ai-gateway/usage/providers/cerebras/), and [ElevenLabs](https://developers.cloudflare.com/ai-gateway/usage/providers/elevenlabs/), giving you more even more options for providers you can use through AI Gateway. Here's a brief overview of each:
* [Cartesia](https://developers.cloudflare.com/ai-gateway/usage/providers/cartesia/) provides text-to-speech models that produce natural-sounding speech with low latency.
* [Cerebras](https://developers.cloudflare.com/ai-gateway/usage/providers/cerebras/) delivers low-latency AI inference to Meta's Llama 3.1 8B and Llama 3.3 70B models.
* [ElevenLabs](https://developers.cloudflare.com/ai-gateway/usage/providers/elevenlabs/) offers text-to-speech models with human-like voices in 32 languages.

To get started with AI Gateway, just update the base URL. Here's how you can send a request to [Cerebras](https://developers.cloudflare.com/ai-gateway/usage/providers/cerebras/) using cURL:
```bash
curl -X POST https://gateway.ai.cloudflare.com/v1/ACCOUNT_TAG/GATEWAY/cerebras/chat/completions \
--header 'content-type: application/json' \
--header 'Authorization: Bearer CEREBRAS_TOKEN' \
--data '{
"model": "llama-3.3-70b",
"messages": [
{
"role": "user",
"content": "What is Cloudflare?"
}
]
}'
```
---
title: Fight CSAM More Easily Than Ever · Changelog
description: Simplified setup for Cloudflare's CSAM Scanning Tool, improving
child safety protections for websites.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-04-easier-onboarding-for-csam-scanning-tool/
md: https://developers.cloudflare.com/changelog/2025-02-04-easier-onboarding-for-csam-scanning-tool/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Fight CSAM More Easily Than Ever
Feb 04, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now implement our **child safety tooling**, the **[CSAM Scanning Tool](https://developers.cloudflare.com/cache/reference/csam-scanning/)**, more easily. Instead of requiring external reporting credentials, you only need a verified email address for notifications to onboard. This change makes the tool more accessible to a wider range of customers.
**How It Works**
When enabled, the tool automatically [hashes images for enabled websites as they enter the Cloudflare cache](https://blog.cloudflare.com/the-csam-scanning-tool/). These hashes are then checked against a database of **known abusive images**.
* **Potential match detected?**
* The **content URL is blocked**, and
* **Cloudflare will notify you** about the found matches via the provided email address.
**Updated Service-Specific Terms**
We have also made updates to our **[Service-Specific Terms](https://www.cloudflare.com/service-specific-terms-application-services/#csam-scanning-tool-terms)** to reflect these changes.
---
title: Expanded AI insights in Cloudflare Radar · Changelog
description: Expanded AI insights with new API endpoints for Internet services
rankings, robots.txt, and inference data
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-04-radar-ai-insights/
md: https://developers.cloudflare.com/changelog/2025-02-04-radar-ai-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Expanded AI insights in Cloudflare Radar
Feb 04, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) has expanded its AI insights with new API endpoints for Internet services rankings, robots.txt analysis, and AI inference data.
#### Internet services ranking
Radar now provides [rankings for Internet services](https://developers.cloudflare.com/radar/glossary/#internet-services-ranking), including Generative AI platforms, based on anonymized 1.1.1.1 resolver data. Previously limited to the annual Year in Review, these insights are now available daily via the [API](https://developers.cloudflare.com/api/resources/radar/subresources/ranking/subresources/internet_services/), through the following endpoints:
* [`/ranking/internet_services/top`](https://developers.cloudflare.com/api/resources/radar/subresources/ranking/subresources/internet_services/methods/top/) show service popularity at a specific date.
* [`/ranking/internet_services/timeseries_groups`](https://developers.cloudflare.com/api/resources/radar/subresources/ranking/subresources/internet_services/methods/timeseries_groups/) track ranking trends over time.
#### Robots.txt
Radar now analyzes [robots.txt](https://developers.cloudflare.com/radar/glossary/#robotstxt) files from the top 10,000 domains, identifying AI bot access rules. AI-focused user agents from [ai.robots.txt](https://github.com/ai-robots-txt/ai.robots.txt) are categorized as:
* **Fully allowed/disallowed** if directives apply to all paths (`*`).
* **Partially allowed/disallowed** if restrictions apply to specific paths.
These insights are now available weekly via the [API](https://developers.cloudflare.com/api/resources/radar/subresources/robots_txt/), through the following endpoints:
* [`/robots_txt/top/user_agents/directive`](https://developers.cloudflare.com/api/resources/radar/subresources/robots_txt/subresources/top/subresources/user_agents/methods/directive/) to get the top AI user agents by directive.
* [`/robots_txt/top/domain_categories`](https://developers.cloudflare.com/api/resources/radar/subresources/robots_txt/subresources/top/methods/domain_categories/) to get the top domain categories by robots.txt files.
#### Workers AI
Radar now provides insights into public AI inference models from [Workers AI](https://developers.cloudflare.com/workers-ai/), tracking usage trends across **models** and **tasks**. These insights are now available via the [API](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/inference/), through the following endpoints:
* [`/ai/inference/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/inference/subresources/summary/) to view aggregated `model` and `task` popularity.
* [`/ai/inference/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/inference/subresources/timeseries_groups/) to track changes over time for `model` or `task`.
Learn more about the new Radar AI insights in our [blog post](https://blog.cloudflare.com/expanded-ai-insights-on-cloudflare-radar/).
---
title: Updated leaked credentials database · Changelog
description: New records added to the leaked credentials database.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-04-updated-leaked-credentials-database/
md: https://developers.cloudflare.com/changelog/2025-02-04-updated-leaked-credentials-database/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Updated leaked credentials database
Feb 04, 2025
[WAF](https://developers.cloudflare.com/waf/)
Added new records to the leaked credentials database from a third-party database.
---
title: Request timeouts and retries with AI Gateway · Changelog
description: AI Gateway has added additional request handling, with request
timeouts and request retries
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-05-aig-request-handling/
md: https://developers.cloudflare.com/changelog/2025-02-05-aig-request-handling/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Request timeouts and retries with AI Gateway
Feb 06, 2025
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
AI Gateway adds additional ways to handle requests - [Request Timeouts](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-timeouts) and [Request Retries](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries), making it easier to keep your applications responsive and reliable.
Timeouts and retries can be used on both the [Universal Endpoint](https://developers.cloudflare.com/ai-gateway/usage/universal/) or directly to a [supported provider](https://developers.cloudflare.com/ai-gateway/usage/providers/).
**Request timeouts** A [request timeout](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-timeouts) allows you to trigger [fallbacks](https://developers.cloudflare.com/ai-gateway/configuration/fallbacks/) or a retry if a provider takes too long to respond.
To set a request timeout directly to a provider, add a `cf-aig-request-timeout` header.
```bash
curl https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/workers-ai/@cf/meta/llama-3.1-8b-instruct \
--header 'Authorization: Bearer {cf_api_token}' \
--header 'Content-Type: application/json' \
--header 'cf-aig-request-timeout: 5000'
--data '{"prompt": "What is Cloudflare?"}'
```
**Request retries** A [request retry](https://developers.cloudflare.com/ai-gateway/configuration/request-handling/#request-retries) automatically retries failed requests, so you can recover from temporary issues without intervening.
To set up request retries directly to a provider, add the following headers:
* cf-aig-max-attempts (number)
* cf-aig-retry-delay (number)
* cf-aig-backoff ("constant" | "linear" | "exponential)
---
title: Check status of Email security or Area 1 · Changelog
description: Check the operational status of Email security and Area 1 on the
Cloudflare Status page.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-07-check-status/
md: https://developers.cloudflare.com/changelog/2025-02-07-check-status/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Check status of Email security or Area 1
Feb 27, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
Concerns about performance for Email security or Area 1? You can now check the operational status of both on the [Cloudflare Status page](https://www.cloudflarestatus.com/).
For Email security, look under **Cloudflare Sites and Services**.
* **Dashboard** is the dashboard for Cloudflare, including Email security
* **Email security (Zero Trust)** is the processing of email
* **API** are the Cloudflare endpoints, including the ones for Email security
For Area 1, under **Cloudflare Sites and Services**:
* **Area 1 - Dash** is the dashboard for Cloudflare, including Email security
* **Email security (Area1)** is the processing of email
* **Area 1 - API** are the Area 1 endpoints

This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Create and deploy Workers from Git repositories · Changelog
description: Get started on Workers by choosing a template or importing a Git repository
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-07-new-ways-to-get-started-on-workers/
md: https://developers.cloudflare.com/changelog/2025-02-07-new-ways-to-get-started-on-workers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Create and deploy Workers from Git repositories
Feb 07, 2025
[Workers](https://developers.cloudflare.com/workers/)
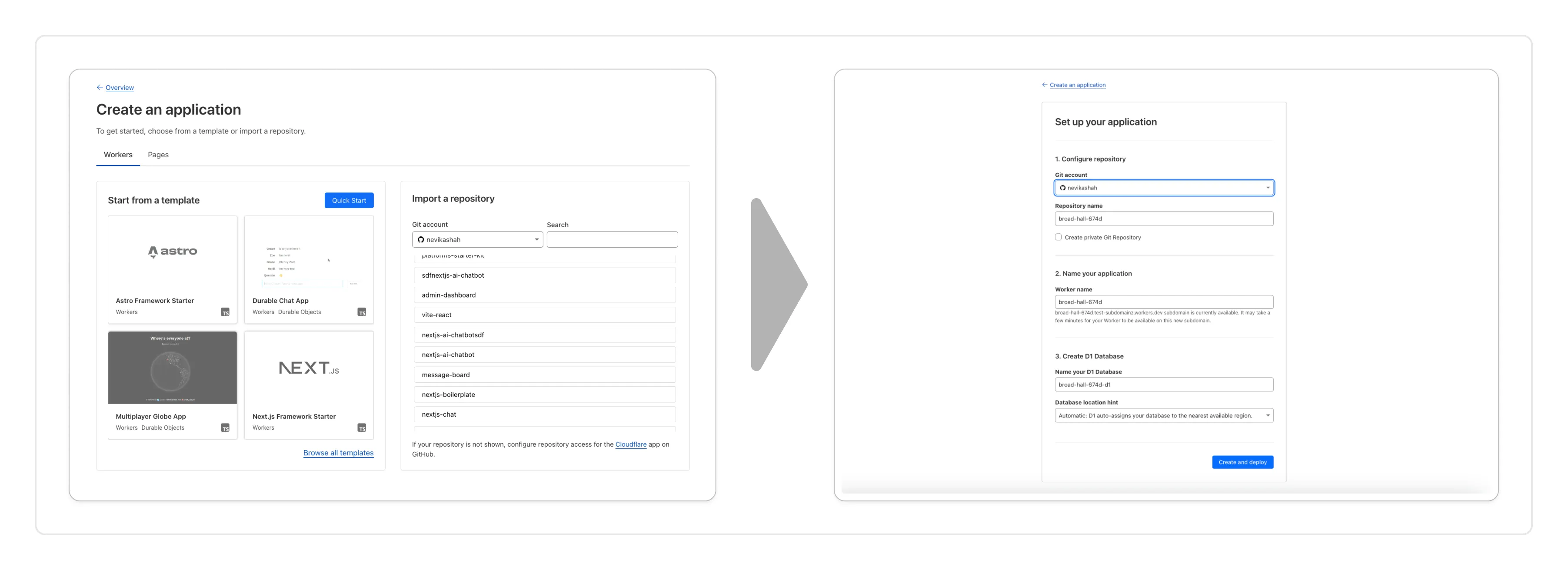
You can now create a Worker by:
* **Importing a Git repository**: Choose an existing Git repo on your GitHub/GitLab account and set up [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/configuration/) to deploy your Worker.
* **Deploying a template with Git**: Choose from a brand new selection of production ready [examples](https://github.com/cloudflare/templates) to help you get started with popular frameworks like [Astro](https://astro.build/), [Remix](https://remix.run/) and [Next](https://nextjs.org/) or build stateful applications with Cloudflare resources like [D1 databases](https://developers.cloudflare.com/d1/), [Workers AI](https://developers.cloudflare.com/workers-ai/) or [Durable Objects](https://developers.cloudflare.com/durable-objects/)! When you're ready to deploy, Cloudflare will set up your project by cloning the template to your GitHub/GitLab account, provisioning any required [resources](https://developers.cloudflare.com/workers/runtime-apis/bindings/) and deploying your Worker.
With every push to your chosen branch, Cloudflare will automatically build and deploy your Worker.
To get started, go to the [Workers dashboard](https://dash.cloudflare.com/?to=/:account/workers-and-pages/create).
These new features are available today in the Cloudflare dashboard to a subset of Cloudflare customers, and will be coming to all customers in the next few weeks. Don't see it in your dashboard, but want early access? Add your Cloudflare Account ID to [this form](https://forms.gle/U1qhkF2snNJDGJJa9).
---
title: Open email links with Security Center · Changelog
description: You can now investigate links in emails with Cloudflare Security
Center to generate a detailed security report.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-07-open-links-security-center/
md: https://developers.cloudflare.com/changelog/2025-02-07-open-links-security-center/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Open email links with Security Center
Feb 07, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You can now investigate links in emails with Cloudflare Security Center to generate a report containing a myriad of technical details: a phishing scan, SSL certificate data, HTTP request and response data, page performance data, DNS records, what technologies and libraries the page uses, and more.

From **Investigation**, go to **View details**, and look for the **Links identified** section. Select **Open in Security Center** next to each link. **Open in Security Center** allows your team to quickly generate a detailed report about the link with no risk to the analyst or your environment.
For more details, refer to [Open links](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#open-links).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: WARP client for macOS (version 2025.1.634.1) · Changelog
description: WARP client for macOS (version 2025.1.634.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-07-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-02-07-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.1.634.1)
Feb 07, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains only a hotfix from the 2025.1.447.1 release. Note: If using macOS Sequoia, Cloudflare recommends the use of macOS 15.2 or later. With macOS 15.2, Apple addressed several issues that may have caused the WARP client to not behave as expected when used with macOS 15.0.x. **Changes and improvements** - Improved device registration retrieval for graceful restarts **Known issues** - macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.2 or later.
---
title: "Custom Errors (beta): Stored Assets & Account-level Rules · Changelog"
description: Cloudflare introduces Custom Errors (beta), building on Custom
Error Responses with new asset storage capabilities
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-11-custom-errors-beta/
md: https://developers.cloudflare.com/changelog/2025-02-11-custom-errors-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Custom Errors (beta): Stored Assets & Account-level Rules
Feb 11, 2025
[Rules](https://developers.cloudflare.com/rules/)
We're introducing [Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) (beta), which builds on our existing Custom Error Responses feature with new asset storage capabilities.
This update allows you to store externally hosted error pages on Cloudflare and reference them in custom error rules, eliminating the need to supply inline content.
This brings the following new capabilities:
* **Custom error assets** – Fetch and store external error pages at the edge for use in error responses.
* **Account-Level custom errors** – Define error handling rules and assets at the account level for consistency across multiple zones. Zone-level rules take precedence over account-level ones, and assets are not shared between levels.
You can use Cloudflare API to upload your existing assets for use with Custom Errors:
```bash
curl "https://api.cloudflare.com/client/v4/zones/{zone_id}/custom_pages/assets" \
--header "Authorization: Bearer " \
--header 'Content-Type: application/json' \
--data '{
"name": "maintenance",
"description": "Maintenance template page",
"url": "https://example.com/"
}'
```
You can then reference the stored asset in a Custom Error rule:
```bash
curl --request PUT \
"https://api.cloudflare.com/client/v4/zones/{zone_id}/rulesets/phases/http_custom_errors/entrypoint" \
--header "Authorization: Bearer " \
--header 'Content-Type: application/json' \
--data '{
"rules": [
{
"action": "serve_error",
"action_parameters": {
"asset_name": "maintenance",
"content_type": "text/html",
"status_code": 503
},
"enabled": true,
"expression": "http.request.uri.path contains \"error\""
}
]
}'
```
---
title: WAF Release - 2025-02-11 · Changelog
description: Cloudflare WAF managed rulesets 2025-02-11 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-11-waf-release/
md: https://developers.cloudflare.com/changelog/2025-02-11-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-02-11
Feb 11, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 742306889c2e4f6087de6646483b4c26 | 100708 | Aviatrix Network - Remote Code Execution - CVE:CVE-2024-50603 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 042228dffe0a4f1587da0e737e924ca3 | 100709 | Next.js - Remote Code Execution - CVE:CVE-2024-46982 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 2a12278325464d6682afb53483a7d8ff | 100710 | Progress Software WhatsUp Gold - Directory Traversal - CVE:CVE-2024-12105 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 82ce3424fbe84e9e99d77332baa8eb34 | 100711 | WordPress - Remote Code Execution - CVE:CVE-2024-56064 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 5afacd39dcfd42f89a6c43f787f5d34e | 100712 | WordPress - Remote Code Execution - CVE:CVE-2024-9047 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 05842b06f0a4415880b58f7fbf72cf8a | 100713 | FortiOS - Auth Bypass - CVE:CVE-2022-40684 | Log | Block | This is a New Detection |
---
title: Configurable multiplexing HTTP/2 to Origin · Changelog
description: Enterprise customers can now configure HTTP/2 multiplexing settings
to optimize origin connections and improve cache performance.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-12-configurable-multiplexing-http2-to-origin/
md: https://developers.cloudflare.com/changelog/2025-02-12-configurable-multiplexing-http2-to-origin/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Configurable multiplexing HTTP/2 to Origin
Feb 12, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now configure HTTP/2 multiplexing settings for origin connections on Enterprise plans. This feature allows you to optimize how Cloudflare manages concurrent requests over HTTP/2 connections to your origin servers, improving cache efficiency and reducing connection overhead.
#### How it works
HTTP/2 multiplexing allows multiple requests to be sent over a single TCP connection. With this configuration option, you can:
1. **Control concurrent streams**: Adjust the maximum number of concurrent streams per connection.
2. **Optimize connection reuse**: Fine-tune connection pooling behavior for your origin infrastructure.
3. **Reduce connection overhead**: Minimize the number of TCP connections required between Cloudflare and your origin.
4. **Improve cache performance**: Better connection management can enhance cache fetch efficiency.
#### Benefits
* **Customizable performance**: Tailor multiplexing settings to your origin's capabilities.
* **Reduced latency**: Fewer connection handshakes improve response times.
* **Lower origin load**: More efficient connection usage reduces server resource consumption.
* **Enhanced scalability**: Better connection management supports higher traffic volumes.
#### Get started
Enterprise customers can configure HTTP/2 multiplexing settings in the [Cloudflare Dashboard](https://dash.cloudflare.com/) or through our [API](https://developers.cloudflare.com/api/).
Important consideration
This setting needs to be tuned carefully for your origin infrastructure. Setting the concurrent stream limit too high can negatively impact performance by saturating the shared TCP connection and overwhelming server processing capacity, leading to increased latency for individual requests.
---
title: Increased Cloudflare Rules limits · Changelog
description: We have upgraded and streamlined limits for Cloudflare Rules
products for everyone.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-12-rules-upgraded-limits/
md: https://developers.cloudflare.com/changelog/2025-02-12-rules-upgraded-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased Cloudflare Rules limits
Feb 12, 2025
[Rules](https://developers.cloudflare.com/rules/)
We have upgraded and streamlined [Cloudflare Rules](https://developers.cloudflare.com/rules/) limits across all plans, simplifying rule management and improving scalability for everyone.
**New limits by product:**
* [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/)
* Free: **20** → **10,000** URL redirects across lists
* Pro: **500** → **25,000** URL redirects across lists
* Business: **500** → **50,000** URL redirects across lists
* Enterprise: **10,000** → **1,000,000** URL redirects across lists
* [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/)
* Free: **5** → **10** connectors
* Enterprise: **125** → **300** connectors
* [Custom Errors](https://developers.cloudflare.com/rules/custom-errors/)
* Pro: **5** → **25** error assets and rules
* Business: **20** → **50** error assets and rules
* Enterprise: **50** → **300** error assets and rules
* [Snippets](https://developers.cloudflare.com/rules/snippets/)
* Pro: **10** → **25** code snippets and rules
* Business: **25** → **50** code snippets and rules
* Enterprise: **50** → **300** code snippets and rules
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/), [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/), [Compression Rules](https://developers.cloudflare.com/rules/compression-rules/), [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/), [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/), and [Transform Rules](https://developers.cloudflare.com/rules/transform/)
* Enterprise: **125** → **300** rules
Gradual rollout
Limits are updated gradually. Some customers may still see previous limits until the rollout is fully completed in the first half of 2025.
---
title: Block files that are password-protected, compressed, or otherwise
unscannable. · Changelog
description: Unscannable files for Download and Upload File Types selectors
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-13-improvements-unscannable-files/
md: https://developers.cloudflare.com/changelog/2025-02-13-improvements-unscannable-files/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Block files that are password-protected, compressed, or otherwise unscannable.
Feb 03, 2025
[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Gateway HTTP policies can now block files that are password-protected, compressed, or otherwise unscannable.
These unscannable files are now matched with the [Download and Upload File Types traffic selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#download-and-upload-file-types) for HTTP policies:
* Password-protected Microsoft Office document
* Password-protected PDF
* Password-protected ZIP archive
* Unscannable ZIP archive
To get started inspecting and modifying behavior based on these and other rules, refer to [HTTP filtering](https://developers.cloudflare.com/cloudflare-one/traffic-policies/initial-setup/http/).
---
title: Upload a certificate bundle with an RSA and ECDSA certificate per custom
hostname · Changelog
description: Upload a certificate bundle with an RSA and ECDSA certificate per
custom hostname
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-14-cert-bundling-for-custom-hostnames/
md: https://developers.cloudflare.com/changelog/2025-02-14-cert-bundling-for-custom-hostnames/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Upload a certificate bundle with an RSA and ECDSA certificate per custom hostname
Feb 14, 2025
[SSL/TLS](https://developers.cloudflare.com/ssl/)
Cloudflare has supported both RSA and ECDSA certificates across our platform for a number of years. Both certificates offer the same security, but ECDSA is more performant due to a smaller key size. However, RSA is more widely adopted and ensures compatibility with legacy clients. Instead of choosing between them, you may want both – that way, ECDSA is used when clients support it, but RSA is available if not.
Now, you can upload both an RSA and ECDSA certificate on a custom hostname via the API.
```plaintext
curl -X POST https://api.cloudflare.com/client/v4/zones/$ZONE_ID/custom_hostnames \
-H 'Content-Type: application/json' \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY" \
-d '{
"hostname": "hostname",
"ssl": {
"custom_cert_bundle": [
{
"custom_certificate": "RSA Cert",
"custom_key": "RSA Key"
},
{
"custom_certificate": "ECDSA Cert",
"custom_key": "ECDSA Key"
}
],
"bundle_method": "force",
"wildcard": false,
"settings": {
"min_tls_version": "1.0"
}
}
}’
```
You can also:
* [Upload](https://developers.cloudflare.com/api/resources/custom_hostnames/methods/create/) an RSA or ECDSA certificate to a custom hostname with an existing ECDSA or RSA certificate, respectively.
* [Replace](https://developers.cloudflare.com/api/resources/custom_hostnames/subresources/certificate_pack/subresources/certificates/methods/update/) the RSA or ECDSA certificate with a certificate of its same type.
* [Delete](https://developers.cloudflare.com/api/resources/custom_hostnames/subresources/certificate_pack/subresources/certificates/methods/delete/) the RSA or ECDSA certificate (if the custom hostname has both an RSA and ECDSA uploaded).
This feature is available for Business and Enterprise customers who have purchased custom certificates.
---
title: Build AI Agents with Example Prompts · Changelog
description: Build applications on Workers with our prompt examples.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-14-example-ai-prompts/
md: https://developers.cloudflare.com/changelog/2025-02-14-example-ai-prompts/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Build AI Agents with Example Prompts
Feb 14, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers ](https://developers.cloudflare.com/workers/)[Workflows](https://developers.cloudflare.com/workflows/)
We've added an [example prompt](https://developers.cloudflare.com/workers/get-started/prompting/) to help you get started with building AI agents and applications on Cloudflare [Workers](https://developers.cloudflare.com/workers/), including [Workflows](https://developers.cloudflare.com/workflows/), [Durable Objects](https://developers.cloudflare.com/durable-objects/), and [Workers KV](https://developers.cloudflare.com/kv/).
You can use this prompt with your favorite AI model, including Claude 3.5 Sonnet, OpenAI's o3-mini, Gemini 2.0 Flash, or Llama 3.3 on Workers AI. Models with large context windows will allow you to paste the prompt directly: provide your own prompt within the `` tags.
```sh
{paste_prompt_here}
user: Build an AI agent using Cloudflare Workflows. The Workflow should run when a new GitHub issue is opened on a specific project with the label 'help' or 'bug', and attempt to help the user troubleshoot the issue by calling the OpenAI API with the issue title and description, and a clear, structured prompt that asks the model to suggest 1-3 possible solutions to the issue. Any code snippets should be formatted in Markdown code blocks. Documentation and sources should be referenced at the bottom of the response. The agent should then post the response to the GitHub issue. The agent should run as the provided GitHub bot account.
```
This prompt is still experimental, but we encourage you to try it out and [provide feedback](https://github.com/cloudflare/cloudflare-docs/issues/new?template=content.edit.yml).
---
title: Customize queue message retention periods · Changelog
description: Customize the retention period for a queue, from a minimum of 60
seconds to a maximum of 14 days.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-14-customize-queue-retention-period/
md: https://developers.cloudflare.com/changelog/2025-02-14-customize-queue-retention-period/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Customize queue message retention periods
Feb 14, 2025
[Queues](https://developers.cloudflare.com/queues/)
You can now customize a queue's message retention period, from a minimum of 60 seconds to a maximum of 14 days. Previously, it was fixed to the default of 4 days.
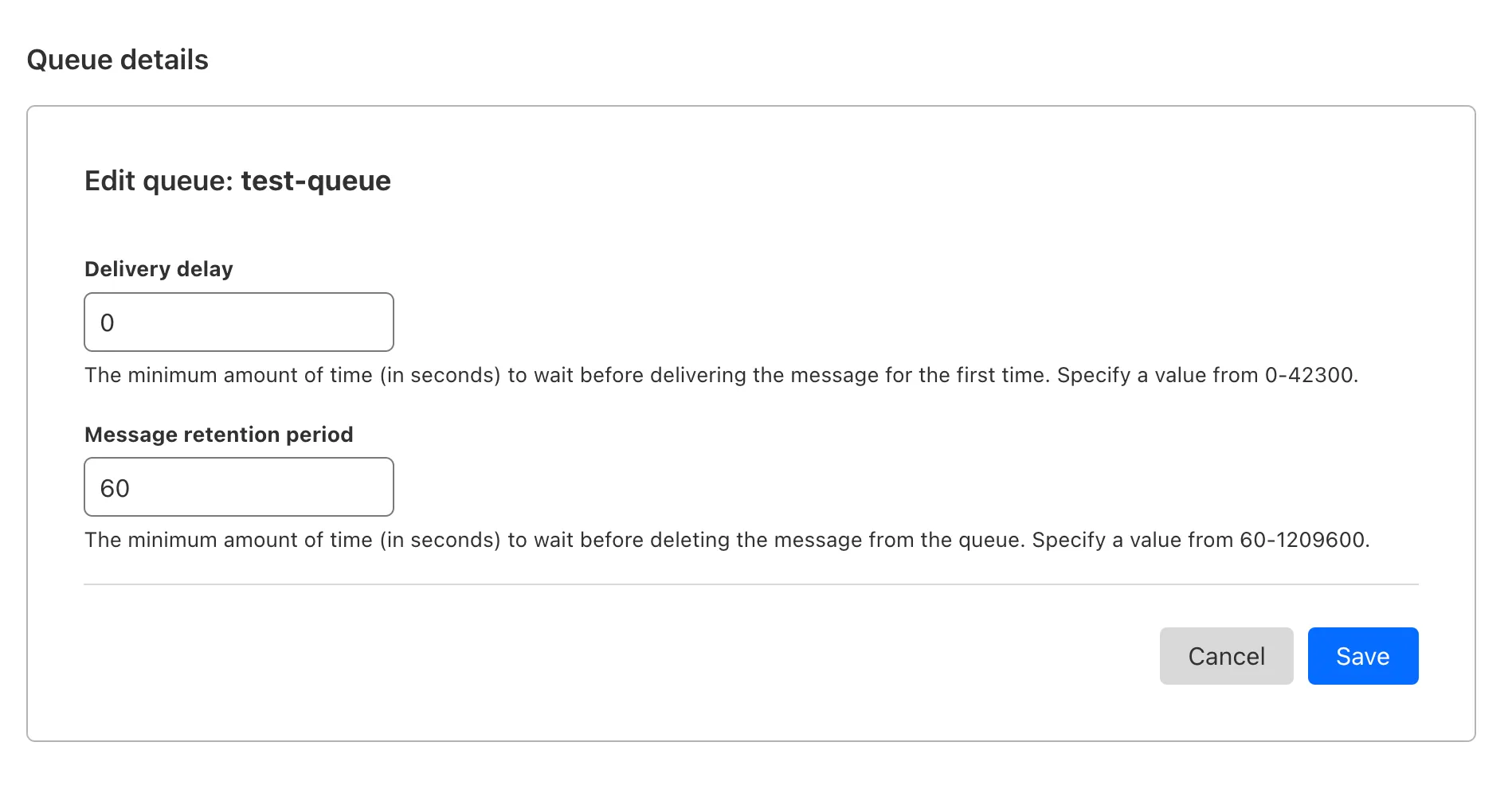
You can customize the retention period on the settings page for your queue, or using Wrangler:
```bash
$ wrangler queues update my-queue --message-retention-period-secs 600
```
This feature is available on all new and existing queues. If you haven't used Cloudflare Queues before, [get started with the Cloudflare Queues guide](https://developers.cloudflare.com/queues/get-started).
---
title: "Rewind, Replay, Resume: Introducing DVR for Stream Live · Changelog"
description: >
Stream has added support for DVR for Live broadcasts. In other words, for
those who didn’t witness the magic of TiVo, you can now allow your viewers to
rewind and replay Live content during broadcasts.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-14-introducing-dvr-for-stream-live/
md: https://developers.cloudflare.com/changelog/2025-02-14-introducing-dvr-for-stream-live/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Rewind, Replay, Resume: Introducing DVR for Stream Live
Feb 14, 2025
[Stream](https://developers.cloudflare.com/stream/)
Previously, all viewers watched "the live edge," or the latest content of the broadcast, synchronously. If a viewer paused for more than a few seconds, the player would automatically "catch up" when playback started again. Seeking through the broadcast was only available once the recording was available after it concluded.
Starting today, customers can make a small adjustment to the player embed or manifest URL to enable the DVR experience for their viewers. By offering this feature as an opt-in adjustment, our customers are empowered to pick the best experiences for their applications.
When building a player embed code or manifest URL, just add `dvrEnabled=true` as a query parameter. There are some things to be aware of when using this option. For more information, refer to [DVR for Live](https://developers.cloudflare.com/stream/stream-live/dvr-for-live/).
---
title: Configure your Magic WAN Connector to connect via static IP assigment ·
Changelog
description: Local console access for bootstrapping Magic WAN Connector
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-14-local-console-access/
md: https://developers.cloudflare.com/changelog/2025-02-14-local-console-access/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Configure your Magic WAN Connector to connect via static IP assigment
Feb 14, 2025
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
You can now locally configure your [Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/) to work in a static IP configuration.
This local method does not require having access to a DHCP Internet connection. However, it does require being comfortable with using tools to access the serial port on Magic WAN Connector as well as using a serial terminal client to access the Connector's environment.
For more details, refer to [WAN with a static IP address](https://developers.cloudflare.com/magic-wan/configuration/connector/configure-hardware-connector/#bootstrap-via-serial-console).
---
title: Super Slurper now transfers data to R2 up to 5x faster · Changelog
description: Super Slurper now transfers data from cloud object storage
providers like AWS S3 and Google Cloud Storage to Cloudflare R2 up to 5x
faster
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-14-r2-super-slurper-faster-migrations/
md: https://developers.cloudflare.com/changelog/2025-02-14-r2-super-slurper-faster-migrations/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Super Slurper now transfers data to R2 up to 5x faster
Feb 14, 2025
[R2](https://developers.cloudflare.com/r2/)
[Super Slurper](https://developers.cloudflare.com/r2/data-migration/super-slurper/) now transfers data from cloud object storage providers like AWS S3 and Google Cloud Storage to [Cloudflare R2](https://developers.cloudflare.com/r2/) up to 5x faster than it did before.
We moved from a centralized service to a distributed system built on the Cloudflare Developer Platform — using [Cloudflare Workers](https://developers.cloudflare.com/workers/), [Durable Objects](https://developers.cloudflare.com/durable-objects/), and [Queues](https://developers.cloudflare.com/queues/) — to both improve performance and increase system concurrency capabilities (and we'll share more details about how we did it soon!)
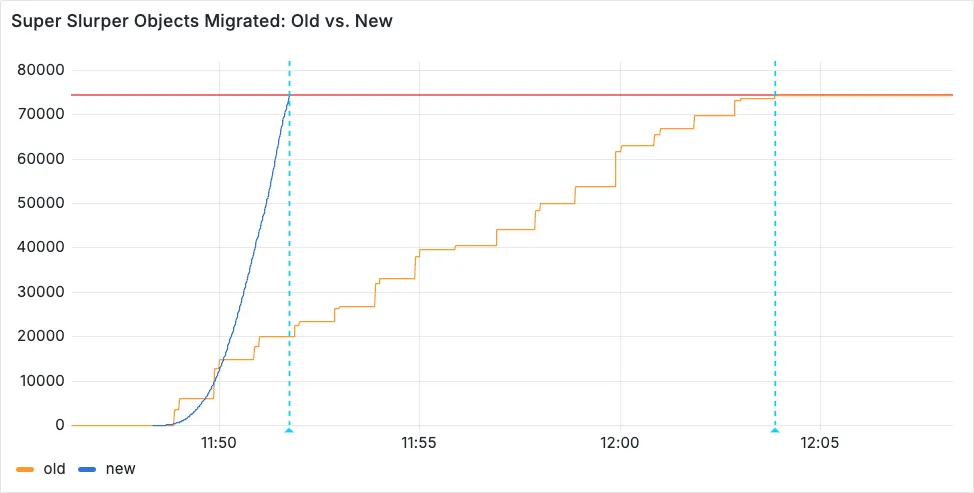
*Time to copy 75,000 objects from AWS S3 to R2 decreased from 15 minutes 30 seconds (old) to 3 minutes 25 seconds (after performance improvements)*
For more information on Super Slurper and how to migrate data from existing object storage to R2, refer to our [documentation](https://developers.cloudflare.com/r2/data-migration/super-slurper/).
---
title: WAF Release - 2025-02-18 · Changelog
description: Cloudflare WAF managed rulesets 2025-02-18 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-18-waf-release/
md: https://developers.cloudflare.com/changelog/2025-02-18-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-02-18
Feb 18, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | d1d45e4f59014f0fb22e0e6aa2ffa4b8 | 100715 | FortiOS - Auth Bypass - CVE:CVE-2024-55591 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 14b5cdeb4cde490ba37d83555a883e12 | 100716 | Ivanti - Auth Bypass - CVE:CVE-2021-44529 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 498fcd81a62a4b5ca943e2de958094d3 | 100717 | SimpleHelp - Auth Bypass - CVE:CVE-2024-57727 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 6e0d8afc36ba4ce9836f81e63b66df22 | 100718 | SonicWall SSLVPN - Auth Bypass - CVE:CVE-2024-53704 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 8eb4536dba1a4da58fbf81c79184699f | 100719 | Yeti Platform - Auth Bypass - CVE:CVE-2024-46507 | Log | Block | This is a New Detection |
---
title: WARP client for Linux (version 2025.1.861.0) · Changelog
description: WARP client for Linux (version 2025.1.861.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-19-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-02-19-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.1.861.0)
Feb 19, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release includes fixes and minor improvements.
**Changes and improvements**
* Improved command line interface for Access for Infrastructure with added function for filtering and ordering.
* Fixed client connectivity issues when switching between managed network profiles that use different WARP protocols.
* Added support for WARP desktop to use additional DoH endpoints to help reduce NAT congestion.
* Improved Wireguard connection stability on reconnections.
* Added additional HTTP/3 QUIC connectivity test to `warp-diag`.
* Added support for collection of system health metrics for enhanced device Digital Experience Monitoring.
* Automated the removal of active registrations for devices with multiple registrations with the same Zero Trust organization.
---
title: WARP client for macOS (version 2025.1.861.0) · Changelog
description: WARP client for macOS (version 2025.1.861.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-19-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-02-19-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.1.861.0)
Feb 19, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
Note: If using macOS Sequoia, Cloudflare recommends the use of macOS 15.3 or later. With macOS 15.3, Apple addressed several issues that may have caused the WARP client to not behave as expected when used with macOS 15.0.x.
**Changes and improvements**
* Improved command line interface for Access for Infrastructure with added function for filtering and ordering.
* Fixed client connectivity issues when switching between managed network profiles that use different WARP protocols.
* Improved OS version posture checks on macOS for greater reliability and availability.
* Added support for WARP desktop to use additional DoH endpoints to help reduce NAT congestion.
* Improved Wireguard connection stability on reconnections.
* Added additional HTTP/3 QUIC connectivity test to `warp-diag`.
* Added support for collection of system health metrics for enhanced device Digital Experience Monitoring.
* Automated the removal of active registrations for devices with multiple registrations with the same Zero Trust organization.
* Fixes issues with deleted registration at start up.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
---
title: WARP client for Windows (version 2025.1.861.0) · Changelog
description: WARP client for Windows (version 2025.1.861.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-19-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-02-19-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.1.861.0)
Feb 19, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains only improvements.
**Changes and improvements**
* Improved command line interface for Access for Infrastructure with added function for filtering and ordering.
* Fixed client connectivity issues when switching between managed network profiles that use different WARP protocols.
* Added support for WARP desktop to use additional DoH endpoints to help reduce NAT congestion.
* Improved connectivity check reliability in certain split tunnel configurations.
* Improved reading of device DNS settings at connection restart.
* Improved WARP connectivity in environments with virtual machine interfaces.
* Improved Wireguard connection stability on reconnections.
* Improved reliability of device posture checks for OS Version, Unique Client ID, Domain Joined, Disk Encryption, and Firewall attributes.
* Added additional HTTP/3 QUIC connectivity test to warp-diag.
* Added support for collection of system health metrics for enhanced device Digital Experience Monitoring.
* Automated the removal of active registrations for devices with multiple registrations with the same Zero Trust organization.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Autofix Worker name configuration errors at build time · Changelog
description: Workers Builds automatically creates a pull request to update the
name field in the wrangler file if it doesn’t match your Worker's name in the
Cloudflare dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-20-builds-name-conflict/
md: https://developers.cloudflare.com/changelog/2025-02-20-builds-name-conflict/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Autofix Worker name configuration errors at build time
Feb 20, 2025
[Workers](https://developers.cloudflare.com/workers/)
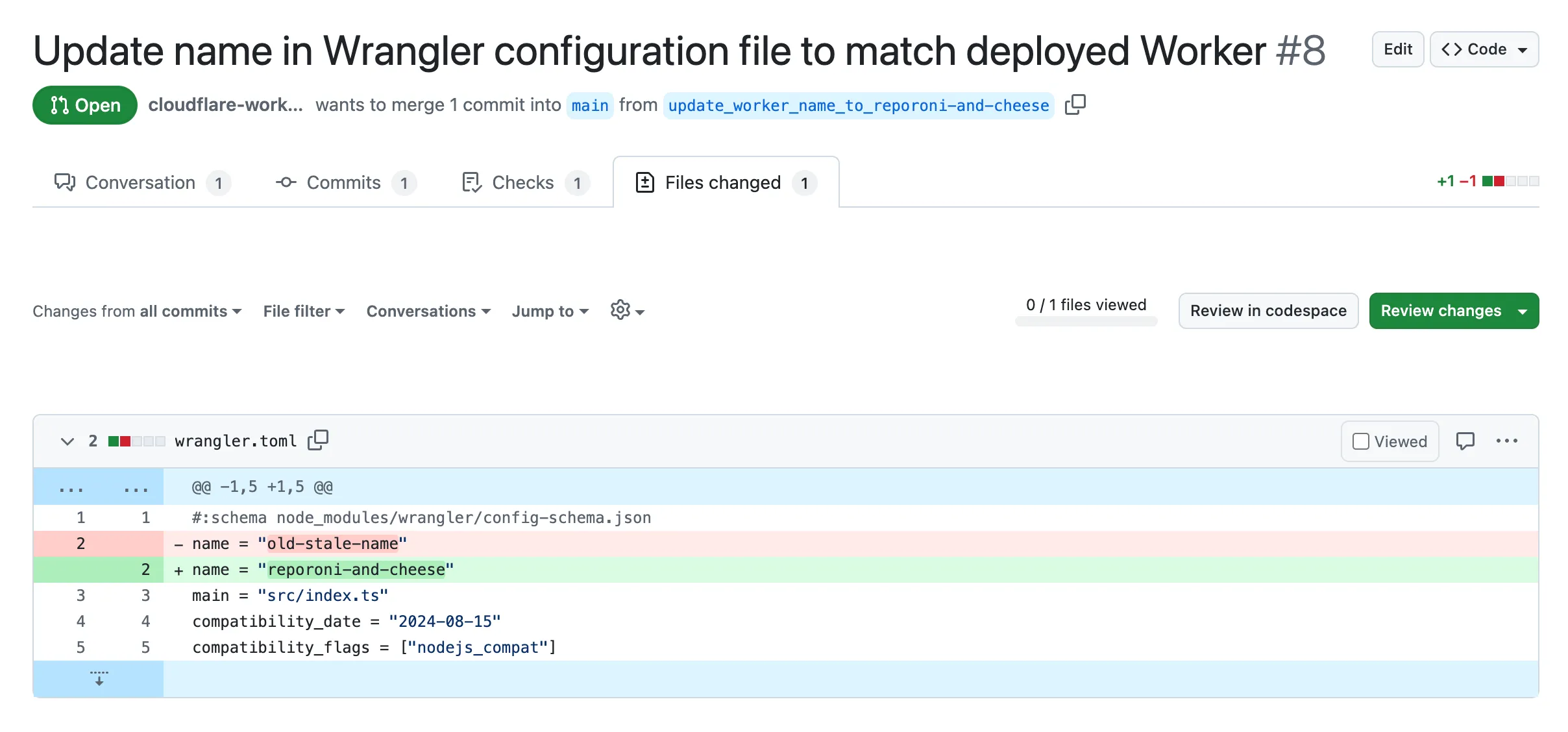
Small misconfigurations shouldn’t break your deployments. Cloudflare is introducing automatic error detection and fixes in [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/), identifying common issues in your wrangler.toml or wrangler.jsonc and proactively offering fixes, so you spend less time debugging and more time shipping.
Here's how it works:
1. Before running your build, Cloudflare checks your Worker's Wrangler configuration file (wrangler.toml or wrangler.jsonc) for common errors.
2. Once you submit a build, if Cloudflare finds an error it can fix, it will submit a pull request to your repository that fixes it.
3. Once you merge this pull request, Cloudflare will run another build.
We're starting with fixing name mismatches between your Wrangler file and the Cloudflare dashboard, a top cause of build failures.
This is just the beginning, we want your feedback on what other errors we should catch and fix next. Let us know in the Cloudflare Developers Discord, [#workers-and-pages-feature-suggestions](https://discord.com/channels/595317990191398933/1064502845061210152).
---
title: Workers for Platforms - Instant dispatch for newly created User Workers ·
Changelog
description: Newly uploaded user Worker scripts are now immediately available
for dispatch upon a successful API response.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-20-synchronous-uploads/
md: https://developers.cloudflare.com/changelog/2025-02-20-synchronous-uploads/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers for Platforms - Instant dispatch for newly created User Workers
Feb 20, 2025
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/) is an architecture wherein a centralized [dispatch Worker](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/#dynamic-dispatch-worker) processes incoming requests and routes them to isolated sub-Workers, called [User Workers](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/#user-workers).

Previously, when a new User Worker was uploaded, there was a short delay before it became available for dispatch. This meant that even though an API request could return a 200 OK response, the script might not yet be ready to handle requests, causing unexpected failures for platforms that immediately dispatch to new Workers.
**With this update, first-time uploads of User Workers are now deployed synchronously**. A 200 OK response guarantees the script is fully provisioned and ready to handle traffic immediately, ensuring more predictable deployments and reducing errors.
---
title: Workers AI updated pricing · Changelog
description: Granular pricing in units and neurons
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-20-updated-pricing-docs/
md: https://developers.cloudflare.com/changelog/2025-02-20-updated-pricing-docs/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers AI updated pricing
Feb 20, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We've updated the Workers AI [pricing](https://developers.cloudflare.com/workers-ai/platform/pricing/) to include the latest models and how model usage maps to Neurons.
* Each model's core input format(s) (tokens, audio seconds, images, etc) now include mappings to Neurons, making it easier to understand how your included Neuron volume is consumed and how you are charged at scale
* Per-model pricing, instead of the previous bucket approach, allows us to be more flexible on how models are charged based on their size, performance and capabilities. As we optimize each model, we can then pass on savings for that model.
* You will still only pay for what you consume: Workers AI inference is serverless, and not billed by the hour.
Going forward, models will be launched with their associated Neuron costs, and we'll be updating the Workers AI dashboard and API to reflect consumption in both raw units and Neurons. Visit the [Workers AI pricing](https://developers.cloudflare.com/workers-ai/platform/pricing/) page to learn more about Workers AI pricing.
---
title: Bind the Images API to your Worker · Changelog
description: >
You can now interact with the Images API directly in your Worker with Image
Bindings.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-21-images-bindings-in-workers/
md: https://developers.cloudflare.com/changelog/2025-02-21-images-bindings-in-workers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Bind the Images API to your Worker
Feb 24, 2025
[Cloudflare Images](https://developers.cloudflare.com/images/)
You can now [interact with the Images API](https://developers.cloudflare.com/images/transform-images/bindings/) directly in your Worker.
This allows more fine-grained control over transformation request flows and cache behavior. For example, you can resize, manipulate, and overlay images without requiring them to be accessible through a URL.
The Images binding can be configured in the Cloudflare dashboard for your Worker or in the Wrangler configuration file in your project's directory:
* wrangler.jsonc
```jsonc
{
"images": {
"binding": "IMAGES", // i.e. available in your Worker on env.IMAGES
},
}
```
* wrangler.toml
```toml
[images]
binding = "IMAGES"
```
Within your Worker code, you can interact with this binding by using `env.IMAGES`.
Here's how you can rotate, resize, and blur an image, then output the image as AVIF:
```ts
const info = await env.IMAGES.info(stream);
// stream contains a valid image, and width/height is available on the info object
const response = (
await env.IMAGES.input(stream)
.transform({ rotate: 90 })
.transform({ width: 128 })
.transform({ blur: 20 })
.output({ format: "image/avif" })
).response();
return response;
```
For more information, refer to [Images Bindings](https://developers.cloudflare.com/images/transform-images/bindings/).
---
title: Workers AI larger context windows · Changelog
description: Updated Workers AI models with larger context windows
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-24-context-windows/
md: https://developers.cloudflare.com/changelog/2025-02-24-context-windows/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers AI larger context windows
Feb 24, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We've updated the Workers AI text generation models to include context windows and limits definitions and changed our APIs to estimate and validate the number of tokens in the input prompt, not the number of characters.
This update allows developers to use larger context windows when interacting with Workers AI models, which can lead to better and more accurate results.
Our [catalog page](https://developers.cloudflare.com/workers-ai/models/) provides more information about each model's supported context window.
---
title: Super Slurper now supports migrations from all S3-compatible storage
providers · Changelog
description: Super Slurper now supports migrations from all S3-compatible storage providers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-24-r2-super-slurper-s3-compatible-support/
md: https://developers.cloudflare.com/changelog/2025-02-24-r2-super-slurper-s3-compatible-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Super Slurper now supports migrations from all S3-compatible storage providers
Feb 24, 2025
[R2](https://developers.cloudflare.com/r2/)
[Super Slurper](https://developers.cloudflare.com/r2/data-migration/super-slurper/) can now migrate data from any S3-compatible object storage provider to [Cloudflare R2](https://developers.cloudflare.com/r2/). This includes transfers from services like MinIO, Wasabi, Backblaze B2, and DigitalOcean Spaces.
For more information on Super Slurper and how to migrate data from your existing S3-compatible storage buckets to R2, refer to our [documentation](https://developers.cloudflare.com/r2/data-migration/super-slurper/).
---
title: WAF Release - 2025-02-24 · Changelog
description: Cloudflare WAF managed rulesets 2025-02-24 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-24-waf-release/
md: https://developers.cloudflare.com/changelog/2025-02-24-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-02-24
Feb 24, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | f7b9d265b86f448989fb0f054916911e | 100718A | SonicWall SSLVPN 2 - Auth Bypass - CVE:CVE-2024-53704 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 77c13c611d2a4fa3a89c0fafc382fdec | 100720 | Palo Alto Networks - Auth Bypass - CVE:CVE-2025-0108 | Log | Block | This is a New Detection |
---
title: Zaraz moves to the “Tag Management” category in the Cloudflare dashboard
· Changelog
description: Easier tag management and configuration with Zaraz at the account level
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-24-zaraz-dash-placement/
md: https://developers.cloudflare.com/changelog/2025-02-24-zaraz-dash-placement/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Zaraz moves to the “Tag Management” category in the Cloudflare dashboard
Feb 24, 2025
[Zaraz](https://developers.cloudflare.com/zaraz/)

Previously, you could only configure Zaraz by going to each individual zone under your Cloudflare account. Now, if you’d like to get started with Zaraz or manage your existing configuration, you can navigate to the [Tag Management](https://dash.cloudflare.com/?to=/:account/tag-management/zaraz) section on the Cloudflare dashboard – this will make it easier to compare and configure the same settings across multiple zones.
These changes will not alter any existing configuration or entitlements for zones you already have Zaraz enabled on. If you’d like to edit existing configurations, you can go to the [Tag Setup](https://dash.cloudflare.com/?to=/:account/tag-management/zaraz) section of the dashboard, and select the zone you'd like to edit.
---
title: Introducing the Agents SDK · Changelog
description: Build and ship AI Agents on Cloudflare using the Agents SDK
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-25-agents-sdk/
md: https://developers.cloudflare.com/changelog/2025-02-25-agents-sdk/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing the Agents SDK
Feb 25, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We've released the [Agents SDK](http://blog.cloudflare.com/build-ai-agents-on-cloudflare/), a package and set of tools that help you build and ship AI Agents.
You can get up and running with a [chat-based AI Agent](https://github.com/cloudflare/agents-starter) (and deploy it to Workers) that uses the Agents SDK, tool calling, and state syncing with a React-based front-end by running the following command:
```sh
npm create cloudflare@latest agents-starter -- --template="cloudflare/agents-starter"
# open up README.md and follow the instructions
```
You can also add an Agent to any existing Workers application by installing the `agents` package directly
```sh
npm i agents
```
... and then define your first Agent:
```ts
import { Agent } from "agents";
export class YourAgent extends Agent {
// Build it out
// Access state on this.state or query the Agent's database via this.sql
// Handle WebSocket events with onConnect and onMessage
// Run tasks on a schedule with this.schedule
// Call AI models
// ... and/or call other Agents.
}
```
Head over to the [Agents documentation](https://developers.cloudflare.com/agents/) to learn more about the Agents SDK, the SDK APIs, as well as how to test and deploying agents to production.
---
title: Use DLP Assist for M365 · Changelog
description: Quickly deploy a free Email DLP solution for Microsoft 365 environments.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-25-dlp-assist-for-m365/
md: https://developers.cloudflare.com/changelog/2025-02-25-dlp-assist-for-m365/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Use DLP Assist for M365
Feb 25, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
Cloudflare Email security customers who have Microsoft 365 environments can quickly deploy an Email DLP (Data Loss Prevention) solution for free.
Simply deploy our add-in, create a DLP policy in Cloudflare, and configure Outlook to trigger behaviors like displaying a banner, alerting end users before sending, or preventing delivery entirely.
Refer to [Outbound Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/email-security/outbound-dlp/) to learn more about this feature.
In GUI alert:

Alert before sending:

Prevent delivery:

This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Workers AI now supports structured JSON outputs. · Changelog
description: Workers AI JSON Mode adds structured outputs support
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-25-json-mode/
md: https://developers.cloudflare.com/changelog/2025-02-25-json-mode/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers AI now supports structured JSON outputs.
Feb 25, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Workers AI now supports structured JSON outputs with [JSON mode](https://developers.cloudflare.com/workers-ai/features/json-mode/), which allows you to request a structured output response when interacting with AI models.
This makes it much easier to retrieve structured data from your AI models, and avoids the (error prone!) need to parse large unstructured text responses to extract your data.
JSON mode in Workers AI is compatible with the OpenAI SDK's [structured outputs](https://platform.openai.com/docs/guides/structured-outputs) `response_format` API, which can be used directly in a Worker:
* JavaScript
```js
import { OpenAI } from "openai";
// Define your JSON schema for a calendar event
const CalendarEventSchema = {
type: "object",
properties: {
name: { type: "string" },
date: { type: "string" },
participants: { type: "array", items: { type: "string" } },
},
required: ["name", "date", "participants"],
};
export default {
async fetch(request, env) {
const client = new OpenAI({
apiKey: env.OPENAI_API_KEY,
// Optional: use AI Gateway to bring logs, evals & caching to your AI requests
// https://developers.cloudflare.com/ai-gateway/usage/providers/openai/
// baseUrl: "https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/openai"
});
const response = await client.chat.completions.create({
model: "gpt-4o-2024-08-06",
messages: [
{ role: "system", content: "Extract the event information." },
{
role: "user",
content: "Alice and Bob are going to a science fair on Friday.",
},
],
// Use the `response_format` option to request a structured JSON output
response_format: {
// Set json_schema and provide ra schema, or json_object and parse it yourself
type: "json_schema",
schema: CalendarEventSchema, // provide a schema
},
});
// This will be of type CalendarEventSchema
const event = response.choices[0].message.parsed;
return Response.json({
calendar_event: event,
});
},
};
```
* TypeScript
```ts
import { OpenAI } from "openai";
interface Env {
OPENAI_API_KEY: string;
}
// Define your JSON schema for a calendar event
const CalendarEventSchema = {
type: "object",
properties: {
name: { type: "string" },
date: { type: "string" },
participants: { type: "array", items: { type: "string" } },
},
required: ["name", "date", "participants"],
};
export default {
async fetch(request: Request, env: Env) {
const client = new OpenAI({
apiKey: env.OPENAI_API_KEY,
// Optional: use AI Gateway to bring logs, evals & caching to your AI requests
// https://developers.cloudflare.com/ai-gateway/usage/providers/openai/
// baseUrl: "https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/openai"
});
const response = await client.chat.completions.create({
model: "gpt-4o-2024-08-06",
messages: [
{ role: "system", content: "Extract the event information." },
{
role: "user",
content: "Alice and Bob are going to a science fair on Friday.",
},
],
// Use the `response_format` option to request a structured JSON output
response_format: {
// Set json_schema and provide ra schema, or json_object and parse it yourself
type: "json_schema",
schema: CalendarEventSchema, // provide a schema
},
});
// This will be of type CalendarEventSchema
const event = response.choices[0].message.parsed;
return Response.json({
calendar_event: event,
});
},
};
```
To learn more about JSON mode and structured outputs, visit the [Workers AI documentation](https://developers.cloudflare.com/workers-ai/features/json-mode/).
---
title: Easily Exclude EU Visitors from RUM · Changelog
description: Enable RUM monitoring for your website and respect privacy laws with ease.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-25-rum-exclude-eu/
md: https://developers.cloudflare.com/changelog/2025-02-25-rum-exclude-eu/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Easily Exclude EU Visitors from RUM
Feb 26, 2024
[Cloudflare Web Analytics](https://developers.cloudflare.com/web-analytics/)
You can now easily enable Real User Monitoring (RUM) monitoring for your hostnames, while safely dropping requests from visitors in the European Union to comply with GDPR and CCPA.

Our Web Analytics product has always been centered on giving you insights into your users' experience that you need to provide the best quality experience, without sacrificing user privacy in the process.
To help with that aim, you can now selectively enable RUM monitoring for your hostname and exclude EU visitor data in a single click. If you opt for this option, we will drop all metrics collected by our EU data centeres automatically.
You can learn more about what metrics are reported by Web Analytics and how it is collected [in the Web Analytics documentation](https://developers.cloudflare.com/web-analytics/data-metrics/). You can enable Web Analytics on any hostname by going to the [Web Analytics](https://dash.cloudflare.com/?to=/:account/web-analytics/sites) section of the dashboard, selecting "Manage Site" for the hostname you want to monitor, and choosing the appropriate enablement option.
---
title: Concurrent Workflow instances limits increased. · Changelog
description: Increased concurrency limits for Workflows instances - workflows
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-25-workflows-concurrency-increased/
md: https://developers.cloudflare.com/changelog/2025-02-25-workflows-concurrency-increased/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Concurrent Workflow instances limits increased.
Feb 25, 2025
[Workflows](https://developers.cloudflare.com/workflows/)
[Workflows](https://developers.cloudflare.com/workflows/) now supports up to 4,500 concurrent (running) instances, up from the previous limit of 100. This limit will continue to increase during the Workflows open beta. This increase applies to all users on the Workers Paid plan, and takes effect immediately.
Review the Workflows [limits documentation](https://developers.cloudflare.com/workflows/reference/limits) and/or dive into the [get started guide](https://developers.cloudflare.com/workflows/get-started/guide/) to start building on Workflows.
---
title: Introducing Guardrails in AI Gateway · Changelog
description: Keep AI interactions secure and risk-free with Guardrails in AI Gateway
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-26-guardrails/
md: https://developers.cloudflare.com/changelog/2025-02-26-guardrails/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing Guardrails in AI Gateway
Feb 26, 2025
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
[AI Gateway](https://developers.cloudflare.com/ai-gateway/) now includes [Guardrails](https://developers.cloudflare.com/ai-gateway/features/guardrails/), to help you monitor your AI apps for harmful or inappropriate content and deploy safely.
Within the AI Gateway settings, you can configure:
* **Guardrails**: Enable or disable content moderation as needed.
* **Evaluation scope**: Select whether to moderate user prompts, model responses, or both.
* **Hazard categories**: Specify which categories to monitor and determine whether detected inappropriate content should be blocked or flagged.

Learn more in the [blog](https://blog.cloudflare.com/guardrails-in-ai-gateway/) or our [documentation](https://developers.cloudflare.com/ai-gateway/features/guardrails/).
---
title: New REST API is in open beta! · Changelog
description: We've released a new REST API in open beta.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-27-br-rest-api-beta/
md: https://developers.cloudflare.com/changelog/2025-02-27-br-rest-api-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New REST API is in open beta!
Feb 27, 2025
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We've released a new REST API for [Browser Rendering](https://developers.cloudflare.com/browser-rendering/) in open beta, making interacting with browsers easier than ever. This new API provides endpoints for common browser actions, with more to be added in the future.
With the **REST API** you can:
* **Capture screenshots** – Use `/screenshot` to take a screenshot of a webpage from provided URL or HTML.
* **Generate PDFs** – Use `/pdf` to convert web pages into PDFs.
* **Extract HTML content** – Use `/content` to retrieve the full HTML from a page. **Snapshot (HTML + Screenshot)** – Use `/snapshot` to capture both the page's HTML and a screenshot in one request
* **Scrape Web Elements** – Use `/scrape` to extract specific elements from a page.
For example, to capture a screenshot:
```bash
curl -X POST 'https://api.cloudflare.com/client/v4/accounts//browser-rendering/screenshot' \
-H 'Authorization: Bearer ' \
-H 'Content-Type: application/json' \
-d '{
"html": "Hello World!",
"screenshotOptions": {
"type": "webp",
"omitBackground": true
}
}' \
--output "screenshot.webp"
```
Learn more in our [documentation](https://developers.cloudflare.com/browser-rendering/rest-api/).
---
title: DNS Insights in Cloudflare Radar · Changelog
description: Expanded DNS insights with new API endpoints for 1.1.1.1 resolver
aggregated traffic data
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-27-radar-dns-insights/
md: https://developers.cloudflare.com/changelog/2025-02-27-radar-dns-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## DNS Insights in Cloudflare Radar
Feb 27, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) has expanded its DNS insights, providing visibility into aggregated traffic and usage trends observed by our [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/) DNS resolver. In addition to global, location, and ASN traffic trends, we are also providing perspectives on protocol usage, query/response characteristics, and DNSSEC usage.
Previously limited to the [`top`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/subresources/top/) locations and ASes endpoints, we have now introduced the following endpoints:
* [`/dns/timeseries`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/methods/timeseries/): Retrieves DNS query volume over time.
* [`/dns/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/subresources/summary/): Retrieves summaries of DNS query distribution across ten different dimensions.
* [`/dns/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/subresources/timeseries_groups/): Retrieves timeseries data for DNS query distribution across ten different dimensions.
For the `summary` and `timeseries_groups` endpoints, the following dimensions are available, displaying the distribution of DNS queries based on:
* `cache_hit`: Cache status (hit vs. miss).
* `dnsssec`: DNSSEC support status (secure, insecure, invalid or other).
* `dnsssec_aware`: DNSSEC client awareness (aware vs. not-aware).
* `dnsssec_e2e`: End-to-end security (secure vs. insecure).
* `ip_version`: IP version (IPv4 vs. IPv6).
* `matching_answer`: Matching answer status (match vs. no-match).
* `protocol`: Transport protocol (UDP, TLS, HTTPS or TCP).
* `query_type`: Query type (`A`, `AAAA`, `PTR`, etc.).
* `response_code`: Response code (`NOERROR`, `NXDOMAIN`, `REFUSED`, etc.).
* `response_ttl`: Response TTL.
Learn more about the new Radar DNS insights in our [blog post](https://blog.cloudflare.com/new-dns-section-on-cloudflare-radar/), and check out the [new Radar page](https://radar.cloudflare.com/dns).
---
title: Use the latest JavaScript features with Wrangler CLI v4.0.0-rc.0 · Changelog
description: You can now try out the v4 RC for Wrangler by installing `wrangler@4.0.0-rc.0`
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-02-28-wrangler-v4-rc/
md: https://developers.cloudflare.com/changelog/2025-02-28-wrangler-v4-rc/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Use the latest JavaScript features with Wrangler CLI v4.0.0-rc.0
Feb 28, 2025
[Workers](https://developers.cloudflare.com/workers/)
We've released a release candidate of the next major version of [Wrangler](https://developers.cloudflare.com/workers/wrangler/), the CLI for Cloudflare Workers — `wrangler@4.0.0-rc.0`.
You can run the following command to install it and be one of the first to try it out:
* npm
```sh
npm i wrangler@v4-rc
```
* yarn
```sh
yarn add wrangler@v4-rc
```
* pnpm
```sh
pnpm add wrangler@v4-rc
```
Unlike previous major versions of Wrangler, which were [foundational rewrites](https://blog.cloudflare.com/wrangler-v2-beta/) and [rearchitectures](https://blog.cloudflare.com/wrangler3/) — Version 4 of Wrangler includes a much smaller set of changes. If you use Wrangler today, your workflow is very unlikely to change. Before we release Wrangler v4 and advance past the release candidate stage, we'll share a detailed migration guide in the Workers developer docs. But for the vast majority of cases, you won't need to do anything to migrate — things will just work as they do today. We are sharing this release candidate in advance of the official release of v4, so that you can try it out early and share feedback.
#### New JavaScript language features that you can now use with Wrangler v4
Version 4 of Wrangler updates the version of [esbuild](https://esbuild.github.io/) that Wrangler uses internally, allowing you to use modern JavaScript language features, including:
##### The `using` keyword from Explicit Resource Management
The [`using` keyword from the Explicit Resource Management standard](https://developers.cloudflare.com/workers/runtime-apis/rpc/lifecycle/#explicit-resource-management) makes it easier to work with the [JavaScript-native RPC system built into Workers](https://developers.cloudflare.com/workers/runtime-apis/rpc/). This means that when you obtain a stub, you can ensure that it is automatically disposed when you exit scope it was created in:
```js
function sendEmail(id, message) {
using user = await env.USER_SERVICE.findUser(id);
await user.sendEmail(message);
// user[Symbol.dispose]() is implicitly called at the end of the scope.
}
```
##### Import attributes
[Import attributes](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Statements/import/with) allow you to denote the type or other attributes of the module that your code imports. For example, you can import a JSON module, using the following syntax:
```js
import data from "./data.json" with { type: "json" };
```
#### Other changes
##### `--local` is now the default for all CLI commands
All commands that access resources (for example, `wrangler kv`, `wrangler r2`, `wrangler d1`) now access local datastores by default, ensuring consistent behavior.
##### Clearer policy for the minimum required version of Node.js required to run Wrangler
Moving forward, the [active, maintenance, and current versions of Node.js](https://nodejs.org/en/about/previous-releases) will be officially supported by Wrangler. This means the minimum officially supported version of Node.js you must have installed for Wrangler v4 will be Node.js v18 or later. This policy mirrors how many other packages and CLIs support older versions of Node.js, and ensures that as long as you are using a version of Node.js that the Node.js project itself supports, this will be supported by Wrangler as well.
##### Features previously deprecated in Wrangler v3 are now removed in Wrangler v4
All previously deprecated features in [Wrangler v2](https://developers.cloudflare.com/workers/wrangler/deprecations/#wrangler-v2) and in [Wrangler v3](https://developers.cloudflare.com/workers/wrangler/deprecations/#wrangler-v3) have now been removed. Additionally, the following features that were deprecated during the Wrangler v3 release have been removed:
* Legacy Assets (using `wrangler dev/deploy --legacy-assets` or the `legacy_assets` config file property). Instead, we recommend you [migrate to Workers assets](https://developers.cloudflare.com/workers/static-assets/).
* Legacy Node.js compatibility (using `wrangler dev/deploy --node-compat` or the `node_compat` config file property). Instead, use the [`nodejs_compat` compatibility flag](https://developers.cloudflare.com/workers/runtime-apis/nodejs). This includes the functionality from legacy `node_compat` polyfills and natively implemented Node.js APIs.
* `wrangler version`. Instead, use `wrangler --version` to check the current version of Wrangler.
* `getBindingsProxy()` (via `import { getBindingsProxy } from "wrangler"`). Instead, use the [`getPlatformProxy()` API](https://developers.cloudflare.com/workers/wrangler/api/#getplatformproxy), which takes exactly the same arguments.
* `usage_model`. This no longer has any effect, after the [rollout of Workers Standard Pricing](https://blog.cloudflare.com/workers-pricing-scale-to-zero/).
We'd love your feedback! If you find a bug or hit a roadblock when upgrading to Wrangler v4, [open an issue on the `cloudflare/workers-sdk` repository on GitHub](https://github.com/cloudflare/workers-sdk/issues/new?template=bug-template.yaml).
---
title: Use Logpush for Email security detections · Changelog
description: Send detection logs to an endpoint of your choice with Cloudflare Logpush.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-01-logpush-detections/
md: https://developers.cloudflare.com/changelog/2025-03-01-logpush-detections/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Use Logpush for Email security detections
Mar 01, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You can now send detection logs to an endpoint of your choice with Cloudflare Logpush.
Filter logs matching specific criteria you have set and select from over 25 fields you want to send. When creating a new Logpush job, remember to select **Email security alerts** as the dataset.

For more information, refer to [Enable detection logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/enable-logs/#enable-detection-logs).
This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: New SAML and OIDC Fields and SAML transforms for Access for SaaS · Changelog
description: Access for SaaS new SAML and OIDC Fields and SAML transforms
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-03-saml-oidc-fields-saml-transformations/
md: https://developers.cloudflare.com/changelog/2025-03-03-saml-oidc-fields-saml-transformations/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New SAML and OIDC Fields and SAML transforms for Access for SaaS
Mar 03, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Access for SaaS applications](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/http-apps/saas-apps/) now include more configuration options to support a wider array of SaaS applications.
**SAML and OIDC Field Additions**
OIDC apps now include:
* Group Filtering via RegEx
* OIDC Claim mapping from an IdP
* OIDC token lifetime control
* Advanced OIDC auth flows including hybrid and implicit flows

SAML apps now include improved SAML attribute mapping from an IdP.

**SAML transformations**
SAML identities sent to Access applications can be fully customized using JSONata expressions. This allows admins to configure the precise identity SAML statement sent to a SaaS application.

---
title: Gain visibility into user actions in Zero Trust Browser Isolation
sessions · Changelog
description: User action logs for Remote Browser Isolation
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-03-user-action-logging/
md: https://developers.cloudflare.com/changelog/2025-03-03-user-action-logging/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Gain visibility into user actions in Zero Trust Browser Isolation sessions
Mar 04, 2025
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
We're excited to announce that new logging capabilities for [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/) through [Logpush](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/) are available in Beta starting today!
With these enhanced logs, administrators can gain visibility into end user behavior in the remote browser and track blocked data extraction attempts, along with the websites that triggered them, in an isolated session.
```json
{
"AccountID": "$ACCOUNT_ID",
"Decision": "block",
"DomainName": "www.example.com",
"Timestamp": "2025-02-27T23:15:06Z",
"Type": "copy",
"UserID": "$USER_ID"
}
```
User Actions available:
* **Copy & Paste**
* **Downloads & Uploads**
* **Printing**
Learn more about how to get started with Logpush in our [documentation](https://developers.cloudflare.com/logs/logpush/).
---
title: WAF Release - 2025-03-03 · Changelog
description: Cloudflare WAF managed rulesets 2025-03-03 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-03-waf-release/
md: https://developers.cloudflare.com/changelog/2025-03-03-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-03-03
Mar 03, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 90356ececae3444b9accb3d393e63099 | 100721 | Ivanti - Remote Code Execution - CVE:CVE-2024-13159, CVE:CVE-2024-13160, CVE:CVE-2024-13161 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 6cf09ce2fa73482abb7f677ecac42ce2 | 100596 | Citrix Content Collaboration ShareFile - Remote Code Execution - CVE:CVE-2023-24489 | N/A | Block | |
---
title: Hyperdrive reduces query latency by up to 90% and now supports IP access
control lists · Changelog
description: Hyperdrive now pools database connections closer to your database
to reduce query latency, and now also provides a documented IP address range
for IP ACLs.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-04-hyperdrive-pooling-near-database-and-ip-range-egress/
md: https://developers.cloudflare.com/changelog/2025-03-04-hyperdrive-pooling-near-database-and-ip-range-egress/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Hyperdrive reduces query latency by up to 90% and now supports IP access control lists
Mar 07, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive now pools database connections in one or more regions close to your database. This means that your uncached queries and new database connections have up to 90% less latency as measured from connection pools.
By improving placement of Hyperdrive database connection pools, Workers' Smart Placement is now more effective when used with Hyperdrive, ensuring that your Worker can be placed as close to your database as possible.
With this update, Hyperdrive also uses [Cloudflare's standard IP address ranges](https://www.cloudflare.com/ips/) to connect to your database. This enables you to configure the firewall policies (IP access control lists) of your database to only allow access from Cloudflare and Hyperdrive.
Refer to [documentation on how Hyperdrive makes connecting to regional databases from Cloudflare Workers fast](https://developers.cloudflare.com/hyperdrive/concepts/how-hyperdrive-works/).
This improvement is enabled on all Hyperdrive configurations.
---
title: Introducing Media Transformations from Cloudflare Stream · Changelog
description: >
Dynamically optimize, clip, and resize video from any origin, no storage
migration needed.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-06-media-transformations/
md: https://developers.cloudflare.com/changelog/2025-03-06-media-transformations/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing Media Transformations from Cloudflare Stream
Mar 06, 2025
[Stream](https://developers.cloudflare.com/stream/)
Today, we are thrilled to announce Media Transformations, a new service that brings the magic of [Image Transformations](https://developers.cloudflare.com/images/transform-images/) to *short-form video files,* wherever they are stored!
For customers with a huge volume of short video — generative AI output, e-commerce product videos, social media clips, or short marketing content — uploading those assets to Stream is not always practical. Sometimes, the greatest friction to getting started was the thought of all that migrating. Customers want a simpler solution that retains their current storage strategy to deliver small, optimized MP4 files. Now you can do that with Media Transformations.
To transform a video or image, [enable transformations](https://developers.cloudflare.com/stream/transform-videos/#getting-started) for your zone, then make a simple request with a specially formatted URL. The result is an MP4 that can be used in an HTML video element without a player library. If your zone already has Image Transformations enabled, then it is ready to optimize videos with Media Transformations, too.
```text
https://example.com/cdn-cgi/media//
```
For example, we have a short video of the mobile in Austin's office. The original is nearly 30 megabytes and wider than necessary for this layout. Consider a simple width adjustment:
```text
https://example.com/cdn-cgi/media/width=640/
https://developers.cloudflare.com/cdn-cgi/media/width=640/https://pub-d9fcbc1abcd244c1821f38b99017347f.r2.dev/aus-mobile.mp4
```
The result is less than 3 megabytes, properly sized, and delivered dynamically so that customers do not have to manage the creation and storage of these transformed assets.
For more information, learn about [Transforming Videos](https://developers.cloudflare.com/stream/transform-videos/).
---
title: One-click Logpush Setup with R2 Object Storage · Changelog
description: Seamlessly configure Logpush to R2 in just one click.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-06-oneclick-logpush/
md: https://developers.cloudflare.com/changelog/2025-03-06-oneclick-logpush/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## One-click Logpush Setup with R2 Object Storage
Mar 06, 2025
[Logs](https://developers.cloudflare.com/logs/)
We’ve streamlined the [Logpush](https://developers.cloudflare.com/logs/logpush/) setup process by integrating R2 bucket creation directly into the Logpush workflow!
Now, you no longer need to navigate multiple pages to manually create an R2 bucket or copy credentials. With this update, you can seamlessly **configure a Logpush job to R2 in just one click**, reducing friction and making setup faster and easier.
This enhancement makes it easier for customers to adopt Logpush and R2.
For more details refer to our [Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/r2/) documentation.
---
title: Set retention polices for your R2 bucket with bucket locks · Changelog
description: Set retention polices for your R2 bucket with bucket locks
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-06-r2-bucket-locks/
md: https://developers.cloudflare.com/changelog/2025-03-06-r2-bucket-locks/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Set retention polices for your R2 bucket with bucket locks
Mar 06, 2025
[R2](https://developers.cloudflare.com/r2/)
You can now use [bucket locks](https://developers.cloudflare.com/r2/buckets/bucket-locks/) to set retention policies on your [R2 buckets](https://developers.cloudflare.com/r2/buckets/) (or specific prefixes within your buckets) for a specified period — or indefinitely. This can help ensure compliance by protecting important data from accidental or malicious deletion.
Locks give you a few ways to ensure your objects are retained (not deleted or overwritten). You can:
* Lock objects for a specific duration, for example 90 days.
* Lock objects until a certain date, for example January 1, 2030.
* Lock objects indefinitely, until the lock is explicitly removed.
Buckets can have up to 1,000 [bucket lock rules](https://developers.cloudflare.com/r2/buckets/). Each rule specifies which objects it covers (via prefix) and how long those objects must remain retained.
Here are a couple of examples showing how you can configure bucket lock rules using [Wrangler](https://developers.cloudflare.com/workers/wrangler/):
#### Ensure all objects in a bucket are retained for at least 180 days
```sh
npx wrangler r2 bucket lock add --name 180-days-all --retention-days 180
```
#### Prevent deletion or overwriting of all logs indefinitely (via prefix)
```sh
npx wrangler r2 bucket lock add --name indefinite-logs --prefix logs/ --retention-indefinite
```
For more information on bucket locks and how to set retention policies for objects in your R2 buckets, refer to our [documentation](https://developers.cloudflare.com/r2/buckets/bucket-locks/).
---
title: Cloudflare One Agent now supports Endpoint Monitoring · Changelog
description: Monitor device health metrics directly from the Cloudflare One agent
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-07-cloudflare-one-device-health-monitoring/
md: https://developers.cloudflare.com/changelog/2025-03-07-cloudflare-one-device-health-monitoring/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare One Agent now supports Endpoint Monitoring
Mar 07, 2025
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into device, network, and application performance across your Cloudflare SASE deployment. The latest release of the Cloudflare One agent (v2025.1.861) now includes device endpoint monitoring capabilities to provide deeper visibility into end-user device performance which can be analyzed directly from the dashboard.
Device health metrics are now automatically collected, allowing administrators to:
* View the last network a user was connected to
* Monitor CPU and RAM utilization on devices
* Identify resource-intensive processes running on endpoints

This feature complements existing DEX features like [synthetic application monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/) and [network path visualization](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/traceroute/), creating a comprehensive troubleshooting workflow that connects application performance with device state.
For more details refer to our [DEX](https://developers.cloudflare.com/cloudflare-one/insights/dex/) documentation.
---
title: Updated leaked credentials database · Changelog
description: New records added to the leaked credentials database.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-07-updated-leaked-credentials-database/
md: https://developers.cloudflare.com/changelog/2025-03-07-updated-leaked-credentials-database/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Updated leaked credentials database
Mar 07, 2025
[WAF](https://developers.cloudflare.com/waf/)
Added new records to the leaked credentials database. The record sources are: Have I Been Pwned (HIBP) database, RockYou 2024 dataset, and another third-party database.
---
title: WAF Release - 2025-03-10 · Changelog
description: Cloudflare WAF managed rulesets 2025-03-10 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-10-waf-release/
md: https://developers.cloudflare.com/changelog/2025-03-10-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-03-10
Mar 10, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | d4f68c1c65c448e58fe4830eb2a51e3d | 100722 | Ivanti - Information Disclosure - CVE:CVE-2025-0282 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | fda130e396224ffc9f0a9e72259073d5 | 100723 | Cisco IOS XE - Information Disclosure - CVE:CVE-2023-20198 | Log | Block | This is a New Detection |
---
title: WAF Release - 2025-03-11 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-03-11 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-11-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-03-11-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-03-11 - Emergency
Mar 11, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 0823d16dd8b94cc6b27a9ab173febb31 | 100731 | Apache Camel - Code Injection - CVE:CVE-2025-27636 | N/A | Block | This is a New Detection |
---
title: Access your Worker's environment variables from process.env · Changelog
description: With Node.js compatibility on, process.env is automatically
populated with environment variables and secrets
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-11-process-env-support/
md: https://developers.cloudflare.com/changelog/2025-03-11-process-env-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Access your Worker's environment variables from process.env
Mar 11, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now access [environment variables](https://developers.cloudflare.com/workers/configuration/environment-variables/) and [secrets](https://developers.cloudflare.com/workers/configuration/secrets/) on [`process.env`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/process/#processenv) when using the [`nodejs_compat` compatibility flag](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#nodejs-compatibility-flag).
```js
const apiClient = ApiClient.new({ apiKey: process.env.API_KEY });
const LOG_LEVEL = process.env.LOG_LEVEL || "info";
```
In Node.js, environment variables are exposed via the global `process.env` object. Some libraries assume that this object will be populated, and many developers may be used to accessing variables in this way.
Previously, the `process.env` object was always empty unless written to in Worker code. This could cause unexpected errors or friction when developing Workers using code previously written for Node.js.
Now, [environment variables](https://developers.cloudflare.com/workers/configuration/environment-variables/), [secrets](https://developers.cloudflare.com/workers/configuration/secrets/), and [version metadata](https://developers.cloudflare.com/workers/runtime-apis/bindings/version-metadata/) can all be accessed on `process.env`.
To opt-in to the new `process.env` behaviour now, add the [`nodejs_compat_populate_process_env`](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#enable-auto-populating-processenv) compatibility flag to your `wrangler.json` configuration:
* wrangler.jsonc
```jsonc
{
// Rest of your configuration
// Add "nodejs_compat_populate_process_env" to your compatibility_flags array
"compatibility_flags": ["nodejs_compat", "nodejs_compat_populate_process_env"],
// Rest of your configuration
```
* wrangler.toml
```toml
compatibility_flags = [ "nodejs_compat", "nodejs_compat_populate_process_env" ]
```
After April 1, 2025, populating `process.env` will become the default behavior when both `nodejs_compat` is enabled and your Worker's `compatibility_date` is after "2025-04-01".
---
title: Threaded replies now possible in Email Workers · Changelog
description: You can now use Email Workers to send multiple replies to the same
email thread.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-12-reply-limits/
md: https://developers.cloudflare.com/changelog/2025-03-12-reply-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Threaded replies now possible in Email Workers
Mar 12, 2025
[Email Routing](https://developers.cloudflare.com/email-routing/)
We’re removing some of the restrictions in Email Routing so that AI Agents and task automation can better handle email workflows, including how Workers can [reply](https://developers.cloudflare.com/email-routing/email-workers/reply-email-workers/) to incoming emails.
It's now possible to keep a threaded email conversation with an [Email Worker](https://developers.cloudflare.com/email-routing/email-workers/) script as long as:
* The incoming email has to have valid [DMARC](https://www.cloudflare.com/learning/dns/dns-records/dns-dmarc-record/).
* The email can only be replied to once in the same `EmailMessage` event.
* The recipient in the reply must match the incoming sender.
* The outgoing sender domain must match the same domain that received the email.
* Every time an email passes through Email Routing or another MTA, an entry is added to the `References` list. We stop accepting replies to emails with more than 100 `References` entries to prevent abuse or accidental loops.
Here's an example of a Worker responding to Emails using a Workers AI model:
```ts
import PostalMime from "postal-mime";
import { createMimeMessage } from "mimetext";
import { EmailMessage } from "cloudflare:email";
export default {
async email(message, env, ctx) {
const email = await PostalMime.parse(message.raw);
const res = await env.AI.run("@cf/meta/llama-2-7b-chat-fp16", {
messages: [
{
role: "user",
content: email.text ?? "",
},
],
});
// message-id is generated by mimetext
const response = createMimeMessage();
response.setHeader("In-Reply-To", message.headers.get("Message-ID")!);
response.setSender("agent@example.com");
response.setRecipient(message.from);
response.setSubject("Llama response");
response.addMessage({
contentType: "text/plain",
data:
res instanceof ReadableStream
? await new Response(res).text()
: res.response!,
});
const replyMessage = new EmailMessage(
"",
message.from,
response.asRaw(),
);
await message.reply(replyMessage);
},
} satisfies ExportedHandler;
```
See [Reply to emails from Workers](https://developers.cloudflare.com/email-routing/email-workers/reply-email-workers/) for more information.
---
title: Cloudflare IP Ranges List · Changelog
description: New Managed IP List, Cloudflare IP Ranges
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-13-new-managed-iplist/
md: https://developers.cloudflare.com/changelog/2025-03-13-new-managed-iplist/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare IP Ranges List
Mar 13, 2025
[Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
Magic Firewall now supports a new managed list of Cloudflare IP ranges. This list is available as an option when creating a Magic Firewall policy based on IP source/destination addresses. When selecting "is in list" or "is not in list", the option "**Cloudflare IP Ranges**" will appear in the dropdown menu.
This list is based on the IPs listed in the Cloudflare [IP ranges](https://www.cloudflare.com/en-gb/ips/). Updates to this managed list are applied automatically.

Note: IP Lists require an advanced Magic Firewall subscription. For more details about Magic Firewall plans, refer to [Plans](https://developers.cloudflare.com/magic-firewall/plans).
---
title: WARP client for macOS (version 2025.2.460.1) · Changelog
description: WARP client for macOS (version 2025.2.460.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-13-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-03-13-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.2.460.1)
Mar 13, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Fixed issue with device revocation and re-registration when switching configurations.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
---
title: WARP client for Windows (version 2025.2.460.1) · Changelog
description: WARP client for Windows (version 2025.2.460.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-13-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-03-13-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.2.460.1)
Mar 13, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* Added the ability to control if the WARP interface IPs are [registered with DNS servers](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#warp-interface-ip-dns-registration) or not.
* Removed DNS logs view from the Windows client GUI. DNS logs can be viewed as part of `warp-diag` or by viewing the log file on the user's local directory.
* Fixed issue that would result in a user receiving multiple re-authentication requests when waking their device from sleep.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Improvements to [Windows multi-user](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/) including support for fast user switching. If you are interested in testing this feature, reach out to your Cloudflare account team.
* Fixed issue with device revocation and re-registration when switching configurations.
* Fixed issue where DEX tests would run during certain sleep states where the networking stack was not fully up. This would result in failures that would be ignored.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Use the latest JavaScript features with Wrangler CLI v4 · Changelog
description: Wrangler v4 is available!
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-13-wrangler-v4/
md: https://developers.cloudflare.com/changelog/2025-03-13-wrangler-v4/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Use the latest JavaScript features with Wrangler CLI v4
Mar 13, 2025
[Workers](https://developers.cloudflare.com/workers/)
We've released the next major version of [Wrangler](https://developers.cloudflare.com/workers/wrangler/), the CLI for Cloudflare Workers — `wrangler@4.0.0`. Wrangler v4 is a major release focused on updates to underlying systems and dependencies, along with improvements to keep Wrangler commands consistent and clear.
You can run the following command to install it in your projects:
* npm
```sh
npm i wrangler@latest
```
* yarn
```sh
yarn add wrangler@latest
```
* pnpm
```sh
pnpm add wrangler@latest
```
Unlike previous major versions of Wrangler, which were [foundational rewrites](https://blog.cloudflare.com/wrangler-v2-beta/) and [rearchitectures](https://blog.cloudflare.com/wrangler3/) — Version 4 of Wrangler includes a much smaller set of changes. If you use Wrangler today, your workflow is very unlikely to change.
A [detailed migration guide](https://developers.cloudflare.com/workers/wrangler/migration/update-v3-to-v4) is available and if you find a bug or hit a roadblock when upgrading to Wrangler v4, [open an issue on the `cloudflare/workers-sdk` repository on GitHub](https://github.com/cloudflare/workers-sdk/issues/new?template=bug-template.yaml).
Going forward, we'll continue supporting Wrangler v3 with bug fixes and security updates until Q1 2026, and with critical security updates until Q1 2027, at which point it will be out of support.
---
title: Set breakpoints and debug your Workers tests with
@cloudflare/vitest-pool-workers · Changelog
description: You can now debug your workers tests with the Workers <> Vitest integration
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-14-breakpoint-debugging-with-vitest/
md: https://developers.cloudflare.com/changelog/2025-03-14-breakpoint-debugging-with-vitest/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Set breakpoints and debug your Workers tests with @cloudflare/vitest-pool-workers
Mar 13, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now debug your Workers tests with our [Vitest integration](https://developers.cloudflare.com/workers/testing/vitest-integration/) by running the following command:
```sh
vitest --inspect --no-file-parallelism
```
Attach a debugger to the port 9229 and you can start stepping through your Workers tests. This is available with `@cloudflare/vitest-pool-workers` v0.7.5 or later.
Learn more in our [documentation](https://developers.cloudflare.com/workers/testing/vitest-integration/debugging/).
---
title: Import `env` to access bindings in your Worker's global scope · Changelog
description: More easily configure your Worker and call bindings from anywhere
with an importable `env`
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-17-importable-env/
md: https://developers.cloudflare.com/changelog/2025-03-17-importable-env/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Import \`env\` to access bindings in your Worker's global scope
Mar 17, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now access [bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) from anywhere in your Worker by importing the `env` object from `cloudflare:workers`.
Previously, `env` could only be accessed during a request. This meant that bindings could not be used in the top-level context of a Worker.
Now, you can import `env` and access bindings such as [secrets](https://developers.cloudflare.com/workers/configuration/secrets/) or [environment variables](https://developers.cloudflare.com/workers/configuration/environment-variables/) in the initial setup for your Worker:
```js
import { env } from "cloudflare:workers";
import ApiClient from "example-api-client";
// API_KEY and LOG_LEVEL now usable in top-level scope
const apiClient = ApiClient.new({ apiKey: env.API_KEY });
const LOG_LEVEL = env.LOG_LEVEL || "info";
export default {
fetch(req) {
// you can use apiClient or LOG_LEVEL, configured before any request is handled
},
};
```
Note
Workers do not allow I/O from outside a request context. This means that even though `env` is accessible from the top-level scope, you will not be able to access every binding's methods.
For instance, environment variables and secrets are accessible, and you are able to call `env.NAMESPACE.get` to get a [Durable Object stub](https://developers.cloudflare.com/durable-objects/api/stub/) in the top-level context. However, calling methods on the Durable Object stub, making [calls to a KV store](https://developers.cloudflare.com/kv/api/), and [calling to other Workers](https://developers.cloudflare.com/workers/runtime-apis/bindings/service-bindings) will not work.
Additionally, `env` was normally accessed as a argument to a Worker's entrypoint handler, such as [`fetch`](https://developers.cloudflare.com/workers/runtime-apis/fetch/). This meant that if you needed to access a binding from a deeply nested function, you had to pass `env` as an argument through many functions to get it to the right spot. This could be cumbersome in complex codebases.
Now, you can access the bindings from anywhere in your codebase without passing `env` as an argument:
```js
// helpers.js
import { env } from "cloudflare:workers";
// env is *not* an argument to this function
export async function getValue(key) {
let prefix = env.KV_PREFIX;
return await env.KV.get(`${prefix}-${key}`);
}
```
For more information, see [documentation on accessing `env`](https://developers.cloudflare.com/workers/runtime-apis/bindings#how-to-access-env).
---
title: New models in Workers AI · Changelog
description: New text-to-speech, reranker, whisper, embeddings models now available!
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-17-new-workers-ai-models/
md: https://developers.cloudflare.com/changelog/2025-03-17-new-workers-ai-models/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New models in Workers AI
Mar 17, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Workers AI is excited to add 4 new models to the catalog, including 2 brand new classes of models with a text-to-speech and reranker model. Introducing:
* [@cf/baai/bge-m3](https://developers.cloudflare.com/workers-ai/models/bge-m3/) - a multi-lingual embeddings model that supports over 100 languages. It can also simultaneously perform dense retrieval, multi-vector retrieval, and sparse retrieval, with the ability to process inputs of different granularities.
* [@cf/baai/bge-reranker-base](https://developers.cloudflare.com/workers-ai/models/bge-reranker-base/) - our first reranker model! Rerankers are a type of text classification model that takes a query and context, and outputs a similarity score between the two. When used in RAG systems, you can use a reranker after the initial vector search to find the most relevant documents to return to a user by reranking the outputs.
* [@cf/openai/whisper-large-v3-turbo](https://developers.cloudflare.com/workers-ai/models/whisper-large-v3-turbo/) - a faster, more accurate speech-to-text model. This model was added earlier but is graduating out of beta with pricing included today.
* [@cf/myshell-ai/melotts](https://developers.cloudflare.com/workers-ai/models/melotts/) - our first text-to-speech model that allows users to generate an MP3 with voice audio from inputted text.
Pricing is available for each of these models on the [Workers AI pricing page](https://developers.cloudflare.com/workers-ai/platform/pricing/).
This docs update includes a few minor bug fixes to the model schema for llama-guard, llama-3.2-1b, which you can review on the [product changelog](https://developers.cloudflare.com/workers-ai/changelog/).
Try it out and let us know what you think! Stay tuned for more models in the coming days.
---
title: Retry Pages & Workers Builds Directly from GitHub · Changelog
description: Rerun builds for your Workers and Pages projects directly inside of GitHub.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-17-rerun-build/
md: https://developers.cloudflare.com/changelog/2025-03-17-rerun-build/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Retry Pages & Workers Builds Directly from GitHub
Mar 17, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Pages](https://developers.cloudflare.com/pages/)
You can now retry your Cloudflare Pages and Workers builds directly from GitHub. No need to switch to the Cloudflare Dashboard for a simple retry!

Let’s say you push a commit, but your build fails due to a spurious error like a network timeout. Instead of going to the Cloudflare Dashboard to manually retry, you can now rerun the build with just a few clicks inside GitHub, keeping you inside your workflow.
For Pages and Workers projects connected to a GitHub repository:
1. When a build fails, go to your GitHub repository or pull request
2. Select the failed Check Run for the build
3. Select "Details" on the Check Run
4. Select "Rerun" to trigger a retry build for that commit
Learn more about [Pages Builds](https://developers.cloudflare.com/pages/configuration/git-integration/github-integration/) and [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/git-integration/github-integration/).
---
title: WAF Release - 2025-03-17 · Changelog
description: Cloudflare WAF managed rulesets 2025-03-17 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-17-waf-release/
md: https://developers.cloudflare.com/changelog/2025-03-17-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-03-17
Mar 17, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 28b2a12993a04e62a98abcd9e59ec18a | 100725 | Fortinet FortiManager - Remote Code Execution - CVE:CVE-2023-42791, CVE:CVE-2024-23666 | Log | Block | |
| Cloudflare Managed Ruleset | f253d755910e4998bd90365d1dbf58df | 100726 | Ivanti - Remote Code Execution - CVE:CVE-2024-8190 | Log | Block | |
| Cloudflare Managed Ruleset | 19ae0094a8d845a1bb1997af0ad61fa7 | 100727 | Cisco IOS XE - Remote Code Execution - CVE:CVE-2023-20198 | Log | Block | |
| Cloudflare Managed Ruleset | 83a677f082264693ad64a2827ee56b66 | 100728 | Sitecore - Remote Code Execution - CVE:CVE-2024-46938 | Log | Block | |
| Cloudflare Managed Ruleset | 166b7ce85ce443538f021228a6752a38 | 100729 | Microsoft SharePoint - Remote Code Execution - CVE:CVE-2023-33160 | Log | Block | |
| Cloudflare Managed Ruleset | 35fe23e7bd324d00816c82d098d47b69 | 100730 | Pentaho - Template Injection - CVE:CVE-2022-43769, CVE:CVE-2022-43939 | Log | Block | |
| Cloudflare Managed Ruleset | 2ce80fe815254f25b3c8f47569fe1e0d | 100700 | Apache SSRF vulnerability CVE-2021-40438 | N/A | Block | |
---
title: Cloudflare One Agent for Android (version 2.4) · Changelog
description: Cloudflare One Agent for Android (version 2.4)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-17-warp-ga-android/
md: https://developers.cloudflare.com/changelog/2025-03-17-warp-ga-android/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare One Agent for Android (version 2.4)
Mar 17, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Android Cloudflare One Agent is now available in the [Google Play Store](https://play.google.com/store/apps/details?id=com.cloudflare.cloudflareoneagent). This release includes a new feature allowing [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url) during enrollment, as well as fixes and minor improvements.
**Changes and improvements**
* Improved in-app error messages.
* Improved mobile client login with support for [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url).
* Fixed an issue preventing admin split tunnel settings taking priority for traffic from certain applications.
---
title: Cloudflare One Agent for iOS (version 1.10) · Changelog
description: Cloudflare One Agent for iOS (version 1.10)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-17-warp-ga-ios/
md: https://developers.cloudflare.com/changelog/2025-03-17-warp-ga-ios/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare One Agent for iOS (version 1.10)
Mar 17, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the iOS Cloudflare One Agent is now available in the [iOS App Store](https://apps.apple.com/us/app/cloudflare-one-agent/id6443476492). This release includes a new feature allowing [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url) during enrollment, as well as fixes and minor improvements.
**Changes and improvements**
* Improved in-app error messages.
* Improved mobile client login with support for [team name insertion by URL](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/manual-deployment/#enroll-using-a-url).
* Bug fixes and performance improvements.
---
title: New API Posture Management for API Shield · Changelog
description: Monitor for API-specific threats and risks with Posture Management
for API Shield
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-18-api-posture-management/
md: https://developers.cloudflare.com/changelog/2025-03-18-api-posture-management/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New API Posture Management for API Shield
Mar 18, 2025
[API Shield](https://developers.cloudflare.com/api-shield/)
Now, API Shield **automatically** labels your API inventory with API-specific risks so that you can track and manage risks to your APIs.
View these risks in [Endpoint Management](https://developers.cloudflare.com/api-shield/management-and-monitoring/) by label:

...or in [Security Center Insights](https://developers.cloudflare.com/security-center/security-insights/):

API Shield will scan for risks on your API inventory daily. Here are the new risks we're scanning for and automatically labelling:
* **cf-risk-sensitive**: applied if the customer is subscribed to the [sensitive data detection ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/sensitive-data-detection/) and the WAF detects sensitive data returned on an endpoint in the last seven days.
* **cf-risk-missing-auth**: applied if the customer has configured a session ID and no successful requests to the endpoint contain the session ID.
* **cf-risk-mixed-auth**: applied if the customer has configured a session ID and some successful requests to the endpoint contain the session ID while some lack the session ID.
* **cf-risk-missing-schema**: added when a learned schema is available for an endpoint that has no active schema.
* **cf-risk-error-anomaly**: added when an endpoint experiences a recent increase in response errors over the last 24 hours.
* **cf-risk-latency-anomaly**: added when an endpoint experiences a recent increase in response latency over the last 24 hours.
* **cf-risk-size-anomaly**: added when an endpoint experiences a spike in response body size over the last 24 hours.
In addition, API Shield has two new 'beta' scans for **Broken Object Level Authorization (BOLA) attacks**. If you're in the beta, you will see the following two labels when API Shield suspects an endpoint is suffering from a BOLA vulnerability:
* **cf-risk-bola-enumeration**: added when an endpoint experiences successful responses with drastic differences in the number of unique elements requested by different user sessions.
* **cf-risk-bola-pollution**: added when an endpoint experiences successful responses where parameters are found in multiple places in the request.
We are currently accepting more customers into our beta. Contact your account team if you are interested in BOLA attack detection for your API.
Refer to the [blog post](https://blog.cloudflare.com/cloudflare-security-posture-management/) for more information about Cloudflare's expanded posture management capabilities.
---
title: npm i agents · Changelog
description: Install the latest version of the `agents` SDK to build multi-agent
applications, use the new RPC API, and visit the latest documentation updates.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-18-npm-i-agents/
md: https://developers.cloudflare.com/changelog/2025-03-18-npm-i-agents/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## npm i agents
Mar 18, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)

#### `agents-sdk` -> `agents` Updated
📝 **We've renamed the Agents package to `agents`**!
If you've already been building with the Agents SDK, you can update your dependencies to use the new package name, and replace references to `agents-sdk` with `agents`:
```sh
# Install the new package
npm i agents
```
```sh
# Remove the old (deprecated) package
npm uninstall agents-sdk
# Find instances of the old package name in your codebase
grep -r 'agents-sdk' .
# Replace instances of the old package name with the new one
# (or use find-replace in your editor)
sed -i 's/agents-sdk/agents/g' $(grep -rl 'agents-sdk' .)
```
All future updates will be pushed to the new `agents` package, and the older package has been marked as deprecated.
#### Agents SDK updates New
We've added a number of big new features to the Agents SDK over the past few weeks, including:
* You can now set `cors: true` when using `routeAgentRequest` to return permissive default CORS headers to Agent responses.
* The regular client now syncs state on the agent (just like the React version).
* `useAgentChat` bug fixes for passing headers/credentials, including properly clearing cache on unmount.
* Experimental `/schedule` module with a prompt/schema for adding scheduling to your app (with evals!).
* Changed the internal `zod` schema to be compatible with the limitations of Google's Gemini models by removing the discriminated union, allowing you to use Gemini models with the scheduling API.
We've also fixed a number of bugs with state synchronization and the React hooks.
* JavaScript
```js
// via https://github.com/cloudflare/agents/tree/main/examples/cross-domain
export default {
async fetch(request, env) {
return (
// Set { cors: true } to enable CORS headers.
(await routeAgentRequest(request, env, { cors: true })) ||
new Response("Not found", { status: 404 })
);
},
};
```
* TypeScript
```ts
// via https://github.com/cloudflare/agents/tree/main/examples/cross-domain
export default {
async fetch(request: Request, env: Env) {
return (
// Set { cors: true } to enable CORS headers.
(await routeAgentRequest(request, env, { cors: true })) ||
new Response("Not found", { status: 404 })
);
},
} satisfies ExportedHandler;
```
#### Call Agent methods from your client code New
We've added a new [`@unstable_callable()`](https://developers.cloudflare.com/agents/api-reference/agents-api/) decorator for defining methods that can be called directly from clients. This allows you call methods from within your client code: you can call methods (with arguments) and get native JavaScript objects back.
* JavaScript
```js
// server.ts
import { unstable_callable, Agent } from "agents";
export class Rpc extends Agent {
// Use the decorator to define a callable method
@unstable_callable({
description: "rpc test",
})
async getHistory() {
return this.sql`SELECT * FROM history ORDER BY created_at DESC LIMIT 10`;
}
}
```
* TypeScript
```ts
// server.ts
import { unstable_callable, Agent, type StreamingResponse } from "agents";
import type { Env } from "../server";
export class Rpc extends Agent {
// Use the decorator to define a callable method
@unstable_callable({
description: "rpc test",
})
async getHistory() {
return this.sql`SELECT * FROM history ORDER BY created_at DESC LIMIT 10`;
}
}
```
#### agents-starter Updated
We've fixed a number of small bugs in the [`agents-starter`](https://github.com/cloudflare/agents-starter) project — a real-time, chat-based example application with tool-calling & human-in-the-loop built using the Agents SDK. The starter has also been upgraded to use the latest [wrangler v4](https://developers.cloudflare.com/changelog/2025-03-13-wrangler-v4/) release.
If you're new to Agents, you can install and run the `agents-starter` project in two commands:
```sh
# Install it
$ npm create cloudflare@latest agents-starter -- --template="cloudflare/agents-starter"
# Run it
$ npm run start
```
You can use the starter as a template for your own Agents projects: open up `src/server.ts` and `src/client.tsx` to see how the Agents SDK is used.
#### More documentation Updated
We've heard your feedback on the Agents SDK documentation, and we're shipping more API reference material and usage examples, including:
* Expanded [API reference documentation](https://developers.cloudflare.com/agents/api-reference/), covering the methods and properties exposed by the Agents SDK, as well as more usage examples.
* More [Client API](https://developers.cloudflare.com/agents/api-reference/agents-api/#client-api) documentation that documents `useAgent`, `useAgentChat` and the new `@unstable_callable` RPC decorator exposed by the SDK.
* New documentation on how to [route requests to agents](https://developers.cloudflare.com/agents/api-reference/routing/) and (optionally) authenticate clients before they connect to your Agents.
Note that the Agents SDK is continually growing: the type definitions included in the SDK will always include the latest APIs exposed by the `agents` package.
If you're still wondering what Agents are, [read our blog on building AI Agents on Cloudflare](https://blog.cloudflare.com/build-ai-agents-on-cloudflare/) and/or visit the [Agents documentation](https://developers.cloudflare.com/agents/) to learn more.
---
title: Leaked Credentials Insights in Cloudflare Radar · Changelog
description: Expanded security insights with new API endpoints for aggregated
authentication request data
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-18-radar-leaked-credentials-insights/
md: https://developers.cloudflare.com/changelog/2025-03-18-radar-leaked-credentials-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Leaked Credentials Insights in Cloudflare Radar
Mar 18, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) has expanded its security insights, providing visibility into aggregate trends in authentication requests, including the detection of leaked credentials through [leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/) scans.
We have now introduced the following endpoints:
* [`/leaked_credential_checks/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/leaked_credentials/subresources/summary/): Retrieves summaries of HTTP authentication requests distribution across two different dimensions.
* [`/leaked_credential_checks/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/leaked_credentials/subresources/timeseries_groups/): Retrieves timeseries data for HTTP authentication requests distribution across two different dimensions.
The following dimensions are available, displaying the distribution of HTTP authentication requests based on:
* `compromised`: Credential status (clean vs. compromised).
* `bot_class`: [Bot class](https://developers.cloudflare.com/radar/concepts/bot-classes) (human vs. bot).
Dive deeper into leaked credential detection in this [blog post](https://blog.cloudflare.com/password-reuse-rampant-half-user-logins-compromised/) and learn more about the expanded Radar security insights in our [blog post](https://blog.cloudflare.com/cloudflare-radar-ddos-leaked-credentials-bots).
---
title: WAF Release - 2025-03-19 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-03-19 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-19-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-03-19-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-03-19 - Emergency
Mar 19, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 470b477e27244fddb479c4c7a2cafae7 | 100736 | Generic HTTP Request Smuggling | N/A | Disabled | This is a New Detection |
---
title: Markdown conversion in Workers AI · Changelog
description: You can now convert documents in multiple formats to Markdown using
the toMarkdown utility method in Workers AI.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-20-markdown-conversion/
md: https://developers.cloudflare.com/changelog/2025-03-20-markdown-conversion/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Markdown conversion in Workers AI
Mar 20, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Document conversion plays an important role when designing and developing AI applications and agents. Workers AI now provides the `toMarkdown` utility method that developers can use to for quick, easy, and convenient conversion and summary of documents in multiple formats to Markdown language.
You can call this new tool using a binding by calling `env.AI.toMarkdown()` or the using the [REST API](https://developers.cloudflare.com/api/resources/ai/) endpoint.
In this example, we fetch a PDF document and an image from R2 and feed them both to `env.AI.toMarkdown()`. The result is a list of converted documents. Workers AI models are used automatically to detect and summarize the image.
```typescript
import { Env } from "./env";
export default {
async fetch(request: Request, env: Env, ctx: ExecutionContext) {
// https://pub-979cb28270cc461d94bc8a169d8f389d.r2.dev/somatosensory.pdf
const pdf = await env.R2.get("somatosensory.pdf");
// https://pub-979cb28270cc461d94bc8a169d8f389d.r2.dev/cat.jpeg
const cat = await env.R2.get("cat.jpeg");
return Response.json(
await env.AI.toMarkdown([
{
name: "somatosensory.pdf",
blob: new Blob([await pdf.arrayBuffer()], {
type: "application/octet-stream",
}),
},
{
name: "cat.jpeg",
blob: new Blob([await cat.arrayBuffer()], {
type: "application/octet-stream",
}),
},
]),
);
},
};
```
This is the result:
```json
[
{
"name": "somatosensory.pdf",
"mimeType": "application/pdf",
"format": "markdown",
"tokens": 0,
"data": "# somatosensory.pdf\n## Metadata\n- PDFFormatVersion=1.4\n- IsLinearized=false\n- IsAcroFormPresent=false\n- IsXFAPresent=false\n- IsCollectionPresent=false\n- IsSignaturesPresent=false\n- Producer=Prince 20150210 (www.princexml.com)\n- Title=Anatomy of the Somatosensory System\n\n## Contents\n### Page 1\nThis is a sample document to showcase..."
},
{
"name": "cat.jpeg",
"mimeType": "image/jpeg",
"format": "markdown",
"tokens": 0,
"data": "The image is a close-up photograph of Grumpy Cat, a cat with a distinctive grumpy expression and piercing blue eyes. The cat has a brown face with a white stripe down its nose, and its ears are pointed upright. Its fur is light brown and darker around the face, with a pink nose and mouth. The cat's eyes are blue and slanted downward, giving it a perpetually grumpy appearance. The background is blurred, but it appears to be a dark brown color. Overall, the image is a humorous and iconic representation of the popular internet meme character, Grumpy Cat. The cat's facial expression and posture convey a sense of displeasure or annoyance, making it a relatable and entertaining image for many people."
}
]
```
See [Markdown Conversion](https://developers.cloudflare.com/workers-ai/features/markdown-conversion/) for more information on supported formats, REST API and pricing.
---
title: AI Gateway launches Realtime WebSockets API · Changelog
description: AI Gateway now supports end-to-end, client-to-provider WebSockets
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-20-websockets/
md: https://developers.cloudflare.com/changelog/2025-03-20-websockets/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Gateway launches Realtime WebSockets API
Mar 21, 2025
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
We are excited to announce that [AI Gateway](https://developers.cloudflare.com/ai-gateway/) now supports real-time AI interactions with the new [Realtime WebSockets API](https://developers.cloudflare.com/ai-gateway/usage/websockets-api/realtime-api/).
This new capability allows developers to establish persistent, low-latency connections between their applications and AI models, enabling natural, real-time conversational AI experiences, including speech-to-speech interactions.
The Realtime WebSockets API works with the [OpenAI Realtime API](https://platform.openai.com/docs/guides/realtime#connect-with-websockets), [Google Gemini Live API](https://ai.google.dev/gemini-api/docs/multimodal-live), and supports real-time text and speech interactions with models from [Cartesia](https://docs.cartesia.ai/api-reference/tts/tts), and [ElevenLabs](https://elevenlabs.io/docs/conversational-ai/api-reference/conversational-ai/websocket).
Here's how you can connect AI Gateway to [OpenAI's Realtime API](https://platform.openai.com/docs/guides/realtime#connect-with-websockets) using WebSockets:
```javascript
import WebSocket from "ws";
const url =
"wss://gateway.ai.cloudflare.com/v1///openai?model=gpt-4o-realtime-preview-2024-12-17";
const ws = new WebSocket(url, {
headers: {
"cf-aig-authorization": process.env.CLOUDFLARE_API_KEY,
Authorization: "Bearer " + process.env.OPENAI_API_KEY,
"OpenAI-Beta": "realtime=v1",
},
});
ws.on("open", () => console.log("Connected to server."));
ws.on("message", (message) => console.log(JSON.parse(message.toString())));
ws.send(
JSON.stringify({
type: "response.create",
response: { modalities: ["text"], instructions: "Tell me a joke" },
}),
);
```
Get started by checking out the [Realtime WebSockets API](https://developers.cloudflare.com/ai-gateway/usage/websockets-api/realtime-api/) documentation.
---
title: Secure DNS Locations Management User Role · Changelog
description: Create secure DNS locations using the new Cloudflare Zero Trust
Locations Write role.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-21-pdns-user-locations-role/
md: https://developers.cloudflare.com/changelog/2025-03-21-pdns-user-locations-role/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Secure DNS Locations Management User Role
Mar 21, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
We're excited to introduce the [**Cloudflare Zero Trust Secure DNS Locations Write role**](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/#secure-dns-locations), designed to provide DNS filtering customers with granular control over third-party access when configuring their Protective DNS (PDNS) solutions.
Many DNS filtering customers rely on external service partners to manage their DNS location endpoints. This role allows you to grant access to external parties to administer DNS locations without overprovisioning their permissions.
**Secure DNS Location Requirements:**
* Mandate usage of [Bring your own DNS resolver IP addresses](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/dns-resolver-ips/#bring-your-own-dns-resolver-ip) if available on the account.
* Require source network filtering for IPv4/IPv6/DoT endpoints; token authentication or source network filtering for the DoH endpoint.
You can assign the new role via Cloudflare Dashboard (`Manage Accounts > Members`) or via API. For more information, refer to the [Secure DNS Locations documentation](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/locations/#secure-dns-locations).
---
title: Dozens of Cloudflare Terraform Provider resources now have proper drift
detection · Changelog
description: Improper drift detection in the Cloudflare Terraform Provider
resulted in dozens of resources always indicating they needed to be updated or
replaced.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-21-resource-force-replacement-bug/
md: https://developers.cloudflare.com/changelog/2025-03-21-resource-force-replacement-bug/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Dozens of Cloudflare Terraform Provider resources now have proper drift detection
Mar 21, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
In [Cloudflare Terraform Provider](https://github.com/cloudflare/terraform-provider-cloudflare) versions 5.2.0 and above, dozens of resources now have proper drift detection. Before this fix, these resources would indicate they needed to be updated or replaced — even if there was no real change. Now, you can rely on your `terraform plan` to only show what resources are expected to change.
This issue affected [resources](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs) related to these products and features:
* API Shield
* Argo Smart Routing
* Argo Tiered Caching
* Bot Management
* BYOIP
* D1
* DNS
* Email Routing
* Hyperdrive
* Observatory
* Pages
* R2
* Rules
* SSL/TLS
* Waiting Room
* Workers
* Zero Trust
---
title: Cloudflare Terraform Provider now properly redacts sensitive values · Changelog
description: Resources in the Cloudflare Terraform Provider that have sensitive
properties will not show those values in logs.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-21-sensitive-values-redacted/
md: https://developers.cloudflare.com/changelog/2025-03-21-sensitive-values-redacted/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Terraform Provider now properly redacts sensitive values
Mar 21, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
In the [Cloudflare Terraform Provider](https://github.com/cloudflare/terraform-provider-cloudflare) versions 5.2.0 and above, sensitive properties of resources are redacted in logs. Sensitive properties in [Cloudflare's OpenAPI Schema](https://raw.githubusercontent.com/cloudflare/api-schemas/refs/heads/main/openapi.yaml) are now annotated with `x-sensitive: true`. This results in proper auto-generation of the corresponding Terraform resources, and prevents sensitive values from being shown when you run Terraform commands.
This issue affected [resources](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs) related to these products and features:
* Alerts and Audit Logs
* Device API
* DLP
* DNS
* Magic Visibility
* Magic WAN
* TLS Certs and Hostnames
* Tunnels
* Turnstile
* Workers
* Zaraz
---
title: WAF Release - 2025-03-22 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-03-22 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-22-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-03-22-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-03-22 - Emergency
Mar 22, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 34583778093748cc83ff7b38f472013e | 100739 | Next.js - Auth Bypass - CVE:CVE-2025-29927 | N/A | Disabled | This is a New Detection |
---
title: New Managed WAF rule for Next.js CVE-2025-29927. · Changelog
description: Automatic deployment of a Web Application Firewall rule to block
requests that attempt to bypass authentication in Next.js applications as part
of CVE-2025-29927.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-22-next-js-vulnerability-waf/
md: https://developers.cloudflare.com/changelog/2025-03-22-next-js-vulnerability-waf/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Managed WAF rule for Next.js CVE-2025-29927.
Mar 22, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Pages ](https://developers.cloudflare.com/pages/)[WAF](https://developers.cloudflare.com/waf/)
**Update: Mon Mar 24th, 11PM UTC**: Next.js has made further changes to address a smaller vulnerability introduced in the patches made to its middleware handling. Users should upgrade to Next.js versions `15.2.4`, `14.2.26`, `13.5.10` or `12.3.6`. **If you are unable to immediately upgrade or are running an older version of Next.js, you can enable the WAF rule described in this changelog as a mitigation**.
**Update: Mon Mar 24th, 8PM UTC**: Next.js has now [backported the patch for this vulnerability](https://github.com/advisories/GHSA-f82v-jwr5-mffw) to cover Next.js v12 and v13. Users on those versions will need to patch to `13.5.9` and `12.3.5` (respectively) to mitigate the vulnerability.
**Update: Sat Mar 22nd, 4PM UTC**: We have changed this WAF rule to opt-in only, as sites that use auth middleware with third-party auth vendors were observing failing requests.
**We strongly recommend updating your version of Next.js (if eligible)** to the patched versions, as your app will otherwise be vulnerable to an authentication bypass attack regardless of auth provider.
#### Enable the Managed Rule (strongly recommended)
This rule is opt-in only for sites on the Pro plan or above in the [WAF managed ruleset](https://developers.cloudflare.com/waf/managed-rules/).
To enable the rule:
1. Head to Security > WAF > Managed rules in the Cloudflare dashboard for the zone (website) you want to protect.
2. Click the three dots next to **Cloudflare Managed Ruleset** and choose **Edit**
3. Scroll down and choose **Browse Rules**
4. Search for **CVE-2025-29927** (ruleId: `34583778093748cc83ff7b38f472013e`)
5. Change the **Status** to **Enabled** and the **Action** to **Block**. You can optionally set the rule to Log, to validate potential impact before enabling it. Log will not block requests.
6. Click **Next**
7. Scroll down and choose **Save**

This will enable the WAF rule and block requests with the `x-middleware-subrequest` header regardless of Next.js version.
#### Create a WAF rule (manual)
For users on the Free plan, or who want to define a more specific rule, you can create a [Custom WAF rule](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/) to block requests with the `x-middleware-subrequest` header regardless of Next.js version.
To create a custom rule:
1. Head to Security > WAF > Custom rules in the Cloudflare dashboard for the zone (website) you want to protect.
2. Give the rule a name - e.g. `next-js-CVE-2025-29927`
3. Set the matching parameters for the rule match any request where the `x-middleware-subrequest` header `exists` per the rule expression below.
```sh
(len(http.request.headers["x-middleware-subrequest"]) > 0)
```
1. Set the action to 'block'. If you want to observe the impact before blocking requests, set the action to 'log' (and edit the rule later).
2. **Deploy** the rule.

#### Next.js CVE-2025-29927
We've made a WAF (Web Application Firewall) rule available to all sites on Cloudflare to protect against the [Next.js authentication bypass vulnerability](https://github.com/advisories/GHSA-f82v-jwr5-mffw) (`CVE-2025-29927`) published on March 21st, 2025.
**Note**: This rule is not enabled by default as it blocked requests across sites for specific authentication middleware.
* This managed rule protects sites using Next.js on Workers and Pages, as well as sites using Cloudflare to protect Next.js applications hosted elsewhere.
* This rule has been made available (but not enabled by default) to all sites as part of our [WAF Managed Ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/) and blocks requests that attempt to bypass authentication in Next.js applications.
* The vulnerability affects almost all Next.js versions, and has been fully patched in Next.js `14.2.26` and `15.2.4`. Earlier, interim releases did not fully patch this vulnerability.
* **Users on older versions of Next.js (`11.1.4` to `13.5.6`) did not originally have a patch available**, but this the patch for this vulnerability and a subsequent additional patch have been backported to Next.js versions `12.3.6` and `13.5.10` as of Monday, March 24th. Users on Next.js v11 will need to deploy the stated workaround or enable the WAF rule.
The managed WAF rule mitigates this by blocking *external* user requests with the `x-middleware-subrequest` header regardless of Next.js version, but we recommend users using Next.js 14 and 15 upgrade to the patched versions of Next.js as an additional mitigation.
---
title: Smart Placement is smarter about running Workers and Pages Functions in
the best locations · Changelog
description: Workers and Pages Functions with Smart Placement enabled will not
unexpectedly return to default locations if request traffic dips.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-22-smart-placement-stablization/
md: https://developers.cloudflare.com/changelog/2025-03-22-smart-placement-stablization/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Smart Placement is smarter about running Workers and Pages Functions in the best locations
Mar 22, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Pages](https://developers.cloudflare.com/pages/)
[Smart Placement](https://developers.cloudflare.com/workers/configuration/placement/) is a unique Cloudflare feature that can make decisions to move your Worker to run in a more optimal location (such as closer to a database). Instead of always running in the default location (the one closest to where the request is received), Smart Placement uses certain “heuristics” (rules and thresholds) to decide if a different location might be faster or more efficient.
Previously, if these heuristics weren't consistently met, your Worker would revert to running in the default location—even after it had been optimally placed. This meant that if your Worker received minimal traffic for a period of time, the system would reset to the default location, rather than remaining in the optimal one.
Now, once Smart Placement has identified and assigned an optimal location, temporarily dropping below the heuristic thresholds will not force a return to default locations. For example in the previous algorithm, a drop in requests for a few days might return to default locations and heuristics would have to be met again. This was problematic for workloads that made requests to a geographically located resource every few days or longer. In this scenario, your Worker would never get placed optimally. This is no longer the case.
---
title: Source Maps are Generally Available · Changelog
description: Source maps are now Generally Available with a larger maximum size limit
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-25-gzip-source-maps/
md: https://developers.cloudflare.com/changelog/2025-03-25-gzip-source-maps/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Source Maps are Generally Available
Mar 25, 2025
[Workers](https://developers.cloudflare.com/workers/)
Source maps are now Generally Available (GA). You can now be uploaded with a maximum gzipped size of 15 MB. Previously, the maximum size limit was 15 MB uncompressed.
Source maps help map between the original source code and the transformed/minified code that gets deployed to production. By uploading your source map, you allow Cloudflare to map the stack trace from exceptions onto the original source code making it easier to debug.

With **no source maps uploaded**: notice how all the Javascript has been minified to one file, so the stack trace is missing information on file name, shows incorrect line numbers, and incorrectly references `js` instead of `ts`.

With **source maps uploaded**: all methods reference the correct files and line numbers.
Uploading source maps and stack trace remapping happens out of band from the Worker execution, so source maps do not affect upload speed, bundle size, or cold starts. The remapped stack traces are accessible through Tail Workers, Workers Logs, and Workers Logpush.
To enable source maps, add the following to your [Pages Function's](https://developers.cloudflare.com/pages/functions/source-maps/) or [Worker's](https://developers.cloudflare.com/workers/observability/source-maps/) wrangler configuration:
* wrangler.jsonc
```jsonc
{
"upload_source_maps": true
}
```
* wrangler.toml
```toml
upload_source_maps = true
```
---
title: Run Workers for up to 5 minutes of CPU-time · Changelog
description: Workers now support up to 5 minutes of CPU time per request.
Allowing more CPU-intensive workloads.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-25-higher-cpu-limits/
md: https://developers.cloudflare.com/changelog/2025-03-25-higher-cpu-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Run Workers for up to 5 minutes of CPU-time
Mar 26, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now run a Worker for up to 5 minutes of CPU time for each request.
Previously, each Workers request ran for a maximum of 30 seconds of CPU time — that is the time that a Worker is actually performing a task (we still allowed unlimited wall-clock time, in case you were waiting on slow resources). This meant that some compute-intensive tasks were impossible to do with a Worker. For instance, you might want to take the cryptographic hash of a large file from R2. If this computation ran for over 30 seconds, the Worker request would have timed out.
By default, Workers are still limited to 30 seconds of CPU time. This protects developers from incurring accidental cost due to buggy code.
By changing the `cpu_ms` value in your Wrangler configuration, you can opt in to any value up to 300,000 (5 minutes).
* wrangler.jsonc
```jsonc
{
// ...rest of your configuration...
"limits": {
"cpu_ms": 300000,
},
// ...rest of your configuration...
}
```
* wrangler.toml
```toml
[limits]
cpu_ms = 300_000
```
Note
CPU time is the amount of time the CPU actually spends doing work during a given request. If a Worker's request makes a sub-request and waits for that request to come back before doing additional work, this time spent waiting **is not** counted towards CPU time.
Worker requests could run for more than 30 seconds of total time prior to this change — only CPU time was limited.
For more information on the updates limits, see the documentation on [Wrangler configuration for `cpu_ms`](https://developers.cloudflare.com/workers/wrangler/configuration/#limits) and on [Workers CPU time limits](https://developers.cloudflare.com/workers/platform/limits/#cpu-time).
For building long-running tasks on Cloudflare, we also recommend checking out [Workflows](https://developers.cloudflare.com/workflows/) and [Queues](https://developers.cloudflare.com/queues/).
---
title: New Pause & Purge APIs for Queues · Changelog
description: Queues now supports the ability to pause delivery and/or delete
messages from a queue, allowing you to better manage queue backlogs.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-25-pause-purge-queues/
md: https://developers.cloudflare.com/changelog/2025-03-25-pause-purge-queues/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Pause & Purge APIs for Queues
Mar 27, 2025
[Queues](https://developers.cloudflare.com/queues/)
[Queues](https://developers.cloudflare.com/queues/) now supports the ability to pause message delivery and/or purge (delete) messages on a queue. These operations can be useful when:
* Your consumer has a bug or downtime, and you want to temporarily stop messages from being processed while you fix the bug
* You have pushed invalid messages to a queue due to a code change during development, and you want to clean up the backlog
* Your queue has a backlog that is stale and you want to clean it up to allow new messages to be consumed
To pause a queue using [Wrangler](https://developers.cloudflare.com/workers/wrangler/), run the `pause-delivery` command. Paused queues continue to receive messages. And you can easily unpause a queue using the `resume-delivery` command.
```bash
$ wrangler queues pause-delivery my-queue
Pausing message delivery for queue my-queue.
Paused message delivery for queue my-queue.
$ wrangler queues resume-delivery my-queue
Resuming message delivery for queue my-queue.
Resumed message delivery for queue my-queue.
```
Purging a queue permanently deletes all messages in the queue. Unlike pausing, purging is an irreversible operation:
```bash
$ wrangler queues purge my-queue
✔ This operation will permanently delete all the messages in queue my-queue. Type my-queue to proceed. … my-queue
Purged queue 'my-queue'
```
You can also do these operations using the [Queues REST API](https://developers.cloudflare.com/api/resources/queues/), or the dashboard page for a queue.

This feature is available on all new and existing queues. Head over to the [pause and purge documentation](https://developers.cloudflare.com/queues/configuration/pause-purge) to learn more. And if you haven't used Cloudflare Queues before, [get started with the Cloudflare Queues guide](https://developers.cloudflare.com/queues/get-started).
---
title: Updates to Account Home - Quick actions, traffic insights, Workers
projects, and more · Changelog
description: Your Account Home just got a major upgrade
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-26-account-home-updates/
md: https://developers.cloudflare.com/changelog/2025-03-26-account-home-updates/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Updates to Account Home - Quick actions, traffic insights, Workers projects, and more
Mar 26, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Recently, Account Home has been updated to streamline your workflows:
* **Recent Workers projects**: You'll now find your projects readily accessible from a new `Developer Platform` tab on Account Home. See recently-modified projects and explore what you can work our developer-focused products.
* **Traffic and security insights**: Get a snapshot of domain performance at a glance with key metrics and trends.
* **Quick actions**: You can now perform common actions for your account, domains, and even Workers in just 1-2 clicks from the 3-dot menu.
* **Keep starred domains front and center**: Now, when you filter for starred domains on Account Home, we'll save your preference so you'll continue to only see starred domains by default.
We can't wait for you to take the new Account Home for a spin.
For more info:
* [Try the updated Account Home](https://dash.cloudflare.com/)
* [Documentation on starred domains](https://developers.cloudflare.com/fundamentals/manage-domains/star-zones/)
---
title: Register and renew .ai and .shop domains at cost · Changelog
description: You can now register and transfer .ai and .shop domains with Cloudflare
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-27-ai-domains-available/
md: https://developers.cloudflare.com/changelog/2025-03-27-ai-domains-available/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Register and renew .ai and .shop domains at cost
Mar 27, 2025
[Registrar](https://developers.cloudflare.com/registrar/)

Cloudflare Registrar now supports `.ai` and `.shop` domains. These are two of our most highly-requested top-level domains (TLDs) and are great additions to the [300+ other TLDs we support](https://domains.cloudflare.com/tlds).
Starting today, customers can:
* Register and renew these domains *at cost* without any markups or add-on fees
* Enjoy best-in-class security and performance with native integrations with Cloudflare DNS, CDN, and SSL services like one-click DNSSEC
* Combat domain hijacking with [Custom Domain Protection](https://www.cloudflare.com/products/registrar/custom-domain-protection/) (available on enterprise plans)
We can't wait to see what AI and e-commerce projects you deploy on Cloudflare. To get started, transfer your domains to Cloudflare or [search for new ones to register](https://domains.cloudflare.com/).
---
title: Audit logs (version 2) - Beta Release · Changelog
description: New version of audit logs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-27-automatic-audit-logs-beta-release/
md: https://developers.cloudflare.com/changelog/2025-03-27-automatic-audit-logs-beta-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Audit logs (version 2) - Beta Release
Mar 27, 2025
[Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/)
The latest version of audit logs streamlines audit logging by automatically capturing all user and system actions performed through the Cloudflare Dashboard or public APIs. This update leverages Cloudflare’s existing API Shield to generate audit logs based on OpenAPI schemas, ensuring a more consistent and automated logging process.
Availability: Audit logs (version 2) is now in Beta, with support limited to **API access**.
Use the following API endpoint to retrieve audit logs:
```js
GET https://api.cloudflare.com/client/v4/accounts//logs/audit?since=&before=
```
You can access detailed documentation for audit logs (version 2) Beta API release [here](https://developers.cloudflare.com/api/resources/accounts/subresources/logs/subresources/audit/methods/list/).
**Key Improvements in the Beta Release:**
* **Automated & standardized logging**: Logs are now generated automatically using a standardized system, replacing manual, team-dependent logging. This ensures consistency across all Cloudflare services.
* **Expanded product coverage**: Increased audit log coverage from 75% to 95%. Key API endpoints such as `/accounts`, `/zones`, and `/organizations` are now included.
* **Granular filtering**: Logs now follow a uniform format, enabling precise filtering by actions, users, methods, and resources—allowing for faster and more efficient investigations.
* **Enhanced context and traceability**: Each log entry now includes detailed context, such as the authentication method used, the interface (API or Dashboard) through which the action was performed, and mappings to Cloudflare Ray IDs for better traceability.
* **Comprehensive activity capture**: Expanded logging to include GET requests and failed attempts, ensuring that all critical activities are recorded.
**Known Limitations in Beta**
* Error handling for the API is not implemented.
* There may be gaps or missing entries in the available audit logs.
* UI is unavailable in this Beta release.
* System-level logs and User-Activity logs are not included.
Support for these features is coming as part of the GA release later this year. For more details, including a sample audit log, check out our blog post: [Introducing Automatic Audit Logs](https://blog.cloudflare.com/introducing-automatic-audit-logs/)
---
title: WARP client for Linux (version 2025.2.600.0) · Changelog
description: WARP client for Linux (version 2025.2.600.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-31-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-03-31-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.2.600.0)
Mar 31, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains support for a new WARP setting, [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices). It also includes significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Fixed an issue with device revocation and re-registration when switching configurations.
* Added a new [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
---
title: WARP client for macOS (version 2025.2.600.0) · Changelog
description: WARP client for macOS (version 2025.2.600.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-31-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-03-31-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.2.600.0)
Mar 31, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains support for a new WARP setting, [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices). It also includes significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Fixed an issue with device revocation and re-registration when switching configurations.
* Added a new [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
---
title: WARP client for Windows (version 2025.2.600.0) · Changelog
description: WARP client for Windows (version 2025.2.600.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-03-31-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-03-31-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.2.600.0)
Mar 31, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains support for a new WARP setting, [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices). It also includes significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
**Changes and improvements**
* Improved [captive portal detection](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/) to make more public networks compatible and have faster detection.
* Improved error messages shown in the app.
* Added the ability to control if the WARP interface IPs are [registered with DNS servers](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#warp-interface-ip-dns-registration) or not.
* Removed DNS logs view from the Windows client GUI. DNS logs can be viewed as part of `warp-diag` or by viewing the log file on the user's local directory.
* Fixed an issue that would result in a user receiving multiple re-authentication requests when waking their device from sleep.
* WARP tunnel protocol details can now be viewed using the `warp-cli tunnel stats` command.
* Improvements to [Windows multi-user](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/) including support for fast user switching. If you are interested in testing this feature, reach out to your Cloudflare account team.
* Fixed an issue with device revocation and re-registration when switching configurations.
* Fixed an issue where DEX tests would run during certain sleep states where the networking stack was not fully up. This would result in failures that would be ignored.
* Added a new [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: CASB and Email security · Changelog
description: Get two free CASB integrations with your Email security subscription.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-01-casb-email-security/
md: https://developers.cloudflare.com/changelog/2025-04-01-casb-email-security/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## CASB and Email security
Apr 01, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
With Email security, you get two free CASB integrations.
Use one SaaS integration for Email security to sync with your directory of users, take actions on delivered emails, automatically provide EMLs for reclassification requests for clean emails, discover CASB findings and more.
With the other integration, you can have a separate SaaS integration for CASB findings for another SaaS provider.
Refer to [Add an integration](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/#add-an-integration) to learn more about this feature.

This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: All cache purge methods now available for all plans · Changelog
description: All Cloudflare plans can purge by tag, prefix, url, host, or
everything to invalidate cached content on the fly.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-01-purge-for-all/
md: https://developers.cloudflare.com/changelog/2025-04-01-purge-for-all/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## All cache purge methods now available for all plans
Apr 03, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now access all Cloudflare cache purge methods — no matter which plan you’re on. Whether you need to update a single asset or instantly invalidate large portions of your site’s content, you now have the same powerful tools previously reserved for Enterprise customers.
**Anyone on Cloudflare can now:**
1. [Purge Everything](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-everything/): Clears all cached content associated with a website.
2. [Purge by Prefix](https://developers.cloudflare.com/cache/how-to/purge-cache/purge_by_prefix/): Targets URLs sharing a common prefix.
3. [Purge by Hostname](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-hostname/): Invalidates content by specific hostnames.
4. [Purge by URL (single-file purge)](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-single-file/): Precisely targets individual URLs.
5. [Purge by Tag](https://developers.cloudflare.com/cache/how-to/purge-cache/purge-by-tags/): Uses Cache-Tag response headers to invalidate grouped assets, offering flexibility for complex cache management scenarios.
Want to learn how each purge method works, when to use them, or what limits apply to your plan? Dive into our [purge cache documentation](https://developers.cloudflare.com/cache/how-to/purge-cache/) and [API reference](https://developers.cloudflare.com/api/resources/cache/methods/purge/) for all the details.
---
title: WAF Release - 2025-04-02 · Changelog
description: Cloudflare WAF managed rulesets 2025-04-02 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-02-waf-release/
md: https://developers.cloudflare.com/changelog/2025-04-02-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-04-02
Apr 02, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 8b8074e73b7d4aba92fc68f3622f0483 | 100732 | Sitecore - Code Injection - CVE:CVE-2025-27218 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 8350947451a1401c934f5e660f101cca | 100733 | Angular-Base64-Upload - Remote Code Execution - CVE:CVE-2024-42640 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | a9ec9cf625ff42769298671d1bbcd247 | 100734 | Apache Camel - Remote Code Execution - CVE:CVE-2025-29891 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 3d6bf99039b54312a1a2165590aea1ca | 100735 | Progress Software WhatsUp Gold - Remote Code Execution - CVE:CVE-2024-4885 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | d104e3246dc14ac7851b4049d9d8c5f2 | 100737 | Apache Tomcat - Remote Code Execution - CVE:CVE-2025-24813 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 21c7a963e1b749e7b1753238a28a42c4 | 100659 | Common Payloads for Server-side Template Injection | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | 887843ffbe90436dadd1543adaa4b037 | 100659 | Common Payloads for Server-side Template Injection - Base64 | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | 3565b80fc5b541b4832c0fc848f6a9cf | 100642 | LDAP Injection | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | 44d7bf9bf0fa4898b8579573e0713e9f | 100642 | LDAP Injection Base64 | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | e35c9a670b864a3ba0203ffb1bc977d1 | 100005 | DotNetNuke - File Inclusion - CVE:CVE-2018-9126, CVE:CVE-2011-1892, CVE:CVE-2022-31474 | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | cd8db44032694fdf8d6e22c1bb70a463 | 100527 | Apache Struts - CVE:CVE-2021-31805 | N/A | Block | N/A |
| Cloudflare Managed Ruleset | 0d838d9ab046443fa3f8b3e50c99546a | 100702 | Command Injection - CVE:CVE-2022-24108 | N/A | Block | N/A |
| Cloudflare Managed Ruleset | 533fbad558ce4c5ebcf013f09a5581d0 | 100622C | Ivanti - Command Injection - CVE:CVE-2023-46805, CVE:CVE-2024-21887, CVE:CVE-2024-22024 | N/A | Block | N/A |
| Cloudflare Managed Ruleset | 04176552f62f4b75bf65981206d0b009 | 100536C | GraphQL Command Injection | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | 25883bf28575433c952b830c1651d0c8 | 100536 | GraphQL Injection | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | 7b70da1bb8d243bd80cd7a73af00f61d | 100536A | GraphQL Introspection | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | 58c4853c250946359472b7eaa41e5b67 | 100536B | GraphQL SSRF | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | 1c241ed5f5bd44b19e17476b433e5b3d | 100559A | Prototype Pollution - Common Payloads | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | af748489e1c2411d80d855954816b26f | 100559A | Prototype Pollution - Common Payloads - Base64 | N/A | Disabled | N/A |
| Cloudflare Managed Ruleset | ccc47ab7e34248c09546c284fcea5ed2 | 100734 | Apache Camel - Remote Code Execution - CVE:CVE-2025-29891 | N/A | Disabled | N/A |
---
title: Playwright for Browser Rendering now available · Changelog
description: Developers can now use the Playwright library for browser
automation with Browser Rendering
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-04-playwright-beta/
md: https://developers.cloudflare.com/changelog/2025-04-04-playwright-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Playwright for Browser Rendering now available
Apr 04, 2025
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We're excited to share that you can now use Playwright's browser automation [capabilities](https://playwright.dev/docs/api/class-playwright) from Cloudflare [Workers](https://developers.cloudflare.com/workers/).
[Playwright](https://playwright.dev/) is an open-source package developed by Microsoft that can do browser automation tasks; it's commonly used to write software tests, debug applications, create screenshots, and crawl pages. Like [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/), we [forked](https://github.com/cloudflare/playwright) Playwright and modified it to be compatible with Cloudflare Workers and [Browser Rendering](https://developers.cloudflare.com/browser-rendering/).
Below is an example of how to use Playwright with Browser Rendering to test a TODO application using assertions:
```ts
import { launch, type BrowserWorker } from "@cloudflare/playwright";
import { expect } from "@cloudflare/playwright/test";
interface Env {
MYBROWSER: BrowserWorker;
}
export default {
async fetch(request: Request, env: Env) {
const browser = await launch(env.MYBROWSER);
const page = await browser.newPage();
await page.goto("https://demo.playwright.dev/todomvc");
const TODO_ITEMS = [
"buy some cheese",
"feed the cat",
"book a doctors appointment",
];
const newTodo = page.getByPlaceholder("What needs to be done?");
for (const item of TODO_ITEMS) {
await newTodo.fill(item);
await newTodo.press("Enter");
}
await expect(page.getByTestId("todo-title")).toHaveCount(TODO_ITEMS.length);
await Promise.all(
TODO_ITEMS.map((value, index) =>
expect(page.getByTestId("todo-title").nth(index)).toHaveText(value),
),
);
},
};
```
Playwright is available as an npm package at [`@cloudflare/playwright`](https://www.npmjs.com/package/@cloudflare/playwright) and the code is at [GitHub](https://github.com/cloudflare/playwright).
Learn more in our [documentation](https://developers.cloudflare.com/browser-rendering/playwright/).
---
title: Workers Fetch API can override Cache Rules · Changelog
description: Customers who use Workers can now programmatically override Cache
Rules for their individual requests.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-04-workers-fetch-api-override-cache-rules/
md: https://developers.cloudflare.com/changelog/2025-04-04-workers-fetch-api-override-cache-rules/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers Fetch API can override Cache Rules
Apr 04, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now programmatically override Cache Rules using the `cf` object in the `fetch()` command. This feature gives you fine-grained control over caching behavior on a per-request basis, allowing Workers to customize cache settings dynamically based on request properties, user context, or business logic.
#### How it works
Using the `cf` object in `fetch()`, you can override specific Cache Rules settings by:
1. **Setting custom cache options**: Pass cache properties in the `cf` object as the second argument to `fetch()` to override default Cache Rules.
2. **Dynamic cache control**: Apply different caching strategies based on request headers, cookies, or other runtime conditions.
3. **Per-request customization**: Bypass or modify Cache Rules for individual requests while maintaining default behavior for others.
4. **Programmatic cache management**: Implement complex caching logic that adapts to your application's needs.
#### What can be configured
Workers can override the following Cache Rules settings through the `cf` object:
* **`cacheEverything`**: Treat all content as static and cache all file types beyond the default cached content.
* **`cacheTtl`**: Set custom time-to-live values in seconds for cached content at the edge, regardless of origin headers.
* **`cacheTtlByStatus`**: Set different TTLs based on the response status code (for example, `{ "200-299": 86400, 404: 1, "500-599": 0 }`).
* **`cacheKey`**: Customize cache keys to control which requests are treated as the same for caching purposes (Enterprise only).
* **`cacheTags`**: Append additional cache tags for targeted cache purging operations.
#### Benefits
* **Enhanced flexibility**: Customize cache behavior without modifying zone-level Cache Rules.
* **Dynamic optimization**: Adjust caching strategies in real-time based on request context.
* **Simplified configuration**: Reduce the number of Cache Rules needed by handling edge cases programmatically.
* **Improved performance**: Fine-tune cache behavior for specific use cases to maximize hit rates.
#### Get started
To get started, refer to the [Workers Fetch API documentation](https://developers.cloudflare.com/workers/runtime-apis/fetch/) and the [cf object properties documentation](https://developers.cloudflare.com/workers/runtime-apis/request/#the-cf-property-requestinitcfproperties).
---
title: Create fully-managed RAG pipelines for your AI applications with AutoRAG
· Changelog
description: AutoRAG lets you create fully-managed, retrieval-augmented
generation (RAG) pipelines that continuously updates and scales on Cloudflare.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-07-autorag-open-beta/
md: https://developers.cloudflare.com/changelog/2025-04-07-autorag-open-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Create fully-managed RAG pipelines for your AI applications with AutoRAG
Apr 07, 2025
[AI Search ](https://developers.cloudflare.com/ai-search/)[Vectorize](https://developers.cloudflare.com/vectorize/)
[AutoRAG](https://developers.cloudflare.com/ai-search/) is now in open beta, making it easy for you to build fully-managed retrieval-augmented generation (RAG) pipelines without managing infrastructure. Just upload your docs to [R2](https://developers.cloudflare.com/r2/get-started/), and AutoRAG handles the rest: embeddings, indexing, retrieval, and response generation via API.

With AutoRAG, you can:
* **Customize your pipeline:** Choose from [Workers AI](https://developers.cloudflare.com/workers-ai) models, configure chunking strategies, edit system prompts, and more.
* **Instant setup:** AutoRAG provisions everything you need from [Vectorize](https://developers.cloudflare.com/vectorize), [AI gateway](https://developers.cloudflare.com/ai-gateway), to pipeline logic for you, so you can go from zero to a working RAG pipeline in seconds.
* **Keep your index fresh:** AutoRAG continuously syncs your index with your data source to ensure responses stay accurate and up to date.
* **Ask questions:** Query your data and receive grounded responses via a [Workers binding](https://developers.cloudflare.com/ai-search/usage/workers-binding/) or [API](https://developers.cloudflare.com/ai-search/usage/rest-api/).
Whether you're building internal tools, AI-powered search, or a support assistant, AutoRAG gets you from idea to deployment in minutes.
Get started in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/ai/autorag) or check out the [guide](https://developers.cloudflare.com/ai-search/get-started/) for instructions on how to build your RAG pipeline today.
---
title: Browser Rendering REST API is Generally Available, with new endpoints and
a free tier · Changelog
description: Browser Rendering updates - free tier and REST API GA with new endpoints
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-07-br-free-ga-playwright/
md: https://developers.cloudflare.com/changelog/2025-04-07-br-free-ga-playwright/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Browser Rendering REST API is Generally Available, with new endpoints and a free tier
Apr 07, 2025
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We’re excited to announce Browser Rendering is now available on the [Workers Free plan](https://www.cloudflare.com/plans/developer-platform/), making it even easier to prototype and experiment with web search and headless browser use-cases when building applications on Workers.
The Browser Rendering **[REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) is now Generally Available**, allowing you to control browser instances from outside of Workers applications. We've added three new endpoints to help automate more browser tasks:
* **Extract structured data** – Use `/json` to retrieve structured data from a webpage.
* **Retrieve links** – Use `/links` to pull all links from a webpage.
* **Convert to Markdown** – Use `/markdown` to convert webpage content into Markdown format.
For example, to fetch the Markdown representation of a webpage:
```bash
curl -X 'POST' 'https://api.cloudflare.com/client/v4/accounts//browser-rendering/markdown' \
-H 'Content-Type: application/json' \
-H 'Authorization: Bearer ' \
-d '{
"url": "https://example.com"
}'
```
For the full list of endpoints, check out our [REST API documentation](https://developers.cloudflare.com/browser-rendering/rest-api/). You can also interact with Browser Rendering via the [Cloudflare TypeScript SDK](https://github.com/cloudflare/cloudflare-typescript).
We also recently landed support for [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/) in Browser Rendering for browser automation from Cloudflare [Workers](https://developers.cloudflare.com/workers/), in addition to [Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/), giving you more flexibility to test across different browser environments.
Visit the [Browser Rendering docs](https://developers.cloudflare.com/browser-rendering/) to learn more about how to use headless browsers in your applications.
---
title: Durable Objects on Workers Free plan · Changelog
description: Durable Objects now available on Workers Free plan.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-07-durable-objects-free-tier/
md: https://developers.cloudflare.com/changelog/2025-04-07-durable-objects-free-tier/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Durable Objects on Workers Free plan
Apr 07, 2025
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
Durable Objects can now be used with zero commitment on the [Workers Free plan](https://developers.cloudflare.com/workers/platform/pricing/) allowing you to build AI agents with [Agents SDK](https://developers.cloudflare.com/agents/), collaboration tools, and real-time applications like chat or multiplayer games.
Durable Objects let you build stateful, serverless applications with millions of tiny coordination instances that run your application code alongside (in the same thread!) your durable storage. Each Durable Object can access its own SQLite database through a [Storage API](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/). A Durable Object class is defined in a Worker script encapsulating the Durable Object's behavior when accessed from a Worker. To try the code below, click the button:
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/hello-world-do-template)
```js
import { DurableObject } from "cloudflare:workers";
// Durable Object
export class MyDurableObject extends DurableObject {
...
async sayHello(name) {
return `Hello, ${name}!`;
}
}
// Worker
export default {
async fetch(request, env) {
// Every unique ID refers to an individual instance of the Durable Object class
const id = env.MY_DURABLE_OBJECT.idFromName("foo");
// A stub is a client used to invoke methods on the Durable Object
const stub = env.MY_DURABLE_OBJECT.get(id);
// Methods on the Durable Object are invoked via the stub
const response = await stub.sayHello("world");
return response;
},
};
```
Free plan [limits](https://developers.cloudflare.com/durable-objects/platform/pricing/) apply to Durable Objects compute and storage usage. Limits allow developers to build real-world applications, with every Worker request able to call a Durable Object on the free plan.
For more information, checkout:
* [Documentation](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/)
* [Zero-latency SQLite storage in every Durable Object blog](https://blog.cloudflare.com/sqlite-in-durable-objects/)
---
title: Capture up to 256 KB of log events in each Workers Invocation · Changelog
description: You can now capture up to 256 KB of log events per Workers
Invocation helping you gain better visibility into application behavior.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-07-increase-trace-events-limit/
md: https://developers.cloudflare.com/changelog/2025-04-07-increase-trace-events-limit/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Capture up to 256 KB of log events in each Workers Invocation
Apr 07, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now capture a maximum of 256 KB of log events per Workers invocation, helping you gain better visibility into application behavior.
All console.log() statements, exceptions, request metadata, and headers are automatically captured during the Worker invocation and emitted as [JSON object](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/workers_trace_events). [Workers Logs](https://developers.cloudflare.com/workers/observability/logs/workers-logs) deserializes this object before indexing the fields and storing them. You can also capture, transform, and export the JSON object in a [Tail Worker](https://developers.cloudflare.com/workers/observability/logs/tail-workers).
256 KB is a 2x increase from the previous 128 KB limit. After you exceed this limit, further context associated with the request will not be recorded in your logs.
This limit is automatically applied to all Workers.
---
title: Build MCP servers with the Agents SDK · Changelog
description: The Agents SDK now includes built-in support for building remote
MCP servers directly as part of your Agent.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-07-mcp-servers-agents-sdk-updates/
md: https://developers.cloudflare.com/changelog/2025-04-07-mcp-servers-agents-sdk-updates/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Build MCP servers with the Agents SDK
Apr 07, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
The Agents SDK now includes built-in support for building remote MCP (Model Context Protocol) servers directly as part of your Agent. This allows you to easily create and manage MCP servers, without the need for additional infrastructure or configuration.
The SDK includes a new `MCPAgent` class that extends the `Agent` class and allows you to expose resources and tools over the MCP protocol, as well as authorization and authentication to enable remote MCP servers.
* JavaScript
```js
export class MyMCP extends McpAgent {
server = new McpServer({
name: "Demo",
version: "1.0.0",
});
async init() {
this.server.resource(`counter`, `mcp://resource/counter`, (uri) => {
// ...
});
this.server.tool(
"add",
"Add two numbers together",
{ a: z.number(), b: z.number() },
async ({ a, b }) => {
// ...
},
);
}
}
```
* TypeScript
```ts
export class MyMCP extends McpAgent {
server = new McpServer({
name: "Demo",
version: "1.0.0",
});
async init() {
this.server.resource(`counter`, `mcp://resource/counter`, (uri) => {
// ...
});
this.server.tool(
"add",
"Add two numbers together",
{ a: z.number(), b: z.number() },
async ({ a, b }) => {
// ...
},
);
}
}
```
See [the example](https://github.com/cloudflare/agents/tree/main/examples/mcp) for the full code and as the basis for building your own MCP servers, and the [client example](https://github.com/cloudflare/agents/tree/main/examples/mcp-client) for how to build an Agent that acts as an MCP client.
To learn more, review the [announcement blog](https://blog.cloudflare.com/building-ai-agents-with-mcp-authn-authz-and-durable-objects) as part of Developer Week 2025.
#### Agents SDK updates
We've made a number of improvements to the [Agents SDK](https://developers.cloudflare.com/agents/), including:
* Support for building MCP servers with the new `MCPAgent` class.
* The ability to export the current agent, request and WebSocket connection context using `import { context } from "agents"`, allowing you to minimize or avoid direct dependency injection when calling tools.
* Fixed a bug that prevented query parameters from being sent to the Agent server from the `useAgent` React hook.
* Automatically converting the `agent` name in `useAgent` or `useAgentChat` to kebab-case to ensure it matches the naming convention expected by [`routeAgentRequest`](https://developers.cloudflare.com/agents/api-reference/routing/).
To install or update the Agents SDK, run `npm i agents@latest` in an existing project, or explore the `agents-starter` project:
```sh
npm create cloudflare@latest -- --template cloudflare/agents-starter
```
See the full release notes and changelog [on the Agents SDK repository](https://github.com/cloudflare/agents/blob/main/packages/agents/CHANGELOG.md) and
---
title: SQLite in Durable Objects GA with 10GB storage per object · Changelog
description: SQLite-backed Durable Objects are generally available.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-07-sqlite-in-durable-objects-ga/
md: https://developers.cloudflare.com/changelog/2025-04-07-sqlite-in-durable-objects-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## SQLite in Durable Objects GA with 10GB storage per object
Apr 07, 2025
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
SQLite in Durable Objects is now generally available (GA) with 10GB SQLite database per Durable Object. Since the [public beta](https://blog.cloudflare.com/sqlite-in-durable-objects/) in September 2024, we've added feature parity and robustness for the SQLite storage backend compared to the preexisting key-value (KV) storage backend for Durable Objects.
SQLite-backed Durable Objects are recommended for all new Durable Object classes, using `new_sqlite_classes` [Wrangler configuration](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#create-sqlite-backed-durable-object-class). Only SQLite-backed Durable Objects have access to Storage API's [SQL](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/#sql-api) and [point-in-time recovery](https://developers.cloudflare.com/durable-objects/api/sqlite-storage-api/#pitr-point-in-time-recovery-api) methods, which provide relational data modeling, SQL querying, and better data management.
```js
export class MyDurableObject extends DurableObject {
sql: SqlStorage
constructor(ctx: DurableObjectState, env: Env) {
super(ctx, env);
this.sql = ctx.storage.sql;
}
async sayHello() {
let result = this.sql
.exec("SELECT 'Hello, World!' AS greeting")
.one();
return result.greeting;
}
}
```
KV-backed Durable Objects remain for backwards compatibility, and a migration path from key-value storage to SQL storage for existing Durable Object classes will be offered in the future.
For more details on SQLite storage, checkout [Zero-latency SQLite storage in every Durable Object blog](https://blog.cloudflare.com/sqlite-in-durable-objects/).
---
title: Workflows is now Generally Available · Changelog
description: Workflows is now GA - ship Workflows that you can rely on in production.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-07-workflows-ga/
md: https://developers.cloudflare.com/changelog/2025-04-07-workflows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workflows is now Generally Available
Apr 07, 2025
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
[Workflows](https://developers.cloudflare.com/workflows/) is now *Generally Available* (or "GA"): in short, it's ready for production workloads. Alongside marking Workflows as GA, we've introduced a number of changes during the beta period, including:
* A new `waitForEvent` API that allows a Workflow to wait for an event to occur before continuing execution.
* Increased concurrency: you can [run up to 4,500 Workflow instances](https://developers.cloudflare.com/changelog/2025-02-25-workflows-concurrency-increased/) concurrently — and this will continue to grow.
* Improved observability, including new CPU time metrics that allow you to better understand which Workflow instances are consuming the most resources and/or contributing to your bill.
* Support for `vitest` for testing Workflows locally and in CI/CD pipelines.
Workflows also supports the new [increased CPU limits](https://developers.cloudflare.com/changelog/2025-03-25-higher-cpu-limits/) that apply to Workers, allowing you to run more CPU-intensive tasks (up to 5 minutes of CPU time per instance), not including the time spent waiting on network calls, AI models, or other I/O bound tasks.
#### Human-in-the-loop
The new `step.waitForEvent` API allows a Workflow instance to wait on events and data, enabling human-in-the-the-loop interactions, such as approving or rejecting a request, directly handling webhooks from other systems, or pushing event data to a Workflow while it's running.
Because Workflows are just code, you can conditionally execute code based on the result of a `waitForEvent` call, and/or call `waitForEvent` multiple times in a single Workflow based on what the Workflow needs.
For example, if you wanted to implement a human-in-the-loop approval process, you could use `waitForEvent` to wait for a user to approve or reject a request, and then conditionally execute code based on the result.
* JavaScript
```js
import { Workflow, WorkflowEvent } from "cloudflare:workflows";
export class MyWorkflow extends WorkflowEntrypoint {
async run(event, step) {
// Other steps in your Workflow
let event = await step.waitForEvent(
"receive invoice paid webhook from Stripe",
{ type: "stripe-webhook", timeout: "1 hour" },
);
// Rest of your Workflow
}
}
```
* TypeScript
```ts
import { Workflow, WorkflowEvent } from "cloudflare:workflows";
export class MyWorkflow extends WorkflowEntrypoint {
async run(event: WorkflowEvent, step: WorkflowStep) {
// Other steps in your Workflow
let event = await step.waitForEvent("receive invoice paid webhook from Stripe", { type: "stripe-webhook", timeout: "1 hour" })
// Rest of your Workflow
}
}
```
You can then send a Workflow an event from an external service via HTTP or from within a Worker using the [Workers API](https://developers.cloudflare.com/workflows/build/workers-api/) for Workflows:
* JavaScript
```js
export default {
async fetch(req, env) {
const instanceId = new URL(req.url).searchParams.get("instanceId");
const webhookPayload = await req.json();
let instance = await env.MY_WORKFLOW.get(instanceId);
// Send our event, with `type` matching the event type defined in
// our step.waitForEvent call
await instance.sendEvent({
type: "stripe-webhook",
payload: webhookPayload,
});
return Response.json({
status: await instance.status(),
});
},
};
```
* TypeScript
```ts
export default {
async fetch(req: Request, env: Env) {
const instanceId = new URL(req.url).searchParams.get("instanceId")
const webhookPayload = await req.json()
let instance = await env.MY_WORKFLOW.get(instanceId);
// Send our event, with `type` matching the event type defined in
// our step.waitForEvent call
await instance.sendEvent({type: "stripe-webhook", payload: webhookPayload})
return Response.json({
status: await instance.status(),
});
},
};
```
Read the [GA announcement blog](https://blog.cloudflare.com/workflows-is-now-generally-available/) to learn more about what landed as part of the Workflows GA.
---
title: Deploy a Workers application in seconds with one-click · Changelog
description: You can now add a Deploy to Cloudflare button to your repository's
README to help other developers set up and deploy your project.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-deploy-to-cloudflare-button/
md: https://developers.cloudflare.com/changelog/2025-04-08-deploy-to-cloudflare-button/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Deploy a Workers application in seconds with one-click
Apr 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now add a [Deploy to Cloudflare](https://developers.cloudflare.com/workers/platform/deploy-buttons/) button to the README of your Git repository containing a Workers application — making it simple for other developers to quickly set up and deploy your project!
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/saas-admin-template)
The Deploy to Cloudflare button:
1. **Creates a new Git repository on your GitHub/ GitLab account**: Cloudflare will automatically clone and create a new repository on your account, so you can continue developing.
2. **Automatically provisions resources the app needs**: If your repository requires Cloudflare primitives like a [Workers KV namespace](https://developers.cloudflare.com/kv/), a [D1 database](https://developers.cloudflare.com/d1/), or an [R2 bucket](https://developers.cloudflare.com/r2/), Cloudflare will automatically provision them on your account and bind them to your Worker upon deployment.
3. **Configures Workers Builds (CI/CD)**: Every new push to your production branch on your newly created repository will automatically build and deploy courtesy of [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/).
4. **Adds preview URLs to each pull request**: If you'd like to test your changes before deploying, you can push changes to a [non-production branch](https://developers.cloudflare.com/workers/ci-cd/builds/build-branches/#configure-non-production-branch-builds) and [preview URLs](https://developers.cloudflare.com/workers/configuration/previews/) will be generated and [posted back to GitHub as a comment](https://developers.cloudflare.com/workers/ci-cd/builds/git-integration/github-integration/#pull-request-comment).
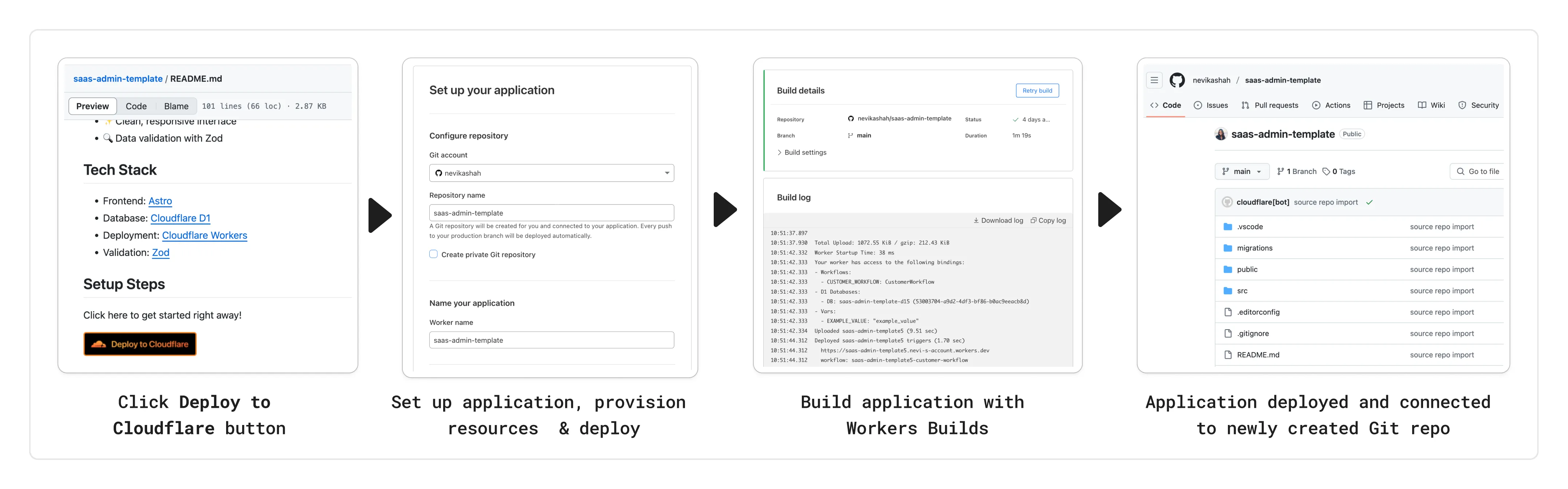
To create a Deploy to Cloudflare button in your README, you can add the following snippet, including your Git repository URL:
```md
[](https://deploy.workers.cloudflare.com/?url=)
```
Check out our [documentation](https://developers.cloudflare.com/workers/platform/deploy-buttons/) for more information on how to set up a deploy button for your application and best practices to ensure a successful deployment for other developers.
---
title: Full-stack frameworks are now Generally Available on Cloudflare Workers ·
Changelog
description: Cloudflare Workers now provides production ready, generally
available (GA) support for React Router v7 (Remix), Astro, Hono, Vue.js, Nuxt,
Svelte (SvelteKit), and more.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-fullstack-on-workers/
md: https://developers.cloudflare.com/changelog/2025-04-08-fullstack-on-workers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Full-stack frameworks are now Generally Available on Cloudflare Workers
Apr 08, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)

The following full-stack frameworks now have Generally Available ("GA") adapters for Cloudflare Workers, and are ready for you to use in production:
* [React Router v7 (Remix)](https://developers.cloudflare.com/workers/framework-guides/web-apps/react-router/)
* [Astro](https://developers.cloudflare.com/workers/framework-guides/web-apps/astro/)
* [Hono](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/hono/)
* [Vue.js](https://developers.cloudflare.com/workers/framework-guides/web-apps/vue/)
* [Nuxt](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/nuxt/)
* [Svelte (SvelteKit)](https://developers.cloudflare.com/workers/framework-guides/web-apps/sveltekit/)
* And [more](https://developers.cloudflare.com/workers/framework-guides/).
The following frameworks are now in **beta**, with GA support coming very soon:
* [Next.js](https://developers.cloudflare.com/workers/framework-guides/web-apps/nextjs/), supported through [@opennextjs/cloudflare](https://opennext.js.org/cloudflare) is now `v1.0-beta`.
* [Angular](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/angular/)
* [SolidJS (SolidStart)](https://developers.cloudflare.com/workers/framework-guides/web-apps/more-web-frameworks/solid/)
You can also build complete full-stack apps on Workers **without a framework**:
* You can [“just use Vite"](https://blog.cloudflare.com/introducing-the-cloudflare-vite-plugin) and React together, and build a back-end API in the same Worker. Follow our [React SPA with an API tutorial](https://developers.cloudflare.com/workers/vite-plugin/tutorial/) to learn how.
**Get started building today with our [framework guides](https://developers.cloudflare.com/workers/framework-guides/)**, or read our [Developer Week 2025 blog post](https://blog.cloudflare.com/full-stack-development-on-cloudflare-workers) about all the updates to building full-stack applications on Workers.
---
title: Hyperdrive Free plan makes fast, global database access available to all
· Changelog
description: Hyperdrive is now available on the Free plan of Cloudflare Workers,
enabling you to build Workers that connect to PostgreSQL or MySQL databases
without compromise.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-hyperdrive-free-plan/
md: https://developers.cloudflare.com/changelog/2025-04-08-hyperdrive-free-plan/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Hyperdrive Free plan makes fast, global database access available to all
Apr 08, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive is now available on the Free plan of Cloudflare Workers, enabling you to build Workers that connect to PostgreSQL or MySQL databases without compromise.
Low-latency access to SQL databases is critical to building full-stack Workers applications. We want you to be able to build on fast, global apps on Workers, regardless of the tools you use. So we made Hyperdrive available for all, to make it easier to build Workers that connect to PostgreSQL and MySQL.
If you want to learn more about how Hyperdrive works, read the [deep dive](https://blog.cloudflare.com/how-hyperdrive-speeds-up-database-access) on how Hyperdrive can make your database queries up to 4x faster.

Visit the docs to [get started](https://developers.cloudflare.com/hyperdrive/get-started/) with Hyperdrive for PostgreSQL or MySQL.
---
title: Hyperdrive introduces support for MySQL and MySQL-compatible databases ·
Changelog
description: You can now connect to MySQL databases from your Workers using
Hyperdrive for optimal performance
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-hyperdrive-mysql-support/
md: https://developers.cloudflare.com/changelog/2025-04-08-hyperdrive-mysql-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Hyperdrive introduces support for MySQL and MySQL-compatible databases
Apr 08, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive now supports connecting to MySQL and MySQL-compatible databases, including Amazon RDS and Aurora MySQL, Google Cloud SQL for MySQL, Azure Database for MySQL, PlanetScale and MariaDB.
Hyperdrive makes your regional, MySQL databases fast when connecting from Cloudflare Workers. It eliminates unnecessary network roundtrips during connection setup, pools database connections globally, and can cache query results to provide the fastest possible response times.
Best of all, you can connect using your existing drivers, ORMs, and query builders with Hyperdrive's secure credentials, no code changes required.
```ts
import { createConnection } from "mysql2/promise";
export interface Env {
HYPERDRIVE: Hyperdrive;
}
export default {
async fetch(request, env, ctx): Promise {
const connection = await createConnection({
host: env.HYPERDRIVE.host,
user: env.HYPERDRIVE.user,
password: env.HYPERDRIVE.password,
database: env.HYPERDRIVE.database,
port: env.HYPERDRIVE.port,
disableEval: true, // Required for Workers compatibility
});
const [results, fields] = await connection.query("SHOW tables;");
ctx.waitUntil(connection.end());
return new Response(JSON.stringify({ results, fields }), {
headers: {
"Content-Type": "application/json",
"Access-Control-Allow-Origin": "*",
},
});
},
} satisfies ExportedHandler;
```
Learn more about [how Hyperdrive works](https://developers.cloudflare.com/hyperdrive/concepts/how-hyperdrive-works/) and [get started building Workers that connect to MySQL with Hyperdrive](https://developers.cloudflare.com/hyperdrive/get-started/).
---
title: Local development support for Email Workers · Changelog
description: Developers can now use wrangler to do local development for Email Workers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-local-development/
md: https://developers.cloudflare.com/changelog/2025-04-08-local-development/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Local development support for Email Workers
Apr 08, 2025
[Email Routing](https://developers.cloudflare.com/email-routing/)
Email Workers enables developers to programmatically take action on anything that hits their email inbox. If you're building with Email Workers, you can now test the behavior of an Email Worker script, receiving, replying and sending emails in your local environment using `wrangler dev`.
Below is an example that shows you how you can receive messages using the `email()` handler and parse them using [postal-mime](https://www.npmjs.com/package/postal-mime):
```ts
import * as PostalMime from "postal-mime";
export default {
async email(message, env, ctx) {
const parser = new PostalMime.default();
const rawEmail = new Response(message.raw);
const email = await parser.parse(await rawEmail.arrayBuffer());
console.log(email);
},
};
```
Now when you run `npx wrangler dev`, wrangler will expose a local `/cdn-cgi/handler/email` endpoint that you can `POST` email messages to and trigger your Worker's `email()` handler:
```bash
curl -X POST 'http://localhost:8787/cdn-cgi/handler/email' \
--url-query 'from=sender@example.com' \
--url-query 'to=recipient@example.com' \
--header 'Content-Type: application/json' \
--data-raw 'Received: from smtp.example.com (127.0.0.1)
by cloudflare-email.com (unknown) id 4fwwffRXOpyR
for ; Tue, 27 Aug 2024 15:50:20 +0000
From: "John"
Reply-To: sender@example.com
To: recipient@example.com
Subject: Testing Email Workers Local Dev
Content-Type: text/html; charset="windows-1252"
X-Mailer: Curl
Date: Tue, 27 Aug 2024 08:49:44 -0700
Message-ID: <6114391943504294873000@ZSH-GHOSTTY>
Hi there'
```
This is what you get in the console:
```json
{
"headers": [
{
"key": "received",
"value": "from smtp.example.com (127.0.0.1) by cloudflare-email.com (unknown) id 4fwwffRXOpyR for ; Tue, 27 Aug 2024 15:50:20 +0000"
},
{ "key": "from", "value": "\"John\" " },
{ "key": "reply-to", "value": "sender@example.com" },
{ "key": "to", "value": "recipient@example.com" },
{ "key": "subject", "value": "Testing Email Workers Local Dev" },
{ "key": "content-type", "value": "text/html; charset=\"windows-1252\"" },
{ "key": "x-mailer", "value": "Curl" },
{ "key": "date", "value": "Tue, 27 Aug 2024 08:49:44 -0700" },
{
"key": "message-id",
"value": "<6114391943504294873000@ZSH-GHOSTTY>"
}
],
"from": { "address": "sender@example.com", "name": "John" },
"to": [{ "address": "recipient@example.com", "name": "" }],
"replyTo": [{ "address": "sender@example.com", "name": "" }],
"subject": "Testing Email Workers Local Dev",
"messageId": "<6114391943504294873000@ZSH-GHOSTTY>",
"date": "2024-08-27T15:49:44.000Z",
"html": "Hi there\n",
"attachments": []
}
```
Local development is a critical part of the development flow, and also works for sending, replying and forwarding emails. See [our documentation](https://developers.cloudflare.com/email-routing/email-workers/local-development/) for more information.
---
title: Improved support for Node.js Crypto and TLS APIs in Workers · Changelog
description: Node.js APIs from the node:crypto and node:tls modules are now
available when using nodejs_compat.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-nodejs-crypto-and-tls/
md: https://developers.cloudflare.com/changelog/2025-04-08-nodejs-crypto-and-tls/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved support for Node.js Crypto and TLS APIs in Workers
Apr 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
When using a Worker with the [`nodejs_compat`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/) compatibility flag enabled, the following Node.js APIs are now available:
* [`node:crypto`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/crypto/)
* [`node:tls`](https://developers.cloudflare.com/workers/runtime-apis/nodejs/tls/)
This make it easier to reuse existing Node.js code in Workers or use npm packages that depend on these APIs.
#### node:crypto
The full [`node:crypto`](https://nodejs.org/api/crypto.html) API is now available in Workers.
You can use it to verify and sign data:
```js
import { sign, verify } from "node:crypto";
const signature = sign("sha256", "-data to sign-", env.PRIVATE_KEY);
const verified = verify("sha256", "-data to sign-", env.PUBLIC_KEY, signature);
```
Or, to encrypt and decrypt data:
```js
import { publicEncrypt, privateDecrypt } from "node:crypto";
const encrypted = publicEncrypt(env.PUBLIC_KEY, "some data");
const plaintext = privateDecrypt(env.PRIVATE_KEY, encrypted);
```
See the [`node:crypto` documentation](https://developers.cloudflare.com/workers/runtime-apis/nodejs/crypto/) for more information.
#### node:tls
The following APIs from `node:tls` are now available:
* [`connect`](https://nodejs.org/api/tls.html#tlsconnectoptions-callback)
* [`TLSSocket`](https://nodejs.org/api/tls.html#class-tlstlssocket)
* [`checkServerIdentity`](https://nodejs.org/api/tls.html#tlscheckserveridentityhostname-cert)
* [`createSecureContext`](https://nodejs.org/api/tls.html#tlscreatesecurecontextoptions)
This enables secure connections over TLS (Transport Layer Security) to external services.
```js
import { connect } from "node:tls";
// ... in a request handler ...
const connectionOptions = { key: env.KEY, cert: env.CERT };
const socket = connect(url, connectionOptions, () => {
if (socket.authorized) {
console.log("Connection authorized");
}
});
socket.on("data", (data) => {
console.log(data);
});
socket.on("end", () => {
console.log("server ends connection");
});
```
See the [`node:tls` documentation](https://developers.cloudflare.com/workers/runtime-apis/nodejs/tls/) for more information.
---
title: The Cloudflare Vite plugin is now Generally Available · Changelog
description: Cloudflare Vite Plugin 1.0 is out now — with official support for
Vite 6, React Router v7, and the full Developer Platform. Now you can run
Vite’s dev server locally, while executing your code directly in the Workers
runtime!
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-vite-plugin/
md: https://developers.cloudflare.com/changelog/2025-04-08-vite-plugin/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## The Cloudflare Vite plugin is now Generally Available
Apr 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
The [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/) has [reached v1.0](https://blog.cloudflare.com/introducing-the-cloudflare-vite-plugin) and is now Generally Available ("GA").
When you use `@cloudflare/vite-plugin`, you can use Vite's local development server and build tooling, while ensuring that while developing, your code runs in [`workerd`](https://github.com/cloudflare/workerd), the open-source Workers runtime.
This lets you get the best of both worlds for a full-stack app — you can use [Hot Module Replacement](https://vite.dev/guide/features.html#hot-module-replacement) from Vite right alongside [Durable Objects](https://developers.cloudflare.com/durable-objects/) and other runtime APIs and bindings that are unique to Cloudflare Workers.
`@cloudflare/vite-plugin` is made possible by the new [environment API](https://vite.dev/guide/api-environment) in Vite, and was built [in partnership with the Vite team](https://blog.cloudflare.com/introducing-the-cloudflare-vite-plugin).
#### Framework support
You can build any type of application with `@cloudflare/vite-plugin`, using any rendering mode, from single page applications (SPA) and static sites to server-side rendered (SSR) pages and API routes.
[React Router v7 (Remix)](https://developers.cloudflare.com/workers/framework-guides/web-apps/react-router/) is the first full-stack framework to provide full support for Cloudflare Vite plugin, allowing you to use all parts of Cloudflare's developer platform, without additional build steps.
You can also build complete full-stack apps on Workers **without a framework** — ["just use Vite"](https://blog.cloudflare.com/introducing-the-cloudflare-vite-plugin) and React together, and build a back-end API in the same Worker. Follow our [React SPA with an API tutorial](https://developers.cloudflare.com/workers/vite-plugin/tutorial/) to learn how.
#### Configuration
If you're already using [Vite](https://vite.dev/) in your build and development toolchain, you can start using our plugin with minimal changes to your `vite.config.ts`:
```ts
import { defineConfig } from "vite";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [cloudflare()],
});
```
Take a look at the [documentation for our Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/) for more information!
---
title: WARP client for macOS (version 2025.2.664.0) · Changelog
description: WARP client for macOS (version 2025.2.664.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-04-08-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.2.664.0)
Apr 08, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for captive portal detection and PF state tables for the 2025.2.600.0 release.
**Changes and improvements**
* Fix to reduce the number of browser tabs opened during captive portal logins.
* Improvement to exclude local DNS traffic entries from PF state table to reduce risk of connectivity issues from exceeding table capacity.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
---
title: WARP client for Windows (version 2025.2.664.0) · Changelog
description: WARP client for Windows (version 2025.2.664.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-08-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-04-08-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.2.664.0)
Apr 08, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for captive portal detection for the 2025.2.600.0 release.
**Changes and improvements**
* Fix to reduce the number of browser tabs opened during captive portal logins.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Hyperdrive now supports custom TLS/SSL certificates · Changelog
description: You can now configure custom certificates for secure database
connections with Hyperdrive, including both server certificate verification
and client certificates
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-09-hyperdrive-custom-certificate-support/
md: https://developers.cloudflare.com/changelog/2025-04-09-hyperdrive-custom-certificate-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Hyperdrive now supports custom TLS/SSL certificates
Apr 09, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive now supports more SSL/TLS security options for your database connections:
* Configure Hyperdrive to verify server certificates with `verify-ca` or `verify-full` SSL modes and protect against man-in-the-middle attacks
* Configure Hyperdrive to provide client certificates to the database server to authenticate itself (mTLS) for stronger security beyond username and password
Use the new `wrangler cert` commands to create certificate authority (CA) certificate bundles or client certificate pairs:
```bash
# Create CA certificate bundle
npx wrangler cert upload certificate-authority --ca-cert your-ca-cert.pem --name your-custom-ca-name
# Create client certificate pair
npx wrangler cert upload mtls-certificate --cert client-cert.pem --key client-key.pem --name your-client-cert-name
```
Then create a Hyperdrive configuration with the certificates and desired SSL mode:
```bash
npx wrangler hyperdrive create your-hyperdrive-config \
--connection-string="postgres://user:password@hostname:port/database" \
--ca-certificate-id \
--mtls-certificate-id
--sslmode verify-full
```
Learn more about [configuring SSL/TLS certificates for Hyperdrive](https://developers.cloudflare.com/hyperdrive/configuration/tls-ssl-certificates-for-hyperdrive/) to enhance your database security posture.
---
title: Investigate your Workers with the Query Builder in the new Observability
dashboard · Changelog
description: Workers Observability now offers a Query Builder to help developers
construct structured queries to investigate their telemtry data.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-09-qb-workers-logs-ga/
md: https://developers.cloudflare.com/changelog/2025-04-09-qb-workers-logs-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Investigate your Workers with the Query Builder in the new Observability dashboard
Apr 09, 2025
[Workers](https://developers.cloudflare.com/workers/)
The [Workers Observability dashboard](https://dash.cloudflare.com/?to=/:account/workers-and-pages/observability/) offers a single place to investigate and explore your [Workers Logs](https://developers.cloudflare.com/workers/observability/logs/workers-logs).
The **Overview** tab shows logs from all your Workers in one place. The **Invocations** view groups logs together by invocation, which refers to the specific trigger that started the execution of the Worker (i.e. fetch). The **Events** view shows logs in the order they were produced, based on timestamp. Previously, you could only view logs for a single Worker.
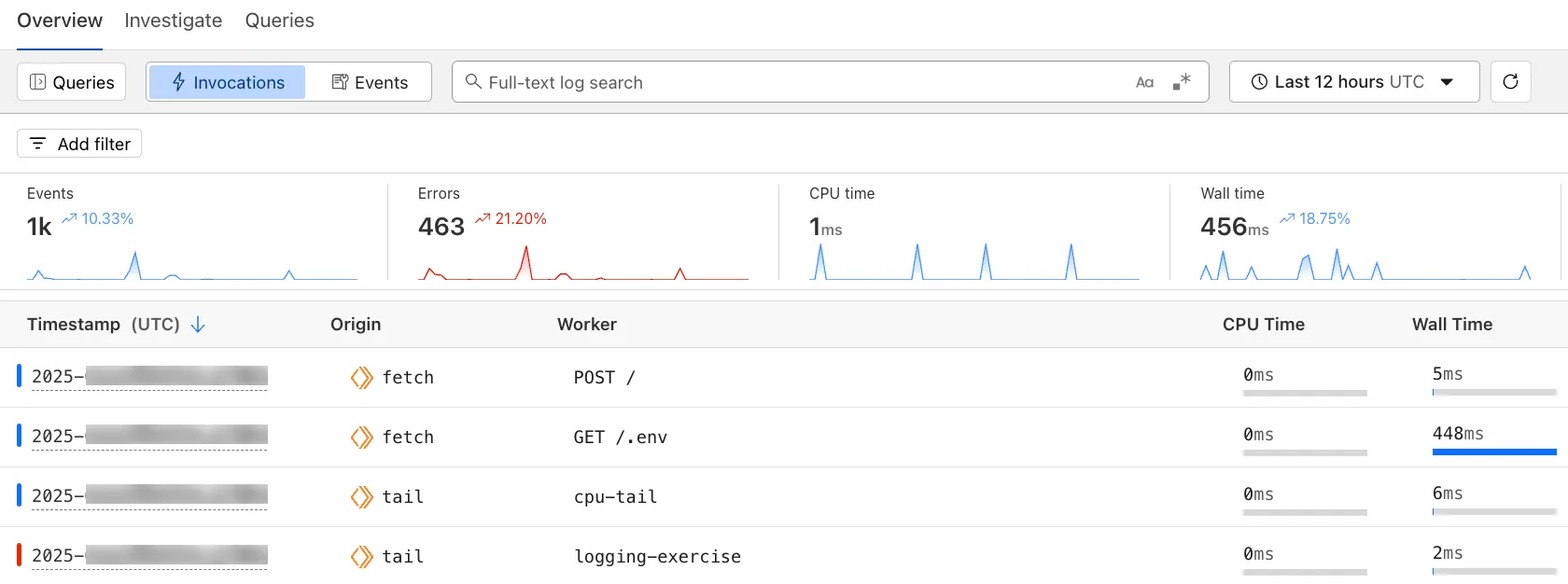
The **Investigate** tab presents a Query Builder, which helps you write structured queries to investigate and visualize your logs. The Query Builder can help answer questions such as:
* Which paths are experiencing the most 5XX errors?
* What is the wall time distribution by status code for my Worker?
* What are the slowest requests, and where are they coming from?
* Who are my top N users?
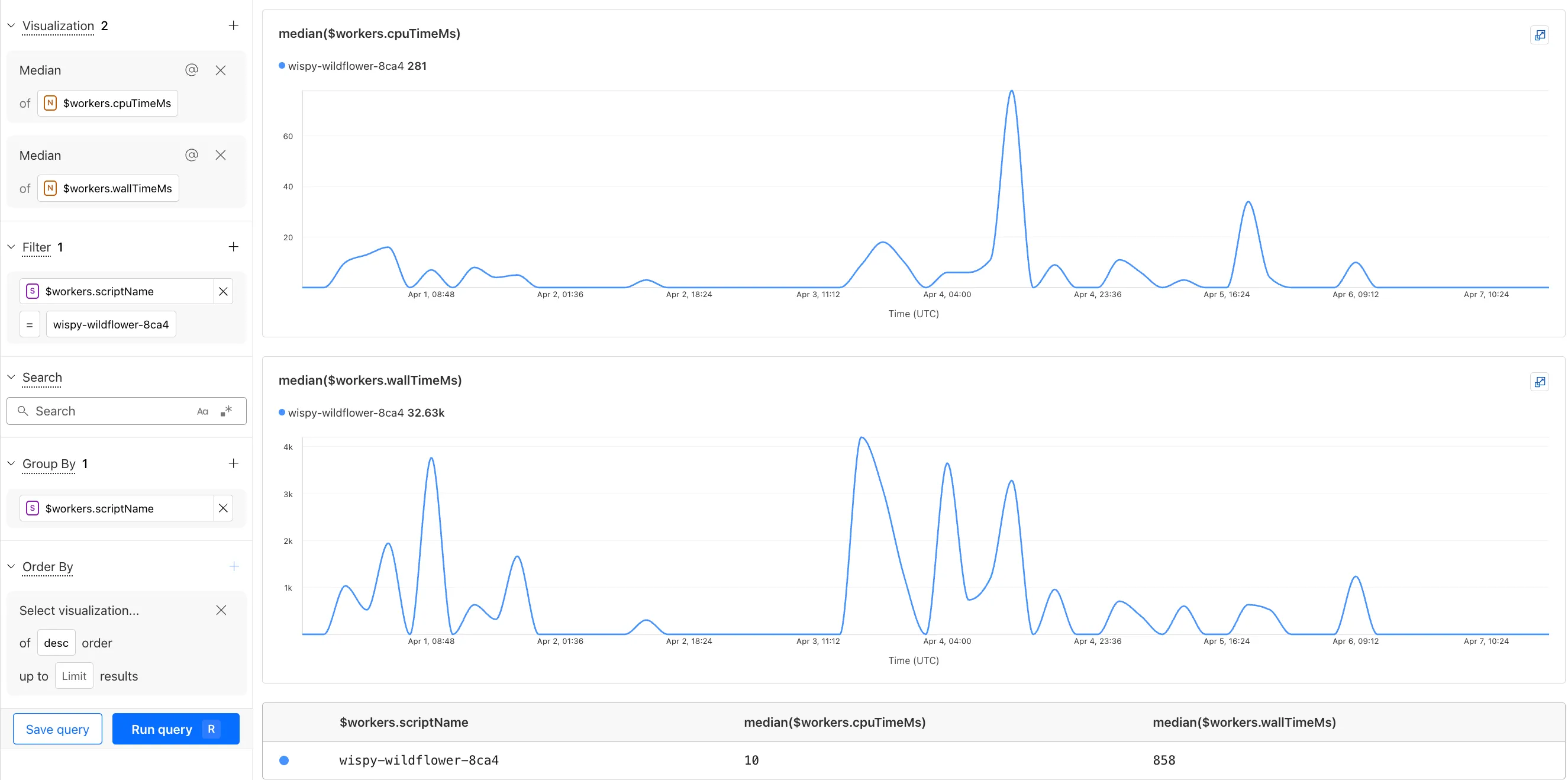
The Query Builder can use any field that you store in your logs as a key to visualize, filter, and group by. Use the Query Builder to quickly access your data, build visualizations, save queries, and share them with your team.
#### Workers Logs is now Generally Available
[Workers Logs](https://developers.cloudflare.com/workers/observability/logs/workers-logs) is now Generally Available. With a [small change](https://developers.cloudflare.com/workers/observability/logs/workers-logs/#enable-workers-logs) to your Wrangler configuration, Workers Logs ingests, indexes, and stores all logs emitted from your Workers for up to 7 days.
We've introduced a number of changes during our beta period, including:
* Dashboard enhancements with customizable fields as columns in the Logs view and support for invocation-based grouping
* Performance improvements to ensure no adverse impact
* Public [API endpoints](https://developers.cloudflare.com/api/resources/workers/subresources/observability/) for broader consumption
The API documents three endpoints: list the keys in the telemetry dataset, run a query, and list the unique values for a key. For more, visit our [REST API documentation](https://developers.cloudflare.com/api/resources/workers/subresources/observability/).
Visit the [docs](https://developers.cloudflare.com/workers/observability/query-builder) to learn more about the capabilities and methods exposed by the Query Builder. Start using Workers Logs and the Query Builder today by enabling observability for your Workers:
* wrangler.jsonc
```jsonc
{
"observability": {
"enabled": true,
"logs": {
"invocation_logs": true,
"head_sampling_rate": 1 // optional. default = 1.
}
}
}
```
* wrangler.toml
```toml
[observability]
enabled = true
[observability.logs]
invocation_logs = true
head_sampling_rate = 1
```
---
title: Cloudflare Zero Trust SCIM User and Group Provisioning Logs · Changelog
description: View all user and group updates, creation and deletion events made
via SCIM across all of your IdP instances in one place
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-09-scim-provisioning-logs/
md: https://developers.cloudflare.com/changelog/2025-04-09-scim-provisioning-logs/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Zero Trust SCIM User and Group Provisioning Logs
Apr 09, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Cloudflare Zero Trust SCIM provisioning](https://developers.cloudflare.com/cloudflare-one/team-and-resources/users/scim) now has a full audit log of all create, update and delete event from any SCIM Enabled IdP. The [SCIM logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/scim-logs/) support filtering by IdP, Event type, Result and many more fields. This will help with debugging user and group update issues and questions.
SCIM logs can be found on the Zero Trust Dashboard under **Logs** -> **SCIM provisioning**.

---
title: Cloudflare Secrets Store now available in Beta · Changelog
description: Manage account level Workers secrets via Cloudflare Secrets Store (beta)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-09-secrets-store-beta/
md: https://developers.cloudflare.com/changelog/2025-04-09-secrets-store-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Secrets Store now available in Beta
Apr 09, 2025
[Secrets Store ](https://developers.cloudflare.com/secrets-store/)[SSL/TLS](https://developers.cloudflare.com/ssl/)
Cloudflare Secrets Store is available today in Beta. You can now store, manage, and deploy account level secrets from a secure, centralized platform to your Workers.

To spin up your Cloudflare Secrets Store, simply click the new Secrets Store tab [in the dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store) or use this Wrangler command:
```sh
wrangler secrets-store store create --remote
```
The following are supported in the Secrets Store beta:
* Secrets Store UI & API: create your store & create, duplicate, update, scope, and delete a secret
* Workers UI: bind a new or existing account level secret to a Worker and deploy in code
* Wrangler: create your store & create, duplicate, update, scope, and delete a secret
* Account Management UI & API: assign Secrets Store permissions roles & view audit logs for actions taken in Secrets Store core platform
For instructions on how to get started, visit our [developer documentation](https://developers.cloudflare.com/secrets-store/).
---
title: Cloudflare Snippets are now Generally Available · Changelog
description: Snippets let you program HTTP traffic with lightweight JavaScript —
now GA and ready for production.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-09-snippets-ga/
md: https://developers.cloudflare.com/changelog/2025-04-09-snippets-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Snippets are now Generally Available
Apr 09, 2025
[Rules](https://developers.cloudflare.com/rules/)

[Cloudflare Snippets](https://developers.cloudflare.com/rules/snippets/) are now generally available at no extra cost across all paid plans — giving you a fast, flexible way to programmatically control HTTP traffic using lightweight JavaScript.
You can now use Snippets to modify HTTP requests and responses with confidence, reliability, and scale. Snippets are production-ready and deeply integrated with Cloudflare Rules, making them ideal for everything from quick dynamic header rewrites to advanced routing logic.
What's new:
* **Snippets are now GA** – Available at no extra cost on all Pro, Business, and Enterprise plans.
* **Ready for production** – Snippets deliver a production-grade experience built for scale.
* **Part of the Cloudflare Rules platform** – Snippets inherit request modifications from other Cloudflare products and support sequential execution, allowing you to run multiple Snippets on the same request and apply custom modifications step by step.
* **Trace integration** – Use [Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/) to see which Snippets were triggered on a request — helping you understand traffic flow and debug more effectively.
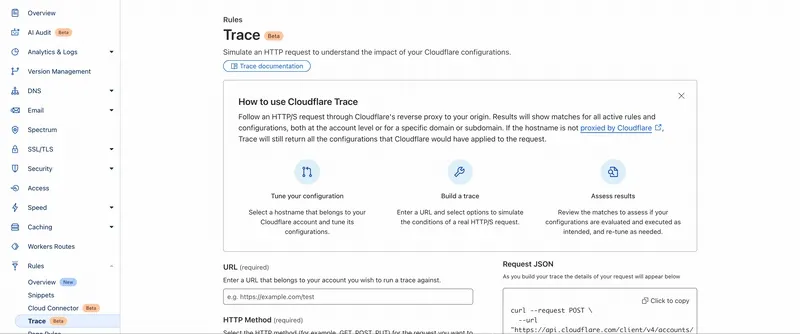
Learn more in the [launch blog post](https://blog.cloudflare.com/snippets/).
---
title: CPU time and Wall time now published for Workers Invocations · Changelog
description: Workers Observability tooling now shows CPU time and Wall time for
a Workers Invocation.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-09-workers-timing/
md: https://developers.cloudflare.com/changelog/2025-04-09-workers-timing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## CPU time and Wall time now published for Workers Invocations
Apr 09, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now observe and investigate the CPU time and Wall time for every Workers Invocations.
* For [Workers Logs](https://developers.cloudflare.com/workers/observability/logs/workers-logs), CPU time and Wall time are surfaced in the [Invocation Log](https://developers.cloudflare.com/workers/observability/logs/workers-logs/#invocation-logs)..
* For [Tail Workers](https://developers.cloudflare.com/workers/observability/logs/tail-workers), CPU time and Wall time are surfaced at the top level of the [Workers Trace Events object](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/workers_trace_events).
* For [Workers Logpush](https://developers.cloudflare.com/workers/observability/logs/logpush), CPU and Wall time are surfaced at the top level of the [Workers Trace Events object](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/workers_trace_events). All new jobs will have these new fields included by default. Existing jobs need to be updated to include CPU time and Wall time.
You can use a Workers Logs filter to search for logs where Wall time exceeds 100ms.

You can also use the Workers Observability [Query Builder](https://dash.cloudflare.com/?to=/:account/workers-and-pages/observability/investigate) to find the median CPU time and median Wall time for all of your Workers.

---
title: D1 Read Replication Public Beta · Changelog
description: Use D1 Sessions API to leverage read replication.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-10-d1-read-replication-beta/
md: https://developers.cloudflare.com/changelog/2025-04-10-d1-read-replication-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## D1 Read Replication Public Beta
Apr 10, 2025
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
D1 read replication is available in public beta to help lower average latency and increase overall throughput for read-heavy applications like e-commerce websites or content management tools.
Workers can leverage read-only database copies, called read replicas, by using D1 [Sessions API](https://developers.cloudflare.com/d1/best-practices/read-replication). A session encapsulates all the queries from one logical session for your application. For example, a session may correspond to all queries coming from a particular web browser session. With Sessions API, D1 queries in a session are guaranteed to be [sequentially consistent](https://developers.cloudflare.com/d1/best-practices/read-replication/#replica-lag-and-consistency-model) to avoid data consistency pitfalls. D1 [bookmarks](https://developers.cloudflare.com/d1/reference/time-travel/#bookmarks) can be used from a previous session to ensure logical consistency between sessions.
```ts
// retrieve bookmark from previous session stored in HTTP header
const bookmark = request.headers.get("x-d1-bookmark") ?? "first-unconstrained";
const session = env.DB.withSession(bookmark);
const result = await session
.prepare(`SELECT * FROM Customers WHERE CompanyName = 'Bs Beverages'`)
.run();
// store bookmark for a future session
response.headers.set("x-d1-bookmark", session.getBookmark() ?? "");
```
Read replicas are automatically created by Cloudflare (currently one in each supported [D1 region](https://developers.cloudflare.com/d1/best-practices/read-replication/#read-replica-locations)), are active/inactive based on query traffic, and are transparently routed to by Cloudflare at no additional cost.
To checkout D1 read replication, deploy the following Worker code using Sessions API, which will prompt you to create a D1 database and enable read replication on said database.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/d1-starter-sessions-api)
To learn more about how read replication was implemented, go to our [blog post](https://blog.cloudflare.com/d1-read-replication-beta).
---
title: Read multiple keys from Workers KV with bulk reads · Changelog
description: You can now retrieve up to 100 keys in a single bulk read request
to Workers KV.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-10-kv-bulk-reads/
md: https://developers.cloudflare.com/changelog/2025-04-10-kv-bulk-reads/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Read multiple keys from Workers KV with bulk reads
Apr 17, 2025
[KV](https://developers.cloudflare.com/kv/)
You can now retrieve up to 100 keys in a single bulk read request made to Workers KV using the binding.
This makes it easier to request multiple KV pairs within a single Worker invocation. Retrieving many key-value pairs using the bulk read operation is more performant than making individual requests since bulk read operations are not affected by [Workers simultaneous connection limits](https://developers.cloudflare.com/workers/platform/limits/#simultaneous-open-connections).
```js
// Read single key
const key = "key-a";
const value = await env.NAMESPACE.get(key);
// Read multiple keys
const keys = ["key-a", "key-b", "key-c", ...] // up to 100 keys
const values : Map = await env.NAMESPACE.get(keys);
// Print the value of "key-a" to the console.
console.log(`The first key is ${values.get("key-a")}.`)
```
Consult the [Workers KV Read key-value pairs API](https://developers.cloudflare.com/kv/api/read-key-value-pairs/) for full details on Workers KV's new bulk reads support.
---
title: Cloudflare Pipelines now available in beta · Changelog
description: Use Cloudflare Pipelines to ingest real time data streams, and load into R2.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-10-launching-pipelines/
md: https://developers.cloudflare.com/changelog/2025-04-10-launching-pipelines/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Pipelines now available in beta
Apr 10, 2025
[Pipelines ](https://developers.cloudflare.com/pipelines/)[R2 ](https://developers.cloudflare.com/r2/)[Workers](https://developers.cloudflare.com/workers/)
[Cloudflare Pipelines](https://developers.cloudflare.com/pipelines) is now available in beta, to all users with a [Workers Paid](https://developers.cloudflare.com/workers/platform/pricing) plan.
Pipelines let you ingest high volumes of real time data, without managing the underlying infrastructure. A single pipeline can ingest up to 100 MB of data per second, via HTTP or from a [Worker](https://developers.cloudflare.com/workers). Ingested data is automatically batched, written to output files, and delivered to an [R2 bucket](https://developers.cloudflare.com/r2) in your account. You can use Pipelines to build a data lake of clickstream data, or to store events from a Worker.
Create your first pipeline with a single command:
```bash
$ npx wrangler@latest pipelines create my-clickstream-pipeline --r2-bucket my-bucket
🌀 Authorizing R2 bucket "my-bucket"
🌀 Creating pipeline named "my-clickstream-pipeline"
✅ Successfully created pipeline my-clickstream-pipeline
Id: 0e00c5ff09b34d018152af98d06f5a1xvc
Name: my-clickstream-pipeline
Sources:
HTTP:
Endpoint: https://0e00c5ff09b34d018152af98d06f5a1xvc.pipelines.cloudflare.com/
Authentication: off
Format: JSON
Worker:
Format: JSON
Destination:
Type: R2
Bucket: my-bucket
Format: newline-delimited JSON
Compression: GZIP
Batch hints:
Max bytes: 100 MB
Max duration: 300 seconds
Max records: 100,000
🎉 You can now send data to your pipeline!
Send data to your pipeline's HTTP endpoint:
curl "https://0e00c5ff09b34d018152af98d06f5a1xvc.pipelines.cloudflare.com/" -d '[{ ...JSON_DATA... }]'
To send data to your pipeline from a Worker, add the following configuration to your config file:
{
"pipelines": [
{
"pipeline": "my-clickstream-pipeline",
"binding": "PIPELINE"
}
]
}
```
Head over to our [getting started guide](https://developers.cloudflare.com/pipelines/getting-started) for an in-depth tutorial to building with Pipelines.
---
title: R2 Data Catalog is a managed Apache Iceberg data catalog built directly
into R2 buckets · Changelog
description: A managed Apache Iceberg data catalog built directly into R2 buckets
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-10-r2-data-catalog-beta/
md: https://developers.cloudflare.com/changelog/2025-04-10-r2-data-catalog-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## R2 Data Catalog is a managed Apache Iceberg data catalog built directly into R2 buckets
Apr 10, 2025
[R2](https://developers.cloudflare.com/r2/)
Today, we're launching [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) in open beta, a managed Apache Iceberg catalog built directly into your [Cloudflare R2](https://developers.cloudflare.com/r2/) bucket.
If you're not already familiar with it, [Apache Iceberg](https://iceberg.apache.org/) is an open table format designed to handle large-scale analytics datasets stored in object storage, offering ACID transactions and schema evolution. R2 Data Catalog exposes a standard Iceberg REST catalog interface, so you can connect engines like [Spark](https://developers.cloudflare.com/r2/data-catalog/config-examples/spark-scala/), [Snowflake](https://developers.cloudflare.com/r2/data-catalog/config-examples/snowflake/), and [PyIceberg](https://developers.cloudflare.com/r2/data-catalog/config-examples/pyiceberg/) to start querying your tables using the tools you already know.
To enable a data catalog on your R2 bucket, find **R2 Data Catalog** in your buckets settings in the dashboard, or run:
```bash
npx wrangler r2 bucket catalog enable my-bucket
```
And that's it. You'll get a catalog URI and warehouse you can plug into your favorite Iceberg engines.
Visit our [getting started guide](https://developers.cloudflare.com/r2/data-catalog/get-started/) for step-by-step instructions on enabling R2 Data Catalog, creating tables, and running your first queries.
---
title: HTTP redirect and custom block page redirect · Changelog
description: Redirect traffic with a Gateway HTTP Redirect policy, or with the
block page in an HTTP or DNS Block policy.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-11-http-redirect-custom-block-page-redirect/
md: https://developers.cloudflare.com/changelog/2025-04-11-http-redirect-custom-block-page-redirect/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## HTTP redirect and custom block page redirect
Apr 11, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
You can now use more flexible redirect capabilities in Cloudflare One with Gateway.
* A new **Redirect** action is available in the HTTP policy builder, allowing admins to redirect users to any URL when their request matches a policy. You can choose to preserve the original URL and query string, and optionally include policy context via query parameters.
* For **Block** actions, admins can now configure a custom URL to display when access is denied. This block page redirect is set at the account level and can be overridden in DNS or HTTP policies. Policy context can also be passed along in the URL.
Learn more in our documentation for [HTTP Redirect](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#redirect) and [Block page redirect](https://developers.cloudflare.com/cloudflare-one/reusable-components/custom-pages/gateway-block-page/#redirect-to-a-block-page).
---
title: Workers AI for Developer Week - faster inference, new models, async batch
API, expanded LoRA support · Changelog
description: Workers AI now has more models, faster inference, async batch API,
and expanded LoRA
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-11-new-models-faster-inference/
md: https://developers.cloudflare.com/changelog/2025-04-11-new-models-faster-inference/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers AI for Developer Week - faster inference, new models, async batch API, expanded LoRA support
Apr 11, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Happy Developer Week 2025! Workers AI is excited to announce a couple of new features and improvements available today. Check out our [blog](https://blog.cloudflare.com/workers-ai-improvements) for all the announcement details.
#### Faster inference + New models
We’re rolling out some in-place improvements to our models that can help speed up inference by 2-4x! Users of the models below will enjoy an automatic speed boost starting today:
* [`@cf/meta/llama-3.3-70b-instruct-fp8-fast`](https://developers.cloudflare.com/workers-ai/models/llama-3.3-70b-instruct-fp8-fast/) gets a speed boost of 2-4x, leveraging techniques like speculative decoding, prefix caching, and an updated inference backend.
* [`@cf/baai/bge-small-en-v1.5`](https://developers.cloudflare.com/workers-ai/models/bge-small-en-v1.5/), [`@cf/baai/bge-base-en-v1.5`](https://developers.cloudflare.com/workers-ai/models/bge-base-en-v1.5/), [`@cf/baai/bge-large-en-v1.5`](https://developers.cloudflare.com/workers-ai/models/bge-large-en-v1.5/) get an updated back end, which should improve inference times by 2x.
* With the `bge` models, we’re also announcing a new parameter called `pooling` which can take `cls` or `mean` as options. We highly recommend using `pooling: cls` which will help generate more accurate embeddings. However, embeddings generated with cls pooling are not backwards compatible with mean pooling. For this to not be a breaking change, the default remains as mean pooling. Please specify `pooling: cls` to enjoy more accurate embeddings going forward.
We’re also excited to launch a few new models in our catalog to help round out your experience with Workers AI. We’ll be deprecating some older models in the future, so stay tuned for a deprecation announcement. Today’s new models include:
* [`@cf/mistralai/mistral-small-3.1-24b-instruct`](https://developers.cloudflare.com/workers-ai/models/mistral-small-3.1-24b-instruct/): a 24B parameter model achieving state-of-the-art capabilities comparable to larger models, with support for vision and tool calling.
* [`@cf/google/gemma-3-12b-it`](https://developers.cloudflare.com/workers-ai/models/gemma-3-12b-it/): well-suited for a variety of text generation and image understanding tasks, including question answering, summarization and reasoning, with a 128K context window, and multilingual support in over 140 languages.
* [`@cf/qwen/qwq-32b`](https://developers.cloudflare.com/workers-ai/models/qwq-32b/): a medium-sized reasoning model, which is capable of achieving competitive performance against state-of-the-art reasoning models, e.g., DeepSeek-R1, o1-mini.
* [`@cf/qwen/qwen2.5-coder-32b-instruct`](https://developers.cloudflare.com/workers-ai/models/qwen2.5-coder-32b-instruct/): the current state-of-the-art open-source code LLM, with its coding abilities matching those of GPT-4o.
#### Batch Inference
Introducing a new batch inference feature that allows you to send us an array of requests, which we will fulfill as fast as possible and send them back as an array. This is really helpful for large workloads such as summarization, embeddings, etc. where you don’t have a human-in-the-loop. Using the batch API will guarantee that your requests are fulfilled eventually, rather than erroring out if we don’t have enough capacity at a given time.
Check out the [tutorial](https://developers.cloudflare.com/workers-ai/features/batch-api/) to get started! Models that support batch inference today include:
* [`@cf/meta/llama-3.3-70b-instruct-fp8-fast`](https://developers.cloudflare.com/workers-ai/models/llama-3.3-70b-instruct-fp8-fast/)
* [`@cf/baai/bge-small-en-v1.5`](https://developers.cloudflare.com/workers-ai/models/bge-small-en-v1.5/)
* [`@cf/baai/bge-base-en-v1.5`](https://developers.cloudflare.com/workers-ai/models/bge-base-en-v1.5/)
* [`@cf/baai/bge-large-en-v1.5`](https://developers.cloudflare.com/workers-ai/models/bge-large-en-v1.5/)
* [`@cf/baai/bge-m3`](https://developers.cloudflare.com/workers-ai/models/bge-m3/)
* [`@cf/meta/m2m100-1.2b`](https://developers.cloudflare.com/workers-ai/models/m2m100-1.2b/)
#### Expanded LoRA support
We’ve upgraded our LoRA experience to include 8 newer models, and can support ranks of up to 32 with a 300MB safetensors file limit (previously limited to rank of 8 and 100MB safetensors) Check out our [LoRAs page](https://developers.cloudflare.com/workers-ai/features/fine-tunes/loras/) to get started. Models that support LoRAs now include:
* [`@cf/meta/llama-3.2-11b-vision-instruct`](https://developers.cloudflare.com/workers-ai/models/llama-3.2-11b-vision-instruct/)
* [`@cf/meta/llama-3.3-70b-instruct-fp8-fast`](https://developers.cloudflare.com/workers-ai/models/llama-3.3-70b-instruct-fp8-fast/)
* [`@cf/meta/llama-guard-3-8b`](https://developers.cloudflare.com/workers-ai/models/llama-guard-3-8b/)
* [`@cf/meta/llama-3.1-8b-instruct-fast`](https://developers.cloudflare.com/workers-ai/models/llama-3.1-8b-instruct-fast/) (coming soon)
* [`@cf/deepseek-ai/deepseek-r1-distill-qwen-32b`](https://developers.cloudflare.com/workers-ai/models/deepseek-r1-distill-qwen-32b/) (coming soon)
* [`@cf/qwen/qwen2.5-coder-32b-instruct`](https://developers.cloudflare.com/workers-ai/models/qwen2.5-coder-32b-instruct/)
* [`@cf/qwen/qwq-32b`](https://developers.cloudflare.com/workers-ai/models/qwq-32b/)
* [`@cf/mistralai/mistral-small-3.1-24b-instruct`](https://developers.cloudflare.com/workers-ai/models/mistral-small-3.1-24b-instruct/)
* [`@cf/google/gemma-3-12b-it`](https://developers.cloudflare.com/workers-ai/models/gemma-3-12b-it/)
---
title: New predefined detection entry for ICD-11 · Changelog
description: ICD-11 is now available for DLP detections.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-14-icd11-support/
md: https://developers.cloudflare.com/changelog/2025-04-14-icd11-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New predefined detection entry for ICD-11
Apr 14, 2025
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You now have access to the World Health Organization (WHO) 2025 edition of the [International Classification of Diseases 11th Revision (ICD-11)](https://www.who.int/news/item/14-02-2025-who-releases-2025-update-to-the-international-classification-of-diseases-%28icd-11%29) as a predefined detection entry. The new dataset can be found in the [Health Information](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/predefined-profiles/#health-information) predefined profile.
ICD-10 dataset remains available for use.
---
title: WAF Release - 2025-04-14 · Changelog
description: Cloudflare WAF managed rulesets 2025-04-14 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-14-waf-release/
md: https://developers.cloudflare.com/changelog/2025-04-14-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-04-14
Apr 14, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 9209bb65527f4c088bca5ffad6b2d36c | 100739A | Next.js - Auth Bypass - CVE:CVE-2025-29927 - 2 | Log | Disabled | This is a New Detection |
---
title: Signed URLs and Infrastructure Improvements on Stream Live WebRTC Beta ·
Changelog
description: >
Dynamically optimize, clip, and resize video from any origin, no storage
migration needed.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-14-webrtc-beta-signed-urls/
md: https://developers.cloudflare.com/changelog/2025-04-14-webrtc-beta-signed-urls/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Signed URLs and Infrastructure Improvements on Stream Live WebRTC Beta
Apr 11, 2025
[Stream](https://developers.cloudflare.com/stream/)
Cloudflare [Stream](https://developers.cloudflare.com/stream/) has completed an infrastructure upgrade for our [Live WebRTC beta](https://developers.cloudflare.com/stream/webrtc-beta/) support which brings increased scalability and improved playback performance to all customers. WebRTC allows broadcasting directly from a browser (or supported WHIP client) with ultra-low latency to tens of thousands of concurrent viewers across the globe.
Additionally, as part of this upgrade, the WebRTC beta now supports Signed URLs to protect playback, just like our standard live stream options (HLS/DASH).
For more information, learn about the [Stream Live WebRTC beta](https://developers.cloudflare.com/stream/webrtc-beta/).
---
title: Fixed and documented Workers Routes and Secrets API · Changelog
description: The Workers Routes API now returns a correct response and the
Secrets API has been added to the Cloudflare API docs.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-15-workers-api-fixes/
md: https://developers.cloudflare.com/changelog/2025-04-15-workers-api-fixes/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Fixed and documented Workers Routes and Secrets API
Apr 15, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
#### Workers Routes API
Previously, a request to the Workers [Create Route API](https://developers.cloudflare.com/api/resources/workers/subresources/routes/methods/create/) always returned `null` for "script" and an empty string for "pattern" even if the request was successful.
```bash
curl https://api.cloudflare.com/client/v4/zones/$CF_ACCOUNT_ID/workers/routes \
-X PUT \
-H "Authorization: Bearer $CF_API_TOKEN" \
-H 'Content-Type: application/json' \
--data '{ "pattern": "example.com/*", "script": "hello-world-script" }'
```
```json
{
"result": {
"id": "bf153a27ba2b464bb9f04dcf75de1ef9",
"pattern": "",
"script": null,
"request_limit_fail_open": false
},
"success": true,
"errors": [],
"messages": []
}
```
Now, it properly returns all values!
```json
{
"result": {
"id": "bf153a27ba2b464bb9f04dcf75de1ef9",
"pattern": "example.com/*",
"script": "hello-world-script",
"request_limit_fail_open": false
},
"success": true,
"errors": [],
"messages": []
}
```
#### Workers Secrets API
The [Workers](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/subresources/secrets/) and [Workers for Platforms](https://developers.cloudflare.com/api/resources/workers_for_platforms/subresources/dispatch/subresources/namespaces/subresources/scripts/subresources/secrets/) secrets APIs are now properly documented in the Cloudflare OpenAPI docs. Previously, these endpoints were not publicly documented, leaving users confused on how to directly manage their secrets via the API. Now, you can find the proper endpoints in our public documentation, as well as in our API Library SDKs such as [cloudflare-typescript](https://github.com/cloudflare/cloudflare-typescript) (>4.2.0) and [cloudflare-python](https://github.com/cloudflare/cloudflare-python) (>4.1.0).
Note the `cloudflare_workers_secret` and `cloudflare_workers_for_platforms_script_secret` [Terraform resources](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs) are being removed in a future release. This resource is not recommended for managing secrets. Users should instead use the:
* [Secrets Store](https://developers.cloudflare.com/api/resources/secrets_store/) with the "Secrets Store Secret" binding on Workers and Workers for Platforms Script Upload
* "Secret Text" Binding on [Workers Script Upload](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/methods/update/) and [Workers for Platforms Script Upload](https://developers.cloudflare.com/api/resources/workers_for_platforms/subresources/dispatch/subresources/namespaces/subresources/scripts/methods/update/)
* Workers (and WFP) Secrets API
---
title: Increased limits for Queues pull consumers · Changelog
description: Queues now supports consuming up to 5,000 messages per second per
queue over HTTP.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-17-pull-consumer-limits/
md: https://developers.cloudflare.com/changelog/2025-04-17-pull-consumer-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased limits for Queues pull consumers
Apr 17, 2025
[Queues](https://developers.cloudflare.com/queues/)
[Queues pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/) can now pull and acknowledge up to **5,000 messages / second per queue**. Previously, pull consumers were rate limited to 1,200 requests / 5 minutes, aggregated across all queues.
Pull consumers allow you to consume messages over HTTP from any environment—including outside of [Cloudflare Workers](https://developers.cloudflare.com/workers). They’re also useful when you need fine-grained control over how quickly messages are consumed.
To setup a new queue with a pull based consumer using [Wrangler](https://developers.cloudflare.com/workers/wrangler/), run:
```sh
npx wrangler queues create my-queue
npx wrangler queues consumer http add my-queue
```
You can also configure a pull consumer using the [REST API](https://developers.cloudflare.com/api/resources/queues/subresources/consumers/methods/create/) or the Queues dashboard.
Once configured, you can pull messages from the queue using any HTTP client. You'll need a [Cloudflare API Token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with `queues_read` and `queues_write` permissions. For example:
```bash
curl "https://api.cloudflare.com/client/v4/accounts/${CF_ACCOUNT_ID}/queues/${QUEUE_ID}/messages/pull" \
--header "Authorization: Bearer ${API_TOKEN}" \
--header "Content-Type: application/json" \
--data '{ "visibility_timeout": 10000, "batch_size": 2 }'
```
To learn more about how to acknowledge messages, pull batches at once, and setup multiple consumers, refer to the [pull consumer documentation](https://developers.cloudflare.com/queues/configuration/pull-consumers).
As always, Queues doesn't charge for data egress. Pull operations continue to be billed at the [existing rate](https://developers.cloudflare.com/queues/platform/pricing), of $0.40 / million operations. The increased limits are available now, on all new and existing queues. If you're new to Queues, [get started with the Cloudflare Queues guide](https://developers.cloudflare.com/queues/get-started).
---
title: Custom fields raw and transformed values support · Changelog
description: Configure request header and response headers values can log eiterh
raw or transformed value
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-18-custom-fields-raw-transformed-values/
md: https://developers.cloudflare.com/changelog/2025-04-18-custom-fields-raw-transformed-values/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Custom fields raw and transformed values support
Apr 18, 2025
[Logs](https://developers.cloudflare.com/logs/)
Custom Fields now support logging both **raw and transformed values** for request and response headers in the HTTP requests dataset.
These fields are configured per zone and apply to all Logpush jobs in that zone that include request headers, response headers. Each header can be logged in only one format—either raw or transformed—not both.
By default:
* Request headers are logged as raw values
* Response headers are logged as transformed values
These defaults can be overidden to suit your logging needs.
Note
Transformed and raw values for request and response headers are available **only via the API** and cannot be set through the UI.
For more information refer to [Custom fields](https://developers.cloudflare.com/logs/logpush/logpush-job/custom-fields/) documentation
---
title: Access bulk policy tester · Changelog
description: Test and simulate Access policies before deploying them to
production. The Access bulk policy tester allows you to test your policies
against your entire user population before and after deploying them.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-21-access-bulk-policy-tester/
md: https://developers.cloudflare.com/changelog/2025-04-21-access-bulk-policy-tester/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Access bulk policy tester
Apr 21, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
The [Access bulk policy tester](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/policy-management/#test-all-policies-in-an-application) is now available in the Cloudflare Zero Trust dashboard. The bulk policy tester allows you to simulate Access policies against your entire user base before and after deploying any changes. The policy tester will simulate the configured policy against each user's last seen identity and device posture (if applicable).

---
title: Cron triggers are now supported in Python Workers · Changelog
description: You can now set up scheduled handlers in your Python Workers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-22-python-worker-cron-triggers/
md: https://developers.cloudflare.com/changelog/2025-04-22-python-worker-cron-triggers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cron triggers are now supported in Python Workers
Apr 24, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now create Python Workers which are executed via a cron trigger.
This is similar to how it's done in JavaScript Workers, simply define a scheduled event listener in your Worker:
```python
from workers import handler
@handler
async def on_scheduled(event, env, ctx):
print("cron processed")
```
Define a cron trigger configuration in your Wrangler configuration file:
* wrangler.jsonc
```jsonc
{
"triggers": {
// Schedule cron triggers:
// - At every 3rd minute
// - At 15:00 (UTC) on first day of the month
// - At 23:59 (UTC) on the last weekday of the month
"crons": [
"*/3 * * * *",
"0 15 1 * *",
"59 23 LW * *"
]
}
}
```
* wrangler.toml
```toml
[triggers]
crons = [ "*/3 * * * *", "0 15 1 * *", "59 23 LW * *" ]
```
Then test your new handler by using Wrangler with the `--test-scheduled` flag and making a request to `/cdn-cgi/handler/scheduled?cron=*+*+*+*+*`:
```sh
npx wrangler dev --test-scheduled
curl "http://localhost:8787/cdn-cgi/handler/scheduled?cron=*+*+*+*+*"
```
Consult the [Workers Cron Triggers page](https://developers.cloudflare.com/workers/configuration/cron-triggers/) for full details on cron triggers in Workers.
---
title: WAF Release - 2025-04-22 · Changelog
description: Cloudflare WAF managed rulesets 2025-04-22 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-22-waf-release/
md: https://developers.cloudflare.com/changelog/2025-04-22-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-04-22
Apr 22, 2025
[WAF](https://developers.cloudflare.com/waf/)
Each of this week's rule releases covers a distinct CVE, with half of the rules targeting Remote Code Execution (RCE) attacks. Of the 6 CVEs covered, four were scored as critical, with the other two scored as high.
When deciding which exploits to tackle, Cloudflare tunes into the attackers' areas of focus. Cloudflare's network intelligence provides a unique lens into attacker activity – for instance, through the volume of blocked requests related with CVE exploits after updating WAF Managed Rules with new detections.
From this week's releases, one indicator that RCE is a "hot topic" attack type is the fact that the Oracle PeopleSoft RCE rule accounts for half of all of the new rule matches. This rule patches CVE-2023-22047, a high-severity vulnerability in the Oracle PeopleSoft suite that allows unauthenticated attackers to access PeopleSoft Enterprise PeopleTools data through remote code execution. This is particularly concerning because of the nature of the data managed by PeopleSoft – this can include payroll records or student profile information. This CVE, along with five others, are addressed with the latest detection update to WAF Managed Rules.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | faa032d9825e4844a1188f3ba5be3327 | 100738 | GitLab - Auth Bypass - CVE:CVE-2023-7028 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 2e96b6d5cdd94f7782b90e266c9531fa | 100740 | Splunk Enterprise - Remote Code Execution - CVE:CVE-2025-20229 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5c9c095bc1e5411195edb893f40bbc2b | 100741 | Oracle PeopleSoft - Remote Code Execution - CVE:CVE-2023-22047 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 1d7a3932296c42fd827055335462167c | 100742 | CrushFTP - Auth Bypass - CVE:CVE-2025-31161 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5eb7ed601e6844828b9bdb05caa7b208 | 100743 | Ivanti - Buffer Error - CVE:CVE-2025-22457 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 410317f1e32b41859fa3214dd52139a8 | 100744 | Oracle Access Manager - Remote Code Execution - CVE:CVE-2021-35587 | Log | Disabled | This is a New Detection |
---
title: WARP client for macOS (version 2025.4.589.1) · Changelog
description: WARP client for macOS (version 2025.4.589.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-22-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-04-22-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.4.589.1)
Apr 22, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
**Changes and improvements**
* Fixed an issue where managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Improved captive portal detection.
* Added a TCP fallback for the MASQUE tunnel protocol to improve compatibility with networks on MASQUE.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Added a [Collect Captive Portal Diag](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/#get-captive-portal-logs) button in the client GUI to make it easier for users to collect captive portal debugging diagnostics.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
---
title: WARP client for Windows (version 2025.4.589.1) · Changelog
description: WARP client for Windows (version 2025.4.589.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-22-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-04-22-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.4.589.1)
Apr 22, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
**Changes and improvements**
* Fixed an issue causing reconnection loops when captive portals are detected.
* Fixed an issue that caused WARP client disk encryption posture checks to fail due to missing drive names.
* Fixed an issue where managed network policies could incorrectly report network location beacons as missing.
* Improved error reporting for DEX tests.
* Improved WARP client UI high contrast mode.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Added a TCP fallback for the MASQUE tunnel protocol to improve compatibility with networks on MASQUE.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Added a [Collect Captive Portal Diag](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/captive-portals/#get-captive-portal-logs) button in the client GUI to make it easier for users to collect captive portal debugging diagnostics.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Metadata filtering and multitenancy support in AutoRAG · Changelog
description: Add metadata filters to AutoRAG queries to enable multitenancy and
control the scope of retrieved results.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-23-autorag-metadata-filtering/
md: https://developers.cloudflare.com/changelog/2025-04-23-autorag-metadata-filtering/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Metadata filtering and multitenancy support in AutoRAG
Apr 23, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
You can now filter [AutoRAG](https://developers.cloudflare.com/ai-search/) search results by `folder` and `timestamp` using [metadata filtering](https://developers.cloudflare.com/ai-search/configuration/metadata) to narrow down the scope of your query.
This makes it easy to build [multitenant experiences](https://developers.cloudflare.com/ai-search/how-to/multitenancy/) where each user can only access their own data. By organizing your content into per-tenant folders and applying a `folder` filter at query time, you ensure that each tenant retrieves only their own documents.
**Example folder structure:**
```bash
customer-a/logs/
customer-a/contracts/
customer-b/contracts/
```
**Example query:**
```js
const response = await env.AI.autorag("my-autorag").search({
query: "When did I sign my agreement contract?",
filters: {
type: "eq",
key: "folder",
value: "customer-a/contracts/",
},
});
```
You can use metadata filtering by creating a new AutoRAG or reindexing existing data. To reindex all content in an existing AutoRAG, update any chunking setting and select **Sync index**. Metadata filtering is available for all data indexed on or after **April 21, 2025**.
If you are new to AutoRAG, get started with the [Get started AutoRAG guide](https://developers.cloudflare.com/ai-search/get-started/).
---
title: Custom Errors are now Generally Available · Changelog
description: A new UI for error handling is now available — letting you manage
Error Pages, Custom Error Rules, and Assets from the dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-24-custom-errors-ga/
md: https://developers.cloudflare.com/changelog/2025-04-24-custom-errors-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Custom Errors are now Generally Available
Apr 24, 2025
[Rules](https://developers.cloudflare.com/rules/)
[Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) are now generally available for all paid plans — bringing a unified and powerful experience for customizing error responses at both the zone and account levels.
You can now manage **Custom Error Rules**, **Custom Error Assets**, and redesigned **Error Pages** directly from the Cloudflare dashboard. These features let you deliver tailored messaging when errors occur, helping you maintain brand consistency and improve user experience — whether it’s a 404 from your origin or a security challenge from Cloudflare.
What's new:
* **Custom Errors are now GA** – Available on all paid plans and ready for production traffic.
* **UI for Custom Error Rules and Assets** – Manage your zone-level rules from the Rules > Overview and your zone-level assets from the Rules > Settings tabs.
* **Define inline content or upload assets** – Create custom responses directly in the rule builder, upload new or reuse previously stored assets.
* **Refreshed UI and new name for Error Pages** – Formerly known as “Custom Pages,” Error Pages now offer a cleaner, more intuitive experience for both zone and account-level configurations.
* **Powered by Ruleset Engine** – Custom Error Rules support [conditional logic](https://developers.cloudflare.com/ruleset-engine/rules-language/) and override Error Pages for 500 and 1000 class errors, as well as errors originating from your origin or [other Cloudflare products](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/). You can also configure [Response Header Transform Rules](https://developers.cloudflare.com/rules/transform/response-header-modification/) to add, change, or remove HTTP headers from responses returned by Custom Error Rules.
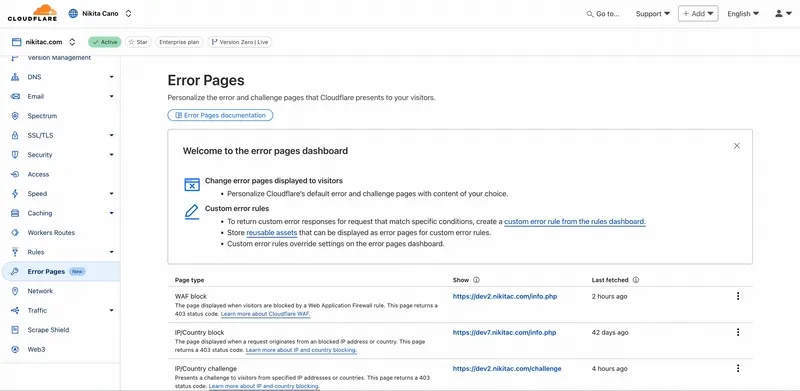
Learn more in the [Custom Errors documentation](https://developers.cloudflare.com/rules/custom-errors/).
---
title: FQDN Filtering For Gateway Egress Policies · Changelog
description: Select your egress IP depending on your upstream fully qualified
domain name (FQDN), application, or category
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-28-fdqn-filtering-egress-policies/
md: https://developers.cloudflare.com/changelog/2025-04-28-fdqn-filtering-egress-policies/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## FQDN Filtering For Gateway Egress Policies
Apr 28, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Cloudflare One administrators can now control which egress IP is used based on a destination's fully qualified domain name (FDQN) within Gateway Egress policies.
* Host, Domain, Content Categories, and Application selectors are now available in the Gateway Egress policy builder in beta.
* During the beta period, you can use these selectors with traffic on-ramped to Gateway with the WARP client, proxy endpoints (commonly deployed with PAC files), or Cloudflare Browser Isolation.
* For WARP client support, additional configuration is required. For more information, refer to the [WARP client configuration documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/#limitations).

This will help apply egress IPs to your users' traffic when an upstream application or network requires it, while the rest of their traffic can take the most performant egress path.
---
title: WAF Release - 2025-04-26 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-04-26 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-26-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-04-26-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-04-26 - Emergency
Apr 26, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 54ea354d7f2d43c69b238d1419fcc883 | 100755 | React.js - Router and Remix Vulnerability - CVE:CVE-2025-43864, CVE:CVE-2025-43865 | Block | Block | This is a New Detection |
---
title: Dark Mode for Zero Trust Dashboard · Changelog
description: Use Dark Mode in the Zero Trust Dashboard
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-04-30-zero-trust-dashboard-dark-mode/
md: https://developers.cloudflare.com/changelog/2025-04-30-zero-trust-dashboard-dark-mode/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Dark Mode for Zero Trust Dashboard
Apr 30, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
The [Cloudflare Zero Trust dashboard](https://one.dash.cloudflare.com/) now supports Cloudflare's native dark mode for all accounts and plan types.
Zero Trust Dashboard will automatically accept your user-level preferences for system settings, so if your Dashboard appearance is set to 'system' or 'dark', the Zero Trust dashboard will enter dark mode whenever the rest of your Cloudflare account does.

* Zero Trust Dashboard
To update your view preference in the Zero Trust dashboard:
1. Log into the [Zero Trust dashboard](https://one.dash.cloudflare.com/).
2. Select your user icon.
3. Select **Dark Mode**.
* Core Dashboard
To update your view preference in the Core dashboard:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com).
2. Go to **My Profile**
3. For **Appearance**, choose **Dark**.
---
title: Browser Isolation Overview page for Zero Trust · Changelog
description: A new home page experience for deploying and managing browser
isolation deployments.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-01-browser-isolation-overview-page/
md: https://developers.cloudflare.com/changelog/2025-05-01-browser-isolation-overview-page/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Browser Isolation Overview page for Zero Trust
May 01, 2025
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
A new **Browser Isolation Overview** page is now available in the Cloudflare Zero Trust dashboard. This centralized view simplifies the management of [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/) deployments, providing:
* **Streamlined Onboarding:** Easily set up and manage isolation policies from one location.
* **Quick Testing:** Validate [clientless web application isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/) with ease.
* **Simplified Configuration:** Configure [isolated access applications](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/isolate-application/) and policies efficiently.
* **Centralized Monitoring:** Track aggregate usage and blocked actions.
This update consolidates previously disparate settings, accelerating deployment, improving visibility into isolation activity, and making it easier to ensure your protections are working effectively.

To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and find Browser Isolation in the side navigation bar.
---
title: R2 Dashboard experience gets new updates · Changelog
description: R2 Dashboard experience gets new updates
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-01-r2-dashboard-updates/
md: https://developers.cloudflare.com/changelog/2025-05-01-r2-dashboard-updates/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## R2 Dashboard experience gets new updates
May 01, 2025
[R2](https://developers.cloudflare.com/r2/)
We're excited to announce several improvements to the [Cloudflare R2](https://developers.cloudflare.com/r2/) dashboard experience that make managing your object storage easier and more intuitive:

#### All-new settings page
We've redesigned the bucket settings page, giving you a centralized location to manage all your bucket configurations in one place.
#### Improved navigation and sharing
* Deeplink support for prefix directories: Navigate through your bucket hierarchy without losing your state. Your browser's back button now works as expected, and you can share direct links to specific prefix directories with teammates.
* Objects as clickable links: Objects are now proper links that you can copy or `CMD + Click` to open in a new tab.
#### Clearer public access controls
* Renamed "r2.dev domain" to "Public Development URL" for better clarity when exposing bucket contents for non-production workloads.
* Public Access status now clearly displays "Enabled" when your bucket is exposed to the internet (via Public Development URL or Custom Domains).
We've also made numerous other usability improvements across the board to make your R2 experience smoother and more productive.
---
title: WAF Release - 2025-05-05 · Changelog
description: Cloudflare WAF managed rulesets 2025-05-05 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-05-waf-release/
md: https://developers.cloudflare.com/changelog/2025-05-05-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-05-05
May 05, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's analysis covers five CVEs with varying impact levels. Four are rated critical, while one is rated high severity. Remote Code Execution vulnerabilities dominate this set.
**Key Findings**
GFI KerioControl (CVE-2024-52875) contains an unauthenticated Remote Code Execution (RCE) vulnerability that targets firewall appliances. This vulnerability can let attackers gain root level system access, making this CVE particularly attractive for threat actors.
The SonicWall SMA vulnerabilities remain concerning due to their continued exploitation since 2021. These critical vulnerabilities in remote access solutions create dangerous entry points to networks.
**Impact**
Customers using the Managed Ruleset will receive rule coverage following this week's release. Below is a breakdown of the recommended prioritization based on current exploitation trends:
* GFI KerioControl (CVE-2024-52875) - Highest priority; unauthenticated RCE
* SonicWall SMA (Multiple vulnerabilities) - Critical for network appliances
* XWiki (CVE-2025-24893) - High priority for development environments
* Langflow (CVE-2025-3248) - Important for AI workflow platforms
* MinIO (CVE-2025-31489) - Important for object storage implementations
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 921660147baa48eaa9151077d0b7a392 | 100724 | GFI KerioControl - Remote Code Execution - CVE:CVE-2024-52875 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | a3900934273b4a488111f810717a9e42 | 100748 | XWiki - Remote Code Execution - CVE:CVE-2025-24893 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 616ad0e03892473191ca1df4e9cf745d | 100750 | SonicWall SMA - Dangerous File Upload - CVE:CVE-2021-20040, CVE:CVE-2021-20041, CVE:CVE-2021-20042 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 1a11fbe84b49451193ee1ee6d29da333 | 100751 | Langflow - Remote Code Execution - CVE:CVE-2025-3248 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 5eb7ed601e6844828b9bdb05caa7b208 | 100752 | MinIO - Auth Bypass - CVE:CVE-2025-31489 | Log | Block | This is a New Detection |
---
title: UDP and ICMP Monitor Support for Private Load Balancing Endpoints · Changelog
description: Use UDP or ICMP to monitor the health of your private IP-based applications.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-06-private-health-monitoring-methods/
md: https://developers.cloudflare.com/changelog/2025-05-06-private-health-monitoring-methods/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## UDP and ICMP Monitor Support for Private Load Balancing Endpoints
May 06, 2025
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
Cloudflare Load Balancing now supports **UDP (Layer 4)** and **ICMP (Layer 3)** health monitors for **private endpoints**. This makes it simple to track the health and availability of internal services that don’t respond to HTTP, TCP, or other protocol probes.
#### What you can do:
* Set up **ICMP ping monitors** to check if your private endpoints are reachable.
* Use **UDP monitors** for lightweight health checks on non-TCP workloads, such as DNS, VoIP, or custom UDP-based services.
* Gain better visibility and uptime guarantees for services running behind **Private Network Load Balancing**, without requiring public IP addresses.
This enhancement is ideal for internal applications that rely on low-level protocols, especially when used in conjunction with [**Cloudflare Tunnel**](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/), [**WARP**](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/), and [**Magic WAN**](https://developers.cloudflare.com/magic-wan/) to create a secure and observable private network.
Learn more about [Private Network Load Balancing](https://developers.cloudflare.com/load-balancing/private-network/) or view the full list of [supported health monitor protocols](https://developers.cloudflare.com/load-balancing/monitors/#supported-protocols).
---
title: Terraform v5.4.0 now available · Changelog
description: Terraform v5.4.0 fixes a number of known bugs in the v5 Provider
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-06-terraform-v540-provider/
md: https://developers.cloudflare.com/changelog/2025-05-06-terraform-v540-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.4.0 now available
May 06, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). Unlike the earlier Terraform providers, v5 is automatically generated based on the OpenAPI Schemas for our REST APIs. Since launch, we have seen an unexpectedly high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by customers. These issues currently impact about 15% of resources. We have been working diligently to address these issues across the company, and have released the v5.4.0 release which includes a number of bug fixes. Please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Removes the `worker_platforms_script_secret` resource from the provider (see [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade#cloudflare_worker_secret) for alternatives—applicable to both Workers and Workers for Platforms)
* Removes duplicated fields in `cloudflare_cloud_connector_rules` resource
* Fixes `cloudflare_workers_route` id issues [#5134](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5134) [#5501](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5501)
* Fixes issue around refreshing resources that have unsupported response types
Affected resources
* `cloudflare_certificate_pack`
* `cloudflare_registrar_domain`
* `cloudflare_stream_download`
* `cloudflare_stream_webhook`
* `cloudflare_user`
* `cloudflare_workers_kv`
* `cloudflare_workers_script`
* Fixes `cloudflare_workers_kv` state refresh issues
* Fixes issues around configurability of nested properties without computed values for the following resources
Affected resources
* `cloudflare_account`
* `cloudflare_account_dns_settings`
* `cloudflare_account_token`
* `cloudflare_api_token`
* `cloudflare_cloud_connector_rules`
* `cloudflare_custom_ssl`
* `cloudflare_d1_database`
* `cloudflare_dns_record`
* `email_security_trusted_domains`
* `cloudflare_hyperdrive_config`
* `cloudflare_keyless_certificate`
* `cloudflare_list_item`
* `cloudflare_load_balancer`
* `cloudflare_logpush_dataset_job`
* `cloudflare_magic_network_monitoring_configuration`
* `cloudflare_magic_transit_site`
* `cloudflare_magic_transit_site_lan`
* `cloudflare_magic_transit_site_wan`
* `cloudflare_magic_wan_static_route`
* `cloudflare_notification_policy`
* `cloudflare_pages_project`
* `cloudflare_queue`
* `cloudflare_queue_consumer`
* `cloudflare_r2_bucket_cors`
* `cloudflare_r2_bucket_event_notification`
* `cloudflare_r2_bucket_lifecycle`
* `cloudflare_r2_bucket_lock`
* `cloudflare_r2_bucket_sippy`
* `cloudflare_ruleset`
* `cloudflare_snippet_rules`
* `cloudflare_snippets`
* `cloudflare_spectrum_application`
* `cloudflare_workers_deployment`
* `cloudflare_zero_trust_access_application`
* `cloudflare_zero_trust_access_group`
* Fixed defaults that made `cloudflare_workers_script` fail when using Assets
* Fixed Workers Logpush setting in `cloudflare_workers_script` mistakenly being readonly
* Fixed `cloudflare_pages_project` broken when using "source"
The detailed [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.4.0) is available on GitHub.
#### Upgrading
If you are evaluating a move from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues either by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare), or by opening a [support ticket](https://www.support.cloudflare.com/s/?language=en_US).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: Send forensic copies to storage without DLP profiles · Changelog
description: HTTP policies can now be configured to send forensic copies for all
allow and block policies.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-07-forensic-copy-update/
md: https://developers.cloudflare.com/changelog/2025-05-07-forensic-copy-update/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Send forensic copies to storage without DLP profiles
May 07, 2025
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now [send DLP forensic copies](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#send-http-requests-to-logpush-destination/) to third-party storage for any HTTP policy with an `Allow` or `Block` action, without needing to include a DLP profile. This change increases flexibility for data handling and forensic investigation use cases.
By default, Gateway will send all matched HTTP requests to your configured DLP Forensic Copy jobs.

---
title: URL Scanner now supports geo-specific scanning · Changelog
description: Enterprise users can now choose the location from which URL scans
are performed.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-07-url-scanner-geoegress/
md: https://developers.cloudflare.com/changelog/2025-05-07-url-scanner-geoegress/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## URL Scanner now supports geo-specific scanning
May 08, 2025
[Security Center](https://developers.cloudflare.com/security-center/)
Enterprise customers can now choose the geographic location from which a URL scan is performed — either via [Security Center](https://developers.cloudflare.com/security-center/investigate/) in the Cloudflare dashboard or via the [URL Scanner API](https://developers.cloudflare.com/api/resources/url_scanner/subresources/scans/methods/create/).
This feature gives security teams greater insight into how a website behaves across different regions, helping uncover targeted, location-specific threats.
**What’s new:**
* Location Picker: Select a location for the scan via **Security Center → Investigate** in the dashboard or through the API.
* Region-aware scanning: Understand how content changes by location — useful for detecting regionally tailored attacks.
* Default behavior: If no location is set, scans default to the user’s current geographic region.
Learn more in the [Security Center documentation](https://developers.cloudflare.com/security-center/).
---
title: Improved memory efficiency for WebAssembly Workers · Changelog
description: With the introduction of FinalizationRegistry in Workers Runtime,
toolchains like Emscripten and wasm-bindgen can automatically reclaim unused
WebAssembly heap and reduce memory leaks.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-08-finalization-registry/
md: https://developers.cloudflare.com/changelog/2025-05-08-finalization-registry/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved memory efficiency for WebAssembly Workers
May 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
[FinalizationRegistry](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/FinalizationRegistry) is now available in Workers. You can opt-in using the [`enable_weak_ref`](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#enable-finalizationregistry-and-weakref) compatibility flag.
This can reduce memory leaks when using WebAssembly-based Workers, which includes [Python Workers](https://developers.cloudflare.com/workers/languages/python/) and [Rust Workers](https://developers.cloudflare.com/workers/languages/rust/). The FinalizationRegistry works by enabling toolchains such as [Emscripten](https://emscripten.org/) and [wasm-bindgen](https://rustwasm.github.io/wasm-bindgen/) to automatically free WebAssembly heap allocations. If you are using WASM and seeing Exceeded Memory errors and cannot determine a cause using [memory profiling](https://developers.cloudflare.com/workers/observability/dev-tools/memory-usage/), you may want to enable the FinalizationRegistry.
For more information refer to the [`enable_weak_ref`](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#enable-finalizationregistry-and-weakref) compatibility flag documentation.
---
title: Improved Payload Logging for WAF Managed Rules · Changelog
description: We have upgraded WAF Payload Logging to enhance rule diagnostics and usability.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-08-improved-payload-logging/
md: https://developers.cloudflare.com/changelog/2025-05-08-improved-payload-logging/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved Payload Logging for WAF Managed Rules
May 08, 2025
[WAF](https://developers.cloudflare.com/waf/)
We have upgraded WAF Payload Logging to enhance rule diagnostics and usability:
* **Targeted logging**: Logs now capture only the specific portions of requests that triggered WAF rules, rather than entire request segments.
* **Visual highlighting**: Matched content is visually highlighted in the UI for faster identification.
* **Enhanced context**: Logs now include surrounding context to make diagnostics more effective.
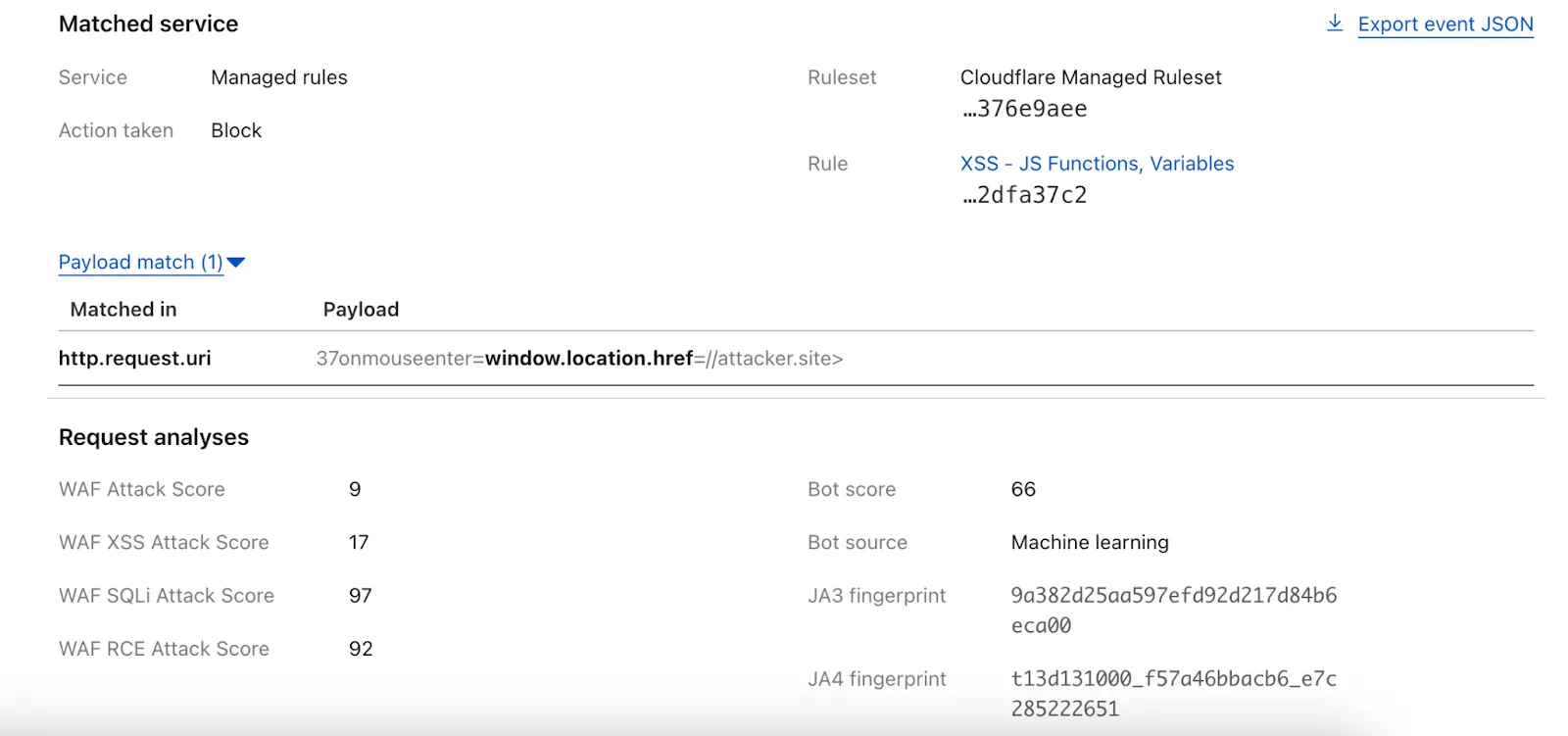
Payload Logging is available to all Enterprise customers. If you have not used Payload Logging before, check how you can [get started](https://developers.cloudflare.com/waf/managed-rules/payload-logging/).
**Note:** The structure of the `encrypted_matched_data` field in Logpush has changed from `Map` to `Map`. If you rely on this field in your Logpush jobs, you should review and update your processing logic accordingly.
---
title: Open email attachments with Browser Isolation · Changelog
description: A new attachment section in Email security allows you to safely
open attachments to view and investigate.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-08-open-attachments-with-browser-isolation/
md: https://developers.cloudflare.com/changelog/2025-05-08-open-attachments-with-browser-isolation/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Open email attachments with Browser Isolation
May 15, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You can now safely open email attachments to view and investigate them.
What this means is that messages now have a **Attachments** section. Here, you can view processed attachments and their classifications (for example, *Malicious*, *Suspicious*, *Encrypted*). Next to each attachment, a **Browser Isolation** icon allows your team to safely open the file in a **clientless, isolated browser** with no risk to the analyst or your environment.

To use this feature, you must:
* Enable **Clientless Web Isolation** in your Zero Trust settings.
* Have **Browser Isolation (BISO)** seats assigned.
For more details, refer to our [setup guide](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/).
Some attachment types may not render in Browser Isolation. If there is a file type that you would like to be opened with Browser Isolation, reach out to your Cloudflare contact.
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Publish messages to Queues directly via HTTP · Changelog
description: You can now publish messages to Cloudflare Queues from any HTTP client.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-09-publish-to-queues-via-http/
md: https://developers.cloudflare.com/changelog/2025-05-09-publish-to-queues-via-http/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Publish messages to Queues directly via HTTP
May 09, 2025
[Queues](https://developers.cloudflare.com/queues/)
You can now publish messages to [Cloudflare Queues](https://developers.cloudflare.com/queues/) directly via HTTP from any service or programming language that supports sending HTTP requests. Previously, publishing to queues was only possible from within [Cloudflare Workers](https://developers.cloudflare.com/workers/). You can already consume from queues via Workers or [HTTP pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/), and now publishing is just as flexible.
Publishing via HTTP requires a [Cloudflare API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with `Queues Edit` permissions for authentication. Here's a simple example:
```bash
curl "https://api.cloudflare.com/client/v4/accounts//queues//messages" \
-X POST \
-H 'Authorization: Bearer ' \
--data '{ "body": { "greeting": "hello", "timestamp": "2025-07-24T12:00:00Z"} }'
```
You can also use our [SDKs](https://developers.cloudflare.com/fundamentals/api/reference/sdks/) for TypeScript, Python, and Go.
To get started with HTTP publishing, check out our [step-by-step example](https://developers.cloudflare.com/queues/examples/publish-to-a-queue-via-http/) and the full API documentation in our [API reference](https://developers.cloudflare.com/api/resources/queues/subresources/messages/methods/push/).
---
title: More ways to match — Snippets now support Custom Lists, Bot Score, and
WAF Attack Score · Changelog
description: Snippets and Cloud Connector now support user-defined IP, AS, and
Hostname Custom Lists — plus Bot Score and WAF Attack Score in Snippets.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-09-snippets-cloud-connector-lists-waf-bot-scores/
md: https://developers.cloudflare.com/changelog/2025-05-09-snippets-cloud-connector-lists-waf-bot-scores/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## More ways to match — Snippets now support Custom Lists, Bot Score, and WAF Attack Score
May 09, 2025
[Rules](https://developers.cloudflare.com/rules/)
You can now use IP, Autonomous System (AS), and Hostname [custom lists](https://developers.cloudflare.com/waf/tools/lists/custom-lists/) to route traffic to [Snippets](https://developers.cloudflare.com/rules/snippets/) and [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/), giving you greater precision and control over how you match and process requests at the edge.
In Snippets, you can now also match on [Bot Score](https://developers.cloudflare.com/bots/concepts/bot-score/) and [WAF Attack Score](https://developers.cloudflare.com/waf/detections/attack-score/), unlocking smarter edge logic for everything from request filtering and mitigation to [tarpitting](https://developers.cloudflare.com/rules/snippets/examples/slow-suspicious-requests/) and logging.
**What’s new:**
* [Custom lists](https://developers.cloudflare.com/waf/tools/lists/custom-lists/) matching – Snippets and Cloud Connector now support user-created IP, AS, and Hostname lists via dashboard or [Lists API](https://developers.cloudflare.com/api/resources/rules/subresources/lists/methods/list/). Great for shared logic across zones.
* [Bot Score](https://developers.cloudflare.com/bots/concepts/bot-score/) and [WAF Attack Score](https://developers.cloudflare.com/waf/detections/attack-score/) – Use Cloudflare’s intelligent traffic signals to detect bots or attacks and take advanced, tailored actions with just a few lines of code.
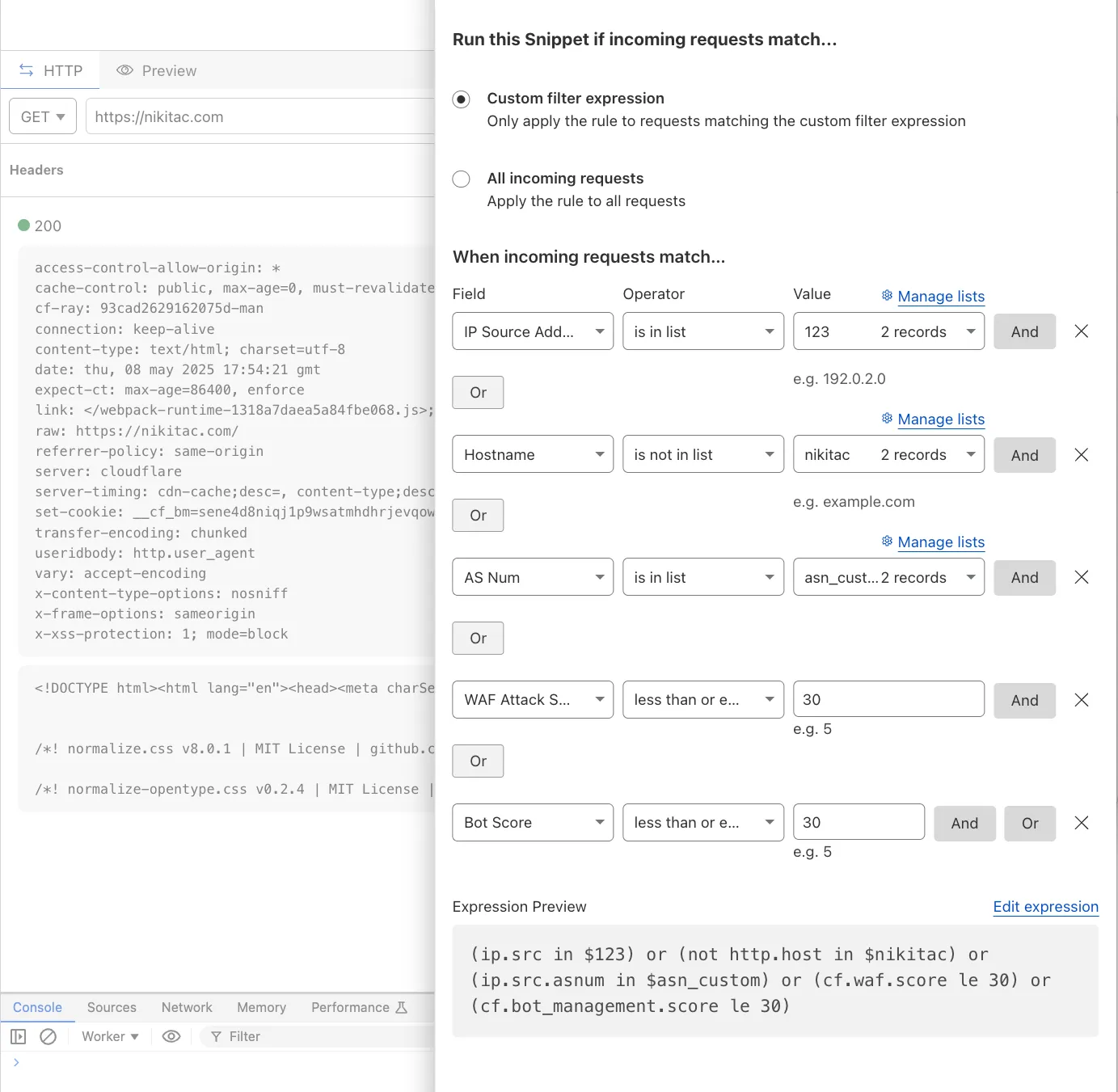
These enhancements unlock new possibilities for building smarter traffic workflows with minimal code and maximum efficiency.
Learn more in the [Snippets](https://developers.cloudflare.com/rules/snippets/) and [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/) documentation.
---
title: Case Sensitive Custom Word Lists · Changelog
description: Custom Word Lists can now be configured to enforce case sensitivity.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-12-case-sensitive-cwl/
md: https://developers.cloudflare.com/changelog/2025-05-12-case-sensitive-cwl/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Case Sensitive Custom Word Lists
May 12, 2025
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now configure [custom word lists](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#custom-wordlist) to enforce case sensitivity. This setting supports flexibility where needed and aims to reduce false positives where letter casing is critical.

---
title: WARP client for Linux (version 2025.4.929.0) · Changelog
description: WARP client for Linux (version 2025.4.929.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-12-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-05-12-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.4.929.0)
May 12, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains two significant changes all customers should be aware of:
1. All DNS traffic now flows inside the WARP tunnel. Customers are no longer required to configure their local firewall rules to allow our [DoH IP addresses and domains](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#doh-ip).
2. When using MASQUE, the connection will fall back to HTTP/2 (TCP) when we detect that HTTP/3 traffic is blocked. This allows for a much more reliable connection on some public WiFi networks.
**Changes and improvements**
* Fixed an issue where the managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Added a TCP fallback for the MASQUE tunnel protocol to improve connectivity on networks that block UDP or HTTP/3 specifically.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improvement for WARP to check if tunnel connectivity fails or times out at device wake before attempting to reconnect.
* Fixed an issue causing WARP connection disruptions after network changes.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for macOS (version 2025.4.929.0) · Changelog
description: WARP client for macOS (version 2025.4.929.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-12-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-05-12-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.4.929.0)
May 12, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains two significant changes all customers should be aware of:
1. All DNS traffic now flows inside the WARP tunnel. Customers are no longer required to configure their local firewall rules to allow our [DoH IP addresses and domains](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#doh-ip).
2. When using MASQUE, the connection will fall back to HTTP/2 (TCP) when we detect that HTTP/3 traffic is blocked. This allows for a much more reliable connection on some public WiFi networks.
**Changes and improvements**
* Fixed an issue where the managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Improved captive portal detection.
* Added a TCP fallback for the MASQUE tunnel protocol to improve connectivity on networks that block UDP or HTTP/3 specifically.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
* Improvement for WARP to check if tunnel connectivity fails or times out at device wake before attempting to reconnect.
* Fixed an issue causing WARP connection disruptions after network changes.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
---
title: New Applications Added for DNS Filtering · Changelog
description: Manage outbound traffic for 273 new applications with DNS policy options
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-13-new-applications-added/
md: https://developers.cloudflare.com/changelog/2025-05-13-new-applications-added/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Applications Added for DNS Filtering
May 13, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
You can now create DNS policies to manage outbound traffic for an expanded list of applications. This update adds support for 273 new applications, giving you more control over your organization's outbound traffic.
With this update, you can:
* Create DNS policies for a wider range of applications
* Manage outbound traffic more effectively
* Improve your organization's security and compliance posture
For more information on creating DNS policies, see our [DNS policy documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/).
---
title: SAML HTTP-POST bindings support for RBI · Changelog
description: Enable secure access to SSO-enabled applications in the remote browser.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-13-rbi-saml-post-support/
md: https://developers.cloudflare.com/changelog/2025-05-13-rbi-saml-post-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## SAML HTTP-POST bindings support for RBI
May 13, 2025
[Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/)
Remote Browser Isolation (RBI) now supports SAML HTTP-POST bindings, enabling seamless authentication for SSO-enabled applications that rely on POST-based SAML responses from Identity Providers (IdPs) within a Remote Browser Isolation session. This update resolves a previous limitation that caused `405` errors during login and improves compatibility with multi-factor authentication (MFA) flows.
With expanded support for major IdPs like Okta and Azure AD, this enhancement delivers a more consistent and user-friendly experience across authentication workflows. Learn how to [set up Remote Browser Isolation](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/).
---
title: Domain Categories improvements · Changelog
description: We have added 7 new Domain Categories and renamed 3 Domain
Categories, to better reflect online content and enable DNS filtering
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-14-domain-category-improvements/
md: https://developers.cloudflare.com/changelog/2025-05-14-domain-category-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Domain Categories improvements
May 14, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
**New categories added**
| Parent ID | Parent Name | Category ID | Category Name |
| - | - | - | - |
| 1 | Ads | 66 | Advertisements |
| 3 | Business & Economy | 185 | Personal Finance |
| 3 | Business & Economy | 186 | Brokerage & Investing |
| 21 | Security Threats | 187 | Compromised Domain |
| 21 | Security Threats | 188 | Potentially Unwanted Software |
| 6 | Education | 189 | Reference |
| 9 | Government & Politics | 190 | Charity and Non-profit |
**Changes to existing categories**
| Original Name | New Name |
| - | - |
| Religion | Religion & Spirituality |
| Government | Government/Legal |
| Redirect | URL Alias/Redirect |
Refer to [Gateway domain categories](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) to learn more.
---
title: Hyperdrive achieves FedRAMP Moderate-Impact Authorization · Changelog
description: Hyperdrive has been approved for FedRAMP Authorization and is now
available in the FedRAMP Marketplace
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-14-hyperdrive-fedramp/
md: https://developers.cloudflare.com/changelog/2025-05-14-hyperdrive-fedramp/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Hyperdrive achieves FedRAMP Moderate-Impact Authorization
May 14, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
Hyperdrive has been approved for FedRAMP Authorization and is now available in the [FedRAMP Marketplace](https://marketplace.fedramp.gov/products/FR2000863987).
FedRAMP is a U.S. government program that provides standardized assessment and authorization for cloud products and services. As a result of this product update, Hyperdrive has been approved as an authorized service to be used by U.S. federal agencies at the Moderate Impact level.
For detailed information regarding FedRAMP and its implications, please refer to the [official FedRAMP documentation for Cloudflare](https://marketplace.fedramp.gov/products/FR2000863987).
---
title: Introducing Origin Restrictions for Media Transformations · Changelog
description: >
Control which sources can be used for original media when requesting
transformations.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-14-media-transformations-origin-restrictions/
md: https://developers.cloudflare.com/changelog/2025-05-14-media-transformations-origin-restrictions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing Origin Restrictions for Media Transformations
May 14, 2025
[Stream](https://developers.cloudflare.com/stream/)
We are adding [source origin restrictions](https://developers.cloudflare.com/stream/transform-videos/sources/) to the Media Transformations beta. This allows customers to restrict what sources can be used to fetch images and video for transformations. This feature is the same as --- and uses the same settings as --- [Image Transformations sources](https://developers.cloudflare.com/images/transform-images/sources/).
When transformations is first enabled, the default setting only allows transformations on images and media from the same website or domain being used to make the transformation request. In other words, by default, requests to `example.com/cdn-cgi/media` can only reference originals on `example.com`.

Adding access to other sources, or allowing any source, [is easy to do](https://developers.cloudflare.com/images/transform-images/sources/) in the **Transformations** tab under **Stream**. Click each domain enabled for Transformations and set its sources list to match the needs of your content. The user making this change will need permission to edit zone settings.
For more information, learn about [Transforming Videos](https://developers.cloudflare.com/stream/transform-videos/).
---
title: Durable Objects are now supported in Python Workers · Changelog
description: You can now create Durable Objects using Python
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-14-python-worker-durable-object/
md: https://developers.cloudflare.com/changelog/2025-05-14-python-worker-durable-object/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Durable Objects are now supported in Python Workers
May 16, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Durable Objects](https://developers.cloudflare.com/durable-objects/)
You can now create [Durable Objects](https://developers.cloudflare.com/durable-objects/) using [Python Workers](https://developers.cloudflare.com/workers/languages/python/). A Durable Object is a special kind of Cloudflare Worker which uniquely combines compute with storage, enabling stateful long-running applications which run close to your users. For more info see [here](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/).
You can define a Durable Object in Python in a similar way to JavaScript:
```python
from workers import DurableObject, Response, WorkerEntrypoint
from urllib.parse import urlparse
class MyDurableObject(DurableObject):
def __init__(self, ctx, env):
self.ctx = ctx
self.env = env
def fetch(self, request):
result = self.ctx.storage.sql.exec("SELECT 'Hello, World!' as greeting").one()
return Response(result.greeting)
class Default(WorkerEntrypoint):
async def fetch(self, request):
url = urlparse(request.url)
id = env.MY_DURABLE_OBJECT.idFromName(url.path)
stub = env.MY_DURABLE_OBJECT.get(id)
greeting = await stub.fetch(request.url)
return greeting
```
Define the Durable Object in your Wrangler configuration file:
* wrangler.jsonc
```jsonc
{
"durable_objects": {
"bindings": [
{
"name": "MY_DURABLE_OBJECT",
"class_name": "MyDurableObject"
}
]
}
}
```
* wrangler.toml
```toml
[[durable_objects.bindings]]
name = "MY_DURABLE_OBJECT"
class_name = "MyDurableObject"
```
Then define the storage backend for your Durable Object:
* wrangler.jsonc
```jsonc
{
"migrations": [
{
"tag": "v1", // Should be unique for each entry
"new_sqlite_classes": [ // Array of new classes
"MyDurableObject"
]
}
]
}
```
* wrangler.toml
```toml
[[migrations]]
tag = "v1"
new_sqlite_classes = [ "MyDurableObject" ]
```
Then test your new Durable Object locally by running `wrangler dev`:
```plaintext
npx wrangler dev
```
Consult the [Durable Objects documentation](https://developers.cloudflare.com/durable-objects/) for more details.
---
title: WARP client for Windows (version 2025.4.929.0) · Changelog
description: WARP client for Windows (version 2025.4.929.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-14-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-05-14-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.4.929.0)
May 14, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains two significant changes all customers should be aware of:
1. All DNS traffic now flows inside the WARP tunnel. Customers are no longer required to configure their local firewall rules to allow our [DoH IP addresses and domains](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#doh-ip).
2. When using MASQUE, the connection will fall back to HTTP/2 (TCP) when we detect that HTTP/3 traffic is blocked. This allows for a much more reliable connection on some public WiFi networks.
**Changes and improvements**
* Fixed an issue causing reconnection loops when captive portals are detected.
* Fixed an issue that caused WARP client disk encryption posture checks to fail due to missing drive names.
* Fixed an issue where managed network policies could incorrectly report network location beacons as missing.
* Improved DEX test error reporting.
* Fixed an issue where some parts of the WARP Client UI were missing in high contrast mode.
* Fixed an issue causing client notifications to fail in IPv6 only environments which prevented the client from receiving configuration changes to settings like device profile.
* Added a TCP fallback for the MASQUE tunnel protocol to improve connectivity on networks that block UDP or HTTP/3 specifically.
* Added new IP addresses for [tunnel connectivity checks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/firewall/#connectivity-checks). If your organization uses a firewall or other policies you will need to exempt these IPs.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* Improved the error message displayed in the client GUI when the rate limit for entering an incorrect admin override code is met.
* Improved handling of non-SLAAC IPv6 interface addresses for better connectivity in IPv6 only environments.
* Fixed an issue where frequent network changes could cause WARP to become unresponsive.
* Improvement for WARP to check if tunnel connectivity fails or times out at device wake before attempting to reconnect.
* Fixed an issue causing WARP connection disruptions after network changes.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
---
title: Open email links with Browser Isolation · Changelog
description: New investigation feature for links
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-15-open-links-browser-isolation/
md: https://developers.cloudflare.com/changelog/2025-05-15-open-links-browser-isolation/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Open email links with Browser Isolation
May 08, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You can now safely open links in emails to view and investigate them.

From **Investigation**, go to **View details**, and look for the **Links identified** section. Next to each link, the Cloudflare dashboard will display an **Open in Browser Isolation** icon which allows your team to safely open the link in a clientless, isolated browser with no risk to the analyst or your environment. Refer to [Open links](https://developers.cloudflare.com/cloudflare-one/email-security/investigation/search-email/#open-links) to learn more about this feature.
To use this feature, you must:
* Enable **Clientless Web Isolation** in your Zero Trust settings.
* Have **Browser Isolation (RBI)** seats assigned.
For more details, refer to our [setup guide](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Increased limits for Cloudflare for SaaS and Secrets Store free and
pay-as-you-go plans · Changelog
description: With upgraded limits to [all free and paid
plans](https://www.cloudflare.com/plans/), you can now extend the benefits of
Cloudflare to more end customers via [Cloudflare for
SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)
and deploy more account level variables through [Cloudflare Secrets
Store](https://developers.cloudflare.com/secrets-store/).
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-19-paygo-updates/
md: https://developers.cloudflare.com/changelog/2025-05-19-paygo-updates/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased limits for Cloudflare for SaaS and Secrets Store free and pay-as-you-go plans
May 27, 2025
[SSL/TLS ](https://developers.cloudflare.com/ssl/)[Cloudflare for SaaS ](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/)[Secrets Store](https://developers.cloudflare.com/secrets-store/)
With upgraded limits to [all free and paid plans](https://www.cloudflare.com/plans/), you can now scale more easily with [Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/) and [Secrets Store](https://developers.cloudflare.com/secrets-store/).
[Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/) allows you to extend the benefits of Cloudflare to your customers via their own custom or vanity domains. Now, the [limit for custom hostnames](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/plans/) on a Cloudflare for SaaS pay-as-you-go plan has been **raised from 5,000 custom hostnames to 50,000 custom hostnames.**
With custom origin server -- previously an enterprise-only feature -- you can route traffic from one or more custom hostnames somewhere other than your default proxy fallback. [Custom origin server](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/advanced-settings/custom-origin/) is now available to Cloudflare for SaaS customers on Free, Pro, and Business plans.
You can enable custom origin server on a per-custom hostname basis [via the API](https://developers.cloudflare.com/api/resources/custom_hostnames/methods/edit/) or the UI:

Currently [in beta with a Workers integration](https://blog.cloudflare.com/secrets-store-beta/), [Cloudflare Secrets Store](https://developers.cloudflare.com/secrets-store/) allows you to store, manage, and deploy account level secrets from a secure, centralized platform your [Cloudflare Workers](https://developers.cloudflare.com/workers/). Now, you can create and deploy **100 secrets per account**. Try it out [in the dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store), with [Wrangler](https://developers.cloudflare.com/secrets-store/integrations/workers/), or [via the API](https://developers.cloudflare.com/api/resources/secrets_store/) today.
---
title: Terraform v5.5.0 now available · Changelog
description: Terraform v5.5.0 fixes a number of known bugs in the v5 Provider
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-19-terraform-v550-provider/
md: https://developers.cloudflare.com/changelog/2025-05-19-terraform-v550-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.5.0 now available
May 19, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). Unlike the earlier Terraform providers, v5 is automatically generated based on the OpenAPI Schemas for our REST APIs. Since launch, we have seen an unexpectedly high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by customers. These issues currently impact about 15% of resources. We have been working diligently to address these issues across the company, and have released the v5.5.0 release which includes a number of bug fixes. Please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Broad fixes across resources with recurring diffs, including, but not limited to:
* `cloudflare_zero_trust_gateway_policy`
* `cloudflare_zero_trust_access_application`
* `cloudflare_zero_trust_tunnel_cloudflared_route`
* `cloudflare_zone_setting`
* `cloudflare_ruleset`
* `cloudflare_page_rule`
* Zone settings can be re-applied without client errors
* Page rules conversion errors are fixed
* Failure to apply changes to `cloudflare_zero_trust_tunnel_cloudflared_route`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.5.0) in GitHub.
#### Issues Closed
* [#5304: Importing cloudflare\_zero\_trust\_gateway\_policy invalid attribute filter value](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5304)
* [#5303: cloudflare\_page\_rule import does not set values for all of the fields in terraform state](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5303)
* [#5178: cloudflare\_page\_rule Page rule creation with redirect fails](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5178)
* [#5336: cloudflare\_turnstile\_wwidget not able to udpate](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5336)
* [#5418: cloudflare\_cloud\_connector\_rules: Provider returned invalid result object after apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5418)
* [#5423: cloudflare\_zone\_setting: "Invalid value for zone setting always\_use\_https"](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5423)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
If you are evaluating a move from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: WAF Release - 2025-05-19 · Changelog
description: Cloudflare WAF managed rulesets 2025-05-19 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-19-waf-release/
md: https://developers.cloudflare.com/changelog/2025-05-19-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-05-19
May 19, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's analysis covers four vulnerabilities, with three rated critical due to their Remote Code Execution (RCE) potential. One targets a high-traffic frontend platform, while another targets a popular content management system. These detections are now part of the Cloudflare Managed Ruleset in *Block* mode.
**Key Findings**
* Commvault Command Center (CVE-2025-34028) exposes an unauthenticated RCE via insecure command injection paths in the web UI. This is critical due to its use in enterprise backup environments.
* BentoML (CVE-2025-27520) reveals an exploitable vector where serialized payloads in model deployment APIs can lead to arbitrary command execution. This targets modern AI/ML infrastructure.
* Craft CMS (CVE-2024-56145) allows RCE through template injection in unauthenticated endpoints. It poses a significant risk for content-heavy websites with plugin extensions.
* Apache HTTP Server (CVE-2024-38475) discloses sensitive server config data due to misconfigured `mod_proxy` behavior. While not RCE, this is useful for pre-attack recon.
**Impact**
These newly detected vulnerabilities introduce critical risk across modern web stacks, AI infrastructure, and content platforms: unauthenticated RCEs in Commvault, BentoML, and Craft CMS enable full system compromise with minimal attacker effort.
Apache HTTPD information leak can support targeted reconnaissance, increasing the success rate of follow-up exploits. Organizations using these platforms should prioritize patching and monitor for indicators of exploitation using updated WAF detection rules.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 5c3559ad62994e5b932d7d0075129820 | 100745 | Apache HTTP Server - Information Disclosure - CVE:CVE-2024-38475 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 28a22a685bba478d99bc904526a517f1 | 100747 | Commvault Command Center - Remote Code Execution - CVE:CVE-2025-34028 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 2e6bb954d0634e368c49d7d1d7619ccb | 100749 | BentoML - Remote Code Execution - CVE:CVE-2025-27520 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 91250eebec894705b62305b2f15bfda4 | 100753 | Craft CMS - Remote Code Execution - CVE:CVE-2024-56145 | Log | Block | This is a New Detection |
---
title: Debug, profile, and view logs for your Worker in Chrome Devtools — now
supported in the Cloudflare Vite plugin · Changelog
description: The Cloudflare Vite plugin now supports debugging Cloudflare
Workers using Chrome Devtools
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-21-vite-plugin-chrome-devtools/
md: https://developers.cloudflare.com/changelog/2025-05-21-vite-plugin-chrome-devtools/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Debug, profile, and view logs for your Worker in Chrome Devtools — now supported in the Cloudflare Vite plugin
May 30, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now [debug, profile, view logs, and analyze memory usage for your Worker](https://developers.cloudflare.com/workers/observability/dev-tools/) using [Chrome Devtools](https://developer.chrome.com/docs/devtools) when your Worker runs locally using the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/).
Previously, this was only possible if your Worker ran locally using the [Wrangler CLI](https://developers.cloudflare.com/workers/wrangler/), and now you can do all the same things if your Worker uses [Vite](https://vite.dev/).
When you run `vite`, you'll now see a debug URL in your console:
```plaintext
VITE v6.3.5 ready in 461 ms
➜ Local: http://localhost:5173/
➜ Network: use --host to expose
➜ Debug: http://localhost:5173/__debug
➜ press h + enter to show help
```
Open the URL in Chrome, and an instance of Chrome Devtools will open and connect to your Worker running locally. You can then use Chrome Devtools to debug and introspect performance issues. For example, you can navigate to the Performance tab to understand where CPU time is spent in your Worker:
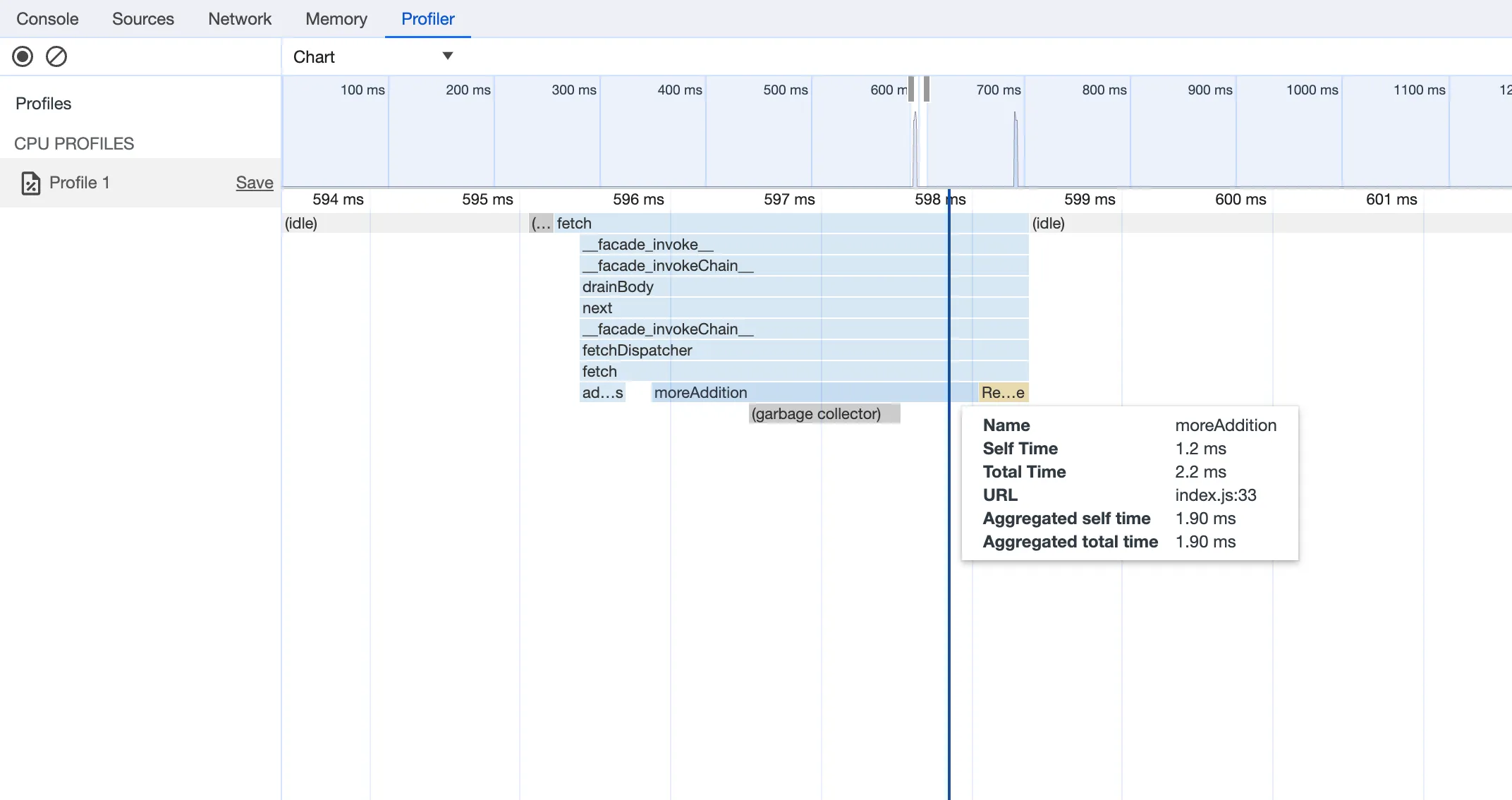
For more information on how to get the most out of Chrome Devtools, refer to the following docs:
* [Debug code by setting breakpoints](https://developers.cloudflare.com/workers/observability/dev-tools/breakpoints/)
* [Profile CPU usage](https://developers.cloudflare.com/workers/observability/dev-tools/cpu-usage/)
* [Observe memory usage and debug memory leaks](https://developers.cloudflare.com/workers/observability/dev-tools/memory-usage/)
---
title: Handle incoming request cancellation in Workers with Request.signal · Changelog
description: Workers can now add event listeners on Request.signal and perform
tasks when the request is cancelled by the client
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-22-handle-request-cancellation/
md: https://developers.cloudflare.com/changelog/2025-05-22-handle-request-cancellation/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Handle incoming request cancellation in Workers with Request.signal
May 22, 2025
[Workers](https://developers.cloudflare.com/workers/)
In Cloudflare Workers, you can now attach an event listener to [`Request`](https://developers.cloudflare.com/workers/runtime-apis/request/) objects, using the [`signal` property](https://developer.mozilla.org/en-US/docs/Web/API/Request/signal). This allows you to perform tasks when the request to your Worker is canceled by the client. To use this feature, you must set the [`enable_request_signal`](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#enable-requestsignal-for-incoming-requests) compatibility flag.
You can use a listener to perform cleanup tasks or write to logs before your Worker's invocation ends. For example, if you run the Worker below, and then abort the request from the client, a log will be written:
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
// This sets up an event listener that will be called if the client disconnects from your
// worker.
request.signal.addEventListener("abort", () => {
console.log("The request was aborted!");
});
const { readable, writable } = new IdentityTransformStream();
sendPing(writable);
return new Response(readable, {
headers: { "Content-Type": "text/plain" },
});
},
};
async function sendPing(writable) {
const writer = writable.getWriter();
const enc = new TextEncoder();
for (;;) {
// Send 'ping' every second to keep the connection alive
await writer.write(enc.encode("ping\r\n"));
await scheduler.wait(1000);
}
}
```
* TypeScript
```ts
export default {
async fetch(request, env, ctx): Promise {
// This sets up an event listener that will be called if the client disconnects from your
// worker.
request.signal.addEventListener('abort', () => {
console.log('The request was aborted!');
});
const { readable, writable } = new IdentityTransformStream();
sendPing(writable);
return new Response(readable, { headers: { 'Content-Type': 'text/plain' } });
},
} satisfies ExportedHandler;
async function sendPing(writable: WritableStream): Promise {
const writer = writable.getWriter();
const enc = new TextEncoder();
for (;;) {
// Send 'ping' every second to keep the connection alive
await writer.write(enc.encode('ping\r\n'));
await scheduler.wait(1000);
}
}
```
For more information see the [`Request` documentation](https://developers.cloudflare.com/workers/runtime-apis/request).
---
title: WARP client for Linux (version 2025.4.943.0) · Changelog
description: WARP client for Linux (version 2025.4.943.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-22-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-05-22-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.4.943.0)
May 22, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for [managed networks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/managed-networks/) for the 2025.4.929.0 release.
**Changes and improvements**
* Fixed an issue where it could take up to 3 minutes for the correct device profile to be applied in some circumstances. In the worst case, it should now only take up to 40 seconds. This will be improved further in a future release.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for macOS (version 2025.4.943.0) · Changelog
description: WARP client for macOS (version 2025.4.943.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-22-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-05-22-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.4.943.0)
May 22, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for [managed networks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/managed-networks/) for the 2025.4.929.0 release.
**Changes and improvements**
* Fixed an issue where it could take up to 3 minutes for the correct device profile to be applied in some circumstances. In the worst case, it should now only take up to 40 seconds. This will be improved further in a future release.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
---
title: WARP client for Windows (version 2025.4.943.0) · Changelog
description: WARP client for Windows (version 2025.4.943.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-22-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-05-22-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.4.943.0)
May 22, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for [managed networks](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/managed-networks/) for the 2025.4.929.0 release.
**Changes and improvements**
* Fixed an issue where it could take up to 3 minutes for the correct device profile to be applied in some circumstances. In the worst case, it should now only take up to 40 seconds. This will be improved further in a future release.
**Known issues**
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
---
title: New GraphQL Analytics API Explorer and MCP Server · Changelog
description: Easily explore, build, and run GraphQL queries with two new tools
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-23-graphql-api-explorer/
md: https://developers.cloudflare.com/changelog/2025-05-23-graphql-api-explorer/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New GraphQL Analytics API Explorer and MCP Server
May 23, 2025
[Analytics](https://developers.cloudflare.com/analytics/)
We’ve launched two powerful new tools to make the GraphQL Analytics API more accessible:
#### GraphQL API Explorer
The new [GraphQL API Explorer](https://graphql.cloudflare.com/explorer) helps you build, test, and run queries directly in your browser. Features include:
* In-browser schema documentation to browse available datasets and fields
* Interactive query editor with autocomplete and inline documentation
* A "Run in GraphQL API Explorer" button to execute example queries from our docs
* Seamless OAuth authentication — no manual setup required

#### GraphQL Model Context Protocol (MCP) Server
MCP Servers let you use natural language tools like Claude to generate structured queries against your data. See our [blog post](https://blog.cloudflare.com/thirteen-new-mcp-servers-from-cloudflare/) for details on how they work and which servers are available. The new [GraphQL MCP server](https://github.com/cloudflare/mcp-server-cloudflare/tree/main/apps/graphql) helps you discover and generate useful queries for the GraphQL Analytics API. With this server, you can:
* Explore what data is available to query
* Generate and refine queries using natural language, with one-click links to run them in the API Explorer
* Build dashboards and visualizations from structured query outputs
Example prompts include:
* “Show me HTTP traffic for the last 7 days for example.com”
* “What GraphQL node returns firewall events?”
* “Can you generate a link to the Cloudflare GraphQL API Explorer with a pre-populated query and variables?”
We’re continuing to expand these tools, and your feedback helps shape what’s next. [Explore the documentation](https://developers.cloudflare.com/analytics/graphql-api/) to learn more and get started.
---
title: Gateway Protocol Detection Now Available for PAYGO and Free Plans · Changelog
description: Gateway protocol detection is now available on customer plan types!
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-27-protocol-detection-availability/
md: https://developers.cloudflare.com/changelog/2025-05-27-protocol-detection-availability/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Gateway Protocol Detection Now Available for PAYGO and Free Plans
May 27, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
All Cloudflare One Gateway users can now use Protocol detection logging and filtering, including those on Pay-as-you-go and Free plans.
With Protocol Detection, admins can identify and enforce policies on traffic proxied through Gateway based on the underlying network protocol (for example, HTTP, TLS, or SSH), enabling more granular traffic control and security visibility no matter your plan tier.
This feature is available to enable in your account network settings for all accounts. For more information on using Protocol Detection, refer to the [Protocol detection documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/protocol-detection/).
---
title: WAF Release - 2025-05-27 · Changelog
description: Cloudflare WAF managed rulesets 2025-05-27 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-27-waf-release/
md: https://developers.cloudflare.com/changelog/2025-05-27-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-05-27
May 27, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s roundup covers nine vulnerabilities, including six critical RCEs and one dangerous file upload. Affected platforms span cloud services, CI/CD pipelines, CMSs, and enterprise backup systems. Several are now addressed by updated WAF managed rulesets.
**Key Findings**
* Ingress-Nginx (CVE-2025-1098): Unauthenticated RCE via unsafe annotation handling. Impacts Kubernetes clusters.
* GitHub Actions (CVE-2025-30066): RCE through malicious workflow inputs. Targets CI/CD pipelines.
* Craft CMS (CVE-2025-32432): Template injection enables unauthenticated RCE. High risk to content-heavy sites.
* F5 BIG-IP (CVE-2025-31644): RCE via TMUI exploit, allowing full system compromise.
* AJ-Report (CVE-2024-15077): RCE through untrusted template execution. Affects reporting dashboards.
* NAKIVO Backup (CVE-2024-48248): RCE via insecure script injection. High-value target for ransomware.
* SAP NetWeaver (CVE-2025-31324): Dangerous file upload flaw enables remote shell deployment.
* Ivanti EPMM (CVE-2025-4428, 4427): Auth bypass allows full access to mobile device management.
* Vercel (CVE-2025-32421): Information leak via misconfigured APIs. Useful for attacker recon.
**Impact**
These vulnerabilities expose critical components across Kubernetes, CI/CD pipelines, and enterprise systems to severe threats including unauthenticated remote code execution, authentication bypass, and information leaks. High-impact flaws in Ingress-Nginx, Craft CMS, F5 BIG-IP, and NAKIVO Backup enable full system compromise, while SAP NetWeaver and AJ-Report allow remote shell deployment and template-based attacks. Ivanti EPMM’s auth bypass further risks unauthorized control over mobile device fleets.
GitHub Actions and Vercel introduce supply chain and reconnaissance risks, allowing malicious workflow inputs and data exposure that aid in targeted exploitation. Organizations should prioritize immediate patching, enhance monitoring, and deploy updated WAF and IDS signatures to defend against likely active exploitation.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 6a61a14f44af4232a44e45aad127592a | 100746 | Vercel - Information Disclosure | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | bd30b3c43eb44335ab6013c195442495 | 100754 | AJ-Report - Remote Code Execution - CVE:CVE-2024-15077 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 6a13bd6e5fc94b1d9c97eb87dfee7ae4 | 100756 | NAKIVO Backup - Remote Code Execution - CVE:CVE-2024-48248 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | a4af6f2f15c9483fa9eab01d1c52f6d0 | 100757 | Ingress-Nginx - Remote Code Execution - CVE:CVE-2025-1098 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | bd30b3c43eb44335ab6013c195442495 | 100759 | SAP NetWeaver - Dangerous File Upload - CVE:CVE-2025-31324 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | dab2df4f548349e3926fee845366ccc1 | 100760 | Craft CMS - Remote Code Execution - CVE:CVE-2025-32432 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 5eb23f172ed64ee08895e161eb40686b | 100761 | GitHub Action - Remote Code Execution - CVE:CVE-2025-30066 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 827037f2d5f941789efcba6260fc041c | 100762 | Ivanti EPMM - Auth Bypass - CVE:CVE-2025-4428, CVE:CVE-2025-4427 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | ddee6d1c4f364768b324609cebafdfe6 | 100763 | F5 Big IP - Remote Code Execution - CVE:CVE-2025-31644 | Log | Disabled | This is a New Detection |
---
title: Playwright MCP server is now compatible with Browser Rendering · Changelog
description: You can now deploy Playwright MCP and use any MCP client to get AI
models to interact with Browser Rendering
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-28-playwright-mcp/
md: https://developers.cloudflare.com/changelog/2025-05-28-playwright-mcp/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Playwright MCP server is now compatible with Browser Rendering
May 28, 2025
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We're excited to share that you can now use the [Playwright MCP](https://github.com/cloudflare/playwright-mcp) server with Browser Rendering.
Once you [deploy the server](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/#deploying), you can use any MCP client with it to interact with Browser Rendering. This allows you to run AI models that can automate browser tasks, such as taking screenshots, filling out forms, or scraping data.

Playwright MCP is available as an npm package at [`@cloudflare/playwright-mcp`](https://www.npmjs.com/package/@cloudflare/playwright-mcp). To install it, type:
* npm
```sh
npm i -D @cloudflare/playwright-mcp
```
* yarn
```sh
yarn add -D @cloudflare/playwright-mcp
```
* pnpm
```sh
pnpm add -D @cloudflare/playwright-mcp
```
Deploying the server is then as easy as:
```ts
import { env } from "cloudflare:workers";
import { createMcpAgent } from "@cloudflare/playwright-mcp";
export const PlaywrightMCP = createMcpAgent(env.BROWSER);
export default PlaywrightMCP.mount("/sse");
```
Check out the full code at [GitHub](https://github.com/cloudflare/playwright-mcp).
Learn more about Playwright MCP in our [documentation](https://developers.cloudflare.com/browser-rendering/playwright/playwright-mcp/).
---
title: Updated attack score model · Changelog
description: An updated attack score model for Cloudflare WAF to reduce false positives.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-28-updated-attack-score-model/
md: https://developers.cloudflare.com/changelog/2025-05-28-updated-attack-score-model/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Updated attack score model
May 28, 2025
[WAF](https://developers.cloudflare.com/waf/)
We have deployed an updated attack score model focused on enhancing the detection of multiple false positives (FPs).
As a result of this improvement, some changes in observed attack scores are expected.
---
title: Fine-tune image optimization — WebP now supported in Configuration Rules
· Changelog
description: Configuration Rules now let you selectively enable or disable
Polish with WebP format for precise control over image optimization.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-30-configuration-rules-webp/
md: https://developers.cloudflare.com/changelog/2025-05-30-configuration-rules-webp/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Fine-tune image optimization — WebP now supported in Configuration Rules
May 30, 2025
[Rules](https://developers.cloudflare.com/rules/)
You can now enable [Polish](https://developers.cloudflare.com/images/polish/activate-polish/) with the `webp` format directly in [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/), allowing you to optimize image delivery for specific routes, user agents, or A/B tests — without applying changes zone-wide.
**What’s new:**
* [WebP](https://developers.cloudflare.com/images/polish/compression/#webp) is now a supported [value](https://developers.cloudflare.com/rules/configuration-rules/settings/#polish) in the **Polish** setting for Configuration Rules.
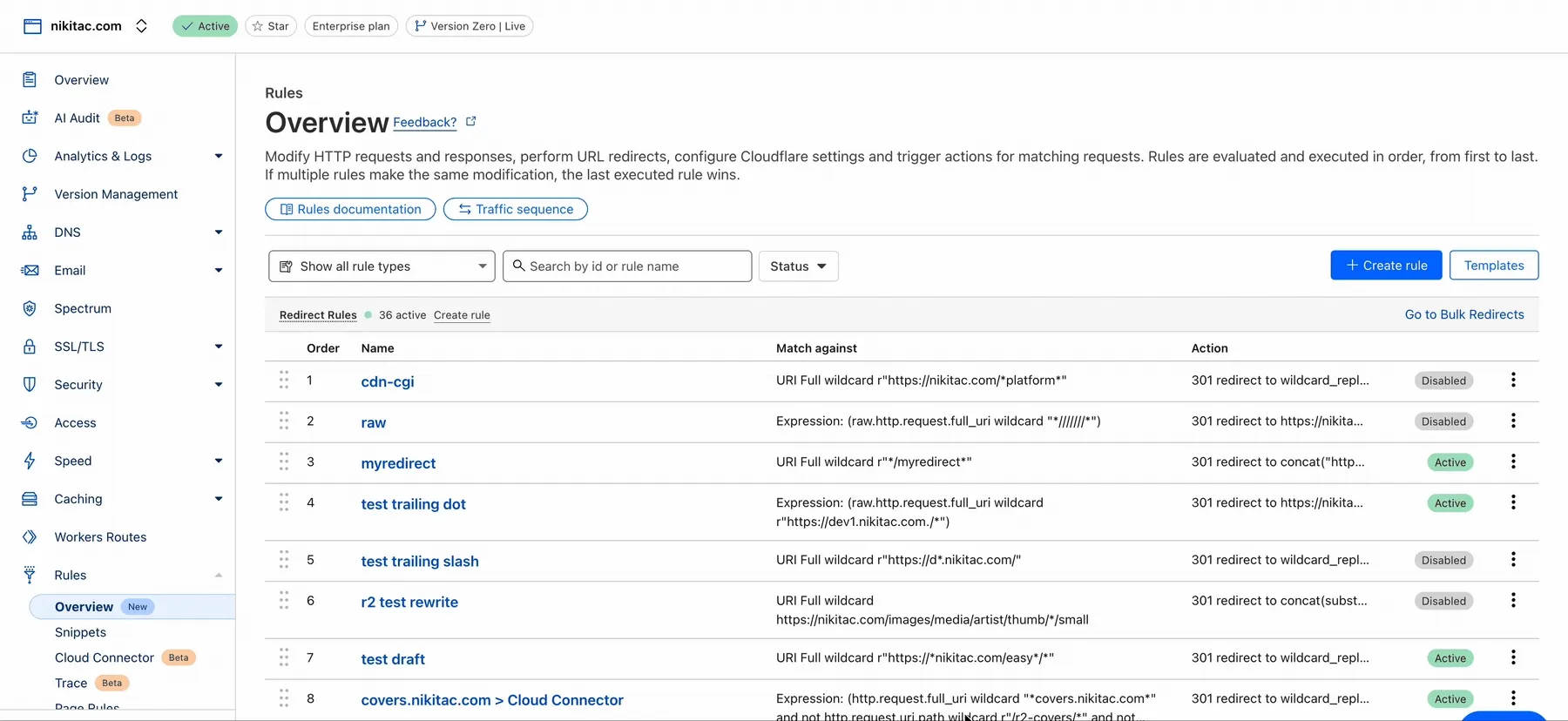
This gives you more precise control over how images are compressed and delivered, whether you're targeting modern browsers, running experiments, or tailoring performance by geography or device type.
Learn more in the [Polish](https://developers.cloudflare.com/images/polish/) and [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/) documentation.
---
title: 50-500ms Faster D1 REST API Requests · Changelog
description: D1 REST API request latency improvements.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-30-d1-rest-api-latency/
md: https://developers.cloudflare.com/changelog/2025-05-30-d1-rest-api-latency/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## 50-500ms Faster D1 REST API Requests
May 29, 2025
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
Users using Cloudflare's [REST API](https://developers.cloudflare.com/api/resources/d1/) to query their D1 database can see lower end-to-end request latency now that D1 authentication is performed at the closest Cloudflare network data center that received the request. Previously, authentication required D1 REST API requests to proxy to Cloudflare's core, centralized data centers, which added network round trips and latency.
Latency improvements range from 50-500 ms depending on request location and [database location](https://developers.cloudflare.com/d1/configuration/data-location/) and only apply to the REST API. REST API requests and databases outside the United States see a bigger benefit since Cloudflare's primary core data centers reside in the United States.
D1 query endpoints like `/query` and `/raw` have the most noticeable improvements since they no longer access Cloudflare's core data centers. D1 control plane endpoints such as those to create and delete databases see smaller improvements, since they still require access to Cloudflare's core data centers for other control plane metadata.
---
title: Cloudflare Pages builds now provide Node.js v22 by default · Changelog
description: A new V3 build image for Cloudflare Pages includes Node.js v22 as
the default version
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-05-30-pages-build-image-v3/
md: https://developers.cloudflare.com/changelog/2025-05-30-pages-build-image-v3/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Pages builds now provide Node.js v22 by default
May 30, 2025
[Pages](https://developers.cloudflare.com/pages/)
When you use the built-in build system that is part of [Cloudflare Pages](https://developers.cloudflare.com/pages/), the [Build Image](https://developers.cloudflare.com/pages/configuration/build-image/) now includes Node.js v22. Previously, Node.js v18 was provided by default, and Node.js v18 is now end-of-life (EOL).
If you are creating a new Pages project, the new V3 build image that includes Node.js v22 will be used by default. If you have an existing Pages project, you can update to the latest build image by navigating to Settings > Build & deployments > Build system version in the Cloudflare dashboard for a specific Pages project.
Note that you can always specify a particular version of Node.js or other built-in dependencies by [setting an environment variable](https://developers.cloudflare.com/pages/configuration/build-image/#override-default-versions).
For more, refer to the [developer docs for Cloudflare Pages builds](https://developers.cloudflare.com/pages/configuration/build-image)
---
title: Cloudflare User Groups & Enhanced Permission Policies are now in Beta ·
Changelog
description: Simplifying the management of users, groups, and permissions within Cloudflare.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-02-user-groups-beta/
md: https://developers.cloudflare.com/changelog/2025-06-02-user-groups-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare User Groups & Enhanced Permission Policies are now in Beta
Jun 02, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
We're excited to announce the Public Beta launch of **User Groups for Cloudflare Dashboard** and **System for Cross Domain Identity Management (SCIM) User Groups**, expanding our RBAC capabilities to simplify user and group management at scale.
We've also visually overhauled the **Permission Policies UI** to make defining permissions more intuitive.
**What's New**
**User Groups \[BETA]**: [User Groups](https://developers.cloudflare.com/fundamentals/manage-members/user-groups/) are a new Cloudflare IAM primitive that enable administrators to create collections of account members that are treated equally from an access control perspective. User Groups can be assigned permission policies, with individual members in the group inheriting all permissions granted to the User Group. User Groups can be created manually or via our APIs.
**SCIM User Groups \[BETA]**: Centralize & simplify your user and group management at scale by syncing memberships directly from your upstream identity provider (like Okta or Entra ID) to the Cloudflare Platform. This ensures Cloudflare stays in sync with your identity provider, letting you apply Permission Policies to those synced groups directly within the Cloudflare Dashboard.
Note
SCIM Virtual Groups (identified by the pattern `CF--` in your IdP) are deprecated as of 06/02/25. We recommend migrating SCIM Virtual Groups implementations to use [SCIM User Groups](https://developers.cloudflare.com/fundamentals/account/account-security/scim-setup/). If you did not use Virtual Groups, no action is needed.
**Revamped Permission Policies UI \[BETA]**: As Cloudflare's services have grown, so has the need for precise, role-based access control. We've given the Permission Policies builder a visual overhaul to make it much easier for administrators to find and define the exact permissions they want for specific principals.
Note
When opting into the Beta for User Groups and Permission Policies, you'll be transitioning to a new experience. Please be aware that opting out isn't currently available.
For more info:
* [Get started with User Groups](https://developers.cloudflare.com/fundamentals/manage-members/user-groups/)
* [Explore our SCIM integration guide](https://developers.cloudflare.com/fundamentals/account/account-security/scim-setup/)
---
title: WAF Release - 2025-06-02 · Changelog
description: Cloudflare WAF managed rulesets 2025-06-02 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-02-waf-release/
md: https://developers.cloudflare.com/changelog/2025-06-02-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-06-02
Jun 02, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s roundup highlights five high-risk vulnerabilities affecting SD-WAN, load balancers, and AI platforms. Several flaws enable unauthenticated remote code execution or authentication bypass.
**Key Findings**
* Versa Concerto SD-WAN (CVE-2025-34026, CVE-2025-34027): Authentication bypass vulnerabilities allow attackers to gain unauthorized access to SD-WAN management interfaces, compromising network segmentation and control.
* Kemp LoadMaster (CVE-2024-7591): Remote Code Execution vulnerability enables attackers to execute arbitrary commands, potentially leading to full device compromise within enterprise load balancing environments.
* AnythingLLM (CVE-2024-0759): Server-Side Request Forgery (SSRF) flaw allows external attackers to force the LLM backend to make unauthorized internal network requests, potentially exposing sensitive internal resources.
* Anyscale Ray (CVE-2023-48022): Remote Code Execution vulnerability affecting distributed AI workloads, allowing attackers to execute arbitrary code on Ray cluster nodes.
* Server-Side Request Forgery (SSRF) - Generic & Obfuscated Payloads: Ongoing advancements in SSRF payload techniques observed, including obfuscation and expanded targeting of cloud metadata services and internal IP ranges.
**Impact**
These vulnerabilities expose critical infrastructure across networking, AI platforms, and SaaS integrations. Unauthenticated RCE and auth bypass flaws in Versa Concerto, Kemp LoadMaster, and Anyscale Ray allow full system compromise. AnythingLLM and SSRF payload variants expand attack surfaces into internal cloud resources, sensitive APIs, and metadata services, increasing risk of privilege escalation, data theft, and persistent access.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 752cfb5e6f9c46f0953c742139b52f02 | 100764 | Versa Concerto SD-WAN - Auth Bypass - CVE:CVE-2025-34027 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | a01171de18034901b48a5549a34edb97 | 100765 | Versa Concerto SD-WAN - Auth Bypass - CVE:CVE-2025-34026 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 840b35492a7543c18ffe50fc0d99b2db | 100766 | Kemp LoadMaster - Remote Code Execution - CVE:CVE-2024-7591 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 121b7070de3a459dbe80d7ed95aa3a4f | 100767 | AnythingLLM - SSRF - CVE:CVE-2024-0759 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 215417f989e2485a9c50eca0840a0966 | 100768 | Anyscale Ray - Remote Code Execution - CVE:CVE-2023-48022 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 3ed619a17d4141bda3a8c3869d16ee18 | 100781 | SSRF - Generic Payloads | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 7ce73f6a70be49f8944737465c963d9d | 100782 | SSRF - Obfuscated Payloads | N/A | Disabled | This is a New Detection |
---
title: AI Gateway adds OpenAI compatible endpoint · Changelog
description: AI Gateway has added OpenAI compatibility
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-03-aig-openai-compatible-endpoint/
md: https://developers.cloudflare.com/changelog/2025-06-03-aig-openai-compatible-endpoint/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Gateway adds OpenAI compatible endpoint
Jun 03, 2025
[AI Gateway](https://developers.cloudflare.com/ai-gateway/)
Users can now use an [OpenAI Compatible endpoint](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) in AI Gateway to easily switch between providers, while keeping the exact same request and response formats. We're launching now with the chat completions endpoint, with the embeddings endpoint coming up next.
To get started, use the OpenAI compatible chat completions endpoint URL with your own account id and gateway id and switch between providers by changing the `model` and `apiKey` parameters.
```js
import OpenAI from "openai";
const client = new OpenAI({
apiKey: "YOUR_PROVIDER_API_KEY", // Provider API key
baseURL:
"https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/compat",
});
const response = await client.chat.completions.create({
model: "google-ai-studio/gemini-2.0-flash",
messages: [{ role: "user", content: "What is Cloudflare?" }],
});
console.log(response.choices[0].message.content);
```
Additionally, the [OpenAI Compatible endpoint](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) can be combined with our [Universal Endpoint](https://developers.cloudflare.com/ai-gateway/usage/universal/) to add fallbacks across multiple providers. That means AI Gateway will return every response in the same standardized format, no extra parsing logic required!
Learn more in the [OpenAI Compatibility](https://developers.cloudflare.com/ai-gateway/usage/chat-completion/) documentation.
---
title: Improved onboarding for Shopify merchants · Changelog
description: Shopify merchants can easily set up Orange-to-Orange (O2O).
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-03-shopify-o2o-improvements/
md: https://developers.cloudflare.com/changelog/2025-06-03-shopify-o2o-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved onboarding for Shopify merchants
Jun 03, 2025
[DNS](https://developers.cloudflare.com/dns/)
Shopify merchants can now onboard to **Orange-to-Orange (O2O)** automatically, without needing to contact support or community members.
What's new:
* **Automatic enablement** – O2O is available for all mutual Cloudflare and Shopify customers.
* **Branded record display** – Merchants see a Shopify logo in DNS records, complete with helpful tooltips.

* **Checkout protection** – Workers and Snippets are blocked from running on the checkout path to reduce risk and improve security.
For more information, refer to the [provider guide](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/saas-customers/provider-guides/shopify/).
---
title: View an architecture diagram of your Worker directly in the Cloudflare
dashboard · Changelog
description: Explore and modify your Workers' architecture directly in the
Cloudflare dashboard
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-03-visualize-your-worker-architecture/
md: https://developers.cloudflare.com/changelog/2025-06-03-visualize-your-worker-architecture/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## View an architecture diagram of your Worker directly in the Cloudflare dashboard
Jun 03, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now visualize, explore and modify your Worker’s architecture directly in the Cloudflare dashboard, making it easier to understand how your application connects to Cloudflare resources like [D1 databases](https://developers.cloudflare.com/d1), [Durable Objects](https://developers.cloudflare.com/durable-objects), [KV namespaces](https://developers.cloudflare.com/kv), and [more](https://developers.cloudflare.com/workers/runtime-apis/bindings/).
With this new view, you can easily:
* Explore existing bindings in a visual, architecture-style diagram
* Add and manage bindings directly from the same interface
* Discover the full range of compute, storage, AI, and media resources you can attach to your Workers application.
To get started, head to the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/workers-and-pages) and open the **Bindings** tab of any Workers application.
---
title: New Account-Level Load Balancing UI and Private Load Balancers · Changelog
description: You can now manage all of your load balancers in one place with the
new Load Balancing UI.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-04-account-load-balancing-ui/
md: https://developers.cloudflare.com/changelog/2025-06-04-account-load-balancing-ui/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Account-Level Load Balancing UI and Private Load Balancers
Jun 04, 2025
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
We've made two large changes to load balancing:
* Redesigned the user interface, now centralized at the **account level**.
* Introduced [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to the UI, enabling you to manage traffic for all of your external and internal applications in a single spot.
This update streamlines how you manage load balancers across multiple zones and extends robust traffic management to your private network infrastructure.

**Key Enhancements:**
* **Account-Level UI Consolidation:**
* **Unified Management:** Say goodbye to navigating individual zones for load balancing tasks. You can now view, configure, and monitor all your load balancers across every zone in your account from a single, intuitive interface at the account level.
* **Improved Efficiency:** This centralized approach provides a more streamlined workflow, making it faster and easier to manage both your public-facing and internal traffic distribution.
* **Private Network Load Balancing:**
* **Secure Internal Application Access:** Create [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to distribute traffic to applications hosted within your private network, ensuring they are not exposed to the public Internet.
* **WARP & Magic WAN Integration:** Effortlessly direct internal traffic from users connected via Cloudflare WARP or through your Magic WAN infrastructure to the appropriate internal endpoint pools.
* **Enhanced Security for Internal Resources:** Combine reliable Load Balancing with Zero Trust access controls to ensure your internal services are both performant and only accessible by verified users.

---
title: Performance and size optimization for the Cloudflare adapter for Open
Next · Changelog
description: Update to the latest version of `@opennextjs/cloudflare` to
automatically benefit from these improvements.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-05-open-next-size/
md: https://developers.cloudflare.com/changelog/2025-06-05-open-next-size/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Performance and size optimization for the Cloudflare adapter for Open Next
Jun 05, 2025
[Workers](https://developers.cloudflare.com/workers/)
With the release of the Cloudflare adapter for Open Next v1.0.0 in May 2025, we already had followups plans [to improve performance and size](https://blog.cloudflare.com/deploying-nextjs-apps-to-cloudflare-workers-with-the-opennext-adapter/#1-0-and-the-road-ahead).
`@opennextjs/cloudflare` v1.2 released on June 5, 2025 delivers on these enhancements. By removing `babel` from the app code and dropping a dependency on `@ampproject/toolbox-optimizer`, we were able to reduce generated bundle sizes. Additionally, by stopping preloading of all app routes, we were able to improve the cold start time.
This means that users will now see a decrease from 14 to 8MiB (2.3 to 1.6MiB gzipped) in generated bundle size for a Next app created via create-next-app, and typically 100ms faster startup times for their medium-sized apps.
Users only need to update to the latest version of `@opennextjs/cloudflare` to automatically benefit from these improvements.
Note that we published [CVE-2005-6087](https://github.com/opennextjs/opennextjs-cloudflare/security/advisories/GHSA-rvpw-p7vw-wj3m) for a SSRF vulnerability in the `@opennextjs/cloudflare` package. The vulnerability has been fixed from `@opennextjs/cloudflare` v1.3.0 onwards. Please update to any version after this one.
---
title: WARP client for macOS (version 2025.5.735.1) · Changelog
description: WARP client for macOS (version 2025.5.735.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-05-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-06-05-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.5.735.1)
Jun 05, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed an issue where the Cloudflare WARP application may not have automatically relaunched after an update.
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements including showing connectivity status in the client and sending system notifications for captive portal sign in.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to gracefully handle changes made by MDM while WARP is not running.
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
---
title: WARP client for Windows (version 2025.5.735.1) · Changelog
description: WARP client for Windows (version 2025.5.735.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-05-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-06-05-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.5.735.1)
Jun 05, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains improvements and new exciting features, including [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) and [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements including showing connectivity status in the client and sending system notifications for captive portal sign in.
* Fixed a bug where in Gateway with DoH mode, connection to DNS servers was not automatically restored after reconnecting WARP.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to gracefully handle changes made by MDM while WARP is not running.
* Improvement for multi-user mode to avoid unnecessary key rotations when transitioning from a pre-login to a logged-in state.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Added [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) to device profile settings. With SCCM VPN boundary support enabled, operating systems will register WARP's local interface IP with the on-premise DNS server when reachable.
**Known issues**
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected. To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: More flexible fallback handling — Custom Errors now support fetching
assets returned with 4xx or 5xx status codes · Changelog
description: Custom Errors can now fetch and store fallback assets even if the
origin returns a 4xx or 5xx status code.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-09-custom-errors-fetch-4xx-5xx-assets/
md: https://developers.cloudflare.com/changelog/2025-06-09-custom-errors-fetch-4xx-5xx-assets/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## More flexible fallback handling — Custom Errors now support fetching assets returned with 4xx or 5xx status codes
Jun 09, 2025
[Rules](https://developers.cloudflare.com/rules/)
[Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) can now fetch and store [assets](https://developers.cloudflare.com/rules/custom-errors/create-rules/#create-a-custom-error-asset-dashboard) and [error pages](https://developers.cloudflare.com/rules/custom-errors/#error-pages) from your origin even if they are served with a 4xx or 5xx HTTP status code — previously, only 200 OK responses were allowed.
**What’s new:**
* You can now upload error pages and error assets that return error status codes (for example, 403, 500, 502, 503, 504) when fetched.
* These assets are stored and minified at the edge, so they can be reused across multiple Custom Error rules without triggering requests to the origin.
This is especially useful for retrieving error content or downtime banners from your backend when you can’t override the origin status code.
Learn more in the [Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) documentation.
---
title: Match Workers subrequests by upstream zone — cf.worker.upstream_zone now
supported in Transform Rules · Changelog
description: Transform Rules now support the cf.worker.upstream_zone field,
letting you conditionally apply rules based on which zone sent Workers
subrequest.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-09-transform-rule-subrequest-matching/
md: https://developers.cloudflare.com/changelog/2025-06-09-transform-rule-subrequest-matching/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Match Workers subrequests by upstream zone — cf.worker.upstream\_zone now supported in Transform Rules
Jun 09, 2025
[Rules](https://developers.cloudflare.com/rules/)
You can now use the [`cf.worker.upstream_zone`](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/cf.worker.upstream_zone/) field in [Transform Rules](https://developers.cloudflare.com/rules/transform/) to control rule execution based on whether a request originates from [Workers](https://developers.cloudflare.com/workers/), including subrequests issued by Workers in other zones.
**What's new:**
* `cf.worker.upstream_zone` is now supported in Transform Rules expressions.
* Skip or apply logic conditionally when handling [Workers subrequests](https://developers.cloudflare.com/workers/platform/limits/#subrequests).
For example, to add a header when the subrequest comes from another zone:
Text in **Expression Editor** (replace `myappexample.com` with your domain):
```txt
(cf.worker.upstream_zone != "" and cf.worker.upstream_zone != "myappexample.com")
```
Selected operation under **Modify request header**: *Set static*
**Header name**: `X-External-Workers-Subrequest`
**Value**: `1`
This gives you more granular control in how you handle incoming requests for your zone.
Learn more in the [Transform Rules](https://developers.cloudflare.com/rules/transform/) documentation and [Rules language fields](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/) reference.
---
title: WAF Release - 2025-06-09 · Changelog
description: Cloudflare WAF managed rulesets 2025-06-09 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-09-waf-release/
md: https://developers.cloudflare.com/changelog/2025-06-09-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-06-09
Jun 09, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s update spotlights four critical vulnerabilities across CMS platforms, VoIP systems, and enterprise applications. Several flaws enable remote code execution or privilege escalation, posing significant enterprise risks.
**Key Findings**
* WordPress OttoKit Plugin (CVE-2025-27007): Privilege escalation flaw allows unauthenticated attackers to create or elevate user accounts, compromising WordPress administrative control.
* SAP NetWeaver (CVE-2025-42999): Remote Code Execution vulnerability enables attackers to execute arbitrary code on SAP NetWeaver systems, threatening core ERP and business operations.
* Fortinet FortiVoice (CVE-2025-32756): Buffer error vulnerability may lead to memory corruption and potential code execution, directly impacting enterprise VoIP infrastructure.
* Camaleon CMS (CVE-2024-46986): Remote Code Execution vulnerability allows attackers to gain full control over Camaleon CMS installations, exposing hosted content and underlying servers.
**Impact**
These vulnerabilities target widely deployed CMS, ERP, and VoIP systems. RCE flaws in SAP NetWeaver and Camaleon CMS allow full takeover of business-critical applications. Privilege escalation in OttoKit exposes WordPress environments to full administrative compromise. FortiVoice buffer handling issues risk destabilizing or fully compromising enterprise telephony systems.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 4afd50a3ef1948bba87c4e620debd86e | 100769 | WordPress OttoKit Plugin - Privilege Escalation - CVE:CVE-2025-27007 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 24134c41c3e940daa973b4b95f57b448 | 100770 | SAP NetWeaver - Remote Code Execution - CVE:CVE-2025-42999 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 4f219ac0be3545a5be5f0bf34df8857a | 100779 | Fortinet FortiVoice - Buffer Error - CVE:CVE-2025-32756 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | bc8dfbe8cbac4c039725ec743b840107 | 100780 | Camaleon CMS - Remote Code Execution - CVE:CVE-2024-46986 | Log | Block | This is a New Detection |
---
title: Workers native integrations were removed from the Cloudflare dashboard ·
Changelog
description: The Workers native integrations have been removed from the Workers
dashboard. Existing integrations continue to work, and new connections should
be configured using Wrangler secrets or the dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-09-workers-integrations-changes/
md: https://developers.cloudflare.com/changelog/2025-06-09-workers-integrations-changes/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers native integrations were removed from the Cloudflare dashboard
Jun 09, 2025
[Workers](https://developers.cloudflare.com/workers/)
Workers native integrations were [originally launched in May 2023](https://blog.cloudflare.com/announcing-database-integrations/) to connect to popular database and observability providers with your Worker in just a few clicks. We are changing how developers connect Workers to these external services. The **Integrations** tab in the dashboard has been removed in favor of a more direct, command-line-based approach using [Wrangler secrets](https://developers.cloudflare.com/workers/wrangler/commands/#secret).
#### What's changed
* **Integrations tab removed**: The integrations setup flow is no longer available in the Workers dashboard.
* **Manual secret configuration**: New connections should be configured by adding credentials as secrets to your Workers using `npx wrangler secret put` commands.
#### Impact on existing integrations
**Existing integrations will continue to work without any changes required.** If you have integrations that were previously created through the dashboard, they will remain functional.
#### Updating existing integrations
If you'd like to modify your existing integration, you can update the secrets, environment variables, or [Tail Workers](https://developers.cloudflare.com/workers/observability/logs/tail-workers/) that were created from the original integration setup.
* **Update secrets**: Use `npx wrangler secret put ` to update credential values.
* **Modify environment variables**: Update variables through the dashboard or Wrangler configuration.
* **Dashboard management**: Access your Worker's settings in the [Cloudflare dashboard](https://dash.cloudflare.com) to modify connections created by our removed native integrations feature.
If you have previously set up an observability integration with [Sentry](https://sentry.io), the following environment variables were set and are still modifiable:
* `BLOCKED_HEADERS`: headers to exclude sending to Sentry
* `EXCEPTION_SAMPLING_RATE`: number from 0 - 100, where 0 = no events go through to Sentry, and 100 = all events go through to Sentry
* `STATUS_CODES_TO_SAMPLING_RATES`: a map of status codes -- like 400 or with wildcards like 4xx -- to sampling rates described above
#### Setting up new database and observability connections
For new connections, refer to our step-by-step guides on connecting to popular database and observability providers including: [Sentry](https://developers.cloudflare.com/workers/observability/third-party-integrations/sentry), [Turso](https://developers.cloudflare.com/workers/databases/third-party-integrations/turso/), [Neon](https://developers.cloudflare.com/workers/databases/third-party-integrations/neon/), [Supabase](https://developers.cloudflare.com/workers/databases/third-party-integrations/supabase/), [PlanetScale](https://developers.cloudflare.com/workers/databases/third-party-integrations/planetscale/), [Upstash](https://developers.cloudflare.com/workers/databases/third-party-integrations/upstash/), [Xata](https://developers.cloudflare.com/workers/databases/third-party-integrations/xata/).
---
title: Access git commit sha and branch name as environment variables in Workers
Builds · Changelog
description: Workers Builds now automatically injects environment variables
containingGit metadata, including the commit SHA and branch name.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-10-default-env-vars/
md: https://developers.cloudflare.com/changelog/2025-06-10-default-env-vars/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Access git commit sha and branch name as environment variables in Workers Builds
Jun 10, 2025
[Workers](https://developers.cloudflare.com/workers/)
[Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/) connects your Worker to a [Git repository](https://developers.cloudflare.com/workers/ci-cd/builds/git-integration/), and automates building and deploying your code on each pushed change.
To make CI/CD pipelines even more flexible, Workers Builds now automatically injects [default environment variables](https://developers.cloudflare.com/workers/ci-cd/builds/configuration/#environment-variable) into your build process (much like the defaults in [Cloudflare Pages projects](https://developers.cloudflare.com/pages/configuration/build-configuration/#environment-variables)). You can use these variables to customize your build process based on the deployment context, such as the branch or commit.
The following environment variables are injected by default:
| Environment Variable | Injected value | Example use-case |
| - | - | - |
| `CI` | `true` | Changing build behavior when run on CI versus locally |
| `WORKERS_CI` | `1` | Changing build behavior when run on Workers Builds versus locally |
| `WORKERS_CI_BUILD_UUID` | `` | Passing the Build UUID along to custom workflows |
| `WORKERS_CI_COMMIT_SHA` | `` | Passing current commit ID to error reporting, for example, Sentry |
| `WORKERS_CI_BRANCH` | ` **Settings** > **Environment variables**.
Learn more in the [Build configuration documentation](https://developers.cloudflare.com/workers/ci-cd/builds/configuration/#environment-variables).
---
title: Increased limits for Media Transformations · Changelog
description: >
Media Transformations now supports inputs up to 100MB and output videos as
long as 1 minute.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-10-media-transformations-limits-increase/
md: https://developers.cloudflare.com/changelog/2025-06-10-media-transformations-limits-increase/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased limits for Media Transformations
Jun 10, 2025
[Stream](https://developers.cloudflare.com/stream/)
We have increased the limits for [Media Transformations](https://developers.cloudflare.com/stream/transform-videos/):
* Input file size limit is now 100MB (was 40MB)
* Output video duration limit is now 1 minute (was 30 seconds)
Additionally, we have improved caching of the input asset, resulting in fewer requests to origin storage even when transformation options may differ.
For more information, learn about [Transforming Videos](https://developers.cloudflare.com/stream/transform-videos/).
---
title: NSEC3 support for DNSSEC · Changelog
description: Cloudflare DNSSEC supports NSEC3 for proof of non-existence.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-11-nsec3-support/
md: https://developers.cloudflare.com/changelog/2025-06-11-nsec3-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## NSEC3 support for DNSSEC
Jun 11, 2025
[DNS](https://developers.cloudflare.com/dns/)
Enterprise customers can now select NSEC3 as method for proof of non-existence on their zones.
What's new:
* **NSEC3 support for live-signed zones** – For both primary and secondary zones that are configured to be live-signed (also known as "on-the-fly signing"), NSEC3 can now be selected as proof of non-existence.
* **NSEC3 support for pre-signed zones** – Secondary zones that are transferred to Cloudflare in a [pre-signed setup](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/cloudflare-as-secondary/dnssec-for-secondary/#set-up-pre-signed-dnssec) now also support NSEC3 as proof of non-existence.
For more information and how to enable NSEC3, refer to the [NSEC3 documentation](https://developers.cloudflare.com/dns/dnssec/enable-nsec3/).
---
title: Internal DNS (beta) now manageable in the Cloudflare dashboard · Changelog
description: The Internal DNS (beta) is now fully available in the Cloudflare dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-16-internal-dns-beta-ui/
md: https://developers.cloudflare.com/changelog/2025-06-16-internal-dns-beta-ui/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Internal DNS (beta) now manageable in the Cloudflare dashboard
Jun 16, 2025
[DNS](https://developers.cloudflare.com/dns/)
Participating beta testers can now fully configure [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/) directly in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/internal-dns).
#### Internal DNS enables customers to:
* Map internal hostnames to private IPs for services, devices, and applications not exposed to the public Internet
* Resolve internal DNS queries securely through [Cloudflare Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
* Use split-horizon DNS to return different responses based on network context
* Consolidate internal and public DNS zones within a single management platform
#### What’s new in this release:
* Beta participants can now create and manage internal zones and views in the Cloudflare dashboard

Note
The Internal DNS beta is currently only available to Enterprise customers.
To learn more and get started, refer to the [Internal DNS documentation](https://developers.cloudflare.com/dns/internal-dns/).
---
title: WAF Release - 2025-06-16 · Changelog
description: Cloudflare WAF managed rulesets 2025-06-16 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-16-waf-release/
md: https://developers.cloudflare.com/changelog/2025-06-16-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-06-16
Jun 16, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s roundup highlights multiple critical vulnerabilities across popular web frameworks, plugins, and enterprise platforms. The focus lies on remote code execution (RCE), server-side request forgery (SSRF), and insecure file upload vectors that enable full system compromise or data exfiltration.
**Key Findings**
* Cisco IOS XE (CVE-2025-20188): Critical RCE vulnerability enabling unauthenticated attackers to execute arbitrary commands on network infrastructure devices, risking total router compromise.
* Axios (CVE-2024-39338): SSRF flaw impacting server-side request control, allowing attackers to manipulate internal service requests when misconfigured with unsanitized user input.
* vBulletin (CVE-2025-48827, CVE-2025-48828): Two high-impact RCE flaws enabling attackers to remotely execute PHP code, compromising forum installations and underlying web servers.
* Invision Community (CVE-2025-47916): A critical RCE vulnerability allowing authenticated attackers to run arbitrary code in community platforms, threatening data and lateral movement risk.
* CrushFTP (CVE-2025-32102, CVE-2025-32103): SSRF vulnerabilities in upload endpoint processing permit attackers to pivot internal network scans and abuse internal services.
* Roundcube (CVE-2025-49113): RCE via email processing enables attackers to execute code upon viewing a crafted email — particularly dangerous for webmail deployments.
* WooCommerce WordPress Plugin (CVE-2025-47577): Dangerous file upload vulnerability permits unauthenticated users to upload executable payloads, leading to full WordPress site takeover.
* Cross-Site Scripting (XSS) Detection Improvements: Enhanced detection patterns.
**Impact**
These vulnerabilities span core systems — from routers to e-commerce to email. RCE in Cisco IOS XE, Roundcube, and vBulletin poses full system compromise. SSRF in Axios and CrushFTP supports internal pivoting, while WooCommerce’s file upload bug opens doors to mass WordPress exploitation.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 233bcf0ce50f400989a7e44a35fefd53 | 100783 | Cisco IOS XE - Remote Code Execution - CVE:CVE-2025-20188 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 9284e3b1586341acb4591bfd8332af5d | 100784 | Axios - SSRF - CVE:CVE-2024-39338 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 2672b175a25548aa8e0107b12e1648d2 | 100785 | vBulletin - Remote Code Execution - CVE:CVE-2025-48827, CVE:CVE-2025-48828 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | b77a19fb053744b49eacdab00edcf1ef | 100786 | Invision Community - Remote Code Execution - CVE:CVE-2025-47916 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | aec2274743064523a9667248d6f5eb48 | 100791 | CrushFTP - SSRF - CVE:CVE-2025-32102, CVE:CVE-2025-32103 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 7b80e1f5575d4d99bb7d56ae30baa18a | 100792 | Roundcube - Remote Code Execution - CVE:CVE-2025-49113 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 52d76f9394494b0382c7cb00229ba236 | 100793 | XSS - Ontoggle | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | d38e657bd43f4d809c28157dfa338296 | 100794 | WordPress WooCommerce Plugin - Dangerous File Upload - CVE:CVE-2025-47577 | Log | Block | This is a New Detection |
---
title: Grant account members read-only access to the Workers Platform · Changelog
description: You can now grant members of your Cloudflare account read-only
access to the Workers Platform.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-16-workers-platform-admin-role/
md: https://developers.cloudflare.com/changelog/2025-06-16-workers-platform-admin-role/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Grant account members read-only access to the Workers Platform
Jun 16, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now grant members of your Cloudflare account read-only access to the Workers Platform.
The new "Workers Platform (Read-only)" role grants read-only access to all products typically used as part of Cloudflare's Developer Platform, including [Workers](https://developers.cloudflare.com/workers/), [Pages](https://developers.cloudflare.com/pages/), [Durable Objects](https://developers.cloudflare.com/durable-objects/), [KV](https://developers.cloudflare.com/kv/), [R2](https://developers.cloudflare.com/r2/), Zones, [Zone Analytics](https://developers.cloudflare.com/analytics/account-and-zone-analytics/zone-analytics/) and [Page Rules](https://developers.cloudflare.com/rules/). When Cloudflare introduces new products to the Workers platform, we will add additional read-only permissions to this role.
Additionally, the role previously named "Workers Admin" has been renamed to "Workers Platform Admin". This change ensures that the name more accurately reflects the permissions granted — this role has always granted access to more than just Workers — it grants read and write access to the products mentioned above, and similarly, as new products are added to the Workers platform, we will add additional read and write permissions to this role.
You can review the updated roles in the [developer docs](https://developers.cloudflare.com/fundamentals/manage-members/roles/).
---
title: Control which routes invoke your Worker script for Single Page
Applications · Changelog
description: New configuration options for specifying which routes invoke your
Worker script.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-17-advanced-routing/
md: https://developers.cloudflare.com/changelog/2025-06-17-advanced-routing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Control which routes invoke your Worker script for Single Page Applications
Jun 17, 2025
[Workers](https://developers.cloudflare.com/workers/)
For those building [Single Page Applications (SPAs) on Workers](https://developers.cloudflare.com/workers/static-assets/routing/single-page-application/#advanced-routing-control), you can now explicitly define which routes invoke your Worker script in Wrangler configuration. The [`run_worker_first` config option](https://developers.cloudflare.com/workers/static-assets/binding/#run_worker_first) has now been expanded to accept an array of route patterns, allowing you to more granularly specify when your Worker script runs.
**Configuration example:**
* wrangler.jsonc
```jsonc
{
"name": "my-spa-worker",
"compatibility_date": "2026-02-07",
"main": "./src/index.ts",
"assets": {
"directory": "./dist/",
"not_found_handling": "single-page-application",
"binding": "ASSETS",
"run_worker_first": ["/api/*", "!/api/docs/*"]
}
}
```
* wrangler.toml
```toml
name = "my-spa-worker"
compatibility_date = "2026-02-07"
main = "./src/index.ts"
[assets]
directory = "./dist/"
not_found_handling = "single-page-application"
binding = "ASSETS"
run_worker_first = [ "/api/*", "!/api/docs/*" ]
```
This new routing control was done in partnership with our community and customers who provided great feedback on [our public proposal](https://github.com/cloudflare/workers-sdk/discussions/9143). Thank you to everyone who brought forward use-cases and feedback on the design!
#### Prerequisites
To use advanced routing control with `run_worker_first`, you'll need:
* [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/) v4.20.0 and above
* [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/get-started/) v1.7.0 and above
---
title: Gateway will now evaluate Network policies before HTTP policies from July
14th, 2025 · Changelog
description: Gateway Network policies (Layer 4) will be evaluated before HTTP
(Layer 7) policies from July 14th, 2025
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-17-new-order-of-enforcement/
md: https://developers.cloudflare.com/changelog/2025-06-17-new-order-of-enforcement/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Gateway will now evaluate Network policies before HTTP policies from July 14th, 2025
Jun 18, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) will now evaluate [Network (Layer 4) policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/) **before** [HTTP (Layer 7) policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/). This change preserves your existing security posture and does not affect which traffic is filtered — but it may impact how notifications are displayed to end users.
This change will roll out progressively between **July 14–18, 2025**. If you use HTTP policies, we recommend reviewing your configuration ahead of rollout to ensure the user experience remains consistent.
#### Updated order of enforcement
**Previous order:**
1. DNS policies
2. HTTP policies
3. Network policies
**New order:**
1. DNS policies
2. **Network policies**
3. **HTTP policies**
#### Action required: Review your Gateway HTTP policies
This change may affect block notifications. For example:
* You have an **HTTP policy** to block `example.com` and display a block page.
* You also have a **Network policy** to block `example.com` silently (no client notification).
With the new order, the Network policy will trigger first — and the user will no longer see the HTTP block page.
To ensure users still receive a block notification, you can:
* Add a client notification to your Network policy, or
* Use only the HTTP policy for that domain.
***
#### Why we’re making this change
This update is based on user feedback and aims to:
* Create a more intuitive model by evaluating network-level policies before application-level policies.
* Minimize [526 connection errors](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/cloudflare-5xx-errors/error-526/#error-526-in-the-zero-trust-context) by verifying the network path to an origin before attempting to establish a decrypted TLS connection.
***
To learn more, visit the [Gateway order of enforcement documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/order-of-enforcement/).
---
title: SSRF vulnerability in @opennextjs/cloudflare proactively mitigated for
all Cloudflare customers · Changelog
description: Mitigations have been put in place for all existing and future
deployments of sites with the Cloudflare adapter for Open Next in response to
an identified Server-Side Request Forgery (SSRF) vulnerability in the
@opennextjs/cloudflare package
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-17-open-next-ssrf/
md: https://developers.cloudflare.com/changelog/2025-06-17-open-next-ssrf/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## SSRF vulnerability in @opennextjs/cloudflare proactively mitigated for all Cloudflare customers
Jun 17, 2025
[Workers](https://developers.cloudflare.com/workers/)
Mitigations have been put in place for all existing and future deployments of sites with the Cloudflare adapter for Open Next in response to an identified Server-Side Request Forgery (SSRF) vulnerability in the `@opennextjs/cloudflare` package.
The vulnerability stemmed from an unimplemented feature in the Cloudflare adapter for Open Next, which allowed users to proxy arbitrary remote content via the `/_next/image` endpoint.
This issue allowed attackers to load remote resources from arbitrary hosts under the victim site's domain for any site deployed using the Cloudflare adapter for Open Next. For example: `https://victim-site.com/_next/image?url=https://attacker.com`. In this example, attacker-controlled content from `attacker.com` is served through the victim site's domain (`victim-site.com`), violating the same-origin policy and potentially misleading users or other services.
References: ,
#### Impact
* SSRF via unrestricted remote URL loading
* Arbitrary remote content loading
* Potential internal service exposure or phishing risks through domain abuse
#### Mitigation
The following mitigations have been put in place:
**Server side updates** to Cloudflare's platform to restrict the content loaded via the `/_next/image` endpoint to images. The update automatically mitigates the issue for all existing and any future sites deployed to Cloudflare using the affected version of the Cloudflare adapter for Open Next
**Root cause fix:** Pull request [#727](https://github.com/opennextjs/opennextjs-cloudflare/pull/727) to the Cloudflare adapter for Open Next. The patched version of the adapter has been released as `@opennextjs/cloudflare@1.3.0`
**Package dependency update:** Pull request [cloudflare/workers-sdk#9608](https://github.com/cloudflare/workers-sdk/pull/9608) to create-cloudflare (c3) to use the fixed version of the Cloudflare adapter for Open Next. The patched version of create-cloudflare has been published as `create-cloudflare@2.49.3`.
In addition to the automatic mitigation deployed on Cloudflare's platform, we encourage affected users to upgrade to `@opennext/cloudflare` v1.3.0 and use the [`remotePatterns`](https://nextjs.org/docs/pages/api-reference/components/image#remotepatterns) filter in Next config if they need to allow-list external urls with images assets.
---
title: Terraform v5.6.0 now available · Changelog
description: Terraform v5.6.0 fixes a number of known bugs in the v5 Provider
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-17-terraform-v560-provider/
md: https://developers.cloudflare.com/changelog/2025-06-17-terraform-v560-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.6.0 now available
Jun 17, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). Unlike the earlier Terraform providers, v5 is automatically generated based on the OpenAPI Schemas for our REST APIs. Since launch, we have seen an unexpectedly high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by customers. These issues currently impact about 15% of resources. We have been working diligently to address these issues across the company, and have released the v5.6.0 release which includes a number of bug fixes. Please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Broad fixes across resources with recurring diffs, including, but not limited to:
* `cloudflare_zero_trust_access_identity_provider`
* `cloudflare_zone`
* `cloudflare_page_rules` runtime panic when setting `cache_level` to `cache_ttl_by_status`
* Failure to serialize requests in `cloudflare_zero_trust_tunnel_cloudflared_config`
* Undocumented field 'priority' on `zone_lockdown` resource
* Missing importability for `cloudflare_zero_trust_device_default_profile_local_domain_fallback` and `cloudflare_account_subscription`
* New resources:
* `cloudflare_schema_validation_operation_settings`
* `cloudflare_schema_validation_schemas`
* `cloudflare_schema_validation_settings`
* `cloudflare_zero_trust_device_settings`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.6.0) in GitHub.
#### Issues Closed
* [#5098: 500 Server Error on updating 'zero\_trust\_tunnel\_cloudflared\_virtual\_network' Terraform resource](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5098)
* [#5148: cloudflare\_user\_agent\_blocking\_rule doesn’t actually support user agents](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5148)
* [#5472: cloudflare\_zone showing changes in plan after following upgrade steps](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5472)
* [#5508: cloudflare\_zero\_trust\_tunnel\_cloudflared\_config failed to serialize http request](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5508)
* [#5509: cloudflare\_zone: Problematic Terraform behaviour with paused zones](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5509)
* [#5520: Resource 'cloudflare\_magic\_wan\_static\_route' is not working](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5520)
* [#5524: Optional fields cause crash in cloudflare\_zero\_trust\_tunnel\_cloudflared(s) when left null](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5524)
* [#5526: Provider v5 migration issue: no import method for cloudflare\_zero\_trust\_device\_default\_profile\_local\_domain\_fallback](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5526)
* [#5532: cloudflare\_zero\_trust\_access\_identity\_provider detects changes on every plan](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5532)
* [#5561: cloudflare\_zero\_trust\_tunnel\_cloudflared: cannot rotate tunnel secret](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5561)
* [#5569: cloudflare\_zero\_trust\_device\_custom\_profile\_local\_domain\_fallback not allowing multiple DNS Server entries](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5569)
* [#5577: Panic modifying page\_rule resource](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5577)
* [#5653: cloudflare\_zone\_setting resource schema confusion in 5.5.0: value vs enabled](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5653)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
If you are evaluating a move from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: WARP client for macOS (version 2025.5.828.1) · Changelog
description: WARP client for macOS (version 2025.5.828.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-17-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-06-17-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.5.828.1)
Jun 17, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains new improvements in addition to the features and improvements introduced in Beta client version 2025.5.735.1.
**Changes and improvements**
* Improvement for WARP connectivity issues on macOS due to the operating system not accepting DNS server configurations.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
---
title: WARP client for Windows (version 2025.5.828.1) · Changelog
description: WARP client for Windows (version 2025.5.828.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-17-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-06-17-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.5.828.1)
Jun 17, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains new improvements in addition to the features and improvements introduced in Beta client version 2025.5.735.1.
**Changes and improvements**
* Improvement to better handle multi-user fast user switching.
* Fix for an issue causing WARP connectivity to fail without full system reboot.
**Known issues**
* Microsoft has confirmed a regression with Windows 11 starting around 24H2 that may cause performance issues for some users. These performance issues could manifest as mouse lag, audio cracking, or other slowdowns. A fix from Microsoft is expected in early July.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected. To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Automate Worker deployments with a simplified SDK and more reliable
Terraform provider · Changelog
description: Various fixes and improvements have been made to Workers Terraform
resources, SDKs, APIs, and API docs.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-17-workers-terraform-sdk-api-fixes/
md: https://developers.cloudflare.com/changelog/2025-06-17-workers-terraform-sdk-api-fixes/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Automate Worker deployments with a simplified SDK and more reliable Terraform provider
Jun 19, 2025
[D1 ](https://developers.cloudflare.com/d1/)[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
#### Simplified Worker Deployments with our SDKs
We've simplified the programmatic deployment of Workers via our [Cloudflare SDKs](https://developers.cloudflare.com/fundamentals/api/reference/sdks/). This update abstracts away the low-level complexities of the `multipart/form-data` upload process, allowing you to focus on your code while we handle the deployment mechanics.
This new interface is available in:
* [cloudflare-typescript](https://github.com/cloudflare/cloudflare-typescript) (4.4.1)
* [cloudflare-python](https://github.com/cloudflare/cloudflare-python) (4.3.1)
For complete examples, see our guide on [programmatic Worker deployments](https://developers.cloudflare.com/workers/platform/infrastructure-as-code).
#### The Old way: Manual API calls
Previously, deploying a Worker programmatically required manually constructing a `multipart/form-data` HTTP request, packaging your code and a separate `metadata.json` file. This was more complicated and verbose, and prone to formatting errors.
For example, here's how you would upload a Worker script previously with cURL:
```bash
curl https://api.cloudflare.com/client/v4/accounts//workers/scripts/my-hello-world-script \
-X PUT \
-H 'Authorization: Bearer ' \
-F 'metadata={
"main_module": "my-hello-world-script.mjs",
"bindings": [
{
"type": "plain_text",
"name": "MESSAGE",
"text": "Hello World!"
}
],
"compatibility_date": "$today"
};type=application/json' \
-F 'my-hello-world-script.mjs=@-;filename=my-hello-world-script.mjs;type=application/javascript+module' <
#### Terraform provider improvements
We've also made several fixes and enhancements to the [Cloudflare Terraform provider](https://github.com/cloudflare/terraform-provider-cloudflare):
* Fixed the [`cloudflare_workers_script`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_script) resource in Terraform, which previously was producing a diff even when there were no changes. Now, your `terraform plan` outputs will be cleaner and more reliable.
* Fixed the [`cloudflare_workers_for_platforms_dispatch_namespace`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_for_platforms_dispatch_namespace), where the provider would attempt to recreate the namespace on a `terraform apply`. The resource now correctly reads its remote state, ensuring stability for production environments and CI/CD workflows.
* The [`cloudflare_workers_route`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_route) resource now allows for the `script` property to be empty, null, or omitted to indicate that pattern should be negated for all scripts (see routes [docs](https://developers.cloudflare.com/workers/configuration/routing/routes)). You can now reserve a pattern or temporarily disable a Worker on a route without deleting the route definition itself.
* Using `primary_location_hint` in the [`cloudflare_d1_database`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/d1_database) resource will no longer always try to recreate. You can now safely change the location hint for a D1 database without causing a destructive operation.
#### API improvements
We've also properly documented the [Workers Script And Version Settings](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/subresources/script_and_version_settings) in our public OpenAPI spec and SDKs.
---
title: Log Explorer is GA · Changelog
description: Log Explorer is now GA - providing native observability and forensics
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-18-log-explorer-ga/
md: https://developers.cloudflare.com/changelog/2025-06-18-log-explorer-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Log Explorer is GA
Jun 18, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/) is now GA, providing native observability and forensics for traffic flowing through Cloudflare.
Search and analyze your logs, natively in the Cloudflare dashboard. These logs are also stored in Cloudflare's network, eliminating many of the costs associated with other log providers.
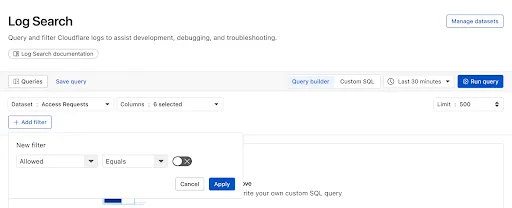
With Log Explorer, you can now:
* **Monitor security and performance issues with custom dashboards** – use natural language to define charts for measuring response time, error rates, top statistics and more.
* **Investigate and troubleshoot issues with Log Search** – use data type-aware search filters or custom sql to investigate detailed logs.
* **Save time and collaborate with saved queries** – save Log Search queries for repeated use or sharing with other users in your account.
* **Access Log Explorer at the account and zone level** – easily find Log Explorer at the account and zone level for querying any dataset.
For help getting started, refer to [our documentation](https://developers.cloudflare.com/log-explorer/).
---
title: Remote bindings public beta - Connect to remote resources (D1, KV, R2,
etc.) during local development · Changelog
description: You can now connect to R2 buckets, D1 databases, and other
resources running on Cloudflare, while running your Worker's code locally, on
your own machine.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-18-remote-bindings-beta/
md: https://developers.cloudflare.com/changelog/2025-06-18-remote-bindings-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Remote bindings public beta - Connect to remote resources (D1, KV, R2, etc.) during local development
Jun 18, 2025
[Workers](https://developers.cloudflare.com/workers/)
Today [we announced the public beta](https://github.com/cloudflare/workers-sdk/discussions/9660) of [remote bindings](https://developers.cloudflare.com/workers/development-testing/#remote-bindings) for local development. With remote bindings, you can now connect to deployed resources like [R2 buckets](https://developers.cloudflare.com/r2/) and [D1 databases](https://developers.cloudflare.com/d1/) while running Worker code on your local machine. This means you can test your local code changes against real data and services, without the overhead of deploying for each iteration.
#### Example configuration
To enable remote mode, add `"experimental_remote" : true` to each binding that you want to rely on a remote resource running on Cloudflare:
* wrangler.jsonc
```jsonc
{
"name": "my-worker",
"compatibility_date": "2026-02-07",
"r2_buckets": [
{
"bucket_name": "screenshots-bucket",
"binding": "screenshots_bucket",
"experimental_remote": true,
},
],
}
```
* wrangler.toml
```toml
name = "my-worker"
compatibility_date = "2026-02-07"
[[r2_buckets]]
bucket_name = "screenshots-bucket"
binding = "screenshots_bucket"
experimental_remote = true
```
When remote bindings are configured, your Worker **still executes locally**, but all binding calls are proxied to the deployed resource that runs on Cloudflare's network.
**You can try out remote bindings for local development today with:**
* [Wrangler v4.20.3](https://developers.cloudflare.com/workers/development-testing/#using-wrangler-with-remote-bindings): Use the `wrangler dev --x-remote-bindings` command.
* The [Cloudflare Vite Plugin](https://developers.cloudflare.com/workers/development-testing/#using-vite-with-remote-bindings): Refer to the documentation for how to enable in your Vite config.
* The [Cloudflare Vitest Plugin](https://developers.cloudflare.com/workers/development-testing/#using-vitest-with-remote-bindings): Refer to the documentation for how to enable in your Vitest config.
**Have feedback?** Join the discussion in our [beta announcement](https://github.com/cloudflare/workers-sdk/discussions/9660) to share feedback or report any issues.
---
title: View custom metadata in responses and guide AI-search with context in
AutoRAG · Changelog
description: You can now view custom metadata in AutoRAG search responses and
use a context field to provide additional guidance to AI-generated answers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-19-autorag-custom-metadata-and-context/
md: https://developers.cloudflare.com/changelog/2025-06-19-autorag-custom-metadata-and-context/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## View custom metadata in responses and guide AI-search with context in AutoRAG
Jun 19, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
In [AutoRAG](https://developers.cloudflare.com/ai-search/), you can now view your object's custom metadata in the response from [`/search`](https://developers.cloudflare.com/ai-search/usage/workers-binding/) and [`/ai-search`](https://developers.cloudflare.com/ai-search/usage/workers-binding/), and optionally add a `context` field in the custom metadata of an object to provide additional guidance for AI-generated answers.
You can add [custom metadata](https://developers.cloudflare.com/r2/api/workers/workers-api-reference/#r2putoptions) to an object when uploading it to your R2 bucket.
#### Object's custom metadata in search responses
When you run a search, AutoRAG now returns any custom metadata associated with the object. This metadata appears in the response inside `attributes` then `file` , and can be used for downstream processing.
For example, the `attributes` section of your search response may look like:
```json
{
"attributes": {
"timestamp": 1750001460000,
"folder": "docs/",
"filename": "launch-checklist.md",
"file": {
"url": "https://wiki.company.com/docs/launch-checklist",
"context": "A checklist for internal launch readiness, including legal, engineering, and marketing steps."
}
}
}
```
#### Add a `context` field to guide LLM answers
When you include a custom metadata field named `context`, AutoRAG attaches that value to each chunk of the file. When you run an `/ai-search` query, this `context` is passed to the LLM and can be used as additional input when generating an answer.
We recommend using the `context` field to describe supplemental information you want the LLM to consider, such as a summary of the document or a source URL. If you have several different metadata attributes, you can join them together however you choose within the `context` string.
For example:
```json
{
"context": "summary: 'Checklist for internal product launch readiness, including legal, engineering, and marketing steps.'; url: 'https://wiki.company.com/docs/launch-checklist'"
}
```
This gives you more control over how your content is interpreted, without requiring you to modify the original contents of the file.
Learn more in AutoRAG's [metadata filtering documentation](https://developers.cloudflare.com/ai-search/configuration/metadata).
---
title: Filter your AutoRAG search by file name · Changelog
description: You can now filter AutoRAG search queries by file name, allowing
you to control which files can be retrieved for a given query.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-19-autorag-filename-filter/
md: https://developers.cloudflare.com/changelog/2025-06-19-autorag-filename-filter/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Filter your AutoRAG search by file name
Jun 19, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
In [AutoRAG](https://developers.cloudflare.com/ai-search/), you can now [filter](https://developers.cloudflare.com/ai-search/configuration/metadata/) by an object's file name using the `filename` attribute, giving you more control over which files are searched for a given query.
This is useful when your application has already determined which files should be searched. For example, you might query a PostgreSQL database to get a list of files a user has access to based on their permissions, and then use that list to limit what AutoRAG retrieves.
For example, your search query may look like:
```js
const response = await env.AI.autorag("my-autorag").search({
query: "what is the project deadline?",
filters: {
type: "eq",
key: "filename",
value: "project-alpha-roadmap.md",
},
});
```
This allows you to connect your application logic with AutoRAG's retrieval process, making it easy to control what gets searched without needing to reindex or modify your data.
Learn more in AutoRAG's [metadata filtering documentation](https://developers.cloudflare.com/ai-search/configuration/metadata/).
---
title: Increased blob size limits in Workers Analytics Engine · Changelog
description: We’ve increased the total allowed size of blob fields per request
from 5 KB to 16 KB in the Workers Analytics Engine.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-20-increased-blob-size-limits-in-workers-analytics/
md: https://developers.cloudflare.com/changelog/2025-06-20-increased-blob-size-limits-in-workers-analytics/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased blob size limits in Workers Analytics Engine
Jun 20, 2025
[Workers](https://developers.cloudflare.com/workers/)
We’ve increased the total allowed size of [`blob`](https://developers.cloudflare.com/analytics/analytics-engine/get-started/#2-write-data-points-from-your-worker) fields on data points written to [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/) from **5 KB to 16 KB**.
This change gives you more flexibility when logging rich observability data — such as base64-encoded payloads, AI inference traces, or custom metadata — without hitting request size limits.
You can find full details on limits for queries, filters, payloads, and more [here in the Workers Analytics Engine limits documentation](https://developers.cloudflare.com/analytics/analytics-engine/limits/).
* JavaScript
```js
export default {
async fetch(request, env) {
env.analyticsDataset.writeDataPoint({
// The sum of all of the blob's sizes can now be 16 KB
blobs: [
// The URL of the request to the Worker
request.url,
// Some metadata about your application you'd like to store
JSON.stringify(metadata),
// The version of your Worker this datapoint was collected from
env.versionMetadata.tag,
],
indexes: ["sample-index"],
});
},
};
```
* TypeScript
```ts
export default {
async fetch(request, env) {
env.analyticsDataset.writeDataPoint({
// The sum of all of the blob's sizes can now be 16 KB
blobs: [
// The URL of the request to the Worker
request.url,
// Some metadata about your application you'd like to store
JSON.stringify(metadata),
// The version of your Worker this datapoint was collected from
env.versionMetadata.tag,
],
indexes: ["sample-index"],
});
}
};
```
---
title: Account-level DNS analytics now available via GraphQL Analytics API · Changelog
description: Authoritative DNS analytics can now be accessed on the account
level via the GraphQL Analytics API.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-23-account-level-dns-analytics-api/
md: https://developers.cloudflare.com/changelog/2025-06-23-account-level-dns-analytics-api/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Account-level DNS analytics now available via GraphQL Analytics API
Jun 19, 2025
[DNS](https://developers.cloudflare.com/dns/)
Authoritative DNS analytics are now available on the **account level** via the [Cloudflare GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/).
This allows users to query DNS analytics across multiple zones in their account, by using the `accounts` filter.
Here is an example to retrieve the most recent DNS queries across all zones in your account that resulted in an `NXDOMAIN` response over a given time frame. Please replace `a30f822fcd7c401984bf85d8f2a5111c` with your actual account ID.
```graphql
query GetLatestNXDOMAINResponses {
viewer {
accounts(filter: { accountTag: "a30f822fcd7c401984bf85d8f2a5111c" }) {
dnsAnalyticsAdaptive(
filter: {
date_geq: "2025-06-16"
date_leq: "2025-06-18"
responseCode: "NXDOMAIN"
}
limit: 10000
orderBy: [datetime_DESC]
) {
zoneTag
queryName
responseCode
queryType
datetime
}
}
}
}
```
[Run in GraphQL API Explorer](https://graphql.cloudflare.com/explorer?query=I4VwpgTgngBA4mALgGQIaLAZ0QOQBoAiA8gLICCAkjgEpYAOA9gHaZYwDeAUDDAG4CWYAO6QO3HjFQBjKQxBNEmABQAzfgBsMEAFwdJMuQoAqqAOa6ARKgDMABhUAOAExOVUgCYB2KQBZbARgBOBx8AI0cAVncHFSdUCP9EqQsYAF8ASjEJCXcWMiZUdShEfilMMndUOhLeMCVxbJ41TUhdLkbGyowAfVMwYEsnWycIgFpbADZR-wmLBo6YLrBu9X7B4bHJ6Yc5hYkIemZWAGEGdzBLfGJyKl2F1Pns9X4AW35EXX9bb9tHiQYIOcIAAhKC6ADaSxKL2WBAAogBlY4AXT+mXaCwAXswwCZTH8eKBIFAcKgYQSYAdMIwWGBTucKUToEYoHQwBSoa92R0HtleWlOKkgA\&variables=N4XyA)
To learn more and get started, refer to the [DNS Analytics documentation](https://developers.cloudflare.com/dns/additional-options/analytics/#analytics).
---
title: Cloudflare User Groups & SCIM User Groups are now in GA · Changelog
description: Simplifying the management of users, groups, and permissions within Cloudflare.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-23-user-groups-ga/
md: https://developers.cloudflare.com/changelog/2025-06-23-user-groups-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare User Groups & SCIM User Groups are now in GA
Jun 23, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
We're announcing the GA of **User Groups for Cloudflare Dashboard** and **System for Cross Domain Identity Management (SCIM) User Groups**, strengthening our RBAC capabilities with stable, production-ready primitives for managing access at scale.
**What's New**
**User Groups \[GA]**: [User Groups](https://developers.cloudflare.com/fundamentals/manage-members/user-groups/) are a new Cloudflare IAM primitive that enable administrators to create collections of account members that are treated equally from an access control perspective. User Groups can be assigned permission policies, with individual members in the group inheriting all permissions granted to the User Group. User Groups can be created manually or via our APIs.
**SCIM User Groups \[GA]**: Centralize & simplify your user and group management at scale by syncing memberships directly from your upstream identity provider (like Okta or Entra ID) to the Cloudflare Platform. This ensures Cloudflare stays in sync with your identity provider, letting you apply Permission Policies to those synced groups directly within the Cloudflare Dashboard.
**Stability & Scale**: These features have undergone extensive testing during the Public Beta period and are now ready for production use across enterprises of all sizes.
Note
SCIM Virtual Groups (identified by the pattern `CF--` in your IdP) are now officially deprecated as of June 2, 2025. SCIM Virtual Groups end-of-life will take effect on December 2, 2025. We strongly recommend migrating to SCIM User Groups to ensure continued support for SCIM synchronization to the Cloudflare Dashboard. If you haven’t used Virtual Groups, no action is required.
For more info:
* [Get started with User Groups](https://developers.cloudflare.com/fundamentals/manage-members/user-groups/)
* [Explore our SCIM integration guide](https://developers.cloudflare.com/fundamentals/account/account-security/scim-setup/)
---
title: Run AI-generated code on-demand with Code Sandboxes (new) · Changelog
description: You can start creating sandboxes today by installing our new Sandbox package.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-24-announcing-sandboxes/
md: https://developers.cloudflare.com/changelog/2025-06-24-announcing-sandboxes/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Run AI-generated code on-demand with Code Sandboxes (new)
Jun 25, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers ](https://developers.cloudflare.com/workers/)[Workflows](https://developers.cloudflare.com/workflows/)
AI is supercharging app development for everyone, but we need a safe way to run untrusted, LLM-written code. We’re introducing [Sandboxes](https://www.npmjs.com/package/@cloudflare/sandbox), which let your Worker run actual processes in a secure, container-based environment.
```ts
import { getSandbox } from "@cloudflare/sandbox";
export { Sandbox } from "@cloudflare/sandbox";
export default {
async fetch(request: Request, env: Env) {
const sandbox = getSandbox(env.Sandbox, "my-sandbox");
return sandbox.exec("ls", ["-la"]);
},
};
```
#### Methods
* `exec(command: string, args: string[], options?: { stream?: boolean })`:Execute a command in the sandbox.
* `gitCheckout(repoUrl: string, options: { branch?: string; targetDir?: string; stream?: boolean })`: Checkout a git repository in the sandbox.
* `mkdir(path: string, options: { recursive?: boolean; stream?: boolean })`: Create a directory in the sandbox.
* `writeFile(path: string, content: string, options: { encoding?: string; stream?: boolean })`: Write content to a file in the sandbox.
* `readFile(path: string, options: { encoding?: string; stream?: boolean })`: Read content from a file in the sandbox.
* `deleteFile(path: string, options?: { stream?: boolean })`: Delete a file from the sandbox.
* `renameFile(oldPath: string, newPath: string, options?: { stream?: boolean })`: Rename a file in the sandbox.
* `moveFile(sourcePath: string, destinationPath: string, options?: { stream?: boolean })`: Move a file from one location to another in the sandbox.
* `ping()`: Ping the sandbox.
Sandboxes are still experimental. We're using them to explore how isolated, container-like workloads might scale on Cloudflare — and to help define the developer experience around them.
You can try it today from your Worker, with just a few lines of code. Let us know what you build.
---
title: "@cloudflare/actors library - SDK for Durable Objects in beta · Changelog"
description: "@cloudflare/actors library with Durable Objects helpers and patterns."
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-25-actors-package-alpha/
md: https://developers.cloudflare.com/changelog/2025-06-25-actors-package-alpha/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## @cloudflare/actors library - SDK for Durable Objects in beta
Jun 25, 2025
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
The new [@cloudflare/actors](https://www.npmjs.com/package/@cloudflare/actors) library is now in beta!
The `@cloudflare/actors` library is a new SDK for Durable Objects and provides a powerful set of abstractions for building real-time, interactive, and multiplayer applications on top of Durable Objects. With beta usage and feedback, `@cloudflare/actors` will become the recommended way to build on Durable Objects and draws upon Cloudflare's experience building products/features on Durable Objects.
The name "actors" originates from the [actor programming model](https://developers.cloudflare.com/durable-objects/concepts/what-are-durable-objects/#actor-programming-model), which closely ties to how Durable Objects are modelled.
The `@cloudflare/actors` library includes:
* Storage helpers for querying embeddeded, per-object SQLite storage
* Storage helpers for managing SQL schema migrations
* Alarm helpers for scheduling multiple alarms provided a date, delay in seconds, or cron expression
* `Actor` class for using Durable Objects with a defined pattern
* Durable Objects [Workers API](https://developers.cloudflare.com/durable-objects/api/base/) is always available for your application as needed
Storage and alarm helper methods can be combined with [any Javascript class](https://github.com/cloudflare/actors?tab=readme-ov-file#storage--alarms-with-durableobject-class) that defines your Durable Object, i.e, ones that extend `DurableObject` including the `Actor` class.
```js
import { Storage } from "@cloudflare/actors/storage";
export class ChatRoom extends DurableObject {
storage: Storage;
constructor(ctx: DurableObjectState, env: Env) {
super(ctx, env)
this.storage = new Storage(ctx.storage);
this.storage.migrations = [{
idMonotonicInc: 1,
description: "Create users table",
sql: "CREATE TABLE IF NOT EXISTS users (id INTEGER PRIMARY KEY)"
}]
}
async fetch(request: Request): Promise {
// Run migrations before executing SQL query
await this.storage.runMigrations();
// Query with SQL template
let userId = new URL(request.url).searchParams.get("userId");
const query = this.storage.sql`SELECT * FROM users WHERE id = ${userId};`
return new Response(`${JSON.stringify(query)}`);
}
}
```
`@cloudflare/actors` library introduces the `Actor` class pattern. `Actor` lets you access Durable Objects without writing the Worker that communicates with your Durable Object (the Worker is created for you). By default, requests are routed to a Durable Object named "default".
```js
export class MyActor extends Actor {
async fetch(request: Request): Promise {
return new Response('Hello, World!')
}
}
export default handler(MyActor);
```
You can [route](https://developers.cloudflare.com/durable-objects/get-started/#3-instantiate-and-communicate-with-a-durable-object) to different Durable Objects by name within your `Actor` class using [`nameFromRequest`](https://github.com/cloudflare/actors?tab=readme-ov-file#actor-with-custom-name).
```js
export class MyActor extends Actor {
static nameFromRequest(request: Request): string {
let url = new URL(request.url);
return url.searchParams.get("userId") ?? "foo";
}
async fetch(request: Request): Promise {
return new Response(`Actor identifier (Durable Object name): ${this.identifier}`);
}
}
export default handler(MyActor);
```
For more examples, check out the library [README](https://github.com/cloudflare/actors?tab=readme-ov-file#getting-started). `@cloudflare/actors` library is a place for more helpers and built-in patterns, like retry handling and Websocket-based applications, to reduce development overhead for common Durable Objects functionality. Please share feedback and what more you would like to see on our [Discord channel](https://discord.com/channels/595317990191398933/773219443911819284).
---
title: Remote bindings (beta) now works with Next.js — connect to remote
resources (D1, KV, R2, etc.) during local development · Changelog
description: You can now use remote bindings with OpenNext applications.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-25-getplatformproxy-support-remote-bindings/
md: https://developers.cloudflare.com/changelog/2025-06-25-getplatformproxy-support-remote-bindings/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Remote bindings (beta) now works with Next.js — connect to remote resources (D1, KV, R2, etc.) during local development
Jun 30, 2025
[Workers](https://developers.cloudflare.com/workers/)
We [recently announced](https://github.com/cloudflare/workers-sdk/discussions/9660) our public beta for [remote bindings](https://developers.cloudflare.com/workers/development-testing/#remote-bindings), which allow you to connect to deployed resources running on your Cloudflare account (like [R2 buckets](https://developers.cloudflare.com/r2) or [D1 databases](https://developers.cloudflare.com/d1)) while running a local development session.
Now, you can use remote bindings with your Next.js applications through the [`@opennextjs/cloudflare` adaptor](https://opennext.js.org/cloudflare/bindings#remote-bindings) by enabling the experimental feature in your `next.config.ts`:
```diff
initOpenNextCloudflareForDev();
initOpenNextCloudflareForDev({
experimental: { remoteBindings: true }
});
```
Then, all you have to do is specify which bindings you want connected to the deployed resource on your Cloudflare account via the `experimental_remote` flag in your binding definition:
* wrangler.jsonc
```jsonc
{
"r2_buckets": [
{
"bucket_name": "testing-bucket",
"binding": "MY_BUCKET",
"experimental_remote": true,
},
],
}
```
* wrangler.toml
```toml
[[r2_buckets]]
bucket_name = "testing-bucket"
binding = "MY_BUCKET"
experimental_remote = true
```
You can then run `next dev` to start a local development session (or start a preview with `opennextjs-cloudflare preview`), and all requests to `env.MY_BUCKET` will be proxied to the remote `testing-bucket` — rather than the [default local binding simulations](https://developers.cloudflare.com/workers/development-testing/#bindings-during-local-development).
#### Remote bindings & ISR
Remote bindings are also used during the build process, which comes with significant benefits for pages using [Incremental Static Regeneration (ISR)](https://opennext.js.org/aws/inner_workings/components/server/node#isrssg). During the build step for an ISR page, your server executes the page's code just as it would for normal user requests. If a page needs data to display (like fetching user info from [KV](https://developers.cloudflare.com/kv)), those requests are actually made. The server then uses this fetched data to render the final HTML.
Data fetching is a critical part of this process, as the finished HTML is only as good as the data it was built with. If the build process can't fetch real data, you end up with a pre-rendered page that's empty or incomplete.
**With remote bindings support in OpenNext,** your pre-rendered pages are built with real data from the start. The build process uses any configured remote bindings, and any data fetching occurs against the deployed resources on your Cloudflare account.
**Want to learn more?** Get started with [remote bindings and OpenNext](https://opennext.js.org/cloudflare/bindings#remote-bindings).
**Have feedback?** Join the discussion in our [beta announcement](https://github.com/cloudflare/workers-sdk/discussions/9660) to share feedback or report any issues.
---
title: Run and connect Workers in separate dev commands with the Cloudflare Vite
plugin · Changelog
description: Workers running in separate dev commands can now communicate with
each other using the Cloudflare Vite plugin.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-26-vite-plugin-cross-commands-binding/
md: https://developers.cloudflare.com/changelog/2025-06-26-vite-plugin-cross-commands-binding/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Run and connect Workers in separate dev commands with the Cloudflare Vite plugin
Jun 26, 2025
[Workers](https://developers.cloudflare.com/workers/)
Workers can now talk to each other across separate dev commands using service bindings and tail consumers, whether started with `vite dev` or `wrangler dev`.
Simply start each Worker in its own terminal:
```sh
# Terminal 1
vite dev
# Terminal 2
wrangler dev
```
This is useful when different teams maintain different Workers, or when each Worker has its own build setup or tooling.
Check out the [Developing with multiple Workers](https://developers.cloudflare.com/workers/development-testing/multi-workers) guide to learn more about the different approaches and when to use each one.
---
title: Mail authentication requirements for Email Routing · Changelog
description: Emails will need to be authenticated either via SPF or DKIM in
order to be forwarded.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-30-mail-authentication/
md: https://developers.cloudflare.com/changelog/2025-06-30-mail-authentication/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Mail authentication requirements for Email Routing
Jun 30, 2025
[Email Routing](https://developers.cloudflare.com/email-routing/)
The Email Routing platform supports [SPF](https://datatracker.ietf.org/doc/html/rfc7208) records and [DKIM (DomainKeys Identified Mail)](https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail) signatures and honors these protocols when the sending domain has them configured. However, if the sending domain doesn't implement them, we still forward the emails to upstream mailbox providers.
Starting on July 3, 2025, we will require all emails to be authenticated using at least one of the protocols, SPF or DKIM, to forward them. We also strongly recommend that all senders implement the DMARC protocol.
If you are using a Worker with an Email trigger to receive email messages and forward them upstream, you will need to handle the case where the forward action may fail due to missing authentication on the incoming email.
SPAM has been a long-standing issue with email. By enforcing mail authentication, we will increase the efficiency of identifying abusive senders and blocking bad emails. If you're an email server delivering emails to large mailbox providers, it's likely you already use these protocols; otherwise, please ensure you have them properly configured.
---
title: Cloudflare One Agent for Android (version 2.4.2) · Changelog
description: Cloudflare One Agent for Android (version 2.4.2)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-30-warp-ga-android/
md: https://developers.cloudflare.com/changelog/2025-06-30-warp-ga-android/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare One Agent for Android (version 2.4.2)
Jun 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Android Cloudflare One Agent is now available in the [Google Play Store](https://play.google.com/store/apps/details?id=com.cloudflare.cloudflareoneagent). This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate [protection of post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* QLogs are now disabled by default and can be enabled in the app by turning on **Enable qlogs** under **Settings** > **Advanced** > **Diagnostics** > **Debug Logs**. The QLog setting from previous releases will no longer be respected.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* The WARP client now applies [post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be enabled by [MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Fixed an issue that caused WARP connection failures on ChromeOS devices.
---
title: Cloudflare One Agent for iOS (version 1.11) · Changelog
description: Cloudflare One Agent for iOS (version 1.11)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-30-warp-ga-ios/
md: https://developers.cloudflare.com/changelog/2025-06-30-warp-ga-ios/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare One Agent for iOS (version 1.11)
Jun 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the iOS Cloudflare One Agent is now available in the [iOS App Store](https://apps.apple.com/us/app/cloudflare-one-agent/id6443476492). This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate [protection of post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* QLogs are now disabled by default and can be enabled in the app by turning on **Enable qlogs** under **Settings** > **Advanced** > **Diagnostics** > **Debug Logs**. The QLog setting from previous releases will no longer be respected.
* DNS over HTTPS traffic is now included in the WARP tunnel by default.
* The WARP client now applies [post-quantum cryptography](https://blog.cloudflare.com/pq-2024/) end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be enabled by [MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
---
title: WARP client for Linux (version 2025.5.893.0) · Changelog
description: WARP client for Linux (version 2025.5.893.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-30-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-06-30-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.5.893.0)
Jun 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements and fixes:
* Captive portal sign in notifications will now be sent through operating system notification services.
* Fix for firewall configuration issue affecting clients in DoH only mode.
* Improved the connectivity status message in the client GUI.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to handle client configuration changes made by MDM while WARP is not running.
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for macOS (version 2025.5.893.0) · Changelog
description: WARP client for macOS (version 2025.5.893.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-30-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-06-30-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.5.893.0)
Jun 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains improvements and new exciting features, including [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed an issue where WARP sometimes failed to automatically relaunch after updating.
* Fixed a device registration issue causing WARP connection failures when changing networks.
* Captive portal improvements and fixes:
* Captive portal sign in notifications will now be sent through operating system notification services.
* Fix for firewall configuration issue affecting clients in DoH only mode.
* Improved the connectivity status message in the client GUI.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to handle client configuration changes made by an MDM while WARP is not running.
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Improvement for WARP connectivity issues on macOS due to the operating system not accepting DNS server configurations.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
---
title: WARP client for Windows (version 2025.5.893.0) · Changelog
description: WARP client for Windows (version 2025.5.893.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-06-30-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-06-30-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.5.893.0)
Jun 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains improvements and new exciting features, including [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) and [post-quantum cryptography](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum). By tunneling your corporate network traffic over Cloudflare, you can now gain the immediate protection of post-quantum cryptography without needing to upgrade any of your individual corporate applications or systems.
**Changes and improvements**
* Fixed a device registration issue that caused WARP connection failures when changing networks.
* Captive portal improvements and fixes:
* Captive portal sign in notifications will now be sent through operating system notification services.
* Fix for firewall configuration issue affecting clients in DoH only mode.
* Improved the connectivity status message in the client GUI.
* Fixed a bug affecting clients in Gateway with DoH mode where the original DNS servers were not restored after disabling WARP.
* The WARP client now applies post-quantum cryptography end-to-end on enabled devices accessing resources behind a Cloudflare Tunnel. This feature can be [enabled by MDM](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/parameters/#enable_post_quantum).
* Improvement to handle client configuration changes made by an MDM while WARP is not running.
* Improvements for multi-user experience to better handle fast user switching and transitions from a pre-login to a logged-in state.
* Added a WARP client device posture check for SAN attributes to the [client certificate check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/).
* Fixed an issue affecting Split Tunnel Include mode, where traffic outside the tunnel was blocked when switching between Wi-Fi and Ethernet networks.
* Added [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) to device profile settings. With SCCM VPN boundary support enabled, operating systems will register WARP's local interface IP with the on-premise DNS server when reachable.
* Fix for an issue causing WARP connectivity to fail without full system reboot.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5060829](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Cloudflare Access Logging supports the Customer Metadata Boundary (CMB) ·
Changelog
description: Access logs will now respect the CMB.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-01-access-supports-customer-metadata-boundary/
md: https://developers.cloudflare.com/changelog/2025-07-01-access-supports-customer-metadata-boundary/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Access Logging supports the Customer Metadata Boundary (CMB)
Aug 14, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
Cloudflare Access logs now support the [Customer Metadata Boundary (CMB)](https://developers.cloudflare.com/data-localization/metadata-boundary/). If you have configured the CMB for your account, all Access logging will respect that configuration.
Note
For EU CMB customers, the logs will not be stored by Access and will appear as empty in the dashboard. EU CMB customers should utilize [Logpush](https://developers.cloudflare.com/logs/logpush/) to retain their Access logging, if desired.
---
title: Access RDP securely from your browser — now in open beta · Changelog
description: Connect to internal Windows servers via a web browser — no VPN or
RDP client required.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-01-browser-based-rdp-open-beta/
md: https://developers.cloudflare.com/changelog/2025-07-01-browser-based-rdp-open-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Access RDP securely from your browser — now in open beta
Jul 01, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Browser-based RDP](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/) with [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) is now available in open beta for all Cloudflare customers. It enables secure, remote Windows server access without VPNs or RDP clients.
With browser-based RDP, you can:
* **Control how users authenticate to internal RDP resources** with single sign-on (SSO), multi-factor authentication (MFA), and granular access policies.
* **Record who is accessing which servers and when** to support regulatory compliance requirements and to gain greater visibility in the event of a security event.
* **Eliminate the need to install and manage software on user devices**. You will only need a web browser.
* **Reduce your attack surface** by keeping your RDP servers off the public Internet and protecting them from common threats like credential stuffing or brute-force attacks.

To get started, see [Connect to RDP in a browser](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/).
---
title: Introducing Pay Per Crawl (private beta) · Changelog
description: A new feature which allows site owners to charge crawlers for
access to their content
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-01-pay-per-crawl/
md: https://developers.cloudflare.com/changelog/2025-07-01-pay-per-crawl/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing Pay Per Crawl (private beta)
Jul 01, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
We are introducing a new feature of [AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/) — Pay Per Crawl. [Pay Per Crawl](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/) enables site owners to require payment from AI crawlers every time the crawlers access their content, thereby fostering a fairer Internet by enabling site owners to control and monetize how their content gets used by AI.

**For Site Owners:**
* Set pricing and select which crawlers to charge for content access
* Manage payments via Stripe
* Monitor analytics on successful content deliveries
**For AI Crawler Owners:**
* Use HTTP headers to request and accept pricing
* Receive clear confirmations on charges for accessed content
Learn more in the [Pay Per Crawl documentation](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/what-is-pay-per-crawl/).
---
title: Bot & Crawler Insights in Cloudflare Radar · Changelog
description: Expanded visibility into crawler, referral, and bot activity with
new Radar API endpoints
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-01-radar-bots-insights/
md: https://developers.cloudflare.com/changelog/2025-07-01-radar-bots-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Bot & Crawler Insights in Cloudflare Radar
Jul 01, 2025
[Radar](https://developers.cloudflare.com/radar/)
#### Web crawlers insights
[**Radar**](https://developers.cloudflare.com/radar/) now offers expanded insights into web crawlers, giving you greater visibility into aggregated trends in crawl and refer activity.
We have introduced the following endpoints:
* [`/bots/crawlers/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/subresources/web_crawlers/methods/summary/): Returns an overview of crawler HTTP request distributions across key dimensions.
* [`/bots/crawlers/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/subresources/web_crawlers/methods/timeseries_groups/): Provides time-series data on crawler request distributions across the same dimensions.
These endpoints allow analysis across the following dimensions:
* `user_agent`: Parsed data from the `User-Agent` header.
* `referer`: Parsed data from the `Referer` header.
* `crawl_refer_ratio`: Ratio of HTML page crawl requests to HTML page referrals by platform.
#### Broader bot insights
In addition to crawler-specific insights, Radar now provides a broader set of bot endpoints:
* [`/bots/`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/): Lists all bots.
* [`/bots/{bot_slug}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/get/): Returns detailed metadata for a specific bot.
* [`/bots/timeseries`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/timeseries/): Time-series data for bot activity.
* [`/bots/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/summary/): Returns an overview of bot HTTP request distributions across key dimensions.
* [`/bots/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/timeseries_groups/): Provides time-series data on bot request distributions across the same dimensions.
These endpoints support filtering and breakdowns by:
* `bot`: Bot name.
* `bot_operator`: The organization or entity operating the bot.
* `bot_category`: Classification of bot type.
The previously available `verified_bots` endpoints have now been deprecated in favor of this set of bot insights APIs. While current data still focuses on verified bots, we plan to expand support for unverified bot traffic in the future.
Learn more about the new Radar bot and crawler insights in our [blog post](https://blog.cloudflare.com/ai-search-crawl-refer-ratio-on-radar).
---
title: AI Crawl Control refresh · Changelog
description: More intuitive AI crawler management
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-01-refresh/
md: https://developers.cloudflare.com/changelog/2025-07-01-refresh/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Crawl Control refresh
Jul 01, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
We redesigned the AI Crawl Control dashboard to provide more intuitive and granular control over AI crawlers.
* From the new **AI Crawlers** tab: block specific AI crawlers.
* From the new **Metrics** tab: view AI Crawl Control metrics.
 
To get started, explore:
* [Manage AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/).
* [Analyze AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/).
---
title: Enhanced support for static assets with the Cloudflare Vite plugin · Changelog
description: The Cloudflare Vite plugin now supports using all of Vite's static
assets features in your Worker
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-01-vite-plugin-enhanced-assets-support/
md: https://developers.cloudflare.com/changelog/2025-07-01-vite-plugin-enhanced-assets-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Enhanced support for static assets with the Cloudflare Vite plugin
Jul 01, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now use any of Vite's [static asset handling](https://vite.dev/guide/assets) features in your Worker as well as in your frontend. These include importing assets as URLs, importing as strings and importing from the `public` directory as well as inlining assets.
Additionally, assets imported as URLs in your Worker are now automatically moved to the client build output.
Here is an example that fetches an imported asset using the [assets binding](https://developers.cloudflare.com/workers/static-assets/binding/#binding) and modifies the response.
```ts
// Import the asset URL
// This returns the resolved path in development and production
import myImage from "./my-image.png";
export default {
async fetch(request, env) {
// Fetch the asset using the binding
const response = await env.ASSETS.fetch(new URL(myImage, request.url));
// Create a new `Response` object that can be modified
const modifiedResponse = new Response(response.body, response);
// Add an additional header
modifiedResponse.headers.append("my-header", "imported-asset");
// Return the modfied response
return modifiedResponse;
},
};
```
Refer to [Static Assets](https://developers.cloudflare.com/workers/vite-plugin/reference/static-assets/) in the Cloudflare Vite plugin docs for more info.
---
title: Deploy to Cloudflare buttons now support Worker environment variables,
secrets, and Secrets Store secrets · Changelog
description: Worker environment variables, secrets, and Secrets Store secrets
can now be used in Workers templates
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-01-workers-deploy-button-supports-environment-variables-and-secrets/
md: https://developers.cloudflare.com/changelog/2025-07-01-workers-deploy-button-supports-environment-variables-and-secrets/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Deploy to Cloudflare buttons now support Worker environment variables, secrets, and Secrets Store secrets
Jul 29, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Secrets Store](https://developers.cloudflare.com/secrets-store/)
Any template which uses [Worker environment variables](https://developers.cloudflare.com/workers/configuration/environment-variables/), [secrets](https://developers.cloudflare.com/workers/configuration/secrets/), or [Secrets Store secrets](https://developers.cloudflare.com/secrets-store/) can now be deployed using a [Deploy to Cloudflare button](https://developers.cloudflare.com/workers/platform/deploy-buttons/).
Define environment variables and secrets store bindings in your Wrangler configuration file as normal:
* wrangler.jsonc
```jsonc
{
"name": "my-worker",
"main": "./src/index.ts",
"compatibility_date": "2026-02-07",
"vars": {
"API_HOST": "https://example.com",
},
"secrets_store_secrets": [
{
"binding": "API_KEY",
"store_id": "demo",
"secret_name": "api-key"
}
]
}
```
* wrangler.toml
```toml
name = "my-worker"
main = "./src/index.ts"
compatibility_date = "2026-02-07"
[vars]
API_HOST = "https://example.com"
[[secrets_store_secrets]]
binding = "API_KEY"
store_id = "demo"
secret_name = "api-key"
```
Add secrets to a `.dev.vars.example` or `.env.example` file:
```ini
COOKIE_SIGNING_KEY=my-secret # comment
```
And optionally, you can add a description for these bindings in your template's `package.json` to help users understand how to configure each value:
```json
{
"name": "my-worker",
"private": true,
"cloudflare": {
"bindings": {
"API_KEY": {
"description": "Select your company's API key for connecting to the example service."
},
"COOKIE_SIGNING_KEY": {
"description": "Generate a random string using `openssl rand -hex 32`."
}
}
}
}
```
These secrets and environment variables will be presented to users in the dashboard as they deploy this template, allowing them to configure each value. Additional information about creating templates and Deploy to Cloudflare buttons can be found in [our documentation](https://developers.cloudflare.com/workers/platform/deploy-buttons/).
---
title: Hyperdrive now supports configuring the amount of database connections ·
Changelog
description: Hyperdrive configurations can now be set to use a specific number
of connections to your origin database.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-02-hyperdrive-configurable-connection-count/
md: https://developers.cloudflare.com/changelog/2025-07-02-hyperdrive-configurable-connection-count/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Hyperdrive now supports configuring the amount of database connections
Jul 03, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
You can now specify the number of connections your Hyperdrive configuration uses to connect to your origin database.
All configurations have a minimum of 5 connections. The maximum connection count for a Hyperdrive configuration depends on the [Hyperdrive limits of your Workers plan](https://developers.cloudflare.com/hyperdrive/platform/limits/).
This feature allows you to right-size your connection pool based on your database capacity and application requirements. You can configure connection counts through the Cloudflare dashboard or API.
Refer to the [Hyperdrive configuration documentation](https://developers.cloudflare.com/hyperdrive/concepts/connection-pooling/) for more information.
---
title: Workers now supports JavaScript debug terminals in VSCode, Cursor and
Windsurf IDEs · Changelog
description: Wrangler, the Cloudflare Vite plugin, and Miniflare now support
breakpoint debugging via JavaScript debug terminals in VSCode
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-04-javascript-debug-terminals/
md: https://developers.cloudflare.com/changelog/2025-07-04-javascript-debug-terminals/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers now supports JavaScript debug terminals in VSCode, Cursor and Windsurf IDEs
Jul 04, 2025
[Workers](https://developers.cloudflare.com/workers/)
Workers now support breakpoint debugging using VSCode's built-in [JavaScript Debug Terminals](https://code.visualstudio.com/docs/nodejs/nodejs-debugging#_javascript-debug-terminal). All you have to do is open a JS debug terminal (`Cmd + Shift + P` and then type `javascript debug`) and run `wrangler dev` (or `vite dev`) from within the debug terminal. VSCode will automatically connect to your running Worker (even if you're running multiple Workers at once!) and start a debugging session.
In 2023 we announced [breakpoint debugging support](https://blog.cloudflare.com/debugging-cloudflare-workers/) for Workers, which meant that you could easily debug your Worker code in Wrangler's built-in devtools (accessible via the `[d]` hotkey) as well as multiple other devtools clients, [including VSCode](https://developers.cloudflare.com/workers/observability/dev-tools/breakpoints/). For most developers, breakpoint debugging via VSCode is the most natural flow, but until now it's required [manually configuring a `launch.json` file](https://developers.cloudflare.com/workers/observability/dev-tools/breakpoints/#setup-vs-code-to-use-breakpoints), running `wrangler dev`, and connecting via VSCode's built-in debugger. Now it's much more seamless!
---
title: Cloudy summaries for Access and Gateway Logs · Changelog
description: Cloudy summaries for Access and Gateway Logs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-07-cloudy-summaries-access-gateway/
md: https://developers.cloudflare.com/changelog/2025-07-07-cloudy-summaries-access-gateway/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudy summaries for Access and Gateway Logs
Jul 07, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Cloudy, Cloudflare's AI Agent, will now automatically summarize your [Access](https://developers.cloudflare.com/cloudflare-one/insights/logs/audit-logs/) and [Gateway](https://developers.cloudflare.com/cloudflare-one/insights/logs/gateway-logs/) block logs.
In the log itself, Cloudy will summarize what occurred and why. This will be helpful for quick troubleshooting and issue correlation.

If you have feedback about the Cloudy summary - good or bad - you can provide that right from the summary itself.
---
title: New App Library for Zero Trust Dashboard · Changelog
description: New App Library for Zero Trust Dashboard
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-07-dashboard-app-library/
md: https://developers.cloudflare.com/changelog/2025-07-07-dashboard-app-library/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New App Library for Zero Trust Dashboard
Jul 07, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Cloudflare Zero Trust customers can use the App Library to get full visibility over the SaaS applications that they use in their Gateway policies, CASB integrations, and Access for SaaS applications.
**App Library**, found under **My Team**, makes information available about all Applications that can be used across the Zero Trust product suite.

You can use the App Library to see:
* How Applications are defined
* Where they are referenced in policies
* Whether they have Access for SaaS configured
* Review their CASB findings and integration status.
Within individual Applications, you can also track their usage across your organization, and better understand user behavior.
---
title: Increased IP List Limits for Enterprise Accounts · Changelog
description: We have significantly increased the limits for IP Lists on
Enterprise plans to provide greater flexibility and control.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-07-increased-ip-list-limits/
md: https://developers.cloudflare.com/changelog/2025-07-07-increased-ip-list-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased IP List Limits for Enterprise Accounts
Jul 07, 2025
[WAF](https://developers.cloudflare.com/waf/)
We have significantly increased the limits for [IP Lists](https://developers.cloudflare.com/waf/tools/lists/) on Enterprise plans to provide greater flexibility and control:
* **Total number of lists**: Increased from 10 to 1,000.
* **Total number of list items**: Increased from 10,000 to 500,000.
Limits for other list types and plans remain unchanged. For more details, refer to the [lists availability](https://developers.cloudflare.com/waf/tools/lists/#availability).
---
title: WAF Release - 2025-07-07 · Changelog
description: Cloudflare WAF managed rulesets 2025-07-07 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-07-waf-release/
md: https://developers.cloudflare.com/changelog/2025-07-07-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-07-07
Jul 07, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s roundup uncovers critical vulnerabilities affecting enterprise VoIP systems, webmail platforms, and a popular JavaScript framework. The risks range from authentication bypass to remote code execution (RCE) and buffer handling flaws, each offering attackers a path to elevate access or fully compromise systems.
**Key Findings**
* Next.js - Auth Bypass: A newly detected authentication bypass flaw in the Next.js framework allows attackers to access protected routes or APIs without proper authorization, undermining application access controls.
* Fortinet FortiVoice (CVE-2025-32756): A buffer error vulnerability in FortiVoice systems that could lead to memory corruption and potential code execution or service disruption in enterprise telephony environments.
* Roundcube (CVE-2025-49113): A critical RCE flaw allowing unauthenticated attackers to execute arbitrary PHP code via crafted requests, leading to full compromise of mail servers and user inboxes.
**Impact**
These vulnerabilities affect core business infrastructure, from web interfaces to voice communications and email platforms. The Roundcube RCE and FortiVoice buffer flaw offer potential for deep system access, while the Next.js auth bypass undermines trust boundaries in modern web apps.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | b6558cac8c874bd6878734057eb35ee6 | 100795 | Next.js - Auth Bypass | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 58fcf6d9c05d4b7a8f41e0a3c329aeb0 | 100796 | Fortinet FortiVoice - Buffer Error - CVE:CVE-2025-32756 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 34ed0624bc864ea88bbea55bab314023 | 100797 | Roundcube - Remote Code Execution - CVE:CVE-2025-49113 | Log | Disabled | This is a New Detection |
---
title: Faster indexing and new Jobs view in AutoRAG · Changelog
description: Track your indexing pipeline in real time with 3–5× faster indexing
and a new Jobs dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-08-autorag-jobs-view/
md: https://developers.cloudflare.com/changelog/2025-07-08-autorag-jobs-view/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Faster indexing and new Jobs view in AutoRAG
Jul 08, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
You can now expect **3-5× faster indexing** in AutoRAG, and with it, a brand new **Jobs view** to help you monitor indexing progress.
With each AutoRAG, indexing jobs are automatically triggered to sync your data source (i.e. R2 bucket) with your Vectorize index, ensuring new or updated files are reflected in your query results. You can also trigger jobs manually via the [Sync API](https://developers.cloudflare.com/api/resources/ai-search/subresources/rags/) or by clicking “Sync index” in the dashboard.
With the new jobs observability, you can now:
* View the status, job ID, source, start time, duration and last sync time for each indexing job
* Inspect real-time logs of job events (e.g. `Starting indexing data source...`)
* See a history of past indexing jobs under the Jobs tab of your AutoRAG
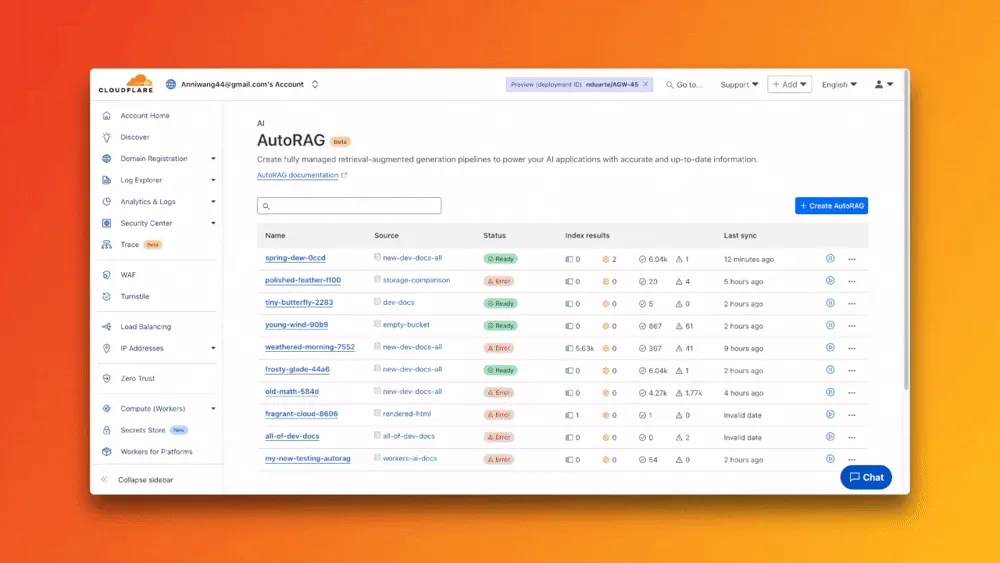
This makes it easier to understand what’s happening behind the scenes.
**Coming soon:** We’re adding APIs to programmatically check indexing status, making it even easier to integrate AutoRAG into your workflows.
Try it out today on the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/ai/autorag).
---
title: New onboarding guides for Zero Trust · Changelog
description: New onboarding guides for Zero Trust
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-09-onboarding-resources/
md: https://developers.cloudflare.com/changelog/2025-07-09-onboarding-resources/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New onboarding guides for Zero Trust
Jul 10, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Use our brand new onboarding experience for Cloudflare Zero Trust. New and returning users can now engage with a **Get Started** tab with walkthroughs for setting up common use cases end-to-end.

There are eight brand new onboarding guides in total:
* Securely access a private network (sets up device client and Tunnel)
* Device-to-device / mesh networking (sets up and connects multiple device clients)
* Network to network connectivity (sets up and connects multiple WARP Connectors, makes reference to Magic WAN availability for Enterprise)
* Secure web traffic (sets up device client, Gateway, pre-reqs, and initial policies)
* Secure DNS for networks (sets up a new DNS location and Gateway policies)
* Clientless web access (sets up Access to a web app, Tunnel, and public hostname)
* Clientless SSH access (all the same + the web SSH experience)
* Clientless RDP access (all the same + RDP-in-browser)
Each flow walks the user through the steps to configure the essential elements, and provides a “more details” panel with additional contextual information about what the user will accomplish at the end, along with why the steps they take are important.
Try them out now in the [Zero Trust dashboard](https://one.dash.cloudflare.com/?to=/:account/home)!
---
title: Usage tracking · Changelog
description: Log Explorer customers can now monitor their data ingestion volume
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-09-usage-tracking/
md: https://developers.cloudflare.com/changelog/2025-07-09-usage-tracking/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Usage tracking
Jul 09, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/) customers can now monitor their data ingestion volume to keep track of their billing. Monthly usage is displayed at the top of the [Log Search](https://developers.cloudflare.com/log-explorer/log-search/) and [Manage Datasets](https://developers.cloudflare.com/log-explorer/manage-datasets/) screens in Log Explorer.
---
title: Terraform v5.7.0 now available · Changelog
description: Terraform v5.7.0 fixes a number of known bugs in the v5 Provider
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-11-terraform-v570-provider/
md: https://developers.cloudflare.com/changelog/2025-07-11-terraform-v570-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.7.0 now available
Jul 14, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high mumber of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare community related to the v5 release, with 13.5% of resources impacted. We have committed to releasing improvements on a 2 week cadeance to ensure it's stability and relability, including the v5.7 release.
Thank you for continuing to raise issues and please keep an eye on this changelog for more information about upcoming releases.
#### Changes
* Addressed permanent diff bug on Cloudflare Tunnel config
* State is now saved correctly for Zero Trust Access applications
* Exact match is now working as expected within `data.cloudflare_zero_trust_access_applications`
* `cloudflare_zero_trust_access_policy` now supports OIDC claims & diff issues resolved
* Self hosted applications with private IPs no longer require a public domain for `cloudflare_zero_trust_access_application`.
* New resource:
* `cloudflare_zero_trust_tunnel_warp_connector`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.7.0) in GitHub.
#### Issues Closed
* [#5563: cloudflare\_logpull\_retention is missing import](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5563)
* [#5608: cloudflare\_zero\_trust\_access\_policy in 5.5.0 provider gives error upon apply unexpected new value: .app\_count: was cty.NumberIntVal(0), but now cty.NumberIntVal(1)](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5608)
* [#5612: data.cloudflare\_zero\_trust\_access\_applications does not exact match](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5612)
* [#5532: cloudflare\_zero\_trust\_access\_identity\_provider detects changes on every plan](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5532)
* [#5662: cloudflare\_zero\_trust\_access\_policy does not support OIDC claims](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5662)
* [#5565: Running Terraform with the cloudflare\_zero\_trust\_access\_policy resource results in updates on every apply, even when no changes are made - breaks idempotency](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5565)
* [#5529: cloudflare\_zero\_trust\_access\_application: self hosted applications with private ips require public domain](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5529)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding on migration to v5 while we work on stablization of the v5 provider. This will ensure Cloudflare can work ahead and avoid any blocking issues.
If you'd like more information on migrating from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: WAF Release - 2025-07-14 · Changelog
description: Cloudflare WAF managed rulesets 2025-07-14 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-14-waf-release/
md: https://developers.cloudflare.com/changelog/2025-07-14-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-07-14
Jul 14, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s vulnerability analysis highlights emerging web application threats that exploit modern JavaScript behavior and SQL parsing ambiguities. Attackers continue to refine techniques such as attribute overloading and obfuscated logic manipulation to evade detection and compromise front-end and back-end systems.
**Key Findings**
* XSS – Attribute Overloading: A novel cross-site scripting technique where attackers abuse custom or non-standard HTML attributes to smuggle payloads into the DOM. These payloads evade traditional sanitization logic, especially in frameworks that loosely validate attributes or trust unknown tokens.
* XSS – onToggle Event Abuse: Exploits the lesser-used onToggle event (triggered by elements like ``) to execute arbitrary JavaScript when users interact with UI elements. This vector is often overlooked by static analyzers and can be embedded in seemingly benign components.
**Impact**
These vulnerabilities target both user-facing components and back-end databases, introducing potential vectors for credential theft, session hijacking, or full data exfiltration. The XSS variants bypass conventional filters through overlooked HTML behaviors, while the obfuscated SQLi enables attackers to stealthily probe back-end logic, making them especially difficult to detect and block.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | a8918353372b4191b10684eb2aa3d845 | 100798 | XSS - Attribute Overloading | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 31dd299ba375414dac9260c037548d06 | 100799 | XSS - OnToggle | Log | Block | This is a New Detection |
---
title: Faster, more reliable UDP traffic for Cloudflare Tunnel · Changelog
description: We've re-architected how Cloudflare Tunnel handles UDP traffic.
Your real-time applications are now faster and more stable, especially on
Tunnels with mixed TCP and UDP traffic.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-15-udp-improvements/
md: https://developers.cloudflare.com/changelog/2025-07-15-udp-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Faster, more reliable UDP traffic for Cloudflare Tunnel
Jul 15, 2025
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
Your real-time applications running over [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) are now faster and more reliable. We've completely re-architected the way `cloudflared` proxies UDP traffic in order to isolate it from other traffic, ensuring latency-sensitive applications like private DNS are no longer slowed down by heavy TCP traffic (like file transfers) on the same Tunnel.
This is a foundational improvement to Cloudflare Tunnel, delivered automatically to all customers. There are no settings to configure — your UDP traffic is already flowing faster and more reliably.
**What’s new:**
* **Faster UDP performance**: We've significantly reduced the latency for establishing new UDP sessions, making applications like private DNS much more responsive.
* **Greater reliability for mixed traffic**: UDP packets are no longer affected by heavy TCP traffic, preventing timeouts and connection drops for your real-time services.
Learn more about running [TCP or UDP applications](https://developers.cloudflare.com/reference-architecture/architectures/sase/#connecting-applications) and [private networks](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/) through [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/).
---
title: "New detection entry type: Document Matching for DLP · Changelog"
description: Upload a document as a detection entry type to be identified in
traffic utilizing Gateway or at rest with CASB.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-17-document-matching/
md: https://developers.cloudflare.com/changelog/2025-07-17-document-matching/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New detection entry type: Document Matching for DLP
Jul 17, 2025
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now create [document-based](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#documents) detection entries in DLP by uploading example documents. Cloudflare will encrypt your documents and create a unique fingerprint of the file. This fingerprint is then used to identify similar documents or snippets within your organization's traffic and stored files.

**Key features and benefits:**
* **Upload documents, forms, or templates:** Easily upload .docx and .txt files (up to 10 MB) that contain sensitive information you want to protect.
* **Granular control with similarity percentage:** Define a minimum similarity percentage (0-100%) that a document must meet to trigger a detection, reducing false positives.
* **Comprehensive coverage:** Apply these document-based detection entries in:
* **Gateway policies:** To inspect network traffic for sensitive documents as they are uploaded or shared.
* **CASB (Cloud Access Security Broker):** To scan files stored in cloud applications for sensitive documents at rest.
* **Identify sensitive data:** This new detection entry type is ideal for identifying sensitive data within completed forms, templates, or even small snippets of a larger document, helping you prevent data exfiltration and ensure compliance.
Once uploaded and processed, you can add this new document entry into a DLP profile and policies to enhance your data protection strategy.
---
title: The Cloudflare Vite plugin now supports Vite 7 · Changelog
description: The Cloudflare Vite plugin now supports Vite 7
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-17-vite-plugin-vite-7-support/
md: https://developers.cloudflare.com/changelog/2025-07-17-vite-plugin-vite-7-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## The Cloudflare Vite plugin now supports Vite 7
Jul 17, 2025
[Workers](https://developers.cloudflare.com/workers/)
[Vite 7](https://vite.dev/blog/announcing-vite7) is now supported in the Cloudflare Vite plugin. See the [Vite changelog](https://github.com/vitejs/vite/blob/main/packages/vite/CHANGELOG.md#700-2025-06-24) for a list of changes.
Note that the minimum Node.js versions supported by Vite 7 are 20.19 and 22.12. We continue to support Vite 6 so you do not need to immediately upgrade.
---
title: New APIs for Brand Protection setup · Changelog
description: You can now use the Brand Protection API endpoints to manage your
Brand Protection queries
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-18-brand-protection-api/
md: https://developers.cloudflare.com/changelog/2025-07-18-brand-protection-api/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New APIs for Brand Protection setup
Jul 18, 2025
[Security Center](https://developers.cloudflare.com/security-center/)
The Brand Protection API is now available, allowing users to create new queries and delete existing ones, fetch matches and more!
What you can do:
* **create new string or logo query**
* **delete string or logo queries**
* **download matches for both logo and string queries**
* **read matches for both logo and string queries**
Ready to start? Check out the [Brand Protection API](https://developers.cloudflare.com/api/resources/brand_protection/) in our documentation.
---
title: WAF Release - 2025-07-21 - Emergency · Changelog
description: This week's update highlights several high-impact vulnerabilities
affecting Microsoft SharePoint Server.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-21-emergency/
md: https://developers.cloudflare.com/changelog/2025-07-21-emergency/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-07-21 - Emergency
Jul 21, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's update highlights several high-impact vulnerabilities affecting Microsoft SharePoint Server. These flaws, involving unsafe deserialization, allow unauthenticated remote code execution over the network, posing a critical threat to enterprise environments relying on SharePoint for collaboration and document management.
**Key Findings**
* Microsoft SharePoint Server (CVE-2025-53770): A critical vulnerability involving unsafe deserialization of untrusted data, enabling unauthenticated remote code execution over the network. This flaw allows attackers to execute arbitrary code on vulnerable SharePoint servers without user interaction.
* Microsoft SharePoint Server (CVE-2025-53771): A closely related deserialization issue that can be exploited by unauthenticated attackers, potentially leading to full system compromise. The vulnerability highlights continued risks around insecure serialization logic in enterprise collaboration platforms.
**Impact**
Together, these vulnerabilities significantly weaken the security posture of on-premise Microsoft SharePoint Server deployments. By enabling remote code execution without authentication, they open the door for attackers to gain persistent access, deploy malware, and move laterally across enterprise environments.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 34dac2b38b904163bc587cc32168f6f0 | 100817 | Microsoft SharePoint - Deserialization - CVE:CVE-2025-53770 | N/A | Block | This is a New Detection |
| Cloudflare Managed Ruleset | d21f327516a145bc9d1b05678de656c4 | 100818 | Microsoft SharePoint - Deserialization - CVE:CVE-2025-53771 | N/A | Block | This is a New Detection |
For more details, also refer to [our blog](https://blog.cloudflare.com/cloudflare-protects-against-critical-sharepoint-vulnerability-cve-2025-53770/).
---
title: Subaddressing support in Email Routing · Changelog
description: Subaddressing, also known as plus addressing, is now supported in
Email Routing.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-21-subaddressing/
md: https://developers.cloudflare.com/changelog/2025-07-21-subaddressing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Subaddressing support in Email Routing
Jul 21, 2025
[Email Routing](https://developers.cloudflare.com/email-routing/)
Subaddressing, as defined in [RFC 5233](https://www.rfc-editor.org/rfc/rfc5233), also known as plus addressing, is now supported in Email Routing. This enables using the "+" separator to augment your custom addresses with arbitrary detail information.
Now you can send an email to `user+detail@example.com` and it will be captured by the `user@example.com` custom address. The `+detail` part is ignored by Email Routing, but it can be captured next in the processing chain in the logs, an [Email Worker](https://developers.cloudflare.com/email-routing/email-workers/) or an [Agent application](https://github.com/cloudflare/agents/tree/main/examples/email-agent).
Customers can use this feature to dynamically add context to their emails, such as tracking the source of an email or categorizing emails without needing to create multiple custom addresses.

Check our [Developer Docs](https://developers.cloudflare.com/email-routing/setup/email-routing-addresses/#subaddressing) to learn on to enable subaddressing in Email Routing.
---
title: WAF Release - 2025-07-21 · Changelog
description: Cloudflare WAF managed rulesets 2025-07-21 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-21-waf-release/
md: https://developers.cloudflare.com/changelog/2025-07-21-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-07-21
Jul 21, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's update spotlights several critical vulnerabilities across Citrix NetScaler Memory Disclosure, FTP servers and network application. Several flaws enable unauthenticated remote code execution or sensitive data exposure, posing a significant risk to enterprise security.
**Key Findings**
* Wing FTP Server (CVE-2025-47812): A critical Remote Code Execution (RCE) vulnerability that enables unauthenticated attackers to execute arbitrary code with root/SYSTEM-level privileges by exploiting a Lua injection flaw.
* Infoblox NetMRI (CVE-2025-32813): A remote unauthenticated command injection flaw that allows an attacker to execute arbitrary commands, potentially leading to unauthorized access.
* Citrix Netscaler ADC (CVE-2025-5777, CVE-2023-4966): A sensitive information disclosure vulnerability, also known as "Citrix Bleed2", that allows the disclosure of memory and subsequent remote access session hijacking.
* Akamai CloudTest (CVE-2025-49493): An XML External Entity (XXE) injection that could lead to read local files on the system by manipulating XML input.
**Impact**
These vulnerabilities affect critical enterprise infrastructure, from file transfer services and network management appliances to application delivery controllers. The Wing FTP RCE and Infoblox command injection flaws offer direct paths to deep system compromise, while the Citrix "Bleed2" and Akamai XXE vulnerabilities undermine system integrity by enabling session hijacking and sensitive data theft.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 6ab3bd3b58fb4325ac2d3cc73461ec9e | 100804 | BerriAI - SSRF - CVE:CVE-2024-6587 | Log | Log | This is a New Detection |
| Cloudflare Managed Ruleset | 0e17d8761f1a47d5a744a75b5199b58a | 100805 | Wing FTP Server - Remote Code Execution - CVE:CVE-2025-47812 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 81ace5a851214a2f9c58a1e7919a91a4 | 100807 | Infoblox NetMRI - Command Injection - CVE:CVE-2025-32813 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | cd8fa74e8f6f476c9380ae217899130f | 100808 | Citrix Netscaler ADC - Buffer Error - CVE:CVE-2025-5777 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | e012c7bece304a1daf80935ed1cf8e08 | 100809 | Citrix Netscaler ADC - Information Disclosure - CVE:CVE-2023-4966 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 5d348a573a834ffd968faffc6e70469f | 100810 | Akamai CloudTest - XXE - CVE:CVE-2025-49493 | Log | Block | This is a New Detection |
---
title: Browser Rendering now supports local development · Changelog
description: You can now use local development with Browser Rendering
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-22-br-local-dev/
md: https://developers.cloudflare.com/changelog/2025-07-22-br-local-dev/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Browser Rendering now supports local development
Jul 22, 2025
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
You can now run your Browser Rendering locally using `npx wrangler dev`, which spins up a browser directly on your machine before deploying to Cloudflare's global network. By running tests locally, you can quickly develop, debug, and test changes without needing to deploy or worry about usage costs.

Get started with this [example guide](https://developers.cloudflare.com/browser-rendering/workers-bindings/screenshots/) that shows how to use Cloudflare's [fork of Puppeteer](https://developers.cloudflare.com/browser-rendering/puppeteer/) (you can also use [Playwright](https://developers.cloudflare.com/browser-rendering/playwright/)) to take screenshots of webpages and store the results in [Workers KV](https://developers.cloudflare.com/kv/).
---
title: Audio mode for Media Transformations · Changelog
description: >
Media Transformations now supports `audio` mode, which extracts audio from a
video.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-22-media-transformations-audio-mode/
md: https://developers.cloudflare.com/changelog/2025-07-22-media-transformations-audio-mode/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Audio mode for Media Transformations
Jul 22, 2025
[Stream](https://developers.cloudflare.com/stream/)
We now support `audio` mode! Use this feature to extract audio from a source video, outputting an M4A file to use in downstream workflows like [AI inference](https://developers.cloudflare.com/workers-ai/), content moderation, or transcription.
For example,
```text
https://example.com/cdn-cgi/media//
https://example.com/cdn-cgi/media/mode=audio,time=3s,duration=60s/
```
For more information, learn about [Transforming Videos](https://developers.cloudflare.com/stream/transform-videos/).
---
title: WARP client for Linux (version 2025.5.943.0) · Changelog
description: WARP client for Linux (version 2025.5.943.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-23-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-07-23-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.5.943.0)
Jul 23, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* WARP proxy mode now uses the operating system's DNS settings. Changes made to system DNS settings while in proxy mode require the client to be turned off then back on to take effect.
* Fixed an issue affecting clients in Split Tunnel Include mode, where access to split-tunneled traffic was blocked after reconnecting the client.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for macOS (version 2025.5.943.0) · Changelog
description: WARP client for macOS (version 2025.5.943.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-23-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-07-23-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.5.943.0)
Jul 23, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* WARP proxy mode now uses the operating system's DNS settings. Changes made to system DNS settings while in proxy mode require the client to be turned off then back on to take effect.
* Fixed an issue affecting clients in Split Tunnel Include mode, where access to split-tunneled traffic was blocked after reconnecting the client.
* For macOS deployments, the WARP client can now be managed using an `mdm.xml` file placed in `/Library/Application Support/Cloudflare/mdm.xml`. This new configuration option offers an alternative to the still supported method of deploying a managed plist through an MDM solution.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.5.943.0) · Changelog
description: WARP client for Windows (version 2025.5.943.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-23-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-07-23-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.5.943.0)
Jul 23, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* WARP proxy mode now uses the operating system's DNS settings. Changes made to system DNS settings while in proxy mode require the client to be turned off then back on to take effect.
* Changes to the [SCCM VPN boundary support](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#sccm-vpn-boundary-support) feature to no longer restart the SMS Agent Host (`ccmexec.exe`) service.
* Fixed an issue affecting clients in Split Tunnel Include mode, where access to split-tunneled traffic was blocked after reconnecting the client.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Test out code changes before shipping with per-branch preview deployments
for Cloudflare Workers · Changelog
description: Get shareable preview links for every code change you make to a
Cloudflare Worker, making it easier to test and collaborate before going live
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-23-workers-preview-urls/
md: https://developers.cloudflare.com/changelog/2025-07-23-workers-preview-urls/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Test out code changes before shipping with per-branch preview deployments for Cloudflare Workers
Jul 22, 2025
[Workers](https://developers.cloudflare.com/workers/)
Now, when you connect your Cloudflare Worker to a git repository on GitHub or GitLab, each branch of your repository has its own stable preview URL, that you can use to preview code changes before merging the pull request and deploying to production.
This works the same way that Cloudflare Pages does — every time you create a pull request, you'll automatically get a shareable preview link where you can see your changes running, without affecting production. The link stays the same, even as you add commits to the same branch. These preview URLs are named after your branch and are posted as a comment to each pull request. The URL stays the same with every commit and always points to the latest version of that branch.
#### Preview URL types
Each comment includes **two preview URLs** as shown above:
* **Commit Preview URL**: Unique to the specific version/commit (e.g., `-..workers.dev`)
* **Branch Preview URL**: A stable alias based on the branch name (e.g., `-..workers.dev`)
#### How it works
When you create a pull request:
* **A preview alias is automatically created** based on the Git branch name (e.g., `` becomes `-..workers.dev`)
* **No configuration is needed**, the alias is generated for you
* **The link stays the same** even as you add commits to the same branch
* **Preview URLs are posted directly to your pull request as comments** (just like they are in Cloudflare Pages)
#### Custom alias name
You can also assign a custom preview alias using the [Wrangler CLI](https://developers.cloudflare.com/workers/wrangler/), by passing the `--preview-alias` flag when [uploading a version](https://developers.cloudflare.com/workers/wrangler/commands/#versions-upload) of your Worker:
```bash
wrangler versions upload --preview-alias staging
```
#### Limitations while in beta
* Only available on the **workers.dev** subdomain (custom domains not yet supported)
* Requires **Wrangler v4.21.0+**
* Preview URLs are not generated for Workers that use [Durable Objects](https://developers.cloudflare.com/durable-objects/)
* Not yet supported for [Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
---
title: Gateway HTTP Filtering on all ports available in open BETA · Changelog
description: Gateway can now apply HTTP filtering to all HTTP requests proxied!
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-24-http-inspection-on-all-ports/
md: https://developers.cloudflare.com/changelog/2025-07-24-http-inspection-on-all-ports/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Gateway HTTP Filtering on all ports available in open BETA
Jul 24, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) can now apply [HTTP filtering](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/) to all proxied HTTP requests, not just traffic on standard HTTP (`80`) and HTTPS (`443`) ports. This means all requests can now be filtered by [A/V scanning](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/antivirus-scanning/), [file sandboxing](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/file-sandboxing/), [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/#data-in-transit), and more.
You can turn this [setting](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/protocol-detection/#inspect-on-all-ports) on by going to **Settings** > **Network** > **Firewall** and choosing *Inspect on all ports*.

To learn more, refer to [Inspect on all ports (Beta)](https://developers.cloudflare.com/cloudflare-one/traffic-policies/network-policies/protocol-detection/#inspect-on-all-ports).
---
title: WARP client for macOS (version 2025.6.824.1) · Changelog
description: WARP client for macOS (version 2025.6.824.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-24-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-07-24-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.6.824.1)
Jul 24, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement to managed network detection checks for faster switching between managed networks.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.6.824.1) · Changelog
description: WARP client for Windows (version 2025.6.824.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-24-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-07-24-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.6.824.1)
Jul 24, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Improvements to better manage multi-user pre-login registrations.
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement to managed network detection checks for faster switching between managed networks.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with `KB5055523` installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Introducing pricing for the Browser Rendering API — $0.09 per browser
hour · Changelog
description: Browser Rendering pricing announcement
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-28-br-pricing/
md: https://developers.cloudflare.com/changelog/2025-07-28-br-pricing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing pricing for the Browser Rendering API — $0.09 per browser hour
Jul 28, 2025
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We’ve launched pricing for [Browser Rendering](https://developers.cloudflare.com/browser-rendering/), including a free tier and a pay-as-you-go model that scales with your needs. Starting **August 20, 2025**, Cloudflare will begin billing for Browser Rendering.
There are two ways to use Browser Rendering. Depending on the method you use, here’s how billing will work:
* [**REST API**](https://developers.cloudflare.com/browser-rendering/rest-api/): Charged for **Duration** only ($/browser hour)
* [**Workers Bindings**](https://developers.cloudflare.com/browser-rendering/workers-bindings/): Charged for both **Duration** and **Concurrency** ($/browser hour and # of concurrent browsers)
Included usage and pricing by plan
| Plan | Included duration | Included concurrency | Price (beyond included) |
| - | - | - | - |
| **Workers Free** | 10 minutes per day | 3 concurrent browsers | N/A |
| **Workers Paid** | 10 hours per month | 10 concurrent browsers (averaged monthly) | **1. REST API**: $0.09 per additional browser hour **2. Workers Bindings**: $0.09 per additional browser hour $2.00 per additional concurrent browser |
What you need to know:
* **Workers Free Plan:** 10 minutes of browser usage per day with 3 concurrent browsers at no charge.
* **Workers Paid Plan:** 10 hours of browser usage per month with 10 concurrent browsers (averaged monthly) at no charge. Additional usage is charged as shown above.
You can monitor usage via the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/workers/browser-rendering). Go to **Compute (Workers)** > **Browser Rendering**.

If you've been using Browser Rendering and do not wish to incur charges, ensure your usage stays within your plan's [included usage](https://developers.cloudflare.com/browser-rendering/pricing/). To estimate costs, take a look at these [example pricing scenarios](https://developers.cloudflare.com/browser-rendering/pricing/#examples-of-workers-paid-pricing).
---
title: Scam domain category introduced under Security Threats · Changelog
description: You can now create policies specifically targeting the Scam content
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-28-spam-domain-category-introduced/
md: https://developers.cloudflare.com/changelog/2025-07-28-spam-domain-category-introduced/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Scam domain category introduced under Security Threats
Jul 28, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
We have introduced a new Security Threat category called **Scam**. Relevant domains are marked with the Scam category. Scam typically refers to fraudulent websites and schemes designed to trick victims into giving away money or personal information.
**New category added**
| Parent ID | Parent Name | Category ID | Category Name |
| - | - | - | - |
| 21 | Security Threats | 191 | Scam |
Refer to [Gateway domain categories](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) to learn more.
---
title: WAF Release - 2025-07-28 · Changelog
description: Cloudflare WAF managed rulesets 2025-07-28 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-28-waf-release/
md: https://developers.cloudflare.com/changelog/2025-07-28-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-07-28
Jul 28, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s update spotlights several vulnerabilities across Apache Tomcat, MongoDB, and Fortinet FortiWeb. Several flaws related with a memory leak in Apache Tomcat can lead to a denial-of-service attack. Additionally, a code injection flaw in MongoDB's Mongoose library allows attackers to bypass security controls to access restricted data.
**Key Findings**
* Fortinet FortiWeb (CVE-2025-25257): An improper neutralization of special elements used in a SQL command vulnerability in Fortinet FortiWeb versions allows an unauthenticated attacker to execute unauthorized SQL code or commands.
* Apache Tomcat (CVE-2025-31650): A improper Input Validation vulnerability in Apache Tomcat that could create memory leak when incorrect error handling for some invalid HTTP priority headers resulted in incomplete clean-up of the failed request.
* MongoDB (CVE-2024-53900, CVE:CVE-2025-23061): Improper use of `$where` in match and a nested `$where` filter with a `populate()` match in Mongoose can lead to search injection.
**Impact**
These vulnerabilities target user-facing components, web application servers, and back-end databases. A SQL injection flaw in Fortinet FortiWeb can lead to data theft or system compromise. A separate issue in Apache Tomcat involves a memory leak from improper input validation, which could be exploited for a denial-of-service (DoS) attack. Finally, a vulnerability in MongoDB's Mongoose library allows attackers to bypass security filters and access unauthorized data through malicious search queries.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 6ab3bd3b58fb4325ac2d3cc73461ec9e | 100804 | BerriAI - SSRF - CVE:CVE-2024-6587 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 2e6c4d02f42a4c3ca90649d50cb13e1d | 100812 | Fortinet FortiWeb - Remote Code Execution - CVE:CVE-2025-25257 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | fd360d8fd9994e6bab6fb06067fae7f7 | 100813 | Apache Tomcat - DoS - CVE:CVE-2025-31650 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | f9e01e28c5d6499cac66364b4b6a5bb1 | 100815 | MongoDB - Remote Code Execution - CVE:CVE-2024-53900, CVE:CVE-2025-23061 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 700d4fcc7b1f481a80cbeee5688f8e79 | 100816 | MongoDB - Remote Code Execution - CVE:CVE-2024-53900, CVE:CVE-2025-23061 | Log | Block | This is a New Detection |
---
title: Audit logs (version 2) - UI Beta Release · Changelog
description: New version of audit logs UI
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-29-audit-logs-v2-ui-beta/
md: https://developers.cloudflare.com/changelog/2025-07-29-audit-logs-v2-ui-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Audit logs (version 2) - UI Beta Release
Jul 29, 2025
[Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/)
The Audit Logs v2 UI is now available to all Cloudflare customers in Beta. This release builds on the public [Beta of the Audit Logs v2 API](https://developers.cloudflare.com/changelog/?product=audit-logs) and introduces a redesigned user interface with powerful new capabilities to make it easier to investigate account activity.
**Enabling the new UI**
To try the new user interface, go to **Manage Account > Audit Logs**. The previous version of Audit Logs remains available and can be re-enabled at any time using the **Switch back to old Audit Logs** link in the banner at the top of the page.
**New Features:**
* **Advanced Filtering**: Filter logs by actor, resource, method, and more for faster insights.
* **On-hover filter controls**: Easily include or exclude values in queries by hovering over fields within a log entry.
* **Detailed Log Sidebar**: View rich context for each log entry without leaving the main view.
* **JSON Log View**: Inspect the raw log data in a structured JSON format.
* **Custom Time Ranges**: Define your own time windows to view historical activity.
* **Infinite Scroll**: Seamlessly browse logs without clicking through pages.

For more details on Audit Logs v2, see the [Audit Logs documentation](https://developers.cloudflare.com/fundamentals/account/account-security/audit-logs/).
**Known issues**
* A small number of audit logs may currently be unavailable in Audit Logs v2. In some cases, certain fields such as actor information may be missing in certain audit logs. We are actively working to improve coverage and completeness for General Availability.
* Export to CSV is not supported in the new UI.
We are actively refining the Audit Logs v2 experience and welcome your feedback. You can share overall feedback by clicking the thumbs up or thumbs down icons at the top of the page, or provide feedback on specific audit log entries using the thumbs icons next to each audit log line or by filling out our [feedback form](https://docs.google.com/forms/d/e/1FAIpQLSfXGkJpOG1jUPEh-flJy9B13icmcdBhveFwe-X0EzQjJQnQfQ/viewform?usp=sharing).
---
title: Magic Transit and Magic WAN health check data is fully compatible with
the CMB EU setting. · Changelog
description: Magic Transit and Magic WAN customers that enable the CMB EU
setting can access their health check data in the Cloudflare dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-07-30-mt-mwan-health-check-cmb-eu/
md: https://developers.cloudflare.com/changelog/2025-07-30-mt-mwan-health-check-cmb-eu/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Magic Transit and Magic WAN health check data is fully compatible with the CMB EU setting.
Jul 30, 2025
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Today, we are excited to announce that all Magic Transit and Magic WAN customers with CMB EU ([Customer Metadata Boundary - Europe](https://developers.cloudflare.com/data-localization/metadata-boundary/)) enabled in their account will be able to access GRE, IPsec, and CNI health check and traffic volume data in the Cloudflare dashboard and via API.
This ensures that all Magic Transit and Magic WAN customers with CMB EU enabled will be able to access all Magic Transit and Magic WAN features.
Specifically, these two GraphQL endpoints are now compatible with CMB EU:
* `magicTransitTunnelHealthChecksAdaptiveGroups`
* `magicTransitTunnelTrafficAdaptiveGroups`
---
title: Develop locally with Containers and the Cloudflare Vite plugin · Changelog
description: The Cloudflare Vite plugin now supports configuring Containers in your Worker
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-01-containers-in-vite-dev/
md: https://developers.cloudflare.com/changelog/2025-08-01-containers-in-vite-dev/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Develop locally with Containers and the Cloudflare Vite plugin
Aug 01, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now configure and run [Containers](https://developers.cloudflare.com/containers) alongside your [Worker](https://developers.cloudflare.com/workers) during local development when using the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/). Previously, you could only develop locally when using [Wrangler](https://developers.cloudflare.com/workers/wrangler/) as your local development server.
#### Configuration
You can simply configure your Worker and your Container(s) in your Wrangler configuration file:
* wrangler.jsonc
```jsonc
{
"name": "container-starter",
"main": "src/index.js",
"containers": [
{
"class_name": "MyContainer",
"image": "./Dockerfile",
"instances": 5
}
],
"durable_objects": {
"bindings": [
{
"class_name": "MyContainer",
"name": "MY_CONTAINER"
}
]
},
"migrations": [
{
"new_sqlite_classes": [
"MyContainer"
],
"tag": "v1"
}
],
}
```
* wrangler.toml
```toml
name = "container-starter"
main = "src/index.js"
[[containers]]
class_name = "MyContainer"
image = "./Dockerfile"
instances = 5
[[durable_objects.bindings]]
class_name = "MyContainer"
name = "MY_CONTAINER"
[[migrations]]
new_sqlite_classes = [ "MyContainer" ]
tag = "v1"
```
#### Worker Code
Once your Worker and Containers are configured, you can access the Container instances from your Worker code:
```ts
import { Container, getContainer } from "@cloudflare/containers";
export class MyContainer extends Container {
defaultPort = 4000; // Port the container is listening on
sleepAfter = "10m"; // Stop the instance if requests not sent for 10 minutes
}
async fetch(request, env) {
const { "session-id": sessionId } = await request.json();
// Get the container instance for the given session ID
const containerInstance = getContainer(env.MY_CONTAINER, sessionId)
// Pass the request to the container instance on its default port
return containerInstance.fetch(request);
}
```
#### Local development
To develop your Worker locally, start a local dev server by running
```sh
vite dev
```
in your terminal.
#### Resources
Learn more about [Cloudflare Containers](https://developers.cloudflare.com/containers/) or the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/) in our developer docs.
---
title: Terraform v5.8.2 now available · Changelog
description: Terraform v5.8.2 stablizes a number of resources and known issues
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-01-terraform-v582-provider/
md: https://developers.cloudflare.com/changelog/2025-08-01-terraform-v582-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.8.2 now available
Aug 01, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high mumber of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a 2 week cadeance to ensure it's stability and reliability. We have also pivoted from an issue-to-issue approach to a resource-per-resource approach - we will be focusing on specific resources for every release, stablizing the release and closing all associated bugs with that resource before moving onto resolving migration issues.
Thank you for continuing to raise issues. We triage them weekly and they help make our products stronger.
#### Changes
* Resources stablized:
* `cloudflare_custom_pages`
* `cloudflare_page_rule`
* `cloudflare_dns_record`
* `cloudflare_argo_tiered_caching`
* Addressed chronic drift issues in `cloudflare_logpush_job`, `cloudflare_zero_trust_dns_location`, `cloudflare_ruleset` & `cloudflare_api_token`
* `cloudflare_zone_subscripton` returns expected values `rate_plan.id` from former versions
* `cloudflare_workers_script` can now successfully be destroyed with bindings & migration for Durable Objects now recorded in tfstate
* Ability to configure `add_headers` under `cloudflare_zero_trust_gateway_policy`
* Other bug fixes
For a more detailed look at all of the changes, see the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.8.2) in GitHub.
#### Issues Closed
* [#5666: cloudflare\_ruleset example lists id which is a read-only field](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5666)
* [#5578: cloudflare\_logpush\_job plan always suggests changes](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5578)
* [#5552: 5.4.0: Since provider update, existing cloudflare\_list\_item would be recreated "created" state](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5552)
* [#5670: cloudflare\_zone\_subscription: uses wrong ID field in Read/Update](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5670)
* [#5548: cloudflare\_api\_token resource always shows changes (drift)](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5548)
* [#5634: cloudflare\_workers\_script with bindings fails to be destroyed](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5634)
* [#5616: cloudflare\_workers\_script Unable to deploy worker assets](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5616)
* [#5331: cloudflare\_workers\_script 500 internal server error when uploading python](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5331)
* [#5701: cloudflare\_workers\_script migrations for Durable Objects not recorded in tfstate; cannot be upgraded between versions](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5701)
* [#5704: cloudflare\_workers\_script randomly fails to deploy when changing compatibility\_date](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5704)
* [#5439: cloudflare\_workers\_script (v5.2.0) ignoring content and bindings properties](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5439)
* [#5522: cloudflare\_workers\_script always detects changes after apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5522)
* [#5693: cloudflare\_zero\_trust\_access\_identity\_provider gives recurring change on OTP pin login](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5693)
* [#5567: cloudflare\_r2\_custom\_domain doesn't roundtrip jurisdiction properly](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5567)
* [#5179: Bad request with when creating cloudflare\_api\_shield\_schema resource](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5179)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding off on migration to v5 while we work on stablization. This help will you avoid any blocking issues while the Terraform resources are actively being stablized.
If you'd like more information on migrating from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition, although these do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: Increased disk space for Workers Builds · Changelog
description: Increased the available disk space for Workers Builds from 8 GB to
20 GB for all plans during the ongoing open beta. - workers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-04-builds-increased-disk-size/
md: https://developers.cloudflare.com/changelog/2025-08-04-builds-increased-disk-size/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased disk space for Workers Builds
Aug 04, 2025
[Workers](https://developers.cloudflare.com/workers/)
As part of the ongoing open beta for [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/), we’ve increased the available disk space for builds from **8 GB** to **20 GB** for both Free and Paid plans.
This provides more space for larger projects, dependencies, and build artifacts while improving overall build reliability.
| Metric | Free Plan | Paid Plans |
| - | - | - |
| Disk Space | 20 GB | 20 GB |
All other [build limits](https://developers.cloudflare.com/workers/ci-cd/builds/limits-and-pricing/) — including CPU, memory, build minutes, and timeout remain unchanged.
---
title: Certificate Transparency Insights in Cloudflare Radar · Changelog
description: New Certificate Transparency (CT) insights in Cloudflare Radar,
with new API endpoints for certificate issuance trends
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-04-radar-ct-insights/
md: https://developers.cloudflare.com/changelog/2025-08-04-radar-ct-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Certificate Transparency Insights in Cloudflare Radar
Aug 06, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) now introduces Certificate Transparency (CT) insights, providing visibility into certificate issuance trends based on Certificate Transparency logs currently monitored by Cloudflare.
The following API endpoints are now available:
* [`/ct/timeseries`](https://developers.cloudflare.com/api/resources/radar/subresources/ct/methods/timeseries/): Retrieves certificate issuance time series.
* [`/ct/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/ct/methods/summary/): Retrieves certificate distribution by dimension.
* [`/ct/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/ct/methods/timeseries_groups/): Retrieves time series of certificate distribution by dimension.
* [`/ct/authorities`](https://developers.cloudflare.com/api/resources/radar/subresources/ct/subresources/authorities/methods/list/): Lists certification authorities.
* [`/ct/authorities/{ca_slug}`](https://developers.cloudflare.com/api/resources/radar/subresources/ct/subresources/authorities/methods/get/): Retrieves details about a Certification Authority (CA). CA information is derived from the [Common CA Database (CCADB)](https://www.ccadb.org/).
* [`/ct/logs`](https://developers.cloudflare.com/api/resources/radar/subresources/ct/subresources/logs/methods/list/): Lists CT logs.
* [`/ct/logs/{log_slug}`](https://developers.cloudflare.com/api/resources/radar/subresources/ct/subresources/logs/methods/get/): Retrieves details about a CT log. CT log information is derived from the [Google Chrome log list](https://googlechrome.github.io/CertificateTransparency/log_lists.html).
For the `summary` and `timeseries_groups` endpoints, the following dimensions are available (and also usable as filters):
* `ca`: Certification Authority (certificate issuer)
* `ca_owner`: Certification Authority Owner
* `duration`: Certificate validity duration (between NotBefore and NotAfter dates)
* `entry_type`: Entry type (certificate vs. pre-certificate)
* `expiration_status`: Expiration status (valid vs. expired)
* `has_ips`: Presence of IP addresses in certificate [Subject Alternative Names (SANs)](https://developers.cloudflare.com/ssl/origin-configuration/origin-ca/#hostname-and-wildcard-coverage)
* `has_wildcards`: Presence of wildcard DNS names in certificate SANs
* `log`: CT log name
* `log_api`: CT log API ([RFC6962](https://datatracker.ietf.org/doc/html/rfc6962) vs. [Static](https://c2sp.org/static-ct-api))
* `log_operator`: CT log operator
* `public_key_algorithm`: Public key algorithm of certificate's key
* `signature_algorithm`: Signature algorithm used by CA to sign certificate
* `tld`: Top-level domain for DNS names found in certificates SANs
* `validation_level`: [Validation level](https://www.cloudflare.com/learning/ssl/types-of-ssl-certificates/)
Check out the new Certificate Transparency insights in the [new Radar page](https://radar.cloudflare.com/certificate-transparency).
---
title: WAF Release - 2025-08-04 · Changelog
description: Cloudflare WAF managed rulesets 2025-08-04 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-04-waf-release/
md: https://developers.cloudflare.com/changelog/2025-08-04-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-08-04
Aug 04, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's highlight focuses on a series of significant vulnerabilities identified across widely adopted web platforms, from enterprise-grade CMS to essential backend administration tools. The findings reveal multiple vectors for attack, including critical flaws that allow for full server compromise and others that enable targeted attacks against users.
**Key Findings**
* Sitecore (CVE-2025-34509, CVE-2025-34510, CVE-2025-34511): A hardcoded credential allows remote attackers to access administrative APIs. Once authenticated, they can exploit an additional vulnerability to upload arbitrary files, leading to remote code execution.
* Grafana (CVE-2025-4123): A cross-site scripting (XSS) vulnerability allows an attacker to redirect users to a malicious website, which can then execute arbitrary JavaScript in the victim's browser.
* LaRecipe (CVE-2025-53833): Through Server-Side Template Injection, attackers can execute arbitrary commands on the server, potentially access sensitive environment variables, and escalate access depending on server configuration.
* CentOS WebPanel (CVE-2025-48703): A command injection vulnerability could allow a remote attacker to execute arbitrary commands on the server.
* WordPress (CVE-2023-5561): This vulnerability allows unauthenticated attackers to determine the email addresses of users who have published public posts on an affected website.
* WordPress Plugin - WPBookit (CVE-2025-6058): A missing file type validation allows unauthenticated attackers to upload arbitrary files to the server, creating the potential for remote code execution.
* WordPress Theme - Motors (CVE-2025-4322): Due to improper identity validation, an unauthenticated attacker can change the passwords of arbitrary users, including administrators, to gain access to their accounts.
**Impact**
These vulnerabilities pose a multi-layered threat to widely adopted web technologies, ranging from enterprise-grade platforms like Sitecore to everyday solutions such as WordPress, and backend tools like CentOS WebPanel. The most severe risks originate in remote code execution (RCE) flaws found in Sitecore, CentOS WebPanel, LaRecipe, and the WPBookit plugin. These allow attackers to bypass security controls and gain deep access to the server, enabling them to steal sensitive data, deface websites, install persistent malware, or use the compromised server as a launchpad for further attacks.
The privilege escalation vulnerability is the Motors theme, which allows for a complete administrative account takeover on WordPress sites. This effectively hands control of the application to an attacker, who can then manipulate content, exfiltrate user data, and alter site functionality without needing to breach the server itself.
The Grafana cross-site scripting (XSS) flaw can be used to hijack authenticated user sessions or steal credentials, turning a trusted user's browser into an attack vector.
Meanwhile, the information disclosure flaw in WordPress core provides attackers with valid user emails, fueling targeted phishing campaigns that aim to secure the same account access achievable through the other exploits.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | b8ab4644f8044f3485441ee052f30a13 | 100535A | Sitecore - Dangerous File Upload - CVE:CVE-2025-34510, CVE:CVE-2025-34511 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 06d1fe0bd6e44d868e6b910b5045a97f | 100535 | Sitecore - Information Disclosure - CVE:CVE-2025-34509 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | f71ce87ea6e54eab999223df579cd3e0 | 100543 | Grafana - Directory Traversal - CVE:CVE-2025-4123 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | bba3d37891a440fb8bc95b970cbd9abc | 100545 | WordPress - Information Disclosure - CVE:CVE-2023-5561 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 28108d25f1cf470c8e7648938f634977 | 100820 | CentOS WebPanel - Remote Code Execution - CVE:CVE-2025-48703 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 9d69c796a61444a3aca33dc282ae64c1 | 100821 | LaRecipe - SSTI - CVE:CVE-2025-53833 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 9b5c5e13d2ca4253a89769f2194f7b2d | 100822 | WordPress:Plugin:WPBookit - Remote Code Execution - CVE:CVE-2025-6058 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 69d43d704b0641898141a4300bf1b661 | 100823 | WordPress:Theme:Motors - Privilege Escalation - CVE:CVE-2025-4322 | Log | Block | This is a New Detection |
---
title: Agents SDK adds MCP Elicitation support, http-streamable suppport, task
queues, email integration and more · Changelog
description: Major update brings MCP elicitation, enhanced transport
options,auto transport selection, improved error handling, and reliable prop
updates, task queues, and email support
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-05-agents-mcp-update/
md: https://developers.cloudflare.com/changelog/2025-08-05-agents-mcp-update/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Agents SDK adds MCP Elicitation support, http-streamable suppport, task queues, email integration and more
Aug 05, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
The latest releases of [@cloudflare/agents](https://github.com/cloudflare/agents) brings major improvements to MCP transport protocols support and agents connectivity. Key updates include:
#### MCP elicitation support
MCP servers can now request user input during tool execution, enabling interactive workflows like confirmations, forms, and multi-step processes. This feature uses durable storage to preserve elicitation state even during agent hibernation, ensuring seamless user interactions across agent lifecycle events.
```ts
// Request user confirmation via elicitation
const confirmation = await this.elicitInput({
message: `Are you sure you want to increment the counter by ${amount}?`,
requestedSchema: {
type: "object",
properties: {
confirmed: {
type: "boolean",
title: "Confirm increment",
description: "Check to confirm the increment",
},
},
required: ["confirmed"],
},
});
```
Check out our [demo](https://github.com/whoiskatrin/agents/tree/main/examples/mcp-elicitation-demo) to see elicitation in action.
#### HTTP streamable transport for MCP
MCP now supports HTTP streamable transport which is recommended over SSE. This transport type offers:
* **Better performance**: More efficient data streaming and reduced overhead
* **Improved reliability**: Enhanced connection stability and error recover- **Automatic fallback**: If streamable transport is not available, it gracefully falls back to SSE
```ts
export default MyMCP.serve("/mcp", {
binding: "MyMCP",
});
```
The SDK automatically selects the best available transport method, gracefully falling back from streamable-http to SSE when needed.
#### Enhanced MCP connectivity
Significant improvements to MCP server connections and transport reliability:
* **Auto transport selection**: Automatically determines the best transport method, falling back from streamable-http to SSE as needed
* **Improved error handling**: Better connection state management and error reporting for MCP servers
* **Reliable prop updates**: Centralized agent property updates ensure consistency across different contexts
#### Lightweight .queue for fast task deferral
You can use `.queue()` to enqueue background work — ideal for tasks like processing user messages, sending notifications etc.
```ts
class MyAgent extends Agent {
doSomethingExpensive(payload) {
// a long running process that you want to run in the background
}
queueSomething() {
await this.queue("doSomethingExpensive", somePayload); // this will NOT block further execution, and runs in the background
await this.queue("doSomethingExpensive", someOtherPayload); // the callback will NOT run until the previous callback is complete
// ... call as many times as you want
}
}
```
Want to try it yourself? Just define a method like processMessage in your agent, and you’re ready to scale.
#### New email adapter
Want to build an AI agent that can receive and respond to emails automatically? With the new email adapter and onEmail lifecycle method, now you can.
```ts
export class EmailAgent extends Agent {
async onEmail(email: AgentEmail) {
const raw = await email.getRaw();
const parsed = await PostalMime.parse(raw);
// create a response based on the email contents
// and then send a reply
await this.replyToEmail(email, {
fromName: "Email Agent",
body: `Thanks for your email! You've sent us "${parsed.subject}". We'll process it shortly.`,
});
}
}
```
You route incoming mail like this:
```ts
export default {
async email(email, env) {
await routeAgentEmail(email, env, {
resolver: createAddressBasedEmailResolver("EmailAgent"),
});
},
};
```
You can find a full example [here](https://github.com/cloudflare/agents/tree/main/examples/email-agent).
#### Automatic context wrapping for custom methods
Custom methods are now automatically wrapped with the agent's context, so calling `getCurrentAgent()` should work regardless of where in an agent's lifecycle it's called. Previously this would not work on RPC calls, but now just works out of the box.
```ts
export class MyAgent extends Agent {
async suggestReply(message) {
// getCurrentAgent() now correctly works, even when called inside an RPC method
const { agent } = getCurrentAgent()!;
return generateText({
prompt: `Suggest a reply to: "${message}" from "${agent.name}"`,
tools: [replyWithEmoji],
});
}
}
```
Try it out and tell us what you build!
---
title: OpenAI open models now available on Workers AI · Changelog
description: Partnering with OpenAI as a Day 0 launch partner to bring you 2 new
open models on Workers AI
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-05-openai-open-models/
md: https://developers.cloudflare.com/changelog/2025-08-05-openai-open-models/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## OpenAI open models now available on Workers AI
Aug 05, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers AI](https://developers.cloudflare.com/workers-ai/)
We're thrilled to be a Day 0 partner with [OpenAI](http://openai.com/index/introducing-gpt-oss) to bring their [latest open models](https://openai.com/index/gpt-oss-model-card/) to Workers AI, including support for Responses API, Code Interpreter, and Web Search (coming soon).
Get started with the new models at `@cf/openai/gpt-oss-120b` and `@cf/openai/gpt-oss-20b`. Check out the [blog](https://blog.cloudflare.com/openai-gpt-oss-on-workers-ai) for more details about the new models, and the [`gpt-oss-120b`](https://developers.cloudflare.com/workers-ai/models/gpt-oss-120b) and [`gpt-oss-20b`](https://developers.cloudflare.com/workers-ai/models/gpt-oss-20b) model pages for more information about pricing and context windows.
#### Responses API
If you call the model through:
* Workers Binding, it will accept/return Responses API – `env.AI.run(“@cf/openai/gpt-oss-120b”)`
* REST API on `/run` endpoint, it will accept/return Responses API – `https://api.cloudflare.com/client/v4/accounts//ai/run/@cf/openai/gpt-oss-120b`
* REST API on new `/responses` endpoint, it will accept/return Responses API – `https://api.cloudflare.com/client/v4/accounts//ai/v1/responses`
* REST API for OpenAI Compatible endpoint, it will return Chat Completions (coming soon) – `https://api.cloudflare.com/client/v4/accounts//ai/v1/chat/completions`
```plaintext
curl https://api.cloudflare.com/client/v4/accounts//ai/v1/responses \
-H "Content-Type: application/json" \
-H "Authorization: Bearer $CLOUDFLARE_API_KEY" \
-d '{
"model": "@cf/openai/gpt-oss-120b",
"reasoning": {"effort": "medium"},
"input": [
{
"role": "user",
"content": "What are the benefits of open-source models?"
}
]
}'
```
#### Code Interpreter
The model is natively trained to support stateful code execution, and we've implemented support for this feature using our [Sandbox SDK](https://github.com/cloudflare/sandbox-sdk) and [Containers](https://blog.cloudflare.com/containers-are-available-in-public-beta-for-simple-global-and-programmable/). Cloudflare's Developer Platform is uniquely positioned to support this feature, so we're very excited to bring our products together to support this new use case.
#### Web Search (coming soon)
We are working to implement Web Search for the model, where users can bring their own Exa API Key so the model can browse the Internet.
---
title: Cloudflare Sandbox SDK adds streaming, code interpreter, Git support,
process control and more · Changelog
description: The latest release transforms the Sandbox SDK into a full
edge-native code execution platform, enabling secure, containerized runtimes
with real-time streaming, language interpreters, Git integration, process
lifecycle management, and port forwarding.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-05-sandbox-sdk-major-update/
md: https://developers.cloudflare.com/changelog/2025-08-05-sandbox-sdk-major-update/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Sandbox SDK adds streaming, code interpreter, Git support, process control and more
Aug 05, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We’ve shipped a major release for the [@cloudflare/sandbox](https://github.com/cloudflare/sandbox-sdk) SDK, turning it into a full-featured, container-based execution platform that runs securely on Cloudflare Workers.
This update adds live streaming of output, persistent Python and JavaScript code interpreters with rich output support (charts, tables, HTML, JSON), file system access, Git operations, full background process control, and the ability to expose running services via public URLs.
This makes it ideal for building AI agents, CI runners, cloud REPLs, data analysis pipelines, or full developer tools — all without managing infrastructure.
#### Code interpreter (Python, JS, TS)
Create persistent code contexts with support for rich visual + structured outputs.
#### createCodeContext(options)
Creates a new code execution context with persistent state.
```ts
// Create a Python context
const pythonCtx = await sandbox.createCodeContext({ language: "python" });
// Create a JavaScript context
const jsCtx = await sandbox.createCodeContext({ language: "javascript" });
```
Options:
* language: Programming language ('python' | 'javascript' | 'typescript')
* cwd: Working directory (default: /workspace)
* envVars: Environment variables for the context
#### runCode(code, options)
Executes code with optional streaming callbacks.
```ts
// Simple execution
const execution = await sandbox.runCode('print("Hello World")', {
context: pythonCtx,
});
// With streaming callbacks
await sandbox.runCode(
`
for i in range(5):
print(f"Step {i}")
time.sleep(1)
`,
{
context: pythonCtx,
onStdout: (output) => console.log("Real-time:", output.text),
onResult: (result) => console.log("Result:", result),
},
);
```
Options:
* language: Programming language ('python' | 'javascript' | 'typescript')
* cwd: Working directory (default: /workspace)
* envVars: Environment variables for the context
#### Real-time streaming output
Returns a streaming response for real-time processing.
```ts
const stream = await sandbox.runCodeStream(
"import time; [print(i) for i in range(10)]",
);
// Process the stream as needed
```
#### Rich output handling
Interpreter outputs are auto-formatted and returned in multiple formats:
* text
* html (e.g., Pandas tables)
* png, svg (e.g., Matplotlib charts)
* json (structured data)
* chart (parsed visualizations)
```ts
const result = await sandbox.runCode(
`
import seaborn as sns
import matplotlib.pyplot as plt
data = sns.load_dataset("flights")
pivot = data.pivot("month", "year", "passengers")
sns.heatmap(pivot, annot=True, fmt="d")
plt.title("Flight Passengers")
plt.show()
pivot.to_dict()
`,
{ context: pythonCtx },
);
if (result.png) {
console.log("Chart output:", result.png);
}
```
#### Preview URLs from Exposed Ports
Start background processes and expose them with live URLs.
```ts
await sandbox.startProcess("python -m http.server 8000");
const preview = await sandbox.exposePort(8000);
console.log("Live preview at:", preview.url);
```
#### Full process lifecycle control
Start, inspect, and terminate long-running background processes.
```ts
const process = await sandbox.startProcess("node server.js");
console.log(`Started process ${process.id} with PID ${process.pid}`);
// Monitor the process
const logStream = await sandbox.streamProcessLogs(process.id);
for await (const log of parseSSEStream(logStream)) {
console.log(`Server: ${log.data}`);
}
```
* listProcesses() - List all running processes
* getProcess(id) - Get detailed process status
* killProcess(id, signal) - Terminate specific processes
* killAllProcesses() - Kill all processes
* streamProcessLogs(id, options) - Stream logs from running processes
* getProcessLogs(id) - Get accumulated process output
#### Git integration
Clone Git repositories directly into the sandbox.
```ts
await sandbox.gitCheckout("https://github.com/user/repo", {
branch: "main",
targetDir: "my-project",
});
```
Sandboxes are still experimental. We're using them to explore how isolated, container-like workloads might scale on Cloudflare — and to help define the developer experience around them.
---
title: Improvements to Monitoring Using Zone Settings · Changelog
description: Monitors configured with a probe zone have been migrated to new infrastructure.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-06-zone-monitoring-improvements/
md: https://developers.cloudflare.com/changelog/2025-08-06-zone-monitoring-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improvements to Monitoring Using Zone Settings
Aug 06, 2025
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
Cloudflare Load Balancing Monitors support loading and applying settings for a specific zone to monitoring requests to origin endpoints. This feature has been migrated to new infrastructure to improve reliability, performance, and accuracy.
All zone monitors have been tested against the new infrastructure. There should be no change to health monitoring results of currently healthy and active pools. Newly created or re-enabled pools may need validation of their monitor zone settings before being introduced to service, especially regarding correct application of mTLS.
#### What you can expect:
* More reliable application of zone settings to monitoring requests, including
* Authenticated Origin Pulls
* Aegis Egress IP Pools
* Argo Smart Routing
* HTTP/2 to Origin
* Improved support and bug fixes for retries, redirects, and proxied origin resolution
* Improved performance and reliability of monitoring requests withing the Cloudflare network
* Unrelated CDN or WAF configuration changes should have no risk of impact to pool health
---
title: Requests made from Cloudflare Workers can now force a revalidation of
their cache with the origin · Changelog
description: New runtime APIs allow you to control when subrequests revalidate
cache, increasing compatibility with popular NPM packages
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-07-cache-no-cache/
md: https://developers.cloudflare.com/changelog/2025-08-07-cache-no-cache/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Requests made from Cloudflare Workers can now force a revalidation of their cache with the origin
Aug 07, 2025
[Workers](https://developers.cloudflare.com/workers/)
By setting the value of the `cache` property to `no-cache`, you can force [Cloudflare's cache](https://developers.cloudflare.com/workers/reference/how-the-cache-works/) to revalidate its contents with the origin when making subrequests from [Cloudflare Workers](https://developers.cloudflare.com/workers).
* JavaScript
```js
export default {
async fetch(req, env, ctx) {
const request = new Request("https://cloudflare.com", {
cache: "no-cache",
});
const response = await fetch(request);
return response;
},
};
```
* TypeScript
```ts
export default {
async fetch(req, env, ctx): Promise {
const request = new Request("https://cloudflare.com", { cache: 'no-cache'});
const response = await fetch(request);
return response;
}
} satisfies ExportedHandler
```
When `no-cache` is set, the Worker request will first look for a match in Cloudflare's cache, then:
* If there is a match, a conditional request is sent to the origin, regardless of whether or not the match is fresh or stale. If the resource has not changed, the cached version is returned. If the resource has changed, it will be downloaded from the origin, updated in the cache, and returned.
* If there is no match, Workers will make a standard request to the origin and cache the response.
This increases compatibility with NPM packages and JavaScript frameworks that rely on setting the [`cache`](https://developers.cloudflare.com/workers/runtime-apis/request/#options) property, which is a cross-platform standard part of the [`Request`](https://developers.cloudflare.com/workers/runtime-apis/request/) interface. Previously, if you set the `cache` property on `Request` to `'no-cache'`, the Workers runtime threw an exception.
* Learn [how the Cache works with Cloudflare Workers](https://developers.cloudflare.com/workers/reference/how-the-cache-works/)
* Enable [Node.js compatibility](https://developers.cloudflare.com/workers/runtime-apis/nodejs/) for your Cloudflare Worker
* Explore [Runtime APIs](https://developers.cloudflare.com/workers/runtime-apis/) and [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) available in Cloudflare Workers
---
title: WAF Release - 2025-08-07 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-08-07 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-07-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-08-07-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-08-07 - Emergency
Aug 07, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s highlight focuses on two critical vulnerabilities affecting key infrastructure and enterprise content management platforms. Both flaws present significant remote code execution risks that can be exploited with minimal or no user interaction.
**Key Findings**
* Squid (≤6.3) — CVE-2025-54574: A heap buffer overflow occurs when processing Uniform Resource Names (URNs). This vulnerability may allow remote attackers to execute arbitrary code on the server. The issue has been resolved in version 6.4.
* Adobe AEM (≤6.5.23) — CVE-2025-54253: Due to a misconfiguration, attackers can achieve remote code execution without requiring any user interaction, posing a severe threat to affected deployments.
**Impact**
Both vulnerabilities expose critical attack vectors that can lead to full server compromise. The Squid heap buffer overflow allows remote code execution by crafting malicious URNs, which can lead to server takeover or denial of service. Given Squid’s widespread use as a caching proxy, this flaw could be exploited to disrupt network traffic or gain footholds inside secure environments.
Adobe AEM’s remote code execution vulnerability enables attackers to run arbitrary code on the content management server without any user involvement. This puts sensitive content, application integrity, and the underlying infrastructure at extreme risk. Exploitation could lead to data theft, defacement, or persistent backdoor installation.
These findings reinforce the urgency of updating to the patched versions — Squid 6.4 and Adobe AEM 6.5.24 or later — and reviewing configurations to prevent exploitation.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | f61ed7c1e7e24c3380289e41ef7e015b | 100844 | Adobe Experience Manager Forms - Remote Code Execution - CVE:CVE-2025-54253 | N/A | Block | This is a New Detection |
| Cloudflare Managed Ruleset | e76e65f5a3aa43f49e0684a6baec057a | 100840 | Squid - Buffer Overflow - CVE:CVE-2025-54574 | N/A | Block | This is a New Detection |
---
title: Expanded Email Link Isolation · Changelog
description: You can now apply email link isolation based on disposition
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-07-expanded-link-isolation/
md: https://developers.cloudflare.com/changelog/2025-08-07-expanded-link-isolation/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Expanded Email Link Isolation
Aug 07, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
When you deploy MX or Inline, not only can you apply email link isolation to suspicious links in all emails (including benign), you can now also apply email link isolation to all links of a specified disposition. This provides more flexibility in controlling user actions within emails.
For example, you may want to deliver suspicious messages but isolate the links found within them so that users who choose to interact with the links will not accidentally expose your organization to threats. This means your end users are more secure than ever before.

To isolate all links within a message based on the disposition, select **Settings** > **Link Actions** > **View** and select **Configure**. As with other other links you isolate, an interstitial will be provided to warn users that this site has been isolated and the link will be recrawled live to evaluate if there are any changes in our threat intel. Learn more about this feature on [Configure link actions](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/configure-link-actions/).
This feature is available across these Email security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Directly import `waitUntil` in Workers for easily spawning background
tasks · Changelog
description: You can now import `waitUntil` from `cloudflare:workers` to extend
execution of background tasks without requiring the request context
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-08-add-waituntil-cloudflare-workers/
md: https://developers.cloudflare.com/changelog/2025-08-08-add-waituntil-cloudflare-workers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Directly import \`waitUntil\` in Workers for easily spawning background tasks
Aug 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now import [`waitUntil`](https://developers.cloudflare.com/workers/runtime-apis/context/#waituntil) from `cloudflare:workers` to extend your Worker's execution beyond the request lifecycle from anywhere in your code.
Previously, `waitUntil` could only be accessed through the [execution context](https://developers.cloudflare.com/workers/runtime-apis/context/) (`ctx`) parameter passed to your Worker's handler functions. This meant that if you needed to schedule background tasks from deeply nested functions or utility modules, you had to pass the `ctx` object through multiple function calls to access `waitUntil`.
Now, you can import `waitUntil` directly and use it anywhere in your Worker without needing to pass `ctx` as a parameter:
```js
import { waitUntil } from "cloudflare:workers";
export function trackAnalytics(eventData) {
const analyticsPromise = fetch("https://analytics.example.com/track", {
method: "POST",
body: JSON.stringify(eventData),
});
// Extend execution to ensure analytics tracking completes
waitUntil(analyticsPromise);
}
```
This is particularly useful when you want to:
* Schedule background tasks from utility functions or modules
* Extend execution for analytics, logging, or cleanup operations
* Avoid passing the execution context through multiple layers of function calls
```js
import { waitUntil } from "cloudflare:workers";
export default {
async fetch(request, env, ctx) {
// Background task that should complete even after response is sent
cleanupTempData(env.KV_NAMESPACE);
return new Response("Hello, World!");
}
};
function cleanupTempData(kvNamespace) {
// This function can now use waitUntil without needing ctx
const deletePromise = kvNamespace.delete("temp-key");
waitUntil(deletePromise);
}
```
Note
The imported `waitUntil` function works the same way as [`ctx.waitUntil()`](https://developers.cloudflare.com/workers/runtime-apis/context/#waituntil). It extends your Worker's execution to wait for the provided promise to settle, but does not block the response from being sent to the client.
For more information, see the [`waitUntil` documentation](https://developers.cloudflare.com/workers/runtime-apis/context/#waituntil).
---
title: Wrangler and the Cloudflare Vite plugin support `.env` files in local
development · Changelog
description: Use `.env` files to provide secrets and override environment
variables on the `env` object during local development.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-08-dot-env-in-local-dev/
md: https://developers.cloudflare.com/changelog/2025-08-08-dot-env-in-local-dev/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Wrangler and the Cloudflare Vite plugin support \`.env\` files in local development
Aug 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
Now, you can use `.env` files to provide secrets and override environment variables on the `env` object during local development with Wrangler and the Cloudflare Vite plugin.
Previously in local development, if you wanted to provide secrets or environment variables during local development, you had to use `.dev.vars` files. This is still supported, but you can now also use `.env` files, which are more familiar to many developers.
#### Using `.env` files in local development
You can create a `.env` file in your project root to define environment variables that will be used when running `wrangler dev` or `vite dev`. The `.env` file should be formatted like a `dotenv` file, such as `KEY="VALUE"`:
```bash
TITLE="My Worker"
API_TOKEN="dev-token"
```
When you run `wrangler dev` or `vite dev`, the environment variables defined in the `.env` file will be available in your Worker code via the `env` object:
```javascript
export default {
async fetch(request, env) {
const title = env.TITLE; // "My Worker"
const apiToken = env.API_TOKEN; // "dev-token"
const response = await fetch(
`https://api.example.com/data?token=${apiToken}`,
);
return new Response(`Title: ${title} - ` + (await response.text()));
},
};
```
#### Multiple environments with `.env` files
If your Worker defines multiple [environments](https://developers.cloudflare.com/workers/wrangler/environments/), you can set different variables for each environment (ex: production or staging) by creating files named `.env.`.
When you use `wrangler --env ` or `CLOUDFLARE_ENV= vite dev`, the corresponding environment-specific file will also be loaded and merged with the `.env` file.
For example, if you want to set different environment variables for the `staging` environment, you can create a file named `.env.staging`:
```bash
API_TOKEN="staging-token"
```
When you run `wrangler dev --env staging` or `CLOUDFLARE_ENV=staging vite dev`, the environment variables from `.env.staging` will be merged onto those from `.env`.
```javascript
export default {
async fetch(request, env) {
const title = env.TITLE; // "My Worker" (from `.env`)
const apiToken = env.API_TOKEN; // "staging-token" (from `.env.staging`, overriding the value from `.env`)
const response = await fetch(
`https://api.example.com/data?token=${apiToken}`,
);
return new Response(`Title: ${title} - ` + (await response.text()));
},
};
```
#### Find out more
For more information on how to use `.env` files with Wrangler and the Cloudflare Vite plugin, see the following documentation:
* [Environment variables and secrets](https://developers.cloudflare.com/workers/development-testing/environment-variables)
* [Wrangler Documentation](https://developers.cloudflare.com/workers/wrangler)
* [Cloudflare Vite Plugin Documentation](https://developers.cloudflare.com/workers/wrangler/vite)
---
title: Introducing observability and metrics for Stream Live Inputs · Changelog
description: >
Use new observability on Stream Live Inputs to better understand
broadcast-side health and performance, now easily available in Dash and
programmatically via GraphQL.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-08-stream-live-observability/
md: https://developers.cloudflare.com/changelog/2025-08-08-stream-live-observability/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing observability and metrics for Stream Live Inputs
Aug 08, 2025
[Stream](https://developers.cloudflare.com/stream/)
New information about broadcast metrics and events is now available in [Cloudflare Stream](https://developers.cloudflare.com/stream/) in the Live Input details of the Dashboard.

You can now easily understand broadcast-side health and performance with new observability, which can help when troubleshooting common issues, particularly for new customers who are just getting started, and platform customers who may have limited visibility into how their end-users configure their encoders.
To get started, start a live stream ([just getting started?](https://developers.cloudflare.com/stream/examples/obs-from-scratch/)), then visit the Live Input details page in Dash.
See our new live [Troubleshooting](https://developers.cloudflare.com/stream/stream-live/troubleshooting/) guide to learn what these metrics mean and how to use them to address common broadcast issues.
---
title: Workers per-branch preview URLs now support long branch names · Changelog
description: Branch names that create URLs longer than 63 characters now get
hash-based preview URLs instead of failing, ensuring every pull request has a
working preview link.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-08-support-long-branch-names-preview-aliases/
md: https://developers.cloudflare.com/changelog/2025-08-08-support-long-branch-names-preview-aliases/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers per-branch preview URLs now support long branch names
Aug 14, 2025
[Workers](https://developers.cloudflare.com/workers/)
We've updated [preview URLs](https://developers.cloudflare.com/workers/configuration/previews/) for Cloudflare Workers to support long branch names.
Previously, branch and Worker names exceeding the 63-character DNS limit would cause alias generation to fail, leaving pull requests without aliased preview URLs. This particularly impacted teams relying on descriptive branch naming.
Now, Cloudflare automatically truncates long branch names and appends a unique hash, ensuring every pull request gets a working preview link.
#### How it works
* **63 characters or less**: `-` → Uses actual branch name as is
* **64 characters or more**: `---` → Uses truncated name with 4-character hash
* **Hash generation**: The hash is derived from the full branch name to ensure uniqueness
* **Stable URLs**: The same branch always generates the same hash across all commits
#### Requirements and compatibility
* **Wrangler 4.30.0 or later**: This feature requires updating to wrangler\@4.30.0+
* **No configuration needed**: Works automatically with existing preview URL setups
---
title: MessageChannel and MessagePort · Changelog
description: The MessageChannel and MessagePort APIs are now available in Workers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-11-messagechannel/
md: https://developers.cloudflare.com/changelog/2025-08-11-messagechannel/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## MessageChannel and MessagePort
Aug 11, 2025
[Workers](https://developers.cloudflare.com/workers/)
A minimal implementation of the [MessageChannel API](https://developer.mozilla.org/en-US/docs/Web/API/MessageChannel) is now available in Workers. This means that you can use `MessageChannel` to send messages between different parts of your Worker, but not across different Workers.
The `MessageChannel` and `MessagePort` APIs will be available by default at the global scope with any worker using a compatibility date of `2025-08-15` or later. It is also available using the `expose_global_message_channel` compatibility flag, or can be explicitly disabled using the `no_expose_global_message_channel` compatibility flag.
```js
const { port1, port2 } = new MessageChannel();
port2.onmessage = (event) => {
console.log('Received message:', event.data);
};
port2.postMessage('Hello from port2!');
```
Any value that can be used with the `structuredClone(...)` API can be sent over the port.
#### Differences
There are a number of key limitations to the `MessageChannel` API in Workers:
* Transfer lists are currently not supported. This means that you will not be able to transfer ownership of objects like `ArrayBuffer` or `MessagePort` between ports.
* The `MessagePort` is not yet serializable. This means that you cannot send a `MessagePort` object through the `postMessage` method or via JSRPC calls.
* The `'messageerror'` event is only partially supported. If the `'onmessage'` handler throws an error, the `'messageerror'` event will be triggered, however, it will not be triggered when there are errors serializing or deserializing the message data. Instead, the error will be thrown when the `postMessage` method is called on the sending port.
* The `'close'` event will be emitted on both ports when one of the ports is closed, however it will not be emitted when the Worker is terminated or when one of the ports is garbage collected.
---
title: WAF Release - 2025-08-11 · Changelog
description: Cloudflare WAF managed rulesets 2025-08-11 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-11-waf-release/
md: https://developers.cloudflare.com/changelog/2025-08-11-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-08-11
Aug 11, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's update focuses on a wide range of enterprise software, from network infrastructure and security platforms to content management systems and development frameworks. Flaws include unsafe deserialization, OS command injection, SSRF, authentication bypass, and arbitrary file upload — many of which allow unauthenticated remote code execution. Notable risks include Cisco Identity Services Engine and Ivanti EPMM, where successful exploitation could grant attackers full administrative control of core network infrastructure and popular web services such as WordPress, SharePoint, and Ingress-Nginx, where security bypasses and arbitrary file uploads could lead to complete site or server compromise.
**Key Findings**
* Cisco Identity Services Engine (CVE-2025-20281): Insufficient input validation in a specific API of Cisco Identity Services Engine (ISE) and ISE-PIC allows an unauthenticated, remote attacker to execute arbitrary code with root privileges on an affected device.
* Wazuh Server (CVE-2025-24016): An unsafe deserialization vulnerability in Wazuh Server (versions 4.4.0 to 4.9.0) allows for remote code execution and privilege escalation. By injecting unsanitized data, an attacker can trigger an exception to execute arbitrary code on the server.
* CrushFTP (CVE-2025-54309): A flaw in AS2 validation within CrushFTP allows remote attackers to gain administrative access via HTTPS on systems not using the DMZ proxy feature. This flaw can lead to unauthorized file access and potential system compromise.
* Kentico Xperience CMS (CVE-2025-2747, CVE-2025-2748): Vulnerabilities in Kentico Xperience CMS could enable cross-site scripting (XSS), allowing attackers to inject malicious scripts into web pages. Additionally, a flaw could allow unauthenticated attackers to bypass the Staging Sync Server's authentication, potentially leading to administrative control over the CMS.
* Node.js (CVE-2025-27210): An incomplete fix for a previous vulnerability (CVE-2025-23084) in Node.js affects the `path.join()` API method on Windows systems. The vulnerability can be triggered using reserved Windows device names such as `CON`, `PRN`, or `AUX`.
* WordPress:Plugin:Simple File List (CVE-2025-34085, CVE-2020-36847): This vulnerability in the Simple File List plugin for WordPress allows an unauthenticated remote attacker to upload arbitrary files to a vulnerable site. This can be exploited to achieve remote code execution on the server.\
(Note: CVE-2025-34085 has been rejected as a duplicate.)
* GeoServer (CVE-2024-29198): A Server-Side Request Forgery (SSRF) vulnerability exists in GeoServer's Demo request endpoint, which can be exploited where the Proxy Base URL has not been configured.
* Ivanti EPMM (CVE-2025-6771): An OS command injection vulnerability in Ivanti Endpoint Manager Mobile (EPMM) before versions 12.5.0.2, 12.4.0.3, and 12.3.0.3 allows a remote, authenticated attacker with high privileges to execute arbitrary code.
* Microsoft SharePoint (CVE-2024-38018): This is a remote code execution vulnerability affecting Microsoft SharePoint Server.
* Manager-IO (CVE-2025-54122): A critical unauthenticated full read Server-Side Request Forgery (SSRF) vulnerability is present in the proxy handler of both Manager Desktop and Server editions up to version 25.7.18.2519. This allows an unauthenticated attacker to bypass network isolation and access internal services.
* Ingress-Nginx (CVE-2025-1974): A vulnerability in the Ingress-Nginx controller for Kubernetes allows an attacker to bypass access control rules. An unauthenticated attacker with access to the pod network can achieve arbitrary code execution in the context of the ingress-nginx controller.
* PaperCut NG/MF (CVE-2023-2533): A Cross-Site Request Forgery (CSRF) vulnerability has been identified in PaperCut NG/MF. Under specific conditions, an attacker could exploit this to alter security settings or execute arbitrary code if they can deceive an administrator with an active login session into clicking a malicious link.
* SonicWall SMA (CVE-2025-40598): This vulnerability could allow an unauthenticated attacker to bypass security controls. This allows a remote, unauthenticated attacker to potentially execute arbitrary JavaScript code.
* WordPress (CVE-2025-5394): The "Alone – Charity Multipurpose Non-profit WordPress Theme" for WordPress is vulnerable to arbitrary file uploads. A missing capability check allows unauthenticated attackers to upload ZIP files containing webshells disguised as plugins, leading to remote code execution.
**Impact**
These vulnerabilities span a broad range of enterprise technologies, including network access control systems, monitoring platforms, web servers, CMS platforms, cloud services, and collaboration tools. Exploitation techniques range from remote code execution and command injection to authentication bypass, SQL injection, path traversal, and configuration weaknesses.
A critical flaw in perimeter devices like Ivanti EPMM or SonicWall SMA could allow an unauthenticated attacker to gain remote code execution, completely breaching the primary network defense. A separate vulnerability within Cisco's Identity Services Engine could then be exploited to bypass network segmentation, granting an attacker widespread internal access. Insecure deserialization issues in platforms like Wazuh Server and CrushFTP could then be used to run malicious payloads or steal sensitive files from administrative consoles. Weaknesses in web delivery controllers like Ingress-Nginx or popular content management systems such as WordPress, SharePoint, and Kentico Xperience create vectors to bypass security controls, exfiltrate confidential data, or fully compromise servers.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | ec6480c81253494b947d891e51bc8df1 | 100538 | GeoServer - SSRF - CVE:CVE-2024-29198 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | b8cb07170b5e4c2b989119cac9e0b290 | 100548 | Ivanti EPMM - Remote Code Execution - CVE:CVE-2025-6771 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | b3524bf5f5174b65bc892122ad93cda8 | 100550 | Microsoft SharePoint - Remote Code Execution - CVE:CVE-2024-38018 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | e1369c5d629f4f10a14141381dca5738 | 100562 | Manager-IO - SSRF - CVE:CVE-2025-54122 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 136f67e2b6a84f15ab9a82a52e9137e1 | 100565 | Cisco Identity Services Engine - Remote Code Execution - CVE:CVE-2025-20281 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | ed759f7e44184fa398ef71785d8102e1 | 100567 | Ingress-Nginx - Remote Code Execution - CVE:CVE-2025-1974 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 71b8e7b646f94d79873213cd99105c43 | 100569 | PaperCut NG/MF - Remote Code Execution - CVE:CVE-2023-2533 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 2450bfbb0cfb4804b109d1c42c81dc88 | 100571 | SonicWall SMA - XSS - CVE:CVE-2025-40598 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 8ce1903b67e24205a93f5fe6926c96d4 | 100573 | WordPress - Dangerous File Upload - CVE:CVE-2025-5394 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 7fdb3c7bc7b74703aeef4ab240ec2fda | 100806 | Wazuh Server - Remote Code Execution - CVE:CVE-2025-24016 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | fe088163f51f4928a3c8d91e2401fa3b | 100824 | CrushFTP - Remote Code Execution - CVE:CVE-2025-54309 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 3638baed75924604987b86d874920ace | 100824A | CrushFTP - Remote Code Execution - CVE:CVE-2025-54309 - 2 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | dda4f95b3a3e4ebb9e194aa5c7e63549 | 100825 | AMI MegaRAC - Auth Bypass - CVE:CVE-2024-54085 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 7dc07014cefa4ce9adf21da7b79037e6 | 100826 | Kentico Xperience CMS - Auth Bypass - CVE:CVE-2025-2747 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 7c7a0a37e79a4949ba840c9acaf261aa | 100827 | Kentico Xperience CMS - XSS - CVE:CVE-2025-2748 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 54dd826f578c483196ce852b6f1c2d12 | 100828 | Node.js - Directory Traversal - CVE:CVE-2025-27210 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | a2867f7456c14213a94509a40341fccc | 100829 | WordPress:Plugin:Simple File List - Remote Code Execution - CVE:CVE-2025-34085 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 4cdb0e792d1a428a897526624cefeeda | 100829A | WordPress:Plugin:Simple File List - Remote Code Execution - CVE:CVE-2025-34085 - 2 | Log | Disabled | This is a New Detection |
---
title: IBM Cloud Logs as Logpush destination · Changelog
description: Enable IBM Cloud Logs as a Logpush destination
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-13-ibm-cloud-logs-destination/
md: https://developers.cloudflare.com/changelog/2025-08-13-ibm-cloud-logs-destination/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## IBM Cloud Logs as Logpush destination
Aug 13, 2025
[Logs](https://developers.cloudflare.com/logs/)
Cloudflare Logpush now supports IBM Cloud Logs as a native destination.
Logs from Cloudflare can be sent to [IBM Cloud Logs](https://www.ibm.com/products/cloud-logs) via [Logpush](https://developers.cloudflare.com/logs/logpush/). The setup can be done through the Logpush UI in the Cloudflare Dashboard or by using the [Logpush API](https://developers.cloudflare.com/api/resources/logpush/subresources/jobs/). The integration requires IBM Cloud Logs HTTP Source Address and an IBM API Key. The feature also allows for filtering events and selecting specific log fields.
For more information, refer to [Destination Configuration](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/ibm-cloud-logs/) documentation.
---
title: Python Workers handlers now live in an entrypoint class · Changelog
description: We are changing how Python Workers are structured by default.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-14-new-python-handlers/
md: https://developers.cloudflare.com/changelog/2025-08-14-new-python-handlers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Python Workers handlers now live in an entrypoint class
Aug 14, 2025
[Workers](https://developers.cloudflare.com/workers/)
We are changing how Python Workers are structured by default. Previously, handlers were defined at the top-level of a module as `on_fetch`, `on_scheduled`, etc. methods, but now they live in an entrypoint class.
Here's an example of how to now define a Worker with a fetch handler:
```python
from workers import Response, WorkerEntrypoint
class Default(WorkerEntrypoint):
async def fetch(self, request):
return Response("Hello World!")
```
To keep using the old-style handlers, you can specify the `disable_python_no_global_handlers` compatibility flag in your wrangler file:
* wrangler.jsonc
```jsonc
{
"compatibility_flags": [
"disable_python_no_global_handlers"
]
}
```
* wrangler.toml
```toml
compatibility_flags = [ "disable_python_no_global_handlers" ]
```
Consult the [Python Workers documentation](https://developers.cloudflare.com/workers/languages/python/) for more details.
---
title: Terraform provider improvements — Python Workers support, smaller plan
diffs, and API SDK fixes · Changelog
description: Multiple improvements to the Workers Terraform resources and SDKs
including fixes for plan diffs, file uploads, and Python Workers support.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-14-workers-terraform-and-sdk-improvements/
md: https://developers.cloudflare.com/changelog/2025-08-14-workers-terraform-and-sdk-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform provider improvements — Python Workers support, smaller plan diffs, and API SDK fixes
Aug 14, 2025
[Workers](https://developers.cloudflare.com/workers/)
The recent [Cloudflare Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_script) and SDK releases (such as [cloudflare-typescript](https://github.com/cloudflare/cloudflare-typescript)) bring significant improvements to the Workers developer experience. These updates focus on reliability, performance, and adding [Python Workers](https://developers.cloudflare.com/workers/languages/python/) support.
#### Terraform Improvements
#### Fixed Unwarranted Plan Diffs
Resolved several issues with the `cloudflare_workers_script` resource that resulted in unwarranted plan diffs, including:
* Using Durable Objects migrations
* Using some bindings such as `secret_text`
* Using smart placement
A resource should never show a plan diff if there isn't an actual change. This fix reduces unnecessary noise in your Terraform plan and is available in Cloudflare Terraform Provider 5.8.0.
#### Improved File Management
You can now specify `content_file` and `content_sha256` instead of `content`. This prevents the Workers script content from being stored in the state file which greatly reduces plan diff size and noise. If your workflow synced plans remotely, this should now happen much faster since there is less data to sync. This is available in Cloudflare Terraform Provider 5.7.0.
```tf
resource "cloudflare_workers_script" "my_worker" {
account_id = "123456789"
script_name = "my_worker"
main_module = "worker.mjs"
content_file = "worker.mjs"
content_sha256 = filesha256("worker.mjs")
}
```
#### Assets Headers and Redirects Support
Fixed the `cloudflare_workers_script` resource to properly support headers and redirects for Assets:
```tf
resource "cloudflare_workers_script" "my_worker" {
account_id = "123456789"
script_name = "my_worker"
main_module = "worker.mjs"
content_file = "worker.mjs"
content_sha256 = filesha256("worker.mjs")
assets = {
config = {
headers = file("_headers")
redirects = file("_redirects")
}
# Completion jwt from:
# https://developers.cloudflare.com/api/resources/workers/subresources/assets/subresources/upload/
jwt = "jwt"
}
}
```
Available in Cloudflare Terraform Provider 5.8.0.
#### Python Workers Support
Added support for uploading [Python Workers](https://developers.cloudflare.com/workers/languages/python/) (beta) in Terraform. You can now deploy Python Workers with:
```tf
resource "cloudflare_workers_script" "my_worker" {
account_id = "123456789"
script_name = "my_worker"
content_file = "worker.py"
content_sha256 = filesha256("worker.py")
content_type = "text/x-python"
}
```
Available in Cloudflare Terraform Provider 5.8.0.
#### SDK Enhancements
#### Improved File Upload API
Fixed an issue where Workers script versions in the SDK did not allow uploading files. This now works, and also has an improved files upload interface:
```js
const scriptContent = `
export default {
async fetch(request, env, ctx) {
return new Response('Hello World!', { status: 200 });
}
};
`;
client.workers.scripts.versions.create('my-worker', {
account_id: '123456789',
metadata: {
main_module: 'my-worker.mjs',
},
files: [
await toFile(
Buffer.from(scriptContent),
'my-worker.mjs',
{
type: "application/javascript+module",
}
)
]
});
```
Will be available in cloudflare-typescript 4.6.0. A similar change will be available in cloudflare-python 4.4.0.
#### Fixed updating KV values
Previously when creating a KV value like this:
```js
await cf.kv.namespaces.values.update("my-kv-namespace", "key1", {
account_id: "123456789",
metadata: "my metadata",
value: JSON.stringify({
hello: "world"
})
});
```
...and recalling it in your Worker like this:
```ts
const value = await c.env.KV.get<{hello: string}>("key1", "json");
```
You'd get back this: `{metadata:'my metadata', value:"{'hello':'world'}"}` instead of the correct value of `{hello: 'world'}`
This is fixed in cloudflare-typescript 4.5.0 and will be fixed in cloudflare-python 4.4.0.
---
title: Steer Traffic by AS Number in Load Balancing Custom Rules · Changelog
description: You can now create Load Balancing custom rules to steer traffic
based on the incoming request's Autonomous System Number (ASN).
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-asnum-support-in-custom-rules/
md: https://developers.cloudflare.com/changelog/2025-08-15-asnum-support-in-custom-rules/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Steer Traffic by AS Number in Load Balancing Custom Rules
Aug 15, 2025
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
You can now create more granular, network-aware Custom Rules in Cloudflare Load Balancing using the Autonomous System Number (ASN) of an incoming request.
This allows you to steer traffic with greater precision based on the network source of a request. For example, you can route traffic from specific Internet Service Providers (ISPs) or enterprise customers to dedicated infrastructure, optimize performance, or enforce compliance by directing certain networks to preferred data centers.

To get started, create a [Custom Rule](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-rules/) in your Load Balancer and select **AS Num** from the **Field** dropdown.
---
title: Save time with bulk query creation in Brand Protection · Changelog
description: Quickly create and save multiple Brand Protection queries via API.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-brand-protection-bulk-endpoint/
md: https://developers.cloudflare.com/changelog/2025-08-15-brand-protection-bulk-endpoint/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Save time with bulk query creation in Brand Protection
Aug 15, 2025
[Security Center](https://developers.cloudflare.com/security-center/)
[Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/) detects domains that may be impersonating your brand — from common misspellings (`cloudfalre.com`) to malicious concatenations (`cloudflare-okta.com`). Saved search queries run continuously and alert you when suspicious domains appear.
You can now create and save multiple queries in a single step, streamlining setup and management. Available now via the [Brand Protection bulk query creation API](https://developers.cloudflare.com/api/resources/brand_protection/subresources/queries/methods/bulk/).
---
title: Extended retention · Changelog
description: Log Explorer customers can now extend the retention period
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-extended-retention/
md: https://developers.cloudflare.com/changelog/2025-08-15-extended-retention/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Extended retention
Aug 15, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
Customers can now rely on Log Explorer to meet their log retention compliance requirements.
Contract customers can choose to store their logs in Log Explorer for up to two years, at an additional cost of $0.10 per GB per month. Customers interested in this feature can contact their account team to have it added to their contract.
---
title: Google Bard Application replaced by Gemini · Changelog
description: The Google Bard application has been fully replaced with Gemini
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-gemini-application-replaces-bard/
md: https://developers.cloudflare.com/changelog/2025-08-15-gemini-application-replaces-bard/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Google Bard Application replaced by Gemini
Jul 22, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
The **Google Bard** application (ID: 1198) has been deprecated and fully removed from the system. It has been replaced by the **Gemini** application (ID: 1340). Any existing Gateway policies that reference the old Google Bard application will no longer function. To ensure your policies continue to work as intended, you should update them to use the new Gemini application. We recommend replacing all instances of the deprecated Bard application with the new Gemini application in your Gateway policies. For more information about application policies, please see the [Cloudflare Gateway documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
---
title: Monitor Groups for Advanced Health Checking With Load Balancing · Changelog
description: Group multiple health monitors to create sophisticated,
multi-service health assessments for your pools.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-monitor-groups-for-load-balancing/
md: https://developers.cloudflare.com/changelog/2025-08-15-monitor-groups-for-load-balancing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Monitor Groups for Advanced Health Checking With Load Balancing
Oct 16, 2025
[Load Balancing](https://developers.cloudflare.com/load-balancing/)
Cloudflare Load Balancing now supports Monitor Groups, a powerful new way to combine multiple health monitors into a single, logical group. This allows you to create sophisticated health checks that more accurately reflect the true availability of your applications by assessing multiple services at once.
With Monitor Groups, you can ensure that all critical components of an application are healthy before sending traffic to an origin pool, enabling smarter failover decisions and greater resilience. This feature is now available via the API for customers with an Enterprise Load Balancing subscription.
#### What you can do:
* **Combine Multiple Monitors**: Group different health monitors (for example, HTTP, TCP) that check various application components, like a primary API gateway and a specific `/login` service.
* **Isolate Monitors for Observation**: Mark a monitor as "monitoring only" to receive alerts and data without it affecting a pool's health status or traffic steering. This is perfect for testing new checks or observing non-critical dependencies.
* **Improve Steering Intelligence**: Latency for Dynamic Steering is automatically averaged across all active monitors in a group, providing a more holistic view of an origin's performance.
This enhancement is ideal for complex, multi-service applications where the health of one component depends on another. By aggregating health signals, Monitor Groups provide a more accurate and comprehensive assessment of your application's true status.
For detailed information and API configuration guides, please visit our [developer documentation](https://developers.cloudflare.com/load-balancing/monitors/monitor-groups) for Monitor Groups.
---
title: The Node.js and Web File System APIs in Workers · Changelog
description: The node:fs and Web File System APIs are now available in Workers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-nodejs-fs/
md: https://developers.cloudflare.com/changelog/2025-08-15-nodejs-fs/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## The Node.js and Web File System APIs in Workers
Aug 15, 2025
[Workers](https://developers.cloudflare.com/workers/)
Implementations of the [`node:fs` module](https://nodejs.org/docs/latest/api/fs.html) and the [Web File System API](https://developer.mozilla.org/en-US/docs/Web/API/File_System_Access_API) are now available in Workers.
#### Using the `node:fs` module
The `node:fs` module provides access to a virtual file system in Workers. You can use it to read and write files, create directories, and perform other file system operations.
The virtual file system is ephemeral with each individual request havig its own isolated temporary file space. Files written to the file system will not persist across requests and will not be shared across requests or across different Workers.
Workers running with the `nodejs_compat` compatibility flag will have access to the `node:fs` module by default when the compatibility date is set to `2025-09-01` or later. Support for the API can also be enabled using the `enable_nodejs_fs_module` compatibility flag together with the `nodejs_compat` flag. The `node:fs` module can be disabled using the `disable_nodejs_fs_module` compatibility flag.
```js
import fs from "node:fs";
const config = JSON.parse(fs.readFileSync("/bundle/config.json", "utf-8"));
export default {
async fetch(request) {
return new Response(`Config value: ${config.value}`);
},
};
```
There are a number of initial limitations to the `node:fs` implementation:
* The glob APIs (e.g. `fs.globSync(...)`) are not implemented.
* The file watching APIs (e.g. `fs.watch(...)`) are not implemented.
* The file timestamps (modified time, access time, etc) are only partially supported. For now, these will always return the Unix epoch.
Refer to the [Node.js documentation](https://nodejs.org/docs/latest/api/fs.html) for more information on the `node:fs` module and its APIs.
#### The Web File System API
The Web File System API provides access to the same virtual file system as the `node:fs` module, but with a different API surface. The Web File System API is only available in Workers running with the `enable_web_file_system` compatibility flag. The `nodejs_compat` compatibility flag is not required to use the Web File System API.
```js
const root = navigator.storage.getDirectory();
export default {
async fetch(request) {
const tmp = await root.getDirectoryHandle("/tmp");
const file = await tmp.getFileHandle("data.txt", { create: true });
const writable = await file.createWritable();
const writer = writable.getWriter();
await writer.write("Hello, World!");
await writer.close();
return new Response("File written successfully!");
},
};
```
As there are still some parts of the Web File System API tht are not fully standardized, there may be some differences between the Workers implementation and the implementations in browsers.
---
title: SFTP support for SSH with Cloudflare Access for Infrastructure · Changelog
description: SSH with Cloudflare Access for Infrastructure now supports SFTP for
easy file transfer.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-sftp/
md: https://developers.cloudflare.com/changelog/2025-08-15-sftp/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## SFTP support for SSH with Cloudflare Access for Infrastructure
Aug 15, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[SSH with Cloudflare Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/) now supports SFTP. It is compatible with SFTP clients, such as Cyberduck.
---
title: "Workers Static Assets: Corrected handling of double slashes in redirect
rule paths · Changelog"
description: Corrected handling of double slashes in redirect rule paths
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-static-assets-redirect-url/
md: https://developers.cloudflare.com/changelog/2025-08-15-static-assets-redirect-url/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers Static Assets: Corrected handling of double slashes in redirect rule paths
Aug 15, 2025
[Workers](https://developers.cloudflare.com/workers/)
[Static Assets](https://developers.cloudflare.com/workers/static-assets/): Fixed a bug in how [redirect rules](https://developers.cloudflare.com/workers/static-assets/redirects/) defined in your Worker's `_redirects` file are processed.
If you're serving Static Assets with a `_redirects` file containing a rule like `/ja/* /:splat`, paths with double slashes were previously misinterpreted as external URLs. For example, visiting `/ja//example.com` would incorrectly redirect to `https://example.com` instead of `/example.com` on your domain. This has been fixed and double slashes now correctly resolve as local paths. Note: [Cloudflare Pages](https://developers.cloudflare.com/pages/) was not affected by this issue.
---
title: Terraform v5.8.4 now available · Changelog
description: Terraform v5.8.4 stablizes a number of resources and known issues
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-15-terraform-v584-provider/
md: https://developers.cloudflare.com/changelog/2025-08-15-terraform-v584-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.8.4 now available
Aug 15, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare Community related to the v5 release. We have committed to releasing improvements on a two week cadence to ensure stability and reliability.
One key change we adopted in recent weeks is a pivot to more comprehensive, test-driven development. We are still evaluating individual issues, but are also investing in much deeper testing to drive our stabilization efforts. We will subsequently be investing in comprehensive migration scripts. As a result, you will see several of the highest traffic APIs have been stabilized in the most recent release, and are supported by comprehensive acceptance tests.
Thank you for continuing to raise issues. We triage them weekly and they help make our products stronger.
#### Changes
* Resources stabilized:
* `cloudflare_argo_smart_routing`
* `cloudflare_bot_management`
* `cloudflare_list`
* `cloudflare_list_item`
* `cloudflare_load_balancer`
* `cloudflare_load_balancer_monitor`
* `cloudflare_load_balancer_pool`
* `cloudflare_spectrum_application`
* `cloudflare_managed_transforms`
* `cloudflare_url_normalization_settings`
* `cloudflare_snippet`
* `cloudflare_snippet_rules`
* `cloudflare_zero_trust_access_application`
* `cloudflare_zero_trust_access_group`
* `cloudflare_zero_trust_access_identity_provider`
* `cloudflare_zero_trust_access_mtls_certificate`
* `cloudflare_zero_trust_access_mtls_hostname_settings`
* `cloudflare_zero_trust_access_policy`
* `cloudflare_zone`
* Multipart handling restored for `cloudflare_snippet`
* `cloudflare_bot_management` diff issues resolves when running `terraform plan` and `terraform apply`
* Other bug fixes
For a more detailed look at all of the changes, refer to the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.8.4) in GitHub.
#### Issues Closed
* [#5017: 'Uncaught Error: No such module' using cloudflare\_snippets](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5017)
* [#5701: cloudflare\_workers\_script migrations for Durable Objects not recorded in tfstate; cannot be upgraded between versions](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5701)
* [#5640: cloudflare\_argo\_smart\_routing importing doesn't read the actual value](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5640)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new one if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding off on migration to v5 while we work on stablization. This help will you avoid any blocking issues while the Terraform resources are actively being stablized.
If you'd like more information on migrating to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition. These migration scripts do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: WAF Release - 2025-08-18 · Changelog
description: Cloudflare WAF managed rulesets 2025-08-18 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-18-waf-release/
md: https://developers.cloudflare.com/changelog/2025-08-18-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-08-18
Aug 18, 2025
[WAF](https://developers.cloudflare.com/waf/)
**This week's update**
This week, a series of critical vulnerabilities were discovered impacting core enterprise and open-source infrastructure. These flaws present a range of risks, providing attackers with distinct pathways for remote code execution, methods to breach internal network boundaries, and opportunities for critical data exposure and operational disruption.
**Key Findings**
* SonicWall SMA (CVE-2025-32819, CVE-2025-32820, CVE-2025-32821): A remote authenticated attacker with SSLVPN user privileges can bypass path traversal protections. These vulnerabilities enable a attacker to bypass security checks to read, modify, or delete arbitrary files. An attacker with administrative privileges can escalate this further, using a command injection flaw to upload malicious files, which could ultimately force the appliance to reboot to its factory default settings.
* Ms-Swift Project (CVE-2025-50460): An unsafe deserialization vulnerability exists in the Ms-Swift project's handling of YAML configuration files. If an attacker can control the content of a configuration file passed to the application, they can embed a malicious payload that will execute arbitrary code and it can be executed during deserialization.
* Apache Druid (CVE-2023-25194): This vulnerability in Apache Druid allows an attacker to cause the server to connect to a malicious LDAP server. By sending a specially crafted LDAP response, the attacker can trigger an unrestricted deserialization of untrusted data. If specific "gadgets" (classes that can be abused) are present in the server's classpath, this can be escalated to achieve Remote Code Execution (RCE).
* Tenda AC8v4 (CVE-2025-51087, CVE-2025-51088): Vulnerabilities allow an authenticated attacker to trigger a stack-based buffer overflow. By sending malformed arguments in a request to specific endpoints, an attacker can crash the device or potentially achieve arbitrary code execution.
* Open WebUI (CVE-2024-7959): This vulnerability allows a user to change the OpenAI URL endpoint to an arbitrary internal network address without proper validation. This flaw can be exploited to access internal services or cloud metadata endpoints, potentially leading to remote command execution if the attacker can retrieve instance secrets or access sensitive internal APIs.
* BentoML (CVE-2025-54381): The vulnerability exists in the serialization/deserialization handlers for multipart form data and JSON requests, which automatically download files from user-provided URLs without proper validation of internal network addresses. This allows attackers to fetch from unintended internal services, including cloud metadata and localhost.
* Adobe Experience Manager Forms (CVE-2025-54254): An Improper Restriction of XML External Entity Reference ('XXE') vulnerability that could lead to arbitrary file system read in Adobe AEM (≤6.5.23).
**Impact**
These vulnerabilities affect core infrastructure, from network security appliances like SonicWall to data platforms such as Apache Druid and ML frameworks like BentoML. The code execution and deserialization flaws are particularly severe, offering deep system access that allows attackers to steal data, disrupt services, and establish a foothold for broader intrusions. Simultaneously, SSRF and XXE vulnerabilities undermine network boundaries, exposing sensitive internal data and creating pathways for lateral movement. Beyond data-centric threats, flaws in edge devices like the Tenda router introduce the tangible risk of operational disruption, highlighting a multi-faceted threat to the security and stability of key enterprise systems.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 326ebb56d46a4c269bb699d3418d9a3b | 100574 | SonicWall SMA - Remote Code Execution - CVE:CVE-2025-32819, CVE:CVE-2025-32820, CVE:CVE-2025-32821 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 69f4f161dec04aca8a73a3231e6fefdb | 100576 | Ms-Swift Project - Remote Code Execution - CVE:CVE-2025-50460 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | d62935357ff846d9adefb58108ac45b3 | 100585 | Apache Druid - Remote Code Execution - CVE:CVE-2023-25194 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 4f6148a760804bf8ad8ebccfe4855472 | 100834 | Tenda AC8v4 - Auth Bypass - CVE:CVE-2025-51087, CVE:CVE-2025-51088 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 1474121b01ba40629f8246f8022ab542 | 100835 | Open WebUI - SSRF - CVE:CVE-2024-7959 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 96abffdb7e224ce69ddf89eb6339f132 | 100837 | SQLi - OOB | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | a0b20ec638d14800a1d6827cb83d2625 | 100841 | BentoML - SSRF - CVE:CVE-2025-54381 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 40fd793035c947c5ac75add1739180d2 | 100841A | BentoML - SSRF - CVE:CVE-2025-54381 - 2 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 08dcb20b9acf47e3880a0b886ab910c2 | 100841B | BentoML - SSRF - CVE:CVE-2025-54381 - 3 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 309cfb7eeb42482e9ad896f12197ec51 | 100845 | Adobe Experience Manager Forms - XSS - CVE:CVE-2025-54254 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 6e039776c2d6418ab6e8f05196f34ce3 | 100845A | Adobe Experience Manager Forms - XSS - CVE:CVE-2025-54254 - 2 | Log | Block | This is a New Detection |
---
title: Subscribe to events from Cloudflare services with Queues · Changelog
description: Subscribe to events from Cloudflare services to build custom
workflows, integrations, and logic.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-19-event-subscriptions/
md: https://developers.cloudflare.com/changelog/2025-08-19-event-subscriptions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Subscribe to events from Cloudflare services with Queues
Aug 19, 2025
[Queues](https://developers.cloudflare.com/queues/)
You can now subscribe to events from other Cloudflare services (for example, [Workers KV](https://developers.cloudflare.com/kv/), [Workers AI](https://developers.cloudflare.com/workers-ai), [Workers](https://developers.cloudflare.com/workers)) and consume those events via [Queues](https://developers.cloudflare.com/queues/), allowing you to build custom workflows, integrations, and logic in response to account activity.

Event subscriptions allow you to receive messages when events occur across your Cloudflare account. Cloudflare products can publish structured events to a queue, which you can then consume with [Workers](https://developers.cloudflare.com/workers/) or [pull via HTTP from anywhere](https://developers.cloudflare.com/queues/configuration/pull-consumers/).
To create a subscription, use the dashboard or [Wrangler](https://developers.cloudflare.com/workers/wrangler/commands/#subscription-create):
```bash
npx wrangler queues subscription create my-queue --source r2 --events bucket.created
```
An event is a structured record of something happening in your Cloudflare account – like a Workers AI batch request being queued, a Worker build completing, or an R2 bucket being created. Events follow a consistent structure:
```json
{
"type": "cf.r2.bucket.created",
"source": {
"type": "r2"
},
"payload": {
"name": "my-bucket",
"location": "WNAM"
},
"metadata": {
"accountId": "f9f79265f388666de8122cfb508d7776",
"eventTimestamp": "2025-07-28T10:30:00Z"
}
}
```
Current [event sources](https://developers.cloudflare.com/queues/event-subscriptions/events-schemas/) include [R2](https://developers.cloudflare.com/r2/), [Workers KV](https://developers.cloudflare.com/kv/), [Workers AI](https://developers.cloudflare.com/workers-ai/), [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/), [Vectorize](https://developers.cloudflare.com/vectorize/), [Super Slurper](https://developers.cloudflare.com/r2/data-migration/super-slurper/), and [Workflows](https://developers.cloudflare.com/workflows/). More sources and events are on the way.
For more information on event subscriptions, available events, and how to get started, refer to our [documentation](https://developers.cloudflare.com/queues/event-subscriptions/).
---
title: Easier debugging in Workers with improved Wrangler error screen · Changelog
description: Wrangler's error screen now features light and dark themes, more
reliable source map resolution, and better error cause display.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-19-improved-wrangler-error-screen/
md: https://developers.cloudflare.com/changelog/2025-08-19-improved-wrangler-error-screen/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Easier debugging in Workers with improved Wrangler error screen
Aug 19, 2025
[Workers](https://developers.cloudflare.com/workers/)
Wrangler's error screen has received several improvements to enhance your debugging experience!
The error screen now features a refreshed design thanks to [youch](https://www.npmjs.com/package/youch), with support for both light and dark themes, improved source map resolution logic that handles missing source files more reliably, and better error cause display.
| Before | After (Light) | After (Dark) |
| - | - | - |
| 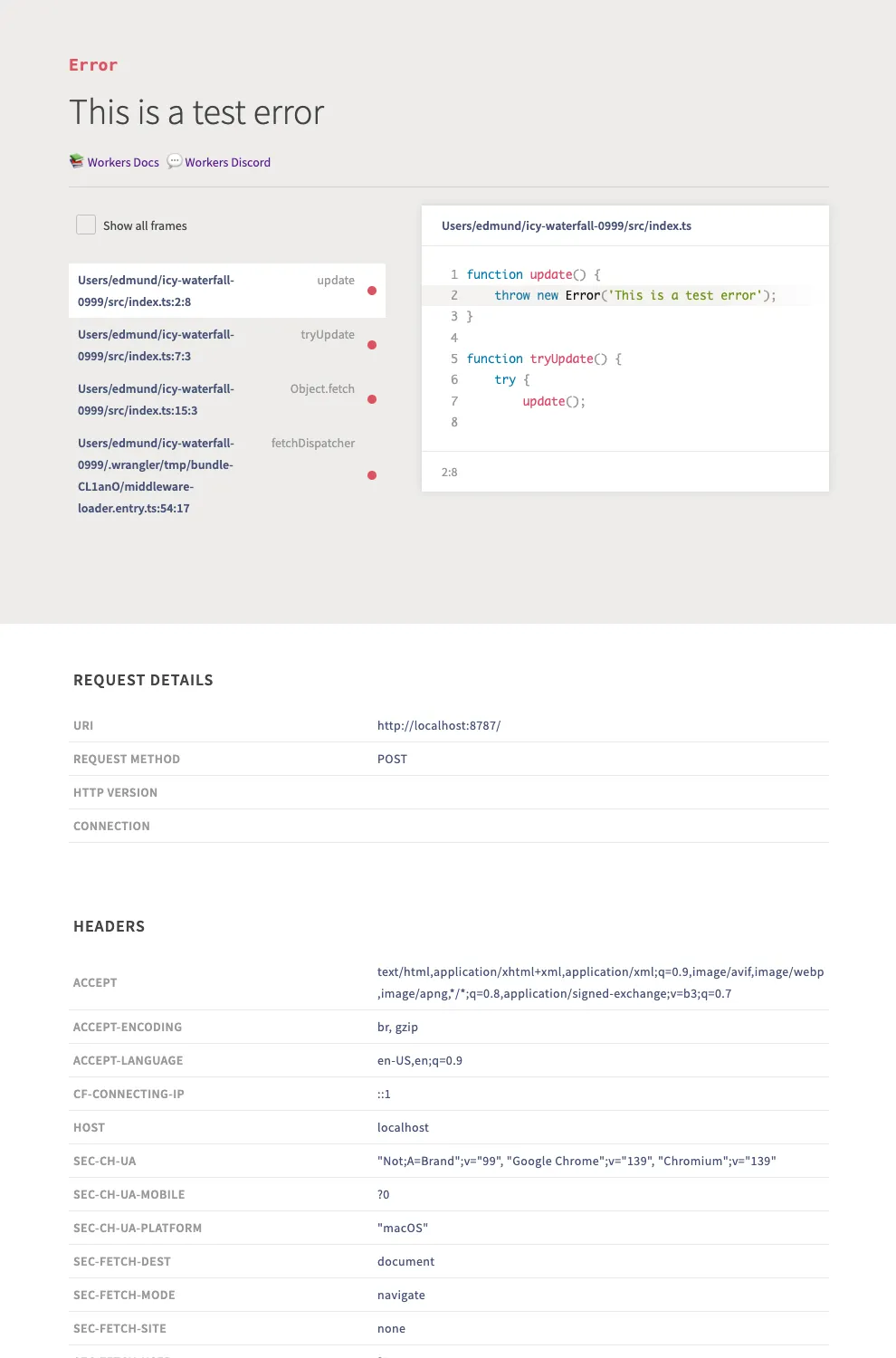 |  | 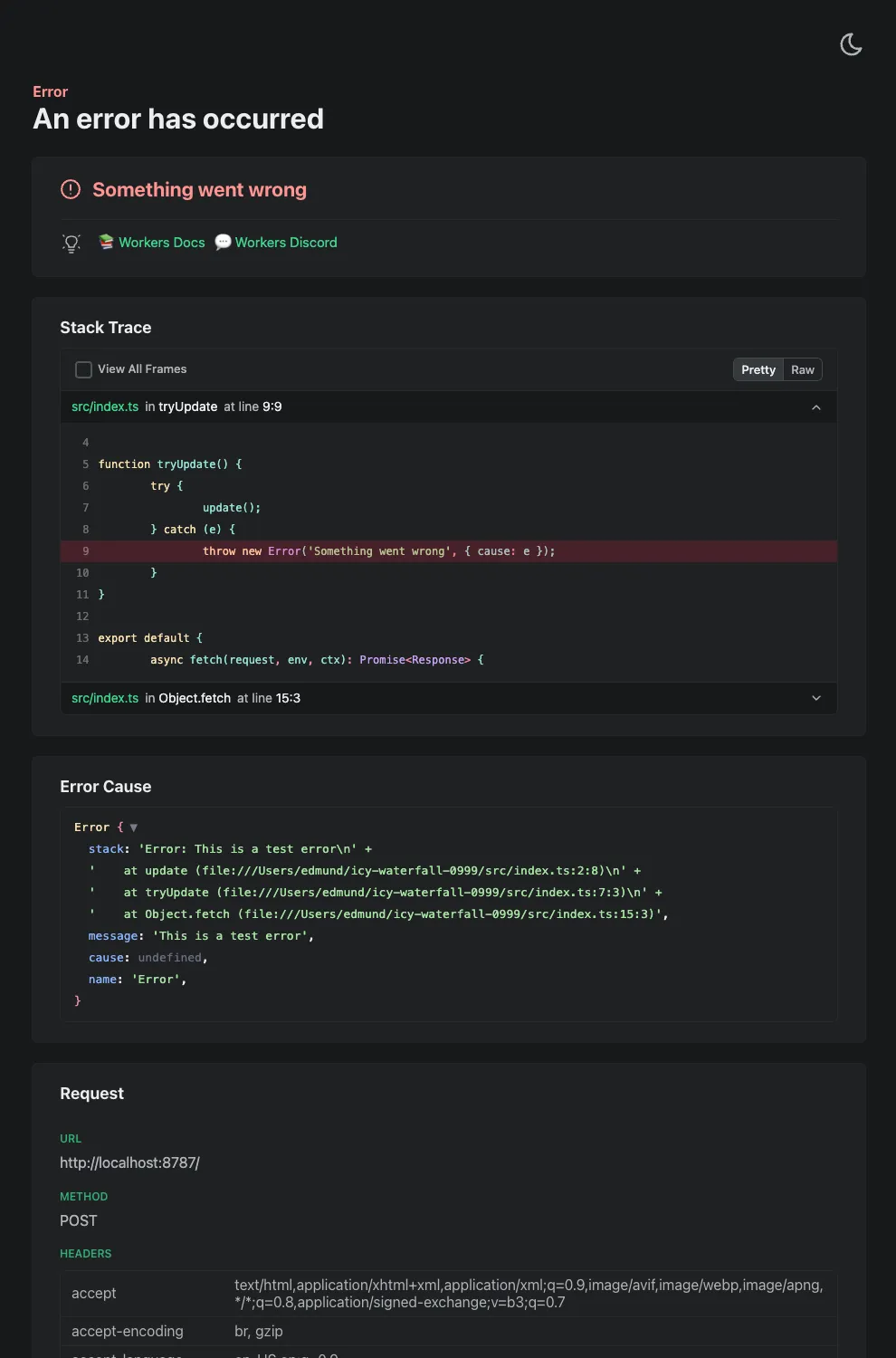 |
Try it out now with `npx wrangler@latest dev` in your Workers project.
---
title: WARP client for Linux (version 2025.6.1335.0) · Changelog
description: WARP client for Linux (version 2025.6.1335.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-19-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-08-19-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.6.1335.0)
Aug 19, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement for faster client connectivity on high-latency captive portal networks.
* Fixed an issue where recursive CNAME records could cause intermittent WARP connectivity issues.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for macOS (version 2025.6.1335.0) · Changelog
description: WARP client for macOS (version 2025.6.1335.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-19-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-08-19-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.6.1335.0)
Aug 19, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement for faster client connectivity on high-latency captive portal networks.
* Fixed an issue where recursive CNAME records could cause intermittent WARP connectivity issues.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.6.1335.0) · Changelog
description: WARP client for Windows (version 2025.6.1335.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-19-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-08-19-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.6.1335.0)
Aug 19, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Improvements to better manage multi-user pre-login registrations.
* Fixed an issue preventing devices from reaching split-tunneled traffic even when WARP was disconnected.
* Fix to prevent WARP from re-enabling its firewall rules after a user-initiated disconnect.
* Improvement for faster client connectivity on high-latency captive portal networks.
* Fixed an issue where recursive CNAME records could cause intermittent WARP connectivity issues.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 version KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Gateway BYOIP Dedicated Egress IPs now available. · Changelog
description: Gateway now supports egressing customer traffic using IPv4/v6
prefixes they already own.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-21-byoip-dedicated-egress-ip/
md: https://developers.cloudflare.com/changelog/2025-08-21-byoip-dedicated-egress-ip/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Gateway BYOIP Dedicated Egress IPs now available.
Aug 21, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Enterprise Gateway users can now use Bring Your Own IP (BYOIP) for dedicated egress IPs.
Admins can now onboard and use their own IPv4 or IPv6 prefixes to egress traffic from Cloudflare, delivering greater control, flexibility, and compliance for network traffic.
Get started by following the [BYOIP onboarding process](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/dedicated-egress-ips/#bring-your-own-ip-address-byoip). Once your IPs are onboarded, go to **Gateway** > **Egress policies** and select or create an egress policy. In **Select an egress IP**, choose *Use dedicated egress IPs (Cloudflare or BYOIP)*, then select your BYOIP address from the dropdown menu.

For more information, refer to [BYOIP for dedicated egress IPs](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/dedicated-egress-ips/#bring-your-own-ip-address-byoip).
---
title: New getByName() API to access Durable Objects · Changelog
description: Get a Durable Object client with a single line of code.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-21-durable-objects-get-by-name/
md: https://developers.cloudflare.com/changelog/2025-08-21-durable-objects-get-by-name/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New getByName() API to access Durable Objects
Aug 21, 2025
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
You can now create a client (a [Durable Object stub](https://developers.cloudflare.com/durable-objects/api/stub/)) to a Durable Object with the new `getByName` method, removing the need to convert Durable Object names to IDs and then create a stub.
```js
// Before: (1) translate name to ID then (2) get a client
const objectId = env.MY_DURABLE_OBJECT.idFromName("foo"); // or .newUniqueId()
const stub = env.MY_DURABLE_OBJECT.get(objectId);
// Now: retrieve client to Durable Object directly via its name
const stub = env.MY_DURABLE_OBJECT.getByName("foo");
// Use client to send request to the remote Durable Object
const rpcResponse = await stub.sayHello();
```
Each Durable Object has a globally-unique name, which allows you to send requests to a specific object from anywhere in the world. Thus, a Durable Object can be used to coordinate between multiple clients who need to work together. You can have billions of Durable Objects, providing isolation between application tenants.
To learn more, visit the Durable Objects [API Documentation](https://developers.cloudflare.com/durable-objects/api/namespace/#getbyname) or the [getting started guide](https://developers.cloudflare.com/durable-objects/get-started/).
---
title: WARP client for Windows (version 2025.6.1400.0) · Changelog
description: WARP client for Windows (version 2025.6.1400.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-21-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-08-21-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.6.1400.0)
Aug 21, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains a hotfix for pre-login for multi-user for the 2025.6.1135.0 release.
**Changes and improvements**
* Fixes an issue where new pre-login registrations were not being properly created.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about Win32/ClickFix.ABA being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, please reconnect the WARP client by toggling off and back on.
---
title: Audit logs (version 2) - Logpush Beta Release · Changelog
description: New version of audit logs UI
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-22-audit-logs-v2-logpush/
md: https://developers.cloudflare.com/changelog/2025-08-22-audit-logs-v2-logpush/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Audit logs (version 2) - Logpush Beta Release
Aug 22, 2025
[Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/)
[Audit Logs v2 dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/audit_logs_v2/) is now available via Logpush.
This expands on earlier releases of Audit Logs v2 in the [API](https://developers.cloudflare.com/changelog/2025-03-27-automatic-audit-logs-beta-release/) and [Dashboard UI](https://developers.cloudflare.com/changelog/2025-07-29-audit-logs-v2-ui-beta/).
We recommend creating a new Logpush job for the Audit Logs v2 dataset.
Timelines for General Availability (GA) of Audit Logs v2 and the retirement of Audit Logs v1 will be shared in upcoming updates.
For more details on Audit Logs v2, refer to the [Audit Logs documentation](https://developers.cloudflare.com/fundamentals/account/account-security/audit-logs/).
---
title: Dedicated Egress IP for Logpush · Changelog
description: Set up dedicated egress IPs for Logpush using Aegis IPs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-22-dedicated-egress-ip-logpush/
md: https://developers.cloudflare.com/changelog/2025-08-22-dedicated-egress-ip-logpush/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Dedicated Egress IP for Logpush
Aug 22, 2025
[Logs](https://developers.cloudflare.com/logs/)
Cloudflare Logpush can now deliver logs from using fixed, dedicated egress IPs. By routing Logpush traffic through a Cloudflare zone enabled with [Aegis IP](https://developers.cloudflare.com/smart-shield/configuration/dedicated-egress-ips/), your log destination only needs to allow Aegis IPs making setup more secure.
Highlights:
* Fixed egress IPs ensure your destination only accepts traffic from known addresses.
* Works with any supported Logpush destination.
* Recommended to use a dedicated zone as a proxy for easier management.
To get started, work with your Cloudflare account team to provision Aegis IPs, then configure your Logpush job to deliver logs through the proxy zone. For full setup instructions, refer to the [Logpush documentation](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/egress-ip/).
---
title: Workers KV completes hybrid storage provider rollout for improved
performance, fault-tolerance · Changelog
description: Workers KV adds new storage providers on Cloudflare's
infrastructure, delivering significant latency improvements with p95 latency
reduced by 67% and p99 by 29%.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-22-kv-performance-improvements/
md: https://developers.cloudflare.com/changelog/2025-08-22-kv-performance-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers KV completes hybrid storage provider rollout for improved performance, fault-tolerance
Aug 22, 2025
[KV](https://developers.cloudflare.com/kv/)
Workers KV has completed rolling out performance improvements across all KV namespaces, providing a significant latency reduction on read operations for all KV users. This is due to architectural changes to KV's underlying storage infrastructure, which introduces a new metadata later and substantially improves redundancy.

#### Performance improvements
The new hybrid architecture delivers substantial latency reductions throughout Europe, Asia, Middle East, Africa regions. Over the past 2 weeks, we have observed the following:
* **p95 latency**: Reduced from \~150ms to \~50ms (67% decrease)
* **p99 latency**: Reduced from \~350ms to \~250ms (29% decrease)
---
title: WAF Release - 2025-08-22 · Changelog
description: Cloudflare WAF managed rulesets 2025-08-22 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-22-waf-release/
md: https://developers.cloudflare.com/changelog/2025-08-22-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-08-22
Aug 22, 2025
[WAF](https://developers.cloudflare.com/waf/)
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 0f3b6b9377334707b604be925fcca5c8 | 100850 | Command Injection - Generic 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 36b0532eb3c941449afed2d3744305c4 | 100851 | Remote Code Execution - Java Deserialization | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5d3c0d0958d14512bd2a7d902b083459 | 100852 | Command Injection - Generic 3 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 6e2f7a696ea74c979e7d069cefb7e5b9 | 100853 | Remote Code Execution - Common Bash Bypass Beta | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 735666d7268545a5ae6cfd0b78513ad7 | 100854 | XSS - Generic JavaScript | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 82780ba6f5df49dcb8d09af0e9a5daac | 100855 | Command Injection - Generic 4 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 8e305924a7dc4f91a2de931a480f6093 | 100856 | PHP Object Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 1d34e0d05c10473ca824e66fd4ae0a33 | 100857 | Generic - Parameter Fuzzing | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | b517e4b79d7a47fbb61f447b1121ee45 | 100858 | Code Injection - Generic 4 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 1f9accf629dc42cb84a7a14420de01e3 | 100859 | SQLi - UNION - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | e95939eacf7c4484b47101d5c0177e21 | 100860 | Command Injection - Generic 5 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 7b426e6f456043f4a21c162085f4d7b3 | 100861 | Command Execution - Generic | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5fac82bd1c03463fb600cfa83fa8ee7f | 100862 | GraphQL Injection - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | ab2cb1f2e2ad4da6a2685b1dc7a41d4b | 100863 | Command Injection - Generic 6 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 549b4fe1564a448d848365d565e3c165 | 100864 | Code Injection - Generic 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 8ef3c3f91eef46919cc9cb6d161aafdc | 100865 | PHP Object Injection - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 57e8ba867e6240d2af8ea0611cc3c3f8 | 100866 | SQLi - LIKE 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | a967a167874b42b6898be46e48ac2221 | 100867 | SQLi - DROP - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | cf79a868cc934bcc92b86ff01f4eec13 | 100868 | Code Injection - Generic 3 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 97a52405eaae47ae9627dbb22755f99e | 100869 | Command Injection - Generic 7 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5b3ce84c099040c6a25cee2d413592e2 | 100870 | Command Injection - Generic 8 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5940a9ace2f04d078e35d435d2dd41b5 | 100871 | SQLi - LIKE 3 | N/A | Disabled | This is a New Detection |
---
title: Build durable multi-step applications in Python with Workflows (now in
beta) · Changelog
description: Python Workflows is now open beta - build Workflows in Python.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-22-workflows-python-beta/
md: https://developers.cloudflare.com/changelog/2025-08-22-workflows-python-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Build durable multi-step applications in Python with Workflows (now in beta)
Aug 22, 2025
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
You can now build [Workflows](https://developers.cloudflare.com/workflows/) using Python. With Python Workflows, you get automatic retries, state persistence, and the ability to run multi-step operations that can span minutes, hours, or weeks using Python’s familiar syntax and the [Python Workers](https://developers.cloudflare.com/workers/languages/python/) runtime.
Python Workflows use the same step-based execution model as JavaScript Workflows, but with Python syntax and access to Python’s ecosystem. Python Workflows also enable [DAG (Directed Acyclic Graph) workflows](https://developers.cloudflare.com/workflows/python/dag/), where you can define complex dependencies between steps using the depends parameter.
Here’s a simple example:
```python
from workers import Response, WorkflowEntrypoint
class PythonWorkflowStarter(WorkflowEntrypoint):
async def run(self, event, step):
@step.do("my first step")
async def my_first_step():
# do some work
return "Hello Python!"
await my_first_step()
await step.sleep("my-sleep-step", "10 seconds")
@step.do("my second step")
async def my_second_step():
# do some more work
return "Hello again!"
await my_second_step()
class Default(WorkerEntrypoint):
async def fetch(self, request):
await self.env.MY_WORKFLOW.create()
return Response("Hello Workflow creation!")
```
Note
Python Workflows requires a `compatibility_date = "2025-08-01"`, or lower, in your wrangler toml file.
Python Workflows support the same core capabilities as JavaScript Workflows, including sleep scheduling, event-driven workflows, and built-in error handling with configurable retry policies.
To learn more and get started, refer to [Python Workflows documentation](https://developers.cloudflare.com/workflows/python/).
---
title: New DLP topic based detection entries for AI prompt protection · Changelog
description: Analyze and secure user prompts to popular generative AI services
with new, DLP topic classifications.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-25-ai-prompt-protection/
md: https://developers.cloudflare.com/changelog/2025-08-25-ai-prompt-protection/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New DLP topic based detection entries for AI prompt protection
Aug 25, 2025
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You now have access to a comprehensive suite of capabilities to secure your organization's use of generative AI. AI prompt protection introduces four key features that work together to provide deep visibility and granular control.
1. **Prompt Detection for AI Applications**
DLP can now natively detect and inspect user prompts submitted to popular AI applications, including **Google Gemini**, **ChatGPT**, **Claude**, and **Perplexity**.
1. **Prompt Analysis and Topic Classification**
Our DLP engine performs deep analysis on each prompt, applying [topic classification](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics). These topics are grouped into two evaluation categories:
* **Content:** PII, Source Code, Credentials and Secrets, Financial Information, and Customer Data.
* **Intent:** Jailbreak attempts, requests for malicious code, or attempts to extract PII.
To help you apply these topics quickly, we have also released five new predefined profiles (for example, AI Prompt: AI Security, AI Prompt: PII) that bundle these new topics.

1. **Granular Guardrails**
You can now build guardrails using Gateway HTTP policies with [application granular controls](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#application-granular-controls). Apply a DLP profile containing an [AI prompt topic detection](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics) to individual AI applications (for example, `ChatGPT`) and specific user actions (for example, `SendPrompt`) to block sensitive prompts.

2. **Full Prompt Logging**
To aid in incident investigation, an optional setting in your Gateway policy allows you to [capture prompt logs](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-policies/logging-options/#log-generative-ai-prompt-content) to store the full interaction of prompts that trigger a policy match. To make investigations easier, logs can be filtered by `conversation_id`, allowing you to reconstruct the full context of an interaction that led to a policy violation.

AI prompt protection is now available in open beta. To learn more about it, read the [blog](https://blog.cloudflare.com/ai-prompt-protection/#closing-the-loop-logging) or refer to [AI prompt topics](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/detection-entries/#ai-prompt-topics).
---
title: Manage and deploy your AI provider keys through Bring Your Own Key (BYOK)
with AI Gateway, now powered by Cloudflare Secrets Store · Changelog
description: Cloudflare Secrets Store is now integrated with AI Gateway,
allowing you to store, manage, and deploy your AI provider keys in a secure
and seamless configuration through [Bring Your Own
Key](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/).
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-25-secrets-store-ai-gateway/
md: https://developers.cloudflare.com/changelog/2025-08-25-secrets-store-ai-gateway/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Manage and deploy your AI provider keys through Bring Your Own Key (BYOK) with AI Gateway, now powered by Cloudflare Secrets Store
Aug 25, 2025
[Secrets Store ](https://developers.cloudflare.com/secrets-store/)[AI Gateway ](https://developers.cloudflare.com/ai-gateway/)[SSL/TLS](https://developers.cloudflare.com/ssl/)
Cloudflare Secrets Store is now integrated with AI Gateway, allowing you to store, manage, and deploy your AI provider keys in a secure and seamless configuration through [Bring Your Own Key](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/). Instead of passing your AI provider keys directly in every request header, you can centrally manage each key with Secrets Store and deploy in your gateway configuration using only a reference, rather than passing the value in plain text.
You can now create a secret directly from your AI Gateway [in the dashboard](http://dash.cloudflare.com/?to=/:account/ai-gateway) by navigating into your gateway -> **Provider Keys** -> **Add**.

You can also create your secret with the newly available **ai\_gateway** scope via [wrangler](https://developers.cloudflare.com/workers/wrangler/commands/), the [Secrets Store dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store), or the [API](https://developers.cloudflare.com/api/resources/secrets_store/).
Then, pass the key in the request header using its Secrets Store reference:
```plaintext
curl -X POST https://gateway.ai.cloudflare.com/v1//my-gateway/anthropic/v1/messages \
--header 'cf-aig-authorization: ANTHROPIC_KEY_1 \
--header 'anthropic-version: 2023-06-01' \
--header 'Content-Type: application/json' \
--data '{"model": "claude-3-opus-20240229", "messages": [{"role": "user", "content": "What is Cloudflare?"}]}'
```
Or, using Javascript:
```plaintext
import Anthropic from '@anthropic-ai/sdk';
const anthropic = new Anthropic({
apiKey: "ANTHROPIC_KEY_1",
baseURL: "https://gateway.ai.cloudflare.com/v1//my-gateway/anthropic",
});
const message = await anthropic.messages.create({
model: 'claude-3-opus-20240229',
messages: [{role: "user", content: "What is Cloudflare?"}],
max_tokens: 1024
});
```
For more information, check out the [blog](https://blog.cloudflare.com/ai-gateway-aug-2025-refresh)!
---
title: WAF Release - 2025-08-25 · Changelog
description: Cloudflare WAF managed rulesets 2025-08-25 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-25-waf-release/
md: https://developers.cloudflare.com/changelog/2025-08-25-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-08-25
Aug 25, 2025
[WAF](https://developers.cloudflare.com/waf/)
**This week's update**
This week, critical vulnerabilities were disclosed that impact widely used open-source infrastructure, creating high-risk scenarios for code execution and operational disruption.
**Key Findings**
* Apache HTTP Server – Code Execution (CVE-2024-38474): A flaw in Apache HTTP Server allows attackers to achieve remote code execution, enabling full compromise of affected servers. This vulnerability threatens the confidentiality, integrity, and availability of critical web services.
* Laravel (CVE-2024-55661): A security flaw in Laravel introduces the potential for remote code execution under specific conditions. Exploitation could provide attackers with unauthorized access to application logic and sensitive backend data.
**Impact**
These vulnerabilities pose severe risks to enterprise environments and open-source ecosystems. Remote code execution enables attackers to gain deep system access, steal data, disrupt services, and establish persistent footholds for broader intrusions. Given the widespread deployment of Apache HTTP Server and Laravel in production systems, timely patching and mitigation are critical.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | c550282a0f7343ca887bdab528050359 | 100822\_BETA | WordPress:Plugin:WPBookit - Remote Code Execution - CVE:CVE-2025-6058 | N/A | Disabled | This was merged in to the original rule "WordPress:Plugin:WPBookit - Remote Code Execution - CVE:CVE-2025-6058" (ID: 9b5c5e13d2ca4253a89769f2194f7b2d ) |
| Cloudflare Managed Ruleset | 456b1e8f827b4ed89fb4a54b3bdcdbad | 100831 | Apache HTTP Server - Code Execution - CVE:CVE-2024-38474 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 7dcc01e1dd074e42a26c8ca002eaac5b | 100846 | Laravel - Remote Code Execution - CVE:CVE-2024-55661 | Log | Disabled | This is a New Detection |
---
title: Content type returned in Workers Assets for Javascript files is now
`text/javascript` · Changelog
description: Updated JavaScript asset responses to use the standardized
text/javascript Content-Type header (previously `application/javascript`) for
better alignment with the HTML spec and browser expectations.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-25-workers-assets-javascript-content-type/
md: https://developers.cloudflare.com/changelog/2025-08-25-workers-assets-javascript-content-type/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Content type returned in Workers Assets for Javascript files is now \`text/javascript\`
Aug 25, 2025
[Workers](https://developers.cloudflare.com/workers/)
JavaScript asset responses have been updated to use the `text/javascript` Content-Type header instead of `application/javascript`. While both MIME types are widely supported by browsers, the HTML Living Standard explicitly recommends `text/javascript` as the preferred type going forward.
This change improves:
* Standards alignment: Ensures consistency with the HTML spec and modern web platform guidance.
* Interoperability: Some developer tools, validators, and proxies expect text/javascript and may warn or behave inconsistently with application/javascript.
* Future-proofing: By following the spec-preferred MIME type, we reduce the risk of deprecation warnings or unexpected behavior in evolving browser environments.
* Consistency: Most frameworks, CDNs, and hosting providers now default to text/javascript, so this change matches common ecosystem practice.
Because all major browsers accept both MIME types, this update is backwards compatible and should not cause breakage.
Users will see this change on the next deployment of their assets.
---
title: Manage and restrict access to internal MCP servers with Cloudflare Access
· Changelog
description: Access self-hosted applications now support MCP OAuth. This allows
MCP clients to connect to self-hosted applications through an Access-protected
MCP server.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-26-access-mcp-oauth/
md: https://developers.cloudflare.com/changelog/2025-08-26-access-mcp-oauth/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Manage and restrict access to internal MCP servers with Cloudflare Access
Aug 26, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
You can now control who within your organization has access to internal MCP servers, by putting internal MCP servers behind [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/).
[Self-hosted applications](https://developers.cloudflare.com/cloudflare-one/access-controls/ai-controls/linked-apps/) in Cloudflare Access now support OAuth for MCP server authentication. This allows Cloudflare to delegate access from any self-hosted application to an MCP server via OAuth. The OAuth access token authorizes the MCP server to make requests to your self-hosted applications on behalf of the authorized user, using that user's specific permissions and scopes.
For example, if you have an MCP server designed for internal use within your organization, you can configure Access policies to ensure that only authorized users can access it, regardless of which MCP client they use. Support for internal, self-hosted MCP servers also works with MCP server portals, allowing you to provide a single MCP endpoint for multiple MCP servers. For more on MCP server portals, read the [blog post](https://blog.cloudflare.com/zero-trust-mcp-server-portals/) on the Cloudflare Blog.
---
title: New CASB integrations for ChatGPT, Claude, and Gemini · Changelog
description: Cloudflare CASB now scans ChatGPT, Claude, and Gemini for
misconfigurations, sensitive data exposure, and compliance issues, helping
organizations adopt AI with confidence.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-26-casb-ai-integrations/
md: https://developers.cloudflare.com/changelog/2025-08-26-casb-ai-integrations/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New CASB integrations for ChatGPT, Claude, and Gemini
Aug 26, 2025
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
[Cloudflare CASB](https://www.cloudflare.com/zero-trust/products/casb/) now supports three of the most widely used GenAI platforms — **OpenAI ChatGPT**, **Anthropic Claude**, and **Google Gemini**. These API-based integrations give security teams agentless visibility into posture, data, and compliance risks across their organization’s use of generative AI.

#### Key capabilities
* **Agentless connections** — connect ChatGPT, Claude, and Gemini tenants via API; no endpoint software required
* **Posture management** — detect insecure settings and misconfigurations that could lead to data exposure
* **DLP detection** — identify sensitive data in uploaded chat attachments or files
* **GenAI-specific insights** — surface risks unique to each provider’s capabilities
#### Learn more
* [ChatGPT integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/openai/)
* [Claude integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/anthropic/)
* [Gemini integration docs](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/google-workspace/gemini/)
These integrations are available to all Cloudflare One customers today.
---
title: MCP server portals · Changelog
description: Cloudflare Zero Trust MCP server portals allow admins to centralize
all of their MCP servers and enforce user-specific security policies.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-26-mcp-server-portals/
md: https://developers.cloudflare.com/changelog/2025-08-26-mcp-server-portals/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## MCP server portals
Aug 26, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)

An [MCP server portal](https://developers.cloudflare.com/cloudflare-one/access-controls/ai-controls/mcp-portals/) centralizes multiple Model Context Protocol (MCP) servers onto a single HTTP endpoint. Key benefits include:
* **Streamlined access to multiple MCP servers**: MCP server portals support both unauthenticated MCP servers as well as MCP servers secured using any third-party or custom OAuth provider. Users log in to the portal URL through Cloudflare Access and are prompted to authenticate separately to each server that requires OAuth.
* **Customized tools per portal**: Admins can tailor an MCP portal to a particular use case by choosing the specific tools and prompt templates that they want to make available to users through the portal. This allows users to access a curated set of tools and prompts — the less external context exposed to the AI model, the better the AI responses tend to be.
* **Observability**: Once the user's AI agent is connected to the portal, Cloudflare Access logs the indiviudal requests made using the tools in the portal.
This is available in an open beta for all customers across all plans! For more information check out our [blog](https://blog.cloudflare.com/zero-trust-mcp-server-portals/) for this release.
---
title: List all vectors in a Vectorize index with the new list-vectors operation
· Changelog
description: Enumerate all vector identifiers in your Vectorize indexes for bulk
operations, auditing, and data migration.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-26-vectorize-list-vectors/
md: https://developers.cloudflare.com/changelog/2025-08-26-vectorize-list-vectors/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## List all vectors in a Vectorize index with the new list-vectors operation
Aug 26, 2025
[Vectorize](https://developers.cloudflare.com/vectorize/)
You can now list all vector identifiers in a Vectorize index using the new `list-vectors` operation. This enables bulk operations, auditing, and data migration workflows through paginated requests that maintain snapshot consistency.
The operation is available via Wrangler CLI and REST API. Refer to the [list-vectors best practices guide](https://developers.cloudflare.com/vectorize/best-practices/list-vectors/) for detailed usage guidance.
---
title: Enhanced crawler insights and custom 402 responses · Changelog
description: Get detailed crawler analytics with trend charts and configure
custom payment-required responses for blocked AI crawlers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-27-ai-crawl-control-launch/
md: https://developers.cloudflare.com/changelog/2025-08-27-ai-crawl-control-launch/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Enhanced crawler insights and custom 402 responses
Aug 27, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
We improved AI crawler management with detailed analytics and introduced custom HTTP 402 responses for blocked crawlers. AI Audit has been renamed to AI Crawl Control and is now generally available.
**Enhanced Crawlers tab:**
* View total allowed and blocked requests for each AI crawler
* Trend charts show crawler activity over your selected time range per crawler

**Custom block responses (paid plans):** You can now return HTTP 402 "Payment Required" responses when blocking AI crawlers, enabling direct communication with crawler operators about licensing terms.
For users on paid plans, when blocking AI crawlers you can configure:
* **Response code:** Choose between 403 Forbidden or 402 Payment Required
* **Response body:** Add a custom message with your licensing contact information

Example 402 response:
```http
HTTP 402 Payment Required
Date: Mon, 24 Aug 2025 12:56:49 GMT
Content-type: application/json
Server: cloudflare
Cf-Ray: 967e8da599d0c3fa-EWR
Cf-Team: 2902f6db750000c3fa1e2ef400000001
{
"message": "Please contact the site owner for access."
}
```
---
title: Deepgram and Leonardo partner models now available on Workers AI · Changelog
description: State-of-the-art TTS, STT and image generation models, hosted on
Workers AI infrastructure
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-27-partner-models/
md: https://developers.cloudflare.com/changelog/2025-08-27-partner-models/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Deepgram and Leonardo partner models now available on Workers AI
Aug 27, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
New state-of-the-art models have landed on Workers AI! This time, we're introducing new **partner models** trained by our friends at [Deepgram](https://deepgram.com) and [Leonardo](https://leonardo.ai), hosted on Workers AI infrastructure.
As well, we're introuding a new turn detection model that enables you to detect when someone is done speaking — useful for building voice agents!
Read the [blog](https://blog.cloudflare.com/workers-ai-partner-models) for more details and check out some of the new models on our platform:
* [`@cf/deepgram/aura-1`](https://developers.cloudflare.com/workers-ai/models/aura-1) is a text-to-speech model that allows you to input text and have it come to life in a customizable voice
* [`@cf/deepgram/nova-3`](https://developers.cloudflare.com/workers-ai/models/nova-3) is speech-to-text model that transcribes multilingual audio at a blazingly fast speed
* [`@cf/pipecat-ai/smart-turn-v2`](https://developers.cloudflare.com/workers-ai/models/smart-turn-v2) helps you detect when someone is done speaking
* [`@cf/leonardo/lucid-origin`](https://developers.cloudflare.com/workers-ai/models/lucid-origin) is a text-to-image model that generates images with sharp graphic design, stunning full-HD renders, or highly specific creative direction
* [`@cf/leonardo/phoenix-1.0`](https://developers.cloudflare.com/workers-ai/models/phoenix-1.0) is a text-to-image model with exceptional prompt adherence and coherent text
You can filter out new partner models with the `Partner` capability on our [Models](https://developers.cloudflare.com/workers-ai/models) page.
As well, we're introducing WebSocket support for some of our audio models, which you can filter though the `Realtime` capability on our [Models](https://developers.cloudflare.com/workers-ai/models) page. WebSockets allows you to create a bi-directional connection to our inference server with low latency — perfect for those that are building voice agents.
An example python snippet on how to use WebSockets with our new Aura model:
```plaintext
import json
import os
import asyncio
import websockets
uri = f"wss://api.cloudflare.com/client/v4/accounts/{ACCOUNT_ID}/ai/run/@cf/deepgram/aura-1"
input = [
"Line one, out of three lines that will be provided to the aura model.",
"Line two, out of three lines that will be provided to the aura model.",
"Line three, out of three lines that will be provided to the aura model. This is a last line.",
]
async def text_to_speech():
async with websockets.connect(uri, additional_headers={"Authorization": os.getenv("CF_TOKEN")}) as websocket:
print("connection established")
for line in input:
print(f"sending `{line}`")
await websocket.send(json.dumps({"type": "Speak", "text": line}))
print("line was sent, flushing")
await websocket.send(json.dumps({"type": "Flush"}))
print("flushed, recving")
resp = await websocket.recv()
print(f"response received {resp}")
if __name__ == "__main__":
asyncio.run(text_to_speech())
```
---
title: Shadow IT - SaaS analytics dashboard · Changelog
description: An upgraded analytics experience for analyzing SaaS Shadow IT with
Cloudflare One.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-27-shadow-it-analytics/
md: https://developers.cloudflare.com/changelog/2025-08-27-shadow-it-analytics/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Shadow IT - SaaS analytics dashboard
Aug 27, 2025
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust has significantly upgraded its **Shadow IT analytics**, providing you with unprecedented visibility into your organizations use of SaaS tools. With this dashboard, you can review who is using an application and volumes of data transfer to the application.
You can review these metrics against application type, such as Artificial Intelligence or Social Media. You can also mark applications with an approval status, including **Unreviewed**, **In Review**, **Approved**, and **Unapproved** designating how they can be used in your organization.

These application statuses can also be used in Gateway HTTP policies, so you can block, isolate, limit uploads and downloads, and more based on the application status.
Both the analytics and policies are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
---
title: DEX MCP Server · Changelog
description: A Model Context Protocol (MCP) Server for Digital Experience
Monitoring (DEX) is now available
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-29-dex-mcp-server/
md: https://developers.cloudflare.com/changelog/2025-08-29-dex-mcp-server/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## DEX MCP Server
Aug 29, 2025
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into device connectivity and performance across your Cloudflare SASE deployment.
We've released an MCP server [(Model Context Protocol)](https://cloudflare.com/learning/ai/what-is-model-context-protocol-mcp/) for DEX.
The DEX MCP server is an AI tool that allows customers to ask a question like, "Show me the connectivity and performance metrics for the device used by carly@acme.com", and receive an answer that contains data from the DEX API.
Any Cloudflare One customer using a Free, PayGo, or Enterprise account can access the DEX MCP Server. This feature is available to everyone.
Customers can test the new DEX MCP server in less than one minute. To learn more, read the [DEX MCP server documentation](https://developers.cloudflare.com/cloudflare-one/insights/dex/dex-mcp-server/).
---
title: WAF Release - 2025-08-29 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-08-29 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-29-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-08-29-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-08-29 - Emergency
Aug 29, 2025
[WAF](https://developers.cloudflare.com/waf/)
**This week's update**
This week, new critical vulnerabilities were disclosed in Next.js’s image optimization functionality, exposing a broad range of production environments to risks of data exposure and cache manipulation.
**Key Findings**
* CVE-2025-55173: Arbitrary file download from the server via image optimization.
* CVE-2025-57752: Cache poisoning leading to unauthorized data disclosure.
**Impact**
Exploitation could expose sensitive files, leak user or backend data, and undermine application trust. Given Next.js’s wide use, immediate patching and cache hardening are strongly advised.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | ea55f8aac44246cc9b827eea9ff4bfe3 | 100613 | Next.js - Dangerous File Download - CVE:CVE-2025-55173 | N/A | Block | This is a new detection |
| Cloudflare Managed Ruleset | e2b2d77a79cc4a76bf7ba53d69b9ea7d | 100616 | Next.js - Information Disclosure - CVE:CVE-2025-57752 | N/A | Block | This is a new detection |
---
title: Smart Tiered Cache Fallback to Generic · Changelog
description: Smart Tiered Cache now falls back to Generic Tiered Cache when
origin location cannot be determined, improving cache precision.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-29-smart-tiered-cache-fallback-to-generic/
md: https://developers.cloudflare.com/changelog/2025-08-29-smart-tiered-cache-fallback-to-generic/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Smart Tiered Cache Fallback to Generic
Aug 29, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
[Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#smart-tiered-cache) now falls back to [Generic Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/#generic-global-tiered-cache) when the origin location cannot be determined, improving cache precision for your content.
Previously, when Smart Tiered Cache was unable to select the optimal upper tier (such as when origins are masked by Anycast IPs), latency could be negatively impacted. This fallback now uses Generic Tiered Cache instead, providing better performance and cache efficiency.
#### How it works
When Smart Tiered Cache falls back to Generic Tiered Cache:
1. **Multiple upper-tiers**: Uses all of Cloudflare's global data centers as a network of upper-tiers instead of a single optimal location.
2. **Distributed cache requests**: Lower-tier data centers can query any available upper-tier for cached content.
3. **Improved global coverage**: Provides better cache hit ratios across geographically distributed visitors.
4. **Automatic fallback**: Seamlessly transitions when origin location cannot be determined, such as with Anycast-masked origins.
#### Benefits
* **Preserves high performance during fallback**: Smart Tiered Cache now maintains strong cache efficiency even when optimal upper tier selection is not possible.
* **Minimizes latency impact**: Automatically uses Generic Tiered Cache topology to keep performance high when origin location cannot be determined.
* **Seamless experience**: No configuration changes or intervention required when fallback occurs.
* **Improved resilience**: Smart Tiered Cache remains effective across diverse origin infrastructure, including Anycast-masked origins.
#### Get started
This improvement is automatically applied to all zones using [Smart Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/). No action is required on your part.
---
title: Terraform v5.9 now available · Changelog
description: Terraform v5.9 stabilizes a number of resources and known issues
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-29-terrform-v59-provider/
md: https://developers.cloudflare.com/changelog/2025-08-29-terrform-v59-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.9 now available
Aug 29, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new [Terraform v5 Provider](https://developers.cloudflare.com/changelog/2025-02-03-terraform-v5-provider/). We are aware of the high number of [issues](https://github.com/cloudflare/terraform-provider-cloudflare) reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a 2 week cadence to ensure its stability and reliability, including the v5.9 release. We have also pivoted from an issue-to-issue approach to a resource-per-resource approach - we will be focusing on specific resources for every release, stabilizing the release, and closing all associated bugs with that resource before moving onto resolving migration issues.
Thank you for continuing to raise issues. We triage them weekly and they help make our products stronger.
This release includes a new resource, `cloudflare_snippet`, which replaces `cloudflare_snippets`. `cloudflare_snippet` is now considered deprecated but can still be used. Please utilize `cloudflare_snippet` as soon as possible.
#### Changes
* Resources stabilized:
* `cloudflare_zone_setting`
* `cloudflare_worker_script`
* `cloudflare_worker_route`
* `tiered_cache`
* **NEW** resource `cloudflare_snippet` which should be used in place of `cloudflare_snippets`. `cloudflare_snippets` is now deprecated. This enables the management of Cloudflare's snippet functionality through Terraform.
* DNS Record Improvements: Enhanced handling of DNS record drift detection
* Load Balancer Fixes: Resolved `created_on` field inconsistencies and improved pool configuration handling
* Bot Management: Enhanced auto-update model state consistency and fight mode configurations
* Other bug fixes
For a more detailed look at all of the changes, refer to the [changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.9.0) in GitHub.
#### Issues Closed
* [#5921: In cloudflare\_ruleset removing an existing rule causes recreation of later rules](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5921)
* [#5904: cloudflare\_zero\_trust\_access\_application is not idempotent](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5904)
* [#5898: (cloudflare\_workers\_script) Durable Object migrations not applied](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5898)
* [#5892: cloudflare\_workers\_script secret\_text environment variable gets replaced on every deploy](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5892)
* [#5891: cloudflare\_zone suddenly started showing drift](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5891)
* [#5882: cloudflare\_zero\_trust\_list always marked for change due to read only attributes](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5882)
* [#5879: cloudflare\_zero\_trust\_gateway\_certificate unable to manage resource (cant mark as active/inactive)](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5879)
* [#5858: cloudflare\_dns\_records is always updated in-place](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5858)
* [#5839: Recurring change on cloudflare\_zero\_trust\_gateway\_policy after upgrade to V5 provider & also setting expiration fails](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5839)
* [#5811: Reusable policies are imported as inline type for cloudflare\_zero\_trust\_access\_application](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5811)
* [#5795: cloudflare\_zone\_setting inconsistent value of "editable" upon apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5795)
* [#5789: Pagination issue fetching all policies in "cloudflare\_zero\_trust\_access\_policies" data source](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5789)
* [#5770: cloudflare\_zero\_trust\_access\_application type warp diff on every apply](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5770)
* [#5765: V5 / cloudflare\_zone\_dnssec fails with HTTP/400 "Malformed request body"](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5765)
* [#5755: Unable to manage Cloudflare managed WAF rules via Terraform](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5755)
* [#5738: v4 to v5 upgrade failing Error: no schema available AND Unable to Read Previously Saved State for UpgradeResourceState](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5738)
* [#5727: cloudflare\_ruleset http\_request\_cache\_settings bypass mismatch between dashboard and terraform](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5727)
* [#5700: cloudflare\_account\_member invalid type 'string' for field 'roles'](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5700)
If you have an unaddressed issue with the provider, we encourage you to check the [open issues](https://github.com/cloudflare/terraform-provider-cloudflare/issues) and open a new issue if one does not already exist for what you are experiencing.
#### Upgrading
We suggest holding off on migration to v5 while we work on stabilization. This help will you avoid any blocking issues while the Terraform resources are actively being stabilized.
If you'd like more information on migrating from v4 to v5, please make use of the [migration guide](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/guides/version-5-upgrade). We have provided automated migration scripts using Grit which simplify the transition. These do not support implementations which use Terraform modules, so customers making use of modules need to migrate manually. Please make use of `terraform plan` to test your changes before applying, and let us know if you encounter any additional issues by reporting to our [GitHub repository](https://github.com/cloudflare/terraform-provider-cloudflare).
#### For more info
* [Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
* [GitHub Repository](https://github.com/cloudflare/terraform-provider-cloudflare)
---
title: Cloudflare One WARP Diagnostic AI Analyzer · Changelog
description: Cloudflare One WARP Diagnostic AI Analyzer
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-08-29-warp-ai-diag-analyzer/
md: https://developers.cloudflare.com/changelog/2025-08-29-warp-ai-diag-analyzer/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare One WARP Diagnostic AI Analyzer
Aug 29, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
We're excited to share a new AI feature, the [WARP diagnostic analyzer](https://blog.cloudflare.com/AI-troubleshoot-warp-and-network-connectivity-issues/), to help you troubleshoot and resolve WARP connectivity issues faster. This beta feature is now available in the [Zero Trust dashboard](https://one.dash.cloudflare.com/) to all users. The AI analyzer makes it easier for you to identify the root cause of client connectivity issues by parsing [remote captures](https://developers.cloudflare.com/cloudflare-one/insights/dex/remote-captures/#start-a-remote-capture) of [WARP diagnostic logs](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/troubleshooting/warp-logs/#warp-diag-logs). The WARP diagnostic analyzer provides a summary of impact that may be experienced on the device, lists notable events that may contribute to performance issues, and recommended troubleshooting steps and articles to help you resolve these issues. Refer to [WARP diagnostics analyzer (beta)](https://developers.cloudflare.com/cloudflare-one/insights/dex/remote-captures/#warp-diagnostics-analyzer-beta) to learn more about how to maximize using the WARP diagnostic analyzer to troubleshoot the WARP client.
---
title: Updated Email security roles · Changelog
description: More granular controls for Email security roles
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-01-updated-new-roles/
md: https://developers.cloudflare.com/changelog/2025-09-01-updated-new-roles/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Updated Email security roles
Sep 01, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
To provide more granular controls, we refined the [existing roles](https://developers.cloudflare.com/cloudflare-one/roles-permissions/#email-security-roles) for Email security and launched a new Email security role as well.
All Email security roles no longer have read or write access to any of the other Zero Trust products:
* **Email Configuration Admin**
* **Email Integration Admin**
* **Email security Read Only**
* **Email security Analyst**
* **Email security Policy Admin**
* **Email security Reporting**
To configure [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/email-security/outbound-dlp/) or [Remote Browser Isolation (RBI)](https://developers.cloudflare.com/cloudflare-one/remote-browser-isolation/setup/clientless-browser-isolation/#set-up-clientless-web-isolation), you now need to be an admin for the Zero Trust dashboard with the **Cloudflare Zero Trust** role.
Also through customer feedback, we have created a new additive role to allow **Email security Analyst** to create, edit, and delete Email security policies, without needing to provide access via the **Email Configuration Admin** role. This role is called **Email security Policy Admin**, which can read all settings, but has write access to [allow policies](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/allow-policies/), [trusted domains](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/trusted-domains/), and [blocked senders](https://developers.cloudflare.com/cloudflare-one/email-security/settings/detection-settings/blocked-senders/).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: WAF Release - 2025-09-01 · Changelog
description: Cloudflare WAF managed rulesets 2025-09-01 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-01-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-01-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-01
Sep 01, 2025
[WAF](https://developers.cloudflare.com/waf/)
**This week's update**
This week, a critical vulnerability was disclosed in Fortinet FortiWeb (versions 7.6.3 and below, versions 7.4.7 and below, versions 7.2.10 and below, and versions 7.0.10 and below), linked to improper parameter handling that could allow unauthorized access.
**Key Findings**
* Fortinet FortiWeb (CVE-2025-52970): A vulnerability may allow an unauthenticated remote attacker with access to non-public information to log in as any existing user on the device via a specially crafted request.
**Impact**
Exploitation could allow an unauthenticated attacker to impersonate any existing user on the device, potentially enabling them to modify system settings or exfiltrate sensitive information, posing a serious security risk. Upgrading to the latest vendor-released version is strongly recommended.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 636b145a49a84946b990d4fac49b7cf8 | 100586 | Fortinet FortiWeb - Auth Bypass - CVE:CVE-2025-52970 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | b5ef1ace353841a0856b5e07790c9dde | 100136C | XSS - JavaScript - Headers and Body | N/A | N/A | Rule metadata description refined. Detection unchanged. |
---
title: Increased static asset limits for Workers · Changelog
description: Paid and Workers for Platforms users can now upload up to 100,000
static assets per Worker version, up from the previous limit of 20,000.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-02-increased-static-asset-limits/
md: https://developers.cloudflare.com/changelog/2025-09-02-increased-static-asset-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased static asset limits for Workers
Sep 04, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
You can now upload up to **100,000 static assets** per Worker version
* Paid and Workers for Platforms users can now upload up to **100,000 static assets** per Worker version, a 5x increase from the previous limit of 20,000.
* Customers on the free plan still have the same limit as before — 20,000 static assets per version of your Worker
* The individual file size limit of 25 MiB remains unchanged for all customers.
This increase allows you to build larger applications with more static assets without hitting limits.
#### Wrangler
To take advantage of the increased limits, you must use **Wrangler version 4.34.0 or higher**. Earlier versions of Wrangler will continue to enforce the previous 20,000 file limit.
#### Learn more
For more information about Workers static assets, see the [Static Assets documentation](https://developers.cloudflare.com/workers/static-assets/) and [Platform Limits](https://developers.cloudflare.com/workers/platform/limits/#static-assets).
---
title: Cloudflare Tunnel and Networks API will no longer return deleted
resources by default starting December 1, 2025 · Changelog
description: The is_deleted parameter for specific Cloudflare Tunnel and Zero
Trust Networks list API endpoints will default to false. To retrieve deleted
resources, you must explicitly set this parameter to true.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-02-tunnel-networks-list-endpoints-new-default/
md: https://developers.cloudflare.com/changelog/2025-09-02-tunnel-networks-list-endpoints-new-default/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Tunnel and Networks API will no longer return deleted resources by default starting December 1, 2025
Sep 02, 2025
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
Starting **December 1, 2025**, list endpoints for the [Cloudflare Tunnel API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/) and [Zero Trust Networks API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/) will no longer return deleted tunnels, routes, subnets and virtual networks by default. This change makes the API behavior more intuitive by only returning active resources unless otherwise specified.
No action is required if you already explicitly set `is_deleted=false` or if you only need to list active resources.
This change affects the following API endpoints:
* List all tunnels: [`GET /accounts/{account_id}/tunnels`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/methods/list/)
* List [Cloudflare Tunnels](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/): [`GET /accounts/{account_id}/cfd_tunnel`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/subresources/cloudflared/methods/list/)
* List [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) tunnels: [`GET /accounts/{account_id}/warp_connector`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/subresources/warp_connector/methods/list/)
* List tunnel routes: [`GET /accounts/{account_id}/teamnet/routes`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/routes/methods/list/)
* List subnets: [`GET /accounts/{account_id}/zerotrust/subnets`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/subnets/methods/list/)
* List virtual networks: [`GET /accounts/{account_id}/teamnet/virtual_networks`](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/subresources/virtual_networks/methods/list/)
#### What is changing?
The default behavior of the `is_deleted` query parameter will be updated.
| Scenario | Previous behavior (before December 1, 2025) | New behavior (from December 1, 2025) |
| - | - | - |
| `is_deleted` parameter is omitted | Returns **active & deleted** tunnels, routes, subnets and virtual networks | Returns **only active** tunnels, routes, subnets and virtual networks |
#### Action required
If you need to retrieve deleted (or all) resources, please update your API calls to explicitly include the `is_deleted` parameter before **December 1, 2025**.
To get a list of only deleted resources, you must now explicitly add the `is_deleted=true` query parameter to your request:
```bash
# Example: Get ONLY deleted Tunnels
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/tunnels?is_deleted=true" \
-H "Authorization: Bearer $API_TOKEN"
# Example: Get ONLY deleted Virtual Networks
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/teamnet/virtual_networks?is_deleted=true" \
-H "Authorization: Bearer $API_TOKEN"
```
Following this change, retrieving a complete list of both active and deleted resources will require two separate API calls: one to get active items (by omitting the parameter or using `is_deleted=false`) and one to get deleted items (`is_deleted=true`).
#### Why we’re making this change
This update is based on user feedback and aims to:
* **Create a more intuitive default:** Aligning with common API design principles where list operations return only active resources by default.
* **Reduce unexpected results:** Prevents users from accidentally operating on deleted resources that were returned unexpectedly.
* **Improve performance:** For most users, the default query result will now be smaller and more relevant.
To learn more, please visit the [Cloudflare Tunnel API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/tunnels/) and [Zero Trust Networks API](https://developers.cloudflare.com/api/resources/zero_trust/subresources/networks/) documentation.
---
title: Agents SDK v0.1.0 and workers-ai-provider v2.0.0 with AI SDK v5 support ·
Changelog
description: The latest release updates the Agents SDK with full AI SDK v5
compatibility, updated workers-ai-provider v2.0.0 with enhanced streaming and
tool support, seamless legacy message migration, tool confirmation detection,
and React hooks for building production-ready AI chat interfaces.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-03-agents-sdk-beta-v5/
md: https://developers.cloudflare.com/changelog/2025-09-03-agents-sdk-beta-v5/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Agents SDK v0.1.0 and workers-ai-provider v2.0.0 with AI SDK v5 support
Sep 10, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We've shipped a new release for the [Agents SDK](https://github.com/cloudflare/agents) bringing full compatibility with [AI SDK v5](https://ai-sdk.dev/docs/introduction) and introducing automatic message migration that handles all legacy formats transparently.
This release includes improved streaming and tool support, tool confirmation detection (for "human in the loop" systems), enhanced React hooks with automatic tool resolution, improved error handling for streaming responses, and seamless migration utilities that work behind the scenes.
This makes it ideal for building production AI chat interfaces with Cloudflare Workers AI models, agent workflows, human-in-the-loop systems, or any application requiring reliable message handling across SDK versions — all while maintaining backward compatibility.
Additionally, we've updated workers-ai-provider v2.0.0, the official provider for Cloudflare Workers AI models, to be compatible with AI SDK v5.
#### useAgentChat(options)
Creates a new chat interface with enhanced v5 capabilities.
```ts
// Basic chat setup
const { messages, sendMessage, addToolResult } = useAgentChat({
agent,
experimental_automaticToolResolution: true,
tools,
});
// With custom tool confirmation
const chat = useAgentChat({
agent,
experimental_automaticToolResolution: true,
toolsRequiringConfirmation: ["dangerousOperation"],
});
```
#### Automatic Tool Resolution
Tools are automatically categorized based on their configuration:
```ts
const tools = {
// Auto-executes (has execute function)
getLocalTime: {
description: "Get current local time",
inputSchema: z.object({}),
execute: async () => new Date().toLocaleString(),
},
// Requires confirmation (no execute function)
deleteFile: {
description: "Delete a file from the system",
inputSchema: z.object({
filename: z.string(),
}),
},
// Server-executed (no client confirmation)
analyzeData: {
description: "Analyze dataset on server",
inputSchema: z.object({ data: z.array(z.number()) }),
serverExecuted: true,
},
} satisfies Record;
```
#### Message Handling
Send messages using the new v5 format with parts array:
```ts
// Text message
sendMessage({
role: "user",
parts: [{ type: "text", text: "Hello, assistant!" }],
});
// Multi-part message with file
sendMessage({
role: "user",
parts: [
{ type: "text", text: "Analyze this image:" },
{ type: "image", image: imageData },
],
});
```
#### Tool Confirmation Detection
Simplified logic for detecting pending tool confirmations:
```ts
const pendingToolCallConfirmation = messages.some((m) =>
m.parts?.some(
(part) => isToolUIPart(part) && part.state === "input-available",
),
);
// Handle tool confirmation
if (pendingToolCallConfirmation) {
await addToolResult({
toolCallId: part.toolCallId,
tool: getToolName(part),
output: "User approved the action",
});
}
```
#### Automatic Message Migration
Seamlessly handle legacy message formats without code changes.
```ts
// All these formats are automatically converted:
// Legacy v4 string content
const legacyMessage = {
role: "user",
content: "Hello world",
};
// Legacy v4 with tool calls
const legacyWithTools = {
role: "assistant",
content: "",
toolInvocations: [
{
toolCallId: "123",
toolName: "weather",
args: { city: "SF" },
state: "result",
result: "Sunny, 72°F",
},
],
};
// Automatically becomes v5 format:
// {
// role: "assistant",
// parts: [{
// type: "tool-call",
// toolCallId: "123",
// toolName: "weather",
// args: { city: "SF" },
// state: "result",
// result: "Sunny, 72°F"
// }]
// }
```
#### Tool Definition Updates
Migrate tool definitions to use the new `inputSchema` property.
```ts
// Before (AI SDK v4)
const tools = {
weather: {
description: "Get weather information",
parameters: z.object({
city: z.string(),
}),
execute: async (args) => {
return await getWeather(args.city);
},
},
};
// After (AI SDK v5)
const tools = {
weather: {
description: "Get weather information",
inputSchema: z.object({
city: z.string(),
}),
execute: async (args) => {
return await getWeather(args.city);
},
},
};
```
#### Cloudflare Workers AI Integration
Seamless integration with Cloudflare Workers AI models through the updated workers-ai-provider v2.0.0.
#### Model Setup with Workers AI
Use Cloudflare Workers AI models directly in your agent workflows:
```ts
import { createWorkersAI } from "workers-ai-provider";
import { useAgentChat } from "agents/ai-react";
// Create Workers AI model (v2.0.0 - same API, enhanced v5 internals)
const model = createWorkersAI({
binding: env.AI,
})("@cf/meta/llama-3.2-3b-instruct");
```
#### Enhanced File and Image Support
Workers AI models now support v5 file handling with automatic conversion:
```ts
// Send images and files to Workers AI models
sendMessage({
role: "user",
parts: [
{ type: "text", text: "Analyze this image:" },
{
type: "file",
data: imageBuffer,
mediaType: "image/jpeg",
},
],
});
// Workers AI provider automatically converts to proper format
```
#### Streaming with Workers AI
Enhanced streaming support with automatic warning detection:
```ts
// Streaming with Workers AI models
const result = await streamText({
model: createWorkersAI({ binding: env.AI })("@cf/meta/llama-3.2-3b-instruct"),
messages,
onChunk: (chunk) => {
// Enhanced streaming with warning handling
console.log(chunk);
},
});
```
#### Import Updates
Update your imports to use the new v5 types:
```ts
// Before (AI SDK v4)
import type { Message } from "ai";
import { useChat } from "ai/react";
// After (AI SDK v5)
import type { UIMessage } from "ai";
// or alias for compatibility
import type { UIMessage as Message } from "ai";
import { useChat } from "@ai-sdk/react";
```
#### Resources
* [Migration Guide](https://github.com/cloudflare/agents/blob/main/docs/migration-to-ai-sdk-v5.md) - Comprehensive migration documentation
* [AI SDK v5 Documentation](https://ai-sdk.dev/docs/migration-guides/migration-guide-5-0) - Official AI SDK migration guide
* [An Example PR showing the migration from AI SDK v4 to v5](https://github.com/cloudflare/agents-starter/pull/105)
* [GitHub Issues](https://github.com/cloudflare/agents/issues) - Report bugs or request features
#### Feedback Welcome
We'd love your feedback! We're particularly interested in feedback on:
* **Migration experience** - How smooth was the upgrade process?
* **Tool confirmation workflow** - Does the new automatic detection work as expected?
* **Message format handling** - Any edge cases with legacy message conversion?
---
title: Logging headers and cookies using custom fields · Changelog
description: Log Explorer now supports logging and querying header and cookie fields
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-03-log-headers-and-cookies/
md: https://developers.cloudflare.com/changelog/2025-09-03-log-headers-and-cookies/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Logging headers and cookies using custom fields
Sep 03, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
[Log Explorer](https://developers.cloudflare.com/log-explorer/) now supports logging and filtering on header or cookie fields in the [`http_requests` dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/).
Create a custom field to log desired header or cookie values into the `http_requests` dataset and Log Explorer will import these as searchable fields. Once configured, use the custom SQL editor in Log Explorer to view or filter on these requests.
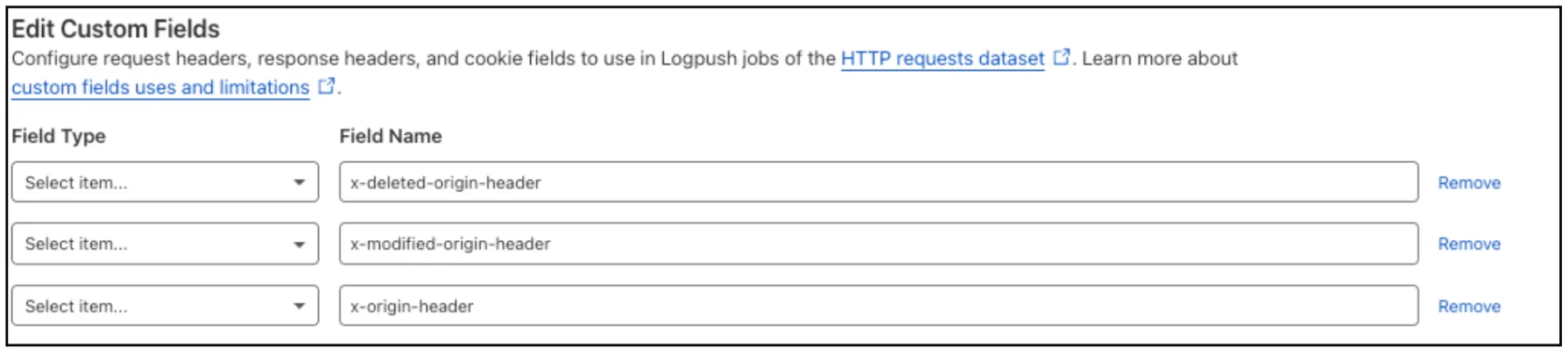
For more details, refer to [Headers and cookies](https://developers.cloudflare.com/log-explorer/log-search/#headers-and-cookies).
---
title: A new, simpler REST API for Cloudflare Workers (Beta) · Changelog
description: Simpler Workers API, SDK methods, and Terraform resources for
directly managing Workers, Versions, and Deployments
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-03-new-workers-api/
md: https://developers.cloudflare.com/changelog/2025-09-03-new-workers-api/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## A new, simpler REST API for Cloudflare Workers (Beta)
Sep 04, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now manage [**Workers**](https://developers.cloudflare.com/api/resources/workers/subresources/beta/subresources/workers/methods/create/), [**Versions**](https://developers.cloudflare.com/api/resources/workers/subresources/beta/subresources/workers/models/worker/#\(schema\)), and [**Deployments**](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/subresources/content/methods/update/) as separate resources with a new, resource-oriented API (Beta).
This new API is supported in the [Cloudflare Terraform provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs) and the [Cloudflare Typescript SDK](https://github.com/cloudflare/cloudflare-typescript), allowing platform teams to manage a Worker's infrastructure in Terraform, while development teams handle code deployments from a separate repository or workflow. We also designed this API with AI agents in mind, as a clear, predictable structure is essential for them to reliably build, test, and deploy applications.
#### Try it out
* [**New beta API endpoints**](https://developers.cloudflare.com/api/resources/workers/subresources/beta/)
* [**Cloudflare TypeScript SDK v5.0.0**](https://github.com/cloudflare/cloudflare-typescript)
* [**Cloudflare Go SDK v6.0.0**](https://github.com/cloudflare/cloudflare-go)
* [**Terraform provider v5.9.0**](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs): [`cloudflare_worker`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker) , [`cloudflare_worker_version`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker_version), and [`cloudflare_workers_deployments`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_deployment) resources.
* See full examples in our [Infrastructure as Code (IaC) guide](https://developers.cloudflare.com/workers/platform/infrastructure-as-code)
#### Before: Eight+ endpoints with mixed responsibilities
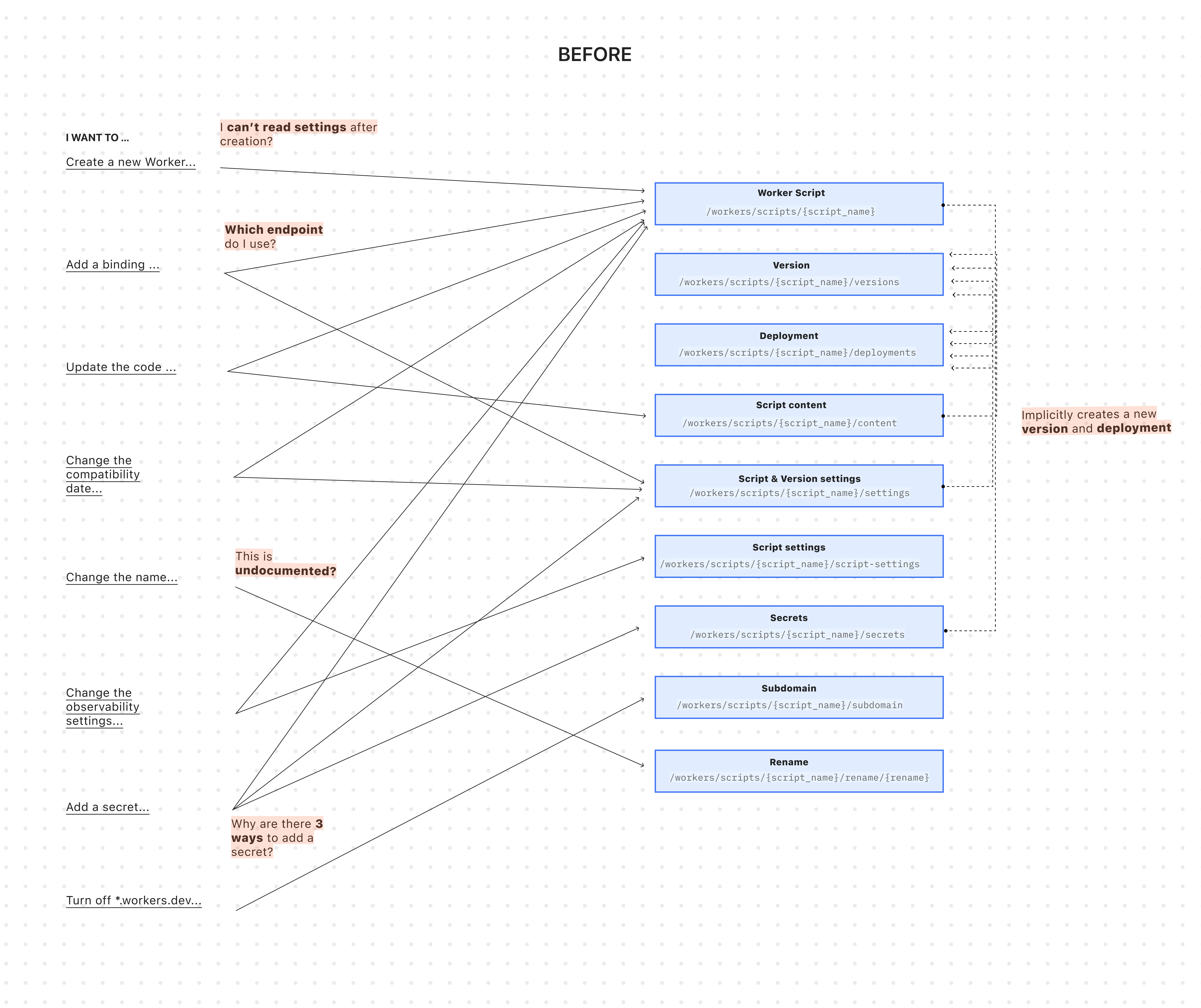
The existing API was originally designed for simple, one-shot script uploads:
```sh
curl -X PUT "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/workers/scripts/$SCRIPT_NAME" \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY" \
-H "Content-Type: multipart/form-data" \
-F 'metadata={
"main_module": "worker.js",
"compatibility_date": "$today$"
}' \
-F "worker.js=@worker.js;type=application/javascript+module"
```
This API worked for creating a basic Worker, uploading all of its code, and deploying it immediately — but came with challenges:
* **A Worker couldn't exist without code**: To create a Worker, you had to upload its code in the same API request. This meant platform teams couldn't provision Workers with the proper settings, and then hand them off to development teams to deploy the actual code.
* **Several endpoints implicitly created deployments**: Simple updates like adding a secret or changing a script's content would implicitly create a new version and immediately deploy it.
* **Updating a setting was confusing**: Configuration was scattered across eight endpoints with overlapping responsibilities. This ambiguity made it difficult for human developers (and even more so for AI agents) to reliably update a Worker via API.
* **Scripts used names as primary identifiers**: This meant simple renames could turn into a risky migration, requiring you to create a brand new Worker and update every reference. If you were using Terraform, this could inadvertently destroy your Worker altogether.
#### After: Three resources with clear boundaries
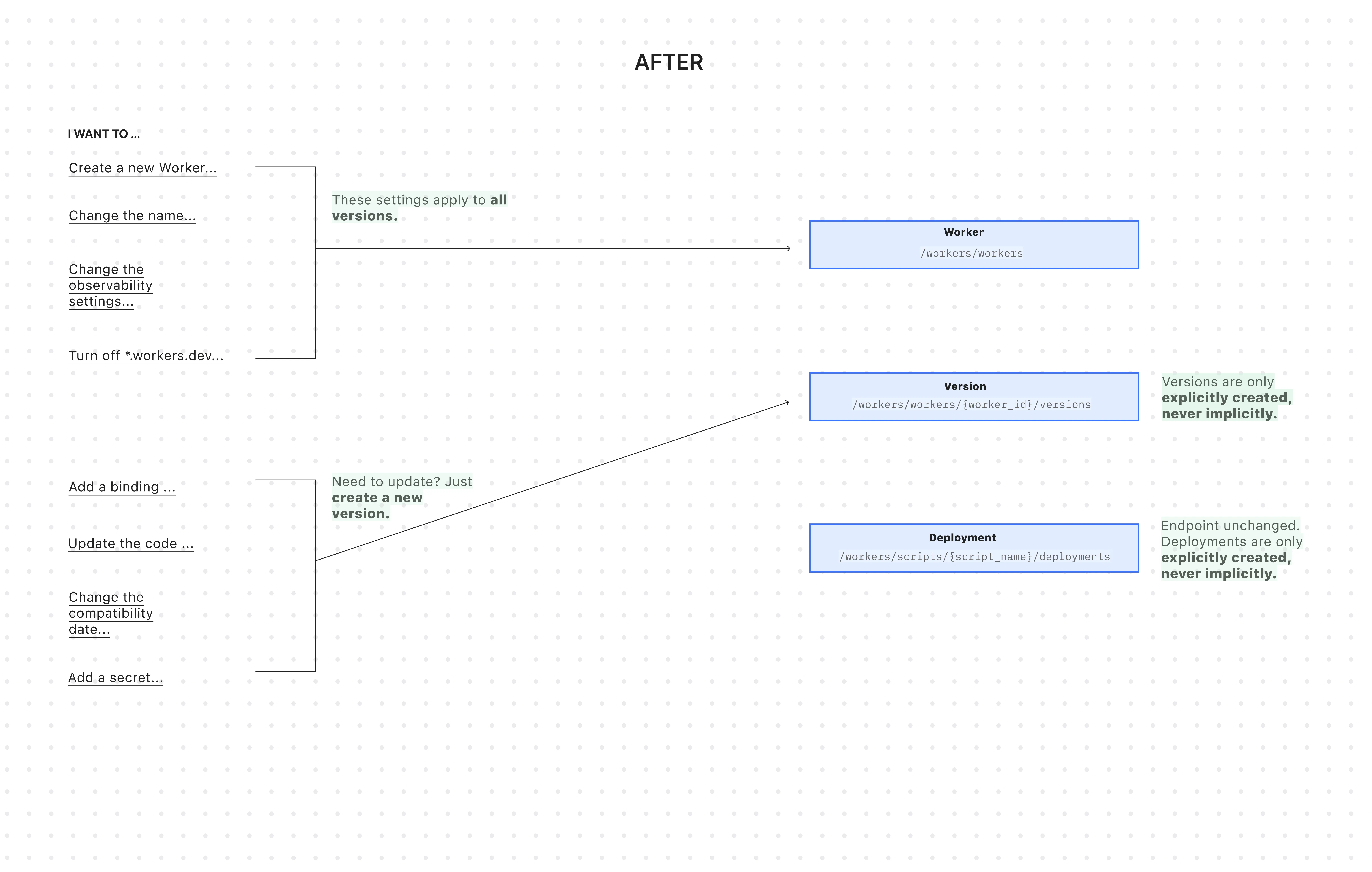
All endpoints now use simple JSON payloads, with script content embedded as `base64`-encoded strings -- a more consistent and reliable approach than the previous `multipart/form-data` format.
* **Worker**: The parent resource representing your application. It has a stable UUID and holds persistent settings like `name`, `tags`, and `logpush`. You can now create a Worker to establish its identity and settings **before** any code is uploaded.
* **Version**: An immutable snapshot of your code and its specific configuration, like bindings and `compatibility_date`. Creating a new version is a safe action that doesn't affect live traffic.
* **Deployment**: An explicit action that directs traffic to a specific version.
Note
[Workers](https://developers.cloudflare.com/api/resources/workers/subresources/beta/subresources/workers/) and [Versions](https://developers.cloudflare.com/api/resources/workers/subresources/beta/subresources/workers/subresources/versions/) use the new `/workers/` beta endpoints, while [Deployments](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/subresources/deployments/) remain on the existing `/scripts/` endpoint. Pair the new endpoints with the existing Deployment API for a complete workflow.
#### Why this matters
#### You can now create Workers before uploading code
Workers are now standalone resources that can be created and configured without any code. Platform teams can provision Workers with the right settings, then hand them off to development teams for implementation.
#### Example: Typescript SDK
```ts
// Step 1: Platform team creates the Worker resource (no code needed)
const worker = await client.workers.beta.workers.create({
name: "payment-service",
account_id: "...",
observability: {
enabled: true,
},
});
// Step 2: Development team adds code and creates a version later
const version = await client.workers.beta.workers.versions.create(worker.id, {
account_id: "...",
main_module: "worker.js",
compatibility_date: "$today",
bindings: [ /*...*/ ],
modules: [
{
name: "worker.js",
content_type: "application/javascript+module",
content_base64: Buffer.from(scriptContent).toString("base64"),
},
],
});
// Step 3: Deploy explicitly when ready
const deployment = await client.workers.scripts.deployments.create(worker.name, {
account_id: "...",
strategy: "percentage",
versions: [
{
percentage: 100,
version_id: version.id,
},
],
});
```
#### Example: Terraform
If you use Terraform, you can now declare the Worker in your Terraform configuration and manage configuration outside of Terraform in your Worker's [`wrangler.jsonc` file](https://developers.cloudflare.com/workers/wrangler/configuration/) and deploy code changes using [Wrangler](https://developers.cloudflare.com/workers/wrangler/).
```tf
resource "cloudflare_worker" "my_worker" {
account_id = "..."
name = "my-important-service"
}
# Manage Versions and Deployments here or outside of Terraform
# resource "cloudflare_worker_version" "my_worker_version" {}
# resource "cloudflare_workers_deployment" "my_worker_deployment" {}
```
#### Deployments are always explicit, never implicit
Creating a version and deploying it are now always explicit, separate actions - never implicit side effects. To update version-specific settings (like bindings), you create a new version with those changes. The existing deployed version remains unchanged until you explicitly deploy the new one.
```sh
# Step 1: Create a new version with updated settings (doesn't affect live traffic)
POST /workers/workers/{id}/versions
{
"compatibility_date": "$today",
"bindings": [
{
"name": "MY_NEW_ENV_VAR",
"text": "new_value",
"type": "plain_text"
}
],
"modules": [...]
}
# Step 2: Explicitly deploy when ready (now affects live traffic)
POST /workers/scripts/{script_name}/deployments
{
"strategy": "percentage",
"versions": [
{
"percentage": 100,
"version_id": "new_version_id"
}
]
}
```
#### Settings are clearly organized by scope
Configuration is now logically divided: [**Worker settings**](https://developers.cloudflare.com/api/resources/workers/subresources/beta/subresources/workers/) (like `name` and `tags`) persist across all versions, while [**Version settings**](https://developers.cloudflare.com/api/resources/workers/subresources/beta/subresources/workers/subresources/versions/) (like `bindings` and `compatibility_date`) are specific to each code snapshot.
```sh
# Worker settings (the parent resource)
PUT /workers/workers/{id}
{
"name": "payment-service",
"tags": ["production"],
"logpush": true,
}
```
```sh
# Version settings (the "code")
POST /workers/workers/{id}/versions
{
"compatibility_date": "$today",
"bindings": [...],
"modules": [...]
}
```
#### `/workers` API endpoints now support UUIDs (in addition to names)
The `/workers/workers/` path now supports addressing a Worker by both its immutable UUID and its mutable name.
```sh
# Both work for the same Worker
GET /workers/workers/29494978e03748669e8effb243cf2515 # UUID (stable for automation)
GET /workers/workers/payment-service # Name (convenient for humans)
```
This dual approach means:
* Developers can use readable names for debugging.
* Automation can rely on stable UUIDs to prevent errors when Workers are renamed.
* Terraform can rename Workers without destroying and recreating them.
#### Learn more
* [Infrastructure as Code (IaC) guide](https://developers.cloudflare.com/workers/platform/infrastructure-as-code)
* [API documentation](https://developers.cloudflare.com/api/resources/workers/subresources/beta/)
* [Versions and Deployments overview](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/)
#### Technical notes
* The pre-existing Workers REST API remains fully supported. Once the new API exits beta, we'll provide a migration timeline with ample notice and comprehensive migration guides.
* Existing Terraform resources and SDK methods will continue to be fully supported through the current major version.
* While the Deployments API currently remains on the `/scripts/` endpoint, we plan to introduce a new Deployments endpoint under `/workers/` to match the new API structure.
---
title: Introducing new headers for rate limiting on Cloudflare's API · Changelog
description: Cloudflare's API handles rate limiting automatically in the SDKs
and how to respond appropriately in your code.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-03-rate-limiting-improvement/
md: https://developers.cloudflare.com/changelog/2025-09-03-rate-limiting-improvement/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing new headers for rate limiting on Cloudflare's API
Sep 03, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Cloudflare's API now supports rate limiting headers using the pattern developed by the [IETF draft on rate limiting](https://ietf-wg-httpapi.github.io/ratelimit-headers/draft-ietf-httpapi-ratelimit-headers.html). This allows API consumers to know how many more calls are left until the rate limit is reached, as well as how long you will need to wait until more capacity is available.
Our SDKs automatically work with these new headers, backing off when rate limits are approached. There is no action required for users of the latest Cloudflare SDKs to take advantage of this.
As always, if you need any help with rate limits, please contact Support.
#### Changes
#### New Headers
**Headers that are always returned:**
* `Ratelimit`: List of service limit items, composed of the limit name, the remaining quota (`r`) and the time next window resets (`t`). For example: `"default";r=50;t=30`
* `Ratelimit-Policy`: List of quota policy items, composed of the policy name, the total quota (`q`) and the time window the quota applies to (`w`). For example: `"burst";q=100;w=60`
**Returned only when a rate limit has been reached (error code: 429):**
* Retry-After: Number of Seconds until more capacity is available, rounded up
#### SDK Back offs
* All of Cloudflare's latest SDKs will automatically respond to the headers, instituting a backoff when limits are approached.
#### GraphQL and Edge APIs
These new headers and back offs are only available for Cloudflare REST APIs, and will not affect GraphQL.
#### For more information
* [Rate limits at Cloudflare](https://developers.cloudflare.com/fundamentals/api/reference/limits/)
---
title: WAF Release - 2025-09-04 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-09-04 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-04-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-04-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-04 - Emergency
Sep 04, 2025
[WAF](https://developers.cloudflare.com/waf/)
**This week's update**
This week, new critical vulnerabilities were disclosed in Sitecore’s Sitecore Experience Manager (XM), Sitecore Experience Platform (XP), specifically versions 9.0 through 9.3, and 10.0 through 10.4. These flaws are caused by unsafe data deserialization and code reflection, leaving affected systems at high risk of exploitation.
**Key Findings**
* CVE-2025-53690: Remote Code Execution through Insecure Deserialization
* CVE-2025-53691: Remote Code Execution through Insecure Deserialization
* CVE-2025-53693: HTML Cache Poisoning through Unsafe Reflections
**Impact**
Exploitation could allow attackers to execute arbitrary code remotely on the affected system and conduct cache poisoning attacks, potentially leading to further compromise. Applying the latest vendor-released solution without delay is strongly recommended.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 588edc74df1f4609b3c2f7ef0ee2c15e | 100878 | Sitecore - Remote Code Execution - CVE:CVE-2025-53691 | N/A | Block | This is a new detection |
| Cloudflare Managed Ruleset | d1bd7563e6254db48ce703807c5b669c | 100631 | Sitecore - Cache Poisoning - CVE:CVE-2025-53693 | N/A | Block | This is a new detection |
| Cloudflare Managed Ruleset | ed94c7ce5301411a94a21a096c410240 | 100879 | Sitecore - Remote Code Execution - CVE:CVE-2025-53690 | N/A | Block | This is a new detection |
---
title: Bidirectional tunnel health checks are compatible with all Magic on-ramps
· Changelog
description: Bidirectional tunnel health check return packets are accepted by
any Magic on-ramp
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-05-bidirectional-health-check-any-on-ramp/
md: https://developers.cloudflare.com/changelog/2025-09-05-bidirectional-health-check-any-on-ramp/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Bidirectional tunnel health checks are compatible with all Magic on-ramps
Sep 05, 2025
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
All bidirectional tunnel health check return packets are accepted by any Magic on-ramp.
Previously, when a Magic tunnel had a bidirectional health check configured, the bidirectional health check would pass when the return packets came back to Cloudflare over the same tunnel that was traversed by the forward packets.
There are SD-WAN devices, like VeloCloud, that do not offer controls to steer traffic over one tunnel versus another in a high availability tunnel configuration.
Now, when a Magic tunnel has a bidirectional health check configured, the bidirectional health check will pass when the return packet traverses over any tunnel in a high availability configuration.
---
title: Introducing EmbeddingGemma from Google on Workers AI · Changelog
description: Partnering with Google to bring to you EmbeddingGemma best-in-class
embedding performance for RAG and semantic search
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-05-embeddinggemma/
md: https://developers.cloudflare.com/changelog/2025-09-05-embeddinggemma/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing EmbeddingGemma from Google on Workers AI
Sep 05, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We're excited to be a launch partner alongside [Google](https://developers.googleblog.com/en/introducing-embeddinggemma/) to bring their newest embedding model, **EmbeddingGemma**, to Workers AI that delivers best-in-class performance for its size, enabling RAG and semantic search use cases.
[`@cf/google/embeddinggemma-300m`](https://developers.cloudflare.com/workers-ai/models/embeddinggemma-300m/) is a 300M parameter embedding model from Google, built from Gemma 3 and the same research used to create Gemini models. This multilingual model supports 100+ languages, making it ideal for RAG systems, semantic search, content classification, and clustering tasks.
**Using EmbeddingGemma in AI Search:** Now you can leverage EmbeddingGemma directly through AI Search for your RAG pipelines. EmbeddingGemma's multilingual capabilities make it perfect for global applications that need to understand and retrieve content across different languages with exceptional accuracy.
To use EmbeddingGemma for your AI Search projects:
1. Go to **Create** in the [AI Search dashboard](https://dash.cloudflare.com/?to=/:account/ai/ai-search)
2. Follow the setup flow for your new RAG instance
3. In the **Generate Index** step, open up **More embedding models** and select `@cf/google/embeddinggemma-300m` as your embedding model
4. Complete the setup to create an AI Search
Try it out and let us know what you think!
---
title: Increased vCPU for Workers Builds on paid plans · Changelog
description: Increased the available vCPU for Workers Builds from 2 to 4 vCPUs
for paid plans, improving build performance and parallel processing
capabilities. - workers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-07-builds-increased-cpu-paid/
md: https://developers.cloudflare.com/changelog/2025-09-07-builds-increased-cpu-paid/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased vCPU for Workers Builds on paid plans
Sep 18, 2025
[Workers](https://developers.cloudflare.com/workers/)
We recently [increased the available disk space](https://developers.cloudflare.com/changelog/2025-08-04-builds-increased-disk-size/) from 8 GB to 20 GB for **all** plans. Building on that improvement, we’re now doubling the CPU power available for paid plans — from 2 vCPU to **4 vCPU**.
These changes continue our focus on making [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/) faster and more reliable.
| Metric | Free Plan | Paid Plans |
| - | - | - |
| CPU | 2 vCPU | **4 vCPU** |
#### Performance Improvements
* **Fast build times**: Even single-threaded workloads benefit from having more vCPUs
* **2x faster multi-threaded builds**: Tools like [esbuild](https://esbuild.github.io/) and [webpack](https://webpack.js.org/) can now utilize additional cores, delivering near-linear performance scaling
All other [build limits](https://developers.cloudflare.com/workers/ci-cd/builds/limits-and-pricing/) — including memory, build minutes, and timeout remain unchanged.
---
title: Custom IKE ID for IPsec Tunnels · Changelog
description: Customers can now set a custom IKE ID for their IPsec Tunnels
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-08-custom-ike-id-ipsec-tunnels/
md: https://developers.cloudflare.com/changelog/2025-09-08-custom-ike-id-ipsec-tunnels/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Custom IKE ID for IPsec Tunnels
Sep 08, 2025
[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Now, Magic WAN customers can configure a custom IKE ID for their IPsec tunnels. Customers that are using Magic WAN and a VeloCloud SD-WAN device together can utilize this new feature to create a high availability configuration.
This feature is available via API only. Customers can read the Magic WAN documentation to learn more about the [Custom IKE ID feature and the API call to configure it](https://developers.cloudflare.com/magic-wan/configuration/common-settings/custom-ike-id-ipsec/).
---
title: Reminders about two-factor authentication backup codes · Changelog
description: Don't get locked out of your account, make sure you've got backup codes
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-08-reminders-about-two-factor-authentication-backup-codes/
md: https://developers.cloudflare.com/changelog/2025-09-08-reminders-about-two-factor-authentication-backup-codes/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Reminders about two-factor authentication backup codes
Sep 08, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Two-factor authentication is the best way to help protect your account from account takeovers, but if you lose your second factor, you could be locked out of your account. Lock outs are one of the top reasons customers contact Cloudflare support, and our policies often don't allow us to bypass two-factor authentication for customers that are locked out. Today we are releasing an improvement where Cloudflare will periodically remind you to securely save your backup codes so you don't get locked out in the future.
#### For more information
* [Two-factor authentication](https://developers.cloudflare.com/fundamentals/user-profiles/2fa/)
---
title: WAF Release - 2025-09-08 · Changelog
description: Cloudflare WAF managed rulesets 2025-09-08 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-08-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-08-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-08
Sep 08, 2025
[WAF](https://developers.cloudflare.com/waf/)
**This week's update**
This week’s focus highlights newly disclosed vulnerabilities in web frameworks, enterprise applications, and widely deployed CMS plugins. The vulnerabilities include SSRF, authentication bypass, arbitrary file upload, and remote code execution (RCE), exposing organizations to high-impact risks such as unauthorized access, system compromise, and potential data exposure. In addition, security rule enhancements have been deployed to cover general command injection and server-side injection attacks, further strengthening protections.
**Key Findings**
* Next.js (CVE-2025-57822): Improper handling of redirects in custom middleware can lead to server-side request forgery (SSRF) when user-supplied headers are forwarded. Attackers could exploit this to access internal services or cloud metadata endpoints. The issue has been resolved in versions 14.2.32 and 15.4.7. Developers using custom middleware should upgrade and verify proper redirect handling in `next()` calls.
* ScriptCase (CVE-2025-47227, CVE-2025-47228): In the Production Environment extension in Netmake ScriptCase through 9.12.006 (23), two vulnerabilities allow attackers to reset admin accounts and execute system commands, potentially leading to full compromise of affected deployments.
* Sar2HTML (CVE-2025-34030): In Sar2HTML version 3.2.2 and earlier, insufficient input sanitization of the plot parameter allows remote, unauthenticated attackers to execute arbitrary system commands. Exploitation could compromise the underlying server and its data.
* Zhiyuan OA (CVE-2025-34040): An arbitrary file upload vulnerability exists in the Zhiyuan OA platform. Improper validation in the `wpsAssistServlet` interface allows unauthenticated attackers to upload crafted files via path traversal, which can be executed on the web server, leading to remote code execution.
* WordPress:Plugin:InfiniteWP Client (CVE-2020-8772): A vulnerability in the InfiniteWP Client plugin allows attackers to perform restricted actions and gain administrative control of connected WordPress sites.
**Impact**
These vulnerabilities could allow attackers to gain unauthorized access, execute malicious code, or take full control of affected systems. The Next.js SSRF flaw may expose internal services or cloud metadata endpoints to attackers. Exploitations of ScriptCase and Sar2HTML could result in remote code execution, administrative takeover, and full server compromise. In Zhiyuan OA, the arbitrary file upload vulnerability allows attackers to execute malicious code on the web server, potentially exposing sensitive data and applications. The authentication bypass in WordPress InfiniteWP Client enables attackers to gain administrative access, risking data exposure and unauthorized control of connected sites.
Administrators are strongly advised to apply vendor patches immediately, remove unsupported software, and review authentication and access controls to mitigate these risks.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 7c5812a31fd94996b3299f7e963d7afc | 100007D | Command Injection - Common Attack Commands Args | Log | Block | This rule has been merged into the original rule "Command Injection - Common Attack Commands" (ID: 89557ce9b26e4d4dbf29e90c28345b9b ) for New WAF customers only. |
| Cloudflare Managed Ruleset | cd528243d6824f7ab56182988230a75b | 100617 | Next.js - SSRF - CVE:CVE-2025-57822 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 503b337dac5c409d8f833a6ba22dabf1 | 100659\_BETA | Common Payloads for Server-Side Template Injection - Beta | Log | Block | This rule is merged into the original rule "Common Payloads for Server-Side Template Injection" (ID: 21c7a963e1b749e7b1753238a28a42c4 ) |
| Cloudflare Managed Ruleset | 6d24266148f24f5e9fa487f8b416b7ca | 100824B | CrushFTP - Remote Code Execution - CVE:CVE-2025-54309 - 3 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 154b217c43d04f11a13aeff05db1fa6b | 100848 | ScriptCase - Auth Bypass - CVE:CVE-2025-47227 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | cad6f1c8c6d44ef59929e6532c62d330 | 100849 | ScriptCase - Command Injection - CVE:CVE-2025-47228 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | e7464139fd3e44938b56716bef971afd | 100872 | WordPress:Plugin:InfiniteWP Client - Missing Authorization - CVE:CVE-2020-8772 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 0181ebb2cc234f2d863412e1bab19b0b | 100873 | Sar2HTML - Command Injection - CVE:CVE-2025-34030 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 34d5c7c7b08b40eaad5b2bb3f24c0fbe | 100875 | Zhiyuan OA - Remote Code Execution - CVE:CVE-2025-34040 | Log | Block | This is a New Detection |
---
title: Deploy static sites to Workers without a configuration file · Changelog
description: Wrangler now guides you through deploying static assets with
interactive prompts and automatic configuration generation when no
wrangler.jsonc file exists.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-09-interactive-wrangler-assets/
md: https://developers.cloudflare.com/changelog/2025-09-09-interactive-wrangler-assets/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Deploy static sites to Workers without a configuration file
Sep 09, 2025
[Workers](https://developers.cloudflare.com/workers/)
Deploying static site to Workers is now easier. When you run `wrangler deploy [directory]` or `wrangler deploy --assets [directory]` without an existing [configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/), [Wrangler CLI](https://developers.cloudflare.com/workers/wrangler/) now guides you through the deployment process with interactive prompts.
#### Before and after
**Before:** Required remembering multiple flags and parameters
```bash
wrangler deploy --assets ./dist --compatibility-date 2025-09-09 --name my-project
```
**After:** Simple directory deployment with guided setup
```bash
wrangler deploy dist
# Interactive prompts handle the rest as shown in the example flow below
```
#### What's new
**Interactive prompts for missing configuration:**
* Wrangler detects when you're trying to deploy a directory of static assets
* Prompts you to confirm the deployment type
* Asks for a project name (with smart defaults)
* Automatically sets the compatibility date to today
**Automatic configuration generation:**
* Creates a `wrangler.jsonc` file with your deployment settings
* Stores your choices for future deployments
* Eliminates the need to remember complex command-line flags
#### Example workflow
```bash
# Deploy your built static site
wrangler deploy dist
# Wrangler will prompt:
✔ It looks like you are trying to deploy a directory of static assets only. Is this correct? … yes
✔ What do you want to name your project? … my-astro-site
# Automatically generates a wrangler.jsonc file and adds it to your project:
{
"name": "my-astro-site",
"compatibility_date": "2025-09-09",
"assets": {
"directory": "dist"
}
}
# Next time you run wrangler deploy, this will use the configuration in your newly generated wrangler.jsonc file
wrangler deploy
```
#### Requirements
* You must use Wrangler version 4.24.4 or later in order to use this feature
---
title: Built with Cloudflare button · Changelog
description: Our new "Built with Cloudflare" button can be used to share your
stack of choice with the world.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-10-built-with-cloudflare-button/
md: https://developers.cloudflare.com/changelog/2025-09-10-built-with-cloudflare-button/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Built with Cloudflare button
Sep 10, 2025
[Workers](https://developers.cloudflare.com/workers/)
We've updated our "Built with Cloudflare" button to make it easier to share that you're building on Cloudflare with the world. Embed it in your project's README, blog post, or wherever you want to let people know.

Check out the [documentation](https://developers.cloudflare.com/workers/platform/built-with-cloudflare) for usage information.
---
title: WARP client for macOS (version 2025.7.106.1) · Changelog
description: WARP client for macOS (version 2025.7.106.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-10-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-09-10-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.7.106.1)
Sep 10, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements including enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
**Changes and improvements**
* Enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
* Fixed a bug preventing the `warp-diag captive-portal` command from running successfully due to the client not parsing SSID on macOS.
* Improvements to maintain Global WARP Override settings when switching between organization configurations.
* The [MASQUE protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) is now the default protocol for all new WARP device profiles.
* Improvement to limit idle connections in DoH mode to avoid unnecessary resource usage that can lead to DoH requests not resolving.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.7.106.1) · Changelog
description: WARP client for Windows (version 2025.7.106.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-10-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-09-10-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.7.106.1)
Sep 10, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements including enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
**Changes and improvements**
* Enhancements to [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) for even faster resolution. The MASQUE protocol is now the only protocol that can use Proxy mode. If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) or all devices matching the profile will lose connectivity.
* Improvement to keep TCP connections up the first time WARP connects on devices so that remote desktop sessions (such as RDP or SSH) continue to work.
* Improvements to maintain Global WARP Override settings when switching between organization configurations.
* The [MASQUE protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) is now the default protocol for all new WARP device profiles.
* Improvement to limit idle connections in DoH mode to avoid unnecessary resource usage that can lead to DoH requests not resolving.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about Win32/ClickFix.ABA being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Contextual pivots · Changelog
description: Log Search now lets you pivot directly to related Cloudflare tools
and documentation for faster investigations and actions.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-11-contextual-pivots/
md: https://developers.cloudflare.com/changelog/2025-09-11-contextual-pivots/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Contextual pivots
Sep 11, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
Directly from [Log Search](https://developers.cloudflare.com/log-explorer/log-search/) results, customers can pivot to other parts of the Cloudflare dashboard to immediately take action as a result of their investigation.
From the `http_requests` or `fw_events` dataset results, right click on an IP Address or JA3 Fingerprint to pivot to the Investigate portal to lookup the reputation of an IP address or JA3 fingerprint.

Easily learn about error codes by linking directly to our documentation from the **EdgeResponseStatus** or **OriginResponseStatus** fields.
From the `gateway_http` dataset, click on a **policyid** to link directly to the Zero Trust dashboard to review or make changes to a specific Gateway policy.

---
title: D1 automatically retries read-only queries · Changelog
description: D1 now detects read-only queries and automatically attempts up to
two retries to execute those queries in the event of failures with retryable
errors.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-11-d1-automatic-read-retries/
md: https://developers.cloudflare.com/changelog/2025-09-11-d1-automatic-read-retries/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## D1 automatically retries read-only queries
Sep 11, 2025
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
D1 now detects read-only queries and automatically attempts up to two retries to execute those queries in the event of failures with retryable errors. You can access the number of execution attempts in the returned [response metadata](https://developers.cloudflare.com/d1/worker-api/return-object/#d1result) property `total_attempts`.
At the moment, only read-only queries are retried, that is, queries containing only the following SQLite keywords: `SELECT`, `EXPLAIN`, `WITH`. Queries containing any [SQLite keyword](https://sqlite.org/lang_keywords.html) that leads to database writes are not retried.
The retry success ratio among read-only retryable errors varies from 5% all the way up to 95%, depending on the underlying error and its duration (like network errors or other internal errors).
The retry success ratio among all retryable errors is lower, indicating that there are write-queries that could be retried. Therefore, we recommend D1 users to continue applying [retries in their own code](https://developers.cloudflare.com/d1/best-practices/retry-queries/) for queries that are not read-only but are idempotent according to the business logic of the application.

D1 ensures that any retry attempt does not cause database writes, making the automatic retries safe from side-effects, even if a query causing changes slips through the read-only detection. D1 achieves this by checking for modifications after every query execution, and if any write occurred due to a retry attempt, the query is rolled back.
The read-only query detection heuristics are simple for now, and there is room for improvement to capture more cases of queries that can be retried, so this is just the beginning.
---
title: DNS filtering for private network onramps · Changelog
description: Magic WAN and WARP Connector traffic can now privately route DNS
queries to the Gateway resolver without public Internet exposure.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-11-dns-filtering-for-private-network-onramps/
md: https://developers.cloudflare.com/changelog/2025-09-11-dns-filtering-for-private-network-onramps/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## DNS filtering for private network onramps
Sep 11, 2025
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
[Magic WAN](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-gateway/#dns-filtering) and [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/site-to-internet/#configure-dns-resolver-on-devices) users can now securely route their DNS traffic to the Gateway resolver without exposing traffic to the public Internet.
Routing DNS traffic to the Gateway resolver allows DNS resolution and filtering for traffic coming from private networks while preserving source internal IP visibility. This ensures Magic WAN users have full integration with our Cloudflare One features, including [Internal DNS](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/#internal-dns) and [hostname-based policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/#selector-prerequisites).
To configure DNS filtering, change your Magic WAN or WARP Connector DNS settings to use Cloudflare's shared resolver IPs, `172.64.36.1` and `172.64.36.2`. Once you configure DNS resolution and filtering, you can use *Source Internal IP* as a traffic selector in your [resolver policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/) for routing private DNS traffic to your [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/).
---
title: Worker version rollback limit increased from 10 to 100 · Changelog
description: Workers can now be deployed and rolled back to their most recent
100 versions, up from the previous limit of 10.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-11-increased-version-rollback-limit/
md: https://developers.cloudflare.com/changelog/2025-09-11-increased-version-rollback-limit/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Worker version rollback limit increased from 10 to 100
Sep 11, 2025
[Workers](https://developers.cloudflare.com/workers/)
The number of recent versions available for a Worker rollback has been increased from 10 to 100.
This allows you to:
* Promote any of the 100 most recent versions to be the active deployment.
* Split traffic using [gradual deployments](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/gradual-deployments/) between your latest code and any of the 100 most recent versions.
You can do this through the Cloudflare dashboard or with [Wrangler's rollback command](https://developers.cloudflare.com/workers/wrangler/commands/#rollback)
Learn more about [versioned deployments](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/) and [rollbacks](https://developers.cloudflare.com/workers/configuration/versions-and-deployments/rollbacks/).
---
title: New results table view · Changelog
description: The Log Search results table now features a more streamlined and
customizable experience.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-11-new-results-table-view/
md: https://developers.cloudflare.com/changelog/2025-09-11-new-results-table-view/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New results table view
Sep 11, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
The results table view of **Log Search** has been updated with additional functionality and a more streamlined user experience. Users can now easily:
* Remove/add columns.
* Resize columns.
* Sort columns.
* Copy values from any field.
---
title: Regional Email Processing for Germany, India, or Australia · Changelog
description: Customers can now choose their preferred mail processing location
to be Germany, India, or Australia during onboarding
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-11-regional-email-processing-gia/
md: https://developers.cloudflare.com/changelog/2025-09-11-regional-email-processing-gia/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Regional Email Processing for Germany, India, or Australia
Sep 11, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
We’re excited to announce that Email security customers can now choose their preferred mail processing location directly from the UI when onboarding a domain. This feature is available for the following onboarding methods: **MX**, **BCC**, and **Journaling**.
#### What’s new
Customers can now select where their email is processed. The following regions are supported:
* **Germany**
* **India**
* **Australia**
Global processing remains the default option, providing flexibility to meet both compliance requirements or operational preferences.
#### How to use it
When onboarding a domain with MX, BCC, or Journaling:
1. Select the desired processing location (Germany, India, or Australia).
2. The UI will display updated processing addresses specific to that region.
3. For MX onboarding, if your domain is managed by Cloudflare, you can automatically update MX records directly from the UI.
#### Availability
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
#### What’s next
We’re expanding the list of processing locations to match our [Data Localization Suite (DLS)](https://developers.cloudflare.com/data-localization/) footprint, giving customers the broadest set of regional options in the market without the complexity of self-hosting.
---
title: WAF Release - 2025-09-15 · Changelog
description: Cloudflare WAF managed rulesets 2025-09-15 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-15-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-15-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-15
Sep 15, 2025
[WAF](https://developers.cloudflare.com/waf/)
**This week's update**
This week's focus highlights newly disclosed vulnerabilities in DevOps tooling, data visualization platforms, and enterprise CMS solutions. These issues include sensitive information disclosure and remote code execution, putting organizations at risk of credential leakage, unauthorized access, and full system compromise.
**Key Findings**
* Argo CD (CVE-2025-55190): Exposure of sensitive information could allow attackers to access credential data stored in configurations, potentially leading to compromise of Kubernetes workloads and secrets.
* DataEase (CVE-2025-57773): Insufficient input validation enables JNDI injection and insecure deserialization, resulting in remote code execution (RCE). Successful exploitation grants attackers control over the application server.
* Sitecore (CVE-2025-53694): A sensitive information disclosure flaw allows unauthorized access to confidential information stored in Sitecore deployments, raising the risk of data breaches and privilege escalation.
**Impact**
These vulnerabilities expose organizations to serious risks, including credential theft, unauthorized access, and full system compromise. Argo CD's flaw may expose Kubernetes secrets, DataEase exploitation could give attackers remote execution capabilities, and Sitecore's disclosure issue increases the likelihood of sensitive data leakage and business impact.
Administrators are strongly advised to apply vendor patches immediately, rotate exposed credentials, and review access controls to mitigate these risks.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 199cce9ab21e40bcb535f01b2ee2085f | 100646 | Argo CD - Information Disclosure - CVE:CVE-2025-55190s | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | e513bb21b6a44f9cbfcd2462f5e20788 | 100874 | DataEase - JNDI injection - CVE:CVE-2025-57773 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | be097f5a71a04f27aa87b60d005a12fd | 100880 | Sitecore - Information Disclosure - CVE:CVE-2025-53694 | Log | Block | This is a New Detection |
---
title: DNS Firewall Analytics — now in the Cloudflare dashboard · Changelog
description: Quickly set up common rules with pre-built templates.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-16-dnsfw-analytics-ui/
md: https://developers.cloudflare.com/changelog/2025-09-16-dnsfw-analytics-ui/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## DNS Firewall Analytics — now in the Cloudflare dashboard
Sep 16, 2025
[DNS](https://developers.cloudflare.com/dns/)
#### What's New
Access [GraphQL-powered DNS Firewall analytics](https://developers.cloudflare.com/dns/dns-firewall/analytics/) directly in the Cloudflare dashboard.

#### Explore Four Interactive Panels
* **Query summary**: Describes trends over time, segmented by dimensions.
* **Query statistics**: Describes totals, cached/uncached queries, and processing/response times.
* **DNS queries by data center**: Describes global view and the top 10 data centers.
* **Top query statistics**: Shows a breakdown by key dimensions, with search and expand options (up to top 100 items).
Additional features:
* Apply filters and time ranges once. Changes reflect across all panels.
* Filter by dimensions like query name, query type, cluster, data center, protocol (UDP/TCP), IP version, response code/reason, and more.
* Access up to 62 days of historical data with flexible intervals.
#### Availability
Available to all DNS Firewall customers as part of their existing subscription.
#### Where to Find It
* In the Cloudflare dashboard, go to the **DNS Firewall** page.
[Go to **Analytics**](https://dash.cloudflare.com/?to=/:account/dns-firewall/analytics)
* Refer to the [DNS Firewall Analytics](https://developers.cloudflare.com/dns/dns-firewall/analytics/) to learn more.
---
title: New AI-Enabled Search for Zero Trust Dashboard · Changelog
description: New AI-Enabled Search for Zero Trust Dashboard
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-16-new-ai-enabled-search-for-zero-trust-dashboard/
md: https://developers.cloudflare.com/changelog/2025-09-16-new-ai-enabled-search-for-zero-trust-dashboard/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New AI-Enabled Search for Zero Trust Dashboard
Sep 16, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust Dashboard has a brand new, AI-powered search functionality. You can search your account by resources (applications, policies, device profiles, settings, etc.), pages, products, and more.

**Ask Cloudy** — You can also ask Cloudy, our AI agent, questions about Cloudflare Zero Trust. Cloudy is trained on our developer documentation and implementation guides, so it can tell you how to configure functionality, best practices, and can make recommendations.
Cloudy can then stay open with you as you move between pages to build configuration or answer more questions.
**Find Recents** — Recent searches and Cloudy questions also have a new tab under Zero Trust Overview.
---
title: Remote bindings GA - Connect to remote resources (D1, KV, R2, etc.)
during local development · Changelog
description: You can now connect to R2 buckets, D1 databases, and other
resources running on Cloudflare, while running your Worker's code locally, on
your own machine.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-16-remote-bindings-ga/
md: https://developers.cloudflare.com/changelog/2025-09-16-remote-bindings-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Remote bindings GA - Connect to remote resources (D1, KV, R2, etc.) during local development
Sep 16, 2025
[Workers](https://developers.cloudflare.com/workers/)
Three months ago [we announced the public beta](https://developers.cloudflare.com/changelog/2025-06-18-remote-bindings-beta/) of [remote bindings](https://developers.cloudflare.com/workers/development-testing/#remote-bindings) for local development. Now, we're excited to say that it's available for everyone in Wrangler, Vite, and Vitest without using an experimental flag!
With remote bindings, you can now connect to deployed resources like [R2 buckets](https://developers.cloudflare.com/r2/) and [D1 databases](https://developers.cloudflare.com/d1/) while running Worker code on your local machine. This means you can test your local code changes against real data and services, without the overhead of deploying for each iteration.
#### Example configuration
To enable remote bindings, add `"remote" : true` to each binding that you want to rely on a remote resource running on Cloudflare:
* wrangler.jsonc
```jsonc
{
"name": "my-worker",
"compatibility_date": "2026-02-07",
"r2_buckets": [
{
"bucket_name": "screenshots-bucket",
"binding": "screenshots_bucket",
"remote": true,
},
],
}
```
* wrangler.toml
```toml
name = "my-worker"
compatibility_date = "2026-02-07"
[[r2_buckets]]
bucket_name = "screenshots-bucket"
binding = "screenshots_bucket"
remote = true
```
When remote bindings are configured, your Worker **still executes locally**, but all binding calls are proxied to the deployed resource that runs on Cloudflare's network.
**You can [try out remote bindings](https://developers.cloudflare.com/workers/development-testing/#remote-bindings) for local development today with:**
* [Wrangler v4.37.0](https://developers.cloudflare.com/workers/wrangler/)
* The [Cloudflare Vite Plugin](https://developers.cloudflare.com/workers/vite-plugin/)
* The [Cloudflare Vitest Plugin](https://developers.cloudflare.com/workers/testing/vitest-integration/)
---
title: Preview URLs now default to opt-in · Changelog
description: We performed a one-time update to disable preview URLs on Workers
with workers.dev disabled to require an explicit opt-in.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-17-update-preview-url-setting/
md: https://developers.cloudflare.com/changelog/2025-09-17-update-preview-url-setting/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Preview URLs now default to opt-in
Sep 17, 2025
[Workers](https://developers.cloudflare.com/workers/)
To prevent the accidental exposure of applications, we've updated how [Worker preview URLs](https://developers.cloudflare.com/workers/configuration/previews/) (`-..workers.dev`) are handled. We made this change to ensure preview URLs are only active when intentionally configured, improving the default security posture of your Workers.
#### One-Time Update for Workers with workers.dev Disabled
We performed a one-time update to disable preview URLs for existing Workers where the [workers.dev subdomain](https://developers.cloudflare.com/workers/configuration/routing/workers-dev/) was also disabled.
Because preview URLs were historically enabled by default, users who had intentionally disabled their workers.dev route may not have realized their Worker was still accessible at a separate preview URL. This update was performed to ensure that using a preview URL is always an intentional, opt-in choice.
If your Worker was affected, its preview URL (`-..workers.dev`) will now direct to an informational page explaining this change.
**How to Re-enable Your Preview URL**
If your preview URL was disabled, you can re-enable it [via the Cloudflare dashboard](https://developers.cloudflare.com/workers/configuration/previews/#toggle-preview-urls-enable-or-disable) by navigating to your Worker's Settings page and toggling on the Preview URL.
Alternatively, you can use Wrangler by adding the `preview_urls = true` setting to your Wrangler file and redeploying the Worker.
* wrangler.jsonc
```jsonc
{
"preview_urls": true
}
```
* wrangler.toml
```toml
preview_urls = true
```
**Note:** You can set `preview_urls = true` with any Wrangler version that supports the preview URL flag (v3.91.0+). However, we recommend updating to v4.34.0 or newer, as this version defaults `preview_urls` to false, ensuring preview URLs are always enabled by explicit choice.
---
title: Connect and secure any private or public app by hostname, not IP — with
hostname routing for Cloudflare Tunnel · Changelog
description: Create Tunnel routes based on hostnames or domains — not just IPs —
to simplify Zero Trust and egress policies.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-18-tunnel-hostname-routing/
md: https://developers.cloudflare.com/changelog/2025-09-18-tunnel-hostname-routing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Connect and secure any private or public app by hostname, not IP — with hostname routing for Cloudflare Tunnel
Sep 18, 2025
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
You can now route private traffic to [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) based on a hostname or domain, moving beyond the limitations of IP-based routing. This new capability is **free for all Cloudflare One customers**.
Previously, Tunnel routes could only be defined by IP address or [CIDR range](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/connect-cidr/). This created a challenge for modern applications with dynamic or ephemeral IP addresses, often forcing administrators to maintain complex and brittle IP lists.

**What’s new:**
* **Hostname & Domain Routing**: Create routes for individual hostnames (e.g., `payroll.acme.local`) or entire domains (e.g., `*.acme.local`) and direct their traffic to a specific Tunnel.
* **Simplified Zero Trust Policies**: Build resilient policies in Cloudflare Access and Gateway using stable hostnames, making it dramatically easier to apply per-resource authorization for your private applications.
* **Precise Egress Control**: Route traffic for public hostnames (e.g., `bank.example.com`) through a specific Tunnel to enforce a dedicated source IP, solving the IP allowlist problem for third-party services.
* **No More IP Lists**: This feature makes the workaround of maintaining dynamic IP Lists for Tunnel connections obsolete.
Get started in the Tunnels section of the Zero Trust dashboard with your first [private hostname](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/connect-private-hostname/) or [public hostname](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/egress-cloudflared/) route.
Learn more in our [blog post](https://blog.cloudflare.com/tunnel-hostname-routing/).
---
title: New Metrics View in AutoRAG · Changelog
description: Track file indexing, search activity, and top retrievals to
understand how your AutoRAG instance is being used.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-19-autorag-metrics/
md: https://developers.cloudflare.com/changelog/2025-09-19-autorag-metrics/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Metrics View in AutoRAG
Sep 19, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
[AutoRAG](https://developers.cloudflare.com/ai-search/) now includes a **Metrics** tab that shows how your data is indexed and searched. Get a clear view of the health of your indexing pipeline, compare usage between `ai-search` and `search`, and see which files are retrieved most often.
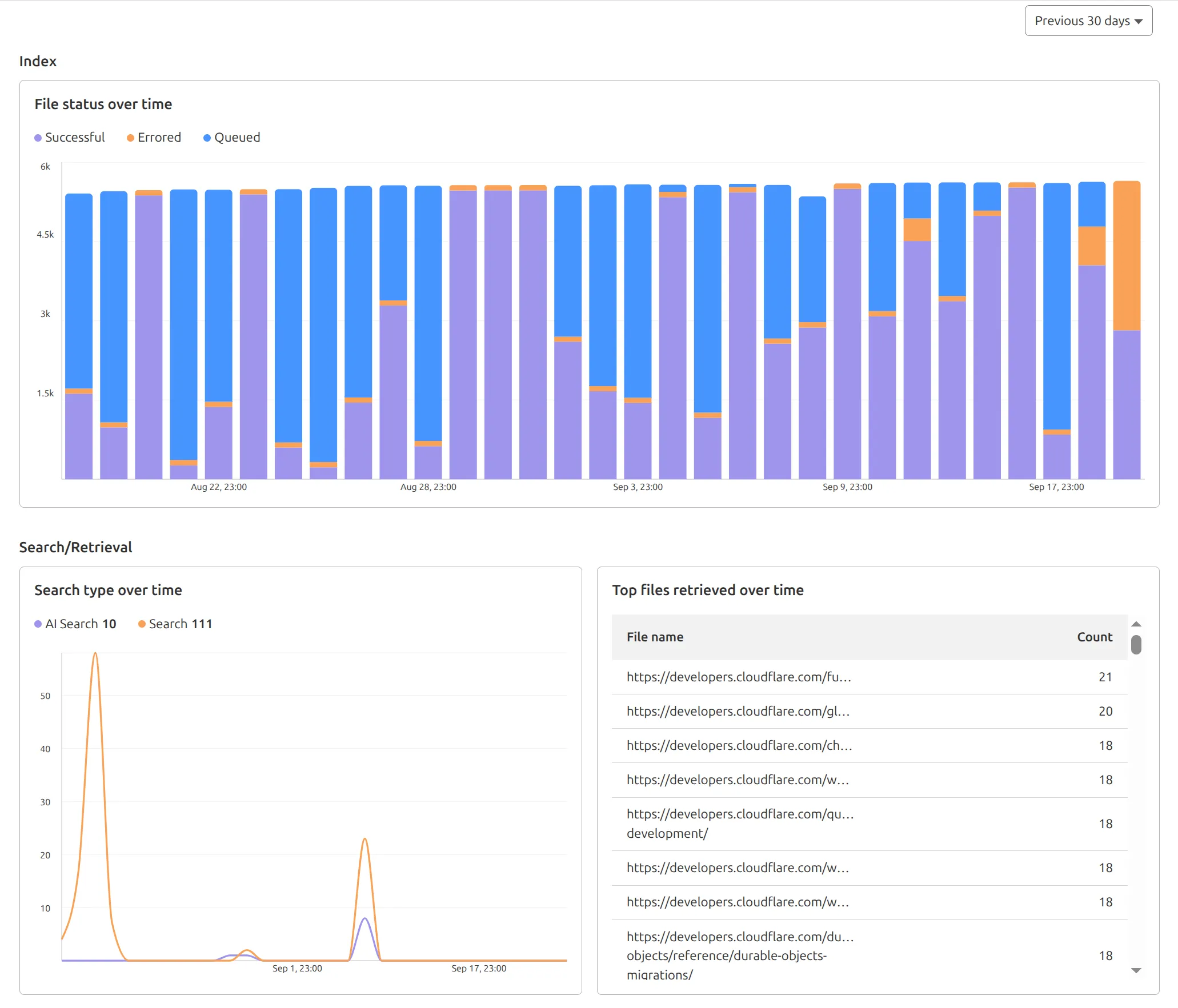
You can find these metrics within each AutoRAG instance:
* Indexing: Track how files are ingested and see status changes over time.
* Search breakdown: Compare usage between `ai-search` and `search` endpoints.
* Top file retrievals: Identify which files are most frequently retrieved in a given period.
Try it today in [AutoRAG](https://developers.cloudflare.com/ai-search/get-started/).
---
title: Rate Limiting in Workers is now GA · Changelog
description: Workers Rate Limiting is now Generally Available
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-19-ratelimit-workers-ga/
md: https://developers.cloudflare.com/changelog/2025-09-19-ratelimit-workers-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Rate Limiting in Workers is now GA
Sep 19, 2025
[Workers](https://developers.cloudflare.com/workers/)
[Rate Limiting within Cloudflare Workers](https://developers.cloudflare.com/workers/runtime-apis/bindings/rate-limit/) is now Generally Available (GA).
The `ratelimit` binding is now stable and recommended for all production workloads. Existing deployments using the unsafe binding will continue to function to allow for a smooth transition.
For more details, refer to [Workers Rate Limiting](https://developers.cloudflare.com/workers/runtime-apis/bindings/rate-limit/) documentation.
---
title: Panic Recovery for Rust Workers · Changelog
description: Deployments on workers-rs are now more reliable with automatic panic recovery
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-19-workers-rs-panic-recovery/
md: https://developers.cloudflare.com/changelog/2025-09-19-workers-rs-panic-recovery/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Panic Recovery for Rust Workers
Sep 19, 2025
[Workers](https://developers.cloudflare.com/workers/)
In [workers-rs](https://github.com/cloudflare/workers-rs), Rust panics were previously non-recoverable. A panic would put the Worker into an invalid state, and further function calls could result in memory overflows or exceptions.
Now, when a panic occurs, in-flight requests will throw 500 errors, but the Worker will automatically and instantly recover for future requests.
This ensures more reliable deployments. Automatic panic recovery is enabled for all new workers-rs deployments as of version 0.6.5, with no configuration required.
#### Fixing Rust Panics with Wasm Bindgen
Rust Workers are built with Wasm Bindgen, which treats panics as non-recoverable. After a panic, the entire Wasm application is considered to be in an invalid state.
We now attach a default panic handler in Rust:
```rust
std::panic::set_hook(Box::new(move |panic_info| {
hook_impl(panic_info);
}));
```
Which is registered by default in the JS initialization:
```js
import { setPanicHook } from "./index.js";
setPanicHook(function (err) {
console.error("Panic handler!", err);
});
```
When a panic occurs, we reset the Wasm state to revert the Wasm application to how it was when the application started.
#### Resetting VM State in Wasm Bindgen
We worked upstream on the Wasm Bindgen project to implement a new [`--experimental-reset-state-function` compilation option](https://github.com/wasm-bindgen/wasm-bindgen/pull/4644) which outputs a new `__wbg_reset_state` function.
This function clears all internal state related to the Wasm VM, and updates all function bindings in place to reference the new WebAssembly instance.
One other necessary change here was associating Wasm-created JS objects with an instance identity. If a JS object created by an earlier instance is then passed into a new instance later on, a new "stale object" error is specially thrown when using this feature.
#### Layered Solution
Building on this new Wasm Bindgen feature, layered with our new default panic handler, we also added a proxy wrapper to ensure all top-level exported class instantiations (such as for Rust Durable Objects) are tracked and fully reinitialized when resetting the Wasm instance. This was necessary because the workerd runtime will instantiate exported classes, which would then be associated with the Wasm instance.
This approach now provides full panic recovery for Rust Workers on subsequent requests.
Of course, we never want panics, but when they do happen they are isolated and can be investigated further from the error logs - avoiding broader service disruption.
#### WebAssembly Exception Handling
In the future, full support for recoverable panics could be implemented without needing reinitialization at all, utilizing the [WebAssembly Exception Handling](https://github.com/WebAssembly/exception-handling/blob/main/proposals/exception-handling/Exceptions.md) proposal, part of the newly announced [WebAssembly 3.0](https://webassembly.org/news/2025-09-17-wasm-3.0/) specification. This would allow unwinding panics as normal JS errors, and concurrent requests would no longer fail.
**We're making significant improvements to the reliability of [Rust Workers](https://github.com/cloudflare/workers-rs). Join us in `#rust-on-workers` on the [Cloudflare Developers Discord](https://discord.gg/cloudflaredev) to stay updated.**
---
title: Access Remote Desktop Protocol (RDP) destinations securely from your
browser — now generally available! · Changelog
description: Connect to internal Windows servers via a web browser — no VPN or
RDP client required.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-22-browser-based-rdp-ga/
md: https://developers.cloudflare.com/changelog/2025-09-22-browser-based-rdp-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Access Remote Desktop Protocol (RDP) destinations securely from your browser — now generally available!
Sep 22, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Browser-based RDP](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/) with [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) is now generally available for all Cloudflare customers. It enables secure, remote Windows server access without VPNs or RDP clients.
Since we announced our [open beta](https://developers.cloudflare.com/changelog/access/#2025-06-30), we've made a few improvements:
* Support for targets with IPv6.
* Support for [Magic WAN](https://developers.cloudflare.com/magic-wan/) and [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) as on-ramps.
* More robust error messaging on the login page to help you if you encounter an issue.
* Worldwide keyboard support. Whether your day-to-day is in Portuguese, Chinese, or something in between, your browser-based RDP experience will look and feel exactly like you are using a desktop RDP client.
* Cleaned up some other miscellaneous issues, including but not limited to enhanced support for Entra ID accounts and support for usernames with spaces, quotes, and special characters.
As a refresher, here are some benefits browser-based RDP provides:
* **Control how users authenticate to internal RDP resources** with single sign-on (SSO), multi-factor authentication (MFA), and granular access policies.
* **Record who is accessing which servers and when** to support regulatory compliance requirements and to gain greater visibility in the event of a security event.
* **Eliminate the need to install and manage software on user devices**. You will only need a web browser.
* **Reduce your attack surface** by keeping your RDP servers off the public Internet and protecting them from common threats like credential stuffing or brute-force attacks.

To get started, refer to [Connect to RDP in a browser](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/rdp-browser/).
---
title: WAF Release - 2025-09-22 · Changelog
description: Cloudflare WAF managed rulesets 2025-09-22 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-22-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-22-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-22
Sep 22, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week emphasizes two critical vendor-specific vulnerabilities: a full elevation-of-privilege in Microsoft Azure Networking (CVE-2025-54914) and a server-side template injection (SSTI) leading to remote code execution (RCE) in Skyvern (CVE-2025-49619). These are complemented by enhancements in generic detections (SQLi, SSRF) to improve baseline coverage.
**Key Findings**
* Azure (CVE-2025-54914): Vulnerability in Azure Networking allowing elevation of privileges.
* Skyvern (CVE-2025-49619): Skyvern ≤ 0.1.85 has a server-side template injection (SSTI) vulnerability in its Prompt field (workflow blocks) via Jinja2. Authenticated users with low privileges can get remote code execution (blind).
* Generic SQLi / SSRF improvements: Expanded rule coverage to detect obfuscated SQL injection patterns and SSRF across host, local, and cloud contexts.
**Impact**
These vulnerabilities allow attackers to escalate privileges or execute code under conditions where previously they could not:
* Azure CVE-2025-54914 enables an attacker from the network with no credentials to gain high-level access within Azure Networking; could lead to full compromise of networking components.
* Skyvern CVE-2025-49619 allows authenticated users with minimal privilege to exploit SSTI for remote code execution, undermining isolation of workflow components.
* The improvements for SQLi and SSRF reduce risk from common injection and request-based attacks.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | c36a425ae0c94789a9bc34f06a135cbf | 100146 | SSRF - Host - 2 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | dfa84b0aed5a4b45b953a36a57035abf | 100146B | SSRF - Local - 2 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 276073e60c7a4b4d91faba1fbbe18d50 | 100146C | SSRF - Cloud - 2 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 78c856218f2d40f4b5988c8c956c1961 | 100714 | Azure - Auth Bypass - CVE:CVE-2025-54914 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 9f1c8d4cbf3848dbb940771bc5ced231 | 100758 | Skyvern - Remote Code Execution - CVE:CVE-2025-49619 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 6be7e7829f3b43c688e1ac4284a619a1 | 100773 | Next.js - SSRF | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 0cc3f50216bf4b448210bcc3983ff2dd | 100774 | Adobe Commerce - Remote Code Execution - CVE:CVE-2025-54236 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 53bfaeb311a049e3877fa15c0380a1a6 | 100800\_BETA | SQLi - Obfuscated Boolean - Beta | Log | Block | This rule has been merged into the original rule (ID: 7663ea44178441a0b3205c145563445f ) |
---
title: Invalid Submissions Feedback · Changelog
description: Feedback for invalid submissions that prevent Email security from
providing continuous protection
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-23-invalid-submissions/
md: https://developers.cloudflare.com/changelog/2025-09-23-invalid-submissions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Invalid Submissions Feedback
Sep 23, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
Email security relies on your submissions to continuously improve our detection models. However, we often receive submissions in formats that cannot be ingested, such as incomplete EMLs, screenshots, or text files.
To ensure all customer feedback is actionable, we have launched two new features to manage invalid submissions sent to our team and user [submission aliases](https://developers.cloudflare.com/cloudflare-one/email-security/settings/phish-submissions/submission-addresses/):
* **Email Notifications:** We now automatically notify users by email when they provide an invalid submission, educating them on the correct format. To disable notifications, go to **[Settings](https://one.dash.cloudflare.com/?to=/:account/email-security/settings)** > **Invalid submission emails** and turn the feature off.

* **Invalid Submission dashboard:** You can quickly identify which users need education to provide valid submissions so Cloudflare can provide continuous protection.

Learn more about this feature on [invalid submissions](https://developers.cloudflare.com/cloudflare-one/email-security/submissions/invalid-submissions/).
This feature is available across these Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Improved support for running multiple Workers with `wrangler dev` · Changelog
description: Workers running with wrangler dev using multiple config files can
now communicate with Workers running in separate dev commands.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-23-wrangler-dev-multi-config-cross-command-support/
md: https://developers.cloudflare.com/changelog/2025-09-23-wrangler-dev-multi-config-cross-command-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improved support for running multiple Workers with \`wrangler dev\`
Sep 23, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can run multiple Workers in a single dev command by passing multiple config files to `wrangler dev`:
```sh
wrangler dev --config ./web/wrangler.jsonc --config ./api/wrangler.jsonc
```
Previously, if you ran the command above and then also ran wrangler dev for a different Worker, the Workers running in separate wrangler dev sessions could not communicate with each other. This prevented you from being able to use [Service Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/service-bindings/) and [Tail Workers](https://developers.cloudflare.com/workers/observability/logs/tail-workers/) in local development, when running separate wrangler dev sessions.
Now, the following works as expected:
```sh
# Terminal 1: Run your application that includes both Web and API workers
wrangler dev --config ./web/wrangler.jsonc --config ./api/wrangler.jsonc
# Terminal 2: Run your auth worker separately
wrangler dev --config ./auth/wrangler.jsonc
```
These Workers can now communicate with each other across separate dev commands, regardless of your development setup.
```js
export default {
async fetch(request, env) {
// This service binding call now works across dev commands
const authorized = await env.AUTH.isAuthorized(request);
if (!authorized) {
return new Response('Unauthorized', { status: 401 });
}
return new Response('Hello from API Worker!', { status: 200 });
},
};
```
Check out the [Developing with multiple Workers](https://developers.cloudflare.com/workers/development-testing/multi-workers) guide to learn more about the different approaches and when to use each one.
---
title: WAF Release - 2025-09-24 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-09-24 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-24-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-24-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-24 - Emergency
Sep 24, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights a critical vendor-specific vulnerability: a deserialization flaw in the License Servlet of Fortra’s GoAnywhere MFT. By forging a license response signature, an attacker can trigger deserialization of arbitrary objects, potentially leading to command injection.
**Key Findings**
* GoAnywhere MFT (CVE-2025-10035): Deserialization vulnerability in the License Servlet that allows attackers with a forged license response signature to deserialize arbitrary objects, potentially resulting in command injection.
**Impact**
GoAnywhere MFT (CVE-2025-10035): Exploitation enables attackers to escalate privileges or achieve remote code execution via command injection.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 8fe242c7c0d64d689f4fc9a1e08b39f3 | 100787 | Fortra GoAnywhere - Auth Bypass - CVE:CVE-2025-10035 | N/A | Block | This is a New Detection |
---
title: Run more Containers with higher resource limits · Changelog
description: Containers limits have been increased to allow for more concurrent instances
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-24-higher-container-resource-limits/
md: https://developers.cloudflare.com/changelog/2025-09-24-higher-container-resource-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Run more Containers with higher resource limits
Sep 25, 2025
[Containers](https://developers.cloudflare.com/containers/)
You can now run more Containers concurrently with higher limits on CPU, memory, and disk.
| Limit | New Limit | Previous Limit |
| - | - | - |
| Memory for concurrent live Container instances | 400GiB | 40GiB |
| vCPU for concurrent live Container instances | 100 | 20 |
| Disk for concurrent live Container instances | 2TB | 100GB |
You can now run 1000 instances of the `dev` instance type, 400 instances of `basic`, or 100 instances of `standard` concurrently.
This opens up new possibilities for running larger-scale workloads on Containers.
See the [getting started guide](https://developers.cloudflare.com/containers/get-started/) to deploy your first Container, and the [limits documentation](https://developers.cloudflare.com/containers/platform-details/limits/) for more details on the available instance types and limits.
---
title: AI Search (formerly AutoRAG) now with More Models To Choose From · Changelog
description: Use models from different providers in AI Search (formerly AutoRAG)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-ai-search-more-models/
md: https://developers.cloudflare.com/changelog/2025-09-25-ai-search-more-models/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Search (formerly AutoRAG) now with More Models To Choose From
Sep 25, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
AutoRAG is now AI Search! The new name marks a new and bigger mission: to make world-class search infrastructure available to every developer and business.
With AI Search you can now use models from different providers like OpenAI and Anthropic. By attaching your provider keys to the AI Gateway linked to your AI Search instance, you can use many more models for both embedding and inference.
To use AI Search with other [model providers](https://developers.cloudflare.com/ai-search/configuration/models/):
1. **Add provider keys to AI Gateway**
1. Go to AI > AI Gateway in the dashboard.
2. Select or create an AI gateway.
3. In Provider Keys, choose your provider, click Add, and enter the key.
2. **Connect a gateway to AI Search**: When creating a new AI Search, select the AI Gateway with your provider keys. For an existing AI Search, go to Settings and switch to a gateway that has your keys under Resources.
3. **Select models**: Embedding models are only available to be changed when creating a new AI Search. Generation model can be selected when creating a new AI Search and can be changed at any time in Settings.
Once configured, your AI Search instance will be able to reference models available through your AI Gateway when making a `/ai-search` request:
```javascript
export default {
async fetch(request, env) {
// Query your AI Search instance with a natural language question to an OpenAI model
const result = await env.AI.autorag("my-ai-search").aiSearch({
query: "What's new for Cloudflare Birthday Week?",
model: "openai/gpt-5"
});
// Return only the generated answer as plain text
return new Response(result.response, {
headers: { "Content-Type": "text/plain" },
});
},
};
```
In the coming weeks we will also roll out updates to align the APIs with the new name. The existing APIs will continue to be supported for the time being. Stay tuned to the [AI Search Changelog](https://developers.cloudflare.com/changelog/?product=ai-search) and [Discord](https://discord.cloudflare.com/) for more updates!
---
title: Announcing R2 SQL · Changelog
description: Run SQL queries against Apache Iceberg tables in R2 Data Catalog
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-announcing-r2-sql-open-beta/
md: https://developers.cloudflare.com/changelog/2025-09-25-announcing-r2-sql-open-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Announcing R2 SQL
Sep 25, 2025
[R2 SQL](https://developers.cloudflare.com/r2-sql/)
Today, we're launching the **open beta** for [R2 SQL](https://developers.cloudflare.com/r2-sql/): A serverless, distributed query engine that can efficiently analyze petabytes of data in [Apache Iceberg](https://iceberg.apache.org/) tables managed by [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog).
R2 SQL is ideal for exploring analytical and time-series data stored in R2, such as logs, events from [Pipelines](https://developers.cloudflare.com/pipelines/), or clickstream and user behavior data.
If you already have a table in R2 Data Catalog, running queries is as simple as:
```bash
npx wrangler r2 sql query YOUR_WAREHOUSE "
SELECT
user_id,
event_type,
value
FROM events.user_events
WHERE event_type = 'CHANGELOG' or event_type = 'BLOG'
AND __ingest_ts > '2025-09-24T00:00:00Z'
ORDER BY __ingest_ts DESC
LIMIT 100"
```
To get started with R2 SQL, check out our [getting started guide](https://developers.cloudflare.com/r2-sql/get-started/) or learn more about supported features in the [SQL reference](https://developers.cloudflare.com/r2-sql/sql-reference/). For a technical deep dive into how we built R2 SQL, read our [blog post](https://blog.cloudflare.com/r2-sql-deep-dive/).
---
title: Refine DLP Scans with New Body Phase Selector · Changelog
description: Gain more control over your DLP detections and reduce false
positives by specifying whether to scan the HTTP request or response body.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-body-phase-selector/
md: https://developers.cloudflare.com/changelog/2025-09-25-body-phase-selector/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Refine DLP Scans with New Body Phase Selector
Sep 25, 2025
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now more precisely control your HTTP DLP policies by specifying whether to scan the request or response body, helping to reduce false positives and target specific data flows.
In the Gateway HTTP policy builder, you will find a new selector called *Body Phase*. This allows you to define the direction of traffic the DLP engine will inspect:
* *Request Body*: Scans data sent from a user's machine to an upstream service. This is ideal for monitoring data uploads, form submissions, or other user-initiated data exfiltration attempts.
* *Response Body*: Scans data sent to a user's machine from an upstream service. Use this to inspect file downloads and website content for sensitive data.
For example, consider a policy that blocks Social Security Numbers (SSNs). Previously, this policy might trigger when a user visits a website that contains example SSNs in its content (the response body). Now, by setting the **Body Phase** to *Request Body*, the policy will only trigger if the user attempts to upload or submit an SSN, ignoring the content of the web page itself.
All policies without this selector will continue to scan both request and response bodies to ensure continued protection.
For more information, refer to [Gateway HTTP policy selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#body-phase/).
---
title: Browser Rendering Playwright GA, Stagehand support (Beta), and higher
limits · Changelog
description: Browser Rendering birthday week announcements
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-br-playwright-ga-stagehand-limits/
md: https://developers.cloudflare.com/changelog/2025-09-25-br-playwright-ga-stagehand-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Browser Rendering Playwright GA, Stagehand support (Beta), and higher limits
Sep 25, 2025
[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
We’re shipping three updates to Browser Rendering:
* Playwright support is now Generally Available and synced with [Playwright v1.55](https://playwright.dev/docs/release-notes#version-155), giving you a stable foundation for critical automation and AI-agent workflows.
* We’re also adding [Stagehand support (Beta)](https://developers.cloudflare.com/browser-rendering/stagehand/) so you can combine code with natural language instructions to build more resilient automations.
* Finally, we’ve tripled [limits](https://developers.cloudflare.com/browser-rendering/limits/#workers-paid) for paid plans across both the [REST API](https://developers.cloudflare.com/browser-rendering/rest-api/) and [Workers Bindings](https://developers.cloudflare.com/browser-rendering/workers-bindings/) to help you scale.
To get started with Stagehand, refer to the [Stagehand](https://developers.cloudflare.com/browser-rendering/stagehand/) example that uses Stagehand and [Workers AI](https://developers.cloudflare.com/workers-ai/) to search for a movie on this [example movie directory](https://demo.playwright.dev/movies), extract its details using natural language (title, year, rating, duration, and genre), and return the information along with a screenshot of the webpage.
```ts
const stagehand = new Stagehand({
env: "LOCAL",
localBrowserLaunchOptions: { cdpUrl: endpointURLString(env.BROWSER) },
llmClient: new WorkersAIClient(env.AI),
verbose: 1,
});
await stagehand.init();
const page = stagehand.page;
await page.goto('https://demo.playwright.dev/movies');
// if search is a multi-step action, stagehand will return an array of actions it needs to act on
const actions = await page.observe('Search for "Furiosa"');
for (const action of actions)
await page.act(action);
await page.act('Click the search result');
// normal playwright functions work as expected
await page.waitForSelector('.info-wrapper .cast');
let movieInfo = await page.extract({
instruction: 'Extract movie information',
schema: z.object({
title: z.string(),
year: z.number(),
rating: z.number(),
genres: z.array(z.string()),
duration: z.number().describe("Duration in minutes"),
}),
});
await stagehand.close();
```

---
title: R2 Data Catalog now supports compaction · Changelog
description: Users can now enable compaction on R2 Data Catalog
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-data-catalog-compaction/
md: https://developers.cloudflare.com/changelog/2025-09-25-data-catalog-compaction/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## R2 Data Catalog now supports compaction
Sep 25, 2025
[R2](https://developers.cloudflare.com/r2/)
You can now enable automatic compaction for [Apache Iceberg](https://iceberg.apache.org/) tables in [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) to improve query performance.
Compaction is the process of taking a group of small files and combining them into fewer larger files. This is an important maintenance operation as it helps ensure that query performance remains consistent by reducing the number of files that needs to be scanned.
To enable automatic compaction in R2 Data Catalog, find it under **R2 Data Catalog** in your R2 bucket settings in the dashboard.

Or with [Wrangler](https://developers.cloudflare.com/workers/wrangler/), run:
```bash
npx wrangler r2 bucket catalog compaction enable --target-size 128 --token
```
To get started with compaction, check out [manage catalogs](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/). For best practices and limitations, refer to [about compaction](https://developers.cloudflare.com/r2/data-catalog/table-maintenance/).
---
title: Application granular controls for operations in SaaS applications · Changelog
description: Gateway now provides granular control over File Sharing and AI Chat
applications
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-new-granular-controls-for-saas-applications/
md: https://developers.cloudflare.com/changelog/2025-09-25-new-granular-controls-for-saas-applications/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Application granular controls for operations in SaaS applications
Sep 30, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Gateway users can now apply granular controls to their file sharing and AI chat applications through [HTTP policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies).
The new feature offers two methods of controlling SaaS applications:
* **Application Controls** are curated groupings of Operations which provide an easy way for users to achieve a specific outcome. Application Controls may include *Upload*, *Download*, *Prompt*, *Voice*, and *Share* depending on the application.
* **Operations** are controls aligned to the most granular action a user can take. This provides a fine-grained approach to enforcing policy and generally aligns to the SaaS providers API specifications in naming and function.
Get started using [Application Granular Controls](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/granular-controls) and refer to the list of [supported applications](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/granular-controls/#compatible-applications).
---
title: Pipelines now supports SQL transformations and Apache Iceberg · Changelog
description: Transform streaming data with SQL and write to Apache Iceberg tables in R2
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-pipelines-sql/
md: https://developers.cloudflare.com/changelog/2025-09-25-pipelines-sql/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Pipelines now supports SQL transformations and Apache Iceberg
Sep 25, 2025
[Pipelines](https://developers.cloudflare.com/pipelines/)
Today, we're launching the new [Cloudflare Pipelines](https://developers.cloudflare.com/pipelines/): a streaming data platform that ingests events, transforms them with [SQL](https://developers.cloudflare.com/pipelines/sql-reference/select-statements/), and writes to [R2](https://developers.cloudflare.com/r2/) as [Apache Iceberg](https://iceberg.apache.org/) tables or Parquet files.
Pipelines can receive events via [HTTP endpoints](https://developers.cloudflare.com/pipelines/streams/writing-to-streams/#send-via-http) or [Worker bindings](https://developers.cloudflare.com/pipelines/streams/writing-to-streams/#send-via-workers), transform them with SQL, and deliver to R2 with exactly-once guarantees. This makes it easy to build analytics-ready warehouses for server logs, mobile application events, IoT telemetry, or clickstream data without managing streaming infrastructure.
For example, here's a pipeline that ingests clickstream events and filters out bot traffic while extracting domain information:
```sql
INSERT into events_table
SELECT
user_id,
lower(event) AS event_type,
to_timestamp_micros(ts_us) AS event_time,
regexp_match(url, '^https?://([^/]+)')[1] AS domain,
url,
referrer,
user_agent
FROM events_json
WHERE event = 'page_view'
AND NOT regexp_like(user_agent, '(?i)bot|spider');
```
Get started by creating a pipeline in the dashboard or running a single command in [Wrangler](https://developers.cloudflare.com/workers/wrangler/):
```bash
npx wrangler pipelines setup
```
Check out our [getting started guide](https://developers.cloudflare.com/pipelines/getting-started/) to learn how to create a pipeline that delivers events to an [Iceberg table](https://developers.cloudflare.com/r2/data-catalog/) you can query with R2 SQL. Read more about today's announcement in our [blog post](https://blog.cloudflare.com/cloudflare-data-platform).
---
title: Sign in with GitHub · Changelog
description: GitHub now available as a social login provider
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-sign-in-with-github/
md: https://developers.cloudflare.com/changelog/2025-09-25-sign-in-with-github/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Sign in with GitHub
Sep 25, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Cloudflare has launched sign in with GitHub as a log in option. This feature is available to all users with a verified email address who are not using SSO. To use it, simply click on the `Sign in with GitHub` button on the dashboard login page. You will be logged in with your primary GitHub email address.
#### For more information
* [Log in to Cloudflare](https://developers.cloudflare.com/fundamentals/user-profiles/login/)
---
title: SSO for all · Changelog
description: Single sign-on is now free for all users
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-sso-for-all/
md: https://developers.cloudflare.com/changelog/2025-09-25-sso-for-all/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## SSO for all
Sep 25, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Single sign-on (SSO) streamlines the process of logging into Cloudflare for Enterprise customers who manage a custom email domain and manage their own identity provider. Instead of managing a password and two-factor authentication credentials directly for Cloudflare, SSO lets you reuse your existing login infrastructure to seamlessly log in. SSO also provides additional security opportunities such as device health checks which are not available natively within Cloudflare.
Historically, SSO was only available for Enterprise accounts. Today, we are announcing that we are making SSO available to all users for free. We have also added the ability to directly manage SSO configurations using the API. This removes the previous requirement to contact support to configure SSO.
#### For more information
* [Every Cloudflare feature, available to all](https://blog.cloudflare.com/enterprise-grade-features-for-all/)
* [Configure Dashboard SSO](https://developers.cloudflare.com/fundamentals/manage-members/dashboard-sso/)
---
title: Announcing Workers VPC Services (Beta) · Changelog
description: Access private resources in your VPC from Cloudflare Workers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-25-workers-vpc/
md: https://developers.cloudflare.com/changelog/2025-09-25-workers-vpc/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Announcing Workers VPC Services (Beta)
Nov 05, 2025
[Workers VPC](https://developers.cloudflare.com/workers-vpc/)
**Workers VPC Services** is now available, enabling your Workers to securely access resources in your private networks, without having to expose them on the public Internet.
#### What's new
* **VPC Services**: Create secure connections to internal APIs, databases, and services using familiar Worker binding syntax
* **Multi-cloud Support**: Connect to resources in private networks in any external cloud (AWS, Azure, GCP, etc.) or on-premise using Cloudflare Tunnels
```js
export default {
async fetch(request, env, ctx) {
// Perform application logic in Workers here
// Sample call to an internal API running on ECS in AWS using the binding
const response = await env.AWS_VPC_ECS_API.fetch("https://internal-host.example.com");
// Additional application logic in Workers
return new Response();
},
};
```
#### Getting started
Set up a Cloudflare Tunnel, create a VPC Service, add service bindings to your Worker, and access private resources securely. [Refer to the documentation](https://developers.cloudflare.com/workers-vpc/) to get started.
---
title: Workers Analytics Engine adds supports for new SQL functions · Changelog
description: Workers Analytics Engine now supports additional SQL functions
including new mathematical operations, aggregate functions, and bit functions!
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-26-analytics-engine-sql-enhancements/
md: https://developers.cloudflare.com/changelog/2025-09-26-analytics-engine-sql-enhancements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers Analytics Engine adds supports for new SQL functions
Oct 02, 2025
[Workers Analytics Engine ](https://developers.cloudflare.com/analytics/analytics-engine/)[Workers](https://developers.cloudflare.com/workers/)
You can now perform more powerful queries directly in [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/) with a major expansion of our SQL function library.
Workers Analytics Engine allows you to ingest and store high-cardinality data at scale (such as custom analytics) and query your data through a simple SQL API.
Today, we've expanded Workers Analytics Engine's SQL capabilities with several new functions:
[**New aggregate functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/aggregate-functions/)
* `argMin()` - Returns the value associated with the minimum in a group
* `argMax()` - Returns the value associated with the maximum in a group
* `topK()` - Returns an array of the most frequent values in a group
* `topKWeighted()` - Returns an array of the most frequent values in a group using weights
* `first_value()` - Returns the first value in an ordered set of values within a partition
* `last_value()` - Returns the last value in an ordered set of values within a partition
[**New bit functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/bit-functions/)
* `bitAnd()` - Returns the bitwise AND of two expressions
* `bitCount()` - Returns the number of bits set to one in the binary representation of a number
* `bitHammingDistance()` - Returns the number of bits that differ between two numbers
* `bitNot()` - Returns a number with all bits flipped
* `bitOr()` - Returns the inclusive bitwise OR of two expressions
* `bitRotateLeft()` - Rotates all bits in a number left by specified positions
* `bitRotateRight()` - Rotates all bits in a number right by specified positions
* `bitShiftLeft()` - Shifts all bits in a number left by specified positions
* `bitShiftRight()` - Shifts all bits in a number right by specified positions
* `bitTest()` - Returns the value of a specific bit in a number
* `bitXor()` - Returns the bitwise exclusive-or of two expressions
[**New mathematical functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/mathematical-functions/)
* `abs()` - Returns the absolute value of a number
* `log()` - Computes the natural logarithm of a number
* `round()` - Rounds a number to a specified number of decimal places
* `ceil()` - Rounds a number up to the nearest integer
* `floor()` - Rounds a number down to the nearest integer
* `pow()` - Returns a number raised to the power of another number
[**New string functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/string-functions/)
* `lowerUTF8()` - Converts a string to lowercase using UTF-8 encoding
* `upperUTF8()` - Converts a string to uppercase using UTF-8 encoding
[**New encoding functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/encoding-functions/)
* `hex()` - Converts a number to its hexadecimal representation
* `bin()` - Converts a string to its binary representation
[**New type conversion functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/type-conversion-functions/)
* `toUInt8()` - Converts any numeric expression, or expression resulting in a string representation of a decimal, into an unsigned 8 bit integer
#### Ready to get started?
Whether you're building usage-based billing systems, customer analytics dashboards, or other custom analytics, these functions let you get the most out of your data. [Get started ](https://developers.cloudflare.com/analytics/analytics-engine/get-started/)with Workers Analytics Engine and explore all available functions in our [SQL reference documentation](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/).
---
title: Automatic loopback bindings via ctx.exports · Changelog
description: You no longer have to configure bindings explicitly when they point
back to your own Worker's top-level exports
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-26-ctx-exports/
md: https://developers.cloudflare.com/changelog/2025-09-26-ctx-exports/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Automatic loopback bindings via ctx.exports
Sep 26, 2025
[Workers](https://developers.cloudflare.com/workers/)
The [`ctx.exports` API](https://developers.cloudflare.com/workers/runtime-apis/context/#exports) contains automatically-configured bindings corresponding to your Worker's top-level exports. For each top-level export extending `WorkerEntrypoint`, `ctx.exports` will contain a [Service Binding](https://developers.cloudflare.com/workers/runtime-apis/bindings/service-bindings) by the same name, and for each export extending `DurableObject` (and for which storage has been configured via a [migration](https://developers.cloudflare.com/durable-objects/reference/durable-objects-migrations/)), `ctx.exports` will contain a [Durable Object namespace binding](https://developers.cloudflare.com/durable-objects/api/namespace/). This means you no longer have to configure these bindings explicitly in `wrangler.jsonc`/`wrangler.toml`.
Example:
```js
import { WorkerEntrypoint } from "cloudflare:workers";
export class Greeter extends WorkerEntrypoint {
greet(name) {
return `Hello, ${name}!`;
}
}
export default {
async fetch(request, env, ctx) {
let greeting = await ctx.exports.Greeter.greet("World")
return new Response(greeting);
}
}
```
At present, you must use [the `enable_ctx_exports` compatibility flag](https://developers.cloudflare.com/workers/configuration/compatibility-flags#enable-ctxexports) to enable this API, though it will be on by default in the future.
[See the API reference for more information.](https://developers.cloudflare.com/workers/runtime-apis/context/#exports)
---
title: WAF Release - 2025-09-26 · Changelog
description: Cloudflare WAF managed rulesets 2025-09-26 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-26-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-26-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-26
Sep 26, 2025
[WAF](https://developers.cloudflare.com/waf/)
**Managed Ruleset Updated**
This update introduces 11 new detections in the Cloudflare Managed Ruleset (all currently set to Disabled mode to preserve remediation logic and allow quick activation if needed). The rules cover a broad spectrum of threats - SQL injection techniques, command and code injection, information disclosure of common files, URL anomalies, and cross-site scripting.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 3ffd242b4ba242ca965022d3a67d8561 | 100859A | SQLi - UNION - 3 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 91d9cf56355b4ab88481b2fd4de80468 | 100889 | Command Injection - Generic 9 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | c15ca8e8290f485287037665f2be3ddf | 100890 | Information Disclosure - Common Files - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 56669615f2984c2cac8c608980a252a8 | 100891 | Anomaly:URL - Relative Paths | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | c41789fb6370431d809567d17e7d3865 | 100894 | XSS - Inline Function | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | b995d0b930604fa6b8d9b2a13792565c | 100895 | XSS - DOM | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | ab8277e3f432400bbd9403dd42978e38 | 100896 | SQLi - MSSQL Length Enumeration | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 3ec33bc5ac77495a9f55020e3ab43f7e | 100897 | Generic Rules - Code Injection - 3 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 4375dc90c7af4c55908f6b95c1686741 | 100898 | SQLi - Evasion | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 945c5aa9f45141dd872d7ec920999be0 | 100899 | SQLi - Probing 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 2c20b5e8684043f48620ff77b4026c88 | 100900 | SQLi - Probing | N/A | Disabled | This is a New Detection |
---
title: WAF Release - 2025-09-28 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-09-28 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-28-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-28-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-28 - Emergency
Sep 28, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights multiple critical Cisco vulnerabilities (CVE-2025-20363, CVE-2025-20333, CVE-2025-20362). This flaw stems from improper input validation in HTTP(S) requests. An authenticated VPN user could send crafted requests to execute code as root, potentially compromising the device.
**Key Findings**
* Cisco (CVE-2025-20333, CVE-2025-20362, CVE-2025-20363): Multiple vulnerabilities that could allow attackers to exploit unsafe deserialization and input validation flaws. Successful exploitation may result in arbitrary code execution, privilege escalation, or command injection on affected systems.
**Impact**
Cisco (CVE-2025-20333, CVE-2025-20362, CVE-2025-20363): Exploitation enables attackers to escalate privileges or achieve remote code execution via command injection.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | a1bef4ada0b146d2862cad439ee0ab84 | 100788 | Cisco Secure Firewall Adaptive Security Appliance - Remote Code Execution - CVE:CVE-2025-20333, CVE:CVE-2025-20362, CVE:CVE-2025-20363 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 51de6ce6596a40eb8200452ad30f768e | 100788A | Cisco Secure Firewall Adaptive Security Appliance - Remote Code Execution - CVE:CVE-2025-20333, CVE:CVE-2025-20362, CVE:CVE-2025-20363 | N/A | Disabled | This is a New Detection |
---
title: Regional Data in Cloudflare Radar · Changelog
description: New Regional traffic insights, bringing a more localized
perspective to the traffic trends shown on Radar
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-29-radar-regional-data/
md: https://developers.cloudflare.com/changelog/2025-09-29-radar-regional-data/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Regional Data in Cloudflare Radar
Sep 29, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) now introduces Regional Data, providing traffic insights that bring a more localized perspective to the traffic trends shown on Radar.
The following API endpoints are now available:
* [`Get Geolocation`](https://developers.cloudflare.com/api/resources/radar/subresources/geolocations/methods/get/) - Retrieves geolocation by `geoId`.
* [`List Geolocations`](https://developers.cloudflare.com/api/resources/radar/subresources/geolocations/methods/list/) - Lists geolocations.
* [`NetFlows Summary By Dimension`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/methods/summary_v2/) - Retrieves NetFlows summary by dimension.
All `summary` and `timeseries_groups` endpoints in [`HTTP`](https://developers.cloudflare.com/api/resources/radar/subresources/http/) and [`NetFlows`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/) now include an `adm1` dimension for grouping data by first level administrative division (for example, state, province, etc.)
A new filter `geoId` was also added to all endpoints in [`HTTP`](https://developers.cloudflare.com/api/resources/radar/subresources/http/) and [`NetFlows`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/), allowing filtering by a specific administrative division.
Check out the new Regional traffic insights on a country specific traffic page [new Radar page](https://radar.cloudflare.com/traffic/pt).
---
title: WAF Release - 2025-09-29 · Changelog
description: Cloudflare WAF managed rulesets 2025-09-29 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-29-waf-release/
md: https://developers.cloudflare.com/changelog/2025-09-29-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-09-29
Sep 29, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights four important vendor- and component-specific issues: an authentication bypass in SimpleHelp (CVE-2024-57727), an information-disclosure flaw in Flowise Cloud (CVE-2025-58434), an SSRF in the WordPress plugin Ditty (CVE-2025-8085), and a directory-traversal bug in Vite (CVE-2025-30208). These are paired with improvements to our generic detection coverage (SQLi, SSRF) to raise the baseline and reduce noisy gaps.
**Key Findings**
* SimpleHelp (CVE-2024-57727): Authentication bypass in SimpleHelp that can allow unauthorized access to management interfaces or sessions.
* Flowise Cloud (CVE-2025-58434): Information-disclosure vulnerability in Flowise Cloud that may expose sensitive configuration or user data to unauthenticated or low-privileged actors.
* WordPress:Plugin: Ditty (CVE-2025-8085): SSRF in the Ditty WordPress plugin enabling server-side requests that could reach internal services or cloud metadata endpoints.
* Vite (CVE-2025-30208): Directory-traversal vulnerability in Vite allowing access to filesystem paths outside the intended web root.
**Impact**
These vulnerabilities allow attackers to gain access, escalate privileges, or execute actions that were previously unavailable:
* SimpleHelp (CVE-2024-57727): An authentication bypass that can let unauthenticated attackers access management interfaces or hijack sessions — enabling lateral movement, credential theft, or privilege escalation within affected environments.
* Flowise Cloud (CVE-2025-58434): Information-disclosure flaw that can expose sensitive configuration, tokens, or user data; leaked secrets may be chained into account takeover or privileged access to backend services.
* WordPress:Plugin: Ditty (CVE-2025-8085): SSRF that enables server-side requests to internal services or cloud metadata endpoints, potentially allowing attackers to retrieve credentials or reach otherwise inaccessible infrastructure, leading to privilege escalation or cloud resource compromise.
* Vite (CVE-2025-30208): Directory-traversal vulnerability that can expose filesystem contents outside the web root (configuration files, keys, source code), which attackers can use to escalate privileges or further compromise systems.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 6fe90532af50427484a5275c8c2e30fb | 100717 | SimpleHelp - Auth Bypass - CVE:CVE-2024-57727 | Log | Block | This rule is merged to 100717 in legacy WAF and 498fcd81a62a4b5ca943e2de958094d3 in new WAF |
| Cloudflare Managed Ruleset | 013ef5de3f074fd5a43cdd70d58b886b | 100775 | Flowise Cloud - Information Disclosure - CVE:CVE-2025-58434 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 68fc5c086ccb4b40a35a63b19bce1ff4 | 100881 | WordPress:Plugin:Ditty - SSRF - CVE:CVE-2025-8085 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 9e1a56e6b3bc49b187bf6e35ddc329dd | 100887 | Vite - Directory Traversal - CVE:CVE-2025-30208 | Log | Block | This is a New Detection |
---
title: WARP client for Linux (version 2025.7.176.0) · Changelog
description: WARP client for Linux (version 2025.7.176.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-30-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-09-30-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.7.176.0)
Sep 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements including an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com/).
**Changes and improvements**
* MASQUE is now the default [tunnel protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) for all new WARP device profiles.
* Improvement to limit idle connections in [Gateway with DoH mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#gateway-with-doh) to avoid unnecessary resource usage that can lead to DoH requests not resolving.
* Improvements to maintain [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings when [switching between organizations](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/switch-organizations/#switch-organizations-in-warp).
* Improvements to maintain client connectivity during network changes.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for macOS (version 2025.7.176.0) · Changelog
description: WARP client for macOS (version 2025.7.176.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-30-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-09-30-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.7.176.0)
Sep 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed a bug preventing the `warp-diag captive-portal` command from running successfully due to the client not parsing SSID on macOS.
* Improvements to maintain [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings when [switching between organizations](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/switch-organizations/#switch-organizations-in-warp).
* MASQUE is now the default [tunnel protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) for all new WARP device profiles.
* Improvement to limit idle connections in [Gateway with DoH mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#gateway-with-doh) to avoid unnecessary resource usage that can lead to DoH requests not resolving.
* Improvements to maintain client connectivity during network changes.
* The WARP client now supports macOS Tahoe (version 26.0).
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.7.176.0) · Changelog
description: WARP client for Windows (version 2025.7.176.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-09-30-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-09-30-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.7.176.0)
Sep 30, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes and improvements.
**Changes and improvements**
* MASQUE is now the default [tunnel protocol](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#device-tunnel-protocol) for all new WARP device profiles.
* Improvement to limit idle connections in [Gateway with DoH mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#gateway-with-doh) to avoid unnecessary resource usage that can lead to DoH requests not resolving.
* Improvement to maintain TCP connections to reduce interruptions in long-lived connections such as RDP or SSH.
* Improvements to maintain [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings when [switching between organizations](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/switch-organizations/#switch-organizations-in-warp).
* Improvements to maintain client connectivity during network changes.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: New Confidence Intervals in GraphQL Analytics API · Changelog
description: Confidence intervals are now supported in the GraphQL Analytics API
to show statistical ranges for sampled data results
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-01-confidence-intervals/
md: https://developers.cloudflare.com/changelog/2025-10-01-confidence-intervals/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Confidence Intervals in GraphQL Analytics API
Oct 01, 2025
[Analytics](https://developers.cloudflare.com/analytics/)
The GraphQL Analytics API now supports confidence intervals for `sum` and `count` fields on adaptive (sampled) datasets. Confidence intervals provide a statistical range around sampled results, helping verify accuracy and quantify uncertainty.
* **Supported datasets**: Adaptive (sampled) datasets only.
* **Supported fields**: All `sum` and `count` fields.
* **Usage**: The confidence `level` must be provided as a decimal between 0 and 1 (e.g. `0.90`, `0.95`, `0.99`).
* **Default**: If no confidence level is specified, no intervals are returned.
For examples and more details, see the [GraphQL Analytics API documentation](https://developers.cloudflare.com/analytics/graphql-api/features/confidence-intervals/).
---
title: Fine-grained Permissioning for Access for Apps, IdPs, & Targets now in
Public Beta · Changelog
description: Expanding Role-Based-Access-Control with resource-level controls in
Cloudflare Zero Trust.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-01-fine-grained-permissioning-beta/
md: https://developers.cloudflare.com/changelog/2025-10-01-fine-grained-permissioning-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Fine-grained Permissioning for Access for Apps, IdPs, & Targets now in Public Beta
Oct 02, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Fine-grained permissions for **Access Applications, Identity Providers (IdPs), and Targets** is now available in Public Beta. This expands our RBAC model beyond account & zone-scoped roles, enabling administrators to grant permissions scoped to individual resources.
#### What's New
* **[Access Applications](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/http-apps/)**: Grant admin permissions to specific Access Applications.
* **[Identity Providers](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/)**: Grant admin permissions to individual Identity Providers.
* **[Targets](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/non-http/infrastructure-apps/#1-add-a-target)**: Grant admin rights to specific Targets

Note
During the public beta, members must also be assigned an account-scoped, read only role to view resources in the dashboard. This restriction will be lifted in a future release.
* **Account Read Only** plus a fine-grained permission for a specific App, IdP, or Target
* **Cloudflare Zero Trust Read Only** plus fine-grained permission for a specific App, IdP, or Target
For more info:
* [Get started with Cloudflare Permissioning](https://developers.cloudflare.com/fundamentals/manage-members/roles/)
* [Manage Member Permissioning via the UI & API](https://developers.cloudflare.com/fundamentals/manage-members/manage)
---
title: Return markdown · Changelog
description: Users can now retrieve markdown, rather than HTML, from Cloudflare
documentation
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-01-md-returned/
md: https://developers.cloudflare.com/changelog/2025-10-01-md-returned/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Return markdown
Oct 01, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Users can now specify that they want to retrieve Cloudflare documentation as markdown rather than the previous HTML default. This can significantly reduce token consumption when used alongside Large Language Model (LLM) tools.
```sh
curl https://developers.cloudflare.com/workers/ -H 'Accept: text/markdown' -v
```
If you maintain your own site and want to adopt this practice using Cloudflare Workers for your own users you can follow the example [here](https://github.com/cloudflare/cloudflare-docs/pull/25493).
---
title: Larger Container instance types · Changelog
description: New Container instance types provide more resources for your
container applications
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-01-new-container-instance-types/
md: https://developers.cloudflare.com/changelog/2025-10-01-new-container-instance-types/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Larger Container instance types
Oct 01, 2025
[Containers](https://developers.cloudflare.com/containers/)
New instance types provide up to 4 vCPU, 12 GiB of memory, and 20 GB of disk per container instance.
| Instance Type | vCPU | Memory | Disk |
| - | - | - | - |
| lite | 1/16 | 256 MiB | 2 GB |
| basic | 1/4 | 1 GiB | 4 GB |
| standard-1 | 1/2 | 4 GiB | 8 GB |
| standard-2 | 1 | 6 GiB | 12 GB |
| standard-3 | 2 | 8 GiB | 16 GB |
| standard-4 | 4 | 12 GiB | 20 GB |
The `dev` and `standard` instance types are preserved for backward compatibility and are aliases for `lite` and `standard-1`, respectively. The `standard-1` instance type now provides up to 8 GB of disk instead of only 4 GB.
See the [getting started guide](https://developers.cloudflare.com/containers/get-started/) to deploy your first Container, and the [limits documentation](https://developers.cloudflare.com/containers/platform-details/limits/) for more details on the available instance types and limits.
---
title: Expanded File Type Controls for Executables and Disk Images · Changelog
description: Block uploads and downloads of Apple Disk Images (DMG), Microsoft
Application Installers (MSIX), and macOS Installer Packages (MPKG) to prevent
the transfer of unauthorized software.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-01-new-file-type-support/
md: https://developers.cloudflare.com/changelog/2025-10-01-new-file-type-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Expanded File Type Controls for Executables and Disk Images
Oct 01, 2025
[Data Loss Prevention](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)
You can now enhance your security posture by blocking additional application installer and disk image file types with Cloudflare Gateway. Preventing the download of unauthorized software packages is a critical step in securing endpoints from malware and unwanted applications.
We have expanded Gateway's file type controls to include:
* Apple Disk Image (dmg)
* Microsoft Software Installer (msix, appx)
* Apple Software Package (pkg)
You can find these new options within the [*Upload File Types* and *Download File Types* selectors](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#download-and-upload-file-types) when creating or editing an HTTP policy. The file types are categorized as follows:
* **System**: *Apple Disk Image (dmg)*
* **Executable**: *Microsoft Software Installer (msix)*, *Microsoft Software Installer (appx)*, *Apple Software Package (pkg)*
To ensure these file types are blocked effectively, please note the following behaviors:
* DMG: Due to their file structure, DMG files are blocked at the very end of the transfer. A user's download may appear to progress but will fail at the last moment, preventing the browser from saving the file.
* MSIX: To comprehensively block Microsoft Software Installers, you should also include the file type *Unscannable*. MSIX files larger than 100 MB are identified as Unscannable ZIP files during inspection.
To get started, go to your HTTP policies in Zero Trust. For a full list of file types, refer to [supported file types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/#supported-file-types).
---
title: New Deepgram Flux model available on Workers AI · Changelog
description: Partner voice activity detection model
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-02-deepgram-flux/
md: https://developers.cloudflare.com/changelog/2025-10-02-deepgram-flux/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Deepgram Flux model available on Workers AI
Oct 02, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Deepgram's newest Flux model [`@cf/deepgram/flux`](https://developers.cloudflare.com/workers-ai/models/flux/) is now available on Workers AI, hosted directly on Cloudflare's infrastructure. We're excited to be a launch partner with Deepgram and offer their new Speech Recognition model built specifically for enabling voice agents. Check out [Deepgram's blog](https://deepgram.com/flux) for more details on the release.
The Flux model can be used in conjunction with Deepgram's speech-to-text model [`@cf/deepgram/nova-3`](https://developers.cloudflare.com/workers-ai/models/nova-3/) and text-to-speech model [`@cf/deepgram/aura-1`](https://developers.cloudflare.com/workers-ai/models/aura-1/) to build end-to-end voice agents. Having Deepgram on Workers AI takes advantage of our edge GPU infrastructure, for ultra low latency voice AI applications.
#### Promotional Pricing
For the month of October 2025, Deepgram's Flux model will be free to use on Workers AI. Official pricing will be announced soon and charged after the promotional pricing period ends on October 31, 2025. Check out the [model page](https://developers.cloudflare.com/workers-ai/models/flux/) for pricing details in the future.
#### Example Usage
The new Flux model is WebSocket only as it requires live bi-directional streaming in order to recognize speech activity.
1. Create a worker that establishes a websocket connection with `@cf/deepgram/flux`
```js
export default {
async fetch(request, env, ctx): Promise {
const resp = await env.AI.run("@cf/deepgram/flux", {
encoding: "linear16",
sample_rate: "16000"
}, {
websocket: true
});
return resp;
},
} satisfies ExportedHandler;
```
1. Deploy your worker
```bash
npx wrangler deploy
```
1. Write a client script to connect to your worker and start sending random audio bytes to it
```js
const ws = new WebSocket('wss://');
ws.onopen = () => {
console.log('Connected to WebSocket');
// Generate and send random audio bytes
// You can replace this part with a function
// that reads from your mic or other audio source
const audioData = generateRandomAudio();
ws.send(audioData);
console.log('Audio data sent');
};
ws.onmessage = (event) => {
// Transcription will be received here
// Add your custom logic to parse the data
console.log('Received:', event.data);
};
ws.onerror = (error) => {
console.error('WebSocket error:', error);
};
ws.onclose = () => {
console.log('WebSocket closed');
};
// Generate random audio data (1 second of noise at 44.1kHz, mono)
function generateRandomAudio() {
const sampleRate = 44100;
const duration = 1;
const numSamples = sampleRate * duration;
const buffer = new ArrayBuffer(numSamples * 2);
const view = new Int16Array(buffer);
for (let i = 0; i < numSamples; i++) {
view[i] = Math.floor(Math.random() * 65536 - 32768);
}
return buffer;
}
```
---
title: One-click Cloudflare Access for Workers · Changelog
description: You can now enable Cloudflare Access for your workers.dev and
preview URLs in a single click.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-03-one-click-access-for-workers/
md: https://developers.cloudflare.com/changelog/2025-10-03-one-click-access-for-workers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## One-click Cloudflare Access for Workers
Oct 03, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now enable [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) for your [`workers.dev`](https://developers.cloudflare.com/workers/configuration/routing/workers-dev/) and [Preview URLs](https://developers.cloudflare.com/workers/configuration/previews/) in a single click.
Access allows you to limit access to your Workers to specific users or groups. You can limit access to yourself, your teammates, your organization, or anyone else you specify in your [Access policy](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/).
To enable Cloudflare Access:
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. In **Overview**, select your Worker.
3. Go to **Settings** > **Domains & Routes**.
4. For `workers.dev` or Preview URLs, click **Enable Cloudflare Access**.
5. Optionally, to configure the Access application, click **Manage Cloudflare Access**. There, you can change the email addresses you want to authorize. View [Access policies](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/#selectors) to learn about configuring alternate rules.
To fully secure your application, it is important that you validate the JWT that Cloudflare Access adds to the `Cf-Access-Jwt-Assertion` header on the incoming request.
The following code will validate the JWT using the [jose NPM package](https://www.npmjs.com/package/jose):
```javascript
import { jwtVerify, createRemoteJWKSet } from "jose";
export default {
async fetch(request, env, ctx) {
// Verify the POLICY_AUD environment variable is set
if (!env.POLICY_AUD) {
return new Response("Missing required audience", {
status: 403,
headers: { "Content-Type": "text/plain" },
});
}
// Get the JWT from the request headers
const token = request.headers.get("cf-access-jwt-assertion");
// Check if token exists
if (!token) {
return new Response("Missing required CF Access JWT", {
status: 403,
headers: { "Content-Type": "text/plain" },
});
}
try {
// Create JWKS from your team domain
const JWKS = createRemoteJWKSet(
new URL(`${env.TEAM_DOMAIN}/cdn-cgi/access/certs`),
);
// Verify the JWT
const { payload } = await jwtVerify(token, JWKS, {
issuer: env.TEAM_DOMAIN,
audience: env.POLICY_AUD,
});
// Token is valid, proceed with your application logic
return new Response(`Hello ${payload.email || "authenticated user"}!`, {
headers: { "Content-Type": "text/plain" },
});
} catch (error) {
// Token verification failed
return new Response(`Invalid token: ${error.message}`, {
status: 403,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
#### Required environment variables
Add these [environment variables](https://developers.cloudflare.com/workers/configuration/environment-variables/) to your Worker:
* `POLICY_AUD`: Your application's AUD tag
* `TEAM_DOMAIN`: `https://.cloudflareaccess.com`
Both of these appear in the modal that appears when you enable Cloudflare Access.
You can set these variables by adding them to your Worker's [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/), or via the Cloudflare dashboard under **Workers & Pages** > **your-worker** > **Settings** > **Environment Variables**.
---
title: WAF Release - 2025-10-03 · Changelog
description: Cloudflare WAF managed rulesets 2025-10-03 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-03-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-03-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-03
Oct 03, 2025
[WAF](https://developers.cloudflare.com/waf/)
**Managed Ruleset Updated**
This update introduces 21 new detections in the Cloudflare Managed Ruleset (all currently set to Disabled mode to preserve remediation logic and allow quick activation if needed). The rules cover a broad spectrum of threats - SQL injection techniques, command and code injection, information disclosure of common files, URL anomalies, and cross-site scripting.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 0d02c2fb14eb4cec9c2e2b58d61fac74 | 100902 | Generic Rules - Command Execution - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | c3079865ce9a41368657026b514aeeb8 | 100908 | Generic Rules - Command Execution - 3 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 107ae2922b654bb28df7ca978d46a6f4 | 100910 | Generic Rules - Command Execution - 4 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 68bdb75ae6d24e139a83e5731bd0a329 | 100915 | Generic Rules - Command Execution - 5 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | ea04bb580f7d400386c7dc1d5e51450a | 100899 | Generic Rules - Content-Type Abuse | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 233364f656ff42b8acc41dcd7996012f | 100914 | Generic Rules - Content-Type Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 1aa695281c954513be3d003b93209312 | 100911 | Generic Rules - Cookie Header Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | d9f9e4f5bf11489da52dccb40f373b3f | 100905 | Generic Rules - NoSQL Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5a1897b714e044a887c0f3f078a0ed04 | 100913 | Generic Rules - NoSQL Injection - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 4d6fd28df4f1494e95e70d2c5d649624 | 100907 | Generic Rules - Parameter Pollution | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 61181e3af5304f7396c7d01cfd1c674e | 100906 | Generic Rules - PHP Object Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | ed5190bfbe1b45a6a645126334c88168 | 100904 | Generic Rules - Prototype Pollution | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 3ec33bc5ac77495a9f55020e3ab43f7e | 100897 | Generic Rules - Prototype Pollution 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | c6d752c4909e4b7e8eff6c780d94ee22 | 100903 | Generic Rules - Reverse Shell | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | caf37e7800bb4635bcc2eefcd5add8e3 | 100909 | Generic Rules - Reverse Shell - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 475d090baead467c88dfabbb565c78b0 | 100898 | Generic Rules - SSJI NoSQL | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | f4c7f98934264c9c937eec1212b837a0 | 100896 | Generic Rules - SSRF | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | efd01b814d144e90b36522b311c4fb00 | 100895 | Generic Rules - Template Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 00a9a0d663da4add95b863abd3ed0123 | 100895A | Generic Rules - Template Injection - 2 | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | e58c0fffee4f4374bd37f2577501a1d9 | 100912 | Generic Rules - XXE | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | ab09ba8d00eb4cdbb7a6a65ddc55cdb6 | 100900 | Relative Paths - Anomaly Headers | N/A | Disabled | This is a New Detection |
---
title: R2 Data Catalog table-level compaction · Changelog
description: Control compaction settings for individual Iceberg tables
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-06-data-catalog-table-compaction/
md: https://developers.cloudflare.com/changelog/2025-10-06-data-catalog-table-compaction/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## R2 Data Catalog table-level compaction
Oct 06, 2025
[R2](https://developers.cloudflare.com/r2/)
You can now enable compaction for individual [Apache Iceberg](https://iceberg.apache.org/) tables in [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/), giving you fine-grained control over different workloads.
```bash
# Enable compaction for a specific table (no token required)
npx wrangler r2 bucket catalog compaction enable --target-size 256
```
This allows you to:
* Apply different target file sizes per table
* Disable compaction for specific tables
* Optimize based on table-specific access patterns
Learn more at [Manage catalogs](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/).
---
title: New Overview Page for Cloudflare Workers · Changelog
description: A new Overview page gives you a quick view of your Worker’s
activity, recent versions, and bindings.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-06-new-worker-overview-page/
md: https://developers.cloudflare.com/changelog/2025-10-06-new-worker-overview-page/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Overview Page for Cloudflare Workers
Oct 07, 2025
[Workers](https://developers.cloudflare.com/workers/)

Each of your Workers now has a new overview page in the Cloudflare dashboard.
The goal is to make it easier to understand your Worker without digging through multiple tabs. Think of it as a new home base, a place to get a high-level overview on what's going on.
It's the first place you land when you open a Worker in the dashboard, and it gives you an immediate view of what’s going on. You can see requests, errors, and CPU time at a glance. You can view and add bindings, and see recent versions of your app, including who published them.
Navigation is also simpler, with visually distinct tabs at the top of the page. At the bottom right you'll find guided steps for what to do next that are based on the state of your Worker, such as adding a [binding](https://developers.cloudflare.com/workers/runtime-apis/bindings/) or connecting a custom domain.
We plan to add more here over time. Better insights, more controls, and ways to manage your Worker from one page.
If you have feedback or suggestions for the new Overview page or your Cloudflare Workers experience in general, we'd love to hear from you. Join the Cloudflare developer community on [Discord](https://discord.com/channels/595317990191398933/1064502845061210152).
---
title: Browser Support Detection for PQ Encryption on Cloudflare Radar · Changelog
description: New browser support detection for PQ encryption on Radar
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-06-radar-pq-encryption-test/
md: https://developers.cloudflare.com/changelog/2025-10-06-radar-pq-encryption-test/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Browser Support Detection for PQ Encryption on Cloudflare Radar
Oct 06, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) now includes browser detection for Post-quantum (PQ) encryption. The [Post-quantum encryption card](https://radar.cloudflare.com/adoption-and-usage#post-quantum-encryption) now checks whether a user’s browser supports post-quantum encryption. If support is detected, information about the key agreement in use is displayed.

---
title: WAF Release - 2025-10-06 · Changelog
description: Cloudflare WAF managed rulesets 2025-10-06 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-06-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-06-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-06
Oct 06, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s highlights prioritise an emergency Oracle E-Business Suite RCE rule deployed to block active, high-impact exploitation. Also addressed are high-severity Chaos Mesh controller command-injection flaws that enable unauthenticated in-cluster RCE and potential cluster compromise, plus a form-data multipart boundary issue that permits HTTP Parameter Pollution (HPP). Two new generic SQLi detections were added to catch inline-comment obfuscation and information disclosure techniques.
**Key Findings**
* New emergency rule released for Oracle E-Business Suite (CVE-2025-61882) addressing an actively exploited remote code execution vulnerability in core business application modules. Immediate mitigation deployed to protect enterprise workloads.
* Chaos Mesh (CVE-2025-59358,CVE-2025-59359,CVE-2025-59360,CVE-2025-59361): A GraphQL debug endpoint on the Chaos Controller Manager is exposed without authentication; several controller mutations (`cleanTcs`, `killProcesses`, `cleanIptables`) are vulnerable to OS command injection.
* Form-Data (CVE-2025-7783): Attackers who can observe `Math.random()` outputs and control request fields in form-data may exploit this flaw to perform HTTP parameter pollution, leading to request tampering or data manipulation.
* Two new generic SQLi detections added to enhance baseline coverage against inline-comment obfuscation and information disclosure attempts.
**Impact**
* CVE-2025-61882 — Oracle E-Business Suite remote code execution (emergency detection): attacker-controlled input can yield full system compromise, data exfiltration, and operational outage; immediate blocking enforced.
* CVE-2025-59358 / CVE-2025-59359 / CVE-2025-59360 / CVE-2025-59361 — Unauthenticated command-injection in Chaos Mesh controllers allowing remote code execution, cluster compromise, and service disruption (high availability risk).
* CVE-2025-7783 — Predictable multipart boundaries in form-data enabling HTTP Parameter Pollution; results include request tampering, parameter overwrite, and downstream data integrity loss.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 0c9bf31ab6fa41fc8f12daaf8650f52f | 100882 | Chaos Mesh - Missing Authentication - CVE:CVE-2025-59358 | Log | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5d459ed434ed446c9580c73c2b8c3680 | 100883 | Chaos Mesh - Command Injection - CVE:CVE-2025-59359 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | a2591ba5befa4815a6861aefef859a04 | 100884 | Chaos Mesh - Command Injection - CVE:CVE-2025-59361 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 05eea4fabf6f4cf3aac1094b961f26a7 | 100886 | Form-Data - Parameter Pollution - CVE:CVE-2025-7783 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 90514c7810694b188f56979826a4074c | 100888 | Chaos Mesh - Command Injection - CVE:CVE-2025-59360 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 42fbc8c09ec84578b9633ffc31101b2f | 100916 | Oracle E-Business Suite - Remote Code Execution - CVE:CVE-2025-61882 | N/A | Block | This is a New Detection |
| Cloudflare Managed Ruleset | badc687a3ba3420a844220b129aa43c3 | 100917 | Generic Rules - SQLi - Inline Comment Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 28fa27511f29428899ceb5a273c10b6f | 100918 | Generic Rules - SQLi - Information Disclosure | N/A | Disabled | This is a New Detection |
---
title: WAF Release - 2025-10-07 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-10-07 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-07-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-07-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-07 - Emergency
Oct 07, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights multiple critical Cisco vulnerabilities (CVE-2025-20363, CVE-2025-20333, CVE-2025-20362). This flaw stems from improper input validation in HTTP(S) requests. An authenticated VPN user could send crafted requests to execute code as root, potentially compromising the device. The initial two rules were made available on September 28, with a third rule added today, October 7, for more robust protection.
* Cisco (CVE-2025-20333, CVE-2025-20362, CVE-2025-20363): Multiple vulnerabilities that could allow attackers to exploit unsafe deserialization and input validation flaws. Successful exploitation may result in arbitrary code execution, privilege escalation, or command injection on affected systems.
**Impact**
Cisco (CVE-2025-20333, CVE-2025-20362, CVE-2025-20363): Exploitation enables attackers to escalate privileges or achieve remote code execution via command injection. Administrators are strongly advised to apply vendor updates immediately.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 12f808a5315441688f3b7c8a3a4d1bd6 | 100788B | Cisco Secure Firewall Adaptive Security Appliance - Remote Code Execution - CVE:CVE-2025-20333, CVE:CVE-2025-20362, CVE:CVE-2025-20363 | N/A | Block | This is a New Detection |
---
title: Automated reminders for backup codes · Changelog
description: Cloudflare reminds you to download your 2FA recovery keys
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-07-recovery-codes/
md: https://developers.cloudflare.com/changelog/2025-10-07-recovery-codes/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Automated reminders for backup codes
Oct 07, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
The most common reason users contact Cloudflare support is lost two-factor authentication (2FA) credentials. Cloudflare supports both app-based and hardware keys for 2FA, but you could lose access to your account if you lose these. Over the past few weeks, we have been rolling out email and in-product reminders that remind you to also download backup codes (sometimes called recovery keys) that can get you back into your account in the event you lose your 2FA credentials. Download your backup codes now by logging into Cloudflare, then navigating to **Profile** > **Security & Authentication** > **Backup codes**.
#### Sign-in security best practices
Cloudflare is critical infrastructure, and you should protect it as such. Please review the following best practices and make sure you are doing your part to secure your account.
* Use a unique password for every website, including Cloudflare, and store it in a password manager like 1Password or Keeper. These services are cross-platform and simplify the process of managing secure passwords.
* Use 2FA to make it harder for an attacker to get into your account in the event your password is leaked
* Store your backup codes securely. A password manager is the best place since it keeps the backup codes encrypted, but you can also print them and put them somewhere safe in your home.
* If you use an app to manage your 2FA keys, enable cloud backup, so that you don't lose your keys in the event you lose your phone.
* If you use a custom email domain to sign in, [configure SSO](https://developers.cloudflare.com/fundamentals/manage-members/dashboard-sso/).
* If you use a public email domain like Gmail or Hotmail, you can also use social login with Apple, GitHub, or Google to sign in.
* If you manage a Cloudflare account for work:
* Have at least two administrators in case one of them unexpectedly leaves your company
* Use SCIM to automate permissions management for members in your Cloudflare account
---
title: WARP client for Linux (version 2025.8.779.0) · Changelog
description: WARP client for Linux (version 2025.8.779.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-07-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-10-07-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.8.779.0)
Oct 07, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains significant fixes and improvements including an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com/).
**Changes and improvements**
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) has been enhanced for even faster resolution. Proxy mode now supports SOCKS4, SOCK5, and HTTP CONNECT over an L4 tunnel with custom congestion control optimizations instead of the previous L3 tunnel to Cloudflare's network. This has more than doubled Proxy mode throughput in lab speed testing, by an order of magnitude in some cases.
* The MASQUE protocol is now the only protocol that can use [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode). If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new WARP mode or switch to the MASQUE protocol. Otherwise, all devices matching the profile will lose connectivity.
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for macOS (version 2025.8.779.0) · Changelog
description: WARP client for macOS (version 2025.8.779.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-07-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-10-07-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.8.779.0)
Oct 07, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains significant fixes and improvements.
**Changes and improvements**
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) has been enhanced for even faster resolution. Proxy mode now supports SOCKS4, SOCK5, and HTTP CONNECT over an L4 tunnel with custom congestion control optimizations instead of the previous L3 tunnel to Cloudflare's network. This has more than doubled Proxy mode throughput in lab speed testing, by an order of magnitude in some cases.
* The MASQUE protocol is now the only protocol that can use [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode). If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new WARP mode or switch to the MASQUE protocol. Otherwise, all devices matching the profile will lose connectivity.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.8.779.0) · Changelog
description: WARP client for Windows (version 2025.8.779.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-07-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-10-07-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.8.779.0)
Oct 07, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains significant fixes and improvements.
**Changes and improvements**
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) has been enhanced for even faster resolution. Proxy mode now supports SOCKS4, SOCK5, and HTTP CONNECT over an L4 tunnel with custom congestion control optimizations instead of the previous L3 tunnel to Cloudflare's network. This has more than doubled Proxy mode throughput in lab speed testing, by an order of magnitude in some cases.
* The MASQUE protocol is now the only protocol that can use [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode). If you previously configured a device profile to use Proxy mode with Wireguard, you will need to select a new WARP mode or switch to the MASQUE protocol. Otherwise, all devices matching the profile will lose connectivity.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: You can now deploy full-stack apps on Workers using Terraform · Changelog
description: The Cloudflare Terraform provider v5.11.0 now lets you define a
directory of static assets, and handles the heavy lifting of uploading them
and detecting changes.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-09-assets-terraform/
md: https://developers.cloudflare.com/changelog/2025-10-09-assets-terraform/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## You can now deploy full-stack apps on Workers using Terraform
Oct 09, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now upload Workers with [static assets](https://developers.cloudflare.com/workers/static-assets/) (like HTML, CSS, JavaScript, images) with the [Cloudflare Terraform provider v5.11.0](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs), making it even easier to deploy and manage full-stack apps with IaC.
**Previously**, you couldn't use Terraform to upload static assets without writing custom scripts to handle generating an [asset manifest](https://developers.cloudflare.com/workers/static-assets/direct-upload/#upload-manifest), calling the [Cloudflare API to upload assets in chunks](https://developers.cloudflare.com/workers/static-assets/direct-upload/#upload-static-assets), and handling change detection.
**Now**, you simply define the directory where your assets are built, and we handle the rest. Check out the [examples](https://developers.cloudflare.com/changelog/#examples) for what this looks like in Terraform configuration.
You can get started today with [the Cloudflare Terraform provider (v5.11.0)](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs), using either the existing [`cloudflare_workers_script` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_script), or the beta [`cloudflare_worker_version` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker_version).
#### Examples
#### With `cloudflare_workers_script`
Here's how you can use the existing [`cloudflare_workers_script`](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs/resources/workers_script) resource to upload your Worker code and assets in one shot.
```hcl
resource "cloudflare_workers_script" "my_app" {
account_id = var.account_id
script_name = "my-app"
content_file = "./dist/worker/index.js"
content_sha256 = filesha256("./dist/worker/index.js")
main_module = "index.js"
# Just point to your assets directory - that's it!
assets = {
directory = "./dist/static"
}
}
```
#### With `cloudflare_worker`, `cloudflare_worker_version`, and `cloudflare_workers_deployment`
And here's an example using the beta [`cloudflare_worker_version`](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs/resources/worker_version) resource, alongside the [`cloudflare_worker`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker) and [`cloudflare_workers_deployment`](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs/resources/workers_deployment) resources:
```hcl
# This tracks the existence of your Worker, so that you
# can upload code and assets separately from tracking Worker state.
resource "cloudflare_worker" "my_app" {
account_id = var.account_id
name = "my-app"
}
resource "cloudflare_worker_version" "my_app_version" {
account_id = var.account_id
worker_id = cloudflare_worker.my_app.id
# Just point to your assets directory - that's it!
assets = {
directory = "./dist/static"
}
modules = [{
name = "index.js"
content_file = "./dist/worker/index.js"
content_type = "application/javascript+module"
}]
}
resource "cloudflare_workers_deployment" "my_app_deployment" {
account_id = var.account_id
script_name = cloudflare_worker.my_app.name
strategy = "percentage"
versions = [{
version_id = cloudflare_worker_version.my_app_version.id
percentage = 100
}]
}
```
#### What's changed
Under the hood, the Cloudflare Terraform provider now handles the same logic that Wrangler uses for static asset uploads. This includes scanning your assets directory, computing hashes for each file, generating a manifest with file metadata, and calling the Cloudflare API to upload any missing files in chunks. We support large directories with parallel uploads and chunking, and when the asset manifest hash changes, we detect what's changed and trigger an upload for *only* those changed files.
#### Try it out
* Get started with [the Cloudflare Terraform provider (v5.11.0)](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs)
* You can use either the existing [`cloudflare_workers_script` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_script) to upload your Worker code and assets in one resource.
* Or you can use the new beta [`cloudflare_worker_version` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker_version) (along with the [`cloudflare_worker`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker) and [`cloudflare_workers_deployment`](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs/resources/workers_deployment)) resources to more granularly control the lifecycle of each Worker resource.
---
title: Expanded CT log activity insights on Cloudflare Radar · Changelog
description: Expanded Certificate Transparency (CT) log insights in Cloudflare
Radar, including inclusion activity and growth rate
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-09-radar-ct-log-activity-insights/
md: https://developers.cloudflare.com/changelog/2025-10-09-radar-ct-log-activity-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Expanded CT log activity insights on Cloudflare Radar
Oct 09, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) has expanded its Certificate Transparency (CT) log insights with new stats that provide greater visibility into log activity:
* **Log growth rate**: The average throughput of the CT log over the past 7 days, measured in certificates per hour.
* **Included certificate count**: The total number of certificates already included in this CT log.
* **Eligible-for-inclusion certificate count**: The number of certificates eligible for inclusion in this log but not yet included. This metric is based on certificates signed by trusted root CAs within the log’s accepted date range.
* **Last update**: The timestamp of the most recent update to the CT log.
These new statistics have been added to the response of the [Get Certificate Log Details](https://developers.cloudflare.com/api/resources/radar/subresources/ct/subresources/logs/methods/get/) API endpoint, and are displayed on the [CT log information page](https://radar.cloudflare.com/certificate-transparency/log/nimbus2025#log-activity).

---
title: You can now deploy and manage Workflows in Terraform · Changelog
description: You can now deploy and manage Workflows in Terraform, using the
[Cloudflare Terraform provider
v5.11.0](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workflow).
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-09-workflows-terraform/
md: https://developers.cloudflare.com/changelog/2025-10-09-workflows-terraform/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## You can now deploy and manage Workflows in Terraform
Oct 09, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now create and manage [Workflows](https://developers.cloudflare.com/workflows/) using Terraform, now supported in the [Cloudflare Terraform provider v5.11.0](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workflow). Workflows allow you to build durable, multi-step applications -- without needing to worry about retrying failed tasks or managing infrastructure.
Now, you can deploy and manage Workflows through Terraform using the new [`cloudflare_workflow` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workflow):
```hcl
resource "cloudflare_workflow" "my_workflow" {
account_id = var.account_id
workflow_name = "my-workflow"
class_name = "MyWorkflow"
script_name = "my-worker"
}
```
#### Examples
Here are full examples of how to configure `cloudflare_workflow` in Terraform, using the existing [`cloudflare_workers_script` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workers_script), and the beta [`cloudflare_worker_version` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker_version).
#### With `cloudflare_workflow` and `cloudflare_workers_script`
```hcl
resource "cloudflare_workers_script" "workflow_worker" {
account_id = var.cloudflare_account_id
script_name = "my-workflow-worker"
content_file = "${path.module}/../dist/worker/index.js"
content_sha256 = filesha256("${path.module}/../dist/worker/index.js")
main_module = "index.js"
}
resource "cloudflare_workflow" "workflow" {
account_id = var.cloudflare_account_id
workflow_name = "my-workflow"
class_name = "MyWorkflow"
script_name = cloudflare_workers_script.workflow_worker.script_name
}
```
#### With `cloudflare_workflow`, and the new beta resources
You can more granularly control the lifecycle of each Worker resource using the beta [`cloudflare_worker_version`](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs/resources/worker_version) resource, alongside the [`cloudflare_worker`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/worker) and [`cloudflare_workers_deployment`](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs/resources/workers_deployment) resources.
```hcl
resource "cloudflare_worker" "workflow_worker" {
account_id = var.cloudflare_account_id
name = "my-workflow-worker"
}
resource "cloudflare_worker_version" "workflow_worker_version" {
account_id = var.cloudflare_account_id
worker_id = cloudflare_worker.workflow_worker.id
main_module = "index.js"
modules = [{
name = "index.js"
content_file = "${path.module}/../dist/worker/index.js"
content_type = "application/javascript+module"
}]
}
resource "cloudflare_workers_deployment" "workflow_deployment" {
account_id = var.cloudflare_account_id
script_name = cloudflare_worker.workflow_worker.name
strategy = "percentage"
versions = [{
version_id = cloudflare_worker_version.workflow_worker_version.id
percentage = 100
}]
}
resource "cloudflare_workflow" "my_workflow" {
account_id = var.cloudflare_account_id
workflow_name = "my-workflow"
class_name = "MyWorkflow"
script_name = cloudflare_worker.workflow_worker.name
}
```
#### Try it out
* Get started with [the Cloudflare Terraform provider (v5.11.0)](https://registry.terraform.io/providers/cloudflare/cloudflare/5.11.0/docs) and the new [`cloudflare_workflow` resource](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/workflow).
---
title: Worker startup time limit increased to 1 second · Changelog
description: Worker startup time limit has been increased from 400 ms to 1s
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-10-increased-startup-time/
md: https://developers.cloudflare.com/changelog/2025-10-10-increased-startup-time/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Worker startup time limit increased to 1 second
Oct 10, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now upload a Worker that takes up 1 second to parse and execute its global scope. Previously, startup time was limited to 400 ms.
This allows you to run Workers that import more complex packages and execute more code prior to requests being handled.
For more information, see the documentation on [Workers startup limits](https://developers.cloudflare.com/workers/platform/limits/#worker-startup-time).
---
title: New domain categories added · Changelog
description: We have added 3 new domain categories under the Technology parent category
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-10-new-domain-categories/
md: https://developers.cloudflare.com/changelog/2025-10-10-new-domain-categories/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New domain categories added
Oct 10, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
We have added three new domain categories under the Technology parent category, to better reflect online content and improve DNS filtering.
**New categories added**
| Parent ID | Parent Name | Category ID | Category Name |
| - | - | - | - |
| 26 | Technology | 194 | Keep Awake Software |
| 26 | Technology | 192 | Remote Access |
| 26 | Technology | 193 | Shareware/Freeware |
Refer to [Gateway domain categories](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) to learn more.
---
title: WAF Release - 2025-10-13 · Changelog
description: Cloudflare WAF managed rulesets 2025-10-13 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-13-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-13-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-13
Oct 13, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s highlights include a new JinJava rule targeting a sandbox-bypass flaw that could allow malicious template input to escape execution controls. The rule improves detection for unsafe template rendering paths.
**Key Findings**
New WAF rule deployed for JinJava (CVE-2025-59340) to block a sandbox bypass in the template engine that permits attacker-controlled type construction and arbitrary class instantiation; in vulnerable environments this can escalate to remote code execution and full server compromise.
**Impact**
* CVE-2025-59340 — Exploitation enables attacker-supplied type descriptors / Jackson `ObjectMapper` abuse, allowing arbitrary class loading, file/URL access (LFI/SSRF primitives) and, with suitable gadget chains, potential remote code execution and system compromise.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | b327d6442e2d4848b4aab3cbc04bab5f | 100892 | JinJava - SSTI - CVE:CVE-2025-59340 | Log | Block | This is a New Detection |
---
title: Enhanced AI Crawl Control metrics with new drilldowns and filters · Changelog
description: Analyze crawler activity with requests over time charts, referrer
breakdowns, and configurable filters with data export capabilities
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-14-enhanced-metrics-drilldowns/
md: https://developers.cloudflare.com/changelog/2025-10-14-enhanced-metrics-drilldowns/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Enhanced AI Crawl Control metrics with new drilldowns and filters
Oct 14, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
AI Crawl Control now provides enhanced metrics and CSV data exports to help you better understand AI crawler activity across your sites.
#### What's new
#### Track crawler requests over time
Visualize crawler activity patterns over time, and group data by different dimensions:
* **By Crawler** — Track activity from individual AI crawlers (GPTBot, ClaudeBot, Bytespider)
* **By Category** — Analyze crawler purpose or type
* **By Operator** — Discover which companies (OpenAI, Anthropic, ByteDance) are crawling your site
* **By Host** — Break down activity across multiple subdomains
* **By Status Code** — Monitor HTTP response codes to crawlers (200s, 300s, 400s, 500s)

#### Analyze referrer data (Paid plans)
Identify traffic sources with referrer analytics:
* View top referrers driving traffic to your site
* Understand discovery patterns and content popularity from AI operators

#### Export data
Download your filtered view as a CSV:
* Includes all applied filters and groupings
* Useful for custom reporting and deeper analysis
#### Get started
1. Log in to the Cloudflare dashboard, and select your account and domain.
2. Go to **AI Crawl Control** > **Metrics**.
3. Use the grouping tabs to explore different views of your data.
4. Apply filters to focus on specific crawlers, time ranges, or response codes.
5. Select **Download CSV** to export your filtered data for further analysis.
Learn more about [AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control).
---
title: Single sign-on now manageable in the user experience · Changelog
description: Cloudflare single sign-on is available for all users, and can be
quickly configured in the Cloudflare dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-14-sso-self-service-ux/
md: https://developers.cloudflare.com/changelog/2025-10-14-sso-self-service-ux/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Single sign-on now manageable in the user experience
Oct 14, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)

During Birthday Week, we announced that [single sign-on (SSO) is available for free](https://blog.cloudflare.com/enterprise-grade-features-for-all/) to everyone who signs in with a custom email domain and maintains a compatible [identity provider](https://developers.cloudflare.com/cloudflare-one/integrations/identity-providers/). SSO minimizes user friction around login and provides the strongest security posture available. At the time, this could only be configured using the API.
Today, we are launching a new user experience which allows users to manage their SSO configuration from within the Cloudflare dashboard. You can access this by going to **Manage account** > **Members** > **Settings**.
#### For more information
* [Cloudflare dashboard SSO](https://developers.cloudflare.com/fundamentals/manage-members/dashboard-sso/)
---
title: View and edit Durable Object data in UI with Data Studio (Beta) · Changelog
description: Access Durable Objects stored data via Cloudflare dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-16-durable-objects-data-studio/
md: https://developers.cloudflare.com/changelog/2025-10-16-durable-objects-data-studio/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## View and edit Durable Object data in UI with Data Studio (Beta)
Oct 16, 2025
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)

You can now view and write to each Durable Object's storage using a UI editor on the Cloudflare dashboard. Only Durable Objects using [SQLite storage](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage/#create-sqlite-backed-durable-object-class) can use Data Studio.
[Go to **Durable Objects**](https://dash.cloudflare.com/?to=/:account/workers/durable-objects)
Data Studio unlocks easier data access with Durable Objects for prototyping application data models to debugging production storage usage. Before, querying your Durable Objects data required deploying a Worker.
To access a Durable Object, you can provide an object's unique name or ID generated by Cloudflare. Data Studio requires you to have at least the `Workers Platform Admin` role, and all queries are captured with audit logging for your security and compliance needs. Queries executed by Data Studio send requests to your remote, deployed objects and incur normal usage billing.
To learn more, visit the Data Studio [documentation](https://developers.cloudflare.com/durable-objects/observability/data-studio/). If you have feedback or suggestions for the new Data Studio, please share your experience on [Discord](https://discord.com/channels/595317990191398933/773219443911819284)
---
title: Increased HTTP header size limit to 128 KB · Changelog
description: Cloudflare's CDN and Workers platform now support up to 128 KB for
request and response headers
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-16-header-limit-increase/
md: https://developers.cloudflare.com/changelog/2025-10-16-header-limit-increase/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased HTTP header size limit to 128 KB
Oct 16, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
#### CDN now supports 128 KB request and response headers 🚀
We're excited to announce a significant increase in the maximum header size supported by Cloudflare's Content Delivery Network (CDN). Cloudflare now supports up to **128 KB** for both **request and response headers**.
Previously, customers were limited to a total of 32 KB for request or response headers, with a maximum of 16 KB per individual header. Larger headers could cause requests to fail with `HTTP 413` (Request Header Fields Too Large) errors.
***
#### What's new?
* **Support for large headers:** You can now utilize much larger headers, whether as a single large header up to 128 KB or split over multiple headers.
* **Reduces `413` and `520` HTTP errors:** This change drastically reduces the likelihood of customers encountering `HTTP 413` errors from large request headers or `HTTP 520` errors caused by oversized response headers, improving the overall reliability of your web applications.
* **Enhanced functionality:** This is especially beneficial for applications that rely on:
* A large number of cookies.
* Large Content-Security-Policy (CSP) response headers.
* Advanced use cases with Cloudflare Workers that generate large response headers.
This enhancement improves compatibility with Cloudflare's CDN, enabling more use cases that previously failed due to header size limits.
***
To learn more and get started, refer to the [Cloudflare Fundamentals documentation](https://developers.cloudflare.com/fundamentals/reference/connection-limits/#request-limits).
---
title: On-Demand Security Report · Changelog
description: Generate on-demand reports to prove Email security value
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-16-on-demand-security-report/
md: https://developers.cloudflare.com/changelog/2025-10-16-on-demand-security-report/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## On-Demand Security Report
Oct 17, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
You can now generate on-demand security reports directly from the Cloudflare dashboard. This new feature provides a comprehensive overview of your email security posture, making it easier than ever to demonstrate the value of Cloudflare’s Email security to executives and other decision makers.
These reports offer several key benefits:
* **Executive Summary:** Quickly view the performance of Email security with a high-level executive summary.
* **Actionable Insights:** Dive deep into trend data, breakdowns of threat types, and analysis of top targets to identify and address vulnerabilities.
* **Configuration Transparency:** Gain a clear view of your policy, submission, and domain configurations to ensure optimal setup.
* **Account Takeover Risks:** Get a snapshot of your M365 risky users (requires a Microsoft Entra ID P2 license and [M365 SaaS integration](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/microsoft-365/)).

This feature is available across the following Email security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: WARP client for macOS (version 2025.9.173.1) · Changelog
description: WARP client for macOS (version 2025.9.173.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-16-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-10-16-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.9.173.1)
Oct 16, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes, improvements, and new features including Path Maximum Transmission Unit Discovery (PMTUD). With PMTUD enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to debug connectivity issues.
**Changes and improvements**
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to debug connectivity issues.
* Deleting registrations no longer returns an error when succeeding.
* Path Maximum Transmission Unit Discovery (PMTUD) is now used to discover the effective MTU of the connection. This allows the client to improve connection performance optimized for the current network.
**Known issues**
* macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.9.173.1) · Changelog
description: WARP client for Windows (version 2025.9.173.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-16-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-10-16-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.9.173.1)
Oct 16, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes, improvements, and new features including Path Maximum Transmission Unit Discovery (PMTUD). With PMTUD enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to debug connectivity issues.
**Changes and improvements**
* Improvements for [Windows multi-user](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/) to maintain the [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) state when switching between users.
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to debug connectivity issues.
* Deleting registrations no longer returns an error when succeeding.
* Path Maximum Transmission Unit Discovery (PMTUD) is now used to discover the effective MTU of the connection. This allows the client to improve connection performance optimized for the current network.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: New Application Security reports (Closed Beta) · Changelog
description: A monthly recap of your cyber security insights and trends your
Cloudflare account.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-17-app-sec-reports/
md: https://developers.cloudflare.com/changelog/2025-10-17-app-sec-reports/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Application Security reports (Closed Beta)
Oct 17, 2025
[Security Center](https://developers.cloudflare.com/security-center/)
Cloudflare's new **Application Security report**, currently in Closed Beta, is now available in the dashboard.
[Go to **Security reports**](https://dash.cloudflare.com/?to=/:account/security-center/reports)
The reports are generated monthly and provide cyber security insights trends for all of the Enterprise zones in your Cloudflare account.
The reports also include an industry benchmark, comparing your cyber security landscape to peers in your industry.
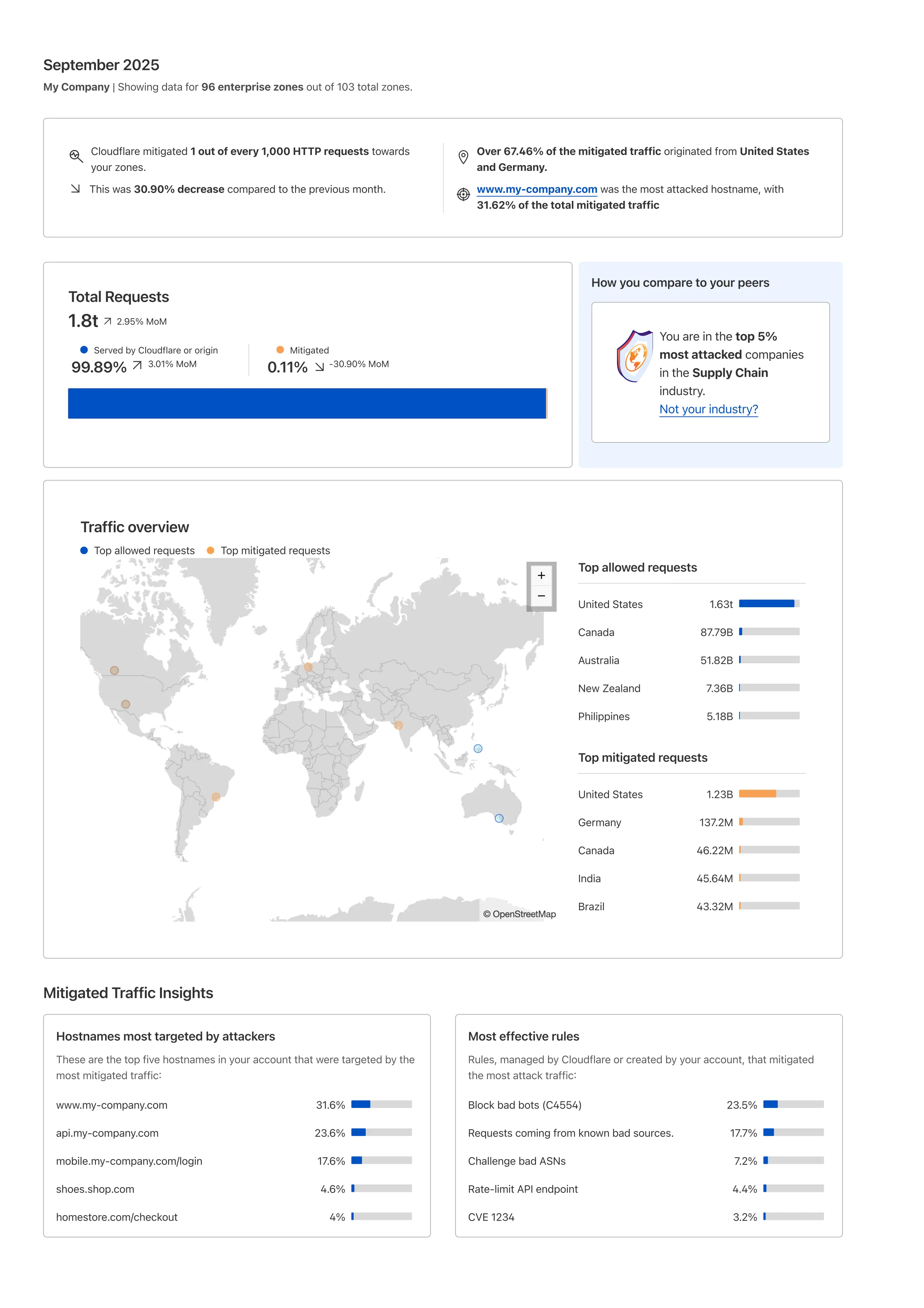
Learn more about the reports by referring to the [Security Reports documentation](https://developers.cloudflare.com/security-center/app-security-reports/).
Use the feedback survey link at the top of the page to help us improve the reports.
---
title: New detections released for WAF managed rulesets · Changelog
description: New Cloudflare WAF managed rulesets release to improve protection
against attacker-controlled payloads
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-17-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-17-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New detections released for WAF managed rulesets
Oct 17, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week we introduced several new detections across Cloudflare Managed Rulesets, expanding coverage for high-impact vulnerability classes such as SSRF, SQLi, SSTI, Reverse Shell attempts, and Prototype Pollution. These rules aim to improve protection against attacker-controlled payloads that exploit misconfigurations or unvalidated input in web applications.
**Key Findings**
New detections added for multiple exploit categories:
SSRF (Server-Side Request Forgery) — new rules targeting both local and cloud metadata abuse patterns (Beta).
SQL Injection (SQLi) — rules for common patterns, sleep/time-based injections, and string/wait function exploitation across headers and URIs.
SSTI (Server-Side Template Injection) — arithmetic-based probe detections introduced across URI, header, and body fields.
Reverse Shell and XXE payloads — enhanced heuristics for command execution and XML external entity misuse.
Prototype Pollution — new Beta rule identifying common JSON payload structures used in object prototype poisoning.
PHP Wrapper Injection and HTTP Parameter Pollution detections — to catch path traversal and multi-parameter manipulation attempts.
Anomaly Header Checks — detecting CRLF injection attempts in header names.
**Impact**
These updates help detect multi-vector payloads that blend SSRF + RCE or SQLi + SSTI attacks, especially in cloud-hosted applications with exposed metadata endpoints or unsafe template rendering.
Prototype Pollution and HTTP parameter pollution rules address emerging JavaScript supply-chain exploitation patterns increasingly seen in real-world incidents.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 72f0ff933fb0492eb71cda50589f2a1d | N/A | Anomaly:Header - name - CR, LF | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5d0377e4435f467488614170132fab7e | N/A | Generic Rules - Reverse Shell - Body | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 54e32f7f802c4a699182e8921a027008 | N/A | Generic Rules - Reverse Shell - Header | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 7cbda8dbafbc465d9b64a8f2958d0486 | N/A | Generic Rules - Reverse Shell - URI | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | b9f3420674cf481da32333dc8e0cf7ad | N/A | Generic Rules - XXE - Body | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | ad55483512f0440b81426acdbf8aab5e | N/A | Generic Rules - SQLi - Common Patterns - Header URI | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 849c0618d1674f1c92ba6f9b2e466337 | N/A | Generic Rules - SQLi - Sleep Function - Header URI | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 1b4db4c4bd0649c095c27c6cb686ab47 | N/A | Generic Rules - SQLi - String Function - Header URI | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | fa2055b84af94ba4b925f834b0633709 | N/A | Generic Rules - SQLi - WaitFor Function - Header URI | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 158177dec2504acdba1f2da201a076eb | N/A | SSRF - Local - Beta | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 98bfd6bb46074d5b8d1c4b39743a63ec | N/A | SSRF - Local - 2 - Beta | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 54e1733b10da4a599e06c6fbc2e84e2d | N/A | SSRF - Cloud - Beta | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | ecd26d61a75e46f6a4449a06ab8af26f | N/A | SSRF - Cloud - 2 - Beta | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | c16f4e133c4541f293142d02e6e8dc5b | N/A | SSTI - Arithmetic Probe - URI | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | f4fd9904e7624666b8c49cd62550d794 | N/A | SSTI - Arithmetic Probe - Header | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 5c0875604f774c36a4f9b69c659d12a6 | N/A | SSTI - Arithmetic Probe - Body | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | fae6fa37ae9249d58628e54b1a3e521e | N/A | PHP Wrapper Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 9c02e585db34440da620eb668f76bd74 | N/A | PHP Wrapper Injection | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | cb67fe56a84747b8b64277dc091e296d | N/A | HTTP parameter pollution | N/A | Disabled | This is a New Detection |
| Cloudflare Managed Ruleset | 443b54d984944cd69043805ee34214ef | N/A | Prototype Pollution - Common Payloads - Beta | N/A | Disabled | This is a New Detection |
---
title: Schedule DNS policies from the UI · Changelog
description: All users can now create and manage scheduled DNS policies directly
from the Cloudflare One dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-20-schedule-dns-policies-from-the-ui/
md: https://developers.cloudflare.com/changelog/2025-10-20-schedule-dns-policies-from-the-ui/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Schedule DNS policies from the UI
Oct 20, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
Admins can now create [scheduled DNS policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/timed-policies/) directly from the Zero Trust dashboard, without using the API. You can configure policies to be active during specific, recurring times, such as blocking social media during business hours or gaming sites on school nights.
* **Preset Schedules**: Use built-in templates for common scenarios like Business Hours, School Days, Weekends, and more.
* **Custom Schedules**: Define your own schedule with specific days and up to three non-overlapping time ranges per day.
* **Timezone Control**: Choose to enforce a schedule in a specific timezone (for example, US Eastern) or based on the local time of each user.
* **Combined with Duration**: Policies can have both a schedule and a duration. If both are set, the duration's expiration takes precedence.
You can see the flow in the demo GIF:

This update makes time-based DNS policies accessible to all Gateway customers, removing the technical barrier of the API.
---
title: WAF Release - 2025-10-20 · Changelog
description: Cloudflare WAF managed rulesets 2025-10-20 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-20-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-20-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-20
Oct 20, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s update introduces an enhanced rule that expands detection coverage for a critical vulnerability in Oracle E-Business Suite. It also improves an existing rule to provide more reliable coverage in request processing.
**Key Findings**
New WAF rule deployed for Oracle E-Business Suite (CVE-2025-61882) to block unauthenticated attacker's network access via HTTP to compromise Oracle Concurrent Processing. If successfully exploited, this vulnerability may result in remote code execution.
**Impact**
* Successful exploitation of CVE-2025-61882 allows unauthenticated attackers to execute arbitrary code remotely by chaining multiple weaknesses, enabling lateral movement into internal services, data exfiltration, and large-scale extortionware deployment within Oracle E-Business Suite environments.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 933fc13202cd4e8ba498c0f32b4101ab | 100598A | Remote Code Execution - Common Bash Bypass - Beta | Log | Block | This rule is merged into the original rule "Remote Code Execution - Common Bash Bypass" (ID: f8238867ed3e4d3a9a7b731a50cec478 ) |
| Cloudflare Managed Ruleset | 185b5df42d1e44e0aeb8f8b8a1118614 | 100916A | Oracle E-Business Suite - Remote Code Execution - CVE:CVE-2025-61882 - 2 | Log | Block | This is a New Detection |
| Cloudflare Managed Ruleset | 646bccf7e9dc46918a4150d6c22b51d3 | N/A | HTTP Truncated | N/A | Disabled | This is a New Detection |
---
title: New Robots.txt tab for tracking crawler compliance · Changelog
description: Monitor robots.txt file health, track crawler violations, and gain
visibility into how AI crawlers interact with your directives.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-21-track-robots-txt/
md: https://developers.cloudflare.com/changelog/2025-10-21-track-robots-txt/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Robots.txt tab for tracking crawler compliance
Oct 21, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
AI Crawl Control now includes a **Robots.txt** tab that provides insights into how AI crawlers interact with your `robots.txt` files.
#### What's new
The Robots.txt tab allows you to:
* Monitor the health status of `robots.txt` files across all your hostnames, including HTTP status codes, and identify hostnames that need a `robots.txt` file.
* Track the total number of requests to each `robots.txt` file, with breakdowns of successful versus unsuccessful requests.
* Check whether your `robots.txt` files contain [Content Signals](https://contentsignals.org/) directives for AI training, search, and AI input.
* Identify crawlers that request paths explicitly disallowed by your `robots.txt` directives, including the crawler name, operator, violated path, specific directive, and violation count.
* Filter `robots.txt` request data by crawler, operator, category, and custom time ranges.
#### Take action
When you identify non-compliant crawlers, you can:
* Block the crawler in the [Crawlers tab](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/)
* Create custom [WAF rules](https://developers.cloudflare.com/waf/) for path-specific security
* Use [Redirect Rules](https://developers.cloudflare.com/rules/url-forwarding/) to guide crawlers to appropriate areas of your site
To get started, go to **AI Crawl Control** > **Robots.txt** in the Cloudflare dashboard. Learn more in the [Track robots.txt documentation](https://developers.cloudflare.com/ai-crawl-control/features/track-robots-txt/).
---
title: WAF Release - 2025-10-23 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-10-23 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-23-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-23-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-23 - Emergency
Oct 23, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights enhancements to detection signatures improving coverage for vulnerabilities in Adobe Commerce and Magento Open Source, linked to CVE-2025-54236.
**Key Findings**
This vulnerability allows unauthenticated attackers to take over customer accounts through the Commerce REST API and, in certain configurations, may lead to remote code execution. The latest update enhances detection logic to provide more resilient protection against exploitation attempts.
**Impact**
Adobe Commerce (CVE-2025-54236): Exploitation may allow attackers to hijack sessions, execute arbitrary commands, steal data, and disrupt storefronts, resulting in confidentiality and integrity risks for merchants. Administrators are strongly encouraged to apply vendor patches without delay.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 6e04fa2b9eb34fb088034d3fc6ef59a1 | N/A | Adobe Commerce - Remote Code Execution - CVE:CVE-2025-54236 | N/A | Block | This is a New Detection |
---
title: "Workers AI Markdown Conversion: New endpoint to list supported formats ·
Changelog"
description: You can now programmatically get a list of all supported file
formats that can be converted by our Markdown Conversion utility.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-23-new-markdown-conversion-endpoint/
md: https://developers.cloudflare.com/changelog/2025-10-23-new-markdown-conversion-endpoint/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers AI Markdown Conversion: New endpoint to list supported formats
Oct 23, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
Developers can now programmatically retrieve a list of all file formats supported by the [Markdown Conversion utility](https://developers.cloudflare.com/workers-ai/features/markdown-conversion/) in Workers AI.
You can use the [`env.AI`](https://developers.cloudflare.com/workers-ai/configuration/bindings/) binding:
```typescript
await env.AI.toMarkdown().supported()
```
Or call the REST API:
```bash
curl https://api.cloudflare.com/client/v4/accounts/{ACCOUNT_ID}/ai/tomarkdown/supported \
-H 'Authorization: Bearer {API_TOKEN}'
```
Both return a list of file formats that users can convert into Markdown:
```json
[
{
"extension": ".pdf",
"mimeType": "application/pdf",
},
{
"extension": ".jpeg",
"mimeType": "image/jpeg",
},
...
]
```
Learn more about our [Markdown Conversion utility](https://developers.cloudflare.com/workers-ai/features/markdown-conversion/).
---
title: Workers Preview URL default behavior now matches your workers.dev setting
· Changelog
description: If a Workers Preview URL setting is not explicitly configured, its
default behavior will now match the setting of the workers.dev subdomain.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-23-preview-url-default-behavior/
md: https://developers.cloudflare.com/changelog/2025-10-23-preview-url-default-behavior/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers Preview URL default behavior now matches your workers.dev setting
Oct 23, 2025
[Workers](https://developers.cloudflare.com/workers/)
We have updated the default behavior for Cloudflare Workers [Preview URLs](https://developers.cloudflare.com/workers/configuration/previews/). **Going forward, if a preview URL setting is not [explicitly configured](https://developers.cloudflare.com/workers/configuration/previews/#toggle-preview-urls-enable-or-disable) during deployment, its default behavior will automatically match the setting of your [`workers.dev` subdomain](https://developers.cloudflare.com/workers/configuration/routing/workers-dev/).**
This change is intended to provide a more intuitive and secure experience by aligning your preview URL's default state with your `workers.dev` configuration to prevent cases where a preview URL might remain public even after you disabled your `workers.dev` route.
**What this means for you:**
* **If neither setting is configured:** both the workers.dev route and the preview URL will default to enabled
* **If your workers.dev route is enabled and you do not explicitly set Preview URLs to enabled or disabled:** Preview URLs will default to enabled
* **If your workers.dev route is disabled and you do not explicitly set Preview URLs to enabled or disabled:** Preview URLs will default to disabled
You can override the default setting by explicitly enabling or disabling the preview URL in your Worker's configuration through the [API](https://developers.cloudflare.com/api/resources/workers/subresources/scripts/subresources/subdomain/), [Dashboard](https://developers.cloudflare.com/workers/configuration/previews/#from-the-dashboard), or [Wrangler](https://developers.cloudflare.com/workers/configuration/previews/#from-the-wrangler-configuration-file).
**Wrangler Version Behavior**
The default behavior depends on the version of Wrangler you are using. This new logic applies to the latest version. Here is a summary of the behavior across different versions:
* **Before v4.34.0:** Preview URLs defaulted to enabled, regardless of the workers.dev setting.
* **v4.34.0 up to (but not including) v4.44.0:** Preview URLs defaulted to disabled, regardless of the workers.dev setting.
* **v4.44.0 or later:** Preview URLs now default to matching your workers.dev setting.
**Why we’re making this change**
In July, [we introduced preview URLs to Workers](https://developers.cloudflare.com/changelog/2025-07-23-workers-preview-urls/), which let you preview code changes before deploying to production. This made disabling your Worker’s workers.dev URL an ambiguous action — the preview URL, served as a subdomain of `workers.dev` (ex: `preview-id-worker-name.account-name.workers.dev`) would still be live even if you had disabled your Worker’s `workers.dev` route. If you misinterpreted what it meant to disable your `workers.dev` route, you might unintentionally leave preview URLs enabled when you didn’t mean to, and expose them to the public Internet.
To address this, we made a [one-time update](https://developers.cloudflare.com/changelog/2025-09-17-update-preview-url-setting/) to disable preview URLs on existing Workers that had their workers.dev route disabled and changed the default behavior to be disabled for all new deployments where a preview URL setting was not explicitly configured.
While this change helped secure many customers, it was disruptive for customers who keep their `workers.dev` route enabled and actively use the preview functionality, as it now required them to explicitly enable preview URLs on every redeployment.This new, more intuitive behavior ensures that your preview URL settings align with your `workers.dev` configuration by default, providing a more secure and predictable experience.
**Securing access to `workers.dev` and preview URL endpoints**
To further secure your `workers.dev` subdomain and preview URL, you can [enable Cloudflare Access with a single click](https://developers.cloudflare.com/changelog/2025-10-03-one-click-access-for-workers/) in your Worker's settings to limit access to specific users or groups.
---
title: Automatic resource provisioning for KV, R2, and D1 · Changelog
description: Wrangler can now automatically provision KV, R2, and D1 resources
when deploying your Worker
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-24-automatic-resource-provisioning/
md: https://developers.cloudflare.com/changelog/2025-10-24-automatic-resource-provisioning/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Automatic resource provisioning for KV, R2, and D1
Oct 24, 2025
[Workers](https://developers.cloudflare.com/workers/)
Previously, if you wanted to develop or deploy a worker with attached resources, you'd have to first manually create the desired resources. Now, if your Wrangler configuration file includes a KV namespace, D1 database, or R2 bucket that does not yet exist on your account, you can develop locally and deploy your application seamlessly, without having to run additional commands.
Automatic provisioning is launching as an open beta, and we'd love to hear your feedback to help us make improvements! It currently works for KV, R2, and D1 bindings. You can disable the feature using the `--no-x-provision` flag.
To use this feature, update to wrangler\@4.45.0 and add bindings to your config file *without* resource IDs e.g.:
```jsonc
{
"kv_namespaces": [{ "binding": "MY_KV" }],
"d1_databases": [{ "binding": "MY_DB" }],
"r2_buckets": [{ "binding": "MY_R2" }],
}
```
`wrangler dev` will then automatically create these resources for you locally, and on your next run of `wrangler deploy`, Wrangler will call the Cloudflare API to create the requested resources and link them to your Worker.
Though resource IDs will be automatically written back to your Wrangler config file after resource creation, resources will stay linked across future deploys even without adding the resource IDs to the config file. This is especially useful for shared templates, which now no longer need to include account-specific resource IDs when adding a binding.
---
title: WAF Release - 2025-10-24 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-10-24 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-24-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-24-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-24 - Emergency
Oct 24, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces a new detection signature that enhances coverage for a critical vulnerability in Windows Server Update Services (WSUS), tracked as CVE-2025-59287.
**Key Findings**
The vulnerability allows unauthenticated attackers to potentially achieve remote code execution. The updated detection logic strengthens defenses by improving resilience against exploitation attempts targeting this flaw.
**Impact**
Successful exploitation of CVE-2025-59287 could enable attackers to hijack sessions, execute arbitrary commands, exfiltrate sensitive data, and disrupt storefront operations. These actions pose significant confidentiality and integrity risks to affected environments. Administrators should apply vendor patches immediately to mitigate exposure.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 5eaeb5ea6e5a4bce867eb3ffbd72ba08 | N/A | Windows Server - Deserialization - CVE:CVE-2025-59287 | N/A | Block | This is a New Detection |
---
title: Build TanStack Start apps with the Cloudflare Vite plugin · Changelog
description: TanStack Start can now be used with the Cloudflare Vite plugin
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-24-tanstack-start/
md: https://developers.cloudflare.com/changelog/2025-10-24-tanstack-start/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Build TanStack Start apps with the Cloudflare Vite plugin
Oct 24, 2025
[Workers](https://developers.cloudflare.com/workers/)
The [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/) now supports [TanStack Start](https://tanstack.com/start/) apps. Get started with new or existing projects.
#### New projects
Create a new TanStack Start project that uses the Cloudflare Vite plugin via the `create-cloudflare` CLI:
* npm
```sh
npm create cloudflare@latest -- my-tanstack-start-app --framework=tanstack-start
```
* yarn
```sh
yarn create cloudflare my-tanstack-start-app --framework=tanstack-start
```
* pnpm
```sh
pnpm create cloudflare@latest my-tanstack-start-app --framework=tanstack-start
```
#### Existing projects
Migrate an existing TanStack Start project to use the Cloudflare Vite plugin:
1. Install `@cloudflare/vite-plugin` and `wrangler`
* npm
```sh
npm i -D @cloudflare/vite-plugin wrangler
```
* yarn
```sh
yarn add -D @cloudflare/vite-plugin wrangler
```
* pnpm
```sh
pnpm add -D @cloudflare/vite-plugin wrangler
```
1. Add the Cloudflare plugin to your Vite config
```ts
import { defineConfig } from "vite";
import { tanstackStart } from "@tanstack/react-start/plugin/vite";
import viteReact from "@vitejs/plugin-react";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [
cloudflare({ viteEnvironment: { name: "ssr" } }),
tanstackStart(),
viteReact(),
],
});
```
1. Add your Worker config file
* wrangler.jsonc
```jsonc
{
"$schema": "./node_modules/wrangler/config-schema.json",
"name": "my-tanstack-start-app",
"compatibility_date": "2026-02-07",
"compatibility_flags": [
"nodejs_compat"
],
"main": "@tanstack/react-start/server-entry"
}
```
* wrangler.toml
```toml
"$schema" = "./node_modules/wrangler/config-schema.json"
name = "my-tanstack-start-app"
compatibility_date = "2026-02-07"
compatibility_flags = [ "nodejs_compat" ]
main = "@tanstack/react-start/server-entry"
```
1. Modify the scripts in your `package.json`
```json
{
"scripts": {
"dev": "vite dev",
"build": "vite build && tsc --noEmit",
"start": "node .output/server/index.mjs",
"preview": "vite preview",
"deploy": "npm run build && wrangler deploy",
"cf-typegen": "wrangler types"
}
}
```
See the [TanStack Start framework guide](https://developers.cloudflare.com/workers/framework-guides/web-apps/tanstack-start/) for more info.
---
title: Reranking and API-based system prompt configuration in AI Search · Changelog
description: Improve result accuracy with reranking and dynamically control AI
Search responses by setting system prompts in API requests.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-27-ai-search-reranking-system-prompt/
md: https://developers.cloudflare.com/changelog/2025-10-27-ai-search-reranking-system-prompt/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Reranking and API-based system prompt configuration in AI Search
Oct 28, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
[AI Search](https://developers.cloudflare.com/ai-search/) now supports reranking for improved retrieval quality and allows you to set the system prompt directly in your API requests.
#### Rerank for more relevant results
You can now enable [reranking](https://developers.cloudflare.com/ai-search/configuration/reranking/) to reorder retrieved documents based on their semantic relevance to the user’s query. Reranking helps improve accuracy, especially for large or noisy datasets where vector similarity alone may not produce the optimal ordering.
You can enable and configure reranking in the dashboard or directly in your API requests:
```javascript
const answer = await env.AI.autorag("my-autorag").aiSearch({
query: "How do I train a llama to deliver coffee?",
model: "@cf/meta/llama-3.3-70b-instruct-fp8-fast",
reranking: {
enabled: true,
model: "@cf/baai/bge-reranker-base"
}
});
```
#### Set system prompts in API
Previously, [system prompts](https://developers.cloudflare.com/ai-search/configuration/system-prompt/) could only be configured in the dashboard. You can now define them directly in your API requests, giving you per-query control over behavior. For example:
```javascript
// Dynamically set query and system prompt in AI Search
async function getAnswer(query, tone) {
const systemPrompt = `You are a ${tone} assistant.`;
const response = await env.AI.autorag("my-autorag").aiSearch({
query: query,
system_prompt: systemPrompt
});
return response;
}
// Example usage
const query = "What is Cloudflare?";
const tone = "friendly";
const answer = await getAnswer(query, tone);
console.log(answer);
```
Learn more about [Reranking](https://developers.cloudflare.com/ai-search/configuration/reranking/) and [System Prompt](https://developers.cloudflare.com/ai-search/configuration/system-prompt/) in AI Search.
---
title: TLD Insights in Cloudflare Radar · Changelog
description: New Top-Level Domain (TLD) insights in Cloudflare Radar, including
popularity, traffic, and security
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-27-radar-tld-insights/
md: https://developers.cloudflare.com/changelog/2025-10-27-radar-tld-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## TLD Insights in Cloudflare Radar
Oct 27, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) now introduces Top-Level Domain (TLD) insights, providing visibility into popularity based on the DNS magnitude metric, detailed TLD information including its type, manager, DNSSEC support, RDAP support, and WHOIS data, and trends such as DNS query volume and geographic distribution observed by the [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/) DNS resolver.
The following dimensions were added to the Radar DNS API, specifically, to the [`/dns/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/methods/summary_v2/) and [`/dns/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/dns/methods/timeseries_groups_v2/) endpoints:
* `tld`: Top-level domain extracted from DNS queries; can also be used as a filter.
* `tld_dns_magnitude`: Top-level domain ranking by [DNS magnitude](https://developers.cloudflare.com/radar/glossary#dns-magnitude).
And the following endpoints were added:
* [`/tlds`](https://developers.cloudflare.com/api/resources/radar/subresources/tlds/methods/list/) - Lists all TLDs.
* [`/tlds/{tld}`](https://developers.cloudflare.com/api/resources/radar/subresources/tlds/methods/get/) - Retrieves information about a specific TLD.

Learn more about the new Radar DNS insights in our [blog post](https://blog.cloudflare.com/introducing-tld-insights-on-cloudflare-radar/), and check out the [new Radar page](https://radar.cloudflare.com/tlds).
---
title: Cloudforce One RFI tokens are now visible in the dashboard · Changelog
description: The Requests for Information (RFI) dashboard now shows the number
of tokens used for each RFI
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-27-rfi-tokens-in-dash/
md: https://developers.cloudflare.com/changelog/2025-10-27-rfi-tokens-in-dash/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudforce One RFI tokens are now visible in the dashboard
Oct 27, 2025
[Security Center](https://developers.cloudflare.com/security-center/)
The Requests for Information (RFI) dashboard now shows users the number of tokens used by each submitted RFI to better understand usage of tokens and how they relate to each request submitted.
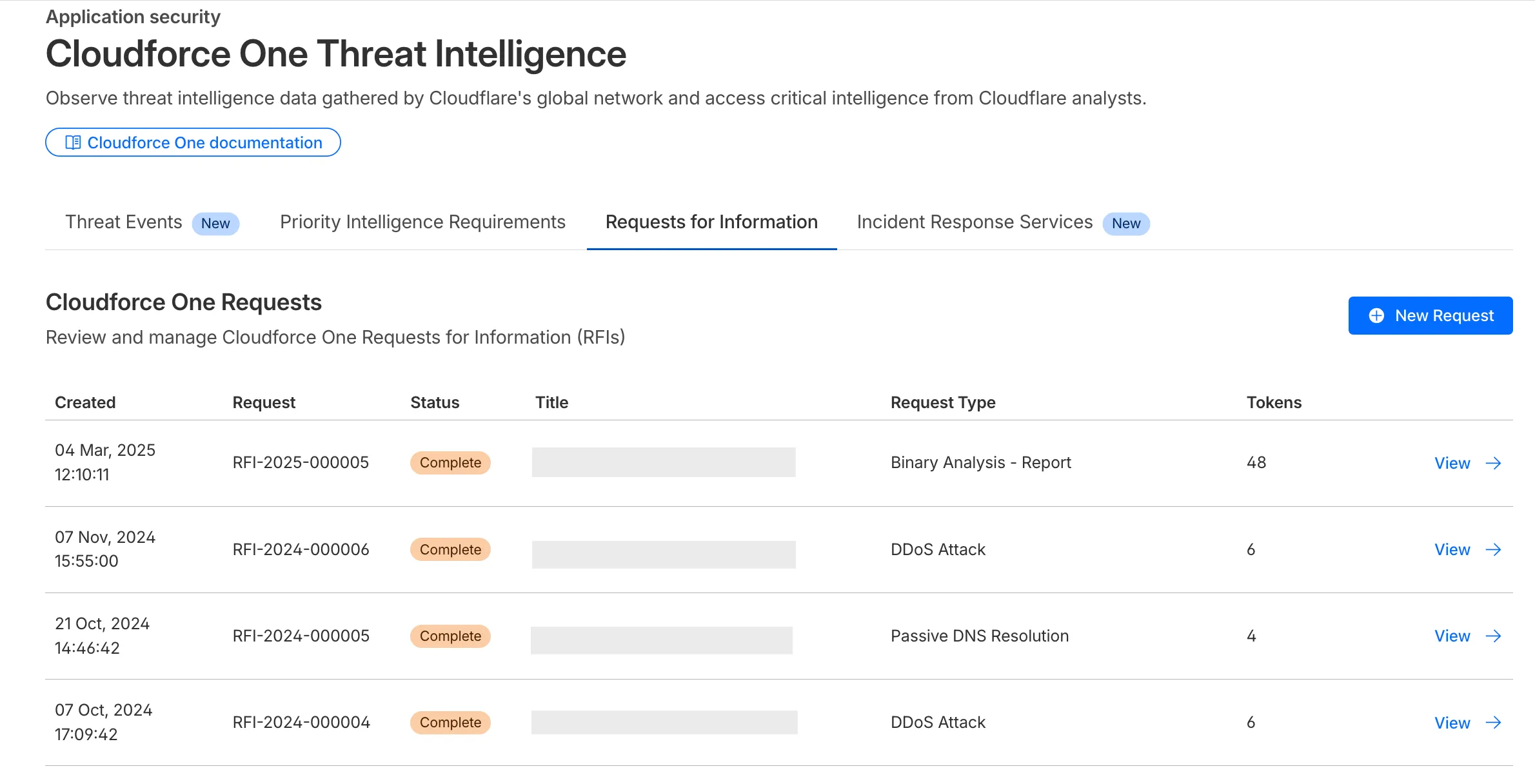
What’s new:
* Users can now see the number of tokens used for a submitted request for information.
* Users can see the remaining tokens allocated to their account for the quarter.
* Users can only select the Routine priority for the `Strategic Threat Research` request type.
Cloudforce One subscribers can try it now in [Application Security > Threat Intelligence > Requests for Information](https://dash.cloudflare.com/?to=/:account/security-center/threat-intelligence/requests).
---
title: Azure Sentinel Connector · Changelog
description: New Azure Sentinel Connector based on Codeless Connector Framework (CCF)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-27-sentinel-connector/
md: https://developers.cloudflare.com/changelog/2025-10-27-sentinel-connector/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Azure Sentinel Connector
Oct 27, 2025
[Logs](https://developers.cloudflare.com/logs/)
Logpush now supports integration with [Microsoft Sentinel](https://www.microsoft.com/en-us/security/business/siem-and-xdr/microsoft-sentinel).The new Azure Sentinel Connector built on Microsoft’s Codeless Connector Framework (CCF), is now avaialble. This solution replaces the previous Azure Functions-based connector, offering significant improvements in security, data control, and ease of use for customers. Logpush customers can send logs to Azure Blob Storage and configure this new Sentinel Connector to ingest those logs directly into Microsoft Sentinel.
This upgrade significantly streamlines log ingestion, improves security, and provides greater control:
* Simplified Implementation: Easier for engineering teams to set up and maintain.
* Cost Control: New support for Data Collection Rules (DCRs) allows you to filter and transform logs at ingestion time, offering potential cost savings.
* Enhanced Security: CCF provides a higher level of security compared to the older Azure Functions connector.
* ata Lake Integration: Includes native integration with Data Lake.
Find the new solution [here](https://marketplace.microsoft.com/en-us/product/azure-application/cloudflare.azure-sentinel-solution-cloudflare-ccf?tab=Overview) and refer to the [Cloudflare's developer documention](https://developers.cloudflare.com/analytics/analytics-integrations/sentinel/#supported-logs:~:text=WorkBook%20fields,-Analytic%20rules)for more information on the connector, including setup steps, supported logs and Microsfot's resources.
---
title: Access private hostname applications support all ports/protocols · Changelog
description: Cloudflare Access for private hostname applications can now secure
traffic on all ports and protocols. 🔒
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-28-access-application-support-for-all-ports-and-protocols/
md: https://developers.cloudflare.com/changelog/2025-10-28-access-application-support-for-all-ports-and-protocols/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Access private hostname applications support all ports/protocols
Oct 28, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
[Cloudflare Access for private hostname applications](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/non-http/self-hosted-private-app/) can now secure traffic on all ports and protocols.
Previously, applying Zero Trust policies to private applications required the application to use HTTPS on port `443` and support Server Name Indicator (SNI).
This update removes that limitation. As long as the application is reachable via a Cloudflare off-ramp, you can now enforce your critical security controls — like single sign-on (SSO), MFA, device posture, and variable session lengths — to any private application. This allows you to extend Zero Trust security to services like SSH, RDP, internal databases, and other non-HTTPS applications.

For example, you can now create a self-hosted application in Access for `ssh.testapp.local` running on port `22`. You can then build a policy that only allows engineers in your organization to connect after they pass an SSO/MFA check and are using a corporate device.
This feature is generally available across all plans.
---
title: CASB introduces new granular roles · Changelog
description: Cloudflare CASB adds two new granular roles, CASB Read and CASB,
for more precise user access control.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-28-casb-roles/
md: https://developers.cloudflare.com/changelog/2025-10-28-casb-roles/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## CASB introduces new granular roles
Oct 28, 2025
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
Cloudflare CASB (Cloud Access Security Broker) now supports two new granular roles to provide more precise access control for your security teams:
* **Cloudflare CASB Read:** Provides read-only access to view CASB findings and dashboards. This role is ideal for security analysts, compliance auditors, or team members who need visibility without modification rights.
* **Cloudflare CASB:** Provides full administrative access to configure and manage all aspects of the CASB product.
These new roles help you better enforce the principle of least privilege. You can now grant specific members access to CASB security findings without assigning them broader permissions, such as the **Super Administrator** or **Administrator** roles.
To enable [Data Loss Prevention (DLP)](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/dlp-profiles/), scans in CASB, account members will need the **Cloudflare Zero Trust** role.
You can find these new roles when inviting members or creating API tokens in the Cloudflare dashboard under **Manage Account** > **Members**.
To learn more about managing roles and permissions, refer to the [Manage account members and roles documentation](https://developers.cloudflare.com/fundamentals/manage-members/roles/).
---
title: Increased Workflows instance and concurrency limits · Changelog
description: Higher concurrency and creation limits for Workflow instances now available
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-28-raising-limits/
md: https://developers.cloudflare.com/changelog/2025-10-28-raising-limits/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased Workflows instance and concurrency limits
Oct 31, 2025
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
We've raised the [Cloudflare Workflows](https://developers.cloudflare.com/workflows/) account-level limits for all accounts on the [Workers paid plan](https://developers.cloudflare.com/workers/platform/pricing/):
* **Instance creation rate** increased from 100 workflow instances per 10 seconds to 100 instances per second
* **Concurrency limit** increased from 4,500 to 10,000 workflow instances per account
These increases mean you can create new instances up to 10x faster, and have more workflow instances concurrently executing. To learn more and get started with Workflows, refer to [the getting started guide](https://developers.cloudflare.com/workflows/get-started/guide/).
If your application requires a higher limit, fill out the [Limit Increase Request Form](https://developers.cloudflare.com/workers/platform/limits/) or contact your account team. Please refer to [Workflows pricing](https://developers.cloudflare.com/workflows/reference/pricing/) for more information.
---
title: Access Workers preview URLs from the Build details page · Changelog
description: You can now access Preview URLs directly from the build details page
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-30-builds-preview/
md: https://developers.cloudflare.com/changelog/2025-10-30-builds-preview/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Access Workers preview URLs from the Build details page
Oct 30, 2025
[Workers](https://developers.cloudflare.com/workers/)
You can now access [preview URLs](https://developers.cloudflare.com/workers/configuration/previews/) directly from the build details page, making it easier to test your changes when reviewing builds in the dashboard.
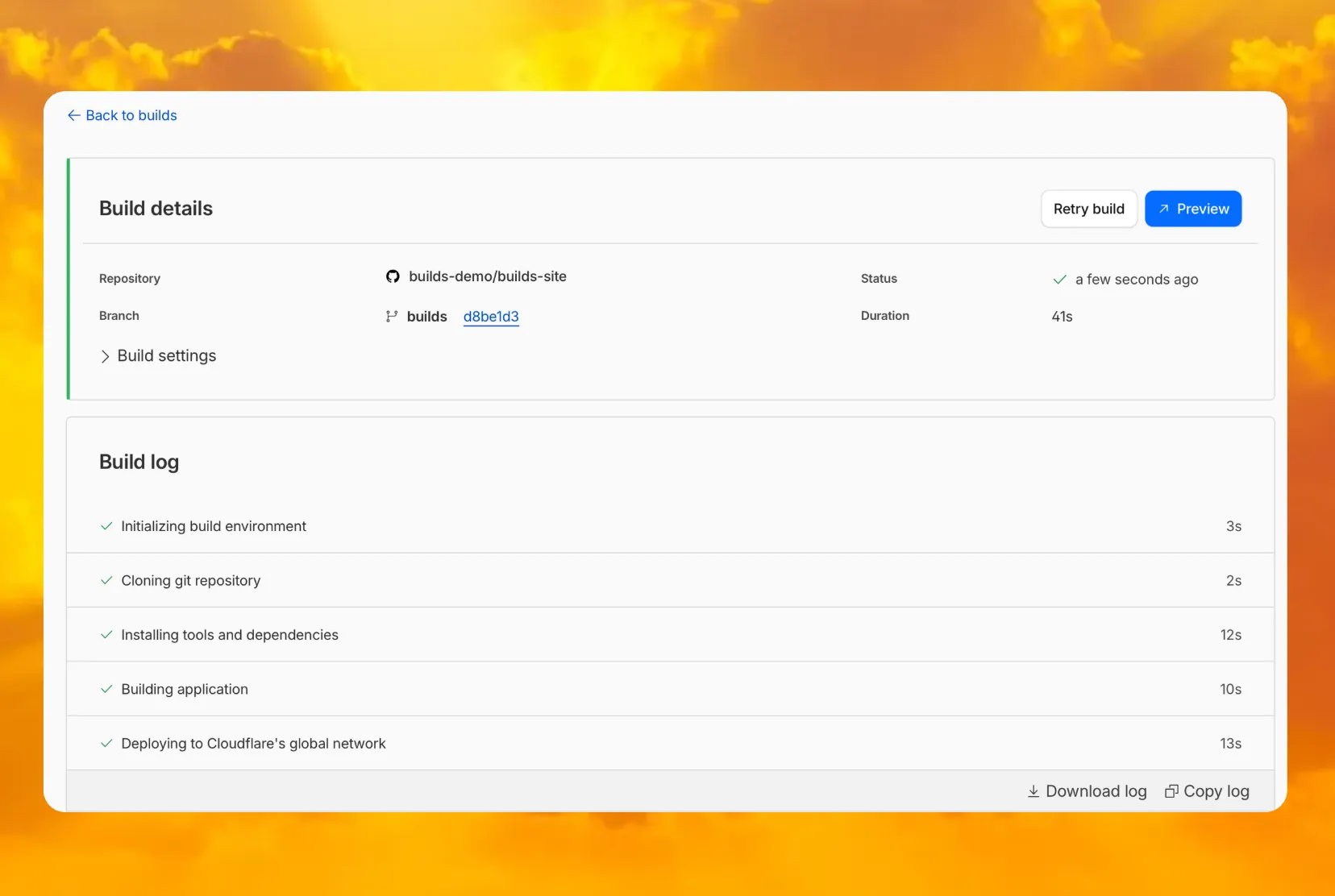
**What's new**
* A **Preview** button now appears in the top-right corner of the build details page for successful builds
* Click it to instantly open the latest preview URL
* Matches the same experience you're familiar with from Pages
---
title: Introducing email two-factor authentication · Changelog
description: Cloudflare now offers email two-factor authentication to protect your account
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-30-email-2fa/
md: https://developers.cloudflare.com/changelog/2025-10-30-email-2fa/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Introducing email two-factor authentication
Oct 30, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
Two-factor authentication (2FA) is one of the best ways to protect your account from the risk of account takeover. Cloudflare has offered phishing resistant 2FA options including hardware based keys (for example, a Yubikey) and app based TOTP (time-based one-time password) options which use apps like Google or Microsoft's Authenticator app. Unfortunately, while these solutions are very secure, they can be lost if you misplace the hardware based key, or lose the phone which includes that app. The result is that users sometimes get locked out of their accounts and need to contact support.
Today, we are announcing the addition of email as a 2FA factor for all Cloudflare accounts. Email 2FA is in wide use across the industry as a least common denominator for 2FA because it is low friction, loss resistant, and still improves security over username/password login only. We also know that most commercial email providers already require 2FA, so your email address is usually well protected already.
You can now enable email 2FA on the Cloudflare dashboard:
1. Go to **Profile** at the top right corner.
2. Select **Authentication**.
3. Under **Two-Factor Authentication**, select **Set up**.
#### Sign-in security best practices
Cloudflare is critical infrastructure, and you should protect it as such. Review the following best practices and make sure you are doing your part to secure your account:
* Use a unique password for every website, including Cloudflare, and store it in a password manager like 1Password or Keeper. These services are cross-platform and simplify the process of managing secure passwords.
* Use 2FA to make it harder for an attacker to get into your account in the event your password is leaked.
* Store your backup codes securely. A password manager is the best place since it keeps the backup codes encrypted, but you can also print them and put them somewhere safe in your home.
* If you use an app to manage your 2FA keys, enable cloud backup, so that you don't lose your keys in the event you lose your phone.
* If you use a custom email domain to sign in, [configure SSO](https://developers.cloudflare.com/fundamentals/manage-members/dashboard-sso/).
* If you use a public email domain like Gmail or Hotmail, you can also use social login with Apple, GitHub, or Google to sign in.
* If you manage a Cloudflare account for work:
* Have at least two administrators in case one of them unexpectedly leaves your company.
* Use SCIM to automate permissions management for members in your Cloudflare account.
---
title: WAF Release - 2025-10-30 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-10-30 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-30-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-10-30-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-10-30 - Emergency
Oct 30, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces a new detection signature that enhances coverage for a critical vulnerability in Oracle E-Business Suite, tracked as CVE-2025-61884.
**Key Findings**
The flaw is easily exploitable and allows an unauthenticated attacker with network access to compromise Oracle Configurator, which can grant access to sensitive resources and configuration data. The affected versions include 12.2.3 through 12.2.14.
**Impact**
Successful exploitation of CVE-2025-61884 may result in unauthorized access to critical business data or full exposure of information accessible through Oracle Configurator. Administrators are strongly advised to apply vendor's patches and recommended mitigations to reduce this exposure.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 2749f13f8cb34a3dbd49c8c48827402f | N/A | Oracle E-Business Suite - SSRF - CVE:CVE-2025-61884 | N/A | Block | This is a New Detection |
---
title: Revamped Member Management UI · Changelog
description: Simplifying the management of users, groups, and permissions within Cloudflare.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-30-member-management-improvements/
md: https://developers.cloudflare.com/changelog/2025-10-30-member-management-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Revamped Member Management UI
Oct 30, 2025
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
As Cloudflare's platform has grown, so has the need for precise, role-based access control. We’ve redesigned the Member Management experience in the Dashboard to help administrators more easily discover, assign, and refine permissions for specific principals.
#### What's New
**Refreshed member invite flow**
We overhauled the Invite Members UI to simplify inviting users and assigning permissions.

**Refreshed Members Overview Page**
We've updated the Members Overview Page to clearly display:
* Member 2FA status
* Which members hold Super Admin privileges
* API access settings per member
* Member onboarding state (accepted vs pending invite)

**New Member Permission Policies Details View**
We've created a new member details screen that shows all permission policies associated with a member; including policies inherited from group associations to make it easier for members to understand the effective permissions they have.

**Improved Member Permission Workflow**
We redesigned the permission management experience to make it faster and easier for administrators to review roles and grant access.

**Account-scoped Policies Restrictions Relaxed**
Previously, customers could only associate a single account-scoped policy with a member. We've relaxed this restriction, and now Administrators can now assign multiple account-scoped policies to the same member; bringing policy assignment behavior in-line with user-groups and providing greater flexibility in managing member permissions.
---
title: New TCP-based fields available in Rulesets · Changelog
description: Cloudflare Rulesets now support evaluating TCP connections and TCP
RTT as part of request logic.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-30-tcp-rtt-and-tcp-fields/
md: https://developers.cloudflare.com/changelog/2025-10-30-tcp-rtt-and-tcp-fields/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New TCP-based fields available in Rulesets
Oct 30, 2025
[Rules](https://developers.cloudflare.com/rules/)
#### Build rules based on TCP transport and latency
Cloudflare now provides two new request fields in the Ruleset engine that let you make decisions based on whether a request used TCP and the measured TCP round-trip time between the client and Cloudflare. These fields help you understand protocol usage across your traffic and build policies that respond to network performance. For example, you can distinguish TCP from QUIC traffic or route high latency requests to alternative origins when needed.
***
#### New fields
| Field | Type | Description |
| - | - | - |
| `cf.edge.client_tcp` | Boolean | Indicates whether the request used TCP. A value of true means the client connected using TCP instead of QUIC. |
| `cf.timings.client_tcp_rtt_msec` | Number | Reports the smoothed TCP round-trip time between the client and Cloudflare in milliseconds. For example, a value of 20 indicates roughly twenty milliseconds of RTT. |
Example filter expression:
```plaintext
cf.edge.client_tcp && cf.timings.client_tcp_rtt_msec < 100
```
More information can be found in the Rules language [fields reference](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/).
---
title: Report logo misuse to Cloudflare directly from the Brand Protection
dashboard · Changelog
description: You can now use the Brand Protection logo dashboard to report abuse
on the Cloudflare network
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-31-brand-protection-logo-dashboard-report-abuse/
md: https://developers.cloudflare.com/changelog/2025-10-31-brand-protection-logo-dashboard-report-abuse/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Report logo misuse to Cloudflare directly from the Brand Protection dashboard
Oct 31, 2025
[Security Center](https://developers.cloudflare.com/security-center/)
The Brand Protection logo query dashboard now allows you to use the **Report to Cloudflare** button to submit an Abuse report directly from the Brand Protection logo queries dashboard. While you could previously report new domains that were impersonating your brand before, now you can do the same for websites found to be using your logo wihtout your permission. The abuse reports wiull be prefilled and you will only need to validate a few fields before you can click the submit button, after which our team process your request.
Ready to start? Check out the [Brand Protection docs](https://developers.cloudflare.com/security-center/brand-protection/).
---
title: Workers WebSocket message size limit increased from 1 MiB to 32 MiB · Changelog
description: The maximum WebSocket message size limit for all Workers has been
increased from 1 MiB to 32 MiB.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-10-31-increased-websocket-message-size-limit/
md: https://developers.cloudflare.com/changelog/2025-10-31-increased-websocket-message-size-limit/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers WebSocket message size limit increased from 1 MiB to 32 MiB
Oct 31, 2025
[Workers ](https://developers.cloudflare.com/workers/)[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Browser Rendering](https://developers.cloudflare.com/browser-rendering/)
Workers, including those using [Durable Objects](https://developers.cloudflare.com/durable-objects/) and [Browser Rendering](https://developers.cloudflare.com/browser-rendering/workers-bindings/), may now process WebSocket messages up to 32 MiB in size. Previously, this limit was 1 MiB.
This change allows Workers to handle use cases requiring large message sizes, such as processing Chrome Devtools Protocol messages.
For more information, please see the [Durable Objects startup limits](https://developers.cloudflare.com/durable-objects/platform/limits/#SQLite-backed-Durable-Objects-general-limits).
---
title: WAF Release - 2025-11-03 · Changelog
description: Cloudflare WAF managed rulesets 2025-11-03 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-03-waf-release/
md: https://developers.cloudflare.com/changelog/2025-11-03-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-11-03
Nov 03, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights enhancements to detection signatures improving coverage for vulnerabilities in Adobe Commerce and Magento Open Source, linked to CVE-2025-54236.
**Key Findings**
This vulnerability allows unauthenticated attackers to take over customer accounts through the Commerce REST API and, in certain configurations, may lead to remote code execution. The latest update provides enhanced detection logic for resilient protection against exploitation attempts.
**Impact**
* Adobe Commerce (CVE-2025-54236): Exploitation may allow attackers to hijack sessions, execute arbitrary commands, steal data, and disrupt storefronts, resulting in confidentiality and integrity risks for merchants. Administrators are strongly encouraged to apply vendor patches without delay.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | f5295d8333b7428c816654d8cb6d5fe5 | 100774C | Adobe Commerce - Remote Code Execution - CVE:CVE-2025-54236 | Log | Block | This is an improved detection. |
---
title: Log Explorer now supports query cancellation · Changelog
description: Log Explorer users can now cancel in-progress queries, improving
productivity and workflow.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-04-query-cancellation/
md: https://developers.cloudflare.com/changelog/2025-11-04-query-cancellation/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Log Explorer now supports query cancellation
Nov 04, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We're excited to announce that Log Explorer users can now cancel queries that are currently running.
This new feature addresses a common pain point: waiting for a long, unintended, or misconfigured query to complete before you can submit a new, correct one. With query cancellation, you can immediately stop the execution of any undesirable query, allowing you to quickly craft and submit a new query, significantly improving your investigative workflow and productivity within Log Explorer.
---
title: D1 can restrict data localization with jurisdictions · Changelog
description: A D1 database can set a jurisdiction at creation, which limits the
location to run and store the database.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-05-d1-jurisdiction/
md: https://developers.cloudflare.com/changelog/2025-11-05-d1-jurisdiction/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## D1 can restrict data localization with jurisdictions
Nov 05, 2025
[D1 ](https://developers.cloudflare.com/d1/)[Workers](https://developers.cloudflare.com/workers/)
You can now set a [jurisdiction](https://developers.cloudflare.com/d1/configuration/data-location/) when creating a D1 database to guarantee where your database runs and stores data. Jurisdictions can help you comply with data localization regulations such as GDPR. Supported jurisdictions include `eu` and `fedramp`.
A jurisdiction can only be set at database creation time via wrangler, REST API or the UI and cannot be added/updated after the database already exists.
```sh
npx wrangler@latest d1 create db-with-jurisdiction --jurisdiction eu
```
```plaintext
curl -X POST "https://api.cloudflare.com/client/v4/accounts//d1/database" \
-H "Authorization: Bearer $TOKEN" \
-H "Content-Type: application/json" \
--data '{"name": "db-wth-jurisdiction", "jurisdiction": "eu" }'
```
To learn more, visit D1's data location [documentation](https://developers.cloudflare.com/d1/configuration/data-location/).
---
title: WAF Release - 2025-11-05 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-11-05 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-05-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-11-05-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-11-05 - Emergency
Nov 05, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s emergency release introduces a new detection signature that enhances coverage for a critical vulnerability in the React Native Metro Development Server, tracked as CVE-2025-11953.
**Key Findings**
The Metro Development Server exposes an HTTP endpoint that is vulnerable to OS command injection (CWE-78). An unauthenticated network attacker can send a crafted request to this endpoint and execute arbitrary commands on the host running Metro. The vulnerability affects Metro/cli-server-api builds used by React Native Community CLI in pre-patch development releases.
**Impact**
Successful exploitation of CVE-2025-11953 may result in remote command execution on developer workstations or CI/build agents, leading to credential and secret exposure, source tampering, and potential lateral movement into internal networks. Administrators and developers are strongly advised to apply the vendor's patches and restrict Metro’s network exposure to reduce this risk.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | db6b9e1ac1494971ae8c70aac8e30c5b | N/A | React Native Metro - Command Injection - CVE:CVE-2025-11953 | N/A | Block | This is a New Detection |
---
title: Logpush Permission Update for Zero Trust Datasets · Changelog
description: Additional permissions required for ZT datasets
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-05-logpush-permissions-update/
md: https://developers.cloudflare.com/changelog/2025-11-05-logpush-permissions-update/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Logpush Permission Update for Zero Trust Datasets
Nov 05, 2025
[Logs](https://developers.cloudflare.com/logs/)
[Permissions](https://developers.cloudflare.com/logs/logpush/permissions/) for managing Logpush jobs related to [Zero Trust datasets](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/) (Access, Gateway, and DEX) have been updated to improve data security and enforce appropriate access controls.
To view, create, update, or delete Logpush jobs for Zero Trust datasets, users must now have both of the following permissions:
* Logs Edit
* Zero Trust: PII Read
Note
Update your UI, API or Terraform configurations to include the new permissions. Requests to Zero Trust datasets will fail due to insufficient access without the additional permission.
---
title: Applications to be remapped to the new categories · Changelog
description: We are preparing to remap some existing applications to better
reflect their category
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-06-applications-recategorised-plan/
md: https://developers.cloudflare.com/changelog/2025-11-06-applications-recategorised-plan/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Applications to be remapped to the new categories
Nov 06, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
We have previously added new application categories to better reflect their content and improve HTTP traffic management: refer to [Changelog](https://developers.cloudflare.com/cloudflare-one/changelog/gateway/#2025-10-28). While the new categories are live now, we want to ensure you have ample time to review and adjust any existing rules you have configured against old categories. The remapping of existing applications into these new categories will be completed by January 30, 2026. This timeline allows you a dedicated period to:
* Review the new category structure.
* Identify any policies you have that target the older categories.
* Adjust your rules to reference the new, more precise categories before the old mappings change. Once the applications have been fully remapped by January 30, 2026, you might observe some changes in the traffic being mitigated or allowed by your existing policies. We encourage you to use the intervening time to prepare for a smooth transition.
**Applications being remappedd**
| Application Name | Existing Category | New Category |
| - | - | - |
| Google Photos | File Sharing | Photography & Graphic Design |
| Flickr | File Sharing | Photography & Graphic Design |
| ADP | Human Resources | Business |
| Greenhouse | Human Resources | Business |
| myCigna | Human Resources | Health & Fitness |
| UnitedHealthcare | Human Resources | Health & Fitness |
| ZipRecruiter | Human Resources | Business |
| Amazon Business | Human Resources | Business |
| Jobcenter | Human Resources | Business |
| Jobsuche | Human Resources | Business |
| Zenjob | Human Resources | Business |
| DocuSign | Legal | Business |
| Postident | Legal | Business |
| Adobe Creative Cloud | Productivity | Photography & Graphic Design |
| Airtable | Productivity | Development |
| Autodesk Fusion360 | Productivity | IT Management |
| Coursera | Productivity | Education |
| Microsoft Power BI | Productivity | Business |
| Tableau | Productivity | Business |
| Duolingo | Productivity | Education |
| Adobe Reader | Productivity | Business |
| AnpiReport | Productivity | Travel |
| ビズリーチ | Productivity | Business |
| doda (デューダ) | Productivity | Business |
| 求人ボックス | Productivity | Business |
| マイナビ2026 | Productivity | Business |
| Power Apps | Productivity | Business |
| RECRUIT AGENT | Productivity | Business |
| シフトボード | Productivity | Business |
| スタンバイ | Productivity | Business |
| Doctolib | Productivity | Health & Fitness |
| Miro | Productivity | Photography & Graphic Design |
| MyFitnessPal | Productivity | Health & Fitness |
| Sentry Mobile | Productivity | Travel |
| Slido | Productivity | Photography & Graphic Design |
| Arista Networks | Productivity | IT Management |
| Atlassian | Productivity | Business |
| CoderPad | Productivity | Business |
| eAgreements | Productivity | Business |
| Vmware | Productivity | IT Management |
| Vmware Vcenter | Productivity | IT Management |
| AWS Skill Builder | Productivity | Education |
| Microsoft Office 365 (GCC) | Productivity | Business |
| Microsoft Exchange Online (GCC) | Productivity | Business |
| Canva | Sales & Marketing | Photography & Graphic Design |
| Instacart | Shopping | Food & Drink |
| Wawa | Shopping | Food & Drink |
| McDonald's | Shopping | Food & Drink |
| Vrbo | Shopping | Travel |
| American Airlines | Shopping | Travel |
| Booking.com | Shopping | Travel |
| Ticketmaster | Shopping | Entertainment & Events |
| Airbnb | Shopping | Travel |
| DoorDash | Shopping | Food & Drink |
| Expedia | Shopping | Travel |
| EasyPark | Shopping | Travel |
| UEFA Tickets | Shopping | Entertainment & Events |
| DHL Express | Shopping | Business |
| UPS | Shopping | Business |
For more information on creating HTTP policies, refer to [Applications and app types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
---
title: Automatic Return Routing (Beta) · Changelog
description: Magic WAN learns return paths for on-ramped traffic without static routes
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-06-automatic-return-routing-beta/
md: https://developers.cloudflare.com/changelog/2025-11-06-automatic-return-routing-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Automatic Return Routing (Beta)
Nov 06, 2025
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Magic WAN now supports Automatic Return Routing (ARR), allowing customers to configure Magic on-ramps (IPsec/GRE/CNI) to learn the return path for traffic flows without requiring static routes.
Key benefits:
* **Route-less mode**: Static or dynamic routes are optional when using ARR.
* **Overlapping IP space support**: Traffic originating from customer sites can use overlapping private IP ranges.
* **Symmetric routing**: Return traffic is guaranteed to use the same connection as the original on-ramp.
This feature is currently in beta and requires the new Unified Routing mode (beta).
For configuration details, refer to [Configure Automatic Return Routing](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-automatic-return-routing-beta).
---
title: Designate WAN link for breakout traffic · Changelog
description: Pin breakout traffic to specific WAN ports for deterministic egress control
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-06-connector-designate-wan-link-breakout/
md: https://developers.cloudflare.com/changelog/2025-11-06-connector-designate-wan-link-breakout/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Designate WAN link for breakout traffic
Nov 06, 2025
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Magic WAN Connector now allows you to designate a specific WAN port for breakout traffic, giving you deterministic control over the egress path for latency-sensitive applications.
With this feature, you can:
* Pin breakout traffic for specific applications to a preferred WAN port.
* Ensure critical traffic (such as Zoom or Teams) always uses your fastest or most reliable connection.
* Benefit from automatic failover to standard WAN port priority if the preferred port goes down.
This is useful for organizations with multiple ISP uplinks who need predictable egress behavior for performance-sensitive traffic.
For configuration details, refer to [Designate WAN ports for breakout apps](https://developers.cloudflare.com/magic-wan/configuration/connector/network-options/application-based-policies/breakout-traffic/#designate-wan-ports-for-breakout-apps).
---
title: Workers automatic tracing, now in open beta · Changelog
description: Gain instant visibility into Workers execution with automatic
tracing and OpenTelemetry exports
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-07-automatic-tracing/
md: https://developers.cloudflare.com/changelog/2025-11-07-automatic-tracing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers automatic tracing, now in open beta
Nov 07, 2025
[Workers](https://developers.cloudflare.com/workers/)
Enable automatic tracing on your Workers, giving you detailed metadata and timing information for every operation your Worker performs.
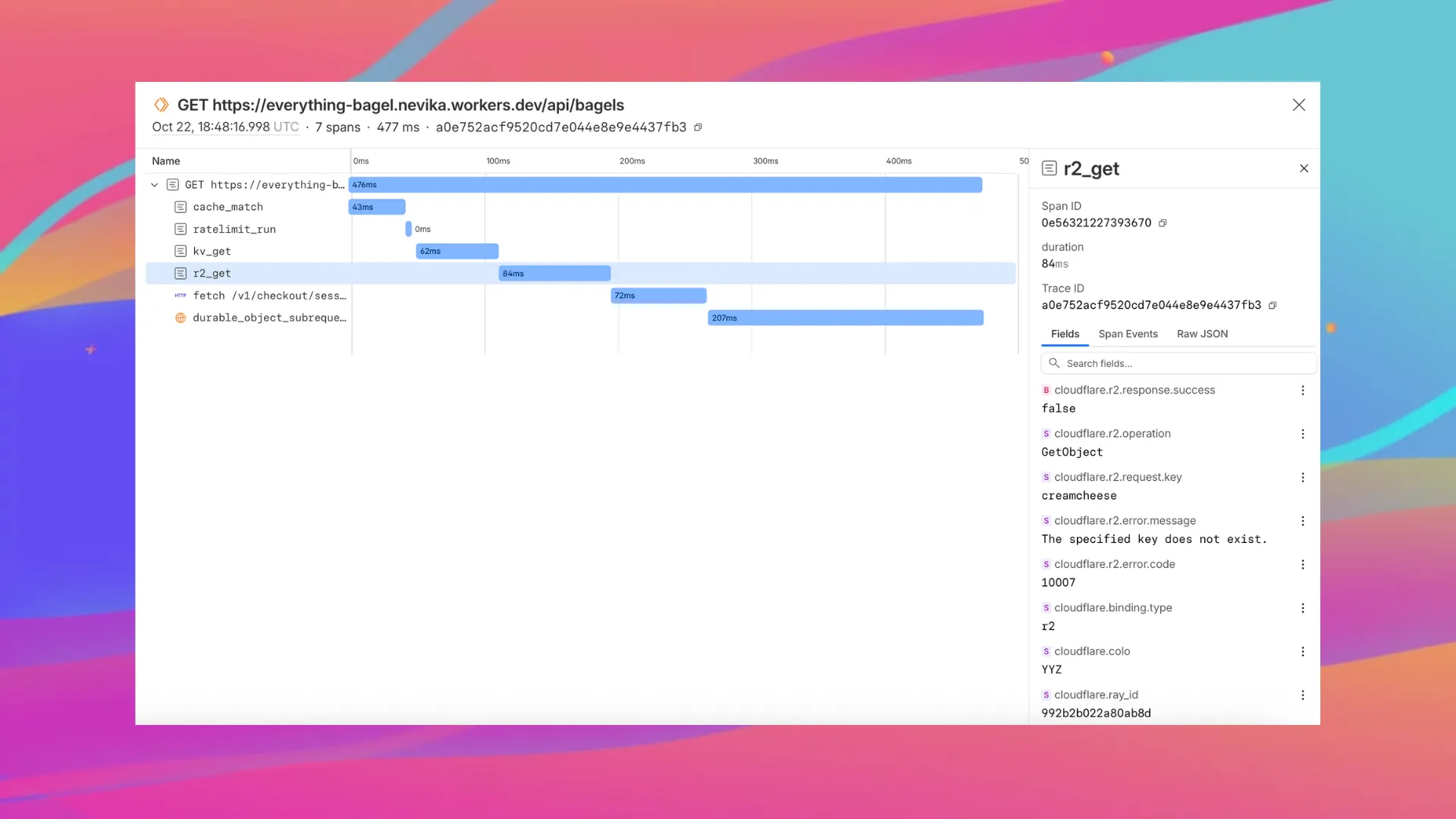
Tracing helps you identify performance bottlenecks, resolve errors, and understand how your Worker interacts with other services on the Workers platform. You can now answer questions like:
* Which calls are slowing down my application?
* Which queries to my database take the longest?
* What happened within a request that resulted in an error?
**You can now:**
* View traces alongside your logs in the Workers Observability dashboard
* Export traces (and correlated logs) to any [OTLP-compatible destination](https://opentelemetry.io/docs/specs/otel/protocol/), such as [Honeycomb](https://developers.cloudflare.com/workers/observability/exporting-opentelemetry-data/honeycomb/), [Sentry](https://developers.cloudflare.com/workers/observability/exporting-opentelemetry-data/sentry/) or [Grafana](https://developers.cloudflare.com/workers/observability/exporting-opentelemetry-data/grafana-cloud/), by configuring a tracing destination in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/workers-and-pages/observability/destinations)
* Analyze and query across span attributes (operation type, status, duration, errors)
#### To get started, set:
```jsonc
{
"observability": {
"tracing": {
"enabled": true,
},
},
}
```
Note
In the future, Cloudflare plans to enable automatic tracing in addition to logs when you set `observability.enabled = true` in your Wrangler configuration.
While automatic tracing is in early beta, this setting will not enable tracing by default, and will only enable logs.
An updated [`compatibility_date`](https://developers.cloudflare.com/workers/configuration/compatibility-dates/) will be required for this change to take effect.
#### Want to learn more?
* [Read the announcement](https://blog.cloudflare.com/workers-tracing-now-in-open-beta/)
* [Check out the documentation](https://developers.cloudflare.com/workers/observability/traces/)
---
title: Inspect Cache Keys with Cloudflare Trace · Changelog
description: View the specific cache key generated for requests to troubleshoot
caching behavior and rules configuration.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-07-cache-keys-for-cloudflare-trace/
md: https://developers.cloudflare.com/changelog/2025-11-07-cache-keys-for-cloudflare-trace/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Inspect Cache Keys with Cloudflare Trace
Nov 07, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now see the exact cache key generated for any request directly in Cloudflare Trace. This visibility helps you troubleshoot cache hits and misses, and verify that your Custom Cache Keys — configured via Cache Rules or Page Rules — are working as intended.
Previously, diagnosing caching behavior required inferring the key from configuration settings. Now, you can confirm that your custom logic for headers, query strings, and device types is correctly applied.
Access Trace via the [dashboard](https://developers.cloudflare.com/rules/trace-request/how-to/#use-trace-in-the-dashboard) or [API](https://developers.cloudflare.com/api/resources/request_tracer/methods/trace/), either manually for ad-hoc debugging or automated as part of your quality-of-service monitoring.
#### Example scenario
If you have a Cache Rule that segments content based on a specific cookie (for example, `user_region`), run a Trace with that cookie present to confirm the `user_region` value appears in the resulting cache key.
The Trace response includes the cache key in the `cache` object:
```json
{
"step_name": "request",
"type": "cache",
"matched": true,
"public_name": "Cache Parameters",
"cache": {
"key": {
"zone_id": "023e105f4ecef8ad9ca31a8372d0c353",
"scheme": "https",
"host": "example.com",
"uri": "/images/hero.jpg"
},
"key_string": "023e105f4ecef8ad9ca31a8372d0c353::::https://example.com/images/hero.jpg:::::"
}
}
```
#### Get started
To learn more, refer to the [Trace documentation](https://developers.cloudflare.com/rules/trace-request/) and our guide on [Custom Cache Keys](https://developers.cloudflare.com/cache/how-to/cache-keys/).
---
title: Select Wrangler environments using the CLOUDFLARE_ENV environment
variable · Changelog
description: Wrangler now supports the CLOUDFLARE_ENV environment variable to
select the active environment without using the --env flag.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-09-cloudflare-env-variable/
md: https://developers.cloudflare.com/changelog/2025-11-09-cloudflare-env-variable/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Select Wrangler environments using the CLOUDFLARE\_ENV environment variable
Nov 09, 2025
[Workers](https://developers.cloudflare.com/workers/)
Wrangler now supports using the `CLOUDFLARE_ENV` [environment variable](https://developers.cloudflare.com/workers/wrangler/system-environment-variables/#supported-environment-variables) to select the active [environment](https://developers.cloudflare.com/workers/wrangler/environments/) for your Worker commands. This provides a more flexible way to manage environments, especially when working with build tools and CI/CD pipelines.
#### What's new
**Environment selection via environment variable:**
* Set `CLOUDFLARE_ENV` to specify which environment to use for Wrangler commands
* Works with all Wrangler commands that support the `--env` flag
* The `--env` command line argument takes precedence over the `CLOUDFLARE_ENV` environment variable
#### Example usage
```bash
# Deploy to the production environment using CLOUDFLARE_ENV
CLOUDFLARE_ENV=production wrangler deploy
# Upload a version to the staging environment
CLOUDFLARE_ENV=staging wrangler versions upload
# The --env flag takes precedence over CLOUDFLARE_ENV
CLOUDFLARE_ENV=dev wrangler deploy --env production
# This will deploy to production, not dev
```
#### Use with build tools
The `CLOUDFLARE_ENV` environment variable is particularly useful when working with build tools like Vite. You can set the environment once during the build process, and it will be used for both building and deploying your Worker:
```bash
# Set the environment for both build and deploy
CLOUDFLARE_ENV=production npm run build & wrangler deploy
```
When using `@cloudflare/vite-plugin`, the build process generates a ["redirected deploy config"](https://developers.cloudflare.com/workers/wrangler/configuration/#generated-wrangler-configuration) that is flattened to only contain the active environment. Wrangler will validate that the environment specified matches the environment used during the build to prevent accidentally deploying a Worker built for one environment to a different environment.
#### Learn more
* [System environment variables](https://developers.cloudflare.com/workers/wrangler/system-environment-variables/)
* [Environments](https://developers.cloudflare.com/workers/wrangler/environments/)
---
title: Crawler drilldowns with extended actions menu · Changelog
description: Drill down into individual crawler behavior with status code charts
and export data for use in WAF rules, Redirect Rules, and robots.txt files.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-10-ai-crawl-control-crawler-info/
md: https://developers.cloudflare.com/changelog/2025-11-10-ai-crawl-control-crawler-info/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Crawler drilldowns with extended actions menu
Nov 10, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
AI Crawl Control now supports per-crawler drilldowns with an extended actions menu and status code analytics. Drill down into Metrics, Cloudflare Radar, and Security Analytics, or export crawler data for use in [WAF custom rules](https://developers.cloudflare.com/waf/custom-rules/), [Redirect Rules](https://developers.cloudflare.com/rules/url-forwarding/), and robots.txt files.
#### What's new
#### Status code distribution chart
The **Metrics** tab includes a status code distribution chart showing HTTP response codes (2xx, 3xx, 4xx, 5xx) over time. Filter by individual crawler, category, operator, or time range to analyze how specific crawlers interact with your site.

#### Extended actions menu
Each crawler row includes a three-dot menu with per-crawler actions:
* **View Metrics** — Filter the AI Crawl Control Metrics page to the selected crawler.
* **View on Cloudflare Radar** — Access verified crawler details on Cloudflare Radar.
* **Copy User Agent** — Copy user agent strings for use in WAF custom rules, Redirect Rules, or robots.txt files.
* **View in Security Analytics** — Filter Security Analytics by detection IDs (Bot Management customers).
* **Copy Detection ID** — Copy detection IDs for use in WAF custom rules (Bot Management customers).

#### Get started
1. Log in to the Cloudflare dashboard, and select your account and domain.
2. Go to **AI Crawl Control** > **Metrics** to access the status code distribution chart.
3. Go to **AI Crawl Control** > **Crawlers** and select the three-dot menu for any crawler to access per-crawler actions.
4. Select multiple crawlers to use bulk copy buttons for user agents or detection IDs.
Learn more about [AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/).
---
title: WAF Release - 2025-11-10 · Changelog
description: Cloudflare WAF managed rulesets 2025-11-10 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-10-waf-release/
md: https://developers.cloudflare.com/changelog/2025-11-10-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-11-10
Nov 10, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces new detections for Prototype Pollution across three common vectors: URI, Body, and Header/Form.
**Key Findings**
* These attacks can affect both API and web applications by altering normal behavior or bypassing security controls.
**Impact**
Exploitation may allow attackers to change internal logic or cause unexpected behavior in applications using JavaScript or Node.js frameworks. Developers should sanitize input keys and avoid merging untrusted data structures.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 32405a50728746dd8caa057b606285e6 | N/A | Generic Rules - Prototype Pollution - URI | Log | Disabled | This is a new detection |
| Cloudflare Managed Ruleset | a7da00c63c4243d2a72456fe4f59ff26 | N/A | Generic Rules - Prototype Pollution - Body | Log | Disabled | This is a new detection |
| Cloudflare Managed Ruleset | 833078bdcfa04bb7aa7b8fb67efbeb39 | N/A | Generic Rules - Prototype Pollution - Header - Form | Log | Disabled | This is a new detection |
---
title: cloudflared proxy-dns command will be removed starting February 2, 2026 ·
Changelog
description: To address a vulnerability in an underlying library, the
`cloudflared proxy-dns` command will be removed from new `cloudflared`
releases. Users are advised to migrate to the Cloudflare WARP client or WARP
Connector.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-11-cloudflared-proxy-dns/
md: https://developers.cloudflare.com/changelog/2025-11-11-cloudflared-proxy-dns/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## cloudflared proxy-dns command will be removed starting February 2, 2026
Nov 11, 2025
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
Starting February 2, 2026, the `cloudflared proxy-dns` command will be removed from all new `cloudflared` [releases](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/downloads/).
This change is being made to enhance security and address a potential vulnerability in an underlying DNS library. This vulnerability is specific to the `proxy-dns` command and does not affect any other `cloudflared` features, such as the core [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) service.
The `proxy-dns` command, which runs a client-side [DNS-over-HTTPS (DoH)](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/) proxy, has been an officially undocumented feature for several years. This functionality is fully and securely supported by our actively developed products.
Versions of `cloudflared` released before this date will not be affected and will continue to operate. However, note that our [official support policy](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/downloads/#deprecated-releases) for any `cloudflared` release is one year from its release date.
#### Migration paths
We strongly advise users of this undocumented feature to migrate to one of the following officially supported solutions before February 2, 2026, to continue benefiting from secure [DNS-over-HTTPS](https://developers.cloudflare.com/1.1.1.1/encryption/dns-over-https/).
#### End-user devices
The preferred method for enabling DNS-over-HTTPS on user devices is the [Cloudflare WARP client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/). The WARP client automatically secures and proxies all DNS traffic from your device, integrating it with your organization's [Zero Trust policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) and [posture checks](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/).
#### Servers, routers, and IoT devices
For scenarios where installing a client on every device is not possible (such as servers, routers, or IoT devices), we recommend using the [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/).
Instead of running `cloudflared proxy-dns` on a machine, you can install the WARP Connector on a single Linux host within your private network. This connector will act as a gateway, securely routing all DNS and network traffic from your [entire subnet](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/site-to-internet/) to Cloudflare for [filtering and logging](https://developers.cloudflare.com/cloudflare-one/traffic-policies/).
---
title: Logpush Health Dashboards · Changelog
description: Introducing Logpush Health Dashboards
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-11-health-dashboards/
md: https://developers.cloudflare.com/changelog/2025-11-11-health-dashboards/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Logpush Health Dashboards
Nov 11, 2025
[Logs](https://developers.cloudflare.com/logs/)
We’re excited to introduce **Logpush Health Dashboards**, giving customers real-time visibility into the status, reliability, and performance of their [Logpush](https://developers.cloudflare.com/logs/logpush/) jobs. Health dashboards make it easier to detect delivery issues, monitor job stability, and track performance across destinations. The dashboards are divided into two sections:
* **Upload Health**: See how much data was successfully uploaded, where drops occurred, and how your jobs are performing overall. This includes data completeness, success rate, and upload volume.
* **Upload Reliability** – Diagnose issues impacting stability, retries, or latency, and monitor key metrics such as retry counts, upload duration, and destination availability.

Health Dashboards can be accessed from the Logpush page in the Cloudflare dashboard at the account or zone level, under the Health tab. For more details, refer to our [**Logpush Health Dashboards**](https://developers.cloudflare.com/logs/logpush/logpush-health) documentation, which includes a comprehensive troubleshooting guide to help interpret and resolve common issues.
---
title: Resize your custom SQL window in Log Explorer · Changelog
description: Easily resize the custom SQL query window in Log Explorer to view
long queries without scrolling.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-11-resize-sql-window/
md: https://developers.cloudflare.com/changelog/2025-11-11-resize-sql-window/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Resize your custom SQL window in Log Explorer
Nov 11, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We're excited to announce a quality-of-life improvement for Log Explorer users. You can now resize the custom SQL query window to accommodate longer and more complex queries.
Previously, if you were writing a long custom SQL query, the fixed-size window required excessive scrolling to view the full query. This update allows you to easily drag the bottom edge of the query window to make it taller. This means you can view your entire custom query at once, improving the efficiency and experience of writing and debugging complex queries.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/).
---
title: WARP client for Linux (version 2025.9.558.0) · Changelog
description: WARP client for Linux (version 2025.9.558.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-11-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2025-11-11-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.9.558.0)
Nov 11, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features including [Path Maximum Transmission Unit Discovery (PMTUD)](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery). When PMTUD is enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to diagnose connectivity issues.
WARP client version 2025.8.779.0 introduced an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com/).
**Changes and improvements**
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to diagnose connectivity issues.
* Fixed an issue where deleting a registration was erroneously reported as having failed.
* Path Maximum Transmission Unit Discovery (PMTUD) may now be used to discover the effective MTU of the connection. This allows the WARP client to improve connectivity optimized for each network. PMTUD is disabled by default. To enable it, refer to the [PMTUD documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery).
---
title: WARP client for macOS (version 2025.9.558.0) · Changelog
description: WARP client for macOS (version 2025.9.558.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-11-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2025-11-11-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.9.558.0)
Nov 11, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features including [Path Maximum Transmission Unit Discovery (PMTUD)](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery). When PMTUD is enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to diagnose connectivity issues.
**Changes and improvements**
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to diagnose connectivity issues.
* Fixed an issue where deleting a registration was erroneously reported as having failed.
* Path Maximum Transmission Unit Discovery (PMTUD) may now be used to discover the effective MTU of the connection. This allows the WARP client to improve connectivity optimized for each network. PMTUD is disabled by default. To enable it, refer to the [PMTUD documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery).
**Known issues**
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
---
title: WARP client for Windows (version 2025.9.558.0) · Changelog
description: WARP client for Windows (version 2025.9.558.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-11-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2025-11-11-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.9.558.0)
Nov 11, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features including [Path Maximum Transmission Unit Discovery (PMTUD)](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery). When PMTUD is enabled, the client will dynamically adjust packet sizing to optimize connection performance. There is also a new connection status message in the GUI to inform users that the local network connection may be unstable. This will make it easier to diagnose connectivity issues.
**Changes and improvements**
* Fixed an inconsistency with [Global WARP override](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#disconnect-warp-on-all-devices) settings in multi-user environments when switching between users.
* The GUI now displays the health of the tunnel and DNS connections by showing a connection status message when the network may be unstable. This will make it easier to diagnose connectivity issues.
* Fixed an issue where deleting a registration was erroneously reported as having failed.
* Path Maximum Transmission Unit Discovery (PMTUD) may now be used to discover the effective MTU of the connection. This allows the WARP client to improve connectivity optimized for each network. PMTUD is disabled by default. To enable it, refer to the [PMTUD documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/#enable-path-mtu-discovery).
* Improvements for the [OS version](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/os-version/) WARP client check. Windows Updated Build Revision (UBR) numbers can now be checked by the client to ensure devices have required security patches and features installed.
* The WARP client now supports Windows 11 ARM-based machines. For information on known limitations, refer to the [Known limitations page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/troubleshooting/known-limitations/#warp-disconnected-on-windows-arm).
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices using WARP client 2025.4.929.0 and up may experience Local Domain Fallback failures if a fallback server has not been configured. To configure a fallback server, refer to [Route traffic to fallback server](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/configure-warp/route-traffic/local-domains/#route-traffic-to-fallback-server).
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: More SQL aggregate, date and time functions available in Workers
Analytics Engine · Changelog
description: Workers Analytics Engine now supports more SQL functions for
aggregation and for working with dates and times
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-12-analytics-engine-further-sql-enhancements/
md: https://developers.cloudflare.com/changelog/2025-11-12-analytics-engine-further-sql-enhancements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## More SQL aggregate, date and time functions available in Workers Analytics Engine
Nov 12, 2025
[Workers Analytics Engine ](https://developers.cloudflare.com/analytics/analytics-engine/)[Workers](https://developers.cloudflare.com/workers/)
You can now perform more powerful queries directly in [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/) with a major expansion of our SQL function library.
Workers Analytics Engine allows you to ingest and store high-cardinality data at scale (such as custom analytics) and query your data through a simple SQL API.
Today, we've expanded Workers Analytics Engine's SQL capabilities with several new functions:
[**New aggregate functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/aggregate-functions/)
* `countIf()` - count the number of rows which satisfy a provided condition
* `sumIf()` - calculate a sum from rows which satisfy a provided condition
* `avgIf()` - calculate an average from rows which satisfy a provided condition
[**New date and time functions:**](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/date-time-functions/)
* `toYear()`
* `toMonth()`
* `toDayOfMonth()`
* `toDayOfWeek()`
* `toHour()`
* `toMinute()`
* `toSecond()`
* `toStartOfYear()`
* `toStartOfMonth()`
* `toStartOfWeek()`
* `toStartOfDay()`
* `toStartOfHour()`
* `toStartOfFifteenMinutes()`
* `toStartOfTenMinutes()`
* `toStartOfFiveMinutes()`
* `toStartOfMinute()`
* `today()`
* `toYYYYMM()`
#### Ready to get started?
Whether you're building usage-based billing systems, customer analytics dashboards, or other custom analytics, these functions let you get the most out of your data. [Get started ](https://developers.cloudflare.com/analytics/analytics-engine/get-started/)with Workers Analytics Engine and explore all available functions in our [SQL reference documentation](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/).
---
title: New BOLA Vulnerability Detection for API Shield · Changelog
description: Find broken object level authorization attacks with BOLA
Vulnerability Detection for API Shield
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-12-bola-attack-detection/
md: https://developers.cloudflare.com/changelog/2025-11-12-bola-attack-detection/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New BOLA Vulnerability Detection for API Shield
Nov 12, 2025
[API Shield](https://developers.cloudflare.com/api-shield/)
Now, API Shield automatically searches for and highlights **Broken Object Level Authorization (BOLA) attacks** on managed API endpoints. API Shield will highlight both BOLA enumeration attacks and BOLA pollution attacks, telling you what was attacked, by who, and for how long.
You can find these attacks three different ways: Security Overview, Endpoint details, or Security Analytics. If these attacks are not found on your managed API endpoints, there will not be an overview card or security analytics suspicious activity card.

From the endpoint details, you can select **View attack** to find details about the BOLA attacker’s sessions.

From here, select **View in Analytics** to observe attacker traffic over time for the last seven days.

Your search will filter to traffic on that endpoint in the last seven days, along with the malicious session IDs found in the attack. Session IDs are hashed for privacy and will not be found in your origin logs. Refer to IP and JA4 fingerprint to cross-reference behavior at the origin.
At any time, you can also start your investigation into attack traffic from Security Analytics by selecting the suspicious activity card.

We urge you to take all of this client information to your developer team to research the attacker behavior and ensure any broken authorization policies in your API are fixed at the source in your application, preventing further abuse.
In addition, this release marks the end of the beta period for these scans. All Enterprise customers with API Shield subscriptions will see these new attacks if found on their zone.
---
title: DEX Logpush jobs · Changelog
description: There are four new DEX and WARP client data sets available to all
Cloudflare One customers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-12-dex-logpush-jobsmdx/
md: https://developers.cloudflare.com/changelog/2025-11-12-dex-logpush-jobsmdx/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## DEX Logpush jobs
Nov 12, 2025
[Digital Experience Monitoring](https://developers.cloudflare.com/cloudflare-one/insights/dex/)
[Digital Experience Monitoring (DEX)](https://developers.cloudflare.com/cloudflare-one/insights/dex/) provides visibility into WARP device metrics, connectivity, and network performance across your Cloudflare SASE deployment.
We've released four new WARP and DEX device data sets that can be exported via [Cloudflare Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/). These Logpush data sets can be exported to R2, a cloud bucket, or a SIEM to build a customized logging and analytics experience.
1. [DEX Application Tests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dex_application_tests/)
2. [DEX Device State Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dex_device_state_events/)
3. [WARP Config Changes](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/warp_config_changes/)
4. [WARP Toggle Changes](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/warp_toggle_changes/)
To create a new DEX or WARP Logpush job, customers can go to the account level of the Cloudflare dashboard > Analytics & Logs > Logpush to get started.

---
title: Fixed custom SQL date picker inconsistencies · Changelog
description: Log Explorer now correctly handles custom SQL date field filters.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-13-fixed-custom-date/
md: https://developers.cloudflare.com/changelog/2025-11-13-fixed-custom-date/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Fixed custom SQL date picker inconsistencies
Nov 13, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We've resolved a bug in Log Explorer that caused inconsistencies between the custom SQL date field filters and the date picker dropdown. Previously, users attempting to filter logs based on a custom date field via a SQL query sometimes encountered unexpected results or mismatching dates when using the interactive date picker.
This fix ensures that the custom SQL date field filters now align correctly with the selection made in the date picker dropdown, providing a reliable and predictable filtering experience for your log data. This is particularly important for users creating custom log views based on time-sensitive fields.
---
title: Log Explorer adds 14 new datasets · Changelog
description: Investigate security and performance with 14 new Cloudflare product
datasets in Log Explorer.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-13-new-datasets/
md: https://developers.cloudflare.com/changelog/2025-11-13-new-datasets/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Log Explorer adds 14 new datasets
Nov 13, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We've significantly enhanced Log Explorer by adding support for 14 additional Cloudflare product datasets.
This expansion enables Operations and Security Engineers to gain deeper visibility and telemetry across a wider range of Cloudflare services. By integrating these new datasets, users can now access full context to efficiently investigate security incidents, troubleshoot application performance issues, and correlate logged events across different layers (like application and network) within a single interface. This capability is crucial for a complete and cohesive understanding of event flows across your Cloudflare environment.
The newly supported datasets include:
#### Zone Level
* `Dns_logs`
* `Nel_reports`
* `Page_shield_events`
* `Spectrum_events`
* `Zaraz_events`
#### Account Level
* `Audit Logs`
* `Audit_logs_v2`
* `Biso_user_actions`
* `DNS firewall logs`
* `Email_security_alerts`
* `Magic Firewall IDS`
* `Network Analytics`
* `Sinkhole HTTP`
* `ipsec_logs`
Note
`Auditlog` and `Auditlog_v2` datasets require `audit-log.read` permission for querying.
The `biso_user_actions` dataset requires either the `Super Admin` or `ZT PII` role for querying.
#### Example: Correlating logs
You can now use Log Explorer to query and filter with each of these datasets. For example, you can identify an IP address exhibiting suspicious behavior in the `FW_event` logs, and then instantly pivot to the `Network Analytics` logs or `Access` logs to see its network-level traffic profile or if it bypassed a corporate policy.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/) and the [Cloudflare Logs documentation](https://developers.cloudflare.com/logs/).
---
title: Log Explorer now shows query result distribution · Changelog
description: Visualize your Log Explorer query results with a graphical
distribution chart over time.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-13-query-result-distribution/
md: https://developers.cloudflare.com/changelog/2025-11-13-query-result-distribution/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Log Explorer now shows query result distribution
Nov 04, 2025
[Log Explorer](https://developers.cloudflare.com/log-explorer/)
We're excited to announce a new feature in Log Explorer that significantly enhances how you analyze query results: the Query results distribution chart.
This new chart provides a graphical distribution of your results over the time window of the query. Immediately after running a query, you will see the distribution chart above your result table. This visualization allows Log Explorer users to quickly spot trends, identify anomalies, and understand the temporal concentration of log events that match their criteria. For example, you can visually confirm if a spike in traffic or errors occurred at a specific time, allowing you to focus your investigation efforts more effectively. This feature makes it faster and easier to extract meaningful insights from your vast log data.
The chart will dynamically update to reflect the logs matching your current query.
---
title: New SaaS Security weekly digests with API CASB · Changelog
description: Cloudflare CASB now offers a weekly email digest, summarizing your
organization's latest SaaS security findings, integration health, and content
exposures.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-14-casb-digest/
md: https://developers.cloudflare.com/changelog/2025-11-14-casb-digest/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New SaaS Security weekly digests with API CASB
Nov 14, 2025
[CASB](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)
You can now stay on top of your SaaS security posture with the new **CASB Weekly Digest** notification. This opt-in email digest is delivered to your inbox every Monday morning and provides a high-level summary of your organization's Cloudflare API CASB findings from the previous week.
This allows security teams and IT administrators to get proactive, at-a-glance visibility into new risks and integration health without having to log in to the dashboard.
To opt in, navigate to **Manage Account** > **Notifications** in the Cloudflare dashboard to configure the **CASB Weekly Digest** alert type.
#### Key capabilities
* **At-a-glance summary** — Review new high/critical findings, most frequent finding types, and new content exposures from the past 7 days.
* **Integration health** — Instantly see the status of all your connected SaaS integrations (Healthy, Unhealthy, or Paused) to spot API connection issues.
* **Proactive alerting** — The digest is sent automatically to all subscribed users every Monday morning.
* **Easy to configure** — Users can opt in by enabling the notification in the Cloudflare dashboard under **Manage Account** > **Notifications**.
#### Learn more
* Configure [notification preferences](https://developers.cloudflare.com/notifications/) in Cloudflare.
The CASB Weekly Digest notification is available to all Cloudflare users today.
---
title: Generate Cloudflare Access SSH certificate authority (CA) directly from
the Cloudflare dashboard · Changelog
description: Rather than generating the SSH CA using Cloudflare's API, you can
now generate it directly from the dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-14-ssh-ca-enhancements/
md: https://developers.cloudflare.com/changelog/2025-11-14-ssh-ca-enhancements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Generate Cloudflare Access SSH certificate authority (CA) directly from the Cloudflare dashboard
Nov 14, 2025
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
SSH with [Cloudflare Access for Infrastructure](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/) allows you to use short-lived SSH certificates to eliminate SSH key management and reduce security risks associated with lost or stolen keys.
Previously, users had to generate this certificate by using the [Cloudflare API](https://developers.cloudflare.com/api/) directly. With this update, you can now create and manage this certificate in the [Cloudflare One dashboard](https://one.dash.cloudflare.com) from the **Access controls** > **Service credentials** page.

For more details, refer to [Generate a Cloudflare SSH CA](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/ssh/ssh-infrastructure-access/#generate-a-cloudflare-ssh-ca).
---
title: WAF Release - 2025-11-17 · Changelog
description: Cloudflare WAF managed rulesets 2025-11-17 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-17-waf-release/
md: https://developers.cloudflare.com/changelog/2025-11-17-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-11-17
Nov 17, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights enhancements to detection signatures improving coverage for vulnerabilities in DELMIA Apriso, linked to CVE-2025-6205.
**Key Findings**
This vulnerability allows unauthenticated attackers to gain privileged access to the application. The latest update provides enhanced detection logic for resilient protection against exploitation attempts.
**Impact**
* DELMIA Apriso (CVE-2025-6205): Exploitation could allow an unauthenticated remote attacker to bypass security checks by sending specially crafted requests to the application's message processor. This enables the creation of arbitrary employee accounts, which can be leveraged to modify system configurations and achieve full system compromise.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | ec1e2aa190e64e7cb468e16dd256f4bc | N/A | DELMIA Apriso - Auth Bypass - CVE:CVE-2025-6205 | Log | Block | This is a new detection. |
| Cloudflare Managed Ruleset | fae6fa37ae9249d58628e54b1a3e521e | N/A | PHP Wrapper Injection - Body | N/A | Disabled | Rule metadata description refined. Detection unchanged. |
| Cloudflare Managed Ruleset | 9c02e585db34440da620eb668f76bd74 | N/A | PHP Wrapper Injection - URI | N/A | Disabled | Rule metadata description refined. Detection unchanged. |
---
title: Adjustment to Final Disposition Column · Changelog
description: We have adjusted the final disposition column for submitted email
misses for non-Phishguard customers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-18-temporary-adjustment-to-final-disposition-column/
md: https://developers.cloudflare.com/changelog/2025-11-18-temporary-adjustment-to-final-disposition-column/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Adjustment to Final Disposition Column
Nov 18, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
#### Adjustment to Final Disposition column
#### The **Final Disposition** column in **Submissions** > **Team Submissions** tab is changing for non-Phishguard customers.
#### What's Changing
* Column will be called **Status** instead of **Final Disposition**
* Column status values will now be: **Submitted**, **Accepted** or **Rejected**.
#### Next Steps
We will listen carefully to your feedback and continue to find comprehensive ways to communicate updates on your submissions. Your submissions will continue to be addressed at an even greater rate than before, fuelling faster and more accurate email security improvement.
---
title: AI Search support for crawling login protected website content · Changelog
description: Index websites behind login walls by adding custom authentication
headers to AI Search's website crawler.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-19-add-extra-headers-for-website-crawling/
md: https://developers.cloudflare.com/changelog/2025-11-19-add-extra-headers-for-website-crawling/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Search support for crawling login protected website content
Nov 19, 2025
[AI Search](https://developers.cloudflare.com/ai-search/)
[AI Search](https://developers.cloudflare.com/ai-search/) now supports [custom HTTP headers](https://developers.cloudflare.com/ai-search/configuration/data-source/website/#access-protected-content) for website crawling, solving a common problem where valuable content behind authentication or access controls could not be indexed.
Previously, AI Search could only crawl publicly accessible pages, leaving knowledge bases, documentation, and other protected content out of your search results. With custom headers support, you can now include authentication credentials that allow the crawler to access this protected content.
This is particularly useful for indexing content like:
* **Internal documentation** behind corporate login systems
* **Premium content** that requires users to provide access to unlock
* **Sites protected by Cloudflare Access** using service tokens
To add custom headers when creating an AI Search instance, select **Parse options**. In the **Extra headers** section, you can add up to five custom headers per Website data source.

For example, to crawl a site protected by [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/), you can add service token credentials as custom headers:
```plaintext
CF-Access-Client-Id: your-token-id.access
CF-Access-Client-Secret: your-token-secret
```
The crawler will automatically include these headers in all requests, allowing it to access protected pages that would otherwise be blocked.
Learn more about [configuring custom headers for website crawling](https://developers.cloudflare.com/ai-search/configuration/data-source/website/#access-protected-content) in AI Search.
---
title: Terraform v5.13.0 now available · Changelog
description: Terraform v5.13.0 stabilizes a number of resources and known issues
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-20-terraform-v5130-provider/
md: https://developers.cloudflare.com/changelog/2025-11-20-terraform-v5130-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.13.0 now available
Nov 20, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new Terraform v5 Provider. We are aware of the high number of issues reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) to ensure its stability and reliability, including the v5.13 release. We have also pivoted from an [issue-to-issue approach to a resource-per-resource approach](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) - we will be focusing on specific resources to not only stabilize the resource but also ensure it is migration-friendly for those migrating from v4 to v5.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes new features, new resources and data sources, bug fixes, updates to our Developer Documentation, and more.
#### Breaking Change
Please be aware that there are breaking changes for the `cloudflare_api_token` and `cloudflare_account_token` resources. These changes eliminate configuration drift caused by policy ordering differences in the Cloudflare API.
For more specific information about the changes or the actions required, please see the [detailed Repository changelog](https://github.com/cloudflare/terraform-provider-cloudflare/releases/tag/v5.13.0).
#### Features
* **New resources and data sources added**
* cloudflare\_connectivity\_directory
* cloudflare\_sso\_connector
* cloudflare\_universal\_ssl\_setting
* **api\_token+account\_tokens:** state upgrader and schema bump ([#6472](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6472))
* **docs:** make docs explicit when a resource does not have import support
* **magic\_transit\_connector:** support self-serve license key ([#6398](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6398))
* **worker\_version:** add content\_base64 support
* **worker\_version:** boolean support for run\_worker\_first ([#6407](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6407))
* **workers\_script\_subdomains:** add import support ([#6375](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6375))
* **zero\_trust\_access\_application:** add proxy\_endpoint for ZT Access Application ([#6453](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6453))
* **zero\_trust\_dlp\_predefined\_profile:** Switch DLP Predefined Profile endpoints, introduce enabled\_entries attribut
#### Bug Fixes
* **account\_token:** token policy order and nested resources ([#6440](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6440))
* allow r2\_bucket\_event\_notification to be applied twice without failing ([#6419](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6419))
* **cloudflare\_worker+cloudflare\_worker\_version:** import for the resources ([#6357](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6357))
* **dns\_record:** inconsistent apply error ([#6452](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6452))
* **pages\_domain:** resource tests ([#6338](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6338))
* **pages\_project:** unintended resource state drift ([#6377](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6377))
* **queue\_consumer:** id population ([#6181](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6181))
* **workers\_kv:** multipart request ([#6367](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6367))
* **workers\_kv:** updating workers metadata attribute to be read from endpoint ([#6386](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6386))
* **workers\_script\_subdomain:** add note to cloudflare\_workers\_script\_subdomain about redundancy with cloudflare\_worker ([#6383](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6383))
* **workers\_script:** allow config.run\_worker\_first to accept list input
* **zero\_trust\_device\_custom\_profile\_local\_domain\_fallback:** drift issues ([#6365](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6365))
* **zero\_trust\_device\_custom\_profile:** resolve drift issues ([#6364](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6364))
* **zero\_trust\_dex\_test:** correct configurability for 'targeted' attribute to fix drift
* **zero\_trust\_tunnel\_cloudflared\_config:** remove warp\_routing from cloudflared\_config ([#6471](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6471))
#### Upgrading
We suggest holding off on migration to v5 while we work on stabilization. This help will you avoid any blocking issues while the Terraform resources are actively being stabilized. We will be releasing a new migration tool in March 2026 to help support v4 to v5 transitions for our most popular resources.
#### For more info
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: Environment variable limits increase for Workers Builds · Changelog
description: Workers Builds now supports up to 64 environment variables per
Worker with 5 KB per variable, up from a previous 5 KB total limit.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-21-builds-env-var-increase/
md: https://developers.cloudflare.com/changelog/2025-11-21-builds-env-var-increase/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Environment variable limits increase for Workers Builds
Nov 21, 2025
[Workers](https://developers.cloudflare.com/workers/)
[Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/) now supports up to 64 environment variables, and each environment variable can be up to 5 KB in size. The previous limit was 5 KB total across all environment variables.
This change enables better support for complex build configurations, larger application settings, and more flexible CI/CD workflows.
For more details, refer to the [build limits documentation](https://developers.cloudflare.com/workers/ci-cd/builds/limits-and-pricing/#environment-variable-limits).
---
title: WAF Release - 2025-11-21 · Changelog
description: Cloudflare WAF managed rulesets 2025-11-21 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-21-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-11-21-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-11-21
Nov 21, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces a critical detection for CVE-2025-61757, a vulnerability in the Oracle Identity Manager REST WebServices component.
**Key Findings**
This flaw allows unauthenticated attackers with network access over HTTP to fully compromise the Identity Manager, potentially leading to a complete takeover.
**Impact**
Oracle Identity Manager (CVE-2025-61757): Exploitation could allow an unauthenticated remote attacker to bypass security checks by sending specially crafted requests to the application's message processor. This enables the creation of arbitrary employee accounts, which can be leveraged to modify system configurations and achieve full system compromise.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | fa584616fe2241608cb8bd1339fdbe7e | N/A | Oracle Identity Manager - Pre-Auth RCE - CVE:CVE-2025-61757 | N/A | Block | This is a new detection. |
---
title: Mount R2 buckets in Containers · Changelog
description: Containers now support mounting FUSE volumes
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-21-fuse-support-in-containers/
md: https://developers.cloudflare.com/changelog/2025-11-21-fuse-support-in-containers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Mount R2 buckets in Containers
Nov 21, 2025
[Containers ](https://developers.cloudflare.com/containers/)[R2](https://developers.cloudflare.com/r2/)
[Containers](https://developers.cloudflare.com/containers/) now support mounting R2 buckets as FUSE (Filesystem in Userspace) volumes, allowing applications to interact with [R2](https://developers.cloudflare.com/r2/) using standard filesystem operations.
Common use cases include:
* Bootstrapping containers with datasets, models, or dependencies for [sandboxes](https://developers.cloudflare.com/sandbox/) and [agent](https://developers.cloudflare.com/agents/) environments
* Persisting user configuration or application state without managing downloads
* Accessing large static files without bloating container images or downloading at startup
FUSE adapters like [tigrisfs](https://github.com/tigrisdata/tigrisfs), [s3fs](https://github.com/s3fs-fuse/s3fs-fuse), and [gcsfuse](https://github.com/GoogleCloudPlatform/gcsfuse) can be installed in your container image and configured to mount buckets at startup.
```dockerfile
FROM alpine:3.20
# Install FUSE and dependencies
RUN apk update && \
apk add --no-cache ca-certificates fuse curl bash
# Install tigrisfs
RUN ARCH=$(uname -m) && \
if [ "$ARCH" = "x86_64" ]; then ARCH="amd64"; fi && \
if [ "$ARCH" = "aarch64" ]; then ARCH="arm64"; fi && \
VERSION=$(curl -s https://api.github.com/repos/tigrisdata/tigrisfs/releases/latest | grep -o '"tag_name": "[^"]*' | cut -d'"' -f4) && \
curl -L "https://github.com/tigrisdata/tigrisfs/releases/download/${VERSION}/tigrisfs_${VERSION#v}_linux_${ARCH}.tar.gz" -o /tmp/tigrisfs.tar.gz && \
tar -xzf /tmp/tigrisfs.tar.gz -C /usr/local/bin/ && \
rm /tmp/tigrisfs.tar.gz && \
chmod +x /usr/local/bin/tigrisfs
# Create startup script that mounts bucket
RUN printf '#!/bin/sh\n\
set -e\n\
mkdir -p /mnt/r2\n\
R2_ENDPOINT="https://${R2_ACCOUNT_ID}.r2.cloudflarestorage.com"\n\
/usr/local/bin/tigrisfs --endpoint "${R2_ENDPOINT}" -f "${BUCKET_NAME}" /mnt/r2 &\n\
sleep 3\n\
ls -lah /mnt/r2\n\
' > /startup.sh && chmod +x /startup.sh
CMD ["/startup.sh"]
```
See the [Mount R2 buckets with FUSE](https://developers.cloudflare.com/containers/examples/r2-fuse-mount/) example for a complete guide on mounting R2 buckets and/or other S3-compatible storage buckets within your containers.
---
title: New CPU Pricing for Containers and Sandboxes · Changelog
description: New Container pricing changes CPU billing to be based on active
usage, rather than provisioned CPU resources
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-21-new-cpu-pricing/
md: https://developers.cloudflare.com/changelog/2025-11-21-new-cpu-pricing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New CPU Pricing for Containers and Sandboxes
Nov 21, 2025
[Containers](https://developers.cloudflare.com/containers/)
[Containers](https://developers.cloudflare.com/containers/) and [Sandboxes](https://developers.cloudflare.com/sandbox/) pricing for CPU time is now based on active usage only, instead of provisioned resources.
This means that you now pay less for Containers and Sandboxes.
#### An Example Before and After
Imagine running the `standard-2` instance type for one hour, which can use up to 1 vCPU, but on average you use only 20% of your CPU capacity.
CPU-time is priced at *$0.00002 per vCPU-second*.
Previously, you would be charged for the CPU allocated to the instance multiplied by the time it was active, in this case 1 hour.
CPU cost would have been: **$0.072** — 1 vCPU \* 3600 seconds \* $0.00002
Now, since you are only using 20% of your CPU capacity, your CPU cost is cut to 20% of the previous amount.
CPU cost is now: **$0.0144** — 1 vCPU \* 3600 seconds \* $0.00002 \* 20% utilization
This can significantly reduce costs for Containers and Sandboxes.
Note
Memory cost and disk pricing remain unchanged, and is still calculated based on *provisioned* resources.
See the documentation to learn more about [Containers](https://developers.cloudflare.com/containers/get-started/), [Sandboxes](https://developers.cloudflare.com/sandbox/), and [associated pricing](https://developers.cloudflare.com/containers/pricing).
---
title: Threat insights are now available in the Threat Events platform · Changelog
description: Threat events users can now access threat insights curated by our
threat intelligence analysts
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-21-threat-events-now-show-events-insights/
md: https://developers.cloudflare.com/changelog/2025-11-21-threat-events-now-show-events-insights/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Threat insights are now available in the Threat Events platform
Nov 21, 2025
[Security Center](https://developers.cloudflare.com/security-center/)
The threat events platform now has threat insights available for some relevant parent events. Threat intelligence analyst users can access these insights for their threat hunting activity. Insights are also highlighted in the Cloudflare dashboard by a small `lightning icon` and the insights can refer to multiple, connected events, potentially part of the same attack or campaign and associated with the same threat actor.
For more information, refer to [Analyze threat events](https://developers.cloudflare.com/security-center/cloudforce-one/#analyze-threat-events).
---
title: Better local deployment flow for Cloudflare Workers · Changelog
description: Wrangler now provides a better user experience when deploying a
worker that was previously deployed via the Cloudflare dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-21-wrangler-deploy-remote-config-management/
md: https://developers.cloudflare.com/changelog/2025-11-21-wrangler-deploy-remote-config-management/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Better local deployment flow for Cloudflare Workers
Nov 21, 2025
[Workers](https://developers.cloudflare.com/workers/)
Until now, if a Worker had been previously deployed via the [Cloudflare Dashboard](https://dash.cloudflare.com), a subsequent deployment done via the Cloudflare Workers CLI, [**Wrangler**](https://developers.cloudflare.com/workers/wrangler/) (through the [`deploy` command](https://developers.cloudflare.com/workers/wrangler/commands/#deploy)), would allow the user to override the Worker's dashboard settings without providing details on what dashboard settings would be lost.
Now instead, `wrangler deploy` presents a helpful representation of the differences between the [local configuration](https://developers.cloudflare.com/workers/wrangler/configuration/) and the remote dashboard settings, and offers to update your local configuration file for you.
See example below showing a before and after for `wrangler deploy` when a local configuration is expected to override a Worker's dashboard settings:
Before
After

Also, if instead Wrangler detects that a deployment would override remote dashboard settings but in an additive way, without modifying or removing any of them, it will simply proceed with the deployment without requesting any user interaction.
Update to [Wrangler](https://developers.cloudflare.com/workers/wrangler/) v4.50.0 or greater to take advantage of this improved deploy flow.
---
title: Cloud Services Observability in Cloudflare Radar · Changelog
description: New HTTP Origins insights in Cloudflare Radar, including service
status, traffic, and connectivity metrics
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-24-radar-cloud-observability/
md: https://developers.cloudflare.com/changelog/2025-11-24-radar-cloud-observability/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloud Services Observability in Cloudflare Radar
Nov 24, 2025
[Radar](https://developers.cloudflare.com/radar/)
[**Radar**](https://developers.cloudflare.com/radar/) introduces HTTP Origins insights, providing visibility into the status of traffic between Cloudflare's global network and cloud-based origin infrastructure.
The new [`Origins`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/) API provides provides the following endpoints:
* [`/origins`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/list/) - Lists all origins (cloud providers and associated regions).
* [`/origins/{origin}`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/get/) - Retrieves information about a specific origin (cloud provider).
* [`/origins/timeseries`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/timeseries/) - Retrieves normalized time series data for a specific origin, including the following metrics:
* `REQUESTS`: Number of requests
* `CONNECTION_FAILURES`: Number of connection failures
* `RESPONSE_HEADER_RECEIVE_DURATION`: Duration of the response header receive
* `TCP_HANDSHAKE_DURATION`: Duration of the TCP handshake
* `TCP_RTT`: TCP round trip time
* `TLS_HANDSHAKE_DURATION`: Duration of the TLS handshake
* [`/origins/summary`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/summary/) - Retrieves HTTP requests to origins summarized by a dimension.
* [`/origins/timeseries_groups`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/methods/timeseries_groups/) - Retrieves timeseries data for HTTP requests to origins grouped by a dimension.
The following dimensions are available for the `summary` and `timeseries_groups` endpoints:
* `region`: Origin region
* `success_rate`: Success rate of requests (2XX versus 5XX response codes)
* `percentile`: Percentiles of metrics listed above
Additionally, the [`Annotations`](https://developers.cloudflare.com/api/resources/radar/subresources/annotations/) and [`Traffic Anomalies`](https://developers.cloudflare.com/api/resources/radar/subresources/traffic_anomalies/) APIs have been extended to support origin outages and anomalies, enabling automated detection and alerting for origin infrastructure issues.

Check out the [new Radar page](https://radar.cloudflare.com/cloud-observatory).
---
title: WAF Release - 2025-11-24 · Changelog
description: Cloudflare WAF managed rulesets 2025-11-24 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-24-waf-release/
md: https://developers.cloudflare.com/changelog/2025-11-24-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-11-24
Nov 24, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week highlights enhancements to detection signatures improving coverage for vulnerabilities in FortiWeb, linked to CVE-2025-64446, alongside new detection logic expanding protection against PHP Wrapper Injection techniques.
**Key Findings**
This vulnerability enables an unauthenticated attacker to bypass access controls by abusing the `CGIINFO` header. The latest update strengthens detection logic to ensure a reliable identification of crafted requests attempting to exploit this flaw.
**Impact**
* FortiWeb (CVE-2025-64446): Exploitation allows a remote unauthenticated adversary to circumvent authentication mechanisms by sending a manipulated `CGIINFO` header to FortiWeb’s backend CGI handler. Successful exploitation grants unintended access to restricted administrative functionality, potentially enabling configuration tampering or system-level actions.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | b957ace6e9844bf29244401c4e2e1a2e | N/A | FortiWeb - Authentication Bypass via CGIINFO Header - CVE:CVE-2025-64446 | Log | Block | This is a new detection |
| Cloudflare Managed Ruleset | e3871391a93248fa98a78e03b6c44ed5 | N/A | PHP Wrapper Injection - Body - Beta | Log | Disabled | This rule has been merged into the original rule "PHP Wrapper Injection - Body" (ID:fae6fa37ae9249d58628e54b1a3e521e ) |
| Cloudflare Managed Ruleset | e6b1b66e0e3b46969102baed900f4015 | N/A | PHP Wrapper Injection - URI - Beta | Log | Disabled | This rule has been merged into the original rule "PHP Wrapper Injection - URI" (ID:9c02e585db34440da620eb668f76bd74 ) |
---
title: Audit Logs for Cache Purge Events · Changelog
description: Review detailed logs of cache purge requests to track activity and
verify content revalidation targets.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-25-audit-logs-for-cache-purge-events/
md: https://developers.cloudflare.com/changelog/2025-11-25-audit-logs-for-cache-purge-events/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Audit Logs for Cache Purge Events
Nov 25, 2025
[Cache / CDN](https://developers.cloudflare.com/cache/)
You can now review detailed audit logs for cache purge events, giving you visibility into what purge requests were sent, what they contained, and by whom. Audit your purge requests via the Dashboard or API for all purge methods:
* Purge everything
* List of prefixes
* List of tags
* List of hosts
* List of files
#### Example
The detailed audit payload is visible within the Cloudflare Dashboard (under **Manage Account** > **Audit Logs**) and via the API. Below is an example of the Audit Logs v2 payload structure:
```json
{
"action": {
"result": "success",
"type": "create"
},
"actor": {
"id": "1234567890abcdef",
"email": "user@example.com",
"type": "user"
},
"resource": {
"product": "purge_cache",
"request": {
"files": [
"https://example.com/images/logo.png",
"https://example.com/css/styles.css"
]
}
},
"zone": {
"id": "023e105f4ecef8ad9ca31a8372d0c353",
"name": "example.com"
}
}
```
#### Get started
To get started, refer to the [Audit Logs documentation](https://developers.cloudflare.com/fundamentals/account/account-security/audit-logs/).
---
title: Launching FLUX.2 [dev] on Workers AI · Changelog
description: Partnering with Black Forest Labs to bring their latest FLUX.2
model to Workers AI
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-25-flux-2-dev-workers-ai/
md: https://developers.cloudflare.com/changelog/2025-11-25-flux-2-dev-workers-ai/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Launching FLUX.2 \[dev] on Workers AI
Nov 25, 2025
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We've partnered with Black Forest Labs (BFL) to bring their latest FLUX.2 \[dev] model to Workers AI! This model excels in generating high-fidelity images with physical world grounding, multi-language support, and digital asset creation. You can also create specific super images with granular controls like JSON prompting.
Read the [BFL blog](https://bfl.ai/flux2) to learn more about the model itself. Read our [Cloudflare blog](https://blog.cloudflare.com/flux-2-workers-ai) to see the model in action, or try it out yourself on our [multi modal playground](https://multi-modal.ai.cloudflare.com/).
Pricing documentation is available on the [model page](https://developers.cloudflare.com/workers-ai/models/flux-2-dev/) or [pricing page](https://developers.cloudflare.com/workers-ai/platform/pricing/). Note, we expect to drop pricing in the next few days after iterating on the model performance.
#### Workers AI Platform specifics
The model hosted on Workers AI is able to support up to 4 image inputs (512x512 per input image). Note, this image model is one of the most powerful in the catalog and is expected to be slower than the other image models we currently support. One catch to look out for is that this model takes multipart form data inputs, even if you just have a prompt.
With the REST API, the multipart form data input looks like this:
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-dev' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=a sunset at the alps' \
--form steps=25
--form width=1024
--form height=1024
```
With the Workers AI binding, you can use it as such:
```javascript
const form = new FormData();
form.append('prompt', 'a sunset with a dog');
form.append('width', '1024');
form.append('height', '1024');
//this dummy request is temporary hack
//we're pushing a change to address this soon
const formRequest = new Request('http://dummy', {
method: 'POST',
body: form
});
const formStream = formRequest.body;
const formContentType = formRequest.headers.get('content-type') || 'multipart/form-data';
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-dev", {
multipart: {
body: formStream,
contentType: formContentType
}
});
```
The parameters you can send to the model are detailed here:
JSON Schema for Model
**Required Parameters**
* `prompt` (string) - Text description of the image to generate
**Optional Parameters**
* `input_image_0` (string) - Binary image
* `input_image_1` (string) - Binary image
* `input_image_2` (string) - Binary image
* `input_image_3` (string) - Binary image
* `steps` (integer) - Number of inference steps. Higher values may improve quality but increase generation time
* `guidance` (float) - Guidance scale for generation. Higher values follow the prompt more closely
* `width` (integer) - Width of the image, default `1024` Range: 256-1920
* `height` (integer) - Height of the image, default `768` Range: 256-1920
* `seed` (integer) - Seed for reproducibility
````plaintext
## Multi-Reference Images
The FLUX.2 model is great at generating images based on reference images. You can use this feature to apply the style of one image to another, add a new character to an image, or iterate on past generate images. You would use it with the same multipart form data structure, with the input images in binary.
For the prompt, you can reference the images based on the index, like `take the subject of image 1 and style it like image 0` or even use natural language like `place the dog beside the woman`.
Note: you have to name the input parameter as `input_image_0`, `input_image_1`, `input_image_2` for it to work correctly. All input images must be smaller than 512x512.
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-dev' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=take the subject of image 1 and style it like image 0' \
--form input_image_0=@/Users/johndoe/Desktop/icedoutkeanu.png \
--form input_image_1=@/Users/johndoe/Desktop/me.png \
--form steps=25
--form width=1024
--form height=1024
````
Through Workers AI Binding:
```javascript
//helper function to convert ReadableStream to Blob
async function streamToBlob(stream: ReadableStream, contentType: string): Promise {
const reader = stream.getReader();
const chunks = [];
while (true) {
const { done, value } = await reader.read();
if (done) break;
chunks.push(value);
}
return new Blob(chunks, { type: contentType });
}
const image0 = await fetch("http://image-url");
const image1 = await fetch("http://image-url");
const form = new FormData();
const image_blob0 = await streamToBlob(image0.body, "image/png");
const image_blob1 = await streamToBlob(image1.body, "image/png");
form.append('input_image_0', image_blob0)
form.append('input_image_1', image_blob1)
form.append('prompt', 'take the subject of image 1and style it like image 0')
//this dummy request is temporary hack
//we're pushing a change to address this soon
const formRequest = new Request('http://dummy', {
method: 'POST',
body: form
});
const formStream = formRequest.body;
const formContentType = formRequest.headers.get('content-type') || 'multipart/form-data';
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-dev", {
multipart: {
body: form,
contentType: "multipart/form-data"
}
})
```
#### JSON Prompting
The model supports prompting in JSON to get more granular control over images. You would pass the JSON as the value of the 'prompt' field in the multipart form data. See the JSON schema below on the base parameters you can pass to the model.
JSON Prompting Schema
```json
{
"type": "object",
"properties": {
"scene": {
"type": "string",
"description": "Overall scene setting or location"
},
"subjects": {
"type": "array",
"items": {
"type": "object",
"properties": {
"type": {
"type": "string",
"description": "Type of subject (e.g., desert nomad, blacksmith, DJ, falcon)"
},
"description": {
"type": "string",
"description": "Physical attributes, clothing, accessories"
},
"pose": {
"type": "string",
"description": "Action or stance"
},
"position": {
"type": "string",
"enum": ["foreground", "midground", "background"],
"description": "Depth placement in scene"
}
},
"required": ["type", "description", "pose", "position"]
}
},
"style": {
"type": "string",
"description": "Artistic rendering style (e.g., digital painting, photorealistic, pixel art, noir sci-fi, lifestyle photo, wabi-sabi photo)"
},
"color_palette": {
"type": "array",
"items": { "type": "string" },
"minItems": 3,
"maxItems": 3,
"description": "Exactly 3 main colors for the scene (e.g., ['navy', 'neon yellow', 'magenta'])"
},
"lighting": {
"type": "string",
"description": "Lighting condition and direction (e.g., fog-filtered sun, moonlight with star glints, dappled sunlight)"
},
"mood": {
"type": "string",
"description": "Emotional atmosphere (e.g., harsh and determined, playful and modern, peaceful and dreamy)"
},
"background": {
"type": "string",
"description": "Background environment details"
},
"composition": {
"type": "string",
"enum": [
"rule of thirds",
"circular arrangement",
"framed by foreground",
"minimalist negative space",
"S-curve",
"vanishing point center",
"dynamic off-center",
"leading leads",
"golden spiral",
"diagonal energy",
"strong verticals",
"triangular arrangement"
],
"description": "Compositional technique"
},
"camera": {
"type": "object",
"properties": {
"angle": {
"type": "string",
"enum": ["eye level", "low angle", "slightly low", "bird's-eye", "worm's-eye", "over-the-shoulder", "isometric"],
"description": "Camera perspective"
},
"distance": {
"type": "string",
"enum": ["close-up", "medium close-up", "medium shot", "medium wide", "wide shot", "extreme wide"],
"description": "Framing distance"
},
"focus": {
"type": "string",
"enum": ["deep focus", "macro focus", "selective focus", "sharp on subject", "soft background"],
"description": "Focus type"
},
"lens": {
"type": "string",
"enum": ["14mm", "24mm", "35mm", "50mm", "70mm", "85mm"],
"description": "Focal length (wide to telephoto)"
},
"f-number": {
"type": "string",
"description": "Aperture (e.g., f/2.8, the smaller the number the more blurry the background)"
},
"ISO": {
"type": "number",
"description": "Light sensitivity value (comfortable range between 100 & 6400, lower = less sensitivity)"
}
}
},
"effects": {
"type": "array",
"items": { "type": "string" },
"description": "Post-processing effects (e.g., 'lens flare small', 'subtle film grain', 'soft bloom', 'god rays', 'chromatic aberration mild')"
}
},
"required": ["scene", "subjects"]
}
```
#### Other features to try
* The model also supports the most common latin and non-latin character languages
* You can prompt the model with specific hex codes like `#2ECC71`
* Try creating digital assets like landing pages, comic strips, infographics too!
---
title: Agents SDK v0.2.24 with resumable streaming, MCP improvements, and
schedule fixes · Changelog
description: This release adds resumable streaming over websockets, enhanced MCP
client APIs with connection state observability, improved schedule
reliability, and SSE transport enhancements.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-11-26-agents-resumable-streaming/
md: https://developers.cloudflare.com/changelog/2025-11-26-agents-resumable-streaming/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Agents SDK v0.2.24 with resumable streaming, MCP improvements, and schedule fixes
Nov 26, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
The latest release of [@cloudflare/agents](https://github.com/cloudflare/agents) brings resumable streaming, significant MCP client improvements, and critical fixes for schedules and Durable Object lifecycle management.
#### Resumable streaming
`AIChatAgent` now supports resumable streaming, allowing clients to reconnect and continue receiving streamed responses without losing data. This is useful for:
* Long-running AI responses
* Users on unreliable networks
* Users switching between devices mid-conversation
* Background tasks where users navigate away and return
* Real-time collaboration where multiple clients need to stay in sync
Streams are maintained across page refreshes, broken connections, and syncing across open tabs and devices.
#### Other improvements
* Default JSON schema validator added to MCP client
* [Schedules](https://developers.cloudflare.com/agents/api-reference/schedule-tasks/) can now safely destroy the agent
#### MCP client API improvements
The `MCPClientManager` API has been redesigned for better clarity and control:
* **New `registerServer()` method**: Register MCP servers without immediately connecting
* **New `connectToServer()` method**: Establish connections to registered servers
* **Improved reconnect logic**: `restoreConnectionsFromStorage()` now properly handles failed connections
```ts
// Register a server to Agent
const { id } = await this.mcp.registerServer({
name: "my-server",
url: "https://my-mcp-server.example.com",
});
// Connect when ready
await this.mcp.connectToServer(id);
// Discover tools, prompts and resources
await this.mcp.discoverIfConnected(id);
```
The SDK now includes a formalized `MCPConnectionState` enum with states: `idle`, `connecting`, `authenticating`, `connected`, `discovering`, and `ready`.
#### Enhanced MCP discovery
MCP discovery fetches the available tools, prompts, and resources from an MCP server so your agent knows what capabilities are available. The `MCPClientConnection` class now includes a dedicated `discover()` method with improved reliability:
* Supports cancellation via AbortController
* Configurable timeout (default 15s)
* Discovery failures now throw errors immediately instead of silently continuing
#### Bug fixes
* Fixed a bug where [schedules](https://developers.cloudflare.com/agents/api-reference/schedule-tasks/) meant to fire immediately with this.schedule(0, ...) or `this.schedule(new Date(), ...)` would not fire
* Fixed an issue where schedules that took longer than 30 seconds would occasionally time out
* Fixed SSE transport now properly forwards session IDs and request headers
* Fixed AI SDK stream events convertion to UIMessageStreamPart
#### Upgrade
To update to the latest version:
```sh
npm i agents@latest
```
---
title: Build image policies for Workers Builds and Cloudflare Pages · Changelog
description: Workers Builds and Cloudflare Pages now have documented build image
policies outlining deprecation timelines and version update procedures.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-01-build-image-policies-dev-plat/
md: https://developers.cloudflare.com/changelog/2025-12-01-build-image-policies-dev-plat/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Build image policies for Workers Builds and Cloudflare Pages
Dec 18, 2025
[Workers](https://developers.cloudflare.com/workers/)
We've published build image policies for [Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/build-image/#build-image-policy) and [Cloudflare Pages](https://developers.cloudflare.com/pages/configuration/build-image/#build-image-policy), which establish:
* **Minor version updates**: We typically update preinstalled software to the latest available minor version without notice. For tools that don't follow semantic versioning (e.g., Bun or Hugo), we provide 3 months’ notice.
* **Major version updates**: Before preinstalled software reaches end-of-life, we update to the next stable LTS version with 3 months’ notice.
* **Build image version deprecation (Pages only)**: We provide 6 months’ notice before deprecation. Projects on v1 or v2 will be automatically moved to v3 on their specified deprecation dates.
To prepare for updates, monitor the [Cloudflare Changelog](https://developers.cloudflare.com/changelog/), dashboard notifications, and email. You can also [override default versions](https://developers.cloudflare.com/workers/ci-cd/builds/build-image/#overriding-default-versions) to maintain specific versions.
---
title: WAF Release - 2025-12-01 · Changelog
description: Cloudflare WAF managed rulesets 2025-12-01 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-01-waf-release/
md: https://developers.cloudflare.com/changelog/2025-12-01-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-12-01
Dec 01, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces new detections for remote code execution attempts targeting Monsta FTP (CVE-2025-34299), alongside improvements to an existing XSS detection to enhance coverage.
**Key Findings**
* CVE-2025-34299 is a critical remote code execution flaw in Monsta FTP, arising from improper handling of user-supplied parameters within the file-handling interface. Certain builds allow crafted requests to bypass sanitization and reach backend PHP functions that execute arbitrary commands. Attackers can send manipulated parameters through the web panel to trigger command execution within the application’s runtime environment.
**Impact**
If exploited, the vulnerability enables full remote command execution on the underlying server, allowing takeover of the hosting environment, unauthorized file access, and potential lateral movement. As the flaw can be triggered without authentication on exposed Monsta FTP instances, it represents a severe risk for publicly reachable deployments.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 480da5e7984542a6b8d8d88da4fcc8a8 | N/A | Monsta FTP - Remote Code Execution - CVE:CVE-2025-34299 | Log | Block | This is a new detection |
| Cloudflare Managed Ruleset | 2380b125c53d42ac94479c42b7492846 | N/A | XSS - JS Context Escape - Beta | Log | Block | This rule is merged into the original rule "XSS - JS Context Escape" (ID: c1ad1bc37caa4cbeb104f44f7a3769d3 ) |
---
title: WAF Release - 2025-12-02 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-12-02 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-02-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-12-02-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-12-02 - Emergency
Dec 02, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's emergency release introduces a new rule to block a critical RCE vulnerability in widely-used web frameworks through unsafe deserialization patterns.
**Key Findings**
New WAF rule deployed for RCE Generic Framework to block malicious POST requests containing unsafe deserialization patterns. If successfully exploited, this vulnerability allows attackers with network access via HTTP to execute arbitrary code remotely.
**Impact**
* Successful exploitation allows unauthenticated attackers to execute arbitrary code remotely through crafted serialization payloads, enabling complete system compromise, data exfiltration, and potential lateral movement within affected environments.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 33aa8a8a948b48b28d40450c5fb92fba | N/A | RCE Generic - Framework | N/A | Block | This is a new detection. |
| Cloudflare Free Ruleset | 2b5d06e34a814a889bee9a0699702280 | N/A | RCE Generic - Framework | N/A | Block | This is a new detection. |
---
title: WAF Release - 2025-12-03 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-12-03 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-03-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-12-03-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-12-03 - Emergency
Dec 03, 2025
[WAF](https://developers.cloudflare.com/waf/)
The WAF rule deployed yesterday to block unsafe deserialization-based RCE has been updated. The rule description now reads “React – RCE – CVE-2025-55182”, explicitly mapping to the recently disclosed React Server Components vulnerability. Detection logic remains unchanged.
**Key Findings**
Rule description updated to reference React – RCE – CVE-2025-55182 while retaining existing unsafe-deserialization detection.
**Impact**
Improved classification and traceability with no change to coverage against remote code execution attempts.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 33aa8a8a948b48b28d40450c5fb92fba | N/A | React - RCE - CVE:CVE-2025-55182 | N/A | Block | Rule metadata description changed. Detection unchanged. |
| Cloudflare Free Ruleset | 2b5d06e34a814a889bee9a0699702280 | N/A | React - RCE - CVE:CVE-2025-55182 | N/A | Block | Rule metadata description changed. Detection unchanged. |
---
title: One-click Access protection for Workers now creates reusable Cloudflare
Access policies · Changelog
description: Workers now use reusable Access policies to reduce duplication and
make it easier to manage access across multiple Workers.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-03-reusable-access-policies/
md: https://developers.cloudflare.com/changelog/2025-12-03-reusable-access-policies/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## One-click Access protection for Workers now creates reusable Cloudflare Access policies
Dec 04, 2025
[Workers](https://developers.cloudflare.com/workers/)
Workers applications now use reusable [Cloudflare Access policies](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) to reduce duplication and simplify access management across multiple Workers.
Previously, enabling Cloudflare Access on a Worker created per-application policies, unique to each application. Now, we create reusable policies that can be shared across applications:
* **Preview URLs**: All Workers preview URLs share a single "Cloudflare Workers Preview URLs" policy across your account. This policy is automatically created the first time you enable Access on any preview URL. By sharing a single policy across all preview URLs, you can configure access rules once and have them apply company-wide to all Workers which protect preview URLs. This makes it much easier to manage who can access preview environments without having to update individual policies for each Worker.
* **Production workers.dev URLs**: When enabled, each Worker gets its own reusable policy (named ` - Production`) by default. We recognize production services often have different access requirements and having individual policies here makes it easier to configure service-to-service authentication or protect internal dashboards or applications with specific user groups. Keeping these policies separate gives you the flexibility to configure exactly the right access rules for each production service. When you disable Access on a production Worker, the associated policy is automatically cleaned up if it's not being used by other applications.
This change reduces policy duplication, simplifies cross-company access management for preview environments, and provides the flexibility needed for production services. You can still customize access rules by editing the reusable policies in the Zero Trust dashboard.
To enable Cloudflare Access on your Worker:
1. In the Cloudflare dashboard, go to **Workers & Pages**.
2. Select your Worker.
3. Go to **Settings** > **Domains & Routes**.
4. For `workers.dev` or Preview URLs, click **Enable Cloudflare Access**.
5. Optionally, click **Manage Cloudflare Access** to customize the policy.
For more information on configuring Cloudflare Access for Workers, refer to the [Workers Access documentation](https://developers.cloudflare.com/workers/configuration/routing/workers-dev/#cloudflare-access).
---
title: Reclassifications to Submissions · Changelog
description: Submission terminology update to reflect outcomes
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-03-submission-terminology-update/
md: https://developers.cloudflare.com/changelog/2025-12-03-submission-terminology-update/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Reclassifications to Submissions
Dec 03, 2025
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
We have updated the terminology “Reclassify” and “Reclassifications” to “Submit” and “Submissions” respectively. This update more accurately reflects the outcome of providing these items to Cloudflare.
Submissions are leveraged to tune future variants of campaigns. To respect data sanctity, providing a submission does not change the original disposition of the emails submitted.

This applies to all Email Security packages:
* **Advantage**
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Connect to remote databases during local development with wrangler dev ·
Changelog
description: You can now connect directly to remote databases from wrangler dev
using localConnectionString, with TLS support enabling secure connections
while keeping your Worker code running locally
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-04-hyperdrive-remote-database-local-dev/
md: https://developers.cloudflare.com/changelog/2025-12-04-hyperdrive-remote-database-local-dev/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Connect to remote databases during local development with wrangler dev
Dec 04, 2025
[Hyperdrive](https://developers.cloudflare.com/hyperdrive/)
You can now connect directly to remote databases and databases requiring TLS with `wrangler dev`. This lets you run your Worker code locally while connecting to remote databases, without needing to use `wrangler dev --remote`.
The `localConnectionString` field and `CLOUDFLARE_HYPERDRIVE_LOCAL_CONNECTION_STRING_` environment variable can be used to configure the connection string used by `wrangler dev`.
```jsonc
{
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "your-hyperdrive-id",
"localConnectionString": "postgres://user:password@remote-host.example.com:5432/database?sslmode=require"
}
]
}
```
Learn more about [local development with Hyperdrive](https://developers.cloudflare.com/hyperdrive/configuration/local-development/).
---
title: Increased WAF payload limit for all plans · Changelog
description: Updating WAF to run on requests body of up to 1 MB
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-05-rcs-vuln/
md: https://developers.cloudflare.com/changelog/2025-12-05-rcs-vuln/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased WAF payload limit for all plans
Dec 05, 2025
[WAF](https://developers.cloudflare.com/waf/)
Cloudflare WAF now inspects request-payload size of up to 1 MB across all plans to enhance our detection capabilities for React RCE (CVE-2025-55182).
**Key Findings**
React payloads commonly have a default maximum size of 1 MB. Cloudflare WAF previously inspected up to 128 KB on Enterprise plans, with even lower limits on other plans.
**Update:** We later reinstated the maximum request-payload size the Cloudflare WAF inspects. Refer to [Updating the WAF maximum payload values](https://developers.cloudflare.com/changelog/2025-12-05-waf-max-payload-size-change/) for details.
---
title: Terraform v5.14.0 now available · Changelog
description: Terraform v5.14.0 stabilizes a number of resources and known issues
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-05-terraform-v5140-provider/
md: https://developers.cloudflare.com/changelog/2025-12-05-terraform-v5140-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.14.0 now available
Dec 05, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new Terraform v5 Provider. We are aware of the high number of issues reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) to ensure its stability and reliability, including the v5.14 release. We have also pivoted from an [issue-to-issue approach to a resource-per-resource approach](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) - we will be focusing on specific resources to not only stabilize the resource but also ensure it is migration-friendly for those migrating from v4 to v5.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes bug fixes, the stabilization of even more popular resources, and more.
#### Deprecation notice
Resource affected: `api_shield_discovery_operation`
Cloudflare continuously discovers and updates API endpoints and web assets of your web applications. To improve the maintainability of these dynamic resources, we are working on reducing the need to actively engage with discovered operations.
The corresponding public API endpoint of [discovered operations](https://developers.cloudflare.com/api/resources/api_gateway/subresources/discovery/subresources/operations/) is not affected and will continue to be supported.
#### Features
* **pages\_project**: Add v4 -> v5 migration tests ([#6506](https://github.com/cloudflare/terraform-provider-cloudflare/pull/6506))
#### Bug fixes
* **account\_members**: Makes member policies a set ([#6488](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6488))
* **pages\_project**: Ensures non empty refresh plans ([#6515](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6515))
* **R2**: Improves sweeper ([#6512](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6512))
* **workers\_kv**: Ignores value import state for verify ([#6521](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6521))
* **workers\_script**: No longer treats the migrations attribute as WriteOnly ([#6489](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6489))
* **workers\_script**: Resolves resource drift when worker has unmanaged secret ([#6504](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6504))
* **zero\_trust\_device\_posture\_rule**: Preserves input.version and other fields ([#6500](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6500)) and ([#6503](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6503))
* **zero\_trust\_dlp\_custom\_profile**: Adds sweepers for `dlp_custom_profile`
* **zone\_subscription|account\_subscription**: Adds `partners_ent` as valid enum for `rate_plan.id` ([#6505](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6505))
* **zone**: Ensures datasource model schema parity ([#6487](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6487))
* **subscription**: Updates import signature to accept account\_id/subscription\_id to import account subscription ([#6510](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6510))
#### Upgrade to newer version
We suggest waiting to migrate to v5 while we work on stabilization. This helps with avoiding any blocking issues while the Terraform resources are actively being [stabilized](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237). We will be releasing a new migration tool in March 2026 to help support v4 to v5 transitions for our most popular resources.
#### For more information
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: Updating the WAF maximum payload values · Changelog
description: We are changing the maximum request-payload size inspected by the
Cloudflare WAF
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-05-waf-max-payload-size-change/
md: https://developers.cloudflare.com/changelog/2025-12-05-waf-max-payload-size-change/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Updating the WAF maximum payload values
Dec 05, 2025
[WAF](https://developers.cloudflare.com/waf/)
We are reinstating the maximum request-payload size the Cloudflare WAF inspects, with WAF on Enterprise zones inspecting up to 128 KB.
**Key Findings**
On [December 5, 2025](https://developers.cloudflare.com/changelog/2025-12-05-rcs-vuln/), we initially attempted to increase the maximum WAF payload limit to 1 MB across all plans. However, an automatic rollout for all customers proved impractical because the increase led to a surge in false positives for existing managed rules.
This issue was particularly notable within the Cloudflare Managed Ruleset and the Cloudflare OWASP Core Ruleset, impacting customer traffic.
**Impact**
Customers on paid plans can increase the limit to 1 MB for any of their zones by contacting Cloudflare Support. Free zones are already protected up to 1 MB and do not require any action.
---
title: Python cold start improvements · Changelog
description: Improved Python Worker cold start performance
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-08-python-cold-start-improvements/
md: https://developers.cloudflare.com/changelog/2025-12-08-python-cold-start-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Python cold start improvements
Dec 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
Python Workers now feature improved cold start performance, reducing initialization time for new Worker instances. This improvement is particularly noticeable for Workers with larger dependency sets or complex initialization logic.
Every time you deploy a Python Worker, a memory snapshot is captured after the top level of the Worker is executed. This snapshot captures all imports, including package imports that are often costly to load. The memory snapshot is loaded when the Worker is first started, avoiding the need to reload the Python runtime and all dependencies on each cold start.
We set up a benchmark that imports common packages ([httpx](https://www.python-httpx.org/), [fastapi](https://fastapi.tiangolo.com/) and [pydantic](https://docs.pydantic.dev/latest/)) to see how Python Workers stack up against other platforms:
| Platform | Mean Cold Start (ms) |
| - | - |
| Cloudflare Python Workers | 1027 |
| AWS Lambda | 2502 |
| Google Cloud Run | 3069 |
These benchmarks run continuously. You can view the results and the methodology on our [benchmark page](https://cold.edgeworker.net).
In additional testing, we have found that without any memory snapshot, the cold start for this benchmark takes around 10 seconds, so this change improves cold start performance by roughly a factor of 10.
To get started with Python Workers, check out our [Python Workers overview](https://developers.cloudflare.com/workers/languages/python/).
---
title: Easy Python package management with Pywrangler · Changelog
description: Simplified Python package management in Python Workers using Pywrangler
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-08-python-pywrangler/
md: https://developers.cloudflare.com/changelog/2025-12-08-python-pywrangler/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Easy Python package management with Pywrangler
Dec 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
We are introducing a brand new tool called Pywrangler, which simplifies package management in Python Workers by automatically installing Workers-compatible Python packages into your project.
With Pywrangler, you specify your Worker's Python dependencies in your `pyproject.toml` file:
```toml
[project]
name = "python-beautifulsoup-worker"
version = "0.1.0"
description = "A simple Worker using beautifulsoup4"
requires-python = ">=3.12"
dependencies = [
"beautifulsoup4"
]
[dependency-groups]
dev = [
"workers-py",
"workers-runtime-sdk"
]
```
You can then develop and deploy your Worker using the following commands:
```bash
uv run pywrangler dev
uv run pywrangler deploy
```
Pywrangler automatically downloads and vendors the necessary packages for your Worker, and these packages are bundled with the Worker when you deploy.
Consult the [Python packages documentation](https://developers.cloudflare.com/workers/languages/python/packages/) for full details on Pywrangler and Python package management in Workers.
---
title: Wrangler config is optional when using Vite plugin · Changelog
description: When using the Cloudflare Vite plugin in an assets-only (static)
site, a Wrangler configuration file is now optional.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-08-vite-optional-config/
md: https://developers.cloudflare.com/changelog/2025-12-08-vite-optional-config/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Wrangler config is optional when using Vite plugin
Dec 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
When using the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/) to build and deploy Workers, a Wrangler configuration file is now optional for assets-only (static) sites. If no `wrangler.toml`, `wrangler.json`, or `wrangler.jsonc` file is found, the plugin generates sensible defaults for an assets-only site. The `name` is based on the `package.json` or the project directory name, and the `compatibility_date` uses the latest date supported by your installed Miniflare version.
This allows easier setup for static sites using Vite. Note that SPAs will still need to [set `assets.not_found_handling` to `single-page-application`](https://developers.cloudflare.com/workers/static-assets/routing/single-page-application/) in order to function correctly.
---
title: Configure Workers programmatically using the Vite plugin · Changelog
description: The Cloudflare Vite plugin can now programmatically configure
Workers without a Wrangler config file, or modify existing configuration.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-08-vite-programmatic-config/
md: https://developers.cloudflare.com/changelog/2025-12-08-vite-programmatic-config/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Configure Workers programmatically using the Vite plugin
Dec 08, 2025
[Workers](https://developers.cloudflare.com/workers/)
The [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/) now supports programmatic configuration of Workers without a Wrangler configuration file. You can use the `config` option to define Worker settings directly in your Vite configuration, or to modify existing configuration loaded from a Wrangler config file. This is particularly useful when integrating with other build tools or frameworks, as it allows them to control Worker configuration without needing users to manage a separate config file.
#### The `config` option
The Vite plugin's new `config` option accepts either a partial configuration object or a function that receives the current configuration and returns overrides. This option is applied after any config file is loaded, allowing the plugin to override specific values or define Worker configuration entirely in code.
#### Example usage
Setting `config` to an object to provide configuration values that merge with defaults and config file settings:
```ts
import { defineConfig } from "vite";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [
cloudflare({
config: {
name: "my-worker",
compatibility_flags: ["nodejs_compat"],
send_email: [
{
name: "EMAIL",
},
],
},
}),
],
});
```
Use a function to modify the existing configuration:
```ts
import { defineConfig } from "vite";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [
cloudflare({
config: (userConfig) => {
delete userConfig.compatibility_flags;
},
}),
],
});
```
Return an object with values to merge:
```ts
import { defineConfig } from "vite";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [
cloudflare({
config: (userConfig) => {
if (!userConfig.compatibility_flags.includes("no_nodejs_compat")) {
return { compatibility_flags: ["nodejs_compat"] };
}
},
}),
],
});
```
#### Auxiliary Workers
Auxiliary Workers also support the `config` option, enabling multi-Worker architectures without config files.
Define auxiliary Workers without config files using `config` inside the `auxiliaryWorkers` array:
```ts
import { defineConfig } from "vite";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [
cloudflare({
config: {
name: "entry-worker",
main: "./src/entry.ts",
services: [{ binding: "API", service: "api-worker" }],
},
auxiliaryWorkers: [
{
config: {
name: "api-worker",
main: "./src/api.ts",
},
},
],
}),
],
});
```
For more details and examples, see [Programmatic configuration](https://developers.cloudflare.com/workers/vite-plugin/reference/programmatic-configuration/).
---
title: WARP client for macOS (version 2025.10.118.1) · Changelog
description: WARP client for macOS (version 2025.10.118.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-09-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2025-12-09-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.10.118.1)
Dec 09, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
---
title: WARP client for Windows (version 2025.10.118.1) · Changelog
description: WARP client for Windows (version 2025.10.118.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-09-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2025-12-09-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.10.118.1)
Dec 09, 2025
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where sending large messages to the WARP daemon by Inter-Process Communication (IPC) could cause WARP to crash and result in service interruptions.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: WAF Release - 2025-12-10 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-12-10 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-10-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-12-10-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-12-10 - Emergency
Dec 10, 2025
[WAF](https://developers.cloudflare.com/waf/)
This additional week's emergency release introduces improvements to our existing rule for React – Remote Code Execution – CVE-2025-55182 - 2, along with two new generic detections covering server-side function exposure and resource-exhaustion patterns.
**Key Findings**
Enhanced detection logic for React – RCE – CVE-2025-55182, added Generic – Server Function Source Code Exposure, and added Generic – Server Function Resource Exhaustion.
**Impact**
These updates strengthen protection against React RCE exploitation attempts and broaden coverage for common server-function abuse techniques that may expose internal logic or disrupt application availability.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | bc1aee59731c488ca8b5314615fce168 | N/A | React - Remote Code Execution - CVE:CVE-2025-55182 - 2 | N/A | Block | This is an improved detection. |
| Cloudflare Free Ruleset | cbdd3f48396e4b7389d6efd174746aff | N/A | React - Remote Code Execution - CVE:CVE-2025-55182 - 2 | N/A | Block | This is an improved detection. |
| Cloudflare Managed Ruleset | 17c5123f1ac049818765ebf2fefb4e9b | N/A | Generic - Server Function Source Code Exposure | N/A | Block | This is a new detection. |
| Cloudflare Free Ruleset | 3114709a3c3b4e3685052c7b251e86aa | N/A | Generic - Server Function Source Code Exposure | N/A | Block | This is a new detection. |
| Cloudflare Managed Ruleset | 2694f1610c0b471393b21aef102ec699 | N/A | Generic - Server Function Resource Exhaustion | N/A | Disabled | This is a new detection. |
---
title: Pay Per Crawl (Private beta) - Discovery API, custom pricing, and
advanced configuration · Changelog
description: Pay Per Crawl adds Discovery API for crawler content discovery,
custom in-band pricing for dynamic content pricing, granular URI-based
configuration, and enhanced error handling with standardized crawler-error
codes.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-10-pay-per-crawl-enhancements/
md: https://developers.cloudflare.com/changelog/2025-12-10-pay-per-crawl-enhancements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Pay Per Crawl (Private beta) - Discovery API, custom pricing, and advanced configuration
Dec 10, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
Pay Per Crawl is introducing enhancements for both AI crawler operators and site owners, focusing on programmatic discovery, flexible pricing models, and granular configuration control.
#### For AI crawler operators
#### Discovery API
A new authenticated API endpoint allows verified crawlers to programmatically discover domains participating in Pay Per Crawl. Crawlers can use this to build optimized crawl queues, cache domain lists, and identify new participating sites. This eliminates the need to discover payable content through trial requests.
The API endpoint is `GET https://crawlers-api.ai-audit.cfdata.org/charged_zones` and requires Web Bot Auth authentication. Refer to [Discover payable content](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/discover-payable-content/) for authentication steps, request parameters, and response schema.
#### Payment header signature requirement
Payment headers (`crawler-exact-price` or `crawler-max-price`) must now be included in the Web Bot Auth `signature-input` header components. This security enhancement prevents payment header tampering, ensures authenticated payment intent, validates crawler identity with payment commitment, and protects against replay attacks with modified pricing. Crawlers must add their payment header to the list of signed components when [constructing the signature-input header](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/#22-sign-your-request-with-web-bot-auth).
#### New `crawler-error` header
Pay Per Crawl error responses now include a new `crawler-error` header with 11 specific [error codes](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/#error-code-reference) for programmatic handling. Error response bodies remain unchanged for compatibility. These codes enable robust error handling, automated retry logic, and accurate spending tracking.
#### For site owners
#### Configure free pages
Site owners can now offer free access to specific pages like homepages, navigation, or discovery pages while charging for other content. Create a [Configuration Rule](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-site-owner/advanced-configuration/#disable-pay-per-crawl-by-uri-pattern) in **Rules** > **Configuration Rules**, set your URI pattern using wildcard, exact, or prefix matching on the **URI Full** field, and enable the **Disable Pay Per Crawl** setting. When disabled for a URI pattern, crawler requests pass through without blocking or charging.
Some paths are always free to crawl. These paths are: `/robots.txt`, `/sitemap.xml`, `/security.txt`, `/.well-known/security.txt`, `/crawlers.json`.
#### Get started
**AI crawler operators**: [Discover payable content](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/discover-payable-content/) | [Crawl pages](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-ai-owner/crawl-pages/)
**Site owners**: [Advanced configuration](https://developers.cloudflare.com/ai-crawl-control/features/pay-per-crawl/use-pay-per-crawl-as-site-owner/advanced-configuration/)
---
title: Get notified when your Workers builds succeed or fail · Changelog
description: Use Queue Event Subscriptions to receive Workers Builds events and
send notifications to Slack or any destination.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-11-builds-event-subscriptions/
md: https://developers.cloudflare.com/changelog/2025-12-11-builds-event-subscriptions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Get notified when your Workers builds succeed or fail
Jan 09, 2026
[Workers ](https://developers.cloudflare.com/workers/)[Queues](https://developers.cloudflare.com/queues/)
You can now receive notifications when your Workers' builds start, succeed, fail, or get cancelled using [Event Subscriptions](https://developers.cloudflare.com/queues/event-subscriptions/).
[Workers Builds](https://developers.cloudflare.com/workers/ci-cd/builds/) publishes events to a [Queue](https://developers.cloudflare.com/queues/) that your Worker can read messages from, and then send notifications wherever you need — Slack, Discord, email, or any webhook endpoint.
You can deploy [this Worker](https://github.com/cloudflare/templates/tree/main/workers-builds-notifications-template) to your own Cloudflare account to send build notifications to Slack:
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/templates/tree/main/workers-builds-notifications-template)
The template includes:
* Build status with Preview/Live URLs for successful deployments
* Inline error messages for failed builds
* Branch, commit hash, and author name

For setup instructions, refer to the [template README](https://github.com/cloudflare/templates/tree/main/workers-builds-notifications-template#readme) or the [Event Subscriptions documentation](https://developers.cloudflare.com/queues/event-subscriptions/manage-event-subscriptions/).
---
title: WAF Release - 2025-12-11 - Emergency · Changelog
description: Cloudflare WAF managed rulesets 2025-12-11 emergency release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-11-emergency-waf-release/
md: https://developers.cloudflare.com/changelog/2025-12-11-emergency-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-12-11 - Emergency
Dec 11, 2025
[WAF](https://developers.cloudflare.com/waf/)
This emergency release introduces rules for CVE-2025-55183 and CVE-2025-55184, targeting server-side function exposure and resource-exhaustion patterns, respectively.
**Key Findings**
Added coverage for Leaking Server Functions (CVE-2025-55183) and React Function DoS detection (CVE-2025-55184).
**Impact**
These updates strengthen protection for server-function abuse techniques (CVE-2025-55183, CVE-2025-55184) that may expose internal logic or disrupt application availability.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 17c5123f1ac049818765ebf2fefb4e9b | N/A | React - Leaking Server Functions - CVE:CVE-2025-55183 | N/A | Block | This was labeled as Generic - Server Function Source Code Exposure. |
| Cloudflare Free Ruleset | 3114709a3c3b4e3685052c7b251e86aa | N/A | React - Leaking Server Functions - CVE:CVE-2025-55183 | N/A | Block | This was labeled as Generic - Server Function Source Code Exposure. |
| Cloudflare Managed Ruleset | 2694f1610c0b471393b21aef102ec699 | N/A | React - DoS - CVE:CVE-2025-55184 | N/A | Disabled | This was labeled as Generic – Server Function Resource Exhaustion. |
---
title: SentinelOne as Logpush destination · Changelog
description: Enable SentinelOne as a Logpush destination
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-11-sentinelone-destination/
md: https://developers.cloudflare.com/changelog/2025-12-11-sentinelone-destination/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## SentinelOne as Logpush destination
Dec 11, 2025
[Logs](https://developers.cloudflare.com/logs/)
Cloudflare Logpush now supports **SentinelOne** as a native destination.
Logs from Cloudflare can be sent to [SentinelOne AI SIEM](https://www.sentinelone.com/) via [Logpush](https://developers.cloudflare.com/logs/logpush/). The destination can be configured through the Logpush UI in the Cloudflare dashboard or by using the [Logpush API](https://developers.cloudflare.com/api/resources/logpush/subresources/jobs/).
For more information, refer to the [Destination Configuration](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/sentinelone/) documentation.
---
title: R2 SQL now supports aggregations and schema discovery · Changelog
description: Perform aggregations, grouping, and filtering on Apache Iceberg
tables stored in R2 Data Catalog
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-12-aggregation-support-and-more/
md: https://developers.cloudflare.com/changelog/2025-12-12-aggregation-support-and-more/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## R2 SQL now supports aggregations and schema discovery
Dec 12, 2025
[R2 SQL](https://developers.cloudflare.com/r2-sql/)
R2 SQL now supports aggregation functions, `GROUP BY`, `HAVING`, along with schema discovery commands to make it easy to explore your data catalog.
#### Aggregation Functions
You can now perform aggregations on Apache Iceberg tables in [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) using standard SQL functions including `COUNT(*)`, `SUM()`, `AVG()`, `MIN()`, and `MAX()`. Combine these with `GROUP BY` to analyze data across dimensions, and use `HAVING` to filter aggregated results.
```sql
-- Calculate average transaction amounts by department
SELECT department, COUNT(*), AVG(total_amount)
FROM my_namespace.sales_data
WHERE region = 'North'
GROUP BY department
HAVING COUNT(*) > 50
ORDER BY AVG(total_amount) DESC
```
```sql
-- Find high-value departments
SELECT department, SUM(total_amount)
FROM my_namespace.sales_data
GROUP BY department
HAVING SUM(total_amount) > 50000
```
#### Schema Discovery
New metadata commands make it easy to explore your data catalog and understand table structures:
* `SHOW DATABASES` or `SHOW NAMESPACES` - List all available namespaces
* `SHOW TABLES IN namespace_name` - List tables within a namespace
* `DESCRIBE namespace_name.table_name` - View table schema and column types
```bash
❯ npx wrangler r2 sql query "{ACCOUNT_ID}_{BUCKET_NAME}" "DESCRIBE default.sales_data;"
⛅️ wrangler 4.54.0
─────────────────────────────────────────────
┌──────────────────┬────────────────┬──────────┬─────────────────┬───────────────┬───────────────────────────────────────────────────────────────────────────────────────────────────┐
│ column_name │ type │ required │ initial_default │ write_default │ doc │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sale_id │ BIGINT │ false │ │ │ Unique identifier for each sales transaction │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sale_timestamp │ TIMESTAMPTZ │ false │ │ │ Exact date and time when the sale occurred (used for partitioning) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ department │ TEXT │ false │ │ │ Product department (8 categories: Electronics, Beauty, Home, Toys, Sports, Food, Clothing, Books) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ category │ TEXT │ false │ │ │ Product category grouping (4 categories: Premium, Standard, Budget, Clearance) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ region │ TEXT │ false │ │ │ Geographic sales region (5 regions: North, South, East, West, Central) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ product_id │ INT │ false │ │ │ Unique identifier for the product sold │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ quantity │ INT │ false │ │ │ Number of units sold in this transaction (range: 1-50) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ unit_price │ DECIMAL(10, 2) │ false │ │ │ Price per unit in dollars (range: $5.00-$500.00) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ total_amount │ DECIMAL(10, 2) │ false │ │ │ Total sale amount before tax (quantity × unit_price with discounts applied) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ discount_percent │ INT │ false │ │ │ Discount percentage applied to this sale (0-50%) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ tax_amount │ DECIMAL(10, 2) │ false │ │ │ Tax amount collected on this sale │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ profit_margin │ DECIMAL(10, 2) │ false │ │ │ Profit margin on this sale as a decimal percentage │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ customer_id │ INT │ false │ │ │ Unique identifier for the customer who made the purchase │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ is_online_sale │ BOOLEAN │ false │ │ │ Boolean flag indicating if sale was made online (true) or in-store (false) │
├──────────────────┼────────────────┼──────────┼─────────────────┼───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sale_date │ DATE │ false │ │ │ Calendar date of the sale (extracted from sale_timestamp) │
└──────────────────┴────────────────┴──────────┴─────────────────┴───────────────┴───────────────────────────────────────────────────────────────────────────────────────────────────┘
Read 0 B across 0 files from R2
On average, 0 B / s
```
To learn more about the new aggregation capabilities and schema discovery commands, check out the [SQL reference](https://developers.cloudflare.com/r2-sql/sql-reference/). If you're new to R2 SQL, visit our [getting started guide](https://developers.cloudflare.com/r2-sql/get-started/) to begin querying your data.
---
title: Billing for SQLite Storage · Changelog
description: SQLite storage billing in January 2026
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-12-durable-objects-sqlite-storage-billing/
md: https://developers.cloudflare.com/changelog/2025-12-12-durable-objects-sqlite-storage-billing/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Billing for SQLite Storage
Dec 12, 2025
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
Storage billing for SQLite-backed Durable Objects will be enabled in January 2026, with a target date of January 7, 2026 (no earlier).
To view your SQLite storage usage, go to the **Durable Objects** page
[Go to **Durable Objects**](https://dash.cloudflare.com/?to=/:account/workers/durable-objects)
If you do not want to incur costs, please take action such as optimizing queries or deleting unnecessary stored data in order to reduce your SQLite storage usage ahead of the January 7th target. Only usage on and after the billing target date will incur charges.
Developers on the Workers Paid plan with Durable Object's SQLite storage usage beyond included limits will incur charges according to [SQLite storage pricing](https://developers.cloudflare.com/durable-objects/platform/pricing/#sqlite-storage-backend) announced in September 2024 with the [public beta](https://blog.cloudflare.com/sqlite-in-durable-objects/). Developers on the Workers Free plan will not be charged.
Compute billing for SQLite-backed Durable Objects has been enabled since the initial public beta. SQLite-backed Durable Objects currently incur [charges for requests and duration](https://developers.cloudflare.com/durable-objects/platform/pricing/#compute-billing), and no changes are being made to compute billing.
For more information about SQLite storage pricing and limits, refer to the [Durable Objects pricing documentation](https://developers.cloudflare.com/durable-objects/platform/pricing/#sqlite-storage-backend).
---
title: New Best Practices guide for Durable Objects · Changelog
description: A comprehensive guide to building effective Durable Objects applications.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-15-rules-of-durable-objects/
md: https://developers.cloudflare.com/changelog/2025-12-15-rules-of-durable-objects/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Best Practices guide for Durable Objects
Dec 15, 2025
[Durable Objects ](https://developers.cloudflare.com/durable-objects/)[Workers](https://developers.cloudflare.com/workers/)
A new [Rules of Durable Objects](https://developers.cloudflare.com/durable-objects/best-practices/rules-of-durable-objects/) guide is now available, providing opinionated best practices for building effective Durable Objects applications. This guide covers design patterns, storage strategies, concurrency, and common anti-patterns to avoid.
Key guidance includes:
* **Design around your "atom" of coordination** — Create one Durable Object per logical unit (chat room, game session, user) instead of a global singleton that becomes a bottleneck.
* **Use SQLite storage with RPC methods** — SQLite-backed Durable Objects with typed RPC methods provide the best developer experience and performance.
* **Understand input and output gates** — Learn how Cloudflare's runtime prevents data races by default, how write coalescing works, and when to use `blockConcurrencyWhile()`.
* **Leverage Hibernatable WebSockets** — Reduce costs for real-time applications by allowing Durable Objects to sleep while maintaining WebSocket connections.
The [testing documentation](https://developers.cloudflare.com/durable-objects/examples/testing-with-durable-objects/) has also been updated with modern patterns using `@cloudflare/vitest-pool-workers`, including examples for testing SQLite storage, alarms, and direct instance access:
* JavaScript
```js
import { env, runDurableObjectAlarm } from "cloudflare:test";
import { it, expect } from "vitest";
it("can test Durable Objects with isolated storage", async () => {
const stub = env.COUNTER.getByName("test");
// Call RPC methods directly on the stub
await stub.increment();
expect(await stub.getCount()).toBe(1);
// Trigger alarms immediately without waiting
await runDurableObjectAlarm(stub);
});
```
* TypeScript
```ts
import { env, runDurableObjectAlarm } from "cloudflare:test";
import { it, expect } from "vitest";
it("can test Durable Objects with isolated storage", async () => {
const stub = env.COUNTER.getByName("test");
// Call RPC methods directly on the stub
await stub.increment();
expect(await stub.getCount()).toBe(1);
// Trigger alarms immediately without waiting
await runDurableObjectAlarm(stub);
});
```
---
title: New duplicate action for supported Cloudflare One resources · Changelog
description: New duplicate action for supported Cloudflare One resources
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-16-new-duplicate-action-for-supported-cloudflare-one-resources/
md: https://developers.cloudflare.com/changelog/2025-12-16-new-duplicate-action-for-supported-cloudflare-one-resources/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New duplicate action for supported Cloudflare One resources
Dec 16, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
You can now duplicate specific Cloudflare One resources with a single click from the dashboard.
Initially supported resources:
* Access Applications
* Access Policies
* Gateway Policies
To try this out, simply click on the overflow menu (⋮) from the resource table and click *Duplicate*. We will continue to add the Duplicate action for resources throughout 2026.
---
title: Support for ctx.exports in @cloudflare/vitest-pool-workers · Changelog
description: The Workers Vitest integration now supports the ctx.exports API for
accessing your Worker's exports during tests.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-16-vitest-ctx-exports-support/
md: https://developers.cloudflare.com/changelog/2025-12-16-vitest-ctx-exports-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Support for ctx.exports in @cloudflare/vitest-pool-workers
Dec 16, 2025
[Workers](https://developers.cloudflare.com/workers/)
The [`@cloudflare/vitest-pool-workers`](https://developers.cloudflare.com/workers/testing/vitest-integration/) package now supports the [`ctx.exports` API](https://developers.cloudflare.com/workers/runtime-apis/context/#exports), allowing you to access your Worker's top-level exports during tests.
You can access `ctx.exports` in unit tests by calling `createExecutionContext()`:
```ts
import { createExecutionContext } from "cloudflare:test";
import { it, expect } from "vitest";
it("can access ctx.exports", async () => {
const ctx = createExecutionContext();
const result = await ctx.exports.MyEntryPoint.myMethod();
expect(result).toBe("expected value");
});
```
Alternatively, you can import `exports` directly from `cloudflare:workers`:
```ts
import { exports } from "cloudflare:workers";
import { it, expect } from "vitest";
it("can access imported exports", async () => {
const result = await exports.MyEntryPoint.myMethod();
expect(result).toBe("expected value");
});
```
See the [context-exports fixture](https://github.com/cloudflare/workers-sdk/tree/main/fixtures/vitest-pool-workers-examples/context-exports) for a complete example.
---
title: Configure your framework for Cloudflare automatically · Changelog
description: Our new autoconfig feature makes deploying your web app to
Cloudflare Workers as simple as running a single command.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-16-wrangler-autoconfig/
md: https://developers.cloudflare.com/changelog/2025-12-16-wrangler-autoconfig/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Configure your framework for Cloudflare automatically
Dec 16, 2025
[Workers](https://developers.cloudflare.com/workers/)
Wrangler now supports automatic configuration for popular web frameworks in experimental mode, making it even easier to deploy to Cloudflare Workers.
Previously, if you wanted to deploy an application using a popular web framework like Next.js or Astro, you had to follow tutorials to set up your application for deployment to Cloudflare Workers. This usually involved creating a Wrangler file, installing adapters, or changing configuration options.
Now `wrangler deploy` does this for you. Starting with Wrangler 4.55, you can use `npx wrangler deploy --x-autoconfig` in the directory of any web application using one of the supported frameworks. Wrangler will then proceed to configure and deploy it to your Cloudflare account.
You can also configure your application without deploying it by using the new `npx wrangler setup` command. This enables you to easily review what changes we are making so your application is ready for Cloudflare Workers.
The following application frameworks are supported starting today:
* Next.js
* Astro
* Nuxt
* TanStack Start
* SolidStart
* React Router
* SvelteKit
* Docusaurus
* Qwik
* Analog
Automatic configuration also supports static sites by detecting the assets directory and build command. From a single index.html file to the output of a generator like Jekyll or Hugo, you can just run `npx wrangler deploy --x-autoconfig` to upload to Cloudflare.
We're really excited to bring you automatic configuration so you can do more with Workers. Please let us know if you run into challenges using this experimentally. We’ve opened a [GitHub discussion](https://github.com/cloudflare/workers-sdk/discussions/11667) and would love to hear your feedback.
---
title: Shadow IT - domain level SaaS analytics · Changelog
description: Cloudflare One's SaaS Shadow IT dashboard now includes domain level
data transfer metrics.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-17-shadow-it-domain-analytics/
md: https://developers.cloudflare.com/changelog/2025-12-17-shadow-it-domain-analytics/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Shadow IT - domain level SaaS analytics
Dec 17, 2025
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust has again upgraded its **Shadow IT analytics**, providing you with unprecedented visibility into your organizations use of SaaS tools. With this dashboard, you can review who is using an application and volumes of data transfer to the application.
With this update, you can review data transfer metrics at the domain level, rather than just the application level, providing more granular insight into your data transfer patterns.

These metrics can be filtered by all available filters on the dashboard, including user, application, or content category.
Both the analytics and policies are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
---
title: Workers for Platforms - Dashboard Improvements · Changelog
description: Manage namespaces, Dispatch Workers, tags, and bindings directly in
the dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-18-dashboard-improvements/
md: https://developers.cloudflare.com/changelog/2025-12-18-dashboard-improvements/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers for Platforms - Dashboard Improvements
Dec 18, 2025
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/)
[Workers for Platforms](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/) lets you build multi-tenant platforms on [Cloudflare Workers](https://developers.cloudflare.com/workers/), allowing your end users to deploy and run their own code on your platform. It's designed for anyone building an AI vibe coding platform, e-commerce platform, website builder, or any product that needs to securely execute user-generated code at scale.
Previously, setting up Workers for Platforms required using the API. Now, the Workers for Platforms UI supports namespace creation, dispatch worker templates, and tag management, making it easier for Workers for Platforms customers to build and manage multi-tenant platforms directly from the Cloudflare dashboard.

#### Key improvements
* **Namespace Management:** You can now create and configure [dispatch namespaces](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/how-workers-for-platforms-works/#dispatch-namespace) directly within the dashboard to start a new platform setup.
* **Dispatch Worker Templates:** New Dispatch Worker templates allow you to quickly define how traffic is routed to individual Workers within your namespace. Refer to the [Dynamic Dispatch documentation](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/dynamic-dispatch/) for more examples.
* **Tag Management:** You can now set and update [tags](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/tags/) on User Workers, making it easier to group and manage your Workers.
* **Binding Visibility:** [Bindings](https://developers.cloudflare.com/cloudflare-for-platforms/workers-for-platforms/configuration/bindings/) attached to User Workers are now visible directly within the User Worker view.
* **Deploy Vibe Coding Platform in one-click:** Deploy a [reference implementation](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-vibe-coding-platform/) of an AI vibe coding platform directly from the dashboard. Powered by the Cloudflare's [VibeSDK](https://github.com/cloudflare/vibesdk), this starter kit integrates with Workers for Platforms to handle the deployment of AI-generated projects at scale.
To get started, go to **Workers for Platforms** under **Compute & AI** in the [Cloudflare dashboard](https://dash.cloudflare.com/).
---
title: New AI Crawl Control Overview tab · Changelog
description: AI Crawl Control now opens to an Overview tab showing an executive
summary, operator-grouped AI crawlers, and key metrics at a glance.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-18-overview-tab/
md: https://developers.cloudflare.com/changelog/2025-12-18-overview-tab/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New AI Crawl Control Overview tab
Dec 18, 2025
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
The **Overview** tab is now the default view in AI Crawl Control. The previous default view with controls for individual AI crawlers is available in the **Crawlers** tab.
#### What's new
* **Executive summary** — Monitor total requests, volume change, most common status code, most popular path, and high-volume activity
* **Operator grouping** — Track crawlers by their operating companies (OpenAI, Microsoft, Google, ByteDance, Anthropic, Meta)
* **Customizable filters** — Filter your snapshot by date range, crawler, operator, hostname, or path

#### Get started
1. Log in to the Cloudflare dashboard and select your account and domain.
2. Go to **AI Crawl Control**, where the **Overview** tab opens by default with your activity snapshot.
3. Use filters to customize your view by date range, crawler, operator, hostname, or path.
4. Navigate to the **Crawlers** tab to manage controls for individual crawlers.
Learn more about [analyzing AI traffic](https://developers.cloudflare.com/ai-crawl-control/features/analyze-ai-traffic/) and [managing AI crawlers](https://developers.cloudflare.com/ai-crawl-control/features/manage-ai-crawlers/).
---
title: R2 Data Catalog now supports automatic snapshot expiration · Changelog
description: Automatically remove old Apache Iceberg table snapshots to improve
performance and reduce storage costs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-18-r2-data-catalog-snapshot-expiration/
md: https://developers.cloudflare.com/changelog/2025-12-18-r2-data-catalog-snapshot-expiration/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## R2 Data Catalog now supports automatic snapshot expiration
Dec 18, 2025
[R2](https://developers.cloudflare.com/r2/)
[R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) now supports automatic snapshot expiration for Apache Iceberg tables.
In Apache Iceberg, a snapshot is metadata that represents the state of a table at a given point in time. Every mutation creates a new snapshot which enable powerful features like time travel queries and rollback capabilities but will accumulate over time.
Without regular cleanup, these accumulated snapshots can lead to:
* Metadata overhead
* Slower table operations
* Increased storage costs.
Snapshot expiration in R2 Data Catalog automatically removes old table snapshots based on your configured retention policy, improving performance and storage costs.
```bash
# Enable catalog-level snapshot expiration
# Expire snapshots older than 7 days, always retain at least 10 recent snapshots
npx wrangler r2 bucket catalog snapshot-expiration enable my-bucket \
--older-than-days 7 \
--retain-last 10
```
Snapshot expiration uses two parameters to determine which snapshots to remove:
* `--older-than-days`: age threshold in days
* `--retain-last`: minimum snapshot count to retain
Both conditions must be met before a snapshot is expired, ensuring you always retain recent snapshots even if they exceed the age threshold.
This feature complements [automatic compaction](https://developers.cloudflare.com/r2/data-catalog/table-maintenance/), which optimizes query performance by combining small data files into larger ones. Together, these automatic maintenance operations keep your Iceberg tables performant and cost-efficient without manual intervention.
To learn more about snapshot expiration and how to configure it, visit our [table maintenance documentation](https://developers.cloudflare.com/r2/data-catalog/table-maintenance/) or see [how to manage catalogs](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/).
---
title: WAF Release - 2025-12-18 · Changelog
description: Cloudflare WAF managed rulesets 2025-12-18 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-18-waf-release/
md: https://developers.cloudflare.com/changelog/2025-12-18-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2025-12-18
Dec 18, 2025
[WAF](https://developers.cloudflare.com/waf/)
This week's release focuses on improvements to existing detections to enhance coverage.
**Key Findings**
* Existing rule enhancements have been deployed to improve detection resilience against broad classes of web attacks and strengthen behavioral coverage.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 6429f7386b1546cf9dfce631be5ec20c | N/A | Atlassian Confluence - Code Injection - CVE:CVE-2021-26084 - Beta | Log | Block | This rule is merged into the original rule "Atlassian Confluence - Code Injection - CVE:CVE-2021-26084" (ID: e8c550810618437c953cf3a969e0b97a ) |
| Cloudflare Managed Ruleset | 9108ddb347b3497e9f9351640d9206e3 | N/A | PostgreSQL - SQLi - Copy - Beta | Log | Block | This rule is merged into the original rule "PostgreSQL - SQLi - COPY" (ID: 705a6b5569d5472596910e3ce7265a4e ) |
| Cloudflare Managed Ruleset | cb687d73cc954092b58b90b00cd00ba7 | N/A | Generic Rules - Command Execution - Body | Log | Disabled | This is a new detection. |
| Cloudflare Managed Ruleset | bf30657ffa2a424cbf6570dbcd679ad4 | N/A | Generic Rules - Command Execution - Header | Log | Disabled | This is a new detection. |
| Cloudflare Managed Ruleset | 6df040f716194070a242967cfd181fb3 | N/A | Generic Rules - Command Execution - URI | Log | Disabled | This is a new detection. |
| Cloudflare Managed Ruleset | 39a4fdc37be948709fa7492e7a95bc3a | N/A | SQLi - Tautology - URI - Beta | Log | Block | This rule is merged into the original rule "SQLi - Tautology - URI" (ID: 4c580ea1b5174183b7f5e940b3de2e0a ) |
| Cloudflare Managed Ruleset | 810e0ffe1dd84e67b159129b432ac90d | N/A | SQLi - WaitFor Function - Beta | Log | Block | This rule is merged into the original rule "SQLi - WaitFor Function" (ID: b16fe708799441dea3049a99d5faba59 ) |
| Cloudflare Managed Ruleset | 80690005fef342e0ad6bc9af596c741e | N/A | SQLi - AND/OR Digit Operator Digit 2 - Beta | Log | Block | This rule is merged into the original rule "SQLi - AND/OR Digit Operator Digit" (ID: 98e7e08ae64247e2801ca4b388d80772 ) |
| Cloudflare Managed Ruleset | eaf11ab80b0d491cbb7186f303b2f3fe | N/A | SQLi - Equation 2 - Beta | Log | Block | This rule is merged into the original rule "SQLi - Equation" (ID: 133c6f83cdf14509a4ca6b82a72a6b3a ) |
---
title: Retrieve your authentication token with `wrangler auth token` · Changelog
description: A new command to retrieve your current authentication credentials
for use with other tools and scripts.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-18-wrangler-auth-token/
md: https://developers.cloudflare.com/changelog/2025-12-18-wrangler-auth-token/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Retrieve your authentication token with \`wrangler auth token\`
Dec 18, 2025
[Workers](https://developers.cloudflare.com/workers/)
Wrangler now includes a new [`wrangler auth token`](https://developers.cloudflare.com/workers/wrangler/commands/#auth-token) command that retrieves your current authentication token or credentials for use with other tools and scripts.
```sh
wrangler auth token
```
The command returns whichever authentication method is currently configured, in priority order: API token from `CLOUDFLARE_API_TOKEN`, or OAuth token from `wrangler login` (automatically refreshed if expired).
Use the `--json` flag to get structured output including the token type:
```sh
wrangler auth token --json
```
The JSON output includes the authentication type:
```jsonc
// API token
{ "type": "api_token", "token": "..." }
// OAuth token
{ "type": "oauth", "token": "..." }
// API key/email (only available with --json)
{ "type": "api_key", "key": "...", "email": "..." }
```
API key/email credentials from `CLOUDFLARE_API_KEY` and `CLOUDFLARE_EMAIL` require the `--json` flag since this method uses two values instead of a single token.
---
title: Static prerendering support for TanStack Start · Changelog
description: TanStack Start apps can now prerender routes to static HTML at
build time using the Cloudflare Vite plugin.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-19-tanstack-start-prerendering/
md: https://developers.cloudflare.com/changelog/2025-12-19-tanstack-start-prerendering/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Static prerendering support for TanStack Start
Dec 19, 2025
[Workers](https://developers.cloudflare.com/workers/)
[TanStack Start](https://tanstack.com/start/) apps can now prerender routes to static HTML at build time with access to build time environment variables and bindings, and serve them as [static assets](https://developers.cloudflare.com/workers/static-assets/). To enable prerendering, configure the `prerender` option of the TanStack Start plugin in your Vite config:
```ts
import { defineConfig } from "vite";
import { cloudflare } from "@cloudflare/vite-plugin";
import { tanstackStart } from "@tanstack/react-start/plugin/vite";
export default defineConfig({
plugins: [
cloudflare({ viteEnvironment: { name: "ssr" } }),
tanstackStart({
prerender: {
enabled: true,
},
}),
],
});
```
This feature requires `@tanstack/react-start` v1.138.0 or later. See the [TanStack Start framework guide](https://developers.cloudflare.com/workers/framework-guides/web-apps/tanstack-start/#static-prerendering) for more details.
---
title: Terraform v5.15.0 now available · Changelog
description: Terraform v5.15.0 stabilizes a number of resources and known issues
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-19-terraform-v5150-provider/
md: https://developers.cloudflare.com/changelog/2025-12-19-terraform-v5150-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.15.0 now available
Dec 19, 2025
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
Earlier this year, we announced the launch of the new Terraform v5 Provider. We are aware of the high number of issues reported by the Cloudflare community related to the v5 release. We have committed to releasing improvements on a [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) to ensure its stability and reliability, including the v5.15 release. We have also pivoted from an [issue-to-issue approach to a resource-per-resource approach](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) - we will be focusing on specific resources to not only stabilize the resource but also ensure it is migration-friendly for those migrating from v4 to v5.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes bug fixes, the stabilization of even more popular resources, and more.
#### Features
* **ai\_search:** Add AI Search endpoints ([6f02adb](https://github.com/cloudflare/terraform-provider-cloudflare/commit/6f02adb420e872457f71f95b49cb527663388915))
* **certificate\_pack:** Ensure proper Terraform resource ID handling for path parameters in API calls ([081f32a](https://github.com/cloudflare/terraform-provider-cloudflare/commit/081f32acab4ce9a194a7ff51c8e9fcabd349895a))
* **worker\_version:** Support `startup_time_ms` ([286ab55](https://github.com/cloudflare/terraform-provider-cloudflare/commit/286ab55bea8d5be0faa5a2b5b8b157e4a2214eba))
* **zero\_trust\_dlp\_custom\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_dlp\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_dlp\_integration\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_dlp\_predefined\_entry:** Support `upload_status` ([7dc0fe3](https://github.com/cloudflare/terraform-provider-cloudflare/commit/7dc0fe3b23726ead8dc075f86728a0540846d90c))
* **zero\_trust\_gateway\_policy:** Support `forensic_copy` ([5741fd0](https://github.com/cloudflare/terraform-provider-cloudflare/commit/5741fd0ed9f7270d20731cc47ec45eb0403a628b))
* **zero\_trust\_list:** Support additional types (category, location, device) ([5741fd0](https://github.com/cloudflare/terraform-provider-cloudflare/commit/5741fd0ed9f7270d20731cc47ec45eb0403a628b))
#### Bug fixes
* **access\_rules:** Add validation to prevent state drift. Ideally, we'd use Semantic Equality but since that isn't an option, this will remove a foot-gun. ([4457791](https://github.com/cloudflare/terraform-provider-cloudflare/commit/44577911b3cbe45de6279aefa657bdee73c0794d))
* **cloudflare\_pages\_project:** Addressing drift issues ([6edffcf](https://github.com/cloudflare/terraform-provider-cloudflare/commit/6edffcfcf187fdc9b10b624b9a9b90aed2fb2b2e)) ([3db318e](https://github.com/cloudflare/terraform-provider-cloudflare/commit/3db318e747423bf10ce587d9149e90edcd8a77b0))
* **cloudflare\_worker:** Can be cleanly imported ([4859b52](https://github.com/cloudflare/terraform-provider-cloudflare/commit/4859b52968bb25570b680df9813f8e07fd50728f))
* **cloudflare\_worker:** Ensure clean imports ([5b525bc](https://github.com/cloudflare/terraform-provider-cloudflare/commit/5b525bc478a4e2c9c0d4fd659b92cc7f7c18016a))
* **list\_items:** Add validation for IP List items to avoid inconsistent state ([b6733dc](https://github.com/cloudflare/terraform-provider-cloudflare/commit/b6733dc4be909a5ab35895a88e519fc2582ccada))
* **zero\_trust\_access\_application:** Remove all conditions from sweeper ([3197f1a](https://github.com/cloudflare/terraform-provider-cloudflare/commit/3197f1aed61be326d507d9e9e3b795b9f1d18fd7))
* **spectrum\_application:** Map missing fields during spectrum resource import ([#6495](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6495)) ([ddb4e72](https://github.com/cloudflare/terraform-provider-cloudflare/commit/ddb4e722b82c735825a549d651a9da219c142efa))
#### Upgrade to newer version
We suggest waiting to migrate to v5 while we work on stabilization. This helps with avoiding any blocking issues while the Terraform resources are actively being [stabilized](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237). We will be releasing a new migration tool in March 2026 to help support v4 to v5 transitions for our most popular resources.
#### For more information
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
---
title: Agents SDK v0.3.0, workers-ai-provider v3.0.0, and ai-gateway-provider
v3.0.0 with AI SDK v6 support · Changelog
description: The latest release updates the Agents SDK v0.3.0 with full AI SDK
v6 compatibility, workers-ai-provider v3.0.0 and ai-gateway-provider v3.0.0
with enhanced streaming and tool support, unified tool pattern, dynamic tool
approval, and React hooks for building production-ready AI chat interfaces.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-22-agents-sdk-ai-sdk-v6/
md: https://developers.cloudflare.com/changelog/2025-12-22-agents-sdk-ai-sdk-v6/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Agents SDK v0.3.0, workers-ai-provider v3.0.0, and ai-gateway-provider v3.0.0 with AI SDK v6 support
Dec 22, 2025
[Agents ](https://developers.cloudflare.com/agents/)[Workers](https://developers.cloudflare.com/workers/)
We've shipped a new release for the [Agents SDK](https://github.com/cloudflare/agents) v0.3.0 bringing full compatibility with [AI SDK v6](https://ai-sdk.dev/docs/introduction) and introducing the unified tool pattern, dynamic tool approval, and enhanced React hooks with improved tool handling.
This release includes improved streaming and tool support, dynamic tool approval (for "human in the loop" systems), enhanced React hooks with `onToolCall` callback, improved error handling for streaming responses, and seamless migration from v5 patterns.
This makes it ideal for building production AI chat interfaces with Cloudflare Workers AI models, agent workflows, human-in-the-loop systems, or any application requiring reliable tool execution and approval workflows.
Additionally, we've updated **workers-ai-provider v3.0.0**, the official provider for Cloudflare Workers AI models, and **ai-gateway-provider v3.0.0**, the provider for Cloudflare AI Gateway, to be compatible with AI SDK v6.
#### Agents SDK v0.3.0
#### Unified Tool Pattern
AI SDK v6 introduces a unified tool pattern where all tools are defined on the server using the `tool()` function. This replaces the previous client-side `AITool` pattern.
#### Server-Side Tool Definition
```ts
import { tool } from "ai";
import { z } from "zod";
// Server: Define ALL tools on the server
const tools = {
// Server-executed tool
getWeather: tool({
description: "Get weather for a city",
inputSchema: z.object({ city: z.string() }),
execute: async ({ city }) => fetchWeather(city)
}),
// Client-executed tool (no execute = client handles via onToolCall)
getLocation: tool({
description: "Get user location from browser",
inputSchema: z.object({})
// No execute function
}),
// Tool requiring approval (dynamic based on input)
processPayment: tool({
description: "Process a payment",
inputSchema: z.object({ amount: z.number() }),
needsApproval: async ({ amount }) => amount > 100,
execute: async ({ amount }) => charge(amount)
})
};
```
#### Client-Side Tool Handling
```ts
// Client: Handle client-side tools via onToolCall callback
import { useAgentChat } from "agents/ai-react";
const { messages, sendMessage, addToolOutput } = useAgentChat({
agent,
onToolCall: async ({ toolCall, addToolOutput }) => {
if (toolCall.toolName === "getLocation") {
const position = await new Promise((resolve, reject) => {
navigator.geolocation.getCurrentPosition(resolve, reject);
});
addToolOutput({
toolCallId: toolCall.toolCallId,
output: {
lat: position.coords.latitude,
lng: position.coords.longitude
}
});
}
}
});
```
**Key benefits of the unified tool pattern:**
* **Server-defined tools**: All tools are defined in one place on the server
* **Dynamic approval**: Use `needsApproval` to conditionally require user confirmation
* **Cleaner client code**: Use `onToolCall` callback instead of managing tool configs
* **Type safety**: Full TypeScript support with proper tool typing
#### useAgentChat(options)
Creates a new chat interface with enhanced v6 capabilities.
```ts
// Basic chat setup with onToolCall
const { messages, sendMessage, addToolOutput } = useAgentChat({
agent,
onToolCall: async ({ toolCall, addToolOutput }) => {
// Handle client-side tool execution
await addToolOutput({
toolCallId: toolCall.toolCallId,
output: { result: "success" }
});
}
});
```
#### Dynamic Tool Approval
Use `needsApproval` on server tools to conditionally require user confirmation:
```ts
const paymentTool = tool({
description: "Process a payment",
inputSchema: z.object({
amount: z.number(),
recipient: z.string()
}),
needsApproval: async ({ amount }) => amount > 1000,
execute: async ({ amount, recipient }) => {
return await processPayment(amount, recipient);
}
});
```
#### Tool Confirmation Detection
The `isToolUIPart` and `getToolName` functions now check both static and dynamic tool parts:
```ts
import { isToolUIPart, getToolName } from "ai";
const pendingToolCallConfirmation = messages.some((m) =>
m.parts?.some(
(part) => isToolUIPart(part) && part.state === "input-available",
),
);
// Handle tool confirmation
if (pendingToolCallConfirmation) {
await addToolOutput({
toolCallId: part.toolCallId,
output: "User approved the action"
});
}
```
If you need the v5 behavior (static-only checks), use the new functions:
```ts
import { isStaticToolUIPart, getStaticToolName } from "ai";
```
#### convertToModelMessages() is now async
The `convertToModelMessages()` function is now asynchronous. Update all calls to await the result:
```ts
import { convertToModelMessages } from "ai";
const result = streamText({
messages: await convertToModelMessages(this.messages),
model: openai("gpt-4o")
});
```
#### ModelMessage type
The `CoreMessage` type has been removed. Use `ModelMessage` instead:
```ts
import { convertToModelMessages, type ModelMessage } from "ai";
const modelMessages: ModelMessage[] = await convertToModelMessages(messages);
```
#### generateObject mode option removed
The `mode` option for `generateObject` has been removed:
```ts
// Before (v5)
const result = await generateObject({
mode: "json",
model,
schema,
prompt
});
// After (v6)
const result = await generateObject({
model,
schema,
prompt
});
```
#### Structured Output with generateText
While `generateObject` and `streamObject` are still functional, the recommended approach is to use `generateText`/`streamText` with the `Output.object()` helper:
```ts
import { generateText, Output, stepCountIs } from "ai";
const { output } = await generateText({
model: openai("gpt-4"),
output: Output.object({
schema: z.object({ name: z.string() })
}),
stopWhen: stepCountIs(2),
prompt: "Generate a name"
});
```
> **Note**: When using structured output with `generateText`, you must configure multiple steps with `stopWhen` because generating the structured output is itself a step.
#### workers-ai-provider v3.0.0
Seamless integration with Cloudflare Workers AI models through the updated workers-ai-provider v3.0.0 with AI SDK v6 support.
#### Model Setup with Workers AI
Use Cloudflare Workers AI models directly in your agent workflows:
```ts
import { createWorkersAI } from "workers-ai-provider";
import { useAgentChat } from "agents/ai-react";
// Create Workers AI model (v3.0.0 - enhanced v6 internals)
const model = createWorkersAI({
binding: env.AI,
})("@cf/meta/llama-3.2-3b-instruct");
```
#### Enhanced File and Image Support
Workers AI models now support v6 file handling with automatic conversion:
```ts
// Send images and files to Workers AI models
sendMessage({
role: "user",
parts: [
{ type: "text", text: "Analyze this image:" },
{
type: "file",
data: imageBuffer,
mediaType: "image/jpeg",
},
],
});
// Workers AI provider automatically converts to proper format
```
#### Streaming with Workers AI
Enhanced streaming support with automatic warning detection:
```ts
// Streaming with Workers AI models
const result = await streamText({
model: createWorkersAI({ binding: env.AI })("@cf/meta/llama-3.2-3b-instruct"),
messages: await convertToModelMessages(messages),
onChunk: (chunk) => {
// Enhanced streaming with warning handling
console.log(chunk);
},
});
```
#### ai-gateway-provider v3.0.0
The ai-gateway-provider v3.0.0 now supports AI SDK v6, enabling you to use Cloudflare AI Gateway with multiple AI providers including Anthropic, Azure, AWS Bedrock, Google Vertex, and Perplexity.
#### AI Gateway Setup
Use Cloudflare AI Gateway to add analytics, caching, and rate limiting to your AI applications:
```ts
import { createAIGateway } from "ai-gateway-provider";
// Create AI Gateway provider (v3.0.0 - enhanced v6 internals)
const model = createAIGateway({
gatewayUrl: "https://gateway.ai.cloudflare.com/v1/your-account-id/gateway",
headers: {
"Authorization": `Bearer ${env.AI_GATEWAY_TOKEN}`
}
})({
provider: "openai",
model: "gpt-4o"
});
```
#### Migration from v5
#### Deprecated APIs
The following APIs are deprecated in favor of the unified tool pattern:
| Deprecated | Replacement |
| - | - |
| `AITool` type | Use AI SDK's `tool()` function on server |
| `extractClientToolSchemas()` | Define tools on server, no client schemas needed |
| `createToolsFromClientSchemas()` | Define tools on server with `tool()` |
| `toolsRequiringConfirmation` option | Use `needsApproval` on server tools |
| `experimental_automaticToolResolution` | Use `onToolCall` callback |
| `tools` option in `useAgentChat` | Use `onToolCall` for client-side execution |
| `addToolResult()` | Use `addToolOutput()` |
#### Breaking Changes Summary
1. **Unified Tool Pattern**: All tools must be defined on the server using `tool()`
2. **`convertToModelMessages()` is async**: Add `await` to all calls
3. **`CoreMessage` removed**: Use `ModelMessage` instead
4. **`generateObject` mode removed**: Remove `mode` option
5. **`isToolUIPart` behavior changed**: Now checks both static and dynamic tool parts
#### Installation
Update your dependencies to use the latest versions:
```bash
npm install agents@^0.3.0 workers-ai-provider@^3.0.0 ai-gateway-provider@^3.0.0 ai@^6.0.0 @ai-sdk/react@^3.0.0 @ai-sdk/openai@^3.0.0
```
#### Resources
* [Migration Guide](https://github.com/cloudflare/agents/blob/main/docs/migration-to-ai-sdk-v6.md) - Comprehensive migration documentation from v5 to v6
* [AI SDK v6 Documentation](https://ai-sdk.dev/docs/migration-guides/migration-guide-6-0) - Official AI SDK migration guide
* [AI SDK v6 Announcement](https://vercel.com/blog/ai-sdk-6) - Learn about new features in v6
* [AI SDK Documentation](https://sdk.vercel.ai/docs) - Complete AI SDK reference
* [GitHub Issues](https://github.com/cloudflare/agents/issues) - Report bugs or request features
#### Feedback Welcome
We'd love your feedback! We're particularly interested in feedback on:
* **Migration experience** - How smooth was the upgrade from v5 to v6?
* **Unified tool pattern** - How does the new server-defined tool pattern work for you?
* **Dynamic tool approval** - Does the `needsApproval` feature meet your needs?
* **AI Gateway integration** - How well does the new provider work with your setup?
---
title: Breakout traffic visibility via NetFlow · Changelog
description: NetFlow export from Magic WAN Connector for breakout traffic monitoring
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2025-12-31-connector-breakout-traffic-netflow/
md: https://developers.cloudflare.com/changelog/2025-12-31-connector-breakout-traffic-netflow/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Breakout traffic visibility via NetFlow
Dec 31, 2025
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Magic WAN Connector now exports NetFlow data for breakout traffic to Magic Network Monitoring (MNM), providing visibility into traffic that bypasses Cloudflare's security filtering.
This feature allows you to:
* Monitor breakout traffic statistics in the Cloudflare dashboard.
* View traffic patterns for applications configured to bypass Cloudflare.
* Maintain visibility across all traffic passing through your Magic WAN Connector.
For more information, refer to [NetFlow statistics](https://developers.cloudflare.com/magic-wan/analytics/netflow-analytics/).
---
title: Build microfrontend applications on Workers · Changelog
description: Split a single application into independently deployable frontends
using a router Worker and service bindings, enabling teams to develop and
deploy features independently.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-01-microfrontends/
md: https://developers.cloudflare.com/changelog/2026-01-01-microfrontends/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Build microfrontend applications on Workers
Jan 01, 2026
[Workers](https://developers.cloudflare.com/workers/)
You can now deploy microfrontends to Cloudflare, splitting a single application into smaller, independently deployable units that render as one cohesive application. This lets different teams using different frameworks develop, test, and deploy each microfrontend without coordinating releases.
Microfrontends solve several challenges for large-scale applications:
* **Independent deployments**: Teams deploy updates on their own schedule without redeploying the entire application
* **Framework flexibility**: Build multi-framework applications (for example, Astro, Remix, and Next.js in one app)
* **Gradual migration**: Migrate from a monolith to a distributed architecture incrementally
Create a microfrontend project:
[](https://dash.cloudflare.com/?to=/:account/workers-and-pages/create?type=vmfe)
This template automatically creates a router worker with pre-configured routing logic, and lets you configure [Service bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/service-bindings/) to Workers you have already deployed to your Cloudflare account. The router Worker analyzes incoming requests, matches them against configured routes, and forwards requests to the appropriate microfrontend via service bindings. The router automatically rewrites HTML, CSS, and headers to ensure assets load correctly from each microfrontend's mount path. The router includes advanced features like preloading for faster navigation between microfrontends, smooth page transitions using the View Transitions API, and automatic path rewriting for assets, redirects, and cookies.
Each microfrontend can be a full-framework application, a static site with Workers Static Assets, or any other Worker-based application.
Get started with the [microfrontends template](https://dash.cloudflare.com/?to=/:account/workers-and-pages/create?type=vmfe), or read the [microfrontends documentation](https://developers.cloudflare.com/workers/framework-guides/web-apps/microfrontends/) for implementation details.
---
title: Custom container instance types now available for all users · Changelog
description: Configure custom vCPU, memory, and disk allocations for your
container instances
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-05-custom-instance-types/
md: https://developers.cloudflare.com/changelog/2026-01-05-custom-instance-types/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Custom container instance types now available for all users
Jan 05, 2026
[Containers](https://developers.cloudflare.com/containers/)
Custom instance types are now enabled for all [Cloudflare Containers](https://developers.cloudflare.com/containers) users. You can now specify specific vCPU, memory, and disk amounts, rather than being limited to pre-defined [instance types](https://developers.cloudflare.com/containers/platform-details/limits/#instance-types). Previously, only select Enterprise customers were able to customize their instance type.
To use a custom instance type, specify the `instance_type` property as an object with `vcpu`, `memory_mib`, and `disk_mb` fields in your Wrangler configuration:
```toml
[[containers]]
image = "./Dockerfile"
instance_type = { vcpu = 2, memory_mib = 6144, disk_mb = 12000 }
```
Individual limits for custom instance types are based on the `standard-4` instance type (4 vCPU, 12 GiB memory, 20 GB disk). You must allocate at least 1 vCPU for custom instance types. For workloads requiring less than 1 vCPU, use the predefined instance types like `lite` or `basic`.
See the [limits documentation](https://developers.cloudflare.com/containers/platform-details/limits/#custom-instance-types) for the full list of constraints on custom instance types. See the [getting started guide](https://developers.cloudflare.com/containers/get-started/) to deploy your first Container,
---
title: Workers Analytics Engine SQL now supports filtering using HAVING and LIKE
· Changelog
description: Workers Analytics Engine's SQL API now supports SQL's HAVING and LIKE features
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-07-analytics-engine-support-for-like-and-having/
md: https://developers.cloudflare.com/changelog/2026-01-07-analytics-engine-support-for-like-and-having/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Workers Analytics Engine SQL now supports filtering using HAVING and LIKE
Jan 07, 2026
[Workers Analytics Engine ](https://developers.cloudflare.com/analytics/analytics-engine/)[Workers](https://developers.cloudflare.com/workers/)
You can now use the `HAVING` clause and `LIKE` pattern matching operators in [Workers Analytics Engine](https://developers.cloudflare.com/analytics/analytics-engine/).
Workers Analytics Engine allows you to ingest and store high-cardinality data at scale and query your data through a simple SQL API.
#### Filtering using `HAVING`
The `HAVING` clause complements the `WHERE` clause by enabling you to filter groups based on aggregate values. While `WHERE` filters rows before aggregation, `HAVING` filters groups after aggregation is complete.
You can use `HAVING` to filter groups where the average exceeds a threshold:
```sql
SELECT
blob1 AS probe_name,
avg(double1) AS average_temp
FROM temperature_readings
GROUP BY probe_name
HAVING average_temp > 10
```
You can also filter groups based on aggregates such as the number of items in the group:
```sql
SELECT
blob1 AS probe_name,
count() AS num_readings
FROM temperature_readings
GROUP BY probe_name
HAVING num_readings > 100
```
#### Pattern matching using `LIKE`
The new pattern matching operators enable you to search for strings that match specific patterns using wildcard characters:
* `LIKE` - case-sensitive pattern matching
* `NOT LIKE` - case-sensitive pattern exclusion
* `ILIKE` - case-insensitive pattern matching
* `NOT ILIKE` - case-insensitive pattern exclusion
Pattern matching supports two wildcard characters: `%` (matches zero or more characters) and `_` (matches exactly one character).
You can match strings starting with a prefix:
```sql
SELECT *
FROM logs
WHERE blob1 LIKE 'error%'
```
You can also match file extensions (case-insensitive):
```sql
SELECT *
FROM requests
WHERE blob2 ILIKE '%.jpg'
```
Another example is excluding strings containing specific text:
```sql
SELECT *
FROM events
WHERE blob3 NOT ILIKE '%debug%'
```
#### Ready to get started?
Learn more about the [`HAVING` clause](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/statements/#having-clause) or [pattern matching operators](https://developers.cloudflare.com/analytics/analytics-engine/sql-reference/operators/#pattern-matching-operators) in the Workers Analytics Engine SQL reference documentation.
---
title: Cloudflare admin activity logs capture creation of DNS over HTTP (DoH)
users · Changelog
description: Cloudflare admin activity logs display when a DoH user is created.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-08-access-audit-log-for-doh-users/
md: https://developers.cloudflare.com/changelog/2026-01-08-access-audit-log-for-doh-users/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare admin activity logs capture creation of DNS over HTTP (DoH) users
Jan 08, 2026
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)
Cloudflare [admin activity logs](https://developers.cloudflare.com/cloudflare-one/insights/logs/) now capture each time a [DNS over HTTP (DoH) user](https://developers.cloudflare.com/cloudflare-one/networks/resolvers-and-proxies/dns/dns-over-https/) is created.
These logs can be viewed from the [Cloudflare One dashboard](https://one.dash.cloudflare.com/), pulled via the [Cloudflare API](https://developers.cloudflare.com/api/), and exported through [Logpush](https://developers.cloudflare.com/cloudflare-one/insights/logs/logpush/).
---
title: Shell tab completions for Wrangler CLI · Changelog
description: Wrangler now supports shell tab completions for Bash, Zsh, Fish,
and PowerShell, making it faster to navigate commands and flags.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-09-wrangler-tab-completion/
md: https://developers.cloudflare.com/changelog/2026-01-09-wrangler-tab-completion/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Shell tab completions for Wrangler CLI
Jan 09, 2026
[Workers](https://developers.cloudflare.com/workers/)
Wrangler now includes built-in shell tab completion support, making it faster and easier to navigate commands without memorizing every option. Press Tab as you type to autocomplete commands, subcommands, flags, and even option values like log levels.
Tab completions are supported for Bash, Zsh, Fish, and PowerShell.
#### Setup
Generate the completion script for your shell and add it to your configuration file:
```sh
# Bash
wrangler complete bash >> ~/.bashrc
# Zsh
wrangler complete zsh >> ~/.zshrc
# Fish
wrangler complete fish >> ~/.config/fish/config.fish
# PowerShell
wrangler complete powershell >> $PROFILE
```
After adding the script, restart your terminal or source your configuration file for the changes to take effect. Then you can simply press Tab to see available completions:
```sh
wrangler d # completes to 'deploy', 'dev', 'd1', etc.
wrangler kv # shows subcommands: namespace, key, bulk
```
Tab completions are dynamically generated from Wrangler's command registry, so they stay up-to-date as new commands and options are added. This feature is powered by [`@bomb.sh/tab`](https://github.com/bombshell-dev/tab/).
See the [`wrangler complete` documentation](https://developers.cloudflare.com/workers/wrangler/commands/#complete) for more details.
---
title: Validate your generated types with `wrangler types --check` · Changelog
description: A new flag for `wrangler types` lets you verify your generated
types are up to date without modifying any files.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-11-wrangler-types-check/
md: https://developers.cloudflare.com/changelog/2026-01-11-wrangler-types-check/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Validate your generated types with \`wrangler types --check\`
Jan 12, 2026
[Workers](https://developers.cloudflare.com/workers/)
Wrangler now supports a `--check` flag for the `wrangler types` command. This flag validates that your generated types are up to date without writing any changes to disk.
This is useful in CI/CD pipelines where you want to ensure that developers have regenerated their types after making changes to their Wrangler configuration. If the types are out of date, the command will exit with a non-zero status code.
```sh
npx wrangler types --check
```
If your types are up to date, the command will succeed silently. If they are out of date, you'll see an error message indicating which files need to be regenerated.
For more information, see the [Wrangler types documentation](https://developers.cloudflare.com/workers/wrangler/commands/#types).
---
title: Metro code field now available in Rules · Changelog
description: The ip.src.metro_code field is now populated with DMA (Designated
Market Area) data for IP geolocation.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-12-dma-metro-code-field/
md: https://developers.cloudflare.com/changelog/2026-01-12-dma-metro-code-field/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Metro code field now available in Rules
Jan 12, 2026
[Rules](https://developers.cloudflare.com/rules/)
The `ip.src.metro_code` field in the Ruleset Engine is now populated with DMA (Designated Market Area) data.
You can use this field to build rules that target traffic based on geographic market areas, enabling more granular location-based policies for your applications.
#### Field details
| Field | Type | Description |
| - | - | - |
| `ip.src.metro_code` | String \| null | The metro code (DMA) of the incoming request's IP address. Returns the designated market area code for the client's location. |
Example filter expression:
```plaintext
ip.src.metro_code eq "501"
```
For more information, refer to the [Fields reference](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/ip.src.metro_code/).
---
title: Enhanced visibility for post-delivery actions · Changelog
description: Additional post delivery action log details for failures
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-12-enhanced-visibility-post-delivery-actions/
md: https://developers.cloudflare.com/changelog/2026-01-12-enhanced-visibility-post-delivery-actions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Enhanced visibility for post-delivery actions
Jan 12, 2026
[Email security](https://developers.cloudflare.com/cloudflare-one/email-security/)
The Action Log now provides enriched data for post-delivery actions to improve troubleshooting. In addition to success confirmations, failed actions now display the targeted Destination folder and a specific failure reason within the Activity field.
Note
Error messages will vary depending on whether you are using Google Workspace or Microsoft 365.

This update allows you to see the full lifecycle of a failed action. For instance, if an administrator tries to move an email that has already been deleted or moved manually, the log will now show the multiple retry attempts and the specific destination error.
This applies to all Email Security packages:
* **Enterprise**
* **Enterprise + PhishGuard**
---
title: Cloudflare Threat Events now support STIX2 format · Changelog
description: Customers can now export threat events in STIX2 format for seamless
integration with TIP, SIEM, and SOAR platforms.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-12-stix2-available-for-threat-events-api/
md: https://developers.cloudflare.com/changelog/2026-01-12-stix2-available-for-threat-events-api/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Threat Events now support STIX2 format
Jan 12, 2026
[Security Center](https://developers.cloudflare.com/security-center/)
We are excited to announce that **Cloudflare Threat Events** now supports the **STIX2 (Structured Threat Information Expression)** format. This was a highly requested feature designed to streamline how security teams consume and act upon our threat intelligence.
By adopting this industry-standard format, you can now integrate Cloudflare's threat events data more effectively into your existing security ecosystem.
#### Key benefits
* Eliminate the need for custom parsers, as STIX2 allows for "out of the box" ingestion into major **Threat Intel Platforms (TIPs)**, **SIEMs**, and **SOAR** tools.
* STIX2 provides a standardized way to represent relationships between indicators, sightings, and threat actors, giving your analysts a clearer picture of the threat landscape.
For technical details on how to query events using this format, please refer to our [Threat Events API Documentation](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/threat_events/methods/list/).
***
---
title: WAF Release - 2026-01-12 · Changelog
description: Cloudflare WAF managed rulesets 2026-01-12 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-12-waf-release/
md: https://developers.cloudflare.com/changelog/2026-01-12-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2026-01-12
Jan 12, 2026
[WAF](https://developers.cloudflare.com/waf/)
This week's release focuses on improvements to existing detections to enhance coverage.
**Key Findings**
* Existing rule enhancements have been deployed to improve detection resilience against SQL Injection.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 72963b917ef74697b5bde02f48a1841a | N/A | SQLi - AND/OR MAKE\_SET/ELT - Beta | Log | Block | This rule is merged into the original rule "SQLi - AND/OR MAKE\_SET/ELT" (ID: 0f41a593c8fe42c38a26f709252d3934 ) |
| Cloudflare Managed Ruleset | adf076af09b2484ca9e7881f9e553ad3 | N/A | SQLi - Benchmark Function - Beta | Log | Block | This rule is merged into the original rule "SQLi - Benchmark Function" (ID: ac4e9ebfb43a4f3998f6072d2ebc44ad ) |
---
title: AI Crawl Control Read Only role now available · Changelog
description: Assign read-only access to AI Crawl Control for team members who
need to monitor crawler activity without edit permissions.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-13-ai-crawl-control-read-only-role/
md: https://developers.cloudflare.com/changelog/2026-01-13-ai-crawl-control-read-only-role/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Crawl Control Read Only role now available
Jan 13, 2026
[AI Crawl Control](https://developers.cloudflare.com/ai-crawl-control/)
Account administrators can now assign the **AI Crawl Control Read Only** role to provide read-only access to AI Crawl Control at the domain level.
Users with this role can view the **Overview**, **Crawlers**, **Metrics**, **Robots.txt**, and **Settings** tabs but cannot modify crawler actions or settings.
This role is specific for AI Crawl Control. You still require correct permissions to access other areas / features of the dashboard.
To assign, go to **Manage Account** > **Members** and add a policy with the **AI Crawl Control Read Only** role scoped to the desired domain.
---
title: WARP client for Linux (version 2025.10.186.0) · Changelog
description: WARP client for Linux (version 2025.10.186.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-13-warp-linux-ga/
md: https://developers.cloudflare.com/changelog/2026-01-13-warp-linux-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Linux (version 2025.10.186.0)
Jan 13, 2026
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Linux WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features, including the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/).
WARP client version 2025.8.779.0 introduced an updated public key for Linux packages. The public key must be updated if it was installed before September 12, 2025 to ensure the repository remains functional after December 4, 2025. Instructions to make this update are available at [pkg.cloudflareclient.com](https://pkg.cloudflareclient.com).
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* Linux [disk encryption posture check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/disk-encryption/) now supports non-filesystem encryption types like `dm-crypt`.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where the GUI becomes unresponsive when the **Re-Authenticate in browser** button is clicked.
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
---
title: WARP client for macOS (version 2025.10.186.0) · Changelog
description: WARP client for macOS (version 2025.10.186.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-13-warp-macos-ga/
md: https://developers.cloudflare.com/changelog/2026-01-13-warp-macos-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2025.10.186.0)
Jan 13, 2026
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the macOS WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features, including the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/).
**Changes and improvements**
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
---
title: WARP client for Windows (version 2025.10.186.0) · Changelog
description: WARP client for Windows (version 2025.10.186.0)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-13-warp-windows-ga/
md: https://developers.cloudflare.com/changelog/2026-01-13-warp-windows-ga/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2025.10.186.0)
Jan 13, 2026
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new GA release for the Windows WARP client is now available on the [stable releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/).
This release contains minor fixes, improvements, and new features. New features include the ability to manage WARP client connectivity for all devices in your fleet using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/), and a new WARP client device posture check for [Antivirus](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/antivirus/).
**Changes and improvements**
* Added a new feature to manage WARP client connectivity for all devices using an [external signal](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/external-disconnect/). This feature allows administrators to send a global signal from an on-premises HTTPS endpoint that force disconnects or reconnects all WARP clients in an account based on configuration set on the endpoint.
* Fixed an issue that caused occasional audio degradation and increased CPU usage on Windows by optimizing route configurations for large [domain-based split tunnel rules](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/split-tunnels/#domain-based-split-tunnels).
* The [Local Domain Fallback](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/route-traffic/local-domains/) feature has been fixed for devices running WARP client version 2025.4.929.0 and newer. Previously, these devices could experience failures with Local Domain Fallback unless a fallback server was explicitly configured. This configuration is no longer a requirement for the feature to function correctly.
* [Proxy mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/#proxy-mode) now supports transparent HTTP proxying in addition to CONNECT-based proxying.
* Fixed an issue where sending large messages to the daemon by Inter-Process Communication (IPC) could cause the daemon to fail and result in service interruptions.
* Added support for a new WARP client device posture check for [Antivirus](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/antivirus/). The check confirms the presence of an antivirus program on a Windows device with the option to check if the antivirus is up to date.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: "`wrangler types` now generates types for all environments · Changelog"
description: The `wrangler types` command now aggregates bindings from all
environments by default, ensuring complete type coverage across your
deployment environments.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-13-wrangler-types-multi-environment/
md: https://developers.cloudflare.com/changelog/2026-01-13-wrangler-types-multi-environment/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## \`wrangler types\` now generates types for all environments
Jan 13, 2026
[Workers](https://developers.cloudflare.com/workers/)
The `wrangler types` command now generates TypeScript types for bindings from **all environments** defined in your Wrangler configuration file by default.
Previously, `wrangler types` only generated types for bindings in the top-level configuration (or a single environment when using the `--env` flag). This meant that if you had environment-specific bindings — for example, a KV namespace only in production or an R2 bucket only in staging — those bindings would be missing from your generated types, causing TypeScript errors when accessing them.
Now, running `wrangler types` collects bindings from all environments and includes them in the generated `Env` type. This ensures your types are complete regardless of which environment you deploy to.
#### Generating types for a specific environment
If you want the previous behavior of generating types for only a specific environment, you can use the `--env` flag:
```sh
wrangler types --env production
```
Learn more about [generating types for your Worker](https://developers.cloudflare.com/workers/wrangler/commands/#types) in the Wrangler documentation.
---
title: URL Scanner now supports PDF report downloads · Changelog
description: Users can now download a comprehensive PDF report of their URL
scans directly from the Cloudflare dashboard.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-14-download-url-scanner-report-pdf/
md: https://developers.cloudflare.com/changelog/2026-01-14-download-url-scanner-report-pdf/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## URL Scanner now supports PDF report downloads
Jan 14, 2026
[Security Center](https://developers.cloudflare.com/security-center/)
We have expanded the reporting capabilities of the Cloudflare URL Scanner. In addition to existing JSON and HAR exports, users can now generate and download a **PDF report** directly from the Cloudflare dashboard. This update streamlines how security analysts can share findings with stakeholders who may not have access to the Cloudflare dashboard or specialized tools to parse JSON and HAR files.
**Key Benefits:**
* Consolidate scan results, including screenshots, security signatures, and metadata, into a single, portable document
* Easily share professional-grade summaries with non-technical stakeholders or legal teams for faster incident response
**What’s new:**
* **PDF Export Button:** A new download option is available in the URL Scanner results page within the Cloudflare dashboard
* **Unified Documentation:** Access all scan details—from high-level summaries to specific security flags—in one offline-friendly file
To get started with the URL Scanner and explore our reporting capabilities, visit the [URL Scanner API documentation](https://developers.cloudflare.com/api/resources/url_scanner/).
***
---
title: Launching FLUX.2 [klein] 4B on Workers AI · Changelog
description: New ultra-fast FLUX.2 [klein] 4B model on Workers AI
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-15-flux-2-klein-4b-workers-ai/
md: https://developers.cloudflare.com/changelog/2026-01-15-flux-2-klein-4b-workers-ai/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Launching FLUX.2 \[klein] 4B on Workers AI
Jan 15, 2026
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We've partnered with Black Forest Labs (BFL) again to bring their optimized FLUX.2 \[klein] 4B model to Workers AI! This distilled model offers faster generation and cost-effective pricing, while maintaining great output quality. With a fixed 4-step inference process, Klein 4B is ideal for rapid prototyping and real-time applications where speed matters.
Read the [BFL blog](https://bfl.ai/blog) to learn more about the model itself, or try it out yourself on our [multi modal playground](https://multi-modal.ai.cloudflare.com/).
Pricing documentation is available on the [model page](https://developers.cloudflare.com/workers-ai/models/flux-2-klein-4b/) or [pricing page](https://developers.cloudflare.com/workers-ai/platform/pricing/).
#### Workers AI Platform specifics
The model hosted on Workers AI is optimized for speed with a **fixed 4-step inference process** and supports up to 4 image inputs. Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted. Like FLUX.2 \[dev], this image model uses multipart form data inputs, even if you just have a prompt.
With the REST API, the multipart form data input looks like this:
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-4b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=a sunset at the alps' \
--form width=1024 \
--form height=1024
```
With the Workers AI binding, you can use it as such:
```javascript
const form = new FormData();
form.append("prompt", "a sunset with a dog");
form.append("width", "1024");
form.append("height", "1024");
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-4b", {
multipart: {
body: formStream,
contentType: formContentType,
},
});
const formStream = formRequest.body;
const formContentType =
formRequest.headers.get("content-type") || "multipart/form-data";
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-4b", {
multipart: {
body: formStream,
contentType: formContentType,
},
});
```
The parameters you can send to the model are detailed here:
JSON Schema for Model
**Required Parameters**
* `prompt` (string) - Text description of the image to generate
**Optional Parameters**
* `input_image_0` (string) - Binary image
* `input_image_1` (string) - Binary image
* `input_image_2` (string) - Binary image
* `input_image_3` (string) - Binary image
* `guidance` (float) - Guidance scale for generation. Higher values follow the prompt more closely
* `width` (integer) - Width of the image, default `1024` Range: 256-1920
* `height` (integer) - Height of the image, default `768` Range: 256-1920
* `seed` (integer) - Seed for reproducibility
**Note:** Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted.
````plaintext
## Multi-Reference Images
The FLUX.2 klein-4b model supports generating images based on reference images, just like FLUX.2 [dev]. You can use this feature to apply the style of one image to another, add a new character to an image, or iterate on past generated images. You would use it with the same multipart form data structure, with the input images in binary. The model supports up to 4 input images.
For the prompt, you can reference the images based on the index, like `take the subject of image 1 and style it like image 0` or even use natural language like `place the dog beside the woman`.
Note: you have to name the input parameter as `input_image_0`, `input_image_1`, `input_image_2`, `input_image_3` for it to work correctly. All input images must be smaller than 512x512.
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-4b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=take the subject of image 1 and style it like image 0' \
--form input_image_0=@/Users/johndoe/Desktop/icedoutkeanu.png \
--form input_image_1=@/Users/johndoe/Desktop/me.png \
--form width=1024 \
--form height=1024
````
Through Workers AI Binding:
```javascript
//helper function to convert ReadableStream to Blob
async function streamToBlob(stream: ReadableStream, contentType: string): Promise {
const reader = stream.getReader();
const chunks = [];
while (true) {
const { done, value } = await reader.read();
if (done) break;
chunks.push(value);
}
return new Blob(chunks, { type: contentType });
}
const image0 = await fetch("http://image-url");
const image1 = await fetch("http://image-url");
const form = new FormData();
const image_blob0 = await streamToBlob(image0.body, "image/png");
const image_blob1 = await streamToBlob(image1.body, "image/png");
form.append('input_image_0', image_blob0)
form.append('input_image_1', image_blob1)
form.append('prompt', 'take the subject of image 1 and style it like image 0')
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-4b", {
multipart: {
body: form,
contentType: "multipart/form-data"
}
})
```
---
title: Network Services navigation update · Changelog
description: Network Services navigation update
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-15-networking-navigation-update/
md: https://developers.cloudflare.com/changelog/2026-01-15-networking-navigation-update/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Network Services navigation update
Jan 15, 2026
[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Magic Firewall ](https://developers.cloudflare.com/magic-firewall/)[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Magic Network Monitoring](https://developers.cloudflare.com/magic-network-monitoring/)
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

---
title: WAF Release - 2026-01-15 · Changelog
description: Cloudflare WAF managed rulesets 2026-01-15 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-15-waf-release/
md: https://developers.cloudflare.com/changelog/2026-01-15-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2026-01-15
Jan 15, 2026
[WAF](https://developers.cloudflare.com/waf/)
This week's release focuses on improvements to existing detections to enhance coverage.
**Key Findings**
* Existing rule enhancements have been deployed to improve detection resilience against SQL Injection.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | eb3f44c07266448b9fa54ee7ad7dad3e | N/A | SQLi - String Function - Beta | Log | Block | This rule is merged into the original rule "SQLi - String Function" (ID: 63e03eecddfc4b3fb0cad587d32b798c ) |
| Cloudflare Managed Ruleset | adf076af09b2484ca9e7881f9e553ad3 | N/A | SQLi - Sub Query - Beta | Log | Block | This rule is merged into the original rule "SQLi - Sub Query" (ID: 6ec5ecf52c094330aff99a38743e66b1 ) |
---
title: Verify WARP Connector connectivity with a simple ping · Changelog
description: You can now ping the WARP Connector host directly on its LAN IP to
quickly validate connectivity after installation.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-15-warp-connector-ping-support/
md: https://developers.cloudflare.com/changelog/2026-01-15-warp-connector-ping-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Verify WARP Connector connectivity with a simple ping
Jan 15, 2026
[Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/)
We have made it easier to validate connectivity when deploying [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) as part of your [software-defined private network](https://developers.cloudflare.com/reference-architecture/architectures/sase/#connecting-networks).
You can now `ping` the WARP Connector host directly on its LAN IP address immediately after installation. This provides a fast, familiar way to confirm that the Connector is online and reachable within your network before testing access to downstream services.
Starting with [version 2025.10.186.0](https://developers.cloudflare.com/changelog/2026-01-13-warp-linux-ga/), WARP Connector responds to traffic addressed to its own LAN IP, giving you immediate visibility into Connector reachability.
Learn more about deploying [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/) and building private network connectivity with [Cloudflare One](https://developers.cloudflare.com/cloudflare-one/).
---
title: Enhanced HTTP/3 request cancellation visibility · Changelog
description: Cloudflare now provides more accurate visibility into client
request cancellations over HTTP/3, improving observability and reducing
unnecessary origin load
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-19-http3-499-reporting-improvement/
md: https://developers.cloudflare.com/changelog/2026-01-19-http3-499-reporting-improvement/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Enhanced HTTP/3 request cancellation visibility
Jan 19, 2026
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
#### Enhanced HTTP/3 request cancellation visibility
Cloudflare now provides more accurate visibility into HTTP/3 client request cancellations, giving you better insight into real client behavior and reducing unnecessary load on your origins.
Previously, when an HTTP/3 client cancelled a request, the cancellation was not always actioned immediately. This meant requests could continue through the CDN — potentially all the way to your origin — even after the client had abandoned them. In these cases, logs would show the upstream response status (such as `200` or a timeout-related code) rather than reflecting the client cancellation.
Now, Cloudflare terminates cancelled HTTP/3 requests immediately and accurately logs them with a `499` status code.
***
#### Better observability for client behavior
When HTTP/3 clients cancel requests, Cloudflare now immediately reflects this in your logs with a `499` status code. This gives you:
* **More accurate traffic analysis**: Understand exactly when and how often clients cancel requests.
* **Clearer debugging**: Distinguish between true errors and intentional client cancellations.
* **Better availability metrics**: Separate client-initiated cancellations from server-side issues.
***
#### Reduced origin load
Cloudflare now terminates cancelled requests faster, which means:
* **Less wasted compute**: Your origin no longer processes requests that clients have already abandoned.
* **Lower bandwidth usage**: Responses are no longer generated and transmitted for cancelled requests.
* **Improved efficiency**: Resources are freed up to handle active requests.
***
#### What to expect in your logs
You may notice an increase in `499` status codes for HTTP/3 traffic. For HTTP/3, a `499` indicates the client [cancelled the request stream](https://datatracker.ietf.org/doc/html/rfc9114#section-4.1.1) before receiving a complete response — the underlying connection may remain open. This is a normal part of web traffic.
**Tip**: If you use `499` codes in availability calculations, consider whether client-initiated cancellations should be excluded from error rates. These typically represent normal user behavior — such as closing a browser, navigating away from a page, mobile network drops, or cancelling a download — rather than service issues.
***
For more information, refer to [Error 499](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/4xx-client-error/error-499/).
---
title: AI Search path filtering for website and R2 data sources · Changelog
description: Control which paths to include or exclude from indexing.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-ai-search-path-filtering/
md: https://developers.cloudflare.com/changelog/2026-01-20-ai-search-path-filtering/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## AI Search path filtering for website and R2 data sources
Jan 20, 2026
[AI Search](https://developers.cloudflare.com/ai-search/)
[AI Search](https://developers.cloudflare.com/ai-search/) now includes [path filtering](https://developers.cloudflare.com/ai-search/configuration/path-filtering/) for both [website](https://developers.cloudflare.com/ai-search/configuration/data-source/website/#path-filtering) and [R2](https://developers.cloudflare.com/ai-search/configuration/data-source/r2/#path-filtering) data sources. You can now control which content gets indexed by defining include and exclude rules for paths.
By controlling what gets indexed, you can improve the relevance and quality of your search results. You can also use path filtering to split a single data source across multiple AI Search instances for specialized search experiences.

Path filtering uses [micromatch](https://github.com/micromatch/micromatch) patterns, so you can use `*` to match within a directory and `**` to match across directories.
| Use case | Include | Exclude |
| - | - | - |
| Index docs but skip drafts | `**/docs/**` | `**/docs/drafts/**` |
| Keep admin pages out of results | — | `**/admin/**` |
| Index only English content | `**/en/**` | — |
Configure path filters when creating a new instance or update them anytime from **Settings**. Check out [path filtering](https://developers.cloudflare.com/ai-search/configuration/path-filtering/) to learn more.
---
title: Create AI Search instances programmatically via REST API · Changelog
description: Create AI Search instances programmatically using the REST API.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-ai-search-simplified-api/
md: https://developers.cloudflare.com/changelog/2026-01-20-ai-search-simplified-api/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Create AI Search instances programmatically via REST API
Jan 20, 2026
[AI Search](https://developers.cloudflare.com/ai-search/)
You can now create [AI Search](https://developers.cloudflare.com/ai-search/) instances programmatically using the [API](https://developers.cloudflare.com/ai-search/get-started/api/). For example, use the API to create instances for each customer in a multi-tenant application or manage AI Search alongside your other infrastructure.
If you have created an AI Search instance via the [dashboard](https://developers.cloudflare.com/ai-search/get-started/dashboard/) before, you already have a [service API token](https://developers.cloudflare.com/ai-search/configuration/service-api-token/) registered and can start creating instances programmatically right away. If not, follow the [API guide](https://developers.cloudflare.com/ai-search/get-started/api/) to set up your first instance.
For example, you can now create separate search instances for each language on your website:
```bash
for lang in en fr es de; do
curl -X POST "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/ai-search/instances" \
-H "Authorization: Bearer $API_TOKEN" \
-H "Content-Type: application/json" \
--data '{
"id": "docs-'"$lang"'",
"type": "web-crawler",
"source": "example.com",
"source_params": {
"path_include": ["**/'"$lang"'/**"]
}
}'
done
```
Refer to the [REST API reference](https://developers.cloudflare.com/api/resources/ai_search/subresources/instances/methods/create/) for additional configuration options.
---
title: New functions for array and map operations · Changelog
description: Rulesets now support split, join, has_key, and has_value functions
for advanced expression logic.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-array-map-functions/
md: https://developers.cloudflare.com/changelog/2026-01-20-array-map-functions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New functions for array and map operations
Jan 20, 2026
[Rules](https://developers.cloudflare.com/rules/)
#### New functions for array and map operations
Cloudflare Rulesets now include new functions that enable advanced expression logic for evaluating arrays and maps. These functions allow you to build rules that match against lists of values in request or response headers, enabling use cases like country-based blocking using custom headers.
***
#### New functions
| Function | Description |
| - | - |
| `split(source, delimiter)` | Splits a string into an array of strings using the specified delimiter. |
| `join(array, delimiter)` | Joins an array of strings into a single string using the specified delimiter. |
| `has_key(map, key)` | Returns `true` if the specified key exists in the map. |
| `has_value(map, value)` | Returns `true` if the specified value exists in the map. |
***
#### Example use cases
**Check if a country code exists in a header list:**
```txt
has_value(split(http.response.headers["x-allow-country"][0], ","), ip.src.country)
```
**Check if a specific header key exists:**
```txt
has_key(http.request.headers, "x-custom-header")
```
**Join array values for logging or comparison:**
```txt
join(http.request.headers.names, ", ")
```
For more information, refer to the [Functions reference](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/).
---
title: Use auxiliary Workers alongside full-stack frameworks · Changelog
description: Auxiliary Workers are now fully supported when using full-stack
frameworks with the Cloudflare Vite plugin
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-auxiliary-workers/
md: https://developers.cloudflare.com/changelog/2026-01-20-auxiliary-workers/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Use auxiliary Workers alongside full-stack frameworks
Jan 20, 2026
[Workers](https://developers.cloudflare.com/workers/)
Auxiliary Workers are now fully supported when using full-stack frameworks, such as [React Router](https://developers.cloudflare.com/workers/framework-guides/web-apps/react-router/) and [TanStack Start](https://developers.cloudflare.com/workers/framework-guides/web-apps/tanstack-start/), that integrate with the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/reference/api/). They are included alongside the framework's build output in the build output directory. Note that this feature requires Vite 7 or above.
Auxiliary Workers are additional Workers that can be called via [service bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/service-bindings/) from your main (entry) Worker. They are defined in the plugin config, as in the example below:
```ts
import { defineConfig } from "vite";
import { tanstackStart } from "@tanstack/react-start/plugin/vite";
import { cloudflare } from "@cloudflare/vite-plugin";
export default defineConfig({
plugins: [
tanstackStart(),
cloudflare({
viteEnvironment: { name: "ssr" },
auxiliaryWorkers: [{ configPath: "./wrangler.aux.jsonc" }],
}),
],
});
```
See the Vite plugin [API docs](https://developers.cloudflare.com/workers/vite-plugin/reference/api/) for more info.
---
title: Cloudflare Typescript SDK v6.0.0-beta.1 now available · Changelog
description: Cloudflare Typescript SDK v6.0.0-beta.1 fixes a number of known bugs
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-cloudflare-typescript-v600-beta1/
md: https://developers.cloudflare.com/changelog/2026-01-20-cloudflare-typescript-v600-beta1/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Typescript SDK v6.0.0-beta.1 now available
Jan 20, 2026
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[SDK](https://developers.cloudflare.com/sdk/)
> **Disclaimer:** Please note that v6.0.0-beta.1 is in Beta and we are still testing it for stability.
Full Changelog: [v5.2.0...v6.0.0-beta.1](https://github.com/cloudflare/cloudflare-typescript/compare/v5.2.0...v6.0.0-beta.1)
In this release, you'll see a large number of breaking changes. This is primarily due to a change in OpenAPI definitions, which our libraries are based off of, and codegen updates that we rely on to read those OpenAPI definitions and produce our SDK libraries. As the codegen is always evolving and improving, so are our code bases.
Some breaking changes were introduced due to bug fixes, also listed below.
Please ensure you read through the list of changes below before moving to this version - this will help you understand any down or upstream issues it may cause to your environments.
***
#### Breaking Changes
#### Addressing - Parameter Requirements Changed
* `BGPPrefixCreateParams.cidr`: optional → **required**
* `PrefixCreateParams.asn`: `number | null` → `number`
* `PrefixCreateParams.loa_document_id`: required → **optional**
* `ServiceBindingCreateParams.cidr`: optional → **required**
* `ServiceBindingCreateParams.service_id`: optional → **required**
#### API Gateway
* `ConfigurationUpdateResponse` removed
* `PublicSchema` → `OldPublicSchema`
* `SchemaUpload` → `UserSchemaCreateResponse`
* `ConfigurationUpdateParams.properties` removed; use `normalize`
#### CloudforceOne - Response Type Changes
* `ThreatEventBulkCreateResponse`: `number` → complex object with counts and errors
#### D1 Database - Query Parameters
* `DatabaseQueryParams`: simple interface → union type (`D1SingleQuery | MultipleQueries`)
* `DatabaseRawParams`: same change
* Supports batch queries via `batch` array
#### DNS Records - Type Renames (21 types)
All record type interfaces renamed from `*Record` to short names:
* `RecordResponse.ARecord` → `RecordResponse.A`
* `RecordResponse.AAAARecord` → `RecordResponse.AAAA`
* `RecordResponse.CNAMERecord` → `RecordResponse.CNAME`
* `RecordResponse.MXRecord` → `RecordResponse.MX`
* `RecordResponse.NSRecord` → `RecordResponse.NS`
* `RecordResponse.PTRRecord` → `RecordResponse.PTR`
* `RecordResponse.TXTRecord` → `RecordResponse.TXT`
* `RecordResponse.CAARecord` → `RecordResponse.CAA`
* `RecordResponse.CERTRecord` → `RecordResponse.CERT`
* `RecordResponse.DNSKEYRecord` → `RecordResponse.DNSKEY`
* `RecordResponse.DSRecord` → `RecordResponse.DS`
* `RecordResponse.HTTPSRecord` → `RecordResponse.HTTPS`
* `RecordResponse.LOCRecord` → `RecordResponse.LOC`
* `RecordResponse.NAPTRRecord` → `RecordResponse.NAPTR`
* `RecordResponse.SMIMEARecord` → `RecordResponse.SMIMEA`
* `RecordResponse.SRVRecord` → `RecordResponse.SRV`
* `RecordResponse.SSHFPRecord` → `RecordResponse.SSHFP`
* `RecordResponse.SVCBRecord` → `RecordResponse.SVCB`
* `RecordResponse.TLSARecord` → `RecordResponse.TLSA`
* `RecordResponse.URIRecord` → `RecordResponse.URI`
* `RecordResponse.OpenpgpkeyRecord` → `RecordResponse.Openpgpkey`
#### IAM Resource Groups
* `ResourceGroupCreateResponse.scope`: optional single → **required array**
* `ResourceGroupCreateResponse.id`: optional → **required**
#### Origin CA Certificates - Parameter Requirements Changed
* `OriginCACertificateCreateParams.csr`: optional → **required**
* `OriginCACertificateCreateParams.hostnames`: optional → **required**
* `OriginCACertificateCreateParams.request_type`: optional → **required**
#### Pages
* Renamed: `DeploymentsSinglePage` → `DeploymentListResponsesV4PagePaginationArray`
* Domain response fields: many optional → **required**
#### Pipelines - v0 to v1 Migration
* Entire v0 API deprecated; use v1 methods (`createV1`, `listV1`, etc.)
* New sub-resources: `Sinks`, `Streams`
#### R2
* `EventNotificationUpdateParams.rules`: optional → **required**
* Super Slurper: `bucket`, `secret` now required in source params
#### Radar
* `dataSource`: `string` → typed enum (23 values)
* `eventType`: `string` → typed enum (6 values)
* V2 methods require `dimension` parameter (breaking signature change)
#### Resource Sharing
* Removed: `status_message` field from all recipient response types
#### Schema Validation
* Consolidated `SchemaCreateResponse`, `SchemaListResponse`, `SchemaEditResponse`, `SchemaGetResponse` → `PublicSchema`
* Renamed: `SchemaListResponsesV4PagePaginationArray` → `PublicSchemasV4PagePaginationArray`
#### Spectrum
* Renamed union members: `AppListResponse.UnionMember0` → `SpectrumConfigAppConfig`
* Renamed union members: `AppListResponse.UnionMember1` → `SpectrumConfigPaygoAppConfig`
#### Workers
* Removed: `WorkersBindingKindTailConsumer` type (all occurrences)
* Renamed: `ScriptsSinglePage` → `ScriptListResponsesSinglePage`
* Removed: `DeploymentsSinglePage`
#### Zero-Trust DLP
* `datasets.create()`, `update()`, `get()` return types changed
* `PredefinedGetResponse` union members renamed to `UnionMember0-5`
#### Zero-Trust Tunnels
* Removed: `CloudflaredCreateResponse`, `CloudflaredListResponse`, `CloudflaredDeleteResponse`, `CloudflaredEditResponse`, `CloudflaredGetResponse`
* Removed: `CloudflaredListResponsesV4PagePaginationArray`
***
#### Features
#### Abuse Reports (`client.abuseReports`)
* **Reports**: `create`, `list`, `get`
* **Mitigations**: sub-resource for abuse mitigations
#### AI Search (`client.aisearch`)
* **Instances**: `create`, `update`, `list`, `delete`, `read`, `stats`
* **Items**: `list`, `get`
* **Jobs**: `create`, `list`, `get`, `logs`
* **Tokens**: `create`, `update`, `list`, `delete`, `read`
#### Connectivity (`client.connectivity`)
* **Directory Services**: `create`, `update`, `list`, `delete`, `get`
* Supports IPv4, IPv6, dual-stack, and hostname configurations
#### Organizations (`client.organizations`)
* **Organizations**: `create`, `update`, `list`, `delete`, `get`
* **OrganizationProfile**: `update`, `get`
* Hierarchical organization support with parent/child relationships
#### R2 Data Catalog (`client.r2DataCatalog`)
* **Catalog**: `list`, `enable`, `disable`, `get`
* **Credentials**: `create`
* **MaintenanceConfigs**: `update`, `get`
* **Namespaces**: `list`
* **Tables**: `list`, maintenance config management
* Apache Iceberg integration
#### Realtime Kit (`client.realtimeKit`)
* **Apps**: `get`, `post`
* **Meetings**: `create`, `get`, participant management
* **Livestreams**: 10+ methods for streaming
* **Recordings**: start, pause, stop, get
* **Sessions**: transcripts, summaries, chat
* **Webhooks**: full CRUD
* **ActiveSession**: polls, kick participants
* **Analytics**: organization analytics
#### Token Validation (`client.tokenValidation`)
* **Configuration**: `create`, `list`, `delete`, `edit`, `get`
* **Credentials**: `update`
* **Rules**: `create`, `list`, `delete`, `bulkCreate`, `bulkEdit`, `edit`, `get`
* JWT validation with RS256/384/512, PS256/384/512, ES256, ES384
#### Alerting Silences (`client.alerting.silences`)
* `create`, `update`, `list`, `delete`, `get`
#### IAM SSO (`client.iam.sso`)
* `create`, `update`, `list`, `delete`, `get`, `beginVerification`
#### Pipelines v1 (`client.pipelines`)
* **Sinks**: `create`, `list`, `delete`, `get`
* **Streams**: `create`, `update`, `list`, `delete`, `get`
#### Zero-Trust AI Controls / MCP (`client.zeroTrust.access.aiControls.mcp`)
* **Portals**: `create`, `update`, `list`, `delete`, `read`
* **Servers**: `create`, `update`, `list`, `delete`, `read`, `sync`
#### Accounts
* `managed_by` field with `parent_org_id`, `parent_org_name`
#### Addressing LOA Documents
* `auto_generated` field on `LOADocumentCreateResponse`
#### Addressing Prefixes
* `delegate_loa_creation`, `irr_validation_state`, `ownership_validation_state`, `ownership_validation_token`, `rpki_validation_state`
#### AI
* Added `toMarkdown.supported()` method to get all supported conversion formats
#### AI Gateway
* `zdr` field added to all responses and params
#### Alerting
* New alert type: `abuse_report_alert`
* `type` field added to PolicyFilter
#### Browser Rendering
* `ContentCreateParams`: refined to discriminated union (`Variant0 | Variant1`)
* Split into URL-based and HTML-based parameter variants for better type safety
#### Client Certificates
* `reactivate` parameter in edit
#### CloudforceOne
* `ThreatEventCreateParams.indicatorType`: required → optional
* `hasChildren` field added to all threat event response types
* `datasetIds` query parameter on `AttackerListParams`, `CategoryListParams`, `TargetIndustryListParams`
* `categoryUuid` field on `TagCreateResponse`
* `indicators` array for multi-indicator support per event
* `uuid` and `preserveUuid` fields for UUID preservation in bulk create
* `format` query parameter (`'json' | 'stix2'`) on `ThreatEventListParams`
* `createdAt`, `datasetId` fields on `ThreatEventEditParams`
#### Content Scanning
* Added `create()`, `update()`, `get()` methods
#### Custom Pages
* New page types: `basic_challenge`, `under_attack`, `waf_challenge`
#### D1
* `served_by_colo` - colo that handled query
* `jurisdiction` - `'eu' | 'fedramp'`
* **Time Travel** (`client.d1.database.timeTravel`): `getBookmark()`, `restore()` - point-in-time recovery
#### Email Security
* New fields on `InvestigateListResponse`/`InvestigateGetResponse`: `envelope_from`, `envelope_to`, `postfix_id_outbound`, `replyto`
* New detection classification: `'outbound_ndr'`
* Enhanced `Finding` interface with `attachment`, `detection`, `field`, `portion`, `reason`, `score`
* Added `cursor` query parameter to `InvestigateListParams`
#### Gateway Lists
* New list types: `CATEGORY`, `LOCATION`, `DEVICE`
#### Intel
* New issue type: `'configuration_suggestion'`
* `payload` field: `unknown` → typed `Payload` interface with `detection_method`, `zone_tag`
#### Leaked Credential Checks
* Added `detections.get()` method
#### Logpush
* New datasets: `dex_application_tests`, `dex_device_state_events`, `ipsec_logs`, `warp_config_changes`, `warp_toggle_changes`
#### Load Balancers
* `Monitor.port`: `number` → `number | null`
* `Pool.load_shedding`: `LoadShedding` → `LoadShedding | null`
* `Pool.origin_steering`: `OriginSteering` → `OriginSteering | null`
#### Magic Transit
* `license_key` field on connectors
* `provision_license` parameter for auto-provisioning
* IPSec: `custom_remote_identities` with FQDN support
* Snapshots: Bond interface, `probed_mtu` field
#### Pages
* New response types: `ProjectCreateResponse`, `ProjectListResponse`, `ProjectEditResponse`, `ProjectGetResponse`
* Deployment methods return specific response types instead of generic `Deployment`
#### Queues
* Added `subscriptions.get()` method
* Enhanced `SubscriptionGetResponse` with typed event source interfaces
* New event source types: Images, KV, R2, Vectorize, Workers AI, Workers Builds, Workflows
#### R2
* Sippy: new provider `s3` (S3-compatible endpoints)
* Sippy: `bucketUrl` field for S3-compatible sources
* Super Slurper: `keys` field on source response schemas (specify specific keys to migrate)
* Super Slurper: `pathPrefix` field on source schemas
* Super Slurper: `region` field on S3 source params
#### Radar
* Added `geolocations.list()`, `geolocations.get()` methods
* Added V2 dimension-based methods (`summaryV2`, `timeseriesGroupsV2`) to radar sub-resources
#### Resource Sharing
* Added `terminal` boolean field to Resource Error interfaces
#### Rules
* Added `id` field to `ItemDeleteParams.Item`
#### Rulesets
* New buffering fields on `SetConfigRule`: `request_body_buffering`, `response_body_buffering`
#### Secrets Store
* New scopes: `'dex'`, `'access'` (in addition to `'workers'`, `'ai_gateway'`)
#### SSL Certificate Packs
* Response types now proper interfaces (was `unknown`)
* Fields now required: `id`, `certificates`, `hosts`, `status`, `type`
#### Security Center
* `payload` field: `unknown` → typed `Payload` interface with `detection_method`, `zone_tag`
#### Shared Types
* Added: `CloudflareTunnelsV4PagePaginationArray` pagination class
#### Workers
* Added `subdomains.delete()` method
* `Worker.references` - track external dependencies (domains, Durable Objects, queues)
* `Worker.startup_time_ms` - startup timing
* `Script.observability` - observability settings with logging
* `Script.tag`, `Script.tags` - immutable ID and tags
* Placement: support for region, hostname, host-based placement
* `tags`, `tail_consumers` now accept `| null`
* Telemetry: `traces` field, `$containers` event info, `durableObjectId`, `transactionName`, `abr_level` fields
#### Workers for Platforms
* `ScriptUpdateResponse`: new fields `entry_point`, `observability`, `tag`, `tags`
* `placement` field now union of 4 variants (smart mode, region, hostname, host)
* `tags`, `tail_consumers` now nullable
* `TagUpdateParams.body` now accepts `null`
#### Workflows
* `instance_retention`: `unknown` → typed `InstanceRetention` interface with `error_retention`, `success_retention`
* New status option: `'restart'` added to `StatusEditParams.status`
#### Zero-Trust Devices
* External emergency disconnect settings (4 new fields)
* `antivirus` device posture check type
* `os_version_extra` documentation improvements
#### Zones
* New response types: `SubscriptionCreateResponse`, `SubscriptionUpdateResponse`, `SubscriptionGetResponse`
#### Zero-Trust Access Applications
* New `ApplicationType` values: `'mcp'`, `'mcp_portal'`, `'proxy_endpoint'`
* New destination type: `ViaMcpServerPortalDestination` for MCP server access
#### Zero-Trust Gateway
* Added `rules.listTenant()` method
#### Zero-Trust Gateway - Proxy Endpoints
* `ProxyEndpoint`: interface → discriminated union (`ZeroTrustGatewayProxyEndpointIP | ZeroTrustGatewayProxyEndpointIdentity`)
* `ProxyEndpointCreateParams`: interface → union type
* Added `kind` field: `'ip' | 'identity'`
#### Zero-Trust Tunnels
* `WARPConnector*Response`: union type → interface
***
#### Deprecations
* **API Gateway**: `UserSchemas`, `Settings`, `SchemaValidation` resources
* **Audit Logs**: `auditLogId.not` (use `id.not`)
* **CloudforceOne**: `ThreatEvents.get()`, `IndicatorTypes.list()`
* **Devices**: `public_ip` field (use DEX API)
* **Email Security**: `item_count` field in Move responses
* **Pipelines**: v0 methods (use v1)
* **Radar**: old `summary()` and `timeseriesGroups()` methods (use V2)
* **Rulesets**: `disable_apps`, `mirage` fields
* **WARP Connector**: `connections` field
* **Workers**: `environment` parameter in Domains
* **Zones**: `ResponseBuffering` page rule
***
#### Bug Fixes
* **mcp:** correct code tool API endpoint ([599703c](https://github.com/cloudflare/cloudflare-typescript/commit/599703c45672dc899455d74b124018efd4b75095))
* **mcp:** return correct lines on typescript errors ([5d6f999](https://github.com/cloudflare/cloudflare-typescript/commit/5d6f9998ed9999aaa95e1bda8cf50929f3555cf1))
* **organization\_profile:** fix bad reference ([d84ea77](https://github.com/cloudflare/cloudflare-typescript/commit/d84ea77094400055c06554812b84c2f0c8d00cc4))
* **schema\_validation:** correctly reflect model to openapi mapping ([bb86151](https://github.com/cloudflare/cloudflare-typescript/commit/bb861516774b159d80e0f46a5f3abc5a4c9f9d49))
* **workers:** fix tests ([2ee37f7](https://github.com/cloudflare/cloudflare-typescript/commit/2ee37f7adf5a4637d65f61fc225e135eec2579fc))
***
#### Documentation
* Added deprecation notices with migration paths
* **api\_gateway:** deprecate API Shield Schema Validation resources ([8a4b20f](https://github.com/cloudflare/cloudflare-typescript/commit/8a4b20f7a572422f74179fbdb4f1c4fb555e3e40))
* Improved JSDoc examples across all resources
* **workers:** expose subdomain delete documentation ([4f7cc1f](https://github.com/cloudflare/cloudflare-typescript/commit/4f7cc1f2b8861a5b8abc193d287f78264a425062))
---
title: New Workers KV Dashboard UI · Changelog
description: Try out the redesigned Workers KV dashboard with a new homepage
interface for improved navigation and management
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-kv-dash-ui-homepage/
md: https://developers.cloudflare.com/changelog/2026-01-20-kv-dash-ui-homepage/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Workers KV Dashboard UI
Jan 20, 2026
[KV](https://developers.cloudflare.com/kv/)
[Workers KV](https://developers.cloudflare.com/kv/) has an updated dashboard UI with new dashboard styling that makes it easier to navigate and see analytics and settings for a KV namespace.
The new dashboard features a **streamlined homepage** for easy access to your namespaces and key operations, with consistent design with the rest of the dashboard UI updates. It also provides an **improved analytics view**.

The updated dashboard is now available for all Workers KV users. Log in to the [Cloudflare Dashboard](https://dash.cloudflare.com/) to start exploring the new interface.
---
title: Import SQL files as additional modules by default · Changelog
description: The `.sql` file extension is now automatically configured to be
importable in your Worker code
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-sql-module-rule/
md: https://developers.cloudflare.com/changelog/2026-01-20-sql-module-rule/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Import SQL files as additional modules by default
Jan 20, 2026
[Workers](https://developers.cloudflare.com/workers/)
The `.sql` file extension is now automatically configured to be importable in your Worker code when using [Wrangler](https://developers.cloudflare.com/workers/wrangler/bundling/#including-non-javascript-modules) or the [Cloudflare Vite plugin](https://developers.cloudflare.com/workers/vite-plugin/reference/non-javascript-modules/). This is particular useful for importing migrations in Durable Objects and means you no longer need to configure custom rules when using [Drizzle](https://orm.drizzle.team/docs/connect-cloudflare-do).
SQL files are imported as JavaScript strings:
```ts
// `example` will be a JavaScript string
import example from "./example.sql";
```
---
title: Terraform v5.16.0 now available · Changelog
description: Terraform v5.16.0 stabilizes a number of resources and known issues
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-terraform-v5160-provider/
md: https://developers.cloudflare.com/changelog/2026-01-20-terraform-v5160-provider/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Terraform v5.16.0 now available
Jan 20, 2026
[Cloudflare Fundamentals ](https://developers.cloudflare.com/fundamentals/)[Terraform](https://developers.cloudflare.com/terraform/)
In January 2025, we announced the launch of the new Terraform v5 Provider. We greatly appreciate the proactive engagement and valuable feedback from the Cloudflare community following the v5 release. In response, we've established a consistent and rapid [2-3 week cadence](https://github.com/cloudflare/terraform-provider-cloudflare/issues/5774) for releasing targeted improvements, demonstrating our commitment to stability and reliability.
With the help of the community, we have a growing number of resources that we have marked as [stable](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237), with that list continuing to grow with every release. The most used [resources](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237) are on track to be stable by the end of March 2026, when we will also be releasing a new migration tool to you migrate from v4 to v5 with ease.
Thank you for continuing to raise issues. They make our provider stronger and help us build products that reflect your needs.
This release includes bug fixes, the stabilization of even more popular resources, and more.
#### Features
* **custom\_pages:** add "waf\_challenge" as new supported error page type identifier in both resource and data source schemas
* **list:** enhance CIDR validator to check for normalized CIDR notation requiring network address for IPv4 and IPv6
* **magic\_wan\_gre\_tunnel:** add automatic\_return\_routing attribute for automatic routing control
* **magic\_wan\_gre\_tunnel:** add BGP configuration support with new BGP model attribute
* **magic\_wan\_gre\_tunnel:** add bgp\_status computed attribute for BGP connection status information
* **magic\_wan\_gre\_tunnel:** enhance schema with BGP-related attributes and validators
* **magic\_wan\_ipsec\_tunnel:** add automatic\_return\_routing attribute for automatic routing control
* **magic\_wan\_ipsec\_tunnel:** add BGP configuration support with new BGP model attribute
* **magic\_wan\_ipsec\_tunnel:** add bgp\_status computed attribute for BGP connection status information
* **magic\_wan\_ipsec\_tunnel:** add custom\_remote\_identities attribute for custom identity configuration
* **magic\_wan\_ipsec\_tunnel:** enhance schema with BGP and identity-related attributes
* **ruleset:** add request body buffering support
* **ruleset:** enhance ruleset data source with additional configuration options
* **workers\_script:** add observability logs attributes to list data source model
* **workers\_script:** enhance list data source schema with additional configuration options
#### Bug Fixes
* **account\_member**: fix resource importability issues
* **dns\_record:** remove unnecessary fmt.Sprintf wrapper around LoadTestCase call in test configuration helper function
* **load\_balancer:** fix session\_affinity\_ttl type expectations to match Float64 in initial creation and Int64 after migration
* **workers\_kv:** handle special characters correctly in URL encoding
#### Documentation
* **account\_subscription:** update schema description for rate\_plan.sets attribute to clarify it returns an array of strings
* **api\_shield:** add resource-level description for API Shield management of auth ID characteristics
* **api\_shield:** enhance auth\_id\_characteristics.name attribute description to include JWT token configuration format requirements
* **api\_shield:** specify JSONPath expression format for JWT claim locations
* **hyperdrive\_config:** add description attribute to name attribute explaining its purpose in dashboard and API identification
* **hyperdrive\_config:** apply description improvements across resource, data source, and list data source schemas
* **hyperdrive\_config:** improve schema descriptions for cache settings to clarify default values
* **hyperdrive\_config:** update port description to clarify defaults for different database types
#### For more information
* [Terraform Provider](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs)
* [Documentation on using Terraform with Cloudflare](https://developers.cloudflare.com/terraform/)
* [List of stabilized resources](https://github.com/cloudflare/terraform-provider-cloudflare/issues/6237)
---
title: WAF Release - 2026-01-20 · Changelog
description: Cloudflare WAF managed rulesets 2026-01-20 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-20-waf-release/
md: https://developers.cloudflare.com/changelog/2026-01-20-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2026-01-20
Jan 20, 2026
[WAF](https://developers.cloudflare.com/waf/)
This week's release focuses on improvements to existing detections to enhance coverage.
**Key Findings**
* Existing rule enhancements have been deployed to improve detection resilience against SQL injection.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | a291bd530fa346d18cc1ce5a68d90c8f | N/A | SQLi - Comment - Beta | Log | Block | This rule is merged into the original rule "SQLi - Comment" (ID: 42c424998d2a42c9808ab49c6d8d8fe4 ) |
| Cloudflare Managed Ruleset | da289f9e692e4f5397d915fbfaa045cf | N/A | SQLi - Comparison - Beta | Log | Block | This rule is merged into the original rule "SQLi - Comparison" (ID: 8166da327a614849bfa29317e7907480 ) |
---
title: New Placement Hints for Workers · Changelog
description: Explicit placement hints for legacy cloud infrastructure.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-22-explicit-placement-hints/
md: https://developers.cloudflare.com/changelog/2026-01-22-explicit-placement-hints/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Placement Hints for Workers
Jan 22, 2026
[Workers](https://developers.cloudflare.com/workers/)
You can now configure Workers to run close to infrastructure in legacy cloud regions to minimize latency to existing services and databases. This is most useful when your Worker makes multiple round trips.
To [set a placement hint](https://developers.cloudflare.com/workers/configuration/placement/#use-placement-hints), set the `placement.region` property in your Wrangler configuration file:
* wrangler.jsonc
```jsonc
{
"placement": {
"region": "aws:us-east-1",
},
}
```
* wrangler.toml
```toml
[placement]
region = "aws:us-east-1"
```
Placement hints support Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure region identifiers. Workers run in the [Cloudflare data center](https://www.cloudflare.com/network/) with the lowest latency to the specified cloud region.
If your existing infrastructure is not in these cloud providers, expose it to placement probes with `placement.host` for layer 4 checks or `placement.hostname` for layer 7 checks. These probes are designed to locate single-homed infrastructure and are not suitable for anycasted or multicasted resources.
* wrangler.jsonc
```jsonc
{
"placement": {
"host": "my_database_host.com:5432",
},
}
```
* wrangler.toml
```toml
[placement]
host = "my_database_host.com:5432"
```
- wrangler.jsonc
```jsonc
{
"placement": {
"hostname": "my_api_server.com",
},
}
```
- wrangler.toml
```toml
[placement]
hostname = "my_api_server.com"
```
This is an extension of [Smart Placement](https://developers.cloudflare.com/workers/configuration/placement/#use-smart-placement), which automatically places your Workers closer to back-end APIs based on measured latency. When you do not know the location of your back-end APIs or have multiple back-end APIs, set `mode: "smart"`:
* wrangler.jsonc
```jsonc
{
"placement": {
"mode": "smart",
},
}
```
* wrangler.toml
```toml
[placement]
mode = "smart"
```
---
title: New cryptographic functions — encode_base64() and sha256() · Changelog
description: Rulesets now support encode_base64() and sha256() functions for
generating signed request headers directly in expressions.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-22-sha256-base64-encode-functions/
md: https://developers.cloudflare.com/changelog/2026-01-22-sha256-base64-encode-functions/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New cryptographic functions — encode\_base64() and sha256()
Jan 22, 2026
[Rules](https://developers.cloudflare.com/rules/)
Cloudflare Rulesets now includes `encode_base64()` and `sha256()` functions, enabling you to generate signed request headers directly in rule expressions. These functions support common patterns like constructing a canonical string from request attributes, computing a SHA256 digest, and Base64-encoding the result.
***
#### New functions
| Function | Description | Availability |
| - | - | - |
| `encode_base64(input, flags)` | Encodes a string to Base64 format. Optional `flags` parameter: `u` for URL-safe encoding, `p` for padding (adds `=` characters to make the output length a multiple of 4, as required by some systems). By default, output is standard Base64 without padding. | All plans (in header transform rules) |
| `sha256(input)` | Computes a SHA256 hash of the input string. | Requires enablement |
Note
The `sha256()` function is available as an Enterprise add-on and requires a specific entitlement. Contact your account team to enable it.
***
#### Examples
**Encode a string to Base64 format:**
```txt
encode_base64("hello world")
```
Returns: `aGVsbG8gd29ybGQ`
**Encode a string to Base64 format with padding:**
```txt
encode_base64("hello world", "p")
```
Returns: `aGVsbG8gd29ybGQ=`
**Perform a URL-safe Base64 encoding of a string:**
```txt
encode_base64("hello world", "u")
```
Returns: `aGVsbG8gd29ybGQ`
**Compute the SHA256 hash of a secret token:**
```txt
sha256("my-token")
```
Returns a hash that your origin can validate to authenticate requests.
**Compute the SHA256 hash of a string and encode the result to Base64 format:**
```txt
encode_base64(sha256("my-token"))
```
Combines hashing and encoding for systems that expect Base64-encoded signatures.
For more information, refer to the [Functions reference](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/).
---
title: Vectorize indexes now support up to 10 million vectors · Changelog
description: Vectorize indexes now support up to 10 million vectors.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-23-increased-index-capacity/
md: https://developers.cloudflare.com/changelog/2026-01-23-increased-index-capacity/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Vectorize indexes now support up to 10 million vectors
Jan 23, 2026
[Vectorize](https://developers.cloudflare.com/vectorize/)
You can now store up to 10 million vectors in a single Vectorize index, doubling the previous limit of 5 million vectors. This enables larger-scale semantic search, recommendation systems, and retrieval-augmented generation (RAG) applications without splitting data across multiple indexes.
Vectorize continues to support indexes with up to 1,536 dimensions per vector at 32-bit precision. Refer to the [Vectorize limits documentation](https://developers.cloudflare.com/vectorize/platform/limits/) for complete details.
---
title: New 2FA Experience for Login · Changelog
description: Users without 2FA enabled get prompted to enroll on login
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-23-new-2fa-experience/
md: https://developers.cloudflare.com/changelog/2026-01-23-new-2fa-experience/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New 2FA Experience for Login
Jan 23, 2026
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)

In an effort to improve overall user security, users without 2FA will be prompted upon login to enroll in email 2FA. This will improve user security posture while minimizing friction. Users without email 2FA enabled will see a prompt to secure their account with additional factors upon logging in. Enrolling in 2FA remains optional, but strongly encouraged as it is the best way to prevent account takeovers.
We also made changes to existing 2FA screens to improve the user experience. Now we have distinct experiences for each 2FA factor type, reflective of the way that factor works.
#### For more information
* [Configure Email Two Factor Authentication](https://developers.cloudflare.com/fundamentals/user-profiles/2fa/#configure-email-two-factor-authentication)
---
title: Increased Pages file limit to 100,000 for paid plans · Changelog
description: Paid plans can now deploy Pages sites with up to 100,000 files,
increased from the previous limit of 20,000 files.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-23-pages-file-limit-increase/
md: https://developers.cloudflare.com/changelog/2026-01-23-pages-file-limit-increase/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Increased Pages file limit to 100,000 for paid plans
Jan 23, 2026
[Pages](https://developers.cloudflare.com/pages/)
Paid plans can now have up to 100,000 files per Pages site, increased from the previous limit of 20,000 files.
To enable this increased limit, set the environment variable `PAGES_WRANGLER_MAJOR_VERSION=4` in your Pages project settings.
The Free plan remains at 20,000 files per site.
For more details, refer to the [Pages limits documentation](https://developers.cloudflare.com/pages/platform/limits/#files).
---
title: WAF Release - 2026-01-26 · Changelog
description: Cloudflare WAF managed rulesets 2026-01-26 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-26-waf-release/
md: https://developers.cloudflare.com/changelog/2026-01-26-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2026-01-26
Jan 26, 2026
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces new detections for denial-of-service attempts targeting React CVE-2026-23864 ().
**Key Findings**
* CVE-2026-23864 () affects `react-server-dom-parcel`, `react-server-dom-turbopack`, and `react-server-dom-webpack` packages.
* Attackers can send crafted HTTP requests to Server Function endpoints, causing server crashes, out-of-memory exceptions, or excessive CPU usage.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | aaede80b4d414dc89c443cea61680354 | N/A | React Server - DOS - CVE:CVE-2026-23864 - 1 | N/A | Block | This is a new detection. |
| Cloudflare Managed Ruleset | 3e93c9faaafa447c83a525f2dcdffcf8 | N/A | React Server - DOS - CVE:CVE-2026-23864 - 2 | N/A | Block | This is a new detection. |
| Cloudflare Managed Ruleset | 930020d567684f19b05fb35b349edbc6 | N/A | React Server - DOS - CVE:CVE-2026-23864 - 3 | N/A | Block | This is a new detection. |
---
title: Control request and response body buffering in Configuration Rules · Changelog
description: New settings in Configuration Rules let you control how Cloudflare
buffers HTTP request and response bodies before forwarding to origin or
client.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-27-body-buffering-settings/
md: https://developers.cloudflare.com/changelog/2026-01-27-body-buffering-settings/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Control request and response body buffering in Configuration Rules
Jan 27, 2026
[Rules](https://developers.cloudflare.com/rules/)
You can now control how Cloudflare buffers HTTP request and response bodies using two new settings in [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/).
#### Request body buffering
Controls how Cloudflare buffers HTTP request bodies before forwarding them to your origin server:
| Mode | Behavior |
| - | - |
| **Standard** (default) | Cloudflare can inspect a prefix of the request body for enabled functionality such as WAF and Bot Management. |
| **Full** | Buffers the entire request body before sending to origin. |
| **None** | No buffering — the request body streams directly to origin without inspection. |
#### Response body buffering
Controls how Cloudflare buffers HTTP response bodies before forwarding them to the client:
| Mode | Behavior |
| - | - |
| **Standard** (default) | Cloudflare can inspect a prefix of the response body for enabled functionality. |
| **None** | No buffering — the response body streams directly to the client without inspection. |
Warning
Setting body buffering to **None** may break security functionality that requires body inspection, including the Web Application Firewall (WAF) and Bot Management. Ensure that any paths where you disable buffering do not require security inspection.
Availability
These settings only take effect on zones running Cloudflare's [latest CDN proxy](https://blog.cloudflare.com/20-percent-internet-upgrade/). Enterprise customers can contact their account team to enable the latest proxy on their zones.
#### API example
```json
{
"action": "set_config",
"action_parameters": {
"request_body_buffering": "standard",
"response_body_buffering": "none"
}
}
```
For more information, refer to [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/).
---
title: Configure Cloudflare source IPs (beta) · Changelog
description: Configure the source IP range used by Cloudflare services when
sending traffic to private networks
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-27-configure-cloudflare-source-ips/
md: https://developers.cloudflare.com/changelog/2026-01-27-configure-cloudflare-source-ips/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Configure Cloudflare source IPs (beta)
Jan 27, 2026
[Cloudflare One ](https://developers.cloudflare.com/cloudflare-one/)[Magic WAN](https://developers.cloudflare.com/magic-wan/)
Cloudflare source IPs are the IP addresses used by Cloudflare services (such as Load Balancing, Gateway, and Browser Isolation) when sending traffic to your private networks.
For customers using legacy mode routing, traffic to private networks is sourced from public Cloudflare IPs, which may cause IP conflicts. For customers using Unified Routing mode (beta), traffic to private networks is sourced from dedicated, non-Internet-routable private IPv4 range to ensure:
* Symmetric routing over private network connections
* Proper firewall state preservation
* Private traffic stays on secure paths
Key details:
* **IPv4**: Sourced from `100.64.0.0/12` by default, configurable to any `/12` CIDR
* **IPv6**: Sourced from `2606:4700:cf1:5000::/64` (not configurable)
* **Affected connectors**: GRE, IPsec, CNI, WARP Connector, and WARP Client (Cloudflare Tunnel is not affected)
Configuring Cloudflare source IPs requires Unified Routing (beta) and the `Cloudflare One Networks Write` permission.
For configuration details, refer to [Configure Cloudflare source IPs](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-cloudflare-source-ips/).
---
title: Added Timezone preferences settings · Changelog
description: Added timezone preferences settings to the user profile dropdown.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-27-timezone-preferences/
md: https://developers.cloudflare.com/changelog/2026-01-27-timezone-preferences/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Added Timezone preferences settings
Jan 27, 2026
[Cloudflare Fundamentals](https://developers.cloudflare.com/fundamentals/)
You can now set the timezone in the Cloudflare dashboard as Coordinated Universal Time (UTC) or your browser or system's timezone.
#### What's New
Unless otherwise specified in the user interface, all dates and times in the Cloudflare dashboard are now displayed in the selected timezone.
You can change the timezone setting from the user profile dropdown.

The page will reload to apply the new timezone setting.
---
title: WARP client for macOS (version 2026.1.89.1) · Changelog
description: WARP client for macOS (version 2026.1.89.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-27-warp-macos-beta/
md: https://developers.cloudflare.com/changelog/2026-01-27-warp-macos-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for macOS (version 2026.1.89.1)
Jan 27, 2026
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the macOS WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes and improvements.
**Changes and improvements**
* Fixed an issue causing failure of the [local network exclusion](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#allow-users-to-enable-local-network-exclusion) feature when configured with a timeout of `0`.
* Improvement for more accurate reporting of device colocation information in the Cloudflare One dashboard.
---
title: WARP client for Windows (version 2026.1.89.1) · Changelog
description: WARP client for Windows (version 2026.1.89.1)
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-27-warp-windows-beta/
md: https://developers.cloudflare.com/changelog/2026-01-27-warp-windows-beta/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WARP client for Windows (version 2026.1.89.1)
Jan 27, 2026
[Zero Trust WARP Client](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/)
A new Beta release for the Windows WARP client is now available on the [beta releases downloads page](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/download-warp/beta-releases/).
This release contains minor fixes, improvements, and new features.
**Changes and improvements**
* Improvements to [multi-user mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/windows-multiuser/). Fixed an issue where when switching from a pre-login registration to a user registration, Mobile Device Management (MDM) configuration association could be lost.
* Added a new feature to [manage NetBIOS over TCP/IP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#netbios-over-tcpip) functionality on the Windows client. NetBIOS over TCP/IP on the Windows client is now disabled by default and can be enabled in [device profile settings](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/device-profiles/).
* Fixed an issue causing failure of the [local network exclusion](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-settings/#allow-users-to-enable-local-network-exclusion) feature when configured with a timeout of `0`.
* Improvement for the Windows [client certificate posture check](https://developers.cloudflare.com/cloudflare-one/reusable-components/posture-checks/warp-client-checks/client-certificate/) to ensure logged results are from checks that run once users log in.
* Improvement for more accurate reporting of device colocation information in the Cloudflare One dashboard.
**Known issues**
* For Windows 11 24H2 users, Microsoft has confirmed a regression that may lead to performance issues like mouse lag, audio cracking, or other slowdowns. Cloudflare recommends users experiencing these issues upgrade to a minimum [Windows 11 24H2 KB5062553](https://support.microsoft.com/en-us/topic/july-8-2025-kb5062553-os-build-26100-4652-523e69cb-051b-43c6-8376-6a76d6caeefd) or higher for resolution.
* Devices with KB5055523 installed may receive a warning about `Win32/ClickFix.ABA` being present in the installer. To resolve this false positive, update Microsoft Security Intelligence to [version 1.429.19.0](https://www.microsoft.com/en-us/wdsi/definitions/antimalware-definition-release-notes?requestVersion=1.429.19.0) or later.
* DNS resolution may be broken when the following conditions are all true:
* WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
* A custom DNS server address is configured on the primary network adapter.
* The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
---
title: Launching FLUX.2 [klein] 9B on Workers AI · Changelog
description: New ultra-fast FLUX.2 [klein] 9B model on Workers AI
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-28-flux-2-klein-9b-workers-ai/
md: https://developers.cloudflare.com/changelog/2026-01-28-flux-2-klein-9b-workers-ai/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Launching FLUX.2 \[klein] 9B on Workers AI
Jan 28, 2026
[Workers AI](https://developers.cloudflare.com/workers-ai/)
We have partnered with Black Forest Labs (BFL) again to bring their optimized FLUX.2 \[klein] 9B model to Workers AI. This distilled model offers enhanced quality compared to the 4B variant, while maintaining cost-effective pricing. With a fixed 4-step inference process, Klein 9B is ideal for rapid prototyping and real-time applications where both speed and quality matter.
Read the [BFL blog](https://bfl.ai/blog) to learn more about the model itself, or try it out yourself on our [multi modal playground](https://multi-modal.ai.cloudflare.com/).
Pricing documentation is available on the [model page](https://developers.cloudflare.com/workers-ai/models/flux-2-klein-9b/) or [pricing page](https://developers.cloudflare.com/workers-ai/platform/pricing/).
#### Workers AI platform specifics
The model hosted on Workers AI is optimized for speed with a **fixed 4-step inference process** and supports up to 4 image inputs. Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted. Like FLUX.2 \[dev] and FLUX.2 \[klein] 4B, this image model uses multipart form data inputs, even if you just have a prompt.
With the REST API, the multipart form data input looks like this:
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-9b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=a sunset at the alps' \
--form width=1024 \
--form height=1024
```
With the Workers AI binding, you can use it as such:
```javascript
const form = new FormData();
form.append("prompt", "a sunset with a dog");
form.append("width", "1024");
form.append("height", "1024");
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-9b", {
multipart: {
body: form,
contentType: "multipart/form-data",
},
});
```
The parameters you can send to the model are detailed here:
JSON Schema for Model
**Required Parameters**
* `prompt` (string) - Text description of the image to generate
**Optional Parameters**
* `input_image_0` (string) - Binary image
* `input_image_1` (string) - Binary image
* `input_image_2` (string) - Binary image
* `input_image_3` (string) - Binary image
* `guidance` (float) - Guidance scale for generation. Higher values follow the prompt more closely
* `width` (integer) - Width of the image, default `1024` Range: 256-1920
* `height` (integer) - Height of the image, default `768` Range: 256-1920
* `seed` (integer) - Seed for reproducibility
**Note:** Since this is a distilled model, the `steps` parameter is fixed at 4 and cannot be adjusted.
#### Multi-reference images
The FLUX.2 klein-9b model supports generating images based on reference images, just like FLUX.2 \[dev] and FLUX.2 \[klein] 4B. You can use this feature to apply the style of one image to another, add a new character to an image, or iterate on past generated images. You would use it with the same multipart form data structure, with the input images in binary. The model supports up to 4 input images.
For the prompt, you can reference the images based on the index, like `take the subject of image 1 and style it like image 0` or even use natural language like `place the dog beside the woman`.
You must name the input parameter as `input_image_0`, `input_image_1`, `input_image_2`, `input_image_3` for it to work correctly. All input images must be smaller than 512x512.
```bash
curl --request POST \
--url 'https://api.cloudflare.com/client/v4/accounts/{ACCOUNT}/ai/run/@cf/black-forest-labs/flux-2-klein-9b' \
--header 'Authorization: Bearer {TOKEN}' \
--header 'Content-Type: multipart/form-data' \
--form 'prompt=take the subject of image 1 and style it like image 0' \
--form input_image_0=@/Users/johndoe/Desktop/icedoutkeanu.png \
--form input_image_1=@/Users/johndoe/Desktop/me.png \
--form width=1024 \
--form height=1024
```
Through Workers AI Binding:
```javascript
//helper function to convert ReadableStream to Blob
async function streamToBlob(stream: ReadableStream, contentType: string): Promise {
const reader = stream.getReader();
const chunks = [];
while (true) {
const { done, value } = await reader.read();
if (done) break;
chunks.push(value);
}
return new Blob(chunks, { type: contentType });
}
const image0 = await fetch("http://image-url");
const image1 = await fetch("http://image-url");
const form = new FormData();
const image_blob0 = await streamToBlob(image0.body, "image/png");
const image_blob1 = await streamToBlob(image1.body, "image/png");
form.append('input_image_0', image_blob0)
form.append('input_image_1', image_blob1)
form.append('prompt', 'take the subject of image 1 and style it like image 0')
const resp = await env.AI.run("@cf/black-forest-labs/flux-2-klein-9b", {
multipart: {
body: form,
contentType: "multipart/form-data"
}
})
```
---
title: BGP over GRE and IPsec tunnels · Changelog
description: Configure BGP peering over IPsec and GRE tunnels for dynamic routing
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-30-bgp-over-tunnels/
md: https://developers.cloudflare.com/changelog/2026-01-30-bgp-over-tunnels/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## BGP over GRE and IPsec tunnels
Jan 30, 2026
[Magic WAN ](https://developers.cloudflare.com/magic-wan/)[Magic Transit ](https://developers.cloudflare.com/magic-transit/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using IPsec and GRE tunnel on-ramps (beta).
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via IPsec and GRE tunnel on-ramps.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
For configuration details, refer to:
* [Configure BGP routes for Magic WAN](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes)
* [Configure BGP routes for Magic Transit](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes)
---
title: Reduced minimum cache TTL for Workers KV to 30 seconds · Changelog
description: The minimum cacheTtl parameter has been reduced from 60 seconds to
30 seconds, enabling faster cache refreshes and more granular cache control.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-01-30-kv-reduced-minimum-cachettl/
md: https://developers.cloudflare.com/changelog/2026-01-30-kv-reduced-minimum-cachettl/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Reduced minimum cache TTL for Workers KV to 30 seconds
Jan 30, 2026
[KV](https://developers.cloudflare.com/kv/)
The minimum `cacheTtl` parameter for Workers KV has been reduced from 60 seconds to 30 seconds. This change applies to both `get()` and `getWithMetadata()` methods.
This reduction allows you to maintain more up-to-date cached data and have finer-grained control over cache behavior. Applications requiring faster data refresh rates can now configure cache durations as low as 30 seconds instead of the previous 60-second minimum.
The `cacheTtl` parameter defines how long a KV result is cached at the global network location it is accessed from:
```js
// Read with custom cache TTL
const value = await env.NAMESPACE.get("my-key", {
cacheTtl: 30, // Cache for minimum 30 seconds (previously 60)
});
// getWithMetadata also supports the reduced cache TTL
const valueWithMetadata = await env.NAMESPACE.getWithMetadata("my-key", {
cacheTtl: 30, // Cache for minimum 30 seconds
});
```
The default cache TTL remains unchanged at 60 seconds. Upgrade to the latest version of Wrangler to be able to use 30 seconds `cacheTtl`.
This change affects all KV read operations using the binding API. For more information, consult the [Workers KV cache TTL documentation](https://developers.cloudflare.com/kv/api/read-key-value-pairs/#cachettl-parameter).
---
title: WAF Release - 2026-02-02 · Changelog
description: Cloudflare WAF managed rulesets 2026-02-02 release
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-02-02-waf-release/
md: https://developers.cloudflare.com/changelog/2026-02-02-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - 2026-02-02
Feb 02, 2026
[WAF](https://developers.cloudflare.com/waf/)
This week’s release introduces new detections for CVE-2025-64459 and CVE-2025-24893.
**Key Findings**
* CVE-2025-64459: Django versions prior to 5.1.14, 5.2.8, and 4.2.26 are vulnerable to SQL injection via crafted dictionaries passed to QuerySet methods and the `Q()` class.
* CVE-2025-24893: XWiki allows unauthenticated remote code execution through crafted requests to the SolrSearch endpoint, affecting the entire installation.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
| - | - | - | - | - | - | - |
| Cloudflare Managed Ruleset | 7a47683eacce4abd870ab2c630698ff3 | N/A | XWiki - Remote Code Execution - CVE:CVE-2025-24893 2 | Log | Block | This is a new detection. |
| Cloudflare Managed Ruleset | ad5c52f6ca334ef4a844e5e5da8ba7e6 | N/A | Django SQLI - CVE:CVE-2025-64459 | Log | Block | This is a new detection. |
| Cloudflare Managed Ruleset | 8f0d5c98bd24460a9305a1558d667511 | N/A | NoSQL, MongoDB - SQLi - Comparison - 2 | Block | Block | Rule metadata description refined. Detection unchanged. |
---
title: "Agents SDK v0.3.7: Workflows integration, synchronous state, and
scheduleEvery() · Changelog"
description: The Agents SDK v0.3.7 introduces first-class Cloudflare Workflows
integration, synchronous setState() with validation hooks, fixed-interval
scheduling with scheduleEvery(), and callable system improvements.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-02-03-agents-workflows-integration/
md: https://developers.cloudflare.com/changelog/2026-02-03-agents-workflows-integration/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Agents SDK v0.3.7: Workflows integration, synchronous state, and scheduleEvery()
Feb 03, 2026
[Agents ](https://developers.cloudflare.com/agents/)[Workflows](https://developers.cloudflare.com/workflows/)
The latest release of the [Agents SDK](https://github.com/cloudflare/agents) brings first-class support for [Cloudflare Workflows](https://developers.cloudflare.com/workflows/), synchronous state management, and new scheduling capabilities.
#### Cloudflare Workflows integration
Agents excel at real-time communication and state management. Workflows excel at durable execution. Together, they enable powerful patterns where Agents handle WebSocket connections while Workflows handle long-running tasks, retries, and human-in-the-loop flows.
Use the new `AgentWorkflow` class to define workflows with typed access to your Agent:
* JavaScript
```js
import { AgentWorkflow } from "agents/workflows";
export class ProcessingWorkflow extends AgentWorkflow {
async run(event, step) {
// Call Agent methods via RPC
await this.agent.updateStatus(event.payload.taskId, "processing");
// Non-durable: progress reporting to clients
await this.reportProgress({ step: "process", percent: 0.5 });
this.broadcastToClients({ type: "update", taskId: event.payload.taskId });
// Durable via step: idempotent, won't repeat on retry
await step.mergeAgentState({ taskProgress: 0.5 });
const result = await step.do("process", async () => {
return processData(event.payload.data);
});
await step.reportComplete(result);
return result;
}
}
```
* TypeScript
```ts
import { AgentWorkflow } from "agents/workflows";
import type { AgentWorkflowEvent, AgentWorkflowStep } from "agents/workflows";
export class ProcessingWorkflow extends AgentWorkflow {
async run(event: AgentWorkflowEvent, step: AgentWorkflowStep) {
// Call Agent methods via RPC
await this.agent.updateStatus(event.payload.taskId, "processing");
// Non-durable: progress reporting to clients
await this.reportProgress({ step: "process", percent: 0.5 });
this.broadcastToClients({ type: "update", taskId: event.payload.taskId });
// Durable via step: idempotent, won't repeat on retry
await step.mergeAgentState({ taskProgress: 0.5 });
const result = await step.do("process", async () => {
return processData(event.payload.data);
});
await step.reportComplete(result);
return result;
}
}
```
Start workflows from your Agent with `runWorkflow()` and handle lifecycle events:
* JavaScript
```js
export class MyAgent extends Agent {
async startTask(taskId, data) {
const instanceId = await this.runWorkflow("PROCESSING_WORKFLOW", {
taskId,
data,
});
return { instanceId };
}
async onWorkflowProgress(workflowName, instanceId, progress) {
this.broadcast(JSON.stringify({ type: "progress", progress }));
}
async onWorkflowComplete(workflowName, instanceId, result) {
console.log(`Workflow ${instanceId} completed`);
}
async onWorkflowError(workflowName, instanceId, error) {
console.error(`Workflow ${instanceId} failed:`, error);
}
}
```
* TypeScript
```ts
export class MyAgent extends Agent {
async startTask(taskId: string, data: string) {
const instanceId = await this.runWorkflow("PROCESSING_WORKFLOW", {
taskId,
data,
});
return { instanceId };
}
async onWorkflowProgress(
workflowName: string,
instanceId: string,
progress: unknown,
) {
this.broadcast(JSON.stringify({ type: "progress", progress }));
}
async onWorkflowComplete(
workflowName: string,
instanceId: string,
result?: unknown,
) {
console.log(`Workflow ${instanceId} completed`);
}
async onWorkflowError(
workflowName: string,
instanceId: string,
error: unknown,
) {
console.error(`Workflow ${instanceId} failed:`, error);
}
}
```
Key workflow methods on your Agent:
* `runWorkflow(workflowName, params, options?)` — Start a workflow with optional metadata
* `getWorkflow(workflowId)` / `getWorkflows(criteria?)` — Query workflows with cursor-based pagination
* `approveWorkflow(workflowId)` / `rejectWorkflow(workflowId)` — Human-in-the-loop approval flows
* `pauseWorkflow()`, `resumeWorkflow()`, `terminateWorkflow()` — Workflow control
#### Synchronous setState()
State updates are now synchronous with a new `validateStateChange()` validation hook:
* JavaScript
```js
export class MyAgent extends Agent {
validateStateChange(oldState, newState) {
// Return false to reject the change
if (newState.count < 0) return false;
// Return modified state to transform
return { ...newState, lastUpdated: Date.now() };
}
}
```
* TypeScript
```ts
export class MyAgent extends Agent {
validateStateChange(oldState: State, newState: State): State | false {
// Return false to reject the change
if (newState.count < 0) return false;
// Return modified state to transform
return { ...newState, lastUpdated: Date.now() };
}
}
```
#### scheduleEvery() for recurring tasks
The new `scheduleEvery()` method enables fixed-interval recurring tasks with built-in overlap prevention:
* JavaScript
```js
// Run every 5 minutes
await this.scheduleEvery("syncData", 5 * 60 * 1000, { source: "api" });
```
* TypeScript
```ts
// Run every 5 minutes
await this.scheduleEvery("syncData", 5 * 60 * 1000, { source: "api" });
```
#### Callable system improvements
* **Client-side RPC timeout** — Set timeouts on callable method invocations
* **`StreamingResponse.error(message)`** — Graceful stream error signaling
* **`getCallableMethods()`** — Introspection API for discovering callable methods
* **Connection close handling** — Pending calls are automatically rejected on disconnect
- JavaScript
```js
await agent.call("method", [args], {
timeout: 5000,
stream: { onChunk, onDone, onError },
});
```
- TypeScript
```ts
await agent.call("method", [args], {
timeout: 5000,
stream: { onChunk, onDone, onError },
});
```
#### Email and routing enhancements
**Secure email reply routing** — Email replies are now secured with HMAC-SHA256 signed headers, preventing unauthorized routing of emails to agent instances.
**Routing improvements:**
* `basePath` option to bypass default URL construction for custom routing
* Server-sent identity — Agents send `name` and `agent` type on connect
* New `onIdentity` and `onIdentityChange` callbacks on the client
- JavaScript
```js
const agent = useAgent({
basePath: "user",
onIdentity: (name, agentType) => console.log(`Connected to ${name}`),
});
```
- TypeScript
```ts
const agent = useAgent({
basePath: "user",
onIdentity: (name, agentType) => console.log(`Connected to ${name}`),
});
```
#### Upgrade
To update to the latest version:
```sh
npm i agents@latest
```
For the complete Workflows API reference and patterns, see [Run Workflows](https://developers.cloudflare.com/agents/api-reference/run-workflows/).
---
title: Improve Global Upload Performance with R2 Local Uploads - Now in Open
Beta · Changelog
description: R2 Local Uploads reduces total request duration for uploads by up
to 75%. It writes object data to a nearby location, then asynchronously copies
it to your bucket. Data is available immediately.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-02-03-r2-local-uploads/
md: https://developers.cloudflare.com/changelog/2026-02-03-r2-local-uploads/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Improve Global Upload Performance with R2 Local Uploads - Now in Open Beta
Feb 03, 2026
[R2](https://developers.cloudflare.com/r2/)
[Local Uploads](https://developers.cloudflare.com/r2/buckets/local-uploads/) is now available in open beta. Enable it on your [R2](https://developers.cloudflare.com/r2/) bucket to improve upload performance when clients upload data from a different region than your bucket. With Local Uploads enabled, object data is written to storage infrastructure near the client, then asynchronously replicated to your bucket. The object is immediately accessible and remains strongly consistent throughout. Refer to [How R2 works](https://developers.cloudflare.com/r2/how-r2-works/) for details on how data is written to your bucket.
In our tests, we observed **up to 75% reduction in Time to Last Byte (TTLB)** for upload requests when Local Uploads is enabled.

This feature is ideal when:
* Your users are globally distributed
* Upload performance and reliability is critical to your application
* You want to optimize write performance without changing your bucket's primary location
To enable Local Uploads on your bucket, find **Local Uploads** in your bucket settings in the [Cloudflare Dashboard](https://dash.cloudflare.com/?to=/:account/r2/overview), or run:
```sh
npx wrangler r2 bucket local-uploads enable
```
Enabling Local Uploads on a bucket is seamless: existing uploads will complete as expected and there’s no interruption to traffic. There is no additional cost to enable Local Uploads. Upload requests incur the standard [Class A operation costs](https://developers.cloudflare.com/r2/pricing/) same as upload requests made without Local Uploads.
For more information, refer to [Local Uploads](https://developers.cloudflare.com/r2/buckets/local-uploads/).
---
title: Threat actor identification with "also known as" aliases · Changelog
description: Threat events now include aliases and common names for threat
actors to help teams correlate intelligence across different platforms
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-02-03-threat-actor-name-mapping/
md: https://developers.cloudflare.com/changelog/2026-02-03-threat-actor-name-mapping/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Threat actor identification with "also known as" aliases
Feb 03, 2026
[Security Center](https://developers.cloudflare.com/security-center/)
Identifying threat actors can be challenging, because naming conventions often vary across the security industry. To simplify your research, **Cloudflare Threat Events** now include an **Also known as** field, providing a list of common aliases and industry-standard names for the groups we track.
This new field is available in both the Cloudflare dashboard and via the API. In the dashboard, you can view these aliases by expanding the event details side panel (under the **Attacker** field) or by adding it as a column in your configurable table view.
#### Key benefits
* Easily map Cloudflare-tracked actors to the naming conventions used by other vendors without manual cross-referencing.
* Quickly identify if a detected threat actor matches a group your team is already monitoring via other intelligence feeds.
For more information on how to access this data, refer to the [Threat Events API documentation](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/threat_events/).
---
title: Visualize your Workflows in the Cloudflare dashboard · Changelog
description: Visualize your Workflow's step sequence, loops, and branching logic
directly in the Cloudflare dashboard
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-02-03-workflows-visualizer/
md: https://developers.cloudflare.com/changelog/2026-02-03-workflows-visualizer/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Visualize your Workflows in the Cloudflare dashboard
Feb 04, 2026
[Workflows ](https://developers.cloudflare.com/workflows/)[Workers](https://developers.cloudflare.com/workers/)
Cloudflare Workflows now automatically generates visual diagrams from your code
Your Workflow is parsed to provide a visual map of the Workflow structure, allowing you to:
* Understand how steps connect and execute
* Visualize loops and nested logic
* Follow branching paths for conditional logic

You can collapse loops and nested logic to see the high-level flow, or expand them to see every step.
Workflow diagrams are available in beta for all JavaScript and TypeScript Workflows. Find your Workflows in the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/workers/workflows) to see their diagrams.
---
title: Cloudflare Queues now available on Workers Free plan · Changelog
description: Cloudflare Queues now available on Workers Free plan with up to
10,000 operations included per day
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-02-04-queues-free-plan/
md: https://developers.cloudflare.com/changelog/2026-02-04-queues-free-plan/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare Queues now available on Workers Free plan
Feb 04, 2026
[Queues](https://developers.cloudflare.com/queues/)
[Cloudflare Queues](https://developers.cloudflare.com/queues) is now part of the Workers free plan, offering guaranteed message delivery across up to **10,000 queues** to either [Cloudflare Workers](https://developers.cloudflare.com/workers) or [HTTP pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers). Every Cloudflare account now includes **10,000 operations per day** across reads, writes, and deletes. For more details on how each operation is defined, refer to [Queues pricing](https://developers.cloudflare.com/workers/platform/pricing/#queues).
All features of the existing Queues functionality are available on the free plan, including unlimited [event subscriptions](https://developers.cloudflare.com/queues/event-subscriptions/). Note that the maximum retention period on the free tier, however, is 24 hours rather than 14 days.
If you are new to Cloudflare Queues, follow [this guide](https://developers.cloudflare.com/queues/get-started/) or try one of our [tutorials](https://developers.cloudflare.com/queues/tutorials/) to get started.
---
title: Visualize data, share links, and create exports with the new Workers
Observability dashboard · Changelog
description: The new Workers Observability dashboard includes new features like
data visualizations, shareable links, and exports (JSON/CSV).
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-02-06-observability-ui-refresh/
md: https://developers.cloudflare.com/changelog/2026-02-06-observability-ui-refresh/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Visualize data, share links, and create exports with the new Workers Observability dashboard
Feb 06, 2026
[Workers](https://developers.cloudflare.com/workers/)
The [Workers Observability dashboard](https://dash.cloudflare.com/?to=/:account/workers-and-pages/observability/) has some major updates to make it easier to debug your application's issues and share findings with your team.

You can now:
* **Create visualizations** — Build charts from your Worker data directly in a Worker's Observability tab
* **Export data as JSON or CSV** — Download logs and traces for offline analysis or to share with teammates
* **Share events and traces** — Generate direct URLs to specific events, invocations, and traces that open standalone pages with full context
* **Customize table columns** — Improved field picker to add, remove, and reorder columns in the events table
* **Expandable event details** — Expand events inline to view full details without leaving the table
* **Keyboard shortcuts** — Navigate the dashboard with hotkey support

These updates are now live in the Cloudflare dashboard, both in a Worker's Observability tab and in the account-level Observability dashboard for a unified experience. To get started, go to **Workers & Pages** > select your Worker > **Observability**.
---
title: Support for CrowdStrike device scores in User Risk Scoring · Changelog
description: Cloudflare One now supports two new risk scoring behaviors based on
CrowdStrike device posture attributes.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/2026-1-15-crowdstrike-score/
md: https://developers.cloudflare.com/changelog/2026-1-15-crowdstrike-score/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Support for CrowdStrike device scores in User Risk Scoring
Jan 15, 2026
[Risk Score](https://developers.cloudflare.com/cloudflare-one/insights/risk-score/)
Cloudflare One has expanded its \[User Risk Scoring] (/cloudflare-one/insights/risk-score/) capabilities by introducing two new behaviors for organizations using the \[CrowdStrike integration] (/cloudflare-one/integrations/service-providers/crowdstrike/).
Administrators can now automatically escalate the risk score of a user if their device matches specific CrowdStrike Zero Trust Assessment (ZTA) score ranges. This allows for more granular security policies that respond dynamically to the health of the endpoint.
New risk behaviors The following risk scoring behaviors are now available:
* CrowdStrike low device score: Automatically increases a user's risk score when the connected device reports a "Low" score from CrowdStrike.
* CrowdStrike medium device score: Automatically increases a user's risk score when the connected device reports a "Medium" score from CrowdStrike.
These scores are derived from \[CrowdStrike device posture attributes] (/cloudflare-one/integrations/service-providers/crowdstrike/#device-posture-attributes), including OS signals and sensor configurations.
---
title: New Access Analytics in the Cloudflare One Dashboard · Changelog
description: An upgraded analytics experience for Access usage and metrics.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/access-analytics-v2/
md: https://developers.cloudflare.com/changelog/access-analytics-v2/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Access Analytics in the Cloudflare One Dashboard
May 16, 2025
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
A new Access Analytics dashboard is now available to all Cloudflare One customers. Customers can apply and combine multiple filters to dive into specific slices of their Access metrics. These filters include:
* Logins granted and denied
* Access events by type (SSO, Login, Logout)
* Application name (Salesforce, Jira, Slack, etc.)
* Identity provider (Okta, Google, Microsoft, onetimepin, etc.)
* Users (`chris@cloudflare.com`, `sally@cloudflare.com`, `rachel@cloudflare.com`, etc.)
* Countries (US, CA, UK, FR, BR, CN, etc.)
* Source IP address
* App type (self-hosted, Infrastructure, RDP, etc.)

To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and find Analytics in the side navigation bar.
---
title: Data Security Analytics in the Zero Trust dashboard · Changelog
description: An upgraded analytics experience for Gateway usage and metrics.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/cf1-data-security-analytics-v1/
md: https://developers.cloudflare.com/changelog/cf1-data-security-analytics-v1/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Data Security Analytics in the Zero Trust dashboard
Jun 23, 2025
[Data Loss Prevention ](https://developers.cloudflare.com/cloudflare-one/data-loss-prevention/)[CASB ](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Zero Trust now includes **Data security analytics**, providing you with unprecedented visibility into your organization sensitive data.
The new dashboard includes:
* **Sensitive Data Movement Over Time:**
* See patterns and trends in how sensitive data moves across your environment. This helps understand where data is flowing and identify common paths.
* **Sensitive Data at Rest in SaaS & Cloud:**
* View an inventory of sensitive data stored within your corporate SaaS applications (for example, Google Drive, Microsoft 365) and cloud accounts (such as AWS S3).
* **DLP Policy Activity:**
* Identify which of your Data Loss Prevention (DLP) policies are being triggered most often.
* See which specific users are responsible for triggering DLP policies.

To access the new dashboard, log in to [Cloudflare One](https://one.dash.cloudflare.com/) and go to **Insights** on the sidebar.
---
title: Cloudflare One Analytics Dashboards and Exportable Access Report · Changelog
description: An upgraded analytics experience for navigating analytics and new report
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/dashboards-access-report/
md: https://developers.cloudflare.com/changelog/dashboards-access-report/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## Cloudflare One Analytics Dashboards and Exportable Access Report
Jun 05, 2025
[Access ](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Cloudflare One now offers powerful new analytics dashboards to help customers easily discover available insights into their application access and network activity. These dashboards provide a centralized, intuitive view for understanding user behavior, application usage, and security posture.
!\[Cloudflare One Analytics Dashboards]\(\~/assets/images/changelog/cloudflare-one/Analytics Dashboards.png)
Additionally, a new exportable access report is available, allowing customers to quickly view high-level metrics and trends in their application access. A **preview** of the report is shown below, with more to be found in the report:

Both features are accessible in the Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), empowering organizations with better visibility and control.
---
title: New Gateway Analytics in the Cloudflare One Dashboard · Changelog
description: An upgraded analytics experience for Gateway usage and metrics.
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/gateway-analytics-v2/
md: https://developers.cloudflare.com/changelog/gateway-analytics-v2/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Gateway Analytics in the Cloudflare One Dashboard
May 29, 2025
[Gateway ](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
Users can now access significant enhancements to Cloudflare Gateway analytics, providing you with unprecedented visibility into your organization's DNS queries, HTTP requests, and Network sessions. These powerful new dashboards enable you to go beyond raw logs and gain actionable insights into how your users are interacting with the Internet and your protected resources.
You can now visualize and explore:
* Patterns Over Time: Understand trends in traffic volume and blocked requests, helping you identify anomalies and plan for future capacity.
* Top Users & Destinations: Quickly pinpoint the most active users, enabling better policy enforcement and resource allocation.
* Actions Taken: See a clear breakdown of security actions applied by Gateway policies, such as blocks and allows, offering a comprehensive view of your security posture.
* Geographic Regions: Gain insight into the global distribution of your traffic.

To access the new overview, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/) and go to Analytics in the side navigation bar.
---
title: New Application Categories added for HTTP Traffic Management · Changelog
description: Manage outbound traffic with more granular application categories
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/gateway-application-categories-added/
md: https://developers.cloudflare.com/changelog/gateway-application-categories-added/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Application Categories added for HTTP Traffic Management
Oct 28, 2025
[Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/)
To give you precision and flexibility while creating policies to block unwanted traffic, we are introducing new, more granular application categories in the Gateway product.
We have added the following categories to provide more precise organization and allow for finer-grained policy creation, designed around how users interact with different types of applications:
* Business
* Education
* Entertainment & Events
* Food & Drink
* Health & Fitness
* Lifestyle
* Navigation
* Photography & Graphic Design
* Travel
The new categories are live now, but we are providing a transition period for existing applications to be fully remapped to these new categories.
The full remapping will be completed by January 30, 2026.
We encourage you to use this time to:
* Review the new category structure.
* Identify and adjust any existing HTTP policies that reference older categories to ensure a smooth transition.
For more information on creating HTTP policies, refer to [Applications and app types](https://developers.cloudflare.com/cloudflare-one/traffic-policies/application-app-types/).
---
title: HEIC support in Cloudflare Images · Changelog
description: You can use Images to ingest HEIC images
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/heic-support/
md: https://developers.cloudflare.com/changelog/heic-support/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## HEIC support in Cloudflare Images
Jul 08, 2025
[Cloudflare Images](https://developers.cloudflare.com/images/)
You can use Images to ingest HEIC images and serve them in supported output formats like AVIF, WebP, JPEG, and PNG.
When inputting a HEIC image, dimension and sizing limits may still apply. Refer to our documentation to see limits for [uploading to Images](https://developers.cloudflare.com/images/upload-images/) or [transforming a remote image](https://developers.cloudflare.com/images/transform-images/).
---
title: New Applications Added to Zero Trust · Changelog
description: Manage outbound traffic for 42 new applications
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/new-applications-71825/
md: https://developers.cloudflare.com/changelog/new-applications-71825/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Applications Added to Zero Trust
May 18, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
42 new applications have been added for Zero Trust support within the Application Library and Gateway policy enforcement, giving you the ability to investigate or apply inline policies to these applications.
33 of the 42 applications are Artificial Intelligence applications. The others are Human Resources (2 applications), Development (2 applications), Productivity (2 applications), Sales & Marketing, Public Cloud, and Security.
To view all available applications, log in to your Cloudflare [Zero Trust dashboard](https://one.dash.cloudflare.com/), navigate to the **App Library** under **My Team**.
For more information on creating Gateway policies, see our [Gateway policy documentation](https://developers.cloudflare.com/cloudflare-one/traffic-policies/).
---
title: New Cloudflare One Navigation and Product Experience · Changelog
description: New Cloudflare One Navigation and Product Experience
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/new-cloudflare-one-navigation-and-product-experience/
md: https://developers.cloudflare.com/changelog/new-cloudflare-one-navigation-and-product-experience/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## New Cloudflare One Navigation and Product Experience
Nov 17, 2025
[Cloudflare One](https://developers.cloudflare.com/cloudflare-one/)
The Zero Trust dashboard and navigation is receiving significant and exciting updates. The dashboard is being restructured to better support common tasks and workflows, and various pages have been moved and consolidated.
There is a new guided experience on login detailing the changes, and you can use the Zero Trust dashboard search to find product pages by both their new and old names, as well as your created resources. To replay the guided experience, you can find it in Overview > Get Started.

Notable changes
* Product names have been removed from many top-level navigation items to help bring clarity to what they help you accomplish. For example, you can find Gateway policies under ‘Traffic policies' and CASB findings under ‘Cloud & SaaS findings.'
* You can view all analytics, logs, and real-time monitoring tools from ‘Insights.'
* ‘Networks' better maps the ways that your corporate network interacts with Cloudflare. Some pages like Tunnels, are now a tab rather than a full page as part of these changes. You can find them at Networks > Connectors.
* Settings are now located closer to the tools and resources they impact. For example, this means you'll find your WARP configurations at Team & Resources > Devices.

No changes to our API endpoint structure or to any backend services have been made as part of this effort.
---
title: WAF Release - Scheduled changes for 2026-02-09 · Changelog
description: WAF managed ruleset changes scheduled for 2026-02-09
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/changelog/scheduled-waf-release/
md: https://developers.cloudflare.com/changelog/scheduled-waf-release/index.md
---
# Changelog
New updates and improvements at Cloudflare.
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/index.xml)\
[View all RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/)

[← Back to all posts](https://developers.cloudflare.com/changelog/)
## WAF Release - Scheduled changes for 2026-02-09
Feb 03, 2026
[WAF](https://developers.cloudflare.com/waf/)
| Announcement Date | Release Date | Release Behavior | Legacy Rule ID | Rule ID | Description | Comments |
| - | - | - | - | - | - | - |
| 2026-02-03 | 2026-02-09 | Log | N/A | a219dd28a0694faea0f942d4b0089874 | Zimbra - Local File Inclusion - CVE:CVE-2025-68645 | This is a new detection. |
| 2026-02-03 | 2026-02-09 | Log | N/A | b10164cf42ab47b7ab274b9573b09f52 | Vite - WASM Import Path Traversal - CVE:CVE-2025-31125 | This is a new detection. |
---
title: 404 - Page Not Found · Google tag gateway for advertisers docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/google-tag-gateway/404/
md: https://developers.cloudflare.com/google-tag-gateway/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: 404 - Page Not Found · Cloudflare Health Checks docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/health-checks/404/
md: https://developers.cloudflare.com/health-checks/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Concepts · Cloudflare Health Checks docs
description: Review the following topics to learn more about the basic concepts
involved in Cloudflare Health Checks.
lastUpdated: 2024-09-11T14:19:17.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/health-checks/concepts/
md: https://developers.cloudflare.com/health-checks/concepts/index.md
---
Review the following topics to learn more about the basic concepts involved in Cloudflare Health Checks.
* [Health Checks regions](https://developers.cloudflare.com/health-checks/concepts/health-checks-regions/)
---
title: Get started · Cloudflare Health Checks docs
description: This guide will get you started with creating and managing
configured Health Checks.
lastUpdated: 2025-11-17T15:21:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/health-checks/get-started/
md: https://developers.cloudflare.com/health-checks/get-started/index.md
---
Smart Shield
This functionality is now offered as part of Cloudflare's origin server safeguard, Smart Shield. [Learn more](https://developers.cloudflare.com/smart-shield/).
This guide will get you started with creating and managing configured Health Checks.
## Create a Health Check
1. In the Cloudflare dashboard, go to the **Health Checks** page.
[Go to **Health Checks**](https://dash.cloudflare.com/?to=/:account/:zone/traffic/health-checks)
2. Select **Create** and fill out the form, paying special attention to:
* The values for **Interval** and **Check regions**, because decreasing the **Interval** and increasing **Check regions** may increase the load on your origin server.
* **Retries**, which specify the number of retries to attempt in case of a timeout before marking the origin as unhealthy.
* **Response body**, which specifies a substring that must be present in the first 10 KB of the response body for the check to succeed.
3. Select **Save and Deploy**.
## Manage Health Checks
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account and domain.
2. Go to **Traffic** > **Health Checks**.
3. Navigate to your health check and select **Edit**.
4. Edit your Health Check.
5. Select **Save**.
Note
You can also enable, disable, or delete configured Health Checks.
Note
Authenticated origin pull is not supported by Standalone Health Checks.
---
title: Health Checks Analytics · Cloudflare Health Checks docs
description: Once you have set up a standalone Health Check including
notification emails, use Health Check Analytics to debug possible origin
issues.
lastUpdated: 2025-10-09T07:47:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/health-checks/health-checks-analytics/
md: https://developers.cloudflare.com/health-checks/health-checks-analytics/index.md
---
Smart Shield
This functionality is now offered as part of Cloudflare's origin server safeguard, Smart Shield. [Learn more](https://developers.cloudflare.com/smart-shield/).
Once you have set up a standalone Health Check including notification emails, use Health Check Analytics to debug possible origin issues.
To access health check analytics:
1. In the Cloudflare dashboard, go to the **Health Check Analytics** page.
[Go to **Health Check Analytics**](https://dash.cloudflare.com/?to=/:account/:zone/traffic/health-check-analytics)
You can evaluate origin uptime, latency, failure reason, and specific event logs:
* **Health Checks By Uptime**: Shows the percentage of uptime for individual origins over time.
* **Health Checks By Failure Reason**: Shows a breakdown of failures by the specific reason. Refer to [common error code causes and solutions below](#common-error-codes).
* **Health Checks By Latency**: Shows average latency – measured in round trip time — for individual origins over time.
* **Event Log**: Shows individual health check data.
* Select each record for additional details on **Round trip time**, the **Failure Reason**, the **Average Waterfall** (showing chronological data about request stages), **Response status code**, and more.
* Note that **Global** is not a configured region; it represents the aggregated data from all enabled regions.
## Common error codes
### TCP connection failed
#### Cause
Health Checks failed to establish a TCP connection to your origin server.
#### Solution
This typically occurs when there is a network failure between Cloudflare and your origin, and/or a firewall refuses to allow our connection. Ensure your network and firewall configurations are not interfering with traffic.
### HTTP timeout occurred
#### Cause
The origin failed to return an HTTP response within the timeout configured. This happens if you have the timeout set to a low number. For example, one to two seconds.
#### Solution
Cloudflare recommends increasing the HTTP response timeout to allow the origin server to respond.
### Response code mismatch error
#### Cause
Cloudflare receives an HTTP status code that does not match the values defined in the `expected_codes` property of your Health Check configuration.
#### Solution
Response codes must match the `expected_codes`. Confirm the values are correct by comparing the expected response codes and the status code received in the Event Log.
#### Alternate cause
You may also see this issue if you have a Health Check configured to use HTTP connections and your origin server is redirecting to HTTPS. In this case, the response code will often be `301`, `302`, or `303`.
#### Solution
Change your Cloudflare Health Check configuration to use HTTPS or set the value of `follow_redirect` to `true` so that Cloudflare can resolve the correct status code.
### Response body mismatch error
#### Cause
The response body returns from your origin server and does not include the (case-insensitive) value of `expected_body` configured in your Health Check.
Note
We only read the first 10 KB of the response. If you return a larger response, and the `expected_body` is not in the first 10 KB, the Health Check will fail.
#### Solution
Ensure the `expected_body` is in the first 10 KB of the response body.
### TLS untrusted certificate error
#### Cause
The certificate is not trusted by a public Certificate Authority (CA).
#### Solution
If you’re using a self-signed certificate, Cloudflare recommends either using a publicly trusted certificate or setting the `allow_insecure` property on your Health Check to `true`.
### TLS name mismatch error
#### Cause
Our Health Check (client) was not able to match a name on the server certificate to the hostname of the request.
#### Solution
Inspect your Health Check configuration to confirm that the `header` value set in the Cloudflare Health Check is correct.
### TLS protocol error
#### Cause
This error can occur if you are using an older version of TLS or your origin server is not configured for HTTPS.
#### Solution
Ensure that your origin server supports TLS 1.2 or greater and is configured for HTTPS.
### TLS unrecognized name error
#### Cause
The server did not recognize the name provided by the client. When a host header is set, this is set as the ServerName in the initial TLS handshake. If it is not set, Cloudflare will not provide a ServerName, which can cause this error.
#### Solution
Set the host header in your Health Check object.
### No route to host error
#### Cause
The IP address cannot be reached from Cloudflare’s network. Common causes are ISP or hosting provider network issues (e.g. BGP level), or that the IP does not exist.
#### Solution
Ensure IP is accurate, and check if there is an ISP or hosting provider network issue.
### TCP Timeout
#### Cause
Data transmission was not acknowledged and the retransmit of data did not succeed.
#### Solution
Confirm whether the SYN-ACK for the handshake takes place at your origin and contact [Cloudflare support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
### Network Unreachable
#### Cause
Cloudflare cannot connect to the origin web server due to network unavailability. This is usually caused by a network issue or incorrect origin IP.
#### Solution
Check the IP entered for the origin in Cloudflare’s Health Checks configuration or the IP returned via DNS for the origin hostname.
### HTTP Invalid Response
#### Cause
Usually caused by an HTTP 502 error or bad gateway.
#### Solution
Ensure the origin web server responds to requests and that no applications have crashed or are under high load.
### DNS Unknown Host
#### Cause
The origin web server hostname does not exist.
#### Solution
Confirm the origin web server resolves to an IP address.
### Connection Reset by Peer
#### Cause
A network error occurred while the client received data from the origin web server.
#### Solution
Confirm whether the origin web server is experiencing a high amount of traffic or an error.
### Monitor Configuration Error
#### Cause
There was a configuration error in the Health Check and no checks were run against the origin.
#### Solution
Review your Health Check configuration to ensure it matches an expected request to your origin.
### DNS Internal
#### Cause
The origin web server’s hostname resolves to an internal or restricted address. No checks are run against this origin.
#### Solution
Cloudflare does not allow use of an origin web server hostname that resolves to a Cloudflare IP.
### Other Failure
#### Cause
If the failure cannot be classified as any other type of failure mentioned above.
#### Solution
Contact [Cloudflare support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
## Set up alerts
You can configure alerts to notify you of any changes in your health check status.
Health Checks status notification
**Who is it for?**
Customers who want to be warned about changes to server health as determined by [health checks](https://developers.cloudflare.com/health-checks/).
**Other options / filters**
Available filters include:
* You can search for and add health checks from your list of health checks.
* You can choose a trigger to fire the notification when your server becomes **unhealthy**, **healthy**, or **either healthy or unhealthy**.
**Included with**
Professional plans or higher.
**What should you do if you receive one?**
Review your [health check analytics](https://developers.cloudflare.com/health-checks/health-checks-analytics/#common-error-codes).
Refer to [Cloudflare Notifications](https://developers.cloudflare.com/notifications/get-started/) for more information on how to set up an alert.
---
title: How to · Cloudflare Health Checks docs
description: "See the following pages for more information about standalone Health Checks:"
lastUpdated: 2024-09-11T14:19:17.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/health-checks/how-to/
md: https://developers.cloudflare.com/health-checks/how-to/index.md
---
See the following pages for more information about standalone Health Checks:
* [Zone Lockdown](https://developers.cloudflare.com/health-checks/how-to/zone-lockdown/)
* [Health Checks notifications](https://developers.cloudflare.com/health-checks/how-to/health-checks-notifications/)
---
title: 404 - Page Not Found · Cloudflare Hyperdrive docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/hyperdrive/404/
md: https://developers.cloudflare.com/hyperdrive/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Concepts · Cloudflare Hyperdrive docs
description: Learn about the core concepts and architecture behind Hyperdrive.
lastUpdated: 2025-11-12T15:17:36.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/hyperdrive/concepts/
md: https://developers.cloudflare.com/hyperdrive/concepts/index.md
---
Learn about the core concepts and architecture behind Hyperdrive.
---
title: Configuration · Cloudflare Hyperdrive docs
lastUpdated: 2024-09-06T08:27:36.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/hyperdrive/configuration/
md: https://developers.cloudflare.com/hyperdrive/configuration/index.md
---
* [Connect to a private database using Tunnel](https://developers.cloudflare.com/hyperdrive/configuration/connect-to-private-database/)
* [Local development](https://developers.cloudflare.com/hyperdrive/configuration/local-development/)
* [SSL/TLS certificates](https://developers.cloudflare.com/hyperdrive/configuration/tls-ssl-certificates-for-hyperdrive/)
* [Firewall and networking configuration](https://developers.cloudflare.com/hyperdrive/configuration/firewall-and-networking-configuration/)
* [Tune connection pooling](https://developers.cloudflare.com/hyperdrive/configuration/tune-connection-pool/)
* [Rotating database credentials](https://developers.cloudflare.com/hyperdrive/configuration/rotate-credentials/)
---
title: Demos and architectures · Cloudflare Hyperdrive docs
description: Learn how you can use Hyperdrive within your existing application
and architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/hyperdrive/demos/
md: https://developers.cloudflare.com/hyperdrive/demos/index.md
---
Learn how you can use Hyperdrive within your existing application and architecture.
## Demos
Explore the following demo applications for Hyperdrive.
* [Hyperdrive demo:](https://github.com/cloudflare/hyperdrive-demo) A Remix app that connects to a database behind Cloudflare's Hyperdrive, making regional databases feel like they're globally distributed.
## Reference architectures
Explore the following reference architectures that use Hyperdrive:
[Serverless global APIs](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[An example architecture of a serverless API on Cloudflare and aims to illustrate how different compute and data products could interact with each other.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
---
title: Examples · Cloudflare Hyperdrive docs
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/hyperdrive/examples/
md: https://developers.cloudflare.com/hyperdrive/examples/index.md
---
* [Connect to PostgreSQL](https://developers.cloudflare.com/hyperdrive/examples/connect-to-postgres/)
* [Connect to MySQL](https://developers.cloudflare.com/hyperdrive/examples/connect-to-mysql/)
---
title: Getting started · Cloudflare Hyperdrive docs
description: Hyperdrive accelerates access to your existing databases from
Cloudflare Workers, making even single-region databases feel globally
distributed.
lastUpdated: 2026-02-06T18:26:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/hyperdrive/get-started/
md: https://developers.cloudflare.com/hyperdrive/get-started/index.md
---
Hyperdrive accelerates access to your existing databases from Cloudflare Workers, making even single-region databases feel globally distributed.
By maintaining a connection pool to your database within Cloudflare's network, Hyperdrive reduces seven round-trips to your database before you can even send a query: the TCP handshake (1x), TLS negotiation (3x), and database authentication (3x).
Hyperdrive understands the difference between read and write queries to your database, and caches the most common read queries, improving performance and reducing load on your origin database.
This guide will instruct you through:
* Creating your first Hyperdrive configuration.
* Creating a [Cloudflare Worker](https://developers.cloudflare.com/workers/) and binding it to your Hyperdrive configuration.
* Establishing a database connection from your Worker to a public database.
Note
Hyperdrive currently works with PostgreSQL, MySQL and many compatible databases. This includes CockroachDB and Materialize (which are PostgreSQL-compatible), and PlanetScale.
Learn more about the [databases that Hyperdrive supports](https://developers.cloudflare.com/hyperdrive/reference/supported-databases-and-features).
## Prerequisites
Before you begin, ensure you have completed the following:
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages) if you have not already.
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm). Use a Node version manager like [nvm](https://github.com/nvm-sh/nvm) or [Volta](https://volta.sh/) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/) requires a Node version of `16.17.0` or later.
3. Have a publicly accessible PostgreSQL or MySQL (or compatible) database. *If your database is in a private network (like a VPC)*, refer to [Connect to a private database](https://developers.cloudflare.com/hyperdrive/configuration/connect-to-private-database/) for instructions on using Cloudflare Tunnel with Hyperdrive.
## 1. Log in
Before creating your Hyperdrive binding, log in with your Cloudflare account by running:
```sh
npx wrangler login
```
You will be directed to a web page asking you to log in to the Cloudflare dashboard. After you have logged in, you will be asked if Wrangler can make changes to your Cloudflare account. Scroll down and select **Allow** to continue.
## 2. Create a Worker
New to Workers?
Refer to [How Workers works](https://developers.cloudflare.com/workers/reference/how-workers-works/) to learn about the Workers serverless execution model works. Go to the [Workers Get started guide](https://developers.cloudflare.com/workers/get-started/guide/) to set up your first Worker.
Create a new project named `hyperdrive-tutorial` by running:
* npm
```sh
npm create cloudflare@latest -- hyperdrive-tutorial
```
* yarn
```sh
yarn create cloudflare hyperdrive-tutorial
```
* pnpm
```sh
pnpm create cloudflare@latest hyperdrive-tutorial
```
For setup, select the following options:
* For *What would you like to start with?*, choose `Hello World example`.
* For *Which template would you like to use?*, choose `Worker only`.
* For *Which language do you want to use?*, choose `TypeScript`.
* For *Do you want to use git for version control?*, choose `Yes`.
* For *Do you want to deploy your application?*, choose `No` (we will be making some changes before deploying).
This will create a new `hyperdrive-tutorial` directory. Your new `hyperdrive-tutorial` directory will include:
* A `"Hello World"` [Worker](https://developers.cloudflare.com/workers/get-started/guide/#3-write-code) at `src/index.ts`.
* A [`wrangler.jsonc`](https://developers.cloudflare.com/workers/wrangler/configuration/) configuration file. `wrangler.jsonc` is how your `hyperdrive-tutorial` Worker will connect to Hyperdrive.
### Enable Node.js compatibility
[Node.js compatibility](https://developers.cloudflare.com/workers/runtime-apis/nodejs/) is required for database drivers, and needs to be configured for your Workers project.
To enable both built-in runtime APIs and polyfills for your Worker or Pages project, add the [`nodejs_compat`](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#nodejs-compatibility-flag) [compatibility flag](https://developers.cloudflare.com/workers/configuration/compatibility-flags/#nodejs-compatibility-flag) to your [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/), and set your compatibility date to September 23rd, 2024 or later. This will enable [Node.js compatibility](https://developers.cloudflare.com/workers/runtime-apis/nodejs/) for your Workers project.
* wrangler.jsonc
```jsonc
{
"compatibility_flags": [
"nodejs_compat"
],
"compatibility_date": "2026-02-07"
}
```
* wrangler.toml
```toml
compatibility_flags = [ "nodejs_compat" ]
compatibility_date = "2026-02-07"
```
## 3. Connect Hyperdrive to a database
Hyperdrive works by connecting to your database, pooling database connections globally, and speeding up your database access through Cloudflare's network.
It will provide a secure connection string that is only accessible from your Worker which you can use to connect to your database through Hyperdrive. This means that you can use the Hyperdrive connection string with your existing drivers or ORM libraries without needing significant changes to your code.
To create your first Hyperdrive database configuration, change into the directory you just created for your Workers project:
```sh
cd hyperdrive-tutorial
```
To create your first Hyperdrive, you will need:
* The IP address (or hostname) and port of your database.
* The database username (for example, `hyperdrive-demo`).
* The password associated with that username.
* The name of the database you want Hyperdrive to connect to. For example, `postgres` or `mysql`.
Hyperdrive accepts the combination of these parameters in the common connection string format used by database drivers:
* PostgreSQL
```txt
postgres://USERNAME:PASSWORD@HOSTNAME_OR_IP_ADDRESS:PORT/database_name
```
Most database providers will provide a connection string you can copy-and-paste directly into Hyperdrive.
To create a Hyperdrive connection, run the `wrangler` command, replacing the placeholder values passed to the `--connection-string` flag with the values of your existing database:
```sh
npx wrangler hyperdrive create --connection-string="postgres://user:password@HOSTNAME_OR_IP_ADDRESS:PORT/database_name"
```
* MySQL
```txt
mysql://USERNAME:PASSWORD@HOSTNAME_OR_IP_ADDRESS:PORT/database_name
```
Most database providers will provide a connection string you can copy-and-paste directly into Hyperdrive.
To create a Hyperdrive connection, run the `wrangler` command, replacing the placeholder values passed to the `--connection-string` flag with the values of your existing database:
```sh
npx wrangler hyperdrive create --connection-string="mysql://user:password@HOSTNAME_OR_IP_ADDRESS:PORT/database_name"
```
Manage caching
By default, Hyperdrive will cache query results. If you wish to disable caching, pass the flag `--caching-disabled`.
Alternatively, you can use the `--max-age` flag to specify the maximum duration (in seconds) for which items should persist in the cache, before they are evicted. Default value is 60 seconds.
Refer to [Hyperdrive Wrangler commands](https://developers.cloudflare.com/hyperdrive/reference/wrangler-commands/) for more information.
If successful, the command will output your new Hyperdrive configuration:
```json
{
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": ""
}
]
}
```
Copy the `id` field: you will use this in the next step to make Hyperdrive accessible from your Worker script.
Note
Hyperdrive will attempt to connect to your database with the provided credentials to verify they are correct before creating a configuration. If you encounter an error when attempting to connect, refer to Hyperdrive's [troubleshooting documentation](https://developers.cloudflare.com/hyperdrive/observability/troubleshooting/) to debug possible causes.
## 4. Bind your Worker to Hyperdrive
You must create a binding in your [Wrangler configuration file](https://developers.cloudflare.com/workers/wrangler/configuration/) for your Worker to connect to your Hyperdrive configuration. [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) allow your Workers to access resources, like Hyperdrive, on the Cloudflare developer platform.
To bind your Hyperdrive configuration to your Worker, add the following to the end of your Wrangler file:
* wrangler.jsonc
```jsonc
{
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "" // the ID associated with the Hyperdrive you just created
}
]
}
```
* wrangler.toml
```toml
[[hyperdrive]]
binding = "HYPERDRIVE"
id = ""
```
Specifically:
* The value (string) you set for the `binding` (binding name) will be used to reference this database in your Worker. In this tutorial, name your binding `HYPERDRIVE`.
* The binding must be [a valid JavaScript variable name](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Guide/Grammar_and_types#variables). For example, `binding = "hyperdrive"` or `binding = "productionDB"` would both be valid names for the binding.
* Your binding is available in your Worker at `env.`.
If you wish to use a local database during development, you can add a `localConnectionString` to your Hyperdrive configuration with the connection string of your database:
* wrangler.jsonc
```jsonc
{
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "", // the ID associated with the Hyperdrive you just created
"localConnectionString": ""
}
]
}
```
* wrangler.toml
```toml
[[hyperdrive]]
binding = "HYPERDRIVE"
id = ""
localConnectionString = ""
```
Note
Learn more about setting up [Hyperdrive for local development](https://developers.cloudflare.com/hyperdrive/configuration/local-development/).
## 5. Run a query against your database
Once you have created a Hyperdrive configuration and bound it to your Worker, you can run a query against your database.
### Install a database driver
* PostgreSQL
To connect to your database, you will need a database driver which allows you to authenticate and query your database. For this tutorial, you will use [node-postgres (pg)](https://node-postgres.com/), one of the most widely used PostgreSQL drivers.
To install `pg`, ensure you are in the `hyperdrive-tutorial` directory. Open your terminal and run the following command:
* npm
```sh
# This should install v8.13.0 or later
npm i pg
```
* yarn
```sh
# This should install v8.13.0 or later
yarn add pg
```
* pnpm
```sh
# This should install v8.13.0 or later
pnpm add pg
```
If you are using TypeScript, you should also install the type definitions for `pg`:
* npm
```sh
# This should install v8.13.0 or later
npm i -D @types/pg
```
* yarn
```sh
# This should install v8.13.0 or later
yarn add -D @types/pg
```
* pnpm
```sh
# This should install v8.13.0 or later
pnpm add -D @types/pg
```
With the driver installed, you can now create a Worker script that queries your database.
* MySQL
To connect to your database, you will need a database driver which allows you to authenticate and query your database. For this tutorial, you will use [mysql2](https://github.com/sidorares/node-mysql2), one of the most widely used MySQL drivers.
To install `mysql2`, ensure you are in the `hyperdrive-tutorial` directory. Open your terminal and run the following command:
* npm
```sh
# This should install v3.13.0 or later
npm i mysql2
```
* yarn
```sh
# This should install v3.13.0 or later
yarn add mysql2
```
* pnpm
```sh
# This should install v3.13.0 or later
pnpm add mysql2
```
With the driver installed, you can now create a Worker script that queries your database.
* npm
```sh
# This should install v8.13.0 or later
npm i pg
```
* yarn
```sh
# This should install v8.13.0 or later
yarn add pg
```
* pnpm
```sh
# This should install v8.13.0 or later
pnpm add pg
```
* npm
```sh
# This should install v8.13.0 or later
npm i -D @types/pg
```
* yarn
```sh
# This should install v8.13.0 or later
yarn add -D @types/pg
```
* pnpm
```sh
# This should install v8.13.0 or later
pnpm add -D @types/pg
```
* npm
```sh
# This should install v3.13.0 or later
npm i mysql2
```
* yarn
```sh
# This should install v3.13.0 or later
yarn add mysql2
```
* pnpm
```sh
# This should install v3.13.0 or later
pnpm add mysql2
```
### Write a Worker
* PostgreSQL
After you have set up your database, you will run a SQL query from within your Worker.
Go to your `hyperdrive-tutorial` Worker and open the `index.ts` file.
The `index.ts` file is where you configure your Worker's interactions with Hyperdrive.
Populate your `index.ts` file with the following code:
```typescript
// pg 8.13.0 or later is recommended
import { Client } from "pg";
export interface Env {
// If you set another name in the Wrangler config file as the value for 'binding',
// replace "HYPERDRIVE" with the variable name you defined.
HYPERDRIVE: Hyperdrive;
}
export default {
async fetch(request, env, ctx): Promise {
// Create a new client on each request. Hyperdrive maintains the underlying
// database connection pool, so creating a new client is fast.
const sql = new Client({
connectionString: env.HYPERDRIVE.connectionString,
});
try {
// Connect to the database
await sql.connect();
// Sample query
const results = await sql.query(`SELECT * FROM pg_tables`);
// Return result rows as JSON
return Response.json(results.rows);
} catch (e) {
console.error(e);
return Response.json(
{ error: e instanceof Error ? e.message : e },
{ status: 500 },
);
}
},
} satisfies ExportedHandler;
```
Upon receiving a request, the code above does the following:
1. Creates a new database client configured to connect to your database via Hyperdrive, using the Hyperdrive connection string.
2. Initiates a query via `await sql.query()` that outputs all tables (user and system created) in the database (as an example query).
3. Returns the response as JSON to the client. Hyperdrive automatically cleans up the client connection when the request ends, and keeps the underlying database connection open in its pool for reuse.
* MySQL
After you have set up your database, you will run a SQL query from within your Worker.
Go to your `hyperdrive-tutorial` Worker and open the `index.ts` file.
The `index.ts` file is where you configure your Worker's interactions with Hyperdrive.
Populate your `index.ts` file with the following code:
```typescript
// mysql2 v3.13.0 or later is required
import { createConnection } from 'mysql2/promise';
export interface Env {
// If you set another name in the Wrangler config file as the value for 'binding',
// replace "HYPERDRIVE" with the variable name you defined.
HYPERDRIVE: Hyperdrive;
}
export default {
async fetch(request, env, ctx): Promise {
// Create a new connection on each request. Hyperdrive maintains the underlying
// database connection pool, so creating a new connection is fast.
const connection = await createConnection({
host: env.HYPERDRIVE.host,
user: env.HYPERDRIVE.user,
password: env.HYPERDRIVE.password,
database: env.HYPERDRIVE.database,
port: env.HYPERDRIVE.port,
// The following line is needed for mysql2 compatibility with Workers
// mysql2 uses eval() to optimize result parsing for rows with > 100 columns
// Configure mysql2 to use static parsing instead of eval() parsing with disableEval
disableEval: true
});
try{
// Sample query
const [results, fields] = await connection.query(
'SHOW tables;'
);
// Return result rows as JSON
return new Response(JSON.stringify({ results, fields }), {
headers: {
'Content-Type': 'application/json',
'Access-Control-Allow-Origin': '*',
},
});
}
catch(e){
console.error(e);
return Response.json(
{ error: e instanceof Error ? e.message : e },
{ status: 500 },
);
}
},
} satisfies ExportedHandler;
```
Upon receiving a request, the code above does the following:
1. Creates a new database client configured to connect to your database via Hyperdrive, using the Hyperdrive connection string.
2. Initiates a query via `await connection.query` that outputs all tables (user and system created) in the database (as an example query).
3. Returns the response as JSON to the client. Hyperdrive automatically cleans up the client connection when the request ends, and keeps the underlying database connection open in its pool for reuse.
### Run in development mode (optional)
You can test your Worker locally before deploying by running `wrangler dev`. This runs your Worker code on your machine while connecting to your database.
The `localConnectionString` field works with both local and remote databases and allows you to connect directly to your database from your Worker project running locally. You must specify the SSL/TLS mode if required (`sslmode=require` for Postgres, `sslMode=REQUIRED` for MySQL).
To connect to a database during local development, configure `localConnectionString` in your `wrangler.jsonc`:
```jsonc
{
"hyperdrive": [
{
"binding": "HYPERDRIVE",
"id": "your-hyperdrive-id",
"localConnectionString": "postgres://user:password@your-database-host:5432/database",
},
],
}
```
Or set an environment variable:
```sh
export CLOUDFLARE_HYPERDRIVE_LOCAL_CONNECTION_STRING_HYPERDRIVE="postgres://user:password@your-database-host:5432/database"
```
Then start local development:
```sh
npx wrangler dev
```
Note
When using `wrangler dev` with `localConnectionString` or `CLOUDFLARE_HYPERDRIVE_LOCAL_CONNECTION_STRING_HYPERDRIVE`, Hyperdrive caching does not take effect locally.
Alternatively, you can run `wrangler dev --remote` to test against your deployed Hyperdrive configuration with caching enabled, but this runs your entire Worker in Cloudflare's network instead of locally.
Learn more about [local development with Hyperdrive](https://developers.cloudflare.com/hyperdrive/configuration/local-development/).
## 6. Deploy your Worker
You can now deploy your Worker to make your project accessible on the Internet. To deploy your Worker, run:
```sh
npx wrangler deploy
# Outputs: https://hyperdrive-tutorial..workers.dev
```
You can now visit the URL for your newly created project to query your live database.
For example, if the URL of your new Worker is `hyperdrive-tutorial..workers.dev`, accessing `https://hyperdrive-tutorial..workers.dev/` will send a request to your Worker that queries your database directly.
By finishing this tutorial, you have created a Hyperdrive configuration, a Worker to access that database and deployed your project globally.
Reduce latency with Placement
If your Worker makes **multiple sequential queries** per request, use [Placement](https://developers.cloudflare.com/workers/configuration/placement/) to run your Worker close to your database. Each query adds round-trip latency: 20-30ms from a distant region, or 1-3ms when placed nearby. Multiple queries compound this difference.
If your Worker makes only one query per request, placement does not improve end-to-end latency. The total round-trip time is the same whether it happens near the user or near the database.
```jsonc
{
"placement": {
"region": "aws:us-east-1", // Match your database region, for example "gcp:us-east4" or "azure:eastus"
},
}
```
## Next steps
* Learn more about [how Hyperdrive works](https://developers.cloudflare.com/hyperdrive/concepts/how-hyperdrive-works/).
* How to [configure query caching](https://developers.cloudflare.com/hyperdrive/concepts/query-caching/).
* [Troubleshooting common issues](https://developers.cloudflare.com/hyperdrive/observability/troubleshooting/) when connecting a database to Hyperdrive.
If you have any feature requests or notice any bugs, share your feedback directly with the Cloudflare team by joining the [Cloudflare Developers community on Discord](https://discord.cloudflare.com).
---
title: Hyperdrive REST API · Cloudflare Hyperdrive docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/hyperdrive/hyperdrive-rest-api/
md: https://developers.cloudflare.com/hyperdrive/hyperdrive-rest-api/index.md
---
---
title: Observability · Cloudflare Hyperdrive docs
lastUpdated: 2024-09-06T08:27:36.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/hyperdrive/observability/
md: https://developers.cloudflare.com/hyperdrive/observability/index.md
---
* [Troubleshoot and debug](https://developers.cloudflare.com/hyperdrive/observability/troubleshooting/)
* [Metrics and analytics](https://developers.cloudflare.com/hyperdrive/observability/metrics/)
---
title: Platform · Cloudflare Hyperdrive docs
lastUpdated: 2024-09-06T08:27:36.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/hyperdrive/platform/
md: https://developers.cloudflare.com/hyperdrive/platform/index.md
---
* [Pricing](https://developers.cloudflare.com/hyperdrive/platform/pricing/)
* [Limits](https://developers.cloudflare.com/hyperdrive/platform/limits/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
* [Release notes](https://developers.cloudflare.com/hyperdrive/platform/release-notes/)
---
title: Reference · Cloudflare Hyperdrive docs
lastUpdated: 2024-09-06T08:27:36.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/hyperdrive/reference/
md: https://developers.cloudflare.com/hyperdrive/reference/index.md
---
* [Supported databases and features](https://developers.cloudflare.com/hyperdrive/reference/supported-databases-and-features/)
* [FAQ](https://developers.cloudflare.com/hyperdrive/reference/faq/)
* [Wrangler commands](https://developers.cloudflare.com/hyperdrive/reference/wrangler-commands/)
---
title: Tutorials · Cloudflare Hyperdrive docs
description: View tutorials to help you get started with Hyperdrive.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/hyperdrive/tutorials/
md: https://developers.cloudflare.com/hyperdrive/tutorials/index.md
---
View tutorials to help you get started with Hyperdrive.
| Name | Last Updated | Difficulty |
| - | - | - |
| [Connect to a PostgreSQL database with Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/postgres/) | 7 months ago | Beginner |
| [Connect to a MySQL database with Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/mysql/) | 10 months ago | Beginner |
| [Create a serverless, globally distributed time-series API with Timescale](https://developers.cloudflare.com/hyperdrive/tutorials/serverless-timeseries-api-with-timescale/) | over 2 years ago | Beginner |
---
title: 404 - Page Not Found · Cloudflare Images docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/404/
md: https://developers.cloudflare.com/images/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Demos and architectures · Cloudflare Images docs
description: Learn how you can use Images within your existing architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/demos/
md: https://developers.cloudflare.com/images/demos/index.md
---
Learn how you can use Images within your existing architecture.
## Demos
Explore the following demo applications for Images.
* [Wildebeest:](https://github.com/cloudflare/wildebeest) Wildebeest is an ActivityPub and Mastodon-compatible server whose goal is to allow anyone to operate their Fediverse server and identity on their domain without needing to keep infrastructure, with minimal setup and maintenance, and running in minutes.
## Reference architectures
Explore the following reference architectures that use Images:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Optimizing image delivery with Cloudflare image resizing and R2](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/optimizing-image-delivery-with-cloudflare-image-resizing-and-r2/)
[Learn how to get a scalable, high-performance solution to optimizing image delivery.](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/optimizing-image-delivery-with-cloudflare-image-resizing-and-r2/)
---
title: Examples · Cloudflare Images docs
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/examples/
md: https://developers.cloudflare.com/images/examples/index.md
---
[Transcode images](https://developers.cloudflare.com/images/examples/transcode-from-workers-ai/)
[Transcode an image from Workers AI before uploading to R2](https://developers.cloudflare.com/images/examples/transcode-from-workers-ai/)
[Watermarks](https://developers.cloudflare.com/images/examples/watermark-from-kv/)
[Draw a watermark from KV on an image from R2](https://developers.cloudflare.com/images/examples/watermark-from-kv/)
---
title: Getting started · Cloudflare Images docs
description: In this guide, you will get started with Cloudflare Images and make
your first API request.
lastUpdated: 2025-11-17T14:08:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/get-started/
md: https://developers.cloudflare.com/images/get-started/index.md
---
In this guide, you will get started with Cloudflare Images and make your first API request.
## Prerequisites
Before you make your first API request, ensure that you have a Cloudflare Account ID and an API token.
Refer to [Find zone and account IDs](https://developers.cloudflare.com/fundamentals/account/find-account-and-zone-ids/) for help locating your Account ID and [Create an API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) to learn how to create an access your API token.
## Make your first API request
```bash
curl --request POST \
--url https://api.cloudflare.com/client/v4/accounts//images/v1 \
--header 'Authorization: Bearer ' \
--header 'Content-Type: multipart/form-data' \
--form file=@./
```
## Enable transformations on your zone
You can dynamically optimize images that are stored outside of Cloudflare Images and deliver them using [transformation URLs](https://developers.cloudflare.com/images/transform-images/transform-via-url/).
Cloudflare will automatically cache every transformed image on our global network so that you store only the original image at your origin.
To enable transformations on your zone:
1. In the Cloudflare dashboard, go to the **Transformations** page.
[Go to **Transformations**](https://dash.cloudflare.com/?to=/:account/images/transformations)
2. Go to the specific zone where you want to enable transformations.
3. Select **Enable for zone**. This will allow you to optimize and deliver remote images.
Note
With **Resize images from any origin** unchecked, only the initial URL passed will be checked. Any redirect returned will be followed, including if it leaves the zone, and the resulting image will be transformed.
Note
If you are using transformations in a Worker, you need to include the appropriate logic in your Worker code to prevent resizing images from any origin. Unchecking this option in the dash does not apply to transformation requests coming from Cloudflare Workers.
---
title: Images API Reference · Cloudflare Images docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/images-api/
md: https://developers.cloudflare.com/images/images-api/index.md
---
---
title: Manage uploaded images · Cloudflare Images docs
lastUpdated: 2024-08-30T16:09:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/images/manage-images/
md: https://developers.cloudflare.com/images/manage-images/index.md
---
* [Apply blur](https://developers.cloudflare.com/images/manage-images/blur-variants/)
* [Configure webhooks](https://developers.cloudflare.com/images/manage-images/configure-webhooks/)
* [Create variants](https://developers.cloudflare.com/images/manage-images/create-variants/)
* [Enable flexible variants](https://developers.cloudflare.com/images/manage-images/enable-flexible-variants/)
* [Delete variants](https://developers.cloudflare.com/images/manage-images/delete-variants/)
* [Edit images](https://developers.cloudflare.com/images/manage-images/edit-images/)
* [Serve images](https://developers.cloudflare.com/images/manage-images/serve-images/)
* [Export images](https://developers.cloudflare.com/images/manage-images/export-images/)
* [Delete images](https://developers.cloudflare.com/images/manage-images/delete-images/)
* [Browser TTL](https://developers.cloudflare.com/images/manage-images/browser-ttl/)
---
title: Platform · Cloudflare Images docs
lastUpdated: 2024-11-12T19:01:32.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/images/platform/
md: https://developers.cloudflare.com/images/platform/index.md
---
* [Changelog](https://developers.cloudflare.com/images/platform/changelog/)
---
title: Cloudflare Polish · Cloudflare Images docs
description: Cloudflare Polish is a one-click image optimization product that
automatically optimizes images in your site. Polish strips metadata from
images and reduces image size through lossy or lossless compression to
accelerate the speed of image downloads.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/polish/
md: https://developers.cloudflare.com/images/polish/index.md
---
Cloudflare Polish is a one-click image optimization product that automatically optimizes images in your site. Polish strips metadata from images and reduces image size through lossy or lossless compression to accelerate the speed of image downloads.
When an image is fetched from your origin, our systems automatically optimize it in Cloudflare's cache. Subsequent requests for the same image will get the smaller, faster, optimized version of the image, improving the speed of your website.

## Comparison
* **Polish** automatically optimizes all images served from your origin server. It keeps the same image URLs, and does not require changing markup of your pages.
* **Cloudflare Images** API allows you to create new images with resizing, cropping, watermarks, and other processing applied. These images get their own new URLs, and you need to embed them on your pages to take advantage of this service. Images created this way are already optimized, and there is no need to apply Polish to them.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | Yes | Yes | Yes |
---
title: Pricing · Cloudflare Images docs
description: By default, all users are on the Images Free plan. The Free plan
includes access to the transformations feature, which lets you optimize images
stored outside of Images, like in R2.
lastUpdated: 2026-02-05T14:19:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/pricing/
md: https://developers.cloudflare.com/images/pricing/index.md
---
By default, all users are on the Images Free plan. The Free plan includes access to the transformations feature, which lets you optimize images stored outside of Images, like in R2.
The Paid plan allows transformations, as well as access to storage in Images.
Pricing is dependent on which features you use. The table below shows which metrics are used for each use case.
| Use case | Metrics | Availability |
| - | - | - |
| Optimize images stored outside of Images | Images Transformed | Free and Paid plans |
| Optimized images that are stored in Cloudflare Images | Images Stored, Images Delivered | Only Paid plans |
## Images Free
On the Free plan, you can request up to 5,000 unique transformations each month for free.
Once you exceed 5,000 unique transformations:
* Existing transformations in cache will continue to be served as expected.
* New transformations will return a `9422` error. If your source image is from the same domain where the transformation is served, then you can use the [`onerror` parameter](https://developers.cloudflare.com/images/transform-images/transform-via-url/#onerror) to redirect to the original image.
* You will not be charged for exceeding the limits in the Free plan.
To request more than 5,000 unique transformations each month, you can purchase an Images Paid plan.
## Images Paid
When you purchase an Images Paid plan, you can choose your own storage or add storage in Images.
| Metric | Pricing |
| - | - |
| Images Transformed | First 5,000 unique transformations included + $0.50 / 1,000 unique transformations / month |
| Images Stored | $5 / 100,000 images stored / month |
| Images Delivered | $1 / 100,000 images delivered / month |
If you optimize an image stored outside of Images, then you will be billed only for Images Transformed.
Alternatively, Images Stored and Images Delivered apply only to images that are stored in your Images bucket. When you optimize an image that is stored in Images, then this counts toward Images Delivered — not Images Transformed.
## Metrics
### Images Transformed
A unique transformation is a request to transform an original image based on a set of [supported parameters](https://developers.cloudflare.com/images/transform-images/transform-via-url/#options). This metric is used only when optimizing images that are stored outside of Images.
For example, if you transform `thumbnail.jpg` as 100x100, then this counts as one unique transformation. If you transform the same `thumbnail.jpg` as 200x200, then this counts as a separate unique transformation.
You are billed on the number of unique transformations that are requested within each calendar month. Repeat requests for the same transformation within the same month are counted only once for that month.
The `format` parameter counts as only one billable transformation, even if multiple copies of an image are served. In other words, if `width=100,format=auto/thumbnail.jpg` is served to some users as AVIF and to others as WebP, then this counts as one unique transformation instead of two.
#### Example #1
If you serve 2,000 remote images in five different sizes each month, then this results in 10,000 unique transformations. Your estimated cost for the month would be:
| | Usage | Included | Billable quantity | Price |
| - | - | - | - | - |
| Transformations | 10,000 unique transformations [1](#user-content-fn-5) | 5,000 | 5,000 | $2.50 [2](#user-content-fn-6) |
#### Example #2
If you use [R2](https://developers.cloudflare.com/r2/) for storage then your estimated monthly costs will be the sum of your monthly Images costs and monthly [R2 costs](https://developers.cloudflare.com/r2/pricing/#storage-usage).
For example, if you upload 5,000 images to R2 with an average size of 5 MB, and serve 2,000 of those images in five different sizes, then your estimated cost for the month would be:
| | Usage | Included | Billable quantity | Price |
| - | - | - | - | - |
| Storage | 25 GB [3](#user-content-fn-1) | 10 GB | 15 GB | $0.22 [4](#user-content-fn-7) |
| Class A operations | 5,000 writes [5](#user-content-fn-2) | 1 million | 0 | $0.00 [6](#user-content-fn-8) |
| Class B operations | 10,000 reads [7](#user-content-fn-3) | 10 million | 0 | $0.00 [8](#user-content-fn-9) |
| Transformations | 10,000 unique transformations [9](#user-content-fn-4) | 5,000 | 5,000 | $2.50 [10](#user-content-fn-10) |
| **Total** | | | | **$2.72** |
### Images Stored
Storage in Images is available only with an Images Paid plan. You can purchase storage in increments of $5 for every 100,000 images stored per month.
You can create predefined variants to specify how an image should be resized, such as `thumbnail` as 100x100 and `hero` as 1600x500.
Only uploaded images count toward Images Stored; defining variants will not impact your storage limit.
### Images Delivered
For images that are stored in Images, you will incur $1 for every 100,000 images delivered per month. This metric does not include transformed images that are stored in remote sources.
Every image requested by the browser counts as one billable request.
#### Example
A retail website has a product page that uses Images to serve 10 images. If the page was visited 10,000 times this month, then this results in 100,000 images delivered — or $1.00 in billable usage.
## Footnotes
1. 2,000 original images × 5 sizes [↩](#user-content-fnref-5)
2. (5,000 transformations / 1,000) × $0.50 [↩](#user-content-fnref-6)
3. 5,000 objects × 5 MB per object [↩](#user-content-fnref-1)
4. 15 GB × $0.015 / GB-month [↩](#user-content-fnref-7)
5. 5,000 objects × 1 write per object [↩](#user-content-fnref-2)
6. 0 × $4.50 / million requests [↩](#user-content-fnref-8)
7. 2,000 objects × 5 reads per object [↩](#user-content-fnref-3)
8. 0 × $0.36 / million requests [↩](#user-content-fnref-9)
9. 2,000 original images × 5 sizes [↩](#user-content-fnref-4)
10. (5,000 transformations / 1,000) × $0.50 [↩](#user-content-fnref-10)
---
title: Reference · Cloudflare Images docs
lastUpdated: 2024-08-30T13:02:26.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/images/reference/
md: https://developers.cloudflare.com/images/reference/index.md
---
* [Troubleshooting](https://developers.cloudflare.com/images/reference/troubleshooting/)
* [Security](https://developers.cloudflare.com/images/reference/security/)
---
title: Transform images · Cloudflare Images docs
description: Transformations let you optimize and manipulate images stored
outside of the Cloudflare Images product. Transformed images are served from
one of your zones on Cloudflare.
lastUpdated: 2026-01-29T14:40:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/transform-images/
md: https://developers.cloudflare.com/images/transform-images/index.md
---
Transformations let you optimize and manipulate images stored outside of the Cloudflare Images product. Transformed images are served from one of your zones on Cloudflare.
To transform an image, you must [enable transformations for your zone](https://developers.cloudflare.com/images/get-started/#enable-transformations-on-your-zone).
You can transform an image by using a [specially-formatted URL](https://developers.cloudflare.com/images/transform-images/transform-via-url/) or [through Workers](https://developers.cloudflare.com/images/transform-images/transform-via-workers/).
Learn about [pricing and limits for image transformation](https://developers.cloudflare.com/images/pricing/).
## Supported formats and limitations
### Supported input formats
* JPEG
* PNG
* GIF (including animations)
* WebP (including animations)
* SVG
* HEIC
Note
Cloudflare can ingest HEIC images for decoding, but they must be served in web-safe formats such as AVIF, WebP, JPG, or PNG.
### Supported output formats
* JPEG
* PNG
* GIF (including animations)
* WebP (including animations)
* SVG
* AVIF
### Supported features
Transformations can:
* Resize and generate JPEG and PNG images, and optionally AVIF or WebP.
* Save animations as GIF or animated WebP.
* Support ICC color profiles in JPEG and PNG images.
* Preserve JPEG metadata (metadata of other formats is discarded).
* Convert the first frame of GIF/WebP animations to a still image.
## SVG files
Cloudflare Images can deliver SVG files. However, as this is an [inherently scalable format](https://www.w3.org/TR/SVG2/), Cloudflare does not resize SVGs.
As such, Cloudflare Images variants cannot be used to resize SVG files. Variants, named or flexible, are intended to transform bitmap (raster) images into whatever size you want to serve them.
You can, nevertheless, use variants to serve SVGs, using any named variant as a placeholder to allow your image to be delivered. For example:
```txt
https://imagedelivery.net///public
```
Cloudflare recommends you use named variants with SVG files. If you use flexible variants, all your parameters will be ignored. In either case, Cloudflare applies SVG sanitizing to your files.
You can also use image transformations to sanitize SVG files stored in your origin. However, as stated above, transformations will ignore all transform parameters, as Cloudflare does not resize SVGs.
### Sanitized SVGs
Cloudflare sanitizes SVG files with `svg-hush` before serving them. This open-source tool developed by Cloudflare is intended to make SVGs as safe as possible. Because SVG files are XML documents, they can have links or JavaScript features that may pose a security concern. As such, `svg-hush` filters SVGs and removes any potential risky features, such as:
* **Scripting**: Prevents SVG files from being used for cross-site scripting attacks. Although browsers do not allow scripts in the `![]() ` tag, they do allow scripting when SVG files are opened directly as a top-level document.
* **Hyperlinks to other documents**: Makes SVG files less attractive for SEO spam and phishing.
* **References to cross-origin resources**: Stops third parties from tracking who is viewing the image.
SVG files can also contain embedded images in other formats, like JPEG and PNG, in the form of [Data URLs](https://developer.mozilla.org/en-US/docs/Web/HTTP/Basics_of_HTTP/Data_URLs). Cloudflare treats these embedded images just like other images that we process, and optimizes them too. Cloudflare does not support SVG files embedded in SVG recursively, though.
Cloudflare still uses Content Security Policy (CSP) headers to disable unwanted features, but filtering acts as a defense-in-depth in case these headers are lost (for instance, if the image was saved as a file and served elsewhere).
`svg-hush` is open-source. It is written in Rust and can filter SVG files in a streaming fashion without buffering, so it is fast enough for filtering on the fly.
For more information about `svg-hush`, refer to [Cloudflare GitHub repository](https://github.com/cloudflare/svg-hush).
### Format limitations
Since some image formats require longer computational times than others, Cloudflare has to find a proper balance between the time it takes to generate an image and to transfer it over the Internet.
Resizing requests might not be fulfilled with the format the user expects due to these trade-offs Cloudflare has to make. Images differ in size, transformations, codecs and all of these different aspects influence what compression codecs are used.
Cloudflare tries to choose the requested codec, but we operate on a best-effort basis and there are limits that our system needs to follow to satisfy all customers.
AVIF encoding, in particular, can be an order of magnitude slower than encoding to other formats. Cloudflare will fall back to WebP or JPEG if the image is too large to be encoded quickly.
#### Limits per format
Hard limits refers to the maximum image size to process. Soft limits refers to the limits existing when the system is overloaded.
| File format | Hard limits on the longest side (width or height) | Soft limits on the longest side (width or height) |
| - | - | - |
| AVIF | 1,200 pixels1 | 640 pixels |
| Other | 12,000 pixels | N/A |
| WebP | N/A | 2,560 pixels for lossy; 1920 pixels for lossless |
1Hard limit is 1,600 pixels when `format=avif` is explicitly used with [image transformations](https://developers.cloudflare.com/images/transform-images/).
All images have to be less than 70 MB. The maximum image area is limited to 100 megapixels (for example, 10,000 x 10,000 pixels large).
GIF/WebP animations are limited to a total of 50 megapixels (the sum of sizes of all frames). Animations that exceed this will be passed through unchanged without applying any transformations. Note that GIF is an outdated format and has very inefficient compression. High-resolution animations will be slow to process and will have very large file sizes. For video clips, Cloudflare recommends using [video formats like MP4 and WebM instead](https://developers.cloudflare.com/stream/).
Important
SVG files are passed through without resizing. This format is inherently scalable and does not need resizing.
AVIF format is supported on a best-effort basis. Images that cannot be compressed as AVIF will be served as WebP instead.
#### Progressive JPEG
While you can use the `format=jpeg` option to generate images in an interlaced progressive JPEG format, we will fallback to the baseline JPEG format for small and large images specified when:
* The area calculated by width x height is less than 150 x 150.
* The area calculated by width x height is greater than 3000 x 3000.
For example, a 50 x 50 tiny image is always formatted by `baseline-jpeg` even if you specify progressive jpeg (`format=jpeg`).
---
title: Tutorials · Cloudflare Images docs
lastUpdated: 2025-04-03T11:41:17.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/images/tutorials/
md: https://developers.cloudflare.com/images/tutorials/index.md
---
* [Optimize mobile viewing](https://developers.cloudflare.com/images/tutorials/optimize-mobile-viewing/)
* [Transform user-uploaded images before uploading to R2](https://developers.cloudflare.com/images/tutorials/optimize-user-uploaded-image/)
---
title: Upload images · Cloudflare Images docs
description: Cloudflare Images allows developers to upload images using
different methods, for a wide range of use cases.
lastUpdated: 2025-10-30T11:07:38.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/upload-images/
md: https://developers.cloudflare.com/images/upload-images/index.md
---
Cloudflare Images allows developers to upload images using different methods, for a wide range of use cases.
## Supported image formats
You can upload the following image formats to Cloudflare Images:
* PNG
* GIF (including animations)
* JPEG
* WebP (Cloudflare Images also supports uploading animated WebP files)
* SVG
* HEIC
Note
Cloudflare can ingest HEIC images for decoding, but they must be served in web-safe formats such as AVIF, WebP, JPG, or PNG.
## Dimensions and sizes
These are the maximum allowed sizes and dimensions when uploading to Images:
* Maximum image dimension is 12,000 pixels.
* Maximum image area is limited to 100 megapixels (for example, 10,000×10,000 pixels).
* Image metadata is limited to 1024 bytes (when uploaded and stored in Cloudflare).
* Images have a 10 megabyte (MB) size limit (when uploaded and stored in Cloudflare).
* Animated GIFs/WebP, including all frames, are limited to 50 megapixels (MP).
---
title: 404 - Page Not Found · Cloudflare Key Transparency Auditor docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/key-transparency/404/
md: https://developers.cloudflare.com/key-transparency/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API · Cloudflare Key Transparency Auditor docs
lastUpdated: 2024-09-24T11:10:22.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/key-transparency/api/
md: https://developers.cloudflare.com/key-transparency/api/index.md
---
* [Auditor](https://developers.cloudflare.com/key-transparency/api/auditor-information/)
* [Namespaces](https://developers.cloudflare.com/key-transparency/api/namespaces/)
* [Epochs](https://developers.cloudflare.com/key-transparency/api/epochs/)
---
title: Monitor the Auditor · Cloudflare Key Transparency Auditor docs
description: Cloudflare's Key Transparency Auditor validates Log audit proofs
and provides a signature for them. The Log can then distribute these
signatures to its end-users, and provides users with confidence that keys have
not been tampered with.
lastUpdated: 2024-09-27T14:40:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/key-transparency/monitor-the-auditor/
md: https://developers.cloudflare.com/key-transparency/monitor-the-auditor/index.md
---
Cloudflare's Key Transparency Auditor validates Log audit proofs and provides a signature for them. The Log can then distribute these signatures to its end-users, and provides users with confidence that keys have not been tampered with.
In order to verify our work, you can use [Plexi](https://github.com/cloudflare/plexi), a CLI tool that allows anyone to perform proof verification locally via a public [API](https://developers.cloudflare.com/key-transparency/api/).
## Features
* Verify authenticity of a signature, to confirm it has been signed by a given public key
* Verify the validity of [facebook/akd](https://github.com/facebook/akd) proofs
* List Logs an Auditor monitors
## Installation
| Environment | CLI Command |
| - | - |
| [Cargo](https://www.rust-lang.org/tools/install) (Rust 1.81+) | `cargo install plexi` |
## Usage
Use the `--help` option for more details about the commands and their options.
```bash
plexi [OPTIONS]
```
### Configure your auditor remote
`plexi` does not come with a default remote auditor, and you will need to choose your own.
You can do so either by passing `--remote-url=` or setting the `PLEXI_REMOTE_URL` environment variable.
A common remote is provided below:
| Name | Remote |
| - | - |
| Cloudflare | `https://plexi.key-transparency.cloudflare.com` |
If you have deployed your own auditor, you can add a remote by filing a [GitHub issue](https://github.com/cloudflare/plexi/issues).
### List monitored Logs
An auditor monitors multiple Logs at once. To discover which Logs an auditor is monitoring, run the following:
```shell
plexi ls --remote-url 'https://plexi.key-transparency.cloudflare.com'
whatsapp.key-transparency.v1
```
### Audit a signature
The Key Transparency Auditor vouches for Log validity by ensuring epoch uniqueness and verifying the associated proof.
`plexi audit` provides information about a given epoch and its validity. It can perform a local audit to confirm the auditor behaviour.
For instance, to verify WhatsApp Log auditted by Cloudflare Auditor, run the following:
```shell
> plexi audit --remote-url 'https://plexi.key-transparency.cloudflare.com' --namespace 'whatsapp.key-transparency.v1' --long
Namespace
Name : whatsapp.key-transparency.v1
Ciphersuite : ed25519(protobuf)
Signature (2024-09-23T16:53:45Z)
Epoch height : 489193
Epoch digest : cbe5097ae832a3ae51ad866104ffd4aa1f7479e873fd18df9cb96a02fc91ebfe
Signature : fe94973e19da826487b637c019d3ce52f0c08093ada00b4fe6563e2f8117b4345121342bc33aae249be47979dfe704478e2c18aed86e674df9f934b718949c08
Signature verification: success
Proof verification : success
```
---
title: 404 - Page Not Found · Cloudflare Workers KV docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/404/
md: https://developers.cloudflare.com/kv/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Workers Binding API · Cloudflare Workers KV docs
lastUpdated: 2024-11-20T15:28:21.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/api/
md: https://developers.cloudflare.com/kv/api/index.md
---
* [Read key-value pairs](https://developers.cloudflare.com/kv/api/read-key-value-pairs/)
* [Write key-value pairs](https://developers.cloudflare.com/kv/api/write-key-value-pairs/)
* [Delete key-value pairs](https://developers.cloudflare.com/kv/api/delete-key-value-pairs/)
* [List keys](https://developers.cloudflare.com/kv/api/list-keys/)
---
title: Key concepts · Cloudflare Workers KV docs
lastUpdated: 2024-09-03T13:14:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/concepts/
md: https://developers.cloudflare.com/kv/concepts/index.md
---
* [How KV works](https://developers.cloudflare.com/kv/concepts/how-kv-works/)
* [KV bindings](https://developers.cloudflare.com/kv/concepts/kv-bindings/)
* [KV namespaces](https://developers.cloudflare.com/kv/concepts/kv-namespaces/)
---
title: Examples · Cloudflare Workers KV docs
description: Explore the following examples for KV.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/examples/
md: https://developers.cloudflare.com/kv/examples/index.md
---
Explore the following examples for KV.
[Cache data with Workers KV](https://developers.cloudflare.com/kv/examples/cache-data-with-workers-kv/)
[Example of how to use Workers KV to build a distributed application configuration store.](https://developers.cloudflare.com/kv/examples/cache-data-with-workers-kv/)
[Build a distributed configuration store](https://developers.cloudflare.com/kv/examples/distributed-configuration-with-workers-kv/)
[Example of how to use Workers KV to build a distributed application configuration store.](https://developers.cloudflare.com/kv/examples/distributed-configuration-with-workers-kv/)
[Route requests across various web servers](https://developers.cloudflare.com/kv/examples/routing-with-workers-kv/)
[Example of how to use Workers KV to build a distributed application configuration store.](https://developers.cloudflare.com/kv/examples/routing-with-workers-kv/)
[Store and retrieve static assets](https://developers.cloudflare.com/kv/examples/workers-kv-to-serve-assets/)
[Example of how to use Workers KV to store static assets](https://developers.cloudflare.com/kv/examples/workers-kv-to-serve-assets/)
---
title: Demos and architectures · Cloudflare Workers KV docs
description: Learn how you can use KV within your existing application and architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/demos/
md: https://developers.cloudflare.com/kv/demos/index.md
---
Learn how you can use KV within your existing application and architecture.
## Demo applications
Explore the following demo applications for KV.
* [Queues Web Crawler:](https://github.com/cloudflare/queues-web-crawler) An example use-case for Queues, a web crawler built on Browser Rendering and Puppeteer. The crawler finds the number of links to Cloudflare.com on the site, and archives a screenshot to Workers KV.
## Reference architectures
Explore the following reference architectures that use KV:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Programmable Platforms](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[Workers for Platforms provide secure, scalable, cost-effective infrastructure for programmable platforms with global reach.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[You can connect a Cloudflare Worker to get data from Google BigQuery and pass it to Workers AI, to run AI Models, powered by serverless GPUs.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[A/B-testing using Workers](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/a-b-testing-using-workers/)
[Cloudflare's low-latency, fully serverless compute platform, Workers offers powerful capabilities to enable A/B testing using a server-side implementation.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/a-b-testing-using-workers/)
[Serverless global APIs](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[An example architecture of a serverless API on Cloudflare and aims to illustrate how different compute and data products could interact with each other.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[Serverless image content management](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
[Leverage various components of Cloudflare's ecosystem to construct a scalable image management solution](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
---
title: Getting started · Cloudflare Workers KV docs
description: Workers KV provides low-latency, high-throughput global storage to
your Cloudflare Workers applications. Workers KV is ideal for storing user
configuration data, routing data, A/B testing configurations and
authentication tokens, and is well suited for read-heavy workloads.
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/get-started/
md: https://developers.cloudflare.com/kv/get-started/index.md
---
Workers KV provides low-latency, high-throughput global storage to your [Cloudflare Workers](https://developers.cloudflare.com/workers/) applications. Workers KV is ideal for storing user configuration data, routing data, A/B testing configurations and authentication tokens, and is well suited for read-heavy workloads.
This guide instructs you through:
* Creating a KV namespace.
* Writing key-value pairs to your KV namespace from a Cloudflare Worker.
* Reading key-value pairs from a KV namespace.
You can perform these tasks through the Wrangler CLI or through the Cloudflare dashboard.
## Quick start
If you want to skip the setup steps and get started quickly, click on the button below.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/docs-examples/tree/update/kv/kv/kv-get-started)
This creates a repository in your GitHub account and deploys the application to Cloudflare Workers. Use this option if you are familiar with Cloudflare Workers, and wish to skip the step-by-step guidance.
You may wish to manually follow the steps if you are new to Cloudflare Workers.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
## 1. Create a Worker project
New to Workers?
Refer to [How Workers works](https://developers.cloudflare.com/workers/reference/how-workers-works/) to learn about the Workers serverless execution model works. Go to the [Workers Get started guide](https://developers.cloudflare.com/workers/get-started/guide/) to set up your first Worker.
* CLI
Create a new Worker to read and write to your KV namespace.
1. Create a new project named `kv-tutorial` by running:
* npm
```sh
npm create cloudflare@latest -- kv-tutorial
```
* yarn
```sh
yarn create cloudflare kv-tutorial
```
* pnpm
```sh
pnpm create cloudflare@latest kv-tutorial
```
For setup, select the following options:
* For *What would you like to start with?*, choose `Hello World example`.
* For *Which template would you like to use?*, choose `Worker only`.
* For *Which language do you want to use?*, choose `TypeScript`.
* For *Do you want to use git for version control?*, choose `Yes`.
* For *Do you want to deploy your application?*, choose `No` (we will be making some changes before deploying).
This creates a new `kv-tutorial` directory, illustrated below.
Your new `kv-tutorial` directory includes:
* A `"Hello World"` [Worker](https://developers.cloudflare.com/workers/get-started/guide/#3-write-code) in `index.ts`.
* A [`wrangler.jsonc`](https://developers.cloudflare.com/workers/wrangler/configuration/) configuration file. `wrangler.jsonc` is how your `kv-tutorial` Worker accesses your kv database.
2. Change into the directory you just created for your Worker project:
```sh
cd kv-tutorial
```
Note
If you are familiar with Cloudflare Workers, or initializing projects in a Continuous Integration (CI) environment, initialize a new project non-interactively by setting `CI=true` as an [environmental variable](https://developers.cloudflare.com/workers/configuration/environment-variables/) when running `create cloudflare@latest`.
For example: `CI=true npm create cloudflare@latest kv-tutorial --type=simple --git --ts --deploy=false` creates a basic "Hello World" project ready to build on.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select **Create application**.
3. Select **Start with Hello World!** > **Get started**.
4. Name your Worker. For this tutorial, name your Worker `kv-tutorial`.
5. Select **Deploy**.
* npm
```sh
npm create cloudflare@latest -- kv-tutorial
```
* yarn
```sh
yarn create cloudflare kv-tutorial
```
* pnpm
```sh
pnpm create cloudflare@latest kv-tutorial
```
## 2. Create a KV namespace
A [KV namespace](https://developers.cloudflare.com/kv/concepts/kv-namespaces/) is a key-value database replicated to Cloudflare's global network.
* CLI
You can use [Wrangler](https://developers.cloudflare.com/workers/wrangler/) to create a new KV namespace. You can also use it to perform operations such as put, list, get, and delete within your KV namespace.
Note
KV operations are scoped to your account.
To create a KV namespace via Wrangler:
1. Open your terminal and run the following command:
```sh
npx wrangler kv namespace create
```
The `npx wrangler kv namespace create ` subcommand takes a new binding name as its argument. A KV namespace is created using a concatenation of your Worker's name (from your Wrangler file) and the binding name you provide. A `` is randomly generated for you.
For this tutorial, use the binding name `USERS_NOTIFICATION_CONFIG`.
```sh
npx wrangler kv namespace create
```
```sh
🌀 Creating namespace with title "USERS_NOTIFICATION_CONFIG"
✨ Success!
Add the following to your configuration file in your kv_namespaces array:
{
"kv_namespaces": [
{
"binding": "USERS_NOTIFICATION_CONFIG",
"id": ""
}
]
}
```
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers KV** page.
[Go to **Workers KV**](https://dash.cloudflare.com/?to=/:account/workers/kv/namespaces)
2. Select **Create instance**.
3. Enter a name for your namespace. For this tutorial, use `kv_tutorial_namespace`.
4. Select **Create**.
## 3. Bind your Worker to your KV namespace
You must create a binding to connect your Worker with your KV namespace. [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) allow your Workers to access resources, like KV, on the Cloudflare developer platform.
Bindings
A binding is how your Worker interacts with external resources such as [KV namespaces](https://developers.cloudflare.com/kv/concepts/kv-namespaces/). A binding is a runtime variable that the Workers runtime provides to your code. You can declare a variable name in your Wrangler file that binds to these resources at runtime, and interact with them through this variable. Every binding's variable name and behavior is determined by you when deploying the Worker.
Refer to [Environment](https://developers.cloudflare.com/kv/reference/environments/) for more information.
To bind your KV namespace to your Worker:
* CLI
1. In your Wrangler file, add the following with the values generated in your terminal from [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace):
* wrangler.jsonc
```jsonc
{
"kv_namespaces": [
{
"binding": "USERS_NOTIFICATION_CONFIG",
"id": ""
}
]
}
```
* wrangler.toml
```toml
[[kv_namespaces]]
binding = "USERS_NOTIFICATION_CONFIG"
id = ""
```
Binding names do not need to correspond to the namespace you created. Binding names are only a reference. Specifically:
* The value (string) you set for `binding` is used to reference this KV namespace in your Worker. For this tutorial, this should be `USERS_NOTIFICATION_CONFIG`.
* The binding must be [a valid JavaScript variable name](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Guide/Grammar_and_types#variables). For example, `binding = "MY_KV"` or `binding = "routingConfig"` would both be valid names for the binding.
* Your binding is available in your Worker at `env.` from within your Worker. For this tutorial, the binding is available at `env.USERS_NOTIFICATION_CONFIG`.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select the `kv-tutorial` Worker you created in [step 1](https://developers.cloudflare.com/kv/get-started/#1-create-a-worker-project).
3. Got to the **Bindings** tab, then select **Add binding**.
4. Select **KV namespace** > **Add binding**.
5. Name your binding (`BINDING_NAME`) in **Variable name**, then select the KV namespace (`kv_tutorial_namespace`) you created in [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace) from the dropdown menu.
6. Select **Add binding** to deploy your binding.
* wrangler.jsonc
```jsonc
{
"kv_namespaces": [
{
"binding": "USERS_NOTIFICATION_CONFIG",
"id": ""
}
]
}
```
* wrangler.toml
```toml
[[kv_namespaces]]
binding = "USERS_NOTIFICATION_CONFIG"
id = ""
```
## 4. Interact with your KV namespace
You can interact with your KV namespace via [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/) or directly from your [Workers](https://developers.cloudflare.com/workers/) application.
### 4.1. Write a value
* CLI
To write a value to your empty KV namespace using Wrangler:
1. Run the `wrangler kv key put` subcommand in your terminal, and input your key and value respectively. `` and `` are values of your choice.
```sh
npx wrangler kv key put --binding= "" ""
```
In this tutorial, you will add a key `user_1` with value `enabled` to the KV namespace you created in [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace).
```sh
npx wrangler kv key put --binding=USERS_NOTIFICATION_CONFIG "user_1" "enabled"
```
```sh
Writing the value "enabled" to key "user_1" on namespace .
```
Using `--namespace-id`
Instead of using `--binding`, you can also use `--namespace-id` to specify which KV namespace should receive the operation:
```sh
npx wrangler kv key put --namespace-id= "" ""
```
```sh
Writing the value "" to key "" on namespace .
```
Storing values in remote KV namespace
By default, the values are written locally. To create a key and a value in your remote KV namespace, add the `--remote` flag at the end of the command:
```sh
npx wrangler kv key put --namespace-id=xxxxxxxxxxxxxxxx "" ""
```
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers KV** page.
[Go to **Workers KV**](https://dash.cloudflare.com/?to=/:account/workers/kv/namespaces)
2. Select the KV namespace you created (`kv_tutorial_namespace`).
3. Go to the **KV Pairs** tab.
4. Enter a `` of your choice.
5. Enter a `` of your choice.
6. Select **Add entry**.
### 4.2. Get a value
* CLI
To access the value from your KV namespace using Wrangler:
1. Run the `wrangler kv key get` subcommand in your terminal, and input your key value:
```sh
npx wrangler kv key get --binding= ""
```
In this tutorial, you will get the value of the key `user_1` from the KV namespace you created in [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace).
Note
To view the value directly within the terminal, you use the `--text` flag.
```sh
npx wrangler kv key get --binding=USERS_NOTIFICATION_CONFIG "user_1" --text
```
Similar to the `put` command, the `get` command can also be used to access a KV namespace in two ways - with `--binding` or `--namespace-id`:
Warning
Exactly **one** of `--binding` or `--namespace-id` is required.
Refer to the [`kv bulk` documentation](https://developers.cloudflare.com/kv/reference/kv-commands/#kv-bulk) to write a file of multiple key-value pairs to a given KV namespace.
* Dashboard
You can view key-value pairs directly from the dashboard.
1. In the Cloudflare dashboard, go to the **Workers KV** page.
[Go to **Workers KV**](https://dash.cloudflare.com/?to=/:account/workers/kv/namespaces)
2. Go to the KV namespace you created (`kv_tutorial_namespace`).
3. Go to the **KV Pairs** tab.
## 5. Access your KV namespace from your Worker
* CLI
Note
When using [`wrangler dev`](https://developers.cloudflare.com/workers/wrangler/commands/#dev) to develop locally, Wrangler defaults to using a local version of KV to avoid interfering with any of your live production data in KV. This means that reading keys that you have not written locally returns null.
To have `wrangler dev` connect to your Workers KV namespace running on Cloudflare's global network, you can set `"remote" : true` in the KV binding configuration. Refer to the [remote bindings documentation](https://developers.cloudflare.com/workers/development-testing/#remote-bindings) for more information.
Also refer to [KV binding docs](https://developers.cloudflare.com/kv/concepts/kv-bindings/#use-kv-bindings-when-developing-locally).
1. In your Worker script, add your KV binding in the `Env` interface. If you have bootstrapped your project with JavaScript, this step is not required.
```ts
interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
// ... other binding types
}
```
2. Use the `put()` method on `USERS_NOTIFICATION_CONFIG` to create a new key-value pair. You will add a new key `user_2` with value `disabled` to your KV namespace.
```ts
let value = await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
```
3. Use the KV `get()` method to fetch the data you stored in your KV namespace. You will fetch the value of the key `user_2` from your KV namespace.
```ts
let value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
```
Your Worker code should look like this:
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
The code above:
1. Writes a key to your KV namespace using KV's `put()` method.
2. Reads the same key using KV's `get()` method.
3. Checks if the key is null, and returns a `404` response if it is.
4. If the key is not null, it returns the value of the key.
5. Uses JavaScript's [`try...catch`](https://developer.mozilla.org/docs/Web/JavaScript/Reference/Statements/try...catch) exception handling to catch potential errors. When writing or reading from any service, such as Workers KV or external APIs using `fetch()`, you should expect to handle exceptions explicitly.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Go to the `kv-tutorial` Worker you created.
3. Select **Edit Code**.
4. Clear the contents of the `workers.js` file, then paste the following code.
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
The code above:
1. Writes a key to `BINDING_NAME` using KV's `put()` method.
2. Reads the same key using KV's `get()` method, and returns an error if the key is null (or in case the key is not set, or does not exist).
3. Uses JavaScript's [`try...catch`](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Statements/try...catch) exception handling to catch potential errors. When writing or reading from any service, such as Workers KV or external APIs using `fetch()`, you should expect to handle exceptions explicitly.
The browser should simply return the `VALUE` corresponding to the `KEY` you have specified with the `get()` method.
5. Select the dropdown arrow next to **Deploy** and select **Save**.
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
## 6. Deploy your Worker
Deploy your Worker to Cloudflare's global network.
* CLI
1. Run the following command to deploy KV to Cloudflare's global network:
```sh
npm run deploy
```
2. Visit the URL for your newly created Workers KV application.
For example, if the URL of your new Worker is `kv-tutorial..workers.dev`, accessing `https://kv-tutorial..workers.dev/` sends a request to your Worker that writes (and reads) from Workers KV.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select your `kv-tutorial` Worker.
3. Select **Deployments**.
4. From the **Version History** table, select **Deploy version**.
5. From the **Deploy version** page, select **Deploy**.
This deploys the latest version of the Worker code to production.
## Summary
By finishing this tutorial, you have:
1. Created a KV namespace
2. Created a Worker that writes and reads from that namespace
3. Deployed your project globally.
## Next steps
If you have any feature requests or notice any bugs, share your feedback directly with the Cloudflare team by joining the [Cloudflare Developers community on Discord](https://discord.cloudflare.com).
* Learn more about the [KV API](https://developers.cloudflare.com/kv/api/).
* Understand how to use [Environments](https://developers.cloudflare.com/kv/reference/environments/) with Workers KV.
* Read the Wrangler [`kv` command documentation](https://developers.cloudflare.com/kv/reference/kv-commands/).
---
title: Glossary · Cloudflare Workers KV docs
description: Review the definitions for terms used across Cloudflare's KV documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/glossary/
md: https://developers.cloudflare.com/kv/glossary/index.md
---
Review the definitions for terms used across Cloudflare's KV documentation.
| Term | Definition |
| - | - |
| cacheTtl | CacheTtl is a parameter that defines the length of time in seconds that a KV result is cached in the global network location it is accessed from. |
| KV namespace | A KV namespace is a key-value database replicated to Cloudflare’s global network. A KV namespace must require a binding and an id. |
| metadata | A metadata is a serializable value you append to each KV entry. |
---
title: Platform · Cloudflare Workers KV docs
lastUpdated: 2024-09-03T13:14:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/platform/
md: https://developers.cloudflare.com/kv/platform/index.md
---
* [Pricing](https://developers.cloudflare.com/kv/platform/pricing/)
* [Limits](https://developers.cloudflare.com/kv/platform/limits/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
* [Release notes](https://developers.cloudflare.com/kv/platform/release-notes/)
* [Event subscriptions](https://developers.cloudflare.com/kv/platform/event-subscriptions/)
---
title: Reference · Cloudflare Workers KV docs
lastUpdated: 2024-09-03T13:14:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/reference/
md: https://developers.cloudflare.com/kv/reference/index.md
---
* [Wrangler KV commands](https://developers.cloudflare.com/kv/reference/kv-commands/)
* [Environments](https://developers.cloudflare.com/kv/reference/environments/)
* [Data security](https://developers.cloudflare.com/kv/reference/data-security/)
* [FAQ](https://developers.cloudflare.com/kv/reference/faq/)
---
title: Tutorials · Cloudflare Workers KV docs
description: View tutorials to help you get started with KV.
lastUpdated: 2025-05-06T17:35:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/tutorials/
md: https://developers.cloudflare.com/kv/tutorials/index.md
---
View tutorials to help you get started with KV.
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [Use Workers KV directly from Rust](https://developers.cloudflare.com/workers/tutorials/workers-kv-from-rust/) | over 1 year ago | Intermediate |
| [Build a todo list Jamstack application](https://developers.cloudflare.com/workers/tutorials/build-a-jamstack-app/) | over 1 year ago | Beginner |
## Videos
Cloudflare Workflows | Introduction (Part 1 of 3)
In this video, we introduce Cloudflare Workflows, the Newest Developer Platform Primitive at Cloudflare.
Cloudflare Workflows | Batching and Monitoring Your Durable Execution (Part 2 of 3)
Workflows exposes metrics such as execution, error rates, steps, and total duration!
Build a URL Shortener with an AI-based admin section
We are building a URL Shortener, shrty.dev, on Cloudflare. The apps uses Workers KV and Workers Analytics engine. Craig decided to build with Workers AI runWithTools to provide a chat interface for admins.
Build Rust Powered Apps
In this video, we will show you how to build a global database using workers-rs to keep track of every country and city you’ve visited.
Stateful Apps with Cloudflare Workers
Learn how to access external APIs, cache and retrieve data using Workers KV, and create SQL-driven applications with Cloudflare D1.
---
title: Observability · Cloudflare Workers KV docs
lastUpdated: 2024-09-17T08:47:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/observability/
md: https://developers.cloudflare.com/kv/observability/index.md
---
* [Metrics and analytics](https://developers.cloudflare.com/kv/observability/metrics-analytics/)
---
title: KV REST API · Cloudflare Workers KV docs
lastUpdated: 2025-05-20T08:19:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/workers-kv-api/
md: https://developers.cloudflare.com/kv/workers-kv-api/index.md
---
---
title: 404 - Page Not Found · Cloudflare Load Balancing docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/404/
md: https://developers.cloudflare.com/load-balancing/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Additional configuration · Cloudflare Load Balancing docs
description: Beyond creating a simple load balancer, you may want to further
customize how your load balancer routes traffic or integrate your load
balancer with other Cloudflare products.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/additional-options/
md: https://developers.cloudflare.com/load-balancing/additional-options/index.md
---
Beyond [creating a simple load balancer](https://developers.cloudflare.com/load-balancing/load-balancers/create-load-balancer/), you may want to further customize how your load balancer routes traffic or integrate your load balancer with other Cloudflare products.
## Customize load balancer behavior
* Route traffic according to characteristics of each request by [creating custom rules](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-rules/)
* Protect at-risk endpoints from reaching failover by [setting up load shedding](https://developers.cloudflare.com/load-balancing/additional-options/load-shedding/)
* Take endpoints out of rotation for [planned maintenance](https://developers.cloudflare.com/load-balancing/additional-options/planned-maintenance/)
## Integrate with other Cloudflare products
* Bring load balancing to your TCP or UDP applications with [Cloudflare Spectrum](https://developers.cloudflare.com/load-balancing/additional-options/spectrum/)
* Further secure endpoint access with [Cloudflare Tunnel](https://developers.cloudflare.com/load-balancing/additional-options/cloudflare-tunnel/)
## Integrate with 3rd parties
* Increase visibility by [sending health monitor notifications to PagerDuty](https://developers.cloudflare.com/load-balancing/additional-options/pagerduty-integration/)
---
title: API reference · Cloudflare Load Balancing docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/api-reference/
md: https://developers.cloudflare.com/load-balancing/api-reference/index.md
---
---
title: Changelog · Cloudflare Load Balancing docs
description: Cloudflare Load Balancing now supports Monitor Groups, a powerful
new way to combine multiple health monitors into a single, logical group. This
allows you to create sophisticated health checks that more accurately reflect
the true availability of your applications by assessing multiple services at
once.
lastUpdated: 2025-05-06T18:53:27.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/changelog/
md: https://developers.cloudflare.com/load-balancing/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/load-balancing.xml)
## 2025-10-16
**Monitor Groups for Advanced Health Checking With Load Balancing**
Cloudflare Load Balancing now supports Monitor Groups, a powerful new way to combine multiple health monitors into a single, logical group. This allows you to create sophisticated health checks that more accurately reflect the true availability of your applications by assessing multiple services at once.
With Monitor Groups, you can ensure that all critical components of an application are healthy before sending traffic to an origin pool, enabling smarter failover decisions and greater resilience. This feature is now available via the API for customers with an Enterprise Load Balancing subscription.
#### What you can do:
* **Combine Multiple Monitors**: Group different health monitors (for example, HTTP, TCP) that check various application components, like a primary API gateway and a specific `/login` service.
* **Isolate Monitors for Observation**: Mark a monitor as "monitoring only" to receive alerts and data without it affecting a pool's health status or traffic steering. This is perfect for testing new checks or observing non-critical dependencies.
* **Improve Steering Intelligence**: Latency for Dynamic Steering is automatically averaged across all active monitors in a group, providing a more holistic view of an origin's performance.
This enhancement is ideal for complex, multi-service applications where the health of one component depends on another. By aggregating health signals, Monitor Groups provide a more accurate and comprehensive assessment of your application's true status.
For detailed information and API configuration guides, please visit our [developer documentation](https://developers.cloudflare.com/load-balancing/monitors/monitor-groups) for Monitor Groups.
## 2025-08-15
**Steer Traffic by AS Number in Load Balancing Custom Rules**
You can now create more granular, network-aware Custom Rules in Cloudflare Load Balancing using the Autonomous System Number (ASN) of an incoming request.
This allows you to steer traffic with greater precision based on the network source of a request. For example, you can route traffic from specific Internet Service Providers (ISPs) or enterprise customers to dedicated infrastructure, optimize performance, or enforce compliance by directing certain networks to preferred data centers.

To get started, create a [Custom Rule](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-rules/) in your Load Balancer and select **AS Num** from the **Field** dropdown.
## 2025-08-06
**Improvements to Monitoring Using Zone Settings**
Cloudflare Load Balancing Monitors support loading and applying settings for a specific zone to monitoring requests to origin endpoints. This feature has been migrated to new infrastructure to improve reliability, performance, and accuracy.
All zone monitors have been tested against the new infrastructure. There should be no change to health monitoring results of currently healthy and active pools. Newly created or re-enabled pools may need validation of their monitor zone settings before being introduced to service, especially regarding correct application of mTLS.
#### What you can expect:
* More reliable application of zone settings to monitoring requests, including
* Authenticated Origin Pulls
* Aegis Egress IP Pools
* Argo Smart Routing
* HTTP/2 to Origin
* Improved support and bug fixes for retries, redirects, and proxied origin resolution
* Improved performance and reliability of monitoring requests withing the Cloudflare network
* Unrelated CDN or WAF configuration changes should have no risk of impact to pool health
## 2025-06-04
**New Account-Level Load Balancing UI and Private Load Balancers**
We've made two large changes to load balancing:
* Redesigned the user interface, now centralized at the **account level**.
* Introduced [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to the UI, enabling you to manage traffic for all of your external and internal applications in a single spot.
This update streamlines how you manage load balancers across multiple zones and extends robust traffic management to your private network infrastructure.

**Key Enhancements:**
* **Account-Level UI Consolidation:**
* **Unified Management:** Say goodbye to navigating individual zones for load balancing tasks. You can now view, configure, and monitor all your load balancers across every zone in your account from a single, intuitive interface at the account level.
* **Improved Efficiency:** This centralized approach provides a more streamlined workflow, making it faster and easier to manage both your public-facing and internal traffic distribution.
* **Private Network Load Balancing:**
* **Secure Internal Application Access:** Create [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to distribute traffic to applications hosted within your private network, ensuring they are not exposed to the public Internet.
* **WARP & Magic WAN Integration:** Effortlessly direct internal traffic from users connected via Cloudflare WARP or through your Magic WAN infrastructure to the appropriate internal endpoint pools.
* **Enhanced Security for Internal Resources:** Combine reliable Load Balancing with Zero Trust access controls to ensure your internal services are both performant and only accessible by verified users.

## 2025-05-06
**UDP and ICMP Monitor Support for Private Load Balancing Endpoints**
Cloudflare Load Balancing now supports **UDP (Layer 4)** and **ICMP (Layer 3)** health monitors for **private endpoints**. This makes it simple to track the health and availability of internal services that don’t respond to HTTP, TCP, or other protocol probes.
#### What you can do:
* Set up **ICMP ping monitors** to check if your private endpoints are reachable.
* Use **UDP monitors** for lightweight health checks on non-TCP workloads, such as DNS, VoIP, or custom UDP-based services.
* Gain better visibility and uptime guarantees for services running behind **Private Network Load Balancing**, without requiring public IP addresses.
This enhancement is ideal for internal applications that rely on low-level protocols, especially when used in conjunction with [**Cloudflare Tunnel**](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/), [**WARP**](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/), and [**Magic WAN**](https://developers.cloudflare.com/magic-wan/) to create a secure and observable private network.
Learn more about [Private Network Load Balancing](https://developers.cloudflare.com/load-balancing/private-network/) or view the full list of [supported health monitor protocols](https://developers.cloudflare.com/load-balancing/monitors/#supported-protocols).
## 2025-04-15
**Introducing Support for Orange-Clouded Origin Resolution**
Newly created Cloudflare Load Balancers will resolve orange-clouded origin addresses, provided the origins belong to the same account and zone as the Load Balancer. Existing Load Balancers will continue using the current resolution method. If ownership validation fails, the new system falls back to the existing behavior and defaults to a gray-clouded (DNS-only) lookup, typically resolving to anycast addresses.
## 2025-03-13
**Update to Load Balancing analytics**
Load Balancing request rates in analytics may decrease for some customers as an improvement is made to our infrastructure. This decrease in Load Balancing analytics does not indicate a decrease in HTTP requests received.
## 2025-02-20
**Zone name added to Load Balancing API responses**
Load Balancing API responses for Load Balancers now include a `zone_name` property, which provides the name of the zone in the response data.
## 2025-02-10
**Fix for Cloudflare Tunnel Consistency**
Fixes to improve the consistency of Cloudflare Tunnel handling within Cloudflare Load Balancers. These changes ensure more reliable and predictable routing, particularly when tunnels are involved.
## 2025-01-24
**Update to Cloudflare Tunnel Steering**
Introduced changes to the resolution of proxied domains that are backed by Cloudflare Tunnels on the same zone. These changes correct how orange-clouded records are steered to Cloudflare Tunnels via Cloudflare Load Balancers.
## 2025-01-16
**Update to Pool Health Monitoring**
We made changes to how we resolve and monitor proxied origins to assess pool health. Our analysis indicates no impact to customer configurations or operations. Contact customer support if you notice any unexpected behavior.
## 2024-12-20
**Load Balancing with the China Network**
You can now enable load balancers to be deployed to the [China Network](https://developers.cloudflare.com/china-network/). Refer to the [documentation](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-china/) for more details.
---
title: Get started · Cloudflare Load Balancing docs
description: "Get started with load balancing in one of two ways:"
lastUpdated: 2025-01-31T09:20:50.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/get-started/
md: https://developers.cloudflare.com/load-balancing/get-started/index.md
---
Get started with load balancing in one of two ways:
* [Quickstart](https://developers.cloudflare.com/load-balancing/get-started/quickstart/): Get up and running quickly with Load Balancing.
* [Learning path](https://developers.cloudflare.com/learning-paths/load-balancing/concepts/): Check an in-depth walkthrough for how to plan and set up a load balancer.
---
title: Load balancers · Cloudflare Load Balancing docs
description: A load balancer distributes traffic among pools according to pool
health and traffic steering policies. Each load balancer is identified by its
DNS hostname (lb.example.com, dev.example.com, etc.) or IP address.
lastUpdated: 2025-08-20T20:59:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/load-balancers/
md: https://developers.cloudflare.com/load-balancing/load-balancers/index.md
---
A load balancer distributes traffic among pools according to [pool health](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/) and [traffic steering policies](https://developers.cloudflare.com/load-balancing/understand-basics/traffic-steering/steering-policies/). Each load balancer is identified by its DNS hostname (`lb.example.com`, `dev.example.com`, etc.) or IP address.
Note
For an overview of how the Cloudflare Load Balancing solution works, refer to [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/). For more background information on what load balancers are, refer to the Cloudflare [Learning Center](https://www.cloudflare.com/learning/performance/what-is-load-balancing/).
***
## Common configurations
For suggestions, refer to [Common load balancer configurations](https://developers.cloudflare.com/load-balancing/load-balancers/common-configurations/).
## Public vs. Private Load Balancers
Public Load Balancers are designed to handle traffic from the public Internet. When deployed, they automatically receive a hostname, making them immediately accessible. These load balancers can direct traffic to a range of destinations, including public hostnames, public IP addresses, and private IP addresses.
Private Load Balancers, in contrast, are meant for internal use within private networks. They do not automatically receive a hostname, but one can be assigned via Gateway Firewall Policies or through an internal DNS system. Private Load Balancers only accept traffic over a private network on-ramp, such as [Cloudflare WARP](https://developers.cloudflare.com/warp-client/) or [Magic WAN](https://developers.cloudflare.com/magic-wan/). They are capable of forwarding traffic exclusively to private IP addresses.
## Load balancing and existing DNS records
For details about DNS records, refer to [DNS records for load balancing](https://developers.cloudflare.com/load-balancing/load-balancers/dns-records/).
## HTTP keep-alive (persistent HTTP connection)
Cloudflare maintains keep-alive connections to improve performance and reduce cost of recurring TCP connects in the request transaction as Cloudflare proxies customer traffic from its edge network to the site's origin.
Ensure HTTP Keep-Alive connections are enabled on your origin. Cloudflare reuses open TCP connections for up to 15 minutes (900 seconds) after the last HTTP request. Origin web servers close TCP connections if too many are open. HTTP Keep-Alive helps avoid premature reset of connections for requests proxied by Cloudflare.
### Session cookies
**When using HTTP cookies to track and bind user sessions to a specific server**, configure [Session Affinity](https://developers.cloudflare.com/load-balancing/understand-basics/session-affinity/) to parse HTTP requests by cookie header. Doing so directs each request to the correct application server even when HTTP requests share the same TCP connection due to keep-alive.
**For example, F5 BIG-IP load balancers set a session cookie at the beginning of a TCP connection** (if none exists) and then ignore all cookies from subsequent HTTP requests on the same TCP connection. This tends to break session affinity because Cloudflare sends multiple HTTP sessions on the same TCP connection. Configuring the load balancer to parse HTTP requests by cookie headers avoids this issue.
***
## Create load balancers
For step-by-step guidance, refer to [Create a load balancer](https://developers.cloudflare.com/load-balancing/load-balancers/create-load-balancer/).
***
## Properties
For an up-to-date list of load balancer properties, refer to [Load balancer properties](https://developers.cloudflare.com/api/resources/load_balancers/methods/get/) in the Cloudflare API documentation.
***
## API commands
The Cloudflare API supports the following commands for load balancers.
| Command | Method | Endpoint |
| - | - | - |
| [Create Load Balancer](https://developers.cloudflare.com/api/resources/load_balancers/methods/create/) | `POST` | `/zones/:zone_id/load_balancers` |
| [Delete Load Balancer](https://developers.cloudflare.com/api/resources/load_balancers/methods/delete/) | `DELETE` | `/zones/:zone_id/load_balancers/:id` |
| [List Load Balancers](https://developers.cloudflare.com/api/resources/load_balancers/methods/list/) | `GET` | `/zones/:zone_id/load_balancers` |
| [Load Balancer Details](https://developers.cloudflare.com/api/resources/load_balancers/methods/get/) | `GET` | `/zones/:zone_id/load_balancers/:id` |
| [Overwrite specific properties](https://developers.cloudflare.com/api/resources/load_balancers/methods/edit/) | `PATCH` | `/zones/:zone_id/load_balancers/:id` |
| [Overwrite entire Load Balancer](https://developers.cloudflare.com/api/resources/load_balancers/methods/update/) | `PUT` | `/zones/:zone_id/load_balancers/:id` |
---
title: Monitors · Cloudflare Load Balancing docs
description: A monitor issues health monitor requests at regular intervals to
evaluate the health of each endpoint within a pool.
lastUpdated: 2025-11-17T15:22:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/monitors/
md: https://developers.cloudflare.com/load-balancing/monitors/index.md
---
A monitor issues health monitor requests at regular intervals to evaluate the health of each endpoint within a [pool](https://developers.cloudflare.com/load-balancing/pools/).
When a pool [becomes unhealthy](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/), your load balancer takes that pool out of the endpoint rotation.
```mermaid
flowchart RL
accTitle: Load balancing monitor flow
accDescr: Monitors issue health monitor requests, which validate the current status of servers within each pool.
Monitor -- Health Monitor ----> Endpoint2
Endpoint2 -- Response ----> Monitor
subgraph Pool
Endpoint1((Endpoint 1))
Endpoint2((Endpoint 2))
end
```
Health monitor requests that result in a status change for an endpoint are recorded as events in the Load Balancing event logs.
Note
Health monitors associated with load balancers are different from standalone [Health Checks](https://developers.cloudflare.com/health-checks/). For an overview of how the Cloudflare Load Balancing solution works, refer to [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/).
***
## Properties
For an up-to-date list of monitor properties, refer to [Monitor properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/list/) in our API documentation.
***
## Create monitors
For step-by-step guidance, refer to [Create monitors](https://developers.cloudflare.com/load-balancing/monitors/create-monitor/).
### Monitor Groups
Monitor Groups let you combine multiple health monitors into a single logical group to create more accurate, intelligent health checks for your applications. By aggregating results from several monitors, you can better reflect real application health and improve traffic steering resilience. For more details, refer to the [Monitor Groups](https://developers.cloudflare.com/load-balancing/monitors/monitor-groups/) documentation page.
***
## Health monitor regions
When you [attach a monitor to a pool](https://developers.cloudflare.com/load-balancing/monitors/create-monitor/#create-a-monitor), you can select multiple regions to increase reporting accuracy.
For each option selected in a pool's **Health Monitor Regions**, Cloudflare sends health monitor requests from three separate data centers in that region.
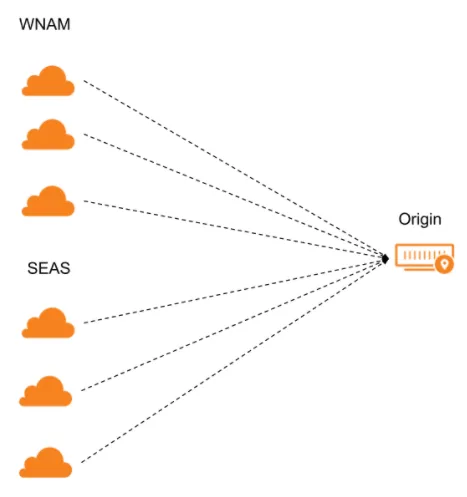
If the majority of data centers for that region pass the health monitor requests, that region is considered healthy. If the majority of regions is healthy, then the endpoint itself will be considered healthy.
### Configurations
**All Data Centers (Enterprise only)**
Health monitor probes are sent from every single data center in Cloudflare’s network to the endpoints within the associated pool. This allows probes to hit each endpoint during intervals set by the customer.
**All Regions**
Three health monitor probes per region are sent to each endpoint in the associated pool. There are a total of 13 regions, resulting in 39 probes.
**Regional**
Three health monitor probes are sent from each specified region within the pool configuration.
Warning
Because of how Cloudflare checks health from [multiple regions](#health-monitor-regions), adding multiple regions — or choosing to check health from **All Data Centers** — can send a lot of traffic to your endpoint.
The same problem can occur when setting low values for a monitor's **Interval**.
***
## Host header prioritization
The host headers used on health monitor requests can be configured either [on the monitor itself](https://developers.cloudflare.com/load-balancing/monitors/create-monitor/) or on the [endpoints within a pool](https://developers.cloudflare.com/load-balancing/pools/create-pool/).
When a host header is specified both on the monitor and on the endpoint, the host header configured on the endpoint takes precedence over the host header configured on the monitor.
When no host header is specified, Cloudflare uses the **Endpoint Address** configured on the endpoints as the host header for the health monitor requests.
For more details, refer to [Override HTTP Host headers](https://developers.cloudflare.com/load-balancing/additional-options/override-http-host-headers/).
***
## API commands
The Cloudflare API supports the following commands for monitors. Examples are given for user-level endpoint but apply to the account-level endpoint as well.
| Command | Method | Endpoint |
| - | - | - |
| [Create Monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/create/) | `POST` | `accounts/:account_id/load_balancers/monitors` |
| [Delete Monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/delete/) | `DELETE` | `accounts/:account_id/load_balancers/monitors/:id` |
| [List Monitors](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/list/) | `GET` | `accounts/:account_id/load_balancers/monitors` |
| [Monitor Details](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/get/) | `GET` | `accounts/:account_id/load_balancers/monitors/:id` |
| [Overwrite specific properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/edit/) | `PATCH` | `accounts/:account_id/load_balancers/monitors/:id` |
| [Overwrite existing monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/update/) | `PUT` | `accounts/:account_id/load_balancers/monitors/:id` |
| [Preview Monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/subresources/previews/methods/create/) | `POST` | `accounts/:account_id/load_balancers/monitors/:id/preview` |
## Supported protocols
The following table summarizes the different types of monitors available in Cloudflare Load Balancing, their monitoring types, and how each health check process evaluates the success criteria to determine endpoint health:
| Monitor type | Monitoring type | Description | Health check process | Success criteria |
| - | - | - | - | - |
| HTTP/HTTPS | Public and private | Used for HTTP and HTTPS endpoints with specific protocol attributes. | The probe is configured with settings and success criteria such as Method, Simulate Zone, Follow Redirects, Request Headers, and Response Body. The probe then evaluates the configured success criteria using the HTTP protocol. Throughout the configured timeout period, the TCP connection is kept active using [keep-alives](https://developers.cloudflare.com/fundamentals/reference/tcp-connections/#tcp-connections-and-keep-alives), even if no response is received. | Success is based on meeting the configured HTTP success criteria. No response within the configured timeout and retries is considered unhealthy. |
| TCP | Public and private | Checks TCP connectivity by attempting to open a connection to the endpoint. | The monitor sends a TCP SYN message to the specified port. A successful health check requires receiving a SYN/ACK message to establish the connection. The connection is closed by sending a FIN or RST packet, or by receiving a FIN packet from the endpoint. | Failure to establish a TCP connection within the configured timeout and retries is considered unhealthy. |
| ICMP Ping | Public and Tunnel | Confirms basic Layer 3 (L3) connectivity to the endpoint using ICMP. The endpoints need to be allowed to reply to ICMP packets and any intervening networking equipment must support ICMP. | The monitor sends an ICMP/ICMPv6 echo request (ping) and expects an ICMP/ICMPv6 echo reply from the endpoint. | The endpoint must reply to the ICMP ping within the configured timeout and retries to be considered healthy. |
| UDP-ICMP | Public and Tunnel | UDP-ICMP monitor works by sending a UDP probe packet after ICMP Ping monitor completes as healthy. | After receiving a successful ICMP reply, the monitor sends a UDP probe packet to the endpoint. If no ICMP Port Unreachable message is received, the endpoint is considered healthy. | If the monitor receives an ICMP Port Unreachable message within the configured timeout and retries, the endpoint is considered unhealthy. |
| SMTP | Public | Verifies SMTP availability at the application layer. | The monitor establishes a TCP connection and sends an SMTP HELO command. It expects a reply with code 250. The monitor then sends an SMTP QUIT command, expecting a reply with code 221. At the end of each interval, the TCP connection is closed by sending a TCP FIN packet. | The endpoint must respond with correct SMTP codes (250 for HELO, 221 for QUIT) within the configured timeout and retries to be considered healthy. |
---
title: Pools · Cloudflare Load Balancing docs
description: Within Cloudflare, pools represent your endpoints and how they are
organized. As such, a pool can be a group of several endpoints, or you could
also have only one endpoint (an origin server, for example) per pool.
lastUpdated: 2025-08-20T20:59:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/pools/
md: https://developers.cloudflare.com/load-balancing/pools/index.md
---
Within Cloudflare, pools represent your endpoints and how they are organized. As such, a pool can be a group of several endpoints, or you could also have only one endpoint (an origin server, for example) per pool.
If you are familiar with DNS terminology, think of a pool as a “record set,” except Cloudflare only returns addresses that are considered healthy. You can attach health monitors to individual pools for customized monitoring. A pool can have either a single monitor or a monitor group attached — but not both.
For more details about how endpoints and pools become unhealthy, refer to [Endpoint and pool health](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/).
Warning
Since load balancing targets are not limited to origin web servers, the term `endpoints` has been introduced. Refer to [Service-Specific Terms](https://www.cloudflare.com/service-specific-terms-other-terms/) for its use in the context of Cloudflare offerings, and to [load balancing concepts](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/) or [Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/load-balancing/) for use case examples.
On the [Load Balancing API](https://developers.cloudflare.com/api/resources/load_balancers/methods/get/), `origin` has been maintained.
***
## Properties
For an up-to-date list of pool properties, refer to [Pool properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/list/) in our API documentation.
***
## Create pools
For step-by-step guidance, refer to [Create pools](https://developers.cloudflare.com/load-balancing/pools/create-pool/).
***
## Per-endpoint Host header override
When your application needs specialized routing (`CNAME` setup or custom hosts like Heroku), change the `Host` header used in health monitor requests. For more details, refer to [Override HTTP Host headers](https://developers.cloudflare.com/load-balancing/additional-options/override-http-host-headers/).
***
## API commands
The Cloudflare API supports the following commands for pools. Examples are given for user-level endpoint but apply to the account-level endpoint as well.
| Command | Method | Endpoint |
| - | - | - |
| [Create Pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/create/) | `POST` | `accounts/:account_id/load_balancers/pools` |
| [Delete Pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/delete/) | `DELETE` | `accounts/:account_id/load_balancers/pools/:id` |
| [List Pools](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/list/) | `GET` | `accounts/:account_id/load_balancers/pools` |
| [Pool Details](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/get/) | `GET` | `accounts/:account_id/load_balancers/pools/:id` |
| [Pool Health Details](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/subresources/health/methods/get/) | `GET` | `account/:account_id/load_balancers/pools/:id/health` |
| [Overwrite specific properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/edit/) | `PATCH` | `accounts/:account_id/load_balancers/pools/:id` |
| [Overwrite existing pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/update/) | `PUT` | `accounts/:account_id/load_balancers/pools/:id` |
| [Preview Pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/subresources/health/methods/create/) | `POST` | `account/:account_id/load_balancers/pools/:id/preview` |
| [List Pool References](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/subresources/references/methods/get/) | `GET` | `accounts/:account_id/load_balancers/pools/:id/references` |
---
title: Private Network Load Balancing · Cloudflare Load Balancing docs
description: Use Private Network Load Balancing to load balance traffic between
servers within a data center or between private applications, and eliminate
the need for hardware appliances.
lastUpdated: 2025-12-16T16:11:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/private-network/
md: https://developers.cloudflare.com/load-balancing/private-network/index.md
---
Private Network Load Balancing enables you to load balance traffic between servers within a data center ([endpoint steering](https://developers.cloudflare.com/load-balancing/understand-basics/traffic-steering/origin-level-steering/)) and between private applications. This helps you eliminate the need for hardware appliances and facilitates the migration of your infrastructure to the cloud, providing advantages such as elastic scalability and enhanced reliability.
Private Network Load Balancing supports not only public IPs but also virtual IPs and private IPs as endpoint values.
Note
This page assumes a certain level of familiarity with how the Cloudflare Load Balancing solution works. For an introductory overview refer to [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/).
***
## Off-ramps
Off-ramps create a direct and secure way for Cloudflare to connect into your networks that are not publicly available.
Since traffic steering decisions or failover mechanisms rely on the health information of pools and endpoints, being able to input your virtual or private IPs directly as endpoints within your load balancer means you can better leverage existing health monitoring.
### Tunnel
Currently, to be able to connect to private IP origins, Cloudflare load balancers require a [Cloudflare tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) with an associated [virtual network (VNet)](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/tunnel-virtual-networks/). If you are connecting to your endpoints using a [published application route](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/routing-to-tunnel/public-load-balancers) a VNet is not necessary.
Once the endpoint and virtual network (VNet) tunnel association is configured, Cloudflare can determine not only the tunnel health but also the health of the corresponding virtual or private IP targets.
Refer to [Set up Private Network Load Balancing for Public traffic to Tunnel](https://developers.cloudflare.com/load-balancing/private-network/public-to-tunnel/) for a detailed guide.
### Magic WAN
Private Network Load Balancing supports off-ramping traffic for Magic WAN tunnels, such as GRE, IPSec or CNI tunnels. For more information refer to the [Set up Private Network Load Balancing with Magic WAN](https://developers.cloudflare.com/load-balancing/private-network/magic-wan/).
***
## On-ramps
Private Network Load Balancing on-ramps, on the other hand, refer to secure paths between the end-user request and the Cloudflare network. Cloudflare Load Balancing supports traffic from [CDN](https://developers.cloudflare.com/cache/), [Spectrum](https://developers.cloudflare.com/spectrum/), [WARP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/) and [Magic WAN](https://developers.cloudflare.com/magic-wan/) and forward that traffic to a load balancer, and then egress to an endpoint behind any off-ramp (CDN/CNI/IPSec/GRE/Tunnel). Your traffic can ingress and egress by any on-ramp/off-ramp combination.
Note
When using [Spectrum](https://developers.cloudflare.com/spectrum/) as an on-ramp and [Magic WAN](https://developers.cloudflare.com/load-balancing/private-network/#magic-wan) as an off-ramp the [proxy protocol](https://developers.cloudflare.com/spectrum/how-to/enable-proxy-protocol/) setting in Spectrum is not supported.
***
## Use cases
* **Requests originating from the public Internet and directed to a private/internal service**: You can route requests from the Internet to your internal services on internal IPs - such as accounting or production automation systems - using [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/).
* **Intelligent traffic routing**: Benefit from failover for your private traffic and have the ability to monitor the health of these IP targets directly, rather than load balancing to a tunnel and only monitoring the health of the tunnel itself.
* **Host applications on non-standard ports**: Easily specify and route traffic to applications hosted on private IP addresses using non-standard ports, allowing greater flexibility in service configuration without requiring changes to existing infrastructure.
* **Public and Private Load Balancers**: Public LBs can direct Internet traffic to private IP addresses, supporting all L7 products like WAF and API Shield. Private LBs direct traffic originating from private networks to private IP addresses and require an on-ramp like WARP or Magic WAN.
---
title: Reference · Cloudflare Load Balancing docs
description: "See the following pages for more information about Cloudflare Load Balancing:"
lastUpdated: 2024-09-20T13:17:28.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/load-balancing/reference/
md: https://developers.cloudflare.com/load-balancing/reference/index.md
---
See the following pages for more information about Cloudflare Load Balancing:
* [Migration guides](https://developers.cloudflare.com/load-balancing/reference/migration-guides/)
* [Analytics](https://developers.cloudflare.com/load-balancing/reference/load-balancing-analytics/)
* [Regions API](https://developers.cloudflare.com/load-balancing/reference/region-mapping-api/)
* [Limitations](https://developers.cloudflare.com/load-balancing/reference/limitations/)
---
title: Reference architecture · Cloudflare Load Balancing docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/reference-architecture-external-link/
md: https://developers.cloudflare.com/load-balancing/reference-architecture-external-link/index.md
---
---
title: Troubleshooting · Cloudflare Load Balancing docs
description: "For more guidance related to common issues with load balancers,
refer to the following resources:"
lastUpdated: 2024-09-20T13:17:28.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/load-balancing/troubleshooting/
md: https://developers.cloudflare.com/load-balancing/troubleshooting/index.md
---
For more guidance related to common issues with load balancers, refer to the following resources:
* [Common error codes](https://developers.cloudflare.com/load-balancing/troubleshooting/common-error-codes/)
* [FAQs](https://developers.cloudflare.com/load-balancing/troubleshooting/load-balancing-faq/)
---
title: Concepts · Cloudflare Load Balancing docs
description: Review the following topics to learn more about the basic concepts
and components involved in Cloudflare Load Balancing.
lastUpdated: 2024-09-20T13:17:28.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/load-balancing/understand-basics/
md: https://developers.cloudflare.com/load-balancing/understand-basics/index.md
---
Review the following topics to learn more about the basic concepts and components involved in Cloudflare Load Balancing.
* [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/)
* [Traffic steering](https://developers.cloudflare.com/load-balancing/understand-basics/traffic-steering/)
* [How endpoints and pools become unhealthy](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/)
* [Proxy status](https://developers.cloudflare.com/load-balancing/understand-basics/proxy-modes/)
* [Session affinity](https://developers.cloudflare.com/load-balancing/understand-basics/session-affinity/)
* [Adaptive routing](https://developers.cloudflare.com/load-balancing/understand-basics/adaptive-routing/)
---
title: 404 - Page Not Found · Cloudflare Log Explorer docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/404/
md: https://developers.cloudflare.com/log-explorer/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Log Explorer API · Cloudflare Log Explorer docs
description: Configuration and Log searches are also available via a public API.
lastUpdated: 2025-10-22T13:43:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/api/
md: https://developers.cloudflare.com/log-explorer/api/index.md
---
Configuration and Log searches are also available via a public API.
## Authentication
Authentication with the API can be done via an API token or API key with an email. Refer to [Create API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) for further instructions.
For detailed information on permissions required for each Log Explorer feature, refer to the [Permissions](https://developers.cloudflare.com/log-explorer/#permissions) section.
## Query data
Log Explorer includes a SQL API for submitting queries.
For example, to find an HTTP request with a specific [Ray ID](https://developers.cloudflare.com/fundamentals/reference/cloudflare-ray-id/), use the following SQL query:
```bash
curl https://api.cloudflare.com/client/v4/zones/{zone_id}/logs/explorer/query/sql \
--header "Authorization: Bearer " \
--url-query query="SELECT clientRequestScheme, clientRequestHost, clientRequestMethod, edgeResponseStatus, clientRequestUserAgent FROM http_requests WHERE RayID = '806c30a3cec56817' LIMIT 1"
```
This command returns the following HTTP request details:
```json
{
"result": [
{
"clientrequestscheme": "https",
"clientrequesthost": "example.com",
"clientrequestmethod": "GET",
"clientrequestuseragent": "curl/7.88.1",
"edgeresponsestatus": 200
}
],
"success": true,
"errors": [],
"messages": []
}
```
As another example, you could find Cloudflare Access requests with selected columns from a specific timeframe by performing the following SQL query:
```bash
curl https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/explorer/query/sql \
--header "Authorization: Bearer " \
--url-query query="SELECT CreatedAt, AppDomain, AppUUID, Action, Allowed, Country, RayID, Email, IPAddress, UserUID FROM access_requests WHERE Date >= '2025-02-06' AND Date <= '2025-02-06' AND CreatedAt >= '2025-02-06T12:28:39Z' AND CreatedAt <= '2025-02-06T12:58:39Z'"
```
This command returns the following request details:
```json
{
"result": [
{
"createdat": "2025-01-14T18:17:55Z",
"appdomain": "example.com",
"appuuid": "a66b4ab0-ccdf-4d60-a6d0-54a59a827d92",
"action": "login",
"allowed": true,
"country": "us",
"rayid": "90fbb07c0b316957",
"email": "user@example.com",
"ipaddress": "1.2.3.4",
"useruid": "52859e81-711e-4de0-8b31-283336060e79"
}
],
"success": true,
"errors": [],
"messages": []
}
```
---
title: Changelog · Cloudflare Log Explorer docs
description: We've resolved a bug in Log Explorer that caused inconsistencies
between the custom SQL date field filters and the date picker dropdown.
Previously, users attempting to filter logs based on a custom date field via a
SQL query sometimes encountered unexpected results or mismatching dates when
using the interactive date picker.
lastUpdated: 2025-06-27T07:53:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/changelog/
md: https://developers.cloudflare.com/log-explorer/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/log-explorer.xml)
## 2025-11-13
**Fixed custom SQL date picker inconsistencies**
We've resolved a bug in Log Explorer that caused inconsistencies between the custom SQL date field filters and the date picker dropdown. Previously, users attempting to filter logs based on a custom date field via a SQL query sometimes encountered unexpected results or mismatching dates when using the interactive date picker.
This fix ensures that the custom SQL date field filters now align correctly with the selection made in the date picker dropdown, providing a reliable and predictable filtering experience for your log data. This is particularly important for users creating custom log views based on time-sensitive fields.
## 2025-11-13
**Log Explorer adds 14 new datasets**
We've significantly enhanced Log Explorer by adding support for 14 additional Cloudflare product datasets.
This expansion enables Operations and Security Engineers to gain deeper visibility and telemetry across a wider range of Cloudflare services. By integrating these new datasets, users can now access full context to efficiently investigate security incidents, troubleshoot application performance issues, and correlate logged events across different layers (like application and network) within a single interface. This capability is crucial for a complete and cohesive understanding of event flows across your Cloudflare environment.
The newly supported datasets include:
#### Zone Level
* `Dns_logs`
* `Nel_reports`
* `Page_shield_events`
* `Spectrum_events`
* `Zaraz_events`
#### Account Level
* `Audit Logs`
* `Audit_logs_v2`
* `Biso_user_actions`
* `DNS firewall logs`
* `Email_security_alerts`
* `Magic Firewall IDS`
* `Network Analytics`
* `Sinkhole HTTP`
* `ipsec_logs`
Note
`Auditlog` and `Auditlog_v2` datasets require `audit-log.read` permission for querying.
The `biso_user_actions` dataset requires either the `Super Admin` or `ZT PII` role for querying.
#### Example: Correlating logs
You can now use Log Explorer to query and filter with each of these datasets. For example, you can identify an IP address exhibiting suspicious behavior in the `FW_event` logs, and then instantly pivot to the `Network Analytics` logs or `Access` logs to see its network-level traffic profile or if it bypassed a corporate policy.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/) and the [Cloudflare Logs documentation](https://developers.cloudflare.com/logs/).
## 2025-11-11
**Resize your custom SQL window in Log Explorer**
We're excited to announce a quality-of-life improvement for Log Explorer users. You can now resize the custom SQL query window to accommodate longer and more complex queries.
Previously, if you were writing a long custom SQL query, the fixed-size window required excessive scrolling to view the full query. This update allows you to easily drag the bottom edge of the query window to make it taller. This means you can view your entire custom query at once, improving the efficiency and experience of writing and debugging complex queries.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/).
## 2025-11-04
**Log Explorer now supports query cancellation**
We're excited to announce that Log Explorer users can now cancel queries that are currently running.
This new feature addresses a common pain point: waiting for a long, unintended, or misconfigured query to complete before you can submit a new, correct one. With query cancellation, you can immediately stop the execution of any undesirable query, allowing you to quickly craft and submit a new query, significantly improving your investigative workflow and productivity within Log Explorer.
## 2025-11-04
**Log Explorer now shows query result distribution**
We're excited to announce a new feature in Log Explorer that significantly enhances how you analyze query results: the Query results distribution chart.
This new chart provides a graphical distribution of your results over the time window of the query. Immediately after running a query, you will see the distribution chart above your result table. This visualization allows Log Explorer users to quickly spot trends, identify anomalies, and understand the temporal concentration of log events that match their criteria. For example, you can visually confirm if a spike in traffic or errors occurred at a specific time, allowing you to focus your investigation efforts more effectively. This feature makes it faster and easier to extract meaningful insights from your vast log data.
The chart will dynamically update to reflect the logs matching your current query.
## 2025-09-11
**Contextual pivots**
Directly from [Log Search](https://developers.cloudflare.com/log-explorer/log-search/) results, customers can pivot to other parts of the Cloudflare dashboard to immediately take action as a result of their investigation.
From the `http_requests` or `fw_events` dataset results, right click on an IP Address or JA3 Fingerprint to pivot to the Investigate portal to lookup the reputation of an IP address or JA3 fingerprint.

Easily learn about error codes by linking directly to our documentation from the **EdgeResponseStatus** or **OriginResponseStatus** fields.

From the `gateway_http` dataset, click on a **policyid** to link directly to the Zero Trust dashboard to review or make changes to a specific Gateway policy.

## 2025-09-11
**New results table view**
The results table view of **Log Search** has been updated with additional functionality and a more streamlined user experience. Users can now easily:
* Remove/add columns.
* Resize columns.
* Sort columns.
* Copy values from any field.

## 2025-09-03
**Logging headers and cookies using custom fields**
[Log Explorer](https://developers.cloudflare.com/log-explorer/) now supports logging and filtering on header or cookie fields in the [`http_requests` dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/).
Create a custom field to log desired header or cookie values into the `http_requests` dataset and Log Explorer will import these as searchable fields. Once configured, use the custom SQL editor in Log Explorer to view or filter on these requests.

For more details, refer to [Headers and cookies](https://developers.cloudflare.com/log-explorer/log-search/#headers-and-cookies).
## 2025-08-15
**Extended retention**
Customers can now rely on Log Explorer to meet their log retention compliance requirements.
Contract customers can choose to store their logs in Log Explorer for up to two years, at an additional cost of $0.10 per GB per month. Customers interested in this feature can contact their account team to have it added to their contract.
## 2025-07-09
**Usage tracking**
[Log Explorer](https://developers.cloudflare.com/log-explorer/) customers can now monitor their data ingestion volume to keep track of their billing. Monthly usage is displayed at the top of the [Log Search](https://developers.cloudflare.com/log-explorer/log-search/) and [Manage Datasets](https://developers.cloudflare.com/log-explorer/manage-datasets/) screens in Log Explorer.

## 2025-06-18
**Log Explorer is GA**
[Log Explorer](https://developers.cloudflare.com/log-explorer/) is now GA, providing native observability and forensics for traffic flowing through Cloudflare.
Search and analyze your logs, natively in the Cloudflare dashboard. These logs are also stored in Cloudflare's network, eliminating many of the costs associated with other log providers.

With Log Explorer, you can now:
* **Monitor security and performance issues with custom dashboards** – use natural language to define charts for measuring response time, error rates, top statistics and more.
* **Investigate and troubleshoot issues with Log Search** – use data type-aware search filters or custom sql to investigate detailed logs.
* **Save time and collaborate with saved queries** – save Log Search queries for repeated use or sharing with other users in your account.
* **Access Log Explorer at the account and zone level** – easily find Log Explorer at the account and zone level for querying any dataset.
For help getting started, refer to [our documentation](https://developers.cloudflare.com/log-explorer/).
---
title: Custom dashboards · Cloudflare Log Explorer docs
description: Custom dashboards allow you to create tailored dashboards to
monitor application security, performance, and usage. You can create monitors
for ongoing monitoring of a previous incident, use them to identify indicators
of suspicious activity, and access templates to help you get started.
lastUpdated: 2025-09-03T17:40:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/custom-dashboards/
md: https://developers.cloudflare.com/log-explorer/custom-dashboards/index.md
---
Custom dashboards allow you to create tailored dashboards to monitor application security, performance, and usage. You can create monitors for ongoing monitoring of a previous incident, use them to identify indicators of suspicious activity, and access templates to help you get started.
Note
Enterprise customers can create up to 100 dashboards.
Customers on Pro and Business plans can create up to 5 dashboards.
Dashboards provide a visual interface that displays key metrics and analytics, helping you monitor and analyze data efficiently. Different dashboards serve different purposes. For example, a security dashboard tracks attack attempts and threats, a performance dashboard monitors API latency and uptime, and a usage dashboard analyzes traffic patterns and user behavior.
Different metrics serve distinct roles in providing insights into your application's performance. For example, total HTTP requests offer an overview of traffic volume, while average response time helps assess application speed. Additionally, usage metrics such as traffic patterns and user behavior provide insight into how users interact with your application. These metrics together enable you to spot trends, identify problems, and make informed, data-driven decisions.
## Create a new dashboard
To create a new dashboard, go to the **Log Explorer** > **Dashboards** page.
[Go to **Custom dashboards**](https://dash.cloudflare.com/?to=/:account/log-explorer/dashboards)
When creating a dashboard, you have two options: building one from scratch or using a pre-designed template.
* A **templates** provide a faster way to set up a dashboard with commonly used metrics and charts. They are useful for standard use cases, such as monitoring security threats, API performance, or bot traffic. Templates help you get started quickly while still allowing modifications to fit your requirements.
* On the other hand, **from-scratch dashboard** gives you full control over its structure, allowing you to choose the exact datasets, metrics, and visualizations that fit your needs. This approach is ideal if you have specific monitoring goals or need a highly customized view of your data.
Choosing between these options depends on whether you need a quick setup with predefined insights or a fully customized dashboard tailored to your unique analysis needs.
### Create a dashboard from scratch
When creating a dashboard from scratch, select the option **Create new**. You can follow the instructions in the following sections to start adding charts to your dashboard.
#### Create a new chart
To create a new chart, select **Add chart**. There are two ways to create a chart:
* **Use a prompt**: Enter a query like `Compare status code ranges over time.` The AI model decides the most appropriate visualization and constructs your chart configuration.
* **Customize your chart**: Select the chart elements manually, including the chart type, title, dataset to query, metrics, and filters. This option gives you full control over your chart's structure.
Refer to the following sections for more information about the charts, datasets, fields, metrics, and filters available.
##### Chart types
The available chart types include:
* **Timeseries**: Displays trends over time, enabling comparisons across multiple series.
* **Categorical**: Compares proportions across different series.
* **Stat**: Highlights a single value, showing its delta and sparkline for quick insights.
* **Percentage**: Represents one value as a percentage of another.
* **Top N**: Identifies the highest-ranking values for a given attribute.
##### Datasets and metrics
The available metrics and filters vary based on the dataset you want to use. For example, when using the HTTP Requests dataset, you can select **origin response duration** as a metric. You can then choose your preferred aggregation method for that metric, such as total, median, or quantiles. The following table outlines the datasets, fields, and available metrics:
| Dataset | Field | Definition | Metrics |
| - | - | - | - |
| HTTP Requests | Requests | The number of requests sent by a client to a server over the HTTP protocol. | Total |
| | DNS Response Time | The time taken for a DNS query to be resolved, measured from when a request is made to when a response is received. | Total, Average, Median, 95th percentile, 99th percentile |
| | Time to First Byte | The duration from when a request is made to when the first byte of the response is received from the server. | Total, Average, Median, 95th percentile, 99th percentile |
| | Bytes returned to the Client | The amount of data (in bytes) sent from the server to the client in response to requests. | Total, Average, Median, 95th percentile, 99th percentile |
| | Number of visits | Unique visits or sessions to a website or application. | Total |
| | Origin response duration | The time taken by the origin server to process and respond to a request. | Total, Average, Median, 95th percentile, 99th percentile |
| Security Events | Security events | Actions taken by Application Security products such as WAF and Bot Management. | Total |
##### Filters
You can also adjust the scope of your analytics by entering filter conditions. This allows you to focus on the most relevant data.
1. Select **Add filter**.
2. Select a **field**, an **operator**, and a **value**. For example, to filter events by source IP address, select the *Source IP* field, select the *equals* operator, and enter the IP address.
3. Select **Apply**.
### Create a dashboard from a template
Alternatively, you can choose to create your dashboard using a pre-designed dashboard template. The templates available are:
* **Bot monitoring**: Allows you to identify automated traffic accessing your website.
* **API Security**: Allows you to monitor data transfers and exceptions for API endpoints in your application.
* **Account takeover**: Allows you to monitor login attempts, usage of leaked credentials, and account takeover attacks.
* **API Performance**: Allows you to view timing data for API endpoints in your application, along with error rates.
* **Performance monitoring**: Allows you to identify slow hosts and paths on your origin server, and view time to first byte metrics over time.
Choose one of the templates and select **Use template**.
## Edit a dashboard or chart
After creating your dashboard, to view your saved dashboards, select **Back to all dashboards** to access the full list. Regardless of the way you choose to create your dashboard, you can always edit existing charts and add new ones as needed.
## Further analysis
For each chart, you can:
* Review related traffic in [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/).
* Explore detailed logs in [Log Search](https://developers.cloudflare.com/log-explorer/log-search/).
This ensures deeper insights into your application's security, performance, and usage patterns.
---
title: FAQ · Cloudflare Log Explorer docs
description: Find answers to common questions about Log Explorer.
lastUpdated: 2025-10-09T09:19:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/faq/
md: https://developers.cloudflare.com/log-explorer/faq/index.md
---
## Which fields (or columns) are available for querying?
All fields listed in [Datasets](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/) for the [supported datasets](https://developers.cloudflare.com/log-explorer/manage-datasets/#supported-datasets) are viewable in Log Explorer.
## Why does my query not complete or time out?
Log Explorer performs best when query parameters focus on narrower ranges of time. You may experience query timeouts when your query would return a large quantity of data. Consider refining your query to improve performance.
## Why do I not see any logs in my queries after enabling the dataset?
Log Explorer starts ingesting logs from the moment you enable the dataset. It will not display logs for events that occurred before the dataset was enabled. Make sure that new events have been generated since enabling the dataset, and check again.
## My query returned an error. How do I figure out what went wrong?
We are actively working on improving error codes. If you receive a generic error, check your SQL syntax (if you are using the custom SQL feature), and make sure you have included a date and a limit. If the query still fails it is likely timing out. Try refining your filters.
## Where is the data stored?
The data is stored in Cloudflare R2. Each Log Explorer dataset is stored on a per-customer level, similar to Cloudflare D1, ensuring that your data is kept separate from that of other customers. In the future, this single-tenant storage model will provide you with the flexibility to create your own retention policies and decide in which regions you want to store your data.
## Does Log Explorer support Customer Metadata Boundary?
Customer Metadata Boundary is currently not supported for Log Explorer.
## Are there any constraints on the log volume that Log Explorer can support?
We are continually scaling the Log Explorer data platform. At present, Log Explorer supports log ingestion rates of up to 50,000 records per second. If your needs exceed this, contact your account team.
## How is Log Explorer different from Logpush? Do I need both?
Log Explorer allows you to search and analyze your Cloudflare logs directly in the dashboard or via API. [Logpush](https://developers.cloudflare.com/logs/logpush/), on the other hand, delivers raw logs to third-party SIEMs or storage systems. You generally do not need both, but some customers choose to use Log Explorer for quick investigation and Logpush for long-term storage or integration with other tools.
## Is there a free version or trial of Log Explorer?
Log Explorer is available as a paid add-on for any Application Services or Zero Trust purchase. There is no free version at this time.
## How is Log Explorer billed?
Log Explorer billing is based on the volume of logs indexed and stored, measured in gigabytes (GB). Your charges scale with the amount of log data you choose to retain in Log Explorer. Unlike query-based billing models (for example, BigQuery), charges are not based on how often you search or scan your data. Once logs are ingested and stored, you can query them without additional cost.
## Are logs from attack traffic included in my Log Explorer usage?
Yes. In general, Log Explorer bills based on the total volume of logs ingested and stored, including attack traffic. Since these logs are often critical for investigating security incidents, they are treated the same as all other log data.
However, logs generated from Layer 7 (L7) DDoS attack traffic are not ingested by default and therefore do not count toward your Log Explorer usage.
## How does Log Explorer store data in R2, and why do I not see it in my own R2 bucket?
Log Explorer uses Cloudflare Logpush and R2 behind the scenes to stream and store logs. For technical and performance reasons, the data is stored in internal, customer-specific R2 buckets managed by Cloudflare. These buckets are single-tenant to keep your data isolated, but they are not visible in your account's R2 interface. You are not billed separately for this storage — it is included in your Log Explorer usage.
## Are Custom Dashboards based on R2 Log Explorer data, or on GraphQL?
Custom Dashboards currently run on [GraphQL](https://developers.cloudflare.com/analytics/graphql-api/sampling/). Over time, this will evolve to include deeper integration between the two features, such as building charts directly from logs.
## How can I track my Log Explorer usage?
Your monthly usage is displayed at the top of the Log Search and Manage Datasets dashboard sections within Log Explorer.
## How do I turn off Log Explorer?
Use the Manage Datasets feature to enable or disable ingestion for individual datasets and zones.
1. In the Cloudflare dashboard, go to the **Manage Account** > **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Under **Subscriptions**, find the Log Explorer subscription, and select **Cancel**.
---
title: Log Search · Cloudflare Log Explorer docs
description: Log Explorer enables you to store and explore your Cloudflare logs
directly within the Cloudflare dashboard or API, giving you visibility into
your logs without the need to forward them to third-party services. Logs are
stored on Cloudflare's global network using the R2 object storage platform and
can be queried via the dashboard or SQL API.
lastUpdated: 2025-12-05T12:51:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/log-search/
md: https://developers.cloudflare.com/log-explorer/log-search/index.md
---
Log Explorer enables you to store and explore your Cloudflare logs directly within the Cloudflare dashboard or API, giving you visibility into your logs without the need to forward them to third-party services. Logs are stored on Cloudflare's global network using the R2 object storage platform and can be queried via the dashboard or SQL API.
## Use Log Explorer
You can filter and view your logs via the Cloudflare dashboard or the API.
1. In the Cloudflare dashboard, go to the **Log Explorer** > **Log Search** page.
[Go to **Log search**](https://dash.cloudflare.com/?to=/:account/log-explorer/log-search)
2. Select the **Dataset** you want to use and in **Columns** select the dataset fields. If you selected a zone scoped dataset, select the zone you would like to use.
3. Enter a **Limit**. A limit is the maximum number of results to return, for example, 50.
4. Select the **Time period** from which you want to query, for example, the previous 12 hours.
5. Select **Add filter** to create your query. Select a **Field**, an **Operator**, and a **Value**, then select **Apply**.
6. A query preview is displayed. Select **Custom SQL** to change the query.
7. Select **Run query** when you are done. The results are displayed below within the **Query results** section.
For example, to find an HTTP request with a specific [Ray ID](https://developers.cloudflare.com/fundamentals/reference/cloudflare-ray-id/), go to **Custom SQL**, and enter the following SQL query:
```sql
SELECT
clientRequestScheme,
clientRequestHost,
clientRequestMethod,
edgeResponseStatus,
clientRequestUserAgent
FROM http_requests
WHERE RayID = '806c30a3cec56817'
LIMIT 1
```
As another example, to find Cloudflare Access requests with selected columns from a specific timeframe you could perform the following SQL query:
```sql
SELECT
CreatedAt,
AppDomain,
AppUUID,
Action,
Allowed,
Country,
RayID,
Email,
IPAddress,
UserUID
FROM access_requests
WHERE Date >= '2025-02-06' AND Date <= '2025-02-06' AND CreatedAt >= '2025-02-06T12:28:39Z' AND CreatedAt <= '2025-02-06T12:58:39Z'
```
### Headers and cookies
To query request headers, response headers, and cookies you must first enable logging for these fields using [Custom fields](https://developers.cloudflare.com/logs/logpush/logpush-job/custom-fields/). Configure the list of custom fields using the API or the dashboard; there is no need to modify the Logpush job itself.
The example below shows how to query HTTP requests by date, timestamp, client country, and a custom request header. Be sure to log the specific headers or cookies you plan to query in advance.
```bash
SELECT clientip, clientrequesthost, clientrequestmethod, edgeendtimestamp, edgestarttimestamp, rayid, clientcountry, requestheaders
FROM http_requests
WHERE Date >= '2025-07-17'
AND Date <= '2025-07-17'
AND edgeendtimestamp >= '2025-07-17T07:54:19Z'
AND edgeendtimestamp <= '2025-07-18T07:54:19Z'
AND clientcountry = 'us'
AND requestheaders."x-test-header" like '%654AM%';
```
### Save queries
After selecting all the fields for your query, you can save it by selecting **Save query**. Provide a name and description to help identify it later. To view your saved and recent queries, select **Queries** — they will appear in a side panel where you can insert a new query, or delete any query.
## Integration with Security Analytics
You can also access the Log Explorer dashboard directly from the [Security Analytics dashboard](https://developers.cloudflare.com/waf/analytics/security-analytics/#logs). When doing so, the filters you applied in Security Analytics will automatically carry over to your query in Log Explorer.
## Optimize your queries
All the tables supported by Log Explorer contain a special column called `date`, which helps to narrow down the amount of data that is scanned to respond to your query, resulting in faster query response times. The value of `date` must be in the form of `YYYY-MM-DD`. For example, to query logs that occurred on October 12, 2023, add the following to your `WHERE` clause: `date = '2023-10-12'`. The column supports the standard operators of `<`, `>`, and `=`.
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/login) and select your account.
2. Go to **Log Explorer** > **Log Search** > **Custom SQL**.
3. Enter the following SQL query:
```sql
SELECT
clientip,
clientrequesthost,
clientrequestmethod,
clientrequesturi,
edgeendtimestamp,
edgeresponsestatus,
originresponsestatus,
edgestarttimestamp,
rayid,
clientcountry,
clientrequestpath,
date
FROM
http_requests
WHERE
date = '2023-10-12' LIMIT 500
```
### Additional query optimization tips
* Narrow your query time frame. Focus on a smaller time window to reduce the volume of data processed. This helps avoid querying excessive amounts of data and speeds up response times.
* Omit `ORDER BY` and `LIMIT` clauses. These clauses can slow down queries, especially when dealing with large datasets. For queries that return a large number of records, reduce the time frame instead of limiting to the newest `N` records from a broader time frame.
* Select only necessary columns. For example, replace `SELECT *` with the list of specific columns you need. You can also use `SELECT RayId` as a first iteration and follow up with a query that filters by the Ray IDs to retrieve additional columns. Additionally, you can use `SELECT COUNT(*)` to probe for time frames with matching records without retrieving the full dataset.
---
title: Manage datasets · Cloudflare Log Explorer docs
description: Log Explorer allows you to enable or disable which datasets are
available to query in Log Search.
lastUpdated: 2025-11-18T15:34:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/manage-datasets/
md: https://developers.cloudflare.com/log-explorer/manage-datasets/index.md
---
Log Explorer allows you to enable or disable which datasets are available to query in Log Search.
## Supported datasets
Log Explorer currently supports the following datasets:
### Zone level
* [HTTP Requests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) (`http_requests`)
* [Firewall Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/firewall_events/) (`firewall_events`)
* [DNS Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/dns_logs/) (`dns_logs`)
* [NEL Reports](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/nel_reports/) (`nel_reports`)
* [Page Shield Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/page_shield_events/) (`page_shield_events`)
* [Spectrum Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/spectrum_events/) (`spectrum_events`)
* [Zaraz Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/zaraz_events/) (`zaraz_events`)
### Account level
* [Access requests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/access_requests/) (`access_requests`)
* [CASB findings](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/casb_findings/) (`casb_findings`)
* [Device posture results](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/device_posture_results/) (`device_posture_results`)
* [Gateway DNS](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/gateway_dns/) (`gateway_dns`)
* [Gateway HTTP](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/gateway_http/) (`gateway_http`)
* [Gateway Network](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/gateway_network/) (`gateway_network`)
* [Zero Trust Network Session Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/zero_trust_network_sessions/) (`zero_trust_network_sessions`)
* [Audit Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/audit_logs/) (`audit_logs`)
* [Audit\_logs\_v2](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/audit_logs_v2/) (`audit_logs_v2`)
* [Browser Isolation User Actions](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/biso_user_actions/) (`biso_user_actions`)
* [DNS firewall logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dns_firewall_logs/) (`dns_firewall_logs`)
* [Email security alerts](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/email_security_alerts/) (`email_security_alerts`)
* [Magic IDS Detections](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/magic_ids_detections/) (`magic_ids_detections`)
* [Network Analytics](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/network_analytics_logs/) (`network_analytics_logs`)
* [Sinkhole HTTP Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/sinkhole_http_logs/) (`sinkhole_http_logs`)
* [IP Sec Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/ipsec_logs/) (`ipsec_logs`)
## Enable Log Explorer
In order for Log Explorer to begin storing logs, you need to enable the desired datasets. You can do this via the dashboard or the API.
1. In the Cloudflare dashboard, go to the **Log Explorer** > **Manage datasets** page.
[Go to **Manage datasets**](https://dash.cloudflare.com/?to=/:account/log-explorer/manage-sources)
2. Select **Add dataset** to select the datasets you want to query.
3. Choose a dataset and then a zone. Then, select **Add**. You can always return to this page to enable more datasets or manage your existing ones.
Note
It may take a few minutes for the logs to become available for querying.
If you are using the API, Use the Log Explorer API to enable Log Explorer for each dataset you wish to store. It may take a few minutes after a log stream is enabled before you can view the logs.
The following `curl` command is an example for enabling the zone-level dataset `http_requests`, as well as the expected response when the command succeeds.
```bash
curl https://api.cloudflare.com/client/v4/zones/{zone_id}/logs/explorer/datasets \
--header "Authorization: Bearer " \
--json '{
"dataset": "http_requests"
}'
```
```json
{
"result": {
"dataset": "http_requests",
"object_type": "zone",
"object_id": "",
"created_at": "2025-06-03T14:33:16Z",
"updated_at": "2025-06-03T14:33:16Z",
"dataset_id": "01973635f7e273a1964a02f4d4502499",
"enabled": true
},
"success": true,
"errors": [],
"messages": []
}
```
To enable an account-level dataset, replace `zones/{zone_id}` with `accounts/{account_id}` in the `curl` command. For example:
```bash
curl https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/explorer/datasets \
--header "Authorization: Bearer " \
--json '{
"dataset": "access_requests"
}'
```
---
title: 404 - Page Not Found · Cloudflare Logs docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/404/
md: https://developers.cloudflare.com/logs/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Audit Logs MCP server · Cloudflare Logs docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/auditlogs-mcp-server/
md: https://developers.cloudflare.com/logs/auditlogs-mcp-server/index.md
---
---
title: SQL queries supported · Cloudflare Log Explorer docs
description: This page outlines the SQL features supported by Log Explorer,
including common aggregation functions, expressions, and query clauses.
lastUpdated: 2025-07-28T13:09:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/sql-queries/
md: https://developers.cloudflare.com/log-explorer/sql-queries/index.md
---
This page outlines the SQL features supported by Log Explorer, including common aggregation functions, expressions, and query clauses.
The diagram below illustrates the general shape of a valid query supported in Log Explorer. It shows how standard SQL clauses — such as `SELECT`, `WHERE`, `GROUP BY`, and `ORDER BY` — can be composed to form supported queries.
Examples of queries include:
* `SELECT * FROM table WHERE (a = 1 OR b = "hello") AND c < 25.89`
* `SELECT a, b, c FROM table WHERE d >= "GB" LIMIT 10`
Note
* A default `LIMIT` of 10,000 is applied if the `LIMIT` clause is omitted.
* The `WHERE` clause supports up to 25 predicates, which can be grouped using parentheses.
### SQL Clauses in detail
The following SQL clauses define the structure and logic of queries in Log Explorer:
* `SELECT` - The `SELECT` clause specifies the columns that you want to retrieve from the database tables. It can include individual column names, expressions, or even wildcard characters to select all columns.
* `FROM` - The `FROM` clause specifies the tables from which to retrieve data. It indicates the source of the data for the `SELECT` statement.
* `WHERE` - The `WHERE` clause filters the rows returned by a query based on specified conditions. It allows you to specify conditions that must be met for a row to be included in the result set.
* `SELECT DISTINCT` - Removes duplicate rows from the result set.
* `GROUP BY` - Groups rows for aggregation. The `GROUP BY` clause is used to group rows that have the same values into summary rows.
* `ORDER BY` - Sorts the result set. The `ORDER BY` clause is used to sort the result set by one or more columns in ascending or descending order.
* `LIMIT` - Restricts the number of rows returned. The `LIMIT` clause is used to constrain the number of rows returned by a query. It is often used in conjunction with the `ORDER BY` clause to retrieve the top `N` rows or to implement pagination.
* `OFFSET` - Skips a specified number of rows before returning results.
The sections that follow break down the remaining components shown in the diagram — such as aggregation functions, string and numeric expressions, and supported operators — in more detail.
## Functions
Log Explorer supports a range of SQL functions to transform, evaluate, or summarize data. These include scalar and aggregation functions.
### Scalar functions
These help manipulate or evaluate values (often strings):
* `ARRAY_CONTAINS(array, element)` – Checks if the array contains the element.
Example
`ARRAY_CONTAINS(['US', 'CA'], ClientCountry)`
Returns rows where `ClientCountry` is either `US` or `CA`.
* `SUBSTRING(string, from_number, for_number)` – Extracts part of a string.
Example
`SUBSTRING(ClientRequestPath, 0, 5)`
Extracts the first `5` characters from `ClientRequestPath`.
* `LOWER(string)` – Converts to lowercase.
Example
`LOWER(ClientRequestUserAgent)`
Converts the user agent string to lowercase.
* `UPPER(string)` – Converts to uppercase.
Example
`UPPER(ClientCountry)`
Converts the country code to uppercase.
### Aggregation functions
Used to perform calculations on sets of rows:
* `SUM(expression)` – Total of values.
Example
`SUM(ClientRequestBytes)`
Adds up the total number of bytes requested by clients.
* `MIN(expression)` – Minimum value.
Example
`MIN(OriginResponseDurationMs)`
Finds the shortest response time from origin servers.
* `MAX(expression)` – Maximum value.
Example
`MAX(OriginResponseDurationMs)`
Finds the longest response time.
* `COUNT(expression)` – Number of rows (can be all rows or non-null values).
Example
`COUNT(ClientRequestUserAgent)`
Counts how many rows have a user agent value.
* `COUNT(DISTINCT expression)` – Number of distinct non-null values.
Example
`COUNT(DISTINCT ClientIP)`
Counts how many unique client IPs made requests.
* `AVG(expression)` – Average of numeric values.
Example
`AVG(OriginResponseDurationMs)`
Computes the average origin response time in milliseconds.
The diagram below represents the grammar for SQL expressions including scalar and aggregate functions.
## Expressions
Conditions or logic used in queries:
* `CASE WHEN` – Conditional logic (like if-else).
* `AS` – Alias for columns or tables.
* `LIKE` – Pattern matching.
* `IN (list)` – Checks if a value is in a list.
* `BETWEEN ... AND ...` – Checks if a value is within a range.
* `Unary operator` – Operates on one operand (for example, `-5`).
* `Binary operator` – Operates on two operands (for example, `5 + 3`).
* `Nested Expressions` – Expression wrapped with parentheses, like `( x > y )` or `( 1 )`.
* `Compound identifier` – Multi-part name (for example, `schema.table.column`).
* `Array` – A collection of values (supported differently across SQL dialects).
* `Literals` - represent values such as strings, numbers, or arrays.
The diagram below represents the grammar for SQL expressions, detailing the various forms an expression can take, including columns, literals, functions, operators, and aliases.
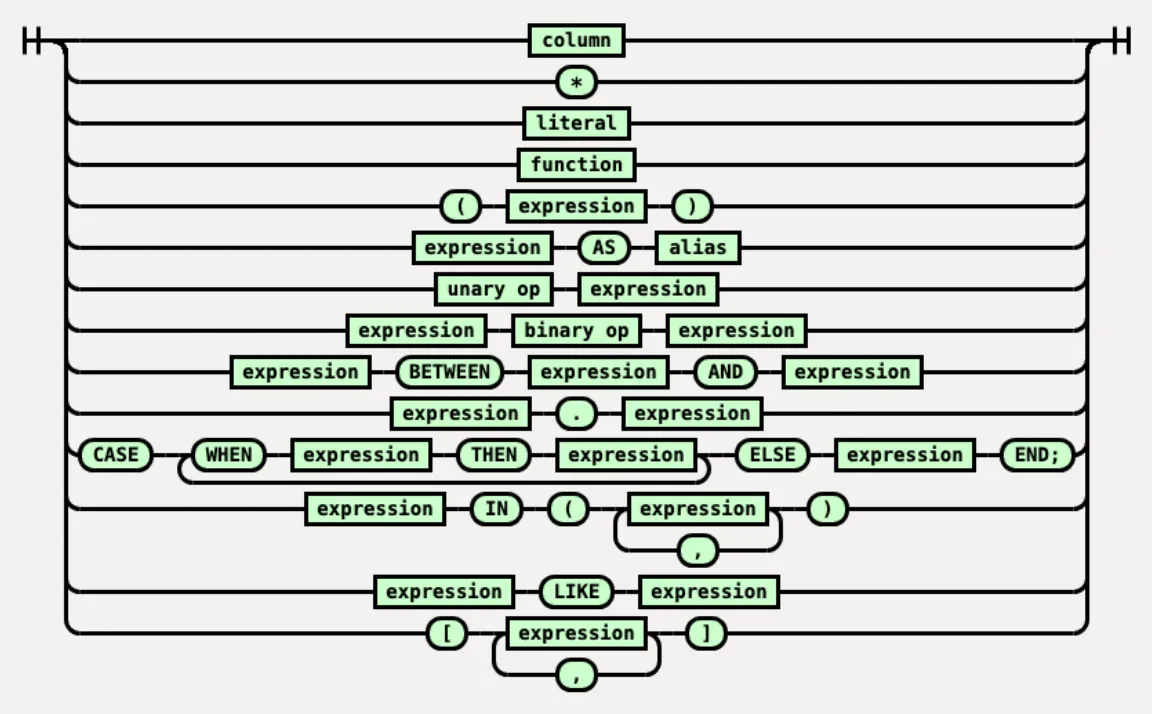
The diagram below defines the grammar for unary operators, which operate on a single operand (for example, negation or logical `NOT`):
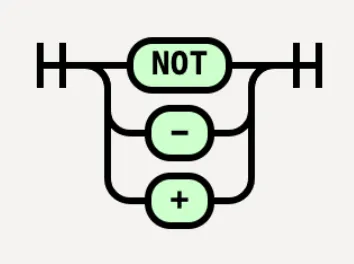
## Binary Operators
Used for arithmetic, comparison, logical operations:
* Arithmetic: `+`, `-`, `*`, `/`, `%` (modulo)
* Comparison: `>`, `<`, `>=`, `<=`, `=`, `!=` (or `<>`)\`
* Logical: `AND`, `OR`, `XOR`
* Bitwise: `&`, `|`, `^`, `>>`, `<<`
* String concat: `||`
---
title: Changelog · Cloudflare Logs docs
lastUpdated: 2025-06-02T11:14:31.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/logs/changelog/
md: https://developers.cloudflare.com/logs/changelog/index.md
---
---
title: FAQ · Cloudflare Logs docs
description: Below you will find answers to the most commonly asked questions
regarding Cloudflare Logs. If you cannot find the answer you are looking for,
go to the community page and post your question there.
lastUpdated: 2026-01-05T14:41:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/faq/
md: https://developers.cloudflare.com/logs/faq/index.md
---
Below you will find answers to the most commonly asked questions regarding Cloudflare Logs. If you cannot find the answer you are looking for, go to the [community page](https://community.cloudflare.com/) and post your question there.
***
## General FAQ
For general questions about Logs.
[General FAQ ❯](https://developers.cloudflare.com/logs/faq/general-faq/)
## Logpush
For questions about Logpush.
[Logpush ❯](https://developers.cloudflare.com/logs/faq/logpush/)
## Instant Logs
For questions about Instant Logs.
[Instant Logs ❯](https://developers.cloudflare.com/logs/faq/instant-logs/)
## Logpull API
For questions about the Logpull API.
[Logpull API ❯](https://developers.cloudflare.com/logs/faq/logpull-api/)
## Common calculations
For questions about common calculations.
[Common calculations ❯](https://developers.cloudflare.com/logs/faq/common-calculations/)
## Random hostnames
For questions about unexpected hostnames in HTTP logs for partial zones.
[Random hostnames ❯](https://developers.cloudflare.com/logs/faq/random-hostnames-partial-zones/)
---
title: Glossary · Cloudflare Logs docs
description: Review the definitions for terms used across Cloudflare's Logs documentation.
lastUpdated: 2025-07-16T10:06:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/glossary/
md: https://developers.cloudflare.com/logs/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Logs documentation.
| Term | Definition |
| - | - |
| debugging | The process of identifying and resolving errors or issues within software applications or systems, often facilitated by analyzing log data. |
| deprecation | Deprecation in software development involves officially labeling a feature as outdated. While a deprecated software feature remains within the software, users are warned and encouraged to adopt alternatives. Eventually, deprecated features may be removed. This approach ensures backward compatibility and gives programmers time to update their code. |
| event | An occurrence or happening that is significant and worthy of being recorded in a log. |
| log | A chronological record of events, actions, or transactions, typically used for tracking and troubleshooting purposes. |
| log file | A file containing a collection of log entries, usually stored in a structured or semi-structured format. |
| logging | The process of recording events, actions, or transactions in a log. |
| timestamp | A data field indicating the date and time when an event occurred, often used for sequencing and analysis. |
---
title: Instant Logs · Cloudflare Logs docs
description: Instant Logs allows Cloudflare customers to access a live stream of
the traffic for their domain from the Cloudflare dashboard or from a
command-line interface (CLI). Seeing data in real time allows you to
investigate an attack, troubleshoot, debug or test out changes made to your
network. Instant Logs is lightweight, simple to use and does not require any
additional setup.
lastUpdated: 2025-12-16T16:50:54.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/instant-logs/
md: https://developers.cloudflare.com/logs/instant-logs/index.md
---
Instant Logs allows Cloudflare customers to access a live stream of the traffic for their domain from the Cloudflare dashboard or from a command-line interface (CLI). Seeing data in real time allows you to investigate an attack, troubleshoot, debug or test out changes made to your network. Instant Logs is lightweight, simple to use and does not require any additional setup.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | Yes | Yes |
## Instant Logs via Cloudflare Dashboard
1. In the Cloudflare dashboard, go to the **Instant Logs** page.
[Go to **Instant Logs**](https://dash.cloudflare.com/?to=/:account/:zone/analytics/instant-logs)
2. Select **Start streaming**.
3. (optional) Select **Add filter** to narrow down the events to be shown.
Fields supported in our [HTTP requests dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) can be used when you add filters. Some fields with additional subscriptions required are not supported in the dashboard, you will need to use CLI instead.
Once a filter is selected and the stream has started, only log lines that match the filter criteria will appear. Filters are not applied retroactively to logs already showing in the dashboard.
## Instant Logs via CLI
### 1. Create an Instant Logs Job
Create a session by sending a `POST` request to the Instant Logs job endpoint with the following parameters:
* **Fields** - List any field available in the [HTTP requests dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/).
* **Sample** - The sample parameter is the sample rate of the records set by the client: `"sample": 1` is 100% of records `"sample": 10` is 10% and so on.
Note
Instant Logs has a maximum data rate supported. For high volume domains, we sample server side as indicated in the `"sampleInterval"` parameter returned in the logs.
* **Filters** - Use filters to drill down into specific events. Filters consist of three parts: key, operator and value.
All supported operators can be found in the [Filters](https://developers.cloudflare.com/logs/logpush/logpush-job/filters/) page.
Below we have three examples of filters:
```bash
# Filter when client IP country is not Canada:
"filter": "{\"where\":{\"and\":[{\"key\":\"ClientCountry\",\"operator\":\"neq\",\"value\":\"ca\"}]}}"
```
```bash
# Filter when the status code returned from Cloudflare is either 200 or 201:
"filter": "{\"where\":{\"and\":[{\"key\":\"EdgeResponseStatus\",\"operator\":\"in\",\"value\":[200,201]}]}}"
```
```bash
# Filter when the request path contains "/static" and the request hostname is "example.com":
"filter": "{\"where\":{\"and\":[{\"key\":\"ClientRequestPath\",\"operator\":\"contains\",\"value\":\"/static\"}, {\"where\":{\"and\":[{\"key\":\"ClientRequestHost\",\"operator\":\"eq\",\"value\":\"example.com\"}]}}"
```
Example request using cURL:
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Logs Read`
```bash
curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/logpush/edge/jobs" \
--request POST \
--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \
--json '{
"fields": "ClientIP,ClientRequestHost,ClientRequestMethod,ClientRequestURI,EdgeEndTimestamp,EdgeResponseBytes,EdgeResponseStatus,EdgeStartTimestamp,RayID",
"sample": 100,
"filter": "",
"kind": "instant-logs"
}'
```
Response:
The response will include a new field called **destination\_conf**. The value of this field is your unique WebSocket address that will receive messages from Cloudflare's global network.
```json
{
"errors": [],
"messages": [],
"result": {
"id": ,
"fields": "ClientIP,ClientRequestHost,ClientRequestMethod,ClientRequestURI,EdgeEndTimestamp,EdgeResponseBytes,EdgeResponseStatus,EdgeStartTimestamp,RayID",
"sample": 100,
"filter": "",
"destination_conf": "wss://logs.cloudflare.com/instant-logs/ws/sessions/",
"kind": "instant-logs"
},
"success": true
}
```
### 2. Connect to WebSocket
Using a CLI utility like [Websocat](https://github.com/vi/websocat), you can connect to the WebSocket and start immediately receiving logs.
```bash
websocat wss://logs.cloudflare.com/instant-logs/ws/sessions/
```
Response:
Once connected to the websocket, you will receive messages of line-delimited JSON.
### Angle Grinder
Now that you have a connection to Cloudflare's websocket and are receiving logs from Cloudflare's global network, you can start slicing and dicing the logs. A handy tool for this is [Angle Grinder](https://github.com/rcoh/angle-grinder). Angle Grinder lets you apply filtering, transformations and aggregations on stdin with first class JSON support. For example, to get the number of visitors from each country you can sum the number of events by the `ClientCountry` field.
```bash
awebsocat wss://logs.cloudflare.com/instant-logs/ws/sessions/ | agrind '* | json | sum(sampleInterval) by ClientCountry'
```
Response:
| **ClientCountry** | **\_sum** |
| - | - |
| pt | `4` |
| fr | `3` |
| us | `3` |
| om | `2` |
| ar | `1` |
| au | `1` |
## Datasets available
For the moment, `HTTP requests` is the only dataset supported. In the future, we will expand to other datasets.
## Export
You can download the table of logs that appears in the dashboard, in JSON format via the **Export** button.
## Limits
Instant Logs has three limits set in place:
* Only one active Instant Logs session per zone.
* Maximum session time is 60 minutes.
* If you stop listening to a socket for more than five minutes.
If either of these limits are reached, the logs stream will automatically stop.
## Connect with us
If you have any feature requests or notice any bugs, share your feedback directly with us by joining the [Cloudflare Developers community on Discord](https://discord.cloudflare.com).
---
title: Logpull · Cloudflare Logs docs
description: Cloudflare Logpull is a REST API for consuming request logs over
HTTP. These logs contain data related to the connecting client, the request
path through the Cloudflare network, and the response from the origin web
server. This data is useful for enriching existing logs on an origin server.
Logpull is available to customers on the Enterprise plan.
lastUpdated: 2025-07-16T14:37:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/logpull/
md: https://developers.cloudflare.com/logs/logpull/index.md
---
Cloudflare Logpull is a REST API for consuming request logs over HTTP. These logs contain data related to the connecting client, the request path through the Cloudflare network, and the response from the origin web server. This data is useful for enriching existing logs on an origin server. Logpull is available to customers on the Enterprise plan.
Warning
Logpull is considered a legacy feature and we recommend using [Logpush](https://developers.cloudflare.com/logs/logpush/) or [Logs Engine](https://developers.cloudflare.com/logs/r2-log-retrieval/) instead for better performance and functionality.
Review the following content to learn more about Logpull.
* [Understanding the basics](https://developers.cloudflare.com/logs/logpull/understanding-the-basics/)
* [Enabling log retention](https://developers.cloudflare.com/logs/logpull/enabling-log-retention/)
* [Requesting logs](https://developers.cloudflare.com/logs/logpull/requesting-logs/)
* [Additional details](https://developers.cloudflare.com/logs/logpull/additional-details/)
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | No | Yes |
### Limitation
Logpull is unavailable when the Customer Metadata Boundary (CMB) is set outside the US region. Specifically, it does not work when CMB is restricted to the EU-only setting. For more details, refer to the [Cloudflare Data Localization](https://developers.cloudflare.com/data-localization/) documentation.
---
title: Logpush · Cloudflare Logs docs
description: Logpush delivers logs in batches as quickly as possible, with no
minimum batch size, potentially delivering files more than once per minute.
This capability enables Cloudflare to provide information almost in real time,
in smaller file sizes.
lastUpdated: 2026-01-26T13:58:45.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/logpush/
md: https://developers.cloudflare.com/logs/logpush/index.md
---
Logpush delivers logs in batches as quickly as possible, with no minimum batch size, potentially delivering files more than once per minute. This capability enables Cloudflare to provide information almost in real time, in smaller file sizes.
The push frequency is automatic and cannot be adjusted—Cloudflare pushes logs in batches as soon as possible. However, users can configure the batch size [using the API](https://developers.cloudflare.com/logs/logpush/logpush-job/api-configuration/#max-upload-parameters) for improved control in case the log destination has specific requirements.
Important limitation
Logpush only pushes logs once as they become available and cannot backfill historical data. If your job is disabled or fails, logs generated during that period are permanently lost. This is why configuring [health notifications](https://developers.cloudflare.com/logs/logpush/logpush-health/) is essential for early detection of issues.
Logpush does not offer storage or search functionality for logs; its primary aim is to send logs as quickly as they arrive.
Cloudflare Logpush supports pushing logs to storage services, SIEMs, and log management providers via the Cloudflare dashboard or API.
Cloudflare aims to support additional services in the future. Interested in a particular service? Take this [survey](https://goo.gl/forms/0KpMfae63WMPjBmD2).
## Estimating log volume
Before setting up a Logpush job, you can estimate the total volume of data that will be pushed to your destination. The volume depends on your traffic, selected fields, and compression.
### Quick sizing for HTTP Requests
A quick sizing estimate for an [HTTP Requests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) dataset:
* \~100–250 bytes per request (compressed, depending on fields selected)
* 1M requests/day → \~100–250 MB/day
* 30M requests/month → \~3–7.5 GB/month
### Daily storage by traffic volume
* 100k req/day → \~25–50 MB/day
* 1M req/day → \~250–500 MB/day
* 10M req/day → \~2.5–5 GB/day
* 100M req/day → \~25–50 GB/day
These ranges reflect field selection, compression, and whether you include extra fields or [custom fields](https://developers.cloudflare.com/logs/logpush/logpush-job/custom-fields/). Other datasets (Firewall, Workers, Load Balancing) add volume separately.
For precise estimates, you can [sample your logs via Logpull](https://developers.cloudflare.com/logs/logpull/additional-details/#estimating-daily-data-volume) using a 1-hour sample.
## Limits
There is currently a max limit of **4 Logpush jobs per zone**. Trying to create a job once the limit has been reached will result in an error message: `creating a new job is not allowed: exceeded max jobs allowed`.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | No | Yes |
Note
Users without an Enterprise plan can still access [Workers Trace Events Logpush](https://developers.cloudflare.com/workers/observability/logs/logpush/) by subscribing to the [Workers Paid](https://developers.cloudflare.com/workers/platform/pricing/) plan.
---
title: Logpush MCP server · Cloudflare Logs docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/logpush-mcp-server/
md: https://developers.cloudflare.com/logs/logpush-mcp-server/index.md
---
---
title: Logs Engine · Cloudflare Logs docs
description: Logs Engine gives you the ability to store your logs in R2 and
query them directly.
lastUpdated: 2025-10-01T13:53:03.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/r2-log-retrieval/
md: https://developers.cloudflare.com/logs/r2-log-retrieval/index.md
---
Logs Engine gives you the ability to store your logs in R2 and query them directly.
Note
Logs Engine is going to be replaced by Log Explorer. For further details, consult the [Log Explorer](https://developers.cloudflare.com/log-explorer/) documentation and to request access, complete the [sign-up form](https://cloudflare.com/lp/log-explorer/).
## Store logs in R2
* Set up a [Logpush to R2](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/r2/) job.
* Create an [R2 access key](https://developers.cloudflare.com/r2/api/tokens/) with at least R2 read permissions.
* Ensure that you have Logshare read permissions.
* Alternatively, create a Cloudflare API token with the following permissions:
* Account scope
* Logs read permissions
## Query logs
You can use the API to query and download your logs by time range or [RayID](https://developers.cloudflare.com/fundamentals/reference/cloudflare-ray-id/).
## Authentication
The following headers are required for all API calls:
* `X-Auth-Email` - the Cloudflare account email address associated with the domain
* `X-Auth-Key` - the Cloudflare API key
Alternatively, API tokens with Logs edit permissions can also be used for authentication:
* `Authorization: Bearer `
### Required headers
In addition to the required authentication headers mentioned, the following headers are required for the API to access logs stored in your R2 bucket.
* `R2-access-key-id` (required) - [R2 Access Key Id](https://developers.cloudflare.com/r2/api/tokens/)
* `R2-secret-access-key` (required) - [R2 Secret Access Key](https://developers.cloudflare.com/r2/api/tokens/)
## List files
List relevant R2 objects containing logs matching the provided query parameters, using the endpoint `GET /accounts/{accountId}/logs/list`.
### Query parameters
* `start` (required) string (TimestampRFC3339) - Start time in RFC 3339 format, for example `start=2022-06-06T16:00:00Z`.
* `end` (required) string (TimestampRFC3339) - End time in RFC 3339 format, for example `end=2022-06-06T16:00:00Z`.
* `bucket` (required) string (Bucket) - R2 bucket name, for example `bucket=cloudflare-logs`.
* `prefix` string (Prefix) - R2 bucket prefix logs are stored under, for example `prefix=http_requests/example.com/{DATE}`.
* `limit` number (Limit) - Maximum number of results to return, for example `limit=100`.
## Retrieve logs by time range
Stream logs stored in R2 that match the provided query parameters, using the endpoint `GET /accounts/{accountId}/logs/retrieve`.
### Query parameters
* `start` (required) string (TimestampRFC3339) - Start time in RFC 3339 format, for example `start=2022-06-06T16:00:00Z`
* `end` (required) string (TimestampRFC3339) - End time in RFC 3339 format, for example `end=2022-06-06T16:00:00Z`
* `bucket` (required) string (Bucket) - R2 bucket name, for example `bucket=cloudflare-logs`
* `prefix` string (Prefix) - R2 bucket prefix logs are stored under, for example `prefix=http_requests/example.com/{DATE}`
### Example API request
```bash
curl --globoff "https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/retrieve?start=2022-06-01T16:00:00Z&end=2022-06-01T16:05:00Z&bucket=cloudflare-logs&prefix=http_requests/example.com/{DATE}" \
--header "X-Auth-Email: " \
--header "X-Auth-Key: " \
--header "R2-Access-Key-Id: R2_ACCESS_KEY_ID" \
--header "R2-Secret-Access-Key: R2_SECRET_ACCESS_KEY"
```
Results can be piped to a file using `> logs.json`.
Additionally, if you want to receive the raw GZIP bytes without them being transparently decompressed by your client, include the header `--header "Accept-Encoding: gzip"`.
## Retrieve logs by Ray ID
Using your logs stored in R2 - the Logpull RayID Lookup feature allows you to query an indexed time range for the presence of an RayID and return the matching result. This feature is available to users with the Logpull RayID Lookup beta subscription.
The ability to look up a RayID is a two-step process. First, a time range needs to be indexed before being able to request a record by the RayID.
Indexes will automatically expire after seven days of no usage.
### Index a time range
Before executing your query, you can specify the time range you would like to index in order to narrow down the scope of the query. In the following example, we index one minute of logs stored in the R2 bucket `"cloudflare-logs"` under the prefix `"http_requests/{DATE}"`.
### Example API request
```bash
curl https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/rayids/index \
--header "Authorization: Bearer " \
--header "R2-Access-Key-Id: " \
--header "R2-Secret-Access-Key: " \
--header "Content-Type: application/json" \
--data-raw '{
"start": "2022-08-16T20:30:00Z",
"end": "2022-08-16T20:31:00",
"bucket": "cloudflare-logs",
"prefix": "http_requests/example.com/{DATE}"
}'
```
## Lookup a RayID
After indexing a time range, perform a `GET` request with the RayID. If a matching result is found in the indexed time range, the record will be returned. Note that the parameters have moved from the request body and into the URL. The `-g` flag is required to avoid the `{DATE}` parameter from being misinterpreted by cURL.
### Example API request
```bash
curl --globoff "https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/rayids/?bucket=cloudflare-logs&prefix=http_requests/example.com/{DATE}" \
--header "Authorization: Bearer " \
--header "R2-Access-Key-Id: " \
--header "R2-Secret-Access-Key: "
```
## Troubleshooting
I am getting an error when accessing the API
* **Error**: Time range returned too many results. Try reducing the time range and try again.
HTTP status code `422` will be returned if the time range between the start and end parameters is too wide. Try querying a shorter time range if you are running into this limit.
* **Error**: Provided token does not have the required features enabled.
Contact your account representative to have the beta Logpull RayID Lookup subscription added to your account.
* **Error**: Time range returned too many results. Try reducing the time range and try again.
High volume zones can produce many log files in R2. Try reducing your start and end time range until you find a duration that works best for your log volume.
How do I know what time range to index?
Currently, there is no process to index logs as they arrive. If you have the RayID and know the time the request was made, try indexing the next 5-10 minutes of logs after the request was completed.
What is the time delay between when an event happens and when I can query for it?
Logpush delivers logs in batches as soon as possible, generally in less than one minute. After this, logs can be accessed using Logs Engine.
Does R2 have retention controls?
R2 does not currently have retention controls in place. You can query back as far as when you created the Logpush job.
Which datasets is Logs Engine compatible with?
The retrieval API is compatible with all the datasets we support. The full list is available on the [Datasets](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/) section.
---
title: Reference · Cloudflare Logs docs
description: "These reference resources are useful for gaining a more in-depth
understanding of the terminology and status codes that are part of the
Cloudflare Logs data. This information is especially important when
integrating your data with third-party tools:"
lastUpdated: 2025-07-24T13:05:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/reference/
md: https://developers.cloudflare.com/logs/reference/index.md
---
These reference resources are useful for gaining a more in-depth understanding of the terminology and status codes that are part of the Cloudflare Logs data. This information is especially important when integrating your data with third-party tools:
* [Pathing status](https://developers.cloudflare.com/logs/reference/pathing-status/)
* [Security fields](https://developers.cloudflare.com/logs/reference/security-fields/)
* [WAF fields](https://developers.cloudflare.com/logs/reference/waf-fields/)
* [ClientRequestSource field](https://developers.cloudflare.com/logs/reference/clientrequestsource/)
* [Change notices](https://developers.cloudflare.com/logs/reference/change-notices/)
---
title: 404 - Page Not Found · Cloudflare Magic Cloud Networking docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/404/
md: https://developers.cloudflare.com/magic-cloud-networking/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Changelog · Cloudflare Magic Cloud Networking docs
description: Review recent changes to Magic Cloud Networking (beta).
lastUpdated: 2025-04-24T15:57:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/changelog/
md: https://developers.cloudflare.com/magic-cloud-networking/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-cloud-networking.xml)
## 2024-12-05
**Generate customized terraform files for building cloud network on-ramps**
You can now generate customized terraform files for building cloud network on-ramps to [Magic WAN](https://developers.cloudflare.com/magic-wan/).
[Magic Cloud](https://developers.cloudflare.com/magic-cloud-networking/) can scan and discover existing network resources and generate the required terraform files to automate cloud resource deployment using their existing infrastructure-as-code workflows for cloud automation.
You might want to do this to:
* Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
* Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
For more details, refer to [Set up with Terraform](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#set-up-with-terraform).
## 2024-11-21
**Import cloud resources for VMs and LBs**
Cloud network discovery now includes cloud native virtual machine (VM) and load-balancer (LB) resources.
## 2024-11-21
**Export resource catalog**
Customers can export their resource catalog including all discovered resource metadata to a downloadable JSON file, suitable for offline analysis.
## 2024-10-01
**Cost visibility for managed cloud configuration**
Customers can now see the cloud provider list price of discovered network resources and will be informed of total cost and delta cost when deploying managed configuration.
## 2024-08-14
**GCP on-ramps**
Magic Cloud Networking supports Google Cloud Platform.
## 2024-07-01
**Closed beta launch**
The Magic Cloud Networking closed beta release is available, with the managed cloud on-ramps feature.
---
title: Cloud on-ramps · Cloudflare Magic Cloud Networking docs
description: Magic Cloud Networking (beta) allows you to create on-ramps from
your cloud networks to Magic WAN. Cloudflare will create virtual private
network (VPN) tunnels between Magic WAN and your cloud provider, configuring
both sides of the connection on your behalf. Cloudflare orchestrates the cloud
provider's native VPN functionality, without requiring deployment of any
additional compute virtual machines (VMs).
lastUpdated: 2025-03-27T12:39:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/
md: https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/index.md
---
Magic Cloud Networking (beta) allows you to create on-ramps from your cloud networks to Magic WAN. Cloudflare will create virtual private network (VPN) tunnels between Magic WAN and your cloud provider, configuring both sides of the connection on your behalf. Cloudflare orchestrates the cloud provider's native VPN functionality, without requiring deployment of any additional compute virtual machines (VMs).
There are two types of on-ramps: single virtual private cloud (VPC) and hubs.
## Prerequisites
Before creating on-ramps from your cloud networks to Magic WAN, make sure you:
* Have a Magic WAN account. Contact your account team to learn more.
* Went through the process of [setting up your cloud provider](https://developers.cloudflare.com/magic-cloud-networking/get-started/).
* Have the correct cloud resources. Refer to [Reference](https://developers.cloudflare.com/magic-cloud-networking/reference/) to check resources by cloud provider.
## Available on-ramps
Magic Cloud Networking has the following cloud on-ramps integrations:
* AWS (single VPC and hubs)
* Azure (single VPC)
* GCP (single VPC)
Refer to [Reference](https://developers.cloudflare.com/magic-cloud-networking/reference/) to learn more about how Cloudflare orchestrates VPN connectivity to your cloud networks.
***
## Set up on-ramps
### Single virtual private cloud
Choose this option if you have a single VPC in your cloud to connect to Magic WAN. To set up a single-VPC on-ramp:
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select **Add new on-ramp**.
4. Go to **Connect an existing VPC to Cloudflare** > **Select**.
5. Give your new on-ramp a name and a description (optional), then select **Continue**.
6. From the drop-down menu, choose your cloud provider. You can choose between AWS, GCP, and Azure. Then, select **Continue**.
7. Select the network that you want to connect to. This list comes from the [cloud integrations](https://developers.cloudflare.com/magic-cloud-networking/get-started/) you have already set up. When you are done, select **Continue**.
8. **Configure route propagation** shows where Cloudflare will install the new routes. Installing these routes is required to correctly configure both Magic WAN and your cloud provider, and ensure successful communication between them:
* **Add routes for your Magic WAN address space to your cloud network**: Select this option to install routes for reaching Magic WAN in your cloud network's route tables (refer to [Magic WAN address space](#magic-wan-address-space) to learn what routes are installed and how to customize them). If you prefer to do this manually, unselect this option.
Warning
Cloudflare recommends that you leave this option selected. If you unselect **Add routes for your Magic WAN address space to your cloud network**, you will need to manually create all the required configurations to allow Magic WAN to connect to your cloud, such as routing tables, transit gateways, and VPNs. Refer to the [Magic WAN How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section, or consult the documentation for your cloud provider for more information.
* **Add routes for your cloud network to Magic WAN**: Select this option to create routes for reaching your cloud network in Magic WAN.
9. Select **Continue**. Applying your settings might take a few seconds to complete.
10. Review the changes in your cloud environment, and select **Approve changes**.
You have successfully created your Magic WAN on-ramp. However, on-ramp creation can take up to an hour before you can use it.
### Hubs
If you want to connect multiple VPCs to Magic WAN, the best way to connect them is using a hub. A hub is a cloud VPN gateway that peers with multiple VPCs, allowing them to share a VPN tunnel to Magic WAN. Each cloud provider has their own term for hubs, so refer to your cloud provider for more information.
Depending on how you have set up your cloud provider, you can:
* **Connect to an existing hub**: Choose this option if you already have a VPN hub in your cloud and you want to connect it to Magic WAN.
* **Create a new hub**: Choose this option if you want to create a new hub and connect it to Magic WAN.
When you configure a hub on-ramp, Cloudflare always manages the VPN tunnel between Magic WAN and the hub. Optionally, you can also choose to have Cloudflare manage peering with VPCs and/or with other hubs:
* **Manage VPC peering:** If you enable this option, Cloudflare will attach your chosen VPCs to the hub.
* **Manage hub peering:** Hubs are regional, so in order to connect VPCs attached to hubs in different regions, those hubs need to be peered. If you enable this option, Cloudflare will peer your chosen hubs to this hub.
#### Connect to an existing hub
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select **Add new on-ramp**.
4. Go to **Connect an existing hub to Cloudflare** > **Select**.
5. Give your new on-ramp a name and a description (optional), then select **Continue**.
6. From the drop-down menu, choose your cloud provider. You can choose between AWS, GCP, and Azure. Then, select **Continue**.
7. Choose an existing hub. This list comes from the [cloud integrations](https://developers.cloudflare.com/magic-cloud-networking/get-started/) you have already set up. When you are done, select **Continue**.
8. (*Optional*) In **VPC peering configuration**, you can enable **Manage VPC peering**. This allows Cloudflare to attach your chosen VPCs to the hub:
1. Select **Manage VPC peering** to enable this feature.
2. Choose the VPCs you want Cloudflare to attach to the hub.
9. Select **Continue**.
10. (*Optional*) In **Configure hub peering**, you can enable **Manage hub peering**. Enabling this option allows Cloudflare to attach remote hubs you have chosen to this hub (establishing connectivity between VPCs attached to any of the peered hubs):
1. Select **Manage hub peering** to enable this feature.
2. Select the remote hubs you want Cloudflare to attach to this hub.
11. Select **Continue**.
12. **Configure route propagation** shows where Cloudflare will install the new routes. Installing these routes is required to correctly configure both Magic WAN and your cloud provider, and ensure successful communication between them:
1. **Add routes for your Magic WAN address space to your cloud network**: Select this option to install routes for reaching Magic WAN in your cloud network's route tables (refer to [Magic WAN address space](#magic-wan-address-space) to learn what routes are installed and how to customize them). If you prefer to do this manually, unselect this option.
Warning
Cloudflare recommends that you leave this option selected. If you unselect **Add routes for your Magic WAN address space to your cloud network**, you will need to manually create all the required configurations to allow Magic WAN to connect to your cloud, such as routing tables, transit gateways, and VPNs. Refer to the [Magic WAN How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section, or consult the documentation for your cloud provider for more information.
2. **Add routes for your cloud network to Magic WAN**: Select this option to create routes for reaching your cloud network in Magic WAN.
13. Select **Continue**. Applying your settings might take a few seconds to complete.
14. Review the changes in your cloud environment, and select **Approve changes**.
You have successfully created your Magic WAN on-ramp. However, on-ramp creation can take up to an hour before you can use it.
#### Create a new hub
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select **Add new on-ramp**.
4. Go to **Create a new hub & connect it to Cloudflare** > **Select**.
5. Give your new on-ramp a name and a description (optional), then select **Continue**.
6. Configure your cloud in **Select your cloud details**:
1. From the drop-down menu, choose your cloud provider. You can choose between AWS, GCP, and Azure.
2. Choose an existing integration. This list comes from the [cloud integrations](https://developers.cloudflare.com/magic-cloud-networking/get-started/) you have already set up.
3. Choose a region in which to create the new hub.
4. Select **Continue**.
7. (*Optional*) In **VPC peering configuration**, you can enable **Manage VPC peering**. This allows Cloudflare to attach your chosen VPCs to the hub:
1. Select **Manage VPC peering** to enable this feature.
2. Choose the VPCs you want Cloudflare to attach to the hub.
8. Select **Continue**.
9. (*Optional*) In **Configure hub peering**, you can enable **Manage hub peering**. Enabling this option allows Cloudflare to attach remote hubs you have chosen to this hub (establishing connectivity between VPCs attached to any of the peered hubs):
1. Select **Manage hub peering** to enable this feature.
2. Select the remote hubs you want Cloudflare to attach to this hub.
10. Select **Continue**.
11. **Configure route propagation** shows where Cloudflare will install the new routes. Installing these routes is required to correctly configure both Magic WAN and your cloud provider, and ensure successful communication between them:
1. **Add routes for your Magic WAN address space to your cloud network**: Select this option to install routes for reaching Magic WAN in your cloud network's route tables (refer to [Magic WAN address space](#magic-wan-address-space) to learn what routes are installed and how to customize them). If you prefer to do this manually, unselect this option.
Warning
Cloudflare recommends that you leave this option selected. If you unselect **Add routes for your Magic WAN address space to your cloud network**, you will need to manually create all the required configurations to allow Magic WAN to connect to your cloud, such as routing tables, transit gateways, and VPNs. Refer to the [Magic WAN How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section, or consult the documentation for your cloud provider for more information.
2. **Add routes for your cloud network to Magic WAN**: Select this option to create routes for reaching your cloud network in Magic WAN.
12. Select **Continue**. Applying your settings might take a few seconds to complete.
13. Review the changes in your cloud environment, and select **Approve changes**.
You have successfully created your Magic WAN on-ramp. However, on-ramp creation can take up to an hour before you can use it.
### Set up with Terraform
You can download a Terraform configuration for a cloud on-ramp.
You might want to do this to:
* Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
* Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
The download will contain two files:
* `main.tf`: Terraform configuration for the new resources needed to create the on-ramp.
* `instructions.txt`: Instructions for modifying resources that already exist in your cloud environment.
If you intend to plan and apply the downloaded configuration using Terraform, you will need to use the [Cloudflare Terraform provider](https://developers.cloudflare.com/terraform/) (in addition to the Terraform provider for the on-ramp's cloud service provider). Use your Cloudflare [Global API Key](https://developers.cloudflare.com/fundamentals/api/get-started/keys/), not an API Token.
Warning
Do not deploy the on-ramp using both Cloudflare and Terraform. If you plan to deploy your on-ramp with Cloudflare (meaning you are both planning to create an on-ramp and applying an on-ramp), Cloudflare creates resources that will result in conflicts when you run Terraform (and vice versa). The Cloudflare dashboard will warn you if it detects you might encounter a conflict.
#### Download Terraform configuration for a new on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud on-ramps**, select **Add new on-ramp** and begin the **Create a Magic WAN cloud on-ramp** workflow following the standard steps.
4. After the **Configure route propagation** step, select **View download options** instead of selecting **Continue**.
5. Select a download option:
1. Choose **Download file and continue** to download the Terraform configuration, review the configuration, and then continue deploying the on-ramp with Cloudflare.
2. Choose **Download file and exit** to download the Terraform configuration that you will apply yourself.
#### Download Terraform configuration for an existing on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud on-ramps**, find the on-ramp you want to download > select the three dots > **Download as Terraform**.
## Update security groups
After setting up your on-ramps, you need to update your network security groups in your cloud provider to allow traffic to/from Magic WAN. Refer to the [Cloud on-ramps](https://developers.cloudflare.com/magic-cloud-networking/reference/) reference page for more information.
***
## Edit on-ramps
### Edit a Magic WAN cloud on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select the on-ramp you want to edit.
4. Select **Edit** in the side panel.
5. In **Basic information**, you can change the name and description of your on-ramp. Select **Save** when you are finished.
6. In **Configurations**, you can modify where the required routes are installed. Select **Continue**.
1. Select **Save and review** after making changes.
2. Review your settings, and select **Approve changes**.
Warning
If you uncheck any of the Propagation settings, you will have to manually configure Magic WAN or your cloud provider to ensure successful communication between them. Refer to the [How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section of Magic WAN, or consult the documentation for your cloud provider for more information.
### Delete a Magic WAN cloud on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select the on-ramp you want to delete.
4. Select **Edit** in the side panel.
5. Choose **Detach** to proceed. Cloudflare will stop managing the cloud resources that were created to build this on-ramp, but will leave them in place. On-ramp connectivity will not be impacted.
***
## Magic WAN address space
By default, Cloudflare installs the following summarized routes in your cloud route tables to direct traffic to Magic WAN:
```txt
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
100.64.0.0/10
```
To override the defaults with custom prefixes:
1. Go to the **Routes** page.
[Go to **Routes**](https://dash.cloudflare.com/?to=/:account/magic-networks/routes)
2. Select **WAN configuration**.
3. Scroll to **Propagated routes to cloud networks**.
4. Delete the prefixes, and enter your custom ones.
5. When you are finished, select **Save changes**.
To install a default route to send all traffic to Magic WAN, enter `0.0.0.0/0` (on Azure, enter `0.0.0.0/1` and `128.0.0.0/1`).
***
## Cost estimates
You can view estimated costs associated with your cloud resources in the Cloudflare dashboard.
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud on-ramps**, find the cloud on-ramp for which you want to check the estimated costs > select the three dots > **Associated Resources**.
4. In the **Associated Resources** page, you can view the estimated monthly costs for all the resources associated with the on-ramp you chose. You can also search for a specific resource using the search box.
---
title: Get started · Cloudflare Magic Cloud Networking docs
description: To get started with Magic Cloud Networking (beta) you need to give
Cloudflare permission to interact with cloud providers on your behalf. You
might have multiple provider accounts for the same cloud provider — for
example, you might want Cloudflare to manage virtual private clouds (VPCs)
belonging to two different AWS accounts.
lastUpdated: 2026-01-22T10:37:48.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/get-started/
md: https://developers.cloudflare.com/magic-cloud-networking/get-started/index.md
---
To get started with Magic Cloud Networking (beta) you need to give Cloudflare permission to interact with cloud providers on your behalf. You might have multiple provider accounts for the same cloud provider — for example, you might want Cloudflare to manage virtual private clouds (VPCs) belonging to two different AWS accounts.
Once Cloudflare has the credentials required to access your cloud environments, Magic Cloud Networking will automatically begin discovering your cloud resources — like routing tables and virtual private networks. Discovered resources appear in your [Cloud resource catalog](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/#cloud-resource-catalog).
## Set up Amazon AWS
### 1. Create integration
1. Go to the **Cloud integrations (beta)** page.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select **Add** > **AWS integration**.
3. Give a descriptive name to your integration. Optionally, you can also add a description for it.
4. Select **Create integration**.
5. Select **Authorize access** to start the process of connecting your Cloudflare account to Amazon AWS.
### 2. Create IAM policy
1. Create a [custom IAM policy](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_create-console.html) in your AWS account, and take note of the name you entered. Then, paste the following [JSON code](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_version.html) in the JSON tab:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:AcceptTransitGatewayPeeringAttachment",
"ec2:CreateTransitGatewayPeeringAttachment",
"ec2:DeleteTransitGatewayPeeringAttachment",
"ec2:DescribeRegions",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:RejectTransitGatewayPeeringAttachment",
"ec2:GetManagedPrefixListEntries",
"ec2:CreateManagedPrefixList",
"ec2:ModifyManagedPrefixList",
"ec2:DeleteManagedPrefixList",
"ec2:CreateTransitGatewayPrefixListReference",
"ec2:DeleteTransitGatewayPrefixListReference",
"ec2:GetTransitGatewayPrefixListReferences",
"ec2:ModifyTransitGatewayPrefixListReference"
],
"Resource": "*"
}
]
}
```
### 3. Authorize access to your AWS account
1. Create an [AWS role](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-custom.html) with the following settings:
* **Trusted entity type**: Select **Custom trust policy**, and paste the custom trust policy returned by the Cloudflare dashboard.
* **Permissions**: Add the IAM policy you created in the previous step, along with these AWS-managed policies:
* `NetworkAdministrator`
* `AmazonEC2ReadOnlyAccess`
* `AmazonVPCReadOnlyAccess`
* `IAMReadOnlyAccess`
* **ARN**: Copy the ARN for your newly created user.
Note
The trust policy may take several minutes to propagate to all regions. It usually takes less than four minutes, but can sometimes take longer. You may have to retry the **Authorize** button while the propagation takes effect.
2. Select **I authorize Cloudflare to access my AWS account.**
3. Select **Authorize**.
Note
The first discovery of resources may not succeed in all regions while the IAM policy is propagating. If you do not see all resources after creating your cloud integration, try re-discovering.
## Set up Microsoft Azure
### 1. Create integration
1. In the Cloudflare dashboard, go to **Cloud integrations (beta)**.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select **Add** > **Azure integration**.
3. Give a descriptive name to your integration. Optionally, you can also add a description for it.
4. Select **Create integration**.
5. Select **Authorize access** to start the process of connecting your Cloudflare account to Microsoft Azure.
### 2. Authorize access to your Azure account
Warning
Magic Cloud does not support personal Microsoft accounts. Sign in using a work or school account that is part of an Azure Entra Tenant.
1. Select **Create service principal**. You will be redirected to Microsoft's login page.
2. Enter your Azure credentials. If your account does not have administrator privileges, you may need to pass this link to an account that has administrator privileges.
3. The next screen lists Cloudflare required permissions to access your account. Select **Accept**.
4. [Add a role assignment](https://learn.microsoft.com/en-us/azure/role-based-access-control/role-assignments-portal). The purpose of this step is to give the app that you registered in step 1 permission to access your Azure Subscription.
* In step 3 of the linked document, select the **Contributor** role from the **Privileged administrator roles** tab.
* In step 4 of the linked document, search for `mcn-provider-integrations-bot-prod` when selecting members.
5. In **Provide account information**, enter your **Tenant ID** and **Subscription ID**.
6. In **Verify account ownership**, [add the tags displayed in the Cloudflare dashboard](https://learn.microsoft.com/en-us/azure/azure-resource-manager/management/tag-resources-portal).
Note
The tags may take several minutes to propagate and become readable to Cloudflare. It usually takes less than four minutes, but can sometimes take longer. You may have to retry the **Authorize** button while the propagation takes effect.
7. Select **I authorize Cloudflare to access my Azure account.** If your account does not have administrator privileges, you may need to pass this link to an account that has administrator privileges.
8. Select **Authorize**.
Note
The first discovery of resources may not succeed in all regions while the IAM policy is propagating. If you do not see all resources after creating your cloud integration, try re-discovering.
## Set up Google Cloud
### 1. Create integration
1. In the Cloudflare dashboard, go to **Cloud integrations (beta)**.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select **Add** > **Google integration**.
3. Give a descriptive name to your integration. Optionally, you can also add a description for it.
4. Select **Create integration**.
5. Select **Authorize access** to start the process of connecting your Cloudflare account to Google Cloud.
### 2. Authorize access to your Google account
1. Create a new [GCP service account](https://cloud.google.com/iam/docs/service-accounts-create) in your **Google account** > **GCP Console** > **IAM & Admin** > **Service Accounts**.
2. Grant the new service account these roles:
* `Compute Network Admin`
* `Compute Viewer`
3. Under **IAM & Admin** > **Service Accounts**, select the service account you just created, and navigate to the **Permissions** tab.
4. Grant the **Service Account Token Creator** role to our bot account to allow it to impersonate this service account. Learn how to grant a specific role [in Google's documentation](https://cloud.google.com/iam/docs/manage-access-service-accounts#grant-single-role):
* `mcn-integrations-bot-prod@mcn-gcp-01.iam.gserviceaccount.com`
5. In the **service account email field**, enter the email account that you used to create the GCP service account.
6. In the **Project ID field**, enter the [project ID](https://support.google.com/googleapi/answer/7014113?hl=en) associated with your project.
7. [Add the label](https://cloud.google.com/resource-manager/docs/creating-managing-labels#create-labels) displayed in the dashboard of your project.
8. Select **I authorize Cloudflare to access my GCP account.** If your account does not have administrator privileges, you may need to pass this link to an account that has administrator privileges.
9. Select **Authorize**.
You have successfully connected your cloud provider to Magic Cloud Networking. Cloud resources found by Magic Cloud Networking are available in the [Cloud resource catalog](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/#cloud-resource-catalog).
Note
The first discovery of resources may not succeed in all regions while the IAM policy is propagating. If you do not see all resources after creating your cloud integration, try re-discovering.
## Next steps
* [Set up Magic WAN](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/) as an on-ramp to your cloud.
* [Manage resources](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/) found by Magic Cloud Networking.
* [Edit](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/#edit-cloud-integrations) cloud integrations.
---
title: Manage resources · Cloudflare Magic Cloud Networking docs
description: Your cloud environment is built from individual cloud resources,
like virtual private clouds (VPCs), subnets, virtual machines (VMs), route
tables, and routes. Magic Cloud Networking (beta) discovers all of your cloud
resources and stores their configuration and status in the Cloud resource
catalog, a read-only snapshot of your cloud environment. Discovery runs
regularly in the background, keeping your catalog up to date as your
environment changes.
lastUpdated: 2026-01-23T15:31:55.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/manage-resources/
md: https://developers.cloudflare.com/magic-cloud-networking/manage-resources/index.md
---
## Cloud resource catalog
Your cloud environment is built from individual cloud resources, like virtual private clouds (VPCs), subnets, virtual machines (VMs), route tables, and routes. Magic Cloud Networking (beta) discovers all of your cloud resources and stores their configuration and status in the Cloud resource catalog, a read-only snapshot of your cloud environment. Discovery runs regularly in the background, keeping your catalog up to date as your environment changes.
To browse the resources in your catalog:
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud resources**, select a resource to inspect its details.
## Edit Cloud integrations
You can change which cloud account the integration is linked to or delete the integration.
1. Go to **Cloud integrations**.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select your integration > **Edit**.
3. In **Linked account details**, select **Link integration to a different cloud account**.
4. Select **Save** when you are finished.
5. (Optional) You can also select **Delete** to delete your cloud integration.
## Download cloud resource catalog
You can download a JSON file containing metadata and configuration for all your cloud resources:
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud resources**, select **Download catalog**.
After your browser finishes downloading the ZIP file, expand it to access the JSON with the information about your cloud resources.
---
title: Reference · Cloudflare Magic Cloud Networking docs
description: Refer to this page for details about how Cloudflare orchestrates
VPN connectivity to your cloud networks.
lastUpdated: 2026-01-22T10:37:48.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/reference/
md: https://developers.cloudflare.com/magic-cloud-networking/reference/index.md
---
Refer to this page for details about how Cloudflare orchestrates VPN connectivity to your cloud networks.
## Cloud on-ramps
### AWS

When using Magic Cloud Networking (beta) to automatically create on-ramps to your AWS account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
* Cloudflare will create a new customer-managed prefix list named **Magic WAN and Cloudflare Edge** populated with your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) prefixes and the IPv4 address ranges for Cloudflare's global network servers (the latter prefixes are necessary if you use any Cloudflare L7 processing features). You must create rules in your Network Security Groups (NSGs) allowing traffic to/from this prefix list in order to have connectivity with Magic WAN. (The prefix list will contain around 15 to 25 entries, which each count against the rules-per-security-group quota for NSGs in your AWS account.)
* Cloudflare will create a Virtual Private Gateway and attach it to your Virtual Private Cloud (VPC). If an existing Virtual Private Gateway is already attached to the VPC, on-ramp creation will fail.
* Cloudflare will enable route propagation from the Virtual Private Gateway into all route tables in your VPC. This will result in a route for each prefix in your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) targeting the gateway.
* Cloudflare will add a route in Magic WAN for each IPv4 CIDR (Classless Inter-Domain Routing) block in your VPC.
### Azure

When using Magic Cloud Networking (beta) to automatically create on-ramps to your Azure account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
* Cloudflare will create a Virtual Network Gateway in your Virtual Network (VNet). Virtual Network Gateways in Azure require a subnet named `GatewaySubnet`. Cloudflare will create a `GatewaySubnet` if one does not already exist in your VNet. If there is not enough unused address space left in your VNet to create a `/27` subnet for the `GatewaySubnet`, or if a `GatewaySubnet` exists but does not have enough address space left for a Virtual Network Gateway, on-ramp creation will fail.
* Cloudflare will enable gateway route propagation on all route tables in your VNet. This will result in a route for each prefix in your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) pointing to the gateway. If your VNet has other Virtual Network Gateways, their routes will also propagate to your route tables. If you delete the on-ramp, route propagation will not be disabled.
* By default, Network Security Groups in Azure contain Allow rules for outbound/inbound traffic to/from the `VirtualNetwork` service tag, which includes Virtual Network Gateway address space (and therefore your Magic WAN Address Space). If you do not want all resources in your VNet to be accessible from Magic WAN, add the appropriate Deny rules to your Network Security Groups (NSGs).
* Cloudflare will add a route in Magic WAN for each IPv4 address range in your VNet.
### GCP

When using Magic Cloud Networking (beta) to automatically create on-ramps to your Google Cloud Platform (GCP) account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
* Cloudflare will reserve a public Internet routable IP address from GCP.
* Cloudflare will create a VPN Gateway and two VPN Tunnels in the region you specify.
* Cloudflare will create routes for each prefix in your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) within your VPC pointing to the VPN Tunnels.
* Cloudflare will add routes in Magic WAN for all subnet CIDR prefixes in your VPC. This includes all regions within the VPC. Traffic bound for a region other than the VPN Gateway's region will be subject to GCP's [Inter-region Pricing](https://cloud.google.com/vpc/network-pricing#inter-region-data-transfer).
* Traffic sent to and from your VM instances through the VPN Tunnels is still subject to VPC firewall rules, and may [require further configuration](https://cloud.google.com/network-connectivity/docs/vpn/how-to/configuring-firewall-rules#firewall_rules).
## Supported resources
Magic Cloud Networking (beta) discovers the following resource types in your cloud environments. These resources are used to build a comprehensive view of your cloud network topology and connectivity.
### AWS
* AWS Customer Gateway
* AWS EC2 Managed Prefix List
* AWS EC2 Transit Gateway
* AWS EC2 Transit Gateway Prefix List
* AWS EC2 Transit Gateway VPC Attachment
* AWS Egress Only Internet Gateway
* AWS Internet Gateway
* AWS Instance
* AWS Network Interface
* AWS Route Table
* AWS Route Table Association
* AWS Security Group
* AWS Subnet
* AWS VPC
* AWS VPC IPv4 CIDR Block Association
* AWS VPC Security Group Egress Rule
* AWS VPC Security Group Ingress Rule
* AWS VPN Connection
* AWS VPN Connection Route
* AWS VPN Gateway
### Azure
* Azure Application Security Group
* Azure Load Balancer
* Azure Load Balancer Backend Address Pool
* Azure Load Balancer NAT Pool
* Azure Load Balancer NAT Rule
* Azure Load Balancer Rule
* Azure Local Network Gateway
* Azure Network Interface
* Azure Network Interface Application Security Group Association
* Azure Network Interface Backend Address Pool Association
* Azure Network Interface Security Group Association
* Azure Network Security Group
* Azure Public IP
* Azure Route
* Azure Route Table
* Azure Subnet
* Azure Subnet Route Table Association
* Azure Virtual Machine
* Azure Virtual Machine Gateway Connection
* Azure Virtual Network
* Azure Virtual Network Gateway
* Azure Virtual Network Gateway Connection
### GCP
* Google Compute Address
* Google Compute Forwarding Rule
* Google Compute Global Address
* Google Compute HA VPN Gateway
* Google Compute Interconnect Attachment
* Google Compute Network
* Google Compute Network Firewall Policy
* Google Compute Network Firewall Policy Rule
* Google Compute Route
* Google Compute Router
* Google Compute Subnetwork
* Google Compute VPN Gateway
* Google Compute VPN Tunnel
---
title: 404 - Page Not Found · Cloudflare Magic Firewall docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/404/
md: https://developers.cloudflare.com/magic-firewall/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About · Cloudflare Magic Firewall docs
description: Review the content below to learn more about concepts related to
Magic Firewall.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/about/
md: https://developers.cloudflare.com/magic-firewall/about/index.md
---
Review the content below to learn more about concepts related to Magic Firewall.
Important
When using Magic Firewall alongside other Cloudflare services that proxy traffic (for example, CDN and Spectrum), be aware of the following:
* Firewall rules that block traffic based on source IP address may not work as intended because rules are evaluated after Cloudflare terminates the incoming TCP connections.
* You must allow [Cloudflare IP addresses](https://www.cloudflare.com/ips/).
* When using Magic Firewall, fragmented packets are reassembled into complete packets before they are inspected. As a result, you cannot create firewall rules for fragments.
- [Analytics](https://developers.cloudflare.com/magic-firewall/about/analytics/)
- [IDS](https://developers.cloudflare.com/magic-firewall/about/ids/)
- [List types](https://developers.cloudflare.com/magic-firewall/about/list-types/)
- [Protocol validation rules](https://developers.cloudflare.com/magic-firewall/about/protocol-validation-rules/)
- [Ruleset logic](https://developers.cloudflare.com/magic-firewall/about/ruleset-logic/)
- [Traffic types](https://developers.cloudflare.com/magic-firewall/about/traffic-types/)
---
title: Best practices · Cloudflare Magic Firewall docs
description: By default, Magic Firewall permits all ingress traffic that has
passed through Cloudflare's core DDoS mitigations. To proactively mitigate
attacks and minimize your attack surface and leakage of attack traffic into
your environment, we recommend implementing your Magic Firewall rules using
the following guidelines.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/best-practices/
md: https://developers.cloudflare.com/magic-firewall/best-practices/index.md
---
By default, Magic Firewall permits all ingress traffic that has passed through Cloudflare's core DDoS mitigations. To proactively mitigate attacks and minimize your attack surface and leakage of attack traffic into your environment, we recommend implementing your Magic Firewall rules using the following guidelines.
The best approach is to replicate your current ingress perimeter firewall rules in Magic Firewall. If you are unable to export your current perimeter firewall rules, contact your Implementation Manager for help translating the rules into Magic Firewall rules.
* [Minimal ruleset](https://developers.cloudflare.com/magic-firewall/best-practices/minimal-ruleset/)
* [Extended ruleset](https://developers.cloudflare.com/magic-firewall/best-practices/extended-ruleset/)
* [Magic Transit egress](https://developers.cloudflare.com/magic-firewall/best-practices/magic-transit-egress/)
---
title: Changelog · Cloudflare Magic Firewall docs
description: The Network Services menu structure in Cloudflare's dashboard has
been updated to reflect solutions and capabilities instead of product names.
This will make it easier for you to find what you need and better reflects how
our services work together.
lastUpdated: 2025-04-24T15:57:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/changelog/
md: https://developers.cloudflare.com/magic-firewall/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-firewall.xml)
## 2026-01-15
**Network Services navigation update**
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

## 2025-03-13
**Cloudflare IP Ranges List**
Magic Firewall now supports a new managed list of Cloudflare IP ranges. This list is available as an option when creating a Magic Firewall policy based on IP source/destination addresses. When selecting "is in list" or "is not in list", the option "**Cloudflare IP Ranges**" will appear in the dropdown menu.
This list is based on the IPs listed in the Cloudflare [IP ranges](https://www.cloudflare.com/en-gb/ips/). Updates to this managed list are applied automatically.

Note: IP Lists require an advanced Magic Firewall subscription. For more details about Magic Firewall plans, refer to [Plans](https://developers.cloudflare.com/magic-firewall/plans).
## 2024-10-02
**Search for custom rules using rule name and/or ID**
The Magic Firewall dashboard now allows you to search custom rules using the rule name and/or ID.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Analytics & Logs** > **Network Analytics**.
3. Select **Magic Firewall**.
4. Add a filter for **Rule ID**.

Additionally, the rule ID URL link has been added to Network Analytics.
## 2024-09-12
**New UI improvements**
The dashboard now displays the order number of custom rules, and improved drag and drop functionality. You can also preview rules on a side panel without leaving the current page.
## 2024-08-16
**Magic Firewall Analytics Rule Log Enhancement**
Customers who create a rule in a disabled mode will see the rule as **Log (rule disabled)**.
---
title: How to · Cloudflare Magic Firewall docs
description: Review the content below to learn how to complete tasks using Magic Firewall.
lastUpdated: 2024-10-03T13:28:13.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-firewall/how-to/
md: https://developers.cloudflare.com/magic-firewall/how-to/index.md
---
Review the content below to learn how to complete tasks using Magic Firewall.
* [Add custom policies](https://developers.cloudflare.com/magic-firewall/how-to/add-policies/)
* [Enable IDS](https://developers.cloudflare.com/magic-firewall/how-to/enable-ids/)
* [Create Rate Limiting policies (beta)](https://developers.cloudflare.com/magic-firewall/how-to/create-rate-limiting-policies/)
* [Enable Magic user roles](https://developers.cloudflare.com/magic-firewall/how-to/enable-magic-roles/)
* [Enable Managed Rulesets](https://developers.cloudflare.com/magic-firewall/how-to/enable-managed-rulesets/)
* [Filter different views](https://developers.cloudflare.com/magic-firewall/how-to/filter-views/)
* [Form expressions](https://developers.cloudflare.com/magic-firewall/how-to/form-expressions/)
* [Use Logpush with IDS](https://developers.cloudflare.com/magic-firewall/how-to/use-logpush-with-ids/)
* [Use IP lists](https://developers.cloudflare.com/magic-firewall/how-to/use-rules-list/)
---
title: Packet captures · Cloudflare Magic Firewall docs
description: "Cloudflare supports two types of packet captures: full and sample.
Full packet captures is the default behavior."
lastUpdated: 2025-06-06T14:58:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/packet-captures/
md: https://developers.cloudflare.com/magic-firewall/packet-captures/index.md
---
Cloudflare supports two types of packet captures: full and sample. Full packet captures is the default behavior.
Note
The maximum packet capture runtime is 24 hours for sample and full packet captures.
## Sample packet captures
Sample packet captures collects historical data on network traffic that has already passed through Cloudflare's network. It will not collect any new traffic sent to Cloudflare's network after the packet capture has started. All sample packet captures will complete immediately after they are started because they query historical traffic data.
Sample packet captures can be viewed in the Cloudflare dashboard. They only include the first 160 bytes of data. This is useful for capturing packet headers, but will not provide detailed packet data. The sample data is collected across all Cloudflare's data centers to build a PCAP file. This allows you to get a global picture of traffic across all data centers.
You should use full packet captures if you need to collect data on packets that pass through your network less frequently.
## Full packet captures
Full packet captures will actively monitor Cloudflare's network for packets that match the selected filters, and will capture the matching packet data. The matching packet data is saved to a cloud storage bucket that is owned and configured by you.
Full packet captures will collect new traffic sent to Cloudflare's network after the packet capture has started, and include the full packet data. This type of capture cannot be viewed in the Cloudflare dashboard. You can download them from a cloud storage bucket and analyze them in Wireshark or another packet capture tool.
Refer to the articles in this section to learn how to use packet captures.
* [PCAPs bucket setup](https://developers.cloudflare.com/magic-firewall/packet-captures/pcaps-bucket-setup/)
* [Collect PCAPs](https://developers.cloudflare.com/magic-firewall/packet-captures/collect-pcaps/)
---
title: Plans · Cloudflare Magic Firewall docs
description: If you are a Magic Transit or Magic WAN user, you are automatically
provided with a standard list of Magic Firewall features. For additional
features available for purchase, refer to the list of advanced features below.
lastUpdated: 2025-10-22T21:11:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/plans/
md: https://developers.cloudflare.com/magic-firewall/plans/index.md
---
If you are a [Magic Transit](https://developers.cloudflare.com/magic-transit/) or [Magic WAN](https://developers.cloudflare.com/magic-wan/) user, you are automatically provided with a standard list of Magic Firewall features. For additional features available for purchase, refer to the list of advanced features below.
## Standard features
* Filtering rules based on protocol, port, IP addresses, packet length, and bit field match.
* Fast propagation of rule changes in less than a minute.
* Single dashboard to manage firewall and network configuration.
* Programmable API for automated deployment and management — compatible with infrastructure-as-code platforms like [Terraform](https://developers.cloudflare.com/terraform/).
* Traffic analytics per rule in the dashboard and using the [GraphQL API](https://developers.cloudflare.com/analytics/graphql-api/).
* Integration with [Magic WAN network-as-a-service](https://developers.cloudflare.com/magic-wan/).
* Included DDoS protection with [Magic Transit](https://developers.cloudflare.com/magic-transit/).
## Advanced features
All standard features are included with the purchase of the advanced features below:
* Customizable IP lists.
* Managed threat intelligence IP lists (Anonymizer, Botnet, Malware, Open Proxies, VPNs).
* Geoblocking based on user location by country.
* Block or allow packets based on Autonomous System Number (ASN).
* Packet captures on demand for network troubleshooting.
* [Protocol validation rules](https://developers.cloudflare.com/magic-firewall/about/protocol-validation-rules/) to inspect traffic validity and enforce a positive security model.
* [Secure Web Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) filtering for outbound Internet traffic (network and HTTP policies). The Secure Web Gateway supports all TCP and UDP ports, as well as traffic sourced from RFC 1918 address space. Gateway will proxy BYOIP traffic to egress via the default Cloudflare IPs or your assigned [dedicated egress IPs](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/dedicated-egress-ips/).
* Intrusion Detection System (IDS).
---
title: Reference · Cloudflare Magic Firewall docs
description: Review the content below for more information about Magic Firewall.
lastUpdated: 2024-10-03T13:28:13.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-firewall/reference/
md: https://developers.cloudflare.com/magic-firewall/reference/index.md
---
Review the content below for more information about Magic Firewall.
* [Magic Firewall fields](https://developers.cloudflare.com/magic-firewall/reference/magic-firewall-fields/)
* [Magic Firewall functions](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/#magic-firewall-functions)
---
title: Tutorials · Cloudflare Magic Firewall docs
description: View tutorials to help you get started with Magic Firewall.
lastUpdated: 2024-10-03T13:28:13.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-firewall/tutorials/
md: https://developers.cloudflare.com/magic-firewall/tutorials/index.md
---
View tutorials to help you get started with Magic Firewall.
| Name | Last Updated | Difficulty |
| - | - | - |
| [GraphQL Analytics](https://developers.cloudflare.com/magic-firewall/tutorials/graphql-analytics/) | almost 4 years ago | Medium |
---
title: 404 - Page Not Found · Cloudflare Magic Network Monitoring docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/404/
md: https://developers.cloudflare.com/magic-network-monitoring/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API · Cloudflare Magic Network Monitoring docs
description: Use Magic Network Monitoring's API to configure your account and rules.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/api/
md: https://developers.cloudflare.com/magic-network-monitoring/api/index.md
---
Use Magic Network Monitoring's API to configure your account and rules.
## Account configuration
Refer to [Account configuration API methods](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/configs/methods/get/) to:
* Create, list, update, and delete Magic Network Monitoring configurations
* List default sampling, router IPs, and rules for an account
## Rules configuration
Refer to [Rules configuration API methods](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/rules/methods/list/) to:
* Create, list, update, and delete rules
* Update advertisement for a rule
---
title: Cloud flow logs (beta) · Cloudflare Magic Network Monitoring docs
description: Customers using Magic Network Monitoring can export virtual private
cloud (VPC) flow logs from their cloud environment to Cloudflare's network.
Cloudflare processes these logs and displays analytics on your cloud traffic
in the dashboard. You can also ingest data on your cloud traffic via our
public GraphQL API, which powers the cloud traffic analytics in the Cloudflare
dashboard.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/cloud-flow-logs/
md: https://developers.cloudflare.com/magic-network-monitoring/cloud-flow-logs/index.md
---
Customers using Magic Network Monitoring can export virtual private cloud (VPC) flow logs from their cloud environment to Cloudflare's network. Cloudflare processes these logs and displays analytics on your cloud traffic in the dashboard. You can also ingest data on your cloud traffic via our public [GraphQL API](https://developers.cloudflare.com/analytics/graphql-api/), which powers the cloud traffic analytics in the Cloudflare dashboard.
Currently, Magic Network Monitoring only supports AWS VPC flow logs via AWS Firehose. You can only configure AWS flow logs via the Magic Network Monitoring API.
To learn how to set up AWS VPC flow logs, refer to [Set up AWS VPC flow logs](https://developers.cloudflare.com/magic-network-monitoring/get-started/#vpc-flow-log-guide).
---
title: Changelog · Cloudflare Magic Network Monitoring docs
description: Review recent changes to Magic Network Monitoring.
lastUpdated: 2025-04-24T15:57:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/changelog/
md: https://developers.cloudflare.com/magic-network-monitoring/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-network-monitoring.xml)
## 2026-01-15
**Network Services navigation update**
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

## 2024-09-24
**Try out Magic Network Monitoring**
The free version of Magic Network Monitoring (MNM) is now available to everyone with a Cloudflare account by default.
1. Log in to your [Cloudflare dashboard](https://dash.cloudflare.com), and select your account.
2. Go to **Analytics & Logs** > **Magic Monitoring**.

For more details, refer to the [Get started guide](https://developers.cloudflare.com/magic-network-monitoring/get-started/).
---
title: FAQ · Cloudflare Magic Network Monitoring docs
description: Find answers to the most commonly asked questions. If you cannot
find the answer you are looking for, refer to the community page to explore
more resources.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/faq/
md: https://developers.cloudflare.com/magic-network-monitoring/faq/index.md
---
Find answers to the most commonly asked questions. If you cannot find the answer you are looking for, refer to the [community page](https://community.cloudflare.com/) to explore more resources.
## I am getting an "Invalid account settings request body: account name format contains illegal characters or is not supported" error when trying to create a rule.
This probably means that your account name has unsupported characters. Make sure your account name does not have characters like, for example, `&`, `<`, `>`, `"`, `'`, `` ` ``.
Refer to [Account name](https://developers.cloudflare.com/fundamentals/account/create-account/#account-name) to learn how to change your account name.
## Can I send NetFlow/sFlow data to Cloudflare in a secure, encrypted way?
Yes. Both enterprise and free customers can send encrypted network flow data to Cloudflare.
Enterprise customers with Magic Transit or Magic WAN can send encrypted network flow data via an IPsec tunnel to Cloudflare's network. You can achieve this by:
1. Configuring your [NetFlow](https://developers.cloudflare.com/magic-network-monitoring/routers/netflow-ipfix-config/) or [sFlow](https://developers.cloudflare.com/magic-network-monitoring/routers/sflow-config/) data to be sent to Cloudflare's network for parsing.
2. Directing that network flow data to be sent over [Magic Transit IPsec tunnels](https://developers.cloudflare.com/magic-transit/how-to/configure-tunnel-endpoints/) or [Magic WAN IPsec tunnels](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-tunnel-endpoints/) to Cloudflare's network.
Cloudflare's network will then identify this traffic via the destination IP address/port, and direct the network flow traffic to Magic Network Monitoring for parsing.
Free customers can route their network flow traffic through a device that is running the WARP client. Then, network flow traffic can be forwarded from the WARP enabled device to Cloudflare's network flow endpoints. Learn more in the [Encrypt network flow data tutorial](https://developers.cloudflare.com/magic-network-monitoring/tutorials/encrypt-network-flow-data/).
## I have Auto-Advertisement enabled and it was triggered by an attack. Do I have to turn Magic Transit off manually?
Once Auto-Advertisement is activated for an IP prefix that is under attack, the IP prefix will continue to be advertised by Cloudflare even if the attack ends. You must manually disable advertisement for that IP prefix. Refer to [Configure dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement) to learn how to withdraw your prefixes, and stop using Magic Transit.
## If Auto-Advertisement is enabled, and the threshold has been triggered, will the IP prefix show as advertised in the dashboard?
Yes, the IP prefix will show as advertised under the [IP Prefixes tab](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement).
## Does Auto-advertisement also work with BGP-controlled advertisements?
No. Auto-advertisement only works with API-controlled advertisement, not BGP-controlled advertisement.
## In the API, Magic Network Monitoring rules have a `bandwidth_threshold` data field. Does the value for this field refer to bytes transferred or current throughput?
The threshold for a [Magic Network Monitoring rule](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/rules/methods/list/) has two values. The first value is `bandwidth_threshold`. This value is a measure of the total ingress throughput on a network at any given moment. The second value is `duration`. The `duration` value refers to the amount of time that `bandwidth_threshold` must be exceeded before an alert is sent to the customer.
For example, you create a Magic Network Monitoring rule with the following parameters:
```txt
"bandwidth_threshold": 50000000
"duration": "1m0s"
```
With this rule, your network needs to receive a throughput greater than 50,000,000 bits per second (50 Gigabits per second or Gbps) for 60 seconds. If both of these conditions are met, then Magic Network Monitoring will send you an alert.
## My router's public IP address is different from the IP address of my network flow `agent-ip`. I cannot change my network flow `agent-ip`, and I am not seeing my router's traffic in Magic Network Monitoring analytics
Set your router's public IP address and network flow `agent-ip` to the same value. However, if you are unable to do this, you can register both your router's public IP and your network flow `agent-ip` in the Magic Network Monitoring [router configuration](https://developers.cloudflare.com/magic-network-monitoring/get-started/). This will prevent Magic Network Monitoring from blocking network traffic received from any unknown IP addresses, and will show your router's network flow data underneath the router's `agent-ip`.
## What is Magic Network Monitoring's data retention policy for NetFlow/sFlow received from customer's routers?
Currently, all data received from a customer's router goes to our servers in the US. If you enable data sovereignty in Europe, you cannot currently use Magic Network Monitoring.
GraphQL analytics is retained for 90 days for enterprise customers. For non-enterprise customers, data retention is seven days. Cloudflare also retains data for six hours in the US, for threshold crossing detection.
---
title: Get started · Cloudflare Magic Network Monitoring docs
description: Magic Network Monitoring includes an onboarding workflow that
guides you step-by-step through the product configuration process. If you are
unable to complete the configuration in one session, you can exit the workflow
and resume it at any time.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/get-started/
md: https://developers.cloudflare.com/magic-network-monitoring/get-started/index.md
---
Magic Network Monitoring includes an onboarding workflow that guides you step-by-step through the product configuration process. If you are unable to complete the configuration in one session, you can exit the workflow and resume it at any time.
To begin using Magic Network Monitoring for network and/or cloud traffic visibility, complete the list of tasks below.
* [NetFlow and sFlow guide](#netflow-and-sflow-guide)
* [VPC flow log guide (beta)](#vpc-flow-log-guide)
If you are an Enterprise customer, Cloudflare can significantly accelerate the onboarding timeline during active-attack scenarios.
Enterprise customers that would like to use Magic Network Monitoring and Magic Transit On Demand together can begin by [configuring Magic Transit](https://developers.cloudflare.com/magic-transit/get-started/).
## NetFlow and sFlow guide
### 1. Verify NetFlow or sFlow capabilities
Verify your routers are capable of exporting NetFlow or sFlow to an IP address on Cloudflare's network. Magic Network Monitoring supports NetFlow v5, NetFlow v9, IPFIX, and sFlow.
Refer to [Supported routers](https://developers.cloudflare.com/magic-network-monitoring/routers/supported-routers) to view a list of supported routers. The list is not exhaustive.
### 2. Register your router with Cloudflare
When you register your router with Cloudflare, your router links your NetFlow or sFlow data to your Cloudflare account.
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. In **Network flow (Magic Network Monitoring)**, select **Configure Network flow**.
2. Select the **Configure routers** tab.
3. (Optional) Under **IP Address**, enter your router's public IP address.
4. Under **Default router sampling rate**, enter a value for the sampling rate. The value should match the sampling rate of your NetFlow or sFlow configuration.
5. Select **Next**.
### 3. Configure your router
Next, configure your router to send NetFlow or sFlow data to Cloudflare. For this step, you will also need to have your router's configuration menu open to input the values shown in the Cloudflare dashboard.
Refer to the [NetFlow and IPFIX configuration guide](https://developers.cloudflare.com/magic-network-monitoring/routers/netflow-ipfix-config/) or the [sFlow configuration guide](https://developers.cloudflare.com/magic-network-monitoring/routers/sflow-config/) for more information.
1. From **Configure routers** in the dashboard, select either **NetFlow Configuration** or **sFlow configuration**.
2. Follow the configuration steps for the selected configuration type.
3. Enter the values shown in your router's configuration.
4. Select **Next**.
### 4. Check your router configuration
After setting up your router, confirm the configuration was successfully set up.
From the **Check routers** page on the dashboard, you can view the status of your routers. Router data typically takes five to ten minutes to appear in the Cloudflare dashboard.
Refer to **Router status description** to confirm whether data is successfully being sent.
When you are done with router configuration, select **Finish onboarding**.
Note
This will only be visible during the onboarding process. When you are finished onboarding, this page will no longer be visible.
### 5. Create rules
Create rules to analyze data for a specific set of destinations or to implement thresholds. Refer to [Rules](https://developers.cloudflare.com/magic-network-monitoring/rules/) for more information.
## VPC flow log guide Beta
### 1. Verify cloud flow log capabilities
Verify that your Amazon Web Services (AWS) account is capable of exporting AWS Virtual Private Cloud (VPC) flow logs through AWS Firehose. Currently, Magic Network Monitoring only supports VPC flow log ingestion for AWS.
### 2. Set up AWS Firehose to export VPC flow logs to Cloudflare
Note
AWS VPC flow logs can only be configured through the Cloudflare API for Magic Network Monitoring. There are no inputs in the dashboard for configuring AWS VPC flow logs.
1. Create an authorization token using [Cloudflare's API for Magic Network Monitoring](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/vpc_flows/subresources/tokens/methods/create/). This authorization token allows Cloudflare to identify and verify the account sending VPC flow logs to our endpoint.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Magic Network Monitoring Admin`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/mnm/vpc-flows/token" \
--request POST \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY"
```
2. In your AWS Firehose stream configuration, set the `HTTP Headers - X-Amz-Firehose-Access-Key` to the authorization token generated in the previous step.
3. Send your AWS Firehose VPC flow log stream towards `https://aws-flow-logs.cloudflare.com/`.
4. Select all of the AWS VPC flow log data fields that you want to send to Cloudflare. You should select the highest number AWS VPC flow log version that supports all the fields you want to export to Cloudflare (refer to [AWS flow log documentation](https://docs.aws.amazon.com/vpc/latest/userguide/flow-log-records.html) for more information). For example, if you need a version 8 field like `reject-reason`, you must export all fields from versions 1 through 8. Cloudflare supports all seven templates for AWS VPC Flow logs.
### 3. Verify your cloud traffic via analytics
After setting up AWS Firehose to send VPC flow logs to Magic Network Monitoring, you can confirm that Cloudflare is receiving the logs as expected by searching for your cloud traffic data in the analytics page of the Magic Network Monitoring dashboard.
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. The default view will be the analytics dashboard for Magic Network Monitoring.
---
title: Glossary · Cloudflare Magic Network Monitoring docs
description: Review the definitions for terms used across Cloudflare's Magic
Network Monitoring documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/glossary/
md: https://developers.cloudflare.com/magic-network-monitoring/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Magic Network Monitoring documentation.
| Term | Definition |
| - | - |
| flow data | Represents records of communication between devices. There are a number of flow data protocols, such as NetFlow or sFlow. |
| NetFlow | Network protocol developed by Cisco to collect and monitor network traffic flow data. |
| sampling | In the context of Magic Network Monitoring, sampling is the process of taking samples of packets for a specific period to identify potential attacks. |
| sFlow | An industry standard packet sampling protocol to monitor network devices. |
---
title: Magic Transit integration · Cloudflare Magic Network Monitoring docs
description: With Magic Transit On Demand, you can use Magic Network Monitoring
to analyze your network traffic and detect Distributed Denial of Service
(DDoS) attacks while Magic Transit is disabled. If an attack is detected, you
can automatically or manually enable Magic Transit to mitigate attacks.
lastUpdated: 2025-10-16T11:21:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/magic-transit-integration/
md: https://developers.cloudflare.com/magic-network-monitoring/magic-transit-integration/index.md
---
With [Magic Transit On Demand](https://developers.cloudflare.com/magic-transit/on-demand/), you can use Magic Network Monitoring to analyze your network traffic and detect Distributed Denial of Service (DDoS) attacks while Magic Transit is disabled. If an attack is detected, you can automatically or manually enable Magic Transit to mitigate attacks.
You can create Magic Network Monitoring rules which monitor specific Internet Protocol (IP) prefixes for DDoS attacks. When a DDoS attack is detected, Cloudflare notifies you by email, [webhook](https://developers.cloudflare.com/notifications/get-started/configure-webhooks/), or [PagerDuty](https://developers.cloudflare.com/notifications/get-started/configure-pagerduty/) with information about the attack. Then, you can [automatically activate IP advertisement](#activate-ip-auto-advertisement) and enable Magic Transit to protect the targeted IP prefixes from DDoS attacks. This feature is referred to as auto-advertisement, and you can enable it for individual Magic Network Monitoring rules through the dashboard or API.
After Magic Transit is activated and your traffic is flowing through Cloudflare, Cloudflare blocks malicious DDoS traffic, and your origin servers receive only clean network traffic through IPsec or Generic Routing Encapsulation (GRE) tunnels.
The following diagrams illustrate this process:



## Activate IP auto-advertisement
Enable IP auto-advertisement to use Magic Network Monitoring rules. You can activate IP auto-advertisement through the dashboard or the API.
### Dashboard
To activate IP advertisement through the Cloudflare dashboard, refer to [Configure dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement).
### API
To activate IP advertisement through the API, refer to the [IP Address Management Dynamic Advertisement API](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/advertisement_status/methods/edit/).
## Magic Network Monitoring rules
To create Magic Network Monitoring rules with auto-advertisement, refer to [Rule Auto-Advertisement](https://developers.cloudflare.com/magic-network-monitoring/rules/#rule-auto-advertisement).
---
title: Magic Network Monitoring free version · Cloudflare Magic Network
Monitoring docs
description: The free version of Magic Network Monitoring is generally available
to everyone with a Cloudflare account by default.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/magic-network-monitoring-free/
md: https://developers.cloudflare.com/magic-network-monitoring/magic-network-monitoring-free/index.md
---
The free version of Magic Network Monitoring is generally available to everyone with a Cloudflare account by default.
All free customers are encouraged to join [Cloudflare's Discord server](https://discord.com/invite/cloudflaredev) to discuss the use cases, configuration, and troubleshooting of Magic Network Monitoring. Free customers are always welcome to provide product feedback and discuss feature requests. The product and engineering team that works on Magic Network Monitoring regularly engages with the Discord community.
You can find the channel by joining the Cloudflare Developers Discord server. Then scroll down in the side bar navigation to the **Cloudflare One** category and select **magic-network-monitoring**.
## Access the free version of Magic Network Monitoring
The free version includes all the features of the enterprise version, but has network flow volume and configuration limitations. These limits are detailed below.
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Complete the onboarding wizard to configure Magic Network Monitoring. Refer to [Get started](https://developers.cloudflare.com/magic-network-monitoring/get-started/) for detailed configuration instructions.
## Limitations
| Configuration limit | Value |
| - | - |
| Number of registered routers | 10 |
| Number of rules | 25 |
| Network flows per second per account | 250 |
---
title: Routers · Cloudflare Magic Network Monitoring docs
lastUpdated: 2024-08-30T16:09:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/routers/
md: https://developers.cloudflare.com/magic-network-monitoring/routers/index.md
---
* [Supported routers](https://developers.cloudflare.com/magic-network-monitoring/routers/supported-routers/)
* [Recommended sampling rate](https://developers.cloudflare.com/magic-network-monitoring/routers/recommended-sampling-rate/)
* [Netflow/IPFIX configuration](https://developers.cloudflare.com/magic-network-monitoring/routers/netflow-ipfix-config/)
* [sFlow configuration](https://developers.cloudflare.com/magic-network-monitoring/routers/sflow-config/)
---
title: Rules · Cloudflare Magic Network Monitoring docs
description: Magic Network Monitoring rules allow you to monitor your network
traffic for Distributed Denial of Service (DDoS) attacks on specific IP
addresses or IP prefixes within your network. If the network traffic that is
monitored by a rule exceeds the rule's threshold or contains a DDoS attack
fingerprint, then you will receive an alert.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/rules/
md: https://developers.cloudflare.com/magic-network-monitoring/rules/index.md
---
Magic Network Monitoring rules allow you to monitor your network traffic for Distributed Denial of Service (DDoS) attacks on specific IP addresses or IP prefixes within your network. If the network traffic that is monitored by a rule exceeds the rule's threshold or contains a DDoS attack fingerprint, then you will receive an alert.
## Rule types
There are three different types of rules that can be configured within Magic Network Monitoring. You can refer to the linked documentation page for each rule type to learn more.
| Rule Type | Rule Description | Rule Availability |
| - | - | - |
| [Dynamic threshold](https://developers.cloudflare.com/magic-network-monitoring/rules/dynamic-threshold/) (recommended) | A dynamic threshold rule will analyze a network's traffic patterns over time and automatically adjust the rule's DDoS threshold, in terms of bits or packets, based on traffic history. | API configuration only |
| [Static threshold](https://developers.cloudflare.com/magic-network-monitoring/rules/static-threshold/) | A static threshold rule allows you to define a constant numeric threshold, in terms of bits or packets, for DDoS traffic monitoring. | API configuration and dashboard configuration |
| [sFlow DDoS attack](https://developers.cloudflare.com/magic-network-monitoring/rules/s-flow-ddos-attack/) | Magic Network Monitoring customers that send sFlow data to Cloudflare can receive alerts when a specific type of DDoS attack is detected within their network traffic. | API configuration only. Only applicable to sFlow data sets |
## Create rules in the dashboard
You can only configure static traffic threshold rules in the Cloudflare dashboard.
Invalid account settings error when trying to create a rule
If you get the following error when trying to create a rule:
`Invalid account settings request body: account name format contains illegal characters or is not supported`
Make sure the name for your Cloudflare account does not contain unsupported characters, like, for example, `&`, `<`, `>`, `"`, `'`, `` ` ``.
Refer to [Account name](https://developers.cloudflare.com/fundamentals/account/create-account/#account-name) to learn how to change your account name.
To create a new rule:
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Select **Configure Network flow**.
2. In the **Configure rules** tab, select **Add new rule**.
3. Create a new static traffic threshold rule according to your needs. Refer to the documentation on [static threshold](https://developers.cloudflare.com/magic-network-monitoring/rules/static-threshold/) rules for more information on each field in the static threshold rule's configuration.
4. Select **Create a new rule** when you are finished.
## Edit rules in the dashboard
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Select **Configure Network flow**.
2. In the **Configure rules** tab, find the static threshold rule you want to edit, and select **Edit**.
3. Edit the appropriate fields. Refer to [Rule configuration fields](https://developers.cloudflare.com/magic-network-monitoring/rules/static-threshold/#rule-configuration-fields) for more information on what each field does.
4. Select **Save** when you are finished.
## Delete rules in the dashboard
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Select **Configure Network flow**.
2. In the **Configure rules** tab, find the static threshold rule you want to delete, and select **Delete**.
3. Select **I understand that deleting a rule is permanent**, and select **Delete** again.
## Common settings that apply to all rule types
### Rule Auto-Advertisement
If you are an Enterprise customer using [Magic Transit On Demand](https://developers.cloudflare.com/magic-transit/on-demand), you can enable **Auto-Advertisement** for any dynamic threshold, static threshold, and sFlow DDoS attack rule. The Auto-Advertisement feature will automatically activate Magic Transit when a static or dynamic rule threshold is exceeded or a DDoS attack fingerprint is identified in sFlow traffic logs.
Follow the previous steps to [create](#create-rules-in-the-dashboard) or [edit](#edit-rules-in-the-dashboard) a rule. Then, enable **Auto-Advertisement**.
#### Rule Auto-Advertisement notifications
Webhook, PagerDuty, and email notifications are sent following an auto-advertisement attempt for all prefixes inside the flagged rule.
You will receive the status of the advertisement for each prefix with the following available statuses:
* **Advertised**: The prefix was successfully advertised.
* **Already Advertised**: The prefix was advertised prior to the auto advertisement attempt.
* **Delayed**: The prefix cannot currently be advertised but will attempt advertisement. After the prefix can be advertised, a new notification is sent with the updated status.
* **Locked**: The prefix is locked and cannot be advertised.
* **Could not Advertise**: Cloudflare was unable to advertise the prefix. This status can occur for multiple reasons, but usually occurs when you are not allowed to advertise a prefix.
* **Error**: A general error occurred during prefix advertisement.
### Rule IP prefixes
Each rule must include a group of IP prefixes in its definition. All IP prefixes inside a rule are evaluated as a whole, and you should set up a rule with multiple IP prefixes when you want the IP prefixes' aggregated traffic to trigger an alert or advertisement. For thresholds on singular IP prefixes or IP addresses, you can create an individual rule with one prefix and the desired rule parameters.
#### Rule IP prefixes example
For a rule with two prefix Classless Inter-Domain Routing (CIDR) blocks and a `packet_threshold` of `10000` as shown below, the rule will be flagged if the joint packet traffic of `192.168.0.0/24` and `172.118.0.0/24` is greater than `10000`. This also means that Cloudflare attempts to auto advertise both CIDR blocks if the rule has the auto advertisement flag enabled. Customers can also [configure Rule IP prefixes at scale using Cloudflare's API](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/rules/).
```json
{
"rules": [
{
"name": "Too many packets",
"prefixes": ["192.168.0.0/24", "172.118.0.0/24"],
"packet_threshold": 10000,
"automatic_advertisement": true,
"duration": "1m0s",
"type": "threshold"
}
]
}
```
For more granular thresholds, create a more focused rule as shown below.
```json
{
"rules": [
{
"name": "Too many packets",
"prefixes": ["172.118.0.0/24"],
"packet_threshold": 1000,
"automatic_advertisement": true,
"duration": "1m0s",
"type": "threshold"
}
]
}
```
---
title: Tutorials · Cloudflare Magic Network Monitoring docs
lastUpdated: 2025-04-09T10:15:00.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/tutorials/
md: https://developers.cloudflare.com/magic-network-monitoring/tutorials/index.md
---
* [Encrypt network flow data](https://developers.cloudflare.com/magic-network-monitoring/tutorials/encrypt-network-flow-data/)
* [GraphQL Analytics](https://developers.cloudflare.com/magic-network-monitoring/tutorials/graphql-analytics/)
* [DDoS testing guide](https://developers.cloudflare.com/magic-network-monitoring/tutorials/ddos-testing-guide/)
---
title: 404 - Page Not Found · Cloudflare Magic Transit docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/404/
md: https://developers.cloudflare.com/magic-transit/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About Magic Transit · Cloudflare Magic Transit docs
description: Magic Transit is a network security and performance solution that
offers Distributed Denial of Service (DDoS) protection, traffic acceleration,
and more for on-premise, cloud-hosted, and hybrid networks.
lastUpdated: 2025-12-19T09:32:41.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/about/
md: https://developers.cloudflare.com/magic-transit/about/index.md
---
Magic Transit is a network security and performance solution that offers Distributed Denial of Service (DDoS) protection, traffic acceleration, and more for on-premise, cloud-hosted, and hybrid networks.
Magic Transit delivers its connectivity, security, and performance benefits by serving as the front door to your IP network. This means it accepts IP packets destined for your network, processes them, and then outputs them to your origin infrastructure.
The Cloudflare network uses [Border Gateway Protocol (BGP)](https://www.cloudflare.com/learning/security/glossary/what-is-bgp/) to announce your company's IP address space, extending your network presence globally, and [anycast](https://www.cloudflare.com/learning/cdn/glossary/anycast-network/) to ingest your traffic. Today, Cloudflare's anycast global network spans [hundreds of cities worldwide](https://www.cloudflare.com/network/).
Once [packets](https://www.cloudflare.com/learning/network-layer/what-is-a-packet/) hit Cloudflare's network, Cloudflare inspects traffic for attacks, filters, steers, accelerates, and sends it to your origin. Magic Transit connects to your origin infrastructure using anycast Generic Routing Encapsulation (GRE) tunnels over the Internet or, with [Cloudflare Network Interconnect (CNI)](https://developers.cloudflare.com/network-interconnect/), through physical or virtual interconnect.
You have two options for your Magic Transit implementation: ingress traffic or ingress and [egress traffic](https://developers.cloudflare.com/magic-transit/reference/egress/). With an egress implementation, you must set up policy-based routing (PBR) or ensure default routing on your end forwards traffic to Cloudflare through tunnels.
```mermaid
flowchart LR
accTitle: Magic Transit
accDescr: Diagram showing how Magic Transit protects traffic on the customer's network.
A(DDoS
` tag, they do allow scripting when SVG files are opened directly as a top-level document.
* **Hyperlinks to other documents**: Makes SVG files less attractive for SEO spam and phishing.
* **References to cross-origin resources**: Stops third parties from tracking who is viewing the image.
SVG files can also contain embedded images in other formats, like JPEG and PNG, in the form of [Data URLs](https://developer.mozilla.org/en-US/docs/Web/HTTP/Basics_of_HTTP/Data_URLs). Cloudflare treats these embedded images just like other images that we process, and optimizes them too. Cloudflare does not support SVG files embedded in SVG recursively, though.
Cloudflare still uses Content Security Policy (CSP) headers to disable unwanted features, but filtering acts as a defense-in-depth in case these headers are lost (for instance, if the image was saved as a file and served elsewhere).
`svg-hush` is open-source. It is written in Rust and can filter SVG files in a streaming fashion without buffering, so it is fast enough for filtering on the fly.
For more information about `svg-hush`, refer to [Cloudflare GitHub repository](https://github.com/cloudflare/svg-hush).
### Format limitations
Since some image formats require longer computational times than others, Cloudflare has to find a proper balance between the time it takes to generate an image and to transfer it over the Internet.
Resizing requests might not be fulfilled with the format the user expects due to these trade-offs Cloudflare has to make. Images differ in size, transformations, codecs and all of these different aspects influence what compression codecs are used.
Cloudflare tries to choose the requested codec, but we operate on a best-effort basis and there are limits that our system needs to follow to satisfy all customers.
AVIF encoding, in particular, can be an order of magnitude slower than encoding to other formats. Cloudflare will fall back to WebP or JPEG if the image is too large to be encoded quickly.
#### Limits per format
Hard limits refers to the maximum image size to process. Soft limits refers to the limits existing when the system is overloaded.
| File format | Hard limits on the longest side (width or height) | Soft limits on the longest side (width or height) |
| - | - | - |
| AVIF | 1,200 pixels1 | 640 pixels |
| Other | 12,000 pixels | N/A |
| WebP | N/A | 2,560 pixels for lossy; 1920 pixels for lossless |
1Hard limit is 1,600 pixels when `format=avif` is explicitly used with [image transformations](https://developers.cloudflare.com/images/transform-images/).
All images have to be less than 70 MB. The maximum image area is limited to 100 megapixels (for example, 10,000 x 10,000 pixels large).
GIF/WebP animations are limited to a total of 50 megapixels (the sum of sizes of all frames). Animations that exceed this will be passed through unchanged without applying any transformations. Note that GIF is an outdated format and has very inefficient compression. High-resolution animations will be slow to process and will have very large file sizes. For video clips, Cloudflare recommends using [video formats like MP4 and WebM instead](https://developers.cloudflare.com/stream/).
Important
SVG files are passed through without resizing. This format is inherently scalable and does not need resizing.
AVIF format is supported on a best-effort basis. Images that cannot be compressed as AVIF will be served as WebP instead.
#### Progressive JPEG
While you can use the `format=jpeg` option to generate images in an interlaced progressive JPEG format, we will fallback to the baseline JPEG format for small and large images specified when:
* The area calculated by width x height is less than 150 x 150.
* The area calculated by width x height is greater than 3000 x 3000.
For example, a 50 x 50 tiny image is always formatted by `baseline-jpeg` even if you specify progressive jpeg (`format=jpeg`).
---
title: Tutorials · Cloudflare Images docs
lastUpdated: 2025-04-03T11:41:17.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/images/tutorials/
md: https://developers.cloudflare.com/images/tutorials/index.md
---
* [Optimize mobile viewing](https://developers.cloudflare.com/images/tutorials/optimize-mobile-viewing/)
* [Transform user-uploaded images before uploading to R2](https://developers.cloudflare.com/images/tutorials/optimize-user-uploaded-image/)
---
title: Upload images · Cloudflare Images docs
description: Cloudflare Images allows developers to upload images using
different methods, for a wide range of use cases.
lastUpdated: 2025-10-30T11:07:38.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/images/upload-images/
md: https://developers.cloudflare.com/images/upload-images/index.md
---
Cloudflare Images allows developers to upload images using different methods, for a wide range of use cases.
## Supported image formats
You can upload the following image formats to Cloudflare Images:
* PNG
* GIF (including animations)
* JPEG
* WebP (Cloudflare Images also supports uploading animated WebP files)
* SVG
* HEIC
Note
Cloudflare can ingest HEIC images for decoding, but they must be served in web-safe formats such as AVIF, WebP, JPG, or PNG.
## Dimensions and sizes
These are the maximum allowed sizes and dimensions when uploading to Images:
* Maximum image dimension is 12,000 pixels.
* Maximum image area is limited to 100 megapixels (for example, 10,000×10,000 pixels).
* Image metadata is limited to 1024 bytes (when uploaded and stored in Cloudflare).
* Images have a 10 megabyte (MB) size limit (when uploaded and stored in Cloudflare).
* Animated GIFs/WebP, including all frames, are limited to 50 megapixels (MP).
---
title: 404 - Page Not Found · Cloudflare Key Transparency Auditor docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/key-transparency/404/
md: https://developers.cloudflare.com/key-transparency/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API · Cloudflare Key Transparency Auditor docs
lastUpdated: 2024-09-24T11:10:22.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/key-transparency/api/
md: https://developers.cloudflare.com/key-transparency/api/index.md
---
* [Auditor](https://developers.cloudflare.com/key-transparency/api/auditor-information/)
* [Namespaces](https://developers.cloudflare.com/key-transparency/api/namespaces/)
* [Epochs](https://developers.cloudflare.com/key-transparency/api/epochs/)
---
title: Monitor the Auditor · Cloudflare Key Transparency Auditor docs
description: Cloudflare's Key Transparency Auditor validates Log audit proofs
and provides a signature for them. The Log can then distribute these
signatures to its end-users, and provides users with confidence that keys have
not been tampered with.
lastUpdated: 2024-09-27T14:40:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/key-transparency/monitor-the-auditor/
md: https://developers.cloudflare.com/key-transparency/monitor-the-auditor/index.md
---
Cloudflare's Key Transparency Auditor validates Log audit proofs and provides a signature for them. The Log can then distribute these signatures to its end-users, and provides users with confidence that keys have not been tampered with.
In order to verify our work, you can use [Plexi](https://github.com/cloudflare/plexi), a CLI tool that allows anyone to perform proof verification locally via a public [API](https://developers.cloudflare.com/key-transparency/api/).
## Features
* Verify authenticity of a signature, to confirm it has been signed by a given public key
* Verify the validity of [facebook/akd](https://github.com/facebook/akd) proofs
* List Logs an Auditor monitors
## Installation
| Environment | CLI Command |
| - | - |
| [Cargo](https://www.rust-lang.org/tools/install) (Rust 1.81+) | `cargo install plexi` |
## Usage
Use the `--help` option for more details about the commands and their options.
```bash
plexi [OPTIONS]
```
### Configure your auditor remote
`plexi` does not come with a default remote auditor, and you will need to choose your own.
You can do so either by passing `--remote-url=` or setting the `PLEXI_REMOTE_URL` environment variable.
A common remote is provided below:
| Name | Remote |
| - | - |
| Cloudflare | `https://plexi.key-transparency.cloudflare.com` |
If you have deployed your own auditor, you can add a remote by filing a [GitHub issue](https://github.com/cloudflare/plexi/issues).
### List monitored Logs
An auditor monitors multiple Logs at once. To discover which Logs an auditor is monitoring, run the following:
```shell
plexi ls --remote-url 'https://plexi.key-transparency.cloudflare.com'
whatsapp.key-transparency.v1
```
### Audit a signature
The Key Transparency Auditor vouches for Log validity by ensuring epoch uniqueness and verifying the associated proof.
`plexi audit` provides information about a given epoch and its validity. It can perform a local audit to confirm the auditor behaviour.
For instance, to verify WhatsApp Log auditted by Cloudflare Auditor, run the following:
```shell
> plexi audit --remote-url 'https://plexi.key-transparency.cloudflare.com' --namespace 'whatsapp.key-transparency.v1' --long
Namespace
Name : whatsapp.key-transparency.v1
Ciphersuite : ed25519(protobuf)
Signature (2024-09-23T16:53:45Z)
Epoch height : 489193
Epoch digest : cbe5097ae832a3ae51ad866104ffd4aa1f7479e873fd18df9cb96a02fc91ebfe
Signature : fe94973e19da826487b637c019d3ce52f0c08093ada00b4fe6563e2f8117b4345121342bc33aae249be47979dfe704478e2c18aed86e674df9f934b718949c08
Signature verification: success
Proof verification : success
```
---
title: 404 - Page Not Found · Cloudflare Workers KV docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/404/
md: https://developers.cloudflare.com/kv/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Workers Binding API · Cloudflare Workers KV docs
lastUpdated: 2024-11-20T15:28:21.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/api/
md: https://developers.cloudflare.com/kv/api/index.md
---
* [Read key-value pairs](https://developers.cloudflare.com/kv/api/read-key-value-pairs/)
* [Write key-value pairs](https://developers.cloudflare.com/kv/api/write-key-value-pairs/)
* [Delete key-value pairs](https://developers.cloudflare.com/kv/api/delete-key-value-pairs/)
* [List keys](https://developers.cloudflare.com/kv/api/list-keys/)
---
title: Key concepts · Cloudflare Workers KV docs
lastUpdated: 2024-09-03T13:14:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/concepts/
md: https://developers.cloudflare.com/kv/concepts/index.md
---
* [How KV works](https://developers.cloudflare.com/kv/concepts/how-kv-works/)
* [KV bindings](https://developers.cloudflare.com/kv/concepts/kv-bindings/)
* [KV namespaces](https://developers.cloudflare.com/kv/concepts/kv-namespaces/)
---
title: Examples · Cloudflare Workers KV docs
description: Explore the following examples for KV.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/examples/
md: https://developers.cloudflare.com/kv/examples/index.md
---
Explore the following examples for KV.
[Cache data with Workers KV](https://developers.cloudflare.com/kv/examples/cache-data-with-workers-kv/)
[Example of how to use Workers KV to build a distributed application configuration store.](https://developers.cloudflare.com/kv/examples/cache-data-with-workers-kv/)
[Build a distributed configuration store](https://developers.cloudflare.com/kv/examples/distributed-configuration-with-workers-kv/)
[Example of how to use Workers KV to build a distributed application configuration store.](https://developers.cloudflare.com/kv/examples/distributed-configuration-with-workers-kv/)
[Route requests across various web servers](https://developers.cloudflare.com/kv/examples/routing-with-workers-kv/)
[Example of how to use Workers KV to build a distributed application configuration store.](https://developers.cloudflare.com/kv/examples/routing-with-workers-kv/)
[Store and retrieve static assets](https://developers.cloudflare.com/kv/examples/workers-kv-to-serve-assets/)
[Example of how to use Workers KV to store static assets](https://developers.cloudflare.com/kv/examples/workers-kv-to-serve-assets/)
---
title: Demos and architectures · Cloudflare Workers KV docs
description: Learn how you can use KV within your existing application and architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/demos/
md: https://developers.cloudflare.com/kv/demos/index.md
---
Learn how you can use KV within your existing application and architecture.
## Demo applications
Explore the following demo applications for KV.
* [Queues Web Crawler:](https://github.com/cloudflare/queues-web-crawler) An example use-case for Queues, a web crawler built on Browser Rendering and Puppeteer. The crawler finds the number of links to Cloudflare.com on the site, and archives a screenshot to Workers KV.
## Reference architectures
Explore the following reference architectures that use KV:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Programmable Platforms](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[Workers for Platforms provide secure, scalable, cost-effective infrastructure for programmable platforms with global reach.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
[Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[You can connect a Cloudflare Worker to get data from Google BigQuery and pass it to Workers AI, to run AI Models, powered by serverless GPUs.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[A/B-testing using Workers](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/a-b-testing-using-workers/)
[Cloudflare's low-latency, fully serverless compute platform, Workers offers powerful capabilities to enable A/B testing using a server-side implementation.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/a-b-testing-using-workers/)
[Serverless global APIs](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[An example architecture of a serverless API on Cloudflare and aims to illustrate how different compute and data products could interact with each other.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
[Serverless image content management](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
[Leverage various components of Cloudflare's ecosystem to construct a scalable image management solution](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
---
title: Getting started · Cloudflare Workers KV docs
description: Workers KV provides low-latency, high-throughput global storage to
your Cloudflare Workers applications. Workers KV is ideal for storing user
configuration data, routing data, A/B testing configurations and
authentication tokens, and is well suited for read-heavy workloads.
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/get-started/
md: https://developers.cloudflare.com/kv/get-started/index.md
---
Workers KV provides low-latency, high-throughput global storage to your [Cloudflare Workers](https://developers.cloudflare.com/workers/) applications. Workers KV is ideal for storing user configuration data, routing data, A/B testing configurations and authentication tokens, and is well suited for read-heavy workloads.
This guide instructs you through:
* Creating a KV namespace.
* Writing key-value pairs to your KV namespace from a Cloudflare Worker.
* Reading key-value pairs from a KV namespace.
You can perform these tasks through the Wrangler CLI or through the Cloudflare dashboard.
## Quick start
If you want to skip the setup steps and get started quickly, click on the button below.
[](https://deploy.workers.cloudflare.com/?url=https://github.com/cloudflare/docs-examples/tree/update/kv/kv/kv-get-started)
This creates a repository in your GitHub account and deploys the application to Cloudflare Workers. Use this option if you are familiar with Cloudflare Workers, and wish to skip the step-by-step guidance.
You may wish to manually follow the steps if you are new to Cloudflare Workers.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
## 1. Create a Worker project
New to Workers?
Refer to [How Workers works](https://developers.cloudflare.com/workers/reference/how-workers-works/) to learn about the Workers serverless execution model works. Go to the [Workers Get started guide](https://developers.cloudflare.com/workers/get-started/guide/) to set up your first Worker.
* CLI
Create a new Worker to read and write to your KV namespace.
1. Create a new project named `kv-tutorial` by running:
* npm
```sh
npm create cloudflare@latest -- kv-tutorial
```
* yarn
```sh
yarn create cloudflare kv-tutorial
```
* pnpm
```sh
pnpm create cloudflare@latest kv-tutorial
```
For setup, select the following options:
* For *What would you like to start with?*, choose `Hello World example`.
* For *Which template would you like to use?*, choose `Worker only`.
* For *Which language do you want to use?*, choose `TypeScript`.
* For *Do you want to use git for version control?*, choose `Yes`.
* For *Do you want to deploy your application?*, choose `No` (we will be making some changes before deploying).
This creates a new `kv-tutorial` directory, illustrated below.
Your new `kv-tutorial` directory includes:
* A `"Hello World"` [Worker](https://developers.cloudflare.com/workers/get-started/guide/#3-write-code) in `index.ts`.
* A [`wrangler.jsonc`](https://developers.cloudflare.com/workers/wrangler/configuration/) configuration file. `wrangler.jsonc` is how your `kv-tutorial` Worker accesses your kv database.
2. Change into the directory you just created for your Worker project:
```sh
cd kv-tutorial
```
Note
If you are familiar with Cloudflare Workers, or initializing projects in a Continuous Integration (CI) environment, initialize a new project non-interactively by setting `CI=true` as an [environmental variable](https://developers.cloudflare.com/workers/configuration/environment-variables/) when running `create cloudflare@latest`.
For example: `CI=true npm create cloudflare@latest kv-tutorial --type=simple --git --ts --deploy=false` creates a basic "Hello World" project ready to build on.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select **Create application**.
3. Select **Start with Hello World!** > **Get started**.
4. Name your Worker. For this tutorial, name your Worker `kv-tutorial`.
5. Select **Deploy**.
* npm
```sh
npm create cloudflare@latest -- kv-tutorial
```
* yarn
```sh
yarn create cloudflare kv-tutorial
```
* pnpm
```sh
pnpm create cloudflare@latest kv-tutorial
```
## 2. Create a KV namespace
A [KV namespace](https://developers.cloudflare.com/kv/concepts/kv-namespaces/) is a key-value database replicated to Cloudflare's global network.
* CLI
You can use [Wrangler](https://developers.cloudflare.com/workers/wrangler/) to create a new KV namespace. You can also use it to perform operations such as put, list, get, and delete within your KV namespace.
Note
KV operations are scoped to your account.
To create a KV namespace via Wrangler:
1. Open your terminal and run the following command:
```sh
npx wrangler kv namespace create
```
The `npx wrangler kv namespace create ` subcommand takes a new binding name as its argument. A KV namespace is created using a concatenation of your Worker's name (from your Wrangler file) and the binding name you provide. A `` is randomly generated for you.
For this tutorial, use the binding name `USERS_NOTIFICATION_CONFIG`.
```sh
npx wrangler kv namespace create
```
```sh
🌀 Creating namespace with title "USERS_NOTIFICATION_CONFIG"
✨ Success!
Add the following to your configuration file in your kv_namespaces array:
{
"kv_namespaces": [
{
"binding": "USERS_NOTIFICATION_CONFIG",
"id": ""
}
]
}
```
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers KV** page.
[Go to **Workers KV**](https://dash.cloudflare.com/?to=/:account/workers/kv/namespaces)
2. Select **Create instance**.
3. Enter a name for your namespace. For this tutorial, use `kv_tutorial_namespace`.
4. Select **Create**.
## 3. Bind your Worker to your KV namespace
You must create a binding to connect your Worker with your KV namespace. [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) allow your Workers to access resources, like KV, on the Cloudflare developer platform.
Bindings
A binding is how your Worker interacts with external resources such as [KV namespaces](https://developers.cloudflare.com/kv/concepts/kv-namespaces/). A binding is a runtime variable that the Workers runtime provides to your code. You can declare a variable name in your Wrangler file that binds to these resources at runtime, and interact with them through this variable. Every binding's variable name and behavior is determined by you when deploying the Worker.
Refer to [Environment](https://developers.cloudflare.com/kv/reference/environments/) for more information.
To bind your KV namespace to your Worker:
* CLI
1. In your Wrangler file, add the following with the values generated in your terminal from [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace):
* wrangler.jsonc
```jsonc
{
"kv_namespaces": [
{
"binding": "USERS_NOTIFICATION_CONFIG",
"id": ""
}
]
}
```
* wrangler.toml
```toml
[[kv_namespaces]]
binding = "USERS_NOTIFICATION_CONFIG"
id = ""
```
Binding names do not need to correspond to the namespace you created. Binding names are only a reference. Specifically:
* The value (string) you set for `binding` is used to reference this KV namespace in your Worker. For this tutorial, this should be `USERS_NOTIFICATION_CONFIG`.
* The binding must be [a valid JavaScript variable name](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Guide/Grammar_and_types#variables). For example, `binding = "MY_KV"` or `binding = "routingConfig"` would both be valid names for the binding.
* Your binding is available in your Worker at `env.` from within your Worker. For this tutorial, the binding is available at `env.USERS_NOTIFICATION_CONFIG`.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select the `kv-tutorial` Worker you created in [step 1](https://developers.cloudflare.com/kv/get-started/#1-create-a-worker-project).
3. Got to the **Bindings** tab, then select **Add binding**.
4. Select **KV namespace** > **Add binding**.
5. Name your binding (`BINDING_NAME`) in **Variable name**, then select the KV namespace (`kv_tutorial_namespace`) you created in [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace) from the dropdown menu.
6. Select **Add binding** to deploy your binding.
* wrangler.jsonc
```jsonc
{
"kv_namespaces": [
{
"binding": "USERS_NOTIFICATION_CONFIG",
"id": ""
}
]
}
```
* wrangler.toml
```toml
[[kv_namespaces]]
binding = "USERS_NOTIFICATION_CONFIG"
id = ""
```
## 4. Interact with your KV namespace
You can interact with your KV namespace via [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/) or directly from your [Workers](https://developers.cloudflare.com/workers/) application.
### 4.1. Write a value
* CLI
To write a value to your empty KV namespace using Wrangler:
1. Run the `wrangler kv key put` subcommand in your terminal, and input your key and value respectively. `` and `` are values of your choice.
```sh
npx wrangler kv key put --binding= "" ""
```
In this tutorial, you will add a key `user_1` with value `enabled` to the KV namespace you created in [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace).
```sh
npx wrangler kv key put --binding=USERS_NOTIFICATION_CONFIG "user_1" "enabled"
```
```sh
Writing the value "enabled" to key "user_1" on namespace .
```
Using `--namespace-id`
Instead of using `--binding`, you can also use `--namespace-id` to specify which KV namespace should receive the operation:
```sh
npx wrangler kv key put --namespace-id= "" ""
```
```sh
Writing the value "" to key "" on namespace .
```
Storing values in remote KV namespace
By default, the values are written locally. To create a key and a value in your remote KV namespace, add the `--remote` flag at the end of the command:
```sh
npx wrangler kv key put --namespace-id=xxxxxxxxxxxxxxxx "" ""
```
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers KV** page.
[Go to **Workers KV**](https://dash.cloudflare.com/?to=/:account/workers/kv/namespaces)
2. Select the KV namespace you created (`kv_tutorial_namespace`).
3. Go to the **KV Pairs** tab.
4. Enter a `` of your choice.
5. Enter a `` of your choice.
6. Select **Add entry**.
### 4.2. Get a value
* CLI
To access the value from your KV namespace using Wrangler:
1. Run the `wrangler kv key get` subcommand in your terminal, and input your key value:
```sh
npx wrangler kv key get --binding= ""
```
In this tutorial, you will get the value of the key `user_1` from the KV namespace you created in [step 2](https://developers.cloudflare.com/kv/get-started/#2-create-a-kv-namespace).
Note
To view the value directly within the terminal, you use the `--text` flag.
```sh
npx wrangler kv key get --binding=USERS_NOTIFICATION_CONFIG "user_1" --text
```
Similar to the `put` command, the `get` command can also be used to access a KV namespace in two ways - with `--binding` or `--namespace-id`:
Warning
Exactly **one** of `--binding` or `--namespace-id` is required.
Refer to the [`kv bulk` documentation](https://developers.cloudflare.com/kv/reference/kv-commands/#kv-bulk) to write a file of multiple key-value pairs to a given KV namespace.
* Dashboard
You can view key-value pairs directly from the dashboard.
1. In the Cloudflare dashboard, go to the **Workers KV** page.
[Go to **Workers KV**](https://dash.cloudflare.com/?to=/:account/workers/kv/namespaces)
2. Go to the KV namespace you created (`kv_tutorial_namespace`).
3. Go to the **KV Pairs** tab.
## 5. Access your KV namespace from your Worker
* CLI
Note
When using [`wrangler dev`](https://developers.cloudflare.com/workers/wrangler/commands/#dev) to develop locally, Wrangler defaults to using a local version of KV to avoid interfering with any of your live production data in KV. This means that reading keys that you have not written locally returns null.
To have `wrangler dev` connect to your Workers KV namespace running on Cloudflare's global network, you can set `"remote" : true` in the KV binding configuration. Refer to the [remote bindings documentation](https://developers.cloudflare.com/workers/development-testing/#remote-bindings) for more information.
Also refer to [KV binding docs](https://developers.cloudflare.com/kv/concepts/kv-bindings/#use-kv-bindings-when-developing-locally).
1. In your Worker script, add your KV binding in the `Env` interface. If you have bootstrapped your project with JavaScript, this step is not required.
```ts
interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
// ... other binding types
}
```
2. Use the `put()` method on `USERS_NOTIFICATION_CONFIG` to create a new key-value pair. You will add a new key `user_2` with value `disabled` to your KV namespace.
```ts
let value = await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
```
3. Use the KV `get()` method to fetch the data you stored in your KV namespace. You will fetch the value of the key `user_2` from your KV namespace.
```ts
let value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
```
Your Worker code should look like this:
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
The code above:
1. Writes a key to your KV namespace using KV's `put()` method.
2. Reads the same key using KV's `get()` method.
3. Checks if the key is null, and returns a `404` response if it is.
4. If the key is not null, it returns the value of the key.
5. Uses JavaScript's [`try...catch`](https://developer.mozilla.org/docs/Web/JavaScript/Reference/Statements/try...catch) exception handling to catch potential errors. When writing or reading from any service, such as Workers KV or external APIs using `fetch()`, you should expect to handle exceptions explicitly.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Go to the `kv-tutorial` Worker you created.
3. Select **Edit Code**.
4. Clear the contents of the `workers.js` file, then paste the following code.
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
The code above:
1. Writes a key to `BINDING_NAME` using KV's `put()` method.
2. Reads the same key using KV's `get()` method, and returns an error if the key is null (or in case the key is not set, or does not exist).
3. Uses JavaScript's [`try...catch`](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Statements/try...catch) exception handling to catch potential errors. When writing or reading from any service, such as Workers KV or external APIs using `fetch()`, you should expect to handle exceptions explicitly.
The browser should simply return the `VALUE` corresponding to the `KEY` you have specified with the `get()` method.
5. Select the dropdown arrow next to **Deploy** and select **Save**.
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
* JavaScript
```js
export default {
async fetch(request, env, ctx) {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
};
```
* TypeScript
```ts
export interface Env {
USERS_NOTIFICATION_CONFIG: KVNamespace;
}
export default {
async fetch(request, env, ctx): Promise {
try {
await env.USERS_NOTIFICATION_CONFIG.put("user_2", "disabled");
const value = await env.USERS_NOTIFICATION_CONFIG.get("user_2");
if (value === null) {
return new Response("Value not found", { status: 404 });
}
return new Response(value);
} catch (err) {
console.error(`KV returned error:`, err);
const errorMessage =
err instanceof Error
? err.message
: "An unknown error occurred when accessing KV storage";
return new Response(errorMessage, {
status: 500,
headers: { "Content-Type": "text/plain" },
});
}
},
} satisfies ExportedHandler;
```
## 6. Deploy your Worker
Deploy your Worker to Cloudflare's global network.
* CLI
1. Run the following command to deploy KV to Cloudflare's global network:
```sh
npm run deploy
```
2. Visit the URL for your newly created Workers KV application.
For example, if the URL of your new Worker is `kv-tutorial..workers.dev`, accessing `https://kv-tutorial..workers.dev/` sends a request to your Worker that writes (and reads) from Workers KV.
* Dashboard
1. In the Cloudflare dashboard, go to the **Workers & Pages** page.
[Go to **Workers & Pages**](https://dash.cloudflare.com/?to=/:account/workers-and-pages)
2. Select your `kv-tutorial` Worker.
3. Select **Deployments**.
4. From the **Version History** table, select **Deploy version**.
5. From the **Deploy version** page, select **Deploy**.
This deploys the latest version of the Worker code to production.
## Summary
By finishing this tutorial, you have:
1. Created a KV namespace
2. Created a Worker that writes and reads from that namespace
3. Deployed your project globally.
## Next steps
If you have any feature requests or notice any bugs, share your feedback directly with the Cloudflare team by joining the [Cloudflare Developers community on Discord](https://discord.cloudflare.com).
* Learn more about the [KV API](https://developers.cloudflare.com/kv/api/).
* Understand how to use [Environments](https://developers.cloudflare.com/kv/reference/environments/) with Workers KV.
* Read the Wrangler [`kv` command documentation](https://developers.cloudflare.com/kv/reference/kv-commands/).
---
title: Glossary · Cloudflare Workers KV docs
description: Review the definitions for terms used across Cloudflare's KV documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/glossary/
md: https://developers.cloudflare.com/kv/glossary/index.md
---
Review the definitions for terms used across Cloudflare's KV documentation.
| Term | Definition |
| - | - |
| cacheTtl | CacheTtl is a parameter that defines the length of time in seconds that a KV result is cached in the global network location it is accessed from. |
| KV namespace | A KV namespace is a key-value database replicated to Cloudflare’s global network. A KV namespace must require a binding and an id. |
| metadata | A metadata is a serializable value you append to each KV entry. |
---
title: Platform · Cloudflare Workers KV docs
lastUpdated: 2024-09-03T13:14:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/platform/
md: https://developers.cloudflare.com/kv/platform/index.md
---
* [Pricing](https://developers.cloudflare.com/kv/platform/pricing/)
* [Limits](https://developers.cloudflare.com/kv/platform/limits/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
* [Release notes](https://developers.cloudflare.com/kv/platform/release-notes/)
* [Event subscriptions](https://developers.cloudflare.com/kv/platform/event-subscriptions/)
---
title: Reference · Cloudflare Workers KV docs
lastUpdated: 2024-09-03T13:14:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/reference/
md: https://developers.cloudflare.com/kv/reference/index.md
---
* [Wrangler KV commands](https://developers.cloudflare.com/kv/reference/kv-commands/)
* [Environments](https://developers.cloudflare.com/kv/reference/environments/)
* [Data security](https://developers.cloudflare.com/kv/reference/data-security/)
* [FAQ](https://developers.cloudflare.com/kv/reference/faq/)
---
title: Tutorials · Cloudflare Workers KV docs
description: View tutorials to help you get started with KV.
lastUpdated: 2025-05-06T17:35:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/tutorials/
md: https://developers.cloudflare.com/kv/tutorials/index.md
---
View tutorials to help you get started with KV.
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [Use Workers KV directly from Rust](https://developers.cloudflare.com/workers/tutorials/workers-kv-from-rust/) | over 1 year ago | Intermediate |
| [Build a todo list Jamstack application](https://developers.cloudflare.com/workers/tutorials/build-a-jamstack-app/) | over 1 year ago | Beginner |
## Videos
Cloudflare Workflows | Introduction (Part 1 of 3)
In this video, we introduce Cloudflare Workflows, the Newest Developer Platform Primitive at Cloudflare.
Cloudflare Workflows | Batching and Monitoring Your Durable Execution (Part 2 of 3)
Workflows exposes metrics such as execution, error rates, steps, and total duration!
Build a URL Shortener with an AI-based admin section
We are building a URL Shortener, shrty.dev, on Cloudflare. The apps uses Workers KV and Workers Analytics engine. Craig decided to build with Workers AI runWithTools to provide a chat interface for admins.
Build Rust Powered Apps
In this video, we will show you how to build a global database using workers-rs to keep track of every country and city you’ve visited.
Stateful Apps with Cloudflare Workers
Learn how to access external APIs, cache and retrieve data using Workers KV, and create SQL-driven applications with Cloudflare D1.
---
title: Observability · Cloudflare Workers KV docs
lastUpdated: 2024-09-17T08:47:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/kv/observability/
md: https://developers.cloudflare.com/kv/observability/index.md
---
* [Metrics and analytics](https://developers.cloudflare.com/kv/observability/metrics-analytics/)
---
title: KV REST API · Cloudflare Workers KV docs
lastUpdated: 2025-05-20T08:19:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/kv/workers-kv-api/
md: https://developers.cloudflare.com/kv/workers-kv-api/index.md
---
---
title: 404 - Page Not Found · Cloudflare Load Balancing docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/404/
md: https://developers.cloudflare.com/load-balancing/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Additional configuration · Cloudflare Load Balancing docs
description: Beyond creating a simple load balancer, you may want to further
customize how your load balancer routes traffic or integrate your load
balancer with other Cloudflare products.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/additional-options/
md: https://developers.cloudflare.com/load-balancing/additional-options/index.md
---
Beyond [creating a simple load balancer](https://developers.cloudflare.com/load-balancing/load-balancers/create-load-balancer/), you may want to further customize how your load balancer routes traffic or integrate your load balancer with other Cloudflare products.
## Customize load balancer behavior
* Route traffic according to characteristics of each request by [creating custom rules](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-rules/)
* Protect at-risk endpoints from reaching failover by [setting up load shedding](https://developers.cloudflare.com/load-balancing/additional-options/load-shedding/)
* Take endpoints out of rotation for [planned maintenance](https://developers.cloudflare.com/load-balancing/additional-options/planned-maintenance/)
## Integrate with other Cloudflare products
* Bring load balancing to your TCP or UDP applications with [Cloudflare Spectrum](https://developers.cloudflare.com/load-balancing/additional-options/spectrum/)
* Further secure endpoint access with [Cloudflare Tunnel](https://developers.cloudflare.com/load-balancing/additional-options/cloudflare-tunnel/)
## Integrate with 3rd parties
* Increase visibility by [sending health monitor notifications to PagerDuty](https://developers.cloudflare.com/load-balancing/additional-options/pagerduty-integration/)
---
title: API reference · Cloudflare Load Balancing docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/api-reference/
md: https://developers.cloudflare.com/load-balancing/api-reference/index.md
---
---
title: Changelog · Cloudflare Load Balancing docs
description: Cloudflare Load Balancing now supports Monitor Groups, a powerful
new way to combine multiple health monitors into a single, logical group. This
allows you to create sophisticated health checks that more accurately reflect
the true availability of your applications by assessing multiple services at
once.
lastUpdated: 2025-05-06T18:53:27.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/changelog/
md: https://developers.cloudflare.com/load-balancing/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/load-balancing.xml)
## 2025-10-16
**Monitor Groups for Advanced Health Checking With Load Balancing**
Cloudflare Load Balancing now supports Monitor Groups, a powerful new way to combine multiple health monitors into a single, logical group. This allows you to create sophisticated health checks that more accurately reflect the true availability of your applications by assessing multiple services at once.
With Monitor Groups, you can ensure that all critical components of an application are healthy before sending traffic to an origin pool, enabling smarter failover decisions and greater resilience. This feature is now available via the API for customers with an Enterprise Load Balancing subscription.
#### What you can do:
* **Combine Multiple Monitors**: Group different health monitors (for example, HTTP, TCP) that check various application components, like a primary API gateway and a specific `/login` service.
* **Isolate Monitors for Observation**: Mark a monitor as "monitoring only" to receive alerts and data without it affecting a pool's health status or traffic steering. This is perfect for testing new checks or observing non-critical dependencies.
* **Improve Steering Intelligence**: Latency for Dynamic Steering is automatically averaged across all active monitors in a group, providing a more holistic view of an origin's performance.
This enhancement is ideal for complex, multi-service applications where the health of one component depends on another. By aggregating health signals, Monitor Groups provide a more accurate and comprehensive assessment of your application's true status.
For detailed information and API configuration guides, please visit our [developer documentation](https://developers.cloudflare.com/load-balancing/monitors/monitor-groups) for Monitor Groups.
## 2025-08-15
**Steer Traffic by AS Number in Load Balancing Custom Rules**
You can now create more granular, network-aware Custom Rules in Cloudflare Load Balancing using the Autonomous System Number (ASN) of an incoming request.
This allows you to steer traffic with greater precision based on the network source of a request. For example, you can route traffic from specific Internet Service Providers (ISPs) or enterprise customers to dedicated infrastructure, optimize performance, or enforce compliance by directing certain networks to preferred data centers.

To get started, create a [Custom Rule](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-rules/) in your Load Balancer and select **AS Num** from the **Field** dropdown.
## 2025-08-06
**Improvements to Monitoring Using Zone Settings**
Cloudflare Load Balancing Monitors support loading and applying settings for a specific zone to monitoring requests to origin endpoints. This feature has been migrated to new infrastructure to improve reliability, performance, and accuracy.
All zone monitors have been tested against the new infrastructure. There should be no change to health monitoring results of currently healthy and active pools. Newly created or re-enabled pools may need validation of their monitor zone settings before being introduced to service, especially regarding correct application of mTLS.
#### What you can expect:
* More reliable application of zone settings to monitoring requests, including
* Authenticated Origin Pulls
* Aegis Egress IP Pools
* Argo Smart Routing
* HTTP/2 to Origin
* Improved support and bug fixes for retries, redirects, and proxied origin resolution
* Improved performance and reliability of monitoring requests withing the Cloudflare network
* Unrelated CDN or WAF configuration changes should have no risk of impact to pool health
## 2025-06-04
**New Account-Level Load Balancing UI and Private Load Balancers**
We've made two large changes to load balancing:
* Redesigned the user interface, now centralized at the **account level**.
* Introduced [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to the UI, enabling you to manage traffic for all of your external and internal applications in a single spot.
This update streamlines how you manage load balancers across multiple zones and extends robust traffic management to your private network infrastructure.

**Key Enhancements:**
* **Account-Level UI Consolidation:**
* **Unified Management:** Say goodbye to navigating individual zones for load balancing tasks. You can now view, configure, and monitor all your load balancers across every zone in your account from a single, intuitive interface at the account level.
* **Improved Efficiency:** This centralized approach provides a more streamlined workflow, making it faster and easier to manage both your public-facing and internal traffic distribution.
* **Private Network Load Balancing:**
* **Secure Internal Application Access:** Create [**Private Load Balancers**](https://developers.cloudflare.com/load-balancing/private-network/) to distribute traffic to applications hosted within your private network, ensuring they are not exposed to the public Internet.
* **WARP & Magic WAN Integration:** Effortlessly direct internal traffic from users connected via Cloudflare WARP or through your Magic WAN infrastructure to the appropriate internal endpoint pools.
* **Enhanced Security for Internal Resources:** Combine reliable Load Balancing with Zero Trust access controls to ensure your internal services are both performant and only accessible by verified users.

## 2025-05-06
**UDP and ICMP Monitor Support for Private Load Balancing Endpoints**
Cloudflare Load Balancing now supports **UDP (Layer 4)** and **ICMP (Layer 3)** health monitors for **private endpoints**. This makes it simple to track the health and availability of internal services that don’t respond to HTTP, TCP, or other protocol probes.
#### What you can do:
* Set up **ICMP ping monitors** to check if your private endpoints are reachable.
* Use **UDP monitors** for lightweight health checks on non-TCP workloads, such as DNS, VoIP, or custom UDP-based services.
* Gain better visibility and uptime guarantees for services running behind **Private Network Load Balancing**, without requiring public IP addresses.
This enhancement is ideal for internal applications that rely on low-level protocols, especially when used in conjunction with [**Cloudflare Tunnel**](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/), [**WARP**](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/), and [**Magic WAN**](https://developers.cloudflare.com/magic-wan/) to create a secure and observable private network.
Learn more about [Private Network Load Balancing](https://developers.cloudflare.com/load-balancing/private-network/) or view the full list of [supported health monitor protocols](https://developers.cloudflare.com/load-balancing/monitors/#supported-protocols).
## 2025-04-15
**Introducing Support for Orange-Clouded Origin Resolution**
Newly created Cloudflare Load Balancers will resolve orange-clouded origin addresses, provided the origins belong to the same account and zone as the Load Balancer. Existing Load Balancers will continue using the current resolution method. If ownership validation fails, the new system falls back to the existing behavior and defaults to a gray-clouded (DNS-only) lookup, typically resolving to anycast addresses.
## 2025-03-13
**Update to Load Balancing analytics**
Load Balancing request rates in analytics may decrease for some customers as an improvement is made to our infrastructure. This decrease in Load Balancing analytics does not indicate a decrease in HTTP requests received.
## 2025-02-20
**Zone name added to Load Balancing API responses**
Load Balancing API responses for Load Balancers now include a `zone_name` property, which provides the name of the zone in the response data.
## 2025-02-10
**Fix for Cloudflare Tunnel Consistency**
Fixes to improve the consistency of Cloudflare Tunnel handling within Cloudflare Load Balancers. These changes ensure more reliable and predictable routing, particularly when tunnels are involved.
## 2025-01-24
**Update to Cloudflare Tunnel Steering**
Introduced changes to the resolution of proxied domains that are backed by Cloudflare Tunnels on the same zone. These changes correct how orange-clouded records are steered to Cloudflare Tunnels via Cloudflare Load Balancers.
## 2025-01-16
**Update to Pool Health Monitoring**
We made changes to how we resolve and monitor proxied origins to assess pool health. Our analysis indicates no impact to customer configurations or operations. Contact customer support if you notice any unexpected behavior.
## 2024-12-20
**Load Balancing with the China Network**
You can now enable load balancers to be deployed to the [China Network](https://developers.cloudflare.com/china-network/). Refer to the [documentation](https://developers.cloudflare.com/load-balancing/additional-options/load-balancing-china/) for more details.
---
title: Get started · Cloudflare Load Balancing docs
description: "Get started with load balancing in one of two ways:"
lastUpdated: 2025-01-31T09:20:50.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/get-started/
md: https://developers.cloudflare.com/load-balancing/get-started/index.md
---
Get started with load balancing in one of two ways:
* [Quickstart](https://developers.cloudflare.com/load-balancing/get-started/quickstart/): Get up and running quickly with Load Balancing.
* [Learning path](https://developers.cloudflare.com/learning-paths/load-balancing/concepts/): Check an in-depth walkthrough for how to plan and set up a load balancer.
---
title: Load balancers · Cloudflare Load Balancing docs
description: A load balancer distributes traffic among pools according to pool
health and traffic steering policies. Each load balancer is identified by its
DNS hostname (lb.example.com, dev.example.com, etc.) or IP address.
lastUpdated: 2025-08-20T20:59:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/load-balancers/
md: https://developers.cloudflare.com/load-balancing/load-balancers/index.md
---
A load balancer distributes traffic among pools according to [pool health](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/) and [traffic steering policies](https://developers.cloudflare.com/load-balancing/understand-basics/traffic-steering/steering-policies/). Each load balancer is identified by its DNS hostname (`lb.example.com`, `dev.example.com`, etc.) or IP address.
Note
For an overview of how the Cloudflare Load Balancing solution works, refer to [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/). For more background information on what load balancers are, refer to the Cloudflare [Learning Center](https://www.cloudflare.com/learning/performance/what-is-load-balancing/).
***
## Common configurations
For suggestions, refer to [Common load balancer configurations](https://developers.cloudflare.com/load-balancing/load-balancers/common-configurations/).
## Public vs. Private Load Balancers
Public Load Balancers are designed to handle traffic from the public Internet. When deployed, they automatically receive a hostname, making them immediately accessible. These load balancers can direct traffic to a range of destinations, including public hostnames, public IP addresses, and private IP addresses.
Private Load Balancers, in contrast, are meant for internal use within private networks. They do not automatically receive a hostname, but one can be assigned via Gateway Firewall Policies or through an internal DNS system. Private Load Balancers only accept traffic over a private network on-ramp, such as [Cloudflare WARP](https://developers.cloudflare.com/warp-client/) or [Magic WAN](https://developers.cloudflare.com/magic-wan/). They are capable of forwarding traffic exclusively to private IP addresses.
## Load balancing and existing DNS records
For details about DNS records, refer to [DNS records for load balancing](https://developers.cloudflare.com/load-balancing/load-balancers/dns-records/).
## HTTP keep-alive (persistent HTTP connection)
Cloudflare maintains keep-alive connections to improve performance and reduce cost of recurring TCP connects in the request transaction as Cloudflare proxies customer traffic from its edge network to the site's origin.
Ensure HTTP Keep-Alive connections are enabled on your origin. Cloudflare reuses open TCP connections for up to 15 minutes (900 seconds) after the last HTTP request. Origin web servers close TCP connections if too many are open. HTTP Keep-Alive helps avoid premature reset of connections for requests proxied by Cloudflare.
### Session cookies
**When using HTTP cookies to track and bind user sessions to a specific server**, configure [Session Affinity](https://developers.cloudflare.com/load-balancing/understand-basics/session-affinity/) to parse HTTP requests by cookie header. Doing so directs each request to the correct application server even when HTTP requests share the same TCP connection due to keep-alive.
**For example, F5 BIG-IP load balancers set a session cookie at the beginning of a TCP connection** (if none exists) and then ignore all cookies from subsequent HTTP requests on the same TCP connection. This tends to break session affinity because Cloudflare sends multiple HTTP sessions on the same TCP connection. Configuring the load balancer to parse HTTP requests by cookie headers avoids this issue.
***
## Create load balancers
For step-by-step guidance, refer to [Create a load balancer](https://developers.cloudflare.com/load-balancing/load-balancers/create-load-balancer/).
***
## Properties
For an up-to-date list of load balancer properties, refer to [Load balancer properties](https://developers.cloudflare.com/api/resources/load_balancers/methods/get/) in the Cloudflare API documentation.
***
## API commands
The Cloudflare API supports the following commands for load balancers.
| Command | Method | Endpoint |
| - | - | - |
| [Create Load Balancer](https://developers.cloudflare.com/api/resources/load_balancers/methods/create/) | `POST` | `/zones/:zone_id/load_balancers` |
| [Delete Load Balancer](https://developers.cloudflare.com/api/resources/load_balancers/methods/delete/) | `DELETE` | `/zones/:zone_id/load_balancers/:id` |
| [List Load Balancers](https://developers.cloudflare.com/api/resources/load_balancers/methods/list/) | `GET` | `/zones/:zone_id/load_balancers` |
| [Load Balancer Details](https://developers.cloudflare.com/api/resources/load_balancers/methods/get/) | `GET` | `/zones/:zone_id/load_balancers/:id` |
| [Overwrite specific properties](https://developers.cloudflare.com/api/resources/load_balancers/methods/edit/) | `PATCH` | `/zones/:zone_id/load_balancers/:id` |
| [Overwrite entire Load Balancer](https://developers.cloudflare.com/api/resources/load_balancers/methods/update/) | `PUT` | `/zones/:zone_id/load_balancers/:id` |
---
title: Monitors · Cloudflare Load Balancing docs
description: A monitor issues health monitor requests at regular intervals to
evaluate the health of each endpoint within a pool.
lastUpdated: 2025-11-17T15:22:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/monitors/
md: https://developers.cloudflare.com/load-balancing/monitors/index.md
---
A monitor issues health monitor requests at regular intervals to evaluate the health of each endpoint within a [pool](https://developers.cloudflare.com/load-balancing/pools/).
When a pool [becomes unhealthy](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/), your load balancer takes that pool out of the endpoint rotation.
```mermaid
flowchart RL
accTitle: Load balancing monitor flow
accDescr: Monitors issue health monitor requests, which validate the current status of servers within each pool.
Monitor -- Health Monitor ----> Endpoint2
Endpoint2 -- Response ----> Monitor
subgraph Pool
Endpoint1((Endpoint 1))
Endpoint2((Endpoint 2))
end
```
Health monitor requests that result in a status change for an endpoint are recorded as events in the Load Balancing event logs.
Note
Health monitors associated with load balancers are different from standalone [Health Checks](https://developers.cloudflare.com/health-checks/). For an overview of how the Cloudflare Load Balancing solution works, refer to [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/).
***
## Properties
For an up-to-date list of monitor properties, refer to [Monitor properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/list/) in our API documentation.
***
## Create monitors
For step-by-step guidance, refer to [Create monitors](https://developers.cloudflare.com/load-balancing/monitors/create-monitor/).
### Monitor Groups
Monitor Groups let you combine multiple health monitors into a single logical group to create more accurate, intelligent health checks for your applications. By aggregating results from several monitors, you can better reflect real application health and improve traffic steering resilience. For more details, refer to the [Monitor Groups](https://developers.cloudflare.com/load-balancing/monitors/monitor-groups/) documentation page.
***
## Health monitor regions
When you [attach a monitor to a pool](https://developers.cloudflare.com/load-balancing/monitors/create-monitor/#create-a-monitor), you can select multiple regions to increase reporting accuracy.
For each option selected in a pool's **Health Monitor Regions**, Cloudflare sends health monitor requests from three separate data centers in that region.

If the majority of data centers for that region pass the health monitor requests, that region is considered healthy. If the majority of regions is healthy, then the endpoint itself will be considered healthy.
### Configurations
**All Data Centers (Enterprise only)**
Health monitor probes are sent from every single data center in Cloudflare’s network to the endpoints within the associated pool. This allows probes to hit each endpoint during intervals set by the customer.
**All Regions**
Three health monitor probes per region are sent to each endpoint in the associated pool. There are a total of 13 regions, resulting in 39 probes.
**Regional**
Three health monitor probes are sent from each specified region within the pool configuration.
Warning
Because of how Cloudflare checks health from [multiple regions](#health-monitor-regions), adding multiple regions — or choosing to check health from **All Data Centers** — can send a lot of traffic to your endpoint.
The same problem can occur when setting low values for a monitor's **Interval**.
***
## Host header prioritization
The host headers used on health monitor requests can be configured either [on the monitor itself](https://developers.cloudflare.com/load-balancing/monitors/create-monitor/) or on the [endpoints within a pool](https://developers.cloudflare.com/load-balancing/pools/create-pool/).
When a host header is specified both on the monitor and on the endpoint, the host header configured on the endpoint takes precedence over the host header configured on the monitor.
When no host header is specified, Cloudflare uses the **Endpoint Address** configured on the endpoints as the host header for the health monitor requests.
For more details, refer to [Override HTTP Host headers](https://developers.cloudflare.com/load-balancing/additional-options/override-http-host-headers/).
***
## API commands
The Cloudflare API supports the following commands for monitors. Examples are given for user-level endpoint but apply to the account-level endpoint as well.
| Command | Method | Endpoint |
| - | - | - |
| [Create Monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/create/) | `POST` | `accounts/:account_id/load_balancers/monitors` |
| [Delete Monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/delete/) | `DELETE` | `accounts/:account_id/load_balancers/monitors/:id` |
| [List Monitors](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/list/) | `GET` | `accounts/:account_id/load_balancers/monitors` |
| [Monitor Details](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/get/) | `GET` | `accounts/:account_id/load_balancers/monitors/:id` |
| [Overwrite specific properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/edit/) | `PATCH` | `accounts/:account_id/load_balancers/monitors/:id` |
| [Overwrite existing monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/methods/update/) | `PUT` | `accounts/:account_id/load_balancers/monitors/:id` |
| [Preview Monitor](https://developers.cloudflare.com/api/resources/load_balancers/subresources/monitors/subresources/previews/methods/create/) | `POST` | `accounts/:account_id/load_balancers/monitors/:id/preview` |
## Supported protocols
The following table summarizes the different types of monitors available in Cloudflare Load Balancing, their monitoring types, and how each health check process evaluates the success criteria to determine endpoint health:
| Monitor type | Monitoring type | Description | Health check process | Success criteria |
| - | - | - | - | - |
| HTTP/HTTPS | Public and private | Used for HTTP and HTTPS endpoints with specific protocol attributes. | The probe is configured with settings and success criteria such as Method, Simulate Zone, Follow Redirects, Request Headers, and Response Body. The probe then evaluates the configured success criteria using the HTTP protocol. Throughout the configured timeout period, the TCP connection is kept active using [keep-alives](https://developers.cloudflare.com/fundamentals/reference/tcp-connections/#tcp-connections-and-keep-alives), even if no response is received. | Success is based on meeting the configured HTTP success criteria. No response within the configured timeout and retries is considered unhealthy. |
| TCP | Public and private | Checks TCP connectivity by attempting to open a connection to the endpoint. | The monitor sends a TCP SYN message to the specified port. A successful health check requires receiving a SYN/ACK message to establish the connection. The connection is closed by sending a FIN or RST packet, or by receiving a FIN packet from the endpoint. | Failure to establish a TCP connection within the configured timeout and retries is considered unhealthy. |
| ICMP Ping | Public and Tunnel | Confirms basic Layer 3 (L3) connectivity to the endpoint using ICMP. The endpoints need to be allowed to reply to ICMP packets and any intervening networking equipment must support ICMP. | The monitor sends an ICMP/ICMPv6 echo request (ping) and expects an ICMP/ICMPv6 echo reply from the endpoint. | The endpoint must reply to the ICMP ping within the configured timeout and retries to be considered healthy. |
| UDP-ICMP | Public and Tunnel | UDP-ICMP monitor works by sending a UDP probe packet after ICMP Ping monitor completes as healthy. | After receiving a successful ICMP reply, the monitor sends a UDP probe packet to the endpoint. If no ICMP Port Unreachable message is received, the endpoint is considered healthy. | If the monitor receives an ICMP Port Unreachable message within the configured timeout and retries, the endpoint is considered unhealthy. |
| SMTP | Public | Verifies SMTP availability at the application layer. | The monitor establishes a TCP connection and sends an SMTP HELO command. It expects a reply with code 250. The monitor then sends an SMTP QUIT command, expecting a reply with code 221. At the end of each interval, the TCP connection is closed by sending a TCP FIN packet. | The endpoint must respond with correct SMTP codes (250 for HELO, 221 for QUIT) within the configured timeout and retries to be considered healthy. |
---
title: Pools · Cloudflare Load Balancing docs
description: Within Cloudflare, pools represent your endpoints and how they are
organized. As such, a pool can be a group of several endpoints, or you could
also have only one endpoint (an origin server, for example) per pool.
lastUpdated: 2025-08-20T20:59:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/pools/
md: https://developers.cloudflare.com/load-balancing/pools/index.md
---
Within Cloudflare, pools represent your endpoints and how they are organized. As such, a pool can be a group of several endpoints, or you could also have only one endpoint (an origin server, for example) per pool.
If you are familiar with DNS terminology, think of a pool as a “record set,” except Cloudflare only returns addresses that are considered healthy. You can attach health monitors to individual pools for customized monitoring. A pool can have either a single monitor or a monitor group attached — but not both.
For more details about how endpoints and pools become unhealthy, refer to [Endpoint and pool health](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/).
Warning
Since load balancing targets are not limited to origin web servers, the term `endpoints` has been introduced. Refer to [Service-Specific Terms](https://www.cloudflare.com/service-specific-terms-other-terms/) for its use in the context of Cloudflare offerings, and to [load balancing concepts](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/) or [Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/load-balancing/) for use case examples.
On the [Load Balancing API](https://developers.cloudflare.com/api/resources/load_balancers/methods/get/), `origin` has been maintained.
***
## Properties
For an up-to-date list of pool properties, refer to [Pool properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/list/) in our API documentation.
***
## Create pools
For step-by-step guidance, refer to [Create pools](https://developers.cloudflare.com/load-balancing/pools/create-pool/).
***
## Per-endpoint Host header override
When your application needs specialized routing (`CNAME` setup or custom hosts like Heroku), change the `Host` header used in health monitor requests. For more details, refer to [Override HTTP Host headers](https://developers.cloudflare.com/load-balancing/additional-options/override-http-host-headers/).
***
## API commands
The Cloudflare API supports the following commands for pools. Examples are given for user-level endpoint but apply to the account-level endpoint as well.
| Command | Method | Endpoint |
| - | - | - |
| [Create Pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/create/) | `POST` | `accounts/:account_id/load_balancers/pools` |
| [Delete Pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/delete/) | `DELETE` | `accounts/:account_id/load_balancers/pools/:id` |
| [List Pools](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/list/) | `GET` | `accounts/:account_id/load_balancers/pools` |
| [Pool Details](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/get/) | `GET` | `accounts/:account_id/load_balancers/pools/:id` |
| [Pool Health Details](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/subresources/health/methods/get/) | `GET` | `account/:account_id/load_balancers/pools/:id/health` |
| [Overwrite specific properties](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/edit/) | `PATCH` | `accounts/:account_id/load_balancers/pools/:id` |
| [Overwrite existing pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/methods/update/) | `PUT` | `accounts/:account_id/load_balancers/pools/:id` |
| [Preview Pool](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/subresources/health/methods/create/) | `POST` | `account/:account_id/load_balancers/pools/:id/preview` |
| [List Pool References](https://developers.cloudflare.com/api/resources/load_balancers/subresources/pools/subresources/references/methods/get/) | `GET` | `accounts/:account_id/load_balancers/pools/:id/references` |
---
title: Private Network Load Balancing · Cloudflare Load Balancing docs
description: Use Private Network Load Balancing to load balance traffic between
servers within a data center or between private applications, and eliminate
the need for hardware appliances.
lastUpdated: 2025-12-16T16:11:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/private-network/
md: https://developers.cloudflare.com/load-balancing/private-network/index.md
---
Private Network Load Balancing enables you to load balance traffic between servers within a data center ([endpoint steering](https://developers.cloudflare.com/load-balancing/understand-basics/traffic-steering/origin-level-steering/)) and between private applications. This helps you eliminate the need for hardware appliances and facilitates the migration of your infrastructure to the cloud, providing advantages such as elastic scalability and enhanced reliability.
Private Network Load Balancing supports not only public IPs but also virtual IPs and private IPs as endpoint values.
Note
This page assumes a certain level of familiarity with how the Cloudflare Load Balancing solution works. For an introductory overview refer to [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/).
***
## Off-ramps
Off-ramps create a direct and secure way for Cloudflare to connect into your networks that are not publicly available.
Since traffic steering decisions or failover mechanisms rely on the health information of pools and endpoints, being able to input your virtual or private IPs directly as endpoints within your load balancer means you can better leverage existing health monitoring.
### Tunnel
Currently, to be able to connect to private IP origins, Cloudflare load balancers require a [Cloudflare tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/) with an associated [virtual network (VNet)](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/cloudflared/tunnel-virtual-networks/). If you are connecting to your endpoints using a [published application route](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/routing-to-tunnel/public-load-balancers) a VNet is not necessary.
Once the endpoint and virtual network (VNet) tunnel association is configured, Cloudflare can determine not only the tunnel health but also the health of the corresponding virtual or private IP targets.
Refer to [Set up Private Network Load Balancing for Public traffic to Tunnel](https://developers.cloudflare.com/load-balancing/private-network/public-to-tunnel/) for a detailed guide.
### Magic WAN
Private Network Load Balancing supports off-ramping traffic for Magic WAN tunnels, such as GRE, IPSec or CNI tunnels. For more information refer to the [Set up Private Network Load Balancing with Magic WAN](https://developers.cloudflare.com/load-balancing/private-network/magic-wan/).
***
## On-ramps
Private Network Load Balancing on-ramps, on the other hand, refer to secure paths between the end-user request and the Cloudflare network. Cloudflare Load Balancing supports traffic from [CDN](https://developers.cloudflare.com/cache/), [Spectrum](https://developers.cloudflare.com/spectrum/), [WARP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/) and [Magic WAN](https://developers.cloudflare.com/magic-wan/) and forward that traffic to a load balancer, and then egress to an endpoint behind any off-ramp (CDN/CNI/IPSec/GRE/Tunnel). Your traffic can ingress and egress by any on-ramp/off-ramp combination.
Note
When using [Spectrum](https://developers.cloudflare.com/spectrum/) as an on-ramp and [Magic WAN](https://developers.cloudflare.com/load-balancing/private-network/#magic-wan) as an off-ramp the [proxy protocol](https://developers.cloudflare.com/spectrum/how-to/enable-proxy-protocol/) setting in Spectrum is not supported.
***
## Use cases
* **Requests originating from the public Internet and directed to a private/internal service**: You can route requests from the Internet to your internal services on internal IPs - such as accounting or production automation systems - using [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/).
* **Intelligent traffic routing**: Benefit from failover for your private traffic and have the ability to monitor the health of these IP targets directly, rather than load balancing to a tunnel and only monitoring the health of the tunnel itself.
* **Host applications on non-standard ports**: Easily specify and route traffic to applications hosted on private IP addresses using non-standard ports, allowing greater flexibility in service configuration without requiring changes to existing infrastructure.
* **Public and Private Load Balancers**: Public LBs can direct Internet traffic to private IP addresses, supporting all L7 products like WAF and API Shield. Private LBs direct traffic originating from private networks to private IP addresses and require an on-ramp like WARP or Magic WAN.
---
title: Reference · Cloudflare Load Balancing docs
description: "See the following pages for more information about Cloudflare Load Balancing:"
lastUpdated: 2024-09-20T13:17:28.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/load-balancing/reference/
md: https://developers.cloudflare.com/load-balancing/reference/index.md
---
See the following pages for more information about Cloudflare Load Balancing:
* [Migration guides](https://developers.cloudflare.com/load-balancing/reference/migration-guides/)
* [Analytics](https://developers.cloudflare.com/load-balancing/reference/load-balancing-analytics/)
* [Regions API](https://developers.cloudflare.com/load-balancing/reference/region-mapping-api/)
* [Limitations](https://developers.cloudflare.com/load-balancing/reference/limitations/)
---
title: Reference architecture · Cloudflare Load Balancing docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/load-balancing/reference-architecture-external-link/
md: https://developers.cloudflare.com/load-balancing/reference-architecture-external-link/index.md
---
---
title: Troubleshooting · Cloudflare Load Balancing docs
description: "For more guidance related to common issues with load balancers,
refer to the following resources:"
lastUpdated: 2024-09-20T13:17:28.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/load-balancing/troubleshooting/
md: https://developers.cloudflare.com/load-balancing/troubleshooting/index.md
---
For more guidance related to common issues with load balancers, refer to the following resources:
* [Common error codes](https://developers.cloudflare.com/load-balancing/troubleshooting/common-error-codes/)
* [FAQs](https://developers.cloudflare.com/load-balancing/troubleshooting/load-balancing-faq/)
---
title: Concepts · Cloudflare Load Balancing docs
description: Review the following topics to learn more about the basic concepts
and components involved in Cloudflare Load Balancing.
lastUpdated: 2024-09-20T13:17:28.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/load-balancing/understand-basics/
md: https://developers.cloudflare.com/load-balancing/understand-basics/index.md
---
Review the following topics to learn more about the basic concepts and components involved in Cloudflare Load Balancing.
* [Load Balancing components](https://developers.cloudflare.com/load-balancing/understand-basics/load-balancing-components/)
* [Traffic steering](https://developers.cloudflare.com/load-balancing/understand-basics/traffic-steering/)
* [How endpoints and pools become unhealthy](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/)
* [Proxy status](https://developers.cloudflare.com/load-balancing/understand-basics/proxy-modes/)
* [Session affinity](https://developers.cloudflare.com/load-balancing/understand-basics/session-affinity/)
* [Adaptive routing](https://developers.cloudflare.com/load-balancing/understand-basics/adaptive-routing/)
---
title: 404 - Page Not Found · Cloudflare Log Explorer docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/404/
md: https://developers.cloudflare.com/log-explorer/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Log Explorer API · Cloudflare Log Explorer docs
description: Configuration and Log searches are also available via a public API.
lastUpdated: 2025-10-22T13:43:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/api/
md: https://developers.cloudflare.com/log-explorer/api/index.md
---
Configuration and Log searches are also available via a public API.
## Authentication
Authentication with the API can be done via an API token or API key with an email. Refer to [Create API token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) for further instructions.
For detailed information on permissions required for each Log Explorer feature, refer to the [Permissions](https://developers.cloudflare.com/log-explorer/#permissions) section.
## Query data
Log Explorer includes a SQL API for submitting queries.
For example, to find an HTTP request with a specific [Ray ID](https://developers.cloudflare.com/fundamentals/reference/cloudflare-ray-id/), use the following SQL query:
```bash
curl https://api.cloudflare.com/client/v4/zones/{zone_id}/logs/explorer/query/sql \
--header "Authorization: Bearer " \
--url-query query="SELECT clientRequestScheme, clientRequestHost, clientRequestMethod, edgeResponseStatus, clientRequestUserAgent FROM http_requests WHERE RayID = '806c30a3cec56817' LIMIT 1"
```
This command returns the following HTTP request details:
```json
{
"result": [
{
"clientrequestscheme": "https",
"clientrequesthost": "example.com",
"clientrequestmethod": "GET",
"clientrequestuseragent": "curl/7.88.1",
"edgeresponsestatus": 200
}
],
"success": true,
"errors": [],
"messages": []
}
```
As another example, you could find Cloudflare Access requests with selected columns from a specific timeframe by performing the following SQL query:
```bash
curl https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/explorer/query/sql \
--header "Authorization: Bearer " \
--url-query query="SELECT CreatedAt, AppDomain, AppUUID, Action, Allowed, Country, RayID, Email, IPAddress, UserUID FROM access_requests WHERE Date >= '2025-02-06' AND Date <= '2025-02-06' AND CreatedAt >= '2025-02-06T12:28:39Z' AND CreatedAt <= '2025-02-06T12:58:39Z'"
```
This command returns the following request details:
```json
{
"result": [
{
"createdat": "2025-01-14T18:17:55Z",
"appdomain": "example.com",
"appuuid": "a66b4ab0-ccdf-4d60-a6d0-54a59a827d92",
"action": "login",
"allowed": true,
"country": "us",
"rayid": "90fbb07c0b316957",
"email": "user@example.com",
"ipaddress": "1.2.3.4",
"useruid": "52859e81-711e-4de0-8b31-283336060e79"
}
],
"success": true,
"errors": [],
"messages": []
}
```
---
title: Changelog · Cloudflare Log Explorer docs
description: We've resolved a bug in Log Explorer that caused inconsistencies
between the custom SQL date field filters and the date picker dropdown.
Previously, users attempting to filter logs based on a custom date field via a
SQL query sometimes encountered unexpected results or mismatching dates when
using the interactive date picker.
lastUpdated: 2025-06-27T07:53:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/changelog/
md: https://developers.cloudflare.com/log-explorer/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/log-explorer.xml)
## 2025-11-13
**Fixed custom SQL date picker inconsistencies**
We've resolved a bug in Log Explorer that caused inconsistencies between the custom SQL date field filters and the date picker dropdown. Previously, users attempting to filter logs based on a custom date field via a SQL query sometimes encountered unexpected results or mismatching dates when using the interactive date picker.
This fix ensures that the custom SQL date field filters now align correctly with the selection made in the date picker dropdown, providing a reliable and predictable filtering experience for your log data. This is particularly important for users creating custom log views based on time-sensitive fields.
## 2025-11-13
**Log Explorer adds 14 new datasets**
We've significantly enhanced Log Explorer by adding support for 14 additional Cloudflare product datasets.
This expansion enables Operations and Security Engineers to gain deeper visibility and telemetry across a wider range of Cloudflare services. By integrating these new datasets, users can now access full context to efficiently investigate security incidents, troubleshoot application performance issues, and correlate logged events across different layers (like application and network) within a single interface. This capability is crucial for a complete and cohesive understanding of event flows across your Cloudflare environment.
The newly supported datasets include:
#### Zone Level
* `Dns_logs`
* `Nel_reports`
* `Page_shield_events`
* `Spectrum_events`
* `Zaraz_events`
#### Account Level
* `Audit Logs`
* `Audit_logs_v2`
* `Biso_user_actions`
* `DNS firewall logs`
* `Email_security_alerts`
* `Magic Firewall IDS`
* `Network Analytics`
* `Sinkhole HTTP`
* `ipsec_logs`
Note
`Auditlog` and `Auditlog_v2` datasets require `audit-log.read` permission for querying.
The `biso_user_actions` dataset requires either the `Super Admin` or `ZT PII` role for querying.
#### Example: Correlating logs
You can now use Log Explorer to query and filter with each of these datasets. For example, you can identify an IP address exhibiting suspicious behavior in the `FW_event` logs, and then instantly pivot to the `Network Analytics` logs or `Access` logs to see its network-level traffic profile or if it bypassed a corporate policy.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/) and the [Cloudflare Logs documentation](https://developers.cloudflare.com/logs/).
## 2025-11-11
**Resize your custom SQL window in Log Explorer**
We're excited to announce a quality-of-life improvement for Log Explorer users. You can now resize the custom SQL query window to accommodate longer and more complex queries.
Previously, if you were writing a long custom SQL query, the fixed-size window required excessive scrolling to view the full query. This update allows you to easily drag the bottom edge of the query window to make it taller. This means you can view your entire custom query at once, improving the efficiency and experience of writing and debugging complex queries.
To learn more and get started, refer to the [Log Explorer documentation](https://developers.cloudflare.com/log-explorer/).
## 2025-11-04
**Log Explorer now supports query cancellation**
We're excited to announce that Log Explorer users can now cancel queries that are currently running.
This new feature addresses a common pain point: waiting for a long, unintended, or misconfigured query to complete before you can submit a new, correct one. With query cancellation, you can immediately stop the execution of any undesirable query, allowing you to quickly craft and submit a new query, significantly improving your investigative workflow and productivity within Log Explorer.
## 2025-11-04
**Log Explorer now shows query result distribution**
We're excited to announce a new feature in Log Explorer that significantly enhances how you analyze query results: the Query results distribution chart.
This new chart provides a graphical distribution of your results over the time window of the query. Immediately after running a query, you will see the distribution chart above your result table. This visualization allows Log Explorer users to quickly spot trends, identify anomalies, and understand the temporal concentration of log events that match their criteria. For example, you can visually confirm if a spike in traffic or errors occurred at a specific time, allowing you to focus your investigation efforts more effectively. This feature makes it faster and easier to extract meaningful insights from your vast log data.
The chart will dynamically update to reflect the logs matching your current query.
## 2025-09-11
**Contextual pivots**
Directly from [Log Search](https://developers.cloudflare.com/log-explorer/log-search/) results, customers can pivot to other parts of the Cloudflare dashboard to immediately take action as a result of their investigation.
From the `http_requests` or `fw_events` dataset results, right click on an IP Address or JA3 Fingerprint to pivot to the Investigate portal to lookup the reputation of an IP address or JA3 fingerprint.

Easily learn about error codes by linking directly to our documentation from the **EdgeResponseStatus** or **OriginResponseStatus** fields.

From the `gateway_http` dataset, click on a **policyid** to link directly to the Zero Trust dashboard to review or make changes to a specific Gateway policy.

## 2025-09-11
**New results table view**
The results table view of **Log Search** has been updated with additional functionality and a more streamlined user experience. Users can now easily:
* Remove/add columns.
* Resize columns.
* Sort columns.
* Copy values from any field.

## 2025-09-03
**Logging headers and cookies using custom fields**
[Log Explorer](https://developers.cloudflare.com/log-explorer/) now supports logging and filtering on header or cookie fields in the [`http_requests` dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/).
Create a custom field to log desired header or cookie values into the `http_requests` dataset and Log Explorer will import these as searchable fields. Once configured, use the custom SQL editor in Log Explorer to view or filter on these requests.

For more details, refer to [Headers and cookies](https://developers.cloudflare.com/log-explorer/log-search/#headers-and-cookies).
## 2025-08-15
**Extended retention**
Customers can now rely on Log Explorer to meet their log retention compliance requirements.
Contract customers can choose to store their logs in Log Explorer for up to two years, at an additional cost of $0.10 per GB per month. Customers interested in this feature can contact their account team to have it added to their contract.
## 2025-07-09
**Usage tracking**
[Log Explorer](https://developers.cloudflare.com/log-explorer/) customers can now monitor their data ingestion volume to keep track of their billing. Monthly usage is displayed at the top of the [Log Search](https://developers.cloudflare.com/log-explorer/log-search/) and [Manage Datasets](https://developers.cloudflare.com/log-explorer/manage-datasets/) screens in Log Explorer.

## 2025-06-18
**Log Explorer is GA**
[Log Explorer](https://developers.cloudflare.com/log-explorer/) is now GA, providing native observability and forensics for traffic flowing through Cloudflare.
Search and analyze your logs, natively in the Cloudflare dashboard. These logs are also stored in Cloudflare's network, eliminating many of the costs associated with other log providers.

With Log Explorer, you can now:
* **Monitor security and performance issues with custom dashboards** – use natural language to define charts for measuring response time, error rates, top statistics and more.
* **Investigate and troubleshoot issues with Log Search** – use data type-aware search filters or custom sql to investigate detailed logs.
* **Save time and collaborate with saved queries** – save Log Search queries for repeated use or sharing with other users in your account.
* **Access Log Explorer at the account and zone level** – easily find Log Explorer at the account and zone level for querying any dataset.
For help getting started, refer to [our documentation](https://developers.cloudflare.com/log-explorer/).
---
title: Custom dashboards · Cloudflare Log Explorer docs
description: Custom dashboards allow you to create tailored dashboards to
monitor application security, performance, and usage. You can create monitors
for ongoing monitoring of a previous incident, use them to identify indicators
of suspicious activity, and access templates to help you get started.
lastUpdated: 2025-09-03T17:40:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/custom-dashboards/
md: https://developers.cloudflare.com/log-explorer/custom-dashboards/index.md
---
Custom dashboards allow you to create tailored dashboards to monitor application security, performance, and usage. You can create monitors for ongoing monitoring of a previous incident, use them to identify indicators of suspicious activity, and access templates to help you get started.
Note
Enterprise customers can create up to 100 dashboards.
Customers on Pro and Business plans can create up to 5 dashboards.
Dashboards provide a visual interface that displays key metrics and analytics, helping you monitor and analyze data efficiently. Different dashboards serve different purposes. For example, a security dashboard tracks attack attempts and threats, a performance dashboard monitors API latency and uptime, and a usage dashboard analyzes traffic patterns and user behavior.
Different metrics serve distinct roles in providing insights into your application's performance. For example, total HTTP requests offer an overview of traffic volume, while average response time helps assess application speed. Additionally, usage metrics such as traffic patterns and user behavior provide insight into how users interact with your application. These metrics together enable you to spot trends, identify problems, and make informed, data-driven decisions.
## Create a new dashboard
To create a new dashboard, go to the **Log Explorer** > **Dashboards** page.
[Go to **Custom dashboards**](https://dash.cloudflare.com/?to=/:account/log-explorer/dashboards)
When creating a dashboard, you have two options: building one from scratch or using a pre-designed template.
* A **templates** provide a faster way to set up a dashboard with commonly used metrics and charts. They are useful for standard use cases, such as monitoring security threats, API performance, or bot traffic. Templates help you get started quickly while still allowing modifications to fit your requirements.
* On the other hand, **from-scratch dashboard** gives you full control over its structure, allowing you to choose the exact datasets, metrics, and visualizations that fit your needs. This approach is ideal if you have specific monitoring goals or need a highly customized view of your data.
Choosing between these options depends on whether you need a quick setup with predefined insights or a fully customized dashboard tailored to your unique analysis needs.
### Create a dashboard from scratch
When creating a dashboard from scratch, select the option **Create new**. You can follow the instructions in the following sections to start adding charts to your dashboard.
#### Create a new chart
To create a new chart, select **Add chart**. There are two ways to create a chart:
* **Use a prompt**: Enter a query like `Compare status code ranges over time.` The AI model decides the most appropriate visualization and constructs your chart configuration.
* **Customize your chart**: Select the chart elements manually, including the chart type, title, dataset to query, metrics, and filters. This option gives you full control over your chart's structure.
Refer to the following sections for more information about the charts, datasets, fields, metrics, and filters available.
##### Chart types
The available chart types include:
* **Timeseries**: Displays trends over time, enabling comparisons across multiple series.
* **Categorical**: Compares proportions across different series.
* **Stat**: Highlights a single value, showing its delta and sparkline for quick insights.
* **Percentage**: Represents one value as a percentage of another.
* **Top N**: Identifies the highest-ranking values for a given attribute.
##### Datasets and metrics
The available metrics and filters vary based on the dataset you want to use. For example, when using the HTTP Requests dataset, you can select **origin response duration** as a metric. You can then choose your preferred aggregation method for that metric, such as total, median, or quantiles. The following table outlines the datasets, fields, and available metrics:
| Dataset | Field | Definition | Metrics |
| - | - | - | - |
| HTTP Requests | Requests | The number of requests sent by a client to a server over the HTTP protocol. | Total |
| | DNS Response Time | The time taken for a DNS query to be resolved, measured from when a request is made to when a response is received. | Total, Average, Median, 95th percentile, 99th percentile |
| | Time to First Byte | The duration from when a request is made to when the first byte of the response is received from the server. | Total, Average, Median, 95th percentile, 99th percentile |
| | Bytes returned to the Client | The amount of data (in bytes) sent from the server to the client in response to requests. | Total, Average, Median, 95th percentile, 99th percentile |
| | Number of visits | Unique visits or sessions to a website or application. | Total |
| | Origin response duration | The time taken by the origin server to process and respond to a request. | Total, Average, Median, 95th percentile, 99th percentile |
| Security Events | Security events | Actions taken by Application Security products such as WAF and Bot Management. | Total |
##### Filters
You can also adjust the scope of your analytics by entering filter conditions. This allows you to focus on the most relevant data.
1. Select **Add filter**.
2. Select a **field**, an **operator**, and a **value**. For example, to filter events by source IP address, select the *Source IP* field, select the *equals* operator, and enter the IP address.
3. Select **Apply**.
### Create a dashboard from a template
Alternatively, you can choose to create your dashboard using a pre-designed dashboard template. The templates available are:
* **Bot monitoring**: Allows you to identify automated traffic accessing your website.
* **API Security**: Allows you to monitor data transfers and exceptions for API endpoints in your application.
* **Account takeover**: Allows you to monitor login attempts, usage of leaked credentials, and account takeover attacks.
* **API Performance**: Allows you to view timing data for API endpoints in your application, along with error rates.
* **Performance monitoring**: Allows you to identify slow hosts and paths on your origin server, and view time to first byte metrics over time.
Choose one of the templates and select **Use template**.
## Edit a dashboard or chart
After creating your dashboard, to view your saved dashboards, select **Back to all dashboards** to access the full list. Regardless of the way you choose to create your dashboard, you can always edit existing charts and add new ones as needed.
## Further analysis
For each chart, you can:
* Review related traffic in [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/).
* Explore detailed logs in [Log Search](https://developers.cloudflare.com/log-explorer/log-search/).
This ensures deeper insights into your application's security, performance, and usage patterns.
---
title: FAQ · Cloudflare Log Explorer docs
description: Find answers to common questions about Log Explorer.
lastUpdated: 2025-10-09T09:19:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/faq/
md: https://developers.cloudflare.com/log-explorer/faq/index.md
---
## Which fields (or columns) are available for querying?
All fields listed in [Datasets](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/) for the [supported datasets](https://developers.cloudflare.com/log-explorer/manage-datasets/#supported-datasets) are viewable in Log Explorer.
## Why does my query not complete or time out?
Log Explorer performs best when query parameters focus on narrower ranges of time. You may experience query timeouts when your query would return a large quantity of data. Consider refining your query to improve performance.
## Why do I not see any logs in my queries after enabling the dataset?
Log Explorer starts ingesting logs from the moment you enable the dataset. It will not display logs for events that occurred before the dataset was enabled. Make sure that new events have been generated since enabling the dataset, and check again.
## My query returned an error. How do I figure out what went wrong?
We are actively working on improving error codes. If you receive a generic error, check your SQL syntax (if you are using the custom SQL feature), and make sure you have included a date and a limit. If the query still fails it is likely timing out. Try refining your filters.
## Where is the data stored?
The data is stored in Cloudflare R2. Each Log Explorer dataset is stored on a per-customer level, similar to Cloudflare D1, ensuring that your data is kept separate from that of other customers. In the future, this single-tenant storage model will provide you with the flexibility to create your own retention policies and decide in which regions you want to store your data.
## Does Log Explorer support Customer Metadata Boundary?
Customer Metadata Boundary is currently not supported for Log Explorer.
## Are there any constraints on the log volume that Log Explorer can support?
We are continually scaling the Log Explorer data platform. At present, Log Explorer supports log ingestion rates of up to 50,000 records per second. If your needs exceed this, contact your account team.
## How is Log Explorer different from Logpush? Do I need both?
Log Explorer allows you to search and analyze your Cloudflare logs directly in the dashboard or via API. [Logpush](https://developers.cloudflare.com/logs/logpush/), on the other hand, delivers raw logs to third-party SIEMs or storage systems. You generally do not need both, but some customers choose to use Log Explorer for quick investigation and Logpush for long-term storage or integration with other tools.
## Is there a free version or trial of Log Explorer?
Log Explorer is available as a paid add-on for any Application Services or Zero Trust purchase. There is no free version at this time.
## How is Log Explorer billed?
Log Explorer billing is based on the volume of logs indexed and stored, measured in gigabytes (GB). Your charges scale with the amount of log data you choose to retain in Log Explorer. Unlike query-based billing models (for example, BigQuery), charges are not based on how often you search or scan your data. Once logs are ingested and stored, you can query them without additional cost.
## Are logs from attack traffic included in my Log Explorer usage?
Yes. In general, Log Explorer bills based on the total volume of logs ingested and stored, including attack traffic. Since these logs are often critical for investigating security incidents, they are treated the same as all other log data.
However, logs generated from Layer 7 (L7) DDoS attack traffic are not ingested by default and therefore do not count toward your Log Explorer usage.
## How does Log Explorer store data in R2, and why do I not see it in my own R2 bucket?
Log Explorer uses Cloudflare Logpush and R2 behind the scenes to stream and store logs. For technical and performance reasons, the data is stored in internal, customer-specific R2 buckets managed by Cloudflare. These buckets are single-tenant to keep your data isolated, but they are not visible in your account's R2 interface. You are not billed separately for this storage — it is included in your Log Explorer usage.
## Are Custom Dashboards based on R2 Log Explorer data, or on GraphQL?
Custom Dashboards currently run on [GraphQL](https://developers.cloudflare.com/analytics/graphql-api/sampling/). Over time, this will evolve to include deeper integration between the two features, such as building charts directly from logs.
## How can I track my Log Explorer usage?
Your monthly usage is displayed at the top of the Log Search and Manage Datasets dashboard sections within Log Explorer.

## How do I turn off Log Explorer?
Use the Manage Datasets feature to enable or disable ingestion for individual datasets and zones.
1. In the Cloudflare dashboard, go to the **Manage Account** > **Billing** page.
[Go to **Billing**](https://dash.cloudflare.com/?to=/:account/billing)
2. Under **Subscriptions**, find the Log Explorer subscription, and select **Cancel**.
---
title: Log Search · Cloudflare Log Explorer docs
description: Log Explorer enables you to store and explore your Cloudflare logs
directly within the Cloudflare dashboard or API, giving you visibility into
your logs without the need to forward them to third-party services. Logs are
stored on Cloudflare's global network using the R2 object storage platform and
can be queried via the dashboard or SQL API.
lastUpdated: 2025-12-05T12:51:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/log-search/
md: https://developers.cloudflare.com/log-explorer/log-search/index.md
---
Log Explorer enables you to store and explore your Cloudflare logs directly within the Cloudflare dashboard or API, giving you visibility into your logs without the need to forward them to third-party services. Logs are stored on Cloudflare's global network using the R2 object storage platform and can be queried via the dashboard or SQL API.
## Use Log Explorer
You can filter and view your logs via the Cloudflare dashboard or the API.
1. In the Cloudflare dashboard, go to the **Log Explorer** > **Log Search** page.
[Go to **Log search**](https://dash.cloudflare.com/?to=/:account/log-explorer/log-search)
2. Select the **Dataset** you want to use and in **Columns** select the dataset fields. If you selected a zone scoped dataset, select the zone you would like to use.
3. Enter a **Limit**. A limit is the maximum number of results to return, for example, 50.
4. Select the **Time period** from which you want to query, for example, the previous 12 hours.
5. Select **Add filter** to create your query. Select a **Field**, an **Operator**, and a **Value**, then select **Apply**.
6. A query preview is displayed. Select **Custom SQL** to change the query.
7. Select **Run query** when you are done. The results are displayed below within the **Query results** section.
For example, to find an HTTP request with a specific [Ray ID](https://developers.cloudflare.com/fundamentals/reference/cloudflare-ray-id/), go to **Custom SQL**, and enter the following SQL query:
```sql
SELECT
clientRequestScheme,
clientRequestHost,
clientRequestMethod,
edgeResponseStatus,
clientRequestUserAgent
FROM http_requests
WHERE RayID = '806c30a3cec56817'
LIMIT 1
```
As another example, to find Cloudflare Access requests with selected columns from a specific timeframe you could perform the following SQL query:
```sql
SELECT
CreatedAt,
AppDomain,
AppUUID,
Action,
Allowed,
Country,
RayID,
Email,
IPAddress,
UserUID
FROM access_requests
WHERE Date >= '2025-02-06' AND Date <= '2025-02-06' AND CreatedAt >= '2025-02-06T12:28:39Z' AND CreatedAt <= '2025-02-06T12:58:39Z'
```
### Headers and cookies
To query request headers, response headers, and cookies you must first enable logging for these fields using [Custom fields](https://developers.cloudflare.com/logs/logpush/logpush-job/custom-fields/). Configure the list of custom fields using the API or the dashboard; there is no need to modify the Logpush job itself.
The example below shows how to query HTTP requests by date, timestamp, client country, and a custom request header. Be sure to log the specific headers or cookies you plan to query in advance.
```bash
SELECT clientip, clientrequesthost, clientrequestmethod, edgeendtimestamp, edgestarttimestamp, rayid, clientcountry, requestheaders
FROM http_requests
WHERE Date >= '2025-07-17'
AND Date <= '2025-07-17'
AND edgeendtimestamp >= '2025-07-17T07:54:19Z'
AND edgeendtimestamp <= '2025-07-18T07:54:19Z'
AND clientcountry = 'us'
AND requestheaders."x-test-header" like '%654AM%';
```
### Save queries
After selecting all the fields for your query, you can save it by selecting **Save query**. Provide a name and description to help identify it later. To view your saved and recent queries, select **Queries** — they will appear in a side panel where you can insert a new query, or delete any query.
## Integration with Security Analytics
You can also access the Log Explorer dashboard directly from the [Security Analytics dashboard](https://developers.cloudflare.com/waf/analytics/security-analytics/#logs). When doing so, the filters you applied in Security Analytics will automatically carry over to your query in Log Explorer.
## Optimize your queries
All the tables supported by Log Explorer contain a special column called `date`, which helps to narrow down the amount of data that is scanned to respond to your query, resulting in faster query response times. The value of `date` must be in the form of `YYYY-MM-DD`. For example, to query logs that occurred on October 12, 2023, add the following to your `WHERE` clause: `date = '2023-10-12'`. The column supports the standard operators of `<`, `>`, and `=`.
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/login) and select your account.
2. Go to **Log Explorer** > **Log Search** > **Custom SQL**.
3. Enter the following SQL query:
```sql
SELECT
clientip,
clientrequesthost,
clientrequestmethod,
clientrequesturi,
edgeendtimestamp,
edgeresponsestatus,
originresponsestatus,
edgestarttimestamp,
rayid,
clientcountry,
clientrequestpath,
date
FROM
http_requests
WHERE
date = '2023-10-12' LIMIT 500
```
### Additional query optimization tips
* Narrow your query time frame. Focus on a smaller time window to reduce the volume of data processed. This helps avoid querying excessive amounts of data and speeds up response times.
* Omit `ORDER BY` and `LIMIT` clauses. These clauses can slow down queries, especially when dealing with large datasets. For queries that return a large number of records, reduce the time frame instead of limiting to the newest `N` records from a broader time frame.
* Select only necessary columns. For example, replace `SELECT *` with the list of specific columns you need. You can also use `SELECT RayId` as a first iteration and follow up with a query that filters by the Ray IDs to retrieve additional columns. Additionally, you can use `SELECT COUNT(*)` to probe for time frames with matching records without retrieving the full dataset.
---
title: Manage datasets · Cloudflare Log Explorer docs
description: Log Explorer allows you to enable or disable which datasets are
available to query in Log Search.
lastUpdated: 2025-11-18T15:34:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/manage-datasets/
md: https://developers.cloudflare.com/log-explorer/manage-datasets/index.md
---
Log Explorer allows you to enable or disable which datasets are available to query in Log Search.
## Supported datasets
Log Explorer currently supports the following datasets:
### Zone level
* [HTTP Requests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) (`http_requests`)
* [Firewall Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/firewall_events/) (`firewall_events`)
* [DNS Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/dns_logs/) (`dns_logs`)
* [NEL Reports](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/nel_reports/) (`nel_reports`)
* [Page Shield Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/page_shield_events/) (`page_shield_events`)
* [Spectrum Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/spectrum_events/) (`spectrum_events`)
* [Zaraz Events](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/zaraz_events/) (`zaraz_events`)
### Account level
* [Access requests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/access_requests/) (`access_requests`)
* [CASB findings](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/casb_findings/) (`casb_findings`)
* [Device posture results](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/device_posture_results/) (`device_posture_results`)
* [Gateway DNS](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/gateway_dns/) (`gateway_dns`)
* [Gateway HTTP](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/gateway_http/) (`gateway_http`)
* [Gateway Network](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/gateway_network/) (`gateway_network`)
* [Zero Trust Network Session Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/zero_trust_network_sessions/) (`zero_trust_network_sessions`)
* [Audit Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/audit_logs/) (`audit_logs`)
* [Audit\_logs\_v2](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/audit_logs_v2/) (`audit_logs_v2`)
* [Browser Isolation User Actions](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/biso_user_actions/) (`biso_user_actions`)
* [DNS firewall logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/dns_firewall_logs/) (`dns_firewall_logs`)
* [Email security alerts](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/email_security_alerts/) (`email_security_alerts`)
* [Magic IDS Detections](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/magic_ids_detections/) (`magic_ids_detections`)
* [Network Analytics](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/network_analytics_logs/) (`network_analytics_logs`)
* [Sinkhole HTTP Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/sinkhole_http_logs/) (`sinkhole_http_logs`)
* [IP Sec Logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/account/ipsec_logs/) (`ipsec_logs`)
## Enable Log Explorer
In order for Log Explorer to begin storing logs, you need to enable the desired datasets. You can do this via the dashboard or the API.
1. In the Cloudflare dashboard, go to the **Log Explorer** > **Manage datasets** page.
[Go to **Manage datasets**](https://dash.cloudflare.com/?to=/:account/log-explorer/manage-sources)
2. Select **Add dataset** to select the datasets you want to query.
3. Choose a dataset and then a zone. Then, select **Add**. You can always return to this page to enable more datasets or manage your existing ones.
Note
It may take a few minutes for the logs to become available for querying.
If you are using the API, Use the Log Explorer API to enable Log Explorer for each dataset you wish to store. It may take a few minutes after a log stream is enabled before you can view the logs.
The following `curl` command is an example for enabling the zone-level dataset `http_requests`, as well as the expected response when the command succeeds.
```bash
curl https://api.cloudflare.com/client/v4/zones/{zone_id}/logs/explorer/datasets \
--header "Authorization: Bearer " \
--json '{
"dataset": "http_requests"
}'
```
```json
{
"result": {
"dataset": "http_requests",
"object_type": "zone",
"object_id": "",
"created_at": "2025-06-03T14:33:16Z",
"updated_at": "2025-06-03T14:33:16Z",
"dataset_id": "01973635f7e273a1964a02f4d4502499",
"enabled": true
},
"success": true,
"errors": [],
"messages": []
}
```
To enable an account-level dataset, replace `zones/{zone_id}` with `accounts/{account_id}` in the `curl` command. For example:
```bash
curl https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/explorer/datasets \
--header "Authorization: Bearer " \
--json '{
"dataset": "access_requests"
}'
```
---
title: 404 - Page Not Found · Cloudflare Logs docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/404/
md: https://developers.cloudflare.com/logs/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Audit Logs MCP server · Cloudflare Logs docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/auditlogs-mcp-server/
md: https://developers.cloudflare.com/logs/auditlogs-mcp-server/index.md
---
---
title: SQL queries supported · Cloudflare Log Explorer docs
description: This page outlines the SQL features supported by Log Explorer,
including common aggregation functions, expressions, and query clauses.
lastUpdated: 2025-07-28T13:09:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/log-explorer/sql-queries/
md: https://developers.cloudflare.com/log-explorer/sql-queries/index.md
---
This page outlines the SQL features supported by Log Explorer, including common aggregation functions, expressions, and query clauses.
The diagram below illustrates the general shape of a valid query supported in Log Explorer. It shows how standard SQL clauses — such as `SELECT`, `WHERE`, `GROUP BY`, and `ORDER BY` — can be composed to form supported queries.

Examples of queries include:
* `SELECT * FROM table WHERE (a = 1 OR b = "hello") AND c < 25.89`
* `SELECT a, b, c FROM table WHERE d >= "GB" LIMIT 10`
Note
* A default `LIMIT` of 10,000 is applied if the `LIMIT` clause is omitted.
* The `WHERE` clause supports up to 25 predicates, which can be grouped using parentheses.
### SQL Clauses in detail
The following SQL clauses define the structure and logic of queries in Log Explorer:
* `SELECT` - The `SELECT` clause specifies the columns that you want to retrieve from the database tables. It can include individual column names, expressions, or even wildcard characters to select all columns.
* `FROM` - The `FROM` clause specifies the tables from which to retrieve data. It indicates the source of the data for the `SELECT` statement.
* `WHERE` - The `WHERE` clause filters the rows returned by a query based on specified conditions. It allows you to specify conditions that must be met for a row to be included in the result set.
* `SELECT DISTINCT` - Removes duplicate rows from the result set.
* `GROUP BY` - Groups rows for aggregation. The `GROUP BY` clause is used to group rows that have the same values into summary rows.
* `ORDER BY` - Sorts the result set. The `ORDER BY` clause is used to sort the result set by one or more columns in ascending or descending order.
* `LIMIT` - Restricts the number of rows returned. The `LIMIT` clause is used to constrain the number of rows returned by a query. It is often used in conjunction with the `ORDER BY` clause to retrieve the top `N` rows or to implement pagination.
* `OFFSET` - Skips a specified number of rows before returning results.
The sections that follow break down the remaining components shown in the diagram — such as aggregation functions, string and numeric expressions, and supported operators — in more detail.
## Functions
Log Explorer supports a range of SQL functions to transform, evaluate, or summarize data. These include scalar and aggregation functions.
### Scalar functions
These help manipulate or evaluate values (often strings):
* `ARRAY_CONTAINS(array, element)` – Checks if the array contains the element.
Example
`ARRAY_CONTAINS(['US', 'CA'], ClientCountry)`
Returns rows where `ClientCountry` is either `US` or `CA`.
* `SUBSTRING(string, from_number, for_number)` – Extracts part of a string.
Example
`SUBSTRING(ClientRequestPath, 0, 5)`
Extracts the first `5` characters from `ClientRequestPath`.
* `LOWER(string)` – Converts to lowercase.
Example
`LOWER(ClientRequestUserAgent)`
Converts the user agent string to lowercase.
* `UPPER(string)` – Converts to uppercase.
Example
`UPPER(ClientCountry)`
Converts the country code to uppercase.
### Aggregation functions
Used to perform calculations on sets of rows:
* `SUM(expression)` – Total of values.
Example
`SUM(ClientRequestBytes)`
Adds up the total number of bytes requested by clients.
* `MIN(expression)` – Minimum value.
Example
`MIN(OriginResponseDurationMs)`
Finds the shortest response time from origin servers.
* `MAX(expression)` – Maximum value.
Example
`MAX(OriginResponseDurationMs)`
Finds the longest response time.
* `COUNT(expression)` – Number of rows (can be all rows or non-null values).
Example
`COUNT(ClientRequestUserAgent)`
Counts how many rows have a user agent value.
* `COUNT(DISTINCT expression)` – Number of distinct non-null values.
Example
`COUNT(DISTINCT ClientIP)`
Counts how many unique client IPs made requests.
* `AVG(expression)` – Average of numeric values.
Example
`AVG(OriginResponseDurationMs)`
Computes the average origin response time in milliseconds.
The diagram below represents the grammar for SQL expressions including scalar and aggregate functions.

## Expressions
Conditions or logic used in queries:
* `CASE WHEN` – Conditional logic (like if-else).
* `AS` – Alias for columns or tables.
* `LIKE` – Pattern matching.
* `IN (list)` – Checks if a value is in a list.
* `BETWEEN ... AND ...` – Checks if a value is within a range.
* `Unary operator` – Operates on one operand (for example, `-5`).
* `Binary operator` – Operates on two operands (for example, `5 + 3`).
* `Nested Expressions` – Expression wrapped with parentheses, like `( x > y )` or `( 1 )`.
* `Compound identifier` – Multi-part name (for example, `schema.table.column`).
* `Array` – A collection of values (supported differently across SQL dialects).
* `Literals` - represent values such as strings, numbers, or arrays.
The diagram below represents the grammar for SQL expressions, detailing the various forms an expression can take, including columns, literals, functions, operators, and aliases.

The diagram below defines the grammar for unary operators, which operate on a single operand (for example, negation or logical `NOT`):

## Binary Operators
Used for arithmetic, comparison, logical operations:
* Arithmetic: `+`, `-`, `*`, `/`, `%` (modulo)
* Comparison: `>`, `<`, `>=`, `<=`, `=`, `!=` (or `<>`)\`
* Logical: `AND`, `OR`, `XOR`
* Bitwise: `&`, `|`, `^`, `>>`, `<<`
* String concat: `||`
---
title: Changelog · Cloudflare Logs docs
lastUpdated: 2025-06-02T11:14:31.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/logs/changelog/
md: https://developers.cloudflare.com/logs/changelog/index.md
---
---
title: FAQ · Cloudflare Logs docs
description: Below you will find answers to the most commonly asked questions
regarding Cloudflare Logs. If you cannot find the answer you are looking for,
go to the community page and post your question there.
lastUpdated: 2026-01-05T14:41:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/faq/
md: https://developers.cloudflare.com/logs/faq/index.md
---
Below you will find answers to the most commonly asked questions regarding Cloudflare Logs. If you cannot find the answer you are looking for, go to the [community page](https://community.cloudflare.com/) and post your question there.
***
## General FAQ
For general questions about Logs.
[General FAQ ❯](https://developers.cloudflare.com/logs/faq/general-faq/)
## Logpush
For questions about Logpush.
[Logpush ❯](https://developers.cloudflare.com/logs/faq/logpush/)
## Instant Logs
For questions about Instant Logs.
[Instant Logs ❯](https://developers.cloudflare.com/logs/faq/instant-logs/)
## Logpull API
For questions about the Logpull API.
[Logpull API ❯](https://developers.cloudflare.com/logs/faq/logpull-api/)
## Common calculations
For questions about common calculations.
[Common calculations ❯](https://developers.cloudflare.com/logs/faq/common-calculations/)
## Random hostnames
For questions about unexpected hostnames in HTTP logs for partial zones.
[Random hostnames ❯](https://developers.cloudflare.com/logs/faq/random-hostnames-partial-zones/)
---
title: Glossary · Cloudflare Logs docs
description: Review the definitions for terms used across Cloudflare's Logs documentation.
lastUpdated: 2025-07-16T10:06:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/glossary/
md: https://developers.cloudflare.com/logs/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Logs documentation.
| Term | Definition |
| - | - |
| debugging | The process of identifying and resolving errors or issues within software applications or systems, often facilitated by analyzing log data. |
| deprecation | Deprecation in software development involves officially labeling a feature as outdated. While a deprecated software feature remains within the software, users are warned and encouraged to adopt alternatives. Eventually, deprecated features may be removed. This approach ensures backward compatibility and gives programmers time to update their code. |
| event | An occurrence or happening that is significant and worthy of being recorded in a log. |
| log | A chronological record of events, actions, or transactions, typically used for tracking and troubleshooting purposes. |
| log file | A file containing a collection of log entries, usually stored in a structured or semi-structured format. |
| logging | The process of recording events, actions, or transactions in a log. |
| timestamp | A data field indicating the date and time when an event occurred, often used for sequencing and analysis. |
---
title: Instant Logs · Cloudflare Logs docs
description: Instant Logs allows Cloudflare customers to access a live stream of
the traffic for their domain from the Cloudflare dashboard or from a
command-line interface (CLI). Seeing data in real time allows you to
investigate an attack, troubleshoot, debug or test out changes made to your
network. Instant Logs is lightweight, simple to use and does not require any
additional setup.
lastUpdated: 2025-12-16T16:50:54.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/instant-logs/
md: https://developers.cloudflare.com/logs/instant-logs/index.md
---
Instant Logs allows Cloudflare customers to access a live stream of the traffic for their domain from the Cloudflare dashboard or from a command-line interface (CLI). Seeing data in real time allows you to investigate an attack, troubleshoot, debug or test out changes made to your network. Instant Logs is lightweight, simple to use and does not require any additional setup.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | Yes | Yes |
## Instant Logs via Cloudflare Dashboard
1. In the Cloudflare dashboard, go to the **Instant Logs** page.
[Go to **Instant Logs**](https://dash.cloudflare.com/?to=/:account/:zone/analytics/instant-logs)
2. Select **Start streaming**.
3. (optional) Select **Add filter** to narrow down the events to be shown.
Fields supported in our [HTTP requests dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) can be used when you add filters. Some fields with additional subscriptions required are not supported in the dashboard, you will need to use CLI instead.
Once a filter is selected and the stream has started, only log lines that match the filter criteria will appear. Filters are not applied retroactively to logs already showing in the dashboard.
## Instant Logs via CLI
### 1. Create an Instant Logs Job
Create a session by sending a `POST` request to the Instant Logs job endpoint with the following parameters:
* **Fields** - List any field available in the [HTTP requests dataset](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/).
* **Sample** - The sample parameter is the sample rate of the records set by the client: `"sample": 1` is 100% of records `"sample": 10` is 10% and so on.
Note
Instant Logs has a maximum data rate supported. For high volume domains, we sample server side as indicated in the `"sampleInterval"` parameter returned in the logs.
* **Filters** - Use filters to drill down into specific events. Filters consist of three parts: key, operator and value.
All supported operators can be found in the [Filters](https://developers.cloudflare.com/logs/logpush/logpush-job/filters/) page.
Below we have three examples of filters:
```bash
# Filter when client IP country is not Canada:
"filter": "{\"where\":{\"and\":[{\"key\":\"ClientCountry\",\"operator\":\"neq\",\"value\":\"ca\"}]}}"
```
```bash
# Filter when the status code returned from Cloudflare is either 200 or 201:
"filter": "{\"where\":{\"and\":[{\"key\":\"EdgeResponseStatus\",\"operator\":\"in\",\"value\":[200,201]}]}}"
```
```bash
# Filter when the request path contains "/static" and the request hostname is "example.com":
"filter": "{\"where\":{\"and\":[{\"key\":\"ClientRequestPath\",\"operator\":\"contains\",\"value\":\"/static\"}, {\"where\":{\"and\":[{\"key\":\"ClientRequestHost\",\"operator\":\"eq\",\"value\":\"example.com\"}]}}"
```
Example request using cURL:
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Logs Read`
```bash
curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/logpush/edge/jobs" \
--request POST \
--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \
--json '{
"fields": "ClientIP,ClientRequestHost,ClientRequestMethod,ClientRequestURI,EdgeEndTimestamp,EdgeResponseBytes,EdgeResponseStatus,EdgeStartTimestamp,RayID",
"sample": 100,
"filter": "",
"kind": "instant-logs"
}'
```
Response:
The response will include a new field called **destination\_conf**. The value of this field is your unique WebSocket address that will receive messages from Cloudflare's global network.
```json
{
"errors": [],
"messages": [],
"result": {
"id": ,
"fields": "ClientIP,ClientRequestHost,ClientRequestMethod,ClientRequestURI,EdgeEndTimestamp,EdgeResponseBytes,EdgeResponseStatus,EdgeStartTimestamp,RayID",
"sample": 100,
"filter": "",
"destination_conf": "wss://logs.cloudflare.com/instant-logs/ws/sessions/",
"kind": "instant-logs"
},
"success": true
}
```
### 2. Connect to WebSocket
Using a CLI utility like [Websocat](https://github.com/vi/websocat), you can connect to the WebSocket and start immediately receiving logs.
```bash
websocat wss://logs.cloudflare.com/instant-logs/ws/sessions/
```
Response:
Once connected to the websocket, you will receive messages of line-delimited JSON.
### Angle Grinder
Now that you have a connection to Cloudflare's websocket and are receiving logs from Cloudflare's global network, you can start slicing and dicing the logs. A handy tool for this is [Angle Grinder](https://github.com/rcoh/angle-grinder). Angle Grinder lets you apply filtering, transformations and aggregations on stdin with first class JSON support. For example, to get the number of visitors from each country you can sum the number of events by the `ClientCountry` field.
```bash
awebsocat wss://logs.cloudflare.com/instant-logs/ws/sessions/ | agrind '* | json | sum(sampleInterval) by ClientCountry'
```
Response:
| **ClientCountry** | **\_sum** |
| - | - |
| pt | `4` |
| fr | `3` |
| us | `3` |
| om | `2` |
| ar | `1` |
| au | `1` |
## Datasets available
For the moment, `HTTP requests` is the only dataset supported. In the future, we will expand to other datasets.
## Export
You can download the table of logs that appears in the dashboard, in JSON format via the **Export** button.
## Limits
Instant Logs has three limits set in place:
* Only one active Instant Logs session per zone.
* Maximum session time is 60 minutes.
* If you stop listening to a socket for more than five minutes.
If either of these limits are reached, the logs stream will automatically stop.
## Connect with us
If you have any feature requests or notice any bugs, share your feedback directly with us by joining the [Cloudflare Developers community on Discord](https://discord.cloudflare.com).
---
title: Logpull · Cloudflare Logs docs
description: Cloudflare Logpull is a REST API for consuming request logs over
HTTP. These logs contain data related to the connecting client, the request
path through the Cloudflare network, and the response from the origin web
server. This data is useful for enriching existing logs on an origin server.
Logpull is available to customers on the Enterprise plan.
lastUpdated: 2025-07-16T14:37:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/logpull/
md: https://developers.cloudflare.com/logs/logpull/index.md
---
Cloudflare Logpull is a REST API for consuming request logs over HTTP. These logs contain data related to the connecting client, the request path through the Cloudflare network, and the response from the origin web server. This data is useful for enriching existing logs on an origin server. Logpull is available to customers on the Enterprise plan.
Warning
Logpull is considered a legacy feature and we recommend using [Logpush](https://developers.cloudflare.com/logs/logpush/) or [Logs Engine](https://developers.cloudflare.com/logs/r2-log-retrieval/) instead for better performance and functionality.
Review the following content to learn more about Logpull.
* [Understanding the basics](https://developers.cloudflare.com/logs/logpull/understanding-the-basics/)
* [Enabling log retention](https://developers.cloudflare.com/logs/logpull/enabling-log-retention/)
* [Requesting logs](https://developers.cloudflare.com/logs/logpull/requesting-logs/)
* [Additional details](https://developers.cloudflare.com/logs/logpull/additional-details/)
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | No | Yes |
### Limitation
Logpull is unavailable when the Customer Metadata Boundary (CMB) is set outside the US region. Specifically, it does not work when CMB is restricted to the EU-only setting. For more details, refer to the [Cloudflare Data Localization](https://developers.cloudflare.com/data-localization/) documentation.
---
title: Logpush · Cloudflare Logs docs
description: Logpush delivers logs in batches as quickly as possible, with no
minimum batch size, potentially delivering files more than once per minute.
This capability enables Cloudflare to provide information almost in real time,
in smaller file sizes.
lastUpdated: 2026-01-26T13:58:45.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/logpush/
md: https://developers.cloudflare.com/logs/logpush/index.md
---
Logpush delivers logs in batches as quickly as possible, with no minimum batch size, potentially delivering files more than once per minute. This capability enables Cloudflare to provide information almost in real time, in smaller file sizes.
The push frequency is automatic and cannot be adjusted—Cloudflare pushes logs in batches as soon as possible. However, users can configure the batch size [using the API](https://developers.cloudflare.com/logs/logpush/logpush-job/api-configuration/#max-upload-parameters) for improved control in case the log destination has specific requirements.
Important limitation
Logpush only pushes logs once as they become available and cannot backfill historical data. If your job is disabled or fails, logs generated during that period are permanently lost. This is why configuring [health notifications](https://developers.cloudflare.com/logs/logpush/logpush-health/) is essential for early detection of issues.
Logpush does not offer storage or search functionality for logs; its primary aim is to send logs as quickly as they arrive.
Cloudflare Logpush supports pushing logs to storage services, SIEMs, and log management providers via the Cloudflare dashboard or API.
Cloudflare aims to support additional services in the future. Interested in a particular service? Take this [survey](https://goo.gl/forms/0KpMfae63WMPjBmD2).
## Estimating log volume
Before setting up a Logpush job, you can estimate the total volume of data that will be pushed to your destination. The volume depends on your traffic, selected fields, and compression.
### Quick sizing for HTTP Requests
A quick sizing estimate for an [HTTP Requests](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) dataset:
* \~100–250 bytes per request (compressed, depending on fields selected)
* 1M requests/day → \~100–250 MB/day
* 30M requests/month → \~3–7.5 GB/month
### Daily storage by traffic volume
* 100k req/day → \~25–50 MB/day
* 1M req/day → \~250–500 MB/day
* 10M req/day → \~2.5–5 GB/day
* 100M req/day → \~25–50 GB/day
These ranges reflect field selection, compression, and whether you include extra fields or [custom fields](https://developers.cloudflare.com/logs/logpush/logpush-job/custom-fields/). Other datasets (Firewall, Workers, Load Balancing) add volume separately.
For precise estimates, you can [sample your logs via Logpull](https://developers.cloudflare.com/logs/logpull/additional-details/#estimating-daily-data-volume) using a 1-hour sample.
## Limits
There is currently a max limit of **4 Logpush jobs per zone**. Trying to create a job once the limit has been reached will result in an error message: `creating a new job is not allowed: exceeded max jobs allowed`.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | No | Yes |
Note
Users without an Enterprise plan can still access [Workers Trace Events Logpush](https://developers.cloudflare.com/workers/observability/logs/logpush/) by subscribing to the [Workers Paid](https://developers.cloudflare.com/workers/platform/pricing/) plan.
---
title: Logpush MCP server · Cloudflare Logs docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/logpush-mcp-server/
md: https://developers.cloudflare.com/logs/logpush-mcp-server/index.md
---
---
title: Logs Engine · Cloudflare Logs docs
description: Logs Engine gives you the ability to store your logs in R2 and
query them directly.
lastUpdated: 2025-10-01T13:53:03.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/r2-log-retrieval/
md: https://developers.cloudflare.com/logs/r2-log-retrieval/index.md
---
Logs Engine gives you the ability to store your logs in R2 and query them directly.
Note
Logs Engine is going to be replaced by Log Explorer. For further details, consult the [Log Explorer](https://developers.cloudflare.com/log-explorer/) documentation and to request access, complete the [sign-up form](https://cloudflare.com/lp/log-explorer/).
## Store logs in R2
* Set up a [Logpush to R2](https://developers.cloudflare.com/logs/logpush/logpush-job/enable-destinations/r2/) job.
* Create an [R2 access key](https://developers.cloudflare.com/r2/api/tokens/) with at least R2 read permissions.
* Ensure that you have Logshare read permissions.
* Alternatively, create a Cloudflare API token with the following permissions:
* Account scope
* Logs read permissions
## Query logs
You can use the API to query and download your logs by time range or [RayID](https://developers.cloudflare.com/fundamentals/reference/cloudflare-ray-id/).
## Authentication
The following headers are required for all API calls:
* `X-Auth-Email` - the Cloudflare account email address associated with the domain
* `X-Auth-Key` - the Cloudflare API key
Alternatively, API tokens with Logs edit permissions can also be used for authentication:
* `Authorization: Bearer `
### Required headers
In addition to the required authentication headers mentioned, the following headers are required for the API to access logs stored in your R2 bucket.
* `R2-access-key-id` (required) - [R2 Access Key Id](https://developers.cloudflare.com/r2/api/tokens/)
* `R2-secret-access-key` (required) - [R2 Secret Access Key](https://developers.cloudflare.com/r2/api/tokens/)
## List files
List relevant R2 objects containing logs matching the provided query parameters, using the endpoint `GET /accounts/{accountId}/logs/list`.
### Query parameters
* `start` (required) string (TimestampRFC3339) - Start time in RFC 3339 format, for example `start=2022-06-06T16:00:00Z`.
* `end` (required) string (TimestampRFC3339) - End time in RFC 3339 format, for example `end=2022-06-06T16:00:00Z`.
* `bucket` (required) string (Bucket) - R2 bucket name, for example `bucket=cloudflare-logs`.
* `prefix` string (Prefix) - R2 bucket prefix logs are stored under, for example `prefix=http_requests/example.com/{DATE}`.
* `limit` number (Limit) - Maximum number of results to return, for example `limit=100`.
## Retrieve logs by time range
Stream logs stored in R2 that match the provided query parameters, using the endpoint `GET /accounts/{accountId}/logs/retrieve`.
### Query parameters
* `start` (required) string (TimestampRFC3339) - Start time in RFC 3339 format, for example `start=2022-06-06T16:00:00Z`
* `end` (required) string (TimestampRFC3339) - End time in RFC 3339 format, for example `end=2022-06-06T16:00:00Z`
* `bucket` (required) string (Bucket) - R2 bucket name, for example `bucket=cloudflare-logs`
* `prefix` string (Prefix) - R2 bucket prefix logs are stored under, for example `prefix=http_requests/example.com/{DATE}`
### Example API request
```bash
curl --globoff "https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/retrieve?start=2022-06-01T16:00:00Z&end=2022-06-01T16:05:00Z&bucket=cloudflare-logs&prefix=http_requests/example.com/{DATE}" \
--header "X-Auth-Email: " \
--header "X-Auth-Key: " \
--header "R2-Access-Key-Id: R2_ACCESS_KEY_ID" \
--header "R2-Secret-Access-Key: R2_SECRET_ACCESS_KEY"
```
Results can be piped to a file using `> logs.json`.
Additionally, if you want to receive the raw GZIP bytes without them being transparently decompressed by your client, include the header `--header "Accept-Encoding: gzip"`.
## Retrieve logs by Ray ID
Using your logs stored in R2 - the Logpull RayID Lookup feature allows you to query an indexed time range for the presence of an RayID and return the matching result. This feature is available to users with the Logpull RayID Lookup beta subscription.
The ability to look up a RayID is a two-step process. First, a time range needs to be indexed before being able to request a record by the RayID.
Indexes will automatically expire after seven days of no usage.
### Index a time range
Before executing your query, you can specify the time range you would like to index in order to narrow down the scope of the query. In the following example, we index one minute of logs stored in the R2 bucket `"cloudflare-logs"` under the prefix `"http_requests/{DATE}"`.
### Example API request
```bash
curl https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/rayids/index \
--header "Authorization: Bearer " \
--header "R2-Access-Key-Id: " \
--header "R2-Secret-Access-Key: " \
--header "Content-Type: application/json" \
--data-raw '{
"start": "2022-08-16T20:30:00Z",
"end": "2022-08-16T20:31:00",
"bucket": "cloudflare-logs",
"prefix": "http_requests/example.com/{DATE}"
}'
```
## Lookup a RayID
After indexing a time range, perform a `GET` request with the RayID. If a matching result is found in the indexed time range, the record will be returned. Note that the parameters have moved from the request body and into the URL. The `-g` flag is required to avoid the `{DATE}` parameter from being misinterpreted by cURL.
### Example API request
```bash
curl --globoff "https://api.cloudflare.com/client/v4/accounts/{account_id}/logs/rayids/?bucket=cloudflare-logs&prefix=http_requests/example.com/{DATE}" \
--header "Authorization: Bearer " \
--header "R2-Access-Key-Id: " \
--header "R2-Secret-Access-Key: "
```
## Troubleshooting
I am getting an error when accessing the API
* **Error**: Time range returned too many results. Try reducing the time range and try again.
HTTP status code `422` will be returned if the time range between the start and end parameters is too wide. Try querying a shorter time range if you are running into this limit.
* **Error**: Provided token does not have the required features enabled.
Contact your account representative to have the beta Logpull RayID Lookup subscription added to your account.
* **Error**: Time range returned too many results. Try reducing the time range and try again.
High volume zones can produce many log files in R2. Try reducing your start and end time range until you find a duration that works best for your log volume.
How do I know what time range to index?
Currently, there is no process to index logs as they arrive. If you have the RayID and know the time the request was made, try indexing the next 5-10 minutes of logs after the request was completed.
What is the time delay between when an event happens and when I can query for it?
Logpush delivers logs in batches as soon as possible, generally in less than one minute. After this, logs can be accessed using Logs Engine.
Does R2 have retention controls?
R2 does not currently have retention controls in place. You can query back as far as when you created the Logpush job.
Which datasets is Logs Engine compatible with?
The retrieval API is compatible with all the datasets we support. The full list is available on the [Datasets](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/) section.
---
title: Reference · Cloudflare Logs docs
description: "These reference resources are useful for gaining a more in-depth
understanding of the terminology and status codes that are part of the
Cloudflare Logs data. This information is especially important when
integrating your data with third-party tools:"
lastUpdated: 2025-07-24T13:05:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/logs/reference/
md: https://developers.cloudflare.com/logs/reference/index.md
---
These reference resources are useful for gaining a more in-depth understanding of the terminology and status codes that are part of the Cloudflare Logs data. This information is especially important when integrating your data with third-party tools:
* [Pathing status](https://developers.cloudflare.com/logs/reference/pathing-status/)
* [Security fields](https://developers.cloudflare.com/logs/reference/security-fields/)
* [WAF fields](https://developers.cloudflare.com/logs/reference/waf-fields/)
* [ClientRequestSource field](https://developers.cloudflare.com/logs/reference/clientrequestsource/)
* [Change notices](https://developers.cloudflare.com/logs/reference/change-notices/)
---
title: 404 - Page Not Found · Cloudflare Magic Cloud Networking docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/404/
md: https://developers.cloudflare.com/magic-cloud-networking/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Changelog · Cloudflare Magic Cloud Networking docs
description: Review recent changes to Magic Cloud Networking (beta).
lastUpdated: 2025-04-24T15:57:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/changelog/
md: https://developers.cloudflare.com/magic-cloud-networking/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-cloud-networking.xml)
## 2024-12-05
**Generate customized terraform files for building cloud network on-ramps**
You can now generate customized terraform files for building cloud network on-ramps to [Magic WAN](https://developers.cloudflare.com/magic-wan/).
[Magic Cloud](https://developers.cloudflare.com/magic-cloud-networking/) can scan and discover existing network resources and generate the required terraform files to automate cloud resource deployment using their existing infrastructure-as-code workflows for cloud automation.
You might want to do this to:
* Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
* Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
For more details, refer to [Set up with Terraform](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#set-up-with-terraform).
## 2024-11-21
**Import cloud resources for VMs and LBs**
Cloud network discovery now includes cloud native virtual machine (VM) and load-balancer (LB) resources.
## 2024-11-21
**Export resource catalog**
Customers can export their resource catalog including all discovered resource metadata to a downloadable JSON file, suitable for offline analysis.
## 2024-10-01
**Cost visibility for managed cloud configuration**
Customers can now see the cloud provider list price of discovered network resources and will be informed of total cost and delta cost when deploying managed configuration.
## 2024-08-14
**GCP on-ramps**
Magic Cloud Networking supports Google Cloud Platform.
## 2024-07-01
**Closed beta launch**
The Magic Cloud Networking closed beta release is available, with the managed cloud on-ramps feature.
---
title: Cloud on-ramps · Cloudflare Magic Cloud Networking docs
description: Magic Cloud Networking (beta) allows you to create on-ramps from
your cloud networks to Magic WAN. Cloudflare will create virtual private
network (VPN) tunnels between Magic WAN and your cloud provider, configuring
both sides of the connection on your behalf. Cloudflare orchestrates the cloud
provider's native VPN functionality, without requiring deployment of any
additional compute virtual machines (VMs).
lastUpdated: 2025-03-27T12:39:57.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/
md: https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/index.md
---
Magic Cloud Networking (beta) allows you to create on-ramps from your cloud networks to Magic WAN. Cloudflare will create virtual private network (VPN) tunnels between Magic WAN and your cloud provider, configuring both sides of the connection on your behalf. Cloudflare orchestrates the cloud provider's native VPN functionality, without requiring deployment of any additional compute virtual machines (VMs).
There are two types of on-ramps: single virtual private cloud (VPC) and hubs.
## Prerequisites
Before creating on-ramps from your cloud networks to Magic WAN, make sure you:
* Have a Magic WAN account. Contact your account team to learn more.
* Went through the process of [setting up your cloud provider](https://developers.cloudflare.com/magic-cloud-networking/get-started/).
* Have the correct cloud resources. Refer to [Reference](https://developers.cloudflare.com/magic-cloud-networking/reference/) to check resources by cloud provider.
## Available on-ramps
Magic Cloud Networking has the following cloud on-ramps integrations:
* AWS (single VPC and hubs)
* Azure (single VPC)
* GCP (single VPC)
Refer to [Reference](https://developers.cloudflare.com/magic-cloud-networking/reference/) to learn more about how Cloudflare orchestrates VPN connectivity to your cloud networks.
***
## Set up on-ramps
### Single virtual private cloud
Choose this option if you have a single VPC in your cloud to connect to Magic WAN. To set up a single-VPC on-ramp:
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select **Add new on-ramp**.
4. Go to **Connect an existing VPC to Cloudflare** > **Select**.
5. Give your new on-ramp a name and a description (optional), then select **Continue**.
6. From the drop-down menu, choose your cloud provider. You can choose between AWS, GCP, and Azure. Then, select **Continue**.
7. Select the network that you want to connect to. This list comes from the [cloud integrations](https://developers.cloudflare.com/magic-cloud-networking/get-started/) you have already set up. When you are done, select **Continue**.
8. **Configure route propagation** shows where Cloudflare will install the new routes. Installing these routes is required to correctly configure both Magic WAN and your cloud provider, and ensure successful communication between them:
* **Add routes for your Magic WAN address space to your cloud network**: Select this option to install routes for reaching Magic WAN in your cloud network's route tables (refer to [Magic WAN address space](#magic-wan-address-space) to learn what routes are installed and how to customize them). If you prefer to do this manually, unselect this option.
Warning
Cloudflare recommends that you leave this option selected. If you unselect **Add routes for your Magic WAN address space to your cloud network**, you will need to manually create all the required configurations to allow Magic WAN to connect to your cloud, such as routing tables, transit gateways, and VPNs. Refer to the [Magic WAN How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section, or consult the documentation for your cloud provider for more information.
* **Add routes for your cloud network to Magic WAN**: Select this option to create routes for reaching your cloud network in Magic WAN.
9. Select **Continue**. Applying your settings might take a few seconds to complete.
10. Review the changes in your cloud environment, and select **Approve changes**.
You have successfully created your Magic WAN on-ramp. However, on-ramp creation can take up to an hour before you can use it.
### Hubs
If you want to connect multiple VPCs to Magic WAN, the best way to connect them is using a hub. A hub is a cloud VPN gateway that peers with multiple VPCs, allowing them to share a VPN tunnel to Magic WAN. Each cloud provider has their own term for hubs, so refer to your cloud provider for more information.
Depending on how you have set up your cloud provider, you can:
* **Connect to an existing hub**: Choose this option if you already have a VPN hub in your cloud and you want to connect it to Magic WAN.
* **Create a new hub**: Choose this option if you want to create a new hub and connect it to Magic WAN.
When you configure a hub on-ramp, Cloudflare always manages the VPN tunnel between Magic WAN and the hub. Optionally, you can also choose to have Cloudflare manage peering with VPCs and/or with other hubs:
* **Manage VPC peering:** If you enable this option, Cloudflare will attach your chosen VPCs to the hub.
* **Manage hub peering:** Hubs are regional, so in order to connect VPCs attached to hubs in different regions, those hubs need to be peered. If you enable this option, Cloudflare will peer your chosen hubs to this hub.
#### Connect to an existing hub
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select **Add new on-ramp**.
4. Go to **Connect an existing hub to Cloudflare** > **Select**.
5. Give your new on-ramp a name and a description (optional), then select **Continue**.
6. From the drop-down menu, choose your cloud provider. You can choose between AWS, GCP, and Azure. Then, select **Continue**.
7. Choose an existing hub. This list comes from the [cloud integrations](https://developers.cloudflare.com/magic-cloud-networking/get-started/) you have already set up. When you are done, select **Continue**.
8. (*Optional*) In **VPC peering configuration**, you can enable **Manage VPC peering**. This allows Cloudflare to attach your chosen VPCs to the hub:
1. Select **Manage VPC peering** to enable this feature.
2. Choose the VPCs you want Cloudflare to attach to the hub.
9. Select **Continue**.
10. (*Optional*) In **Configure hub peering**, you can enable **Manage hub peering**. Enabling this option allows Cloudflare to attach remote hubs you have chosen to this hub (establishing connectivity between VPCs attached to any of the peered hubs):
1. Select **Manage hub peering** to enable this feature.
2. Select the remote hubs you want Cloudflare to attach to this hub.
11. Select **Continue**.
12. **Configure route propagation** shows where Cloudflare will install the new routes. Installing these routes is required to correctly configure both Magic WAN and your cloud provider, and ensure successful communication between them:
1. **Add routes for your Magic WAN address space to your cloud network**: Select this option to install routes for reaching Magic WAN in your cloud network's route tables (refer to [Magic WAN address space](#magic-wan-address-space) to learn what routes are installed and how to customize them). If you prefer to do this manually, unselect this option.
Warning
Cloudflare recommends that you leave this option selected. If you unselect **Add routes for your Magic WAN address space to your cloud network**, you will need to manually create all the required configurations to allow Magic WAN to connect to your cloud, such as routing tables, transit gateways, and VPNs. Refer to the [Magic WAN How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section, or consult the documentation for your cloud provider for more information.
2. **Add routes for your cloud network to Magic WAN**: Select this option to create routes for reaching your cloud network in Magic WAN.
13. Select **Continue**. Applying your settings might take a few seconds to complete.
14. Review the changes in your cloud environment, and select **Approve changes**.
You have successfully created your Magic WAN on-ramp. However, on-ramp creation can take up to an hour before you can use it.
#### Create a new hub
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select **Add new on-ramp**.
4. Go to **Create a new hub & connect it to Cloudflare** > **Select**.
5. Give your new on-ramp a name and a description (optional), then select **Continue**.
6. Configure your cloud in **Select your cloud details**:
1. From the drop-down menu, choose your cloud provider. You can choose between AWS, GCP, and Azure.
2. Choose an existing integration. This list comes from the [cloud integrations](https://developers.cloudflare.com/magic-cloud-networking/get-started/) you have already set up.
3. Choose a region in which to create the new hub.
4. Select **Continue**.
7. (*Optional*) In **VPC peering configuration**, you can enable **Manage VPC peering**. This allows Cloudflare to attach your chosen VPCs to the hub:
1. Select **Manage VPC peering** to enable this feature.
2. Choose the VPCs you want Cloudflare to attach to the hub.
8. Select **Continue**.
9. (*Optional*) In **Configure hub peering**, you can enable **Manage hub peering**. Enabling this option allows Cloudflare to attach remote hubs you have chosen to this hub (establishing connectivity between VPCs attached to any of the peered hubs):
1. Select **Manage hub peering** to enable this feature.
2. Select the remote hubs you want Cloudflare to attach to this hub.
10. Select **Continue**.
11. **Configure route propagation** shows where Cloudflare will install the new routes. Installing these routes is required to correctly configure both Magic WAN and your cloud provider, and ensure successful communication between them:
1. **Add routes for your Magic WAN address space to your cloud network**: Select this option to install routes for reaching Magic WAN in your cloud network's route tables (refer to [Magic WAN address space](#magic-wan-address-space) to learn what routes are installed and how to customize them). If you prefer to do this manually, unselect this option.
Warning
Cloudflare recommends that you leave this option selected. If you unselect **Add routes for your Magic WAN address space to your cloud network**, you will need to manually create all the required configurations to allow Magic WAN to connect to your cloud, such as routing tables, transit gateways, and VPNs. Refer to the [Magic WAN How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section, or consult the documentation for your cloud provider for more information.
2. **Add routes for your cloud network to Magic WAN**: Select this option to create routes for reaching your cloud network in Magic WAN.
12. Select **Continue**. Applying your settings might take a few seconds to complete.
13. Review the changes in your cloud environment, and select **Approve changes**.
You have successfully created your Magic WAN on-ramp. However, on-ramp creation can take up to an hour before you can use it.
### Set up with Terraform
You can download a Terraform configuration for a cloud on-ramp.
You might want to do this to:
* Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
* Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
The download will contain two files:
* `main.tf`: Terraform configuration for the new resources needed to create the on-ramp.
* `instructions.txt`: Instructions for modifying resources that already exist in your cloud environment.
If you intend to plan and apply the downloaded configuration using Terraform, you will need to use the [Cloudflare Terraform provider](https://developers.cloudflare.com/terraform/) (in addition to the Terraform provider for the on-ramp's cloud service provider). Use your Cloudflare [Global API Key](https://developers.cloudflare.com/fundamentals/api/get-started/keys/), not an API Token.
Warning
Do not deploy the on-ramp using both Cloudflare and Terraform. If you plan to deploy your on-ramp with Cloudflare (meaning you are both planning to create an on-ramp and applying an on-ramp), Cloudflare creates resources that will result in conflicts when you run Terraform (and vice versa). The Cloudflare dashboard will warn you if it detects you might encounter a conflict.
#### Download Terraform configuration for a new on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud on-ramps**, select **Add new on-ramp** and begin the **Create a Magic WAN cloud on-ramp** workflow following the standard steps.
4. After the **Configure route propagation** step, select **View download options** instead of selecting **Continue**.
5. Select a download option:
1. Choose **Download file and continue** to download the Terraform configuration, review the configuration, and then continue deploying the on-ramp with Cloudflare.
2. Choose **Download file and exit** to download the Terraform configuration that you will apply yourself.
#### Download Terraform configuration for an existing on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud on-ramps**, find the on-ramp you want to download > select the three dots > **Download as Terraform**.
## Update security groups
After setting up your on-ramps, you need to update your network security groups in your cloud provider to allow traffic to/from Magic WAN. Refer to the [Cloud on-ramps](https://developers.cloudflare.com/magic-cloud-networking/reference/) reference page for more information.
***
## Edit on-ramps
### Edit a Magic WAN cloud on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select the on-ramp you want to edit.
4. Select **Edit** in the side panel.
5. In **Basic information**, you can change the name and description of your on-ramp. Select **Save** when you are finished.
6. In **Configurations**, you can modify where the required routes are installed. Select **Continue**.
1. Select **Save and review** after making changes.
2. Review your settings, and select **Approve changes**.
Warning
If you uncheck any of the Propagation settings, you will have to manually configure Magic WAN or your cloud provider to ensure successful communication between them. Refer to the [How to](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/) section of Magic WAN, or consult the documentation for your cloud provider for more information.
### Delete a Magic WAN cloud on-ramp
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. Select the on-ramp you want to delete.
4. Select **Edit** in the side panel.
5. Choose **Detach** to proceed. Cloudflare will stop managing the cloud resources that were created to build this on-ramp, but will leave them in place. On-ramp connectivity will not be impacted.
***
## Magic WAN address space
By default, Cloudflare installs the following summarized routes in your cloud route tables to direct traffic to Magic WAN:
```txt
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
100.64.0.0/10
```
To override the defaults with custom prefixes:
1. Go to the **Routes** page.
[Go to **Routes**](https://dash.cloudflare.com/?to=/:account/magic-networks/routes)
2. Select **WAN configuration**.
3. Scroll to **Propagated routes to cloud networks**.
4. Delete the prefixes, and enter your custom ones.
5. When you are finished, select **Save changes**.
To install a default route to send all traffic to Magic WAN, enter `0.0.0.0/0` (on Azure, enter `0.0.0.0/1` and `128.0.0.0/1`).
***
## Cost estimates
You can view estimated costs associated with your cloud resources in the Cloudflare dashboard.
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud on-ramps**, find the cloud on-ramp for which you want to check the estimated costs > select the three dots > **Associated Resources**.
4. In the **Associated Resources** page, you can view the estimated monthly costs for all the resources associated with the on-ramp you chose. You can also search for a specific resource using the search box.
---
title: Get started · Cloudflare Magic Cloud Networking docs
description: To get started with Magic Cloud Networking (beta) you need to give
Cloudflare permission to interact with cloud providers on your behalf. You
might have multiple provider accounts for the same cloud provider — for
example, you might want Cloudflare to manage virtual private clouds (VPCs)
belonging to two different AWS accounts.
lastUpdated: 2026-01-22T10:37:48.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/get-started/
md: https://developers.cloudflare.com/magic-cloud-networking/get-started/index.md
---
To get started with Magic Cloud Networking (beta) you need to give Cloudflare permission to interact with cloud providers on your behalf. You might have multiple provider accounts for the same cloud provider — for example, you might want Cloudflare to manage virtual private clouds (VPCs) belonging to two different AWS accounts.
Once Cloudflare has the credentials required to access your cloud environments, Magic Cloud Networking will automatically begin discovering your cloud resources — like routing tables and virtual private networks. Discovered resources appear in your [Cloud resource catalog](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/#cloud-resource-catalog).
## Set up Amazon AWS
### 1. Create integration
1. Go to the **Cloud integrations (beta)** page.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select **Add** > **AWS integration**.
3. Give a descriptive name to your integration. Optionally, you can also add a description for it.
4. Select **Create integration**.
5. Select **Authorize access** to start the process of connecting your Cloudflare account to Amazon AWS.
### 2. Create IAM policy
1. Create a [custom IAM policy](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_create-console.html) in your AWS account, and take note of the name you entered. Then, paste the following [JSON code](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_version.html) in the JSON tab:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:AcceptTransitGatewayPeeringAttachment",
"ec2:CreateTransitGatewayPeeringAttachment",
"ec2:DeleteTransitGatewayPeeringAttachment",
"ec2:DescribeRegions",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:RejectTransitGatewayPeeringAttachment",
"ec2:GetManagedPrefixListEntries",
"ec2:CreateManagedPrefixList",
"ec2:ModifyManagedPrefixList",
"ec2:DeleteManagedPrefixList",
"ec2:CreateTransitGatewayPrefixListReference",
"ec2:DeleteTransitGatewayPrefixListReference",
"ec2:GetTransitGatewayPrefixListReferences",
"ec2:ModifyTransitGatewayPrefixListReference"
],
"Resource": "*"
}
]
}
```
### 3. Authorize access to your AWS account
1. Create an [AWS role](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-custom.html) with the following settings:
* **Trusted entity type**: Select **Custom trust policy**, and paste the custom trust policy returned by the Cloudflare dashboard.
* **Permissions**: Add the IAM policy you created in the previous step, along with these AWS-managed policies:
* `NetworkAdministrator`
* `AmazonEC2ReadOnlyAccess`
* `AmazonVPCReadOnlyAccess`
* `IAMReadOnlyAccess`
* **ARN**: Copy the ARN for your newly created user.
Note
The trust policy may take several minutes to propagate to all regions. It usually takes less than four minutes, but can sometimes take longer. You may have to retry the **Authorize** button while the propagation takes effect.
2. Select **I authorize Cloudflare to access my AWS account.**
3. Select **Authorize**.
Note
The first discovery of resources may not succeed in all regions while the IAM policy is propagating. If you do not see all resources after creating your cloud integration, try re-discovering.
## Set up Microsoft Azure
### 1. Create integration
1. In the Cloudflare dashboard, go to **Cloud integrations (beta)**.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select **Add** > **Azure integration**.
3. Give a descriptive name to your integration. Optionally, you can also add a description for it.
4. Select **Create integration**.
5. Select **Authorize access** to start the process of connecting your Cloudflare account to Microsoft Azure.
### 2. Authorize access to your Azure account
Warning
Magic Cloud does not support personal Microsoft accounts. Sign in using a work or school account that is part of an Azure Entra Tenant.
1. Select **Create service principal**. You will be redirected to Microsoft's login page.
2. Enter your Azure credentials. If your account does not have administrator privileges, you may need to pass this link to an account that has administrator privileges.
3. The next screen lists Cloudflare required permissions to access your account. Select **Accept**.
4. [Add a role assignment](https://learn.microsoft.com/en-us/azure/role-based-access-control/role-assignments-portal). The purpose of this step is to give the app that you registered in step 1 permission to access your Azure Subscription.
* In step 3 of the linked document, select the **Contributor** role from the **Privileged administrator roles** tab.
* In step 4 of the linked document, search for `mcn-provider-integrations-bot-prod` when selecting members.
5. In **Provide account information**, enter your **Tenant ID** and **Subscription ID**.
6. In **Verify account ownership**, [add the tags displayed in the Cloudflare dashboard](https://learn.microsoft.com/en-us/azure/azure-resource-manager/management/tag-resources-portal).
Note
The tags may take several minutes to propagate and become readable to Cloudflare. It usually takes less than four minutes, but can sometimes take longer. You may have to retry the **Authorize** button while the propagation takes effect.
7. Select **I authorize Cloudflare to access my Azure account.** If your account does not have administrator privileges, you may need to pass this link to an account that has administrator privileges.
8. Select **Authorize**.
Note
The first discovery of resources may not succeed in all regions while the IAM policy is propagating. If you do not see all resources after creating your cloud integration, try re-discovering.
## Set up Google Cloud
### 1. Create integration
1. In the Cloudflare dashboard, go to **Cloud integrations (beta)**.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select **Add** > **Google integration**.
3. Give a descriptive name to your integration. Optionally, you can also add a description for it.
4. Select **Create integration**.
5. Select **Authorize access** to start the process of connecting your Cloudflare account to Google Cloud.
### 2. Authorize access to your Google account
1. Create a new [GCP service account](https://cloud.google.com/iam/docs/service-accounts-create) in your **Google account** > **GCP Console** > **IAM & Admin** > **Service Accounts**.
2. Grant the new service account these roles:
* `Compute Network Admin`
* `Compute Viewer`
3. Under **IAM & Admin** > **Service Accounts**, select the service account you just created, and navigate to the **Permissions** tab.
4. Grant the **Service Account Token Creator** role to our bot account to allow it to impersonate this service account. Learn how to grant a specific role [in Google's documentation](https://cloud.google.com/iam/docs/manage-access-service-accounts#grant-single-role):
* `mcn-integrations-bot-prod@mcn-gcp-01.iam.gserviceaccount.com`
5. In the **service account email field**, enter the email account that you used to create the GCP service account.
6. In the **Project ID field**, enter the [project ID](https://support.google.com/googleapi/answer/7014113?hl=en) associated with your project.
7. [Add the label](https://cloud.google.com/resource-manager/docs/creating-managing-labels#create-labels) displayed in the dashboard of your project.
8. Select **I authorize Cloudflare to access my GCP account.** If your account does not have administrator privileges, you may need to pass this link to an account that has administrator privileges.
9. Select **Authorize**.
You have successfully connected your cloud provider to Magic Cloud Networking. Cloud resources found by Magic Cloud Networking are available in the [Cloud resource catalog](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/#cloud-resource-catalog).
Note
The first discovery of resources may not succeed in all regions while the IAM policy is propagating. If you do not see all resources after creating your cloud integration, try re-discovering.
## Next steps
* [Set up Magic WAN](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/) as an on-ramp to your cloud.
* [Manage resources](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/) found by Magic Cloud Networking.
* [Edit](https://developers.cloudflare.com/magic-cloud-networking/manage-resources/#edit-cloud-integrations) cloud integrations.
---
title: Manage resources · Cloudflare Magic Cloud Networking docs
description: Your cloud environment is built from individual cloud resources,
like virtual private clouds (VPCs), subnets, virtual machines (VMs), route
tables, and routes. Magic Cloud Networking (beta) discovers all of your cloud
resources and stores their configuration and status in the Cloud resource
catalog, a read-only snapshot of your cloud environment. Discovery runs
regularly in the background, keeping your catalog up to date as your
environment changes.
lastUpdated: 2026-01-23T15:31:55.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/manage-resources/
md: https://developers.cloudflare.com/magic-cloud-networking/manage-resources/index.md
---
## Cloud resource catalog
Your cloud environment is built from individual cloud resources, like virtual private clouds (VPCs), subnets, virtual machines (VMs), route tables, and routes. Magic Cloud Networking (beta) discovers all of your cloud resources and stores their configuration and status in the Cloud resource catalog, a read-only snapshot of your cloud environment. Discovery runs regularly in the background, keeping your catalog up to date as your environment changes.
To browse the resources in your catalog:
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud resources**, select a resource to inspect its details.
## Edit Cloud integrations
You can change which cloud account the integration is linked to or delete the integration.
1. Go to **Cloud integrations**.
[Go to **Cloud integrations**](https://dash.cloudflare.com/?to=/:account/mcn/integrations)
2. Select your integration > **Edit**.
3. In **Linked account details**, select **Link integration to a different cloud account**.
4. Select **Save** when you are finished.
5. (Optional) You can also select **Delete** to delete your cloud integration.
## Download cloud resource catalog
You can download a JSON file containing metadata and configuration for all your cloud resources:
1. Go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Cloud (beta)** tab.
3. In **Cloud resources**, select **Download catalog**.
After your browser finishes downloading the ZIP file, expand it to access the JSON with the information about your cloud resources.
---
title: Reference · Cloudflare Magic Cloud Networking docs
description: Refer to this page for details about how Cloudflare orchestrates
VPN connectivity to your cloud networks.
lastUpdated: 2026-01-22T10:37:48.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-cloud-networking/reference/
md: https://developers.cloudflare.com/magic-cloud-networking/reference/index.md
---
Refer to this page for details about how Cloudflare orchestrates VPN connectivity to your cloud networks.
## Cloud on-ramps
### AWS

When using Magic Cloud Networking (beta) to automatically create on-ramps to your AWS account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
* Cloudflare will create a new customer-managed prefix list named **Magic WAN and Cloudflare Edge** populated with your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) prefixes and the IPv4 address ranges for Cloudflare's global network servers (the latter prefixes are necessary if you use any Cloudflare L7 processing features). You must create rules in your Network Security Groups (NSGs) allowing traffic to/from this prefix list in order to have connectivity with Magic WAN. (The prefix list will contain around 15 to 25 entries, which each count against the rules-per-security-group quota for NSGs in your AWS account.)
* Cloudflare will create a Virtual Private Gateway and attach it to your Virtual Private Cloud (VPC). If an existing Virtual Private Gateway is already attached to the VPC, on-ramp creation will fail.
* Cloudflare will enable route propagation from the Virtual Private Gateway into all route tables in your VPC. This will result in a route for each prefix in your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) targeting the gateway.
* Cloudflare will add a route in Magic WAN for each IPv4 CIDR (Classless Inter-Domain Routing) block in your VPC.
### Azure

When using Magic Cloud Networking (beta) to automatically create on-ramps to your Azure account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
* Cloudflare will create a Virtual Network Gateway in your Virtual Network (VNet). Virtual Network Gateways in Azure require a subnet named `GatewaySubnet`. Cloudflare will create a `GatewaySubnet` if one does not already exist in your VNet. If there is not enough unused address space left in your VNet to create a `/27` subnet for the `GatewaySubnet`, or if a `GatewaySubnet` exists but does not have enough address space left for a Virtual Network Gateway, on-ramp creation will fail.
* Cloudflare will enable gateway route propagation on all route tables in your VNet. This will result in a route for each prefix in your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) pointing to the gateway. If your VNet has other Virtual Network Gateways, their routes will also propagate to your route tables. If you delete the on-ramp, route propagation will not be disabled.
* By default, Network Security Groups in Azure contain Allow rules for outbound/inbound traffic to/from the `VirtualNetwork` service tag, which includes Virtual Network Gateway address space (and therefore your Magic WAN Address Space). If you do not want all resources in your VNet to be accessible from Magic WAN, add the appropriate Deny rules to your Network Security Groups (NSGs).
* Cloudflare will add a route in Magic WAN for each IPv4 address range in your VNet.
### GCP

When using Magic Cloud Networking (beta) to automatically create on-ramps to your Google Cloud Platform (GCP) account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
* Cloudflare will reserve a public Internet routable IP address from GCP.
* Cloudflare will create a VPN Gateway and two VPN Tunnels in the region you specify.
* Cloudflare will create routes for each prefix in your [Magic WAN Address Space](https://developers.cloudflare.com/magic-cloud-networking/cloud-on-ramps/#magic-wan-address-space) within your VPC pointing to the VPN Tunnels.
* Cloudflare will add routes in Magic WAN for all subnet CIDR prefixes in your VPC. This includes all regions within the VPC. Traffic bound for a region other than the VPN Gateway's region will be subject to GCP's [Inter-region Pricing](https://cloud.google.com/vpc/network-pricing#inter-region-data-transfer).
* Traffic sent to and from your VM instances through the VPN Tunnels is still subject to VPC firewall rules, and may [require further configuration](https://cloud.google.com/network-connectivity/docs/vpn/how-to/configuring-firewall-rules#firewall_rules).
## Supported resources
Magic Cloud Networking (beta) discovers the following resource types in your cloud environments. These resources are used to build a comprehensive view of your cloud network topology and connectivity.
### AWS
* AWS Customer Gateway
* AWS EC2 Managed Prefix List
* AWS EC2 Transit Gateway
* AWS EC2 Transit Gateway Prefix List
* AWS EC2 Transit Gateway VPC Attachment
* AWS Egress Only Internet Gateway
* AWS Internet Gateway
* AWS Instance
* AWS Network Interface
* AWS Route Table
* AWS Route Table Association
* AWS Security Group
* AWS Subnet
* AWS VPC
* AWS VPC IPv4 CIDR Block Association
* AWS VPC Security Group Egress Rule
* AWS VPC Security Group Ingress Rule
* AWS VPN Connection
* AWS VPN Connection Route
* AWS VPN Gateway
### Azure
* Azure Application Security Group
* Azure Load Balancer
* Azure Load Balancer Backend Address Pool
* Azure Load Balancer NAT Pool
* Azure Load Balancer NAT Rule
* Azure Load Balancer Rule
* Azure Local Network Gateway
* Azure Network Interface
* Azure Network Interface Application Security Group Association
* Azure Network Interface Backend Address Pool Association
* Azure Network Interface Security Group Association
* Azure Network Security Group
* Azure Public IP
* Azure Route
* Azure Route Table
* Azure Subnet
* Azure Subnet Route Table Association
* Azure Virtual Machine
* Azure Virtual Machine Gateway Connection
* Azure Virtual Network
* Azure Virtual Network Gateway
* Azure Virtual Network Gateway Connection
### GCP
* Google Compute Address
* Google Compute Forwarding Rule
* Google Compute Global Address
* Google Compute HA VPN Gateway
* Google Compute Interconnect Attachment
* Google Compute Network
* Google Compute Network Firewall Policy
* Google Compute Network Firewall Policy Rule
* Google Compute Route
* Google Compute Router
* Google Compute Subnetwork
* Google Compute VPN Gateway
* Google Compute VPN Tunnel
---
title: 404 - Page Not Found · Cloudflare Magic Firewall docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/404/
md: https://developers.cloudflare.com/magic-firewall/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About · Cloudflare Magic Firewall docs
description: Review the content below to learn more about concepts related to
Magic Firewall.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/about/
md: https://developers.cloudflare.com/magic-firewall/about/index.md
---
Review the content below to learn more about concepts related to Magic Firewall.
Important
When using Magic Firewall alongside other Cloudflare services that proxy traffic (for example, CDN and Spectrum), be aware of the following:
* Firewall rules that block traffic based on source IP address may not work as intended because rules are evaluated after Cloudflare terminates the incoming TCP connections.
* You must allow [Cloudflare IP addresses](https://www.cloudflare.com/ips/).
* When using Magic Firewall, fragmented packets are reassembled into complete packets before they are inspected. As a result, you cannot create firewall rules for fragments.
- [Analytics](https://developers.cloudflare.com/magic-firewall/about/analytics/)
- [IDS](https://developers.cloudflare.com/magic-firewall/about/ids/)
- [List types](https://developers.cloudflare.com/magic-firewall/about/list-types/)
- [Protocol validation rules](https://developers.cloudflare.com/magic-firewall/about/protocol-validation-rules/)
- [Ruleset logic](https://developers.cloudflare.com/magic-firewall/about/ruleset-logic/)
- [Traffic types](https://developers.cloudflare.com/magic-firewall/about/traffic-types/)
---
title: Best practices · Cloudflare Magic Firewall docs
description: By default, Magic Firewall permits all ingress traffic that has
passed through Cloudflare's core DDoS mitigations. To proactively mitigate
attacks and minimize your attack surface and leakage of attack traffic into
your environment, we recommend implementing your Magic Firewall rules using
the following guidelines.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/best-practices/
md: https://developers.cloudflare.com/magic-firewall/best-practices/index.md
---
By default, Magic Firewall permits all ingress traffic that has passed through Cloudflare's core DDoS mitigations. To proactively mitigate attacks and minimize your attack surface and leakage of attack traffic into your environment, we recommend implementing your Magic Firewall rules using the following guidelines.
The best approach is to replicate your current ingress perimeter firewall rules in Magic Firewall. If you are unable to export your current perimeter firewall rules, contact your Implementation Manager for help translating the rules into Magic Firewall rules.
* [Minimal ruleset](https://developers.cloudflare.com/magic-firewall/best-practices/minimal-ruleset/)
* [Extended ruleset](https://developers.cloudflare.com/magic-firewall/best-practices/extended-ruleset/)
* [Magic Transit egress](https://developers.cloudflare.com/magic-firewall/best-practices/magic-transit-egress/)
---
title: Changelog · Cloudflare Magic Firewall docs
description: The Network Services menu structure in Cloudflare's dashboard has
been updated to reflect solutions and capabilities instead of product names.
This will make it easier for you to find what you need and better reflects how
our services work together.
lastUpdated: 2025-04-24T15:57:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/changelog/
md: https://developers.cloudflare.com/magic-firewall/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-firewall.xml)
## 2026-01-15
**Network Services navigation update**
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

## 2025-03-13
**Cloudflare IP Ranges List**
Magic Firewall now supports a new managed list of Cloudflare IP ranges. This list is available as an option when creating a Magic Firewall policy based on IP source/destination addresses. When selecting "is in list" or "is not in list", the option "**Cloudflare IP Ranges**" will appear in the dropdown menu.
This list is based on the IPs listed in the Cloudflare [IP ranges](https://www.cloudflare.com/en-gb/ips/). Updates to this managed list are applied automatically.

Note: IP Lists require an advanced Magic Firewall subscription. For more details about Magic Firewall plans, refer to [Plans](https://developers.cloudflare.com/magic-firewall/plans).
## 2024-10-02
**Search for custom rules using rule name and/or ID**
The Magic Firewall dashboard now allows you to search custom rules using the rule name and/or ID.
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account.
2. Go to **Analytics & Logs** > **Network Analytics**.
3. Select **Magic Firewall**.
4. Add a filter for **Rule ID**.

Additionally, the rule ID URL link has been added to Network Analytics.
## 2024-09-12
**New UI improvements**
The dashboard now displays the order number of custom rules, and improved drag and drop functionality. You can also preview rules on a side panel without leaving the current page.
## 2024-08-16
**Magic Firewall Analytics Rule Log Enhancement**
Customers who create a rule in a disabled mode will see the rule as **Log (rule disabled)**.
---
title: How to · Cloudflare Magic Firewall docs
description: Review the content below to learn how to complete tasks using Magic Firewall.
lastUpdated: 2024-10-03T13:28:13.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-firewall/how-to/
md: https://developers.cloudflare.com/magic-firewall/how-to/index.md
---
Review the content below to learn how to complete tasks using Magic Firewall.
* [Add custom policies](https://developers.cloudflare.com/magic-firewall/how-to/add-policies/)
* [Enable IDS](https://developers.cloudflare.com/magic-firewall/how-to/enable-ids/)
* [Create Rate Limiting policies (beta)](https://developers.cloudflare.com/magic-firewall/how-to/create-rate-limiting-policies/)
* [Enable Magic user roles](https://developers.cloudflare.com/magic-firewall/how-to/enable-magic-roles/)
* [Enable Managed Rulesets](https://developers.cloudflare.com/magic-firewall/how-to/enable-managed-rulesets/)
* [Filter different views](https://developers.cloudflare.com/magic-firewall/how-to/filter-views/)
* [Form expressions](https://developers.cloudflare.com/magic-firewall/how-to/form-expressions/)
* [Use Logpush with IDS](https://developers.cloudflare.com/magic-firewall/how-to/use-logpush-with-ids/)
* [Use IP lists](https://developers.cloudflare.com/magic-firewall/how-to/use-rules-list/)
---
title: Packet captures · Cloudflare Magic Firewall docs
description: "Cloudflare supports two types of packet captures: full and sample.
Full packet captures is the default behavior."
lastUpdated: 2025-06-06T14:58:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/packet-captures/
md: https://developers.cloudflare.com/magic-firewall/packet-captures/index.md
---
Cloudflare supports two types of packet captures: full and sample. Full packet captures is the default behavior.
Note
The maximum packet capture runtime is 24 hours for sample and full packet captures.
## Sample packet captures
Sample packet captures collects historical data on network traffic that has already passed through Cloudflare's network. It will not collect any new traffic sent to Cloudflare's network after the packet capture has started. All sample packet captures will complete immediately after they are started because they query historical traffic data.
Sample packet captures can be viewed in the Cloudflare dashboard. They only include the first 160 bytes of data. This is useful for capturing packet headers, but will not provide detailed packet data. The sample data is collected across all Cloudflare's data centers to build a PCAP file. This allows you to get a global picture of traffic across all data centers.
You should use full packet captures if you need to collect data on packets that pass through your network less frequently.
## Full packet captures
Full packet captures will actively monitor Cloudflare's network for packets that match the selected filters, and will capture the matching packet data. The matching packet data is saved to a cloud storage bucket that is owned and configured by you.
Full packet captures will collect new traffic sent to Cloudflare's network after the packet capture has started, and include the full packet data. This type of capture cannot be viewed in the Cloudflare dashboard. You can download them from a cloud storage bucket and analyze them in Wireshark or another packet capture tool.
Refer to the articles in this section to learn how to use packet captures.
* [PCAPs bucket setup](https://developers.cloudflare.com/magic-firewall/packet-captures/pcaps-bucket-setup/)
* [Collect PCAPs](https://developers.cloudflare.com/magic-firewall/packet-captures/collect-pcaps/)
---
title: Plans · Cloudflare Magic Firewall docs
description: If you are a Magic Transit or Magic WAN user, you are automatically
provided with a standard list of Magic Firewall features. For additional
features available for purchase, refer to the list of advanced features below.
lastUpdated: 2025-10-22T21:11:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-firewall/plans/
md: https://developers.cloudflare.com/magic-firewall/plans/index.md
---
If you are a [Magic Transit](https://developers.cloudflare.com/magic-transit/) or [Magic WAN](https://developers.cloudflare.com/magic-wan/) user, you are automatically provided with a standard list of Magic Firewall features. For additional features available for purchase, refer to the list of advanced features below.
## Standard features
* Filtering rules based on protocol, port, IP addresses, packet length, and bit field match.
* Fast propagation of rule changes in less than a minute.
* Single dashboard to manage firewall and network configuration.
* Programmable API for automated deployment and management — compatible with infrastructure-as-code platforms like [Terraform](https://developers.cloudflare.com/terraform/).
* Traffic analytics per rule in the dashboard and using the [GraphQL API](https://developers.cloudflare.com/analytics/graphql-api/).
* Integration with [Magic WAN network-as-a-service](https://developers.cloudflare.com/magic-wan/).
* Included DDoS protection with [Magic Transit](https://developers.cloudflare.com/magic-transit/).
## Advanced features
All standard features are included with the purchase of the advanced features below:
* Customizable IP lists.
* Managed threat intelligence IP lists (Anonymizer, Botnet, Malware, Open Proxies, VPNs).
* Geoblocking based on user location by country.
* Block or allow packets based on Autonomous System Number (ASN).
* Packet captures on demand for network troubleshooting.
* [Protocol validation rules](https://developers.cloudflare.com/magic-firewall/about/protocol-validation-rules/) to inspect traffic validity and enforce a positive security model.
* [Secure Web Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/) filtering for outbound Internet traffic (network and HTTP policies). The Secure Web Gateway supports all TCP and UDP ports, as well as traffic sourced from RFC 1918 address space. Gateway will proxy BYOIP traffic to egress via the default Cloudflare IPs or your assigned [dedicated egress IPs](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/dedicated-egress-ips/).
* Intrusion Detection System (IDS).
---
title: Reference · Cloudflare Magic Firewall docs
description: Review the content below for more information about Magic Firewall.
lastUpdated: 2024-10-03T13:28:13.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-firewall/reference/
md: https://developers.cloudflare.com/magic-firewall/reference/index.md
---
Review the content below for more information about Magic Firewall.
* [Magic Firewall fields](https://developers.cloudflare.com/magic-firewall/reference/magic-firewall-fields/)
* [Magic Firewall functions](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/#magic-firewall-functions)
---
title: Tutorials · Cloudflare Magic Firewall docs
description: View tutorials to help you get started with Magic Firewall.
lastUpdated: 2024-10-03T13:28:13.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-firewall/tutorials/
md: https://developers.cloudflare.com/magic-firewall/tutorials/index.md
---
View tutorials to help you get started with Magic Firewall.
| Name | Last Updated | Difficulty |
| - | - | - |
| [GraphQL Analytics](https://developers.cloudflare.com/magic-firewall/tutorials/graphql-analytics/) | almost 4 years ago | Medium |
---
title: 404 - Page Not Found · Cloudflare Magic Network Monitoring docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/404/
md: https://developers.cloudflare.com/magic-network-monitoring/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API · Cloudflare Magic Network Monitoring docs
description: Use Magic Network Monitoring's API to configure your account and rules.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/api/
md: https://developers.cloudflare.com/magic-network-monitoring/api/index.md
---
Use Magic Network Monitoring's API to configure your account and rules.
## Account configuration
Refer to [Account configuration API methods](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/configs/methods/get/) to:
* Create, list, update, and delete Magic Network Monitoring configurations
* List default sampling, router IPs, and rules for an account
## Rules configuration
Refer to [Rules configuration API methods](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/rules/methods/list/) to:
* Create, list, update, and delete rules
* Update advertisement for a rule
---
title: Cloud flow logs (beta) · Cloudflare Magic Network Monitoring docs
description: Customers using Magic Network Monitoring can export virtual private
cloud (VPC) flow logs from their cloud environment to Cloudflare's network.
Cloudflare processes these logs and displays analytics on your cloud traffic
in the dashboard. You can also ingest data on your cloud traffic via our
public GraphQL API, which powers the cloud traffic analytics in the Cloudflare
dashboard.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/cloud-flow-logs/
md: https://developers.cloudflare.com/magic-network-monitoring/cloud-flow-logs/index.md
---
Customers using Magic Network Monitoring can export virtual private cloud (VPC) flow logs from their cloud environment to Cloudflare's network. Cloudflare processes these logs and displays analytics on your cloud traffic in the dashboard. You can also ingest data on your cloud traffic via our public [GraphQL API](https://developers.cloudflare.com/analytics/graphql-api/), which powers the cloud traffic analytics in the Cloudflare dashboard.
Currently, Magic Network Monitoring only supports AWS VPC flow logs via AWS Firehose. You can only configure AWS flow logs via the Magic Network Monitoring API.
To learn how to set up AWS VPC flow logs, refer to [Set up AWS VPC flow logs](https://developers.cloudflare.com/magic-network-monitoring/get-started/#vpc-flow-log-guide).
---
title: Changelog · Cloudflare Magic Network Monitoring docs
description: Review recent changes to Magic Network Monitoring.
lastUpdated: 2025-04-24T15:57:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/changelog/
md: https://developers.cloudflare.com/magic-network-monitoring/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-network-monitoring.xml)
## 2026-01-15
**Network Services navigation update**
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

## 2024-09-24
**Try out Magic Network Monitoring**
The free version of Magic Network Monitoring (MNM) is now available to everyone with a Cloudflare account by default.
1. Log in to your [Cloudflare dashboard](https://dash.cloudflare.com), and select your account.
2. Go to **Analytics & Logs** > **Magic Monitoring**.

For more details, refer to the [Get started guide](https://developers.cloudflare.com/magic-network-monitoring/get-started/).
---
title: FAQ · Cloudflare Magic Network Monitoring docs
description: Find answers to the most commonly asked questions. If you cannot
find the answer you are looking for, refer to the community page to explore
more resources.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/faq/
md: https://developers.cloudflare.com/magic-network-monitoring/faq/index.md
---
Find answers to the most commonly asked questions. If you cannot find the answer you are looking for, refer to the [community page](https://community.cloudflare.com/) to explore more resources.
## I am getting an "Invalid account settings request body: account name format contains illegal characters or is not supported" error when trying to create a rule.
This probably means that your account name has unsupported characters. Make sure your account name does not have characters like, for example, `&`, `<`, `>`, `"`, `'`, `` ` ``.
Refer to [Account name](https://developers.cloudflare.com/fundamentals/account/create-account/#account-name) to learn how to change your account name.
## Can I send NetFlow/sFlow data to Cloudflare in a secure, encrypted way?
Yes. Both enterprise and free customers can send encrypted network flow data to Cloudflare.
Enterprise customers with Magic Transit or Magic WAN can send encrypted network flow data via an IPsec tunnel to Cloudflare's network. You can achieve this by:
1. Configuring your [NetFlow](https://developers.cloudflare.com/magic-network-monitoring/routers/netflow-ipfix-config/) or [sFlow](https://developers.cloudflare.com/magic-network-monitoring/routers/sflow-config/) data to be sent to Cloudflare's network for parsing.
2. Directing that network flow data to be sent over [Magic Transit IPsec tunnels](https://developers.cloudflare.com/magic-transit/how-to/configure-tunnel-endpoints/) or [Magic WAN IPsec tunnels](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-tunnel-endpoints/) to Cloudflare's network.
Cloudflare's network will then identify this traffic via the destination IP address/port, and direct the network flow traffic to Magic Network Monitoring for parsing.
Free customers can route their network flow traffic through a device that is running the WARP client. Then, network flow traffic can be forwarded from the WARP enabled device to Cloudflare's network flow endpoints. Learn more in the [Encrypt network flow data tutorial](https://developers.cloudflare.com/magic-network-monitoring/tutorials/encrypt-network-flow-data/).
## I have Auto-Advertisement enabled and it was triggered by an attack. Do I have to turn Magic Transit off manually?
Once Auto-Advertisement is activated for an IP prefix that is under attack, the IP prefix will continue to be advertised by Cloudflare even if the attack ends. You must manually disable advertisement for that IP prefix. Refer to [Configure dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement) to learn how to withdraw your prefixes, and stop using Magic Transit.
## If Auto-Advertisement is enabled, and the threshold has been triggered, will the IP prefix show as advertised in the dashboard?
Yes, the IP prefix will show as advertised under the [IP Prefixes tab](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement).
## Does Auto-advertisement also work with BGP-controlled advertisements?
No. Auto-advertisement only works with API-controlled advertisement, not BGP-controlled advertisement.
## In the API, Magic Network Monitoring rules have a `bandwidth_threshold` data field. Does the value for this field refer to bytes transferred or current throughput?
The threshold for a [Magic Network Monitoring rule](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/rules/methods/list/) has two values. The first value is `bandwidth_threshold`. This value is a measure of the total ingress throughput on a network at any given moment. The second value is `duration`. The `duration` value refers to the amount of time that `bandwidth_threshold` must be exceeded before an alert is sent to the customer.
For example, you create a Magic Network Monitoring rule with the following parameters:
```txt
"bandwidth_threshold": 50000000
"duration": "1m0s"
```
With this rule, your network needs to receive a throughput greater than 50,000,000 bits per second (50 Gigabits per second or Gbps) for 60 seconds. If both of these conditions are met, then Magic Network Monitoring will send you an alert.
## My router's public IP address is different from the IP address of my network flow `agent-ip`. I cannot change my network flow `agent-ip`, and I am not seeing my router's traffic in Magic Network Monitoring analytics
Set your router's public IP address and network flow `agent-ip` to the same value. However, if you are unable to do this, you can register both your router's public IP and your network flow `agent-ip` in the Magic Network Monitoring [router configuration](https://developers.cloudflare.com/magic-network-monitoring/get-started/). This will prevent Magic Network Monitoring from blocking network traffic received from any unknown IP addresses, and will show your router's network flow data underneath the router's `agent-ip`.
## What is Magic Network Monitoring's data retention policy for NetFlow/sFlow received from customer's routers?
Currently, all data received from a customer's router goes to our servers in the US. If you enable data sovereignty in Europe, you cannot currently use Magic Network Monitoring.
GraphQL analytics is retained for 90 days for enterprise customers. For non-enterprise customers, data retention is seven days. Cloudflare also retains data for six hours in the US, for threshold crossing detection.
---
title: Get started · Cloudflare Magic Network Monitoring docs
description: Magic Network Monitoring includes an onboarding workflow that
guides you step-by-step through the product configuration process. If you are
unable to complete the configuration in one session, you can exit the workflow
and resume it at any time.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/get-started/
md: https://developers.cloudflare.com/magic-network-monitoring/get-started/index.md
---
Magic Network Monitoring includes an onboarding workflow that guides you step-by-step through the product configuration process. If you are unable to complete the configuration in one session, you can exit the workflow and resume it at any time.
To begin using Magic Network Monitoring for network and/or cloud traffic visibility, complete the list of tasks below.
* [NetFlow and sFlow guide](#netflow-and-sflow-guide)
* [VPC flow log guide (beta)](#vpc-flow-log-guide)
If you are an Enterprise customer, Cloudflare can significantly accelerate the onboarding timeline during active-attack scenarios.
Enterprise customers that would like to use Magic Network Monitoring and Magic Transit On Demand together can begin by [configuring Magic Transit](https://developers.cloudflare.com/magic-transit/get-started/).
## NetFlow and sFlow guide
### 1. Verify NetFlow or sFlow capabilities
Verify your routers are capable of exporting NetFlow or sFlow to an IP address on Cloudflare's network. Magic Network Monitoring supports NetFlow v5, NetFlow v9, IPFIX, and sFlow.
Refer to [Supported routers](https://developers.cloudflare.com/magic-network-monitoring/routers/supported-routers) to view a list of supported routers. The list is not exhaustive.
### 2. Register your router with Cloudflare
When you register your router with Cloudflare, your router links your NetFlow or sFlow data to your Cloudflare account.
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. In **Network flow (Magic Network Monitoring)**, select **Configure Network flow**.
2. Select the **Configure routers** tab.
3. (Optional) Under **IP Address**, enter your router's public IP address.
4. Under **Default router sampling rate**, enter a value for the sampling rate. The value should match the sampling rate of your NetFlow or sFlow configuration.
5. Select **Next**.
### 3. Configure your router
Next, configure your router to send NetFlow or sFlow data to Cloudflare. For this step, you will also need to have your router's configuration menu open to input the values shown in the Cloudflare dashboard.
Refer to the [NetFlow and IPFIX configuration guide](https://developers.cloudflare.com/magic-network-monitoring/routers/netflow-ipfix-config/) or the [sFlow configuration guide](https://developers.cloudflare.com/magic-network-monitoring/routers/sflow-config/) for more information.
1. From **Configure routers** in the dashboard, select either **NetFlow Configuration** or **sFlow configuration**.
2. Follow the configuration steps for the selected configuration type.
3. Enter the values shown in your router's configuration.
4. Select **Next**.
### 4. Check your router configuration
After setting up your router, confirm the configuration was successfully set up.
From the **Check routers** page on the dashboard, you can view the status of your routers. Router data typically takes five to ten minutes to appear in the Cloudflare dashboard.
Refer to **Router status description** to confirm whether data is successfully being sent.
When you are done with router configuration, select **Finish onboarding**.
Note
This will only be visible during the onboarding process. When you are finished onboarding, this page will no longer be visible.
### 5. Create rules
Create rules to analyze data for a specific set of destinations or to implement thresholds. Refer to [Rules](https://developers.cloudflare.com/magic-network-monitoring/rules/) for more information.
## VPC flow log guide Beta
### 1. Verify cloud flow log capabilities
Verify that your Amazon Web Services (AWS) account is capable of exporting AWS Virtual Private Cloud (VPC) flow logs through AWS Firehose. Currently, Magic Network Monitoring only supports VPC flow log ingestion for AWS.
### 2. Set up AWS Firehose to export VPC flow logs to Cloudflare
Note
AWS VPC flow logs can only be configured through the Cloudflare API for Magic Network Monitoring. There are no inputs in the dashboard for configuring AWS VPC flow logs.
1. Create an authorization token using [Cloudflare's API for Magic Network Monitoring](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/vpc_flows/subresources/tokens/methods/create/). This authorization token allows Cloudflare to identify and verify the account sending VPC flow logs to our endpoint.
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Magic Network Monitoring Admin`
```bash
curl "https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/mnm/vpc-flows/token" \
--request POST \
--header "X-Auth-Email: $CLOUDFLARE_EMAIL" \
--header "X-Auth-Key: $CLOUDFLARE_API_KEY"
```
2. In your AWS Firehose stream configuration, set the `HTTP Headers - X-Amz-Firehose-Access-Key` to the authorization token generated in the previous step.
3. Send your AWS Firehose VPC flow log stream towards `https://aws-flow-logs.cloudflare.com/`.
4. Select all of the AWS VPC flow log data fields that you want to send to Cloudflare. You should select the highest number AWS VPC flow log version that supports all the fields you want to export to Cloudflare (refer to [AWS flow log documentation](https://docs.aws.amazon.com/vpc/latest/userguide/flow-log-records.html) for more information). For example, if you need a version 8 field like `reject-reason`, you must export all fields from versions 1 through 8. Cloudflare supports all seven templates for AWS VPC Flow logs.
### 3. Verify your cloud traffic via analytics
After setting up AWS Firehose to send VPC flow logs to Magic Network Monitoring, you can confirm that Cloudflare is receiving the logs as expected by searching for your cloud traffic data in the analytics page of the Magic Network Monitoring dashboard.
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. The default view will be the analytics dashboard for Magic Network Monitoring.
---
title: Glossary · Cloudflare Magic Network Monitoring docs
description: Review the definitions for terms used across Cloudflare's Magic
Network Monitoring documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/glossary/
md: https://developers.cloudflare.com/magic-network-monitoring/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Magic Network Monitoring documentation.
| Term | Definition |
| - | - |
| flow data | Represents records of communication between devices. There are a number of flow data protocols, such as NetFlow or sFlow. |
| NetFlow | Network protocol developed by Cisco to collect and monitor network traffic flow data. |
| sampling | In the context of Magic Network Monitoring, sampling is the process of taking samples of packets for a specific period to identify potential attacks. |
| sFlow | An industry standard packet sampling protocol to monitor network devices. |
---
title: Magic Transit integration · Cloudflare Magic Network Monitoring docs
description: With Magic Transit On Demand, you can use Magic Network Monitoring
to analyze your network traffic and detect Distributed Denial of Service
(DDoS) attacks while Magic Transit is disabled. If an attack is detected, you
can automatically or manually enable Magic Transit to mitigate attacks.
lastUpdated: 2025-10-16T11:21:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/magic-transit-integration/
md: https://developers.cloudflare.com/magic-network-monitoring/magic-transit-integration/index.md
---
With [Magic Transit On Demand](https://developers.cloudflare.com/magic-transit/on-demand/), you can use Magic Network Monitoring to analyze your network traffic and detect Distributed Denial of Service (DDoS) attacks while Magic Transit is disabled. If an attack is detected, you can automatically or manually enable Magic Transit to mitigate attacks.
You can create Magic Network Monitoring rules which monitor specific Internet Protocol (IP) prefixes for DDoS attacks. When a DDoS attack is detected, Cloudflare notifies you by email, [webhook](https://developers.cloudflare.com/notifications/get-started/configure-webhooks/), or [PagerDuty](https://developers.cloudflare.com/notifications/get-started/configure-pagerduty/) with information about the attack. Then, you can [automatically activate IP advertisement](#activate-ip-auto-advertisement) and enable Magic Transit to protect the targeted IP prefixes from DDoS attacks. This feature is referred to as auto-advertisement, and you can enable it for individual Magic Network Monitoring rules through the dashboard or API.
After Magic Transit is activated and your traffic is flowing through Cloudflare, Cloudflare blocks malicious DDoS traffic, and your origin servers receive only clean network traffic through IPsec or Generic Routing Encapsulation (GRE) tunnels.
The following diagrams illustrate this process:



## Activate IP auto-advertisement
Enable IP auto-advertisement to use Magic Network Monitoring rules. You can activate IP auto-advertisement through the dashboard or the API.
### Dashboard
To activate IP advertisement through the Cloudflare dashboard, refer to [Configure dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement).
### API
To activate IP advertisement through the API, refer to the [IP Address Management Dynamic Advertisement API](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/advertisement_status/methods/edit/).
## Magic Network Monitoring rules
To create Magic Network Monitoring rules with auto-advertisement, refer to [Rule Auto-Advertisement](https://developers.cloudflare.com/magic-network-monitoring/rules/#rule-auto-advertisement).
---
title: Magic Network Monitoring free version · Cloudflare Magic Network
Monitoring docs
description: The free version of Magic Network Monitoring is generally available
to everyone with a Cloudflare account by default.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/magic-network-monitoring-free/
md: https://developers.cloudflare.com/magic-network-monitoring/magic-network-monitoring-free/index.md
---
The free version of Magic Network Monitoring is generally available to everyone with a Cloudflare account by default.
All free customers are encouraged to join [Cloudflare's Discord server](https://discord.com/invite/cloudflaredev) to discuss the use cases, configuration, and troubleshooting of Magic Network Monitoring. Free customers are always welcome to provide product feedback and discuss feature requests. The product and engineering team that works on Magic Network Monitoring regularly engages with the Discord community.
You can find the channel by joining the Cloudflare Developers Discord server. Then scroll down in the side bar navigation to the **Cloudflare One** category and select **magic-network-monitoring**.
## Access the free version of Magic Network Monitoring
The free version includes all the features of the enterprise version, but has network flow volume and configuration limitations. These limits are detailed below.
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Complete the onboarding wizard to configure Magic Network Monitoring. Refer to [Get started](https://developers.cloudflare.com/magic-network-monitoring/get-started/) for detailed configuration instructions.
## Limitations
| Configuration limit | Value |
| - | - |
| Number of registered routers | 10 |
| Number of rules | 25 |
| Network flows per second per account | 250 |
---
title: Routers · Cloudflare Magic Network Monitoring docs
lastUpdated: 2024-08-30T16:09:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/routers/
md: https://developers.cloudflare.com/magic-network-monitoring/routers/index.md
---
* [Supported routers](https://developers.cloudflare.com/magic-network-monitoring/routers/supported-routers/)
* [Recommended sampling rate](https://developers.cloudflare.com/magic-network-monitoring/routers/recommended-sampling-rate/)
* [Netflow/IPFIX configuration](https://developers.cloudflare.com/magic-network-monitoring/routers/netflow-ipfix-config/)
* [sFlow configuration](https://developers.cloudflare.com/magic-network-monitoring/routers/sflow-config/)
---
title: Rules · Cloudflare Magic Network Monitoring docs
description: Magic Network Monitoring rules allow you to monitor your network
traffic for Distributed Denial of Service (DDoS) attacks on specific IP
addresses or IP prefixes within your network. If the network traffic that is
monitored by a rule exceeds the rule's threshold or contains a DDoS attack
fingerprint, then you will receive an alert.
lastUpdated: 2025-11-19T16:38:52.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/rules/
md: https://developers.cloudflare.com/magic-network-monitoring/rules/index.md
---
Magic Network Monitoring rules allow you to monitor your network traffic for Distributed Denial of Service (DDoS) attacks on specific IP addresses or IP prefixes within your network. If the network traffic that is monitored by a rule exceeds the rule's threshold or contains a DDoS attack fingerprint, then you will receive an alert.
## Rule types
There are three different types of rules that can be configured within Magic Network Monitoring. You can refer to the linked documentation page for each rule type to learn more.
| Rule Type | Rule Description | Rule Availability |
| - | - | - |
| [Dynamic threshold](https://developers.cloudflare.com/magic-network-monitoring/rules/dynamic-threshold/) (recommended) | A dynamic threshold rule will analyze a network's traffic patterns over time and automatically adjust the rule's DDoS threshold, in terms of bits or packets, based on traffic history. | API configuration only |
| [Static threshold](https://developers.cloudflare.com/magic-network-monitoring/rules/static-threshold/) | A static threshold rule allows you to define a constant numeric threshold, in terms of bits or packets, for DDoS traffic monitoring. | API configuration and dashboard configuration |
| [sFlow DDoS attack](https://developers.cloudflare.com/magic-network-monitoring/rules/s-flow-ddos-attack/) | Magic Network Monitoring customers that send sFlow data to Cloudflare can receive alerts when a specific type of DDoS attack is detected within their network traffic. | API configuration only. Only applicable to sFlow data sets |
## Create rules in the dashboard
You can only configure static traffic threshold rules in the Cloudflare dashboard.
Invalid account settings error when trying to create a rule
If you get the following error when trying to create a rule:
`Invalid account settings request body: account name format contains illegal characters or is not supported`
Make sure the name for your Cloudflare account does not contain unsupported characters, like, for example, `&`, `<`, `>`, `"`, `'`, `` ` ``.
Refer to [Account name](https://developers.cloudflare.com/fundamentals/account/create-account/#account-name) to learn how to change your account name.
To create a new rule:
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Select **Configure Network flow**.
2. In the **Configure rules** tab, select **Add new rule**.
3. Create a new static traffic threshold rule according to your needs. Refer to the documentation on [static threshold](https://developers.cloudflare.com/magic-network-monitoring/rules/static-threshold/) rules for more information on each field in the static threshold rule's configuration.
4. Select **Create a new rule** when you are finished.
## Edit rules in the dashboard
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Select **Configure Network flow**.
2. In the **Configure rules** tab, find the static threshold rule you want to edit, and select **Edit**.
3. Edit the appropriate fields. Refer to [Rule configuration fields](https://developers.cloudflare.com/magic-network-monitoring/rules/static-threshold/#rule-configuration-fields) for more information on what each field does.
4. Select **Save** when you are finished.
## Delete rules in the dashboard
1. Go to the **Network flow** page.
[Go to **Network flow**](https://dash.cloudflare.com/?to=/:account/networking-insights/analytics/network-analytics/flow-analytics)
1. Select **Configure Network flow**.
2. In the **Configure rules** tab, find the static threshold rule you want to delete, and select **Delete**.
3. Select **I understand that deleting a rule is permanent**, and select **Delete** again.
## Common settings that apply to all rule types
### Rule Auto-Advertisement
If you are an Enterprise customer using [Magic Transit On Demand](https://developers.cloudflare.com/magic-transit/on-demand), you can enable **Auto-Advertisement** for any dynamic threshold, static threshold, and sFlow DDoS attack rule. The Auto-Advertisement feature will automatically activate Magic Transit when a static or dynamic rule threshold is exceeded or a DDoS attack fingerprint is identified in sFlow traffic logs.
Follow the previous steps to [create](#create-rules-in-the-dashboard) or [edit](#edit-rules-in-the-dashboard) a rule. Then, enable **Auto-Advertisement**.
#### Rule Auto-Advertisement notifications
Webhook, PagerDuty, and email notifications are sent following an auto-advertisement attempt for all prefixes inside the flagged rule.
You will receive the status of the advertisement for each prefix with the following available statuses:
* **Advertised**: The prefix was successfully advertised.
* **Already Advertised**: The prefix was advertised prior to the auto advertisement attempt.
* **Delayed**: The prefix cannot currently be advertised but will attempt advertisement. After the prefix can be advertised, a new notification is sent with the updated status.
* **Locked**: The prefix is locked and cannot be advertised.
* **Could not Advertise**: Cloudflare was unable to advertise the prefix. This status can occur for multiple reasons, but usually occurs when you are not allowed to advertise a prefix.
* **Error**: A general error occurred during prefix advertisement.
### Rule IP prefixes
Each rule must include a group of IP prefixes in its definition. All IP prefixes inside a rule are evaluated as a whole, and you should set up a rule with multiple IP prefixes when you want the IP prefixes' aggregated traffic to trigger an alert or advertisement. For thresholds on singular IP prefixes or IP addresses, you can create an individual rule with one prefix and the desired rule parameters.
#### Rule IP prefixes example
For a rule with two prefix Classless Inter-Domain Routing (CIDR) blocks and a `packet_threshold` of `10000` as shown below, the rule will be flagged if the joint packet traffic of `192.168.0.0/24` and `172.118.0.0/24` is greater than `10000`. This also means that Cloudflare attempts to auto advertise both CIDR blocks if the rule has the auto advertisement flag enabled. Customers can also [configure Rule IP prefixes at scale using Cloudflare's API](https://developers.cloudflare.com/api/resources/magic_network_monitoring/subresources/rules/).
```json
{
"rules": [
{
"name": "Too many packets",
"prefixes": ["192.168.0.0/24", "172.118.0.0/24"],
"packet_threshold": 10000,
"automatic_advertisement": true,
"duration": "1m0s",
"type": "threshold"
}
]
}
```
For more granular thresholds, create a more focused rule as shown below.
```json
{
"rules": [
{
"name": "Too many packets",
"prefixes": ["172.118.0.0/24"],
"packet_threshold": 1000,
"automatic_advertisement": true,
"duration": "1m0s",
"type": "threshold"
}
]
}
```
---
title: Tutorials · Cloudflare Magic Network Monitoring docs
lastUpdated: 2025-04-09T10:15:00.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-network-monitoring/tutorials/
md: https://developers.cloudflare.com/magic-network-monitoring/tutorials/index.md
---
* [Encrypt network flow data](https://developers.cloudflare.com/magic-network-monitoring/tutorials/encrypt-network-flow-data/)
* [GraphQL Analytics](https://developers.cloudflare.com/magic-network-monitoring/tutorials/graphql-analytics/)
* [DDoS testing guide](https://developers.cloudflare.com/magic-network-monitoring/tutorials/ddos-testing-guide/)
---
title: 404 - Page Not Found · Cloudflare Magic Transit docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/404/
md: https://developers.cloudflare.com/magic-transit/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About Magic Transit · Cloudflare Magic Transit docs
description: Magic Transit is a network security and performance solution that
offers Distributed Denial of Service (DDoS) protection, traffic acceleration,
and more for on-premise, cloud-hosted, and hybrid networks.
lastUpdated: 2025-12-19T09:32:41.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/about/
md: https://developers.cloudflare.com/magic-transit/about/index.md
---
Magic Transit is a network security and performance solution that offers Distributed Denial of Service (DDoS) protection, traffic acceleration, and more for on-premise, cloud-hosted, and hybrid networks.
Magic Transit delivers its connectivity, security, and performance benefits by serving as the front door to your IP network. This means it accepts IP packets destined for your network, processes them, and then outputs them to your origin infrastructure.
The Cloudflare network uses [Border Gateway Protocol (BGP)](https://www.cloudflare.com/learning/security/glossary/what-is-bgp/) to announce your company's IP address space, extending your network presence globally, and [anycast](https://www.cloudflare.com/learning/cdn/glossary/anycast-network/) to ingest your traffic. Today, Cloudflare's anycast global network spans [hundreds of cities worldwide](https://www.cloudflare.com/network/).
Once [packets](https://www.cloudflare.com/learning/network-layer/what-is-a-packet/) hit Cloudflare's network, Cloudflare inspects traffic for attacks, filters, steers, accelerates, and sends it to your origin. Magic Transit connects to your origin infrastructure using anycast Generic Routing Encapsulation (GRE) tunnels over the Internet or, with [Cloudflare Network Interconnect (CNI)](https://developers.cloudflare.com/network-interconnect/), through physical or virtual interconnect.
You have two options for your Magic Transit implementation: ingress traffic or ingress and [egress traffic](https://developers.cloudflare.com/magic-transit/reference/egress/). With an egress implementation, you must set up policy-based routing (PBR) or ensure default routing on your end forwards traffic to Cloudflare through tunnels.
```mermaid
flowchart LR
accTitle: Magic Transit
accDescr: Diagram showing how Magic Transit protects traffic on the customer's network.
A(DDoS
attack)
B[("Cloudflare global
anycast network
(DDoS protection +
network firewall)")]
C[Customer
network]
D((User))
E([BGP
announcement])
A --x B
E --- B
B-- Anycast
GRE tunnel ---C
B-- Cloudflare
Network
Interconnect ---C
C-- Egress through
Direct Server
Return --> D
D -- Ingress --> B
style A stroke: red,fill: red,color: white
style B stroke: orange,fill: orange,color: black
style C stroke: #ADD8E6,fill: #ADD8E6,color: black
style D stroke: blue,fill: blue,color: white
linkStyle 0 stroke-width:3px,stroke:red
linkStyle 1 stroke-width:2px,stroke:orange
linkStyle 2 stroke-width:2px,stroke:#ADD8E6
linkStyle 3 stroke-width:2px,stroke:gray
linkStyle 4 stroke-width:3px,stroke:green
```
Note
Cloudflare's China Network does not yet support Magic Transit.
For detailed information on Magic Transit architecture, refer to the [Reference section](https://developers.cloudflare.com/magic-transit/reference/).
---
title: Alerts · Cloudflare Magic Transit docs
description: You can configure alerts to receive notifications for changes in your network.
lastUpdated: 2025-09-25T14:23:12.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/alerts/
md: https://developers.cloudflare.com/magic-transit/alerts/index.md
---
You can configure alerts to receive notifications for changes in your network.
Magic Network Monitoring - Auto Advertisement
**Who is it for?**
[Magic Transit on-demand](https://developers.cloudflare.com/magic-transit/on-demand/) customers who use Flow-Based Monitoring and want alerts when Magic Transit is automatically enabled.
**Other options / filters**
None.
**Included with**
Purchase of Magic Transit.
**What should you do if you receive one?**
No action is needed. You can go to the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/magic-transit) to review the health and status of your tunnels.
Magic Network Monitoring - DDoS Attack
**Who is it for?**
[BYOIP](https://developers.cloudflare.com/byoip/) and [Spectrum](https://developers.cloudflare.com/spectrum/) customers with [Network Analytics](https://developers.cloudflare.com/analytics/network-analytics/) who want to receive a notification when Cloudflare has mitigated attacks that generate an average of at least 12,000 packets per second over a five-second period, with a duration of one minute or more.
**Other options / filters**
None.
**Included with**
Purchase of Magic Transit and/or BYOIP.
**What should you do if you receive one?**
No action needed. Refer to [DDoS alerts](https://developers.cloudflare.com/ddos-protection/reference/alerts/) for more information.
Magic Network Monitoring - Volumetric Attack
**Who is it for?**
[Magic Transit on-demand](https://developers.cloudflare.com/magic-transit/on-demand/) customers who are using Flow-Based Monitoring to detect attacks when Magic Transit is disabled.
**Other options / filters**
None.
**Included with**
Purchase of Magic Transit.
**What should you do if you receive one?**
If you do not have auto advertisement enabled, you need to advertise your IP prefixes to enable Magic Transit. For more information, refer to [Dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/).
Magic Tunnel Health Check Alert
**Who is it for?**
Magic Transit and Magic WAN customers who wish to receive alerts when the percentage of tunnel states meeting the selected service-level objective (SLO) drops below the defined threshold for a Magic Tunnel.
**Other options / filters**
* Notification Name: A custom name for the notification.
* Description (optional): A custom description for the notification.
* Notification Email (can be multiple emails): The email address of recipient for the notification.
* Webhooks
* Tunnels: Choose one or more tunnels to monitor.
* SLO: Define SLO threshold for Magic Tunnel health alerts. Available options are *High*, *Medium*, and *Low*.
**Included with**
Purchase of Magic Transit and Magic WAN.
**What should you do if you receive one?**
Refer to the [Magic Transit tunnel health](https://developers.cloudflare.com/magic-transit/network-health/check-tunnel-health-dashboard/) or [Magic WAN tunnel health](https://developers.cloudflare.com/magic-wan/configuration/common-settings/check-tunnel-health-dashboard/) for more information on what the issue might be.
Refer to [Cloudflare Notifications](https://developers.cloudflare.com/notifications/get-started/) for more information on how to set up an alert.
---
title: Analytics · Cloudflare Magic Transit docs
description: Use Magic Transit analytics to monitor network performance and
troubleshoot potential issues.
lastUpdated: 2026-01-20T11:00:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/analytics/
md: https://developers.cloudflare.com/magic-transit/analytics/index.md
---
Use these options to gather information at the start of your troubleshooting workflow. Then, use more detailed network data collection and analysis to identify the root cause.
* Analyze network traffic over time in [Network Analytics](#network-analytics)
* Perform more detailed troubleshooting with:
* [Traceroutes](#traceroutes)
* [Packet captures](#packet-captures)
## Network Analytics
Network Analytics provides detailed analytics on your Magic Transit traffic over time. You can filter data by traffic characteristics and review traffic trends over time.
For details, refer to [Magic Transit Network Analytics](https://developers.cloudflare.com/magic-transit/analytics/network-analytics/).
## Traceroutes
Traceroutes provide a hop-by-hop breakdown of the Internet path network traffic follows from Cloudflare's network to your network.
For details, refer to [Traceroutes](https://developers.cloudflare.com/magic-transit/analytics/traceroutes/).
## Packet captures
Packet captures allow you to analyze the raw packet data your network sends to and receives from Cloudflare's network.
For details, refer to [packet captures](https://developers.cloudflare.com/magic-firewall/packet-captures/).
## Query analytics with GraphQL
GraphQL Analytics provides a GraphQL API to query raw JSON data for your Magic Transit traffic analytics. You can ingest this data into a Security Information and Event Management (SIEM) tool or another platform for further analysis.
* [Querying Magic Transit tunnel bandwidth analytics with GraphQL](https://developers.cloudflare.com/magic-transit/analytics/query-bandwidth/)
* [Querying Magic Transit tunnel health check results with GraphQL](https://developers.cloudflare.com/magic-transit/analytics/query-tunnel-health/)
---
title: Changelog · Cloudflare Magic Transit docs
description: Review recent changes to Magic Transit.
lastUpdated: 2025-12-11T09:33:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/changelog/
md: https://developers.cloudflare.com/magic-transit/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-transit.xml)
## 2026-01-30
**BGP over GRE and IPsec tunnels**
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using IPsec and GRE tunnel on-ramps (beta).
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via IPsec and GRE tunnel on-ramps.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
For configuration details, refer to:
* [Configure BGP routes for Magic WAN](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes)
* [Configure BGP routes for Magic Transit](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes)
## 2026-01-15
**Network Services navigation update**
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

## 2025-07-30
**Magic Transit and Magic WAN health check data is fully compatible with the CMB EU setting.**
Today, we are excited to announce that all Magic Transit and Magic WAN customers with CMB EU ([Customer Metadata Boundary - Europe](https://developers.cloudflare.com/data-localization/metadata-boundary/)) enabled in their account will be able to access GRE, IPsec, and CNI health check and traffic volume data in the Cloudflare dashboard and via API.
This ensures that all Magic Transit and Magic WAN customers with CMB EU enabled will be able to access all Magic Transit and Magic WAN features.
Specifically, these two GraphQL endpoints are now compatible with CMB EU:
* `magicTransitTunnelHealthChecksAdaptiveGroups`
* `magicTransitTunnelTrafficAdaptiveGroups`
## 2024-12-17
**Establish BGP peering over Direct CNI circuits**
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
Refer to [Magic WAN BGP peering](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes) or [Magic Transit BGP peering](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes) to learn more about this feature and how to set it up.
## 2024-10-01
**Early access testing for BGP on CNI 2.0 circuits**
Customers can exchange routes dynamically with their Magic virtual network overlay through Direct CNI or Cloud CNI based connectivity.
---
title: Cloudflare IPs · Cloudflare Magic Transit docs
description: To use Magic Transit, you need to own a publicly routable IP
address block with a minimum size of /24. If you do not own a /24 address
block, you can use Magic Transit with a Cloudflare-owned IP address. This
option is helpful if you do not meet the /24 prefix length requirements or
want to protect a smaller network.
lastUpdated: 2025-10-01T13:13:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/cloudflare-ips/
md: https://developers.cloudflare.com/magic-transit/cloudflare-ips/index.md
---
To use Magic Transit, you need to own a publicly routable IP address block with a minimum size of `/24`. If you do not own a `/24` address block, you can use Magic Transit with a Cloudflare-owned IP address. This option is helpful if you do not meet the `/24` prefix length requirements or want to protect a smaller network.
To protect your network with a Cloudflare IP address, contact your account manager. After you receive your IP address:
* [Create a tunnel](https://developers.cloudflare.com/magic-transit/how-to/configure-tunnel-endpoints/).
* [Set up static routes](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-static-routes) or [BGP peering (beta)](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes).
* [Configure health checks](https://developers.cloudflare.com/magic-transit/network-health/run-endpoint-health-checks/).
* Confirm you properly configured [tunnel](https://developers.cloudflare.com/magic-transit/network-health/update-tunnel-health-checks-frequency/) and endpoint health checks.
* Update your infrastructure at your own pace to use the allocated Cloudflare IPs.
When you use a Cloudflare-owned IP space, you do not need a Letter of Agency (LOA). When using Cloudflare-leased IPs, Cloudflare automatically enables [Magic Transit Egress](https://developers.cloudflare.com/magic-transit/reference/egress/), which routes your egress traffic to Cloudflare instead of the Internet. Set up policy-based routing on your end to ensure return traffic routes properly.
## Check your Cloudflare IPs
You can find your leased Anycast IPs for Magic Transit on the dashboard under [**Address space** > **Leased IPs**](https://dash.cloudflare.com/?to=/:account/ip-addresses/address-space).
---
title: Cloudflare DDoS protection · Cloudflare Magic Transit docs
description: "Cloudflare DDoS protection automatically detects and mitigates
Distributed Denial of Service (DDoS) attacks using its Autonomous Edge. With
Magic Transit, you have access to additional Advanced DDoS mitigation systems,
such as:"
lastUpdated: 2026-01-05T09:41:43.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/ddos/
md: https://developers.cloudflare.com/magic-transit/ddos/index.md
---
Cloudflare DDoS protection automatically detects and mitigates Distributed Denial of Service (DDoS) attacks using its [Autonomous Edge](https://developers.cloudflare.com/ddos-protection/about/components/#autonomous-edge). With Magic Transit, you have access to additional [Advanced DDoS mitigation systems](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/), such as:
* [Advanced TCP protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-tcp-protection/)
* [Advanced DNS protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-dns-protection/)
Refer to [Cloudflare DDoS documentation](https://developers.cloudflare.com/ddos-protection/) for more information.
***
## Execution order
Magic Transit executes mitigation systems in the following order:
1. [DDoS managed rulesets](https://developers.cloudflare.com/ddos-protection/managed-rulesets/)
2. [Advanced TCP Protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-tcp-protection/)
3. [Advanced DNS Protection](https://developers.cloudflare.com/ddos-protection/advanced-ddos-systems/overview/advanced-dns-protection/)
4. [Magic Firewall](https://developers.cloudflare.com/magic-firewall/)
---
title: Get started · Cloudflare Magic Transit docs
description: Before you can begin using Magic Transit, complete the following
onboarding steps. Cloudflare can significantly accelerate this timeline during
active-attack scenarios.
lastUpdated: 2025-05-09T16:24:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/get-started/
md: https://developers.cloudflare.com/magic-transit/get-started/index.md
---
Before you can begin using Magic Transit, complete the following onboarding steps. Cloudflare can significantly accelerate this timeline during active-attack scenarios.
## Scope your configuration
Magic Transit is not a self-serve product. Start by [engaging with our team](https://www.cloudflare.com/network-services/products/magic-transit/) to assess your needs and implementation timeline. During this assessment, Cloudflare reviews specific requirements such as your prefix count and how fast you can go through the necessary steps to implement Magic Transit on your network.
## IPs
To use Magic Transit, you need to own a publicly routable IP address block with a minimum size of `/24`. If you do not own a `/24` address block, you can use Magic Transit with a Cloudflare-owned IP address. This option is helpful if you do not meet the `/24` prefix length requirements or want to protect a smaller network.
To protect your network with a Cloudflare IP address, contact your account manager. After you receive your IP address:
* [Create a tunnel](https://developers.cloudflare.com/magic-transit/how-to/configure-tunnel-endpoints/).
* [Set up static routes](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-static-routes) or [BGP peering (beta)](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes).
* [Configure health checks](https://developers.cloudflare.com/magic-transit/network-health/run-endpoint-health-checks/).
* Confirm you properly configured [tunnel](https://developers.cloudflare.com/magic-transit/network-health/update-tunnel-health-checks-frequency/) and endpoint health checks.
* Update your infrastructure at your own pace to use the allocated Cloudflare IPs.
When you use a Cloudflare-owned IP space, you do not need a Letter of Agency (LOA). When using Cloudflare-leased IPs, Cloudflare automatically enables [Magic Transit Egress](https://developers.cloudflare.com/magic-transit/reference/egress/), which routes your egress traffic to Cloudflare instead of the Internet. Set up policy-based routing on your end to ensure return traffic routes properly.
## Verify router compatibility
Magic Transit relies on anycast tunnels to transmit packets from Cloudflare's global network to your origin network.
The routers at your tunnel endpoints must meet the following requirements for Magic Transit compatibility.
* Support GRE tunnels (or IPsec if GRE is not available).
* Support at least one tunnel per Internet service provider (ISP).
* Support maximum segment size (MSS) clamping.
* Support asymmetric traffic flow (for ingress-only Magic Transit).
## Draft Letter of Agency
Draft a [Letter of Agency (LOA)](https://developers.cloudflare.com/byoip/concepts/loa/) that identifies the prefixes you want to advertise and authorizes Cloudflare to announce them. Our transit providers require the LOA so they can accept the routes we advertise on your behalf.
If you are an Internet service provider (ISP) and advertising prefixes on behalf of a customer, you need an LOA for the ISP and for the customer.
If you are using a [Cloudflare IP address](#ips), you do not need to submit an LOA.
Note
The LOA must be a PDF. Transit providers may reject the LOA if it is a JPG or PNG.
### Example of a Letter of Agency
```txt
[COMPANY LETTERHEAD]
LETTER OF AGENCY ("LOA")
[DATE]
To whom it may concern:
[COMPANY NAME] (the "Company") authorizes Cloudflare, Inc. with AS13335 to advertise the following IP address blocks / originating ASNs:
- - - - - - - - - - - - - - - - - - -
[Subnet & Originating ASN]
[Subnet & Originating ASN]
[Subnet & Originating ASN]
- - - - - - - - - - - - - - - - - - -
As a representative of the Company that is the owner of the aforementioned IP address blocks / originating ASNs, I hereby declare that I am authorized to sign this LOA on the Company’s behalf.
Should you have any questions please email me at [E-MAIL ADDRESS], or call: [TELEPHONE NUMBER]
Regards,
[SIGNATURE]
[NAME TYPED]
[TITLE]
[COMPANY NAME]
[COMPANY ADDRESS]
[COMPANY STAMP]
```
## Verify IRR entries
Verify that your Internet Routing Registry (IRR) entries match your corresponding origin autonomous system numbers (ASNs) to ensure Magic Transit routes traffic to the correct autonomous systems (AS). For guidance, refer to [Verify IRR entries](https://developers.cloudflare.com/byoip/concepts/irr-entries/best-practices/#verify-an-irr-entry).
If you are using a [Cloudflare IP](#ips), you do not need to verify your IRR entries.
### Optional: RPKI check for prefix validation
You can also use the Resource Public Key Infrastructure (RPKI) as an additional option to validate your prefixes. RPKI is a [security framework method](https://blog.cloudflare.com/rpki/) that associates a route with an autonomous system. It uses cryptography to validate the information before being passed to the routers.
If you operate a network (ISP, cloud provider, enterprise, and others), using RPKI ensures that routers correctly recognize your IP prefixes. This prevents service disruptions and protects your brand's reputation. Without RPKI, attackers could announce your IP space, misdirect your traffic, and potentially harm your business.
To check your prefixes, you can use [Cloudflare's RPKI Portal](https://rpki.cloudflare.com/?view=validator).
## Set maximum segment size
Before enabling Magic Transit, you must make sure that you set up the maximum segment size on your network. Cloudflare Magic Transit uses tunnels to deliver [packets](https://www.cloudflare.com/learning/network-layer/what-is-a-packet/) from our global network to your data centers. Cloudflare encapsulates these packets adding new headers. You must account for the space consumed by these headers when configuring the maximum transmission unit (MTU) and maximum segment size (MSS) values for your network.
### MSS clamping recommendations
#### GRE tunnels as off-ramp
The MSS value depends on how your network is set up.
* **Magic Transit ingress-only traffic (DSR):**
* **On your edge router transit ports**: Set a TCP MSS clamp to a maximum of 1,436 bytes.
* **On any IPsec/GRE tunnels with third parties on your Magic Transit prefix**: Apply the MSS clamp on the internal tunnel interface (most likely on a separate firewall behind the GRE-terminating router) to reduce the current value by 24 bytes.
* **For Magic Transit ingress + egress traffic:**
* **On the Magic Transit GRE tunnel internal interface**: Meaning where the Magic Transit egress traffic will traverse. Your devices may do this automatically once the tunnel is configured, but it depends on your devices. Set the TCP MSS clamp to 1,436 bytes maximum.
* **On any IPsec/GRE tunnels with third parties on your Magic Transit prefix**: On the internal tunnel interface (most likely on a separate firewall behind the GRE-terminating router) to reduce its current value by 24 bytes.
#### IPsec tunnels
For IPsec tunnels, the value you need to specify depends on how your network is set up. The MSS clamping value is lower than for GRE tunnels because the physical interface sees IPsec-encrypted [packets](https://www.cloudflare.com/learning/network-layer/what-is-a-packet/), not TCP packets, and MSS clamping does not apply to those.
* **Magic Transit ingress-only traffic (DSR):**
* **On your edge router transit ports**: Set the TCP MSS clamp to 1,436 bytes maximum.
* **On any IPsec/GRE tunnels with third parties on your Magic Transit prefix**: On the internal tunnel interface (most likely on a separate firewall behind the GRE-terminating router) to reduce its current value by 140 bytes.
* **Magic Transit ingress + egress traffic:**
* **On your edge router**: Apply this on your Magic Transit IPsec tunnel internal interface (that is, where the Magic Transit egress traffic will traverse). Your devices may do this automatically once the tunnel is configured, but it depends on your devices. Set the TCP MSS clamp to 1,360 bytes maximum.
* **On any IPsec/GRE tunnels with third parties on your Magic Transit prefix**: On the internal tunnel interface (most likely on a separate firewall behind the IPsec-terminating device in your premises) to reduce its current value by 140 bytes.
Important
Refer to your device documentation to check if it sets IPsec MSS clamping automatically. If not and you are using IPsec inside GRE, you must set MSS clamp manually.
Refer to [Maximum transmission unit and maximum segment size](https://developers.cloudflare.com/magic-transit/reference/mtu-mss/) for more details.
#### Clear Do not fragment (DF)
If you are unable to set the MSS on your physical interfaces to a value lower than 1500 bytes, you can clear the `do not fragment` bit in the IP header. When this option is enabled, Cloudflare fragments [packets](https://www.cloudflare.com/learning/network-layer/what-is-a-packet/) greater than 1500 bytes, and the packets are reassembled on your infrastructure after decapsulation. In most environments, enabling this option does not have a significant impact on traffic throughput.
To enable this option for your network, contact your account team.
Refer to [Maximum transmission unit and maximum segment size](https://developers.cloudflare.com/magic-transit/reference/mtu-mss/) for more details.
## Follow router vendor guidelines
Instructions to adjust MSS by applying MSS clamps vary depending on the vendor of your router.
The following table lists several commonly used router vendors with links to MSS clamping instructions:
| Router device | URL |
| - | - |
| Cisco | [TCP IP Adjust MSS](https://www.cisco.com/en/US/docs/ios-xml/ios/ipapp/command/ip_tcp_adjust-mss_through_ip_wccp_web-cache_accelerated.html#GUID-68044D35-A53E-42C1-A7AB-9236333DA8C4) |
| Juniper | [TCP MSS - Edit System](https://www.juniper.net/documentation/en_US/junos/topics/reference/configuration-statement/tcp-mss-edit-system.html) |
## Configure tunnels
[Configure the tunnels](https://developers.cloudflare.com/magic-transit/how-to/configure-tunnel-endpoints/) on both the Cloudflare side and your router side to connect to your origin infrastructure.
## Configure static routes or BGP peering (beta)
Configure [static routes](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-static-routes) or [BGP peering](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes) to route traffic from Cloudflare's global network to your locations.
## Run pre-flight checks
After setting up your tunnels and routes, Cloudflare validates:
* Tunnel connectivity
* Tunnel and endpoint [health checks](https://developers.cloudflare.com/magic-transit/reference/tunnel-health-checks/#tunnel-health-checks)
* Letter of Agency (LOA)
* Internet Routing Registry (IRR)
* Maximum segment size (MSS) configurations
Cloudflare applies configurations to the global network, which takes around one day to roll out.
## Advertise prefixes
Once pre-flight checks are completed, Cloudflare unlocks your prefixes for you to [advertise via the dashboard, API or BGP](https://developers.cloudflare.com/magic-transit/how-to/advertise-prefixes/) at a time of your choosing. Refer to [Dynamic advertisement best practices](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/) to learn more about advertising prefixes.
If you are using a Cloudflare IP, you do not need to advertise your prefixes.
Warning
You must [put the appropriate MSS clamps](#set-maximum-segment-size) in place before [routing](https://www.cloudflare.com/learning/network-layer/what-is-routing/) changes are made. Failure to apply an MSS clamp can result in dropped packets and hard-to-debug connectivity issues.
Also, when using [Cloudflare Network Interconnect](https://developers.cloudflare.com/magic-transit/network-interconnect/) with Magic Transit you must set the following MSS clamp sizes to accommodate additional overhead:
* GRE tunnels over CNI with Dataplane v1: 1476 bytes
* CNI with Dataplane v2 / CNI with Dataplane v1 with a maximum transmission unit (MTU) size of 1500 bytes handoff does not require an MSS clamp.
MSS clamps are used to backhaul data from the data center where traffic is ingested (close to the end user) to the facility with the CNI link.
---
title: Glossary · Cloudflare Magic Transit docs
description: Review the definitions for terms used across Cloudflare's Magic
Transit documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/glossary/
md: https://developers.cloudflare.com/magic-transit/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Magic Transit documentation.
| Term | Definition |
| - | - |
| letter of agency | Sometimes referred to as a Letter of Authorization. A document that authorizes Cloudflare to advertise your prefixes. This is required so transit providers can accept the routes Cloudflare advertises on your behalf. |
| policy-based routing | Policy-based routing (PBR) is a technique used to make routing decisions based on policies set by your administrador. |
| prefix | A number that identifies the network portion of an IP address. It tells devices if an IP address is on the same network or not. It is shown as a number after a slash (for example, `/31`) at the end of the IP address.Using an analogy, the prefix is like a street address. If an IP is in the same street, it belongs to the same network of devices. |
---
title: How to · Cloudflare Magic Transit docs
lastUpdated: 2024-08-30T16:09:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-transit/how-to/
md: https://developers.cloudflare.com/magic-transit/how-to/index.md
---
* [Configure tunnel endpoints](https://developers.cloudflare.com/magic-transit/how-to/configure-tunnel-endpoints/)
* [Configure routes](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/)
* [Configure IPv6 (beta)](https://developers.cloudflare.com/magic-transit/how-to/ipv6/)
* [Advertise prefixes](https://developers.cloudflare.com/magic-transit/how-to/advertise-prefixes/)
* [Enable Magic user roles](https://developers.cloudflare.com/magic-transit/how-to/enable-magic-roles/)
* [Safely withdraw a BYOIP prefix](https://developers.cloudflare.com/magic-transit/how-to/safely-withdraw-byoip-prefix/)
---
title: Magic Network Monitoring · Cloudflare Magic Transit docs
description: With Magic Transit On Demand, you can use Magic Network Monitoring
to analyze your network traffic and detect Distributed Denial of Service
(DDoS) attacks while Magic Transit is disabled. If an attack is detected, you
can automatically or manually enable Magic Transit to mitigate attacks.
lastUpdated: 2025-10-16T11:21:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/magic-network-monitoring/
md: https://developers.cloudflare.com/magic-transit/magic-network-monitoring/index.md
---
With [Magic Transit On Demand](https://developers.cloudflare.com/magic-transit/on-demand/), you can use Magic Network Monitoring to analyze your network traffic and detect Distributed Denial of Service (DDoS) attacks while Magic Transit is disabled. If an attack is detected, you can automatically or manually enable Magic Transit to mitigate attacks.
You can create Magic Network Monitoring rules which monitor specific Internet Protocol (IP) prefixes for DDoS attacks. When a DDoS attack is detected, Cloudflare notifies you by email, [webhook](https://developers.cloudflare.com/notifications/get-started/configure-webhooks/), or [PagerDuty](https://developers.cloudflare.com/notifications/get-started/configure-pagerduty/) with information about the attack. Then, you can [automatically activate IP advertisement](#activate-ip-auto-advertisement) and enable Magic Transit to protect the targeted IP prefixes from DDoS attacks. This feature is referred to as auto-advertisement, and you can enable it for individual Magic Network Monitoring rules through the dashboard or API.
After Magic Transit is activated and your traffic is flowing through Cloudflare, Cloudflare blocks malicious DDoS traffic, and your origin servers receive only clean network traffic through IPsec or Generic Routing Encapsulation (GRE) tunnels.
The following diagrams illustrate this process:



## Activate IP auto-advertisement
Enable IP auto-advertisement to use Magic Network Monitoring rules. You can activate IP auto-advertisement through the dashboard or the API.
### Dashboard
To activate IP advertisement through the Cloudflare dashboard, refer to [Configure dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement).
### API
To activate IP advertisement through the API, refer to the [IP Address Management Dynamic Advertisement API](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/advertisement_status/methods/edit/).
## Magic Network Monitoring rules
To create Magic Network Monitoring rules with auto-advertisement, refer to [Rule Auto-Advertisement](https://developers.cloudflare.com/magic-network-monitoring/rules/#rule-auto-advertisement).
---
title: Network health · Cloudflare Magic Transit docs
description: Magic Transit uses health check probes to determine the status of
tunnels. Cloudflare uses this information to steer traffic through the best
available route and warn you about potential issues with a tunnel.
Service-level indicators (SLIs) and service-level objectives (SLOs) combine to
determine when Cloudflare sends you tunnel health alerts. Refer to How
Cloudflare calculates Magic Tunnel health alerts for more information about
SLIs and SLOs.
lastUpdated: 2025-12-19T09:32:41.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/network-health/
md: https://developers.cloudflare.com/magic-transit/network-health/index.md
---
Magic Transit uses health check probes to determine the status of tunnels. Cloudflare uses this information to steer traffic through the best available route and warn you about potential issues with a tunnel. Service-level indicators (SLIs) and service-level objectives (SLOs) combine to determine when Cloudflare sends you tunnel health alerts. Refer to [How Cloudflare calculates Magic Tunnel health alerts](https://developers.cloudflare.com/magic-transit/reference/how-cloudflare-calculates-magic-tunnel-health-alerts/) for more information about SLIs and SLOs.
There are two types of health checks available: endpoint and tunnel health checks.
* Endpoint health checks evaluate connectivity from Cloudflare distributed data centers to your origin network. Endpoint probes flow over available tunnels to provide a broad picture of Internet health and do not inform tunnel selection or steering logic.
Cloudflare global network servers issue endpoint health checks outside of customer network namespaces and typically target endpoints beyond the tunnel-terminating border router.
During onboarding, you specify IP addresses to configure endpoint health checks.
* Tunnel health checks monitor the status of the tunnels that route traffic from Cloudflare to your origin network. Magic Transit relies on health checks to steer traffic to the best available routes.
During onboarding, you specify the tunnel endpoints or tunnel health check targets that the tunnel probes from Cloudflare's global network will monitor.
You can access tunnel health check results through the API. Cloudflare aggregates these results from individual health check results on Cloudflare servers.
Refer to [Tunnel health checks](https://developers.cloudflare.com/magic-transit/reference/tunnel-health-checks/) for a deep dive into the different types of health checks, what they do, and how they work.
Note
Magic Transit customers with [Customer Metadata Boundary](https://developers.cloudflare.com/data-localization/metadata-boundary/) enabled for the European Union can access GRE, IPsec, and CNI (Cloudflare Network Interconnect) health check and traffic volume data in the Cloudflare dashboard and through the API. This ensures that customers who need to be General Data Protection Regulation (GDPR) compliant can access all Magic Transit features.
Refer to the following pages for details on how to use the various network health checks available.
* [Run endpoint health checks (beta)](https://developers.cloudflare.com/magic-transit/network-health/run-endpoint-health-checks/)
* [Check tunnel health in the dashboard](https://developers.cloudflare.com/magic-transit/network-health/check-tunnel-health-dashboard/)
* [Update tunnel health checks frequency](https://developers.cloudflare.com/magic-transit/network-health/update-tunnel-health-checks-frequency/)
* [Configure Magic Tunnel health alerts](https://developers.cloudflare.com/magic-transit/network-health/configure-magic-tunnel-health-alerts/)
* [How Cloudflare calculates Magic Tunnel health alerts](https://developers.cloudflare.com/magic-transit/reference/how-cloudflare-calculates-magic-tunnel-health-alerts/)
---
title: Network Interconnect and Magic Transit · Cloudflare Magic Transit docs
description: Cloudflare Network Interconnect (CNI) allows you to connect your
network infrastructure directly with Cloudflare — rather than using the public
Internet — for a more reliable and secure experience. With CNI, you can bring
Cloudflare's full suite of network functions to your physical network edge.
lastUpdated: 2025-09-25T14:23:12.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/network-interconnect/
md: https://developers.cloudflare.com/magic-transit/network-interconnect/index.md
---
Cloudflare Network Interconnect (CNI) allows you to connect your network infrastructure directly with Cloudflare — rather than using the public Internet — for a more reliable and secure experience. With CNI, you can bring Cloudflare's full suite of network functions to your physical network edge.
For more information about Network Interconnect, refer to the [Cloudflare Network Interconnect documentation](https://developers.cloudflare.com/network-interconnect/).
---
title: Magic Transit on-demand · Cloudflare Magic Transit docs
description: If you have access to the Magic Transit on-demand option, you can
configure prefix advertisement from the IP Prefixes page in your Cloudflare
account home or through the Cloudflare API.
lastUpdated: 2025-12-19T09:32:41.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-transit/on-demand/
md: https://developers.cloudflare.com/magic-transit/on-demand/index.md
---
If you have access to the Magic Transit on-demand option, you can [configure prefix advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/#configure-dynamic-advertisement) from the **IP Prefixes** page in your Cloudflare account home or through the [Cloudflare API](https://developers.cloudflare.com/api/resources/addressing/subresources/prefixes/subresources/advertisement_status/methods/edit/).
A common workflow is to enable prefix advertisement during an attack so that you can take advantage of Cloudflare protection and then disable advertisement once the incident is resolved. Dynamic advertisement (through the dashboard or API) does not support prefixes using BGP-controlled advertisements. Specify your preferred on-demand advertisement method during prefix onboarding.
To ensure smooth operation and simplify the advertisement process during an attack scenario, refer to [Dynamic advertisement: Best practices](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/best-practices/).
Note
You cannot use Magic Transit on-demand with Cloudflare leased IPs.
---
title: Partners · Cloudflare Magic Transit docs
lastUpdated: 2025-09-25T14:23:12.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-transit/partners/
md: https://developers.cloudflare.com/magic-transit/partners/index.md
---
* [Kentik](https://developers.cloudflare.com/magic-transit/partners/kentik/)
---
title: Reference · Cloudflare Magic Transit docs
lastUpdated: 2025-09-25T14:23:12.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-transit/reference/
md: https://developers.cloudflare.com/magic-transit/reference/index.md
---
* [Anti-replay protection](https://developers.cloudflare.com/magic-transit/reference/anti-replay-protection/)
* [Bandwidth measurement](https://developers.cloudflare.com/magic-transit/reference/bandwidth-measurement/)
* [Egress traffic](https://developers.cloudflare.com/magic-transit/reference/egress/)
* [GRE and IPsec tunnels](https://developers.cloudflare.com/magic-transit/reference/gre-ipsec-tunnels/)
* [Maximum transmission unit and maximum segment size](https://developers.cloudflare.com/magic-transit/reference/mtu-mss/)
* [Reference architecture](https://developers.cloudflare.com/reference-architecture/architectures/magic-transit/)
* [Traffic steering](https://developers.cloudflare.com/magic-transit/reference/traffic-steering/)
* [Tunnel health checks](https://developers.cloudflare.com/magic-transit/reference/tunnel-health-checks/)
* [How Cloudflare calculates Magic Tunnel health alerts](https://developers.cloudflare.com/magic-transit/reference/how-cloudflare-calculates-magic-tunnel-health-alerts/)
---
title: Troubleshooting · Cloudflare Magic Transit docs
lastUpdated: 2026-01-27T09:26:05.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-transit/troubleshooting/
md: https://developers.cloudflare.com/magic-transit/troubleshooting/index.md
---
* [Troubleshoot with IPsec logs](https://developers.cloudflare.com/magic-transit/troubleshooting/ipsec-troubleshoot/)
* [Troubleshoot tunnel health](https://developers.cloudflare.com/magic-transit/troubleshooting/tunnel-health/)
---
title: 404 - Page Not Found · Cloudflare Magic WAN docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/404/
md: https://developers.cloudflare.com/magic-wan/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Analytics · Cloudflare Magic WAN docs
description: Use Magic WAN analytics to monitor site performance and troubleshoot issues.
lastUpdated: 2026-01-20T17:03:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/analytics/
md: https://developers.cloudflare.com/magic-wan/analytics/index.md
---
Use these options to gather information at the start of your troubleshooting workflow. Then, use more detailed network data collection and analysis to identify the root cause.
* View your entire network at a glance in [Network overview (beta)](#network-overview-beta)
* Analyze network traffic over time in [Network Analytics](#network-analytics)
* Perform more detailed troubleshooting with:
* [Traceroutes](#traceroutes)
* [Packet captures](#packet-captures)
## Network overview (beta)
Network overview (beta) shows the connectivity status and traffic analytics for all Magic WAN sites. Use it when you receive an alert, start troubleshooting, or perform routine monitoring.
For details, refer to [Network overview (beta)](https://developers.cloudflare.com/magic-wan/analytics/site-analytics/).
## Network Analytics
Network Analytics provides detailed analytics on your Magic WAN traffic over time. You can filter data by traffic characteristics and review traffic trends over time.
For details, refer to [Magic WAN Network Analytics](https://developers.cloudflare.com/magic-wan/analytics/network-analytics/).
## Traceroutes
Traceroutes provide a hop-by-hop breakdown of the Internet path network traffic follows from Cloudflare's network to your network.
For details, refer to [Traceroutes](https://developers.cloudflare.com/magic-wan/analytics/traceroutes/).
## Packet captures
Packet captures allow you to analyze the raw packet data your network sends to and receives from Cloudflare's network.
For details, refer to [packet captures](https://developers.cloudflare.com/magic-firewall/packet-captures/).
## Query analytics with GraphQL
GraphQL Analytics provides a GraphQL API to query raw JSON data for your Magic WAN traffic analytics. You can ingest this data into a Security Information and Event Management (SIEM) tool or another platform for further analysis.
* [Querying Magic WAN tunnel bandwidth analytics with GraphQL](https://developers.cloudflare.com/magic-wan/analytics/query-bandwidth/)
* [Querying Magic WAN tunnel health check results with GraphQL](https://developers.cloudflare.com/magic-wan/analytics/query-tunnel-health/)
---
title: Changelog · Cloudflare Magic WAN docs
description: Review recent changes to Magic WAN.
lastUpdated: 2026-01-20T17:03:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/changelog/
md: https://developers.cloudflare.com/magic-wan/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/magic-wan.xml)
## 2026-01-30
**BGP over GRE and IPsec tunnels**
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using IPsec and GRE tunnel on-ramps (beta).
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via IPsec and GRE tunnel on-ramps.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
For configuration details, refer to:
* [Configure BGP routes for Magic WAN](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes)
* [Configure BGP routes for Magic Transit](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes)
## 2026-01-27
**Configure Cloudflare source IPs (beta)**
Cloudflare source IPs are the IP addresses used by Cloudflare services (such as Load Balancing, Gateway, and Browser Isolation) when sending traffic to your private networks.
For customers using legacy mode routing, traffic to private networks is sourced from public Cloudflare IPs, which may cause IP conflicts. For customers using Unified Routing mode (beta), traffic to private networks is sourced from dedicated, non-Internet-routable private IPv4 range to ensure:
* Symmetric routing over private network connections
* Proper firewall state preservation
* Private traffic stays on secure paths
Key details:
* **IPv4**: Sourced from `100.64.0.0/12` by default, configurable to any `/12` CIDR
* **IPv6**: Sourced from `2606:4700:cf1:5000::/64` (not configurable)
* **Affected connectors**: GRE, IPsec, CNI, WARP Connector, and WARP Client (Cloudflare Tunnel is not affected)
Configuring Cloudflare source IPs requires Unified Routing (beta) and the `Cloudflare One Networks Write` permission.
For configuration details, refer to [Configure Cloudflare source IPs](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-cloudflare-source-ips/).
## 2026-01-15
**Network Services navigation update**
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to [Magic Transit](https://developers.cloudflare.com/magic-transit/), [Magic WAN](https://developers.cloudflare.com/magic-wan/), and [Magic Firewall](https://developers.cloudflare.com/magic-firewall/).
**Summary of changes:**
* A new **Overview** page provides access to the most common tasks across Magic Transit and Magic WAN.
* Product names have been removed from top-level navigation.
* Magic Transit and Magic WAN configuration is now organized under **Routes** and **Connectors**. For example, you will find IP Prefixes under **Routes**, and your GRE/IPsec Tunnels under **Connectors.**
* Magic Firewall policies are now called **Firewall Policies.**
* Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as **Appliances** and **Appliance profiles.** They can be found under **Connectors > Appliances.**
* Network analytics, network health, and real-time analytics are now available under **Insights.**
* Packet Captures are found under **Insights > Diagnostics.**
* You can manage your Sites from **Insights > Network health.**
* You can find Magic Network Monitoring under **Insights > Network flow**.
If you would like to provide feedback, complete [this form](https://forms.gle/htWyjRsTjw1usdis5). You can also find these details in the January 7, 2026 email titled **\[FYI] Upcoming Network Services Dashboard Navigation Update**.

## 2025-12-31
**Breakout traffic visibility via NetFlow**
Magic WAN Connector now exports NetFlow data for breakout traffic to Magic Network Monitoring (MNM), providing visibility into traffic that bypasses Cloudflare's security filtering.
This feature allows you to:
* Monitor breakout traffic statistics in the Cloudflare dashboard.
* View traffic patterns for applications configured to bypass Cloudflare.
* Maintain visibility across all traffic passing through your Magic WAN Connector.
For more information, refer to [NetFlow statistics](https://developers.cloudflare.com/magic-wan/analytics/netflow-analytics/).
## 2025-11-06
**Designate WAN link for breakout traffic**
Magic WAN Connector now allows you to designate a specific WAN port for breakout traffic, giving you deterministic control over the egress path for latency-sensitive applications.
With this feature, you can:
* Pin breakout traffic for specific applications to a preferred WAN port.
* Ensure critical traffic (such as Zoom or Teams) always uses your fastest or most reliable connection.
* Benefit from automatic failover to standard WAN port priority if the preferred port goes down.
This is useful for organizations with multiple ISP uplinks who need predictable egress behavior for performance-sensitive traffic.
For configuration details, refer to [Designate WAN ports for breakout apps](https://developers.cloudflare.com/magic-wan/configuration/connector/network-options/application-based-policies/breakout-traffic/#designate-wan-ports-for-breakout-apps).
## 2025-11-06
**Automatic Return Routing (Beta)**
Magic WAN now supports Automatic Return Routing (ARR), allowing customers to configure Magic on-ramps (IPsec/GRE/CNI) to learn the return path for traffic flows without requiring static routes.
Key benefits:
* **Route-less mode**: Static or dynamic routes are optional when using ARR.
* **Overlapping IP space support**: Traffic originating from customer sites can use overlapping private IP ranges.
* **Symmetric routing**: Return traffic is guaranteed to use the same connection as the original on-ramp.
This feature is currently in beta and requires the new Unified Routing mode (beta).
For configuration details, refer to [Configure Automatic Return Routing](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-automatic-return-routing-beta).
## 2025-09-11
**DNS filtering for private network onramps**
[Magic WAN](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-gateway/#dns-filtering) and [WARP Connector](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/warp-connector/site-to-internet/#configure-dns-resolver-on-devices) users can now securely route their DNS traffic to the Gateway resolver without exposing traffic to the public Internet.
Routing DNS traffic to the Gateway resolver allows DNS resolution and filtering for traffic coming from private networks while preserving source internal IP visibility. This ensures Magic WAN users have full integration with our Cloudflare One features, including [Internal DNS](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/#internal-dns) and [hostname-based policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/egress-policies/#selector-prerequisites).
To configure DNS filtering, change your Magic WAN or WARP Connector DNS settings to use Cloudflare's shared resolver IPs, `172.64.36.1` and `172.64.36.2`. Once you configure DNS resolution and filtering, you can use *Source Internal IP* as a traffic selector in your [resolver policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/resolver-policies/) for routing private DNS traffic to your [Internal DNS](https://developers.cloudflare.com/dns/internal-dns/).
## 2025-09-08
**Custom IKE ID for IPsec Tunnels**
Now, Magic WAN customers can configure a custom IKE ID for their IPsec tunnels. Customers that are using Magic WAN and a VeloCloud SD-WAN device together can utilize this new feature to create a high availability configuration.
This feature is available via API only. Customers can read the Magic WAN documentation to learn more about the [Custom IKE ID feature and the API call to configure it](https://developers.cloudflare.com/magic-wan/configuration/common-settings/custom-ike-id-ipsec/).
## 2025-09-05
**Bidirectional tunnel health checks are compatible with all Magic on-ramps**
All bidirectional tunnel health check return packets are accepted by any Magic on-ramp.
Previously, when a Magic tunnel had a bidirectional health check configured, the bidirectional health check would pass when the return packets came back to Cloudflare over the same tunnel that was traversed by the forward packets.
There are SD-WAN devices, like VeloCloud, that do not offer controls to steer traffic over one tunnel versus another in a high availability tunnel configuration.
Now, when a Magic tunnel has a bidirectional health check configured, the bidirectional health check will pass when the return packet traverses over any tunnel in a high availability configuration.
## 2025-07-30
**Magic Transit and Magic WAN health check data is fully compatible with the CMB EU setting.**
Today, we are excited to announce that all Magic Transit and Magic WAN customers with CMB EU ([Customer Metadata Boundary - Europe](https://developers.cloudflare.com/data-localization/metadata-boundary/)) enabled in their account will be able to access GRE, IPsec, and CNI health check and traffic volume data in the Cloudflare dashboard and via API.
This ensures that all Magic Transit and Magic WAN customers with CMB EU enabled will be able to access all Magic Transit and Magic WAN features.
Specifically, these two GraphQL endpoints are now compatible with CMB EU:
* `magicTransitTunnelHealthChecksAdaptiveGroups`
* `magicTransitTunnelTrafficAdaptiveGroups`
## 2025-02-14
**Configure your Magic WAN Connector to connect via static IP assigment**
You can now locally configure your [Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/) to work in a static IP configuration.
This local method does not require having access to a DHCP Internet connection. However, it does require being comfortable with using tools to access the serial port on Magic WAN Connector as well as using a serial terminal client to access the Connector's environment.
For more details, refer to [WAN with a static IP address](https://developers.cloudflare.com/magic-wan/configuration/connector/configure-hardware-connector/#bootstrap-via-serial-console).
## 2024-12-17
**Establish BGP peering over Direct CNI circuits**
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
Refer to [Magic WAN BGP peering](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes) or [Magic Transit BGP peering](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes) to learn more about this feature and how to set it up.
## 2025-02-14
**Sites feature available to all Magic WAN customers**
All Magic WAN customers now have full access to the Magic WAN sites feature. Customers can configure a Magic WAN site either with or without a Magic WAN connector.
## 2024-12-17
**Magic WAN Connector configurable health checks**
Health check rate on Magic WAN Connector IPsec tunnels are now configurable.
## 2024-12-17
**BGP support for Cloudflare Network Interconnect (CNI)**
Magic WAN customers can now establish BGP peering over Direct CNI circuits. Customers can now dynamically exchange routes and path availability status between their router device and the Magic WAN table.
## 2024-12-12
**LAN Policy improvements for the Magic WAN Connector**
Magic WAN Connector LAN Policy now supports unidirectional traffic flows and port-ranges.
## 2024-10-01
**Early access testing for BGP on CNI 2.0 circuits**
Customers can exchange routes dynamically with their Magic virtual network overlay via Direct CNI or Cloud CNI based connectivity.
## 2024-09-27
**Magic WAN Connector sends WARP client traffic to Internet**
All Magic WAN Connectors now route WARP client traffic directly to the Internet, bypassing IPsec tunneling, to prevent double encapsulation of WARP traffic.
## 2024-07-17
**Updates to High Availability on the Magic WAN Connector**
The High Availability feature on Magic WAN Connector now supports additional failover conditions, DHCP lease syncing, and staggered upgrades.
## 2024-06-23
**ICMP support for traffic sourced from private IPs**
Magic WAN will now support ICMP traffic sourced from private IPs going to the Internet via Gateway.
## 2024-06-05
**Application based prioritization**
The Magic WAN Connector can now prioritize traffic on a per-application basis.
## 2024-05-31
**WARP virtual IP addresses**
Customers using Gateway to filter traffic to Magic WAN destinations will now see traffic from Cloudflare egressing with WARP virtual IP addresses (CGNAT range), rather than public Cloudflare IP addresses. This simplifies configuration and improves visibility for customers.
## 2024-01-23
**Network segmentation**
You can define policies in your Connector to either allow traffic to flow between your LANs without it leaving your local premises or to forward it via the Cloudflare network where you can add additional security features.
---
title: Configuration · Cloudflare Magic WAN docs
lastUpdated: 2025-09-25T14:23:12.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-wan/configuration/
md: https://developers.cloudflare.com/magic-wan/configuration/index.md
---
* [Configure with Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/)
* [Manual configuration](https://developers.cloudflare.com/magic-wan/configuration/manually/)
* [Configure cloud on-ramps](https://developers.cloudflare.com/magic-wan/configuration/magic-cloud-networking/)
* [Common settings](https://developers.cloudflare.com/magic-wan/configuration/common-settings/)
---
title: Get started · Cloudflare Magic WAN docs
description: Magic WAN allows you to achieve any-to-any connectivity across
branch and retail sites and data centers, with the Cloudflare connectivity
cloud.
lastUpdated: 2026-01-20T17:03:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/get-started/
md: https://developers.cloudflare.com/magic-wan/get-started/index.md
---
Magic WAN allows you to achieve any-to-any connectivity across branch and retail sites and data centers, with the Cloudflare connectivity cloud.
## Before you begin
Magic WAN is an Enterprise-only product. [Contact Cloudflare](https://www.cloudflare.com/magic-wan/) to acquire Magic WAN. If you plan on using Magic WAN Connector to automatically onboard your locations to Cloudflare, you will need to purchase Magic WAN first.
## Set up method
Magic WAN supports an automatic setup and a manual setup. The automatic setup through Magic WAN Connector is the preferred method.
### Automatic setup
Setting up Magic WAN automatically is done through Magic WAN Connector, and is the preferred method. You can choose between the hardware version and the virtual version of Magic WAN Connector. The virtual version can be installed on your own machines.
If you plan on using Magic WAN Connector, you can skip the prerequisites below, and refer to [Configure with Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/) for more information on how to continue.
### Manual setup
Setting up Magic WAN manually is done through a combination of third-party devices in your premises and the Cloudflare dashboard. To be successful, you need to:
1. Read the [Prerequisites](#prerequisites) below.
2. Follow the steps in [Manual configuration](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-tunnel-endpoints/).
## Prerequisites
Note
The list of prerequisites below is only for customers planning to connect manually to Cloudflare with a third-party device. If you plan on using Magic WAN Connector, skip this section and refer to [Configure with Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/).
### Use compatible tunnel endpoint routers
Magic WAN relies on [GRE](https://developers.cloudflare.com/magic-wan/reference/gre-ipsec-tunnels/) and [IPsec tunnels](https://developers.cloudflare.com/magic-wan/reference/gre-ipsec-tunnels/#ipsec-tunnels) to transmit [packets](https://www.cloudflare.com/learning/network-layer/what-is-a-packet/) from Cloudflare's global network to your origin network. To ensure compatibility with Magic WAN, the routers at your tunnel endpoints must:
* Allow configuration of at least one tunnel per Internet service provider (ISP).
* Support maximum segment size (MSS) clamping.
* Support the configuration parameters for IPsec mentioned in [IPsec tunnels](https://developers.cloudflare.com/magic-wan/reference/gre-ipsec-tunnels/#supported-configuration-parameters).
### Set maximum segment size
Before enabling Magic WAN, you must make sure that you set up the maximum segment size on your network. Cloudflare Magic WAN uses tunnels to deliver [packets](https://www.cloudflare.com/learning/network-layer/what-is-a-packet/) from our global network to your data centers. Cloudflare encapsulates these packets adding new headers. You must account for the space consumed by these headers when configuring the maximum transmission unit (MTU) and maximum segment size (MSS) values for your network.
#### MSS clamping recommendations
##### GRE tunnels as off-ramp
The MSS value depends on how your network is set up.
* **On your edge router**: Apply the clamp to the GRE tunnel internal interface (meaning where the egress traffic will traverse). Set the MSS clamp to 1,436 bytes. Your devices may do this automatically once the tunnel is configured, but it depends on your devices.
##### IPsec tunnels
For IPsec tunnels, the value you need to specify depends on how your network is set up. The MSS clamping value is lower than for GRE tunnels because the physical interface sees IPsec-encrypted packets, not TCP packets, and MSS clamping does not apply to those.
* **On your edge router**: Apply this on your IPsec tunnel internal interface (meaning where the egress traffic will traverse). Your devices may do this automatically once the tunnel is configured, but it depends on your devices. Set the TCP MSS clamp to 1,360 bytes maximum.
Important
Refer to your device documentation to check if it sets IPsec MSS clamping automatically. If that is not the case and you are using IPsec inside GRE, you have to set MSS clamp manually.
Refer to [Maximum transmission unit and maximum segment size](https://developers.cloudflare.com/magic-wan/reference/mtu-mss/) for more details.
### Follow router vendor guidelines
Instructions to adjust MSS by applying MSS clamps vary depending on the vendor of your router.
The following table lists several commonly used router vendors with links to MSS clamping instructions:
| Router device | URL |
| - | - |
| Cisco | [TCP IP Adjust MSS](https://www.cisco.com/en/US/docs/ios-xml/ios/ipapp/command/ip_tcp_adjust-mss_through_ip_wccp_web-cache_accelerated.html#GUID-68044D35-A53E-42C1-A7AB-9236333DA8C4) |
| Juniper | [TCP MSS - Edit System](https://www.juniper.net/documentation/en_US/junos/topics/reference/configuration-statement/tcp-mss-edit-system.html) |
---
title: Glossary · Cloudflare Magic WAN docs
description: Review the definitions for terms used across Cloudflare's Magic WAN
documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/glossary/
md: https://developers.cloudflare.com/magic-wan/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Magic WAN documentation.
| Term | Definition |
| - | - |
| anycast | Anycast is a network addressing and routing method in which incoming requests can be routed to a variety of different locations. Anycast typically routes incoming traffic to the nearest data center with the capacity to process the request efficiently. |
| data packet | A data packet is a unit of data consisting of user and control information. Information in a network is broken down into packets, that might follow different paths to their final destination. |
| equal-cost multi-path routing | A technique that uses hashes calculated from packet data to determine the route chosen. |
| GRE tunnel | Stands for generic routing encapsulation. It is a protocol wrapping one data packet within another type of data packet. This is useful for enabling protocols that are not normally supported by a network. |
| ICMP | Internet Control Message Protocol (ICMP) is used by network devices to send error messages and other operational information. ICMP is useful for diagnostic purposes, for example. |
| Internet key exchange (IKE) | The protocol Cloudflare uses to create the IPsec tunnel between Magic WAN and the customer's device. |
| IPsec tunnel | Stands for Internet Protocol secure. It is a group of protocols for securing connections between devices, by encrypting IP packets. |
| maximum segment size (MSS) | MSS limits the size of packets, or small chunks of data, that travel across a network, such as the Internet. |
| on-ramp | Refers to a way of connecting a business network to Cloudflare. Examples of on-ramps, or ways to connect to Cloudflare, are Anycast GRE tunnels, Anycast IPsec tunnels, Cloudflare Network Interconnect (CNI), Cloudflare Tunnel, and WARP. |
| static route | A fixed configuration to route traffic through Anycast tunnels from Cloudflare global network to the customer's locations. |
| subnet | Also known as subnetwork. It refers to a network that is part of another network. |
| traffic steering | Cloudflare evaluates your route's health and steers traffic according to priorities defined by you and / or tunnel health. |
| tunnel health-check | A probe sent by Cloudflare to check for tunnel health. If a tunnel is not considered healthy, Cloudflare reroutes traffic to one that is considered healthy. |
| WAN | Stands for Wide Area Network. It refers to a computer network that connects groups of computers over large distances. WANs are often used by businesses to connect their office networks. The objective is to make each of the local area networks (LANs) be remotely connected and accessible. |
---
title: Legal · Cloudflare Magic WAN docs
lastUpdated: 2024-08-30T16:09:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-wan/legal/
md: https://developers.cloudflare.com/magic-wan/legal/index.md
---
* [Third party licenses](https://developers.cloudflare.com/magic-wan/legal/3rdparty/)
---
title: Load Balancing · Cloudflare Magic WAN docs
description: You can use Cloudflare Load Balancing with Magic WAN to distribute
traffic across endpoints, reducing strain and improving the performance of
your network. Magic WAN uses Private Network Load Balancing, which supports
both on-ramping and off-ramping traffic to Magic WAN.
lastUpdated: 2026-01-20T17:03:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/load-balancing/
md: https://developers.cloudflare.com/magic-wan/load-balancing/index.md
---
You can use Cloudflare Load Balancing with Magic WAN to distribute traffic across endpoints, reducing strain and improving the performance of your network. Magic WAN uses Private Network Load Balancing, which supports both on-ramping and off-ramping traffic to Magic WAN.
Refer to [Private Network Load Balancing](https://developers.cloudflare.com/load-balancing/private-network/) for more information about the feature and how to set it up. Before using this feature, [enable Load Balancing](https://developers.cloudflare.com/load-balancing/).
---
title: Network Interconnect and Magic WAN · Cloudflare Magic WAN docs
description: Cloudflare Network Interconnect (CNI) allows you to connect your
network infrastructure directly with Cloudflare — rather than using the public
Internet — for a more reliable and secure experience. With CNI, you can bring
Cloudflare's full suite of network functions to your physical network edge.
lastUpdated: 2026-01-20T17:03:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/network-interconnect/
md: https://developers.cloudflare.com/magic-wan/network-interconnect/index.md
---
Cloudflare Network Interconnect (CNI) allows you to connect your network infrastructure directly with Cloudflare — rather than using the public Internet — for a more reliable and secure experience. With CNI, you can bring Cloudflare's full suite of network functions to your physical network edge.
For more information about Network Interconnect, refer to the [Cloudflare Network Interconnect documentation](https://developers.cloudflare.com/network-interconnect/).
Run `traceroute`
If you connect through [GRE](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-tunnel-endpoints/), [IPsec](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-tunnel-endpoints/), [CNI](https://developers.cloudflare.com/network-interconnect/), or [WARP](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/) and want to run `traceroute` to an endpoint behind a [Cloudflare Tunnel](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/), you need to change some settings.
Refer to [Run `traceroute`](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/traceroute/) for more information.
---
title: On-ramps · Cloudflare Magic WAN docs
description: To on-ramp your network traffic to Magic WAN, you can use Magic WAN
Connector, a lightweight software package you can install in corporate network
locations to automatically connect, steer, and shape any IP traffic.
lastUpdated: 2026-01-20T17:03:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/on-ramps/
md: https://developers.cloudflare.com/magic-wan/on-ramps/index.md
---
To on-ramp your network traffic to Magic WAN, you can use [Magic WAN Connector](https://developers.cloudflare.com/magic-wan/configuration/connector/), a lightweight software package you can install in corporate network locations to automatically connect, steer, and shape any IP traffic.
You can also use any device that supports [GRE or IPsec](https://developers.cloudflare.com/magic-wan/configuration/manually/third-party/) tunnels with the supported configuration parameters.
Additional compatible on-ramps include:
* [Cloudflare Network Interconnect (CNI)](https://developers.cloudflare.com/magic-wan/network-interconnect/): Connect your network infrastructure directly with Cloudflare - rather than using the public Internet - for a more reliable and secure experience.
* [Cloudflare Tunnel](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-tunnel/): Magic WAN can be used together with Cloudflare Tunnel for easy access between your networks and applications.
* [WARP](https://developers.cloudflare.com/magic-wan/zero-trust/warp/): Protect corporate devices by securely and privately sending traffic from those devices to Cloudflare's global network, where Cloudflare Gateway can apply advanced web filtering.
- [Magic Cloud Networking](https://developers.cloudflare.com/magic-wan/configuration/magic-cloud-networking/): Automatically create on-ramps from your cloud networks to Magic WAN.
* [Network on-ramp partnerships](https://www.cloudflare.com/network-onramp-partners/): Refer to our [third-party integration tutorials](https://developers.cloudflare.com/magic-wan/configuration/manually/third-party/) for guidance on configuring the most asked for third-party products.
---
title: Reference · Cloudflare Magic WAN docs
lastUpdated: 2024-08-30T16:09:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-wan/reference/
md: https://developers.cloudflare.com/magic-wan/reference/index.md
---
* [Anti-replay protection](https://developers.cloudflare.com/magic-wan/reference/anti-replay-protection/)
* [Bandwidth measurement](https://developers.cloudflare.com/magic-wan/reference/bandwidth-measurement/)
* [Device compatibility](https://developers.cloudflare.com/magic-wan/reference/device-compatibility/)
* [GRE and IPsec tunnels](https://developers.cloudflare.com/magic-wan/reference/gre-ipsec-tunnels/)
* [Maximum transmission unit and maximum segment size](https://developers.cloudflare.com/magic-wan/reference/mtu-mss/)
* [Traffic steering](https://developers.cloudflare.com/magic-wan/reference/traffic-steering/)
* [Tunnel health checks](https://developers.cloudflare.com/magic-wan/reference/tunnel-health-checks/)
* [How Cloudflare calculates Magic Tunnel health alerts](https://developers.cloudflare.com/magic-wan/reference/how-cloudflare-calculates-magic-tunnel-health-alerts/)
---
title: Enable security filters · Cloudflare Magic WAN docs
description: Magic WAN customers have automatic access to Magic Firewall. Magic
Firewall is Cloudflare's firewall-as-a-service solution that allows you to
protect your infrastructure. Magic Firewall supports layers three and four of
the OSI model, and enables you to allow or block traffic on a variety of
packet characteristics.
lastUpdated: 2026-01-20T17:03:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/security/
md: https://developers.cloudflare.com/magic-wan/security/index.md
---
Magic WAN customers have [automatic access to Magic Firewall](https://developers.cloudflare.com/magic-firewall/plans/). Magic Firewall is Cloudflare's firewall-as-a-service solution that allows you to protect your infrastructure. Magic Firewall supports layers three and four of the [OSI model](https://www.cloudflare.com/learning/ddos/glossary/open-systems-interconnection-model-osi/), and enables you to allow or block traffic on a variety of packet characteristics.
Refer to [Magic Firewall](https://developers.cloudflare.com/magic-firewall/) for more information about this product.
As a Magic WAN customer, you can also use Cloudflare Gateway to set up policies to inspect network and HTTP traffic to the Internet or your private network infrastructure. Refer to [Connect to Cloudflare Gateway with Magic WAN](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-gateway/) to learn how to filter Magic WAN traffic with Gateway policies.
---
title: Troubleshooting · Cloudflare Magic WAN docs
lastUpdated: 2026-01-27T09:26:05.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/magic-wan/troubleshooting/
md: https://developers.cloudflare.com/magic-wan/troubleshooting/index.md
---
* [Troubleshoot with IPsec logs](https://developers.cloudflare.com/magic-wan/troubleshooting/ipsec-troubleshoot/)
* [Troubleshoot tunnel health](https://developers.cloudflare.com/magic-wan/troubleshooting/tunnel-health/)
---
title: Cloudflare One integration tutorials · Cloudflare Magic WAN docs
description: Learn how to integrate Cloudflare Magic WAN with other Cloudflare
Cloudflare One products, such as Cloudflare Gateway and Cloudflare WARP.
lastUpdated: 2025-11-04T17:07:51.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/magic-wan/zero-trust/
md: https://developers.cloudflare.com/magic-wan/zero-trust/index.md
---
Review the tutorials to learn more about how you can use Magic WAN with the following Cloudflare One products.
* [Cloudflare Gateway](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-gateway/)
* [Cloudflare Tunnel](https://developers.cloudflare.com/magic-wan/zero-trust/cloudflare-tunnel/)
* [WARP](https://developers.cloudflare.com/magic-wan/zero-trust/warp/)
If you want a deep dive into key architecture and functionalities aspects of Cloudflare One, and learn more about Magic WAN and its structure, refer to [Evolving to a SASE architecture with Cloudflare](https://developers.cloudflare.com/reference-architecture/architectures/sase/).
---
title: 404 - Page Not Found · Cloudflare Migration Guides
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/migration-guides/404/
md: https://developers.cloudflare.com/migration-guides/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: 404 - Page Not Found · Cloudflare MoQ docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/moq/404/
md: https://developers.cloudflare.com/moq/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: 404 - Page Not Found · Cloudflare Network settings docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/404/
md: https://developers.cloudflare.com/network/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Background · Cloudflare MoQ docs
description: Over the years, efficient delivery of live media content has
attracted significant interest from the networking and media streaming
community. Many applications, including live streaming platforms, real-time
communication systems, gaming, and interactive media experiences, require
low-latency media delivery. However, it remained a major challenge to deliver
media content in a scalable, efficient, and robust way over the internet.
Currently, most solutions rely on proprietary protocols or repurpose existing
protocols like HTTP/2 or WebRTC that weren't specifically designed for media
streaming use cases.
lastUpdated: 2025-08-21T15:20:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/moq/about/
md: https://developers.cloudflare.com/moq/about/index.md
---
Over the years, efficient delivery of live media content has attracted significant interest from the networking and media streaming community. Many applications, including live streaming platforms, real-time communication systems, gaming, and interactive media experiences, require low-latency media delivery. However, it remained a major challenge to deliver media content in a scalable, efficient, and robust way over the internet. Currently, most solutions rely on proprietary protocols or repurpose existing protocols like HTTP/2 or WebRTC that weren't specifically designed for media streaming use cases.
Realizing this gap, the IETF Media Over QUIC (MoQ) working group was formed to develop a standardized protocol for media delivery over QUIC transport. The working group brings together expertise from major technology companies, content delivery networks, and academic institutions to create a modern solution for media streaming.
The MoQ protocol leverages QUIC's advanced features such as multiplexing, connection migration, and built-in security to provide an efficient foundation for media delivery. Unlike traditional HTTP-based streaming that treats media as regular web content, MoQ is specifically designed to understand media semantics and optimize delivery accordingly.
Key benefits of MoQ include:
* **Low latency**: QUIC's 0-RTT connection establishment and reduced head-of-line blocking
* **Adaptive streaming**: Native support for different media qualities and bitrates
* **Reliability**: QUIC's connection migration and loss recovery mechanisms
* **Security**: Built-in encryption and authentication through QUIC
* **Efficiency**: Protocol designed specifically for media delivery patterns
The protocol addresses common challenges in live streaming such as handling network congestion, adapting to varying bandwidth conditions, and maintaining synchronization between audio and video streams. MoQ represents a significant step forward in standardizing media delivery for the modern internet.
---
title: gRPC connections · Cloudflare Network settings docs
description: Cloudflare offers support for gRPC to protect your APIs on any
proxied gRPC endpoints. The gRPC protocol helps build efficient APIs with
smaller payloads for reduced bandwidth usage, decreased latency, and faster
implementations.
lastUpdated: 2026-01-14T10:18:43.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/grpc-connections/
md: https://developers.cloudflare.com/network/grpc-connections/index.md
---
Cloudflare offers support for gRPC to protect your APIs on any [proxied gRPC endpoints](https://developers.cloudflare.com/dns/proxy-status/). The gRPC protocol helps build efficient APIs with smaller payloads for reduced bandwidth usage, decreased latency, and faster implementations.
Note
When gRPC is not enabled on a zone, Cloudflare will respond to gRPC requests with a `403 Forbidden` response.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
Charges may occur for gRPC traffic over add-on products such as [Argo Smart Routing](https://developers.cloudflare.com/argo-smart-routing/), [WAF](https://developers.cloudflare.com/waf/), and [Bot Management](https://developers.cloudflare.com/bots/).
## Limitations
Running gRPC traffic on Cloudflare is compatible with most Cloudflare products.
However, the following products have limited capabilities with gRPC requests:
* The [Cloudflare WAF](https://developers.cloudflare.com/waf/) will only run for header inspection during the connection phase. WAF Managed Rules will not run on the content of a gRPC stream.
* Cloudflare Tunnel supports gRPC traffic via [private subnet routing](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/private-net/). Public hostname deployments are not currently supported.
* [Cloudflare Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) does not support gRPC traffic sent through Cloudflare’s reverse proxy. gRPC traffic will be ignored by Access if gRPC is enabled in Cloudflare. We recommend disabling gRPC for any sensitive origin servers protected by Access or enabling another means of authenticating gRPC traffic to your origin servers.
## Enable gRPC
### Requirements
* Your gRPC endpoint must listen on port 443.
* Your gRPC endpoint must support TLS and HTTP/2.
* HTTP/2 must be advertised over ALPN.
* Use `application/grpc` or `application/grpc+
---
title: IP geolocation · Cloudflare Network settings docs
description: IP geolocation adds the CF-IPCountry header to all requests to your
origin server.
lastUpdated: 2025-09-10T08:58:51.000Z
chatbotDeprioritize: false
tags: Geolocation
source_url:
html: https://developers.cloudflare.com/network/ip-geolocation/
md: https://developers.cloudflare.com/network/ip-geolocation/index.md
---
IP geolocation adds the [`CF-IPCountry` header](https://developers.cloudflare.com/fundamentals/reference/http-headers/#cf-ipcountry) to all requests to your origin server.
Cloudflare automatically updates its IP geolocation database multiple times per week.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
## Add IP geolocation information
The recommended procedure to enable IP geolocation information is to [enable the **Add visitor location headers** Managed Transform](https://developers.cloudflare.com/rules/transform/managed-transforms/reference/#add-visitor-location-headers). This Managed Transform adds HTTP request headers with location information for the visitor's IP address, such as city, country, continent, longitude, and latitude.
If you only want the request header for the visitor's country, you can enable **IP Geolocation**.
* Dashboard
To enable **IP Geolocation** in the dashboard:
1. Log in to your [Cloudflare account](https://dash.cloudflare.com) and go to a specific domain.
2. Go to **Network**.
3. For **IP Geolocation**, switch the toggle to **On**.
* API
To enable **IP Geolocation** with the API, send a [`PATCH`](https://developers.cloudflare.com/api/resources/zones/subresources/settings/methods/edit/) request with `ip_geolocation` as the setting name in the URI path, and the `value` parameter set to `"on"`.
Note
In order to use this data, you will need to then retrieve it from the [`CF-IPCountry` header](https://developers.cloudflare.com/fundamentals/reference/http-headers/#cf-ipcountry).
***
## Report an incorrect IP location
If you find an IP address with a location that you believe is incorrect, fill in the [data correction form](https://www.cloudflare.com/lp/ip-corrections/) with the relevant IP address range(s) along with the correct information as applicable (country, state/province, city name, and ZIP code).
If the data is confirmed, Cloudflare will make the necessary changes, which should be reflected within 48 hours.
---
title: IPv6 compatibility · Cloudflare Network settings docs
description: Cloudflare enables IPv6 on all domains without requiring additional
configuration or hardware (as long as your host provides IPv6 support).
lastUpdated: 2025-12-03T22:57:02.000Z
chatbotDeprioritize: false
tags: IPv6
source_url:
html: https://developers.cloudflare.com/network/ipv6-compatibility/
md: https://developers.cloudflare.com/network/ipv6-compatibility/index.md
---
Cloudflare enables IPv6 on all domains without requiring additional configuration or hardware (as long as your host provides IPv6 support).
When IPv6 compatibility is turned on, Cloudflare auto generates [`AAAA` DNS records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#a-and-aaaa) to allow IPv6 clients to connect. On the other hand, when IPv6 compatibility is turned off, Cloudflare does not automatically generate and advertise `AAAA` DNS for the zone. Client software will determine whether to use IPv4 or IPv6 to connect to a hostname that supports both methods.
For [proxied DNS records](https://developers.cloudflare.com/dns/proxy-status/) that have both an IPv6 and IPv4 origin address, Cloudflare will prefer the IPv4 address when connecting to your origin server.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Can customize | No | No | No | Yes |
## Enable IPv6 compatibility
By default, IPv6 compatibility is turned on for your domain and will apply to all domains and subdomains covered by [proxied DNS records](https://developers.cloudflare.com/dns/proxy-status/).
Note
If you have signed up for Cloudflare through a [Cloudflare hosting partner](http://www.cloudflare.com/hosting-partners) or by use [partial setup](https://developers.cloudflare.com/dns/zone-setups/partial-setup/), IPv6 compatibility does not apply to your apex domain.
## Disable IPv6 compatibility
If your origin web server only understands IPv4 formatted IP addresses, non-Enterprise customers should [enable **Pseudo IPv4**](https://developers.cloudflare.com/network/pseudo-ipv4/).
Alternatively, customers with an Enterprise account can disable Cloudflare's IPv6 compatibility.
* Dashboard
To turn off IPv6 compatibility in the dashboard:
1. In the Cloudflare dashboard, go to the **Network** page.
[Go to **Network**](https://dash.cloudflare.com/?to=/:account/:zone/network)
2. Turn off **IPv6 Compatibility**.
* API
To disable IPv6 compatibility using the API, send a [`PATCH`](https://developers.cloudflare.com/api/resources/zones/subresources/settings/methods/edit/) request with `ipv6` as the setting name in the URI path, and the `value` parameter set to `"off"`.
Note
Even when IPv6 is disabled, domains may still receive IPv6 traffic (for example, via the Tor network). To completely disable all IPv6 traffic:
* Turn off [**Onion Routing**](https://developers.cloudflare.com/network/onion-routing/).
* Use a [WAF custom rule](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/) to block `0:0:0:0:0:0:0:0/0` using the filter `ip.src in {::/0}`.
***
## Troubleshoot an IPv6 network issue
Provide the following information to [Cloudflare Support](https://developers.cloudflare.com/support/contacting-cloudflare-support/) if you experience issues with IPv6 connectivity:
* A [traceroute](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/gathering-information-for-troubleshooting-sites/#perform-a-traceroute) that demonstrates the IPv6 connection issues.
* The [Cloudflare data center serving your request](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/gathering-information-for-troubleshooting-sites/#identify-the-cloudflare-data-center-serving-your-request) when the IPv6 issues occur.
* Confirmation of whether [disabling IPv6 Compatibility](#disable-ipv6-compatibility) resolves the issue.
---
title: Maximum upload size · Cloudflare Network settings docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/maximum-upload-size/
md: https://developers.cloudflare.com/network/maximum-upload-size/index.md
---
---
title: Onion Routing and Tor support · Cloudflare Network settings docs
description: Improve the Tor user experience by enabling Onion Routing, which
enables Cloudflare to serve your website’s content directly through the Tor
network and without requiring exit nodes.
lastUpdated: 2025-12-03T22:57:02.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/onion-routing/
md: https://developers.cloudflare.com/network/onion-routing/index.md
---
Improve the Tor user experience by enabling Onion Routing, which enables Cloudflare to serve your website’s content directly through the Tor network and without requiring exit nodes.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
## How it works
Onion Routing helps improve Tor browsing as follows:
* Tor users no longer access your site via exit nodes, which can sometimes be compromised, and may snoop on user traffic.
* Human Tor users and bots can be distinguished by our Onion services, such that interactive challenges are only served to malicious bot traffic.
[Tor Browser](https://tb-manual.torproject.org/about/) users receive an [alt-svc header](https://httpwg.org/specs/rfc7838.html#alt-svc) as part of the response to the first request to your website. The browser then creates a Tor Circuit to access this website using the `.onion` TLD service provided by this header.
You should note that the visible domain in the user interface remains unchanged, as the host header and the SNI are preserved. However, the underlying connection changes to be routed through Tor, as the [UI denotes on the left of the address bar](https://tb-manual.torproject.org/managing-identities/#managing-identities) with a Tor Circuit. Cloudflare does not provide a certificate for the `.onion` domain provided as part of alt-svc flow, which therefore cannot be accessed via HTTPS.
## Enable Onion Routing
* Dashboard
To enable **Onion Routing** in the dashboard:
1. In the Cloudflare dashboard, go to the **Network** page.
[Go to **Network**](https://dash.cloudflare.com/?to=/:account/:zone/network)
2. For **Onion Routing**, switch the toggle to **On**.
* API
To enable **Onion Routing** with the API, send a [`PATCH`](https://developers.cloudflare.com/api/resources/zones/subresources/settings/methods/edit/) request with `opportunistic_onion` as the setting name in the URI path, and the `value` parameter set to `"on"`.
---
title: Pseudo IPv4 · Cloudflare Network settings docs
description: Cloudflare customers can use Pseudo IPv4 if their origin web server
only understands IPv4 formatted IP addresses (meaning it would not support
Cloudflare's default IPv6 compatibility).
lastUpdated: 2025-12-03T22:57:02.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/pseudo-ipv4/
md: https://developers.cloudflare.com/network/pseudo-ipv4/index.md
---
Cloudflare customers can use **Pseudo IPv4** if their origin web server only understands IPv4 formatted IP addresses (meaning it would not support Cloudflare's default [IPv6 compatibility](https://developers.cloudflare.com/network/ipv6-compatibility/)).
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
## Background
Some older origin server analytics and fraud detection software expect IP addresses in an IPv4 format and do not support IPv6 addresses.
**Pseudo IPv4** uses the [Class E IPv4 address space](https://tools.ietf.org/html/rfc1112#section-4) to provide as many unique IPv4 addresses corresponding to IPv6 addresses as possible.
* Example Class E IPv4 address: `240.16.0.1`
* Example IPv6 address: `2400:cb00:f00d:dead:beef:1111:2222:3333`
Note
Class E IPv4 addresses are designated as experimental and are not used for production Internet traffic.
## Configure Pseudo IPv4
Cloudflare offers three options for configuring **Pseudo IPv4**:
* **Off**: Default value.
* **Add Header**: Cloudflare automatically adds the `Cf-Pseudo-IPv4` header with a Class E IPv4 address hashed from the original IPv6 address.
* **Overwrite Headers**:
If **Pseudo IPv4** is set to `Overwrite Headers` - Cloudflare overwrites the existing `Cf-Connecting-IP` and `X-Forwarded-For` headers with a pseudo IPv4 address while preserving the real IPv6 address in `CF-Connecting-IPv6` header.
Note
When using *Overwrite Headers*, no software changes are necessary in your origin web server.
To configure **Pseudo IPv4**:
* Dashboard
To change the **Pseudo IPv4** setting in the dashboard:
1. In the Cloudflare dashboard, go to the **Network** page.
[Go to **Network**](https://dash.cloudflare.com/?to=/:account/:zone/network)
2. For **Pseudo IPv4**, choose your desired setting.
* API
To change **Pseudo IPv4** with the API, send a [`PATCH`](https://developers.cloudflare.com/api/resources/zones/subresources/settings/methods/edit/) request with `pseudo_ipv4` as the setting name in the URI path, and the `value` parameter set to your desired value: `"off"`, `"add_header"`, or `"overwrite_header"`.
---
title: Understanding the True-Client-IP Header · Cloudflare Network settings docs
description: Enabling the True-Client-IP Header adds the True-Client-IP header
to all requests to your origin server, which includes the end user's IP
address.
lastUpdated: 2025-01-28T15:34:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/true-client-ip-header/
md: https://developers.cloudflare.com/network/true-client-ip-header/index.md
---
Enabling the True-Client-IP Header adds the [`True-Client-IP` header](https://developers.cloudflare.com/fundamentals/reference/http-headers/#true-client-ip-enterprise-plan-only) to all requests to your origin server, which includes the end user's IP address.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | No | Yes |
## Add True-Client-IP Header
The recommended procedure to access client IP information is to [enable the **Add "True-Client-IP" header** Managed Transform](https://developers.cloudflare.com/rules/transform/managed-transforms/reference/#add-true-client-ip-header).
Note
To use this data, you will need to then retrieve it from the [`True-Client-IP` header](https://developers.cloudflare.com/fundamentals/reference/http-headers/#cf-ipcountry).
## Additional resources
For additional guidance on using True-Client-IP Header with Cloudflare, refer to the following resources:
* [Available Managed Transforms](https://developers.cloudflare.com/rules/transform/managed-transforms/reference/#add-true-client-ip-header)
* [Cloudflare HTTP headers](https://developers.cloudflare.com/fundamentals/reference/http-headers/#true-client-ip-enterprise-plan-only)
* [Restoring original visitor IPs](https://developers.cloudflare.com/support/troubleshooting/restoring-visitor-ips/restoring-original-visitor-ips/)
---
title: WebSockets · Cloudflare Network settings docs
description: Cloudflare supports proxied WebSocket connections without
additional configuration.
lastUpdated: 2025-12-03T22:57:02.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network/websockets/
md: https://developers.cloudflare.com/network/websockets/index.md
---
Cloudflare supports proxied WebSocket connections without additional configuration.
## Background
WebSockets are open connections sustained between the client and the origin server. Inside a WebSockets connection, the client and the origin can pass data back and forth without having to reestablish sessions. This makes exchanging data within a WebSockets connection fast. WebSockets are often used for real-time applications such as live chat and gaming.
## Enable WebSockets
* Dashboard
To enable **WebSockets** connections to your origin server in the dashboard:
1. In the Cloudflare dashboard, go to the **Network** page.
[Go to **Network**](https://dash.cloudflare.com/?to=/:account/:zone/network)
2. For **WebSockets**, switch the toggle to **On**.
* API
To enable **WebSockets** connections to your origin server with the API, send a [`PATCH`](https://developers.cloudflare.com/api/resources/zones/subresources/settings/methods/edit/) request with `websockets` as the setting name in the URI path, and the `value` parameter set to `"on"`.
## Compatibility notes
| Product | Compatible | Notes |
| - | - | - |
| [Argo](https://developers.cloudflare.com/argo-smart-routing/) | No | Argo is not compatible with WebSockets. |
| [SSL](https://developers.cloudflare.com/ssl/) | Yes | |
| [WAF](https://developers.cloudflare.com/waf/) | Yes\* | The initial HTTP 101 request is subject to WAF managed rules, custom rules, rate limiting rules, and other WAF features like any other WebSockets connection. However, once a connection has been established, the WAF does not perform any further inspections. |
| [Workers](https://developers.cloudflare.com/workers/examples/websockets/) | Yes | You can also use [Durable Objects](https://developers.cloudflare.com/durable-objects/) as an endpoint for WebSocket sessions, giving you full control over messages sent to and from clients. |
Note
Cloudflare also supports [ASP.NET SignalR](http://signalr.net/), which helps negotiate which transport method to use (long polling or WebSockets).
## Availability
WebSockets are supported on all Cloudflare plans.
## Requests and Bandwidth measurement
Given the nature of WebSocket connections, you may notice they differ from typical HTTP traffic in terms of requests and bandwidth usage. If you are an Enterprise customer, it is important to consider how Cloudflare measures requests and bandwidth to accurately estimate your usage.
Cloudflare measures a single WebSocket connection in the following way:
* **Requests**: Cloudflare recognizes only the initial upgrade request per WebSocket connection as an HTTP request. Even though you can send a bidirectional message stream through the established WebSocket connection, it will be counted as a single long-lived HTTP request.
* **Bandwidth**: Cloudflare measures data transfer sent from Cloudflare to the client. This typically means that messages from the WebSocket server behind Cloudflare to the WebSocket client are counted towards bandwidth usage.
Once a WebSocket connection is closed, you can view your aggregated WebSocket usage through [Traffic Analytics](https://developers.cloudflare.com/analytics/account-and-zone-analytics/zone-analytics/#traffic), the [GraphQL Analytics API](https://developers.cloudflare.com/analytics/graphql-api/), and [HTTP requests logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/).
## Technical note
When Cloudflare releases new code to its global network, we may restart servers, which terminates WebSockets connections.
### Best practices
* Implement a [keepalive](https://developer.mozilla.org/en-US/docs/Web/API/WebSockets_API/Writing_WebSocket_servers#pings_and_pongs_the_heartbeat_of_websockets).
* Review and then remove or extend timeout settings on the origin and/or on the client.
### Troubleshooting
Investigating issues with Websocket can be facilitated with client tools like [wscat](https://github.com/websockets/wscat). Being able to reproduce an issue on a single URL with a minimalistic tool helps narrowing down the issue.
The `EdgeStartTimestamp` and `EdgeStopTimestamp` fields in [HTTP requests logs](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/http_requests/) represent the duration of the WebSocket connection (they do not represent the initial HTTP connection).
---
title: 404 - Page Not Found · Cloudflare Network Error Logging docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-error-logging/404/
md: https://developers.cloudflare.com/network-error-logging/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Get started · Cloudflare Network Error Logging docs
description: Network Error Logging is available to users on all plan types.
lastUpdated: 2025-09-15T16:24:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-error-logging/get-started/
md: https://developers.cloudflare.com/network-error-logging/get-started/index.md
---
Network Error Logging is available to users on all plan types.
To enable Network Error Logging for Free and Pro zones:
1. In the Cloudflare dashboard, go to the **Account home** page.
[Go to **Account home**](https://dash.cloudflare.com/?to=/:account/home)
2. Select **Network** and locate **Network Error Logging Monitoring**.
3. Select the toggle to enable Network Error Logging.
To enable this for Business and Enterprise, contact support or your account team.
---
title: View Reports · Cloudflare Network Error Logging docs
description: NEL reports show you why a request failed, the country a request
failed from, and last mile network a request failed from, and the likely
intended Cloudflare data center.
lastUpdated: 2025-09-15T16:24:30.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-error-logging/how-to/
md: https://developers.cloudflare.com/network-error-logging/how-to/index.md
---
Use NEL reports to view information such as:
* Why a request failed
* The country a request failed from
* The last mile network a request failed from
* The Cloudflare data center the request was most likely meant for
1. Log in to your Cloudflare dashboard.
[Go to **Account home**](https://dash.cloudflare.com/?to=/:account/home)
2. Select **Analytics & Logs** > **Edge Reachability**.
Click a tab under **Reachability summary** to view specific information related to your Origin ASN, Origin, IP, or data center. Hover over a location on the map to view the number of reachable requests.
Under **Reachability by data center**, click a location under Data Centers to filter reachability by a specific location.
To view the log fields available for NEL, refer to [NEL reports](https://developers.cloudflare.com/logs/logpush/logpush-job/datasets/zone/nel_reports/).
---
title: Failures · Cloudflare Network Error Logging docs
description: If a user is able to connect to Cloudflare and the site they
connect to has NEL enabled, Cloudflare passes back two headers to the browser
indicating that they should report any network failures to an endpoint
specified in the headers. The browser will operate as usual, and if something
happens that prevents the browser from connecting to the site, the browser
will log the failure as a report and send it to the endpoint.
lastUpdated: 2024-09-30T15:09:32.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-error-logging/reference/
md: https://developers.cloudflare.com/network-error-logging/reference/index.md
---
If a user is able to connect to Cloudflare and the site they connect to has NEL enabled, Cloudflare passes back two headers to the browser indicating that they should report any network failures to an endpoint specified in the headers. The browser will operate as usual, and if something happens that prevents the browser from connecting to the site, the browser will log the failure as a report and send it to the endpoint.
Network Error Logging failures can occur for different reasons which are outlined below.
## Internet Service Provider (ISP) outage
An ISP outage appears to NEL users as failures from one particular last-mile network. By examining NEL data to look at the client autonomous system number (ASN) view, you can see which networks are causing the most impact.
For customers, this scenario appears as an influx of `tcp.timed_out errors`, as well as `tcp.failed`, `h2.protocol_error` and `h3.protocol_error`.
In the event of a last-mile outage, the best course of action is to contact the provider to investigate.
## Transit Flap
Transit flaps look like momentary outages caused by transits re-establishing BGP sessions.
To customers, this will appear as `tcp.timed_out` reports from a variety of ASNs over a short period of time. This could happen for several reasons:
* Maintenance in the transit network necessitated a reset of the session.
* Maintenance or reboots in Cloudflare necessitated a reset of the BGP session.
* Packet loss in the network caused the session to flap.
Heavy packet loss in the network will likely result in a series of flaps over time. Maintenance is typically one impact period that lasts no more than two minutes.
## Infrastructure outage
Infrastructure outages occur at shared peering points, such as Internet exchanges.
These outages appear to customers as an increase in `tcp.timed_out`, `tcp.failed`, and `tcp.aborted reports`. These failures will likely appear across multiple networks for an extended period of time.
Depending on the severity of the report volume, Cloudflare may declare an incident to track remediation. Alternatively, Cloudflare may deactivate peering from these shared points until the issue is resolved.
## Cloudflare outage
Cloudflare outages consist of issues within Cloudflare’s data-center fabric.
These outages appear to customers as an increase in `tcp.timed_out`, `tcp.failed`, and `tcp.aborted` reports and will likely appear across multiple networks for a short period of time.
By pivoting by data center, customers can track the impact across Cloudflare points of presence. Cloudflare-based incidents will always be tracked through a status page, which will indicate whether or not there are issues within the impacted region.
## Provider sending traffic through scrubbing center/blocking traffic
This type of outage manifests as TLS errors, such as `tls.cert.authority_invalid`, `tls.cert.name_invalid,` or others and may also present with `tcp.aborted errors`.
Customers may uncover this behavior by looking at which last-mile ASNs are displaying increased failures, as it will typically be only one.
Customers can seek remediation by contacting the provider that they believe is scrubbing their traffic.
## Certificate issues
Certificate issues are also detectable through NEL. The `TLS.version`, `cipher_mismatch`, or other errors may present across multiple ISPs in multiple Cloudflare locations.
If this is detected in NEL, the issue can be remediated by deploying new certificates or using [Cloudflare’s SSL management suite](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/) to automatically deploy new certificates.
---
title: 404 - Page Not Found · Cloudflare Network Interconnect docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-interconnect/404/
md: https://developers.cloudflare.com/network-interconnect/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Changelog · Cloudflare Network Interconnect docs
description: Review recent changes to Cloudflare Network Interconnect.
lastUpdated: 2025-09-02T14:32:41.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-interconnect/changelog/
md: https://developers.cloudflare.com/network-interconnect/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/network-interconnect.xml)
## 2024-12-17
**Establish BGP peering over Direct CNI circuits**
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering allows customers to:
* Automate the process of adding or removing networks and subnets.
* Take advantage of failure detection and session recovery features.
With this functionality, customers can:
* Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
* Secure the session by MD5 authentication to prevent misconfigurations.
* Exchange routes dynamically between their devices and their Magic routing table.
Refer to [Magic WAN BGP peering](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-bgp-routes) or [Magic Transit BGP peering](https://developers.cloudflare.com/magic-transit/how-to/configure-routes/#configure-bgp-routes) to learn more about this feature and how to set it up.
## 2024-10-01
**Early access testing for BGP on Direct CNI circuits**
Customers can exchange routes dynamically with their Magic virtual network overlay via Direct CNI or Cloud CNI based connectivity.
## 2024-09-02
**Interconnect portal displays all available locations in a list**
Customers can now see all available Direct CNI locations when searching for a Cloudflare site in the Interconnects interface.
---
title: Get started · Cloudflare Network Interconnect docs
description: Connect your network privately to Cloudflare
lastUpdated: 2026-02-05T16:39:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-interconnect/get-started/
md: https://developers.cloudflare.com/network-interconnect/get-started/index.md
---
BGP architecture and resiliency
CNI supports BGP peering with the Magic routing table. For detailed information about BGP architecture, Edge Resiliency Mode, and route propagation behavior, refer to the BGP reference documentation in [Magic Transit](https://developers.cloudflare.com/magic-transit/reference/traffic-steering/#bgp-information) or [Magic WAN](https://developers.cloudflare.com/magic-wan/reference/traffic-steering/#bgp-information) depending on your use case.
## Prerequisites
### CNI port availability
Your Cloudflare account team determines CNI eligibility and port availability. Notably:
* CNI ports are currently offered at no charge to Enterprise customers.
* Non-Enterprise customers (and any third party) may peer with Cloudflare via Internet Exchange according to our [open peering policy](https://www.cloudflare.com/peering-policy/).
* CNI is available at select Cloudflare data centers:
* The type of Dataplane offered in that location will determine specifications of the supported connection, such as the MTU.
* The diversity offered in the location will vary.
* Customers must have a BGP session established for CNI v1 to be operational.
### Prefix requirements
To peer with Cloudflare, advertise prefixes with a prefix length of `/24` or shorter for IPv4 and `/48` or shorter for IPv6.
## Product use cases
CNI provides a private point-to-point IP connection with Cloudflare. There are two Dataplanes that come with different technical specifications.
| | Dataplane v1 | Dataplane v2 |
| - | - | - |
| **Magic Transit Direct Server Return (DSR)** Distributed Denial of Service (DDoS) protection for all ingress traffic from the Internet to your public network. Send egress traffic via your ISP. | Supported with or without a GRE tunnel established over the interconnect circuit. | Supported. |
| **Magic Transit with Egress** DDoS protection for all ingress traffic from the Internet to your public network. Send egress traffic via Cloudflare. | Supported with or without a GRE tunnel established over the interconnect circuit. | Supported. |
| **Magic WAN and Zero Trust** Build a secure, private network backbone connecting your Zero Trust users and applications with all your sites, data centers, and clouds. | Supported with a GRE tunnel established over the interconnect circuit. | Supported. |
| **Peering** Exchange public routes with a single Cloudflare PoP (Point of Presence). | Supported. All customers connecting with the edge data center will exchange public routes at that PoP with AS13335. Connectivity is established at each individual PoP. Routes for other edge locations in Cloudflare's network may not be available. Routes for customer-advertised prefixes will be available only in the connected PoP. | Not supported. |
| **Application Security and Performance** Improve the performance and security of your web applications | **Supported via peering**: Customers can use Argo Smart Routing to direct origin traffic via the edge peering connection when it is determined to be the lowest latency option. Customers must maintain a direct Internet connection which will always be used for a portion of traffic and during failure scenarios. **Supported Via Magic Transit**: Customers may configure any product with an origin server IP address that is protected by Magic Transit. Magic Transit will direct this traffic via the overlay and customer can control interconnect next-hops using the Magic networking routing table. | When the origin IPs are behind Magic Transit over a CNI v2, all Cloudflare services that work with public origins (like Load Balancer, WAF, Cache) will run over the CNI. |
For more details refer to the [prerequisites section](https://developers.cloudflare.com/network-interconnect/get-started/#prerequisites).
## Technical specifications
* **Supported port types**:
* **Dataplane v1**: 10GBASE-LR (single-mode fiber) and 100GBASE-LR (single-mode fiber).
* **Dataplane v2**: 10GBASE-LR (single-mode fiber) and 100GBASE-LR4 (single-mode fiber) optics are supported.
* **Distance limitations:** Cloudflare does not support optical links longer than 10 km. For longer distances, you must use intermediate hardware or a third-party provider to extend the connection.
* **IP addressing:** All CNI connections and Partner CNI connections use a `/31` subnet for point-to-point IP connectivity between your router and Cloudflare.
* **VLAN support:**
* **Dataplane v1**: CNI ports may be assigned a single 802.1Q VLAN tag.
* **Dataplane v2**: VLAN tagging (802.1Q) and QinQ are not yet supported.
* **MTU considerations:**
* **Dataplane v1**: Supports a native 1,500-byte MTU for traffic from Cloudflare to you (ingress), but still requires a 1,476-byte MTU for traffic from you to Cloudflare (egress).
* **Dataplane v2**: Supports a maximum MTU of 1,500 bytes bidirectionally with no GRE requirement.
* **Bidirectional Forwarding Detection (BFD):**
* **Dataplane v1**: BFD provides fast failure detection for BGP sessions and is supported on direct connections. To enable BFD, contact your account team. Note that BFD on a CNI does not impact the failover time for Magic Transit / WAN tunnels, which rely on separate health checks.
* **Dataplane v2**: Not yet supported.
* **Link Aggregation Control Protocol (LACP)**:
* **Dataplane v1**: To increase bandwidth and provide link resiliency, Cloudflare supports combining multiple physical CNI ports into a single logical channel using Link Aggregation Control Protocol (LACP). You can bundle multiple connections to increase total throughput and add redundancy to your private connection with Cloudflare.
* **Dataplane v2**: Not yet supported. Use ECMP instead.
## Performance characteristics
The following are the maximum throughput rates supported by the CNI connection. Actual performance will depend on your specific use case and configuration.
| Direction (use case) | 10G Circuit | 100G Circuit |
| - | - | - |
| From Cloudflare to Customer (all use cases) | Up to 10 Gbps | Up to 100 Gbps |
| From Customer to Cloudflare (peering use case) | Up to 10 Gbps | Up to 100 Gbps |
| From Customer to Cloudflare (Magic Transit/WAN) | **v1**: Up to 1 Gbps per GRE tunnel over the CNI **v2**: Up to 1 Gbps per CNI connection | **v1**: Up to 1 Gbps per GRE tunnel over the CNI **v2**: Up to 1 Gbps per CNI connection |
## Service expectations
Consider the following service levels when planning your deployment:
* **No Formal SLA**:
* CNI is currently offered at no charge and without a formal [Service Level Agreement (SLA)](https://www.cloudflare.com/service-specific-terms-network-services/#cf-network-interconnect-terms).
* Cloudflare will work to restore CNI service in the event of a Cloudflare issue. In some Cloudflare data centers the recovery time could be several days. Therefore, we always recommend backup connectivity to a different device or via an Internet tunnel.
* **Observability**: There is no visibility of the interconnect config/status within the Cloudflare dashboard.
* **Availability**: While network-resilient locations are designed to maintain connectivity during maintenance, single-homed locations can experience full service disruption.
* **Backup Connectivity**: You are required to maintain alternative Internet connectivity as a backup for all CNI implementations.
* **Capacity planning**: You are responsible for capacity planning across your available links to Cloudflare, based on the topology and size of those links.
## Location alignment
### Available locations
Direct connections are available at any Cloudflare data center where you are also located. Make sure to check whether the location of interest has the right dataplane version and diversity requirements for your use case. Refer to [available locations](https://developers.cloudflare.com/network-interconnect/static/cni-locations-21-jan-2026.pdf) (PDF) for details.
### Connectivity partners
Cloudflare partners with leading global providers, including: Console Connect, CoreSite, Digital Realty, Equinix Fabric, Megaport, PacketFabric, and Zayo.
## End-to-end implementation workflow
The process of provisioning a CNI typically takes two to four weeks, depending on the complexity of implementation and third-party provider timelines. The most common delays occur during the physical connection phase, which is outside of Cloudflare's direct control.
1. **Submit request**: Work with your account team to create a CNI request ticket, providing your desired CNI type, location, use case, and technical details. An Implementation Manager will be assigned to guide the process.
2. **Review configuration**: For the v1 Dataplane, the Implementation Manager will provide a detailed configuration document covering IP addressing, VLANs, and other technical specifications. You must review and approve this document. For the v2 Dataplane, this step is not necessary.
3. **Order connection**:
* For a **Direct Interconnect**, you will receive a Letter of Authorization (LOA) from Cloudflare to order the physical cross-connect from the data center facility operator.
* For a **Partner Interconnect**, you will use the provided details to order a virtual circuit from the partner's portal.
4. **Configure network**: Both Cloudflare and your network team will configure the respective network devices according to the approved document.
5. **Test and verify**: Once the connection is physically established, teams will perform basic connectivity tests (for example, ping) and, if applicable, verify that the BGP session can be established.
6. Enable tunnel health checks for [Magic Transit](https://developers.cloudflare.com/magic-transit/how-to/configure-tunnel-endpoints/#add-tunnels) and/or [Magic WAN](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-tunnel-endpoints/#add-tunnels).
7. **Activate services**: Configure your Cloudflare products (for example, Magic Transit) to route traffic over the new CNI. The Implementation Manager will verify end-to-end traffic flow before marking the deployment as complete.
8. [Add maintenance notifications](https://developers.cloudflare.com/network-interconnect/monitoring-and-alerts/#enable-cloudflare-status-maintenance-notification).
## How-to guides
### Provision a Direct Interconnect
1. **Project Kickoff**: In an initial kickoff call, you will confirm the scope and timeline with Cloudflare. Be prepared to provide the following information:
* desired colocation facility
* required port speeds (10G or 100G)
* BGP ASN for Peering/Magic Transit
* BGP password (optional)
2. **Order Cross-Connect**: Cloudflare will issue a Letter of Authorization (LOA). This document grants you permission to order a physical cross-connect between your equipment and a specific port on Cloudflare's hardware within the data center. The end-to-end process for ordering a cross-connect can take one to two weeks or more, depending on the facility provider. Cloudflare's demarcation is the port that is specified in the LOA. You are responsible for the deployment, provisioning, and ongoing support and operation of this connection, and the commercial relationships with the facility provider and any third-party connectivity providers.
### Provision a Partner Interconnect
Cloudflare partners with leading connectivity providers globally. To provision a Partner Interconnect, you will initiate a connection request from your chosen provider's administrative portal. Cloudflare will then review and accept the request to activate the virtual circuit.
### Provision a Cloud Interconnect
Enterprise customers using Magic WAN can get started with Cloud Interconnect by contacting their account team.
#### AWS Direct Connect (beta)
If you are a Magic WAN customer, you can connect to [AWS Direct Connect](https://docs.aws.amazon.com/directconnect/) using Cloud Interconnect. Cloud Interconnect supports AWS Dedicated Direct Connect, which provides a full physical port allocation in AWS. AWS Hosted Direct Connect is not yet supported.
For your AWS Dedicated Direct Connect, you can choose between connection speeds of 10 Gbps or 1 Gbps.
To connect to AWS Direct Connect:
1. Contact your account team to start the Cloud Interconnect provisioning process. Your team will let you know of available interconnect locations so you can choose the best one for you, as well as all the details involved in this process.
2. Log in to your AWS portal and order a Direct Connect.
3. AWS will provide you a Letter of Authorization (LOA) and a VLAN ID that you need to send to your account team.
4. Your account team will continue the process of provisioning your Cloud Interconnect with the AWS documents you have provided. Overall, this process should take around four weeks to finish.
#### Google Cloud interconnect (beta)
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account.
2. Select **Interconnects** > **Create new**.
3. Under **Cloud Interconnect**, select **Create new**.
4. Under **Google Integration**, select **Select integration**.
5. Give your interconnect a name and optionally a description. Make sure the MTU value matches the MTU configured on the [GCP VLAN attachment](https://cloud.google.com/network-connectivity/docs/interconnect/how-to/dedicated/creating-vlan-attachments).
6. Select **Continue**.
7. From the **Interface speed** drop-down menu, select an interface speed. GCP will charge you based on the speed of the interconnect that you choose.
8. Enter your [VLAN attachment pairing key](https://cloud.google.com/network-connectivity/docs/interconnect/how-to/partner/creating-vlan-attachments).
9. Select **Continue**.
10. Review the details you provided, and select **Confirm order**.
Your Google Cloud Platform (GCP) interconnect will take a few minutes to be available. A BGP session will be established but no routes will be exchanged.
#### GCP next steps
You can now select **View interconnects** for a list of all interconnects on your account. Select the interconnect name to show the interconnect details. The interconnect has a unique **Interconnect ID**.
After you have configured your Google Cloud Interconnect, you will need to add routes to use the interconnect:
* To create routes in the Magic routing table to direct traffic towards GCP:
* Add [static routes](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#configure-static-routes) to your Magic WAN routing table with [legacy bidirectional tunnel health checks](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-tunnel-endpoints/#legacy-bidirectional-health-checks) to detect failures and steer traffic to alternative paths.
* Note that routes advertised by BGP from GCP Cloud Router will be ignored.
* To create routes in GCP routing table to direct traffic towards Cloudflare, you must use the GCP Cloud Router:
* Add [custom learned routes to Cloud Router](https://cloud.google.com/network-connectivity/docs/router/how-to/configure-custom-learned-routes).
* Use the BGP session. Reach out to your account team to request a list of one or more prefixes to advertise, and specify the interconnect ID you want to advertise over.
---
title: Monitoring and alerts · Cloudflare Network Interconnect docs
description: Monitor CNI status and configure maintenance alerts
lastUpdated: 2026-01-23T15:31:55.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-interconnect/monitoring-and-alerts/
md: https://developers.cloudflare.com/network-interconnect/monitoring-and-alerts/index.md
---
## Monitoring
The Cloudflare dashboard shows a list of all previously created interconnects, as well as useful information such as IP addresses, speed, type of interconnect, and status.
The Status column displays three statuses:
[Go to **Interconnects**](https://dash.cloudflare.com/?to=/:account/interconnects)
* **Active**: The interconnect port on the Customer Connectivity Router (CCR) is operationally up. This means that the CCR port sees sufficient light levels and has negotiated an Ethernet link.
* **Unhealthy**: The link operational state at interconnect port is down. This might mean the CCR does not see light, cannot negotiate an Ethernet signal, or the light levels are below -20 dBm. You can take general troubleshooting steps to solve the issue (such as checking cables and status lights for connectivity issues). If you are unable to solve the issue in this way, contact your account team.
* **Pending**: The link is not yet active. This is expected and can occur for several reasons: the customer has not received a cross-connect, the device is unresponsive, or physical adjustments may be required, such as swapping RX/TX fibers. The **Pending** status will disappear after the customer completes the cross-connect and status moves to **Active**.
## Alerts (v1 dataplane only)
You can configure notifications for upcoming CNI maintenance events using the Notifications feature in the Cloudflare dashboard. It is recommended to subscribe to two types of notifications to stay fully informed.
**CNI Connection Maintenance Alert (beta):** This alert informs you about maintenance events (scheduled, updated, or canceled) that directly impact your CNI circuits used with the Magic Networking overlay only.
* You will receive warnings up to two weeks in advance for maintenance impacting your Magic Transit/WAN CNI connections.
* You will be notified if the details of a scheduled maintenance change or if it is canceled.
* For recently added maintenance, notifications are sent after a six-hour delay to prevent alerting fatigue from minor adjustments.
**Cloudflare Status Maintenance Notification:** This alert informs you about maintenance for an entire Cloudflare Point of Presence (PoP). While not specific to your CNI, this maintenance will impact all CNI services in that location. This includes connections used only for peering without Magic Networking.
* You will be warned about potentially disruptive maintenance at the PoP level.
* By default, you are notified for all event types (Scheduled, Changed, Canceled), but you can filter these.
* By default, you are notified for all Cloudflare PoPs, but you can filter for only the specific locations where you have CNI circuits.
## How to configure alerts
### Enable CNI Connection Maintenance Alert (beta)
1. In the Cloudflare dashboard, go to the **Notifications** page.
[Go to **Notifications**](https://dash.cloudflare.com/?to=/:account/notifications)
2. Select **Add**.
3. From the product drop-down menu, select *Cloudflare Network Interconnect*.
4. Select **Connection Maintenance Alert**.
5. Give your notification a name and an optional description.
6. Choose your preferred notification method, such as email address.
7. Select **Save**.
### Enable Cloudflare Status Maintenance Notification
First, identify the PoP code for your CNI circuit:
1. In the Cloudflare dashboard, go to the **Connectors** page.
[Go to **Connectors**](https://dash.cloudflare.com/?to=/:account/magic-networks/connections)
2. Select the **Interconnects** tab.
3. Select the CNI you want to enable notifications for.
4. In the menu that appears, note the Data Center code (for example, `gru-b`).
Now, configure the alert:
1. Go to **Notifications** and select **Add**.
2. From the product drop-down menu, select *Cloudflare Status*.
3. Select **Maintenance Notification**.
4. Give your notification a name and choose your notification method.
5. Select **Next**.
6. Optionally, use the **Filter on Event Type** to select only the event types you want to be alerted for (Scheduled, Changed, Canceled).
7. In **Filter on Points of Presence**, enter the three-letter code for your PoP (for example, for `gru-b`, enter `gru`). You can add multiple PoPs, separated by commas.
8. Select **Create**.
---
title: Operational guidance · Cloudflare Network Interconnect docs
description: Maintenance windows and troubleshooting guidance for CNI
lastUpdated: 2026-01-23T11:36:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/network-interconnect/operational-guidance/
md: https://developers.cloudflare.com/network-interconnect/operational-guidance/index.md
---
## Understanding maintenance and availability
Also refer to [Monitoring and alerts](https://developers.cloudflare.com/network-interconnect/monitoring-and-alerts).
Regular network maintenance may impact Cloudflare Network Interconnect (CNI) connectivity.
* **Maintenance impact**: Maintenance windows average six hours. Customers who are not redundantly connected to diverse devices, for instance in single-homed PoPs, will experience a complete service disruption on CNI in that location.
* **Designing for availability**: For critical applications, deploy CNI in locations that support diversity on the device level (multi-homed PoPs). Cloudflare does not guarantee coordinated maintenance between PoP locations.
## Troubleshooting
When facing connectivity problems, your first action should be to check for broader service disruptions. Visit [Cloudflare Status](https://www.cloudflarestatus.com/) to see if any scheduled maintenance or active incidents are impacting services. This helps determine if the issue originates outside your network. Refer to [Monitoring and alerts](https://developers.cloudflare.com/network-interconnect/monitoring-and-alerts/).
If no system-wide problems are reported, gather the following information before submitting a support case. Providing comprehensive details facilitates a faster resolution:
* **Timeline**: When the issue began and ended (if applicable), including the timezone.
* **Identification**: The CNI IP address or point-to-point prefix for the impacted CNI. If your CNI is part of a Magic setup, please also provide the name of the Magic Transit/WAN interconnect as listed in your dashboard.
* **Physical Layer**: Light levels of the CNI link (if applicable).
* **Service Impact**: Confirmation whether Magic Transit / WAN traffic was affected.
* **Problem Description**: A clear summary of the issue (for example, CNI down, Border Gateway Protocol (BGP) session down, prefixes withdrawn).
---
title: 404 - Page Not Found · Cloudflare Notifications docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/notifications/404/
md: https://developers.cloudflare.com/notifications/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API reference · Cloudflare Notifications docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/notifications/api-reference/
md: https://developers.cloudflare.com/notifications/api-reference/index.md
---
---
title: Configure Cloudflare Notifications · Cloudflare Notifications docs
description: The list of notifications available depends on the type of account
you have. Refer to Available Notifications to learn more about what each
notification does and what do to when receiving one.
lastUpdated: 2025-09-04T16:00:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/notifications/get-started/
md: https://developers.cloudflare.com/notifications/get-started/index.md
---
The list of notifications available depends on the type of account you have. Refer to [Available Notifications](https://developers.cloudflare.com/notifications/notification-available/) to learn more about what each notification does and what do to when receiving one.
You can check the [Notification History](https://developers.cloudflare.com/notifications/notification-history/) using the API to view notifications that have been generated for your account.
## Permissions
To create a notification via the Cloudflare dashboard, you will need to have the Super Administrator or Administrator role.
You can also create a notification if you have the account edit role, which allows you create any type of notification.
An API token needs to have the [Notifications Read/Write permission](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) to create a notification,
Some notifications can only be created if you have a Professional, Business or Enterprise account or if you are using a particular Cloudflare product.
## Configure notifications
This guide will help you create, edit, test, or delete notifications using the Cloudflare dashboard.
### Create a notification
You can create a notification via the Cloudflare dashboard.
1. In the Cloudflare dashboard, go to the **Notifications** page.
[Go to **Notifications**](https://dash.cloudflare.com/?to=/:account/notifications)
2. Select **Add**.
3. On the notification you want to create, choose **Select**.
4. Name the notification.
5. Enter an email address to receive the notifications.
Note
Professional and Business plans will have access to more notifications and PagerDuty. Accounts with a paid service will additionally have access to webhooks.
1. (Optional) Specify any additional options for the notification, if required. For example, some notifications require that you select one or more domains or services.
2. Select **Create**.
The browser will navigate back to the list of notifications, where the new notification will appear as **Enabled**.
### Edit a notification
You can edit existing Notifications via the Cloudflare dashboard.
1. In the Cloudflare dashboard, go to the **Notifications** page.
[Go to **Notifications**](https://dash.cloudflare.com/?to=/:account/notifications)
2. On the notification that you want to modify, select **Edit**.
3. Make your changes as needed and select **Save**.
The browser will navigate back to the list of notifications.
### Disable or delete a notification
You can delete or disable existing Notifications via the Cloudflare dashboard.
1. In the Cloudflare dashboard, go to the **Notifications** page.
[Go to **Notifications**](https://dash.cloudflare.com/?to=/:account/notifications)
2. On the notification that you want to disable, select the **Enabled** toggle. To delete it, select **Delete**.
### Test a notification
To verify that notifications will be sent to the correct location or to view which details are available, you can test a notification by selecting **Test** on any enabled notification.
This action sends a notification with fake data.
---
title: Available Notifications · Cloudflare Notifications docs
description: Available Notifications depend on your Cloudflare plan. Cloudflare
offers a variety of Notifications for our products and services, such as
Billing, Denial of Service protection, Magic Transit, and SSL/TLS.
lastUpdated: 2025-05-22T15:53:35.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/notifications/notification-available/
md: https://developers.cloudflare.com/notifications/notification-available/index.md
---
Available Notifications depend on your Cloudflare plan. Cloudflare offers a variety of Notifications for our products and services, such as [Billing](https://developers.cloudflare.com/billing/), [Denial of Service protection](https://developers.cloudflare.com/ddos-protection/), [Magic Transit](https://developers.cloudflare.com/magic-transit/), and [SSL/TLS](https://developers.cloudflare.com/ssl/).
Depending on your plan, you can also configure webhooks, allowing you to connect your account with external services such as Slack and Google Chat, and PagerDuty to receive Cloudflare Notifications.
## Actions available on receiving a Notification
Each Notification carries different types of information about the status of your Cloudflare account, or the type of action you can take.
Refer to information below to understand what each Notification does and what to do when receiving one.
## Billing
Usage Based Billing
**Who is it for?**
Customers who want to receive a notification when the usage of a product goes above a set level.
**Other options / filters**
You can choose the product that you want to be notified about and the threshold that fires the notification. Thresholds depend on the product chosen.
For example:
* Argo Smart Routing has **Notify when total bytes of traffic exceeds** as a threshold.
* Load Balancing has **Notify when total number of DNS Queries exceeds** as a threshold.
**Included with**
Professional plans or higher.
**What should you do if you receive one?**
Review your product usage and adjust the configuration and/or increase the alerting threshold.
## Bots
Bot Detection Alert
**Who is it for?**
Enterprise customers who want to be notified when Cloudflare detects a spike in bot traffic on their zones.
**Other options / filters**
None.
**Included with**
Accounts with at least one Enterprise zone.
**What should you do if you receive one?**
Select the [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) link enclosed in the alert message. Contact support if additional advice is needed on how to investigate the attack further.
**Additional information**
After an alert is created on the dashboard, it may take up to 30 minutes before sufficient data is available to begin detecting traffic anomalies. Verified bot traffic is excluded from bot alerts.
Custom Bot Detection Alert
**Who is it for?**
Enterprise customers who want to be notified when Cloudflare detects a spike in bot traffic on their zones.
**Other options / filters**
Refer to the [alert logic](https://developers.cloudflare.com/bots/reference/alerts/#alert-logic) for more information on additional filters or groupings.
**Included with**
Accounts with at least one Enterprise zone.
**What should you do if you receive one?**
Select the [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) link enclosed in the alert message. Contact support if additional advice is needed on how to investigate the attack further.
**Additional information**
After an alert is created on the dashboard, it may take up to 30 minutes before sufficient data is available to begin detecting traffic anomalies. Verified bot traffic is excluded from both basic and advanced bot alerts.
Alerts with grouping could cause potential noise if you set them up for a high-traffic zone. Grouping alerts function as if you set up separate policies with a filter for each value. Alerts may trigger multiple values in the same group as long as the traffic for each value reaches the threshold of 200.
## Cloudflare Access
Expiring Access Service Token Alert
**Who is it for?**
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) customers who want to receive a notification when their service token is about to expire.
**Other options / filters**
None.
**Included with**
Purchase of Access
**What should you do if you receive one?**
Extend the expiration date of the service token. For more details, refer to [Renew your service token](https://developers.cloudflare.com/cloudflare-one/access-controls/service-credentials/service-tokens/#renew-service-tokens).
## Cloudflare Images
Image Notifications
**Who is it for?**
Customers using [Direct creator uploads](https://developers.cloudflare.com/images/upload-images/direct-creator-upload/) to upload images.
**Other options / filters**
None.
**Included with**
Cloudflare images subscription.
**What should you do if you receive one?**
No action is needed.
Image Transformation Notifications
**Who is it for?**
Customers who are using free image transformations and want to be notified if they exceed their free quota.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
No action is needed.
## Cloudflare Status
Maintenance Notification
**Who is it for?**
Customers interested in knowing about planned [Cloudflare maintenance](https://developers.cloudflare.com/support/troubleshooting/disruptive-maintenance/) for specific data centers. The notification lets you know when maintenance has been scheduled, changed, or canceled on an entire point of presence.
**Other options / filters**
You can filter maintenance notifications for specific points of presence and updates (scheduled, changed, canceled).
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
If the notification is announcing new scheduled maintenance, you may want to add the maintenance to your calendar. During these maintenance windows, you may experience a slight increase in latency to the edge location which is under maintenance.
Incident Alerts
**Who is it for?**
Customers interested in knowing about Cloudflare incidents. The notification lets you know when Cloudflare incidents are created, updated, and resolved.
**Other options / filters**
You can filter incident alerts to specific impact levels (minor, major, critical).
Additionally, incident alerts can be filtered to incidents affecting specific components. By default, incident alerts will trigger a notification for incident updates across all impact levels and components.
The impact level and affected components of an incident may change as the incident progresses. A notification will only be sent if the configured filters match at the time of the incident update. Updates will not be sent retroactively.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
Review your [analytics](https://developers.cloudflare.com/analytics/) page to see if your domain is impacted.
## DDoS Protection
HTTP DDoS Attack Alert
**Who is it for?**
[WAF](https://developers.cloudflare.com/waf/) or [CDN](https://developers.cloudflare.com/cache/) customers who want to receive a notification when Cloudflare has mitigated HTTP attacks that generate more than 100 requests per second.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
No action needed. Refer to [DDoS alerts](https://developers.cloudflare.com/ddos-protection/reference/alerts/) for more information.
Layer 3/4 DDoS Attack Alert
**Who is it for?**
[BYOIP](https://developers.cloudflare.com/byoip/) and [Spectrum](https://developers.cloudflare.com/spectrum/) customers with [Network Analytics](https://developers.cloudflare.com/analytics/network-analytics/) who want to receive a notification when Cloudflare has mitigated attacks that generate an average of at least 12,000 packets per second over a five-second period, with a duration of one minute or more.
**Other options / filters**
None.
**Included with**
Purchase of Magic Transit and/or BYOIP.
**What should you do if you receive one?**
No action needed. Refer to [DDoS alerts](https://developers.cloudflare.com/ddos-protection/reference/alerts/) for more information.
Advanced HTTP DDoS Attack Alert
**Who is it for?**
[WAF](https://developers.cloudflare.com/waf/) or [CDN](https://developers.cloudflare.com/cache/) customers with the [Advanced DDoS Protection](https://developers.cloudflare.com/ddos-protection/) subscription who want to receive a notification when Cloudflare has mitigated attacks that generate more than the configured number of requests per second (100 rps by default).
**Other options / filters**
You can choose when to trigger a notification.
Available filters include:
* The zones in the account for which you wish to receive notifications.
* The specific hostnames for which you wish to receive notifications.
* The minimum requests-per-second rate that will trigger the alert (100 rps by default).
**Included with**
Enterprise plans with the Advanced DDoS Protection add-on.
**What should you do if you receive one?**
No action needed. Refer to [DDoS alerts](https://developers.cloudflare.com/ddos-protection/reference/alerts/) for more information.
Advanced Layer 3/4 DDoS Attack Alert
**Who is it for?**
[BYOIP](https://developers.cloudflare.com/byoip/) and [Magic Transit](https://developers.cloudflare.com/magic-transit/) customers with [Network Analytics](https://developers.cloudflare.com/analytics/network-analytics/) who want to receive a notification when Cloudflare has mitigated attacks that generate more than the configured number of packets per second (12,000 pps by default).
**Other options / filters**
You can choose when to trigger a notification.
Available filters include:
* The IP prefixes for which you wish to receive notifications.
* The specific IP addresses for which you wish to receive notifications.
* The minimum packets-per-second rate that will trigger the alert (12,000 pps by default).
* The minimum megabits-per-second rate that will trigger the alert.
* The protocols for which you wish to receive notifications (all protocols by default).
If you specify multiple filters, Cloudflare applies an `AND` logic. This means the alert will only trigger if all filters you set are true. Keep this in mind when setting up this alert with more than one filter.
**Included with**
Purchase of Magic Transit and/or BYOIP (Enterprise plans).
**What should you do if you receive one?**
No action needed. Refer to [DDoS alerts](https://developers.cloudflare.com/ddos-protection/reference/alerts/) for more information.
## DEX
Device connectivity anomaly
**Who is it for?**
Zero Trust customers who want to be notified when Cloudflare detects a spike or drop in the number of devices connected to the WARP client.
**Other options / filters**
* **Alert configuration**: Choose when to trigger a notification. Available options are *Connectivity spike*, *Connectivity drop*, and *Connectivity spike or drop*.
* Filters:
* **Colo**: Cloudflare data center that the device is connected to.
* **Platform**: Operating system of the device.
* **Version**: WARP client version (for example, `2024.3.409.0`).
* **Mode**: [WARP mode](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/configure-warp/warp-modes/) deployed on the device.
**Included with**
All Cloudflare Zero Trust plans.
**What should you do if you receive one?**
Review your [fleet status](https://developers.cloudflare.com/cloudflare-one/insights/dex/fleet-status/) to investigate why the spike or drop occurred and which devices are impacted.
**Additional information**
To learn more about the alert logic, refer to [Z-score](https://developers.cloudflare.com/cloudflare-one/insights/dex/notifications/#z-score).
DEX test latency
**Who is it for?**
Zero Trust customers who wish to receive alerts when there is a spike or drop in application latency, as measured by the HTTP test [Resource Fetch time](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/http/#test-results) or Traceroute test [Round trip time](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/traceroute/#test-results). Requires setting up a [DEX test](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/).
**Other options / filters**
* **Alert configuration**: Choose when to trigger a notification. Available options are *Latency spike*, *Latency drop*, and *Latency spike or drop*.
* Filters:
* **Colo**: Cloudflare data center that the device is connected to.
* **Platform**: Operating system of the device.
* **Version**: WARP client version (for example, `2024.3.409.0`).
* **Test name**: Choose which DEX test the alert should monitor. You will receive individual notifications for each test.
**Included with**
All Cloudflare Zero Trust plans.
**What should you do if you receive one?**
View your [test results](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/view-results/) to investigate why the spike occurred.
**Additional information**
To learn more about the alert logic, refer to [Z-score](https://developers.cloudflare.com/cloudflare-one/insights/dex/notifications/#z-score).
DEX test low availability
**Who is it for?**
Zero Trust customers who wish to receive alerts when the percentage of successful HTTP or traceroute requests to an application drops below the selected service-level objective (SLO). Requires setting up a [DEX test](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/).
**Other options / filters**
* **Service Level Objective (SLO)**: Specify the availability threshold that will trigger an alert. Enter a percentage in `xx.x` format (for example, `98.0`).
* Filters:
* **Colo**: Cloudflare data center that the device is connected to.
* **Platform**: Operating system of the device.
* **Version**: WARP client version (for example, `2024.3.409.0`).
* **Test name**: Choose which DEX test the alert should monitor. You will receive individual notifications for each test.
**Included with**
All Cloudflare Zero Trust plans.
**What should you do if you receive one?**
View your [test results](https://developers.cloudflare.com/cloudflare-one/insights/dex/tests/view-results/) to investigate why the degradation occurred.
**Additional information**
To learn more about the alert logic, refer to [SLO](https://developers.cloudflare.com/cloudflare-one/insights/dex/notifications/#slo).
## DNS
Secondary DNS all Primaries Failing
**Who is it for?**
Enterprise customers who have at least one secondary zone in their account and want to receive a notification if all of their primary nameservers are failing.
**Other options / filters**
None.
**Included with**
Purchase of Secondary DNS
**What should you do if you receive one?**
1. Confirm that your primary nameservers are up and running.
2. Confirm that the [Access Control Lists (ACLs)](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/access-control-lists/cloudflare-ip-addresses/) on your primary nameservers are configured correctly.
3. Confirm that your primary nameservers are configured correctly in your Cloudflare account (correct IP, port, TSIG).
Secondary DNS Primaries Failing
**Who is it for?**
Enterprise customers who have at least one secondary zone and want to receive a notification if at least one of their primary nameservers is failing while transfers from at least one other primary are still successful.
**Other options / filters**
None.
**Included with**
Purchase of Secondary DNS.
**What should you do if you receive one?**
1. Confirm that your primary nameservers are up and running.
2. Confirm that the [Access Control Lists (ACLs)](https://developers.cloudflare.com/dns/zone-setups/zone-transfers/access-control-lists/cloudflare-ip-addresses/) on your primary nameservers are configured correctly.
3. Confirm that your primary nameservers are configured correctly in your Cloudflare account (correct IP, port, TSIG).
Secondary DNS Successfully Updated
**Who is it for?**
Enterprise customers who have at least one secondary zone in their account and want to receive a notification on successful zone transfers.
**Other options / filters**
None.
**Included with**
Purchase of Secondary DNS.
**What should you do if you receive one?**
No action needed. Everything is working correctly.
Secondary DNS Warning
**Who is it for?**
Customers who are using Cloudflare for Secondary DNS and want to receive notifications about warnings issued by the transferred zone.
**Other options / filters**
None.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
Actions for failure notifications will depend on the type of failure.
## Health Checks
Health Checks status notification
**Who is it for?**
Customers who want to be warned about changes to server health as determined by [health checks](https://developers.cloudflare.com/health-checks/).
**Other options / filters**
Available filters include:
* You can search for and add health checks from your list of health checks.
* You can choose a trigger to fire the notification when your server becomes **unhealthy**, **healthy**, or **either healthy or unhealthy**.
**Included with**
Professional plans or higher.
**What should you do if you receive one?**
Review your [health check analytics](https://developers.cloudflare.com/health-checks/health-checks-analytics/#common-error-codes).
## Load Balancing
Pool Enablement
**Who is it for?**
Customers who want to be warned about status changes (enabled/disabled) in their pools.
**Other options / filters**
Available filters include:
* You can search for and add pools from your list of pools. If no pools are selected, the alert will apply to all pools in the account.
* You can also choose the trigger that fires the notification when the Load Balancing pool is **enabled**, **disabled**, and **either enabled or disabled**.
**Included with**
Purchase of [Load Balancing](https://developers.cloudflare.com/load-balancing/get-started/enable-load-balancing/).
**What should you do if you receive one?**
No action is needed.
Load Balancing Health Alert
**Who is it for?**
Customers who want to be warned about [changes in health status](https://developers.cloudflare.com/load-balancing/understand-basics/health-details/) in their pools or origins.
**Other options / filters**
Available filters include:
* You can search for and add pools from your list of pools, as well as **Include future pools** (if all pools are selected).
* You can choose the trigger that fires the notification when the health status becomes **unhealthy**, **healthy**, or **either unhealthy or healthy**
* You can choose the trigger that fires the notification when the event source health status changes in **pool**, **origin**, or **either pool or origin**.
**Included with**
Purchase of [Load Balancing](https://developers.cloudflare.com/load-balancing/get-started/enable-load-balancing/).
**What should you do if you receive one?**
Evaluate [load balancing analytics](https://developers.cloudflare.com/load-balancing/reference/load-balancing-analytics/) to review changes in health status over time.
## Logpush
Failing Logpush Job Disabled
**Who is it for?**
Enterprise customers who use [Logpush](https://developers.cloudflare.com/logs/) and want to monitor their job health.
**Other options / filters**
* Notification Name: A custom name for the notification.
* Description (optional): A custom description for the notification.
* Notification Email (can be multiple emails): The email address of the recipient for the notification.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
In the email for the notification, you can find the destination name for the failing Logpush job. With this destination name, you should be able to figure out which zone this relates to. There can be multiple reasons why a job fails, but it is best to test that the destination endpoint is healthy, and that necessary credentials are still working. You can also check that the destination has allowlisted [Cloudflare IPs](https://www.cloudflare.com/ips/).
## Magic Transit
Magic Network Monitoring - Auto Advertisement
**Who is it for?**
[Magic Transit on-demand](https://developers.cloudflare.com/magic-transit/on-demand/) customers who use Flow-Based Monitoring and want alerts when Magic Transit is automatically enabled.
**Other options / filters**
None.
**Included with**
Purchase of Magic Transit.
**What should you do if you receive one?**
No action is needed. You can go to the [Cloudflare dashboard](https://dash.cloudflare.com/?to=/:account/magic-transit) to review the health and status of your tunnels.
Magic Network Monitoring - DDoS Attack
**Who is it for?**
[BYOIP](https://developers.cloudflare.com/byoip/) and [Spectrum](https://developers.cloudflare.com/spectrum/) customers with [Network Analytics](https://developers.cloudflare.com/analytics/network-analytics/) who want to receive a notification when Cloudflare has mitigated attacks that generate an average of at least 12,000 packets per second over a five-second period, with a duration of one minute or more.
**Other options / filters**
None.
**Included with**
Purchase of Magic Transit and/or BYOIP.
**What should you do if you receive one?**
No action needed. Refer to [DDoS alerts](https://developers.cloudflare.com/ddos-protection/reference/alerts/) for more information.
Magic Network Monitoring - Volumetric Attack
**Who is it for?**
[Magic Transit on-demand](https://developers.cloudflare.com/magic-transit/on-demand/) customers who are using Flow-Based Monitoring to detect attacks when Magic Transit is disabled.
**Other options / filters**
None.
**Included with**
Purchase of Magic Transit.
**What should you do if you receive one?**
If you do not have auto advertisement enabled, you need to advertise your IP prefixes to enable Magic Transit. For more information, refer to [Dynamic advertisement](https://developers.cloudflare.com/byoip/concepts/dynamic-advertisement/).
Magic Tunnel Health Check Alert
**Who is it for?**
Magic Transit and Magic WAN customers who wish to receive alerts when the percentage of tunnel states meeting the selected service-level objective (SLO) drops below the defined threshold for a Magic Tunnel.
**Other options / filters**
* Notification Name: A custom name for the notification.
* Description (optional): A custom description for the notification.
* Notification Email (can be multiple emails): The email address of recipient for the notification.
* Webhooks
* Tunnels: Choose one or more tunnels to monitor.
* SLO: Define SLO threshold for Magic Tunnel health alerts. Available options are *High*, *Medium*, and *Low*.
**Included with**
Purchase of Magic Transit and Magic WAN.
**What should you do if you receive one?**
Refer to the [Magic Transit tunnel health](https://developers.cloudflare.com/magic-transit/network-health/check-tunnel-health-dashboard/) or [Magic WAN tunnel health](https://developers.cloudflare.com/magic-wan/configuration/common-settings/check-tunnel-health-dashboard/) for more information on what the issue might be.
## Network Interconnect
Connection Maintenance Alert
**Who is it for?**
[Classic CNI](https://developers.cloudflare.com/network-interconnect/classic-cni/) customers who want to be alerted to maintenance events that might affect Classic CNI.
**Other options / filters**
None.
**Included with**
Purchase of Cloudflare Network Interconnect (CNI).
**What should you do if you receive one?**
No action is needed.
## Page Shield
Page Shield New Code Change Detection Alert
**Who is it for?**
[Page Shield](https://developers.cloudflare.com/page-shield/) customers who want to receive a notification when JavaScript dependencies change in the pages of their domain.
**Other options / filters**
None.
**Included with**
Enterprise plans with paid add-on.
**What should you do if you receive one?**
Investigate to confirm that it is an expected change.
**Additional information**
Triggered daily. If configured with a zone filter, the alert is triggered immediately.
Page Shield New Domain Alert
**Who is it for?**
[Page Shield](https://developers.cloudflare.com/page-shield/) customers who want to receive a notification when resources from new host domains appear in their domain.
**Other options / filters**
None.
**Included with**
Business plans or higher.
**What should you do if you receive one?**
Investigate to confirm that it is an expected change.
**Additional information**
Triggered hourly. If configured with a zone filter, the alert is triggered immediately.
Page Shield New Malicious Domain Alert
**Who is it for?**
[Page Shield](https://developers.cloudflare.com/page-shield/) customers who want to receive a notification when resources from a known malicious domain appear in their domain. For more information, refer to [Malicious script and connection detection](https://developers.cloudflare.com/page-shield/how-it-works/malicious-script-detection/).
**Other options / filters**
None.
**Included with**
Enterprise plans with paid add-on.
**What should you do if you receive one?**
Review the information in the Page Shield dashboard about the detected malicious resources, then update the pages where those resources were detected.
For more information, refer to [Review scripts and connections considered malicious](https://developers.cloudflare.com/page-shield/detection/review-malicious-scripts/).
Page Shield New Malicious Script Alert
**Who is it for?**
[Page Shield](https://developers.cloudflare.com/page-shield/) customers who want to receive a notification when Cloudflare classifies JavaScript dependencies in their domain as malicious. For more information, refer to [Malicious script and connection detection](https://developers.cloudflare.com/page-shield/how-it-works/malicious-script-detection/).
**Other options / filters**
None.
**Included with**
Enterprise plans with paid add-on.
**What should you do if you receive one?**
Review the information in the Page Shield dashboard about the detected malicious resources, then update the pages where those resources were detected.
For more information, refer to [Review scripts and connections considered malicious](https://developers.cloudflare.com/page-shield/detection/review-malicious-scripts/).
Page Shield New Malicious URL Alert
**Who is it for?**
[Page Shield](https://developers.cloudflare.com/page-shield/) customers who want to receive a notification when resources from a known malicious URL appear in their domain. For more information, refer to [Malicious script and connection detection](https://developers.cloudflare.com/page-shield/how-it-works/malicious-script-detection/).
**Other options / filters**
None.
**Included with**
Enterprise plans with paid add-on.
**What should you do if you receive one?**
Review the information in the Page Shield dashboard about the detected malicious resources, then update the pages where those resources were detected.
For more information, refer to [Review scripts and connections considered malicious](https://developers.cloudflare.com/page-shield/detection/review-malicious-scripts/).
Page Shield New Resources Alert
**Who is it for?**
[Page Shield](https://developers.cloudflare.com/page-shield/) customers who want to receive a notification when new resources appear in their domain.
**Other options / filters**
None.
**Included with**
Business plans or higher.
**What should you do if you receive one?**
Investigate to confirm that it is an expected change.
**Additional information**
Triggered daily. If configured with a zone filter, the alert is triggered immediately.
Page Shield New Resource Exceeds Max URL Length Alert
**Who is it for?**
[Page Shield](https://developers.cloudflare.com/page-shield/) customers who want to receive a notification when a resource's URL exceeds the maximum allowed length.
**Other options / filters**
None.
**Included with**
Business plans or higher.
**What should you do if you receive one?**
Manually check the resource.
## Pages
Project updates
**Who is it for?**
Customers who want to receive notifications about project-level events in [Cloudflare Pages](https://developers.cloudflare.com/pages/).
**Other options / filters**
Available filters include:
* Pages projects
* Environments
* Different events: **Deployment started**, **Deployment failed**, or **Deployment success**
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
For failed deployments, review our [debugging guide](https://developers.cloudflare.com/pages/configuration/debugging-pages/#check-your-build-log).
## Radar
Radar Alerts
**Who is it for?**
Customers who want to receive a notification when traffic anomalies, outages, route hijacks, or route leaks are impacting one or more countries, regions, or autonomous systems (ASNs) of interest.
**Other options / filters**
Filters include:
* Notification type (anomaly, outage, route hijack, route leak)
* Location (country or region)
* Autonomous systems (ASNs)
You have the option to send the notification via email, webhook, or PagerDuty.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
Further action will depend on your role. Refer to the [Radar documentation](https://developers.cloudflare.com/radar/) for more information.
## Route Leak Detection
Route Leak Detection Alert
**Who is it for?**
[BYOIP customers](https://developers.cloudflare.com/byoip/) who want to receive a notification when their prefixes are advertised in places they should not be.
**Other options / filters**
None.
**Included with**
Purchase of BYOIP.
**What should you do if you receive one?**
Confirm your traffic is healthy. Reach out to your transit providers to ensure you are behaving as expected and ask them to follow up with any providers accepting the unauthorized routes.
## SSL/TLS
Access mTLS Certificate Expiration Alert
**Who is it for?**
[Access](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) customers that use client certificates for mutual TLS authentication. This notification will be sent 30 and 14 days before the expiration of the certificate.
**Other options / filters**
None.
**Included with**
Purchase of [Access](https://developers.cloudflare.com/cloudflare-one/access-controls/service-credentials/mutual-tls-authentication/) and/or [Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/enforce-mtls/).
**What should you do if you receive one?**
Upload a [renewed certificate](https://developers.cloudflare.com/cloudflare-one/access-controls/service-credentials/mutual-tls-authentication/#add-mtls-authentication-to-your-access-configuration).
Advanced Certificate Alert
**Who is it for?**
Customers with [advanced certificates](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/) that want to be alerted on validation, issuance, renewal, and expiration of certificates.
**Other options / filters**
None.
**Included with**
When an advanced certificate is validated, issued, renewed, or expired.
**What should you do if you receive one?**
Action only needed if notification is about a certificate that failed to be issued. Refer to [SSL expired or SSL mismatch errors](https://developers.cloudflare.com/ssl/troubleshooting/version-cipher-mismatch/) for more information.
Hostname-level Authenticated Origin Pulls Certificate Expiration Alert
**Who is it for?**
Customers that upload their own certificate to use with hostname-level Authenticated Origin Pull (AOP) to secure connections from Cloudflare to their origin server. AOP certificate expiration notifications are sent 30 days and 14 days before the certificate expiry.
**Other options / filters**
None.
**Included with**
Authenticated Origin Pull.
**What should you do if you receive one?**
Upload a renewed certificate to use for [hostname-level AOP](https://developers.cloudflare.com/ssl/origin-configuration/authenticated-origin-pull/set-up/per-hostname/).
SSL for SaaS Custom Hostnames Alert
**Who is it for?**
Customers with custom hostname certificates who want to receive a notification on validation, issuance, renewal, and expiration of certificates. For more details around data formatting for webhooks, refer to the [Cloudflare for SaaS docs](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/webhook-definitions/).
**Other options / filters**
None.
**Included with**
Purchase of [Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/).
**What should you do if you receive one?**
You only need to take action if you are notified that you have a certificate that failed. You can find the reasons why a certificate is not being issued in [Troubleshooting SSL errors](https://developers.cloudflare.com/ssl/troubleshooting/general-ssl-errors/).
Universal SSL Alert
**Who is it for?**
Customers with universal certificates who want to receive a notification on validation, issuance, renewal, and expiration notices.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
You only need to take action if you are notified that you have a certificate that failed. You can find the reasons why a certificate is not being issued in [Troubleshooting SSL errors](https://developers.cloudflare.com/ssl/troubleshooting/general-ssl-errors/).
Zone-level Authenticated Origin Pulls Certificate Expiration Alert
**Who is it for?**
Customers that upload their own certificate to use with zone-level Authenticated Origin Pull (AOP) to secure connections from Cloudflare to their origin server. AOP certificate expiration notifications are sent 30 days and 14 days before the certificate expiry.
**Other options / filters**
None.
**Included with**
Authenticated Origin Pull.
**What should you do if you receive one?**
Upload a renewed certificate to use for [zone-level AOP](https://developers.cloudflare.com/ssl/origin-configuration/authenticated-origin-pull/set-up/).
mTLS Certificate Store Certificate Expiration Alert
**Who is it for?**
Customers that upload their own client certificates for mTLS via [bring your own CA](https://developers.cloudflare.com/ssl/client-certificates/byo-ca/).
This notification will be sent 30 and 14 days before the expiration of the certificate.
**Other options / filters**
None.
**Included with**
[Bring your own CA](https://developers.cloudflare.com/ssl/client-certificates/byo-ca/).
The mTLS Certificate Store refers to customer uploaded certificates and does not include client certificates generated with the [Cloudflare CA](https://developers.cloudflare.com/ssl/client-certificates/#how-it-works).
**What should you do if you receive one?**
Upload a renewed certificate.
## Security Center
Brand Protection Alerts
**Who is it for?**
Customers who want a summary of activity related to [Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/).
**Other options / filters**
You can set up Brand Protection Alerts on individual monitored queries. For more details, refer to [Brand Protection Alerts](https://developers.cloudflare.com/security-center/brand-protection/#brand-protection-alerts).
**Included with**
Professional plans or higher.
**What should you do if you receive one?**
Investigate and potentially block any suspicious domains that may be trying to impersonate your brand.
Brand Protection Digest
**Who is it for?**
Customers who want a summary of activity related to [Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/).
**Other options / filters**
You can set up Brand Protection Digest on individual monitored queries. For more details, refer to [Brand Protection Alerts](https://developers.cloudflare.com/security-center/brand-protection/#brand-protection-alerts).
**Included with**
Professional plans or higher.
**What should you do if you receive one?**
Investigate and potentially block any suspicious domains that may be trying to impersonate your brand.
Logo Match Alerts
**Who is it for?**
Customers who want to receive a notification when the [Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/) system detects a new domain which is using the uploaded logo and might be infringing copyright.
**Other options / filters**
You can select the query that you want to be alerted on.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
Review the domains and URLs that are potentially impersonating your brand.
Security Insights
**Who is it for?**
Customers who want to receive notifications based on security insights findings.
**Other options / filters**
You can select the insight(s) you want to be alerted on.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
Review the insight and decide whether you want to resolve it, archive it, or export it.
Abuse report
**Who is it for?**
Customers who want to be alerted in the event that an abuse report is filed against their website.
**Other options / filters**
You can filter the reports based on date, report status, report type, and domain.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
View our guidance on [customer abuse report obligations](https://developers.cloudflare.com/fundamentals/reference/report-abuse/abuse-report-obligations/) and more information on how to [view and submit abuse reports](https://developers.cloudflare.com/fundamentals/reference/report-abuse/submit-report/).
## Stream
Stream Live Notifications
**Who is it for?**
Customers who are using [Stream](https://developers.cloudflare.com/stream/) and want to receive webhooks with the status of their videos.
**Other options / filters**
You can input Stream Live IDs to receive notifications only about those inputs. If left blank, you will receive a list for all inputs.
The following input states will fire notifications. You can toggle them on or off:
* `live_input.connected`
* `live_input.disconnected`
**Included with**
Stream subscription.
**What should you do if you receive one?**
Stream notifications are entirely customizable by the customer. Action will depend on the customizations enabled.
## Traffic Monitoring
Advanced Error Rate Alert
**Who is it for?**
Enterprise customers who want to receive a notification when Cloudflare detects edge and/or origin errors. Refer to [HTTP Traffic Alerts](https://developers.cloudflare.com/notifications/reference/traffic-alerts/) for more information.
**Other options / filters**
Available filters include:
* You can search and add domains from your list of domains.
* You can filter alerts by **edge status code**, **origin status code**, and the **IP Address**.
* You can also choose the trigger that fires the notification. Available triggers are **low sensitivity**, **medium sensitivity**, **high sensitivity**, or **very high sensitivity**.
You can also toggle Alert Grouping to receive separate alerts for your domain, edge status code, and/or origin status code.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
1. Use the link in the notification you received to see which error codes Cloudflare is seeing.
2. Depending on the statuses you are alerting on, refer to [Troubleshooting Cloudflare 5XX errors](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/cloudflare-5xx-errors/).
**Limitations**
Traffic Monitoring alerts are not sent for each individual events, but only when a spike in traffic reaches the threshold for an alert to be sent.
These thresholds cannot be configured. Service level objectives (SLOs) are used to determine the threshold.
Origin Error Rate Alert
**Who is it for?**
Enterprise customers who want to receive a notification when Cloudflare is unable to access their origin server. Refer to [HTTP Traffic Alerts](https://developers.cloudflare.com/notifications/reference/traffic-alerts/) for more information.
**Other options / filters**
Multiple filters available:
* You can search and add domains from your list of domains.
* You can also choose the trigger that fires the notification. Available triggers are **low sensitivity**, **medium sensitivity**, **high sensitivity**, or **very high sensitivity**.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
1. Use the link in the Notification you received to see which error codes Cloudflare is seeing from your origin.
2. Refer to [Troubleshooting Cloudflare 5XX errors](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/cloudflare-5xx-errors/) to learn how to troubleshoot these errors.
**Limitations**
Traffic Monitoring alerts are not sent for each individual events, but only when a spike in traffic reaches the threshold for an alert to be sent.
These thresholds cannot be configured. Service level objectives (SLOs) are used to determine the threshold.
Passive Origin Monitoring
**Who is it for?**
Customers who want to receive a notification when Cloudflare is unable to access their origin. Customers will only receive this notification when their origin is returning a `521` error.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
Refer to [Troubleshooting Cloudflare 5XX errors](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/cloudflare-5xx-errors/) to learn how to troubleshoot these errors.
**Limitations**
Traffic Monitoring alerts are not sent for each individual events, but only when a spike in traffic reaches the threshold for an alert to be sent.
For every account with this alert set up, you will not receive duplicate alerts within the same four-hour time frame. The alert received will contain the most recent set of origins returning 521s.
Traffic Anomalies Alert
**Who is it for?**
Enterprise customers who want to receive a notification when one zone is experiencing an unexpected spike or drop in traffic. Refer to [HTTP Traffic Alerts](https://developers.cloudflare.com/notifications/reference/traffic-alerts/) for more information.
**Other options / filters**
Multiple filters available:
* You can search and add domains from your list of domains.
* You can include or exclude traffic mitigated by the [Web Application Firewall (WAF)](https://developers.cloudflare.com/waf/).
* You can choose whether to be notified of either spikes or drops in traffic.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
Use the link in the Notification you received to view if the spike or drop is significant enough to require further actions.
**Limitations**
Traffic Monitoring alerts are not sent for each individual events, but only when a spike in traffic reaches the threshold for an alert to be sent.
These thresholds cannot be configured. Z-score is used to determine the threshold.
## Trust and Safety Blocks
Block Review Rejection
**Who is it for?**
Customers who want to be notified when Cloudflare Trust & Safety rejects a request for block removal.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
Take care of any abuse on your website. Then, go to the [Cloudflare dashboard](https://dash.cloudflare.com/) and request a review.
New Blocks
**Who is it for?**
Customers who want to be notified when Cloudflare Trust & Safety places a block on their website.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
Take care of any abuse on your website. Then, go to the [Cloudflare dashboard](https://dash.cloudflare.com/) and request a review.
Removed Blocks
**Who is it for?**
Customers who want to be notified when Cloudflare Trust & Safety removes a block from their website.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
This is informational follow up.
## Tunnel
Tunnel Creation or Deletion Event
**Who is it for?**
Customers who want to receive a notification when Cloudflare Tunnels are created or deleted in their account.
**Other options / filters**
None.
**Included with**
All Cloudflare Zero Trust plans.
**What should you do if you receive one?**
No action is needed.
Tunnel Health Alert
**Who is it for?**
Customers who want to be warned about changes in health status for their Cloudflare Tunnels.
**Other options / filters**
None.
**Included with**
All Cloudflare Zero Trust plans.
**What should you do if you receive one?**
Monitor tunnel health over time and consider deploying [`cloudflared` replicas or load balancers](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/configure-tunnels/tunnel-availability/).
**Additional information**
Refer to [Tunnel status](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/troubleshoot-tunnels/common-errors/#tunnel-status) to review the list of possible tunnel statuses (`Healthy`, `Inactive`, `Down` and `Degraded`).
## Web Analytics
Weekly summary
**Who is it for?**
Customers using [Web Analytics](https://developers.cloudflare.com/web-analytics/) to monitor their website's performance.
**Other options / filters**
None.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
No action is needed. This notification is a weekly summary with reports from your Web Analytics account. Refer to [Notifications](https://dash.cloudflare.com/?to=/:account/notifications) in the Cloudflare dashboard to refine your notifications settings.
## Web Application Firewall (WAF)
Advanced Security Events Alert
**Who is it for?**
Enterprise customers who want to receive alerts about spikes in specific services that generate log entries in [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/). For more information, refer to [WAF alerts](https://developers.cloudflare.com/waf/reference/alerts/).
**Other options / filters**
A mandatory [`filters`](https://developers.cloudflare.com/api/resources/alerting/subresources/policies/methods/create/) selection is needed when you create a notification policy which includes the list of services and zones that you want to be alerted on.
* You can search for and add domains from your list of Enterprise zones.
* You can choose which services the alert should monitor (Managed Firewall, Rate Limiting, etc.).
* You can filter events by a targeted action.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
Review the information in [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/) to identify any possible attack or misconfiguration.
**Additional information**
The mean time to detection is five minutes.
When setting up this alert, you can select the services that will be monitored. Each selected service is monitored separately and can be selected as a filter.
**Limitations**
Security Events (WAF) alerts are not sent for each individual events, but only when a spike in traffic reaches the threshold for an alert to be sent.
These thresholds cannot be configured. Z-score is used to determine the threshold.
Security Events Alert
**Who is it for?**
Business and Enterprise customers who want to receive alerts about spikes across all services that generate log entries in [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/). For more information, refer to [WAF alerts](https://developers.cloudflare.com/waf/reference/alerts/).
**Other options / filters**
A mandatory [`filters`](https://developers.cloudflare.com/api/resources/alerting/subresources/policies/methods/create/) selection is needed when you create a notification policy which includes the list of zones that you want to be alerted on.
* You can also search for and add domains from your list of business or enterprise zones. The notification will be sent for the domains chosen.
* You can filter events by a targeted action.
**Included with**
Business and Enterprise plans.
**What should you do if you receive one?**
Review the information in [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/) to identify any possible attack or misconfiguration.
**Additional information**
The mean time to detection is five minutes.
When setting up this alert, you can select the services that will be monitored. Each selected service is monitored separately.
**Limitations**
Security Events (WAF) alerts are not sent for each individual events, but only when a spike in traffic reaches the threshold for an alert to be sent.
These thresholds cannot be configured. Z-score is used to determine the threshold.
---
title: Notification History · Cloudflare Notifications docs
description: Notification History is a log of notifications that have been sent
to your account via the Notifications service. Information contained in
Notification History includes the notification itself, when the notification
was sent, and who the notification was sent to.
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/notifications/notification-history/
md: https://developers.cloudflare.com/notifications/notification-history/index.md
---
Notification History is a log of notifications that have been sent to your account via the Notifications service. Information contained in Notification History includes the notification itself, when the notification was sent, and who the notification was sent to.
## How to access Notification History
Currently, customers can access Notification History [via the Cloudflare API](https://developers.cloudflare.com/api/resources/alerting/subresources/history/methods/list/). Using `GET`, customers can retrieve a list of history records for notifications sent to an account. The records are displayed for the last 30 or 90 days, based on the type of plan.
```txt
GET accounts/{account_id}/alerting/v3/history
```
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/alerting/v3/history?page=1&per_page=25" \
--header "Authorization: Bearer "
```
## Availability
Notification History is available on all plans. The amount of history clients have access to depends on the type of plan:
* **Free, Pro, and Business**: History from the past 30 days.
* **Enterprise**: History from the past 90 days.
Note
Customers will not be able to access Notification History from before 2021-10-11.
---
title: Reference · Cloudflare Notifications docs
description: "Refer to the following pages for more information about Notifications:"
lastUpdated: 2024-08-27T14:57:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/notifications/reference/
md: https://developers.cloudflare.com/notifications/reference/index.md
---
Refer to the following pages for more information about Notifications:
* [HTTP Traffic Alerts](https://developers.cloudflare.com/notifications/reference/traffic-alerts/)
* [Common errors](https://developers.cloudflare.com/notifications/reference/common-errors/)
* [Webhook payload schema](https://developers.cloudflare.com/notifications/reference/webhook-payload-schema/)
---
title: 404 - Page Not Found · Cloudflare Page Shield docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/404/
md: https://developers.cloudflare.com/page-shield/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Alerts · Cloudflare Page Shield docs
description: Cloudflare client-side resource alerts notify you when new scripts
are detected on your domain or when Cloudflare detects resources that are
likely malicious.
lastUpdated: 2025-09-15T09:51:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/alerts/
md: https://developers.cloudflare.com/page-shield/alerts/index.md
---
Note
New resource alerts require a Business plan or higher. Code change and malicious resource alerts require an Enterprise plan with a paid add-on. For details, refer to [Alert types](https://developers.cloudflare.com/page-shield/alerts/alert-types/).
Once you have activated Page Shield's client-side resource monitoring, you can set up one or more alerts informing you of relevant client-side changes on your zones.
You can configure unscoped or scoped alerts:
* **Unscoped alert**: An alert configured for all zones in your Cloudflare account. Unscoped alerts are trigged either daily, hourly, or immediately, depending on the [alert type](https://developers.cloudflare.com/page-shield/alerts/alert-types/).
* **Scoped alert**: An alert scoped to one or more zones. You must configure [policies](https://developers.cloudflare.com/page-shield/policies/) for the zones you select to receive any notifications. Scoped alerts are triggered immediately. Policy violations will not trigger an alert. For more information, refer to [Scoped alerts](#scoped-alerts).
For alerts sent at regular intervals, you might experience a delay between adding a new script and receiving an alert.
For instructions on configuring alerts, refer to [Configure an alert](https://developers.cloudflare.com/page-shield/alerts/configure/).
## Scoped alerts
Note
Applies to Enterprise customers with a paid add-on.
If you have configured [policies](https://developers.cloudflare.com/page-shield/policies/) in a zone, you can filter alert notifications according to those policies. These alerts are called scoped alerts.
When you create a scoped alert using the **Policies of these zones** alert filter, you will only receive the most relevant notifications based on the policies you configured.
For each scoped alert, Cloudflare does the following:
1. Check which policies in a zone are enabled, either in allow or in log mode.
2. For every enabled policy, compare the URL of the new or changed resource against the allowed sources in the policy.
3. If the resource is allowed by the policy, check if the new or modified resource should trigger the current alert.
4. If the alert should trigger, send an alert notification to the configured destinations.
When you create a scoped alert you will not receive notifications for resources that are not allowed by a policy (either [in allow or in log mode](https://developers.cloudflare.com/page-shield/policies/#policy-actions)). These are [policy violations](https://developers.cloudflare.com/page-shield/policies/violations/) that you can review in the dashboard, through GraphQL, or via Logpush.
Note
You will not receive notifications for a scoped alert in the following cases:
* No configured policies in the zone
* Policy is not enabled
For unscoped alerts, you will receive alerts for resources detected in all your zones, and you may receive alerts about resources that violate your configured policies.
---
title: Best practices · Cloudflare Page Shield docs
description: Best practices for using Page Shield.
lastUpdated: 2025-07-10T11:20:10.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/page-shield/best-practices/
md: https://developers.cloudflare.com/page-shield/best-practices/index.md
---
Review the topics below for best practices related to Page Shield's client-side resource monitoring:
* [Handle a client-side resource alert](https://developers.cloudflare.com/page-shield/best-practices/handle-an-alert/)
---
title: Detection · Cloudflare Page Shield docs
description: Learn more about Page Shield's detection features.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/page-shield/detection/
md: https://developers.cloudflare.com/page-shield/detection/index.md
---
* [Monitor resources and cookies](https://developers.cloudflare.com/page-shield/detection/monitor-connections-scripts/)
* [Review resources considered malicious](https://developers.cloudflare.com/page-shield/detection/review-malicious-scripts/)
* [Review changed scripts](https://developers.cloudflare.com/page-shield/detection/review-changed-scripts/)
---
title: Page Shield FAQ · Cloudflare Page Shield docs
description: "When you create policies, Cloudflare will generate content
security policy (CSP) directives from those policies based on their
configuration:"
lastUpdated: 2025-10-14T10:22:38.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/faq/
md: https://developers.cloudflare.com/page-shield/faq/index.md
---
## What happens to CSP HTTP headers set by the origin server when I create a policy?
When you create policies, Cloudflare will generate content security policy (CSP) directives from those policies based on their configuration:
* Log policies will create CSP directives for the `Content-Security-Policy-Report-Only` HTTP header.
* Allow policies will create CSP directives for the `Content-Security-Policy` HTTP header.
Page Shield only adds new CSP HTTP headers to the response. This means that Cloudflare will keep any `Content-Security-Policy-Report-Only` and `Content-Security-Policy` HTTP headers in the response set by the origin server and it will add separate HTTP headers for the policies configured on your Cloudflare zone.
It is recommended that you only have one policy in [allow mode](https://developers.cloudflare.com/page-shield/policies/#policy-actions) (that is, a policy being enforced). If there is more than one `Content-Security-Policy` HTTP header in the response, the most restrictive policy wins. For more information, refer to the [MDN documentation](https://developer.mozilla.org/en-US/docs/Web/HTTP/Reference/Headers/Content-Security-Policy#multiple_content_security_policies).
## Can I add a `nonce` CSP directive to a policy?
Page Shield currently does not support [`nonce`](https://developer.mozilla.org/en-US/docs/Web/HTTP/Guides/CSP#nonces) directives in policies. Instead, you can use a [`hash`](https://developer.mozilla.org/en-US/docs/Web/HTTP/Guides/CSP#hashes) CSP directive. For details on the supported directives and values, refer to [Supported CSP directives](https://developers.cloudflare.com/page-shield/policies/csp-directives/).
---
title: Get started with Cloudflare Page Shield · Cloudflare Page Shield docs
description: Learn how to get started with client-side resource monitoring.
lastUpdated: 2026-01-23T11:42:49.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/get-started/
md: https://developers.cloudflare.com/page-shield/get-started/index.md
---
## 1. Activate client-side resource monitoring
To enable client-side resource monitoring:
* New dashboard
1. In the Cloudflare dashboard, go to the Security **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
2. (Optional) Filter by **Client-side abuse**.
3. Turn on **Continuous script monitoring**.
* Old dashboard
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Security** > **Page Shield**.
3. Select **Enable Page Shield**.
If you do not have access to Page Shield in the Cloudflare dashboard, check if your user has one of the [necessary roles](https://developers.cloudflare.com/page-shield/reference/roles-and-permissions/).
## 2. Review detected resources
When you enable client-side resource monitoring, it may take a while to get the list of detected scripts in your domain.
To review the scripts detected by Cloudflare:
1. Go to the client-side resources page:
* New dashboard
1. In the Cloudflare dashboard, go to the **Web assets** page.
[Go to **Web assets**](https://dash.cloudflare.com/?to=/:account/:zone/security/web-assets)
2. Select the **Client-side resources** tab.
* Old dashboard
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Security** > **Page Shield**.
2. Review the list of detected scripts, checking for any unknown or unexpected scripts.\
[Depending on your plan](https://developers.cloudflare.com/page-shield/#availability), Cloudflare will also:
* Inform you if a script is [considered malicious](https://developers.cloudflare.com/page-shield/how-it-works/malicious-script-detection/).
* [Show the details](https://developers.cloudflare.com/page-shield/detection/monitor-connections-scripts/#view-details) about each detected script.
Depending on your plan, you may be able to also review the connections made by scripts in your domain's pages and check them for malicious activity.
## 3. (Optional) Configure alerts
Once you have activated Page Shield's client-side resource monitoring, you can set up one or more alerts informing you of relevant client-side changes on your zones. The [available alert types](https://developers.cloudflare.com/page-shield/alerts/alert-types/) depend on your Cloudflare plan.
To configure an alert:
1. In the Cloudflare dashboard, go to the **Notifications** page.
[Go to **Notifications**](https://dash.cloudflare.com/?to=/:account/notifications)
2. Choose **Add** and then select **Page Shield** in the **Product** dropdown.
3. Select an [alert type](https://developers.cloudflare.com/page-shield/alerts/alert-types/).
4. Enter the notification name and description.
5. (Optional) If you are an Enterprise customer with a paid add-on, you can [define the zones for which you want to filter alerts](https://developers.cloudflare.com/page-shield/alerts/#scoped-alerts) in **Policies of these zones**. This option requires that you define [policies](https://developers.cloudflare.com/page-shield/policies/) in the selected zones.
6. Select one or more notification destinations (notification email, webhooks, and connected notification services).
7. Select **Create**.
To learn how you can handle an alert, refer to [Handle a client-side resource alert](https://developers.cloudflare.com/page-shield/best-practices/handle-an-alert/).
## 4. (Optional) Define policies
Note
Only available to Enterprise customers with a paid add-on.
[Policies](https://developers.cloudflare.com/page-shield/policies/) — called content security rules in the [new security dashboard](https://developers.cloudflare.com/security/) — define allowed resources on your websites. Create policies to implement a positive security model[1](#user-content-fn-1).
### 4.1. Create a policy with the Log action
When you create a policy with the [*Log* action](https://developers.cloudflare.com/page-shield/policies/#policy-actions), Cloudflare logs any resources not covered by the policy, without blocking any resources. Use this action to validate a new policy before deploying it.
* New dashboard
Notes
Only available to Enterprise customers with a paid add-on.\
In the [new security dashboard](https://developers.cloudflare.com/security/), policies are called content security rules.
1. In the Cloudflare dashboard, go to the **Security rules** page.
[Go to **Security rules**](https://dash.cloudflare.com/?to=/:account/:zone/security/security-rules)
2. Select **Create** > **Content security rules**.
3. []()
Enter a descriptive name for the rule in **Description**.
4. Under **If incoming requests match**, define the scope of the content security rule (or policy). You can use the Expression Builder (specifying one or more values for **Field**, **Operator**, and **Value**) or manually enter an expression using the Expression Editor. For more information, refer to [Edit expressions in the dashboard](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/edit-expressions/).
5. Under **Allow these directives**, select the desired [CSP directives](https://developers.cloudflare.com/page-shield/policies/csp-directives/) for the content security rule by enabling one or more checkboxes.
* To manually enter an allowed source, select **Add source**.
* To refresh the displayed sources based on detected resources, select **Refresh suggestions**.
Note
Cloudflare provides suggestions for **Default**, **Scripts**, and **Connections** directives. For the **Default** directive, suggestions are based on monitored scripts and connections resources.
6. Under **Then take action**, select *Log*.
7. To save and deploy your rule, select **Deploy**.
* Old dashboard
Note
Only available to Enterprise customers with a paid add-on.
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com) and select your account and domain.
2. Go to **Security** > **Page Shield** > **Policies**.
3. Select **Create policy**.
4. Enter a descriptive name for the rule in **Description**.
5. Under **If incoming requests match**, define the policy scope. You can use the Expression Builder (specifying one or more values for **Field**, **Operator**, and **Value**) or manually enter an expression using the Expression Editor. For more information, refer to [Edit expressions in the dashboard](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/edit-expressions/).
6. Under **Allow these directives**, select the desired [CSP directives](https://developers.cloudflare.com/page-shield/policies/csp-directives/) for the policy by enabling one or more checkboxes.
* To manually enter an allowed source, select **Add source**.
* To refresh the displayed sources based on Page Shield's detected resources, select **Refresh suggestions**.
Note
Page Shield provides suggestions for **Default**, **Scripts**, and **Connections** directives. For the **Default** directive, suggestions are based on monitored scripts and connections resources.
7. Under **Then take action**, select *Log*.
8. To save and deploy your rule, select **Deploy**.
### 4.2. Review policy violations
Resources not covered by the policy you created will be reported as [policy violations](https://developers.cloudflare.com/page-shield/policies/violations/). After some time, review the list of policy violations to make sure the policy is correct.
To view policy violation information:
* New dashboard
1. In the Cloudflare dashboard, go to the **Security rules** page.
[Go to **Security rules**](https://dash.cloudflare.com/?to=/:account/:zone/security/security-rules)
2. (Optional) Filter by **Content security rules**.
* Old dashboard
* In the Cloudflare dashboard, go to **Security** > **Page Shield** > **Policies**.
The displayed information includes the following:
* A sparkline next to the policy/rule name, showing violations in the past seven days.
* For policies with associated violations, an expandable details section for each policy, with the top resources present in violation events and a sparkline per top resource.
Update the policy if needed.
### 4.3. Change policy action to Allow
Once you have verified that your policy is correct, change the policy action from *Log* to *Allow*.
When you use the [*Allow* action](https://developers.cloudflare.com/page-shield/policies/#policy-actions), Cloudflare starts blocking any resources not explicitly allowed by the policy.
## Footnotes
1. A positive security model is one that defines what is allowed and rejects everything else. In contrast, a negative security model defines what will be rejected and accepts the rest. [↩](#user-content-fnref-1)
---
title: How Page Shield works · Cloudflare Page Shield docs
description: Page Shield tracks resources (such as scripts) loaded by your
website visitors and provides alerts when it detects new, changed, or
malicious resources.
lastUpdated: 2025-12-16T20:08:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/how-it-works/
md: https://developers.cloudflare.com/page-shield/how-it-works/index.md
---
Page Shield helps manage client-side resources (which include scripts and their connections) loaded by your website visitors, and provides visibility on the [cookies](https://www.cloudflare.com/learning/privacy/what-are-cookies/) recently detected in HTTP traffic. Page Shield can trigger alert notifications when resources change or are considered malicious.
Enabling resource monitoring adds a [Content Security Policy (CSP)](https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP) deployed with a [report-only directive](https://developers.cloudflare.com/page-shield/reference/csp-header/) to collect information from the browser. This allows Cloudflare to provide you with a list of all scripts running on your application and the connections they make to third-party endpoints. Cloudflare also monitors ingress and egress traffic for cookies, either set by origin servers or by the visitor's browser.
The client-side resource monitoring dashboard shows the list of active scripts, connections, and cookies. The **All Reported Scripts** and **All Reported Connections** dashboards show the full list of detected scripts and connections in your domain, respectively, including infrequent and inactive ones.
Cloudflare adds a CSP report-only HTTP header used to monitor webpage resources to a sample of sent responses. This means that there may be a [small delay](https://developers.cloudflare.com/page-shield/troubleshooting/#cloudflare-does-not-show-any-client-side-resources-after-activation) between deploying a script or cookie and having its data displayed in the resource monitoring dashboards.
Enterprise customers with a paid add-on have access to additional classification mechanisms based on threat feeds to determine if a script, or a connection made by a script, is malicious. For more information, refer to [Malicious script and connection detection](https://developers.cloudflare.com/page-shield/how-it-works/malicious-script-detection/).
## Positive security model using policies
Enterprise customers with a paid add-on can create [policies](https://developers.cloudflare.com/page-shield/policies/) to define a positive security model (also known as positive blocking) for resources such as scripts.
When you create policies, Cloudflare will generate content security policy (CSP) directives from those policies based on their configuration:
* Log policies will create CSP directives for the `Content-Security-Policy-Report-Only` HTTP header.
* Allow policies will create CSP directives for the `Content-Security-Policy` HTTP header.
For more information, refer to [Policies](https://developers.cloudflare.com/page-shield/policies/).
## Learn more
For more background on Page Shield and client-side resource monitoring, refer to our [blog post](https://blog.cloudflare.com/page-shield-generally-available/).
---
title: Policies · Cloudflare Page Shield docs
description: Use Page Shield policies to define the resources (scripts) allowed
on your applications.
lastUpdated: 2025-12-16T20:08:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/policies/
md: https://developers.cloudflare.com/page-shield/policies/index.md
---
Note
Only available to Enterprise customers with a paid add-on.
Policies define the resources allowed on your applications through Content Security Policy (CSP) directives. Policies can log violations and also enforce an allowlist of resources, effectively blocking resources not included in the policies. These two types of policies are called log policies and allow policies, respectively.
In the [new security dashboard](https://developers.cloudflare.com/security/), policies are called content security rules, and they are one of the available types of [security rules](https://developers.cloudflare.com/security/rules/). Security rules perform security-related actions on incoming requests that match specified filters.
Create [allow policies](#policy-actions) to define a positive security model, also known as positive blocking. According to this model, you define what is allowed and reject everything else. Such an approach helps you reduce the attack surface for unwanted third-party scripts in your application.
A policy can control both client-side resources monitored by Cloudflare, such as scripts and their connections, and other types of resources. Refer to [Supported CSP directives](https://developers.cloudflare.com/page-shield/policies/csp-directives/) for details.
### Important remarks
Third-party service providers may require specific CSP directives. Refer to your provider's documentation for more information on the CSP directives you need to include in your policy.
## Policy actions
A policy — or content security rule — can perform one of the following actions:
* **Log**: Cloudflare will log any resources not covered by the policy, without blocking any resources. Use this action to validate a new policy before deploying it. Resources not covered by the policy will be reported as [policy violations](https://developers.cloudflare.com/page-shield/policies/violations/).
* **Allow**: Cloudflare will block any resources not explicitly allowed by the policy. Switch to the *Allow* action after validating a new policy with the *Log* action, so that your policy does not block essential application resources, which would affect your application's end users. Policies with the *Allow* action will log [policy violations](https://developers.cloudflare.com/page-shield/policies/violations/) for any blocked resources.
For details on the CSP directives Cloudflare creates for each type of policy action, refer to [How Page Shield works](https://developers.cloudflare.com/page-shield/how-it-works/#positive-security-model-using-policies). For more information on the CSP directives supported by policies, refer to [Supported CSP directives](https://developers.cloudflare.com/page-shield/policies/csp-directives/).
## Next steps
Refer to the following pages for instructions on creating a policy or content security rule:
* [Create a policy in the dashboard](https://developers.cloudflare.com/page-shield/policies/create-dashboard/)
* [Page Shield API: Create a policy](https://developers.cloudflare.com/page-shield/reference/page-shield-api/#create-a-policy)
Shortly after you configure policies, the Cloudflare dashboard will start displaying any [violations](https://developers.cloudflare.com/page-shield/policies/violations/) of those policies.
You can filter Page Shield alert notifications according to the policies you configured in a zone. These alerts are called [scoped alerts](https://developers.cloudflare.com/page-shield/alerts/#scoped-alerts).
---
title: Page Shield reference · Cloudflare Page Shield docs
description: "The following pages include additional information about Page Shield:"
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/page-shield/reference/
md: https://developers.cloudflare.com/page-shield/reference/index.md
---
The following pages include additional information about Page Shield:
* [Configuration settings](https://developers.cloudflare.com/page-shield/reference/settings/)
* [Script and connection statuses](https://developers.cloudflare.com/page-shield/reference/script-statuses/)
* [Page Shield and PCI DSS compliance](https://developers.cloudflare.com/page-shield/reference/pci-dss/)
* [CSP HTTP header format](https://developers.cloudflare.com/page-shield/reference/csp-header/)
* [Roles and permissions](https://developers.cloudflare.com/page-shield/reference/roles-and-permissions/)
* [Page Shield API](https://developers.cloudflare.com/page-shield/reference/page-shield-api/)
---
title: Release notes · Cloudflare Page Shield docs
description: Subscribe to RSS
lastUpdated: 2025-12-16T20:08:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/release-notes/
md: https://developers.cloudflare.com/page-shield/release-notes/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/page-shield/release-notes/index.xml)
## 2025-10-08
**Updated machine learning (ML) model**
The latest ML model has been deployed to all Page Shield add-on customers with better classification precision. Scripts with false positive classification may have a different pattern than the previous model deployment.
## 2025-09-12
**Scoped alerts now support policies in log mode**
[Scoped alerts](https://developers.cloudflare.com/page-shield/alerts/) now take into account your Page Shield policies deployed in log mode. This allows you to simulate an end-to-end workflow before switching your policies to [allow mode](https://developers.cloudflare.com/page-shield/policies/#policy-actions).
## 2025-05-20
**Updated machine learning (ML) model**
The latest ML model has been deployed to all Page Shield add-on customers with better classification precision. Scripts with false positive classification may have a different pattern than the previous model deployment.
## 2025-05-09
**Reports from browser extension injected resources are filtered out**
Script and connection reports caused by browser extension injections are now filtered out, helping you focus on managing application dependencies.
## 2024-12-02
**Alerts based on customer-defined policies**
You can now scope all of Page Shield's alert types to selected zones and their associated policies, alerting only on the resources that have been explicitly allowed.
## 2024-09-30
**New machine learning (ML) scores for detected scripts**
In addition to the global integrity score, Page Shield now provides individual script scores (from 1 to 99) for the following malicious code detections: Magecart, Crypto mining, and Malware.
## 2024-09-18
**Page Shield's script monitor now available in Free plan**
The Page Shield's script monitor feature is now available to all users, including users in the Free plan.
## 2024-09-18
**Page Shield policy changes now available in audit logs**
Cloudflare [Audit Logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/) now include entries for any changes to Page Shield's policies.
## 2024-06-18
**Cookie Monitor now available**
Page Shield now captures HTTP cookies set and used by your web application. The [list of detected cookies](https://developers.cloudflare.com/page-shield/detection/monitor-connections-scripts/) in available in the Cloudflare dashboard or via API.
## 2024-06-14
**Added filter operators for scripts and connections**
You can now filter scripts and connections in the Cloudflare dashboard using the `does not contain` operator. Pages associated with scripts and connections can be filtered by `includes`, `starts with`, and `ends with`.
## 2024-04-26
**Suggestions for the default directive**
When creating a policy in the dashboard, default directive aggregates suggestions of monitored scripts and connections data, enabling defining default directive easier.
## 2024-04-04
**Individual threat intelligence categories**
Instead of aggregating categories of URL and domain data from threat intelligence, they are now listed per type.
## 2024-03-21
**Increase allowed length per policy**
Now each policy supports up to 6,000 characters.
---
title: Troubleshooting · Cloudflare Page Shield docs
description: Cloudflare does not collect data on every single page view.
Instead, it uses a sampling approach to gather information efficiently. This
means that domains with lower traffic might take longer to generate initial
reports, as these domains need more page views to accumulate enough samples.
To speed up the reporting process, it is recommended that you actively
generate traffic to your application after activating client-side resource
monitoring. This will provide Cloudflare with more data to work with, leading
to faster report generation.
lastUpdated: 2025-07-10T11:20:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/page-shield/troubleshooting/
md: https://developers.cloudflare.com/page-shield/troubleshooting/index.md
---
## Cloudflare does not show any client-side resources after activation
Cloudflare does not collect data on every single page view. Instead, it uses a sampling approach to gather information efficiently. This means that domains with lower traffic might take longer to generate initial reports, as these domains need more page views to accumulate enough samples. To speed up the reporting process, it is recommended that you actively generate traffic to your application after [activating client-side resource monitoring](https://developers.cloudflare.com/page-shield/get-started/). This will provide Cloudflare with more data to work with, leading to faster report generation.
## The dashboard shows scripts and connections that I do not recognize
Scripts often reference other scripts outside your application.
But, if you see unexpected scripts on your resource monitoring dashboard, check them for signs of malicious activity.
## I get warnings in my browser's developer tools related to Content Security Policy (CSP)
Cloudflare uses a Content Security Policy (CSP) report-only directive to gather a list of all scripts running on your application.
Some browsers display scripts being reported as warnings in the console pane of their developer tools. For example:
```txt
[Report Only] Refused to execute inline script because it violates
the following Content Security Policy directive: "script-src 'none'".
Either the 'unsafe-inline' keyword, a hash ('sha256-RFWPLDbv2BY+rCkDzsE+0fr8ylGr2R2faWMhq4lfEQc='), or a nonce ('nonce-...')
is required to enable inline execution.
```
You can safely ignore these warnings, since they are related to the reports that Cloudflare requires to detect loaded scripts. For more information, refer to [How Page Shield works](https://developers.cloudflare.com/page-shield/how-it-works/).
## I get policy violation reports for a domain I allowlisted
Policy violations reported via CSP's [report-only directive](https://developers.cloudflare.com/page-shield/reference/csp-header/) do not take into consideration any redirects or redirect HTTP status codes. This is [by design](https://www.w3.org/TR/CSP3/#create-violation-for-request) for security reasons.
Some third-party services you may want to cover in your allow policies perform redirects. An example of such a service is Google Ads, which [does not work well with CSP policies](https://support.google.com/adsense/thread/102839782?hl=en\&msgid=103611259).
For example, if you add the `adservice.google.com` domain to an allow policy, you could get policy violation reports for this domain due to redirects to a different domain (not present in your allow policy). In this case, the violation report would still mention the original domain, and not the domain of the redirected destination, which can cause some confusion.
To try to solve this issue, add the domain of the redirected destination to your allow policy. You may need to add several domains to your policy due to redirects.
---
title: 404 - Page Not Found · Cloudflare Pages docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pages/404/
md: https://developers.cloudflare.com/pages/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Configuration · Cloudflare Pages docs
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pages/configuration/
md: https://developers.cloudflare.com/pages/configuration/index.md
---
* [Branch deployment controls](https://developers.cloudflare.com/pages/configuration/branch-build-controls/)
* [Build caching](https://developers.cloudflare.com/pages/configuration/build-caching/)
* [Build configuration](https://developers.cloudflare.com/pages/configuration/build-configuration/)
* [Build image](https://developers.cloudflare.com/pages/configuration/build-image/)
* [Build watch paths](https://developers.cloudflare.com/pages/configuration/build-watch-paths/)
* [Custom domains](https://developers.cloudflare.com/pages/configuration/custom-domains/)
* [Debugging Pages](https://developers.cloudflare.com/pages/configuration/debugging-pages/)
* [Deploy Hooks](https://developers.cloudflare.com/pages/configuration/deploy-hooks/)
* [Early Hints](https://developers.cloudflare.com/pages/configuration/early-hints/)
* [Git integration](https://developers.cloudflare.com/pages/configuration/git-integration/)
* [Headers](https://developers.cloudflare.com/pages/configuration/headers/)
* [Monorepos](https://developers.cloudflare.com/pages/configuration/monorepos/)
* [Preview deployments](https://developers.cloudflare.com/pages/configuration/preview-deployments/)
* [Redirects](https://developers.cloudflare.com/pages/configuration/redirects/)
* [REST API](https://developers.cloudflare.com/pages/configuration/api/)
* [Rollbacks](https://developers.cloudflare.com/pages/configuration/rollbacks/)
* [Serving Pages](https://developers.cloudflare.com/pages/configuration/serving-pages/)
---
title: Demos and architectures · Cloudflare Pages docs
description: Learn how you can use Pages within your existing application and architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pages/demos/
md: https://developers.cloudflare.com/pages/demos/index.md
---
Learn how you can use Pages within your existing application and architecture.
## Demos
Explore the following demo applications for Pages.
* [Jobs At Conf:](https://github.com/harshil1712/jobs-at-conf-demo) A job lisiting website to add jobs you find at in-person conferences. Built with Cloudflare Pages, R2, D1, Queues, and Workers AI.
* [Upload Image to R2 starter:](https://github.com/harshil1712/nextjs-r2-demo) Upload images to Cloudflare R2 from a Next.js application.
* [Staff Directory demo:](https://github.com/lauragift21/staff-directory) Built using the powerful combination of HonoX for backend logic, Cloudflare Pages for fast and secure hosting, and Cloudflare D1 for seamless database management.
* [Wildebeest:](https://github.com/cloudflare/wildebeest) Wildebeest is an ActivityPub and Mastodon-compatible server whose goal is to allow anyone to operate their Fediverse server and identity on their domain without needing to keep infrastructure, with minimal setup and maintenance, and running in minutes.
* [Multiplayer Doom Workers:](https://github.com/cloudflare/doom-workers) A WebAssembly Doom port with multiplayer support running on top of Cloudflare's global network using Workers, WebSockets, Pages, and Durable Objects.
* [Queues Web Crawler:](https://github.com/cloudflare/queues-web-crawler) An example use-case for Queues, a web crawler built on Browser Rendering and Puppeteer. The crawler finds the number of links to Cloudflare.com on the site, and archives a screenshot to Workers KV.
* [Pages Functions with WebAssembly:](https://github.com/cloudflare/pages-fns-with-wasm-demo) This is a demo application that exemplifies the use of Wasm module imports inside Pages Functions code.
## Reference architectures
Explore the following reference architectures that use Pages:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
---
title: Framework guides · Cloudflare Pages docs
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pages/framework-guides/
md: https://developers.cloudflare.com/pages/framework-guides/index.md
---
* [Analog](https://developers.cloudflare.com/pages/framework-guides/deploy-an-analog-site/)
* [Angular](https://developers.cloudflare.com/pages/framework-guides/deploy-an-angular-site/)
* [Astro](https://developers.cloudflare.com/pages/framework-guides/deploy-an-astro-site/)
* [Blazor](https://developers.cloudflare.com/pages/framework-guides/deploy-a-blazor-site/)
* [Brunch](https://developers.cloudflare.com/pages/framework-guides/deploy-a-brunch-site/)
* [Docusaurus](https://developers.cloudflare.com/pages/framework-guides/deploy-a-docusaurus-site/)
* [Elder.js](https://developers.cloudflare.com/pages/framework-guides/deploy-an-elderjs-site/)
* [Eleventy](https://developers.cloudflare.com/pages/framework-guides/deploy-an-eleventy-site/)
* [Ember](https://developers.cloudflare.com/pages/framework-guides/deploy-an-emberjs-site/)
* [Gatsby](https://developers.cloudflare.com/pages/framework-guides/deploy-a-gatsby-site/)
* [Gridsome](https://developers.cloudflare.com/pages/framework-guides/deploy-a-gridsome-site/)
* [Hexo](https://developers.cloudflare.com/pages/framework-guides/deploy-a-hexo-site/)
* [Hono](https://developers.cloudflare.com/pages/framework-guides/deploy-a-hono-site/)
* [Hugo](https://developers.cloudflare.com/pages/framework-guides/deploy-a-hugo-site/)
* [Jekyll](https://developers.cloudflare.com/pages/framework-guides/deploy-a-jekyll-site/)
* [MkDocs](https://developers.cloudflare.com/pages/framework-guides/deploy-an-mkdocs-site/)
* [Next.js](https://developers.cloudflare.com/pages/framework-guides/nextjs/)
* [Nuxt](https://developers.cloudflare.com/pages/framework-guides/deploy-a-nuxt-site/)
* [Pelican](https://developers.cloudflare.com/pages/framework-guides/deploy-a-pelican-site/)
* [Preact](https://developers.cloudflare.com/pages/framework-guides/deploy-a-preact-site/)
* [Qwik](https://developers.cloudflare.com/pages/framework-guides/deploy-a-qwik-site/)
* [React](https://developers.cloudflare.com/pages/framework-guides/deploy-a-react-site/)
* [Remix](https://developers.cloudflare.com/pages/framework-guides/deploy-a-remix-site/)
* [SolidStart](https://developers.cloudflare.com/pages/framework-guides/deploy-a-solid-start-site/)
* [Sphinx](https://developers.cloudflare.com/pages/framework-guides/deploy-a-sphinx-site/)
* [Static HTML](https://developers.cloudflare.com/pages/framework-guides/deploy-anything/)
* [SvelteKit](https://developers.cloudflare.com/pages/framework-guides/deploy-a-svelte-kit-site/)
* [Vite 3](https://developers.cloudflare.com/pages/framework-guides/deploy-a-vite3-project/)
* [VitePress](https://developers.cloudflare.com/pages/framework-guides/deploy-a-vitepress-site/)
* [Vue](https://developers.cloudflare.com/pages/framework-guides/deploy-a-vue-site/)
* [Zola](https://developers.cloudflare.com/pages/framework-guides/deploy-a-zola-site/)
---
title: Functions · Cloudflare Pages docs
description: Pages Functions allows you to build full-stack applications by
executing code on the Cloudflare network with Cloudflare Workers. With
Functions, you can introduce application aspects such as authenticating,
handling form submissions, or working with middleware. Workers runtime
features are configurable on Pages Functions, including compatibility with a
subset of Node.js APIs and the ability to set a compatibility date or
compatibility flag. Use Functions to deploy server-side code to enable dynamic
functionality without running a dedicated server.
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pages/functions/
md: https://developers.cloudflare.com/pages/functions/index.md
---
Pages Functions allows you to build full-stack applications by executing code on the Cloudflare network with [Cloudflare Workers](https://developers.cloudflare.com/workers/). With Functions, you can introduce application aspects such as authenticating, handling form submissions, or working with middleware. [Workers runtime features](https://developers.cloudflare.com/workers/runtime-apis/) are configurable on Pages Functions, including [compatibility with a subset of Node.js APIs](https://developers.cloudflare.com/workers/runtime-apis/nodejs) and the ability to set a [compatibility date or compatibility flag](https://developers.cloudflare.com/workers/configuration/compatibility-dates/). Use Functions to deploy server-side code to enable dynamic functionality without running a dedicated server.
To provide feedback or ask questions on Functions, join the [Cloudflare Developers Discord](https://discord.com/invite/cloudflaredev) and connect with the Cloudflare team in the [#functions channel](https://discord.com/channels/595317990191398933/910978223968518144).
* [Get started](https://developers.cloudflare.com/pages/functions/get-started/)
* [Routing](https://developers.cloudflare.com/pages/functions/routing/)
* [API reference](https://developers.cloudflare.com/pages/functions/api-reference/)
* [Examples](https://developers.cloudflare.com/pages/functions/examples/)
* [Middleware](https://developers.cloudflare.com/pages/functions/middleware/)
* [Configuration](https://developers.cloudflare.com/pages/functions/wrangler-configuration/)
* [Local development](https://developers.cloudflare.com/pages/functions/local-development/)
* [Bindings](https://developers.cloudflare.com/pages/functions/bindings/)
* [TypeScript](https://developers.cloudflare.com/pages/functions/typescript/)
* [Advanced mode](https://developers.cloudflare.com/pages/functions/advanced-mode/)
* [Pages Plugins](https://developers.cloudflare.com/pages/functions/plugins/)
* [Metrics](https://developers.cloudflare.com/pages/functions/metrics/)
* [Debugging and logging](https://developers.cloudflare.com/pages/functions/debugging-and-logging/)
* [Pricing](https://developers.cloudflare.com/pages/functions/pricing/)
* [Module support](https://developers.cloudflare.com/pages/functions/module-support/)
* [Smart Placement](https://developers.cloudflare.com/pages/functions/smart-placement/)
* [Source maps and stack traces](https://developers.cloudflare.com/pages/functions/source-maps/)
---
title: Getting started · Cloudflare Pages docs
description: "Choose a setup method for your Pages project:"
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pages/get-started/
md: https://developers.cloudflare.com/pages/get-started/index.md
---
Choose a setup method for your Pages project:
* [C3 CLI](https://developers.cloudflare.com/pages/get-started/c3/)
* [Direct Upload](https://developers.cloudflare.com/pages/get-started/direct-upload/)
* [Git integration](https://developers.cloudflare.com/pages/get-started/git-integration/)
---
title: How to · Cloudflare Pages docs
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pages/how-to/
md: https://developers.cloudflare.com/pages/how-to/index.md
---
* [Add a custom domain to a branch](https://developers.cloudflare.com/pages/how-to/custom-branch-aliases/)
* [Add custom HTTP headers](https://developers.cloudflare.com/pages/how-to/add-custom-http-headers/)
* [Deploy a static WordPress site](https://developers.cloudflare.com/pages/how-to/deploy-a-wordpress-site/)
* [Enable Web Analytics](https://developers.cloudflare.com/pages/how-to/web-analytics/)
* [Enable Zaraz](https://developers.cloudflare.com/pages/how-to/enable-zaraz/)
* [Install private packages](https://developers.cloudflare.com/pages/how-to/npm-private-registry/)
* [Preview Local Projects with Cloudflare Tunnel](https://developers.cloudflare.com/pages/how-to/preview-with-cloudflare-tunnel/)
* [Redirecting \*.pages.dev to a Custom Domain](https://developers.cloudflare.com/pages/how-to/redirect-to-custom-domain/)
* [Redirecting www to domain apex](https://developers.cloudflare.com/pages/how-to/www-redirect/)
* [Refactor a Worker to a Pages Function](https://developers.cloudflare.com/pages/how-to/refactor-a-worker-to-pages-functions/)
* [Set build commands per branch](https://developers.cloudflare.com/pages/how-to/build-commands-branches/)
* [Use Direct Upload with continuous integration](https://developers.cloudflare.com/pages/how-to/use-direct-upload-with-continuous-integration/)
* [Use Pages Functions for A/B testing](https://developers.cloudflare.com/pages/how-to/use-worker-for-ab-testing-in-pages/)
---
title: Migrate to Workers · Cloudflare Pages docs
lastUpdated: 2025-05-09T17:32:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pages/migrate-to-workers/
md: https://developers.cloudflare.com/pages/migrate-to-workers/index.md
---
---
title: Migration guides · Cloudflare Pages docs
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pages/migrations/
md: https://developers.cloudflare.com/pages/migrations/index.md
---
* [Migrating a Jekyll-based site from GitHub Pages](https://developers.cloudflare.com/pages/migrations/migrating-jekyll-from-github-pages/)
* [Migrating from Firebase](https://developers.cloudflare.com/pages/migrations/migrating-from-firebase/)
* [Migrating from Netlify to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-netlify/)
* [Migrating from Vercel to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-vercel/)
* [Migrating from Workers Sites to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-workers/)
---
title: Platform · Cloudflare Pages docs
lastUpdated: 2025-09-15T21:45:20.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pages/platform/
md: https://developers.cloudflare.com/pages/platform/index.md
---
* [Limits](https://developers.cloudflare.com/pages/platform/limits/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
* [Changelog](https://developers.cloudflare.com/pages/platform/changelog/)
* [Known issues](https://developers.cloudflare.com/pages/platform/known-issues/)
---
title: Tutorials · Cloudflare Pages docs
description: View tutorials to help you get started with Pages.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pages/tutorials/
md: https://developers.cloudflare.com/pages/tutorials/index.md
---
View tutorials to help you get started with Pages.
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [Point to Pages with a custom domain](https://developers.cloudflare.com/rules/origin-rules/tutorials/point-to-pages-with-custom-domain/) | 10 months ago | Beginner |
| [Migrating from Vercel to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-vercel/) | 10 months ago | Beginner |
| [Build an API for your front end using Pages Functions](https://developers.cloudflare.com/pages/tutorials/build-an-api-with-pages-functions/) | over 1 year ago | Intermediate |
| [Use R2 as static asset storage with Cloudflare Pages](https://developers.cloudflare.com/pages/tutorials/use-r2-as-static-asset-storage-for-pages/) | over 1 year ago | Intermediate |
| [Use Pages as an origin for Load Balancing](https://developers.cloudflare.com/load-balancing/pools/cloudflare-pages-origin/) | over 1 year ago | Beginner |
| [Localize a website with HTMLRewriter](https://developers.cloudflare.com/pages/tutorials/localize-a-website/) | almost 2 years ago | Intermediate |
| [Build a Staff Directory Application](https://developers.cloudflare.com/d1/tutorials/build-a-staff-directory-app/) | almost 2 years ago | Intermediate |
| [Deploy a static WordPress site](https://developers.cloudflare.com/pages/how-to/deploy-a-wordpress-site/) | almost 3 years ago | Intermediate |
| [Build a blog using Nuxt.js and Sanity.io on Cloudflare Pages](https://developers.cloudflare.com/pages/tutorials/build-a-blog-using-nuxt-and-sanity/) | over 3 years ago | Intermediate |
| [Create a HTML form](https://developers.cloudflare.com/pages/tutorials/forms/) | over 3 years ago | Beginner |
| [Migrating from Netlify to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-netlify/) | over 3 years ago | Beginner |
| [Add a React form with Formspree](https://developers.cloudflare.com/pages/tutorials/add-a-react-form-with-formspree/) | about 4 years ago | Beginner |
| [Add an HTML form with Formspree](https://developers.cloudflare.com/pages/tutorials/add-an-html-form-with-formspree/) | about 4 years ago | Beginner |
| [Migrating a Jekyll-based site from GitHub Pages](https://developers.cloudflare.com/pages/migrations/migrating-jekyll-from-github-pages/) | over 4 years ago | Beginner |
| [Migrating from Firebase](https://developers.cloudflare.com/pages/migrations/migrating-from-firebase/) | over 5 years ago | Beginner |
| [Migrating from Workers Sites to Pages](https://developers.cloudflare.com/pages/migrations/migrating-from-workers/) | over 5 years ago | Beginner |
## Videos
OpenAI Relay Server on Cloudflare Workers
In this video, Craig Dennis walks you through the deployment of OpenAI's relay server to use with their realtime API.
Deploy your React App to Cloudflare Workers
Learn how to deploy an existing React application to Cloudflare Workers.
Cloudflare Workflows | Schedule and Sleep For Your Apps (Part 3 of 3)
Cloudflare Workflows allows you to initiate sleep as an explicit step, which can be useful when you want a Workflow to wait, schedule work ahead, or pause until an input or other external state is ready.
---
title: 404 - Page Not Found · Cloudflare Pipelines Docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pipelines/404/
md: https://developers.cloudflare.com/pipelines/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Getting started · Cloudflare Pipelines Docs
description: Create your first pipeline to ingest streaming data and write to R2
Data Catalog as an Apache Iceberg table.
lastUpdated: 2025-11-17T14:08:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pipelines/getting-started/
md: https://developers.cloudflare.com/pipelines/getting-started/index.md
---
This guide will instruct you through:
* Creating your first [R2 bucket](https://developers.cloudflare.com/r2/buckets/) and enabling its [data catalog](https://developers.cloudflare.com/r2/data-catalog/).
* Creating an [API token](https://developers.cloudflare.com/r2/api/tokens/) needed for pipelines to authenticate with your data catalog.
* Creating your first pipeline with a simple ecommerce schema that writes to an [Apache Iceberg](https://iceberg.apache.org/) table managed by R2 Data Catalog.
* Sending sample ecommerce data via HTTP endpoint.
* Validating data in your bucket and querying it with R2 SQL.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
## 1. Create an R2 bucket
* Wrangler CLI
1. If not already logged in, run:
```plaintext
npx wrangler login
```
2. Create an R2 bucket:
```plaintext
npx wrangler r2 bucket create pipelines-tutorial
```
* Dashboard
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
2. Select **Create bucket**.
3. Enter the bucket name: pipelines-tutorial
4. Select **Create bucket**.
## 2. Enable R2 Data Catalog
* Wrangler CLI
Enable the catalog on your R2 bucket:
```plaintext
npx wrangler r2 bucket catalog enable pipelines-tutorial
```
When you run this command, take note of the "Warehouse" and "Catalog URI". You will need these later.
* Dashboard
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
2. Select the bucket: pipelines-tutorial.
3. Switch to the **Settings** tab, scroll down to **R2 Data Catalog**, and select **Enable**.
4. Once enabled, note the **Catalog URI** and **Warehouse name**.
## 3. Create an API token
Pipelines must authenticate to R2 Data Catalog with an [R2 API token](https://developers.cloudflare.com/r2/api/tokens/) that has catalog and R2 permissions.
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
2. Select **Manage API tokens**.
3. Select **Create Account API token**.
4. Give your API token a name.
5. Under **Permissions**, choose the **Admin Read & Write** permission.
6. Select **Create Account API Token**.
7. Note the **Token value**.
Note
This token also includes the R2 SQL Read permission, which allows you to query your data with R2 SQL.
## 4. Create your first pipeline
* Wrangler CLI
First, create a schema file that defines your ecommerce data structure:
**Create `schema.json`:**
```json
{
"fields": [
{
"name": "user_id",
"type": "string",
"required": true
},
{
"name": "event_type",
"type": "string",
"required": true
},
{
"name": "product_id",
"type": "string",
"required": false
},
{
"name": "amount",
"type": "float64",
"required": false
}
]
}
```
Use the interactive setup to create a pipeline that writes to R2 Data Catalog:
```bash
npx wrangler pipelines setup
```
Follow the prompts:
1. **Pipeline name**: Enter `ecommerce`
2. **Stream configuration**:
* Enable HTTP endpoint: `yes`
* Require authentication: `no` (for simplicity)
* Configure custom CORS origins: `no`
* Schema definition: `Load from file`
* Schema file path: `schema.json` (or your file path)
3. **Sink configuration**:
* Destination type: `Data Catalog Table`
* R2 bucket name: `pipelines-tutorial`
* Namespace: `default`
* Table name: `ecommerce`
* Catalog API token: Enter your token from step 3
* Compression: `zstd`
* Roll file when size reaches (MB): `100`
* Roll file when time reaches (seconds): `10` (for faster data visibility in this tutorial)
4. **SQL transformation**: Choose `Use simple ingestion query` to use:
```sql
INSERT INTO ecommerce_sink SELECT * FROM ecommerce_stream
```
After setup completes, note the HTTP endpoint URL displayed in the final output.
* Dashboard
1. In the Cloudflare dashboard, go to **Pipelines** > **Pipelines**.
[Go to **Pipelines**](https://dash.cloudflare.com/?to=/:account/pipelines/overview)
2. Select **Create Pipeline**.
3. **Connect to a Stream**:
* Pipeline name: `ecommerce`
* Enable HTTP endpoint for sending data: Enabled
* HTTP authentication: Disabled (default)
* Select **Next**
4. **Define Input Schema**:
* Select **JSON editor**
* Copy in the schema:
```json
{
"fields": [
{
"name": "user_id",
"type": "string",
"required": true
},
{
"name": "event_type",
"type": "string",
"required": true
},
{
"name": "product_id",
"type": "string",
"required": false
},
{
"name": "amount",
"type": "f64",
"required": false
}
]
}
```
* Select **Next**
5. **Define Sink**:
* Select your R2 bucket: `pipelines-tutorial`
* Storage type: **R2 Data Catalog**
* Namespace: `default`
* Table name: `ecommerce`
* **Advanced Settings**: Change **Maximum Time Interval** to `10 seconds`
* Select **Next**
6. **Credentials**:
* Disable **Automatically create an Account API token for your sink**
* Enter **Catalog Token** from step 3
* Select **Next**
7. **Pipeline Definition**:
* Leave the default SQL query:
```sql
INSERT INTO ecommerce_sink SELECT * FROM ecommerce_stream;
```
* Select **Create Pipeline**
8. After pipeline creation, note the **Stream ID** for the next step.
## 5. Send sample data
Send ecommerce events to your pipeline's HTTP endpoint:
```bash
curl -X POST https://{stream-id}.ingest.cloudflare.com \
-H "Content-Type: application/json" \
-d '[
{
"user_id": "user_12345",
"event_type": "purchase",
"product_id": "widget-001",
"amount": 29.99
},
{
"user_id": "user_67890",
"event_type": "view_product",
"product_id": "widget-002"
},
{
"user_id": "user_12345",
"event_type": "add_to_cart",
"product_id": "widget-003",
"amount": 15.50
}
]'
```
Replace `{stream-id}` with your actual stream endpoint from the pipeline setup.
## 6. Validate data in your bucket
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
2. Select your bucket: `pipelines-tutorial`.
3. You should see Iceberg metadata files and data files created by your pipeline. Note: If you aren't seeing any files in your bucket, try waiting a couple of minutes and trying again.
4. The data is organized in the Apache Iceberg format with metadata tracking table versions.
## 7. Query your data using R2 SQL
Set up your environment to use R2 SQL:
```bash
export WRANGLER_R2_SQL_AUTH_TOKEN=YOUR_API_TOKEN
```
Or create a `.env` file with:
```plaintext
WRANGLER_R2_SQL_AUTH_TOKEN=YOUR_API_TOKEN
```
Where `YOUR_API_TOKEN` is the token you created in step 3. For more information on setting environment variables, refer to [Wrangler system environment variables](https://developers.cloudflare.com/workers/wrangler/system-environment-variables/).
Query your data:
```bash
npx wrangler r2 sql query "YOUR_WAREHOUSE_NAME" "
SELECT
user_id,
event_type,
product_id,
amount
FROM default.ecommerce
WHERE event_type = 'purchase'
LIMIT 10"
```
Replace `YOUR_WAREHOUSE_NAME` with the warehouse name from step 2.
You can also query this table with any engine that supports Apache Iceberg. To learn more about connecting other engines to R2 Data Catalog, refer to [Connect to Iceberg engines](https://developers.cloudflare.com/r2/data-catalog/config-examples/).
## Learn more
[Streams ](https://developers.cloudflare.com/pipelines/streams/)Learn about configuring streams for data ingestion.
[Pipelines ](https://developers.cloudflare.com/pipelines/pipelines/)Understand SQL transformations and pipeline configuration.
[Sinks ](https://developers.cloudflare.com/pipelines/sinks/)Configure data destinations and output formats.
---
title: Observability · Cloudflare Pipelines Docs
lastUpdated: 2025-09-25T04:07:16.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pipelines/observability/
md: https://developers.cloudflare.com/pipelines/observability/index.md
---
* [Metrics and analytics](https://developers.cloudflare.com/pipelines/observability/metrics/)
---
title: Platform · Cloudflare Pipelines Docs
lastUpdated: 2025-09-25T04:07:16.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pipelines/platform/
md: https://developers.cloudflare.com/pipelines/platform/index.md
---
* [Pricing](https://developers.cloudflare.com/pipelines/platform/pricing/)
* [Limits](https://developers.cloudflare.com/pipelines/platform/limits/)
---
title: Pipelines · Cloudflare Pipelines Docs
description: Pipelines connect streams and sinks via SQL transformations, which
can modify events before writing them to storage. This enables you to shift
left, pushing validation, schematization, and processing to your ingestion
layer to make your queries easy, fast, and correct.
lastUpdated: 2025-09-25T04:07:16.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pipelines/pipelines/
md: https://developers.cloudflare.com/pipelines/pipelines/index.md
---
Pipelines connect [streams](https://developers.cloudflare.com/pipelines/streams/) and [sinks](https://developers.cloudflare.com/pipelines/sinks/) via SQL transformations, which can modify events before writing them to storage. This enables you to shift left, pushing validation, schematization, and processing to your ingestion layer to make your queries easy, fast, and correct.
Pipelines enable you to filter, transform, enrich, and restructure events in real-time as data flows from streams to sinks.
## Learn more
[Manage pipelines ](https://developers.cloudflare.com/pipelines/pipelines/manage-pipelines/)Create, configure, and manage SQL transformations between streams and sinks.
---
title: Reference · Cloudflare Pipelines Docs
description: Reference documentation for Cloudflare Pipelines.
lastUpdated: 2025-09-25T04:07:16.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pipelines/reference/
md: https://developers.cloudflare.com/pipelines/reference/index.md
---
[Pipelines](https://developers.cloudflare.com/pipelines/) reference documentation:
* [Legacy pipelines](https://developers.cloudflare.com/pipelines/reference/legacy-pipelines/)
* [Wrangler commands](https://developers.cloudflare.com/pipelines/reference/wrangler-commands/)
---
title: Sinks · Cloudflare Pipelines Docs
description: Sinks define destinations for your data in Cloudflare Pipelines.
They support writing to R2 Data Catalog as Apache Iceberg tables or to R2 as
raw JSON or Parquet files.
lastUpdated: 2025-09-25T04:07:16.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pipelines/sinks/
md: https://developers.cloudflare.com/pipelines/sinks/index.md
---
Sinks define destinations for your data in Cloudflare Pipelines. They support writing to [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/) as Apache Iceberg tables or to [R2](https://developers.cloudflare.com/r2/) as raw JSON or Parquet files.
Sinks provide exactly-once delivery guarantees, ensuring events are never duplicated or dropped. They can be configured to write files frequently for low-latency ingestion or to write larger, less frequent files for better query performance.
## Learn more
[Manage sinks ](https://developers.cloudflare.com/pipelines/sinks/manage-sinks/)Create, configure, and delete sinks using Wrangler or the API.
[Available sinks ](https://developers.cloudflare.com/pipelines/sinks/available-sinks/)Learn about supported sink destinations and their configuration options.
---
title: SQL reference · Cloudflare Pipelines Docs
description: Comprehensive reference for SQL syntax, data types, and functions
supported in Pipelines.
lastUpdated: 2025-09-25T04:07:16.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/pipelines/sql-reference/
md: https://developers.cloudflare.com/pipelines/sql-reference/index.md
---
[Pipelines](https://developers.cloudflare.com/pipelines/) SQL reference documentation:
* [SQL data types](https://developers.cloudflare.com/pipelines/sql-reference/sql-data-types/)
* [SELECT statements](https://developers.cloudflare.com/pipelines/sql-reference/select-statements/)
* [Scalar functions](https://developers.cloudflare.com/pipelines/sql-reference/scalar-functions/)
---
title: Streams · Cloudflare Pipelines Docs
description: Streams are durable, buffered queues that receive and store events
for processing in Cloudflare Pipelines. They provide reliable data ingestion
via HTTP endpoints and Worker bindings, ensuring no data loss even during
downstream processing delays or failures.
lastUpdated: 2025-09-25T04:07:16.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pipelines/streams/
md: https://developers.cloudflare.com/pipelines/streams/index.md
---
Streams are durable, buffered queues that receive and store events for processing in [Cloudflare Pipelines](https://developers.cloudflare.com/pipelines/). They provide reliable data ingestion via HTTP endpoints and Worker bindings, ensuring no data loss even during downstream processing delays or failures.
A single stream can be read by multiple pipelines, allowing you to route the same data to different destinations or apply different transformations. For example, you might send user events to both a real-time analytics pipeline and a data warehouse pipeline.
Streams currently accept events in JSON format and support both structured events with defined schemas and unstructured JSON. When a schema is provided, streams will validate and enforce it for incoming events.
## Learn more
[Manage streams ](https://developers.cloudflare.com/pipelines/streams/manage-streams/)Create, configure, and delete streams using Wrangler or the API.
[Writing to streams ](https://developers.cloudflare.com/pipelines/streams/writing-to-streams/)Send events to streams via HTTP endpoints or Worker bindings.
---
title: 404 - Page Not Found · Cloudflare Privacy Gateway docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-gateway/404/
md: https://developers.cloudflare.com/privacy-gateway/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Get started · Cloudflare Privacy Gateway docs
description: "Privacy Gateway implementation consists of three main parts:"
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-gateway/get-started/
md: https://developers.cloudflare.com/privacy-gateway/get-started/index.md
---
Privacy Gateway implementation consists of three main parts:
1. Application Gateway Server/backend configuration (operated by you).
2. Client configuration (operated by you).
3. Connection to a Privacy Gateway Relay Server (operated by Cloudflare).
***
## Before you begin
Privacy Gateway is currently in closed beta. If you are interested, [contact us](https://www.cloudflare.com/lp/privacy-edge/).
***
## Step 1 - Configure your server
As a customer of the Privacy Gateway, you also need to add server support for OHTTP by implementing an application gateway server. The application gateway is responsible for decrypting incoming requests, forwarding the inner requests to their destination, and encrypting the corresponding response back to the client.
The [server implementation](#resources) will handle incoming requests and produce responses, and it will also advertise its public key configuration for clients to access. The public key configuration is generated securely and made available via an API. Refer to the [README](https://github.com/cloudflare/privacy-gateway-server-go#readme) for details about configuration.
Applications can also implement this functionality themselves. Details about [public key configuration](https://datatracker.ietf.org/doc/html/draft-ietf-ohai-ohttp-05#section-3), HTTP message [encryption and decryption](https://datatracker.ietf.org/doc/html/draft-ietf-ohai-ohttp-05#section-4), and [server-specific details](https://datatracker.ietf.org/doc/html/draft-ietf-ohai-ohttp-05#section-5) can be found in the OHTTP specification.
### Resources
Use the following resources for help with server configuration:
* **Go**:
* [Sample gateway server](https://github.com/cloudflare/privacy-gateway-server-go)
* [Gateway library](https://github.com/chris-wood/ohttp-go)
* **Rust**: [Gateway library](https://github.com/martinthomson/ohttp/tree/main/ohttp-server)
* **JavaScript / TypeScript**: [Gateway library](https://github.com/chris-wood/ohttp-js)
***
## Step 2 - Configure your client
As a customer of the Privacy Gateway, you need to set up client-side support for the gateway. Clients are responsible for encrypting requests, sending them to the Cloudflare Privacy Gateway, and then decrypting the corresponding responses.
Additionally, app developers need to [configure the client](#resources-1) to fetch or otherwise discover the gateway’s public key configuration. How this is done depends on how the gateway makes its public key configuration available. If you need help with this configuration, [contact us](https://www.cloudflare.com/lp/privacy-edge/).
### Resources
Use the following resources for help with client configuration:
* **Objective C**: [Sample application](https://github.com/cloudflare/privacy-gateway-client-demo)
* **Rust**: [Client library](https://github.com/martinthomson/ohttp/tree/main/ohttp-client)
* **JavaScript / TypeScript**: [Client library](https://github.com/chris-wood/ohttp-js)
***
## Step 3 - Review your application
After you have configured your client and server, review your application to make sure you are only sending intended data to Cloudflare and the application backend. In particular, application data should not contain anything unique to an end-user, as this would invalidate the benefits that OHTTP provides.
* Applications should scrub identifying user data from requests forwarded through the Privacy Gateway. This includes, for example, names, email addresses, phone numbers, etc.
* Applications should encourage users to disable crash reporting when using Privacy Gateway. Crash reports can contain sensitive user information and data, including email addresses.
* Where possible, application data should be encrypted on the client device with a key known only to the client. For example, iOS generally has good support for [client-side encryption (and key synchronization via the KeyChain)](https://developer.apple.com/documentation/security/certificate_key_and_trust_services/keys). Android likely has similar features available.
***
## Step 4 - Relay requests through Cloudflare
Before sending any requests, you need to first set up your account with Cloudflare. That requires [contacting us](https://www.cloudflare.com/lp/privacy-edge/) and providing the URL of your application gateway server.
Then, make sure you are forwarding requests to a mutually agreed URL with the following conventions.
```txt
https://.privacy-gateway.cloudflare.com/
```
---
title: Reference · Cloudflare Privacy Gateway docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-gateway/reference/
md: https://developers.cloudflare.com/privacy-gateway/reference/index.md
---
* [Privacy Gateway Metrics](https://developers.cloudflare.com/privacy-gateway/reference/metrics/)
* [Product compatibility](https://developers.cloudflare.com/privacy-gateway/reference/product-compatibility/)
* [Legal](https://developers.cloudflare.com/privacy-gateway/reference/legal/)
* [Limitations](https://developers.cloudflare.com/privacy-gateway/reference/limitations/)
---
title: 404 - Page Not Found · Cloudflare Privacy Proxy docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-proxy/404/
md: https://developers.cloudflare.com/privacy-proxy/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Concepts · Cloudflare Privacy Proxy docs
description: Understand the key concepts behind Privacy Proxy, including how the
protocol works, deployment architectures, and privacy-preserving
authentication.
lastUpdated: 2026-02-03T18:20:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-proxy/concepts/
md: https://developers.cloudflare.com/privacy-proxy/concepts/index.md
---
Understand the key concepts behind Privacy Proxy, including how the protocol works, deployment architectures, and privacy-preserving authentication.
* [How Privacy Proxy works](https://developers.cloudflare.com/privacy-proxy/concepts/how-it-works/)
* [Deployment models](https://developers.cloudflare.com/privacy-proxy/concepts/deployment-models/)
* [Authentication](https://developers.cloudflare.com/privacy-proxy/concepts/authentication/)
* [Geolocation](https://developers.cloudflare.com/privacy-proxy/concepts/geolocation/)
---
title: Get started · Cloudflare Privacy Proxy docs
description: This guide walks you through connecting to Privacy Proxy and
verifying that traffic is proxied correctly.
lastUpdated: 2026-02-03T18:20:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-proxy/get-started/
md: https://developers.cloudflare.com/privacy-proxy/get-started/index.md
---
This guide walks you through connecting to Privacy Proxy and verifying that traffic is proxied correctly.
## Before you begin
Privacy Proxy is a managed service. Before you can connect, Cloudflare will provision an endpoint and provide you with:
* **Proxy endpoint URL**: The hostname for your Privacy Proxy instance (for example, `https://your-proxy.example.com`).
* **Pre-shared key (PSK)**: A secret key for proof-of-concept authentication.
* **Egress IP ranges**: The IP addresses that destination servers will see for proxied traffic.
[Contact us](https://www.cloudflare.com/lp/privacy-edge/) to request access and receive your configuration details.
***
## 1. Configure your client
Privacy Proxy accepts connections over HTTP/2 and HTTP/3 using the HTTP CONNECT method. Because Privacy Proxy requires authentication headers, you cannot configure browsers to connect directly. Instead, use one of the following approaches:
### Use curl for testing locally
For quick tests, use curl with the `--proxy` and `--proxy-header` flags to pass authentication directly:
```sh
curl -v \
--proxy https://your-proxy.example.com \
--proxy-header "Proxy-Authorization: Preshared " \
https://example.com
```
### Use Chaussette
[Chaussette](https://developers.cloudflare.com/privacy-proxy/reference/client-libraries/#chaussette) is a local SOCKS5 proxy that handles authentication and forwards requests to Privacy Proxy.
1. Start Chaussette with your PSK and proxy endpoint:
```sh
MASQUE_PRESHARED_KEY= chaussette \
--listen 127.0.0.1:1987 \
--proxy https://your-proxy.example.com:443
```
2. Configure your browser to use the local SOCKS5 proxy:
```sh
google-chrome --proxy-server="socks5://127.0.0.1:1987"
```
***
## 2. Verify the connection
To confirm that traffic is routing through Privacy Proxy, check your apparent IP address:
```sh
curl -v \
--proxy https://your-proxy.example.com \
--proxy-header "Proxy-Authorization: Preshared " \
https://cloudflare.com/cdn-cgi/trace
```
The response includes connection metadata. Look for the `ip` field, which should show a Cloudflare egress IP address rather than your real IP.
```txt
fl=123f456
h=cloudflare.com
ip=162.159.xxx.xxx
ts=1234567890.123
visit_scheme=https
uag=curl/8.0.0
colo=SJC
http=http/2
loc=US
tls=TLSv1.3
```
The `ip` value confirms the egress IP address used by the proxy.
***
## 3. (Optional) Test geolocation
Privacy Proxy preserves user geolocation by selecting egress IP addresses based on the client's location. You can specify a geohash to test this behavior:
```sh
curl -v \
--proxy https://your-proxy.example.com \
--proxy-header "Proxy-Authorization: Preshared " \
--proxy-header "sec-ch-geohash: xn76c-JP" \
https://cloudflare.com/cdn-cgi/trace
```
The `sec-ch-geohash` header provides a [geohash](https://en.wikipedia.org/wiki/Geohash) that the proxy uses to select an appropriate egress IP. The format is `-`.
The response should show a `loc` value corresponding to the geohash region.
***
## Next steps
* Learn about [deployment models](https://developers.cloudflare.com/privacy-proxy/concepts/deployment-models/) to understand single-hop versus double-hop architectures.
* Review [authentication methods](https://developers.cloudflare.com/privacy-proxy/concepts/authentication/) for production deployments using Privacy Pass.
* Configure [observability](https://developers.cloudflare.com/privacy-proxy/reference/observability/) to monitor proxy traffic with OpenTelemetry.
---
title: Reference · Cloudflare Privacy Proxy docs
description: Technical reference documentation for Privacy Proxy configuration
and monitoring.
lastUpdated: 2026-02-03T18:20:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/privacy-proxy/reference/
md: https://developers.cloudflare.com/privacy-proxy/reference/index.md
---
Technical reference documentation for Privacy Proxy configuration and monitoring.
* [Observability](https://developers.cloudflare.com/privacy-proxy/reference/observability/)
* [HTTP headers](https://developers.cloudflare.com/privacy-proxy/reference/http-headers/)
* [Client libraries](https://developers.cloudflare.com/privacy-proxy/reference/client-libraries/)
---
title: 404 - Page Not Found · Pulumi docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pulumi/404/
md: https://developers.cloudflare.com/pulumi/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Get started · Pulumi docs
description: Follow the recommended steps for your operating system below. For
official instructions on installing Pulumi and other install options, refer to
Install Pulumi.
lastUpdated: 2024-08-20T19:58:51.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pulumi/installing/
md: https://developers.cloudflare.com/pulumi/installing/index.md
---
Follow the recommended steps for your operating system below. For official instructions on installing Pulumi and other install options, refer to [Install Pulumi](https://www.pulumi.com/docs/install/).
Note
Pulumi is free, open source, and optionally pairs with the [Pulumi Cloud](https://www.pulumi.com/product/pulumi-cloud/) to make managing infrastructure secure, reliable, and hassle-free.
Warning
To avoid resource management conflicts, it’s **always** recommended to manage Pulumi-controlled resources via Pulumi.
## Installation
### Mac
Install via Homebrew package manager.
```sh
brew install pulumi/tap/pulumi
```
### Linux
Use the installation script.
```sh
curl -fsSL https://get.pulumi.com | sh
```
### Windows
1. Download the latest installer from the [Pulumi Repository](https://github.com/pulumi/pulumi-winget/releases/latest)
2. Double click the MSI file and complete the wizard.
## Verify installation
To verify your installation, run the following in the terminal:
```sh
pulumi version
```
Note
For upgrades and installation alternatives, refer to [Install Pulumi](https://www.pulumi.com/docs/install/).
## Next steps
Follow the [Hello World tutorial](https://developers.cloudflare.com/pulumi/tutorial/hello-world/) to write a simple Pulumi program. It takes about 10 minutes to complete.
---
title: Tutorials · Pulumi docs
description: Before you begin, make sure you install Pulumi.
lastUpdated: 2024-09-04T14:10:21.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/pulumi/tutorial/
md: https://developers.cloudflare.com/pulumi/tutorial/index.md
---
Before you begin, make sure you [install Pulumi](https://developers.cloudflare.com/pulumi/installing/).
1. [Add a Site](https://developers.cloudflare.com/pulumi/tutorial/add-site/)
* Bring your existing site under Cloudflare with Pulumi IaC.
* Introduction of `pulumi new`, `up`, and `destroy`.
* Cloudflare resources defined: Zone and DNS records.
2. [Manage secrets](https://developers.cloudflare.com/pulumi/tutorial/manage-secrets/)
* Develop Workers securely with Pulumi ESC and Wrangler.
* Introduction to the ESC CLI and the Wrangler CLI.
* Manage Cloudflare credentials, Worker secrets, and `.dev.vars`.
3. [Deploy a Worker](https://developers.cloudflare.com/pulumi/tutorial/hello-world/)
* Brief introduction to deploying a Cloudflare Workers application with Pulumi.
* Introduction of `pulumi new`, `up`, and `destroy`.
* Cloudflare resources defined: Worker script, Worker route, and DNS record.
---
title: 404 - Page Not Found · Cloudflare Queues docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/404/
md: https://developers.cloudflare.com/queues/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Configuration · Cloudflare Queues docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/configuration/
md: https://developers.cloudflare.com/queues/configuration/index.md
---
* [Configure Queues](https://developers.cloudflare.com/queues/configuration/configure-queues/)
* [Batching, Retries and Delays](https://developers.cloudflare.com/queues/configuration/batching-retries/)
* [Pause and Purge](https://developers.cloudflare.com/queues/configuration/pause-purge/)
* [Dead Letter Queues](https://developers.cloudflare.com/queues/configuration/dead-letter-queues/)
* [Pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/)
* [Consumer concurrency](https://developers.cloudflare.com/queues/configuration/consumer-concurrency/)
* [JavaScript APIs](https://developers.cloudflare.com/queues/configuration/javascript-apis/)
* [Local Development](https://developers.cloudflare.com/queues/configuration/local-development/)
* [R2 Event Notifications](https://developers.cloudflare.com/r2/buckets/event-notifications/)
---
title: Demos and architectures · Cloudflare Queues docs
description: Learn how you can use Queues within your existing application and architecture.
lastUpdated: 2026-01-29T15:12:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/demos/
md: https://developers.cloudflare.com/queues/demos/index.md
---
Learn how you can use Queues within your existing application and architecture.
## Reference architectures
Explore the following reference architectures that use Queues:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Serverless ETL pipelines](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-etl/)
[Cloudflare enables fully serverless ETL pipelines, significantly reducing complexity, accelerating time to production, and lowering overall costs.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-etl/)
[Retrieval Augmented Generation (RAG)](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
[RAG combines retrieval with generative models for better text. It uses external knowledge to create factual, relevant responses, improving coherence and accuracy in NLP tasks like chatbots.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
---
title: Event subscriptions overview · Cloudflare Queues docs
description: Subscribe to events from Cloudflare services to build custom
workflows, integrations, and logic with Workers.
lastUpdated: 2025-08-19T15:48:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/event-subscriptions/
md: https://developers.cloudflare.com/queues/event-subscriptions/index.md
---
Event subscriptions allow you to receive messages when events occur across your Cloudflare account. Cloudflare products (e.g., [KV](https://developers.cloudflare.com/kv/), [Workers AI](https://developers.cloudflare.com/workers-ai), [Workers](https://developers.cloudflare.com/workers)) can publish structured events to a queue, which you can then consume with Workers or [HTTP pull consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/) to build custom workflows, integrations, or logic.

## What is an event?
An event is a structured record of something happening in your Cloudflare account – like a Workers AI batch request being queued, a Worker build completing, or an R2 bucket being created. When you subscribe to these events, your queue will automatically start receiving messages when the events occur.
## Learn more
[Manage event subscriptions ](https://developers.cloudflare.com/queues/event-subscriptions/manage-event-subscriptions/)Learn how to create, configure, and manage event subscriptions for your queues.
[Events & schemas ](https://developers.cloudflare.com/queues/event-subscriptions/events-schemas/)Explore available event types and their corresponding data schemas.
---
title: Cloudflare Queues - Examples · Cloudflare Queues docs
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/examples/
md: https://developers.cloudflare.com/queues/examples/index.md
---
[Queues - Publish Directly via HTTP](https://developers.cloudflare.com/queues/examples/publish-to-a-queue-via-http/)
[Publish to a Queue directly via HTTP and Workers.](https://developers.cloudflare.com/queues/examples/publish-to-a-queue-via-http/)
[Queues - Publish Directly via a Worker](https://developers.cloudflare.com/queues/examples/publish-to-a-queue-via-workers/)
[Publish to a Queue directly from your Worker.](https://developers.cloudflare.com/queues/examples/publish-to-a-queue-via-workers/)
[Queues - Use Queues and Durable Objects](https://developers.cloudflare.com/queues/examples/use-queues-with-durable-objects/)
[Publish to a queue from within a Durable Object.](https://developers.cloudflare.com/queues/examples/use-queues-with-durable-objects/)
[Cloudflare Queues - Listing and acknowledging messages from the dashboard](https://developers.cloudflare.com/queues/examples/list-messages-from-dash/)
[Use the dashboard to fetch and acknowledge the messages currently in a queue.](https://developers.cloudflare.com/queues/examples/list-messages-from-dash/)
[Cloudflare Queues - Sending messages from the dashboard](https://developers.cloudflare.com/queues/examples/send-messages-from-dash/)
[Use the dashboard to send messages to a queue.](https://developers.cloudflare.com/queues/examples/send-messages-from-dash/)
[Cloudflare Queues - Queues & R2](https://developers.cloudflare.com/queues/examples/send-errors-to-r2/)
[Example of how to use Queues to batch data and store it in an R2 bucket.](https://developers.cloudflare.com/queues/examples/send-errors-to-r2/)
---
title: Getting started · Cloudflare Queues docs
description: Cloudflare Queues is a flexible messaging queue that allows you to
queue messages for asynchronous processing. By following this guide, you will
create your first queue, a Worker to publish messages to that queue, and a
consumer Worker to consume messages from that queue.
lastUpdated: 2026-01-29T10:38:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/get-started/
md: https://developers.cloudflare.com/queues/get-started/index.md
---
Cloudflare Queues is a flexible messaging queue that allows you to queue messages for asynchronous processing. By following this guide, you will create your first queue, a Worker to publish messages to that queue, and a consumer Worker to consume messages from that queue.
## Prerequisites
To use Queues, you will need:
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
## 1. Create a Worker project
You will access your queue from a Worker, the producer Worker. You must create at least one producer Worker to publish messages onto your queue. If you are using [R2 Bucket Event Notifications](https://developers.cloudflare.com/r2/buckets/event-notifications/), then you do not need a producer Worker.
To create a producer Worker, run:
* npm
```sh
npm create cloudflare@latest -- producer-worker
```
* yarn
```sh
yarn create cloudflare producer-worker
```
* pnpm
```sh
pnpm create cloudflare@latest producer-worker
```
For setup, select the following options:
* For *What would you like to start with?*, choose `Hello World example`.
* For *Which template would you like to use?*, choose `Worker only`.
* For *Which language do you want to use?*, choose `TypeScript`.
* For *Do you want to use git for version control?*, choose `Yes`.
* For *Do you want to deploy your application?*, choose `No` (we will be making some changes before deploying).
This will create a new directory, which will include both a `src/index.ts` Worker script, and a [`wrangler.jsonc`](https://developers.cloudflare.com/workers/wrangler/configuration/) configuration file. After you create your Worker, you will create a Queue to access.
Move into the newly created directory:
```sh
cd producer-worker
```
## 2. Create a queue
To use queues, you need to create at least one queue to publish messages to and consume messages from.
To create a queue, run:
```sh
npx wrangler queues create
```
Choose a name that is descriptive and relates to the types of messages you intend to use this queue for. Descriptive queue names look like: `debug-logs`, `user-clickstream-data`, or `password-reset-prod`.
Queue names must be 1 to 63 characters long. Queue names cannot contain special characters outside dashes (`-`), and must start and end with a letter or number.
You cannot change your queue name after you have set it. After you create your queue, you will set up your producer Worker to access it.
## 3. Set up your producer Worker
To expose your queue to the code inside your Worker, you need to connect your queue to your Worker by creating a binding. [Bindings](https://developers.cloudflare.com/workers/runtime-apis/bindings/) allow your Worker to access resources, such as Queues, on the Cloudflare developer platform.
To create a binding, open your newly generated `wrangler.jsonc` file and add the following:
* wrangler.jsonc
```jsonc
{
"queues": {
"producers": [
{
"queue": "MY-QUEUE-NAME",
"binding": "MY_QUEUE"
}
]
}
}
```
* wrangler.toml
```toml
[[queues.producers]]
queue = "MY-QUEUE-NAME"
binding = "MY_QUEUE"
```
Replace `MY-QUEUE-NAME` with the name of the queue you created in [step 2](https://developers.cloudflare.com/queues/get-started/#2-create-a-queue). Next, replace `MY_QUEUE` with the name you want for your `binding`. The binding must be a valid JavaScript variable name. This is the variable you will use to reference this queue in your Worker.
### Write your producer Worker
You will now configure your producer Worker to create messages to publish to your queue. Your producer Worker will:
1. Take a request it receives from the browser.
2. Transform the request to JSON format.
3. Write the request directly to your queue.
In your Worker project directory, open the `src` folder and add the following to your `index.ts` file:
```ts
export default {
async fetch(request, env, ctx): Promise {
let log = {
url: request.url,
method: request.method,
headers: Object.fromEntries(request.headers),
};
await env..send(log);
return new Response('Success!');
},
} satisfies ExportedHandler;
```
Replace `MY_QUEUE` with the name you have set for your binding from your `wrangler.jsonc` file.
Also add the queue to `Env` interface in `index.ts`.
```ts
export interface Env {
: Queue;
}
```
If this write fails, your Worker will return an error (raise an exception). If this write works, it will return `Success` back with a HTTP `200` status code to the browser.
In a production application, you would likely use a [`try...catch`](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Statements/try...catch) statement to catch the exception and handle it directly (for example, return a custom error or even retry).
### Publish your producer Worker
With your Wrangler file and `index.ts` file configured, you are ready to publish your producer Worker. To publish your producer Worker, run:
```sh
npx wrangler deploy
```
You should see output that resembles the below, with a `*.workers.dev` URL by default.
```plaintext
Uploaded (0.76 sec)
Published (0.29 sec)
https://..workers.dev
```
Copy your `*.workers.dev` subdomain and paste it into a new browser tab. Refresh the page a few times to start publishing requests to your queue. Your browser should return the `Success` response after writing the request to the queue each time.
You have built a queue and a producer Worker to publish messages to the queue. You will now create a consumer Worker to consume the messages published to your queue. Without a consumer Worker, the messages will stay on the queue until they expire, which defaults to four (4) days.
## 4. Create your consumer Worker
A consumer Worker receives messages from your queue. When the consumer Worker receives your queue's messages, it can write them to another source, such as a logging console or storage objects.
In this guide, you will create a consumer Worker and use it to log and inspect the messages with [`wrangler tail`](https://developers.cloudflare.com/workers/wrangler/commands/#tail). You will create your consumer Worker in the same Worker project that you created your producer Worker.
Note
Queues also supports [pull-based consumers](https://developers.cloudflare.com/queues/configuration/pull-consumers/), which allows any HTTP-based client to consume messages from a queue. This guide creates a push-based consumer using Cloudflare Workers.
To create a consumer Worker, open your `index.ts` file and add the following `queue` handler to your existing `fetch` handler:
```ts
export default {
async fetch(request, env, ctx): Promise {
let log = {
url: request.url,
method: request.method,
headers: Object.fromEntries(request.headers),
};
await env..send(log);
return new Response('Success!');
},
async queue(batch, env): Promise {
let messages = JSON.stringify(batch.messages);
console.log(`consumed from our queue: ${messages}`);
},
} satisfies ExportedHandler;
```
Replace `MY_QUEUE` with the name you have set for your binding from your `wrangler.jsonc` file.
Every time messages are published to the queue, your consumer Worker's `queue` handler (`async queue`) is called and it is passed one or more messages.
In this example, your consumer Worker transforms the queue's JSON formatted message into a string and logs that output. In a real world application, your consumer Worker can be configured to write messages to object storage (such as [R2](https://developers.cloudflare.com/r2/)), write to a database (like [D1](https://developers.cloudflare.com/d1/)), further process messages before calling an external API (such as an [email API](https://developers.cloudflare.com/workers/tutorials/)) or a data warehouse with your legacy cloud provider.
When performing asynchronous tasks from within your consumer handler, use `waitUntil()` to ensure the response of the function is handled. Other asynchronous methods are not supported within the scope of this method.
### Connect the consumer Worker to your queue
After you have configured your consumer Worker, you are ready to connect it to your queue.
Each queue can only have one consumer Worker connected to it. If you try to connect multiple consumers to the same queue, you will encounter an error when attempting to publish that Worker.
To connect your queue to your consumer Worker, open your Wrangler file and add this to the bottom:
* wrangler.jsonc
```jsonc
{
"queues": {
"consumers": [
{
"queue": "",
// Required: this should match the name of the queue you created in step 3.
// If you misspell the name, you will receive an error when attempting to publish your Worker.
"max_batch_size": 10, // optional: defaults to 10
"max_batch_timeout": 5 // optional: defaults to 5 seconds
}
]
}
}
```
* wrangler.toml
```toml
[[queues.consumers]]
queue = ""
max_batch_size = 10
max_batch_timeout = 5
```
Replace `MY-QUEUE-NAME` with the queue you created in [step 2](https://developers.cloudflare.com/queues/get-started/#2-create-a-queue).
In your consumer Worker, you are using queues to auto batch messages using the `max_batch_size` option and the `max_batch_timeout` option. The consumer Worker will receive messages in batches of `10` or every `5` seconds, whichever happens first.
`max_batch_size` (defaults to 10) helps to reduce the amount of times your consumer Worker needs to be called. Instead of being called for every message, it will only be called after 10 messages have entered the queue.
`max_batch_timeout` (defaults to 5 seconds) helps to reduce wait time. If the producer Worker is not sending up to 10 messages to the queue for the consumer Worker to be called, the consumer Worker will be called every 5 seconds to receive messages that are waiting in the queue.
### Publish your consumer Worker
With your Wrangler file and `index.ts` file configured, publish your consumer Worker by running:
```sh
npx wrangler deploy
```
## 5. Read messages from your queue
After you set up consumer Worker, you can read messages from the queue.
Run `wrangler tail` to start waiting for our consumer to log the messages it receives:
```sh
npx wrangler tail
```
With `wrangler tail` running, open the Worker URL you opened in [step 3](https://developers.cloudflare.com/queues/get-started/#3-set-up-your-producer-worker).
You should receive a `Success` message in your browser window.
If you receive a `Success` message, refresh the URL a few times to generate messages and push them onto the queue.
With `wrangler tail` running, your consumer Worker will start logging the requests generated by refreshing.
If you refresh less than 10 times, it may take a few seconds for the messages to appear because batch timeout is configured for 10 seconds. After 10 seconds, messages should arrive in your terminal.
If you get errors when you refresh, check that the queue name you created in [step 2](https://developers.cloudflare.com/queues/get-started/#2-create-a-queue) and the queue you referenced in your Wrangler file is the same. You should ensure that your producer Worker is returning `Success` and is not returning an error.
By completing this guide, you have now created a queue, a producer Worker that publishes messages to that queue, and a consumer Worker that consumes those messages from it.
## Related resources
* Learn more about [Cloudflare Workers](https://developers.cloudflare.com/workers/) and the applications you can build on Cloudflare.
---
title: Glossary · Cloudflare Queues docs
description: Review the definitions for terms used across Cloudflare's Queues documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/glossary/
md: https://developers.cloudflare.com/queues/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Queues documentation.
| Term | Definition |
| - | - |
| consumer | A consumer is the term for a client that is subscribing to or consuming messages from a queue. |
| producer | A producer is the term for a client that is publishing or producing messages on to a queue. |
| queue | A queue is a buffer or list that automatically scales as messages are written to it, and allows a consumer Worker to pull messages from that same queue. |
---
title: Observability · Cloudflare Queues docs
lastUpdated: 2025-02-27T10:30:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/queues/observability/
md: https://developers.cloudflare.com/queues/observability/index.md
---
* [Metrics](https://developers.cloudflare.com/queues/observability/metrics/)
---
title: Queues REST API · Cloudflare Queues docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/queues-api/
md: https://developers.cloudflare.com/queues/queues-api/index.md
---
---
title: Reference · Cloudflare Queues docs
lastUpdated: 2025-02-27T10:30:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/queues/reference/
md: https://developers.cloudflare.com/queues/reference/index.md
---
* [How Queues Works](https://developers.cloudflare.com/queues/reference/how-queues-works/)
* [Delivery guarantees](https://developers.cloudflare.com/queues/reference/delivery-guarantees/)
* [Wrangler commands](https://developers.cloudflare.com/queues/reference/wrangler-commands/)
---
title: Platform · Cloudflare Queues docs
lastUpdated: 2025-02-27T10:30:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/queues/platform/
md: https://developers.cloudflare.com/queues/platform/index.md
---
* [Pricing](https://developers.cloudflare.com/queues/platform/pricing/)
* [Limits](https://developers.cloudflare.com/queues/platform/limits/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
* [Changelog](https://developers.cloudflare.com/queues/platform/changelog/)
* [Audit Logs](https://developers.cloudflare.com/queues/platform/audit-logs/)
---
title: Tutorials · Cloudflare Queues docs
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/queues/tutorials/
md: https://developers.cloudflare.com/queues/tutorials/index.md
---
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [Use event notification to summarize PDF files on upload](https://developers.cloudflare.com/r2/tutorials/summarize-pdf/) | over 1 year ago | Intermediate |
| [Handle rate limits of external APIs](https://developers.cloudflare.com/queues/tutorials/handle-rate-limits/) | over 1 year ago | Beginner |
| [Build a web crawler with Queues and Browser Rendering](https://developers.cloudflare.com/queues/tutorials/web-crawler-with-browser-rendering/) | over 1 year ago | Intermediate |
| [Log and store upload events in R2 with event notifications](https://developers.cloudflare.com/r2/tutorials/upload-logs-event-notifications/) | almost 2 years ago | Beginner |
## Videos
Cloudflare Workflows | Introduction (Part 1 of 3)
In this video, we introduce Cloudflare Workflows, the Newest Developer Platform Primitive at Cloudflare.
Cloudflare Workflows | Batching and Monitoring Your Durable Execution (Part 2 of 3)
Workflows exposes metrics such as execution, error rates, steps, and total duration!
---
title: 404 - Page Not Found · R2 SQL docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2-sql/404/
md: https://developers.cloudflare.com/r2-sql/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Getting started · R2 SQL docs
description: Create your first pipeline to ingest streaming data and write to R2
Data Catalog as an Apache Iceberg table.
lastUpdated: 2025-11-17T14:08:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2-sql/get-started/
md: https://developers.cloudflare.com/r2-sql/get-started/index.md
---
This guide will instruct you through:
* Creating your first [R2 bucket](https://developers.cloudflare.com/r2/buckets/) and enabling its [data catalog](https://developers.cloudflare.com/r2/data-catalog/).
* Creating an [API token](https://developers.cloudflare.com/r2/api/tokens/) needed for pipelines to authenticate with your data catalog.
* Creating your first pipeline with a simple ecommerce schema that writes to an [Apache Iceberg](https://iceberg.apache.org/) table managed by R2 Data Catalog.
* Sending sample ecommerce data via HTTP endpoint.
* Validating data in your bucket and querying it with R2 SQL.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
## 1. Create an R2 bucket
* Wrangler CLI
1. If not already logged in, run:
```plaintext
npx wrangler login
```
2. Create an R2 bucket:
```plaintext
npx wrangler r2 bucket create pipelines-tutorial
```
* Dashboard
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
2. Select **Create bucket**.
3. Enter the bucket name: pipelines-tutorial
4. Select **Create bucket**.
## 2. Enable R2 Data Catalog
* Wrangler CLI
Enable the catalog on your R2 bucket:
```plaintext
npx wrangler r2 bucket catalog enable pipelines-tutorial
```
When you run this command, take note of the "Warehouse" and "Catalog URI". You will need these later.
* Dashboard
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
2. Select the bucket: pipelines-tutorial.
3. Switch to the **Settings** tab, scroll down to **R2 Data Catalog**, and select **Enable**.
4. Once enabled, note the **Catalog URI** and **Warehouse name**.
## 3. Create an API token
Pipelines must authenticate to R2 Data Catalog with an [R2 API token](https://developers.cloudflare.com/r2/api/tokens/) that has catalog and R2 permissions.
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
2. Select **Manage API tokens**.
3. Select **Create Account API token**.
4. Give your API token a name.
5. Under **Permissions**, choose the **Admin Read & Write** permission.
6. Select **Create Account API Token**.
7. Note the **Token value**.
Note
This token also includes the R2 SQL Read permission, which allows you to query your data with R2 SQL.
## 4. Create a pipeline
* Wrangler CLI
First, create a schema file that defines your ecommerce data structure:
**Create `schema.json`:**
```json
{
"fields": [
{
"name": "user_id",
"type": "string",
"required": true
},
{
"name": "event_type",
"type": "string",
"required": true
},
{
"name": "product_id",
"type": "string",
"required": false
},
{
"name": "amount",
"type": "float64",
"required": false
}
]
}
```
Use the interactive setup to create a pipeline that writes to R2 Data Catalog:
```bash
npx wrangler pipelines setup
```
Follow the prompts:
1. **Pipeline name**: Enter `ecommerce`
2. **Stream configuration**:
* Enable HTTP endpoint: `yes`
* Require authentication: `no` (for simplicity)
* Configure custom CORS origins: `no`
* Schema definition: `Load from file`
* Schema file path: `schema.json` (or your file path)
3. **Sink configuration**:
* Destination type: `Data Catalog Table`
* R2 bucket name: `pipelines-tutorial`
* Namespace: `default`
* Table name: `ecommerce`
* Catalog API token: Enter your token from step 3
* Compression: `zstd`
* Roll file when size reaches (MB): `100`
* Roll file when time reaches (seconds): `10` (for faster data visibility in this tutorial)
4. **SQL transformation**: Choose `Use simple ingestion query` to use:
```sql
INSERT INTO ecommerce_sink SELECT * FROM ecommerce_stream
```
After setup completes, note the HTTP endpoint URL displayed in the final output.
* Dashboard
1. In the Cloudflare dashboard, go to **Pipelines** > **Pipelines**.
[Go to **Pipelines**](https://dash.cloudflare.com/?to=/:account/pipelines/overview)
2. Select **Create Pipeline**.
3. **Connect to a Stream**:
* Pipeline name: `ecommerce`
* Enable HTTP endpoint for sending data: Enabled
* HTTP authentication: Disabled (default)
* Select **Next**
4. **Define Input Schema**:
* Select **JSON editor**
* Copy in the schema:
```json
{
"fields": [
{
"name": "user_id",
"type": "string",
"required": true
},
{
"name": "event_type",
"type": "string",
"required": true
},
{
"name": "product_id",
"type": "string",
"required": false
},
{
"name": "amount",
"type": "f64",
"required": false
}
]
}
```
* Select **Next**
5. **Define Sink**:
* Select your R2 bucket: `pipelines-tutorial`
* Storage type: **R2 Data Catalog**
* Namespace: `default`
* Table name: `ecommerce`
* **Advanced Settings**: Change **Maximum Time Interval** to `10 seconds`
* Select **Next**
6. **Credentials**:
* Disable **Automatically create an Account API token for your sink**
* Enter **Catalog Token** from step 3
* Select **Next**
7. **Pipeline Definition**:
* Leave the default SQL query:
```sql
INSERT INTO ecommerce_sink SELECT * FROM ecommerce_stream;
```
* Select **Create Pipeline**
8. After pipeline creation, note the **Stream ID** for the next step.
## 5. Send sample data
Send ecommerce events to your pipeline's HTTP endpoint:
```bash
curl -X POST https://{stream-id}.ingest.cloudflare.com \
-H "Content-Type: application/json" \
-d '[
{
"user_id": "user_12345",
"event_type": "purchase",
"product_id": "widget-001",
"amount": 29.99
},
{
"user_id": "user_67890",
"event_type": "view_product",
"product_id": "widget-002"
},
{
"user_id": "user_12345",
"event_type": "add_to_cart",
"product_id": "widget-003",
"amount": 15.50
}
]'
```
Replace `{stream-id}` with your actual stream endpoint from the pipeline setup.
## 6. Validate data in your bucket
1. In the Cloudflare dashboard, go to the **R2 object storage** page.
2. Select your bucket: `pipelines-tutorial`.
3. You should see Iceberg metadata files and data files created by your pipeline. Note: If you aren't seeing any files in your bucket, try waiting a couple of minutes and trying again.
4. The data is organized in the Apache Iceberg format with metadata tracking table versions.
## 7. Query your data using R2 SQL
Set up your environment to use R2 SQL:
```bash
export WRANGLER_R2_SQL_AUTH_TOKEN=YOUR_API_TOKEN
```
Or create a `.env` file with:
```plaintext
WRANGLER_R2_SQL_AUTH_TOKEN=YOUR_API_TOKEN
```
Where `YOUR_API_TOKEN` is the token you created in step 3. For more information on setting environment variables, refer to [Wrangler system environment variables](https://developers.cloudflare.com/workers/wrangler/system-environment-variables/).
Query your data:
```bash
npx wrangler r2 sql query "YOUR_WAREHOUSE_NAME" "
SELECT
user_id,
event_type,
product_id,
amount
FROM default.ecommerce
WHERE event_type = 'purchase'
LIMIT 10"
```
Replace `YOUR_WAREHOUSE_NAME` with the warehouse name from step 2.
You can also query this table with any engine that supports Apache Iceberg. To learn more about connecting other engines to R2 Data Catalog, refer to [Connect to Iceberg engines](https://developers.cloudflare.com/r2/data-catalog/config-examples/).
## Learn more
[Managing R2 Data Catalogs ](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/)Enable or disable R2 Data Catalog on your bucket, retrieve configuration details, and authenticate your Iceberg engine.
[Try another example ](https://developers.cloudflare.com/r2-sql/tutorials/end-to-end-pipeline)Detailed tutorial for setting up a simple fraud detection data pipeline, and generate events for it in Python.
[Pipelines ](https://developers.cloudflare.com/pipelines/)Understand SQL transformations and pipeline configuration.
---
title: Platform · R2 SQL docs
lastUpdated: 2025-09-25T04:13:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/r2-sql/platform/
md: https://developers.cloudflare.com/r2-sql/platform/index.md
---
---
title: Query data · R2 SQL docs
description: Understand how to query data with R2 SQL
lastUpdated: 2025-10-23T14:34:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2-sql/query-data/
md: https://developers.cloudflare.com/r2-sql/query-data/index.md
---
Query [Apache Iceberg](https://iceberg.apache.org/) tables managed by [R2 Data Catalog](https://developers.cloudflare.com/r2/data-catalog/). R2 SQL queries can be made via [Wrangler](https://developers.cloudflare.com/workers/wrangler/) or HTTP API.
## Get your warehouse name
To query data with R2 SQL, you'll need your warehouse name associated with your [catalog](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/). To retrieve it, you can run the [`r2 bucket catalog get` command](https://developers.cloudflare.com/workers/wrangler/commands/#r2-bucket-catalog-get):
```bash
npx wrangler r2 bucket catalog get
```
Alternatively, you can find it in the dashboard by going to the **R2 object storage** page, selecting the bucket, switching to the **Settings** tab, scrolling to **R2 Data Catalog**, and finding **Warehouse name**.
## Query via Wrangler
To begin, install [`npm`](https://docs.npmjs.com/getting-started). Then [install Wrangler, the Developer Platform CLI](https://developers.cloudflare.com/workers/wrangler/install-and-update/).
Wrangler needs an API token with permissions to access R2 Data Catalog, R2 storage, and R2 SQL to execute queries. The `r2 sql query` command looks for the token in the `WRANGLER_R2_SQL_AUTH_TOKEN` environment variable.
Set up your environment:
```bash
export WRANGLER_R2_SQL_AUTH_TOKEN=YOUR_API_TOKEN
```
Or create a `.env` file with:
```plaintext
WRANGLER_R2_SQL_AUTH_TOKEN=YOUR_API_TOKEN
```
Where `YOUR_API_TOKEN` is the token you created with the [required permissions](#authentication). For more information on setting environment variables, refer to [Wrangler system environment variables](https://developers.cloudflare.com/workers/wrangler/system-environment-variables/).
To run a SQL query, run the [`r2 sql query` command](https://developers.cloudflare.com/workers/wrangler/commands/#r2-sql-query):
```bash
npx wrangler r2 sql query "SELECT * FROM namespace.table_name limit 10;"
```
For a full list of supported sql commands, refer to the [R2 SQL reference page](https://developers.cloudflare.com/r2-sql/sql-reference).
## Query via API
Below is an example of using R2 SQL via the REST endpoint:
```bash
curl -X POST \
"https://api.sql.cloudflarestorage.com/api/v1/accounts/{ACCOUNT_ID}/r2-sql/query/{BUCKET_NAME}" \
-H "Authorization: Bearer ${WRANGLER_R2_SQL_AUTH_TOKEN}" \
-H "Content-Type: application/json" \
-d '{
"query": "SELECT * FROM namespace.table_name limit 10;"
}'
```
The API requires an API token with the appropriate permissions in the Authorization header. Refer to [Authentication](#authentication) for details on creating a token.
For a full list of supported sql commands, refer to the [R2 SQL reference page](https://developers.cloudflare.com/r2-sql/sql-reference).
## Authentication
To query data with R2 SQL, you must provide a Cloudflare API token with R2 SQL, R2 Data Catalog, and R2 storage permissions. R2 SQL requires these permissions to access catalog metadata and read the underlying data files stored in R2.
### Create API token in the dashboard
Create an [R2 API token](https://developers.cloudflare.com/r2/api/tokens/#permissions) with the following permissions:
* Access to R2 Data Catalog (read-only)
* Access to R2 storage (Admin read/write)
* Access to R2 SQL (read-only)
Use this token value for the `WRANGLER_R2_SQL_AUTH_TOKEN` environment variable when querying with Wrangler, or in the Authorization header when using the REST API.
### Create API token via API
To create an API token programmatically for use with R2 SQL, you'll need to specify R2 SQL, R2 Data Catalog, and R2 storage permission groups in your [Access Policy](https://developers.cloudflare.com/r2/api/tokens/#access-policy).
#### Example Access Policy
```json
[
{
"id": "f267e341f3dd4697bd3b9f71dd96247f",
"effect": "allow",
"resources": {
"com.cloudflare.edge.r2.bucket.4793d734c0b8e484dfc37ec392b5fa8a_default_my-bucket": "*",
"com.cloudflare.edge.r2.bucket.4793d734c0b8e484dfc37ec392b5fa8a_eu_my-eu-bucket": "*"
},
"permission_groups": [
{
"id": "f45430d92e2b4a6cb9f94f2594c141b8",
"name": "Workers R2 SQL Read"
},
{
"id": "d229766a2f7f4d299f20eaa8c9b1fde9",
"name": "Workers R2 Data Catalog Write"
},
{
"id": "bf7481a1826f439697cb59a20b22293e",
"name": "Workers R2 Storage Write"
}
]
}
]
```
To learn more about how to create API tokens for R2 SQL using the API, including required permission groups and usage examples, refer to the [Create API tokens via API documentation](https://developers.cloudflare.com/r2/api/tokens/#create-api-tokens-via-api).
## Additional resources
[Manage R2 Data Catalogs ](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/)Enable or disable R2 Data Catalog on your bucket, retrieve configuration details, and authenticate your Iceberg engine.
[Build an end to end data pipeline ](https://developers.cloudflare.com/r2-sql/tutorials/end-to-end-pipeline)Detailed tutorial for setting up a simple fraud detection data pipeline, and generate events for it in Python.
---
title: Reference · R2 SQL docs
lastUpdated: 2025-09-25T04:13:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/r2-sql/reference/
md: https://developers.cloudflare.com/r2-sql/reference/index.md
---
---
title: SQL reference · R2 SQL docs
description: Comprehensive reference for SQL syntax and data types supported in R2 SQL.
lastUpdated: 2025-12-12T16:58:55.000Z
chatbotDeprioritize: false
tags: SQL
source_url:
html: https://developers.cloudflare.com/r2-sql/sql-reference/
md: https://developers.cloudflare.com/r2-sql/sql-reference/index.md
---
Note
R2 SQL is in public beta. Supported SQL grammar may change over time.
This page documents the R2 SQL syntax based on the currently supported grammar in public beta.
***
## Query Syntax
```sql
SELECT column_list | aggregation_function
FROM table_name
WHERE conditions --optional
[GROUP BY column_list]
[HAVING conditions]
[ORDER BY column_name [DESC | ASC]]
[LIMIT number]
```
***
## Schema Discovery Commands
R2 SQL supports metadata queries to explore available namespaces and tables.
### SHOW DATABASES
Lists all available namespaces.
```sql
SHOW DATABASES;
```
### SHOW NAMESPACES
Alias for `SHOW DATABASES`. Lists all available namespaces.
```sql
SHOW NAMESPACES;
```
### SHOW TABLES
Lists all tables within a specific namespace.
```sql
SHOW TABLES IN namespace_name;
```
### DESCRIBE
Describes the structure of a table, showing column names and data types.
```sql
DESCRIBE namespace_name.table_name;
```
***
## SELECT Clause
### Syntax
```sql
SELECT column_specification [, column_specification, ...]
```
### Column Specification
* **Column name**: `column_name`
* **All columns**: `*`
### Examples
```sql
SELECT * FROM namespace_name.table_name
SELECT user_id FROM namespace_name.table_name
SELECT user_id, timestamp, status FROM namespace_name.table_name
SELECT timestamp, user_id, response_code FROM namespace_name.table_name
```
***
## Aggregation Functions
### Syntax
```sql
SELECT aggregation_function(column_name)
FROM table_name
GROUP BY column_list
```
### Supported Functions
* **COUNT(\*)**: Counts total rows **note**: only `*` is supported
* **SUM(column)**: Sums numeric values
* **AVG(column)**: Calculates average of numeric values
* **MIN(column)**: Finds minimum value
* **MAX(column)**: Finds maximum value
### Examples
```sql
-- Count rows by department
SELECT department, COUNT(*)
FROM my_namespace.sales_data
GROUP BY department
-- Sum decimal values
SELECT region, SUM(total_amount)
FROM my_namespace.sales_data
GROUP BY region
-- Average by category
SELECT category, AVG(price)
FROM my_namespace.products
GROUP BY category
-- Min and Max
SELECT department, MIN(salary), MAX(salary)
FROM my_namespace.employees
GROUP BY department
-- Invalid: No aliases
SELECT department, COUNT(*) AS total FROM my_namespace.sales_data GROUP BY department
-- Invalid: COUNT column name
SELECT COUNT(department) FROM my_namespace.sales_data
```
***
## FROM Clause
### Syntax
```sql
SELECT * FROM table_name
```
***
## WHERE Clause
### Syntax
```sql
SELECT * WHERE condition [AND|OR condition ...]
```
### Conditions
#### Null Checks
* `column_name IS NULL`
* `column_name IS NOT NULL`
#### Value Comparisons
* `column_name BETWEEN value' AND 'value`
* `column_name = value`
* `column_name >= value`
* `column_name > value`
* `column_name <= value`
* `column_name < value`
* `column_name != value`
* `column_name LIKE 'value%'`
#### Logical Operators
* `AND` - Logical AND
* `OR` - Logical OR
### Data Types
* **integer** - Whole numbers
* **float** - Decimal numbers
* **string** - Text values (quoted)
* **timestamp** - RFC3339 format (`'YYYY-DD-MMT-HH:MM:SSZ'`)
* **date** - Date32/Data64 expressed as a string (`'YYYY-MM-DD'`)
* **boolean** - Explicitly valued (true, false)
### Examples
```sql
SELECT * FROM namespace_name.table_name WHERE timestamp BETWEEN '2025-09-24T01:00:00Z' AND '2025-09-25T01:00:00Z'
SELECT * FROM namespace_name.table_name WHERE status = 200
SELECT * FROM namespace_name.table_name WHERE response_time > 1000
SELECT * FROM namespace_name.table_name WHERE user_id IS NOT NULL
SELECT * FROM namespace_name.table_name WHERE method = 'GET' AND status >= 200 AND status < 300
SELECT * FROM namespace_name.table_name WHERE (status = 404 OR status = 500) AND timestamp > '2024-01-01'
```
***
## GROUP BY Clause
### Syntax
```sql
SELECT column_list, aggregation_function
FROM table_name
[WHERE conditions]
GROUP BY column_list
```
### Examples
```sql
-- Single column grouping
SELECT department, COUNT(*)
FROM my_namespace.sales_data
GROUP BY department
-- Multiple column grouping
SELECT department, category, COUNT(*)
FROM my_namespace.sales_data
GROUP BY department, category
-- With WHERE filter
SELECT region, COUNT(*)
FROM my_namespace.sales_data
WHERE status = 'completed'
GROUP BY region
-- With ORDER BY (COUNT only)
SELECT region, COUNT(*)
FROM my_namespace.sales_data
GROUP BY region
ORDER BY COUNT(*) DESC
LIMIT 10
-- ORDER BY SUM
SELECT department, SUM(amount)
FROM my_namespace.sales_data
GROUP BY department
ORDER BY SUM(amount) DESC
```
***
## HAVING Clause
### Syntax
```sql
SELECT column_list, COUNT(*)
FROM table_name
GROUP BY column_list
HAVING SUM/COUNT/MIN/MAX/AVG(column_name) comparison_operator value
```
### Examples
```sql
-- Filter by count threshold
SELECT department, COUNT(*)
FROM my_namespace.sales_data
GROUP BY department
HAVING COUNT(*) > 1000
-- Multiple conditions
SELECT region, COUNT(*)
FROM my_namespace.sales_data
GROUP BY region
HAVING COUNT(*) >= 100
-- HAVING with SUM
SELECT department, SUM(amount)
FROM my_namespace.sales_data
GROUP BY department
HAVING SUM(amount) > 1000000
```
***
## ORDER BY Clause
### Syntax
```sql
--Note: ORDER BY only supports ordering by the partition key
ORDER BY partition_key [DESC]
```
* **ASC**: Ascending order
* **DESC**: Descending order
* **Default**: DESC on all columns of the partition key
* Can contain any columns from the partition key
### Examples
```sql
SELECT * FROM namespace_name.table_name WHERE ... ORDER BY partition_key_A
SELECT * FROM namespace_name.table_name WHERE ... ORDER BY partition_key_B DESC
SELECT * FROM namespace_name.table_name WHERE ... ORDER BY partition_key_A ASC
```
***
## LIMIT Clause
### Syntax
```sql
LIMIT number
```
* **Range**: 1 to 10,000
* **Type**: Integer only
* **Default**: 500
### Examples
```sql
SELECT * FROM namespace_name.table_name WHERE ... LIMIT 100
```
***
## Complete Query Examples
### Basic Query
```sql
SELECT *
FROM my_namespace.http_requests
WHERE timestamp BETWEEN '2025-09-24T01:00:00Z' AND '2025-09-25T01:00:00Z'
LIMIT 100
```
### Filtered Query with Sorting
```sql
SELECT user_id, timestamp, status, response_time
FROM my_namespace.access_logs
WHERE status >= 400 AND response_time > 5000
ORDER BY response_time DESC
LIMIT 50
```
### Complex Conditions
```sql
SELECT timestamp, method, status, user_agent
FROM my_namespace.http_requests
WHERE (method = 'POST' OR method = 'PUT')
AND status BETWEEN 200 AND 299
AND user_agent IS NOT NULL
ORDER BY timestamp DESC
LIMIT 1000
```
### Null Handling
```sql
SELECT user_id, session_id, date_column
FROM my_namespace.user_events
WHERE session_id IS NOT NULL
AND date_column >= '2024-01-01'
ORDER BY timestamp
LIMIT 500
```
### Aggregation Query
```sql
SELECT department, COUNT(*)
FROM my_namespace.sales_data
WHERE sale_date >= '2024-01-01'
GROUP BY department
ORDER BY COUNT(*) DESC
LIMIT 10
```
### Aggregation with HAVING
```sql
SELECT region, COUNT(*)
FROM my_namespace.sales_data
WHERE status = 'completed'
GROUP BY region
HAVING COUNT(*) > 1000
LIMIT 20
```
### Multiple Column Grouping
```sql
SELECT department, category, MIN(price), MAX(price)
FROM my_namespace.products
GROUP BY department, category
LIMIT 100
```
***
## Data Type Reference
### Supported Types
| Type | Description | Example Values |
| - | - | - |
| `integer` | Whole numbers | `1`, `42`, `-10`, `0` |
| `float` | Decimal numbers | `1.5`, `3.14`, `-2.7`, `0.0` |
| `string` | Text values | `'hello'`, `'GET'`, `'2024-01-01'` |
| `boolean` | Boolean values | `true`, `false` |
| `timestamp` | RFC3339 | `'2025-09-24T01:00:00Z'` |
| `date` | 'YYYY-MM-DD' | `'2025-09-24'` |
### Type Usage in Conditions
```sql
-- Integer comparisons
SELECT * FROM namespace_name.table_name WHERE status = 200
SELECT * FROM namespace_name.table_name WHERE response_time > 1000
-- Float comparisons
SELECT * FROM namespace_name.table_name WHERE cpu_usage >= 85.5
SELECT * FROM namespace_name.table_name WHERE memory_ratio < 0.8
-- String comparisons
SELECT * FROM namespace_name.table_name WHERE method = 'POST'
SELECT * FROM namespace_name.table_name WHERE user_agent != 'bot'
SELECT * FROM namespace_name.table_name WHERE country_code = 'US'
```
***
## Operator Precedence
1. **Comparison operators**: `=`, `!=`, `<`, `<=`, `>`, `>=`, `LIKE`, `BETWEEN`, `IS NULL`, `IS NOT NULL`
2. **AND** (higher precedence)
3. **OR** (lower precedence)
Use parentheses to override default precedence:
```sql
SELECT * FROM namespace_name.table_name WHERE (status = 404 OR status = 500) AND method = 'GET'
```
***
---
title: Troubleshooting guide · R2 SQL docs
description: This guide covers potential errors and limitations you may
encounter when using R2 SQL. R2 SQL is in open beta, and supported
functionality will evolve and change over time.
lastUpdated: 2025-09-25T04:13:57.000Z
chatbotDeprioritize: false
tags: SQL
source_url:
html: https://developers.cloudflare.com/r2-sql/troubleshooting/
md: https://developers.cloudflare.com/r2-sql/troubleshooting/index.md
---
This guide covers potential errors and limitations you may encounter when using R2 SQL. R2 SQL is in open beta, and supported functionality will evolve and change over time.
## Query Structure Errors
### Missing Required Clauses
**Error**: `expected exactly 1 table in FROM clause`
**Problem**: R2 SQL requires specific clauses in your query.
```sql
-- Invalid - Missing FROM clause
SELECT user_id WHERE status = 200;
-- Valid
SELECT user_id
FROM http_requests
WHERE status = 200 AND timestamp BETWEEN '2025-09-24T01:00:00Z' AND '2025-09-25T01:00:00Z';
```
**Solution**: Always include `FROM` in your queries.
***
## SELECT Clause Issues
### Unsupported SQL Functions
**Error**: `Function not supported`
**Problem**: Cannot use aggregate or SQL functions in SELECT.
```sql
-- Invalid - Aggregate functions not supported
SELECT COUNT(*) FROM events WHERE timestamp > '2025-09-24T01:00:00Z'
SELECT AVG(response_time) FROM http_requests WHERE status = 200
SELECT MAX(timestamp) FROM logs WHERE user_id = '123'
```
**Solution**: Use basic column selection, and handle aggregation in your application code.
### JSON Field Access
**Error**: `Cannot access nested fields`
**Problem**: Cannot query individual fields from JSON objects.
```sql
-- Invalid - JSON field access not supported
SELECT metadata.user_id FROM events
SELECT json_field->>'property' FROM logs
-- Valid - Select entire JSON field
SELECT metadata FROM events
SELECT json_field FROM logs
```
**Solution**: Select the entire JSON column and parse it in your application.
### Synthetic Data
**Error**: `aliases (AS) are not supported`
**Problem**: Cannot create synthetic columns with literal values.
```sql
-- Invalid - Synthetic data not supported
SELECT user_id, 'active' as status, 1 as priority FROM users
-- Valid
SELECT user_id, status, priority FROM users WHERE status = 'active'
```
**Solution**: Add the required data to your table schema, or handle it in post-processing.
***
## FROM Clause Issues
### Multiple Tables
**Error**: `Multiple tables not supported` or `JOIN operations not allowed`
**Problem**: Cannot query multiple tables or use JOINs.
```sql
-- Invalid - Multiple tables not supported
SELECT a.*, b.* FROM table1 a, table2 b WHERE a.id = b.id
SELECT * FROM events JOIN users ON events.user_id = users.id
-- Valid - Separate queries
SELECT * FROM table1 WHERE id IN ('id1', 'id2', 'id3')
-- Then in application code, query table2 separately
SELECT * FROM table2 WHERE id IN ('id1', 'id2', 'id3')
```
**Solution**:
* Denormalize your data by including necessary fields in a single table.
* Perform multiple queries and join data in your application.
### Subqueries
**Error**: `only table name is supported in FROM clause`
**Problem**: Cannot use subqueries in FROM clause.
```sql
-- Invalid - Subqueries not supported
SELECT * FROM (SELECT user_id FROM events WHERE status = 200) as active_users
-- Valid - Use direct query with appropriate filters
SELECT user_id FROM events WHERE status = 200
```
**Solution**: Flatten your query logic or use multiple sequential queries.
***
## WHERE Clause Issues
### Array Filtering
**Error**: `This feature is not implemented: GetFieldAccess`
**Problem**: Cannot filter on array fields.
```sql
-- Invalid - Array filtering not supported
SELECT * FROM logs WHERE tags[0] = 'error'
SELECT * FROM events WHERE 'admin' = ANY(roles)
-- Valid alternatives - denormalize or use string contains
SELECT * FROM logs WHERE tags_string LIKE '%error%'
-- Or restructure data to avoid arrays
```
**Solution**:
* Denormalize array data into separate columns.
* Use string concatenation of array values for pattern matching.
* Restructure your schema to avoid array types.
### JSON Object Filtering
**Error**: `unsupported binary operator` or `Error during planning: could not parse compound`
**Problem**: Cannot filter on fields inside JSON objects.
```sql
-- Invalid - JSON field filtering not supported
SELECT * FROM requests WHERE metadata.country = 'US'
SELECT * FROM logs WHERE json_data->>'level' = 'error'
-- Valid alternatives
SELECT * FROM requests WHERE country = 'US' -- If denormalized
-- Or filter entire JSON field and parse in application
SELECT * FROM logs WHERE json_data IS NOT NULL
```
**Solution**:
* Denormalize frequently queried JSON fields into separate columns.
* Filter on the entire JSON field, and handle parsing in your application.
### Column Comparisons
**Error**: `right argument to a binary expression must be a literal`
**Problem**: Cannot compare one column to another in WHERE clause.
```sql
-- Invalid - Column comparisons not supported
SELECT * FROM events WHERE start_time < end_time
SELECT * FROM logs WHERE request_size > response_size
-- Valid - Use computed columns or application logic
-- Add a computed column 'duration' to your schema
SELECT * FROM events WHERE duration > 0
```
**Solution**: Handle comparisons in your application layer.
***
## LIMIT Clause Issues
### Invalid Limit Values
**Error**: `maximum LIMIT is 10000`
**Problem**: Cannot use invalid LIMIT values.
```sql
-- Invalid - Out of range limits
SELECT * FROM events LIMIT 50000 -- Maximum is 10,000
-- Valid
SELECT * FROM events LIMIT 1
SELECT * FROM events LIMIT 10000
```
**Solution**: Use LIMIT values between 1 and 10,000.
### Pagination Attempts
**Error**: `OFFSET not supported`
**Problem**: Cannot use pagination syntax.
```sql
-- Invalid - Pagination not supported
SELECT * FROM events LIMIT 100 OFFSET 200
SELECT * FROM events LIMIT 100, 100
-- Valid alternatives - Use ORDER BY with conditional filters
-- Page 1
SELECT * FROM events WHERE timestamp >= '2024-01-01' ORDER BY timestamp LIMIT 100
-- Page 2 - Use last timestamp from previous page
SELECT * FROM events WHERE timestamp > '2024-01-01T10:30:00Z' ORDER BY timestamp LIMIT 100
```
**Solution**: Implement cursor-based pagination using ORDER BY and WHERE conditions.
***
## Schema Issues
### Dynamic Schema Changes
**Error**: `invalid SQL: only top-level SELECT clause is supported`
**Problem**: Cannot modify table schema or reference non-existent columns.
```sql
-- Invalid - Schema changes not supported
ALTER TABLE events ADD COLUMN new_field STRING
UPDATE events SET status = 200 WHERE user_id = '123'
```
**Solution**:
* Plan your schema carefully before data ingestion.
* Ensure all column names exist in your current schema.
***
## Performance Optimization
### Query Performance Issues
If your queries are running slowly:
1. **Always include partition (timestamp) filters**: This is the most important optimization.
```sql
-- Good
WHERE timestamp BETWEEN '2024-01-01' AND '2024-01-02'
```
2. **Use selective filtering**: Include specific conditions to reduce result sets.
```sql
-- Good
WHERE status = 200 AND country = 'US' AND timestamp > '2024-01-01'
```
3. **Limit result size**: Use appropriate LIMIT values.
```sql
-- Good for exploration
SELECT * FROM events WHERE timestamp > '2024-01-01' LIMIT 100
```
---
title: Tutorials · R2 SQL docs
lastUpdated: 2025-09-25T04:13:57.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/r2-sql/tutorials/
md: https://developers.cloudflare.com/r2-sql/tutorials/index.md
---
---
title: 404 - Page Not Found · Cloudflare R2 docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/404/
md: https://developers.cloudflare.com/r2/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API · Cloudflare R2 docs
lastUpdated: 2024-08-30T16:09:27.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/r2/api/
md: https://developers.cloudflare.com/r2/api/index.md
---
* [Authentication](https://developers.cloudflare.com/r2/api/tokens/)
* [Workers API](https://developers.cloudflare.com/r2/api/workers/)
* [S3](https://developers.cloudflare.com/r2/api/s3/)
* [Error codes](https://developers.cloudflare.com/r2/api/error-codes/)
---
title: Buckets · Cloudflare R2 docs
description: With object storage, all of your objects are stored in buckets.
Buckets do not contain folders that group the individual files, but instead,
buckets have a flat structure which simplifies the way you access and retrieve
the objects in your bucket.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/buckets/
md: https://developers.cloudflare.com/r2/buckets/index.md
---
With object storage, all of your objects are stored in buckets. Buckets do not contain folders that group the individual files, but instead, buckets have a flat structure which simplifies the way you access and retrieve the objects in your bucket.
Learn more about bucket level operations from the items below.
* [Bucket locks](https://developers.cloudflare.com/r2/buckets/bucket-locks/)
* [Create new buckets](https://developers.cloudflare.com/r2/buckets/create-buckets/)
* [Configure CORS](https://developers.cloudflare.com/r2/buckets/cors/)
* [Event notifications](https://developers.cloudflare.com/r2/buckets/event-notifications/)
* [Local uploads](https://developers.cloudflare.com/r2/buckets/local-uploads/)
* [Object lifecycles](https://developers.cloudflare.com/r2/buckets/object-lifecycles/)
* [Public buckets](https://developers.cloudflare.com/r2/buckets/public-buckets/)
* [Storage classes](https://developers.cloudflare.com/r2/buckets/storage-classes/)
---
title: R2 Data Catalog · Cloudflare R2 docs
description: A managed Apache Iceberg data catalog built directly into R2 buckets.
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/data-catalog/
md: https://developers.cloudflare.com/r2/data-catalog/index.md
---
Note
R2 Data Catalog is in **public beta**, and any developer with an [R2 subscription](https://developers.cloudflare.com/r2/pricing/) can start using it. Currently, outside of standard R2 storage and operations, you will not be billed for your use of R2 Data Catalog.
R2 Data Catalog is a managed [Apache Iceberg](https://iceberg.apache.org/) data catalog built directly into your R2 bucket. It exposes a standard Iceberg REST catalog interface, so you can connect the engines you already use, like [Spark](https://developers.cloudflare.com/r2/data-catalog/config-examples/spark-scala/), [Snowflake](https://developers.cloudflare.com/r2/data-catalog/config-examples/snowflake/), and [PyIceberg](https://developers.cloudflare.com/r2/data-catalog/config-examples/pyiceberg/).
R2 Data Catalog makes it easy to turn an R2 bucket into a data warehouse or lakehouse for a variety of analytical workloads including log analytics, business intelligence, and data pipelines. R2's zero-egress fee model means that data users and consumers can access and analyze data from different clouds, data platforms, or regions without incurring transfer costs.
To get started with R2 Data Catalog, refer to the [R2 Data Catalog: Getting started](https://developers.cloudflare.com/r2/data-catalog/get-started/).
## What is Apache Iceberg?
[Apache Iceberg](https://iceberg.apache.org/) is an open table format designed to handle large-scale analytics datasets stored in object storage. Key features include:
* ACID transactions - Ensures reliable, concurrent reads and writes with full data integrity.
* Optimized metadata - Avoids costly full table scans by using indexed metadata for faster queries.
* Full schema evolution - Allows adding, renaming, and deleting columns without rewriting data.
Iceberg is already [widely supported](https://iceberg.apache.org/vendors/) by engines like Apache Spark, Trino, Snowflake, DuckDB, and ClickHouse, with a fast-growing community behind it.
## Why do you need a data catalog?
Although the Iceberg data and metadata files themselves live directly in object storage (like [R2](https://developers.cloudflare.com/r2/)), the list of tables and pointers to the current metadata need to be tracked centrally by a data catalog.
Think of a data catalog as a library's index system. While books (your data) are physically distributed across shelves (object storage), the index provides a single source of truth about what books exist, their locations, and their latest editions. Without this index, readers (query engines) would waste time searching for books, might access outdated versions, or could accidentally shelve new books in ways that make them unfindable.
Similarly, data catalogs ensure consistent, coordinated access, which allows multiple query engines to safely read from and write to the same tables without conflicts or data corruption.
## Learn more
[Get started ](https://developers.cloudflare.com/r2/data-catalog/get-started/)Learn how to enable the R2 Data Catalog on your bucket, load sample data, and run your first query.
[Managing catalogs ](https://developers.cloudflare.com/r2/data-catalog/manage-catalogs/)Enable or disable R2 Data Catalog on your bucket, retrieve configuration details, and authenticate your Iceberg engine.
[Connect to Iceberg engines ](https://developers.cloudflare.com/r2/data-catalog/config-examples/)Find detailed setup instructions for Apache Spark and other common query engines.
---
title: Data migration · Cloudflare R2 docs
description: Quickly and easily migrate data from other cloud providers to R2.
Explore each option further by navigating to their respective documentation
page.
lastUpdated: 2025-05-15T13:16:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/data-migration/
md: https://developers.cloudflare.com/r2/data-migration/index.md
---
Quickly and easily migrate data from other cloud providers to R2. Explore each option further by navigating to their respective documentation page.
| Name | Description | When to use |
| - | - | - |
| [Super Slurper](https://developers.cloudflare.com/r2/data-migration/super-slurper/) | Quickly migrate large amounts of data from other cloud providers to R2. | * For one-time, comprehensive transfers. |
| [Sippy](https://developers.cloudflare.com/r2/data-migration/sippy/) | Incremental data migration, populating your R2 bucket as objects are requested. | - For gradual migration that avoids upfront egress fees.
- To start serving frequently accessed objects from R2 without a full migration. |
For information on how to leverage these tools effectively, refer to [Migration Strategies](https://developers.cloudflare.com/r2/data-migration/migration-strategies/)
---
title: Demos and architectures · Cloudflare R2 docs
description: Explore Cloudflare R2 demos and reference architectures for
fullstack applications, storage, and AI, with examples and use cases.
lastUpdated: 2025-10-30T16:19:51.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/demos/
md: https://developers.cloudflare.com/r2/demos/index.md
---
Learn how you can use R2 within your existing application and architecture.
## Demos
Explore the following demo applications for R2.
* [Jobs At Conf:](https://github.com/harshil1712/jobs-at-conf-demo) A job lisiting website to add jobs you find at in-person conferences. Built with Cloudflare Pages, R2, D1, Queues, and Workers AI.
* [Upload Image to R2 starter:](https://github.com/harshil1712/nextjs-r2-demo) Upload images to Cloudflare R2 from a Next.js application.
* [DMARC Email Worker:](https://github.com/cloudflare/dmarc-email-worker) A Cloudflare worker script to process incoming DMARC reports, store them, and produce analytics.
## Reference architectures
Explore the following reference architectures that use R2:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Storing user generated content](https://developers.cloudflare.com/reference-architecture/diagrams/storage/storing-user-generated-content/)
[Store user-generated content in R2 for fast, secure, and cost-effective architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/storing-user-generated-content/)
[Optimizing and securing connected transportation systems](https://developers.cloudflare.com/reference-architecture/diagrams/iot/optimizing-and-securing-connected-transportation-systems/)
[This diagram showcases Cloudflare components optimizing connected transportation systems. It illustrates how their technologies minimize latency, ensure reliability, and strengthen security for critical data flow.](https://developers.cloudflare.com/reference-architecture/diagrams/iot/optimizing-and-securing-connected-transportation-systems/)
[Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[You can connect a Cloudflare Worker to get data from Google BigQuery and pass it to Workers AI, to run AI Models, powered by serverless GPUs.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[Event notifications for storage](https://developers.cloudflare.com/reference-architecture/diagrams/storage/event-notifications-for-storage/)
[Use Cloudflare Workers or an external service to monitor for notifications about data changes and then handle them appropriately.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/event-notifications-for-storage/)
[On-demand Object Storage Data Migration](https://developers.cloudflare.com/reference-architecture/diagrams/storage/on-demand-object-storage-migration/)
[Use Cloudflare migration tools to migrate data between cloud object storage providers.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/on-demand-object-storage-migration/)
[Optimizing image delivery with Cloudflare image resizing and R2](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/optimizing-image-delivery-with-cloudflare-image-resizing-and-r2/)
[Learn how to get a scalable, high-performance solution to optimizing image delivery.](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/optimizing-image-delivery-with-cloudflare-image-resizing-and-r2/)
[Composable AI architecture](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[The architecture diagram illustrates how AI applications can be built end-to-end on Cloudflare, or single services can be integrated with external infrastructure and services.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[Serverless ETL pipelines](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-etl/)
[Cloudflare enables fully serverless ETL pipelines, significantly reducing complexity, accelerating time to production, and lowering overall costs.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-etl/)
[Egress-free object storage in multi-cloud setups](https://developers.cloudflare.com/reference-architecture/diagrams/storage/egress-free-storage-multi-cloud/)
[Learn how to use R2 to get egress-free object storage in multi-cloud setups.](https://developers.cloudflare.com/reference-architecture/diagrams/storage/egress-free-storage-multi-cloud/)
[Automatic captioning for video uploads](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-video-caption/)
[By integrating automatic speech recognition technology into video platforms, content creators, publishers, and distributors can reach a broader audience, including individuals with hearing impairments or those who prefer to consume content in different languages.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-video-caption/)
[Serverless image content management](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
[Leverage various components of Cloudflare's ecosystem to construct a scalable image management solution](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
---
title: Examples · Cloudflare R2 docs
description: Explore the following examples of how to use SDKs and other tools with R2.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/examples/
md: https://developers.cloudflare.com/r2/examples/index.md
---
Explore the following examples of how to use SDKs and other tools with R2.
* [Authenticate against R2 API using auth tokens](https://developers.cloudflare.com/r2/examples/authenticate-r2-auth-tokens/)
* [Use the Cache API](https://developers.cloudflare.com/r2/examples/cache-api/)
* [Multi-cloud setup](https://developers.cloudflare.com/reference-architecture/diagrams/storage/egress-free-storage-multi-cloud/)
* [Rclone](https://developers.cloudflare.com/r2/examples/rclone/)
* [S3 SDKs](https://developers.cloudflare.com/r2/examples/aws/)
* [Terraform](https://developers.cloudflare.com/r2/examples/terraform/)
* [Terraform (AWS)](https://developers.cloudflare.com/r2/examples/terraform-aws/)
* [Use SSE-C](https://developers.cloudflare.com/r2/examples/ssec/)
---
title: Get started · Cloudflare R2 docs
description: Create your first R2 bucket and store objects using the dashboard,
S3-compatible tools, or Workers.
lastUpdated: 2026-01-26T20:24:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/get-started/
md: https://developers.cloudflare.com/r2/get-started/index.md
---
Cloudflare R2 Storage allows developers to store large amounts of unstructured data without the costly egress bandwidth fees associated with typical cloud storage services.
## Before you begin
You need a Cloudflare account with an R2 subscription. If you do not have one:
1. Go to the [Cloudflare Dashboard](https://dash.cloudflare.com/).
2. Select **Storage & databases > R2 > Overview**
3. Complete the checkout flow to add an R2 subscription to your account.
R2 is free to get started with included free monthly usage. You are billed for your usage on a monthly basis. Refer to [Pricing](https://developers.cloudflare.com/r2/pricing/) for details.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/r2/overview)
## Choose how to access R2
R2 supports multiple access methods, so you can choose the one that fits your use case best:
| Method | Use when |
| - | - |
| [Workers API](https://developers.cloudflare.com/r2/get-started/workers-api/) | You are building an application on Cloudflare Workers that needs to read or write from R2 |
| [S3](https://developers.cloudflare.com/r2/get-started/s3/) | You want to use S3-compatible SDKs to interact with R2 in your existing applications |
| [CLI tools](https://developers.cloudflare.com/r2/get-started/cli/) | You want to upload, download, or manage objects from your terminal |
| [Dashboard](https://dash.cloudflare.com/?to=/:account/r2/overview) | You want to quickly view and manage buckets and objects in the browser |
## Next steps
[Workers API ](https://developers.cloudflare.com/r2/get-started/workers-api/)Use R2 from Cloudflare Workers.
[S3 ](https://developers.cloudflare.com/r2/get-started/s3/)Use R2 with S3-compatible SDKs.
[CLI ](https://developers.cloudflare.com/r2/get-started/cli/)Use R2 from the command line.
---
title: How R2 works · Cloudflare R2 docs
description: Find out how R2 works.
lastUpdated: 2026-02-03T04:13:50.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/how-r2-works/
md: https://developers.cloudflare.com/r2/how-r2-works/index.md
---
Cloudflare R2 is an S3-compatible object storage service with no egress fees, built on Cloudflare's global network. It is [strongly consistent](https://developers.cloudflare.com/r2/reference/consistency/) and designed for high [data durability](https://developers.cloudflare.com/r2/reference/durability/).
R2 is ideal for storing and serving unstructured data that needs to be accessed frequently over the internet, without incurring egress fees. It's a good fit for workloads like serving web assets, training AI models, and managing user-generated content.
## Architecture
R2's architecture is composed of multiple components:
* **R2 Gateway:** The entry point for all API requests that handles authentication and routing logic. This service is deployed across Cloudflare's global network via [Cloudflare Workers](https://developers.cloudflare.com/workers/).
* **Metadata Service:** A distributed layer built on [Durable Objects](https://developers.cloudflare.com/durable-objects/) used to store and manage object metadata (e.g. object key, checksum) to ensure strong consistency of the object across the storage system. It includes a built-in cache layer to speed up access to metadata.
* **Tiered Read Cache:** A caching layer that sits in front of the Distributed Storage Infrastructure that speeds up object reads by using [Cloudflare Tiered Cache](https://developers.cloudflare.com/cache/how-to/tiered-cache/) to serve data closer to the client.
* **Distributed Storage Infrastructure:** The underlying infrastructure that persistently stores encrypted object data.
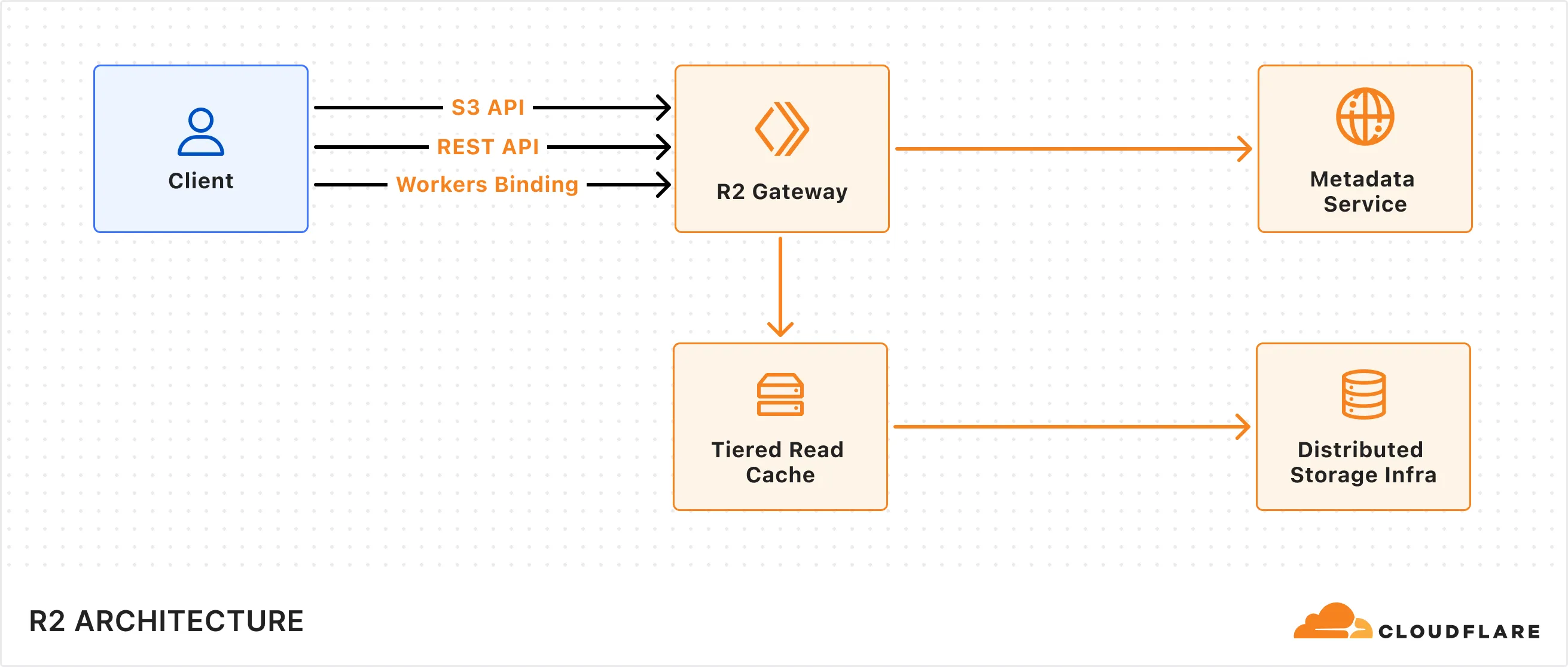
R2 supports multiple client interfaces including [Cloudflare Workers Binding](https://developers.cloudflare.com/r2/api/workers/workers-api-usage/), [S3-compatible API](https://developers.cloudflare.com/r2/api/s3/api/), and a [REST API](https://developers.cloudflare.com/api/resources/r2/) that powers the Cloudflare Dashboard and Wrangler CLI. All requests are routed through the R2 Gateway, which coordinates with the Metadata Service and Distributed Storage Infrastructure to retrieve the object data.
## Write data to R2
When a write request (e.g. uploading an object) is made to R2, the following sequence occurs:
1. **Request handling:** The request is received by the R2 Gateway at the edge, close to the user, where it is authenticated.
2. **Encryption and routing:** The Gateway reaches out to the Metadata Service to retrieve the [encryption key](https://developers.cloudflare.com/r2/reference/data-security/) and determines which storage cluster to write the encrypted data to within the [location](https://developers.cloudflare.com/r2/reference/data-location/) set for the bucket.
3. **Writing to storage:** The encrypted data is written and stored in the distributed storage infrastructure, and replicated within the region (e.g. ENAM) for [durability](https://developers.cloudflare.com/r2/reference/durability/).
4. **Metadata commit:** Finally, the Metadata Service commits the object's metadata, making it visible in subsequent reads. Only after this commit is an `HTTP 200` success response sent to the client, preventing unacknowledged writes.
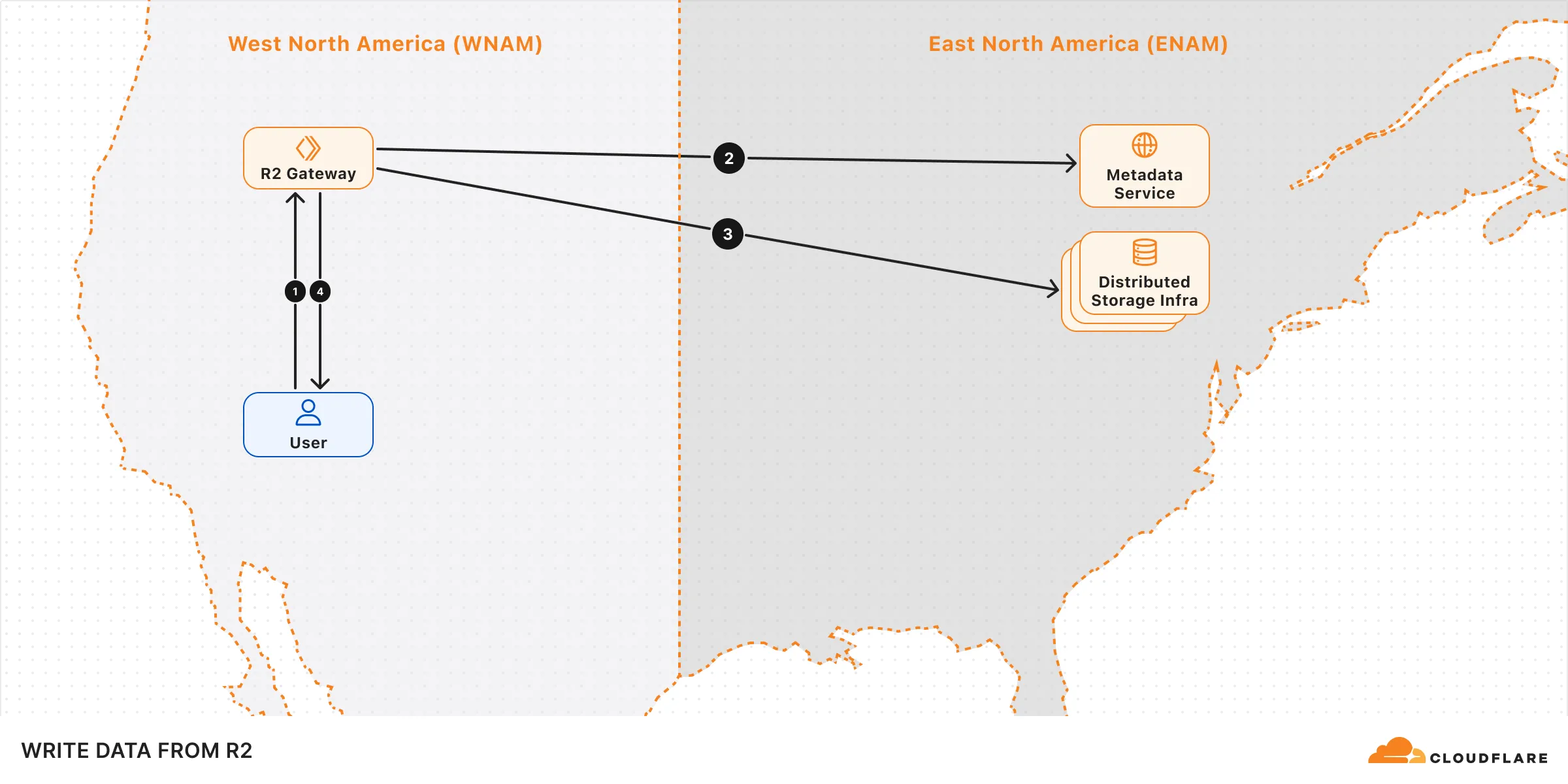
## Read data from R2
When a read request (e.g. fetching an object) is made to R2, the following sequence occurs:
1. **Request handling:** The request is received by the R2 Gateway at the edge, close to the user, where it is authenticated.
2. **Metadata lookup:** The Gateway asks the Metadata Service for the object metadata.
3. **Reading the object:** The Gateway attempts to retrieve the [encrypted](https://developers.cloudflare.com/r2/reference/data-security/) object from the tiered read cache. If it's not available, it retrieves the object from one of the distributed storage data centers within the region that holds the object data.
4. **Serving to client:** The object is decrypted and served to the user.
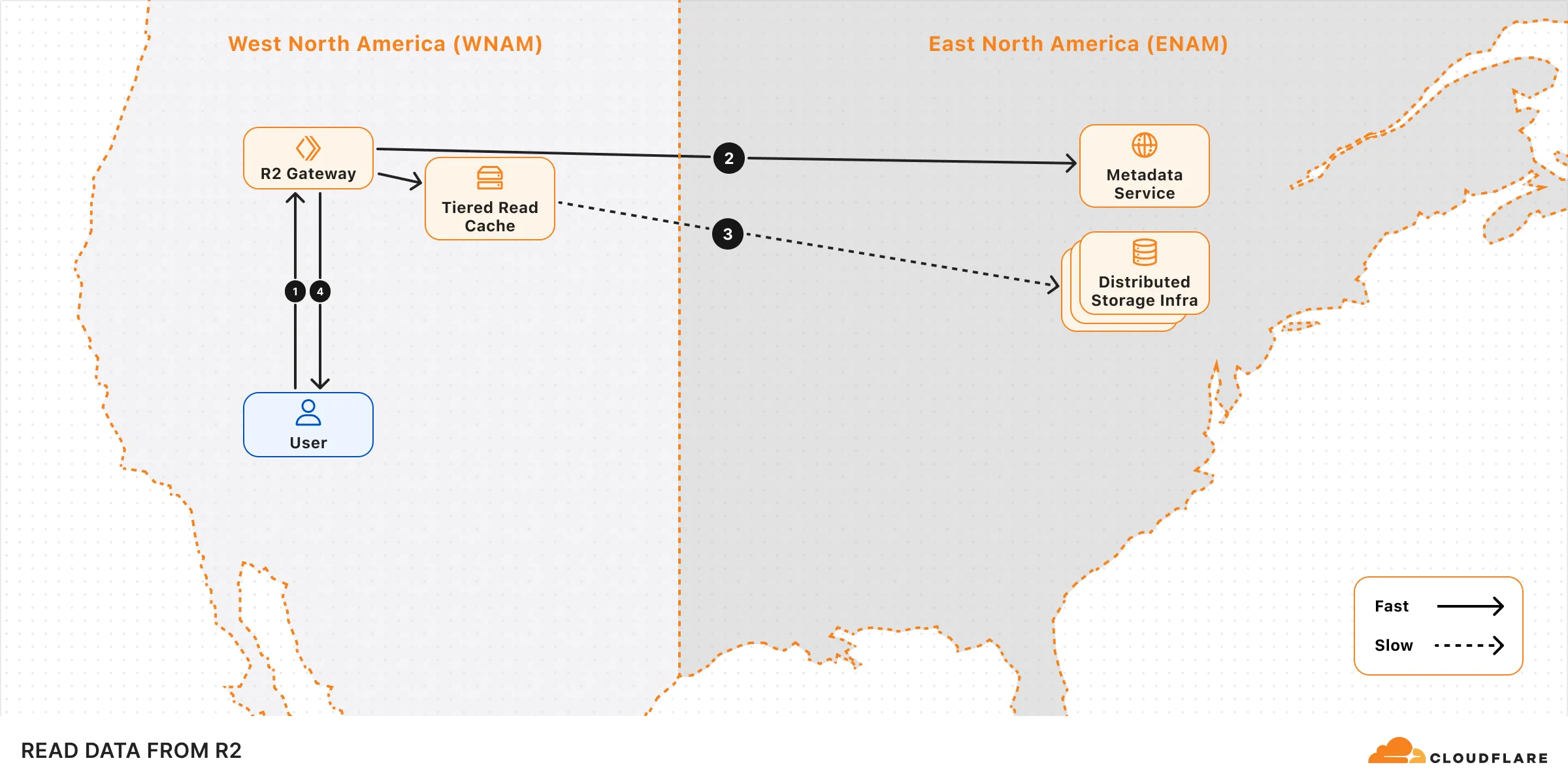
## Performance
The performance of your operations can be influenced by factors such as the bucket's geographical location, request origin, and access patterns.
To optimize upload performance for cross-region requests, enable [Local Uploads](https://developers.cloudflare.com/r2/buckets/local-uploads/) on your bucket.
To optimize read performance, enable [Cloudflare Cache](https://developers.cloudflare.com/cache/) when using a [custom domain](https://developers.cloudflare.com/r2/buckets/public-buckets/#custom-domains). When caching is enabled, read requests can bypass the R2 Gateway and be served directly from Cloudflare's edge cache, reducing latency. Note that cached data may not reflect the latest version immediately.
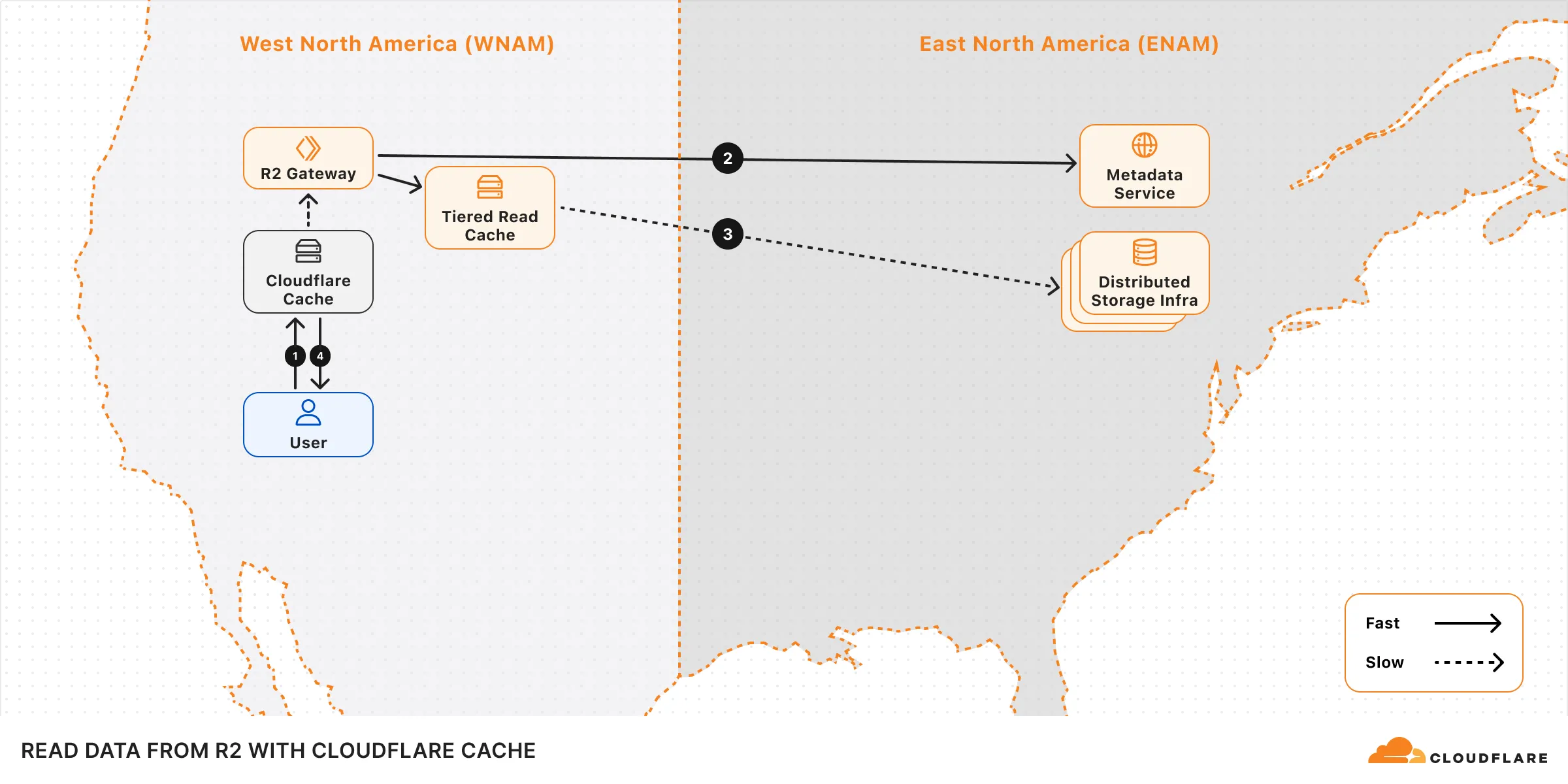
## Learn more
[Consistency ](https://developers.cloudflare.com/r2/reference/consistency/)Learn about R2's consistency model.
[Durability ](https://developers.cloudflare.com/r2/reference/durability/)Learn more about R2's durability guarantee.
[Data location ](https://developers.cloudflare.com/r2/reference/data-location/#jurisdictional-restrictions)Learn how R2 determines where data is stored, and details on jurisdiction restrictions.
[Data security ](https://developers.cloudflare.com/r2/reference/data-security/)Learn about R2's data security properties.
---
title: Objects · Cloudflare R2 docs
description: Objects are individual files or data that you store in an R2 bucket.
lastUpdated: 2025-05-28T15:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/objects/
md: https://developers.cloudflare.com/r2/objects/index.md
---
Objects are individual files or data that you store in an R2 bucket.
* [Upload objects](https://developers.cloudflare.com/r2/objects/upload-objects/)
* [Multipart upload](https://developers.cloudflare.com/r2/objects/multipart-objects/)
* [Download objects](https://developers.cloudflare.com/r2/objects/download-objects/)
* [Delete objects](https://developers.cloudflare.com/r2/objects/delete-objects/)
## Other resources
For information on R2 Workers Binding API, refer to [R2 Workers API reference](https://developers.cloudflare.com/r2/api/workers/workers-api-reference/).
---
title: Platform · Cloudflare R2 docs
lastUpdated: 2025-04-09T22:46:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/r2/platform/
md: https://developers.cloudflare.com/r2/platform/index.md
---
---
title: Pricing · Cloudflare R2 docs
description: "R2 charges based on the total volume of data stored, along with
two classes of operations on that data:"
lastUpdated: 2025-09-30T21:55:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/pricing/
md: https://developers.cloudflare.com/r2/pricing/index.md
---
R2 charges based on the total volume of data stored, along with two classes of operations on that data:
1. [Class A operations](#class-a-operations) which are more expensive and tend to mutate state.
2. [Class B operations](#class-b-operations) which tend to read existing state.
For the Infrequent Access storage class, [data retrieval](#data-retrieval) fees apply. There are no charges for egress bandwidth for any storage class.
All included usage is on a monthly basis.
Note
To learn about potential cost savings from using R2, refer to the [R2 pricing calculator](https://r2-calculator.cloudflare.com/).
## R2 pricing
| | Standard storage | Infrequent Access storage |
| - | - | - |
| Storage | $0.015 / GB-month | $0.01 / GB-month |
| Class A Operations | $4.50 / million requests | $9.00 / million requests |
| Class B Operations | $0.36 / million requests | $0.90 / million requests |
| Data Retrieval (processing) | None | $0.01 / GB |
| Egress (data transfer to Internet) | Free [1](#user-content-fn-1) | Free [1](#user-content-fn-1) |
Billable unit rounding
Cloudflare rounds up your usage to the next billing unit.
For example:
* If you have performed one million and one operations, you will be billed for two million operations.
* If you have used 1.1 GB-month, you will be billed for 2 GB-month.
* If you have retrieved data (for infrequent access storage) for 1.1 GB, you will be billed for 2 GB.
### Free tier
You can use the following amount of storage and operations each month for free.
| | Free |
| - | - |
| Storage | 10 GB-month / month |
| Class A Operations | 1 million requests / month |
| Class B Operations | 10 million requests / month |
| Egress (data transfer to Internet) | Free [1](#user-content-fn-1) |
Warning
The free tier only applies to Standard storage, and does not apply to Infrequent Access storage.
### Storage usage
Storage is billed using gigabyte-month (GB-month) as the billing metric. A GB-month is calculated by averaging the *peak* storage per day over a billing period (30 days).
For example:
* Storing 1 GB constantly for 30 days will be charged as 1 GB-month.
* Storing 3 GB constantly for 30 days will be charged as 3 GB-month.
* Storing 1 GB for 5 days, then 3 GB for the remaining 25 days will be charged as `1 GB * 5/30 month + 3 GB * 25/30 month = 2.66 GB-month`
For objects stored in Infrequent Access storage, you will be charged for the object for the minimum storage duration even if the object was deleted or moved before the duration specified.
### Class A operations
Class A Operations include `ListBuckets`, `PutBucket`, `ListObjects`, `PutObject`, `CopyObject`, `CompleteMultipartUpload`, `CreateMultipartUpload`, `LifecycleStorageTierTransition`, `ListMultipartUploads`, `UploadPart`, `UploadPartCopy`, `ListParts`, `PutBucketEncryption`, `PutBucketCors` and `PutBucketLifecycleConfiguration`.
### Class B operations
Class B Operations include `HeadBucket`, `HeadObject`, `GetObject`, `UsageSummary`, `GetBucketEncryption`, `GetBucketLocation`, `GetBucketCors` and `GetBucketLifecycleConfiguration`.
### Free operations
Free operations include `DeleteObject`, `DeleteBucket` and `AbortMultipartUpload`.
### Data retrieval
Data retrieval fees apply when you access or retrieve data from the Infrequent Access storage class. This includes any time objects are read or copied.
### Minimum storage duration
For objects stored in Infrequent Access storage, you will be charged for the object for the minimum storage duration even if the object was deleted, moved, or replaced before the specified duration.
| Storage class | Minimum storage duration |
| - | - |
| Standard storage | None |
| Infrequent Access storage | 30 days |
## R2 Data Catalog pricing
R2 Data Catalog is in **public beta**, and any developer with an [R2 subscription](https://developers.cloudflare.com/r2/pricing/) can start using it. Currently, outside of standard R2 storage and operations, you will not be billed for your use of R2 Data Catalog. We will provide at least 30 days' notice before we make any changes or start charging for usage.
To learn more about our thinking on future pricing, refer to the [R2 Data Catalog announcement blog](https://blog.cloudflare.com/r2-data-catalog-public-beta).
## Data migration pricing
### Super Slurper
Super Slurper is free to use. You are only charged for the Class A operations that Super Slurper makes to your R2 bucket. Objects with sizes < 100MiB are uploaded to R2 in a single Class A operation. Larger objects use multipart uploads to increase transfer success rates and will perform multiple Class A operations. Note that your source bucket might incur additional charges as Super Slurper copies objects over to R2.
Once migration completes, you are charged for storage & Class A/B operations as described in previous sections.
### Sippy
Sippy is free to use. You are only charged for the operations Sippy makes to your R2 bucket. If a requested object is not present in R2, Sippy will copy it over from your source bucket. Objects with sizes < 200MiB are uploaded to R2 in a single Class A operation. Larger objects use multipart uploads to increase transfer success rates, and will perform multiple Class A operations. Note that your source bucket might incur additional charges as Sippy copies objects over to R2.
As objects are migrated to R2, they are served from R2, and you are charged for storage & Class A/B operations as described in previous sections.
## Pricing calculator
To learn about potential cost savings from using R2, refer to the [R2 pricing calculator](https://r2-calculator.cloudflare.com/).
## R2 billing examples
### Standard storage example
If a user writes 1,000 objects in R2 **Standard storage** for 1 month with an average size of 1 GB and reads each object 1,000 times during the month, the estimated cost for the month would be:
| | Usage | Free Tier | Billable Quantity | Price |
| - | - | - | - | - |
| Storage | (1,000 objects) \* (1 GB per object) = 1,000 GB-months | 10 GB-months | 990 GB-months | $14.85 |
| Class A Operations | (1,000 objects) \* (1 write per object) = 1,000 writes | 1 million | 0 | $0.00 |
| Class B Operations | (1,000 objects) \* (1,000 reads per object) = 1 million reads | 10 million | 0 | $0.00 |
| Data retrieval (processing) | (1,000 objects) \* (1 GB per object) = 1,000 GB | NA | None | $0.00 |
| **TOTAL** | | | | **$14.85** |
### Infrequent access example
If a user writes 1,000 objects in R2 Infrequent Access storage with an average size of 1 GB, stores them for 5 days, and then deletes them (delete operations are free), and during those 5 days each object is read 1,000 times, the estimated cost for the month would be:
| | Usage | Free Tier | Billable Quantity | Price |
| - | - | - | - | - |
| Storage | (1,000 objects) \* (1 GB per object) = 1,000 GB-months | NA | 1,000 GB-months | $10.00 |
| Class A Operations | (1,000 objects) \* (1 write per object) = 1,000 writes | NA | 1,000 | $9.00 |
| Class B Operations | (1,000 objects) \* (1,000 reads per object) = 1 million reads | NA | 1 million | $0.90 |
| Data retrieval (processing) | (1,000 objects) \* (1 GB per object) = 1,000 GB | NA | 1,000 GB | $10.00 |
| **TOTAL** | | | | **$29.90** |
Note that the minimal storage duration for infrequent access storage is 30 days, which means the billable quantity is 1,000 GB-months, rather than 167 GB-months.
### Asset hosting
If a user writes 100,000 files with an average size of 100 KB object and reads 10,000,000 objects per day, the estimated cost in a month would be:
| | Usage | Free Tier | Billable Quantity | Price |
| - | - | - | - | - |
| Storage | (100,000 objects) \* (100KB per object) | 10 GB-months | 0 GB-months | $0.00 |
| Class A Operations | (100,000 writes) | 1 million | 0 | $0.00 |
| Class B Operations | (10,000,000 reads per day) \* (30 days) | 10 million | 290,000,000 | $104.40 |
| **TOTAL** | | | | **$104.40** |
## Cloudflare billing policy
To learn more about how usage is billed, refer to [Cloudflare Billing Policy](https://developers.cloudflare.com/billing/billing-policy/).
## Frequently asked questions
### Will I be charged for unauthorized requests to my R2 bucket?
No. You are not charged for operations when the caller does not have permission to make the request (HTTP 401 `Unauthorized` response status code).
## Footnotes
1. Egressing directly from R2, including via the [Workers API](https://developers.cloudflare.com/r2/api/workers/), [S3 API](https://developers.cloudflare.com/r2/api/s3/), and [`r2.dev` domains](https://developers.cloudflare.com/r2/buckets/public-buckets/#enable-managed-public-access) does not incur data transfer (egress) charges and is free. If you connect other metered services to an R2 bucket, you may be charged by those services. [↩](#user-content-fnref-1) [↩2](#user-content-fnref-1-2) [↩3](#user-content-fnref-1-3)
---
title: R2 SQL · Cloudflare R2 docs
description: R2 SQL is a serverless SQL interface for Cloudflare R2, enabling
querying and analyzing data.
lastUpdated: 2025-10-30T16:19:51.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/r2-sql/
md: https://developers.cloudflare.com/r2/r2-sql/index.md
---
---
title: Reference · Cloudflare R2 docs
lastUpdated: 2025-04-09T22:46:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/r2/reference/
md: https://developers.cloudflare.com/r2/reference/index.md
---
* [Consistency model](https://developers.cloudflare.com/r2/reference/consistency/)
* [Data location](https://developers.cloudflare.com/r2/reference/data-location/)
* [Data security](https://developers.cloudflare.com/r2/reference/data-security/)
* [Durability](https://developers.cloudflare.com/r2/reference/durability/)
* [Unicode interoperability](https://developers.cloudflare.com/r2/reference/unicode-interoperability/)
* [Wrangler commands](https://developers.cloudflare.com/r2/reference/wrangler-commands/)
* [Partners](https://developers.cloudflare.com/r2/reference/partners/)
---
title: Tutorials · Cloudflare R2 docs
description: View tutorials to help you get started with R2.
lastUpdated: 2025-08-14T13:46:41.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/tutorials/
md: https://developers.cloudflare.com/r2/tutorials/index.md
---
View tutorials to help you get started with R2.
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [Build an end to end data pipeline](https://developers.cloudflare.com/r2-sql/tutorials/end-to-end-pipeline/) | 5 months ago | |
| [Point to R2 bucket with a custom domain](https://developers.cloudflare.com/rules/origin-rules/tutorials/point-to-r2-bucket-with-custom-domain/) | 10 months ago | Beginner |
| [Use event notification to summarize PDF files on upload](https://developers.cloudflare.com/r2/tutorials/summarize-pdf/) | over 1 year ago | Intermediate |
| [Use SSE-C](https://developers.cloudflare.com/r2/examples/ssec/) | over 1 year ago | Intermediate |
| [Use R2 as static asset storage with Cloudflare Pages](https://developers.cloudflare.com/pages/tutorials/use-r2-as-static-asset-storage-for-pages/) | over 1 year ago | Intermediate |
| [Create a fine-tuned OpenAI model with R2](https://developers.cloudflare.com/workers/tutorials/create-finetuned-chatgpt-ai-models-with-r2/) | over 1 year ago | Intermediate |
| [Protect an R2 Bucket with Cloudflare Access](https://developers.cloudflare.com/r2/tutorials/cloudflare-access/) | almost 2 years ago | |
| [Log and store upload events in R2 with event notifications](https://developers.cloudflare.com/r2/tutorials/upload-logs-event-notifications/) | almost 2 years ago | Beginner |
| [Use Cloudflare R2 as a Zero Trust log destination](https://developers.cloudflare.com/cloudflare-one/tutorials/r2-logs/) | about 2 years ago | Beginner |
| [Deploy a Browser Rendering Worker with Durable Objects](https://developers.cloudflare.com/browser-rendering/workers-bindings/browser-rendering-with-do/) | over 2 years ago | Beginner |
| [Securely access and upload assets with Cloudflare R2](https://developers.cloudflare.com/workers/tutorials/upload-assets-with-r2/) | over 2 years ago | Beginner |
| [Mastodon](https://developers.cloudflare.com/r2/tutorials/mastodon/) | about 3 years ago | Beginner |
| [Postman](https://developers.cloudflare.com/r2/tutorials/postman/) | over 3 years ago | |
## Videos
Welcome to the Cloudflare Developer Channel
Welcome to the Cloudflare Developers YouTube channel. We've got tutorials and working demos and everything you need to level up your projects. Whether you're working on your next big thing or just dorking around with some side projects, we've got you covered! So why don't you come hang out, subscribe to our developer channel and together we'll build something awesome. You're gonna love it.
Optimize your AI App & fine-tune models (AI Gateway, R2)
In this workshop, Kristian Freeman, Cloudflare Developer Advocate, shows how to optimize your existing AI applications with Cloudflare AI Gateway, and how to finetune OpenAI models using R2.
---
title: Videos · Cloudflare R2 docs
lastUpdated: 2025-06-05T08:11:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/r2/video-tutorials/
md: https://developers.cloudflare.com/r2/video-tutorials/index.md
---
[Introduction to R2 ](https://developers.cloudflare.com/learning-paths/r2-intro/series/r2-1/)Learn about Cloudflare R2, an object storage solution designed to handle your data and files efficiently. It is ideal for storing large media files, creating data lakes, or delivering web assets.
---
title: 404 - Page Not Found · Cloudflare Radar docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/404/
md: https://developers.cloudflare.com/radar/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: API reference · Cloudflare Radar docs
lastUpdated: 2025-05-02T13:54:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/api-reference/
md: https://developers.cloudflare.com/radar/api-reference/index.md
---
---
title: Concepts · Cloudflare Radar docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/concepts/
md: https://developers.cloudflare.com/radar/concepts/index.md
---
* [Aggregation intervals](https://developers.cloudflare.com/radar/concepts/aggregation-intervals/)
* [Bot classes](https://developers.cloudflare.com/radar/concepts/bot-classes/)
* [Confidence levels](https://developers.cloudflare.com/radar/concepts/confidence-levels/)
* [Normalization methods](https://developers.cloudflare.com/radar/concepts/normalization/)
---
title: Get started · Cloudflare Radar docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/get-started/
md: https://developers.cloudflare.com/radar/get-started/index.md
---
* [Make your first API request](https://developers.cloudflare.com/radar/get-started/first-request/)
* [Make comparisons](https://developers.cloudflare.com/radar/get-started/making-comparisons/)
* [Radar API error codes](https://developers.cloudflare.com/radar/get-started/error-codes/)
* [Share a Radar chart](https://developers.cloudflare.com/radar/get-started/embed/)
* [Configure alerts](https://developers.cloudflare.com/radar/get-started/configure-alerts/)
---
title: Glossary · Cloudflare Radar docs
description: This page provides a list of terms and concepts to help you
understand Radar and the information shown.
lastUpdated: 2025-11-24T15:57:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/glossary/
md: https://developers.cloudflare.com/radar/glossary/index.md
---
This page provides a list of terms and concepts to help you understand Radar and the information shown.
## AI bot and crawler traffic
HTTP request activity from user agents associated with AI assistants, AI data scrapers, and AI search crawlers. This information is normalized to show trends in traffic volume, providing insights into the activity levels of AI-driven web interactions over time. User agents included in this analysis are derived from the AI-focused user agents listed in the [ai.robots.txt](https://github.com/ai-robots-txt/ai.robots.txt) repository.
## Application-level attacks
Layer 7 attack information based on mitigated requests, including the most frequent mitigation techniques as well as the trend of mitigated request volume over time. For the "Application layer attack volume" and "Mitigated traffic sources" graphs, the selected location or ASN is the source of the mitigated requests. For the "Application layer attack distribution" graph, the Origin Location graph shows where attacks targeting the selected location are coming from and the Target Location graph shows the target locations of attacks coming from the selected location. "Application layer attack distribution" insights are not available at an ASN level.
## Authentication methods
[SPF](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#spf), [DKIM](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#dkim), and [DMARC](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#dmarc) are policy-driven email authentication methods and when used together, they help prevent spammers, phishers, and other unauthorized parties from sending emails on behalf of a domain they do not own. PASS is the share of processed messages that pass the associated checks. FAIL is the share of processed messages that fail the associated checks. NONE is the share of processed messages for which no associated policy could be found. Data for these metrics comes from Cloudflare’s email routing service.
## Autonomous systems
The Internet is a network of networks, and autonomous systems are the networks that make up the Internet. More specifically, an autonomous system (AS) is a large network or group of networks that has a unified routing policy - the process by which a path through one or more networks is chosen.
Data packets hop from one AS to another until they reach their final destination. Every computer or device that connects to the Internet is connected to an AS. ISPs have one or more ASes, and each AS is assigned an official Autonomous System Number (ASN) for use in Border Gateway Protocol (BGP) routing. For example, Cloudflare's ASN is AS13335. Learn more in the [Cloudflare Learning Center](https://www.cloudflare.com/learning/network-layer/what-is-an-autonomous-system/).
## BGP announcements
Border Gateway Protocol (BGP) is the routing protocol for the Internet. Much like the post office processing mail, BGP picks the most efficient routes for delivering Internet traffic. A BGP announcement is a way for an AS to say to another, "When you receive traffic to this network prefix, please send it to me". That message is then processed and (possibly) forwarded to other ASes, allowing for every AS in the path to learn where to send traffic to that network prefix. Learn more in the [Cloudflare Learning Center](https://www.cloudflare.com/learning/security/glossary/what-is-bgp/).
On Cloudflare Radar, we provide time series charts for both the volume of BGP messages announced by ASes and the total size of their announced IP address space. BGP message volume shows the level of overall routing activity for a given AS, while announced IP address space indicates the size of the networks a given AS operates over time. We represent the IP address space size with the number of minimum routable network prefix sizes, which are the number of /24 prefixes for IPv4 and /48s for IPv6. Correspondingly, a /24 prefix represents 256 IP addresses while a /48 represents 2^80 IP addresses.
## BGP route leaks
[BGP route leaks](https://www.rfc-editor.org/rfc/rfc7908.html) are defined as the propagation of routing announcements beyond their intended scope. In Cloudflare Radar, you can inspect the detected route leak events on the corresponding autonomous system number (ASN) pages. The columns in the table are defined as follows:
* `From`: The autonomous system (AS) from which the routes are learned from.
* `By`: The AS that leaked the routes, or the leaker.
* `To`: The AS that received and propagated the leaked routes.
* `Start` and `End`: The starting and ending time of a route leak event.
* `BGP Msgs.`: The number of BGP announcements that contain leaked routes.
* `Prefixes`: The number of IP prefixes a route leak event affects.
* `Origins`: The number of origin ASes a route leak event affects.
* `Vantage Points`: The number of route collectors that observed a route leak event.
Learn more about our route leak detection system design and usages in [How we detect route leaks and our new Cloudflare Radar route leak service](https://blog.cloudflare.com/route-leak-detection-with-cloudflare-radar/) blog post.
## BGP origin hijacks
[BGP origin hijack](https://www.cloudflare.com/learning/security/glossary/bgp-hijacking/) is one type of BGP anomaly where networks falsely announce ownership for groups of IP addresses (prefixes) that they do not own, control, or route to. A BGP origin hijack can redirect Internet traffic to the hijacker from its legitimate destination, causing data loss with potential leak of private/confidential information.
In Cloudflare Radar, you can inspect the detected BGP origin hijack events in the "BGP Origin Hijacks" table. The columns of the table are defined as follows:
* `ID`: Event ID, clickable and navigates to the event details page.
* `Detected Origin`: The AS that originated the prefixes at the time of detection, potentially being a BGP hijacker.
* `Expected Origin(s)`: The AS(es) that are expected to originate the corresponding prefixes based on various evidences.
* `Start Time (UTC)` and `Duration`: The detected timestamp in UTC with a human-readable time duration for how long the event lasted. Ongoing events will not have a duration value, indicated by the `--` sign.
* `BGP Messages`: The number of BGP messages that contain the detected anomaly.
* `Prefixes`: The prefixes hijacked during the event, showing only one full prefix due to table space limitation.
* `Confidence`: The level of confidence that we have on the event being a true hijacks. Values can be `High`, `Medium`, or `Low`.
* `Tags`: The relevant evidence presented as short tags, presenting key facts we compiled using additional data sources, such as RPKI validation results or network relationship.
You can also access the detection result programmatically via our [public API](https://developers.cloudflare.com/api/resources/radar/subresources/bgp/subresources/hijacks/subresources/events/methods/list/) ([CC BY-NC 4.0](https://creativecommons.org/licenses/by-nc/4.0/) license).
## BGP real-time routes
Cloudflare Radar's prefix routing page displays real-time BGP routes as a [Sankey diagram](https://en.wikipedia.org/wiki/Sankey_diagram). This visualization is built using MRT data from [RouteViews](https://www.routeviews.org/routeviews/) and [RIPE RIS](https://www.ripe.net/analyse/internet-measurements/routing-information-service-ris/), combined with real-time streams from RouteViews' Kafka instance and [RIS Live](https://ris-live.ripe.net/).
By default, the route visualization shows paths from the originating AS to [Tier-1 networks](https://en.wikipedia.org/wiki/Tier_1_network), omitting the segments from Tier-1 networks to BGP route collectors for clarity. Users can choose to see the complete paths using the "Show full paths" toggle.
Above the visualization, a table details the prefix origin, including the originating AS, its visibility percentage across route collectors, and [RPKI](https://blog.cloudflare.com/rpki-details/) validation status (`valid`, `invalid`, `unknown`).
Hovering over a link in the diagram reveals a tooltip with the connected ASNs, the observing BGP route collectors (from [RIPE RIS](https://ris.ripe.net/docs/route-collectors/) and [RouteViews](https://www.routeviews.org/routeviews/collectors/)), and the last update timestamp.
## Certificates
Encryption is a critical part of a safe Internet. SSL/TLS is the standard security technology for establishing an encrypted link between a client and a server.
In Cloudflare Radar, you can view all certificates issued for a given domain by a trusted Certificate Authority that are listed in active certificate transparency logs.
You can review the certificates issued for your domain name to ensure that there have been no incorrect or fraudulent issuances of certificates associated with your domains. You can also sign up to receive alerts from our certificate transparency monitor in the [Cloudflare Dashboard](https://dash.cloudflare.com/).
## Certificate Transparency
[Certificate Transparency (CT)](https://certificate.transparency.dev/) is an Internet security standard for monitoring and auditing the issuance of digital certificates issued by Certification Authorities (CAs). CT helps detect misissued or malicious certificates by requiring CAs to publicly log all certificates they issue in append-only, verifiable logs. These logs are monitored by various entities, including browsers and security researchers, to ensure transparency and trust in the certificate ecosystem.
Key entities in CT include:
* **CAs:** Organizations that issue certificates.
* **CT Logs:** Public, append-only logs where issued certificates are recorded.
* **Monitors:** Parties that check logs for correctness.
The data available in Cloudflare Radar is derived from the CT logs currently monitored by Cloudflare. This enables visibility into certificate issuance trends, distributions, and metadata across the web.
## Connection characteristics
Share of inbound connections to Cloudflare from mail transfer agents with the given characteristics. “IP Version” breaks down connections made over IPv4 and IPv6. “Encryption” breaks down connections made over an encrypted connection using TLS, and those made over an unencrypted connection, in the clear. Data for these metrics comes from Cloudflare’s email routing service.
## Connection quality
Connection quality metrics include download and upload speed, latency (round-trip time), and latency jitter (round-trip time stability), reflecting the best expected performance for specific countries or ASNs. These metrics are derived from speed tests initiated by end users on the [Cloudflare Speed Test website](https://speed.cloudflare.com/), aggregated over the previous 90 days. The underlying raw data is freely accessible for analysis through [Measurement Lab's BigQuery](https://blog.cloudflare.com/aim-database-for-internet-quality/).
In speed, latency, and jitter rankings, only countries where users run speed tests with sufficient regularity are included. Consequently, certain countries may be excluded from the rankings, even though their data can be found in other sections of Radar.
Cloudflare Speed Test measures latency multiple times over the course of the test. Measurements taken before a download or upload begins are aggregated into idle latency and jitter, while measurements taken while a download or upload is in progress are aggregated as loaded latency and jitter.
## Content categories
Cloudflare uses a variety of data sources to categorize domains. Using Cloudflare Radar, you can view the content categories associated with a given domain. Cloudflare customers using [Cloudflare Gateway](https://developers.cloudflare.com/cloudflare-one/traffic-policies/domain-categories/) or [1.1.1.1 for Families](https://developers.cloudflare.com/1.1.1.1/setup/#1111-for-families) can decide to block certain categories, like "Adult Content", in addition to security threats like malware and phishing.
In some cases, a domain may be miscategorized. For example, a social media site might be categorized as "Shopping & Auctions". If you believe a domain is miscategorized, or a domain has not yet been categorized, please provide your suggested category using [this form](https://radar.cloudflare.com/domains/feedback) to bring it to our attention.
## DNS
The [Domain Name System (DNS)](https://www.cloudflare.com/learning/dns/what-is-dns/) is a network service that is most commonly used to translate human-readable domain names into numerical IP addresses that computers can use to talk to each other. It is an essential Internet service, and is also used to look up other network-related information.
The data displayed on Radar for DNS is based on aggregated and anonymized DNS lookups to Cloudflare's [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/) public resolver service.
## DNS magnitude
DNS Magnitude is a metric originally developed by [nic.at](https://www.nic.at/media/files/pdf/dns-magnitude-paper-20200601.pdf) (PDF) to estimate a domain’s overall visibility on the Internet.
Instead of only counting the total number of DNS queries, DNS Magnitude incorporates a sense of how many unique clients send queries to domains within the TLD. This approach gives a more accurate picture of a TLD’s reach, since a small number of sources can generate a large number of queries. Our ranking is based on queries observed at Cloudflare’s [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/) public resolver. We aggregate individual client IP addresses into subnets, referred to here as "networks".
The magnitude value ranges from 0 to 10, with higher values (closer to 10) indicating that the TLD is queried by a broader range of networks.
This reflects greater global visibility and, in some cases, a higher likelihood of name collision across different systems. [According to ICANN](https://www.icann.org/resources/pages/name-collision-2013-12-06-en), a name collision occurs when an attempt to resolve a name used in a private name space (such as under a non-delegated Top-Level Domain) results in a query to the public DNS. When the administrative boundaries of private and public namespaces overlap, name resolution may yield unintended or harmful results. For example, if ICANN were to delegate `.home`, that could cause significant issues for hobbyists that use the (currently non-delegated) TLD within their local networks.
## Domain rankings
Domain Rankings is based on our anonymized and aggregated [1.1.1.1 DNS resolver](https://developers.cloudflare.com/1.1.1.1/) data, complies with our [privacy policy](https://www.cloudflare.com/en-gb/privacypolicy/), and aims to identify the top most popular domains that reflect how people use the Internet globally. Domain Rankings’ popularity metric is best described as the estimated number of unique users that access a domain over some period of time.
Trending domains are domains which are currently experiencing an increase in popularity. Domains Trending Today are domains spiking in popularity, reflecting increased interest potentially related to a particular event or a topic. Domains Trending This Week are domains that have steadily grown in popularity, reflecting an increase of their user base over the week.
## Geographical distribution
Countries contributing traffic to this AS, and their relative contribution as percentage of the total AS traffic seen by Cloudflare.
## HTTP origins
HTTP origins trends provide visibility into the status of traffic between [Cloudflare's global network](https://www.cloudflare.com/network/) and cloud-based [origin infrastructure](https://www.cloudflare.com/learning/cdn/glossary/origin-server/). This data comes from requests sent by Cloudflare to origin servers. The metrics track key indicators such as HTTP status codes, response times, and traffic volume over time, allowing us to identify degradations, outages, or anomalies in origin server performance and availability.
## Internet outages
Internet connectivity can experience outages or disruptions due to a number of factors. These factors include power outages, damage to fiber optic cables, severe weather, natural disasters, or government directed shutdowns. Outages may be sub-national or national in geographic scope, or may impact one or more [ASNs](https://www.cloudflare.com/en-gb/learning/network-layer/what-is-an-autonomous-system/). Some outages may be brief, lasting just a few minutes, while others can stretch on for months — the duration can be related, in part, to the underlying cause. Internet outages listed in the Cloudflare Radar Outage Center are notable drops in traffic that have generally been corroborated with third party-information, which may include a social media or status page post from a telecommunications provider, a news report, or industry/community mailing lists.
An early warning signal that an Internet outage may be underway on a given network or in a given country is an anomalous drop in traffic as compared to historical traffic patterns and trends. Internet anomalies listed in the Cloudflare Radar Outage Center represent an algorithmically-observed anomalous drop in traffic for the listed entity. If a given entry is marked as verified, it means that we have manually corroborated the observed drop in traffic across multiple Cloudflare data sources and/or third-party sources such as [IODA](https://ioda.inetintel.cc.gatech.edu/), or third-party sources of information, such as those listed above. In the case of the latter, an associated Internet outage event will be opened, with the event listed in the Internet Outages table (and API).
## Internet services ranking
Internet services ranking is based on our anonymized and aggregated [1.1.1.1 DNS resolver](https://developers.cloudflare.com/1.1.1.1/) data, complies with our [privacy policy](https://www.cloudflare.com/en-gb/privacypolicy/), and aims to identify the top most popular Internet services that reflect how people use the Internet globally. A service represents one or more domains aggregated together. Ranking popularity metric is best described as the estimated number of unique users that access domains associated with a service, over some period of time.
## Internet traffic trends
Trends observed in Internet traffic originating globally or within a given location or autonomous system within the selected time range, based on aggregated data from our network.
## IP address geolocation
IP address geolocation is the term used for the process of associating an IP address with a location in the physical world. IP geolocation used on Cloudflare Radar comes from a third-party database.
Note that a number of factors may affect the accuracy of the geolocation information, including mobile network architecture, the use of VPN services, and the use of privacy-protecting proxy services.
Learn more from Cloudflare's documentation on [IP geolocation](https://developers.cloudflare.com/network/ip-geolocation/#report-an-incorrect-ip-location) about how to suggest a correction if you believe the location provided is incorrect.
## IPv6 adoption
The IPv4 vs. IPv6 graph shows the distribution of traffic by IP version, and is intended to highlight IPv6 adoption trends.
Note that prior to January 23, 2023, the IPv6 percentage shown in the chart was calculated as (IPv6 requests / IPv4+IPv6 requests). After that date, the IPv6 percentage is calculated as (IPv6 requests / requests for dual-stacked content).
## IQI
The Internet Quality Index estimates connection performance under average utilization, such as web browsing. It is based on end user measurements against a fixed set of Cloudflare and third-party targets, providing numbers for bandwidth, round-trip time (latency), and DNS response time, aggregated by continent, country, or ASN.
The IQI methodology requires a minimum number of measurements to generate estimates. As a result, graphs for smaller countries and ASNs may display occasional gaps, especially during nighttime. These gaps do not indicate outages. The number of measurements underlying IQI does not necessarily correlate with the volume of traffic observed by Cloudflare in a specific country or ASN.
## IRR AS-SETs
An IRR AS-SET is a named collection of Autonomous System Numbers (ASNs) within the Internet Routing Registry (IRR) used to define and manage BGP routing policies. By grouping related networks, such as customers and downstream peers, under a single identifier, network operators can automate the creation of BGP filters, which are essential for preventing the propagation of BGP route leaks. AS-SETs can be hierarchical, meaning they can include other AS-SETs as members, creating a scalable but complex structure. To quantify this complexity, the "AS Cone" measures the total number of unique ASNs in a fully expanded set (its downstream footprint), while "Upstreams" measures how many other AS-SETs include it directly or indirectly, providing insight into its role in the global routing system.
An AS-SET does not inherently includes its owner networks. Cloudflare Radar infers the owner by matching the AS-SET name on [PeeringDB](https://www.peeringdb.com/) or by the name itself. When an AS-SET's owner can be inferred via both methods, we prefer the PeeringDB information.
## Leaked credentials
[Leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/) scans incoming HTTP requests for known authentication patterns from common web apps and any custom detection locations that were configured. Cloudflare Radar provides visibility into aggregate trends in authentication requests, including the detection of leaked credentials.
## Mobile operating systems
The Mobile Operating Systems graph shows the distribution of mobile device requests by operating system, representing trends observed in Internet traffic originating globally or within a given location or autonomous system within the selected time range, based on aggregated data from our network. "Mobile device" includes phones and tablets only, and does not include other types of devices, such as those classified as desktops/laptops, smart TVs, or gaming consoles.
## Most observed TLDs
[Top-level domains, also known as TLDs](https://www.cloudflare.com/learning/dns/top-level-domain/), are found in the right-most portion of a hostname. As of February 2024, there are nearly 1600 Top Level Domains listed in the [IANA Root Zone Database](https://www.iana.org/domains/root/db). On Radar, we are sharing our own perspective on these TLDs, highlighting those with the largest shares of spam and malicious emails. The analysis is based on the sending domain’s TLD, found in the `From:` header of an email message. Data for this metric comes from Cloudflare’s cloud email security service.
## Network-level DDoS attacks
Attacks mitigated by our Level 3 and 4 Denial of Service Attack prevention systems. We show the most used attack vectors as well as the change in attack volume over the selected time range. Selected location is the location of the data center(s) where the attacks were mitigated. Target industry and vertical categories are associated with the customers being attacked.
Industry categories include business types grouped by their primary activities, such as information technology and services, retail, or telecommunications. Vertical categories are high-level groupings that incorporate related industries, such as the "Internet and Telecom" vertical, which includes industries such as "Internet" and "Telecommunications".
Network-level DDoS attacks graphs are based on traffic measured in bytes.
## Post-quantum encryption adoption
The Post-Quantum Encryption Adoption graph shows the share of HTTPS requests to Cloudflare that are encrypted with post-quantum (PQ) cryptography. Additional details about Cloudflare's support for PQ cryptography can be found at [Cloudflare Research](https://pq.cloudflareresearch.com/).
## Robots.txt
A [robots.txt](https://www.cloudflare.com/learning/bots/what-is-robots-txt/) file contains instructions for bots that tell them which webpages they can and cannot access.
The data displayed for robots.txt is based on successfully parsed robots.txt files from the top 10,000 domains. From these files, we count the occurrences of each user agent under the `Allow` and `Disallow` directives. A user agent is classified as "fully allowed" or "fully disallowed" if the directive value is `*`. Otherwise, if the user agent is only allowed or disallowed to crawl specific paths, it is classified as "partially allowed" or "partially disallowed."
Currently, we only include AI-focused user agents listed in the [ai.robots.txt](https://github.com/ai-robots-txt/ai.robots.txt) repository.
## TCP resets and timeouts
In the Transmission Control Protocol (TCP), client-initiated connection resets (via the RST flag, TCP's "panic button") are atypical, and indicate to the server that *something went wrong* requiring the connection to be closed immediately. Similarly, connection timeouts (where the server closes a connection due to an unresponsive client) should not happen in conventional data exchanges. For comparison, a typical TCP connection consists of a 3-way handshake initiated by a client with a SYN packet to the server, then a data exchange moderated with ACK and PSH flags in the data packets, and finally a graceful close initiated from either side with a FIN packet. A FIN close is considered graceful because it ensures both sides complete their data transfer before closing the connection. In contrast, a timeout or RST flag triggers a hard stop, even if data is waiting to be sent or acknowledged. See [RFC 9293](https://datatracker.ietf.org/doc/html/rfc9293) for more details on the TCP protocol.
A TCP server may see timed-out or reset connections for a variety of reasons. Some are benign, such as client applications that lose connectivity or abruptly shut down (e.g., browsers cleaning up closed tabs or port scanners). Others are more concerning, such as [DoS attacks](https://www.cloudflare.com/learning/ddos/syn-flood-ddos-attack/) or third-party interference. In some cases, a close examination of the packets in a connection can help to shed light on the reason for termination. For example, [Global, Passive Detection of Connection Tampering](https://research.cloudflare.com/publications/SundaraRaman2023/) finds that certain packet patterns can be linked to middlebox connection tampering.
On Cloudflare Radar’s [Security & Attacks page](https://radar.cloudflare.com/security-and-attacks), you can view statistics on resets and timeouts from a sample of TCP connections to Cloudflare’s servers, broken down by how far the connection progressed before termination. The plot lines are defined as follows:
* **Post-SYN (mid-handshake)**: Connection resets or timeouts after the server received only a single SYN packet.
* **Post-ACK (immediately post-handshake)**: Connection resets or timeouts after the server received both a SYN packet and an ACK packet, meaning the connection was successfully established.
* **Post-PSH (after first data packet)**: Connection resets or timeouts after the server received a packet with PSH flag set, following connection establishment. The PSH flag indicates that the TCP packet contains data (such as a TLS Client Hello message) ready to deliver to the application.
* **Later (after multiple data packets)**: Connection resets within the first 10 packets from the client, but after the server has received multiple data packets.
* **None**: All other connections.
Learn more about the TCP resets and timeouts dataset in our [blog post](https://blog.cloudflare.com/tcp-resets-timeouts).
## Threat categories
Attackers use multiple types of techniques when carrying out email-based attacks, including links or attachments leading to malware; identity deception, where the message appears to be coming from a trusted contact; and brand impersonation, where the message appears to be coming from a trusted brand. Categories are assigned to the various types of threats found during the analysis of a malicious email message, and a single message can have multiple categories. These categories are aggregated into “Link”, “Attachment”, “Impersonation”, and “Other” groupings. “Link” groups individual threat types where the attacker is trying to get the user to click on something, “Attachment” groups individual threat types where the attacker has attached a file to the email message, and “Impersonation” groups individual threat types where the attacker is impersonating a trusted brand or contact. The “Other” grouping includes other threat types not covered by the previous three. The percentages represent the share of malicious email messages where the given threat categories have been found. Data for this metric comes from Cloudflare’s cloud email security service.
## Threat classification
Malicious email messages may be part of a phishing campaign, where recipients are tricked into sharing personal information like login details, or they are an attempt to spread malware through embedded images, links, or attachments. The percentage shown represents the share of processed messages that are classified as malicious. Data for this metric comes from Cloudflare’s cloud email security service.
## Traffic type filter
* **Human Only Traffic**: Traffic that our algorithms determine as being generated by human activity.
* **Automated Only Traffic**: Traffic that our algorithms determine as being generated by bot or automated script activity.
* **All Traffic**: Use all traffic, which includes both human activity and automated activity.
## Trends
Based on the aggregated HTTP/s metadata we see, we are able to show trends about a diverse set of metrics, including the distribution of mobile device vs. desktop traffic, the percentage of traffic detected as coming from bots, and the distribution of user agents/browsers. We also provide insights into the usage of HTTPS and IPv6.
## Verified bots
Bot traffic describes any non-human traffic to a website or an app. Some bots are useful, such as search engine bots that index content for search or customer service bots that help users. Other bots may be used to perform malicious activities, such as break into user accounts or scan the web for contact information to send spam.
Verified bots, such as the ones from search engines, are usually transparent about who they are. Cloudflare manually approves well-behaved services that benefit the broader Internet and honor robots.txt.
Each entry on the Verified Bots list exists because a corresponding IP address was seen associated with a verified bot in the last 30 days. A verified bot is not necessarily good or bad.
## Visitor location
The data displayed on domain-specific geographic traffic patterns is based solely on data from our recursive DNS services. All data displayed is in accordance with our privacy policies and commitments. This data may include attack traffic and cross-origin requests.
## Web crawlers
[Web crawlers](https://www.cloudflare.com/learning/bots/what-is-a-web-crawler/) are a type of bot that browses the Internet to collect and index website content. They are used by search engines like Google or Bing to make pages discoverable in search results.
They are also used by AI platforms, either to gather content for training large language models, or to retrieve up-to-date information for AI assistants. In both search and AI cases, crawlers work by following links from one page to another, creating a map of online content.
Radar's crawl-to-refer ratio metric is calculated by first mapping crawl requests for HTML pages based on the `User-Agent` header, and referral requests for HTML pages based on the `Referer` header, by platform (e.g., the ratio for Google is based on crawl requests from Googlebot, and referral requests from Google platforms). As with other traffic metrics on Radar, the aggregation resolution for the ratio data is based on the length of the selected timeframe. Additionally, note that traffic referred by native apps may not include a `Referer` header. As such, because the referral counts only include traffic from Web-based tools, these calculations may overstate the respective ratios, but it is unclear by how much.
## WHOIS
WHOIS is a standard for publishing the contact and nameserver information for all registered domains. Each registrar maintains their own WHOIS service. Anyone can query the registrar's WHOIS service to reveal the data behind a given domain.
## Workers AI
[Workers AI](https://developers.cloudflare.com/workers-ai/) allows you to run machine learning models, on the Cloudflare network, from your own code -- whether that be from Workers, Pages, or anywhere via the Cloudflare API. The data displayed for Workers AI is based on the number of Cloudflare accounts using a model during a specific time interval.
---
title: Investigate · Cloudflare Radar docs
description: Explore the different types of data available in Cloudflare Radar,
from NetFlows (what feeds the Internet Traffic Change chart in Radar) to HTTP
requests and DNS queries.
lastUpdated: 2025-02-04T11:06:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/investigate/
md: https://developers.cloudflare.com/radar/investigate/index.md
---
Explore the different types of data available in Cloudflare Radar, from NetFlows (what feeds the [Internet Traffic Change](https://radar.cloudflare.com/) chart in Radar) to HTTP requests and DNS queries.
* [HTTP requests](https://developers.cloudflare.com/radar/investigate/http-requests/)
* [NetFlows](https://developers.cloudflare.com/radar/investigate/netflows/)
* [Application layer attacks](https://developers.cloudflare.com/radar/investigate/application-layer-attacks/)
* [BGP anomalies](https://developers.cloudflare.com/radar/investigate/bgp-anomalies/)
* [DNS](https://developers.cloudflare.com/radar/investigate/dns/)
* [Domains ranking](https://developers.cloudflare.com/radar/investigate/domain-ranking-datasets/)
* [Network layer attacks](https://developers.cloudflare.com/radar/investigate/network-layer-attacks/)
* [Outages](https://developers.cloudflare.com/radar/investigate/outages/)
* [URL Scanner](https://developers.cloudflare.com/radar/investigate/url-scanner/)
---
title: MCP server · Cloudflare Radar docs
lastUpdated: 2025-10-09T17:32:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/mcp-server/
md: https://developers.cloudflare.com/radar/mcp-server/index.md
---
---
title: Reference · Cloudflare Radar docs
description: "Review reference information related to Cloudflare Radar:"
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/reference/
md: https://developers.cloudflare.com/radar/reference/index.md
---
Review reference information related to Cloudflare Radar:
* [Quarterly DDoS threat reports](https://developers.cloudflare.com/radar/reference/quarterly-ddos-reports/)
---
title: Release notes · Cloudflare Radar docs
description: Review recent changes to Cloudflare Radar.
lastUpdated: 2025-05-02T13:54:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/radar/release-notes/
md: https://developers.cloudflare.com/radar/release-notes/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/radar/release-notes/index.xml)
## 2025-12-16
**New client type dimension in Web Crawlers and Mixed Purpose entry**
* Added new Mixed Purpose entry to the `crawl_purpose` dimension of the [Web Crawlers](https://developers.cloudflare.com/api/resources/radar/subresources/bots/subresources/web_crawlers/) API, which as of this release includes Googlebot and Bingbot.
* Added new dimension `client_type` to the [Web Crawlers](https://developers.cloudflare.com/api/resources/radar/subresources/bots/subresources/web_crawlers/) API.
* Added new **HTML page requests by client type graph** to the [AI Insights page](https://radar.cloudflare.com/ai-insights#html-page-requests-by-client-type).
## 2025-11-24
**Add HTTP origins insights**
* Added new [`Origins`](https://developers.cloudflare.com/api/resources/radar/subresources/origins/) API.
* Extended [`Annotations`](https://developers.cloudflare.com/api/resources/radar/subresources/annotations/) and [`Traffic Anomalies`](https://developers.cloudflare.com/api/resources/radar/subresources/traffic_anomalies/) APIs to support origin outages and anomalies.
## 2025-10-27
**Add TLD insights**
* Added new dimensions `tld` and `tld_dns_magnitude` to the [DNS](https://developers.cloudflare.com/api/resources/radar/subresources/dns/) API.
* Added new endpoints [`/tlds`](https://developers.cloudflare.com/api/resources/radar/subresources/tlds/methods/list/) and [`/tlds/{tld}`](https://developers.cloudflare.com/api/resources/radar/subresources/tlds/methods/get/).
## 2025-10-09
**Add CT log activity statistics**
* Added new CT log activity stats to the [Get Certificate Log Details](https://developers.cloudflare.com/api/resources/radar/subresources/ct/subresources/logs/methods/get/) API response.
## 2025-10-06
**Add PQ encryption browser support check**
* Added a [post-quantum encryption browser support check](https://radar.cloudflare.com/adoption-and-usage#browser-support) to the PQ encryption card in the Adoption & Usage section.
## 2025-09-29
**Add geolocation, ADM1 dimension to HTTP endpoints, and NetFlows endpoints**
* Added new [geolocation endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/geolocations/).
* Added new ADM1 dimension to [`HTTP`](https://developers.cloudflare.com/api/resources/radar/subresources/http/) `summary` and `timeseries_groups` endpoints.
* Added new [`NetFlows`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/) summary by dimension endpoint [summary\_v2](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/methods/summary_v2/).
* Added new `geoId` filter to all [`HTTP`](https://developers.cloudflare.com/api/resources/radar/subresources/http/) and [`NetFlows`](https://developers.cloudflare.com/api/resources/radar/subresources/netflows/) endpoints.
## 2025-09-22
**Add IRR AS-SET membership lookup endpoint**
* Added IRR AS-SET membership lookup endpoint
* [`/entities/asns/{asn}/as_set`](https://developers.cloudflare.com/api/resources/radar/subresources/entities/subresources/asns/methods/as_set/)
## 2025-08-27
**Add industry and vertical to AI Bots and Web Crawlers, and bot kind to Bots**
* Added vertical and industry dimensions/filters to:
* [`/ai/bots/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/timeseries_groups/methods/summary/)
* [`/ai/bots/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/timeseries_groups/methods/timeseries_groups/)
* [`/bots/crawlers/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/subresources/web_crawlers/methods/summary/)
* [`/bots/crawlers/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/subresources/web_crawlers/methods/timeseries_groups/)
* Added bot kind dimension/filter to:
* [`/bots/summary/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/summary/)
* [`/bots/timeseries_groups/{dimension}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/timeseries_groups/)
* Added new `botKind` filter to:
* [`/bots/timeseries`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/timeseries/)
* Added new `kind` property/filter to:
* [`/bots`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/list/)
* [`/bots/{bot_slug}`](https://developers.cloudflare.com/api/resources/radar/subresources/bots/methods/get/)
## 2025-08-14
**Add AI Bots crawl purpose**
* Added AI Bots crawl purpose dimension and filter to [summary](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/timeseries_groups/methods/summary/) and [timeseries\_groups](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/timeseries_groups/methods/timeseries_groups/) endpoints.
## 2025-08-06
**Add Certificate Transparency (CT) endpoints**
* Added [CT endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/ct/).
## 2025-07-01
**Add Bots and Web Crawlers endpoints**
* Added new [bots endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/bots/), replacing the deprecated verified bots endpoints. Use the following replacements:
* `/verified_bots/top/bots` → `/bots/summary/bot`
* `/verified_bots/top/categories` → `/bots/summary/bot_category`
* Added [web crawlers endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/bots/subresources/web_crawlers/).
## 2025-03-20
**Endpoint deprecations and new BGP real-time routes endpoint**
* Deprecated endpoints for improved consistency (switch to the following):
* `/attacks/layer3/top/industry` → [`/attacks/layer3/summary/industry`](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/subresources/summary/methods/industry/)
* `/attacks/layer3/top/vertical` → [`/attacks/layer3/summary/vertical`](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/subresources/summary/methods/vertical/)
* `/attacks/layer7/top/industry` → [`/attacks/layer7/summary/industry`](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer7/subresources/summary/methods/industry/)
* `/attacks/layer7/top/vertical` → [`/attacks/layer7/summary/vertical`](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer7/subresources/summary/methods/vertical/)
* Added the [BGP real-time routes endpoint](https://developers.cloudflare.com/api/resources/radar/subresources/bgp/subresources/routes/methods/realtime/).
## 2025-03-18
**Add leaked credential checks endpoints**
* Added [leaked credential checks endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/leaked_credentials/).
## 2025-02-27
**Add DNS endpoints**
* Added [DNS endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/dns/).
## 2025-02-04
**Add Internet services ranking, robots.txt, and AI inference endpoints**
* Added [Internet services ranking endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/ranking/subresources/internet_services/).
* Added [robots.txt endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/robots_txt/).
* Added [AI inference endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/ai/subresources/inference/).
## 2024-06-27
**Change TCP connection tampering API endpoints to TCP Resets Timeouts**
* Changed the connection tampering summary and timeseries API endpoints to TCP resets timeouts [summary](https://developers.cloudflare.com/api/resources/radar/subresources/tcp_resets_timeouts/methods/summary/) and [timeseries](https://developers.cloudflare.com/api/resources/radar/subresources/tcp_resets_timeouts/methods/timeseries_groups/), respectively.
## 2023-11-27
**Add more meta information's**
* Added meta.lastUpdated to all summaries and top endpoints (timeseries and timeseriesGroups already had this).
* Fixed meta.dateRange to return date ranges for all requested series.
## 2023-11-16
**Add new layer 3 endpoints and layer 7 dimensions**
* Added layer 3 [top origin locations](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/subresources/top/subresources/locations/methods/origin/) and [top target location](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/subresources/top/subresources/locations/methods/target/).
* Added layer 7 Summaries by `http_method`, `http_version`, `ip_version`, `managed_rules`, `mitigation_product`.
* Added layer 7 Timeseries Groups by `http_method`, `http_version`, `ip_version`, `managed_rules`, `mitigation_product`, `industry`, `vertical`.
* Added layer 7 Top by `industry`, `vertical`.
* Deprecated layer 7 timeseries groups without dimension.
* To continue getting this data, switch to the new [timeseries group by mitigation\_product](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer7/subresources/timeseries_groups/methods/mitigation_product/) endpoint.
* Deprecated layer 7 summary without dimension.
* To continue getting this data, switch to the new [summary by mitigation\_product](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer7/subresources/summary/methods/mitigation_product/) endpoint.
* Added new [Error codes](https://developers.cloudflare.com/radar/get-started/error-codes/).
## 2023-10-31
**Add new layer 3 direction parameter**
* Added a `direction` parameter to all layer 3 endpoints. Use together with `location` parameter to filter by origin or target location [timeseries groups](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/subresources/timeseries_groups/methods/vector/).
## 2023-09-08
**Add Connection Tampering endpoints**
* Added Connection Tampering [summary](https://developers.cloudflare.com/api/resources/radar/subresources/tcp_resets_timeouts/methods/summary/) and [timeseries](https://developers.cloudflare.com/api/resources/radar/subresources/tcp_resets_timeouts/methods/timeseries_groups/) endpoints.
## 2023-08-14
**Deprecate old layer 3 dataset**
* Added Regional Internet Registry (see field `source` in response) to [get asn by id](https://developers.cloudflare.com/api/resources/radar/subresources/entities/subresources/asns/methods/get/) and [get asn by ip](https://developers.cloudflare.com/api/resources/radar/subresources/entities/subresources/asns/methods/ip/) endpoints.
* Stopped collecting data in the old layer 3 data source.
* Updated layer 3 [timeseries](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/methods/timeseries/) endpoint to start using the new layer 3 data source by default, fetching the old data source now requires sending the parameter `metric=bytes_old`.
* Deprecated layer 3 summary endpoint, this will stop receiving data after 2023-08-14.
* To continue getting this data, switch to the new [timeseries group protocol](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/subresources/summary/methods/protocol/) endpoint.
* Deprecated layer 3 timeseries groups endpoint, this will stop receiving data after 2023-08-14.
* To continue getting this data, switch to the new [timeseries group protocol](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/subresources/timeseries_groups/methods/protocol/) endpoint.
## 2023-07-31
**Fix HTTP timeseries endpoint URLs**
* Updated HTTP `timeseries` endpoints URLs to [`timeseries_groups`](https://developers.cloudflare.com/api/resources/radar/subresources/http/subresources/timeseries_groups/) due to consistency. Old timeseries endpoints are still available, but will soon be removed.
## 2023-07-20
**Add URL Scanner endpoints**
* Added [URL Scanner endpoints](https://developers.cloudflare.com/api/resources/url_scanner/). For more information, refer to [URL Scanner](https://developers.cloudflare.com/radar/investigate/url-scanner/).
## 2023-06-20
**Add Internet quality endpoints**
* Added [Internet quality endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/quality/).
## 2023-06-07
**Add BGP stats, pfx2as and moas endpoints**
* Added BGP [stats](https://developers.cloudflare.com/api/resources/radar/subresources/bgp/subresources/routes/methods/stats/), [pfx2as](https://developers.cloudflare.com/api/resources/radar/subresources/bgp/subresources/routes/methods/pfx2as/) and [moas](https://developers.cloudflare.com/api/resources/radar/subresources/bgp/subresources/routes/methods/moas/) endpoints.
## 2023-05-10
**Added \`IOS\` as an option for the OS parameter in all HTTP**
* Added `IOS` as an option for the OS parameter in all HTTP endpoints ([example](https://developers.cloudflare.com/api/resources/radar/subresources/http/subresources/summary/methods/bot_class/)).
## 2023-03-20
**Add AS112 and email endpoints**
* Added [AS112 endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/as112/).
* Added [email endpoints](https://developers.cloudflare.com/api/resources/radar/subresources/email/).
## 2023-01-23
**Updated IPv6 calculation method**
* IPv6 percentage started to be calculated as (IPv6 requests / requests for dual-stacked content), where as before it was calculated as (IPv6 requests / IPv4+IPv6 requests).
## 2023-01-11
**Add new layer 3 dataset**
* Added new layer 3 data source and related endpoints.
* Updated layer 3 [timeseries](https://developers.cloudflare.com/api/resources/radar/subresources/attacks/subresources/layer3/methods/timeseries/) endpoint to support fetching both current and new data sources. For retro-compatibility reasons, fetching the new data source requires sending the parameter `metric=bytes` else the current data source will be returned.
* Deprecated old layer 3 endpoints timeseries\_groups and summary. Users should upgrade to newer endpoints.
---
title: 404 - Page Not Found · Cloudflare Randomness Beacon docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/randomness-beacon/404/
md: https://developers.cloudflare.com/randomness-beacon/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: About drand · Cloudflare Randomness Beacon docs
description: The drand project aims to address the current lack of services
providing distributed public randomness. Distributed to increase the
resilience and trustworthiness, drand provides a standalone
randomness-as-a-service network that is application agnostic. This is similar
to how NTP networks serve timing information across the globe.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/randomness-beacon/about/
md: https://developers.cloudflare.com/randomness-beacon/about/index.md
---
The drand project aims to address the current lack of services providing distributed public randomness. Distributed to increase the resilience and trustworthiness, drand provides a standalone randomness-as-a-service network that is application agnostic. This is similar to how NTP networks serve timing information across the globe.
drand follows the [KISS principle](https://en.wikipedia.org/wiki/KISS_principle). It relies on well-researched cryptographic building blocks and open-source software design principles and libraries, such as protobuf and gRPC, to ensure high performance and interoperability. drand also attempts to use sane security defaults, such as having TLS enabled by default.
Beyond that, drand adds new features important for its practical deployment, such as being able to securely add and remove members of the network through [resharing](https://ieeexplore.ieee.org/document/1183515) while keeping the same shared public key necessary for randomness verification.
---
title: Cryptographic Background · Cloudflare Randomness Beacon docs
description: drand is an efficient randomness beacon daemon that utilizes
pairing-based cryptography, 𝑡-of-𝑛 distributed key generation, and threshold
BLS signatures to generate publicly-verifiable, unbiasable, unpredictable,
distributed randomness.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/randomness-beacon/cryptographic-background/
md: https://developers.cloudflare.com/randomness-beacon/cryptographic-background/index.md
---
drand is an efficient randomness beacon daemon that utilizes pairing-based cryptography, `𝑡-of-𝑛` distributed key generation, and threshold BLS signatures to generate publicly-verifiable, unbiasable, unpredictable, distributed randomness.
This is an overview of the cryptographic building blocks drand uses to generate publicly-verifiable, unbiasable, and unpredictable randomness in a distributed manner.
The drand beacon has two phases: a setup phase and a beacon phase. Generally, we assume that there are *n* participants, out of which at most *f\
---
title: Operator Guide · Cloudflare Randomness Beacon docs
description: For the most up-to-date operator documentation, please visit
drand.love/operator.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/randomness-beacon/operator-guide/
md: https://developers.cloudflare.com/randomness-beacon/operator-guide/index.md
---
For the most up-to-date operator documentation, please visit [drand.love/operator](https://drand.love/operator/).
---
title: User Guide · Cloudflare Randomness Beacon docs
description: For the most up-to-date user documentation, please visit drand.love/developer.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/randomness-beacon/user-guide/
md: https://developers.cloudflare.com/randomness-beacon/user-guide/index.md
---
For the most up-to-date user documentation, please visit [drand.love/developer](https://drand.love/developer/).
---
title: 404 - Page Not Found · Cloudflare Realtime docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/realtime/404/
md: https://developers.cloudflare.com/realtime/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Realtime Agents · Cloudflare Realtime docs
lastUpdated: 2026-01-15T16:49:28.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/realtime/agents/
md: https://developers.cloudflare.com/realtime/agents/index.md
---
* [Getting started](https://developers.cloudflare.com/realtime/agents/getting-started/)
---
title: Overview · Cloudflare Realtime docs
description: "With RealtimeKit, you can expect:"
lastUpdated: 2025-12-08T11:30:45.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/realtime/realtimekit/
md: https://developers.cloudflare.com/realtime/realtimekit/index.md
---
Add live video and voice to your web or mobile apps in minutes — customizable SDKs, Integrate in just a few lines of code.
With RealtimeKit, you can expect:
* **Fast, simple integration:** Add live video and voice calling to any platform using our SDKs in minutes.
* **Customizable:** Tailor the experience to your needs.
* **Powered by WebRTC:** Built on top of modern, battle-tested WebRTC technology. RealtimeKit sits on top of [Realtime SFU](https://developers.cloudflare.com/realtime/sfu/) handling media track management, peer management, and other complicated tasks for you.
Experience the product:
[Try A Demo Meeting](https://demo.realtime.cloudflare.com)
[Build using Examples](https://github.com/cloudflare/realtimekit-web-examples)
[RealtimeKit Dashboard](https://dash.cloudflare.com/?to=/:account/realtime/kit)
## Build with RealtimeKit
RealtimeKit powers a wide range of usecases — here are the most common ones
#### Group Calls
Experience team meetings, virtual classrooms with interactive plugins, and seamless private or group video chats — all within your platform.
#### Webinars
Host large, interactive one-to-many events with virtual stage management, and engagement tools like plugins, chat, and polls — ideal for product demos, company all-hands, and live workshops
#### Audio Only Calls
Host audio-only calls — perfect for team discussions, support lines, and community hangouts— low bandwidth usage and features like mute controls, hand-raise, and role management.
## Product Suite
* [**UI Kit**](https://developers.cloudflare.com/realtime/realtimekit/ui-kit) UI library of pre-built, customizable components for rapid development — sits on top of the Core SDK.
* [**Core SDK**](https://developers.cloudflare.com/realtime/realtimekit/core) Client SDK built on top of Realtime SFU that provides a full set of APIs for managing video calls, from joining and leaving sessions to muting, unmuting, and toggling audio and video.
* [**Realtime SFU**](https://developers.cloudflare.com/realtime/sfu) efficiently routes media with low latency—all running on Cloudflare’s global network for reliability and scale.
The **Backend Infrastructure** Powering the SDKs is a robust layer that includes REST APIs for managing meetings, participants, recordings and more, along with webhooks for server-side events. A dedicated signalling server coordinates real-time updates.
---
title: Overview · Cloudflare Realtime docs
description: Cloudflare Realtime SFU is infrastructure for real-time
audio/video/data applications. It allows you to build real-time apps without
worrying about scaling or regions. It can act as a selective forwarding unit
(WebRTC SFU), as a fanout delivery system for broadcasting (WebRTC CDN) or
anything in between.
lastUpdated: 2025-08-18T10:34:43.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/realtime/sfu/
md: https://developers.cloudflare.com/realtime/sfu/index.md
---
Build real-time serverless video, audio and data applications.
Cloudflare Realtime SFU is infrastructure for real-time audio/video/data applications. It allows you to build real-time apps without worrying about scaling or regions. It can act as a selective forwarding unit (WebRTC SFU), as a fanout delivery system for broadcasting (WebRTC CDN) or anything in between.
Cloudflare Realtime SFU runs on [Cloudflare's global cloud network](https://www.cloudflare.com/network/) in hundreds of cities worldwide.
[Get started](https://developers.cloudflare.com/realtime/sfu/get-started/)
[Realtime dashboard](https://dash.cloudflare.com/?to=/:account/calls)
[Orange Meets demo app](https://github.com/cloudflare/orange)
---
title: TURN Service · Cloudflare Realtime docs
description: Separately from the SFU, Realtime offers a managed TURN service.
TURN acts as a relay point for traffic between WebRTC clients like the browser
and SFUs, particularly in scenarios where direct communication is obstructed
by NATs or firewalls. TURN maintains an allocation of public IP addresses and
ports for each session, ensuring connectivity even in restrictive network
environments.
lastUpdated: 2025-11-26T14:06:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/realtime/turn/
md: https://developers.cloudflare.com/realtime/turn/index.md
---
Separately from the SFU, Realtime offers a managed TURN service. TURN acts as a relay point for traffic between WebRTC clients like the browser and SFUs, particularly in scenarios where direct communication is obstructed by NATs or firewalls. TURN maintains an allocation of public IP addresses and ports for each session, ensuring connectivity even in restrictive network environments.
Using Cloudflare Realtime TURN service is available free of charge when used together with the Realtime SFU. Otherwise, it costs $0.05/real-time GB outbound from Cloudflare to the TURN client.
## Service address and ports
| Protocol | Primary address | Primary port | Alternate port |
| - | - | - | - |
| STUN over UDP | stun.cloudflare.com | 3478/udp | 53/udp |
| TURN over UDP | turn.cloudflare.com | 3478/udp | 53 udp |
| TURN over TCP | turn.cloudflare.com | 3478/tcp | 80/tcp |
| TURN over TLS | turn.cloudflare.com | 5349/tcp | 443/tcp |
Note
Use of alternate port 53 only by itself is not recommended. Port 53 is blocked by many ISPs, and by popular browsers such as [Chrome](https://chromium.googlesource.com/chromium/src.git/+/refs/heads/master/net/base/port_util.cc#44) and [Firefox](https://github.com/mozilla/gecko-dev/blob/master/netwerk/base/nsIOService.cpp#L132). It is useful only in certain specific scenerios.
## Regions
Cloudflare Realtime TURN service runs on [Cloudflare's global network](https://www.cloudflare.com/network) - a growing global network of thousands of machines distributed across hundreds of locations, with the notable exception of the Cloudflare's [China Network](https://developers.cloudflare.com/china-network/).
When a client tries to connect to `turn.cloudflare.com`, it *automatically* connects to the Cloudflare location closest to them. We achieve this using [anycast routing](https://www.cloudflare.com/learning/cdn/glossary/anycast-network/).
To learn more about the architecture that makes this possible, read this [technical deep-dive about Realtime](https://blog.cloudflare.com/cloudflare-calls-anycast-webrtc).
## Protocols and Ciphers for TURN over TLS
TLS versions supported include TLS 1.1, TLS 1.2, and TLS 1.3.
| OpenSSL Name | TLS 1.1 | TLS 1.2 | TLS 1.3 |
| - | - | - | - |
| AEAD-AES128-GCM-SHA256 | No | No | ✅ |
| AEAD-AES256-GCM-SHA384 | No | No | ✅ |
| AEAD-CHACHA20-POLY1305-SHA256 | No | No | ✅ |
| ECDHE-ECDSA-AES128-GCM-SHA256 | No | ✅ | No |
| ECDHE-RSA-AES128-GCM-SHA256 | No | ✅ | No |
| ECDHE-RSA-AES128-SHA | ✅ | ✅ | No |
| AES128-GCM-SHA256 | No | ✅ | No |
| AES128-SHA | ✅ | ✅ | No |
| AES256-SHA | ✅ | ✅ | No |
## MTU
There is no specific MTU limit for Cloudflare Realtime TURN service.
## Limits
Cloudflare Realtime TURN service places limits on:
* Unique IP address you can communicate with per relay allocation (>5 new IP/sec)
* Packet rate outbound and inbound to the relay allocation (>5-10 kpps)
* Data rate outbound and inbound to the relay allocation (>50-100 Mbps)
Limits apply to each TURN allocation independently
Each limit is for a single TURN allocation (single TURN user) and not account wide. Same limit will apply to each user regardless of the number of unique TURN users.
These limits are suitable for high-demand applications and also have burst rates higher than those documented above. Hitting these limits will result in packet drops.
---
title: 404 - Page Not Found · Cloudflare Reference Architecture docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/reference-architecture/404/
md: https://developers.cloudflare.com/reference-architecture/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Reference Architectures · Cloudflare Reference Architecture docs
description: Reference architecture documents and diagrams are designed to
provide a foundational knowledge of the Cloudflare platform and products.
Building on the information in these documents, you can architect software
solutions based on your specific context and needs.
lastUpdated: 2024-12-12T12:06:35.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/reference-architecture/architectures/
md: https://developers.cloudflare.com/reference-architecture/architectures/index.md
---
Diagrams, design patterns and detailed best practices to help you generate solutions with Cloudflare products.
Reference architecture documents and diagrams are designed to provide a foundational knowledge of the Cloudflare platform and products. Building on the information in these documents, you can architect software solutions based on your specific context and needs.
* [Cloudflare Security Architecture](https://developers.cloudflare.com/reference-architecture/architectures/security/)
* [Content Delivery Network (CDN) Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/cdn/)
* [Enhancing security posture with SentinelOne and Cloudflare One](https://developers.cloudflare.com/reference-architecture/architectures/cloudflare-sase-with-sentinelone/)
* [Evolving to a SASE architecture with Cloudflare](https://developers.cloudflare.com/reference-architecture/architectures/sase/)
* [Load Balancing Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/load-balancing/)
* [Magic Transit Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/magic-transit/)
* [Multi-vendor Application Security and Performance Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/multi-vendor/)
* [Reference Architecture using Cloudflare SASE with Microsoft](https://developers.cloudflare.com/reference-architecture/architectures/cloudflare-sase-with-microsoft/)
* [Understanding Email Security Deployments](https://developers.cloudflare.com/reference-architecture/architectures/email-security-deployments/)
---
title: Find by solution · Cloudflare Reference Architecture docs
description: Use the list below for reference architecture documentation that
relates to a solution area you are interested in.
lastUpdated: 2026-01-19T14:05:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/reference-architecture/by-solution/
md: https://developers.cloudflare.com/reference-architecture/by-solution/index.md
---
Use the list below for reference architecture documentation that relates to a solution area you are interested in.
### Cloudflare Connectivity Cloud
Content that pertains to the Cloudflare platform in general.
#### Reference architectures
* [Cloudflare security reference architecture](https://developers.cloudflare.com/reference-architecture/architectures/security/)
* [Multi-vendor Application Security and Performance Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/multi-vendor/)
* [Protect network infrastructure with Magic Transit](https://developers.cloudflare.com/reference-architecture/architectures/magic-transit/)
* [Protect Hybrid Cloud Networks with Cloudflare Magic Transit](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-hybrid-cloud-networks-with-cloudflare-magic-transit/)
#### Reference architecture diagrams
* [Protecting ISP and telecommunications networks from DDoS attacks](https://developers.cloudflare.com/reference-architecture/diagrams/network/protecting-sp-networks-from-ddos/)
#### Design guides
* [Extend Cloudflare's Benefits to SaaS Providers' End-Customers](https://developers.cloudflare.com/reference-architecture/design-guides/extending-cloudflares-benefits-to-saas-providers-end-customers/)
### Zero Trust / SASE
Architecture documentation related to using Cloudflare for Zero Trust, SSE and SASE initiatives for protecting your applications, data, employees and the corporate network.
#### Reference architectures
* [Evolving to a SASE architecture with Cloudflare](https://developers.cloudflare.com/reference-architecture/architectures/sase/)
* [Using Cloudflare SASE with Microsoft](https://developers.cloudflare.com/reference-architecture/architectures/cloudflare-sase-with-microsoft/)
#### Reference architecture diagrams
* [Access to private apps without having to deploy client agents](https://developers.cloudflare.com/reference-architecture/diagrams/sase/sase-clientless-access-private-dns/)
* [Securing data at rest](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-at-rest/)
* [Securing data in transit](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-in-transit/)
* [Securing data in use](https://developers.cloudflare.com/reference-architecture/diagrams/security/securing-data-in-use/)
* [Extend ZTNA with external authorization and serverless computing](https://developers.cloudflare.com/reference-architecture/diagrams/sase/augment-access-with-serverless/)
* [DNS filtering solution for Internet service providers](https://developers.cloudflare.com/reference-architecture/diagrams/sase/gateway-dns-for-isp/)
* [Magic WAN Connector deployment options](https://developers.cloudflare.com/reference-architecture/diagrams/sase/magic-wan-connector-deployment/)
* [Deploy self-hosted VoIP services for hybrid users](https://developers.cloudflare.com/reference-architecture/diagrams/sase/deploying-self-hosted-voip-services-for-hybrid-users/)
#### Design guides
* [Designing ZTNA access policies for Cloudflare Access](https://developers.cloudflare.com/reference-architecture/design-guides/designing-ztna-access-policies/)
* [Building zero trust architecture into your startup](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-startups/)
* [Network-focused migration from VPN concentrators to Zero Trust Network Access](https://developers.cloudflare.com/reference-architecture/design-guides/network-vpn-migration/)
* [Using a zero trust framework to secure SaaS applications](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-saas/)
#### Implementation guides
* [Secure your Internet traffic and SaaS apps](https://developers.cloudflare.com/learning-paths/secure-internet-traffic/concepts/)
* [Replace your VPN](https://developers.cloudflare.com/learning-paths/replace-vpn/concepts/)
* [Deploy clientless access](https://developers.cloudflare.com/learning-paths/clientless-access/concepts/)
* [Secure your email with Email security](https://developers.cloudflare.com/learning-paths/secure-your-email/concepts/)
### Networking
#### Reference architecture diagrams
* [Protect public networks with Cloudflare](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-public-networks-with-cloudflare/)
* [Bring your own IP space to Cloudflare](https://developers.cloudflare.com/reference-architecture/diagrams/network/bring-your-own-ip-space-to-cloudflare/)
* [Protect hybrid cloud networks with Cloudflare Magic Transit](https://developers.cloudflare.com/reference-architecture/diagrams/network/protect-hybrid-cloud-networks-with-cloudflare-magic-transit/)
* [Protect ISP and telecommunications networks from DDoS attacks](https://developers.cloudflare.com/reference-architecture/diagrams/network/protecting-sp-networks-from-ddos/)
### Application Performance
Content related to DNS, caching, load balancing and other Cloudflare services designed to improve application reliability and performance.
#### Reference architectures
* [Content Delivery Network](https://developers.cloudflare.com/reference-architecture/architectures/cdn/)
* [Load Balancing](https://developers.cloudflare.com/reference-architecture/architectures/load-balancing/)
### Application Security
Content related to protecting your applications from threats such as DDoS attack, SQL injection, exploiting application vulnerabilities, scraping API data and more.
#### Reference architecture diagrams
* [Bot management](https://developers.cloudflare.com/reference-architecture/diagrams/bots/bot-management/)
#### Design guides
* [Secure application delivery](https://developers.cloudflare.com/reference-architecture/design-guides/secure-application-delivery/)
#### Implementation guides
* [Use mTLS with Cloudflare protected resources](https://developers.cloudflare.com/learning-paths/mtls/concepts/)
### Developer Platform
Architecture content for our developer platform.
#### Reference architecture diagrams
##### AI
* [Automatic captioning for video uploads](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-video-caption/)
* [Composable AI architecture](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
* [Content-based asset creation](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-asset-creation/)
* [Multi-vendor AI observability and control](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-multivendor-observability-control/)
* [Retrieval Augmented Generation (RAG)](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
* [Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
##### Serverless
* [Optimizing Image Delivery with Cloudflare Image Resizing and R2](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/optimizing-image-delivery-with-cloudflare-image-resizing-and-r2/)
* [A/B-testing using Workers](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/a-b-testing-using-workers/)
* [Fullstack Applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
* [Serverless ETL pipelines](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-etl/)
* [Serverless global APIs](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-global-apis/)
* [Serverless image content management](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/serverless-image-content-management/)
* [Programmable Platforms](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/programmable-platforms/)
##### Storage
* [Egress-free object storage in multi-cloud setups](https://developers.cloudflare.com/reference-architecture/diagrams/storage/egress-free-storage-multi-cloud/)
* [On-demand Object Storage Data Migration](https://developers.cloudflare.com/reference-architecture/diagrams/storage/on-demand-object-storage-migration/)
* [Event notifications for storage](https://developers.cloudflare.com/reference-architecture/diagrams/storage/event-notifications-for-storage/)
* [Storing User Generated Content](https://developers.cloudflare.com/reference-architecture/diagrams/storage/storing-user-generated-content/)
* [Control and data plane architectural pattern for Durable Objects](https://developers.cloudflare.com/reference-architecture/diagrams/storage/durable-object-control-data-plane-pattern/)
---
title: Design Guides · Cloudflare Reference Architecture docs
description: Design guides take your knowledge from a reference architecture and
walk through the conceptual decisions and directions you should take to
implement a specific solution. They do not replace our product documentation,
but instead provide guidance on the decisions you should make given a certain
solution you are trying to deploy.
lastUpdated: 2024-12-12T12:06:35.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/reference-architecture/design-guides/
md: https://developers.cloudflare.com/reference-architecture/design-guides/index.md
---
Diagrams, design patterns and detailed best practices to help you generate solutions with Cloudflare products.
Design guides take your knowledge from a reference architecture and walk through the conceptual decisions and directions you should take to implement a specific solution. They do not replace our product documentation, but instead provide guidance on the decisions you should make given a certain solution you are trying to deploy.
* [Designing ZTNA access policies for Cloudflare Access](https://developers.cloudflare.com/reference-architecture/design-guides/designing-ztna-access-policies/)
* [Extend Cloudflare's benefits to SaaS providers' end-customers](https://developers.cloudflare.com/reference-architecture/design-guides/extending-cloudflares-benefits-to-saas-providers-end-customers/)
* [Leveraging Cloudflare for your SaaS applications](https://developers.cloudflare.com/reference-architecture/design-guides/leveraging-cloudflare-for-your-saas-applications/)
* [Network-focused migration from VPN concentrators to Zero Trust Network Access](https://developers.cloudflare.com/reference-architecture/design-guides/network-vpn-migration/)
* [Securely deliver applications with Cloudflare](https://developers.cloudflare.com/reference-architecture/design-guides/secure-application-delivery/)
* [Securing guest wireless networks](https://developers.cloudflare.com/reference-architecture/design-guides/securing-guest-wireless-networks/)
* [Streamlined WAF deployment across zones and applications](https://developers.cloudflare.com/reference-architecture/design-guides/streamlined-waf-deployment-across-zones-and-applications/)
* [Using a zero trust framework to secure SaaS applications](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-saas/)
* [Building zero trust architecture into your startup](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-startups/)
---
title: Reference Architecture Diagrams · Cloudflare Reference Architecture docs
description: Reference architecture documents and diagrams are designed to
provide a foundational knowledge of the Cloudflare platform and products.
Building on the information in these documents, you can architect software
solutions based on your specific context and needs.
lastUpdated: 2024-12-12T12:06:35.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/reference-architecture/diagrams/
md: https://developers.cloudflare.com/reference-architecture/diagrams/index.md
---
Diagrams, design patterns, and detailed best practices to help you generate solutions with Cloudflare products.
Reference architecture documents and diagrams are designed to provide a foundational knowledge of the Cloudflare platform and products. Building on the information in these documents, you can architect software solutions based on your specific context and needs.
* [Artificial Intelligence (AI)](https://developers.cloudflare.com/reference-architecture/diagrams/ai/)
* [Bots](https://developers.cloudflare.com/reference-architecture/diagrams/bots/)
* [Content Delivery](https://developers.cloudflare.com/reference-architecture/diagrams/content-delivery/)
* [Internet of Things (IoT)](https://developers.cloudflare.com/reference-architecture/diagrams/iot/)
* [Network](https://developers.cloudflare.com/reference-architecture/diagrams/network/)
* [Secure Access Service Edge (SASE)](https://developers.cloudflare.com/reference-architecture/diagrams/sase/)
* [Security](https://developers.cloudflare.com/reference-architecture/diagrams/security/)
* [Serverless](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/)
* [Storage](https://developers.cloudflare.com/reference-architecture/diagrams/storage/)
---
title: How to use · Cloudflare Reference Architecture docs
description: Below are the different types of architecture content and
information is organized from high level reference architectures, to design
guides with best practices and guidelines to implementation guides which
provide detailed steps to deploy a specific solution.
lastUpdated: 2024-09-27T15:14:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/reference-architecture/how-to-use/
md: https://developers.cloudflare.com/reference-architecture/how-to-use/index.md
---
The reference architecture content in our documentation is designed to help you understand how Cloudflare has been designed and built, and how our products and services integrate with your current IT architecture.
Below are the different types of architecture content and information is organized from high level reference architectures, to design guides with best practices and guidelines to implementation guides which provide detailed steps to deploy a specific solution.
## Reference architectures
[Reference architectures](https://developers.cloudflare.com/reference-architecture/architectures/) provide a foundational knowledge of the Cloudflare platform and products while offering a description for how they relate to your existing infrastructure and business challenges. They are high-level, conceptual documents that walk through the concepts of an area of our platform, mapping our network, products and features to the typical architecture of a customer's environment. Detailed diagrams with supporting content explain how our technology works and how it can be integrated with your own infrastructure. The goal of a reference architecture is:
* Present thought leadership for a broad technology area
* Visualize the architecture of Cloudflare and understand how it's been designed
* Explain integration points between Cloudflare and your infrastructure
## Reference architecture diagrams
A [reference architecture diagram](https://developers.cloudflare.com/reference-architecture/diagrams/) focusses on a specific solution or use case where Cloudflare can be used. One or more diagrams are the primary content with supporting introduction and summary. These can focus on sections from a reference architecture that are not fully developed. The goal of this type of document is:
* Visualize the components of a specific solution's architecture
* Provide a quick answer to a specific question around a use case
## Design guides
These [guides](https://developers.cloudflare.com/reference-architecture/design-guides/) are typically aimed at architects, developers, and IT professionals who are tasked with designing and deploying systems that leverage the company's technologies. They typically focus on a specific solution that would be a subset of the greater architecture. For example, if you have read our [SASE Reference Architecture](https://developers.cloudflare.com/reference-architecture/architectures/sase/), but are a startup, you may want to understand the details of using a [SASE approach for a small startup](https://developers.cloudflare.com/reference-architecture/design-guides/zero-trust-for-startups/). These documents are:
* Helping you think through how to design a deployment of Cloudflare as part of an overall solution.
* More prescriptive than reference architectures, sharing best practices and guidelines.
* Focused on a solution design that you are trying to achieve, such as connecting private networks to Cloudflare, or using a web application firewall to secure a public website.
* Not a replacement for product documentation and do not describe specific product configuration or commands to run.
## Implementation guides
Implementation guides provide [step-by-step instructions](https://developers.cloudflare.com/reference-architecture/implementation-guides/) and practical guidance for how to effectively deploy and configure specific solutions or services. Implementation guides are focused on a specific implementation goal. While a design guide provides the overall best practices for designing a solution, an implementation guide details the actual steps to deploy in the context of a specific job-to-be-done. These documents are:
* Focused on a specific implementation outcome, such as connecting a remote office using the Magic WAN Connector.
* Provide information about the exact commands and configuration steps to take.
---
title: Implementation Guides · Cloudflare Reference Architecture docs
description: Implementation guides provide step-by-step instructions and
practical guidance for how to effectively deploy and configure specific
solutions or services. Implementation guides are focused on a specific
implementation goal.
lastUpdated: 2026-01-19T14:05:23.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/reference-architecture/implementation-guides/
md: https://developers.cloudflare.com/reference-architecture/implementation-guides/index.md
---
Implementation guides provide [step-by-step instructions](https://developers.cloudflare.com/reference-architecture/implementation-guides/) and practical guidance for how to effectively deploy and configure specific solutions or services. Implementation guides are focused on a specific implementation goal.
## Zero Trust
* [Secure your Internet traffic and SaaS apps](https://developers.cloudflare.com/learning-paths/secure-internet-traffic/concepts/)
* [Replace your VPN](https://developers.cloudflare.com/learning-paths/replace-vpn/concepts/)
* [Deploy Zero Trust Web Access](https://developers.cloudflare.com/learning-paths/clientless-access/concepts/)
* [Secure your email with Email security](https://developers.cloudflare.com/learning-paths/secure-your-email/concepts/)
## Application Security
* [Use mTLS with Cloudflare protected resources](https://developers.cloudflare.com/learning-paths/mtls/concepts/)
---
title: 404 - Page Not Found · Cloudflare Registrar docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/404/
md: https://developers.cloudflare.com/registrar/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: What is a registrar · Cloudflare Registrar docs
description: Cloudflare Registrar offers several advantages over other
registrars, such as domain name registration renewal without markups fees. You
only pay what is charged by registries and ICANN. Cloudflare Registrar also
offers additional security features, such as free, one-click activation for
Domain Name System Security Extensions (DNSSEC), custom domain protection, and
WHOIS redaction.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/about/
md: https://developers.cloudflare.com/registrar/about/index.md
---
Cloudflare Registrar offers several advantages over other [registrars](https://www.cloudflare.com/learning/dns/glossary/what-is-a-domain-name-registrar/), such as domain name registration renewal [without markups fees](https://www.cloudflare.com/products/registrar/). You only pay what is charged by registries and [ICANN](https://www.icann.org/). Cloudflare Registrar also offers additional security features, such as free, one-click activation for [Domain Name System Security Extensions (DNSSEC)](https://developers.cloudflare.com/registrar/get-started/enable-dnssec/), [custom domain protection](https://developers.cloudflare.com/registrar/custom-domain-protection/), and [WHOIS redaction](https://developers.cloudflare.com/registrar/account-options/whois-redaction/).
You can buy your domain from Cloudflare Registrar or from a third party. Even when you buy it from a third party, you can manage your domain with Cloudflare to benefit from all the features Cloudflare offers.
---
title: Registration options · Cloudflare Registrar docs
lastUpdated: 2025-07-08T19:21:47.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/account-options/
md: https://developers.cloudflare.com/registrar/account-options/index.md
---
* [Domain management](https://developers.cloudflare.com/registrar/account-options/domain-management/)
* [iCloud Custom Email Domains](https://developers.cloudflare.com/registrar/account-options/icloud-domains/)
* [Move a Cloudflare Registrar domain registration between accounts](https://developers.cloudflare.com/registrar/account-options/inter-account-transfer/)
* [Registrant contact updates](https://developers.cloudflare.com/registrar/account-options/domain-contact-updates/)
* [Renew domains](https://developers.cloudflare.com/registrar/account-options/renew-domains/)
* [Transfer domain out from Cloudflare](https://developers.cloudflare.com/registrar/account-options/transfer-out-from-cloudflare/)
* [WHOIS redaction](https://developers.cloudflare.com/registrar/account-options/whois-redaction/)
---
title: API reference · Cloudflare Registrar docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/api-reference/
md: https://developers.cloudflare.com/registrar/api-reference/index.md
---
---
title: Cloudflare Custom Domain Protection · Cloudflare Registrar docs
description: Cloudflare offers Custom Domain Protection to customers with a
Cloudflare Enterprise plan and high-profile domains who need the highest level
of security against domain hijacking.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/custom-domain-protection/
md: https://developers.cloudflare.com/registrar/custom-domain-protection/index.md
---
Cloudflare offers [Custom Domain Protection](https://www.cloudflare.com/products/registrar/custom-domain-protection/) to customers with a Cloudflare Enterprise plan and high-profile domains who need the highest level of security against domain hijacking.
Custom Domain Protection offers additional safeguard features for registered domains, including:
* **Registry lock**: Cloudflare applies Registry Lock, when available, to all domains registered through Custom Domain Protection. Any changes to a domain requires Cloudflare to first unlock the domain at the registry level.
* **Out-of-band authentication**: All changes to domain ownership or nameserver information are verified and executed manually based on an authentication process defined by the customer.
* **No interface**: Custom Domain Protection does not offer an interface, to remove the possibility of domain hijack through a compromised account.
Contact your account team if you are interested in Cloudflare's Custom Domain Protection.
---
title: FAQ · Cloudflare Registrar docs
description: Below you will find answers to our most commonly asked questions.
If you cannot find the answer you are looking for, refer to the community page
to explore more resources.
lastUpdated: 2026-01-22T11:57:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/faq/
md: https://developers.cloudflare.com/registrar/faq/index.md
---
Below you will find answers to our most commonly asked questions. If you cannot find the answer you are looking for, refer to the [community page](https://community.cloudflare.com/) to explore more resources.
* [Domain transfers](#domain-transfers)
* [Domain registrations](#domain-registrations)
* [Domain restoration](#domain-restoration)
* [Domain deletions](#domain-deletions)
* [Domain management](#domain-management)
* [Billing](#billing)
## Domain transfers
### Why did my transfer fail?
Domain transfers sometimes fail. Refer to [Registrar: troubleshoot stalled domain transfers](https://developers.cloudflare.com/registrar/troubleshooting/) for more information on what might have happened and how to solve the issue.
If you cannot solve the issue, open a support ticket or contact your account team.
### Why did my domain's expiration date change after transferring it to Cloudflare?
ICANN requires that any transfer also extends the expiration date of your domain by at least one year — that is one year from your current expiration date, not one year from the date of transfer. For example, if you transfer a domain on October 10, 2021, but it expires on March 10, 2022, your new expiration date will be March 10, 2023.
Whenever a domain is first registered, the registrant purchases control of that domain for some number of years — up to 10 years. For example, a domain registered on October 8, 2020 will have an expiration date of October 8th in some year between 2021 and 2030, depending on the amount of years originally purchased.
Transferring a domain adds time to the current expiration date, unless your domain already has [10 years on the term](#if-i-registered-my-domain-for-10-years-at-another-registrar-will-i-gain-another-year-if-i-transfer-it-to-cloudflare).
### What happens to my nameservers when I transfer my domain to Cloudflare?
Cloudflare Registrar only supports transfers of domains that are active on a Cloudflare [full setup](https://developers.cloudflare.com/dns/zone-setups/full-setup/). Domains on Cloudflare use [nameservers assigned by Cloudflare](https://developers.cloudflare.com/dns/nameservers/nameserver-options/#assignment-method) to the associated account and those nameservers must remain in place for the domain to be Active.
### How can I see the status of my domain transfer?
Once you initiate a domain transfer, your previous registrar has five days to release the domain. In most cases, they will send you an email to confirm you want to transfer. If you actively acknowledge that email (through a link or the registrar's dashboard), they can process it immediately.
To see the progress of your transfer, go to the **Transfer domains** page in the Cloudflare dashboard to see a list of domain transfers that are in progress.
[Go to **Transfer domains**](https://dash.cloudflare.com/?to=/:account/registrar/transfer)
To accelerate the process, be sure to check with your old registrar how you can approve the transfer out.
Once successful, you will receive an email from Cloudflare and be able to manage the domain in the dashboard under **Overview** of that site.
### Why am I not allowed to transfer my domain?
ICANN prohibits domain transfers within 60 days of a change to the WHOIS data or registrar of a domain. If you modified your contact information, transferred registrars, or registered your domain in the last 60 days, Cloudflare will be unable to process your transfer immediately.
You can leave the domain **In Progress** and Cloudflare will wait until after the 60-day window passes to attempt to process the transfer.
Note
This information does not apply to `.uk` domains.
### Why am I not able to start a transfer?
If you have an [unverified email address](https://developers.cloudflare.com/fundamentals/user-profiles/verify-email-address/), you might experience issues when initiating a domain transfer.
### What happens if I enter the wrong auth code?
If you enter an incorrect auth code (also referred to as authentication code or authorization code), return to the **Domain Registration** page or the **Overview** for your site. You can use the available input field to reenter your authentication code.
### If I registered my domain for 10 years at another registrar, will I gain another year if I transfer it to Cloudflare?
No. A domain cannot have more than 10 years on the term. If you registered your domain for 10 years, you will get 10 years upon transferring it to Cloudflare.
***
## Domain registrations
### My domain's registration was not extended by one year after transferring to Cloudflare
When you transfer your domain to Cloudflare, the registry will extend your registration by one year. However, in one specific circumstance your transfer could result in you keeping your original expiration date.
When a domain expires, the registration enters the auto-renew grace period. During that time, you can renew the domain at your registrar to avoid losing it. If your domain expires at your current registrar, you renew it and then transfer to Cloudflare within 45 days, the registry can restrict the addition of an extra year.
Say you have `example.com` registered and it expires on December 10, 2021. You decide to renew it during the auto-renew grace period on December 20, 2021. That renewal extends the registration to December 20, 2022. You then transfer to Cloudflare on December 30, 2021. Since that transfer is within 45 days of the expiration, the registry may not add the year to your registration. When you transfer to Cloudflare or any registrar in this circumstance, your expiration can still remain December 20th, 2022.
If a year is not added to your registration, you have effectively paid twice for the same added year. Per ICANN rules, you are entitled to request a refund at your previous registrar.
### What Happens When a Domain Expires?
In summary, here is what will happen after a domain expires:
* **Day 0**: Expiration Date.
* **Day 1 - 30**: Grace Period (domain resolves normally).
* **Day 31 - 40**: Suspension Period (domains resolves to suspension page).
* **Day 41 - 70**: Redemption Period.
* **Day 71 - 75**: Pending Delete Period.
Cloudflare currently offers a 40-day grace period for most top-level domains (TLDs).
During this period you may renew/extend the domain at any time from within the dashboard but no further auto-renew attempts will be made. For the first 30 days of the grace period, the domain will continue to resolve as normal. On the 30th day after the expiration date, the domain will be suspended and a parked suspension page will be displayed. You may still renew the domain at any time during this suspension period. On the 40th day, the domain will enter the Redemption Period and will no longer resolve to any web page.
The redemption period lasts for 30 days. During this time, it may be possible to restore and renew the domain. A restore fee may apply in addition to the renewal fee. At the end of the 30 day redemption period, the domain will be placed in pending delete status for a period of five days, after which it will be released and made available for re-registration. The domain cannot be restored or renewed during this period.
If the domain is in a state where it can be restored, the Manage Domain page in the Registrar section of dash will display a message indicating the domain is restorable. You will then will be able to initiate the restore process directly from the dashboard.
Cloudflare does not guarantee against domain loss in the sense of fully indemnifying you for business losses if you lose your domain. However, mechanisms are in place to alert you of domain expiration and redemption grace periods should your domain expire. You can also elect to set up your domain registration to renew automatically. For an additional layer of control over your domains, refer to [Domain Protection Service](https://www.cloudflare.com/products/registrar/custom-domain-protection/).
***
## Domain restoration
### Which domains are eligible to be restored?
Domains that are in the Redemption Period and have an EPP status of redemptionPeriod may be restored. For most TLDs this will include domains that are between 40 and 70 days past expiration.
Currently `.uk` domains cannot be restored using this process. We are working on an alternative process for `.uk` domains and will provide additional information at a later date.
### Is there a fee to restore a domain?
Yes, in most cases there is a restore fee.
The amount varies depending on the TLD. The restore fee is separate from the renewal fee. You will be presented with both the restore and renewal fees before confirming they wish to proceed.
### Will the domain be renewed after the restore has completed?
Yes. We will attempt to renew the domain after the restore has been completed. While not common, it is possible for the renewal transaction to fail.
In the event of a failure, we will make several retry attempts. If we are unable to process the renewal after several retries, you will be presented with a message that you should contact support for assistance.
### How long does the restore process take?
The entire process can take a few minutes to complete.
There are multiple steps to the restore process, and each step must be completed in a specific sequence. These steps are performed automatically by the system. The UI will continue to poll for an updated status and will provide feedback as each step completes.
### What happens if the domain renewal fails?
The restore and the renewal are two distinct processes that happen sequentially.
In rare cases the domain may be successfully restored but the renewal fails. We will make several attempts to renew the domain. However, should all the renewals fail the customer may attempt to manually renew the domain or contact support so we may investigate the cause of the failure.
### Can a restore be reversed or refunded?
No. Once a restore has been completed it can not be reversed. It may be possible to delete the domain again but there are no refunds.
Note
Domain names should be released after a period of 75 days, although the exact deletion timeline is ultimately determined by the domain's registry. You should monitor the domain status to ascertain when it will become available for registration once again.
***
## Domain deletions
### Why am I unable to delete my Registrar domain?
A domain can only be deleted if all the following conditions are met:
* The user initiating the action is a Super Admin or Read/Write Administrator.
* The domain is not delete locked at the registry with either `clientDeleteProhibited` or `serverDeleteProhibited`.
* The domain is not already in `pendingDelete`, `redemptionPeriod`, or in `pendingTransfer`.
* The domain has not been administratively locked by Cloudflare. This typically occurs for legal reasons such as a UDRP filing or court order, but may also be the result of an abuse or payment investigation.
* The domain is NOT a .UK domain. .UK domains currently cannot be deleted at the registry.
If any of the above conditions are not met, the domain cannot be deleted.
### Who has permission to delete a domain registration?
Only Super Admins and Administrators with Read/Write access can initiate the deletion of a domain. Note that only Super Admins will receive the email with the delete token.
### Will I receive a refund for my deleted domain registration?
No. Refunds will not be issued for costs incurred by a domain registration.
### How do I get the domain deletion token?
The delete token is only sent to the Super Admins of the account. If the user requesting the deletion is not a Super Admin they will need to obtain the delete token from one of the Super Admins of the account.
### How long is the domain deletion token valid for?
The delete token is valid for 30 minutes. After the 30 minutes the code will expire and the user must restart the process.
### Will the domain be deleted immediately from my account?
If the domain is within 5 days of the initial registration, the domain will be immediately released by the registry and made available for re-registration. In this scenario the domain will be immediately removed from the registrar section of the account. You may need to refresh the page to force an update of the data.
If the domain is more than 5 days old, it will enter the redemption period and will remain in account until the redemption period expires and the registry releases the domain.
***
## Domain management
### How can I update my telephone number, email, name or address?
You can update both your default contact information and any individual Registrant, Administrator, Technical or Billing contact for your domain registrations by following [Registrant contact updates](https://developers.cloudflare.com/registrar/account-options/domain-contact-updates/). Details that may be updated include name, email, address, organization and telephone number.
### Can I change my nameservers?
No, you must use Cloudflare nameservers for domains on Cloudflare Registrar.
If you only need a subdomain to be on a different service provider, you can [delegate a subdomain](https://developers.cloudflare.com/dns/manage-dns-records/how-to/subdomains-outside-cloudflare/). Also, if you are on the Business or Enterprise plans, you have the option to set up [custom nameservers](https://developers.cloudflare.com/dns/nameservers/custom-nameservers/), which means you will be using Cloudflare nameservers but with custom-branded nameserver names.
If you still need to use different nameservers, you will have to [move your domain to another Registrar](https://developers.cloudflare.com/registrar/account-options/transfer-out-from-cloudflare/).
***
## Billing
### How much does Cloudflare Registrar cost?
Refer to [What is Cloudflare Registrar](https://www.cloudflare.com/learning/dns/what-is-cloudflare-registrar/) for more information on pricing.
### When will I be billed?
You will be billed when you input your authorization code and initiate the transfer of your domain to Cloudflare. Currently, Cloudflare Registrar only uses the primary payment method for any associated transaction. Make sure to copy and paste the code to avoid mistakes. The transfer will not initiate if the code is incorrect.
### Is there a fee to transfer a .UK domain?
No, there is no fee to transfer a `.uk` domain. Also, an additional year is NOT added during the transfer process. However, if the domain is nearing the expiration date and is set to auto-renew, it may be automatically renewed shortly after the completion of the transfer.
---
title: Get started · Cloudflare Registrar docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/get-started/
md: https://developers.cloudflare.com/registrar/get-started/index.md
---
* [Enable DNSSEC](https://developers.cloudflare.com/registrar/get-started/enable-dnssec/)
* [Register a new domain](https://developers.cloudflare.com/registrar/get-started/register-domain/)
* [Transfer your domain to Cloudflare](https://developers.cloudflare.com/registrar/get-started/transfer-domain-to-cloudflare/)
---
title: Top Level Domains supported · Cloudflare Registrar docs
description: Cloudflare supports over 400 top-level domains (TLDs) and is always
evaluating adding new TLDs. We have no specific timeframes for TLDs not yet
listed. You can find the full list of supported and coming soon TLDs on the
TLD policies page.
lastUpdated: 2025-09-11T16:12:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/top-level-domains/
md: https://developers.cloudflare.com/registrar/top-level-domains/index.md
---
Cloudflare supports over 400 [top-level domains (TLDs)](https://www.cloudflare.com/learning/dns/top-level-domain/) and is always evaluating adding new TLDs. We have no specific timeframes for TLDs not yet listed. You can find the full list of supported and coming soon TLDs on the [TLD policies page](https://www.cloudflare.com/tld-policies/).
Note
If you want to register a `.us` domain refer to [Additional requirements for .US domains](https://developers.cloudflare.com/registrar/top-level-domains/us-domains/).
## Domain availability
During your [TLD registration process](https://developers.cloudflare.com/registrar/get-started/register-domain/#how-to-register-a-new-domain), Cloudflare Registrar will inform you if the TLD you are looking for is available to register. If it does not appear in your search list, this means that TLD is not available for registration.
Possible causes for the domain not being available include:
* Someone else owns that domain.
* It is an Internationalized Domain Name (IDN) which Cloudflare Registrar does not support. These domains include international characters (such as `á`, `ü`, among others).
## Transfer a domain
When transferring a domain to Cloudflare Registrar, refer to [Restrictions](https://developers.cloudflare.com/registrar/get-started/transfer-domain-to-cloudflare/#restrictions) for a full list of aspects to consider before starting the transfer.
---
title: Troubleshoot failed domain transfers · Cloudflare Registrar docs
description: After you start the transfer process to Cloudflare Registrar, your
previous registrar has five days to release the domain after a successful
transfer request. If your transfer has not been completed within that time
frame, something has likely gone wrong.
lastUpdated: 2025-09-15T15:28:43.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/registrar/troubleshooting/
md: https://developers.cloudflare.com/registrar/troubleshooting/index.md
---
After you start the transfer process to Cloudflare Registrar, your previous registrar has five days to release the domain after a successful transfer request. If your transfer has not been completed within that time frame, something has likely gone wrong.
Most issues with a stalled transfer can be solved by checking the following details and [restarting the transfer](#restart-your-transfer).
## Registrar lock reapplied
You have reapplied the registrar lock at your current registrar since requesting the transfer. You will need to remove it again to restart the transfer process.
## Transfer rejected
Your transfer has been rejected by your previous registrar. There are several reasons for this to happen:
* You actively rejected the transfer request in the email you received from your registrar or on your registrar's interface.
* Your registrar determined the domain is not eligible for transfer.
* Some registrars allow customers to enable a setting to reject all transfer requests.
* In some instances, registrars may reject the transfer if they suspect malicious behavior.
You will need to restart the transfer and approve the request or contact your current registrar to solve this issue.
## Auth code invalid
Your auth code (also referred to as authentication code and authorization code) has since changed or been deprecated, and Cloudflare cannot complete the transfer. Confirm the code with your current registrar again. To avoid mistakes, copy and paste the auth code provided by your current registrar.
## WHOIS Guard / privacy protection
Some registrars may prohibit transfer requests if you have WHOIS privacy services enabled. You need to first disable those services at your current registrar before you can proceed with the transfer process.
## Restart your transfer
Note
This solution does not apply to `.uk` domains.
1. In the Cloudflare dashboard, go to the **Manage Domains** page.
[Go to **Manage domains**](https://dash.cloudflare.com/?to=/:account/registrar/domains)
2. Find the correct domain and select **Manage**.
3. Select **Cancel Transfer and Retry**. After you initiate the retry, you must re-enter your auth code and confirm your WHOIS information.
---
title: 404 - Page Not Found · Cloudflare Rules docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/404/
md: https://developers.cloudflare.com/rules/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
---
title: Rules changelog · Cloudflare Rules docs
description: You can now control how Cloudflare buffers HTTP request and
response bodies using two new settings in Configuration Rules.
lastUpdated: 2025-11-11T11:19:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/changelog/
md: https://developers.cloudflare.com/rules/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/rules.xml)
## 2026-01-27
**Control request and response body buffering in Configuration Rules**
You can now control how Cloudflare buffers HTTP request and response bodies using two new settings in [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/).
#### Request body buffering
Controls how Cloudflare buffers HTTP request bodies before forwarding them to your origin server:
| Mode | Behavior |
| - | - |
| **Standard** (default) | Cloudflare can inspect a prefix of the request body for enabled functionality such as WAF and Bot Management. |
| **Full** | Buffers the entire request body before sending to origin. |
| **None** | No buffering — the request body streams directly to origin without inspection. |
#### Response body buffering
Controls how Cloudflare buffers HTTP response bodies before forwarding them to the client:
| Mode | Behavior |
| - | - |
| **Standard** (default) | Cloudflare can inspect a prefix of the response body for enabled functionality. |
| **None** | No buffering — the response body streams directly to the client without inspection. |
Warning
Setting body buffering to **None** may break security functionality that requires body inspection, including the Web Application Firewall (WAF) and Bot Management. Ensure that any paths where you disable buffering do not require security inspection.
Availability
These settings only take effect on zones running Cloudflare's [latest CDN proxy](https://blog.cloudflare.com/20-percent-internet-upgrade/). Enterprise customers can contact their account team to enable the latest proxy on their zones.
#### API example
```json
{
"action": "set_config",
"action_parameters": {
"request_body_buffering": "standard",
"response_body_buffering": "none"
}
}
```
For more information, refer to [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/).
## 2026-01-22
**New cryptographic functions — encode\_base64() and sha256()**
Cloudflare Rulesets now includes `encode_base64()` and `sha256()` functions, enabling you to generate signed request headers directly in rule expressions. These functions support common patterns like constructing a canonical string from request attributes, computing a SHA256 digest, and Base64-encoding the result.
***
#### New functions
| Function | Description | Availability |
| - | - | - |
| `encode_base64(input, flags)` | Encodes a string to Base64 format. Optional `flags` parameter: `u` for URL-safe encoding, `p` for padding (adds `=` characters to make the output length a multiple of 4, as required by some systems). By default, output is standard Base64 without padding. | All plans (in header transform rules) |
| `sha256(input)` | Computes a SHA256 hash of the input string. | Requires enablement |
Note
The `sha256()` function is available as an Enterprise add-on and requires a specific entitlement. Contact your account team to enable it.
***
#### Examples
**Encode a string to Base64 format:**
```txt
encode_base64("hello world")
```
Returns: `aGVsbG8gd29ybGQ`
**Encode a string to Base64 format with padding:**
```txt
encode_base64("hello world", "p")
```
Returns: `aGVsbG8gd29ybGQ=`
**Perform a URL-safe Base64 encoding of a string:**
```txt
encode_base64("hello world", "u")
```
Returns: `aGVsbG8gd29ybGQ`
**Compute the SHA256 hash of a secret token:**
```txt
sha256("my-token")
```
Returns a hash that your origin can validate to authenticate requests.
**Compute the SHA256 hash of a string and encode the result to Base64 format:**
```txt
encode_base64(sha256("my-token"))
```
Combines hashing and encoding for systems that expect Base64-encoded signatures.
For more information, refer to the [Functions reference](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/).
## 2026-01-20
**New functions for array and map operations**
#### New functions for array and map operations
Cloudflare Rulesets now include new functions that enable advanced expression logic for evaluating arrays and maps. These functions allow you to build rules that match against lists of values in request or response headers, enabling use cases like country-based blocking using custom headers.
***
#### New functions
| Function | Description |
| - | - |
| `split(source, delimiter)` | Splits a string into an array of strings using the specified delimiter. |
| `join(array, delimiter)` | Joins an array of strings into a single string using the specified delimiter. |
| `has_key(map, key)` | Returns `true` if the specified key exists in the map. |
| `has_value(map, value)` | Returns `true` if the specified value exists in the map. |
***
#### Example use cases
**Check if a country code exists in a header list:**
```txt
has_value(split(http.response.headers["x-allow-country"][0], ","), ip.src.country)
```
**Check if a specific header key exists:**
```txt
has_key(http.request.headers, "x-custom-header")
```
**Join array values for logging or comparison:**
```txt
join(http.request.headers.names, ", ")
```
For more information, refer to the [Functions reference](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/).
## 2026-01-12
**Metro code field now available in Rules**
The `ip.src.metro_code` field in the Ruleset Engine is now populated with DMA (Designated Market Area) data.
You can use this field to build rules that target traffic based on geographic market areas, enabling more granular location-based policies for your applications.
#### Field details
| Field | Type | Description |
| - | - | - |
| `ip.src.metro_code` | String \| null | The metro code (DMA) of the incoming request's IP address. Returns the designated market area code for the client's location. |
Example filter expression:
```plaintext
ip.src.metro_code eq "501"
```
For more information, refer to the [Fields reference](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/ip.src.metro_code/).
## 2025-10-30
**New TCP-based fields available in Rulesets**
#### Build rules based on TCP transport and latency
Cloudflare now provides two new request fields in the Ruleset engine that let you make decisions based on whether a request used TCP and the measured TCP round-trip time between the client and Cloudflare. These fields help you understand protocol usage across your traffic and build policies that respond to network performance. For example, you can distinguish TCP from QUIC traffic or route high latency requests to alternative origins when needed.
***
#### New fields
| Field | Type | Description |
| - | - | - |
| `cf.edge.client_tcp` | Boolean | Indicates whether the request used TCP. A value of true means the client connected using TCP instead of QUIC. |
| `cf.timings.client_tcp_rtt_msec` | Number | Reports the smoothed TCP round-trip time between the client and Cloudflare in milliseconds. For example, a value of 20 indicates roughly twenty milliseconds of RTT. |
Example filter expression:
```plaintext
cf.edge.client_tcp && cf.timings.client_tcp_rtt_msec < 100
```
More information can be found in the Rules language [fields reference](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/).
## 2025-06-09
**More flexible fallback handling — Custom Errors now support fetching assets returned with 4xx or 5xx status codes**
[Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) can now fetch and store [assets](https://developers.cloudflare.com/rules/custom-errors/create-rules/#create-a-custom-error-asset-dashboard) and [error pages](https://developers.cloudflare.com/rules/custom-errors/#error-pages) from your origin even if they are served with a 4xx or 5xx HTTP status code — previously, only 200 OK responses were allowed.
**What’s new:**
* You can now upload error pages and error assets that return error status codes (for example, 403, 500, 502, 503, 504) when fetched.
* These assets are stored and minified at the edge, so they can be reused across multiple Custom Error rules without triggering requests to the origin.
This is especially useful for retrieving error content or downtime banners from your backend when you can’t override the origin status code.
Learn more in the [Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) documentation.
## 2025-06-09
**Match Workers subrequests by upstream zone — cf.worker.upstream\_zone now supported in Transform Rules**
You can now use the [`cf.worker.upstream_zone`](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/cf.worker.upstream_zone/) field in [Transform Rules](https://developers.cloudflare.com/rules/transform/) to control rule execution based on whether a request originates from [Workers](https://developers.cloudflare.com/workers/), including subrequests issued by Workers in other zones.

**What's new:**
* `cf.worker.upstream_zone` is now supported in Transform Rules expressions.
* Skip or apply logic conditionally when handling [Workers subrequests](https://developers.cloudflare.com/workers/platform/limits/#subrequests).
For example, to add a header when the subrequest comes from another zone:
Text in **Expression Editor** (replace `myappexample.com` with your domain):
```txt
(cf.worker.upstream_zone != "" and cf.worker.upstream_zone != "myappexample.com")
```
Selected operation under **Modify request header**: *Set static*
**Header name**: `X-External-Workers-Subrequest`
**Value**: `1`
This gives you more granular control in how you handle incoming requests for your zone.
Learn more in the [Transform Rules](https://developers.cloudflare.com/rules/transform/) documentation and [Rules language fields](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/) reference.
## 2025-05-30
**Fine-tune image optimization — WebP now supported in Configuration Rules**
You can now enable [Polish](https://developers.cloudflare.com/images/polish/activate-polish/) with the `webp` format directly in [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/), allowing you to optimize image delivery for specific routes, user agents, or A/B tests — without applying changes zone-wide.
**What’s new:**
* [WebP](https://developers.cloudflare.com/images/polish/compression/#webp) is now a supported [value](https://developers.cloudflare.com/rules/configuration-rules/settings/#polish) in the **Polish** setting for Configuration Rules.

This gives you more precise control over how images are compressed and delivered, whether you're targeting modern browsers, running experiments, or tailoring performance by geography or device type.
Learn more in the [Polish](https://developers.cloudflare.com/images/polish/) and [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/) documentation.
## 2025-05-09
**More ways to match — Snippets now support Custom Lists, Bot Score, and WAF Attack Score**
You can now use IP, Autonomous System (AS), and Hostname [custom lists](https://developers.cloudflare.com/waf/tools/lists/custom-lists/) to route traffic to [Snippets](https://developers.cloudflare.com/rules/snippets/) and [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/), giving you greater precision and control over how you match and process requests at the edge.
In Snippets, you can now also match on [Bot Score](https://developers.cloudflare.com/bots/concepts/bot-score/) and [WAF Attack Score](https://developers.cloudflare.com/waf/detections/attack-score/), unlocking smarter edge logic for everything from request filtering and mitigation to [tarpitting](https://developers.cloudflare.com/rules/snippets/examples/slow-suspicious-requests/) and logging.
**What’s new:**
* [Custom lists](https://developers.cloudflare.com/waf/tools/lists/custom-lists/) matching – Snippets and Cloud Connector now support user-created IP, AS, and Hostname lists via dashboard or [Lists API](https://developers.cloudflare.com/api/resources/rules/subresources/lists/methods/list/). Great for shared logic across zones.
* [Bot Score](https://developers.cloudflare.com/bots/concepts/bot-score/) and [WAF Attack Score](https://developers.cloudflare.com/waf/detections/attack-score/) – Use Cloudflare’s intelligent traffic signals to detect bots or attacks and take advanced, tailored actions with just a few lines of code.

These enhancements unlock new possibilities for building smarter traffic workflows with minimal code and maximum efficiency.
Learn more in the [Snippets](https://developers.cloudflare.com/rules/snippets/) and [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/) documentation.
## 2025-04-24
**Custom Errors are now Generally Available**
[Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) are now generally available for all paid plans — bringing a unified and powerful experience for customizing error responses at both the zone and account levels.
You can now manage **Custom Error Rules**, **Custom Error Assets**, and redesigned **Error Pages** directly from the Cloudflare dashboard. These features let you deliver tailored messaging when errors occur, helping you maintain brand consistency and improve user experience — whether it’s a 404 from your origin or a security challenge from Cloudflare.
What's new:
* **Custom Errors are now GA** – Available on all paid plans and ready for production traffic.
* **UI for Custom Error Rules and Assets** – Manage your zone-level rules from the Rules > Overview and your zone-level assets from the Rules > Settings tabs.
* **Define inline content or upload assets** – Create custom responses directly in the rule builder, upload new or reuse previously stored assets.
* **Refreshed UI and new name for Error Pages** – Formerly known as “Custom Pages,” Error Pages now offer a cleaner, more intuitive experience for both zone and account-level configurations.
* **Powered by Ruleset Engine** – Custom Error Rules support [conditional logic](https://developers.cloudflare.com/ruleset-engine/rules-language/) and override Error Pages for 500 and 1000 class errors, as well as errors originating from your origin or [other Cloudflare products](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/). You can also configure [Response Header Transform Rules](https://developers.cloudflare.com/rules/transform/response-header-modification/) to add, change, or remove HTTP headers from responses returned by Custom Error Rules.

Learn more in the [Custom Errors documentation](https://developers.cloudflare.com/rules/custom-errors/).
## 2025-04-09
**Cloudflare Snippets are now Generally Available**\

[Cloudflare Snippets](https://developers.cloudflare.com/rules/snippets/) are now generally available at no extra cost across all paid plans — giving you a fast, flexible way to programmatically control HTTP traffic using lightweight JavaScript.
You can now use Snippets to modify HTTP requests and responses with confidence, reliability, and scale. Snippets are production-ready and deeply integrated with Cloudflare Rules, making them ideal for everything from quick dynamic header rewrites to advanced routing logic.
What's new:
* **Snippets are now GA** – Available at no extra cost on all Pro, Business, and Enterprise plans.
* **Ready for production** – Snippets deliver a production-grade experience built for scale.
* **Part of the Cloudflare Rules platform** – Snippets inherit request modifications from other Cloudflare products and support sequential execution, allowing you to run multiple Snippets on the same request and apply custom modifications step by step.
* **Trace integration** – Use [Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/) to see which Snippets were triggered on a request — helping you understand traffic flow and debug more effectively.

Learn more in the [launch blog post](https://blog.cloudflare.com/snippets/).
## 2025-02-12
**Increased Cloudflare Rules limits**
We have upgraded and streamlined [Cloudflare Rules](https://developers.cloudflare.com/rules/) limits across all plans, simplifying rule management and improving scalability for everyone.
**New limits by product:**
* [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/)
* Free: **20** → **10,000** URL redirects across lists
* Pro: **500** → **25,000** URL redirects across lists
* Business: **500** → **50,000** URL redirects across lists
* Enterprise: **10,000** → **1,000,000** URL redirects across lists
* [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/)
* Free: **5** → **10** connectors
* Enterprise: **125** → **300** connectors
* [Custom Errors](https://developers.cloudflare.com/rules/custom-errors/)
* Pro: **5** → **25** error assets and rules
* Business: **20** → **50** error assets and rules
* Enterprise: **50** → **300** error assets and rules
* [Snippets](https://developers.cloudflare.com/rules/snippets/)
* Pro: **10** → **25** code snippets and rules
* Business: **25** → **50** code snippets and rules
* Enterprise: **50** → **300** code snippets and rules
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/), [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/), [Compression Rules](https://developers.cloudflare.com/rules/compression-rules/), [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/), [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/), and [Transform Rules](https://developers.cloudflare.com/rules/transform/)
* Enterprise: **125** → **300** rules
Gradual rollout
Limits are updated gradually. Some customers may still see previous limits until the rollout is fully completed in the first half of 2025.
## 2025-02-11
**Custom Errors (beta): Stored Assets & Account-level Rules**
We're introducing [Custom Errors](https://developers.cloudflare.com/rules/custom-errors/) (beta), which builds on our existing Custom Error Responses feature with new asset storage capabilities.
This update allows you to store externally hosted error pages on Cloudflare and reference them in custom error rules, eliminating the need to supply inline content.
This brings the following new capabilities:
* **Custom error assets** – Fetch and store external error pages at the edge for use in error responses.
* **Account-Level custom errors** – Define error handling rules and assets at the account level for consistency across multiple zones. Zone-level rules take precedence over account-level ones, and assets are not shared between levels.
You can use Cloudflare API to upload your existing assets for use with Custom Errors:
```bash
curl "https://api.cloudflare.com/client/v4/zones/{zone_id}/custom_pages/assets" \
--header "Authorization: Bearer " \
--header 'Content-Type: application/json' \
--data '{
"name": "maintenance",
"description": "Maintenance template page",
"url": "https://example.com/"
}'
```
You can then reference the stored asset in a Custom Error rule:
```bash
curl --request PUT \
"https://api.cloudflare.com/client/v4/zones/{zone_id}/rulesets/phases/http_custom_errors/entrypoint" \
--header "Authorization: Bearer " \
--header 'Content-Type: application/json' \
--data '{
"rules": [
{
"action": "serve_error",
"action_parameters": {
"asset_name": "maintenance",
"content_type": "text/html",
"status_code": 503
},
"enabled": true,
"expression": "http.request.uri.path contains \"error\""
}
]
}'
```
## 2025-01-29
**New Snippets Code Editor**
The new [Snippets](https://developers.cloudflare.com/rules/snippets/) code editor lets you edit Snippet code and rule in one place, making it easier to test and deploy changes without switching between pages.

What’s new:
* **Single-page editing for code and rule** – No need to jump between screens.
* **Auto-complete & syntax highlighting** – Get suggestions and avoid mistakes.
* **Code formatting & refactoring** – Write cleaner, more readable code.
Try it now in [Rules > Snippets](https://dash.cloudflare.com/?to=/:account/:zone/rules/snippets).
## 2025-01-09
**New Rules Overview Interface**
**Rules Overview** gives you a single page to manage all your [Cloudflare Rules](https://developers.cloudflare.com/rules/).

What you can do:
* **See all your rules in one place** – No more clicking around.
* **Find rules faster** – Search by name.
* **Understand execution order** – See how rules run in sequence.
* **Debug easily** – Use [Trace](https://developers.cloudflare.com/rules/trace-request/) without switching tabs.
Check it out in [Rules > Overview](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview).
## 2024-12-11
**Terraform Support for Snippets**
Now, you can manage [Cloudflare Snippets](https://developers.cloudflare.com/rules/snippets/) with [Terraform](https://developers.cloudflare.com/terraform/). Use infrastructure-as-code to deploy and update Snippet code and rules without manual changes in the dashboard.
Example Terraform configuration:
```tf
resource "cloudflare_snippet" "my_snippet" {
zone_id = ""
name = "my_test_snippet_1"
main_module = "file1.js"
files {
name = "file1.js"
content = file("file1.js")
}
}
resource "cloudflare_snippet_rules" "cookie_snippet_rule" {
zone_id = ""
rules {
enabled = true
expression = "http.cookie eq \"a=b\""
description = "Trigger snippet on specific cookie"
snippet_name = "my_test_snippet_1"
}
depends_on = [cloudflare_snippet.my_snippet]
}
```
Learn more in the [Configure Snippets using Terraform](https://developers.cloudflare.com/rules/snippets/create-terraform/) documentation.
## 2024-11-22
**Cloud Connector Now Supports R2**
Now, you can use [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/) to route traffic to your [R2 buckets](https://developers.cloudflare.com/r2/) based on URLs, headers, geolocation, and more.
Example setup:
```bash
curl --request PUT \
"https://api.cloudflare.com/client/v4/zones/{zone_id}/cloud_connector/rules" \
--header "Authorization: Bearer " \
--header "Content-Type: application/json" \
--data '[
{
"expression": "http.request.uri.path wildcard \"/images/*\"",
"provider": "cloudflare_r2",
"description": "Connect to R2 bucket containing images",
"parameters": {
"host": "mybucketcustomdomain.example.com"
}
}
]'
```
Get started using [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/) documentation.
## 2024-10-23
**Simplified UI for URL Rewrites**
It’s now easy to create **wildcard-based [URL Rewrites](https://developers.cloudflare.com/rules/transform/url-rewrite/)**. No need for complex functions—just define your patterns and go.

What’s improved:
* **Full wildcard support** – Create rewrite patterns using intuitive interface.
* **Simplified rule creation** – No need for complex functions.
Try it via [creating a Rewrite URL rule in the dashboard](https://developers.cloudflare.com/rules/transform/url-rewrite/create-dashboard/#wildcard-pattern-parameters).
## 2024-09-20
**Automatic DNS Validation for Cloudflare Rules**
The Cloudflare dashboard now automatically validates [DNS records](https://developers.cloudflare.com/dns/proxy-status/) and [Cloudflare for SaaS custom hostnames](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/domain-support/) for rules targeting specific hostnames or URLs. To prevent misconfigured rules and ensure smoother deployments, you will get proactive warnings for missing or misconfigured DNS records and custom hostnames.
## 2024-09-17
**Compression Rules available to all plans with Zstandard support**
[Compression Rules](https://developers.cloudflare.com/rules/compression-rules/) now support Zstandard compression and are available in all Cloudflare plans. Users in the Free plan will gradually get access throughout 2024.
## 2024-09-13
**Snippets now available in beta**
[Cloudflare Snippets](https://developers.cloudflare.com/rules/snippets/) have transitioned from alpha to beta.
## 2024-09-10
**wildcard\_replace() function now supported in URL rewrites**
You can now use the [`wildcard_replace()`](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/#wildcard_replace) function in rewrite expressions of [URL rewrites](https://developers.cloudflare.com/rules/transform/url-rewrite/).
## 2024-09-05
**New Rules Templates for one-click rule creation**
The new **Rules** > **Templates** page in the Cloudflare dashboard allows you to create common rules with a single click, featuring dozens of pre-built templates. You can also access these templates directly from each product's rule builder. Also, explore the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in the developer docs for real-world use cases and inspiration.
## 2024-08-22
**Simplified UI for Single Redirects with wildcard support**
The simplified UI for [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/) is now available to all users, making URL redirects easier and more intuitive. This update builds on the recent [wildcard support](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/#wildcard_replace) in Ruleset Engine products. Access the new UI under **Rules > Redirect Rules**. Learn more about wildcard support and our open-source Rust crate in the [blog post](https://blog.cloudflare.com/wildcard-rules).
## 2024-08-20
**Cloud Connector now available to all customers**
Cloud Connector (beta) is now available to all customers. For setup details, refer to the [documentation](https://developers.cloudflare.com/rules/cloud-connector/), explore [examples](https://developers.cloudflare.com/rules/cloud-connector/examples/), and check out the [blog post](https://blog.cloudflare.com/cloud-connector).
## 2024-08-16
**Cloud Connector now available to all free customers**
Cloud Connector (beta) is now available to all free and a subset of paid customers. This rollout will be [gradually extended](https://developers.cloudflare.com/rules/cloud-connector/#availability) to all Cloudflare users, simplifying multi-cloud management and enhancing integration with Cloudflare's Connectivity Cloud. For more information, refer to the [blog post](https://blog.cloudflare.com/cloud-connector).
## 2024-08-12
**Cloudflare Snippets limits have been upgraded**
Cloudflare Snippets (alpha) now allow multiple subrequests depending on your plan. For more information, refer to the [Availability](https://developers.cloudflare.com/rules/snippets/#availability).
## 2024-07-31
**Wildcard support added to Ruleset Engine products**
Wildcards are now supported across our Ruleset Engine-based products, including Single Redirects, Cache Rules, Transform Rules, WAF, Waiting Room, and more:
* You can now use the `wildcard` and `strict wildcard` operators with any string field in the Ruleset Engine, such as full URI, host, headers, cookies, user-agent, and country. For more details, refer to [Operators](https://developers.cloudflare.com/ruleset-engine/rules-language/operators/) and [Wildcard matching](https://developers.cloudflare.com/ruleset-engine/rules-language/operators/#wildcard-matching).
* In [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/), the `wildcard_replace()` function allows you to use segments matched by the `wildcard` and `strict wildcard` operators in redirect URL targets. For more information, refer to [Functions](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/#wildcard_replace).
## 2024-07-01
**Cloudflare Snippets now available to all paid customers**
Cloudflare Snippets (alpha) are now available to all paid customers.
## 2024-06-03
**Cloudflare Snippets now available to all Enterprise customers**
Cloudflare Snippets (alpha) are now available to all Enterprise customers. Customers in other paid plans will gradually get access throughout 2024.
## 2024-05-14
**Page Rules migration**
The [Page Rules migration guide](https://developers.cloudflare.com/rules/reference/page-rules-migration/) is now available for users interested in transitioning to modern Rules features instead of Page Rules. Explore the guide for detailed instructions on migrating your configurations.
## 2024-05-13
**New Configuration Rules setting for Web Analytics (RUM)**
You can now turn off Cloudflare Web Analytics, also known as Real User Monitoring (RUM), for specific requests using a configuration rule.
## 2024-04-29
**New Configuration Rules setting for Cloudflare Fonts**
You can now turn on or off Cloudflare Fonts for specific requests using a configuration rule.
## 2024-03-22
**New TLS fields in rule expressions**
Customers can now use new fields `cf.tls_client_hello_length` (the length of the client hello message sent in a TLS handshake), `cf.tls_client_random` (the value of the 32-byte random value provided by the client in a TLS handshake), and `cf.tls_client_extensions_sha1` (the SHA-1 fingerprint of TLS client extensions) in various products built on Ruleset Engine.
## 2024-03-20
**Origin Rules now allow port numbers in Host Header Override**
Customers can now use arbitrary port numbers in Host Header Override in Origin Rules. Previously, only hostname was allowed as a value (for example, `example.com`). Now, you can set the value to `hostname:port` (for example, `example.com:1234`) as well.
---
title: Cloud Connector · Cloudflare Rules docs
description: "Cloud Connector (Beta) allows you to route matching incoming
traffic from your website to a public cloud provider that you define:
Cloudflare R2 object storage or an external provider such as AWS, Google
Cloud, and Azure. With Cloud Connector you can make Cloudflare the control
center for your web traffic, including traffic served from public cloud
providers, without having to configure additional rules."
lastUpdated: 2026-02-03T18:17:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/cloud-connector/
md: https://developers.cloudflare.com/rules/cloud-connector/index.md
---
Cloud Connector (Beta) allows you to route matching incoming traffic from your website to a public cloud provider that you define: [Cloudflare R2](https://developers.cloudflare.com/r2/) object storage or an external provider such as AWS, Google Cloud, and Azure. With Cloud Connector you can make Cloudflare the control center for your web traffic, including traffic served from public cloud providers, without having to configure additional rules.
Note
Cloud Connector requires that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
## How it works
First, you configure a Cloud Connector rule that specifies:
* The cloud provider and a supported cloud service that will accept traffic.
* The traffic that will be routed to that cloud service.
Then, Cloudflare will create the [necessary configurations](#applied-configurations) so that the content is accessible for requests matching your Cloud Connector rule. Your object storage bucket should be public for Cloud Connector to work.
Cloud Connector rules are evaluated last in the request evaluation workflow. When there is a rule match and you have other rules changing the same settings, the Cloud Connector rule will win over other rules.
## Applied configurations
Cloud Connector will perform the following configurations automatically, depending on the cloud provider:
* Modify the `Host` header.
* Adjust SSL/TLS for bucket-related traffic ([AWS S3 website endpoints](https://developers.cloudflare.com/rules/cloud-connector/providers/#ssl-connections-to-aws-s3-endpoints) only).
Additional configurations you may need
Cloud Connector will not apply any of the following configurations:
* **Cache content served from storage bucket**: To define custom cache behavior — like when to cache returned objects and for [how long](https://developers.cloudflare.com/cache/how-to/cache-rules/settings/#edge-ttl) — you will need to create a [cache rule](https://developers.cloudflare.com/cache/how-to/cache-rules/). For an example rule configuration, refer to [Cache Level (Cache Everything)](https://developers.cloudflare.com/cache/how-to/cache-rules/examples/cache-everything/).
* **Create URL rewrites**: To adjust the URL structure from what your website visitors use to obtain a resource and the folder structure being used in the storage bucket, you will need to create a [URL rewrite](https://developers.cloudflare.com/rules/transform/url-rewrite/). For example, you could create a URL rewrite to remove the `/files` prefix from URI paths before routing the request to your object storage bucket. For an example configuration, refer to [Rewrite path for object storage bucket](https://developers.cloudflare.com/rules/transform/examples/rewrite-path-object-storage/).
## Availability
Cloud Connector is available in beta to all customers. The maximum number of rules depends on your Cloudflare plan:
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 10 | 25 | 50 | 300 |
---
title: Compression Rules · Cloudflare Rules docs
description: Use Compression Rules to customize the compression applied to
responses from Cloudflare's global network to your website visitors, based on
the file extension and content type. Compression Rules are powered by the
Ruleset Engine.
lastUpdated: 2025-10-06T10:46:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/compression-rules/
md: https://developers.cloudflare.com/rules/compression-rules/index.md
---
Use Compression Rules to customize the compression applied to responses from Cloudflare's global network to your website visitors, based on the file extension and content type. Compression Rules are powered by the [Ruleset Engine](https://developers.cloudflare.com/ruleset-engine/).
Cloudflare [compresses some responses by default](https://developers.cloudflare.com/speed/optimization/content/compression/), based on the content type. With Compression Rules, you can customize the default behavior, which includes defining preferred compression algorithms for particular file types.
When there is a match for a compression rule configured with several compression algorithms, the selected algorithm is the first one supported by the website visitor, according to the received `accept-encoding` HTTP header. If multiple compression rules match, the last rule wins.
Note
Compression Rules require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
## Get started
Cloudflare provides you with rules templates for common use cases.
1. In the Cloudflare dashboard, go to the Rules **Overview** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview)
2. Select **Templates**, and then select one of the available templates.
You can also refer to the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in the developer docs.
Alternatively, follow the instructions in the following pages to get started:
* [Create a compression rule in the dashboard](https://developers.cloudflare.com/rules/compression-rules/create-dashboard/)
* [Create a compression rule via Cloudflare API](https://developers.cloudflare.com/rules/compression-rules/create-api/)
***
## Availability
Compression Rules are available in all Cloudflare plans.
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 10 | 25 | 50 | 300 |
## Relevant fields
The following fields are commonly used in expressions of compression rules:
| Field in [Expression Builder](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/edit-expressions/#expression-builder) | Field name |
| - | - |
| *Media Type* | [`http.response.content_type.media_type`](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/http.response.content_type.media_type/) |
| *File extension* | [`http.request.uri.path.extension`](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/http.request.uri.path.extension/) |
| N/A | [`raw.http.request.uri.path.extension`](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/raw.http.request.uri.path.extension/) |
## Important remarks
* If there is a match for a compression rule but the client does not support any of the compression algorithms configured in the rule (according to the provided `accept-encoding` request header), the response sent to the client will not be compressed.
* If there is a match for a compression rule but the response sent from the origin server contains a `cache-control: no-transform` HTTP header, the compression rule will not perform any changes to the response.
## Troubleshooting
When troubleshooting Compression Rules, use [Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/) to determine if a rule is triggering for a specific URL.
---
title: Configuration Rules · Cloudflare Rules docs
description: Configuration Rules allow you to customize certain Cloudflare
configuration settings for matching incoming requests.
lastUpdated: 2025-08-22T14:24:45.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/configuration-rules/
md: https://developers.cloudflare.com/rules/configuration-rules/index.md
---
Configuration Rules allow you to customize certain Cloudflare [configuration settings](https://developers.cloudflare.com/rules/configuration-rules/settings/) for matching incoming requests.
The configuration rule expression will determine to which requests the rule settings will apply. For more information on expressions, refer to [Expressions](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/) and [Edit expressions in the dashboard](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/edit-expressions/).
Note
Configuration Rules require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
***
## Rules templates
Cloudflare provides you with rules templates for common use cases.
1. In the Cloudflare dashboard, go to the Rules **Overview** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview)
2. Select **Templates**, and then select one of the available templates.
You can also refer to the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in the developer docs.
## Availability
The number of available configuration rules varies according to your Cloudflare plan:
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 10 | 25 | 50 | 300 |
## Execution order
The execution order of Rules features is the following:
* [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/)
* [URL Rewrite Rules](https://developers.cloudflare.com/rules/transform/url-rewrite/)
* [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/)
* [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/)
* [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/)
* [Managed Transforms](https://developers.cloudflare.com/rules/transform/managed-transforms/)
* [Request Header Transform Rules](https://developers.cloudflare.com/rules/transform/request-header-modification/)
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
* [Snippets](https://developers.cloudflare.com/rules/snippets/)
* [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/)
The different types of rules listed above will take precedence over [Page Rules](https://developers.cloudflare.com/rules/page-rules/). This means that Page Rules will be overridden if there is a match for both Page Rules and the Rules products listed above.
Generally speaking, for [non-terminating actions](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/) the last change made by rules in the same [phase](https://developers.cloudflare.com/ruleset-engine/about/phases/) will win (later rules can overwrite changes done by previous rules). However, for terminating actions (*Block*, *Redirect*, or one of the challenge actions), rule evaluation will stop and the action will be executed immediately.
For example, if multiple rules with the *Redirect* action match, Cloudflare will always use the URL redirect of the first rule that matches. Also, if you configure URL redirects using different Cloudflare products (Single Redirects and Bulk Redirects), the product executed first will apply, if there is a rule match (in this case, Single Redirects).
Refer to the [Phases list](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/) for the product execution order.
Warning
Using Cloudflare challenges along with Rules features may cause challenge loops. Refer to [Rules troubleshooting](https://developers.cloudflare.com/rules/reference/troubleshooting/) for more information.
## Troubleshooting
When troubleshooting Configuration Rules, use [Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/) to determine if a rule is triggering for a specific URL.
---
title: Rules examples · Cloudflare Rules docs
description: Explore the following examples for Rules.
lastUpdated: 2025-11-11T11:19:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/examples/
md: https://developers.cloudflare.com/rules/examples/index.md
---
Explore the following examples for Rules.
Note
We have a separate listing for [Cache rules examples](https://developers.cloudflare.com/cache/how-to/cache-rules/examples/).
Filter resources...
[Route /images to an S3 Bucket using Terraform](https://developers.cloudflare.com/rules/cloud-connector/examples/route-images-to-aws-s3-using-terraform/)
[Route requests with a URI path starting with `/images` to a specific AWS S3 bucket with Cloud Connector using Terraform.](https://developers.cloudflare.com/rules/cloud-connector/examples/route-images-to-aws-s3-using-terraform/)
[Route /images to an S3 Bucket](https://developers.cloudflare.com/rules/cloud-connector/examples/route-images-to-s3/)
[Route requests with a URI path starting with `/images` to a specific AWS S3 bucket using Cloud Connector.](https://developers.cloudflare.com/rules/cloud-connector/examples/route-images-to-s3/)
[Send EU visitors to a Google Cloud Storage bucket](https://developers.cloudflare.com/rules/cloud-connector/examples/send-eu-visitors-to-gcs/)
[Route all traffic from EU visitors to a Google Cloud Storage bucket using Cloud Connector.](https://developers.cloudflare.com/rules/cloud-connector/examples/send-eu-visitors-to-gcs/)
[Serve /static-assets from Azure Blob Storage](https://developers.cloudflare.com/rules/cloud-connector/examples/serve-static-assets-from-azure/)
[Route requests with a URI path starting with `/static-assets` to an Azure Blob Storage container using Cloud Connector.](https://developers.cloudflare.com/rules/cloud-connector/examples/serve-static-assets-from-azure/)
[Disable Brotli compression](https://developers.cloudflare.com/rules/compression-rules/examples/disable-all-brotli/)
[Create a compression rule to turn off Brotli compression for all incoming requests of a given zone.](https://developers.cloudflare.com/rules/compression-rules/examples/disable-all-brotli/)
[Disable compression for AVIF images](https://developers.cloudflare.com/rules/compression-rules/examples/disable-compression-avif/)
[Create a compression rule to turn off compression for AVIF images, based on either the content type or the file extension specified in the request.](https://developers.cloudflare.com/rules/compression-rules/examples/disable-compression-avif/)
[Enable Zstandard compression for default content types](https://developers.cloudflare.com/rules/compression-rules/examples/enable-zstandard/)
[Create a compression rule to turn on Zstandard compression for response content types where Cloudflare applies compression by default.](https://developers.cloudflare.com/rules/compression-rules/examples/enable-zstandard/)
[Use Gzip compression for CSV files](https://developers.cloudflare.com/rules/compression-rules/examples/gzip-for-csv/)
[Create a compression rule to set Gzip compression as the preferred compression method for CSV files.](https://developers.cloudflare.com/rules/compression-rules/examples/gzip-for-csv/)
[Use only Brotli compression for a specific path](https://developers.cloudflare.com/rules/compression-rules/examples/only-brotli-url-path/)
[Create a compression rule to set Brotli as the only supported compression algorithm for a specific URI path.](https://developers.cloudflare.com/rules/compression-rules/examples/only-brotli-url-path/)
[Define a single configuration rule using Terraform](https://developers.cloudflare.com/rules/configuration-rules/examples/define-single-configuration-terraform/)
[Create a configuration rule using Terraform to turn off Email Obfuscation and Browser Integrity Check for API requests in a given zone.](https://developers.cloudflare.com/rules/configuration-rules/examples/define-single-configuration-terraform/)
[Change the HTTP Host header and DNS record](https://developers.cloudflare.com/rules/origin-rules/examples/change-http-host-header/)
[Create an origin rule to change the HTTP `Host` header and the resolved DNS record.](https://developers.cloudflare.com/rules/origin-rules/examples/change-http-host-header/)
[Change the destination port](https://developers.cloudflare.com/rules/origin-rules/examples/change-port/)
[Create an origin rule to change the destination port.](https://developers.cloudflare.com/rules/origin-rules/examples/change-port/)
[Define a single origin rule using Terraform](https://developers.cloudflare.com/rules/origin-rules/examples/define-single-origin-terraform/)
[Create an origin rule using Terraform to override the `Host` header, the resolved hostname, and the destination port of API requests.](https://developers.cloudflare.com/rules/origin-rules/examples/define-single-origin-terraform/)
[A/B testing with same-URL direct access](https://developers.cloudflare.com/rules/snippets/examples/ab-testing-same-url/)
[Set up an A/B test by controlling what response is served based on cookies.](https://developers.cloudflare.com/rules/snippets/examples/ab-testing-same-url/)
[Append dates to cookies to use with A/B testing](https://developers.cloudflare.com/rules/snippets/examples/append-dates-to-cookies/)
[Dynamically set a cookie expiration and test group.](https://developers.cloudflare.com/rules/snippets/examples/append-dates-to-cookies/)
[Auth with headers](https://developers.cloudflare.com/rules/snippets/examples/auth-with-headers/)
[Allow or deny a request based on a known pre-shared key in a header. This is not meant to replace the WebCrypto API.](https://developers.cloudflare.com/rules/snippets/examples/auth-with-headers/)
[Send Bot Management information to origin](https://developers.cloudflare.com/rules/snippets/examples/bot-data-to-origin/)
[Send Bots information to your origin. Refer to Bot Managenent variables for a full list of available fields.](https://developers.cloudflare.com/rules/snippets/examples/bot-data-to-origin/)
[Send suspect bots to a honeypot](https://developers.cloudflare.com/rules/snippets/examples/bots-to-honeypot/)
[Use the bot score field to send bots to a honeypot.](https://developers.cloudflare.com/rules/snippets/examples/bots-to-honeypot/)
[Bulk redirect based on a map object](https://developers.cloudflare.com/rules/snippets/examples/bulk-redirect-map/)
[Redirect requests to certain URLs based on a mapped object to the request's URL.](https://developers.cloudflare.com/rules/snippets/examples/bulk-redirect-map/)
[Country code redirect](https://developers.cloudflare.com/rules/snippets/examples/country-code-redirect/)
[Redirect a response based on the country code in the header of a visitor.](https://developers.cloudflare.com/rules/snippets/examples/country-code-redirect/)
[Custom cache](https://developers.cloudflare.com/rules/snippets/examples/custom-cache/)
[Store, retrieve, and remove assets from cache programmatically. Use this template to optimize performance and implement custom caching strategies.](https://developers.cloudflare.com/rules/snippets/examples/custom-cache/)
[Debugging logs](https://developers.cloudflare.com/rules/snippets/examples/debugging-logs/)
[Send debugging information in an errored response to a logging service.](https://developers.cloudflare.com/rules/snippets/examples/debugging-logs/)
[Define CORS headers](https://developers.cloudflare.com/rules/snippets/examples/define-cors-headers/)
[Adjust Cross-Origin Resource Sharing (CORS) headers and handle preflight requests.](https://developers.cloudflare.com/rules/snippets/examples/define-cors-headers/)
[Add HEX timestamp to a request header](https://developers.cloudflare.com/rules/snippets/examples/hex-timestamp/)
[Add a custom header to requests sent to the origin server with the current timestamp in hexadecimal format for debugging, tracking, or custom routing purposes.](https://developers.cloudflare.com/rules/snippets/examples/hex-timestamp/)
[Follow redirects from the origin](https://developers.cloudflare.com/rules/snippets/examples/follow-redirects/)
[Modify the fetch request to follow redirects from the origin, ensuring the client receives the final response.](https://developers.cloudflare.com/rules/snippets/examples/follow-redirects/)
[Validate JSON web tokens (JWT)](https://developers.cloudflare.com/rules/snippets/examples/jwt-validation/)
[Extract the JWT token from a header, decode it, and implement validation checks to verify it.](https://developers.cloudflare.com/rules/snippets/examples/jwt-validation/)
[Maintenance page](https://developers.cloudflare.com/rules/snippets/examples/maintenance/)
[Serve a custom maintenance page instead of fetching content from the origin server or cache. Ideal for downtime notifications, planned maintenance, or emergency messages.](https://developers.cloudflare.com/rules/snippets/examples/maintenance/)
[Override a Set-Cookie header with a certain value](https://developers.cloudflare.com/rules/snippets/examples/override-set-cookies-value/)
[Get a specific `Set-Cookie` header and update it with a certain value.](https://developers.cloudflare.com/rules/snippets/examples/override-set-cookies-value/)
[Redirect 403 Forbidden to a different page](https://developers.cloudflare.com/rules/snippets/examples/redirect-forbidden-status/)
[If origin responded with `403 Forbidden` error code, redirect to different page.](https://developers.cloudflare.com/rules/snippets/examples/redirect-forbidden-status/)
[Redirect from one domain to another](https://developers.cloudflare.com/rules/snippets/examples/redirect-replaced-domain/)
[Redirect all requests from one domain to another domain.](https://developers.cloudflare.com/rules/snippets/examples/redirect-replaced-domain/)
[Remove fields from API response](https://developers.cloudflare.com/rules/snippets/examples/remove-fields-api-response/)
[If origin responds with `JSON`, parse the response and delete fields to return a modified response.](https://developers.cloudflare.com/rules/snippets/examples/remove-fields-api-response/)
[Remove query strings before sending request to origin](https://developers.cloudflare.com/rules/snippets/examples/remove-query-strings/)
[Remove certain query strings from a request before passing to the origin.](https://developers.cloudflare.com/rules/snippets/examples/remove-query-strings/)
[Remove response headers](https://developers.cloudflare.com/rules/snippets/examples/remove-response-headers/)
[Remove from response all headers that start with a certain name.](https://developers.cloudflare.com/rules/snippets/examples/remove-response-headers/)
[Return information about the incoming request](https://developers.cloudflare.com/rules/snippets/examples/return-incoming-request-properties/)
[Respond with information about the incoming request provided by Cloudflare’s global network.](https://developers.cloudflare.com/rules/snippets/examples/return-incoming-request-properties/)
[Rewrite links on HTML pages](https://developers.cloudflare.com/rules/snippets/examples/rewrite-site-links/)
[Dynamically rewrite links in HTML responses. This is useful for site migrations and branding updates.](https://developers.cloudflare.com/rules/snippets/examples/rewrite-site-links/)
[Change origin and modify paths](https://developers.cloudflare.com/rules/snippets/examples/route-and-rewrite/)
[Route requests to a different origin, prepend a directory to the URL path, and remove specific segments.](https://developers.cloudflare.com/rules/snippets/examples/route-and-rewrite/)
[Set security headers](https://developers.cloudflare.com/rules/snippets/examples/security-headers/)
[Set common security headers such as X-XSS-Protection, X-Frame-Options, and X-Content-Type-Options.](https://developers.cloudflare.com/rules/snippets/examples/security-headers/)
[Send timestamp to origin as a custom header](https://developers.cloudflare.com/rules/snippets/examples/send-timestamp-to-origin/)
[Convert timestamp to hexadecimal format and send it as a custom header to the origin.](https://developers.cloudflare.com/rules/snippets/examples/send-timestamp-to-origin/)
[Route to a different origin based on origin response](https://developers.cloudflare.com/rules/snippets/examples/serve-different-origin/)
[If response to the original request is not `200 OK` or a redirect, send to another origin.](https://developers.cloudflare.com/rules/snippets/examples/serve-different-origin/)
[Sign requests](https://developers.cloudflare.com/rules/snippets/examples/signing-requests/)
[Verify a signed request using the HMAC and SHA-256 algorithms or return a 403.](https://developers.cloudflare.com/rules/snippets/examples/signing-requests/)
[Slow down suspicious requests](https://developers.cloudflare.com/rules/snippets/examples/slow-suspicious-requests/)
[Define a delay to be used when incoming requests match a rule you consider suspicious based on the bot score.](https://developers.cloudflare.com/rules/snippets/examples/slow-suspicious-requests/)
[Add a wildcard CORS response header](https://developers.cloudflare.com/rules/transform/examples/add-cors-header/)
[Create a CORS response header transform rule to add an `Access-Control-Allow-Origin` HTTP header to the response with wildcard as static value. (`cookiename=value`).](https://developers.cloudflare.com/rules/transform/examples/add-cors-header/)
[Add a request header with the current bot score](https://developers.cloudflare.com/rules/transform/examples/add-request-header-bot-score/)
[Create a request header transform rule to add a `X-Bot-Score` HTTP header to the request with the current bot score.](https://developers.cloudflare.com/rules/transform/examples/add-request-header-bot-score/)
[Add request header with a static value](https://developers.cloudflare.com/rules/transform/examples/add-request-header-static-value/)
[Create a request header transform rule to add an `X-Source` HTTP header to the request with a static value (`Cloudflare`).](https://developers.cloudflare.com/rules/transform/examples/add-request-header-static-value/)
[Add a request header for subrequests from other zones](https://developers.cloudflare.com/rules/transform/examples/add-request-header-subrequest-other-zone/)
[Create a request header transform rule to add an HTTP header when the Workers subrequest comes from a different zone.](https://developers.cloudflare.com/rules/transform/examples/add-request-header-subrequest-other-zone/)
[Add a response header with a static value](https://developers.cloudflare.com/rules/transform/examples/add-response-header-static-value/)
[Create a response header transform rule to add a `set-cookie` HTTP header to the response with a static value (`cookiename=value`).](https://developers.cloudflare.com/rules/transform/examples/add-response-header-static-value/)
[Normalize encoded slashes in URL path](https://developers.cloudflare.com/rules/transform/examples/normalize-encoded-slash/)
[Create a URL rewrite rule (part of Transform Rules) to normalize encoded forward slashes (`%2F`) in the request path to standard slashes (`/`).](https://developers.cloudflare.com/rules/transform/examples/normalize-encoded-slash/)
[Remove a request header](https://developers.cloudflare.com/rules/transform/examples/remove-request-header/)
[Create a request header transform rule (part of Transform Rules) to remove the `cf-connecting-ip` HTTP header from the request.](https://developers.cloudflare.com/rules/transform/examples/remove-request-header/)
[Remove a response header](https://developers.cloudflare.com/rules/transform/examples/remove-response-header/)
[Create a response header transform rule (part of Transform Rules) to remove the `cf-connecting-ip` HTTP header from the response.](https://developers.cloudflare.com/rules/transform/examples/remove-response-header/)
[Rewrite blog archive URLs](https://developers.cloudflare.com/rules/transform/examples/rewrite-archive-urls-new-format/)
[Create a transform rule to rewrite the URL format `/posts/---` to the new format `/posts/<YYYY>/<MM>/<DD>/<TITLE>`.](https://developers.cloudflare.com/rules/transform/examples/rewrite-archive-urls-new-format/)
[Rewrite path of moved section of a website](https://developers.cloudflare.com/rules/transform/examples/rewrite-moved-section/)
[Create a URL rewrite rule (part of Transform Rules) to rewrite everything under `/blog/<PATH>` to `/marketing/<PATH>`.](https://developers.cloudflare.com/rules/transform/examples/rewrite-moved-section/)
[Rewrite path of archived blog posts](https://developers.cloudflare.com/rules/transform/examples/rewrite-path-archived-posts/)
[Create a URL rewrite rule (part of Transform Rules) to rewrite any requests for `/news/2012/...` URI paths to `/archive/news/2012/...`.](https://developers.cloudflare.com/rules/transform/examples/rewrite-path-archived-posts/)
[Rewrite path for object storage bucket](https://developers.cloudflare.com/rules/transform/examples/rewrite-path-object-storage/)
[Create a URL rewrite rule (part of Transform Rules) to rewrite any requests for `/files/...` URI paths to `/...`.](https://developers.cloudflare.com/rules/transform/examples/rewrite-path-object-storage/)
[Rewrite image paths with several URL segments](https://developers.cloudflare.com/rules/transform/examples/rewrite-several-url-different-url/)
[Create a URL rewrite rule (part of Transform Rules) to rewrite any requests for `/images/<FOLDER1>/<FOLDER2>/<FILENAME>` to `/img/<FILENAME>`.](https://developers.cloudflare.com/rules/transform/examples/rewrite-several-url-different-url/)
[Rewrite URL query string](https://developers.cloudflare.com/rules/transform/examples/rewrite-url-string-visitors/)
[Create a transform rule to rewrite the request path from `/blog` to `/blog?sort-by=date`.](https://developers.cloudflare.com/rules/transform/examples/rewrite-url-string-visitors/)
[Rewrite page path for visitors in specific countries](https://developers.cloudflare.com/rules/transform/examples/rewrite-welcome-for-countries/)
[Create two URL rewrite rules (part of Transform Rules) to rewrite the path of the welcome page for visitors in specific countries.](https://developers.cloudflare.com/rules/transform/examples/rewrite-welcome-for-countries/)
[Set a response header with the current bot score](https://developers.cloudflare.com/rules/transform/examples/set-response-header-bot-score/)
[Create a response header transform rule (part of Transform Rules) to set an `X-Bot-Score` HTTP header in the response with the current bot score.](https://developers.cloudflare.com/rules/transform/examples/set-response-header-bot-score/)
[Set response header with a static value](https://developers.cloudflare.com/rules/transform/examples/set-response-header-static-value/)
[Create a response header transform rule (part of Transform Rules) to set an `X-Bot-Score` HTTP header in the response to a static value (`Cloudflare`).](https://developers.cloudflare.com/rules/transform/examples/set-response-header-static-value/)
[Perform mobile redirects](https://developers.cloudflare.com/rules/url-forwarding/examples/perform-mobile-redirects/)
[Create a redirect rule to redirect visitors using mobile devices to a different hostname.](https://developers.cloudflare.com/rules/url-forwarding/examples/perform-mobile-redirects/)
[Redirect admin area requests to HTTPS](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-admin-https/)
[Create a redirect rule to redirect requests for the administration area of `store.example.com` to HTTPS, keeping the original path and query string.](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-admin-https/)
[Redirect requests from one domain to another](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-another-domain/)
[Create a redirect rule to redirect all requests to a different domain, maintaining all functionality, except for the discontinued HTTP service (port 80).](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-another-domain/)
[Redirect requests from one country to a domain](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-country/)
[Create a redirect rule to redirect all website visitors from the United Kingdom to a different domain, maintaining the current functionality in the same paths.](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-country/)
[Redirect requests for a domain to a new domain](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-different-domain-root/)
[Create a redirect rule to redirect all URLs for a domain to point to the root of a new domain, including any subdomains of the old domain.](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-different-domain-root/)
[Redirect requests to a different hostname](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-different-hostname/)
[Create a redirect rule to redirect all requests for `smallshop.example.com` to a different hostname using HTTPS, keeping the original path and query string.](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-all-different-hostname/)
[Redirect local visitors to specific subdomains](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-country-subdomains/)
[Create a redirect rule to redirect United Kingdom and France visitors from the `example.com` website's root path (`/`) to their localized subdomains `https://gb.example.com` and `https://fr.example.com`, respectively.](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-country-subdomains/)
[Redirect visitors to a new page URL](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-new-url/)
[Create a redirect rule to redirect visitors from `/contact-us/` to the page's new path `/contacts/`.](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-new-url/)
[Redirect from root to WWW](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-root-to-www/)
[Create a redirect rule to forward HTTPS requests from the root (also known as the “apex” or “naked” domain) to the WWW subdomain.](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-root-to-www/)
[Redirect from WWW to root](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-www-to-root/)
[Create a redirect rule to forward HTTPS requests from the WWW subdomain to the root (also known as the “apex” or “naked” domain).](https://developers.cloudflare.com/rules/url-forwarding/examples/redirect-www-to-root/)
[Remove locale from URL path](https://developers.cloudflare.com/rules/url-forwarding/examples/remove-locale-url/)
[Create a redirect rule to redirect visitors from an old URL format with locale information to a new URL format.](https://developers.cloudflare.com/rules/url-forwarding/examples/remove-locale-url/)
</page>
<page>
---
title: Custom Errors · Cloudflare Rules docs
description: Use Custom Errors to return custom content to your website visitors
in case of HTTP errors returned by an origin server or by a Cloudflare product
(including Cloudflare Workers), or when showing a security challenge.
lastUpdated: 2025-11-25T09:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/custom-errors/
md: https://developers.cloudflare.com/rules/custom-errors/index.md
---
Use Custom Errors to return custom content to your website visitors in case of HTTP errors returned by an origin server or by a Cloudflare product (including [Cloudflare Workers](https://developers.cloudflare.com/workers/)), or when showing a [security challenge](https://developers.cloudflare.com/cloudflare-challenges/).
You can configure custom error content using the following methods:
* [**Error Page**](#error-pages): An HTML page shown to website visitors when a specific error occurs (refer to the different [error page types](https://developers.cloudflare.com/rules/custom-errors/reference/error-page-types/)) or when showing a security challenge. Error Pages can be defined at the zone level and at the account level on paid plans, with zone-level configurations taking precedence.
* [**Custom Error Rule**](#custom-error-rules): Defines the conditions under which Cloudflare will serve a custom error response to visitors in case of HTTP errors (status codes `400` and above), and the exact content that will be served. A matching custom error rule has priority over an Error Page configured at the account or at the zone level that would apply to the same error.
Custom Errors require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
## How it works
Cloudflare has a set of default pages for presenting errors and challenges to your website visitors. You can customize those pages using Error Pages and Custom Error Rules.
When an error of a [specific type](https://developers.cloudflare.com/rules/custom-errors/reference/error-page-types/) occurs, Cloudflare does the following:
1. Search for a configured Error Page at the account level for the specific error.
2. Search for a configured Error Page at the zone level for the specific error (it will have priority over the account-level Error Page, if any).
3. Search for a matching custom error rule at the account level. The rule will have priority over 500 and 1000 class Error Pages at the account or zone level.
4. Search for a matching custom error rule at the zone level. The rule will have priority over 500 and 1000 class Error Pages at the account or zone level and over custom error rules at the account level.
5. If a security rule like a [WAF custom rule](https://developers.cloudflare.com/waf/custom-rules/) or a [rate limiting rule](https://developers.cloudflare.com/waf/rate-limiting-rules/) triggers a custom block response instead of a default Cloudflare WAF block page, the rule-specific block response will have priority over Error Pages or a matching custom error rule.
6. If any of the previous configurations apply, serve the custom error content to the visitor. If not, serve the default error page for the specific error type.
Note
To customize a challenge page or a block page, use an Error Page, since Custom Error Rules will not be applied to security actions originating from Cloudflare products. Keep in mind that [custom WAF response](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/#configure-a-custom-response-for-blocked-requests) takes precedence over an Error Page and custom error rules.
## Availability
Custom Errors are available to all paid plans. The exact features depend on your Cloudflare plan.
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | Yes | Yes | Yes |
| Number of rules | 0 | 25 | 50 | 300 |
| Number of assets | 0 | 25 | 50 | 300 |
| Error Pages | No | Yes | Yes | Yes |
| Origin Error Pages | No | No | No | Yes |
***
## Error Pages
Cloudflare uses a wide range of [error codes](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/) to identify issues in handling request traffic. By default, these error pages mention Cloudflare; however, you can create custom error pages to provide a consistent brand experience for your users.
Error Pages do not apply to responses with an HTTP status code of `500`, `501`, `503`, or `505`. These exceptions help avoid issues with specific API endpoints and other web applications. You can still customize responses for these status codes using Custom Error Rules.
If you are on a Cloudflare paid plan, you can create custom error pages at the zone level or for your entire account. Zone-level error pages have priority over account-level error pages.
Additionally, Enterprise customers can customize 5XX error pages (except errors `520`-`527`) at their origin by turning on **Origin Error Pages** in **Error Pages** in the dashboard.
You can design custom error pages to appear during a security challenge or when an error occurs. For more information on the different error page types, refer to [Error page types](https://developers.cloudflare.com/rules/custom-errors/reference/error-page-types/).
Note
Cloudflare will return the default Cloudflare error page instead of your custom Error Pages if the incoming request does not contain an `accept-encoding` header. This does not apply to responses originating from Custom Error Rules.
## Custom Error Rules
A custom error rule defines the conditions under which Cloudflare will serve custom error content to visitors in case of HTTP errors (status codes `400` and above), and the exact content that will be served to visitors.
When defining the content to serve, you provide either an inline response or the URL of an existing webpage. The URL can point to a webpage or to a different resource such as JSON content.
When you provide a URL, Cloudflare will gather any required images, CSS, and JavaScript code and save a minified version of the full page in the Cloudflare global network. This resource is called a [custom error asset](#custom-error-assets), which you can use in one or more custom error rules in the same scope of the asset (zone or account).
When a custom error rule is triggered, Cloudflare will replace the body with the response you previously defined and (optionally) the response HTTP status code sent to the visitor. Cloudflare will keep any existing HTTP response headers except for `Content-Type` and `Content-Length`.
Additionally, you can configure [Response Header Transform Rules](https://developers.cloudflare.com/rules/transform/response-header-modification/) for error responses to add, change, or remove HTTP headers from the response.
Custom error rules have priority over [Error Pages](#error-pages).
## Custom Error Assets
A custom error asset corresponds to a web resource such as an HTML web page (including any referenced images, CSS, and JavaScript code) that Cloudflare fetches and saves based on a URL you provide, to be served to visitors as an error page.
Once the custom error asset is stored in Cloudflare's global network, the URL you initially provided no longer needs to be available. You can update an existing custom error asset by fetching it again. The metadata associated with each custom error asset includes the timestamp when the last fetch occurred, and this information is displayed in the dashboard.
You can use a custom error asset in one or more [custom error rules](#custom-error-rules) in the same scope where you defined the asset (zone or account).
</page>
<page>
---
title: Cache Rules · Cloudflare Rules docs
lastUpdated: 2025-02-13T11:31:13.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/link-cache-rules/
md: https://developers.cloudflare.com/rules/link-cache-rules/index.md
---
</page>
<page>
---
title: URL normalization · Cloudflare Rules docs
description: Cloudflare provides a URL normalization feature to modify the URLs
of incoming requests so that they conform to a consistent formatting standard.
lastUpdated: 2025-08-22T14:24:45.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/normalization/
md: https://developers.cloudflare.com/rules/normalization/index.md
---
Cloudflare provides a URL normalization feature to modify the URLs of incoming requests so that they conform to a consistent formatting standard.
When you enable URL normalization, all incoming URLs are normalized before they pass to subsequent global network features that accept a URL input, such as WAF custom rules, Workers, and Access. Rule expressions that filter traffic based on URLs will therefore trigger correctly, regardless of the format of the incoming URL. When URL normalization is disabled, Cloudflare forwards the URL to origin in its original form.
Warning
When traffic is proxied via Cloudflare, essential request URL normalization is always applied regardless whether URL normalization is enabled for a specific zone. For example, you cannot disable the conversion of two or more adjacent slashes into a single slash in a request URL by turning off URL normalization.
URL normalization does not perform any redirects, and therefore it will not change the address displayed in the visitor's browser. The normalization operation, when enabled, occurs on the global network and affects Cloudflare features executed later and (optionally) the URL received at the origin server.
Note
URL normalization requires that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
***
## Availability
URL normalization is available in all Cloudflare plans.
## Get started
Learn more about [URL normalization](https://developers.cloudflare.com/rules/normalization/how-it-works/) and how to [configure URL normalization](https://developers.cloudflare.com/rules/normalization/manage/) in the Cloudflare dashboard.
</page>
<page>
---
title: Origin Rules · Cloudflare Rules docs
description: "Origin Rules allow you to customize where the incoming traffic
will go and with which parameters. Currently you can perform the following
overrides:"
lastUpdated: 2025-10-06T10:46:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/origin-rules/
md: https://developers.cloudflare.com/rules/origin-rules/index.md
---
Origin Rules allow you to customize where the incoming traffic will go and with which parameters. Currently you can perform the following overrides:
* [Host header](https://developers.cloudflare.com/rules/origin-rules/features/#host-header): Overrides the `Host` header of incoming requests.
* [Server Name Indication (SNI)](https://developers.cloudflare.com/rules/origin-rules/features/#server-name-indication-sni): Overrides the Server Name Indication (SNI) value of incoming requests.
* [DNS record](https://developers.cloudflare.com/rules/origin-rules/features/#dns-record): Overrides the resolved hostname of incoming requests.
* [Destination port](https://developers.cloudflare.com/rules/origin-rules/features/#destination-port): Overrides the resolved destination port of incoming requests.
The origin rule expression will determine when these overrides will be applied.
For more complex and customized modifications, consider using [Snippets](https://developers.cloudflare.com/rules/snippets/).
Note
Origin Rules require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
## Rules templates
Cloudflare provides you with rules templates for common use cases.
1. In the Cloudflare dashboard, go to the Rules **Overview** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview)
2. Select **Templates**, and then select one of the available templates.
You can also refer to the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in the developer docs.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 10 | 25 | 50 | 300 |
| Override Host header | No | No | No | Yes |
| Override SNI | No | No | No | Yes |
| Override DNS records | No | No | No | Yes |
| Override destination port | Yes | Yes | Yes | Yes |
## Execution order
The execution order of Rules features is the following:
* [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/)
* [URL Rewrite Rules](https://developers.cloudflare.com/rules/transform/url-rewrite/)
* [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/)
* [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/)
* [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/)
* [Managed Transforms](https://developers.cloudflare.com/rules/transform/managed-transforms/)
* [Request Header Transform Rules](https://developers.cloudflare.com/rules/transform/request-header-modification/)
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
* [Snippets](https://developers.cloudflare.com/rules/snippets/)
* [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/)
The different types of rules listed above will take precedence over [Page Rules](https://developers.cloudflare.com/rules/page-rules/). This means that Page Rules will be overridden if there is a match for both Page Rules and the Rules products listed above.
Generally speaking, for [non-terminating actions](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/) the last change made by rules in the same [phase](https://developers.cloudflare.com/ruleset-engine/about/phases/) will win (later rules can overwrite changes done by previous rules). However, for terminating actions (*Block*, *Redirect*, or one of the challenge actions), rule evaluation will stop and the action will be executed immediately.
For example, if multiple rules with the *Redirect* action match, Cloudflare will always use the URL redirect of the first rule that matches. Also, if you configure URL redirects using different Cloudflare products (Single Redirects and Bulk Redirects), the product executed first will apply, if there is a rule match (in this case, Single Redirects).
Refer to the [Phases list](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/) for the product execution order.
Warning
Using Cloudflare challenges along with Rules features may cause challenge loops. Refer to [Rules troubleshooting](https://developers.cloudflare.com/rules/reference/troubleshooting/) for more information.
## Important remarks
If you override the hostname with an origin rule (via `Host` header override or DNS record override) and add a header override to your load balancer configuration, the origin rule will take precedence over the load balancer configuration.
Like [Page Rules](https://developers.cloudflare.com/rules/page-rules/), an origin rule performing a `Host` header override will update the SNI value of the original request to the same value of the `Host` header. To set an SNI value different from the `Host` header override, add an SNI override in the same origin rule or create a separate origin rule for this purpose.
## Troubleshooting
When troubleshooting origin rules, use [Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/) to determine if a rule is triggering for a specific URL.
</page>
<page>
---
title: Page Rules · Cloudflare Rules docs
description: Page Rules trigger one or more actions whenever a certain URL
pattern is matched. Page Rules are available in Rules > Page Rules.
lastUpdated: 2025-02-13T11:31:13.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/page-rules/
md: https://developers.cloudflare.com/rules/page-rules/index.md
---
Page Rules trigger one or more actions whenever a certain URL pattern is matched. Page Rules are available in **Rules** > **Page Rules**.
## Availability
The default number of allowed page rules depends on the domain plan as shown below.
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 3 | 20 | 50 | 125 |
***
## Before getting started
It is important to understand a few Page Rules behaviors.
### Page Rules require proxied DNS records
Page Rules require a [proxied](https://developers.cloudflare.com/dns/proxy-status/) DNS record for your page rule to work. Page Rules will not apply to hostnames that do not exist in DNS or are not being directed to Cloudflare.
Depending on the record type, you can use different values for the target as a placeholder. Either one of these achieves the same outcome and you only need to create one:
```plaintext
www.example.com A 192.0.2.1
www.example.com AAAA 2001:DB8::1
www.example.com CNAME domain.example
```
Cloudflare recommends only using reserved IP addresses or domain names to avoid sending traffic to foreign infrastructure.
For more information on reserved IP addresses or top level domains, please refer to these RFCs:
* [RFC 5737](https://datatracker.ietf.org/doc/html/rfc5737)
* [RFC 3849](https://datatracker.ietf.org/doc/html/rfc3849)
* [RFC 2606](https://datatracker.ietf.org/doc/html/rfc2606)
### Priority order matters
Only the highest priority matching page rule takes effect on a request.
Page Rules are prioritized in descending order in the Cloudflare dashboard, with the highest priority rule at the top. For this reason, Cloudflare recommends ordering your rules from most specific to least specific.
A page rule matches a URL pattern based on the following format (comprised of five segments):
```txt
<SCHEME>://<HOSTNAME>:<PORT>/<PATH>?<QUERY_STRING>
```
An example URL with all the segments looks like the following:
```txt
https://www.example.com:443/image.png?parameter1=value1
```
The `<SCHEME>` and `<PORT>` segments are optional. If omitted, `<SCHEME>` matches both `http://` and `https://` protocols. If no `<PORT>` is specified, the rule will match all ports.
### Disabled page rules
When a page rule is disabled, actions will not trigger, but the rule will:
* Still appear in the Cloudflare dashboard.
* Be editable.
* Count against the number of rules allowed for your domain.
</page>
<page>
---
title: Reference · Cloudflare Rules docs
description: Reference information for Rules.
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/rules/reference/
md: https://developers.cloudflare.com/rules/reference/index.md
---
Refer to the following pages for more information about Rules:
* [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/)
* [Troubleshoot Rules](https://developers.cloudflare.com/rules/reference/troubleshooting/)
* [Page Rules migration guide](https://developers.cloudflare.com/rules/reference/page-rules-migration/)
</page>
<page>
---
title: Cloudflare Snippets · Cloudflare Rules docs
description: Cloudflare Snippets provide a powerful and flexible way to
customize the behavior of your website or application using short pieces of
JavaScript code. With Snippets, you can modify HTTP response headers,
implement JWT validation, perform complex redirects, and much more.
lastUpdated: 2025-11-18T12:40:09.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/snippets/
md: https://developers.cloudflare.com/rules/snippets/index.md
---
Cloudflare Snippets provide a powerful and flexible way to customize the behavior of your website or application using short pieces of JavaScript code. With Snippets, you can modify HTTP response headers, implement JWT validation, perform complex redirects, and much more.
For code samples addressing common use cases, please refer to the [Examples](https://developers.cloudflare.com/rules/snippets/examples/) section.
Note
Snippets require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
## Snippets elements
To create and deploy a snippet, you need to define the following elements:
* **Code snippet**: JavaScript code to be executed during the request-handling process.
* **Snippet rule**: A [filter expression](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/) that determines which requests the Snippet will be applied to. Each snippet can only be associated with one snippet rule.
For more information, refer to [How Snippets work](https://developers.cloudflare.com/rules/snippets/how-it-works/) and [Create a snippet in the dashboard](https://developers.cloudflare.com/rules/snippets/create-dashboard/).
Note
If you have used the Cloudflare API to create a code snippet that is not associated with a snippet rule, the Cloudflare dashboard will show that code snippet in a separate tab called **Unused Snippets**. You can either edit the snippet code and associate it with a snippet rule, or delete the unused code snippet.
## Templates
Cloudflare provides you with rules templates for common use cases.
1. In the Cloudflare dashboard, go to the Rules **Overview** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview)
2. Select **Templates**, and then select one of the available templates.
You can also refer to the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in the developer docs.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | Yes | Yes | Yes |
| Number of snippets | 0 | 25 | 50 | 300 |
| Number of snippet subrequests | 0 | 2 | 3 | 5 |
Each subrequest in a redirect chain counts against the subrequest limit. This means that if a subrequest was redirected it would count as two subrequests. To avoid issues, ensure that you make a subrequest to the end location of the redirect chain.
Currently, [Version Management](https://developers.cloudflare.com/version-management/) does not support Snippets.
## Limits
Cloudflare Snippets are designed for fast, lightweight edge logic. The following limits apply:
| Description | All plans |
| - | - |
| Maximum execution time | 5 ms |
| Maximum memory | 2 MB |
| Maximum total package size | 32 KB |
Need guidance on choosing between Snippets and Workers?
Explore our [detailed guide](https://developers.cloudflare.com/rules/snippets/when-to-use/) for best practices, real-world use cases, and example implementations.
## Execution order
The execution order of Rules features is the following:
* [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/)
* [URL Rewrite Rules](https://developers.cloudflare.com/rules/transform/url-rewrite/)
* [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/)
* [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/)
* [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/)
* [Managed Transforms](https://developers.cloudflare.com/rules/transform/managed-transforms/)
* [Request Header Transform Rules](https://developers.cloudflare.com/rules/transform/request-header-modification/)
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
* [Snippets](https://developers.cloudflare.com/rules/snippets/)
* [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/)
The different types of rules listed above will take precedence over [Page Rules](https://developers.cloudflare.com/rules/page-rules/). This means that Page Rules will be overridden if there is a match for both Page Rules and the Rules products listed above.
Generally speaking, for [non-terminating actions](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/) the last change made by rules in the same [phase](https://developers.cloudflare.com/ruleset-engine/about/phases/) will win (later rules can overwrite changes done by previous rules). However, for terminating actions (*Block*, *Redirect*, or one of the challenge actions), rule evaluation will stop and the action will be executed immediately.
For example, if multiple rules with the *Redirect* action match, Cloudflare will always use the URL redirect of the first rule that matches. Also, if you configure URL redirects using different Cloudflare products (Single Redirects and Bulk Redirects), the product executed first will apply, if there is a rule match (in this case, Single Redirects).
Refer to the [Phases list](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/) for the product execution order.
Warning
Using Cloudflare challenges along with Rules features may cause challenge loops. Refer to [Rules troubleshooting](https://developers.cloudflare.com/rules/reference/troubleshooting/) for more information.
</page>
<page>
---
title: Trace a request with Cloudflare Trace · Cloudflare Rules docs
description: Cloudflare Trace (Beta) follows an HTTP/S request through
Cloudflare's reverse proxy to your origin. Use this tool to understand how
different Cloudflare configurations interact with an HTTP/S request for one of
your hostnames. If the hostname you are testing is not proxied by Cloudflare,
Cloudflare Trace will still return all the configurations that Cloudflare
would have applied to the request.
lastUpdated: 2026-02-03T18:17:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/trace-request/
md: https://developers.cloudflare.com/rules/trace-request/index.md
---
Available on all plans
Cloudflare Trace (Beta) follows an HTTP/S request through Cloudflare's reverse proxy to your origin. Use this tool to understand how different Cloudflare configurations interact with an HTTP/S request for one of your hostnames. If the hostname you are testing is not [proxied by Cloudflare](https://developers.cloudflare.com/dns/proxy-status/), Cloudflare Trace will still return all the configurations that Cloudflare would have applied to the request.
You can define specific request properties to simulate different conditions for an HTTP/S request. Inactive rules configured in Cloudflare products will not be evaluated.
Cloudflare Trace is available to users with an Administrator or Super Administrator role.
## Resources
* [Use Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/how-to/)
* [Cloudflare Trace limitations](https://developers.cloudflare.com/rules/trace-request/limitations/)
* [Cloudflare Trace changelog](https://developers.cloudflare.com/rules/trace-request/changelog/)
</page>
<page>
---
title: Transform Rules · Cloudflare Rules docs
description: Transform Rules allow you to adjust the URI path, query string, and
HTTP headers of requests and responses on the Cloudflare global network.
lastUpdated: 2025-10-06T10:46:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/transform/
md: https://developers.cloudflare.com/rules/transform/index.md
---
Transform Rules allow you to adjust the URI path, query string, and HTTP headers of requests and responses on the Cloudflare global network.
There are several types of Transform Rules:
* [**URL Rewrite Rules**](https://developers.cloudflare.com/rules/transform/url-rewrite/): Rewrite the URL path and query string of an HTTP request.
* [**Request Header Transform Rules**](https://developers.cloudflare.com/rules/transform/request-header-modification/): Set the value of an HTTP request header or remove a request header.
* [**Response Header Transform Rules**](https://developers.cloudflare.com/rules/transform/response-header-modification/): Set the value of an HTTP response header or remove a response header.
* [**Managed Transforms**](https://developers.cloudflare.com/rules/transform/managed-transforms/): Perform common adjustments to HTTP request and response headers with the click of a button.
For more complex header modifications and rewrite logic, consider using [Snippets](https://developers.cloudflare.com/rules/snippets/).
Note
Transform Rules require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
## Get started
Cloudflare provides you with rules templates for common use cases.
1. In the Cloudflare dashboard, go to the Rules **Overview** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview)
2. Select **Templates**, and then select one of the available templates.
You can also refer to the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in the developer docs.
Alternatively, create a transform rule from scratch in the dashboard or via Cloudflare API. Refer to the following sections for detailed instructions:
* [URL Rewrite Rules](https://developers.cloudflare.com/rules/transform/url-rewrite/)
* [Request Header Transform Rules](https://developers.cloudflare.com/rules/transform/request-header-modification/)
* [Response Header Transform Rules](https://developers.cloudflare.com/rules/transform/response-header-modification/)
* [Managed Transforms](https://developers.cloudflare.com/rules/transform/managed-transforms/)
For Terraform examples, refer to [Transform Rules configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/transform-rules/).
Refer to [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/) for more information on building expressions for Transform Rules.
## Availability
Cloudflare Transform Rules are available to all customers. Support for regular expressions depends on your Cloudflare plan.
This table outlines the Transform Rules features available with each customer plan:
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Active Transform Rules | 10 | 25 | 50 | 300 |
| Regex support | No | No | Yes | Yes |
A Cloudflare user must have the [Firewall role](https://developers.cloudflare.com/fundamentals/manage-members/roles/) or one of the Administrator roles to access Transform Rules.
## Transform Rules evaluation
Managed Transforms run before other types of Transform Rules that modify HTTP headers:
* Managed Transforms that adjust HTTP request headers run before Request Header Transform Rules.
* Managed Transforms that adjust HTTP response headers run before Response Header Transform Rules.
Transform Rules run in order. Rules that appear later in the list of Transform Rules can overwrite changes done by previous rules. You can define the rule order in the dashboard or via API.
Request and response fields are immutable within each [phase](https://developers.cloudflare.com/ruleset-engine/about/phases/) while evaluating Transform Rules for a request/response. For more information, refer to [Field values during rule evaluation](https://developers.cloudflare.com/ruleset-engine/about/rules/#field-values-during-rule-evaluation).
Warning
Using Cloudflare challenges along with Rules features such as Transform Rules may cause challenge loops. Refer to [Rules troubleshooting](https://developers.cloudflare.com/rules/reference/troubleshooting/) for more information.
## Troubleshooting
When troubleshooting Transform Rules, use [Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/) to determine if a rule is triggering for a specific URL.
</page>
<page>
---
title: Redirects · Cloudflare Rules docs
description: URL forwarding, also known as URL redirection, navigates the user
from a source URL to a target URL with a specific HTTP status code.
lastUpdated: 2025-10-06T10:46:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/rules/url-forwarding/
md: https://developers.cloudflare.com/rules/url-forwarding/index.md
---
URL forwarding, also known as URL redirection, navigates the user from a source URL to a target URL with a specific HTTP status code.
Use the following Cloudflare products to perform URL redirects, according to your use case:
* [**Single Redirects**](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/): Allow you to create static or dynamic redirects at the zone level. A simple interface with [wildcard support](https://developers.cloudflare.com/ruleset-engine/rules-language/operators/#wildcard-matching) lets you easily define source and target URL patterns without needing complex functions or regular expressions, efficiently covering thousands of URLs with a single rule.
* [**Bulk Redirects**](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/): Allow you to define a large number of redirects at the account level. These URL redirects are essentially static — they do not support string replacement operations or regular expressions. However, you can configure parameters that affect the redirects' URL matching behavior and their runtime behavior.
* [**Snippets**](https://developers.cloudflare.com/rules/snippets/): Use short pieces of JavaScript code for a more flexible way to define complex redirect functionality. Consider a few [examples](https://developers.cloudflare.com/rules/snippets/examples/?operation=Redirect) to get started.
Note
Single Redirects and Bulk Redirects require that you [proxy the DNS records](https://developers.cloudflare.com/dns/proxy-status/) of your domain (or subdomain) through Cloudflare.
## Redirect Rules templates
Cloudflare provides you with rules templates for common use cases.
1. In the Cloudflare dashboard, go to the Rules **Overview** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/:zone/rules/overview)
2. Select **Templates**, and then select one of the available templates.
You can also refer to the [Examples gallery](https://developers.cloudflare.com/rules/examples/) in the developer docs.
## Availability
Single Redirects and Bulk Redirects are available on all Cloudflare plans. The exact quotas and features depend on your plan.
### Bulk redirects
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Bulk Redirect Rules | 15 | 15 | 15 | 50 |
| Bulk Redirect Lists | 5 | 5 | 5 | 25 |
| URL redirects across lists | 10,000 | 25,000 | 50,000 | 1,000,000 |
For *URL redirects across lists*, this table provides the default quota for the Enterprise plan. Bulk Redirects supports several million URL redirects — to get more redirects, contact your account team.
Bulk Redirects features and quotas are per account and they depend on the highest Cloudflare plan on your account.
### Single Redirects
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 10 | 25 | 50 | 300 |
| Wildcard support | Yes | Yes | Yes | Yes |
| Regex support | No | No | Yes | Yes |
Single Redirects features and quotas are per zone and depend on the zone plan.
## Execution order
The execution order of Rules features is the following:
* [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/)
* [URL Rewrite Rules](https://developers.cloudflare.com/rules/transform/url-rewrite/)
* [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/)
* [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/)
* [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/)
* [Managed Transforms](https://developers.cloudflare.com/rules/transform/managed-transforms/)
* [Request Header Transform Rules](https://developers.cloudflare.com/rules/transform/request-header-modification/)
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/)
* [Snippets](https://developers.cloudflare.com/rules/snippets/)
* [Cloud Connector](https://developers.cloudflare.com/rules/cloud-connector/)
The different types of rules listed above will take precedence over [Page Rules](https://developers.cloudflare.com/rules/page-rules/). This means that Page Rules will be overridden if there is a match for both Page Rules and the Rules products listed above.
Generally speaking, for [non-terminating actions](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/) the last change made by rules in the same [phase](https://developers.cloudflare.com/ruleset-engine/about/phases/) will win (later rules can overwrite changes done by previous rules). However, for terminating actions (*Block*, *Redirect*, or one of the challenge actions), rule evaluation will stop and the action will be executed immediately.
For example, if multiple rules with the *Redirect* action match, Cloudflare will always use the URL redirect of the first rule that matches. Also, if you configure URL redirects using different Cloudflare products (Single Redirects and Bulk Redirects), the product executed first will apply, if there is a rule match (in this case, Single Redirects).
Refer to the [Phases list](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/) for the product execution order.
Warning
Using Cloudflare challenges along with Rules features may cause challenge loops. Refer to [Rules troubleshooting](https://developers.cloudflare.com/rules/reference/troubleshooting/) for more information.
## Troubleshooting
When troubleshooting URL redirects, use [Cloudflare Trace](https://developers.cloudflare.com/rules/trace-request/) to determine if a rule is triggering for a specific URL.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Ruleset Engine docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ruleset-engine/404/
md: https://developers.cloudflare.com/ruleset-engine/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: About Ruleset Engine · Cloudflare Ruleset Engine docs
description: The Cloudflare Ruleset Engine allows you to create and deploy rules
and rulesets. The engine syntax, inspired by the Wireshark Display Filter
language, is defined by the Rules language. Cloudflare uses the Ruleset Engine
in different products, allowing you to configure several products using the
same basic syntax.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ruleset-engine/about/
md: https://developers.cloudflare.com/ruleset-engine/about/index.md
---
The Cloudflare Ruleset Engine allows you to create and deploy rules and rulesets. The engine syntax, inspired by the Wireshark Display Filter language, is defined by the [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/). Cloudflare uses the Ruleset Engine in different products, allowing you to configure several products using the same basic syntax.
There are several elements involved in the configuration and use of the Ruleset Engine. These elements are:
* [**Phase**](https://developers.cloudflare.com/ruleset-engine/about/phases/): Defines a stage in the life of a request where you can execute rulesets.
* [**Ruleset**](https://developers.cloudflare.com/ruleset-engine/about/rulesets/): Defines a versioned set of rules. You deploy rulesets to a phase, where they execute.
* [**Rule**](https://developers.cloudflare.com/ruleset-engine/about/rules/): Defines a filter and an action to perform on incoming requests that match the filter expression. A rule with an `execute` action executes a ruleset.
***
## Get started
To view existing rulesets and their properties, refer to [View rulesets](https://developers.cloudflare.com/ruleset-engine/basic-operations/view-rulesets/).
For more information on deploying managed rulesets and defining overrides, refer to [Work with managed rulesets](https://developers.cloudflare.com/ruleset-engine/managed-rulesets/).
For more information on creating and deploying custom rulesets, refer to [Work with custom rulesets](https://developers.cloudflare.com/ruleset-engine/custom-rulesets/).
</page>
<page>
---
title: Basic API operations · Cloudflare Ruleset Engine docs
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ruleset-engine/basic-operations/
md: https://developers.cloudflare.com/ruleset-engine/basic-operations/index.md
---
* [View rulesets](https://developers.cloudflare.com/ruleset-engine/basic-operations/view-rulesets/)
* [Add rules to phase entry point rulesets](https://developers.cloudflare.com/ruleset-engine/basic-operations/add-rule-phase-rulesets/)
* [Deploy rulesets](https://developers.cloudflare.com/ruleset-engine/basic-operations/deploy-rulesets/)
</page>
<page>
---
title: Work with custom rulesets · Cloudflare Ruleset Engine docs
description: "Use the following workflow to deploy a custom ruleset:"
lastUpdated: 2025-12-23T12:15:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ruleset-engine/custom-rulesets/
md: https://developers.cloudflare.com/ruleset-engine/custom-rulesets/index.md
---
Use the following workflow to deploy a custom ruleset:
1. [Create a custom ruleset](https://developers.cloudflare.com/ruleset-engine/custom-rulesets/create-custom-ruleset/), optionally providing a list of rules to include in the custom ruleset.
2. (Optional) [Add rules to your custom ruleset](https://developers.cloudflare.com/ruleset-engine/custom-rulesets/add-rules-ruleset/).
3. [Deploy the custom ruleset](https://developers.cloudflare.com/ruleset-engine/custom-rulesets/deploy-custom-ruleset/) by adding an `execute` rule to a phase entry point ruleset. If you skip this step, the rules of the custom ruleset will not run.
Currently, custom rulesets are only supported by the [Cloudflare WAF](https://developers.cloudflare.com/waf/), both at the account and the zone level.
Note
You cannot execute a custom ruleset from another custom ruleset, only from an [entry point ruleset](https://developers.cloudflare.com/ruleset-engine/about/rulesets/#entry-point-ruleset).
## Change the behavior of a custom ruleset
To modify custom ruleset behavior, Cloudflare recommends [creating a new custom ruleset](https://developers.cloudflare.com/ruleset-engine/custom-rulesets/create-custom-ruleset/) or [editing the custom ruleset](https://developers.cloudflare.com/ruleset-engine/custom-rulesets/add-rules-ruleset/) instead of using overrides.
</page>
<page>
---
title: Work with managed rulesets · Cloudflare Ruleset Engine docs
description: Managed rulesets are preconfigured rulesets provided by Cloudflare
that you can deploy. Only Cloudflare can modify these rulesets.
lastUpdated: 2025-12-23T12:15:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ruleset-engine/managed-rulesets/
md: https://developers.cloudflare.com/ruleset-engine/managed-rulesets/index.md
---
Managed rulesets are preconfigured rulesets provided by Cloudflare that you can deploy. Only Cloudflare can modify these rulesets.
The rules in a managed ruleset have a default configuration. However, you can define [overrides](https://developers.cloudflare.com/ruleset-engine/managed-rulesets/override-managed-ruleset/) that change this default configuration.
Several Cloudflare products include managed rulesets:
* [Web Application Firewall (WAF)](https://developers.cloudflare.com/waf/managed-rules/)
* [DDoS Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/)
* [Magic Firewall](https://developers.cloudflare.com/magic-firewall/how-to/enable-managed-rulesets/)
Check each product's documentation for details on the available managed rulesets.
## More resources
To view available managed rulesets, refer to [View rulesets](https://developers.cloudflare.com/ruleset-engine/basic-operations/view-rulesets/).
To deploy a managed ruleset to a phase, refer to [Deploy a managed ruleset](https://developers.cloudflare.com/ruleset-engine/managed-rulesets/deploy-managed-ruleset/).
To adjust the behavior of a managed ruleset, do one of the following:
* Customize the behavior of one or more rules by using [overrides](https://developers.cloudflare.com/ruleset-engine/managed-rulesets/override-managed-ruleset/).
* Skip one or more managed rules by adding [exceptions](https://developers.cloudflare.com/ruleset-engine/managed-rulesets/create-exception/).
Exceptions (only supported by the WAF) have priority over overrides.
</page>
<page>
---
title: Ruleset Engine reference · Cloudflare Ruleset Engine docs
description: "The following pages include additional information about the Ruleset Engine:"
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ruleset-engine/reference/
md: https://developers.cloudflare.com/ruleset-engine/reference/index.md
---
The following pages include additional information about the Ruleset Engine:
* [Phases list](https://developers.cloudflare.com/ruleset-engine/reference/phases-list/)
</page>
<page>
---
title: Rules language · Cloudflare Ruleset Engine docs
description: The Cloudflare Rules language is a flexible and intuitive
specification for building rule expressions. Based on the widely known
Wireshark display filters, the Rules language allows you to precisely target
HTTP requests with a syntax and semantics familiar to security engineers.
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ruleset-engine/rules-language/
md: https://developers.cloudflare.com/ruleset-engine/rules-language/index.md
---
The Cloudflare Rules language is a flexible and intuitive specification for building rule expressions. Based on the widely known [Wireshark display filters](https://www.wireshark.org/docs/wsug_html_chunked/ChWorkBuildDisplayFilterSection.html), the Rules language allows you to precisely target HTTP requests with a syntax and semantics familiar to security engineers.
Refer to the following pages for more information about the available language elements:
* [Expressions](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/)
* [Operators and grouping symbols](https://developers.cloudflare.com/ruleset-engine/rules-language/operators/)
* [Values](https://developers.cloudflare.com/ruleset-engine/rules-language/values/)
* [Actions](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/)
* [Fields](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/)
* [Functions](https://developers.cloudflare.com/ruleset-engine/rules-language/functions/)
</page>
<page>
---
title: Rulesets API · Cloudflare Ruleset Engine docs
description: The Rulesets API provides an interface for managing and configuring
the execution of rulesets, supporting different Cloudflare products powered by
the Ruleset Engine.
lastUpdated: 2025-12-23T12:15:33.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ruleset-engine/rulesets-api/
md: https://developers.cloudflare.com/ruleset-engine/rulesets-api/index.md
---
The Rulesets API provides an interface for managing and configuring the execution of rulesets, supporting different Cloudflare products powered by the Ruleset Engine.
## Get started
To get started, review the [JSON objects](https://developers.cloudflare.com/ruleset-engine/rulesets-api/json-object/) and the available [endpoints](https://developers.cloudflare.com/ruleset-engine/rulesets-api/endpoints/).
***
## Limits
You should avoid making concurrent updates to the same ruleset. There are rate limits in place to prevent the same ruleset from being concurrently updated too many times. The exact limits depend on the size of the ruleset and volume of requests, and can be different for each ruleset.
The rate limits are most frequently hit when concurrently modifying several rules in the same ruleset. To avoid this, you should [update the entire ruleset in a single operation](https://developers.cloudflare.com/ruleset-engine/rulesets-api/update/) instead.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Sandbox SDK docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/404/
md: https://developers.cloudflare.com/sandbox/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: API Reference · Cloudflare Sandbox SDK docs
description: The Sandbox SDK provides a comprehensive API for executing code,
managing files, running processes, and exposing services in isolated
sandboxes.
lastUpdated: 2026-02-06T17:10:29.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/api/
md: https://developers.cloudflare.com/sandbox/api/index.md
---
The Sandbox SDK provides a comprehensive API for executing code, managing files, running processes, and exposing services in isolated sandboxes.
[Lifecycle](https://developers.cloudflare.com/sandbox/api/lifecycle/)
Create and manage sandbox containers. Get sandbox instances, configure options, and clean up resources.
[Commands](https://developers.cloudflare.com/sandbox/api/commands/)
Execute commands and stream output. Run scripts, manage background processes, and capture execution results.
[Files](https://developers.cloudflare.com/sandbox/api/files/)
Read, write, and manage files in the sandbox filesystem. Includes directory operations and file metadata.
[File Watching](https://developers.cloudflare.com/sandbox/api/file-watching/)
Monitor real-time filesystem changes using native inotify. Build development tools, hot-reload systems, and responsive file processing.
[Code Interpreter](https://developers.cloudflare.com/sandbox/api/interpreter/)
Execute Python and JavaScript code with rich outputs including charts, tables, and formatted data.
[Ports](https://developers.cloudflare.com/sandbox/api/ports/)
Expose services running in the sandbox via preview URLs. Access web servers and APIs from the internet.
[Storage](https://developers.cloudflare.com/sandbox/api/storage/)
Mount S3-compatible buckets (R2, S3, GCS) as local filesystems for persistent data storage across sandbox lifecycles.
[Sessions](https://developers.cloudflare.com/sandbox/api/sessions/)
Create isolated execution contexts within a sandbox. Each session maintains its own shell state, environment variables, and working directory.
</page>
<page>
---
title: Concepts · Cloudflare Sandbox SDK docs
description: These pages explain how the Sandbox SDK works, why it's designed
the way it is, and the concepts you need to understand to use it effectively.
lastUpdated: 2025-10-21T14:02:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/concepts/
md: https://developers.cloudflare.com/sandbox/concepts/index.md
---
These pages explain how the Sandbox SDK works, why it's designed the way it is, and the concepts you need to understand to use it effectively.
* [Architecture](https://developers.cloudflare.com/sandbox/concepts/architecture/) - How the SDK is structured and why
* [Sandbox lifecycle](https://developers.cloudflare.com/sandbox/concepts/sandboxes/) - Understanding sandbox states and behavior
* [Container runtime](https://developers.cloudflare.com/sandbox/concepts/containers/) - How code executes in isolated containers
* [Session management](https://developers.cloudflare.com/sandbox/concepts/sessions/) - When and how to use sessions
* [Preview URLs](https://developers.cloudflare.com/sandbox/concepts/preview-urls/) - How service exposure works
* [Security model](https://developers.cloudflare.com/sandbox/concepts/security/) - Isolation, validation, and safety mechanisms
## Related resources
* [Tutorials](https://developers.cloudflare.com/sandbox/tutorials/) - Learn by building complete applications
* [How-to guides](https://developers.cloudflare.com/sandbox/guides/) - Solve specific problems
* [API reference](https://developers.cloudflare.com/sandbox/api/) - Technical details and method signatures
</page>
<page>
---
title: Configuration · Cloudflare Sandbox SDK docs
description: Configure your Sandbox SDK deployment with Wrangler, customize
container images, and manage environment variables.
lastUpdated: 2025-10-28T17:02:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/configuration/
md: https://developers.cloudflare.com/sandbox/configuration/index.md
---
Configure your Sandbox SDK deployment with Wrangler, customize container images, and manage environment variables.
[Wrangler configuration](https://developers.cloudflare.com/sandbox/configuration/wrangler/)
Configure Durable Objects bindings, container images, and Worker settings in wrangler.jsonc.
[Dockerfile reference](https://developers.cloudflare.com/sandbox/configuration/dockerfile/)
Customize the sandbox container image with your own packages, tools, and configurations.
[Environment variables](https://developers.cloudflare.com/sandbox/configuration/environment-variables/)
Pass configuration and secrets to your sandboxes using environment variables.
[Sandbox options](https://developers.cloudflare.com/sandbox/configuration/sandbox-options/)
Configure sandbox behavior with options like `keepAlive` for long-running processes.
## Related resources
* [Get Started guide](https://developers.cloudflare.com/sandbox/get-started/) - Initial setup walkthrough
* [Wrangler documentation](https://developers.cloudflare.com/workers/wrangler/) - Complete Wrangler reference
* [Docker documentation](https://docs.docker.com/engine/reference/builder/) - Dockerfile syntax
* [Security model](https://developers.cloudflare.com/sandbox/concepts/security/) - Understanding environment isolation
</page>
<page>
---
title: Getting started · Cloudflare Sandbox SDK docs
description: Build your first application with Sandbox SDK - a secure code
execution environment. In this guide, you'll create a Worker that can execute
Python code and work with files in isolated containers.
lastUpdated: 2026-02-06T17:12:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/get-started/
md: https://developers.cloudflare.com/sandbox/get-started/index.md
---
Build your first application with Sandbox SDK - a secure code execution environment. In this guide, you'll create a Worker that can execute Python code and work with files in isolated containers.
What you're building
A simple API that can safely execute Python code and perform file operations in isolated sandbox environments.
## Prerequisites
1. Sign up for a [Cloudflare account](https://dash.cloudflare.com/sign-up/workers-and-pages).
2. Install [`Node.js`](https://docs.npmjs.com/downloading-and-installing-node-js-and-npm).
Node.js version manager
Use a Node version manager like [Volta](https://volta.sh/) or [nvm](https://github.com/nvm-sh/nvm) to avoid permission issues and change Node.js versions. [Wrangler](https://developers.cloudflare.com/workers/wrangler/install-and-update/), discussed later in this guide, requires a Node version of `16.17.0` or later.
### Ensure Docker is running locally
Sandbox SDK uses [Docker](https://www.docker.com/) to build container images alongside your Worker.
You must have Docker running locally when you run `wrangler deploy`. For most people, the best way to install Docker is to follow the [docs for installing Docker Desktop](https://docs.docker.com/desktop/). Other tools like [Colima](https://github.com/abiosoft/colima) may also work.
You can check that Docker is running properly by running the `docker info` command in your terminal. If Docker is running, the command will succeed. If Docker is not running, the `docker info` command will hang or return an error including the message "Cannot connect to the Docker daemon".
## 1. Create a new project
Create a new Sandbox SDK project:
* npm
```sh
npm create cloudflare@latest -- my-sandbox --template=cloudflare/sandbox-sdk/examples/minimal
```
* yarn
```sh
yarn create cloudflare my-sandbox --template=cloudflare/sandbox-sdk/examples/minimal
```
* pnpm
```sh
pnpm create cloudflare@latest my-sandbox --template=cloudflare/sandbox-sdk/examples/minimal
```
This creates a `my-sandbox` directory with everything you need:
* `src/index.ts` - Worker with sandbox integration
* `wrangler.jsonc` - Configuration for Workers and Containers
* `Dockerfile` - Container environment definition
```sh
cd my-sandbox
```
## 2. Explore the template
The template provides a minimal Worker that demonstrates core sandbox capabilities:
```typescript
import { getSandbox, proxyToSandbox, type Sandbox } from "@cloudflare/sandbox";
export { Sandbox } from "@cloudflare/sandbox";
type Env = {
Sandbox: DurableObjectNamespace<Sandbox>;
};
export default {
async fetch(request: Request, env: Env): Promise<Response> {
const url = new URL(request.url);
// Get or create a sandbox instance
const sandbox = getSandbox(env.Sandbox, "my-sandbox");
// Execute Python code
if (url.pathname === "/run") {
const result = await sandbox.exec('python3 -c "print(2 + 2)"');
return Response.json({
output: result.stdout,
error: result.stderr,
exitCode: result.exitCode,
success: result.success,
});
}
// Work with files
if (url.pathname === "/file") {
await sandbox.writeFile("/workspace/hello.txt", "Hello, Sandbox!");
const file = await sandbox.readFile("/workspace/hello.txt");
return Response.json({
content: file.content,
});
}
return new Response("Try /run or /file");
},
};
```
**Key concepts**:
* `getSandbox()` - Gets or creates a sandbox instance by ID. Use the same ID to reuse the same sandbox instance across requests.
* `sandbox.exec()` - Execute shell commands in the sandbox and capture stdout, stderr, and exit codes.
* `sandbox.writeFile()` / `readFile()` - Write and read files in the sandbox filesystem.
## 3. Test locally
Start the development server:
```sh
npm run dev
# If you expect to have multiple sandbox instances, you can increase `max_instances`.
```
Note
First run builds the Docker container (2-3 minutes). Subsequent runs are much faster due to caching.
Test the endpoints:
```sh
# Execute Python code
curl http://localhost:8787/run
# File operations
curl http://localhost:8787/file
```
You should see JSON responses with the command output and file contents.
## 4. Deploy to production
Deploy your Worker and container:
```sh
npx wrangler deploy
```
This will:
1. Build your container image using Docker
2. Push it to Cloudflare's Container Registry
3. Deploy your Worker globally
Wait for provisioning
After first deployment, wait 2-3 minutes before making requests. The Worker deploys immediately, but the container needs time to provision.
Check deployment status:
```sh
npx wrangler containers list
```
## 5. Test your deployment
Visit your Worker URL (shown in deploy output):
```sh
# Replace with your actual URL
curl https://my-sandbox.YOUR_SUBDOMAIN.workers.dev/run
```
Your sandbox is now deployed and can execute code in isolated containers.
Preview URLs require custom domain
If you plan to expose ports from sandboxes (using `exposePort()` for preview URLs), you will need to set up a custom domain with wildcard DNS routing. The `.workers.dev` domain does not support the subdomain patterns required for preview URLs. See [Production Deployment](https://developers.cloudflare.com/sandbox/guides/production-deployment/) when you are ready to expose services.
## Understanding the configuration
Your `wrangler.jsonc` connects three pieces together:
* wrangler.jsonc
```jsonc
{
"containers": [
{
"class_name": "Sandbox",
"image": "./Dockerfile",
"instance_type": "lite",
"max_instances": 1,
},
],
"durable_objects": {
"bindings": [
{
"class_name": "Sandbox",
"name": "Sandbox",
},
],
},
"migrations": [
{
"new_sqlite_classes": ["Sandbox"],
"tag": "v1",
},
],
}
```
* wrangler.toml
```toml
[[containers]]
class_name = "Sandbox"
image = "./Dockerfile"
instance_type = "lite"
max_instances = 1
[[durable_objects.bindings]]
class_name = "Sandbox"
name = "Sandbox"
[[migrations]]
new_sqlite_classes = [ "Sandbox" ]
tag = "v1"
```
- **containers** - Defines the [container image, instance type, and resource limits](https://developers.cloudflare.com/workers/wrangler/configuration/#containers) for your sandbox environment. If you expect to have multiple sandbox instances, you can increase `max_instances`.
- **durable\_objects** - You need not be familiar with [Durable Objects](https://developers.cloudflare.com/durable-objects) to use Sandbox SDK, but if you'd like, you can [learn more about Cloudflare Containers and Durable Objects](https://developers.cloudflare.com/containers/get-started/#each-container-is-backed-by-its-own-durable-object). This configuration creates a [binding](https://developers.cloudflare.com/workers/runtime-apis/bindings#what-is-a-binding) that makes the `Sandbox` Durable Object accessible in your Worker code.
- **migrations** - Registers the `Sandbox` class, implemented by the Sandbox SDK, with [SQLite storage backend](https://developers.cloudflare.com/durable-objects/best-practices/access-durable-objects-storage) (required once)
For detailed configuration options including environment variables, secrets, and custom images, see the [Wrangler configuration reference](https://developers.cloudflare.com/sandbox/configuration/wrangler/).
## Next steps
Now that you have a working sandbox, explore more capabilities:
* [Code interpreter with Workers AI](https://developers.cloudflare.com/sandbox/tutorials/workers-ai-code-interpreter/) - Build an AI-powered code execution system
* [Execute commands](https://developers.cloudflare.com/sandbox/guides/execute-commands/) - Run shell commands and stream output
* [Manage files](https://developers.cloudflare.com/sandbox/guides/manage-files/) - Work with files and directories
* [Expose services](https://developers.cloudflare.com/sandbox/guides/expose-services/) - Get public URLs for services running in your sandbox
* [Production Deployment](https://developers.cloudflare.com/sandbox/guides/production-deployment/) - Set up custom domains for preview URLs
* [API reference](https://developers.cloudflare.com/sandbox/api/) - Complete API documentation
</page>
<page>
---
title: How-to guides · Cloudflare Sandbox SDK docs
description: These guides show you how to solve specific problems and implement
features with the Sandbox SDK. Each guide focuses on a particular task and
provides practical, production-ready solutions.
lastUpdated: 2025-10-21T14:02:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/guides/
md: https://developers.cloudflare.com/sandbox/guides/index.md
---
These guides show you how to solve specific problems and implement features with the Sandbox SDK. Each guide focuses on a particular task and provides practical, production-ready solutions.
[Run background processes](https://developers.cloudflare.com/sandbox/guides/background-processes/)
[Start and manage long-running services and applications.](https://developers.cloudflare.com/sandbox/guides/background-processes/)
[Use code interpreter](https://developers.cloudflare.com/sandbox/guides/code-execution/)
[Execute Python and JavaScript code with rich outputs.](https://developers.cloudflare.com/sandbox/guides/code-execution/)
[Execute commands](https://developers.cloudflare.com/sandbox/guides/execute-commands/)
[Run commands with streaming output, error handling, and shell access.](https://developers.cloudflare.com/sandbox/guides/execute-commands/)
[Expose services](https://developers.cloudflare.com/sandbox/guides/expose-services/)
[Create preview URLs and expose ports for web services.](https://developers.cloudflare.com/sandbox/guides/expose-services/)
[Watch filesystem changes](https://developers.cloudflare.com/sandbox/guides/file-watching/)
[Monitor files and directories in real-time to build responsive development tools and automation workflows.](https://developers.cloudflare.com/sandbox/guides/file-watching/)
[Work with Git](https://developers.cloudflare.com/sandbox/guides/git-workflows/)
[Clone repositories, manage branches, and automate Git operations.](https://developers.cloudflare.com/sandbox/guides/git-workflows/)
[Manage files](https://developers.cloudflare.com/sandbox/guides/manage-files/)
[Read, write, organize, and synchronize files in the sandbox.](https://developers.cloudflare.com/sandbox/guides/manage-files/)
[Mount buckets](https://developers.cloudflare.com/sandbox/guides/mount-buckets/)
[Mount S3-compatible object storage as local filesystems for persistent data storage.](https://developers.cloudflare.com/sandbox/guides/mount-buckets/)
[Deploy to Production](https://developers.cloudflare.com/sandbox/guides/production-deployment/)
[Set up custom domains for preview URLs in production.](https://developers.cloudflare.com/sandbox/guides/production-deployment/)
[WebSocket Connections](https://developers.cloudflare.com/sandbox/guides/websocket-connections/)
[Connect to WebSocket servers running in sandboxes.](https://developers.cloudflare.com/sandbox/guides/websocket-connections/)
[Stream output](https://developers.cloudflare.com/sandbox/guides/streaming-output/)
[Handle real-time output from commands and processes.](https://developers.cloudflare.com/sandbox/guides/streaming-output/)
## Related resources
* [Tutorials](https://developers.cloudflare.com/sandbox/tutorials/) - Step-by-step learning paths
* [API reference](https://developers.cloudflare.com/sandbox/api/) - Complete method documentation
</page>
<page>
---
title: Platform · Cloudflare Sandbox SDK docs
description: Information about the Sandbox SDK platform, including pricing,
limits, and beta status.
lastUpdated: 2025-10-15T17:28:03.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/platform/
md: https://developers.cloudflare.com/sandbox/platform/index.md
---
Information about the Sandbox SDK platform, including pricing, limits, and beta status.
## Available resources
* [Pricing](https://developers.cloudflare.com/sandbox/platform/pricing/) - Understand costs based on the Containers platform
* [Limits](https://developers.cloudflare.com/sandbox/platform/limits/) - Resource limits and best practices
* [Beta Information](https://developers.cloudflare.com/sandbox/platform/beta-info/) - Current status and roadmap
Since Sandbox SDK is built on [Containers](https://developers.cloudflare.com/containers/), it shares the same underlying platform characteristics. Refer to these pages to understand how pricing and limits work for your sandbox deployments.
</page>
<page>
---
title: Tutorials · Cloudflare Sandbox SDK docs
description: Learn how to build applications with Sandbox SDK through
step-by-step tutorials. Each tutorial takes 20-30 minutes.
lastUpdated: 2025-10-21T14:02:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/sandbox/tutorials/
md: https://developers.cloudflare.com/sandbox/tutorials/index.md
---
Learn how to build applications with Sandbox SDK through step-by-step tutorials. Each tutorial takes 20-30 minutes.
[Code interpreter with Workers AI](https://developers.cloudflare.com/sandbox/tutorials/workers-ai-code-interpreter/)
[Build a code interpreter using Workers AI GPT-OSS model with the official workers-ai-provider package.](https://developers.cloudflare.com/sandbox/tutorials/workers-ai-code-interpreter/)
[Data persistence with R2](https://developers.cloudflare.com/sandbox/tutorials/persistent-storage/)
[Mount R2 buckets as local filesystem paths to persist data across sandbox lifecycles.](https://developers.cloudflare.com/sandbox/tutorials/persistent-storage/)
[Run Claude Code on a Sandbox](https://developers.cloudflare.com/sandbox/tutorials/claude-code/)
[Use Claude Code to implement a task in your GitHub repository.](https://developers.cloudflare.com/sandbox/tutorials/claude-code/)
[Build an AI code executor](https://developers.cloudflare.com/sandbox/tutorials/ai-code-executor/)
[Use Claude to generate Python code from natural language and execute it securely in sandboxes.](https://developers.cloudflare.com/sandbox/tutorials/ai-code-executor/)
[Automated testing pipeline](https://developers.cloudflare.com/sandbox/tutorials/automated-testing-pipeline/)
[Build a testing pipeline that clones Git repositories, installs dependencies, runs tests, and reports results.](https://developers.cloudflare.com/sandbox/tutorials/automated-testing-pipeline/)
[Analyze data with AI](https://developers.cloudflare.com/sandbox/tutorials/analyze-data-with-ai/)
[Upload CSV files, generate analysis code with Claude, and return visualizations.](https://developers.cloudflare.com/sandbox/tutorials/analyze-data-with-ai/)
[Build a code review bot](https://developers.cloudflare.com/sandbox/tutorials/code-review-bot/)
[Clone repositories, analyze code with Claude, and post review comments to GitHub PRs.](https://developers.cloudflare.com/sandbox/tutorials/code-review-bot/)
## Before you start
All tutorials assume you have:
* Completed the [Get Started guide](https://developers.cloudflare.com/sandbox/get-started/)
* Basic familiarity with [Workers](https://developers.cloudflare.com/workers/)
* [Docker](https://www.docker.com/) installed and running
## Related resources
* [How-to guides](https://developers.cloudflare.com/sandbox/guides/) - Solve specific problems
* [API reference](https://developers.cloudflare.com/sandbox/api/) - Complete SDK reference
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Secrets Store docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/secrets-store/404/
md: https://developers.cloudflare.com/secrets-store/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Secrets Store access control · Cloudflare Secrets Store docs
description: Learn about role-based access control with Cloudflare Secrets Store
lastUpdated: 2025-09-03T14:48:22.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/secrets-store/access-control/
md: https://developers.cloudflare.com/secrets-store/access-control/index.md
---
Secrets Store allows security administrators to have more control by implementing role-based access. For details about roles at Cloudflare, refer to [Fundamentals](https://developers.cloudflare.com/fundamentals/manage-members/).
Availability
While all Cloudflare accounts will have access to the Secrets Store section on the dashboard, only users with the necessary permissions will be able to interact with it, as described below.
## Relevant roles
Refer to the list below for default role definitions.
#### Super Administrator
* Can create, edit, duplicate, delete, and view secrets metadata.
* Can [add a Secrets Store binding to a Worker](https://developers.cloudflare.com/secrets-store/integrations/workers/).
* Can [create an association between a secret and an AI gateway](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/).
#### Secrets Store Admin
* Can create, edit, duplicate, delete, and view secrets metadata.
#### Secrets Store Deployer
* Can view secrets metadata but cannot create, edit, duplicate, nor delete secrets.
* Can [add a Secrets Store binding to a Worker](https://developers.cloudflare.com/secrets-store/integrations/workers/).
* Can [create an association between a secret and an AI gateway](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/).
#### Secrets Store Reporter
* Can view secrets metadata.
* Cannot perform any actions (create, edit, duplicate, delete secrets), nor use Secrets Store integrations with other Cloudflare products.
## API token permissions
The following API token permissions can also be used to grant access to Secrets Store resources.
* **Account Secrets Store Edit**: Allows a user to create, edit, duplicate, or delete secrets.
* **Account Secrets Store Read**: Allows a user to view secrets metadata.
</page>
<page>
---
title: Audit logs · Cloudflare Secrets Store docs
description: Audit logs provide a comprehensive summary of changes made within
your Cloudflare account. This page lists the actions that are logged for
Secrets Store.
lastUpdated: 2025-05-29T18:16:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/secrets-store/audit-logs/
md: https://developers.cloudflare.com/secrets-store/audit-logs/index.md
---
[Audit logs](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/) provide a comprehensive summary of changes made within your Cloudflare account. This page lists the actions that are logged for Secrets Store.
* Access
* Create
* Duplicating a secret is presented as a `create` log with a field `duplicated_from_id`.
* Update
* A boolean `"value_modified": true` is presented when the secret value is edited.
* Delete
For information on how to access and use audit logs, refer to [Fundamentals](https://developers.cloudflare.com/fundamentals/account/account-security/review-audit-logs/).
</page>
<page>
---
title: Secrets Store integrations · Cloudflare Secrets Store docs
lastUpdated: 2025-04-08T22:03:50.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/secrets-store/integrations/
md: https://developers.cloudflare.com/secrets-store/integrations/index.md
---
* [Workers integration](https://developers.cloudflare.com/secrets-store/integrations/workers/)
* [AI Gateway integration](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/)
</page>
<page>
---
title: Manage account secrets · Cloudflare Secrets Store docs
description: Learn about different operations to manage your secrets in
Cloudflare Secrets Store.
lastUpdated: 2025-05-23T15:11:34.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/secrets-store/manage-secrets/
md: https://developers.cloudflare.com/secrets-store/manage-secrets/index.md
---
Secrets can be API tokens, public/private keys, authorization keys, passwords, or even code variables. The only limitation is that a secret must be a string that does not exceed 1024 bytes.
Once a secret is added to the Secrets Store, it can no longer be decrypted or accessed via API or on the dashboard. Only the service associated with a given secret will be able to access it.
## Limits
Customers who create a secrets store in the open beta can have up to 100 secrets per account. Also, there can only be one store per account.
Production secrets
If you use [Wrangler](https://developers.cloudflare.com/secrets-store/manage-secrets/how-to/#manage-via-wrangler), there is a difference between production secrets and secrets that are only created locally (without the `--remote` flag). The limit of 100 secrets per account only considers production secrets.
## Resources
* [Manage via Wrangler](https://developers.cloudflare.com/workers/wrangler/commands/#secrets-store-secret)
* [Create a secret](https://developers.cloudflare.com/secrets-store/manage-secrets/how-to/#create-a-secret)
* [Duplicate a secret](https://developers.cloudflare.com/secrets-store/manage-secrets/how-to/#duplicate-a-secret)
* [Edit a secret](https://developers.cloudflare.com/secrets-store/manage-secrets/how-to/#edit-a-secret)
* [Delete a secret](https://developers.cloudflare.com/secrets-store/manage-secrets/how-to/#delete-a-secret)
</page>
<page>
---
title: 404 - Page Not Found · Security dashboard docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security/404/
md: https://developers.cloudflare.com/security/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Security Analytics (new dashboard) · Security dashboard docs
description: Security Analytics shows information about all incoming HTTP
requests or mitigated requests (rule matches).
lastUpdated: 2025-10-17T14:13:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security/analytics/
md: https://developers.cloudflare.com/security/analytics/index.md
---
Security Analytics shows information about all incoming HTTP requests or only about requests mitigated by Cloudflare.
Use Security Analytics as your starting point to understand and analyze traffic patterns, and to create security rules based on the filters you applied.
To access Security Analytics in the new security dashboard, go to the **Analytics** page.
[Go to **Analytics**](https://dash.cloudflare.com/?to=/:account/:zone/security/analytics)
By default, Security Analytics queries filter on `requestSource = 'eyeball'`, which represents requests from end users. Note that requests from Cloudflare Workers (subrequests) are not visible in Security Analytics.
## Traffic
The **Traffic** tab displays information about all incoming HTTP requests for your domain, including requests not handled by Cloudflare security products.
In this tab you can perform several tasks:
* View the traffic distribution for your domain.
* Understand which traffic is being mitigated by Cloudflare security products, and where non-mitigated traffic is being served from (Cloudflare global network or [origin server](https://www.cloudflare.com/learning/cdn/glossary/origin-server/)).
* Analyze suspicious traffic and create tailored custom [security rules](https://developers.cloudflare.com/security/rules/) based on applied filters.
* [Find an appropriate rate limit](https://developers.cloudflare.com/waf/rate-limiting-rules/find-rate-limit/) for incoming traffic.
For information on how to use the **Traffic** tab, refer to [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/#adjusting-displayed-data).
If you need to modify existing security-related rules you already configured, consider also using the [Events](#events) tab. This tab displays information about requests affected by Cloudflare security products.
Note
The **Traffic** tab includes functionality available in the [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) page in the previous dashboard navigation structure.
## Events
Use the **Events** tab to review mitigated requests and to tailor your security configurations.
The **Events** tab displays information about requests actioned or flagged by Cloudflare security products. Each incoming HTTP request might generate one or more security events. The tab only shows these events, not the HTTP requests themselves. To obtain information on all incoming HTTP requests, use the [Traffic](#traffic) tab.
Users on a Free plan can view summarized events by date in sampled logs. Customers on paid plans have access to additional graphs and dashboards that summarize the most relevant information about the current behavior of Cloudflare's security features on your domain.
For more information on the **Events** tab, refer to [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/).
Note
The **Events** tab corresponds to the [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/) page in the previous dashboard navigation structure.
</page>
<page>
---
title: Security overview · Security dashboard docs
description: Security overview provides a high-level overview of your domain. It
allows you to identify security action items and review the security posture
of your domain.
lastUpdated: 2025-10-17T14:13:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security/overview/
md: https://developers.cloudflare.com/security/overview/index.md
---
Security overview provides a high-level overview of your domain. It allows you to identify security action items and review the security posture of your domain.
To acess Security overview in the new security dashboard, go to the **Overview** page.
[Go to **Overview**](https://dash.cloudflare.com/?to=/:account/:zone/security/overview)
The Security overview page displays the following information:
* **Traffic last 24 hours** (Free plan only): Allows you to review traffic from the last 24 hours that has been mitigated by Cloudflare.
* **Traffic last 7 days** (paid plans): Allows you to review traffic from the last seven days that has been mitigated by Cloudflare.
* **Security category**: Displays security suggestions categorized by the different types of threats that Cloudflare detects and mitigates.
* **All suggestions**: Displays the full list of available suggestions to improve your security posture.
</page>
<page>
---
title: Security rules · Security dashboard docs
description: Security rules perform security actions on incoming requests that
match specified filters.
lastUpdated: 2025-10-17T14:13:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security/rules/
md: https://developers.cloudflare.com/security/rules/index.md
---
Security rules perform security-related actions on incoming requests that match specified filters. Rules are evaluated and executed in order, from first to last.
To access security rules in the new security dashboard, go to the **Security rules** page.
[Go to **Security rules**](https://dash.cloudflare.com/?to=/:account/:zone/security/security-rules)
## Security rules
The **Security rules** tab includes a list of different types of rules configured in your domain/zone to protect your applications and resources.
To create a security rule:
1. In the Cloudflare dashboard, go to the **Security rules** page.
[Go to **Security rules**](https://dash.cloudflare.com/?to=/:account/:zone/security/security-rules)
2. (Optional) Select **Templates**, and then select a template from the list. You can customize the default configuration of the template before deploying the new rule. Refer to the resources listed in the next step.
3. Select **Create rule** > select the type of rule you want to create. Refer to the following resources about each rule type:
* [Custom rules](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/#rule-form)
* [Rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/create-zone-dashboard/#rule-form)
* [API sequence rules](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/#rule-form)
* [API JWT validation rules](https://developers.cloudflare.com/api-shield/security/jwt-validation/#rule-form) (requires a [token configuration](https://developers.cloudflare.com/security/settings/#all-settings))
* [Managed rules exceptions](https://developers.cloudflare.com/waf/managed-rules/waf-exceptions/define-dashboard/#2-define-basic-exception-parameters)
* [Content security rules](https://developers.cloudflare.com/page-shield/policies/create-dashboard/#rule-form) (previously known as Page Shield policies)
Notes
To deploy a managed ruleset, go to the Security **Settings** page. For more information, refer to [Deploy a managed ruleset](https://developers.cloudflare.com/waf/managed-rules/deploy-zone-dashboard/#deploy-a-managed-ruleset).
The **Security rules** tab includes functionality available in different products in the previous dashboard navigation structure, such as the [WAF](https://developers.cloudflare.com/waf/), [API Shield](https://developers.cloudflare.com/api-shield/), and [Page Shield](https://developers.cloudflare.com/page-shield/).
The tab may show additional rule types if you have configured at least one of the following:
* [IP access rules](https://developers.cloudflare.com/waf/tools/ip-access-rules/)
* [User agent blocking rules](https://developers.cloudflare.com/waf/tools/user-agent-blocking/)
* [Zone lockdown rules](https://developers.cloudflare.com/waf/tools/zone-lockdown/)
## DDoS protection
The **DDoS protection** tab shows the multiple DDoS mitigation services provided by Cloudflare. You can create rules to override these mitigation tools. DDoS attack protection overrides are only available to Enterprise customers with the Advanced DDoS Protection subscription.
To learn more about DDoS protection overrides, refer to the following resources:
* [HTTP DDoS attack protection overrides](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/)
* [Network-layer DDoS attack protection overrides](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/network-overrides/)
Note
You define [overrides for the Network-layer DDoS attack protection managed ruleset](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/network-overrides/configure-dashboard/) at the account level.
</page>
<page>
---
title: Security settings · Security dashboard docs
description: Configure different Cloudflare security features that protect your
web applications, APIs, and resources.
lastUpdated: 2025-10-31T10:10:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security/settings/
md: https://developers.cloudflare.com/security/settings/index.md
---
This page describes the security settings available in the new security dashboard for a given domain.
To access security settings in the new security dashboard, go to the **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
## Security setting categories
Security settings and detection tools are categorized by the type of threat that they detect and mitigate.
### Web application exploits
In the **Web application exploits** security category you can manage the following settings:
* Detection tools:
* [Leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/)
* [Malicious uploads detection](https://developers.cloudflare.com/waf/detections/malicious-uploads/)
* [Sensitive data detection](https://developers.cloudflare.com/waf/managed-rules/reference/sensitive-data-detection/)
* [Cloudflare managed ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/)
* [OWASP Core](https://developers.cloudflare.com/waf/managed-rules/reference/owasp-core-ruleset/) ruleset
* [Firewall for AI](https://developers.cloudflare.com/waf/detections/firewall-for-ai/)
* [Under Attack mode](https://developers.cloudflare.com/fundamentals/reference/under-attack-mode/) in Security Level
* Managed [security.txt](https://developers.cloudflare.com/security-center/infrastructure/security-file/)
Refer to each linked page for details.
Note
The web application exploits security category includes features and settings from the [Cloudflare WAF](https://developers.cloudflare.com/waf/) in the previous dashboard navigation structure.
### DDoS attacks
The **DDoS attacks** security category shows the multiple mitigation services against DDoS attacks provided by Cloudflare.
You can create rules to override DDoS attack protection tools. DDoS attack protection overrides are only available to Enterprise customers with the Advanced DDoS Protection subscription.
To learn more about DDoS protection overrides, refer to the following resources:
* [HTTP DDoS attack protection overrides](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/)
* [Network-layer DDoS attack protection overrides](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/network-overrides/)
Note
You define overrides for the Network-layer DDoS attack protection managed ruleset at the account level in Account Home > **L3/4 DDoS** > **Network-layer DDoS Protection**.
Additionally, you can manage the following settings:
* [Block AI Bots](https://developers.cloudflare.com/bots/concepts/bot/#ai-bots)
* [Bot Management](https://developers.cloudflare.com/bots/get-started/bot-management/) (depending on your Enterprise subscriptions)
* [Browser Integrity Check](https://developers.cloudflare.com/waf/tools/browser-integrity-check/)
* [Challenge Passage](https://developers.cloudflare.com/cloudflare-challenges/challenge-types/challenge-pages/challenge-passage/)
* [Cloudflare managed ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/)
* [Firewall for AI](https://developers.cloudflare.com/waf/detections/firewall-for-ai/)
* [Schema learning](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/schema-learning/)
* [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/) (requires you to upload a schema or apply a learned schema)
* [Under Attack mode](https://developers.cloudflare.com/fundamentals/reference/under-attack-mode/) (under Security Level)
* SSL/TLS DDoS attack protection
### Bot traffic
In the **Bot traffic** security category you can manage the following settings:
* [AI Labyrinth](https://developers.cloudflare.com/bots/additional-configurations/ai-labyrinth/)
* [Block AI Bots](https://developers.cloudflare.com/bots/concepts/bot/#ai-bots)
* [Bot fight mode](https://developers.cloudflare.com/bots/get-started/bot-fight-mode/) (depending on your Cloudflare plan)
* [Super Bot fight mode](https://developers.cloudflare.com/bots/get-started/super-bot-fight-mode/) (depending on your Cloudflare plan)
* [Bot Management](https://developers.cloudflare.com/bots/get-started/bot-management/) (depending on your Enterprise subscriptions)
* AI bot traffic management with [robots.txt](https://developers.cloudflare.com/bots/additional-configurations/managed-robots-txt/)
* API [sequence detection](https://developers.cloudflare.com/api-shield/security/sequence-analytics/) (requires you to configure a session identifier)
Note
The bot traffic security category includes features and settings from [Bots](https://developers.cloudflare.com/bots/) in the previous dashboard navigation structure.
### API abuse
In the **API abuse** security category you can manage the following settings:
* [Developer portal](https://developers.cloudflare.com/api-shield/management-and-monitoring/developer-portal/) creation
* [Endpoint discovery](https://developers.cloudflare.com/api-shield/security/api-discovery/) (always enabled if included in your Enterprise subscriptions; requires you to configure a [session identifier](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/))
* [Endpoint labels](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/)
* [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/) (requires you to add a [JWT configuration](https://developers.cloudflare.com/api-shield/security/jwt-validation/api/#token-configurations))
Note
The API abuse security category includes features and settings from [API Shield](https://developers.cloudflare.com/api-shield/) in the previous dashboard navigation structure.
### Client-side abuse
In the **Client-side abuse** security category you can manage the following settings:
* [Continuous script monitoring](https://developers.cloudflare.com/page-shield/how-it-works/) (previously [Page Shield](https://developers.cloudflare.com/page-shield/)):
* [Reporting endpoint](https://developers.cloudflare.com/page-shield/reference/settings/#reporting-endpoint) to use your hostname instead of a Cloudflare-owned endpoint (only for Enterprise customers with a paid add-on)
* [Data logged in client-side abuse reports](https://developers.cloudflare.com/page-shield/reference/settings/#connection-target-details) (only the hostname or the full URI)
Note
The client-side abuse security category includes features and settings from [Page Shield](https://developers.cloudflare.com/page-shield/) in the previous dashboard navigation structure.
## All settings
The following table links to additional information about each available setting:
| Setting | Location in previous dashboard navigation |
| - | - |
| [AI Labyrinth](https://developers.cloudflare.com/bots/additional-configurations/ai-labyrinth/) | **Security** > **Bots** > **Configure Bot Fight Mode Security** > **Bots** > **Configure Super Bot Fight Mode Security** > **Bots** > **Configure Bot Management** |
| [Block AI Bots](https://developers.cloudflare.com/bots/concepts/bot/#ai-bots) | **Security** > **Bots** > **Configure Bot Fight Mode Security** > **Bots** > **Configure Super Bot Fight Mode Security** > **Bots** > **Configure Bot Management** |
| [Bot Management](https://developers.cloudflare.com/bots/get-started/bot-management/): | **Security** > **Bots** |
| — [JS detections](https://developers.cloudflare.com/bots/additional-configurations/javascript-detections/) | **Security** > **Bots** > **Configure Super Bot Fight Mode Security** > **Bots** > **Configure Bot Management** |
| — [Auto-update machine learning](https://developers.cloudflare.com/bots/reference/machine-learning-models/) | **Security** > **Bots** > **Configure Bot Management** |
| [Browser integrity check](https://developers.cloudflare.com/waf/tools/browser-integrity-check/) | **Security** > **Settings** |
| Challenge Passage: [Timeout](https://developers.cloudflare.com/cloudflare-challenges/challenge-types/challenge-pages/challenge-passage/) | **Security** > **Settings** |
| [Client certificates](https://developers.cloudflare.com/ssl/client-certificates/) | **SSL** > **Client Certificates** |
| [Cloudflare managed ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/) | **Security** > **WAF** > **Managed rules** tab |
| [Continuous script monitoring](https://developers.cloudflare.com/page-shield/how-it-works/): | **Security** > **Page Shield** |
| — [Reporting endpoint](https://developers.cloudflare.com/page-shield/reference/settings/#reporting-endpoint) | **Security** > **Page Shield** > **Settings** |
| — [Data processing](https://developers.cloudflare.com/page-shield/reference/settings/#connection-target-details) | **Security** > **Page Shield** > **Settings** |
| — [Alerts](https://developers.cloudflare.com/page-shield/alerts/configure/) | **Security** > **Page Shield** > **Settings** Account Home > **Notifications** |
| [Create a developer portal](https://developers.cloudflare.com/api-shield/management-and-monitoring/developer-portal/) | **Security** > **API Shield** > **Settings** |
| [Custom fallthrough rules](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-adding-a-fallthrough-rule) | **Security** > **API Shield** > **Settings** |
| [Endpoint discovery](https://developers.cloudflare.com/api-shield/security/api-discovery/): | **API Shield** > **Discovery** |
| — [Session identifiers](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/) | **Security** > **API Shield** > **Settings** |
| [Endpoint labels](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/) | **Security** > **Settings** > **Labels** |
| [Firewall for AI](https://developers.cloudflare.com/waf/detections/firewall-for-ai/) | *N/A* |
| [HTTP DDoS attack protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/): | **Security** > **DDoS** |
| — [Configure overrides](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/http-overrides/configure-dashboard/) | **Security** > **DDoS** |
| [IP access rules](https://developers.cloudflare.com/waf/tools/ip-access-rules/) | **Security** > **WAF** > **Tools** tab **Security** > **WAF** > **Custom rules** tab |
| [IP lists](https://developers.cloudflare.com/waf/tools/lists/custom-lists/#ip-lists) | Account Home > **Manage Account** > **Configurations** |
| [JWT validation](https://developers.cloudflare.com/api-shield/security/jwt-validation/): | **Security** > **API Shield** > **Settings** |
| — [JWT validation rules](https://developers.cloudflare.com/api-shield/security/jwt-validation/#add-a-jwt-validation-rule) | **Security** > **API Shield** > **API Rules** |
| — [Token configurations](https://developers.cloudflare.com/api-shield/security/jwt-validation/#add-a-token-validation-configuration) | **Security** > **API Shield** > **Settings** |
| [Leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/): | **Security** > **Settings** |
| — [Custom username and password location](https://developers.cloudflare.com/waf/detections/leaked-credentials/#custom-detection-locations) | **Security** > **Settings** |
| [Malicious uploads detection](https://developers.cloudflare.com/waf/detections/malicious-uploads/): | **Security** > **Settings** |
| — [Custom content location](https://developers.cloudflare.com/waf/detections/malicious-uploads/#custom-scan-expressions) | **Security** > **Settings** |
| [Manage AI bot traffic with robots.txt](https://developers.cloudflare.com/bots/additional-configurations/managed-robots-txt/) | **Security** > **Bots** > **Configure Bot Fight Mode Security** > **Bots** > **Configure Super Bot Fight Mode Security** > **Bots** > **Configure Bot Management** |
| [mTLS rules](https://developers.cloudflare.com/api-shield/security/mtls/configure/) | **SSL/TLS** > **Client Certificates** |
| [Network-layer DDoS attack protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/network/) | Account Home > **L3/4 DDoS** > **Network-layer DDoS Protection** |
| [OWASP Core](https://developers.cloudflare.com/waf/managed-rules/reference/owasp-core-ruleset/) ruleset | **Security** > **WAF** > **Managed rules** tab |
| Rate limit authentication requests | **Security** > **WAF** > **Rate limiting rules** tab |
| [Replace insecure JavaScript libraries](https://developers.cloudflare.com/waf/tools/replace-insecure-js-libraries/) | **Security** > **Settings** |
| [Schema learning](https://developers.cloudflare.com/api-shield/security/schema-validation/): | **Security** > **API Shield** > **Schema Validation** |
| — [Session identifiers](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/) | **Security** > **API Shield** > **Settings** |
| [Schema validation](https://developers.cloudflare.com/api-shield/security/schema-validation/) | **Security** > **API Shield** > **Schema Validation** |
| — [Endpoints](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/) | **Security** > **API Shield** |
| — [Active schemas](https://developers.cloudflare.com/api-shield/security/schema-validation/#view-active-schemas) | **Security** > **API Shield** > **Schema Validation** |
| — [Default action](https://developers.cloudflare.com/api-shield/security/schema-validation/#change-the-global-default-action-of-schema-validation) | **Security** > **API Shield** > **Schema Validation** |
| [Security Level: Under Attack mode](https://developers.cloudflare.com/fundamentals/reference/under-attack-mode/) | **Security** > **Settings** |
| [Security.txt](https://developers.cloudflare.com/security-center/infrastructure/security-file/) | **Security** > **Settings** |
| [Sensitive data detection](https://developers.cloudflare.com/waf/managed-rules/reference/sensitive-data-detection/#configure-in-the-dashboard) ruleset | **Security** > **Sensitive Data** |
| [Sequence detection](https://developers.cloudflare.com/api-shield/security/sequence-analytics/): | **Security** > **API Shield** > **API Rules** |
| — [Endpoints](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/) | **Security** > **API Shield** |
| — [Session identifiers](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/) | **Security** > **API Shield** > **Settings** |
| [Session identifiers](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/) | **Security** > **API Shield** > **Settings** |
| [SSL/TLS DDoS attack protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/) | **Security** > **DDoS** |
| [Token configurations](https://developers.cloudflare.com/api-shield/security/jwt-validation/) | **Security** > **API Shield** > **Settings** |
| [User agent blocking](https://developers.cloudflare.com/waf/tools/user-agent-blocking/) | **Security** > **WAF** > **Tools** tab **Security** > **WAF** > **Custom rules** tab |
| [Zone lockdown](https://developers.cloudflare.com/waf/tools/zone-lockdown/) | **Security** > **WAF** > **Tools** tab **Security** > **WAF** > **Custom rules** tab |
</page>
<page>
---
title: Web assets · Security dashboard docs
description: Discover web assets such as your API endpoints and instruct
Cloudflare how to best protect them.
lastUpdated: 2025-10-17T14:13:20.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security/web-assets/
md: https://developers.cloudflare.com/security/web-assets/index.md
---
Discover web assets such as your API endpoints and instruct Cloudflare how to best protect them.
To access web assets in the new security dashboard, go to the **Web assets** page.
[Go to **Web assets**](https://dash.cloudflare.com/?to=/:account/:zone/security/web-assets)
## Endpoints
Use the **Endpoints** tab to manage endpoints available on your domain and monitor their health.
You can save endpoints directly from [API Discovery](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#add-endpoints-from-api-discovery), [manually](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#add-endpoints-manually) by method, path, and host, or via [Schema Validation](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#add-endpoints-from-schema-validation).
This will add the specified endpoints to your list of managed endpoints. You can view your list of managed endpoints in the **Endpoints** tab.
For saved endpoints:
* Cloudflare will start collecting [performance data](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#endpoint-analysis) per endpoint.
* You can use the [labeling service](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/) to organize your endpoints by use case.
For more information on how to manage your endpoints, refer to the following resources.
* [Endpoint Management](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/)
* [Schema learning](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/schema-learning/)
* [Endpoint Analysis](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#endpoint-analysis)
## Discovery
**Discovery** continuously finds your active API endpoints via path normalization.
[Add endpoints](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-management/#add-endpoints-from-api-discovery) to produce recommendations and analytics of your APIs. Your [session identifiers](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/) must match your API traffic. Otherwise, API endpoints are also discoverable via [Machine Learning](https://developers.cloudflare.com/api-shield/security/api-discovery/#machine-learning-based-discovery).
Note
**Discovery** is only available for Enterprise customers. If you are an Enterprise customer and interested in this product, contact your account team.
## Sequences
Use **Sequences** to discover how users interact with your API, by tracking the order of API session requests over time. Sequences will group and highlight popular user journeys across your API.
Once you configure [session identifiers](https://developers.cloudflare.com/api-shield/management-and-monitoring/session-identifiers/), the **Sequences** tab will start grouping and highlighting important user journeys (sequences) across your API.
To configure session identifiers:
1. In the Cloudflare dashboard, go to the Security **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
2. Next to **Session identifiers**, select **Configure session identifiers** .
For more information on how Cloudflare identifies API sequences and how you can configure API sequence rules, refer to the following resources:
* [Sequence analytics](https://developers.cloudflare.com/api-shield/security/sequence-analytics/)
* [Sequence mitigation](https://developers.cloudflare.com/api-shield/security/sequence-mitigation/)
Note
The **Sequences** tab includes functionality available in [API Shield](https://developers.cloudflare.com/api-shield/) in the previous dashboard navigation structure.
## Schema validation
Use **Schema validation** to check if your incoming traffic complies with a previously supplied API Schema.
API Schemas are defined by the validity of the API request's properties such as target endpoint, path or query variable format, and HTTP method. A rule is created for incoming traffic and defines which traffic is allowed and which traffic is logged or blocked based on the API schema that you provide or select from the list of learned schemas.
You can add schema validation by:
* [Uploading a schema](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-uploading-a-schema)
* [Applying a learned schema to a single endpoint](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-applying-a-learned-schema-to-a-single-endpoint)
* [Applying a learned schema to an entire hostname](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-applying-a-learned-schema-to-an-entire-hostname)
* [Adding a fallthrough rule](https://developers.cloudflare.com/api-shield/security/schema-validation/#add-validation-by-adding-a-fallthrough-rule)
Note
The **Schema validation** tab includes functionality available in [API Shield](https://developers.cloudflare.com/api-shield/) in the previous dashboard navigation structure.
## Client-side resources
Use **Client-side resources** to [monitor scripts, connections, and cookies](https://developers.cloudflare.com/page-shield/detection/monitor-connections-scripts/) on your domain.
If you notice unexpected scripts or connections on the dashboard, check them for signs of malicious activity. You should also check for any new or unexpected cookies.
Enterprise customers with a paid add-on will have their connections and scripts [classified as potentially malicious](https://developers.cloudflare.com/page-shield/how-it-works/malicious-script-detection/) based on threat feeds.
Note
The **Client-side resources** tab includes functionality available in [Page Shield](https://developers.cloudflare.com/page-shield/) in the previous dashboard navigation structure.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Security Center docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/404/
md: https://developers.cloudflare.com/security-center/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Application Security reports · Cloudflare Security Center docs
description: Application Security reports provide cyber attack insights and
trends for all of the Enterprise zones in your Cloudflare account.
lastUpdated: 2025-10-28T18:39:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/app-security-reports/
md: https://developers.cloudflare.com/security-center/app-security-reports/index.md
---
Application Security reports provide cyber attack insights and trends for all of the Enterprise zones in your Cloudflare account.
The reports are automatically generated on a monthly basis.
You can access reports by going to the **Security reports** page or via the [API](#api). You can access reports from previous months by selecting the month from the dropdown.
[Go to **Security reports**](https://dash.cloudflare.com/?to=/:account/security-center/reports)
To download the report, select **Print report**.
Reports from before April 2025 can be accessed through **Security reports** > **Legacy reports**. Due to limitations in the legacy reports, some customers may not have reports for every month prior to April 2025.
The current reports are curated by Cloudflare and will be expanded to include more insights. The option to create custom reports, filter by various fields, and schedule reports will be added in upcoming improvements.
***
## Report types
Currently, only Application Security reports are available. They cover the entire suite of products such as [HTTP DDoS Protection](https://developers.cloudflare.com/ddos-protection/managed-rulesets/http/), [WAF](https://developers.cloudflare.com/waf/), and [Bot Management](https://developers.cloudflare.com/bots/).
Reports for Application Performance, [Cloudflare One](https://developers.cloudflare.com/cloudflare-one/), and Network Services, such as [Magic Transit](https://developers.cloudflare.com/magic-transit/), will be made available in future improvements.
***
## Report layout
Each report includes the following sections:
* Executive summary
* Distribution of allowed and mitigated requests
* [Industry benchmarks](#industry-benchmarks) that show how you compare to your peers by selecting your industry
* Top five source countries of allowed traffic and mitigated traffic including a map visualization
* Top five most targeted hostnames
* Top five most effective mitigation rules
To view more details, apply filters, analyze the data, and generate ad-hoc reports, use the [Security Analytics dashboard](https://developers.cloudflare.com/waf/analytics/security-analytics/) or [Log Explorer](https://developers.cloudflare.com/log-explorer/).
### Industry benchmarks
Industry benchmarks provide additional context for your mitigated traffic by comparing your organization's attack activity against others in the same industry. These benchmarks help you understand whether the volume and frequency of attacks you experience are typical, higher, or lower than your peers — offering a clear sense of where your organization stands within its threat landscape.
Beyond providing context, benchmarks can also help demonstrate value to stakeholders by quantifying the scale of threats your organization faces and how effectively Cloudflare mitigates them. This information can be useful when communicating your security posture internally or when prioritizing future security investments.
To ensure fairness and accuracy, Cloudflare normalizes your data before comparison. For each month, we calculate the percentage of mitigated requests relative to the total requests across your account and eligible zones. This normalization ensures that benchmarks are based on relative attack intensity rather than total traffic volume so larger or smaller organizations can be compared meaningfully.
The result helps you interpret your mitigated traffic data in context. For example, you may see a statement such as "*You are in the top 25% most attacked companies in the Cosmetics industry.*" This insight enables you to better understand your threat exposure, communicate results to stakeholders, and understand value of the protection Cloudflare provides.
If your account is not assigned an industry or if the shown industry is incorrect, use the link within the report to select the correct industry.
It may take a while for your new selection to take effect, and it may only be applied to future reports.
If you have multiple Cloudflare accounts, select the industry that is most relevant for the specific account.
***
## Prerequisites
You must have at least one Enterprise zone. Application Security reports are automatically enabled on your Enterprise zone. No action is required.
If you do not have any Enterprise zones, a report will not be generated. If you have an account that is not older than one month, a report will not be generated yet.
### Required roles
A Cloudflare user must have one of the following [roles](https://developers.cloudflare.com/fundamentals/manage-members/roles/) to download Application Security reports:
* Super Administrator
* Administrator
***
## API
```sh
GET /accounts/{account_id}/reporting/policies
```
```sh
GET /accounts/{account_id}/reporting/policies/{policy_id}
```
```sh
GET /accounts/{account_id}/reporting/reports
```
```sh
GET /accounts/{account_id}/reporting/reports/{report_id}
```
Data returned by the API
* Account ID
* Account Name
* Account Industry
* Time range
* Total zones
* Total zones analyzed
* Industry percentile (nullable float)
* Total requests (count, percentage)
* Total mitigated requests (count, percentage)
* Total served requests (count, percentage)
* Top 5 hostnames by mitigated requests (hostname, count)
* Top 5 source countries by served requests (country, count)
* Top 5 source countries by mitigated requests (country, count)
* Top 5 rules by mitigated requests (rule name, rule type, count)
Note
The data's time range is independent of when the report is generated.
### Cross-account reports
Each report is generated per account. You can use the [API](#api) to retrieve the reports for all of your accounts and aggregate the data.
***
## Limitations
Application Security reports currently only support US Customer Metadata Boundary (CMB). They do not support the EU CMB yet.
***
## Availability
This feature is available in closed beta to Enterprise customers.
</page>
<page>
---
title: Blocked Content · Cloudflare Security Center docs
description: If your domain has content that has been blocked, Blocked Content
on the dashboard gives you the ability to request the Trust and Safety team to
remove a block.
lastUpdated: 2025-09-03T13:18:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/blocked-content/
md: https://developers.cloudflare.com/security-center/blocked-content/index.md
---
If your domain has content that has been blocked, Blocked Content on the dashboard gives you the ability to request the Trust and Safety team to remove a block.
To view Blocked Content on the dashboard:
1. In the Cloudflare dashboard, go to the **Blocked Content** page.
[Go to **Blocked content**](https://dash.cloudflare.com/?to=/:account/blocked-content)
Note
You must have Admin, Super Admin, or Trust and Safety [role](https://developers.cloudflare.com/fundamentals/manage-members/roles/) to access Blocked Content.
The Security Center dashboard displays three statuses for blocked content: active, pending, or resolved blocks.
## Active blocks
An active block is a block that is in effect on blocking content.
When you select **Request Review**, the status changes to **In Review**, and the block will be reviewed by the Trust and Safety team.
## Pending blocks
A pending block represents a blocking action Cloudflare will take at the scheduled time.
You can view all your pending blocks by selecting **Pending** on the dashboard. Selecting **Request Review** cancels the pending delayed action. This means that the block will not be placed.
## Resolved blocks
Resolved blocks list your recently resolved blocks. Resolved blocks are limited to 30 days of recently resolved blocks. Resolved blocks require no action. You can only sort and/or filter the list.
</page>
<page>
---
title: Brand Protection · Cloudflare Security Center docs
description: Brand Protection gives you the ability to search for new domains
that may be attempting to impersonate your brand. Common misspellings
(cloudfalre.com) and concatenation of services (cloudflare-okta.com) are often
registered by attackers to trick unsuspecting victims into submitting private
information such as passwords. Our system allows you to save search queries
that run continuously and alert you if any new domains match those queries.
lastUpdated: 2025-09-12T09:19:49.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/brand-protection/
md: https://developers.cloudflare.com/security-center/brand-protection/index.md
---
User permission
While the Brand Protection tool is in beta, all Cloudflare Enterprise customers have automatic access to Brand Protection, including five saved queries. Only Admin, Super Admin and users with a Brand Protection role can access Brand Protection
Brand Protection gives you the ability to search for new domains that may be attempting to impersonate your brand. Common misspellings (`cloudfalre.com`) and concatenation of services (`cloudflare-okta.com`) are often registered by attackers to trick unsuspecting victims into submitting private information such as passwords. Our system allows you to save search queries that run continuously and alert you if any new domains match those queries.
## Domain search
To start searching for new domains that might be trying to impersonate your brand:
1. In the Cloudflare dashboard, go to the **Brand Protection** page.
[Go to **Brand protection**](https://dash.cloudflare.com/?to=/:account/security-center/brand-protection)
2. In **String query**, provide a name for your query. You can add multiple brand phrases on the same query, and the results will generate matches for all of those. Once you entered the string queries, select **Search matches**.
3. In the **Character distance**, select from `0-3`. The number of characters the results can differ from your domain.
Note
If a brand phrase or search term has less than five characters, you can only choose a max distance of `0` (zero).
4. You can select **Save query** to monitor it in the future and perform other actions, such as delete, clone and set up alerts, according to your Paid plan limits.
5. To export all matches from a saved query, select your **Query name** > select the three dots > **Export matches**.
In the section **Monitor Strings**, you can check all the string queries that you selected to monitor. You can delete, clone, or create notifications for a string query. Refer to [Brand Protection Alerts](#brand-protection-alerts) to set up notifications.
### Report abuse
Submit abuse report
You can only submit an abuse report if your domain is with [Cloudflare Registrar](https://www.cloudflare.com/products/registrar/), or if the IP used by the domain is hosted by Cloudflare.
To submit abuse reports directly from the dashboard:
1. In the Cloudflare dashboard, go to the **Brand Protection** page.
[Go to **Brand protection**](https://dash.cloudflare.com/?to=/:account/security-center/brand-protection)
2. Go to **Monitor Strings**, select the query you want to report.
3. Select **Report to Cloudflare**.
4. Fill in the details to submit an abuse report.
5. Select **Submit**.
To view abuse reports, in the Cloudflare dashboard, go to the **Abuse Reports** page.
[Go to **Abuse reports**](https://dash.cloudflare.com/?to=/:account/abuse-reports)
You can review abuse reports against your zones and any mitigations taken against reports in response.
You can also **Request review** of most mitigations.
## Logo queries
To set up a new logo query:
1. Select **Monitor Logos** and select **Add logo**.
2. Add a name for your query and upload your logo. Only the `.png`, `.jpeg`, and `.jpg` file extensions are supported.
3. Select **Save logo**.
The browser will return to the **Monitored Logos** page, where you can access your query and configure notifications.
## Investigate a query
In this section, the dashboard displays:
* **Domain overview** where you can request to [change categorization](https://developers.cloudflare.com/security-center/investigate/change-categorization/) and view the resolution history of your domain for up to seven days.
* **WHOIS** that provides details about the date the domain was created, registrant and nameservers.
* **Domain history** that provides information on the domain category and when it was last changed. Refer to [Investigate threats](https://developers.cloudflare.com/security-center/investigate/investigate-threats/) for more details.
* **URL Reports** that provides information on any reported URL.
To investigate a string query:
1. Go to the **Monitor Strings** or **Monitor Logos** section to view all your queries.
2. Select a monitored query to inspect all the domains that matched your query.
3. Next to the domain, select **Domain** or **URL**. This will trigger a search on the [**Investigate**](https://developers.cloudflare.com/security-center/investigate/) section in a separate tab. URL scanner will also be triggered from **Brand Protection** through **Security Center** > **Investigate**. You will also have access to a report which will be generated automatically. The report will display screenshots of the matched domain, and the registrar of your domain.
## Brand Protection API
The [Brand Protection API](https://developers.cloudflare.com/api/resources/brand_protection/) allows you to:
* Create new strings or logo queries
* Delete strings or logo queries
* Download matches for both logo and string queries
* Read matches for both logo and string queries
## Brand Protection Alerts
Brand Protection works with Cloudflare’s ANS (Alerts Notification Service) to provide configurable alerts when new domains are detected.
Any matches that are found during the new domain search are then inserted into an internal alerts table which triggers an alert for the user. This allows you to receive real-time notifications and take immediate action to investigate and potentially block any suspicious domains that may be attempting to impersonate your brand.
Brand Protection Alerts
**Who is it for?**
Customers who want a summary of activity related to [Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/).
**Other options / filters**
You can set up Brand Protection Alerts on individual monitored queries. For more details, refer to [Brand Protection Alerts](https://developers.cloudflare.com/security-center/brand-protection/#brand-protection-alerts).
**Included with**
Professional plans or higher.
**What should you do if you receive one?**
Investigate and potentially block any suspicious domains that may be trying to impersonate your brand.
Brand Protection Digest
**Who is it for?**
Customers who want a summary of activity related to [Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/).
**Other options / filters**
You can set up Brand Protection Digest on individual monitored queries. For more details, refer to [Brand Protection Alerts](https://developers.cloudflare.com/security-center/brand-protection/#brand-protection-alerts).
**Included with**
Professional plans or higher.
**What should you do if you receive one?**
Investigate and potentially block any suspicious domains that may be trying to impersonate your brand.
Logo Match Alerts
**Who is it for?**
Customers who want to receive a notification when the [Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/) system detects a new domain which is using the uploaded logo and might be infringing copyright.
**Other options / filters**
You can select the query that you want to be alerted on.
**Included with**
Enterprise plans.
**What should you do if you receive one?**
Review the domains and URLs that are potentially impersonating your brand.
Security Insights
**Who is it for?**
Customers who want to receive notifications based on security insights findings.
**Other options / filters**
You can select the insight(s) you want to be alerted on.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
Review the insight and decide whether you want to resolve it, archive it, or export it.
Abuse report
**Who is it for?**
Customers who want to be alerted in the event that an abuse report is filed against their website.
**Other options / filters**
You can filter the reports based on date, report status, report type, and domain.
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
View our guidance on [customer abuse report obligations](https://developers.cloudflare.com/fundamentals/reference/report-abuse/abuse-report-obligations/) and more information on how to [view and submit abuse reports](https://developers.cloudflare.com/fundamentals/reference/report-abuse/submit-report/).
To set up a Brand Protection Alert:
1. Go to **Monitor Strings** and locate the query for which you would like to create notifications.
2. Select **alerts**. This should redirect you to the **Add Notification** page, where you can configure what you want to be notified about, and how.
Note
You can also set up the alerts from your [Notifications](https://developers.cloudflare.com/notifications/) menu.
3. Create a notification name, add a description (optional), and select the monitored queries. You can also add a Webhook, and a notification email. You can add multiple email addresses.
4. Select **Save**.
Manage your notifications in the **All notifications** tab. You can disable, edit, delete, or test them.
## Limitations
* While this product is in beta, all Enterprise customers and Cloudforce One subscribers have access to Brand Protection. Enterprise customers are entitled to five saved queries for their account.
* You may only use the Brand Protection search tools to search for domains that may be attempting to impersonate your brand or a brand that has authorized you to conduct such search on its behalf.
</page>
<page>
---
title: Changelog · Cloudflare Security Center docs
description: Identifying threat actors can be challenging, because naming
conventions often vary across the security industry. To simplify your
research, Cloudflare Threat Events now include an Also known as field,
providing a list of common aliases and industry-standard names for the groups
we track.
lastUpdated: 2025-08-08T13:53:13.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/changelog/
md: https://developers.cloudflare.com/security-center/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/security-center.xml)
## 2026-02-03
**Threat actor identification with "also known as" aliases**
Identifying threat actors can be challenging, because naming conventions often vary across the security industry. To simplify your research, **Cloudflare Threat Events** now include an **Also known as** field, providing a list of common aliases and industry-standard names for the groups we track.
This new field is available in both the Cloudflare dashboard and via the API. In the dashboard, you can view these aliases by expanding the event details side panel (under the **Attacker** field) or by adding it as a column in your configurable table view.
#### Key benefits
* Easily map Cloudflare-tracked actors to the naming conventions used by other vendors without manual cross-referencing.
* Quickly identify if a detected threat actor matches a group your team is already monitoring via other intelligence feeds.
For more information on how to access this data, refer to the [Threat Events API documentation](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/threat_events/).
## 2026-01-14
**URL Scanner now supports PDF report downloads**
We have expanded the reporting capabilities of the Cloudflare URL Scanner. In addition to existing JSON and HAR exports, users can now generate and download a **PDF report** directly from the Cloudflare dashboard. This update streamlines how security analysts can share findings with stakeholders who may not have access to the Cloudflare dashboard or specialized tools to parse JSON and HAR files.
**Key Benefits:**
* Consolidate scan results, including screenshots, security signatures, and metadata, into a single, portable document
* Easily share professional-grade summaries with non-technical stakeholders or legal teams for faster incident response
**What’s new:**
* **PDF Export Button:** A new download option is available in the URL Scanner results page within the Cloudflare dashboard
* **Unified Documentation:** Access all scan details—from high-level summaries to specific security flags—in one offline-friendly file
To get started with the URL Scanner and explore our reporting capabilities, visit the [URL Scanner API documentation](https://developers.cloudflare.com/api/resources/url_scanner/).
***
## 2026-01-12
**Cloudflare Threat Events now support STIX2 format**
We are excited to announce that **Cloudflare Threat Events** now supports the **STIX2 (Structured Threat Information Expression)** format. This was a highly requested feature designed to streamline how security teams consume and act upon our threat intelligence.
By adopting this industry-standard format, you can now integrate Cloudflare's threat events data more effectively into your existing security ecosystem.
#### Key benefits
* Eliminate the need for custom parsers, as STIX2 allows for "out of the box" ingestion into major **Threat Intel Platforms (TIPs)**, **SIEMs**, and **SOAR** tools.
* STIX2 provides a standardized way to represent relationships between indicators, sightings, and threat actors, giving your analysts a clearer picture of the threat landscape.
For technical details on how to query events using this format, please refer to our [Threat Events API Documentation](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/threat_events/methods/list/).
***
## 2025-11-21
**Threat insights are now available in the Threat Events platform**
The threat events platform now has threat insights available for some relevant parent events. Threat intelligence analyst users can access these insights for their threat hunting activity. Insights are also highlighted in the Cloudflare dashboard by a small `lightning icon` and the insights can refer to multiple, connected events, potentially part of the same attack or campaign and associated with the same threat actor.
For more information, refer to [Analyze threat events](https://developers.cloudflare.com/security-center/cloudforce-one/#analyze-threat-events).
## 2025-10-31
**Report logo misuse to Cloudflare directly from the Brand Protection dashboard**
The Brand Protection logo query dashboard now allows you to use the **Report to Cloudflare** button to submit an Abuse report directly from the Brand Protection logo queries dashboard. While you could previously report new domains that were impersonating your brand before, now you can do the same for websites found to be using your logo wihtout your permission. The abuse reports wiull be prefilled and you will only need to validate a few fields before you can click the submit button, after which our team process your request.
Ready to start? Check out the [Brand Protection docs](https://developers.cloudflare.com/security-center/brand-protection/).
## 2025-10-27
**Cloudforce One RFI tokens are now visible in the dashboard**
The Requests for Information (RFI) dashboard now shows users the number of tokens used by each submitted RFI to better understand usage of tokens and how they relate to each request submitted.

What’s new:
* Users can now see the number of tokens used for a submitted request for information.
* Users can see the remaining tokens allocated to their account for the quarter.
* Users can only select the Routine priority for the `Strategic Threat Research` request type.
Cloudforce One subscribers can try it now in [Application Security > Threat Intelligence > Requests for Information](https://dash.cloudflare.com/?to=/:account/security-center/threat-intelligence/requests).
## 2025-10-17
**New Application Security reports (Closed Beta)**
Cloudflare's new **Application Security report**, currently in Closed Beta, is now available in the dashboard.
[Go to **Security reports**](https://dash.cloudflare.com/?to=/:account/security-center/reports)
The reports are generated monthly and provide cyber security insights trends for all of the Enterprise zones in your Cloudflare account.
The reports also include an industry benchmark, comparing your cyber security landscape to peers in your industry.

Learn more about the reports by referring to the [Security Reports documentation](https://developers.cloudflare.com/security-center/app-security-reports/).
Use the feedback survey link at the top of the page to help us improve the reports.

## 2025-08-15
**Save time with bulk query creation in Brand Protection**
[Brand Protection](https://developers.cloudflare.com/security-center/brand-protection/) detects domains that may be impersonating your brand — from common misspellings (`cloudfalre.com`) to malicious concatenations (`cloudflare-okta.com`). Saved search queries run continuously and alert you when suspicious domains appear.
You can now create and save multiple queries in a single step, streamlining setup and management. Available now via the [Brand Protection bulk query creation API](https://developers.cloudflare.com/api/resources/brand_protection/subresources/queries/methods/bulk/).
## 2025-07-18
**New APIs for Brand Protection setup**
The Brand Protection API is now available, allowing users to create new queries and delete existing ones, fetch matches and more!
What you can do:
* **create new string or logo query**
* **delete string or logo queries**
* **download matches for both logo and string queries**
* **read matches for both logo and string queries**
Ready to start? Check out the [Brand Protection API](https://developers.cloudflare.com/api/resources/brand_protection/) in our documentation.
## 2025-05-08
**URL Scanner now supports geo-specific scanning**
Enterprise customers can now choose the geographic location from which a URL scan is performed — either via [Security Center](https://developers.cloudflare.com/security-center/investigate/) in the Cloudflare dashboard or via the [URL Scanner API](https://developers.cloudflare.com/api/resources/url_scanner/subresources/scans/methods/create/).
This feature gives security teams greater insight into how a website behaves across different regions, helping uncover targeted, location-specific threats.
**What’s new:**
* Location Picker: Select a location for the scan via **Security Center → Investigate** in the dashboard or through the API.
* Region-aware scanning: Understand how content changes by location — useful for detecting regionally tailored attacks.
* Default behavior: If no location is set, scans default to the user’s current geographic region.
Learn more in the [Security Center documentation](https://developers.cloudflare.com/security-center/).
## 2025-02-03
* Security Center now has a role called Brand Protection. This role gives you access to the Brand Protection feature on the API and Cloudflare dashboard. Brand Protection role also gives you access to the Investigate platform, where you can consume the Threat Intel API and URL scanner API calls.
## 2025-01-20
* On the URL scanner, customers who search for a report will now get a list of all reports related to that specific hostname. A hash is also available in the security report. By selecting the hash, the dashboard will list reports containing the same hash.
## 2024-09-23
* Customers can now export all matches from a saved query. Select your **Query name** > select the three dots > **Export matches**.
## 2024-09-19
* Customers can now create a `security.txt` file file to provide the security research team with a standardized way to report vulnerabilities.
## 2024-07-22
* Customers can now archive multiple Security Insights at the same time. Go to **Security Center** > **Security Insights** and select the insights to archive.
</page>
<page>
---
title: Cloudforce One · Cloudflare Security Center docs
description: Cloudforce One is a threat intelligence solution that offers threat
research reports, brand protection, Request for Information (RFIs), and more.
lastUpdated: 2025-10-10T15:12:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/cloudforce-one/
md: https://developers.cloudflare.com/security-center/cloudforce-one/index.md
---
Note
You must have a Cloudforce One subscription to access Cloudforce One on the dashboard.
Cloudforce One is a threat intelligence solution that offers threat research reports, brand protection, Request for Information (RFIs), and more.
To access Cloudforce One:
1. In the Cloudflare dashboard, go to the **Threat Intelligence** page.
[Go to **Threat intelligence**](https://dash.cloudflare.com/?to=/:account/security-center/threat-intelligence)
You can also use Cloudforce One via [REST API](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/requests/subresources/assets/).
Cloudforce One Threat Intelligence displays the following information:
* **Threat Events** to analyze threat intelligence data.
* **Priority Intelligence Requirements** to review and manage Cloudforce One Priority Intelligence Requirements (PIRs). PIRs are a structured approach to identifying intelligence gaps.
* **Requests for Information** to submit specific queries and requests directly into Cloudforce One's analysis queue.
* **Reports** to get the latest Cloudforce One Threat reports.
## Submit RFIs
To submit RFIs (Request for Information):
1. In the Cloudflare dashboard, go to the **Threat Intelligence** page.
[Go to **Threat intelligence**](https://dash.cloudflare.com/?to=/:account/security-center/threat-intelligence)
2. Select **Requests for Information**.
3. Select **New Request**.
4. Fill in the required fields, then select **Save**.
List of RFI types
The Cloudflare dashboard presents the following request types when you want to configure a Cloudforce One Requests for Information:
* **Binary Analysis - IOCs**: Conduct high level malware analysis to produce [indicators](https://www.cloudflare.com/en-gb/learning/security/what-are-indicators-of-compromise/) such as a call-back domain or IP address.
* **Binary Analysis - Report**: A thorough analysis of a malware sample to produce an attribution assessment and extract the configuration of the sample for further analysis. Useful for customers that are investigating a problem or trying to develop detection logic in an [EDR](https://en.wikipedia.org/wiki/Endpoint_detection_and_response) or network sensor.
* **DDoS Attack**: Confirm if an attack is happening against a specific website to share any available indicators and potential attribution.
* **Indicator Analysis - IOCs**: Conduct DNS lookups, origin pivots, and account pivots to provide indicators such as DNS resolutions, origin IPs, and subdomains. Analysis can include account registration patterns and victimology.
* **Indicator Analysis - Report**: A thorough analysis of indicators written in a formal, structured format. In addition to listing [Indicator of compromise (IOCs)](https://www.cloudflare.com/en-gb/learning/security/what-are-indicators-of-compromise/), the report explains how IOCs function within the attack chain, and adds context by linking IOCs to specific campaigns and/or threat actors and their TTPs.
* **Passive DNS Resolution**: Research the pair of an IP address to the domain it resolved to during a specified period of time.
* **Strategic Threat Research**: Strategic Threat Research goes beyond simple indicators to analyze broader, long-term trends, threat actors, and industries — often supplemented by open-source intelligence to inform high-level management and planning rather than providing immediately actionable intelligence.
* **Threat Detection Signature - IOCs**: Develop a rule such as Yara that will detect a sample, behavior, or network observable such as an IP address, domain, file hash, or attribute of a file or HTTP request.
* **Threat Detection Signature - Report**: A thorough analysis report that investigates the details of a threat detection alert or report for the benefit of customers that are trying to prioritize their response effort or to attribute activity to a threat actor.
* **Traffic Analysis - IOCs**: Review HTTP telemetry of IOCs in question and provide relevant, sanitized traffic which can include victim country and in some cases victim ASNs. Identify malicious files/payloads, and unusual file paths or request patterns.
* **Traffic Analysis - Report**: Report that analyzes HTTP telemetry to identify patterns, anomalies, and data pointing to malicious behavior. Provides context for observed network behaviors and maps them to known TTPs of specific threat groups.
* **Vulnerability**: Investigation to attribute vulnerability exploitation to a threat actor or investigation of IPs, domains, or threat actor groups exploiting the vulnerability. Response can include relevant, sanitized traffic demonstrating exploitation and identification of victim countries and industries.
Once you select **Save**, the dashboard will display an overview of the shared information consisting of:
* **Status**: When you submit the RFI, the status is `Open`. Once the team accepts the RFI, the status changes to `Accept`. When the team commits to answer your RFI, the status changes to `Complete`.
* **Priority**: Priority of request.
* **Request type**: Choose among a selection of request types, such as DDos Attack, Passive DNS Resolution, and more.
* **Request content**: The content of the request.
The **Responses** section allows you to add clarifying questions and comments.
To view your RFI, select **Cloudforce One Requests** on the sidebar, locate your RFI, then select **View**. From here, you can also choose to edit your existing RFI by selecting **Edit**.
To delete your RFI, the status must be `Open`. Go to the RFI you want to delete, and select **Delete**. On the pop-up, select **Delete** to confirm deletion. Once Cloudflare accepts and begins processing RFIs, you will not be able to delete RFIs.
### Upload and download attachment
You can also choose to upload and download an attachment.
Under **Attachments**, select the file you want to upload, then select **Save**.
To download an attachment, select **Download** on the attachment.
## Analyze threat events
Threat events allow you to protect your assets and respond to emerging threats.
To access and analyze threat intelligence data on the dashboard:
1. In the Cloudflare dashboard, go to the **Threat Intelligence** page.
[Go to **Threat intelligence**](https://dash.cloudflare.com/?to=/:account/security-center/threat-intelligence)
You can also access threat events via the [API](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/threat_events/).
Cloudforce One customers have access to the following existing datasets:
* APTs (default)
* DDoS attacks
* Cybercrime
* Compromised devices
* Residential Proxies
* WAF attacks
You can filter **Threat Events** by:
* Attacker
* Attacker Country
* Target Country
* Target Industry
* TLP (Traffic Light Protocol)
* Indicator Type
* [Kill Chain](https://en.wikipedia.org/wiki/Cyber_kill_chain)
* Tags
* Event Category
You can also filter by **Date range**.
Some events will not display **Target Country** and **Target Industry** because they are unknown information. There may be situations where the attacker's information is unknown. When Cloudflare finds a new attacker, the attacker will be assigned a new name.
## Use Cloudy to analyze threat events
You can use Cloudy, Cloudflare's AI Agent, to receive an analysis and summary of threat events.
To analyze threat events using Cloudy:
1. In the Cloudflare dashboard, go to the **Threat Intelligence** page.
[Go to **Threat intelligence**](https://dash.cloudflare.com/?to=/:account/security-center/threat-intelligence)
2. Go to **Threat Events** > **Analyze with Cloudy**.
Cloudy will show you the top threat events, analyze them, and give you a summary of threat events. You can also decide to receive an analysis based on **Attacker**, **Indicator**, and more. For example, you can enter "Give me a summary of threat events for ABC Attacker". Cloudy will then summarize threat events for ABC attacker.
## Receive help for an incident
Cloudforce One allows you to receive help to improve your security posture or recover from a past incident. This allows you to easily report security incidents directly within the Cloudflare dashboard.
1. In the Cloudflare dashboard, go to the **Threat Intelligence** page.
[Go to **Threat intelligence**](https://dash.cloudflare.com/?to=/:account/security-center/threat-intelligence)
2. Go to **Incident response services** then complete the following instructions:
* **Choose service**:
* Select among **Receive post-incident support**, **Request penetration tests**, **Conduct table-top exercises**, **Ask for general security advice**.
* Once you have chosen your desired service, select **Next**.
* **Provide request details**:
* Fill in the information needed based on the service you previously selected. Once you entered all the information, select **Next**.
* Review and submit your request. Then, select **Submit**.
* Once you submit your request, Cloudforce One will reply to you as soon as possible.
## Request help for active attack
If you want to stop an active cyber attack, you can request assistance via the Cloudflare dashboard.
1. In the Cloudflare dashboard, go to the **Account home** page and select your account.
[Go to **Account home**](https://dash.cloudflare.com/?to=/:account/home)
1. On the top bar, select **Support** > **Get help** > **Under attack**.
2. Under **Request help to stop active cyberattacks**, select **Request help**.
3. The dashboard will show you a pop-up where you will need to enter and confirm your phone number.
4. Once you have entered your phone number, select **Confirm number and request help**. Requesting help from the dashboard will page an incident responder and you can expect a call-back as soon as possible. We advise you to wait for the call-back, and only use the phone-line in case you have not heard back from the team within 10 minutes.
</page>
<page>
---
title: Get started · Cloudflare Security Center docs
description: This guide covers the steps you need to take to set up Security
Center in your Cloudflare account for the first time.
lastUpdated: 2025-09-03T13:18:17.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/get-started/
md: https://developers.cloudflare.com/security-center/get-started/index.md
---
This guide covers the steps you need to take to set up Security Center in your Cloudflare account for the first time.
## Prerequisites
* A Cloudflare account
* At least one zone onboarded to Cloudflare
## Enable Security Insights and start initial scan
Security Insights start scans by default. Security Insights will scan your Cloudflare environment and provide you with a list of detected [insights](https://developers.cloudflare.com/security-center/security-insights/). Refer to [How it works](https://developers.cloudflare.com/security-center/security-insights/how-it-works/) to learn more about how Security Insights perform a scan.
The initial scan time depends on the number of IT assets in all the domains of your Cloudflare account. When the scan is complete, the status of the page will change from **Scan in Progress** to **Last scan performed on: `<DATE_TIME>`**.
You can decide to stop a scan, and restart a scan later.
To disable scans:
1. In the Cloudflare dashboard, go to the **Security Insights** page.
[Go to **Security insights**](https://dash.cloudflare.com/?to=/:account/security-center)
2. Go to **Disable Security Center scans**, select **Disable scans**.
To restart a scan:
1. In the Cloudflare dashboard, go to the **Security Insights** page.
[Go to **Security insights**](https://dash.cloudflare.com/?to=/:account/security-center)
2. Select **Scan now**.
### Start a new scan
To manually start a scan:
1. In the Cloudflare dashboard, go to the **Infrastructure** page.
[Go to **Infrastructure**](https://dash.cloudflare.com/?to=/:account/security-center/inventory)
2. Select **Scan now**.
### Scan Frequency
Once you enable Security Insights, Cloudflare performs scans at a [regular frequency](https://developers.cloudflare.com/security-center/security-insights/how-it-works/#scan-frequency), according to your Cloudflare plan.
</page>
<page>
---
title: Custom Indicator Feeds · Cloudflare Security Center docs
description: Cloudflare's threat intelligence team crowdsources attack trends
and protects users automatically, such as from zero-day vulnerabilities like
the HTTP/2 Rapid Reset attack. However, in some cases, Cloudflare will partner
with external entities that have their own feeds which can be shared with
eligible Cloudflare users.
lastUpdated: 2025-11-20T23:13:05.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/indicator-feeds/
md: https://developers.cloudflare.com/security-center/indicator-feeds/index.md
---
Cloudflare's threat intelligence team crowdsources attack trends and protects users automatically, such as from zero-day vulnerabilities like the [HTTP/2 Rapid Reset attack](https://blog.cloudflare.com/technical-breakdown-http2-rapid-reset-ddos-attack/). However, in some cases, Cloudflare will partner with external entities that have their own feeds which can be shared with eligible Cloudflare users.
With Custom Indicator Feeds, Cloudflare provides a threat intelligence feed based on data received from various Cyber Defense Collaboration groups. The security filtering capabilities are available to eligible public and private sector organizations.
## Publicly available feeds
Cloudflare provides some feeds to Gateway users without the need to establish a provider relationship.
| Name | Description | Availability |
| - | - | - |
| [Treasury Early Indicator Feed](https://www.cloudflare.com/press-releases/2024/us-department-of-treasury-pnnl-finserv-threat-intel-feed/), Feed ID 14 | Threat data for financial institutions provided by the US Department of Treasury and Pacific Northwest National Laboratory (PNNL). For more information, contact your account team. | Approved financial services organizations |
| [UK NCSC Public Threat Indicators](https://www.ncsc.gov.uk/information/pdns) Feed ID 24 | Recursive DNS service supplied by the UK National Cyber Security Centre (NCSC) to block DNS-based malware. | All users |
| Cloudforce One - Public Feed Feed ID 34 | Feed of indicators. | All users |
## Get started
Cloudflare threat intelligence data consists of a data exchange between providers and subscribers.
A provider is an organization that has a set of data that they are interested in sharing with other Cloudflare organizations. Any organization can be a provider. Examples of current providers are Government Cyber Defense groups.
Subscribers can be any Cloudflare customer that wants to secure their environment further by creating rules based on provider datasets. Subscribers must be authorized by a provider. Authorization is granted using the [Grant permission to indicator feed endpoint](https://developers.cloudflare.com/api/resources/intel/subresources/indicator_feeds/subresources/permissions/methods/create/).
If your organization is interested in becoming a provider or a subscriber, contact your account team.
### Create a Custom Indicator Feed
Providers can create and manage a Custom Indicator Feed with the [Custom Indicator Feeds API endpoints](https://developers.cloudflare.com/api/resources/intel/subresources/indicator_feeds/methods/list/):
1. Contact your account team to configure your account as an indicator feed provider.
2. Create a feed with the [Create new indicator feed endpoint](https://developers.cloudflare.com/api/resources/intel/subresources/indicator_feeds/methods/create/). Make note of the `feed_id` generated for your feed. For example:
```bash
curl "https://api.cloudflare.com/client/v4/accounts/<ACCOUNT_ID>/intel/indicator-feeds" \
--header 'Content-Type: application/json' \
--header 'X-Auth-Email: <EMAIL>' \
--header 'X-Auth-Key: <API_KEY>' \
--data '{
"description": "Custom indicator feed to detect threats",
"name": "threat_indicator_feed"
}'
```
```json
{
"result": {
"id": 10,
"name": "threat_indicator_feed",
"description": "Custom indicator feed to detect threats",
"created_on": "2024-09-17T21:16:09.412Z",
"modified_on": "2024-09-17T21:16:09.412Z"
},
"success": true,
"errors": [],
"messages": []
}
```
3. Upload data to the feed with the [Update indicator feed data endpoint](https://developers.cloudflare.com/api/resources/intel/subresources/indicator_feeds/subresources/snapshots/methods/update/). Uploaded indicator data must be in a [`.stix2`](https://oasis-open.github.io/cti-documentation/stix/intro) formatted file. The [maximum upload file size](https://developers.cloudflare.com/r2/platform/limits/) is 4.995 GiB.
```bash
curl --request PUT \
"https://api.cloudflare.com/client/v4/accounts/<ACCOUNT_ID>/intel/indicator-feeds/<FEED_ID>/snapshot" \
--header 'Content-Type: multipart/form-data' \
--header 'X-Auth-Email: <EMAIL>' \
--header 'X-Auth-Key: <API_KEY>' \
--form 'source=@/path/to/file'
```
```json
{
"result": {
"file_id": 1,
"filename": "snapshot_file.unified",
"status": "unified"
},
"errors": [],
"messages": [],
"success": true
}
```
Note
Indicator feeds use a snapshot system. To update feeds with new data, providers must upload a file containing all previous and new indicators.
4. (Optional) Verify the status of your feed upload with the [Get indicator feed data endpoint](https://developers.cloudflare.com/api/resources/intel/subresources/indicator_feeds/methods/data/). For example:
```bash
curl --request GET \
"https://api.cloudflare.com/client/v4/accounts/<ACCOUNT_ID>/intel/indicator-feeds/<FEED_ID>/data" \
--header 'Content-Type: application/json' \
--header 'X-Auth-Email: <EMAIL>' \
--header 'X-Auth-Key: <API_KEY>'
```
```json
{
"result": {
"id": 10,
"name": "threat_indicator_feed",
"description": "Custom indicator feed to detect threats",
"created_on": "2023-08-01T18:00:26.65715Z",
"modified_on": "2023-08-01T18:00:26.65715Z",
"latest_upload_status": "Complete"
},
"success": true,
"errors": [],
"messages": []
}
```
5. Grant access to subscribers with the [Grant permission to indicator feed endpoint](https://developers.cloudflare.com/api/resources/intel/subresources/indicator_feeds/subresources/permissions/methods/create/). You can add subscribers to the feed's allowed subscribers list using their [account IDs](https://developers.cloudflare.com/fundamentals/account/find-account-and-zone-ids/). For example:
```bash
curl --request PUT \
"https://api.cloudflare.com/client/v4/accounts/<ACCOUNT_ID>/intel/indicator-feeds/<FEED_ID>/snapshot" \
--header 'Content-Type: multipart/form-data' \
--header 'X-Auth-Email: <EMAIL>' \
--header 'X-Auth-Key: <API_KEY>' \
--data '{
"account_tag": "823f45f16fd2f7e21e1e054aga4d2859",
"feed_id": 10
}'
```
### Use a feed in Gateway
Once an account is granted access to a feed, it will be available to match traffic as a [selector in Gateway DNS policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/#indicator-feeds).
1. In [Cloudflare One](https://one.dash.cloudflare.com/), go to **Traffic policies** > **Firewall policies**. Select **DNS**.
2. To create a new DNS policy, select **Add a policy**.
3. Name your policy.
4. In **Traffic**, add a condition with the **Indicator Feeds** selector. If your account has been granted access to a Custom Indicator Feed, Gateway will list the feed in **Value**. For example, you can block sites that appear in a feed:
| Selector | Operator | Value | Action |
| - | - | - | - |
| Indicator Feeds | in | *Threat Intel Feed* | Block |
5. Select **Create policy**.
For more information on creating Gateway policies, refer to [DNS policies](https://developers.cloudflare.com/cloudflare-one/traffic-policies/dns-policies/).
</page>
<page>
---
title: Infrastructure · Cloudflare Security Center docs
description: After enabling Security Insights and letting the first scan run,
the Infrastructure tab displays an overview of the infrastructure associated
with your Cloudflare account.
lastUpdated: 2024-10-17T14:10:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/infrastructure/
md: https://developers.cloudflare.com/security-center/infrastructure/index.md
---
User permission
Only Super Admin users with edit permissions can start scans, turn scans off, or manage issues.
After [enabling Security Insights](https://developers.cloudflare.com/security-center/get-started/) and letting the first scan run, the **Infrastructure** tab displays an overview of the infrastructure associated with your Cloudflare account.
To open the **Infrastructure** tab, go to Account Home > **Security Center** > **Infrastructure**.
You can perform the following actions:
* Filter the displayed information
* Print or download a PDF report
* Manage your security.txt file
</page>
<page>
---
title: Threat Intelligence APIs · Cloudflare Security Center docs
description: Cloudflare provides a series of endpoints covering various areas of
internet security and insights. Based on your Cloudflare plan type, the limit
of API calls will vary per month.
lastUpdated: 2025-07-18T15:18:28.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/intel-apis/
md: https://developers.cloudflare.com/security-center/intel-apis/index.md
---
Cloudflare provides a series of endpoints covering various areas of internet security and insights. Based on your Cloudflare plan type, the [limit](https://developers.cloudflare.com/security-center/intel-apis/limits/) of API calls will vary per month.
| Intelligence Endpoint | Definition |
| - | - |
| [ASN Intelligence](https://developers.cloudflare.com/api/resources/intel/subresources/asn/methods/get/) | Provides an overview of the Autonomous System Number (ASN) and a list of subnets for it. |
| [Custom Indicator Feed Download](https://developers.cloudflare.com/api/resources/intel/subresources/indicator_feeds/subresources/downloads/methods/get/) | Provides the ability to download any custom indicator feeds that users create. |
| [Domain Intelligence](https://developers.cloudflare.com/api/resources/intel/subresources/domains/methods/get/) | Provides security details and statistics about a domain. |
| [Domain History](https://developers.cloudflare.com/api/resources/intel/subresources/domain_history/methods/get/) | Provides historical security threat and content categories that are currently and previously assigned to a domain. |
| [IP Intelligence](https://developers.cloudflare.com/api/resources/intel/subresources/ips/methods/get/) | Provides the geolocation, ASN, infrastructure type of the ASN, and any security threat categories of an IP address. |
| [Passive DNS by IP](https://developers.cloudflare.com/api/resources/intel/subresources/dns/methods/list/) | Provides a list of all the domains, including first seen and last seen dates, that have resolved to a specific IP address. |
| [Phishing Intelligence](https://developers.cloudflare.com/api/resources/brand_protection/methods/url_info/) | Provides phishing details about a URL. |
| [Miscategorization Intelligence](https://developers.cloudflare.com/api/resources/intel/subresources/miscategorizations/methods/create/) | Enables users to submit requests for modifying a domain's category, subsequently undergoing review by the Cloudflare Intelligence team. |
| [Priority Intelligence Requirements](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/requests/subresources/priority/methods/create/) | Provides a structured approach to identifying intelligence gaps, formulating precise requirements, and organizing them into categories. |
| [Request for Information](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/requests/methods/create/) | Creates a targeted inquiry for specific intelligence insights to help organizations understand and respond to imminent security threats and vulnerabilities. |
| [WHOIS](https://developers.cloudflare.com/api/resources/intel/subresources/whois/methods/get/) | Provides the WHOIS registration information for a specific domain. |
| [DDoS Botnet Threat Feed](https://developers.cloudflare.com/ddos-protection/botnet-threat-feed/) (early access) | Provides information to service providers about their own IP addresses that have participated in HTTP DDoS attacks as observed from Cloudflare's global network. |
| [Cloudforce One](https://developers.cloudflare.com/api/resources/cloudforce_one/subresources/requests/subresources/assets/methods/create/) | Enable users to list, delete, get, or update a request asset. |
| [Brand Protection API](https://developers.cloudflare.com/api/resources/brand_protection/) | Provides the ability to create and delete queries, download matches for logo and string queries, read matches for logo and string queries. |
## API Examples
Below you can find examples of Threat Intelligence API calls. Make sure you are using an [API Token](https://developers.cloudflare.com/fundamentals/api/get-started/create-token/) with the appropriate edit permissions. For comprehensive details, navigate to the respective API documentation using the links above.
### ASN Intelligence
Get ASN Overview
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/intel/asn/13335" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
# Example response:
{
"result": {
"asn": 13335,
"description": "CLOUDFLARENET",
"country": "US",
"type": "isp"
},
"success": true,
"errors": [],
"messages": []
}
```
### Custom Indicator Feed Download
Download Custom Indicator Feed
```bash
curl "https://api.cloudflare.com/client/v4/accounts/10d79d097895ae7ed7942a2b3832186c/intel/indicator-feeds/31/download" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
# Example response:
{
"result": [
{
"type": "bundle",
"id": "bundle--f4a735b7-b330-465d-8e6e-87b3c6a01287",
"objects":
[
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--3d0ad6e0-3d49-4575-a0cb-d0e5c8b81f08",
"created": "2024-07-18T00:00:00Z",
"modified": "2024-07-18T00:00:00Z",
"name": "Malicious domain ahilesopolker.com",
"description": "This domain is associated with malicious activity.",
"pattern": "[domain-name:value = 'ahilesopolker.com']",
"pattern_type": "stix",
"valid_from": "2024-07-18T00:00:00Z"
},
{
"type": "domain-name",
"spec_version": "2.1",
"id": "domain-name--b252f8d7-5b63-4b59-9d58-8f313db76c35",
"value": "ahilesopolker.com",
"object_marking_refs": [ "marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da" ],
"created": "2024-07-18T00:00:00Z",
"modified": "2024-07-18T00:00:00Z"
}
],
},
"success": true,
"errors": [],
"messages": []
}
```
### Domain Intelligence
Get Domain Details
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/intel/domain?domain=cloudflare.com" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
# Example response:
{
"result": {
"domain": "cloudflare.com",
"resolves_to_refs": [
{
"id": "ipv4-addr--71f6bb54-e0c5-5e7d-b939-5698fc15a102",
"value": "104.16.133.229"
},
{
"id": "ipv4-addr--015b0df4-7fcd-5409-9b56-cfd300c662f6",
"value": "104.16.132.229"
},
{
"id": "ipv6-addr--4a7455cd-e8d0-5bfb-8bdb-f6ebb1759508",
"value": "2606:4700::6810:85e5"
},
{
"id": "ipv6-addr--68f89579-7204-5ebd-a851-e91b3a86fc6d",
"value": "2606:4700::6810:84e5"
}
],
"application": {},
"content_categories": [
{
"id": 155,
"super_category_id": 26,
"name": "Technology"
},
{
"id": 26,
"name": "Technology"
}
],
"additional_information": {},
"type": "Apex domain",
"notes": "Apex domain given."
},
"success": true,
"errors": [],
"messages": []
}
```
### Domain History
Get Domain History
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/intel/domain-history?domain=cloudflare.com" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
{
"result": [
{
"domain": "cloudflare.com",
"categorizations": [
{
"categories": [
{
"id": 155,
"name": "Technology"
}
],
"start": "2020-12-16T19:49:30.533482Z",
"end": "2023-05-31T08:12:53.547029Z"
},
{
"categories": [
{
"id": 115,
"name": "Login Screens"
},
{
"id": 155,
"name": "Technology"
}
],
"start": "2023-05-31T08:12:53.547029Z"
}
]
}
],
"success": true,
"errors": [],
"messages": []
}
```
### IP Intelligence
Get IP Overview
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/intel/ip?ipv4=1.1.1.1" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
# Example response:
{
"result": [
{
"ip": "1.1.1.1",
"belongs_to_ref": {
"id": "autonomous-system--2fa28d71-3549-5a38-af05-770b79ad6ea8",
"value": 13335,
"type": "isp",
"country": "US",
"description": "CLOUDFLARENET"
},
"ip_lists": null,
"ptr_lookup": {
"ptr_domains": [
"one.one.one.one."
],
"ptr_lookup_errors": ""
},
"iana_reservations": []
}
],
"success": true,
"errors": [],
"messages": []
}
```
### Passive DNS by IP
Get Passive DNS by IP
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/intel/dns?ipv4=1.1.1.1&start=2023-07-15&end=2023-07-18&per_page=5" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
# Example response:
{
"result": {
"reverse_records": [
{
"first_seen": "2023-07-15T00:00:00Z",
"last_seen": "2023-07-18T00:00:00Z",
"hostname": "internet-ping.svc.starlink.com"
},
{
"first_seen": "2023-07-15T00:00:00Z",
"last_seen": "2023-07-18T00:00:00Z",
"hostname": "one.one.one.one"
},
{
"first_seen": "2023-07-15T00:00:00Z",
"last_seen": "2023-07-18T00:00:00Z",
"hostname": "ping.ui.com"
},
{
"first_seen": "2023-07-15T00:00:00Z",
"last_seen": "2023-07-18T00:00:00Z",
"hostname": "ping.ubnt.com"
},
{
"first_seen": "2023-07-15T00:00:00Z",
"last_seen": "2023-07-18T00:00:00Z",
"hostname": "bflow.tiki.video"
}
],
"count": 778,
"page": 1,
"per_page": 5
},
"success": true,
"errors": [],
"messages": []
}
```
### Phishing Intelligence
Get results for a URL scan
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/brand-protection/url-info?url=http://worcester-realistic-ellen-portland.trycloudflare.com/login.html" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
# Example response:
{
"errors": [],
"messages": [],
"result": [
{
"categorizations": [],
"model_results": [
{
"model_name": "MACHINE_LEARNING_v2",
"model_score": 0.999
}
],
"rule_matches": [
{
"description": "Match frequently used phishing kit (Discord, Facebook, Instagram, Twitter)",
"name": "phishkit.social"
}
],
"scan_status": {
"last_processed": "Wed, 19 Jul 2023 14:15:28 GMT",
"scan_complete": true,
"status_code": 200,
"submission_id": 23098147
},
"url": "http://worcester-realistic-ellen-portland.trycloudflare.com/login.html"
}
],
"success": true
}
```
### Miscategorization Intelligence
Create Miscategorization
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/intel/miscategorization" \
--header "Authorization: Bearer <API_TOKEN>" \
--header "Content-Type: application/json" \
--data '{
"content_adds": [
82
],
"content_removes": [
82
],
"indicator_type": "url",
"ip": null,
"security_adds": [
117,
131
],
"security_removes": [
117
],
"url": "https://wrong-category.example.com"
}'
# Example response:
{
"result": "",
"success": true,
"errors": [],
"messages": []
}
```
### WHOIS
Get WHOIS Record
```bash
curl "https://api.cloudflare.com/client/v4/accounts/{account_id}/intel/whois?domain=cloudflare.com" \
--header "Authorization: Bearer <API_TOKEN>" | jq .
# Example response:
{
"result": {
"domain": "cloudflare.com",
"created_date": "2009-02-17",
"updated_date": "2017-05-24",
"registrant": "DATA REDACTED",
"registrant_org": "DATA REDACTED",
"registrant_country": "United States",
"registrant_email": "https://domaincontact.cloudflareregistrar.com/cloudflare.com",
"registrar": "CloudFlare, Inc.",
"nameservers": [
"ns3.cloudflare.com",
"ns4.cloudflare.com",
"ns5.cloudflare.com",
"ns6.cloudflare.com",
"ns7.cloudflare.com"
]
},
"success": true,
"errors": [],
"messages": []
}
```
</page>
<page>
---
title: Investigate · Cloudflare Security Center docs
description: Investigate allows you to view a domain’s category, the IP it
belongs to, and whether the category has changed before. You can also see
which records it points to, including the country of origin and passive DNS
records. After searching with Investigate, you will get an API curl to
retrieve the same search results.
lastUpdated: 2024-10-17T14:10:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/investigate/
md: https://developers.cloudflare.com/security-center/investigate/index.md
---
User permission
All users can access Investigate. This includes accessing URL scanning, and filter passive DNS range.
Investigate allows you to view a domain’s category, the IP it belongs to, and whether the category has changed before. You can also see which records it points to, including the country of origin and passive DNS records. After searching with Investigate, you will get an API curl to retrieve the same search results.
You can learn more about the IP addresses in your logs by searching via the IP address to view its category and threat data. Enter any IP address, domain name, and hostname to see how it has been categorized from a threat perspective.
Investigate also shows [Web Application Firewall](https://developers.cloudflare.com/waf/) analytics for your websites behind Cloudflare to help you discover what your vulnerabilities are, where attacks come from, and what to do about it.
</page>
<page>
---
title: Security Insights · Cloudflare Security Center docs
description: "Security Insights provides you with a list of insights, covering
different areas of your Cloudflare environment, such as: Cloudflare account
settings, DNS record configurations, SSL/TLS certificates configurations,
Cloudflare Access configurations and Cloudflare WAF configurations."
lastUpdated: 2025-10-24T15:44:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/security-center/security-insights/
md: https://developers.cloudflare.com/security-center/security-insights/index.md
---
User permission
Ensure your user has one of the necessary roles to access Security Insights. Refer to [Roles and permissions](https://developers.cloudflare.com/security-center/security-insights/roles-and-permissions/) for more information.
Security Insights provides you with a list of insights, covering different areas of your Cloudflare environment, such as: Cloudflare account settings, DNS record configurations, SSL/TLS certificates configurations, Cloudflare Access configurations and Cloudflare WAF configurations.
Listed below are the specific insights currently available:
| Insight Name | Description |
| - | - |
| [CASB integration status](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/troubleshooting/) | We detect unhealthy CASB integrations. |
| [Dangling `A` Records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#a-and-aaaa) | A record is pointing to an IPv4 address that you might no longer control. You are at risk of a subdomain takeover. |
| [Dangling `AAAA` Records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#a-and-aaaa) | A record is pointing to an IPv6 address that you might no longer control. You are at risk of a subdomain takeover. |
| [Dangling `CNAME` Records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#a-and-aaaa) | A record is pointing to a resource that cannot be found. You are at risk of a subdomain takeover. |
| [DMARC Record Errors](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#dmarc) | We detect an incorrect or missing `DMARC` record. |
| [Domains missing TLS Encryption](https://developers.cloudflare.com/ssl/get-started/) | We detect that there is no TLS encryption for this domain. |
| [Domains supporting older TLS version](https://developers.cloudflare.com/ssl/reference/protocols/) | This domain supports older versions of the TLS protocol. |
| [Domains without 'Always Use HTTPS'](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/always-use-https/) | HTTP requests to this domain may not redirect to its HTTPS equivalent. |
| [Domains without HSTS](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/http-strict-transport-security/) | HTTP Strict Transport Security (`HSTS`), is a header which allows a website to specify and enforce security policy in client web browsers. This policy enforcement protects secure websites from downgrade attacks SSL stripping and cookie hijacking. |
| [Exposed RDP Servers](https://developers.cloudflare.com/cloudflare-one/networks/connectors/cloudflare-tunnel/use-cases/rdp/) | We detect an RDP server that is exposed to the public Internet. |
| [Get notified of malicious client-side scripts](https://developers.cloudflare.com/page-shield/alerts/) | We detect that Page Shield alerts are not configured. You will not receive notifications when we detect potential malicious scripts executing in your client-side environment. |
| [Increased body response size detected on API endpoints](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/) | Investigate changes, abuse, or successful attacks that may have led to this increase in response body size. |
| [Increased errors detected on API endpoints](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/) | Investigate changes, abuse, or successful attacks that may have led to this increase in errors. |
| [Increased latency detected on API endpoints](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/) | Investigate changes, abuse, or successful attacks that may have led to this increase in response latency. |
| [Managed Rules not deployed](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/) | No managed rules deployed on a WAF protected domain. |
| [Upgrade to new Managed Rules](https://developers.cloudflare.com/waf/reference/legacy/old-waf-managed-rules/upgrade/) | Upgrade to new Managed Rules system required for optimal protection. |
| [Mixed-authentication API endpoints detected](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/#managed-labels) | Not all of the successful requests against API endpoints carried session identifiers. |
| [New API endpoints detected](https://developers.cloudflare.com/api-shield/security/api-discovery/) | API Discovery detects new API endpoints in your zone's traffic. |
| [New CASB integrations found](https://developers.cloudflare.com/cloudflare-one/integrations/cloud-and-saas/) | New CASB integrations have been found. |
| [Overprovisioned Access Policies](https://developers.cloudflare.com/cloudflare-one/access-controls/policies/) | We detect an Access policy to allow everyone access to your application. |
| [Page Shield not enabled](https://developers.cloudflare.com/page-shield/get-started/) | Page Shield helps meet PCI DSS v4.0 compliance regarding requirement 6.4.3. |
| [SPF Record Errors](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#spf) | We detect an incorrect or missing `SPF` record. |
| [Schema Validation missing from eligible API endpoints](https://developers.cloudflare.com/api-shield/security/schema-validation/) | Apply the learned schema to protect your API against fuzzing attacks. |
| [Sensitive data in API response](https://developers.cloudflare.com/api-shield/management-and-monitoring/#sensitive-data-detection) | Sensitive data in API responses detected. |
| [Turn on JavaScript Detection](https://developers.cloudflare.com/bots/additional-configurations/javascript-detections/) | One or more of your Bot Management enabled zones does not have JavaScript Detection enabled, which is a critical part of our bot detection suite. |
| [Unassigned Access seats](https://developers.cloudflare.com/cloudflare-one/) | We detect a Zero Trust subscription that is not configured yet. |
| [Unauthenticated API endpoints detected](https://developers.cloudflare.com/api-shield/management-and-monitoring/endpoint-labels/#managed-labels) | None of the successful requests against API endpoints carried session identifiers. |
| [Unprotected Cloudflare Tunnels](https://developers.cloudflare.com/cloudflare-one/access-controls/applications/http-apps/self-hosted-public-app/#4-connect-your-origin-to-cloudflare) | We detect an application that is served by a Cloudflare Tunnel but not protected by a corresponding Access policy. |
| [Unproxied `A` Records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#a-and-aaaa) | This DNS record is not proxied by Cloudflare. Cloudflare can not protect this origin because it is exposed to the public Internet. |
| [Unproxied `AAAA` Records](https://developers.cloudflare.com/dns/manage-dns-records/reference/dns-record-types/#a-and-aaaa) | This DNS record is not proxied by Cloudflare. Cloudflare can not protect this origin because it is exposed to the public Internet. |
| [Unproxied `CNAME` Records](https://developers.cloudflare.com/dns/proxy-status/#dns-only-records) | This DNS record is not proxied by Cloudflare. Cloudflare can not protect this origin because it is exposed to the public Internet. |
| [Users without MFA](https://developers.cloudflare.com/fundamentals/user-profiles/2fa/) | We detect that a Cloudflare administrative user has not enabled multifactor authentication. |
| [Zones without WAF Managed Rules](https://developers.cloudflare.com/waf/managed-rules/) | We detect that this domain does not have the WAF's Managed Rules enabled. You are at risk from zero-day and other common vulnerabilities. |
| [No Turnstile enabled](https://developers.cloudflare.com/turnstile/) | We detect that there is no Turnstile widget configured on the account. |
For more information on available operations for Security Insights, refer to [Review Security Insights](https://developers.cloudflare.com/security-center/security-insights/review-insights/).
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Smart Shield docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/smart-shield/404/
md: https://developers.cloudflare.com/smart-shield/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Concepts · Cloudflare Smart Shield docs
lastUpdated: 2025-09-17T12:18:58.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/smart-shield/concepts/
md: https://developers.cloudflare.com/smart-shield/concepts/index.md
---
* [Network diagram](https://developers.cloudflare.com/smart-shield/concepts/network-diagram/)
* [Connection reuse](https://developers.cloudflare.com/smart-shield/concepts/connection-reuse/)
</page>
<page>
---
title: Configuration · Cloudflare Smart Shield docs
lastUpdated: 2025-09-17T12:18:58.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/smart-shield/configuration/
md: https://developers.cloudflare.com/smart-shield/configuration/index.md
---
* [Smart Tiered Cache](https://developers.cloudflare.com/smart-shield/configuration/smart-tiered-cache/)
* [Regional Tiered Cache](https://developers.cloudflare.com/smart-shield/configuration/regional-tiered-cache/)
* [Cache Reserve](https://developers.cloudflare.com/smart-shield/configuration/cache-reserve/)
* [Argo Smart Routing](https://developers.cloudflare.com/smart-shield/configuration/argo/)
* [Health Checks](https://developers.cloudflare.com/smart-shield/configuration/health-checks/)
* [Dedicated CDN Egress IPs](https://developers.cloudflare.com/smart-shield/configuration/dedicated-egress-ips/)
</page>
<page>
---
title: Get started · Cloudflare Smart Shield docs
description: Smart Shield is available to all customers as an opt-in configuration.
lastUpdated: 2026-01-21T10:23:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/smart-shield/get-started/
md: https://developers.cloudflare.com/smart-shield/get-started/index.md
---
Smart Shield is available to all customers as an opt-in configuration.
## Before you begin
* You should have a Cloudflare account and [onboard your domain](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/).
* Also make sure the relevant DNS records are set to [proxied](https://developers.cloudflare.com/dns/proxy-status/).
## Steps
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Speed** > **Smart Shield**.
3. (Optional) Explore the different [available packages](#packages-and-availability).
4. Select **Get started for free** or choose a different package and select **Continue** to proceed to the guided onboarding flow.
Access analytics and get insights through the [Observatory](https://developers.cloudflare.com/speed/observatory/) dashboard.
## Packages and availability
### Smart Shield
* Includes [Smart Tiered Cache](https://developers.cloudflare.com/smart-shield/configuration/smart-tiered-cache/) and [Connection Reuse](https://developers.cloudflare.com/smart-shield/concepts/connection-reuse/).
* Pro, Business, and Enterprise customers also have access to [Health Checks](https://developers.cloudflare.com/smart-shield/configuration/health-checks/).
### Smart Shield + Argo
* Includes [Smart Tiered Cache](https://developers.cloudflare.com/smart-shield/configuration/smart-tiered-cache/), [Connection Reuse](https://developers.cloudflare.com/smart-shield/concepts/connection-reuse/), and [Argo Smart Routing](https://developers.cloudflare.com/smart-shield/configuration/argo/).
* Pro, Business, and Enterprise customers also have access to [Health Checks](https://developers.cloudflare.com/smart-shield/configuration/health-checks/).
### Smart Shield Advanced
* Includes [Smart Tiered Cache](https://developers.cloudflare.com/smart-shield/configuration/smart-tiered-cache/), [Connection Reuse](https://developers.cloudflare.com/smart-shield/concepts/connection-reuse/), [Argo Smart Routing](https://developers.cloudflare.com/smart-shield/configuration/argo/), and additional caching customization with [Regional Tiered Cache](https://developers.cloudflare.com/smart-shield/configuration/regional-tiered-cache/) and [Cache Reserve](https://developers.cloudflare.com/smart-shield/configuration/cache-reserve/).
* Pro, Business, and Enterprise customers also have access to [Health Checks](https://developers.cloudflare.com/smart-shield/configuration/health-checks/).
Dedicated CDN Egress IPs
Enterprise customers also have the option to configure [Dedicated CDN Egress IPs](https://developers.cloudflare.com/smart-shield/configuration/dedicated-egress-ips/), allowing you to increase origin security by only allowing traffic from a small list of IP addresses. If you are interested, reach out to your account team.
Dedicated CDN Egress IPs will be available for other plans in the future.
## Further reading
* [Network diagram](https://developers.cloudflare.com/smart-shield/concepts/network-diagram/)
* [Connection reuse](https://developers.cloudflare.com/smart-shield/concepts/connection-reuse/)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Spectrum docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/spectrum/404/
md: https://developers.cloudflare.com/spectrum/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: About · Cloudflare Spectrum docs
description: For more information about concepts related to Spectrum, refer to
the sections below.
lastUpdated: 2024-09-12T14:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/spectrum/about/
md: https://developers.cloudflare.com/spectrum/about/index.md
---
For more information about concepts related to Spectrum, refer to the sections below.
* [BYOIP](https://developers.cloudflare.com/spectrum/about/byoip/)
* [Cloudflare Load Balancing](https://developers.cloudflare.com/spectrum/about/load-balancer/)
* [DDoS Protection for Spectrum](https://developers.cloudflare.com/spectrum/about/ddos-for-spectrum/)
* [FTP](https://developers.cloudflare.com/spectrum/about/ftp/)
* [Static IP](https://developers.cloudflare.com/spectrum/about/static-ip/)
</page>
<page>
---
title: Get started · Cloudflare Spectrum docs
description: Spectrum is available on all paid plans. Pro and Business support
selected protocols only, whereas Enterprise supports all TCP and UDP based
traffic. Refer to Configuration options for more configuration details.
lastUpdated: 2025-10-09T07:47:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/spectrum/get-started/
md: https://developers.cloudflare.com/spectrum/get-started/index.md
---
Spectrum is available on all paid plans. Pro and Business support selected protocols only, whereas Enterprise supports all TCP and UDP based traffic. Refer to [Configuration options](https://developers.cloudflare.com/spectrum/reference/configuration-options/) for more configuration details.
To create a Spectrum application, you can either use an IP address, a CNAME Record or a load balancer. Independently of the method you use, you can create the application through the dashboard or via [API](https://developers.cloudflare.com/api/resources/spectrum/subresources/apps/methods/list/).
Certain fields in Spectrum request and response bodies require an Enterprise plan. Refer to the [Settings by plan](https://developers.cloudflare.com/spectrum/reference/settings-by-plan/) page for more details.
## Create a Spectrum application using an IP address
To create a Spectrum application using an IP address, Cloudflare normally assigns you an arbitrary IP from Cloudflare’s IP pool to your application. If you want to use your own IP addresses, you can use [BYOIP](https://developers.cloudflare.com/spectrum/about/byoip/) or you can also use a [Static IP](https://developers.cloudflare.com/spectrum/about/static-ip/). In these two last cases, you need to create your Spectrum application through the API, as these features are not available via dash. When using the API, the field `origin_direct` takes as input the IP address.
Add your application via Dashboard
1. In the Cloudflare dashboard, go to the **Spectrum** page.
[Go to **Spectrum**](https://dash.cloudflare.com/?to=/:account/:zone/spectrum)
2. Select **Create an Application**. If this is your first time using Spectrum, the **Create an Application** modal appears.
3. Select your **Application Type**.
4. Under **Domain**, enter the domain that will use Spectrum.
5. Under **Edge Port**, enter the port Cloudflare should use for your application.
6. Under **Origin**, enter your application's origin IP and port.
7. If your application requires the client IP and supports [Proxy Protocol](https://www.haproxy.com/blog/haproxy/proxy-protocol/), enable **Proxy Protocols**. Proxy Protocol is a method for a proxy like Cloudflare to send the client IP to the origin application.
8. Select **Add**.
Add your application via API
Below is a curl example and the associated data being posted to the API.
**API example:**
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Zone Settings Write`
```bash
curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/spectrum/apps" \
--request POST \
--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \
--json '{
"protocol": "tcp/22",
"dns": {
"type": "CNAME",
"name": "ssh.example.com"
},
"origin_direct": [
"tcp://192.0.2.1:22"
],
"proxy_protocol": "off",
"ip_firewall": true,
"tls": "full",
"edge_ips": {
"type": "dynamic",
"connectivity": "all"
},
"traffic_type": "direct",
"argo_smart_routing": true
}'
```
**Example data:**
```json
{
"success": true,
"errors": [],
"messages": [],
"result": {
"id": "ea95132c15732412d22c1476fa83f27a",
"protocol": "tcp/22",
"dns": {
"type": "CNAME",
"name": "ssh.example.com"
},
"origin_direct": ["tcp://192.0.2.1:22"],
"proxy_protocol": "off",
"ip_firewall": true,
"tls": "full",
"edge_ips": {
"type": "dynamic",
"connectivity": "all"
},
"traffic_type": "direct",
"argo_smart_routing": true,
"created_on": "2014-01-02T02:20:00Z",
"modified_on": "2014-01-02T02:20:00Z"
}
}
```
## Create a Spectrum application using a CNAME record
To create a Spectrum application using a CNAME record, you will need to create a [CNAME record](https://www.cloudflare.com/learning/dns/dns-records/dns-cname-record/) on your Cloudflare hosted zone that points to your origin's hostname. This is required to resolve to your hostname origin. Refer to [Create DNS records](https://developers.cloudflare.com/dns/manage-dns-records/how-to/create-dns-records/#create-dns-records), for more information. When using a CNAME as an origin, note that Cloudflare needs to be authoritative for that zone. When using the API, the `origin_dns` field takes as input the CNAME record.
Add your application via Dashboard
1. In the Cloudflare dashboard, go to the **Spectrum** page.
[Go to **Spectrum**](https://dash.cloudflare.com/?to=/:account/:zone/spectrum)
2. Select **Create an Application**. If this is your first time using Spectrum, the **Create an Application** modal appears.
3. Select your **Application Type**.
4. Under **Domain**, enter the domain that will use Spectrum.
5. Under **Edge Port**, enter the port Cloudflare should use for your application.
6. Under **Origin**, enter your `CNAME` record name.
7. Select **Add**.
Add your application via API
Below is a curl example and the associated data being posted to the API.
**API example:**
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Zone Settings Write`
```bash
curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/spectrum/apps" \
--request POST \
--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \
--json '{
"dns": {
"type": "CNAME",
"name": "spectrum-cname.example.com"
},
"ip_firewall": false,
"protocol": "tcp/22",
"proxy_protocol": "off",
"tls": "off",
"origin_dns": {
"name": "cname-to-origin.example.com",
"ttl": 1200
},
"origin_port": 22
}'
```
**Example data:**
```json
{
"dns": {
"type": "CNAME",
"name": "spectrum-cname.example.com"
},
"ip_firewall": false,
"protocol": "tcp/22",
"proxy_protocol": "off",
"tls": "off",
"origin_dns": {
"name": "cname-to-origin.example.com",
"ttl": 1200
},
"origin_port": 22
}
```
## Create a Spectrum application using a load balancer
To create a Spectrum application using a load balancer, you will need to generate a load balancer from the dashboard or via the API. Refer to the [Load Balancing documentation](https://developers.cloudflare.com/load-balancing/additional-options/spectrum/#1-configure-your-load-balancer) for more details.
Note
To prevent issues with DNS resolution for a Spectrum application, do not use the same Spectrum hostname as a current Load Balancing hostname.
Add your application via Dashboard
1. In the Cloudflare dashboard, go to the **Spectrum** page.
[Go to **Spectrum**](https://dash.cloudflare.com/?to=/:account/:zone/spectrum)
2. Select **Create an Application**. If this is your first time using Spectrum, the **Create an Application** modal appears.
3. Select your **[Application Type](https://developers.cloudflare.com/spectrum/reference/configuration-options/#application-type)**.
4. Under **Domain**, enter the domain that will use Spectrum.
5. Under **Edge Port**, enter the port Cloudflare should use for your application.
6. Under **Origin**, select **Load Balancer**.
7. Select the load balancer you want to use from the dropdown. Disabled load balancers will not show on the **Load Balancer** menu.
8. Select **Add**.
Add your application via API
Below is a curl example and the associated data being posted to the API.
**API example:**
Required API token permissions
At least one of the following [token permissions](https://developers.cloudflare.com/fundamentals/api/reference/permissions/) is required:
* `Zone Settings Write`
```bash
curl "https://api.cloudflare.com/client/v4/zones/$ZONE_ID/spectrum/apps" \
--request POST \
--header "Authorization: Bearer $CLOUDFLARE_API_TOKEN" \
--json '{
"dns": {
"type": "CNAME",
"name": "spectrum-cname.example.com"
},
"ip_firewall": false,
"protocol": "tcp/22",
"proxy_protocol": "off",
"tls": "off",
"origin_dns": {
"name": "cname-to-origin.example.com",
"ttl": 1200
},
"origin_port": 22
}'
```
**Example data:**
```json
{
"dns": {
"type": "CNAME",
"name": "spectrum-cname.example.com"
},
"ip_firewall": false,
"protocol": "tcp/22",
"proxy_protocol": "off",
"tls": "off",
"origin_dns": {
"name": "cname-to-origin.example.com",
"ttl": 1200
},
"origin_port": 22
}
```
## View traffic
You can now proxy traffic through Cloudflare without additional configuration. As you run traffic through Cloudflare, you will see the last minute of traffic from **Spectrum** in the dashboard.
If you have any feedback, please [let us know](https://community.cloudflare.com/c/website-application-performance/spectrum/48).
</page>
<page>
---
title: Glossary · Cloudflare Spectrum docs
description: Review the definitions for terms used across Cloudflare's Spectrum
documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/spectrum/glossary/
md: https://developers.cloudflare.com/spectrum/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Spectrum documentation.
| Term | Definition |
| - | - |
| ACK (Acknowledge) | The final step in the TCP three-way handshake, confirming the establishment of a connection. |
| FTP (File Transfer Protocol) | A standard network protocol used for transferring files from one host to another over a TCP-based network. |
| FTPS (File Transfer Protocol Secure) | An extension of FTP that adds support for the Transport Layer Security (TLS) or Secure Sockets Layer (SSL) cryptographic protocols. |
| layer 3 | The network layer in the OSI model, responsible for logical addressing, routing, and forwarding of data between devices on different networks. |
| layer 4 | The transport layer in the OSI model, managing end-to-end communication, error-checking, and flow control. |
| MQTT (Message Queuing Telemetry Transport) | A lightweight, publish-subscribe messaging protocol often used for communication in the Internet of Things (IoT) and other resource-constrained scenarios. |
| OSI model (Open Systems Interconnection model) | A conceptual framework that standardizes the functions of a telecommunication or computing system into seven abstraction layers. |
| proxy protocol | A protocol used by network proxies to convey client connection information to the destination server, facilitating proper handling of client requests. |
| reverse proxy | A server that handles requests on behalf of clients, forwarding them to backend servers and managing tasks like load balancing and security. |
| SFTP (Secure File Transfer Protocol) | A secure file transfer protocol that uses the Secure Socket Shell (SSH) protocol for encryption and authentication. |
| SMTP Server (Simple Mail Transfer Protocol Server) | A server responsible for sending, receiving, and relaying email messages over a network, following the SMTP protocol. |
| SYN (Synchronize) | The initial step in establishing a TCP connection, where a device requests a connection with another by sending a SYN packet. |
| SYN-ACK (Synchronize-Acknowledge) | The second step in the TCP three-way handshake, where the server responds to a SYN request with a SYN-ACK packet. |
| TCP (Transmission Control Protocol) | A connection-oriented protocol in the transport layer of the Internet Protocol Suite, providing reliable and ordered delivery of data between devices. |
| UDP (User Datagram Protocol) | UDP (User Datagram Protocol) is a connectionless transport layer protocol that provides fast and lightweight data transmission between devices on a network, prioritizing speed over reliability. |
</page>
<page>
---
title: How to · Cloudflare Spectrum docs
description: For more information on completing Spectrum related tasks, refer to
the sections below.
lastUpdated: 2024-09-12T14:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/spectrum/how-to/
md: https://developers.cloudflare.com/spectrum/how-to/index.md
---
For more information on completing Spectrum related tasks, refer to the sections below.
* [Enable Proxy protocol](https://developers.cloudflare.com/spectrum/how-to/enable-proxy-protocol/)
</page>
<page>
---
title: Protocols per plan · Cloudflare Spectrum docs
description: On this table, you have information about which protocols are
available per plan.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/spectrum/protocols-per-plan/
md: https://developers.cloudflare.com/spectrum/protocols-per-plan/index.md
---
On this table, you have information about which protocols are available per plan.
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | Paid add-on | Paid add-on | Yes |
| TCP | No | No | No | Paid add-on |
| UDP | No | No | No | Paid add-on |
| HTTP | No | No | No | Paid add-on |
| HTTPS | No | No | No | Paid add-on |
| Minecraft (one app allowed) | No | Yes | Yes | Yes |
| SSH (one app allowed) | No | Yes | Yes | Yes |
| RDP (one app allowed) | No | No | Yes | Yes |
</page>
<page>
---
title: Reference · Cloudflare Spectrum docs
description: For more information related to Spectrum, refer to the sections below.
lastUpdated: 2024-09-12T14:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/spectrum/reference/
md: https://developers.cloudflare.com/spectrum/reference/index.md
---
For more information related to Spectrum, refer to the sections below.
* [Analytics](https://developers.cloudflare.com/spectrum/reference/analytics/)
* [Configuration options](https://developers.cloudflare.com/spectrum/reference/configuration-options/)
* [Event logs](https://developers.cloudflare.com/spectrum/reference/logs/)
* [Limitations](https://developers.cloudflare.com/spectrum/reference/limitations/)
* [Settings by plan](https://developers.cloudflare.com/spectrum/reference/settings-by-plan/)
* [Simple Proxy Protocol Header](https://developers.cloudflare.com/spectrum/reference/simple-proxy-protocol-header/)
* [Why Spectrum-enabled hostnames might appear in Layer 7 Analytics](https://developers.cloudflare.com/spectrum/reference/layer-7-analytics/)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Speed docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/speed/404/
md: https://developers.cloudflare.com/speed/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Aggregated Internet Measurement · Cloudflare Speed docs
description: Aggregated Internet Measurement (AIM) helps you understand your
Internet quality to identify scenarios that your Internet connection is good
or bad for. Typically, an Internet speed test provides you with upload and
download speeds, which may not always provide a holistic view of your Internet
quality.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/speed/aim/
md: https://developers.cloudflare.com/speed/aim/index.md
---
Aggregated Internet Measurement (AIM) helps you understand your Internet quality to identify scenarios that your Internet connection is good or bad for. Typically, an Internet speed test provides you with upload and download speeds, which may not always provide a holistic view of your Internet quality.
AIM uses a scoring rubric that assigns point values based on speed tests to help you understand how your Internet quality will perform for streaming, gaming, and webchat/real-time communication (RTC).
## Scoring Rubric
AIM analyzes the following metrics to generate your score:
* Latency
* Packet Loss
* Download
* Upload
* Loaded Latency
* Jitter
After the test is run and a point value is assigned to each metric, the points are translated to a network score for streaming, gaming, and webchat/RTC. These scores will indicate how good your Internet is in each of these scenarios.
The possible network scores are:
* Bad
* Poor
* Average
* Good
* Great
## Improve your network score
You have a few options to help improve network scores.
* **Switch to a wired connection.** When possible, switch to a wired connection instead of wireless to avoid performance issues due to radio interference and signal strength.
* **Move closer to your router.** If you are unable to use a wired connection, try to move closer to your wireless router. Signal strength drops as you move away from your wireless router and a weaker signal means poorer connectivity. Keep in mind that any objects or materials between you and your wireless router can also have a negative impact on signal strength.
* **Upgrade your router.** Ensure you are using a router capable of handling smarter queueing with hardware that will not fall over under load.
* **Contact your ISP.** If you’re using a wired connection or have a good connection to your wireless router and are still seeing issues, you may have issues with your Internet connection and should reach out to your ISP.
</page>
<page>
---
title: Glossary · Cloudflare Speed docs
description: Review the definitions for terms used across Cloudflare's Speed documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/speed/glossary/
md: https://developers.cloudflare.com/speed/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Speed documentation.
| Term | Definition |
| - | - |
| bandwidth | The maximum rate of data transfer across a network. |
| brotli compression | Brotli compression is a data compression algorithm developed by Google, optimized for web content, and designed to achieve higher compression ratios than traditional algorithms like Gzip. |
| compression | The process of reducing the size of files or data to speed up their transfer over the network. |
| core web vitals | Core web vitals are a set of user-centric performance metrics, including Largest Contentful Paint (LCP), Cumulative Layout Shift (CLS), and First Input Delay (FID), used by Google to assess the overall user experience of a webpage. |
| cumulative layout shift (CLS) | Cumulative layout shift (CLS) is a web performance metric that quantifies the visual stability of a webpage by measuring the sum of unexpected layout shifts of elements during the page's loading and rendering process. |
| first contentful paint (FCP) | First contentful paint (FCP) is a web performance metric that measures the time it takes for the first piece of content to be rendered on the screen during the loading of a web page. |
| first input delay (FID) | First input delay (FID) is a web performance metric that measures the delay between a user's first interaction with a page (for example, clicking a button) and the moment the browser responds, indicating the page's interactivity and responsiveness. |
| interaction to next paint (INP) | Interaction to next paint (INP) is a web performance metric that measures the time it takes for a web page to become interactive and respond to user input after the initial paint, providing insights into the user experience during the interaction phase of page loading. |
| largest contentful paint (LCP) | Largest contentful paint (LCP) is a web performance metric that measures the time it takes for the largest content element to be fully rendered and visible to the user during the loading of a web page. |
| latency | The delay between a user action and the corresponding response from the system. |
| lazy loading | Loading images or other resources only when they are about to be displayed, rather than loading everything at once. |
| minification | The process of removing unnecessary characters from code (such as whitespace or comments) to reduce file size and improve loading times. |
| page load time | The time it takes for a web page to fully load in a user's browser. |
| real user monitoring (RUM) | Real user monitoring (RUM) is a web performance monitoring technique that collects and analyzes data based on actual user interactions and experiences, providing insights into how users interact with a website or application in real-time. |
| render time | The time it takes for a browser to display a fully rendered web page after receiving the necessary resources. |
| search engine optimization (SEO) | SEO, or search engine optimization, is the practice of optimizing online content to improve its visibility and ranking in search engine results, thereby increasing organic traffic and relevance. |
| server response time | The time it takes for a server to respond to a request from a user's browser. |
| speed index | Speed index is a web performance metric that quantifies how quickly a user perceives a webpage to load by measuring the visual progression of content rendering over time, providing a comprehensive assessment of the overall user experience during page loading. |
| synthetic test | A synthetic test is an artificial simulation of user interactions and system behaviors designed to evaluate and measure the performance, responsiveness, and functionality of a website or application under controlled conditions. |
| time to first byte (TTFB) | Time to first byte (TTFB) is the duration measured from the initiation of a web page request to the moment the first byte of data is received by the user's browser from the web server, indicating the server's initial response time. |
| time to interactive (TTI) | Time to interactive (TTI) is a web performance metric that measures the time it takes for a web page to become fully interactive and responsive to user input, indicating when users can effectively engage with and use the page. |
| total blocking time (TBT) | Total blocking time (TBT) is a web performance metric that measures the total amount of time between First Contentful Paint (FCP) and Time to Interactive (TTI) where the main thread was blocked for long enough to prevent input responsiveness. |
</page>
<page>
---
title: Observatory (beta) · Cloudflare Speed docs
description: Observatory uses synthetic tests and real user data from browsers
to assess the performance of your website. These data sources produce metrics
that provide different types of insights into your website’s performance.
Cloudflare then uses the analysis run by Observatory to recommend
optimizations with the tools that best suit your performance issues.
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/speed/observatory/
md: https://developers.cloudflare.com/speed/observatory/index.md
---
Observatory uses synthetic tests and real user data from browsers to assess the performance of your website. These data sources produce metrics that provide different types of insights into your website’s performance. Cloudflare then uses the analysis run by Observatory to recommend optimizations with the tools that best suit your performance issues.
## Synthetic tests
As its name suggests, synthetic testing uses servers to simulate the conditions that a user might encounter when accessing your website. This has the advantage of being consistent, as the conditions are easily replicated each time the test is run. It also allows you to have an analysis of how a code change might affect the overall performance of your website, as well as test any URL you want. However, due to its synthetic nature, it cannot replicate the breadth and diversity of different conditions that real users will experience.
Observatory provides two different types of synthetic tests:
### Browser test
The browser test loads the requested page in a headless browser and runs Google Lighthouse on it. This reports key performance metrics and provides light suggestions for improvement.
### Network test
The network test is focused on giving a detailed breakdown of the network and back-end performance of an endpoint. For more information on metrics collected, refer to [Network monitoring metrics](https://developers.cloudflare.com/speed/observatory/test-results/#network-monitoring-metrics).
### Network comparison test
You can also compare network tests in Observatory by selecting any two completed tests. The results for each test are displayed side by side as histograms, allowing you to easily visualize and compare the full distribution of data points across both tests.
## Real user monitoring (RUM)
Real user monitoring (also known as RUM), on the other hand, captures real metrics from real users accessing a website. This provides information that synthetic tests cannot capture, as users might access your website from different parts of the world, with different network conditions, ISPs, browsers and computer hardware. However, RUM data is only applied to your own website. Real user data also includes two user interaction metrics that synthetic tests do not offer - [First Input Delay (FID)](https://web.dev/fid/) and [Interaction to Next Paint (INP)](https://web.dev/inp/).
Free customers have RUM enabled automatically, with EU traffic excluded, and can switch it off if they prefer. Customers on other plans may enable RUM as needed.
[Run test](https://developers.cloudflare.com/speed/observatory/run-speed-test/)
</page>
<page>
---
title: Settings · Cloudflare Speed docs
description: The Optimization section will show you a list of Cloudflare
products that are recommended for enhancing your website's performance.
lastUpdated: 2025-09-26T10:03:24.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/speed/optimization/
md: https://developers.cloudflare.com/speed/optimization/index.md
---
The Optimization section will show you a list of Cloudflare products that are recommended for enhancing your website's performance.
* [Recommendations](https://developers.cloudflare.com/speed/optimization/recommendations/)
* [Measurement](https://developers.cloudflare.com/speed/optimization/measurement/)
* [Image optimization](https://developers.cloudflare.com/speed/optimization/images/)
* [Content optimizations](https://developers.cloudflare.com/speed/optimization/content/)
* [Protocol optimization](https://developers.cloudflare.com/speed/optimization/protocol/)
</page>
<page>
---
title: Smart Shield · Cloudflare Speed docs
lastUpdated: 2025-09-26T10:03:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/speed/smart-shield/
md: https://developers.cloudflare.com/speed/smart-shield/index.md
---
</page>
<page>
---
title: Troubleshooting · Cloudflare Speed docs
description: The following topics are useful for troubleshooting Speed issues.
lastUpdated: 2025-08-12T17:54:27.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/speed/troubleshooting/
md: https://developers.cloudflare.com/speed/troubleshooting/index.md
---
The following topics are useful for troubleshooting Speed issues.
Filter resources...
[FAQ](https://developers.cloudflare.com/speed/observatory/faq/)
[FAQ | Cloudflare Fonts](https://developers.cloudflare.com/speed/optimization/content/fonts/faq/)
[Cloudflare Fonts troubleshooting](https://developers.cloudflare.com/speed/optimization/content/fonts/troubleshooting/)
[Content encoding issues](https://developers.cloudflare.com/speed/optimization/content/troubleshooting/content-encoding-issues/)
[Turn off Auto Minify via API](https://developers.cloudflare.com/speed/optimization/content/troubleshooting/disable-auto-minify/)
[Image optimization on optimized images](https://developers.cloudflare.com/speed/optimization/images/troubleshooting/multiple-optimizations/)
[Troubleshoot missing images](https://developers.cloudflare.com/speed/optimization/images/troubleshooting/troubleshooting-missing-images/)
[Enhanced HTTP/2 Prioritization negatively affects iOS/Safari devices](https://developers.cloudflare.com/speed/optimization/protocol/troubleshooting/enhanced-http2-prioritization-ios-safari/)
[Troubleshoot protocol issues](https://developers.cloudflare.com/speed/optimization/protocol/troubleshooting/protocol-troubleshooting/)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Stream docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/404/
md: https://developers.cloudflare.com/stream/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Changelog · Cloudflare Stream docs
description: Subscribe to RSS
lastUpdated: 2025-02-13T19:35:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/changelog/
md: https://developers.cloudflare.com/stream/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/stream/changelog/index.xml)
## 2025-03-12
**Stream Live WebRTC WHIP/WHEP Upgrades**
Stream Live WHIP/WHEP will be progressively migrated to a new implementation powered by Cloudflare Realtime (Calls) starting Thursday 2025-03-13. No API or integration changes will be required as part of this upgrade. Customers can expect an improved playback experience. Otherwise, this should be a transparent change, although some error handling cases and status reporting may have changed.
For more information review the [Stream Live WebRTC beta](https://developers.cloudflare.com/stream/webrtc-beta/) documentation.
## 2025-02-10
**Stream Player ad support adjustments for Google Ad Exchange Verification**
Adjustments have been made to the Stream player UI when playing advertisements called by a customer-provided VAST or VMAP `ad-url` argument:
A small progress bar has been added along the bottom of the player, and the shadow behind player controls has been reduced. These changes have been approved for use with Google Ad Exchange.
This only impacts customers using the built-in Stream player and calling their own advertisements; Stream never shows ads by default. For more information, refer to [Using the Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/#basic-options).
## 2025-01-30
**Expanded Language Support for Generated Captions**
Eleven new languages are now supported for transcription when using [generated captions](https://developers.cloudflare.com/stream/edit-videos/adding-captions/#generate-a-caption), available for free for video stored in Stream.
## 2024-08-15
**Full HD encoding for Portrait Videos**
Stream now supports full HD encoding for portrait/vertical videos. Videos with a height greater than their width will now be constrained and prepared for adaptive bitrate renditions based on their width. No changes are required to benefit from this update. For more information, refer to [the announcement](https://blog.cloudflare.com/introducing-high-definition-portrait-video-support-for-cloudflare-stream).
## 2024-08-09
**Hide Viewer Count in Live Streams**
A new property `hideLiveViewerCount` has been added to Live Inputs to block access to the count of viewers in a live stream and remove it from the player. For more information, refer to [Start a Live Stream](https://developers.cloudflare.com/stream/stream-live/start-stream-live/).
## 2024-07-23
**New Live Webhooks for Error States**
Stream has added a new notification event for Live broadcasts to alert (via email or webhook) on various error conditions including unsupported codecs, bad GOP/keyframe interval, or quota exhaustion.
When creating/editing a notification, subscribe to `live_input.errored` to receive the new event type. Existing notification subscriptions will not be changed automatically. For more information, refer to [Receive Live Webhooks](https://developers.cloudflare.com/stream/stream-live/webhooks/).
## 2024-06-20
**Generated Captions to Open beta**
Stream has introduced automatically generated captions to open beta for all subscribers at no additional cost. While in beta, only English is supported and videos must be less than 2 hours. For more information, refer to the [product announcement and deep dive](https://blog.cloudflare.com/stream-automatic-captions-with-ai) or refer to the [captions documentation](https://developers.cloudflare.com/stream/edit-videos/adding-captions/) to get started.
## 2024-06-11
**Updated response codes on requests for errored videos**
Stream will now return HTTP error status 424 (failed dependency) when requesting segments, manifests, thumbnails, downloads, or subtitles for videos that are in an errored state. Previously, Stream would return one of several 5xx codes for requests like this.
## 2024-04-11
**Live Instant Clipping for live broadcasts and recordings**
Clipping is now available in open beta for live broadcasts and recordings. For more information, refer to [Live instant clipping](https://developers.cloudflare.com/stream/stream-live/live-instant-clipping/) documentation.
## 2024-02-16
**Tonemapping improvements for HDR content**
In certain cases, videos uploaded with an HDR colorspace (such as footage from certain mobile devices) appeared washed out or desaturated when played back. This issue is resolved for new uploads.
## 2023-11-07
**HLS improvements for on-demand TS output**
HLS output from Cloudflare Stream on-demand videos that use Transport Stream file format now includes a 10 second offset to timestamps. This will have no impact on most customers. A small percentage of customers will see improved playback stability. Caption files were also adjusted accordingly.
## 2023-10-10
**SRT Audio Improvements**
In some cases, playback via SRT protocol was missing an audio track regardless of existence of audio in the broadcast. This issue is now resolved.
## 2023-09-25
**LL-HLS Beta**
Low-Latency HTTP Live Streaming (LL-HLS) is now in open beta. Enable LL-HLS on your [live input](https://developers.cloudflare.com/stream/stream-live/start-stream-live/) for automatic low-latency playback using the Stream built-in player where supported.
For more information, refer to [live input](https://developers.cloudflare.com/stream/stream-live/start-stream-live/) and [custom player](https://developers.cloudflare.com/stream/viewing-videos/using-own-player/) docs.
## 2023-08-08
**Scheduled Deletion**
Stream now supports adding a scheduled deletion date to new and existing videos. Live inputs support deletion policies for automatic recording deletion.
For more, refer to the [video on demand](https://developers.cloudflare.com/stream/uploading-videos/) or [live input](https://developers.cloudflare.com/stream/stream-live/) docs.
## 2023-05-16
**Multiple audio tracks now generally available**
Stream supports adding multiple audio tracks to an existing video.
For more, refer to the [documentation](https://developers.cloudflare.com/stream/edit-videos/adding-additional-audio-tracks/) to get started.
## 2023-04-26
**Player Enhancement Properties**
Cloudflare Stream now supports player enhancement properties.
With player enhancements, you can modify your video player to incorporate elements of your branding, such as your logo, and customize additional options to present to your viewers.
For more, refer to the [documentation](https://developers.cloudflare.com/stream/edit-videos/player-enhancements/) to get started.
## 2023-03-21
**Limits for downloadable MP4s for live recordings**
Previously, generating a download for a live recording exceeding four hours resulted in failure.
To fix the issue, now video downloads are only available for live recordings under four hours. Live recordings exceeding four hours can still be played but cannot be downloaded.
## 2023-01-04
**Earlier detection (and rejection) of non-video uploads**
Cloudflare Stream now detects non-video content on upload using [the POST API](https://developers.cloudflare.com/stream/uploading-videos/upload-video-file/) and returns a 400 Bad Request HTTP error with code `10059`.
Previously, if you or one of your users attempted to upload a file that is not a video (ex: an image), the request to upload would appear successful, but then fail to be encoded later on.
With this change, Stream responds to the upload request with an error, allowing you to give users immediate feedback if they attempt to upload non-video content.
## 2022-12-08
**Faster mp4 downloads of live recordings**
Generating MP4 downloads of live stream recordings is now significantly faster. For more, refer to [the docs](https://developers.cloudflare.com/stream/stream-live/download-stream-live-videos/).
## 2022-11-29
**Multiple audio tracks (closed beta)**
Stream now supports adding multiple audio tracks to an existing video upload. This allows you to:
* Provide viewers with audio tracks in multiple languages
* Provide dubbed audio tracks, or audio commentary tracks (ex: Director’s Commentary)
* Allow your users to customize the customize the audio mix, by providing separate audio tracks for music, speech or other audio tracks.
* Provide Audio Description tracks to ensure your content is accessible. ([WCAG 2.0 Guideline 1.2 1](https://www.w3.org/TR/WCAG20/#media-equiv-audio-desc-only))
To request an invite to the beta, refer to [this post](https://community.cloudflare.com/t/new-in-beta-support-for-multiple-audio-tracks/439629).
## 2022-11-22
**VP9 support for WebRTC live streams (beta)**
Cloudflare Stream now supports [VP9](https://developers.google.com/media/vp9) when streaming using [WebRTC (WHIP)](https://developers.cloudflare.com/stream/webrtc-beta/), currently in beta.
## 2022-11-08
**Reduced time to start WebRTC streaming and playback with Trickle ICE**
Cloudflare Stream's [WHIP](https://datatracker.ietf.org/doc/draft-ietf-wish-whip/) and [WHEP](https://www.ietf.org/archive/id/draft-murillo-whep-01.html) implementations now support [Trickle ICE](https://datatracker.ietf.org/doc/rfc8838/), reducing the time it takes to initialize WebRTC connections, and increasing compatibility with WHIP and WHEP clients.
For more, refer to [the docs](https://developers.cloudflare.com/stream/webrtc-beta/).
## 2022-11-07
**Deprecating the 'per-video' Analytics API**
The “per-video” analytics API is being deprecated. If you still use this API, you will need to switch to using the [GraphQL Analytics API](https://developers.cloudflare.com/stream/getting-analytics/fetching-bulk-analytics/) by February 1, 2023. After this date, the per-video analytics API will be no longer available.
The GraphQL Analytics API provides the same functionality and more, with additional filters and metrics, as well as the ability to fetch data about multiple videos in a single request. Queries are faster, more reliable, and built on a shared analytics system that you can [use across many Cloudflare products](https://developers.cloudflare.com/analytics/graphql-api/features/data-sets/).
For more about this change and how to migrate existing API queries, refer to [this post](https://community.cloudflare.com/t/migrate-to-the-stream-graphql-analytics-api-by-feb-1st-2023/433252) and the [GraphQL Analytics API docs](https://developers.cloudflare.com/stream/getting-analytics/fetching-bulk-analytics/).
## 2022-11-01
**Create an unlimited number of live inputs**
Cloudflare Stream now has no limit on the number of [live inputs](https://developers.cloudflare.com/api/resources/stream/subresources/live_inputs/methods/get/) you can create. Stream is designed to allow your end-users to go live — live inputs can be created quickly on-demand via a single API request for each of user of your platform or app.
For more on creating and managing live inputs, get started with the [docs](https://developers.cloudflare.com/stream/stream-live/).
## 2022-10-20
**More accurate bandwidth estimates for live video playback**
When playing live video, Cloudflare Stream now provides significantly more accurate estimates of the bandwidth needs of each quality level to client video players. This ensures that live video plays at the highest quality that viewers have adequate bandwidth to play.
As live video is streamed to Cloudflare, we transcode it to make it available to viewers at multiple quality levels. During transcoding, we learn about the real bandwidth needs of each segment of video at each quality level, and use this to provide an estimate of the bandwidth requirements of each quality level the in HLS (`.m3u8`) and DASH (`.mpd`) manifests.
If a live stream contains content with low visual complexity, like a slideshow presentation, the bandwidth estimates provided in the HLS manifest will be lower, ensuring that the most viewers possible view the highest quality level, since it requires relatively little bandwidth. Conversely, if a live stream contains content with high visual complexity, like live sports with motion and camera panning, the bandwidth estimates provided in the HLS manifest will be higher, ensuring that viewers with inadequate bandwidth switch down to a lower quality level, and their playback does not buffer.
This change is particularly helpful if you're building a platform or application that allows your end users to create their own live streams, where these end users have their own streaming software and hardware that you can't control. Because this new functionality adapts based on the live video we receive, rather than just the configuration advertised by the broadcaster, even in cases where your end users' settings are less than ideal, client video players will not receive excessively high estimates of bandwidth requirements, causing playback quality to decrease unnecessarily. Your end users don't have to be OBS Studio experts in order to get high quality video playback.
No work is required on your end — this change applies to all live inputs, for all customers of Cloudflare Stream. For more, refer to the [docs](https://developers.cloudflare.com/stream/stream-live/#bitrate-estimates-at-each-quality-level-bitrate-ladder).
## 2022-10-05
**AV1 Codec support for live streams and recordings (beta)**
Cloudflare Stream now supports playback of live videos and live recordings using the [AV1 codec](https://aomedia.org/av1/), which uses 46% less bandwidth than H.264.
For more, read the [blog post](https://blog.cloudflare.com/av1-cloudflare-stream-beta).
## 2022-09-27
**WebRTC live streaming and playback (beta)**
Cloudflare Stream now supports live video streaming over WebRTC, with sub-second latency, to unlimited concurrent viewers.
For more, read the [blog post](https://blog.cloudflare.com/webrtc-whip-whep-cloudflare-stream) or the get started with example code in the [docs](https://developers.cloudflare.com/stream/webrtc-beta).
## 2022-09-15
**Manually control when you start and stop simulcasting**
You can now enable and disable individual live outputs via the API or Stream dashboard, allowing you to control precisely when you start and stop simulcasting to specific destinations like YouTube and Twitch. For more, [read the docs](https://developers.cloudflare.com/stream/stream-live/simulcasting/#control-when-you-start-and-stop-simulcasting).
## 2022-08-15
**Unique subdomain for your Stream Account**
URLs in the Stream Dashboard and Stream API now use a subdomain specific to your Cloudflare Account: `customer-{CODE}.cloudflarestream.com`. This change allows you to:
1. Use [Content Security Policy](https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP) (CSP) directives specific to your Stream subdomain, to ensure that only videos from your Cloudflare account can be played on your website.
2. Allowlist only your Stream account subdomain at the network-level to ensure that only videos from a specific Cloudflare account can be accessed on your network.
No action is required from you, unless you use Content Security Policy (CSP) on your website. For more on CSP, read the [docs](https://developers.cloudflare.com/stream/faq/#i-use-content-security-policy-csp-on-my-website-what-domains-do-i-need-to-add-to-which-directives).
## 2022-08-02
**Clip videos using the Stream API**
You can now change the start and end times of a video uploaded to Cloudflare Stream. For more information, refer to [Clip videos](https://developers.cloudflare.com/stream/edit-videos/video-clipping/).
## 2022-07-26
**Live inputs**
The Live Inputs API now supports optional pagination, search, and filter parameters. For more information, refer to the [Live Inputs API documentation](https://developers.cloudflare.com/api/resources/stream/subresources/live_inputs/methods/list/).
## 2022-05-24
**Picture-in-Picture support**
The [Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/) now displays a button to activate Picture-in-Picture mode, if the viewer's web browser supports the [Picture-in-Picture API](https://developer.mozilla.org/en-US/docs/Web/API/Picture-in-Picture_API).
## 2022-05-13
**Creator ID property**
During or after uploading a video to Stream, you can now specify a value for a new field, `creator`. This field can be used to identify the creator of the video content, linking the way you identify your users or creators to videos in your Stream account. For more, read the [blog post](https://blog.cloudflare.com/stream-creator-management/).
## 2022-03-17
**Analytics panel in Stream Dashboard**
The Stream Dashboard now has an analytics panel that shows the number of minutes of both live and recorded video delivered. This view can be filtered by **Creator ID**, **Video UID**, and **Country**. For more in-depth analytics data, refer to the [bulk analytics documentation](https://developers.cloudflare.com/stream/getting-analytics/fetching-bulk-analytics/).
## 2022-03-16
**Custom letterbox color configuration option for Stream Player**
The Stream Player can now be configured to use a custom letterbox color, displayed around the video ('letterboxing' or 'pillarboxing') when the video's aspect ratio does not match the player's aspect ratio. Refer to the documentation on configuring the Stream Player [here](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/#basic-options).
## 2022-03-10
**Support for SRT live streaming protocol**
Cloudflare Stream now supports the SRT live streaming protocol. SRT is a modern, actively maintained streaming video protocol that delivers lower latency, and better resilience against unpredictable network conditions. SRT supports newer video codecs and makes it easier to use accessibility features such as captions and multiple audio tracks.
For more, read the [blog post](https://blog.cloudflare.com/stream-now-supports-srt-as-a-drop-in-replacement-for-rtmp/).
## 2022-02-17
**Faster video quality switching in Stream Player**
When viewers manually change the resolution of video they want to receive in the Stream Player, this change now happens immediately, rather than once the existing resolution playback buffer has finished playing.
## 2022-02-09
**Volume and playback controls accessible during playback of VAST Ads**
When viewing ads in the [VAST format](https://www.iab.com/guidelines/vast/#:~:text=VAST%20is%20a%20Video%20Ad,of%20the%20digital%20video%20marketplace.) in the Stream Player, viewers can now manually start and stop the video, or control the volume.
## 2022-01-25
**DASH and HLS manifest URLs accessible in Stream Dashboard**
If you choose to use a third-party player with Cloudflare Stream, you can now easily access HLS and DASH manifest URLs from within the Stream Dashboard. For more about using Stream with third-party players, read the docs [here](https://developers.cloudflare.com/stream/viewing-videos/using-own-player/).
## 2022-01-22
**Input health status in the Stream Dashboard**
When a live input is connected, the Stream Dashboard now displays technical details about the connection, which can be used to debug configuration issues.
## 2022-01-06
**Live viewer count in the Stream Player**
The [Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/) now shows the total number of people currently watching a video live.
## 2022-01-04
**Webhook notifications for live stream connections events**
You can now configure Stream to send webhooks each time a live stream connects and disconnects. For more information, refer to the [Webhooks documentation](https://developers.cloudflare.com/stream/stream-live/webhooks).
## 2021-12-07
**FedRAMP Support**
The Stream Player can now be served from a [FedRAMP](https://www.cloudflare.com/press-releases/2021/cloudflare-hits-milestone-in-fedramp-approval/) compliant subdomain.
## 2021-11-23
**24/7 Live streaming support**
You can now use Cloudflare Stream for 24/7 live streaming.
## 2021-11-17
**Persistent Live Stream IDs**
You can now start and stop live broadcasts without having to provide a new video UID to the Stream Player (or your own player) each time the stream starts and stops. [Read the docs](https://developers.cloudflare.com/stream/stream-live/watch-live-stream/#view-by-live-input-id).
## 2021-10-14
**MP4 video file downloads for live videos**
Once a live video has ended and been recorded, you can now give viewers the option to download an MP4 video file of the live recording. For more, read the docs [here](https://developers.cloudflare.com/stream/stream-live/download-stream-live-videos/).
## 2021-09-30
**Serverless Live Streaming**
Stream now supports live video content! For more information, read the [blog post](https://blog.cloudflare.com/stream-live/) and get started by reading the [docs](https://developers.cloudflare.com/stream/stream-live/).
## 2021-07-26
**Thumbnail previews in Stream Player seek bar**
The Stream Player now displays preview images when viewers hover their mouse over the seek bar, making it easier to skip to a specific part of a video.
## 2021-07-26
**MP4 video file downloads (GA)**
All Cloudflare Stream customers can now give viewers the option to download videos uploaded to Stream as an MP4 video file. For more, read the docs [here](https://developers.cloudflare.com/stream/viewing-videos/download-videos/).
## 2021-07-10
**Stream Connect (open beta)**
You can now opt-in to the Stream Connect beta, and use Cloudflare Stream to restream live video to any platform that accepts RTMPS input, including Facebook, YouTube and Twitch.
For more, read the [blog post](https://blog.cloudflare.com/restream-with-stream-connect/) or the [docs](https://developers.cloudflare.com/stream/stream-live/simulcasting/).
## 2021-06-10
**Simplified signed URL token generation**
You can now obtain a signed URL token via a single API request, without needing to generate signed tokens in your own application. [Read the docs](https://developers.cloudflare.com/stream/viewing-videos/securing-your-stream).
## 2021-06-08
**Stream Connect (closed beta)**
You can now use Cloudflare Stream to restream or simulcast live video to any platform that accepts RTMPS input, including Facebook, YouTube and Twitch.
For more, read the [blog post](https://blog.cloudflare.com/restream-with-stream-connect/) or the [docs](https://developers.cloudflare.com/stream/stream-live/simulcasting/).
## 2021-05-03
**MP4 video file downloads (beta)**
You can now give your viewers the option to download videos uploaded to Stream as an MP4 video file. For more, read the docs [here](https://developers.cloudflare.com/stream/viewing-videos/download-videos/).
## 2021-03-29
**Picture quality improvements**
Cloudflare Stream now encodes videos with fewer artifacts, resulting in improved video quality for your viewers.
## 2021-03-25
**Improved client bandwidth hints for third-party video players**
If you use Cloudflare Stream with a third party player, and send the `clientBandwidthHint` parameter in requests to fetch video manifests, Cloudflare Stream now selects the ideal resolution to provide to your client player more intelligently. This ensures your viewers receive the ideal resolution for their network connection.
## 2021-03-25
**Improved client bandwidth hints for third-party video players**
If you use Cloudflare Stream with a third party player, and send the `clientBandwidthHint` parameter in requests to fetch video manifests, Cloudflare Stream now selects the ideal resolution to provide to your client player more intelligently. This ensures your viewers receive the ideal resolution for their network connection.
## 2021-03-17
**Less bandwidth, identical video quality**
Cloudflare Stream now delivers video using 3-10x less bandwidth, with no reduction in quality. This ensures faster playback for your viewers with less buffering, particularly when viewers have slower network connections.
## 2021-03-10
**Stream Player 2.0 (preview)**
A brand new version of the Stream Player is now available for preview. New features include:
* Unified controls across desktop and mobile devices
* Keyboard shortcuts
* Intelligent mouse cursor interactions with player controls
* Phased out support for Internet Explorer 11
For more, refer to [this post](https://community.cloudflare.com/t/announcing-the-preview-build-for-stream-player-2-0/243095) on the Cloudflare Community Forum.
## 2021-03-04
**Faster video encoding**
Videos uploaded to Cloudflare Stream are now available to view 5x sooner, reducing the time your users wait between uploading and viewing videos.
## 2021-01-17
**Removed weekly upload limit, increased max video upload size**
You can now upload videos up to 30GB in size to Cloudflare Stream and also now upload an unlimited number of videos to Cloudflare Stream each week
## 2020-12-14
**Tus support for direct creator uploads**
You can now use the [tus protocol](https://developers.cloudflare.com/stream/uploading-videos/direct-creator-uploads/#advanced-upload-flow-using-tus-for-large-videos) when allowing creators (your end users) to upload their own videos directly to Cloudflare Stream.
In addition, all uploads to Cloudflare Stream made using tus are now faster and more reliable as part of this change.
## 2020-12-09
**Multiple audio track mixdown**
Videos with multiple audio tracks (ex: 5.1 surround sound) are now mixed down to stereo when uploaded to Stream. The resulting video, with stereo audio, is now playable in the Stream Player.
## 2020-12-02
**Storage limit notifications**
Cloudflare now emails you if your account is using 75% or more of your prepaid video storage, so that you can take action and plan ahead.
</page>
<page>
---
title: Edit videos · Cloudflare Stream docs
lastUpdated: 2024-08-30T13:02:26.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/stream/edit-videos/
md: https://developers.cloudflare.com/stream/edit-videos/index.md
---
* [Add additional audio tracks](https://developers.cloudflare.com/stream/edit-videos/adding-additional-audio-tracks/)
* [Add captions](https://developers.cloudflare.com/stream/edit-videos/adding-captions/)
* [Apply watermarks](https://developers.cloudflare.com/stream/edit-videos/applying-watermarks/)
* [Add player enhancements](https://developers.cloudflare.com/stream/edit-videos/player-enhancements/)
* [Clip videos](https://developers.cloudflare.com/stream/edit-videos/video-clipping/)
</page>
<page>
---
title: Examples · Cloudflare Stream docs
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/examples/
md: https://developers.cloudflare.com/stream/examples/index.md
---
[Shaka Player](https://developers.cloudflare.com/stream/examples/shaka-player/)
[Example of video playback with Cloudflare Stream and Shaka Player](https://developers.cloudflare.com/stream/examples/shaka-player/)
[RTMPS playback](https://developers.cloudflare.com/stream/examples/rtmps_playback/)
[Example of sub 1s latency video playback using RTMPS and ffplay](https://developers.cloudflare.com/stream/examples/rtmps_playback/)
[SRT playback](https://developers.cloudflare.com/stream/examples/srt_playback/)
[Example of sub 1s latency video playback using SRT and ffplay](https://developers.cloudflare.com/stream/examples/srt_playback/)
[Android (ExoPlayer)](https://developers.cloudflare.com/stream/examples/android/)
[Example of video playback on Android using ExoPlayer](https://developers.cloudflare.com/stream/examples/android/)
[dash.js](https://developers.cloudflare.com/stream/examples/dash-js/)
[Example of video playback with Cloudflare Stream and the DASH reference player (dash.js)](https://developers.cloudflare.com/stream/examples/dash-js/)
[hls.js](https://developers.cloudflare.com/stream/examples/hls-js/)
[Example of video playback with Cloudflare Stream and the HLS reference player (hls.js)](https://developers.cloudflare.com/stream/examples/hls-js/)
[iOS (AVPlayer)](https://developers.cloudflare.com/stream/examples/ios/)
[Example of video playback on iOS using AVPlayer](https://developers.cloudflare.com/stream/examples/ios/)
[Stream Player](https://developers.cloudflare.com/stream/examples/stream-player/)
[Example of video playback with the Cloudflare Stream Player](https://developers.cloudflare.com/stream/examples/stream-player/)
[Video.js](https://developers.cloudflare.com/stream/examples/video-js/)
[Example of video playback with Cloudflare Stream and Video.js](https://developers.cloudflare.com/stream/examples/video-js/)
[Vidstack](https://developers.cloudflare.com/stream/examples/vidstack/)
[Example of video playback with Cloudflare Stream and Vidstack](https://developers.cloudflare.com/stream/examples/vidstack/)
[First Live Stream with OBS](https://developers.cloudflare.com/stream/examples/obs-from-scratch/)
[Set up and start your first Live Stream using OBS (Open Broadcaster Software) Studio](https://developers.cloudflare.com/stream/examples/obs-from-scratch/)
</page>
<page>
---
title: Frequently asked questions about Cloudflare Stream · Cloudflare Stream docs
description: Cloudflare decides on which bitrate, resolution, and codec is best
for you. We deliver all videos to industry standard H264 codec. We use a few
different adaptive streaming levels from 360p to 1080p to ensure smooth
streaming for your audience watching on different devices and bandwidth
constraints.
lastUpdated: 2025-11-17T14:08:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/faq/
md: https://developers.cloudflare.com/stream/faq/index.md
---
## Stream
### What formats and quality levels are delivered through Cloudflare Stream?
Cloudflare decides on which bitrate, resolution, and codec is best for you. We deliver all videos to industry standard H264 codec. We use a few different adaptive streaming levels from 360p to 1080p to ensure smooth streaming for your audience watching on different devices and bandwidth constraints.
### Can I download original video files from Stream?
You cannot download the *exact* input file that you uploaded. However, depending on your use case, you can use the [Downloadable Videos](https://developers.cloudflare.com/stream/viewing-videos/download-videos/) feature to get encoded MP4s for use cases like offline viewing.
### Is there a limit to the amount of videos I can upload?
* By default, a video upload can be at most 30 GB.
* By default, you can have up to 120 videos queued or being encoded simultaneously. Videos in the `ready` status are playable but may still be encoding certain quality levels until the `pctComplete` reaches 100. Videos in the `error`, `ready`, or `pendingupload` state do not count toward this limit. If you need the concurrency limit raised, [contact Cloudflare support](https://developers.cloudflare.com/support/contacting-cloudflare-support/) explaining your use case and why you would like the limit raised.
Note
The limit to the number of videos only applies to videos being uploaded to Cloudflare Stream. This limit is not related to the number of end users streaming videos.
* An account cannot upload videos if the total video duration exceeds the video storage capacity purchased.
Limits apply to Direct Creator Uploads at the time of upload URL creation.
Uploads over these limits will receive a [429 (Too Many Requests)](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/4xx-client-error/error-429/) or [413 (Payload too large)](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/4xx-client-error/error-413/) HTTP status codes with more information in the response body. Please write to Cloudflare support or your customer success manager for higher limits.
### Can I embed videos on Stream even if my domain is not on Cloudflare?
Yes. Stream videos can be embedded on any domain, even domains not on Cloudflare.
### What input file formats are supported?
Users can upload video in the following file formats:
MP4, MKV, MOV, AVI, FLV, MPEG-2 TS, MPEG-2 PS, MXF, LXF, GXF, 3GP, WebM, MPG, QuickTime
### Does Stream support High Dynamic Range (HDR) video content?
When HDR videos are uploaded to Stream, they are re-encoded and delivered in SDR format, to ensure compatibility with the widest range of viewing devices.
### What frame rates (FPS) are supported?
Cloudflare Stream supports video file uploads for any FPS, however videos will be re-encoded for 70 FPS playback. If the original video file has a frame rate lower than 70 FPS, Stream will re-encode at the original frame rate.
If the frame rate is variable we will drop frames (for example if there are more than 1 frames within 1/30 seconds, we will drop the extra frames within that period).
### What browsers does Stream work on?
You can embed the Stream player on the following platforms:
Note
Cloudflare Stream is not available on Chromium, as Chromium does not support H.264 videos.
### What are the recommended upload settings for video uploads?
If you are producing a brand new file for Cloudflare Stream, we recommend you use the following settings:
* MP4 containers, AAC audio codec, H264 video codec, 30 or below frames per second
* moov atom should be at the front of the file (Fast Start)
* H264 progressive scan (no interlacing)
* H264 high profile
* Closed GOP
* Content should be encoded and uploaded in the same frame rate it was recorded
* Mono or Stereo audio (Stream will mix audio tracks with more than 2 channels down to stereo)
Below are bitrate recommendations for encoding new videos for Stream:
### If I cancel my stream subscription, are the videos deleted?
Videos are removed if the subscription is not renewed within 30 days.
### I use Content Security Policy (CSP) on my website. What domains do I need to add to which directives?
If your website uses [Content Security Policy (CSP)](https://developer.mozilla.org/en-US/docs/Web/HTTP/Reference/Headers/Content-Security-Policy) directives, depending on your configuration, you may need to add Cloudflare Stream's domains to particular directives, in order to allow videos to be viewed or uploaded by your users.
If you use the provided [Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/), `videodelivery.net` and `*.cloudflarestream.com` must be included in the `frame-src` or `default-src` directive to allow the player's `<iframe>` element to load.
```http
Content-Security-Policy: frame-src 'self' videodelivery.net *.cloudflarestream.com
```
If you use your **own** Player, add `*.videodelivery.net` and `*.cloudflarestream.com` to the `media-src`, `img-src` and `connect-src` CSP directives to allow video files and thumbnail images to load.
```http
Content-Security-Policy: media-src 'self' videodelivery.net *.cloudflarestream.com; img-src 'self' *.videodelivery.net *.cloudflarestream.com; connect-src 'self' *.videodelivery.net *.cloudflarestream.com
```
If you allow users to upload their own videos directly to Cloudflare Stream, add `*.videodelivery.net` and `*.cloudflarestream.com` to the `connect-src` CSP directive.
```http
Content-Security-Policy: connect-src 'self' *.videodelivery.net *.cloudflarestream.com
```
To ensure **only** videos from **your** Cloudflare Stream account can be played on your website, replace `*` in `*.cloudflarestream.com` and `*.videodelivery.net` in the examples above with `customer-<CODE>`, replacing `<CODE>` with your unique customer code. To find your unique customer code in the Cloudflare dashboard, go to the **Stream** page.
[Go to **Videos**](https://dash.cloudflare.com/?to=/:account/stream/videos)
This code is unique to your Cloudflare Account.
### Why is PageSpeed Insights giving a bad score when using the Stream Player?
If your website loads in a lot of player instances, PageSpeed Insights will penalize the JavaScript load for each player instance. Our testing shows that when actually loading the page, the script itself is only downloaded once with the local browser cache retrieving the script for the other player objects on the same page. Therefore, we believe that the PageSpeed Insights score is not matching real-world behavior in this situation.
If you are using thumbnails, you can use [animated thumbnails](https://developers.cloudflare.com/stream/viewing-videos/displaying-thumbnails/#animated-gif-thumbnails) that link to the video pages.
If multiple players are on the same page, you can lazy load any players that are not visible in the initial viewport. For more information about lazy loading, refer to [Mozilla's lazy loading documentation](https://developer.mozilla.org/en-US/docs/Web/HTML/Element/iframe#lazy).
</page>
<page>
---
title: Get started · Cloudflare Stream docs
description: You can upload videos using the API or directly on the Stream page
of the Cloudflare dashboard.
lastUpdated: 2025-11-17T14:08:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/get-started/
md: https://developers.cloudflare.com/stream/get-started/index.md
---
Media Transformations is now GA:
Billing for Media Transformations will begin on November 1st, 2025.
* [Upload your first video](https://developers.cloudflare.com/stream/get-started#upload-your-first-video)
* [Start your first live stream](https://developers.cloudflare.com/stream/get-started#start-your-first-live-stream)
## Upload your first video
### Step 1: Upload an example video from a public URL
You can upload videos using the API or directly on the **Stream** page of the Cloudflare dashboard.
[Go to **Videos**](https://dash.cloudflare.com/?to=/:account/stream/videos)
To use the API, replace the `API_TOKEN` and `ACCOUNT_ID` values with your credentials in the example below.
```bash
curl \
-X POST \
-d '{"url":"https://storage.googleapis.com/stream-example-bucket/video.mp4","meta":{"name":"My First Stream Video"}}' \
-H "Authorization: Bearer <API_TOKEN>" \
https://api.cloudflare.com/client/v4/accounts/<ACCOUNT_ID>/stream/copy
```
### Step 2: Wait until the video is ready to stream
Because Stream must download and process the video, the video might not be available for a few seconds depending on the length of your video. You should poll the Stream API until `readyToStream` is `true`, or use [webhooks](https://developers.cloudflare.com/stream/manage-video-library/using-webhooks/) to be notified when a video is ready for streaming.
Use the video UID from the first step to poll the video:
```bash
curl \
-H "Authorization: Bearer <API_TOKEN>" \
https://api.cloudflare.com/client/v4/accounts/<ACCOUNT_ID>/stream/<VIDEO_UID>
```
```json
{
"result": {
"uid": "6b9e68b07dfee8cc2d116e4c51d6a957",
"preview": "https://customer-f33zs165nr7gyfy4.cloudflarestream.com/6b9e68b07dfee8cc2d116e4c51d6a957/watch",
"thumbnail": "https://customer-f33zs165nr7gyfy4.cloudflarestream.com/6b9e68b07dfee8cc2d116e4c51d6a957/thumbnails/thumbnail.jpg",
"readyToStream": true,
"status": {
"state": "ready"
},
"meta": {
"downloaded-from": "https://storage.googleapis.com/stream-example-bucket/video.mp4",
"name": "My First Stream Video"
},
"created": "2020-10-16T20:20:17.872170843Z",
"size": 9032701
//...
},
"success": true,
"errors": [],
"messages": []
}
```
### Step 3: Play the video in your website or app
Videos uploaded to Stream can be played on any device and platform, from websites to native apps. See [Play videos](https://developers.cloudflare.com/stream/viewing-videos) for details and examples of video playback across platforms.
To play video on your website with the [Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/), copy the `uid` of the video from the request above, along with your unique customer code, and replace `<CODE>` and `<VIDEO_UID>` in the embed code below:
```html
<iframe
src="https://customer-<CODE>.cloudflarestream.com/<VIDEO_UID>/iframe"
title="Example Stream video"
frameborder="0"
allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture"
allowfullscreen
>
</iframe>
```
The embed code above can also be found on the **Stream** page of the Cloudflare dashboard.
[Go to **Videos**](https://dash.cloudflare.com/?to=/:account/stream/videos)
### Next steps
* [Edit your video](https://developers.cloudflare.com/stream/edit-videos/) and add captions or watermarks
* [Customize the Stream player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/)
## Start your first live stream
### Step 1: Create a live input
You can create a live input using the API or the **Live inputs** page of the Cloudflare dashboard.
[Go to **Live inputs**](https://dash.cloudflare.com/?to=/:account/stream/inputs)
To use the API, replace the `API_TOKEN` and `ACCOUNT_ID` values with your credentials in the example below.
```bash
curl -X POST \
-H "Authorization: Bearer <API_TOKEN>" \
-D '{"meta": {"name":"test stream"},"recording": { "mode": "automatic" }}' \
https://api.cloudflare.com/client/v4/accounts/<ACCOUNT_ID>/stream/live_inputs
```
```json
{
"uid": "f256e6ea9341d51eea64c9454659e576",
"rtmps": {
"url": "rtmps://live.cloudflare.com:443/live/",
"streamKey": "MTQ0MTcjM3MjI1NDE3ODIyNTI1MjYyMjE4NTI2ODI1NDcxMzUyMzcf256e6ea9351d51eea64c9454659e576"
},
"created": "2021-09-23T05:05:53.451415Z",
"modified": "2021-09-23T05:05:53.451415Z",
"meta": {
"name": "test stream"
},
"status": null,
"recording": {
"mode": "automatic",
"requireSignedURLs": false,
"allowedOrigins": null
}
}
```
### Step 2: Copy the RTMPS URL and key, and use them with your live streaming application.
We recommend using [Open Broadcaster Software (OBS)](https://obsproject.com/) to get started.
### Step 3: Play the live stream in your website or app
Live streams can be played on any device and platform, from websites to native apps, using the same video players as videos uploaded to Stream. See [Play videos](https://developers.cloudflare.com/stream/viewing-videos) for details and examples of video playback across platforms.
To play the live stream you just started on your website with the [Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/), copy the `uid` of the live input from the request above, along with your unique customer code, and replace `<CODE>` and `<VIDEO_UID>` in the embed code below:
```html
<iframe
src="https://customer-<CODE>.cloudflarestream.com/<VIDEO_UID>/iframe"
title="Example Stream video"
frameborder="0"
allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture"
allowfullscreen
>
</iframe>
```
The embed code above can also be found on the **Stream** page of the Cloudflare dashboard.
[Go to **Videos**](https://dash.cloudflare.com/?to=/:account/stream/videos)
### Next steps
* [Secure your stream](https://developers.cloudflare.com/stream/viewing-videos/securing-your-stream/)
* [View live viewer counts](https://developers.cloudflare.com/stream/getting-analytics/live-viewer-count/)
## Accessibility considerations
To make your video content more accessible, include [captions](https://developers.cloudflare.com/stream/edit-videos/adding-captions/) and [high-quality audio recording](https://www.w3.org/WAI/media/av/av-content/).
</page>
<page>
---
title: Analytics · Cloudflare Stream docs
description: "Stream provides server-side analytics that can be used to:"
lastUpdated: 2025-09-09T16:21:39.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/getting-analytics/
md: https://developers.cloudflare.com/stream/getting-analytics/index.md
---
Stream provides server-side analytics that can be used to:
* Identify most viewed video content in your app or platform.
* Identify where content is viewed from and when it is viewed.
* Understand which creators on your platform are publishing the most viewed content, and analyze trends.
You can access data on either:
* The Stream **Analytics** page of the Cloudflare dashboard.
[Go to **Analytics**](https://dash.cloudflare.com/?to=/:account/stream/analytics)
* The [GraphQL Analytics API](https://developers.cloudflare.com/stream/getting-analytics/fetching-bulk-analytics).
Users will need the **Analytics** permission to access analytics via Dash or GraphQL.
</page>
<page>
---
title: Manage videos · Cloudflare Stream docs
lastUpdated: 2024-08-22T17:44:03.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/stream/manage-video-library/
md: https://developers.cloudflare.com/stream/manage-video-library/index.md
---
</page>
<page>
---
title: Pricing · Cloudflare Stream docs
description: "Cloudflare Stream lets you broadcast, store, and deliver video
using a simple, unified API and simple pricing. Stream bills on two dimensions
only:"
lastUpdated: 2025-11-17T14:08:01.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/pricing/
md: https://developers.cloudflare.com/stream/pricing/index.md
---
Media Transformations is now GA:
Billing for Media Transformations will begin on November 1st, 2025.
## Pricing for Stream
Cloudflare Stream lets you broadcast, store, and deliver video using a simple, unified API and simple pricing. Stream bills on two dimensions only:
* **Minutes of video stored:** the total duration of uploaded video and live recordings
* **Minutes of video delivered:** the total duration of video delivered to end users
On-demand and live video are billed the same way.
Ingress (sending your content to us) and encoding are always free. Bandwidth is already included in "video delivered" with no additional egress (traffic/bandwidth) fees.
### Minutes of video stored
Storage is a prepaid pricing dimension purchased in increments of $5 per 1,000 minutes stored, regardless of file size. You can check how much storage you have and how much you have used on the **Stream** page of the Cloudflare dashboard.
[Go to **Videos**](https://dash.cloudflare.com/?to=/:account/stream/videos)
Storage is consumed by:
* Original videos uploaded to your account
* Recordings of live broadcasts
* The reserved `maxDurationSeconds` for Direct Creator and TUS uploads which have not been completed. After these uploads are complete or the upload link expires, this reservation is released.
Storage is not consumed by:
* Videos in an unplayable or errored state
* Expired Direct Creator upload links
* Deleted videos
* Downloadable files generated for [MP4 Downloads](https://developers.cloudflare.com/stream/viewing-videos/download-videos/)
* Multiple quality levels that Stream generates for each uploaded original
Storage consumption is rounded up to the second of video duration; file size does not matter. Video stored in Stream does not incur additional storage fees from other storage products such as R2.
Note
If you run out of storage, you will not be able to upload new videos or start new live streams until you purchase more storage or delete videos.
Enterprise customers *may* continue to upload new content beyond their contracted quota without interruption.
### Minutes of video delivered
Delivery is a post-paid, usage-based pricing dimension billed at $1 per 1,000 minutes delivered. You can check how much delivery you have used on the **Billing** page or the Stream **Analytics** page of the Cloudflare dashboard.
[Go to **Billing** ](https://dash.cloudflare.com/?to=/:account/billing)[Go to **Analytics**](https://dash.cloudflare.com/?to=/:account/stream/analytics)
Delivery is counted for the following uses:
* Playback on the web or an app using [Stream's built-in player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/) or the [HLS or DASH manifests](https://developers.cloudflare.com/stream/viewing-videos/using-own-player/)
* MP4 Downloads
* Simulcasting via SRT or RTMP live outputs
Delivery is counted by HTTP requests for video segments or parts of the MP4. Therefore:
* Client-side preloading and buffering is counted as billable delivery.
* Content played from client-side/browser cache is *not* billable, like a short looping video. Some mobile app player libraries do not cache HLS segments by default.
* MP4 Downloads are billed by percentage of the file delivered.
Minutes delivered for web playback (Stream Player, HLS, and DASH) are rounded to the *segment* length: for uploaded content, segments are four seconds. Live broadcast and recording segments are determined by the keyframe interval or GOP size of the original broadcast.
### Example scenarios
**Two people each watch thirty minutes of a video or live broadcast. How much would it cost?**
This will result in 60 minutes of Minutes Delivered usage (or $0.06). Stream bills on total minutes of video delivered across all users.
**I have a really large file. Does that cost more?**
The cost to store a video is based only on its duration, not its file size. If the file is within the [30GB max file size limitation](https://developers.cloudflare.com/stream/faq/#is-there-a-limit-to-the-amount-of-videos-i-can-upload), it will be accepted. Be sure to use an [upload method](https://developers.cloudflare.com/stream/uploading-videos/) like Upload from Link or TUS that handles large files well.
**If I make a Direct Creator Upload link with a maximum duration (`maxDurationSeconds`) of 600 seconds which expires in 1 hour, how is storage consumed?**
* Ten minutes (600 seconds) will be subtracted from your available storage immediately.
* If the link is unused in one hour, those 10 minutes will be released.
* If the creator link is used to upload a five minute video, when the video is uploaded and processed, the 10 minute reservation will be released and the true five minute duration of the file will be counted.
* If the creator link is used to upload a five minute video but it fails to encode, the video will be marked as errored, the reserved storage will be released, and no storage use will be counted.
**I am broadcasting live, but no one is watching. How much does that cost?**
A live broadcast with no viewers will cost $0 for minutes delivered, but the recording of the broadcast will count toward minutes of video stored.
If someone watches the recording, that will be counted as minutes of video delivered.
If the recording is deleted, the storage use will be released.
**I want to store and deliver millions of minutes a month. Do you have volume pricing?**
Yes, contact our [Sales Team](https://www.cloudflare.com/plans/enterprise/contact/).
## Pricing for Media Transformations
After November 1st, 2025, Media Transforamtions and Image Transformations will use the same subscriptions and usage metrics.
* Generating a still frame (single image) from a video counts as 1 transformation.
* Generating an optimized video or extracting audio counts as 1 transformation *per second of the output* content.
* Each unique transformation, as determined by input and unique combination of flags, is only billed once per calendar month.
* All Media and Image Transformations cost $0.50 per 1,000 monthly unique transformation operations, with a free monthly allocation of 5,000.
</page>
<page>
---
title: Stream API Reference · Cloudflare Stream docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/stream-api/
md: https://developers.cloudflare.com/stream/stream-api/index.md
---
</page>
<page>
---
title: Stream live video · Cloudflare Stream docs
description: Cloudflare Stream lets you or your users stream live video, and
play live video in your website or app, without managing and configuring any
of your own infrastructure.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/stream-live/
md: https://developers.cloudflare.com/stream/stream-live/index.md
---
Cloudflare Stream lets you or your users [stream live video](https://www.cloudflare.com/learning/video/what-is-live-streaming/), and play live video in your website or app, without managing and configuring any of your own infrastructure.
## How Stream works
Stream handles video streaming end-to-end, from ingestion through delivery.
1. For each live stream, you create a unique live input, either using the Stream Dashboard or API.
2. Each live input has a unique Stream Key, that you provide to the creator who is streaming live video.
3. Creators use this Stream Key to broadcast live video to Cloudflare Stream, over either RTMPS or SRT.
4. Cloudflare Stream encodes this live video at multiple resolutions and delivers it to viewers, using Cloudflare's Global Network. You can play video on your website using the [Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/) or using [any video player that supports HLS or DASH](https://developers.cloudflare.com/stream/viewing-videos/using-own-player/).
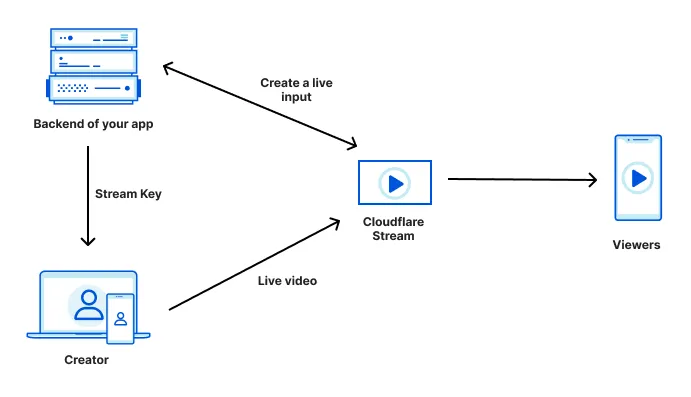
## RTMP reconnections
As long as your streaming software reconnects, Stream Live will continue to ingest and stream your live video. Make sure the streaming software you use to push RTMP feeds automatically reconnects if the connection breaks. Some apps like OBS reconnect automatically while other apps like FFmpeg require custom configuration.
## Bitrate estimates at each quality level (bitrate ladder)
Cloudflare Stream transcodes and makes live streams available to viewers at multiple quality levels. This is commonly referred to as [Adaptive Bitrate Streaming (ABR)](https://www.cloudflare.com/learning/video/what-is-adaptive-bitrate-streaming).
With ABR, client video players need to be provided with estimates of how much bandwidth will be needed to play each quality level (ex: 1080p). Stream creates and updates these estimates dynamically by analyzing the bitrate of your users' live streams. This ensures that live video plays at the highest quality a viewer has adequate bandwidth to play, even in cases where the broadcaster's software or hardware provides incomplete or inaccurate information about the bitrate of their live content.
### How it works
If a live stream contains content with low visual complexity, like a slideshow presentation, the bandwidth estimates provided in the HLS and DASH manifests will be lower — a stream like this has a low bitrate and requires relatively little bandwidth, even at high resolution. This ensures that as many viewers as possible view the highest quality level.
Conversely, if a live stream contains content with high visual complexity, like live sports with motion and camera panning, the bandwidth estimates provided in the manifest will be higher — a stream like this has a high bitrate and requires more bandwidth. This ensures that viewers with inadequate bandwidth switch down to a lower quality level, and their playback does not buffer.
### How you benefit
If you're building a creator platform or any application where your end users create their own live streams, your end users likely use streaming software or hardware that you cannot control. In practice, these live streaming setups often send inaccurate or incomplete information about the bitrate of a given live stream, or are misconfigured by end users.
Stream adapts based on the live video that we actually receive, rather than blindly trusting the advertised bitrate. This means that even in cases where your end users' settings are less than ideal, client video players will still receive the most accurate bitrate estimates possible, ensuring the highest quality video playback for your viewers, while avoiding pushing configuration complexity back onto your users.
## Transition from live playback to a recording
Recordings are available for live streams within 60 seconds after a live stream ends.
You can check a video's status to determine if it's ready to view by making a [`GET` request to the `stream` endpoint](https://developers.cloudflare.com/stream/stream-live/watch-live-stream/#use-the-api) and viewing the `state` or by [using the Cloudflare dashboard](https://developers.cloudflare.com/stream/stream-live/watch-live-stream/#use-the-dashboard).
After the live stream ends, you can [replay live stream recordings](https://developers.cloudflare.com/stream/stream-live/replay-recordings/) in the `ready` state by using one of the playback URLs.
## Billing
Stream Live is billed identically to the rest of Cloudflare Stream.
* You pay $5 per 1000 minutes of recorded video.
* You pay $1 per 1000 minutes of delivered video.
All Stream Live videos are automatically recorded. There is no additional cost for encoding and packaging live videos.
</page>
<page>
---
title: Transform videos · Cloudflare Stream docs
description: You can optimize and manipulate videos stored outside of Cloudflare
Stream with Media Transformations. Transformed videos and images are served
from one of your zones on Cloudflare.
lastUpdated: 2026-01-29T11:44:10.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/transform-videos/
md: https://developers.cloudflare.com/stream/transform-videos/index.md
---
Media Transformations is now GA:
Billing for Media Transformations will begin on November 1st, 2025.
You can optimize and manipulate videos stored *outside* of Cloudflare Stream with Media Transformations. Transformed videos and images are served from one of your zones on Cloudflare.
To transform a video or image, you must [enable transformations](https://developers.cloudflare.com/stream/transform-videos/#getting-started) for your zone. If your zone already has Image Transformations enabled, you can also optimize videos with Media Transformations.
## Getting started
You can dynamically optimize and generate still images from videos that are stored *outside* of Cloudflare Stream with Media Transformations.
Cloudflare will automatically cache every transformed video or image on our global network so that you store only the original image at your origin.
To enable transformations on your zone:
1. In the Cloudflare dashboard, go to the **Transformations** page.
[Go to **Transformations**](https://dash.cloudflare.com/?to=/:account/stream/video-transformations)
2. Locate the specific zone where you want to enable transformations.
3. Select **Enable** for the zone.
## Transform a video by URL
You can convert and resize videos by requesting them via a specially-formatted URL, without writing any code. The URL format is:
```plaintext
https://example.com/cdn-cgi/media/<OPTIONS>/<SOURCE-VIDEO>
```
* `example.com`: Your website or zone on Cloudflare, with Transformations enabled.
* `/cdn-cgi/media/`: A prefix that identifies a special path handled by Cloudflare's built-in media transformation service.
* `<OPTIONS>`: A comma-separated list of options. Refer to the available options below.
* `<SOURCE-VIDEO>`: A full URL (starting with `https://` or `http://`) of the original asset to resize.
For example, this URL will source an HD video from an R2 bucket, shorten it, crop and resize it as a square, and remove the audio.
```plaintext
https://example.com/cdn-cgi/media/mode=video,time=5s,duration=5s,width=500,height=500,fit=crop,audio=false/https://pub-8613b7f94d6146408add8fefb52c52e8.r2.dev/aus-mobile-demo.mp4
```
The result is an MP4 that can be used in an HTML video element without a player library.
## Options
### `mode`
Specifies the kind of output to generate.
* `video`: Outputs an H.264/AAC optimized MP4 file.
* `frame`: Outputs a still image.
* `spritesheet`: Outputs a JPEG with multiple frames.
* `audio`: Outputs an AAC encoded M4A file.
### `time`
Specifies when to start extracting the output in the input file. Depends on `mode`:
* When `mode` is `spritesheet`, `video`, or `audio`, specifies the timestamp where the output will start.
* When `mode` is `frame`, specifies the timestamp from which to extract the still image.
* Formats as a time string, for example: 5s, 2m
* Acceptable range: 0 – 10m
* Default: 0
### `duration`
The duration of the output video or spritesheet. Depends on `mode`:
* When `mode` is `video` or `audio`, specifies the duration of the output.
* When `mode` is `spritesheet`, specifies the time range from which to select frames.
* Acceptable range: 1s - 60s (or 1m)
* Default: input duration or 60 seconds, whichever is shorter
### `fit`
In combination with `width` and `height`, specifies how to resize and crop the output. If the output is resized, it will always resize proportionally so content is not stretched.
* `contain`: Respecting aspect ratio, scales a video up or down to be entirely contained within output dimensions.
* `scale-down`: Same as contain, but downscales to fit only. Do not upscale.
* `cover`: Respecting aspect ratio, scales a video up or down to entirely cover the output dimensions, with a center-weighted crop of the remainder.
### `height`
Specifies maximum height of the output in pixels. Exact behavior depends on `fit`.
* Acceptable range: 10-2000 pixels
### `width`
Specifies the maximum width of the image in pixels. Exact behavior depends on `fit`.
* Acceptable range: 10-2000 pixels
### `audio`
When `mode` is `video`, specifies whether or not to include the source audio in the output.
* `true`: Includes source audio.
* `false`: Output will be silent.
* Default: `true`
When `mode` is `audio`, audio cannot be false.
### `format`
If `mode` is `frame`, specifies the image output format.
* Acceptable options: `jpg`, `png`
If `mode` is `audio`, specifies the audio output format.
* Acceptable options: `m4a` (default)
### `filename`
Specifies the filename to use in the returned Content-Disposition header. If not specified, the filename will be derived from the source URL.
* Acceptable values:
* Maximum of 120 characters in length.
* Can only contain lowercase letters (a-z), numbers (0-9), hyphens (-), underscores (\_), and an optional extension. A valid name satisfies this regular expression: `^[a-zA-Z0-9-_]+.?[a-zA-Z0-9-_]+$`.
* Examples: `default.mp4`, `shortened-clip_5s`
## Source video requirements
* Input video must be less than 100MB.
* Input video should be an MP4 with H.264 encoded video and AAC or MP3 encoded audio. Other formats may work but are untested.
* Origin must support either HTTP HEAD and range requests, and must return a Content-Range header.
## Limitations
* Maximum input file size is 100 MB. Maximum duration of input video is 10 minutes.
* Media Transformations are not compatible with [Bring Your Own IP (BYOIP)](https://developers.cloudflare.com/byoip/).
* Input video should be an MP4 with H.264 encoded video and AAC or MP3 encoded audio, or animated GIF. Other formats may work but are untested.
## Pricing
After November 1st, 2025, Media Transformations and Image Transformations will use the same subscriptions and usage metrics.
* Generating a still frame (single image) from a video counts as 1 transformation.
* Generating an optimized video or extracting audio counts as 1 transformation *per second of the output* content.
* Each unique transformation, as determined by input and unique combination of flags, is only billed once per calendar month.
* All Media and Image Transformations cost $0.50 per 1,000 monthly unique transformation operations, with a free monthly allocation of 5,000.
</page>
<page>
---
title: Upload videos · Cloudflare Stream docs
description: Before you upload your video, review the options for uploading a
video, supported formats, and recommendations.
lastUpdated: 2025-07-28T14:52:18.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/uploading-videos/
md: https://developers.cloudflare.com/stream/uploading-videos/index.md
---
Before you upload your video, review the options for uploading a video, supported formats, and recommendations.
## Upload options
| Upload method | When to use |
| - | - |
| [Stream Dashboard](https://dash.cloudflare.com/?to=/:account/stream) | Upload videos from the Stream Dashboard without writing any code. |
| [Upload with a link](https://developers.cloudflare.com/stream/uploading-videos/upload-via-link/) | Upload videos using a link, such as an S3 bucket or content management system. |
| [Upload video file](https://developers.cloudflare.com/stream/uploading-videos/upload-video-file/) | Upload videos stored on a computer. |
| [Direct creator uploads](https://developers.cloudflare.com/stream/uploading-videos/direct-creator-uploads/) | Allows end users of your website or app to upload videos directly to Cloudflare Stream. |
## Supported video formats
Note
Files must be less than 30 GB, and content should be encoded and uploaded in the same frame rate it was recorded.
* MP4
* MKV
* MOV
* AVI
* FLV
* MPEG-2 TS
* MPEG-2 PS
* MXF
* LXF
* GXF
* 3GP
* WebM
* MPG
* Quicktime
## Recommendations for on-demand videos
* Optional but ideal settings:
* MP4 containers
* AAC audio codec
* H264 video codec
* 60 or fewer frames per second
* Closed GOP (*Only required for live streaming.*)
* Mono or Stereo audio. Stream will mix audio tracks with more than two channels down to stereo.
</page>
<page>
---
title: Play video · Cloudflare Stream docs
lastUpdated: 2024-08-30T13:02:26.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/stream/viewing-videos/
md: https://developers.cloudflare.com/stream/viewing-videos/index.md
---
* [Use your own player](https://developers.cloudflare.com/stream/viewing-videos/using-own-player/)
* [Use the Stream Player](https://developers.cloudflare.com/stream/viewing-videos/using-the-stream-player/)
* [Secure your Stream](https://developers.cloudflare.com/stream/viewing-videos/securing-your-stream/)
* [Display thumbnails](https://developers.cloudflare.com/stream/viewing-videos/displaying-thumbnails/)
* [Download video or audio](https://developers.cloudflare.com/stream/viewing-videos/download-videos/)
</page>
<page>
---
title: WebRTC · Cloudflare Stream docs
description: Sub-second latency live streaming (using WHIP) and playback (using
WHEP) to unlimited concurrent viewers.
lastUpdated: 2026-02-02T10:17:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/stream/webrtc-beta/
md: https://developers.cloudflare.com/stream/webrtc-beta/index.md
---
Sub-second latency live streaming (using WHIP) and playback (using WHEP) to unlimited concurrent viewers.
WebRTC is ideal for when you need live video to playback in near real-time, such as:
* When the outcome of a live event is time-sensitive (live sports, financial news)
* When viewers interact with the live stream (live Q\&A, auctions, etc.)
* When you want your end users to be able to easily go live or create their own video content, from a web browser or native app
Note
WebRTC streaming is currently in beta, and we'd love to hear what you think. Join the Cloudflare Discord server [using this invite](https://discord.com/invite/cloudflaredev/) and hop into our [Discord channel](https://discord.com/channels/595317990191398933/893253103695065128) to let us know what you're building with WebRTC!
## Step 1: Create a live input
Create a live input using one of the two options:
* Use the **Live inputs** page of the Cloudflare dashboard.
[Go to **Live inputs**](https://dash.cloudflare.com/?to=/:account/stream/inputs)
* Make a POST request to the [`/live_inputs` API endpoint](https://developers.cloudflare.com/api/resources/stream/subresources/live_inputs/methods/create/)
```json
{
"uid": "1a553f11a88915d093d45eda660d2f8c",
...
"webRTC": {
"url": "https://customer-<CODE>.cloudflarestream.com/<SECRET>/webRTC/publish"
},
"webRTCPlayback": {
"url": "https://customer-<CODE>.cloudflarestream.com/<INPUT_UID>/webRTC/play"
},
...
}
```
## Step 2: Go live using WHIP
Every live input has a unique URL that one creator can be stream to. This URL should *only* be shared with the creator — anyone with this URL has the ability to stream live video to this live input.
Copy the URL from either:
* The **Live inputs** page of the Cloudflare dashboard.
[Go to **Live inputs**](https://dash.cloudflare.com/?to=/:account/stream/inputs)
* The `webRTC` key in the API response (see above).
Paste this URL into the example code.
```javascript
// Add a <video> element to the HTML page this code runs in:
// <video id="input-video" autoplay muted></video>
import WHIPClient from "./WHIPClient.js";
const url = "<WEBRTC_URL_FROM_YOUR_LIVE_INPUT>"; // add the webRTC URL from your live input here
const videoElement = document.getElementById("input-video");
const client = new WHIPClient(url, videoElement);
```
Once the creator grants permission to their camera and microphone, live video and audio will automatically start being streamed to Cloudflare, using WebRTC.
You can also use this URL with any client that supports the [WebRTC-HTTP ingestion protocol (WHIP)](https://www.ietf.org/archive/id/draft-ietf-wish-whip-16.html). See [supported WHIP clients](#supported-whip-and-whep-clients) for a list of clients we have tested and confirmed compatibility with Cloudflare Stream.
## Step 3: Play live video using WHEP
Copy the URL from either:
* The **Live inputs** page of the Cloudflare dashboard.
[Go to **Live inputs**](https://dash.cloudflare.com/?to=/:account/stream/inputs)
* The `webRTCPlayback` key in the API response (see above)
There are no limits on the number of concurrent viewers.
Paste this URL into the example code.
```javascript
// Add a <video> element to the HTML page this code runs in:
// <video id="output-video" autoplay muted></video>
import WHEPClient from "./WHEPClient.js";
const url = "<WEBRTC_URL_FROM_YOUR_LIVE_INPUT>"; // add the webRTCPlayback URL from your live input here
const videoElement = document.getElementById("output-video");
const client = new WHEPClient(url, videoElement);
```
As long as the creator is actively streaming, viewers should see their broadcast in their browser, with less than 1 second of latency.
You can also use this URL with any client that supports the [WebRTC-HTTP egress protocol (WHEP)](https://www.ietf.org/archive/id/draft-murillo-whep-01.html). See [supported WHEP clients](#supported-whip-and-whep-clients) for a list of clients we have tested and confirmed compatibility with Cloudflare Stream.
## Using WebRTC in native apps
If you are building a native app, the example code above can run within a [WkWebView (iOS)](https://developer.apple.com/documentation/webkit/wkwebview), [WebView (Android)](https://developer.android.com/reference/android/webkit/WebView) or using [react-native-webrtc](https://github.com/react-native-webrtc/react-native-webrtc/blob/master/Documentation/BasicUsage.md). If you need to use WebRTC without a webview, you can use Google's Java and Objective-C native [implementations of WebRTC APIs](https://webrtc.googlesource.com/src/+/refs/heads/main/sdk).
## Debugging WebRTC
* **Chrome**: Navigate to `chrome://webrtc-internals` to view detailed logs and graphs.
* **Firefox**: Navigate to `about:webrtc` to view information about WebRTC sessions, similar to Chrome.
* **Safari**: To enable WebRTC logs, from the inspector, open the settings tab (cogwheel icon), and set WebRTC logging to "Verbose" in the dropdown menu.
## Supported WHIP and WHEP clients
Beyond the example WHIP client and example WHEP client used in the examples above, we have tested and confirmed that the following clients are compatible with Cloudflare Stream:
### WHIP
* [OBS (Open Broadcaster Software)](https://obsproject.com)
* [@eyevinn/whip-web-client](https://www.npmjs.com/package/@eyevinn/whip-web-client) (TypeScript)
* [whip-go](https://github.com/ggarber/whip-go) (Go)
* [gst-plugins-rs](https://gitlab.freedesktop.org/gstreamer/gst-plugins-rs) (Gstreamer plugins, written in Rust)
* [Larix Broadcaster](https://softvelum.com/larix/) (free apps for iOS and Android with WebRTC based on Pion, SDK available)
### WHEP
* [@eyevinn/webrtc-player](https://www.npmjs.com/package/@eyevinn/webrtc-player) (TypeScript)
* [@eyevinn/wrtc-egress](https://www.npmjs.com/package/@eyevinn/wrtc-egress) (TypeScript)
* [gst-plugins-rs](https://gitlab.freedesktop.org/gstreamer/gst-plugins-rs) (Gstreamer plugins, written in Rust)
As more WHIP and WHEP clients are published, we are committed to supporting them and being fully compliant with the both protocols.
## Supported codecs
* [VP9](https://developers.google.com/media/vp9) (recommended for highest quality)
* [VP8](https://en.wikipedia.org/wiki/VP8)
* [h264](https://en.wikipedia.org/wiki/Advanced_Video_Coding) (Constrained Baseline Profile Level 3.1, referred to as `42e01f` in the SDP offer's `profile-level-id` parameter.)
## Conformance with WHIP and WHEP specifications
Cloudflare Stream fully supports all aspects of the [WHIP](https://www.ietf.org/archive/id/draft-ietf-wish-whip-16.html) and [WHEP](https://www.ietf.org/archive/id/draft-murillo-whep-01.html) specifications, including:
* [Trickle ICE](https://datatracker.ietf.org/doc/rfc8838/)
* [Server and client offer modes](https://www.ietf.org/archive/id/draft-murillo-whep-01.html#section-3) for WHEP
You can find the specific version of WHIP and WHEP being used in the `protocol-version` header in WHIP and WHEP API responses. The value of this header references the IETF draft slug for each protocol. Currently, Stream uses `draft-ietf-wish-whip-06` (expected to be the final WHIP draft revision) and `draft-murillo-whep-01` (the most current WHEP draft).
## Limitations while in beta
* [Recording](https://developers.cloudflare.com/stream/stream-live/watch-live-stream/#live-stream-recording-playback) is not yet supported (coming soon)
* [Simulcasting](https://developers.cloudflare.com/stream/stream-live/simulcasting) (restreaming) is not yet supported (coming soon)
* [Live viewer counts](https://developers.cloudflare.com/stream/getting-analytics/live-viewer-count/) are not yet supported (coming soon)
* [Analytics](https://developers.cloudflare.com/stream/getting-analytics/fetching-bulk-analytics/) are not yet supported (coming soon)
* WHIP and WHEP must be used together — we do not yet support streaming using RTMP/SRT and playing using WHEP, or streaming using WHIP and playing using HLS or DASH. (coming soon)
* Once generally available, WebRTC streaming will be priced just like the rest of Cloudflare Stream, based on minutes stored and minutes of video delivered.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare SSL/TLS docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/404/
md: https://developers.cloudflare.com/ssl/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Changelog · Cloudflare SSL/TLS docs
description: Cloudflare Secrets Store is now integrated with AI Gateway,
allowing you to store, manage, and deploy your AI provider keys in a secure
and seamless configuration through Bring Your Own Key. Instead of passing your
AI provider keys directly in every request header, you can centrally manage
each key with Secrets Store and deploy in your gateway configuration using
only a reference, rather than passing the value in plain text.
lastUpdated: 2025-04-23T17:56:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/changelog/
md: https://developers.cloudflare.com/ssl/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/ssl.xml)
## 2025-08-25
**Manage and deploy your AI provider keys through Bring Your Own Key (BYOK) with AI Gateway, now powered by Cloudflare Secrets Store**
Cloudflare Secrets Store is now integrated with AI Gateway, allowing you to store, manage, and deploy your AI provider keys in a secure and seamless configuration through [Bring Your Own Key](https://developers.cloudflare.com/ai-gateway/configuration/bring-your-own-keys/). Instead of passing your AI provider keys directly in every request header, you can centrally manage each key with Secrets Store and deploy in your gateway configuration using only a reference, rather than passing the value in plain text.
You can now create a secret directly from your AI Gateway [in the dashboard](http://dash.cloudflare.com/?to=/:account/ai-gateway) by navigating into your gateway -> **Provider Keys** -> **Add**.

You can also create your secret with the newly available **ai\_gateway** scope via [wrangler](https://developers.cloudflare.com/workers/wrangler/commands/), the [Secrets Store dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store), or the [API](https://developers.cloudflare.com/api/resources/secrets_store/).
Then, pass the key in the request header using its Secrets Store reference:
```plaintext
curl -X POST https://gateway.ai.cloudflare.com/v1/<ACCOUNT_ID>/my-gateway/anthropic/v1/messages \
--header 'cf-aig-authorization: ANTHROPIC_KEY_1 \
--header 'anthropic-version: 2023-06-01' \
--header 'Content-Type: application/json' \
--data '{"model": "claude-3-opus-20240229", "messages": [{"role": "user", "content": "What is Cloudflare?"}]}'
```
Or, using Javascript:
```plaintext
import Anthropic from '@anthropic-ai/sdk';
const anthropic = new Anthropic({
apiKey: "ANTHROPIC_KEY_1",
baseURL: "https://gateway.ai.cloudflare.com/v1/<ACCOUNT_ID>/my-gateway/anthropic",
});
const message = await anthropic.messages.create({
model: 'claude-3-opus-20240229',
messages: [{role: "user", content: "What is Cloudflare?"}],
max_tokens: 1024
});
```
For more information, check out the [blog](https://blog.cloudflare.com/ai-gateway-aug-2025-refresh)!
## 2025-05-27
**Increased limits for Cloudflare for SaaS and Secrets Store free and pay-as-you-go plans**
With upgraded limits to [all free and paid plans](https://www.cloudflare.com/plans/), you can now scale more easily with [Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/) and [Secrets Store](https://developers.cloudflare.com/secrets-store/).
[Cloudflare for SaaS](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/) allows you to extend the benefits of Cloudflare to your customers via their own custom or vanity domains. Now, the [limit for custom hostnames](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/plans/) on a Cloudflare for SaaS pay-as-you-go plan has been **raised from 5,000 custom hostnames to 50,000 custom hostnames.**
With custom origin server -- previously an enterprise-only feature -- you can route traffic from one or more custom hostnames somewhere other than your default proxy fallback. [Custom origin server](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/start/advanced-settings/custom-origin/) is now available to Cloudflare for SaaS customers on Free, Pro, and Business plans.
You can enable custom origin server on a per-custom hostname basis [via the API](https://developers.cloudflare.com/api/resources/custom_hostnames/methods/edit/) or the UI:

Currently [in beta with a Workers integration](https://blog.cloudflare.com/secrets-store-beta/), [Cloudflare Secrets Store](https://developers.cloudflare.com/secrets-store/) allows you to store, manage, and deploy account level secrets from a secure, centralized platform your [Cloudflare Workers](https://developers.cloudflare.com/workers/). Now, you can create and deploy **100 secrets per account**. Try it out [in the dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store), with [Wrangler](https://developers.cloudflare.com/secrets-store/integrations/workers/), or [via the API](https://developers.cloudflare.com/api/resources/secrets_store/) today.
## 2025-04-09
**Cloudflare Secrets Store now available in Beta**
Cloudflare Secrets Store is available today in Beta. You can now store, manage, and deploy account level secrets from a secure, centralized platform to your Workers.

To spin up your Cloudflare Secrets Store, simply click the new Secrets Store tab [in the dashboard](http://dash.cloudflare.com/?to=/:account/secrets-store) or use this Wrangler command:
```sh
wrangler secrets-store store create <name> --remote
```
The following are supported in the Secrets Store beta:
* Secrets Store UI & API: create your store & create, duplicate, update, scope, and delete a secret
* Workers UI: bind a new or existing account level secret to a Worker and deploy in code
* Wrangler: create your store & create, duplicate, update, scope, and delete a secret
* Account Management UI & API: assign Secrets Store permissions roles & view audit logs for actions taken in Secrets Store core platform
For instructions on how to get started, visit our [developer documentation](https://developers.cloudflare.com/secrets-store/).
## 2025-02-14
**Upload a certificate bundle with an RSA and ECDSA certificate per custom hostname**
Cloudflare has supported both RSA and ECDSA certificates across our platform for a number of years. Both certificates offer the same security, but ECDSA is more performant due to a smaller key size. However, RSA is more widely adopted and ensures compatibility with legacy clients. Instead of choosing between them, you may want both – that way, ECDSA is used when clients support it, but RSA is available if not.
Now, you can upload both an RSA and ECDSA certificate on a custom hostname via the API.
```plaintext
curl -X POST https://api.cloudflare.com/client/v4/zones/$ZONE_ID/custom_hostnames \
-H 'Content-Type: application/json' \
-H "X-Auth-Email: $CLOUDFLARE_EMAIL" \
-H "X-Auth-Key: $CLOUDFLARE_API_KEY" \
-d '{
"hostname": "hostname",
"ssl": {
"custom_cert_bundle": [
{
"custom_certificate": "RSA Cert",
"custom_key": "RSA Key"
},
{
"custom_certificate": "ECDSA Cert",
"custom_key": "ECDSA Key"
}
],
"bundle_method": "force",
"wildcard": false,
"settings": {
"min_tls_version": "1.0"
}
}
}’
```
You can also:
* [Upload](https://developers.cloudflare.com/api/resources/custom_hostnames/methods/create/) an RSA or ECDSA certificate to a custom hostname with an existing ECDSA or RSA certificate, respectively.
* [Replace](https://developers.cloudflare.com/api/resources/custom_hostnames/subresources/certificate_pack/subresources/certificates/methods/update/) the RSA or ECDSA certificate with a certificate of its same type.
* [Delete](https://developers.cloudflare.com/api/resources/custom_hostnames/subresources/certificate_pack/subresources/certificates/methods/delete/) the RSA or ECDSA certificate (if the custom hostname has both an RSA and ECDSA uploaded).
This feature is available for Business and Enterprise customers who have purchased custom certificates.
## 2024-10-18
**New cloudflare\_branding flag allows hostnames with over 64 characters for all CAs**
To order certificates for hostnames longer than 64 characters, customers can now use the `cloudflare_branding` flag when ordering a certificate via [API](https://developers.cloudflare.com/api/resources/ssl/subresources/certificate_packs/methods/create/). Setting `cloudflare_branding` to `true` will cause `sni.cloudflaressl.com` to be used as the common name, while the long hostname is added as part of the subject alternative name (SAN).
## 2024-09-19
**SSL.com available with ACM and SSL for SaaS**
SSL.com is one of the [certificate authorities](https://developers.cloudflare.com/ssl/reference/certificate-authorities/) that Cloudflare partners with. SSL.com is now available as an option to customers with Advanced Certificate Manager (ACM) or SSL for SaaS. Consider our [reference documentation](https://developers.cloudflare.com/ssl/reference/certificate-authorities/#sslcom) for details.
</page>
<page>
---
title: Client certificates (mTLS) · Cloudflare SSL/TLS docs
description: Use Cloudflare public key infrastructure (PKI) to create client
certificates and enforce mutual Transport Layer Security (mTLS) encryption.
lastUpdated: 2026-02-04T14:06:08.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/client-certificates/
md: https://developers.cloudflare.com/ssl/client-certificates/index.md
---
Use Cloudflare's public key infrastructure (PKI) to create client certificates, or [bring your own CA for mTLS](https://developers.cloudflare.com/ssl/client-certificates/byo-ca/).
[Mutual TLS (mTLS)](https://www.cloudflare.com/learning/access-management/what-is-mutual-tls/) authentication is a common security practice that uses client certificates to ensure traffic between client and server is bidirectionally secure and trusted. mTLS also allows requests that do not authenticate via an identity provider — such as Internet-of-things (IoT) devices — to demonstrate they can reach a given resource.
mTLS at Cloudflare
For a broader overview, refer to the [mTLS at Cloudflare learning path](https://developers.cloudflare.com/learning-paths/mtls/concepts/).
***
## How it works
Client certificates issued from a given CA are installed on client devices that should be granted access. Then, for any host that has [mTLS enabled](https://developers.cloudflare.com/ssl/client-certificates/enable-mtls/), Cloudflare - acting as the server in this case - requires a certificate from the client trying to access the hostname.
If a certificate is presented, Cloudflare validates the client certificate against CAs set at account level. This means that these certificates can be used for validation across multiple zones/domains (`example.com`), as long as the zones are under the same Cloudflare account and mTLS has been enabled for the requested hosts (`host.example.com`).
The account-level CAs can be:
* The Cloudflare-managed CA: This is the default option. Certificates and hostname associations are listed on your [dashboard](https://dash.cloudflare.com/?to=/:account/:zone/ssl-tls/client-certificates/).
* [BYOCA](https://developers.cloudflare.com/ssl/client-certificates/byo-ca/) certificates: This is an API-only option, available on Enterprise accounts. Certificates and hostname associations are **not** listed on your dashboard.
Cloudflare then stores the validation result in a field called [`cf.tls_client_auth.cert_verified`](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/cf.tls_client_auth.cert_verified/):
* **Success**: `cf.tls_client_auth.cert_verified` is `true`, and you can find client certificate details in [specific mTLS fields](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/?search-term=cf.tls_client_auth).
* **Failure**: `cf.tls_client_auth.cert_verified` is `false`.
***
## Use cases
As explained in the [mTLS learning path](https://developers.cloudflare.com/learning-paths/mtls/concepts/), there are different use cases and implementation options for mTLS. Consider the following links for specific guidance.
* [Application security](https://developers.cloudflare.com/learning-paths/mtls/mtls-app-security/)
* [mTLS for Zero Trust](https://developers.cloudflare.com/cloudflare-one/access-controls/service-credentials/mutual-tls-authentication/) (Cloudflare Access integration)
* [mTLS with API Shield](https://developers.cloudflare.com/api-shield/security/mtls/configure/)
* [mTLS Workers binding](https://developers.cloudflare.com/workers/runtime-apis/bindings/mtls/)
Apart from the mTLS Workers binding, any of the above implementations can use your own CA instead of the Cloudflare-managed one. Refer to [Bring your own CA](https://developers.cloudflare.com/ssl/client-certificates/byo-ca/).
### mTLS and Workers
Use the [mTLS Workers binding](https://developers.cloudflare.com/workers/runtime-apis/bindings/mtls/) when you need your worker to present a client certificate to an external service. To authenticate requests from a client to your worker instead, refer to [SSL/TLS > Client certificates](https://dash.cloudflare.com/?to=/:account/:zone/ssl-tls/client-certificates/) and the regular [mTLS for application security](https://developers.cloudflare.com/learning-paths/mtls/mtls-app-security/) implementation.
```mermaid
flowchart LR
accTitle: mTLS from client to worker versus mTLS from worker to external service
accDescr: Diagram showing two different implementations that can be considered for mTLS with Cloudflare Workers.
A[Client] <--App security mTLS--> B((Cloudflare))<--mTLS worker binding--> C[(External service)]
```
***
## Further resources
* [Create a client certificate](https://developers.cloudflare.com/ssl/client-certificates/create-a-client-certificate/)
* [Enable mTLS](https://developers.cloudflare.com/ssl/client-certificates/enable-mtls/)
* [Bring your own CA for mTLS](https://developers.cloudflare.com/ssl/client-certificates/byo-ca/)
* [Forward certificate to server](https://developers.cloudflare.com/ssl/client-certificates/forward-a-client-certificate/)
* [Label client certificates](https://developers.cloudflare.com/ssl/client-certificates/label-client-certificate/)
* [Revoke a client certificate](https://developers.cloudflare.com/ssl/client-certificates/revoke-client-certificate/)
* [Configure your mobile app or IoT device](https://developers.cloudflare.com/ssl/client-certificates/configure-your-mobile-app-or-iot-device/)
* [Troubleshooting](https://developers.cloudflare.com/ssl/client-certificates/troubleshooting/)
* [mTLS for Zero Trust](https://developers.cloudflare.com/cloudflare-one/access-controls/service-credentials/mutual-tls-authentication/)
</page>
<page>
---
title: Concepts · Cloudflare SSL/TLS docs
description: This page defines and articulates key concepts that are relevant to
Cloudflare SSL/TLS and are used in the Cloudflare SSL/TLS documentation.
lastUpdated: 2025-09-23T08:43:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/concepts/
md: https://developers.cloudflare.com/ssl/concepts/index.md
---
This page defines and articulates key concepts that are relevant to Cloudflare SSL/TLS and are used in this documentation. For more concepts and broader descriptions, check out the [Cloudflare Learning Center](https://www.cloudflare.com/learning/ssl/what-is-ssl/).
## SSL/TLS certificate
An SSL/TLS certificate is what enables websites and applications to establish secure connections. With SSL/TLS, a client - such as a browser - can verify the authenticity and integrity of the server it is connecting with, and use encryption to exchange information.
Since [Cloudflare's global network](https://www.cloudflare.com/network/) is at the core of several products and services that Cloudflare offers, what this implies in terms of SSL/TLS is that, instead of only one certificate, there can actually be two certificates involved in a single request: an edge certificate and an origin certificate.
### Edge certificate
The [edge certificates](https://developers.cloudflare.com/ssl/edge-certificates/) are the ones that Cloudflare presents to clients visiting your website or application. You can manage edge certificates through the [Cloudflare Dashboard](https://dash.cloudflare.com/?to=/:account/:zone/ssl-tls/edge-certificates).
### Origin certificate
[Origin certificates](https://developers.cloudflare.com/ssl/origin-configuration/) guarantee the security and authentication on the other side of the network, between Cloudflare and the origin server of your website or application. Origin certificates are managed on your origin server.
[SSL/TLS encryption modes](https://developers.cloudflare.com/ssl/origin-configuration/ssl-modes/) control whether and how Cloudflare will use both these ceritifcates, and you can choose between different modes on the [SSL/TLS overview page](https://dash.cloudflare.com/?to=/:account/:zone/ssl-tls).
## Validity period
One common aspect of every SSL/TLS certificate is that they must have a fixed expiration date. If a certificate is expired, clients - such as your visitor's browser - will consider that a secure connection cannot be established, resulting in warnings or errors.
Different [certificate authorities (CAs)](#certificate-authority-ca) support different validity periods. Cloudflare works with them to guarantee that both [Universal](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/) and [Advanced](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/) edge certificates are always renewed.
## Certificate authority (CA)
A [certificate authority (CA)](https://developers.cloudflare.com/ssl/reference/certificate-authorities/) is a trusted third party that generates and gives out SSL/TLS certificates. The CA digitally signs the certificates with their own private key, allowing client devices - such as your visitor's browser - to verify that the certificate is trustworthy.
As explained in the article about [what is an ssl certificate](https://www.cloudflare.com/learning/ssl/what-is-an-ssl-certificate/), this means that, besides not being expired, an SSL/TLS certificate should be issued by a certificate authority (CA) in order to avoid warnings or errors.
## Validation level
SSL/TLS certificates vary in terms of the level to which a CA has validated them. As explained in the article about [types of certificates](https://www.cloudflare.com/learning/ssl/types-of-ssl-certificates/), SSL/TLS certificates can be DV (Domain Validated), OV (Organization Validated) or EV (Extended Validation).
Certificates issued through Cloudflare - [Universal](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/), [Advanced](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/), and [Custom Hostname](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/) certificates - are Domain Validated (DV). You can [upload a custom certificate](https://developers.cloudflare.com/ssl/edge-certificates/custom-certificates/) if your organization needs OV or EV certificates.
## Origin pull
When visitors request content from your website or application, Cloudflare first attempts to [serve content from the cache](https://www.cloudflare.com/learning/cdn/what-is-caching/). If this attempt fails, Cloudflare sends a request back to your origin web server to get the content. This request between Cloudflare and your origin web server is called origin pull.
This relates to the difference between [edge certificates](#edge-certificate) and [origin certificates](#origin-certificate), and also explains why some specifications such as [cipher suites](#cipher-suites) can be set differently depending on whether they refer to the connection between Cloudflare and your visitor's browser or between Cloudflare and your origin server.
## Cipher suites
Besides the authentication and integrity aspects that valid certificates guarantee, the other important aspect of SSL/TLS certificates is encryption. Cipher suites determine the set of algorithms that can be used for encryption/decryption and that will be negotiated during an [SSL/TLS handshake](https://www.cloudflare.com/learning/ssl/what-happens-in-a-tls-handshake/).
For the purpose of this documentation, keep in mind that [cipher suites supported at Cloudflare's network](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/cipher-suites/supported-cipher-suites/) may not be the same as [cipher suites presented by Cloudflare to your origin server](https://developers.cloudflare.com/ssl/origin-configuration/cipher-suites/).
## Trust store
The list of [certificate authority (CA)](#certificate-authority-ca) and intermediate certificates that are trusted by operating systems, web browsers or other software that interacts with SSL/TLS certificates is called trust store. Cloudflare maintains its trust store on a public [GitHub repository](https://github.com/cloudflare/cfssl_trust).
While for most cases you do not have to worry about this list or how it is used when a client checks your SSL/TLS certificate, some features such as [Custom Origin Trust Store](https://developers.cloudflare.com/ssl/origin-configuration/custom-origin-trust-store/), and processes such as [bundle methodologies](https://developers.cloudflare.com/ssl/edge-certificates/custom-certificates/bundling-methodologies/), are directly related to it.
## Chain of trust
Depending on your organization requirements, or if you have to troubleshoot an issue with your certificates, for example, you might come across the terms root certificate, intermediate certificate and leaf certificate.
These terms refer to the way in which the certificate presented to a client - the leaf certificate - has to be traceable back to a trusted certificate authority (CA) certificate - the [root certificate](https://en.wikipedia.org/wiki/Root_certificate). This process is structured around a [chain of trust](https://en.wikipedia.org/wiki/Chain_of_trust).
</page>
<page>
---
title: Edge certificates · Cloudflare SSL/TLS docs
description: Edge certificates are the SSL/TLS certificates that Cloudflare
presents to your visitors. Consider how different certificate types align to
common use cases.
lastUpdated: 2025-01-10T11:24:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/edge-certificates/
md: https://developers.cloudflare.com/ssl/edge-certificates/index.md
---
Consider the information below for guidance on how to choose different edge certificates for common use cases, or refer to the other pages in this section for more options.
If you are not familiar with what SSL/TLS certificates are, refer to [Concepts](https://developers.cloudflare.com/ssl/concepts/).
## Use cases
### Simplify issuance and renewal
Issuing and renewing certificates can take up a lot of time from your technical teams. Leverage Cloudflare [Universal SSL](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/) or [advanced certificates](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/) to simplify this process.
Advanced certificates offer more customization than Universal SSL.
With [custom certificates](https://developers.cloudflare.com/ssl/edge-certificates/custom-certificates/), you have full control in terms of certificate authority (CA) or certificate [validation level](https://developers.cloudflare.com/ssl/concepts/#validation-level), but you need to handle issuance and renewal on your own.
### Meet cipher suites requirements
The different algorithms used in SSL/TLS encryption can vary in terms of how secure they are.
Through [cipher suites customization](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/cipher-suites/customize-cipher-suites/) you can control which ciphers are used for your domain and/or specific hostnames, making it possible to achieve balance between highly available marketing websites (`www.example.com`) that even legacy devices can access and highly secure services or applications (`shop.example.com`) that require [standards compliance](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/cipher-suites/compliance-status/).
Cipher suites customization applies to any edge certificate used in connections to a given hostname. However, to enable [custom cipher suites and other features](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/#advanced-certificate-manager), you must [purchase the Advanced Certificate Manager add-on](https://dash.cloudflare.com/?to=/:account/:zone/ssl-tls/acm/).
If you already have Advanced Certificate Manager, use the API to set up custom cipher suites. Refer to [Customize cipher suites](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/cipher-suites/customize-cipher-suites/) for more guidance.
### Automate domain control validation (DCV)
If you want to use Cloudflare but manage DNS externally ([partial setup](https://developers.cloudflare.com/dns/zone-setups/partial-setup/)), you may need to perform [domain control validation (DCV)](https://developers.cloudflare.com/ssl/edge-certificates/changing-dcv-method/) to prove that you have control over your domain before your SSL/TLS certificate can be issued.
To make this process easier and automate DCV at certificate renewal, use [advanced certificates](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/) and set up [delegated DCV](https://developers.cloudflare.com/ssl/edge-certificates/changing-dcv-method/methods/delegated-dcv/).
</page>
<page>
---
title: Get started with SSL/TLS · Cloudflare SSL/TLS docs
description: Follow the steps below to enable SSL/TLS protection for your application.
lastUpdated: 2025-08-20T18:47:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/get-started/
md: https://developers.cloudflare.com/ssl/get-started/index.md
---
Follow the steps below to enable SSL/TLS protection for your application.
## Before you begin
* [Create an account and register an application](https://developers.cloudflare.com/fundamentals/account/)
## Choose an edge certificate
As explained in the [concepts page](https://developers.cloudflare.com/ssl/concepts/#ssltls-certificate), edge certificates are the SSL/TLS certificates that Cloudflare presents to your visitors.
Cloudflare offers a variety of options for your application's edge certificates:
* [**Universal certificates**](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/):
By default, Cloudflare issues — and [renews](https://developers.cloudflare.com/ssl/reference/certificate-validity-periods/#universal-ssl) — free, unshared, publicly trusted SSL certificates to all domains [added to](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/) and [activated on](https://developers.cloudflare.com/dns/zone-setups/reference/domain-status/) Cloudflare.
* [**Advanced certificates**](https://developers.cloudflare.com/ssl/edge-certificates/advanced-certificate-manager/):
Use advanced certificates when you want something more customizable than [Universal SSL](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/) but still want the convenience of SSL certificate issuance and renewal.
* [**Custom certificates**](https://developers.cloudflare.com/ssl/edge-certificates/custom-certificates/):
Custom certificates are meant for Business and Enterprise customers who want to use their own SSL certificates.
* [**Keyless certificates**](https://developers.cloudflare.com/ssl/keyless-ssl/) (Enterprise only):
Keyless SSL allows security-conscious clients to upload their own custom certificates and benefit from Cloudflare, but without exposing their TLS private keys.
Refer to [Edge certificates](https://developers.cloudflare.com/ssl/edge-certificates/) for more information on how different certificate types can respond to common use cases.
For SaaS providers
Cloudflare for SaaS allows you to extend the security and performance benefits of Cloudflare's network to your customers via their own custom or vanity domains.
For more details, refer to [Cloudflare for SaaS (managed hostnames)](https://developers.cloudflare.com/cloudflare-for-platforms/cloudflare-for-saas/security/certificate-management/).
## Choose your encryption mode
Once you have chosen your edge certificate, [choose an encryption mode](https://developers.cloudflare.com/ssl/origin-configuration/ssl-modes/).
Encryption modes specify how Cloudflare encrypts connections between (a) visitors and Cloudflare, and (b) Cloudflare and your origin server. For more context about this two-part process refer to the [concepts page](https://developers.cloudflare.com/ssl/concepts/#ssltls-certificate).
Note that some encryption modes will require you to have a valid [origin certificate](https://developers.cloudflare.com/ssl/concepts/#origin-certificate), which is managed on your origin server. Each encryption mode setup page lists out this and other requirements and you can also [consider other Cloudflare options to use with your origin server](https://developers.cloudflare.com/ssl/origin-configuration/), such as [Origin CA certificates](https://developers.cloudflare.com/ssl/origin-configuration/origin-ca/).
## Enforce HTTPS connections
Even if your application has an active edge certificate, visitors can still access resources over unsecured HTTP connections.
Using various Cloudflare settings, however, you can force all or most visitor connections to [use HTTPS](https://developers.cloudflare.com/ssl/edge-certificates/encrypt-visitor-traffic/).
## Optional - Enable additional features
After you have chosen your encryption mode and enforced HTTPS connections, evaluate the following settings:
* [Edge certificates](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/): Customize different aspects of your edge certificates, from enabling **Opportunistic Encryption** to specifying a **Minimum TLS Version**.
* [Authenticated origin pull](https://developers.cloudflare.com/ssl/origin-configuration/authenticated-origin-pull/): Ensure all requests to your origin server originate from the Cloudflare network.
* [Notifications](https://developers.cloudflare.com/notifications/notification-available/): Set up alerts related to certificate validation status, issuance, renewal, and expiration.
</page>
<page>
---
title: Keyless SSL · Cloudflare SSL/TLS docs
description: Keyless SSL allows security-conscious clients to upload their own
custom certificates and benefit from Cloudflare, but without exposing their
TLS private keys.
lastUpdated: 2025-08-20T18:47:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/keyless-ssl/
md: https://developers.cloudflare.com/ssl/keyless-ssl/index.md
---
Keyless SSL allows security-conscious clients to upload their own custom certificates and benefit from Cloudflare, but without exposing their TLS private keys.
Before configuring Keyless SSL, you should read our [technical background](https://blog.cloudflare.com/keyless-ssl-the-nitty-gritty-technical-details/) on how the technology works and where your infrastructure sits within the scope of the TLS handshake.
The source code for our key server (what you will run) and keyless client (what our servers will contact your key server with) can be [found on GitHub](https://github.com/cloudflare/gokeyless).
***
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | No | Paid add-on |
Keyless SSL is only available to Enterprise customers that maintain their own SSL certificate purchased from a valid Certificate Authority. Cloudflare does not supply any certificates for use with Keyless SSL.
***
## Limitations
TLS 1.3 is not supported for Keyless SSL.
</page>
<page>
---
title: Origin server · Cloudflare SSL/TLS docs
description: "Learn more about SSL/TLS protection options for your origin servers:"
lastUpdated: 2024-09-17T14:50:54.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ssl/origin-configuration/
md: https://developers.cloudflare.com/ssl/origin-configuration/index.md
---
Learn more about SSL/TLS protection options for your origin servers:
* [Encryption modes](https://developers.cloudflare.com/ssl/origin-configuration/ssl-modes/)
* [SSL/TLS Recommender](https://developers.cloudflare.com/ssl/origin-configuration/ssl-tls-recommender/)
* [Cloudflare origin CA](https://developers.cloudflare.com/ssl/origin-configuration/origin-ca/)
* [Authenticated Origin Pulls (mTLS)](https://developers.cloudflare.com/ssl/origin-configuration/authenticated-origin-pull/)
* [Custom Origin Trust Store](https://developers.cloudflare.com/ssl/origin-configuration/custom-origin-trust-store/)
* [Cipher suites](https://developers.cloudflare.com/ssl/origin-configuration/cipher-suites/)
</page>
<page>
---
title: Post-quantum cryptography (PQC) · Cloudflare SSL/TLS docs
description: Get an overview of how Cloudflare is deploying post-quantum
cryptography to protect you against harvest now, decrypt later.
lastUpdated: 2025-10-29T10:17:37.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/post-quantum-cryptography/
md: https://developers.cloudflare.com/ssl/post-quantum-cryptography/index.md
---
Post-quantum cryptography (PQC) refers to cryptographic algorithms that have been designed to resist attacks from [quantum computers](https://www.cloudflare.com/learning/ssl/quantum/what-is-quantum-computing/). Cloudflare has been researching and [writing about post-quantum](https://blog.cloudflare.com/tag/post-quantum/) since 2017.
To protect you against the risk of [harvest now, decrypt later attacks](https://en.wikipedia.org/wiki/Harvest_now,_decrypt_later), and considering all the [connections](#three-connections-in-the-life-of-a-request) that take place when your website or application is on Cloudflare, we have deployed and are actively expanding the use of [post-quantum hybrid key agreement](#hybrid-key-agreement).
Refer to [Cloudflare Radar](https://radar.cloudflare.com/adoption-and-usage#post-quantum-encryption-adoption) for current statistics on the adoption of PQ encryption in requests to Cloudflare, and visit [pq.cloudflareresearch.com](https://pq.cloudflareresearch.com) to check if your connection is secured using PQ key agreement.
TLS 1.3
Cloudflare post-quantum key agreements are only supported in protocols based on TLS 1.3 (including HTTP/3) and are disabled for websites in [FIPS mode](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/tls-decryption/#fips-compliance).
## Three building blocks of TLS
Before TLS can protect your communications, three cryptographic algorithms have to be agreed on during the [TLS handshake](https://www.cloudflare.com/learning/ssl/what-happens-in-a-tls-handshake/):
* **Symmetric ciphers:** Algorithms used to encrypt and decrypt data, ensuring confidentiality and integrity (such as `CHACHA20-POLY1305`).
* **Key agreement:** A cryptographic protocol that allows client and server to safely agree on a shared key (such as `ECDH`).
* **Signature algorithms:** Cryptographic algorithms used to generate the digital signatures in TLS certificates (such as `RSA` and `ECDSA`).
As explained in our [blog post](https://blog.cloudflare.com/pq-2025/#already-post-quantum-secure-symmetric-cryptography), symmetric ciphers are already post-quantum secure, which means there are two migrations left to occur.
### Hybrid key agreement
With TLS 1.3, [X25519](https://en.wikipedia.org/wiki/Curve25519) - an Elliptic Curve Diffie-Hellman (ECDH) protocol - is the most commonly used algorithm in key agreement. However, its security can be broken by quantum computers using [Shor's algorithm](https://en.wikipedia.org/wiki/Shor%27s_algorithm).
It is urgent to migrate key agreement to post-quantum algorithms as soon as possible. The objective is to protect against an adversary capable of harvesting today's encrypted communications and storing it until some time in the future when they can gain access to a sufficiently powerful quantum computer to decrypt it.
In response to this, Cloudflare is an early adopter of ML-KEM, the post-quantum key agreement selected by the US National Institute of Standards and Technology (NIST). For a detailed timeline and more background information refer to [State of the post-quantum Internet in 2025](https://blog.cloudflare.com/pq-2025/).
Cloudflare has deployed the following hybrid key agreements:
* [X25519MLKEM768](https://datatracker.ietf.org/doc/draft-kwiatkowski-tls-ecdhe-mlkem/) (Recommended)
* TLS identifier: `0x11ec`
* [X25519Kyber768Draft00](https://datatracker.ietf.org/doc/draft-tls-westerbaan-xyber768d00/) (Obsolete)
* TLS identifier: `0x6399`
A hybrid key agreement lays the groundwork as more and more [clients](#1-visitor-to-cloudflare) adopt post-quantum cryptography, while also maintaining the current security provided by X25519. It is a safer path in case of an unexpected breakthrough that renders all variants of ML-KEM insecure.
### Post-quantum signatures
The migration to post-quantum signatures is less urgent and more involved. Cloudflare is closely following the developments of new standards, testing their performance, and working together with browsers to understand user impact.
For details refer to [A look at the latest post-quantum signature standardization candidates](https://blog.cloudflare.com/another-look-at-pq-signatures/).
## Three connections in the life of a request
```mermaid
flowchart LR
accTitle: Three connections - from visitor to Cloudflare to origin server
accDescr: Diagram showing connections for an uncached request.
A[Visitor]
subgraph Cloudflare
X[(Cloudflare <br />service A)]
B[(Cloudflare <br />service B)]
end
C[(Origin server)]
A --1--> X
X --2--> B
B --3--> C
```
### 1. Visitor to Cloudflare
As of [October 2022](https://blog.cloudflare.com/post-quantum-for-all/), all websites and APIs served through Cloudflare over TLS 1.3 support post-quantum hybrid key agreement. However, the connection is only post-quantum secured if the client also supports PQC.
Refer to [Post-quantum cryptography support](https://developers.cloudflare.com/ssl/post-quantum-cryptography/pqc-support/) for a list of browsers and other clients that are compatible with hybrid key agreements.
### 2. Internal connections
As announced in [September 2023](https://blog.cloudflare.com/post-quantum-cryptography-ga/), most internal connections for Cloudflare's products and systems have been upgraded to use PQC.
### 3. Cloudflare to your origin
Finally, Cloudflare also supports [hybrid key agreements](#hybrid-key-agreement) when connecting to origins. In this case, post-quantum secured connections will depend on the origin servers also supporting PQC. Customers can also configure connections to origin servers via [PQ Cloudflare Tunnel](https://developers.cloudflare.com/ssl/post-quantum-cryptography/pqc-and-zero-trust/).
Refer to [Post-quantum cryptography between Cloudflare and origin servers](https://developers.cloudflare.com/ssl/post-quantum-cryptography/pqc-to-origin/) for details.
## Protect corporate network traffic
With [Zero Trust](https://developers.cloudflare.com/cloudflare-one/), Cloudflare allows organizations to upgrade their sensitive network traffic to PQC without the hassle of individually upgrading each and every corporate application, system, or network connection. Refer to [Post-quantum cryptography in Cloudflare's Zero Trust platform](https://developers.cloudflare.com/ssl/post-quantum-cryptography/pqc-and-zero-trust/) for details.
</page>
<page>
---
title: Reference · Cloudflare SSL/TLS docs
description: "For more on Cloudflare SSL/TLS, refer to these articles:"
lastUpdated: 2024-09-17T14:50:54.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/ssl/reference/
md: https://developers.cloudflare.com/ssl/reference/index.md
---
For more on Cloudflare SSL/TLS, refer to these articles:
* [TLS protocols](https://developers.cloudflare.com/ssl/reference/protocols/)
* [Certificate and hostname priority](https://developers.cloudflare.com/ssl/reference/certificate-and-hostname-priority/)
* [Certificate authorities](https://developers.cloudflare.com/ssl/reference/certificate-authorities/)
* [Browser compatibility](https://developers.cloudflare.com/ssl/reference/browser-compatibility/)
* [Migration guides](https://developers.cloudflare.com/ssl/reference/migration-guides/)
* [Certificate pinning](https://developers.cloudflare.com/ssl/reference/certificate-pinning/)
* [Certificate statuses](https://developers.cloudflare.com/ssl/reference/certificate-statuses/)
* [Validity periods and renewal](https://developers.cloudflare.com/ssl/reference/certificate-validity-periods/)
* [Features and plans](https://developers.cloudflare.com/ssl/reference/all-features/)
* [Cloudflare and CVE-2019-1559](https://developers.cloudflare.com/ssl/reference/cloudflare-and-cve-2019-1559/)
* [PCI compliance and vulnerabilities mitigation](https://developers.cloudflare.com/ssl/reference/compliance-and-vulnerabilities/)
</page>
<page>
---
title: Cloudflare for SaaS · Cloudflare SSL/TLS docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/saas/
md: https://developers.cloudflare.com/ssl/saas/index.md
---
</page>
<page>
---
title: Troubleshooting · Cloudflare SSL/TLS docs
description: "For FAQs and other troubleshooting information, refer to the
following resources:"
lastUpdated: 2025-08-12T17:54:27.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/ssl/troubleshooting/
md: https://developers.cloudflare.com/ssl/troubleshooting/index.md
---
For FAQs and other troubleshooting information, refer to the following resources:
Filter resources...
[Troubleshooting client certificates](https://developers.cloudflare.com/ssl/client-certificates/troubleshooting/)
[Troubleshooting Keyless SSL](https://developers.cloudflare.com/ssl/keyless-ssl/troubleshooting/)
[General FAQ](https://developers.cloudflare.com/ssl/troubleshooting/faq/)
[General SSL errors](https://developers.cloudflare.com/ssl/troubleshooting/general-ssl-errors/)
[Mixed content errors](https://developers.cloudflare.com/ssl/troubleshooting/mixed-content-errors/)
[Fix VERSION\_OR\_CIPHER\_MISMATCH](https://developers.cloudflare.com/ssl/troubleshooting/version-cipher-mismatch/)
[ERR\_TOO\_MANY\_REDIRECTS](https://developers.cloudflare.com/ssl/troubleshooting/too-many-redirects/)
[Cloudflare and CVE-2019-1559](https://developers.cloudflare.com/ssl/reference/cloudflare-and-cve-2019-1559/)
[Troubleshooting Domain Control Validation](https://developers.cloudflare.com/ssl/edge-certificates/changing-dcv-method/troubleshooting/)
[Troubleshooting | Custom certificates](https://developers.cloudflare.com/ssl/edge-certificates/custom-certificates/troubleshooting/)
[CAs and edge certificates FAQ](https://developers.cloudflare.com/ssl/edge-certificates/troubleshooting/ca-faq/)
[Certification Authority Authorization (CAA) FAQ](https://developers.cloudflare.com/ssl/edge-certificates/troubleshooting/caa-records/)
[Troubleshooting Universal SSL](https://developers.cloudflare.com/ssl/edge-certificates/universal-ssl/troubleshooting/)
[Troubleshooting Cloudflare origin CA](https://developers.cloudflare.com/ssl/origin-configuration/origin-ca/troubleshooting/)
[Troubleshooting - Cipher suites — Edge certificates](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/cipher-suites/troubleshooting/)
[Total TLS error messages](https://developers.cloudflare.com/ssl/edge-certificates/additional-options/total-tls/error-messages/)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Style Guide
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/404/
md: https://developers.cloudflare.com/style-guide/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: AI Tooling · Cloudflare Style Guide
description: Use the following AI tools to get the most out of Cloudflare (and our docs).
lastUpdated: 2026-02-06T14:40:34.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/ai-tooling/
md: https://developers.cloudflare.com/style-guide/ai-tooling/index.md
---
Use the following AI tools to get the most out of Cloudflare (and our docs).
## llms.txt
We have implemented `llms.txt`, `llms-full.txt` and also created per-page Markdown links as follows:
* [`llms.txt`](https://developers.cloudflare.com/llms.txt)
* [`llms-full.txt`](https://developers.cloudflare.com/llms-full.txt)
* We also provide a `llms-full.txt` file on a per-product basis, i.e [`/workers/llms-full.txt`](https://developers.cloudflare.com/workers/llms-full.txt)
* [`/$page/index.md`](index.md)
* Add `/index.md` to the end of any page to get the Markdown version, i.e [`/style-guide/index.md`](https://developers.cloudflare.com/style-guide/index.md)
In the top right of this page, you will see a `Page options` button where you can copy the current page as Markdown that can be given to your LLM of choice.

## MCP
Cloudflare runs a catalog of managed remote MCP Servers which you can connect to using OAuth on clients like [Claude](https://modelcontextprotocol.io/quickstart/user), [Windsurf](https://docs.windsurf.com/windsurf/cascade/mcp), our own [AI Playground](https://playground.ai.cloudflare.com/) or any [SDK that supports MCP](https://github.com/cloudflare/agents/tree/main/packages/agents/src/mcp).
* Cursor
To install in Cursor, use this [Direct install link](https://cursor.com/en-US/install-mcp?name=cloudflare\&config=eyJjb21tYW5kIjoibnB4IG1jcC1yZW1vdGUgaHR0cHM6Ly9kb2NzLm1jcC5jbG91ZGZsYXJlLmNvbS9zc2UifQ%3D%3D).
* VSCode
To install in VSCode, use this [Direct install link](vscode:mcp/install?%7B%22name%22%3A%22cloudflare%22%2C%22url%22%3A%22https%3A%2F%2Fdocs.mcp.cloudflare.com%2Fmcp%22%7D).
* Manually
To install manually, add the following specification to your MCP config:
```json
{
"mcpServers": {
"cloudflare": {
"command": "npx",
"args": ["mcp-remote", "https://docs.mcp.cloudflare.com/mcp"]
}
}
}
```
Note
For other MCP servers offered by Cloudflare, refer to [Cloudflare's MCP servers](https://developers.cloudflare.com/agents/model-context-protocol/mcp-servers-for-cloudflare/).
## Skills
Our docs site also supports [agent skills](https://agentskills.io/home) that are defined in the [Cloudflare Skills repo](https://github.com/cloudflare/skills).
To install them:
```sh
$ npx skills add https://developers.cloudflare.com
```
</page>
<page>
---
title: API docs content strategy · Cloudflare Style Guide
description: "The API docs content strategy aims to:"
lastUpdated: 2025-07-15T13:59:35.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/api-content-strategy/
md: https://developers.cloudflare.com/style-guide/api-content-strategy/index.md
---
The API docs content strategy aims to:
* Reduce internal and external user frustration
* Align with industry standards in terms of naming conventions and descriptions
* Create world-class content that is just as good, or better, than very popular API documentation
By ensuring Cloudflare's API content is straightforward, easy to navigate, and consistent, we can create world-class API content that eliminates user frustration and serves as an example of good API documentation.
* [API content types](https://developers.cloudflare.com/style-guide/api-content-strategy/api-content-types/)
* [Guidelines for cURL commands](https://developers.cloudflare.com/style-guide/api-content-strategy/guidelines-for-curl-commands/)
* [Method types & common verbs](https://developers.cloudflare.com/style-guide/api-content-strategy/method-types-and-command-verbs/)
</page>
<page>
---
title: Contributions · Cloudflare Style Guide
description: The Cloudflare Docs are open source and hosted on the
cloudflare-docs repository on GitHub. This means that anyone, including those
who are not part of the Cloudflare organization, can contribute to them. We
welcome all suggestions that help keep our docs high quality and up to date.
lastUpdated: 2025-10-28T15:24:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/contributions/
md: https://developers.cloudflare.com/style-guide/contributions/index.md
---
The [Cloudflare Docs](https://developers.cloudflare.com/) are open source and hosted on the [cloudflare-docs repository](https://github.com/cloudflare/cloudflare-docs) on GitHub. This means that anyone, including those who are not part of the Cloudflare organization, can contribute to them. We welcome all suggestions that help keep our docs high quality and up to date.
To contribute to our docs, you will need to [create an account on GitHub](https://docs.github.com/en/get-started/start-your-journey/creating-an-account-on-github) (if you do not have one already) and log in. Then you have three options:
* [GitHub issue](#create-a-github-issue): Quickly submit a general suggestion.
* [Quick edit (edit button)](#quick-edit): Quickly create a pull request. This is best if you want to edit a single page in your web browser and do not need to preview your changes.
* [Full development](#full-development): Create a pull request. This is best if you want to edit multiple pages and preview your changes. This can be done in your web browser (with [Codespaces](https://docs.github.com/codespaces)) or on your local machine (with [Visual Studio Code](https://code.visualstudio.com/)).
In addition to using the [Cloudflare Style Guide](https://developers.cloudflare.com/style-guide/) for guidance on grammar and style, we recommend browsing our [components](https://developers.cloudflare.com/style-guide/components/) to add additional formatting such as buttons, tabs, and collapsible sections.
## Create a GitHub issue
To create a GitHub issue:
1. [Log in to GitHub](https://github.com/login) and go to the [cloudflare-docs repository](https://github.com/cloudflare/cloudflare-docs).
2. Select **Issues** and then **New issue**.
3. Select the issue type, fill out the form, and select **Create**.
[Learn more about creating GitHub issues.](https://docs.github.com/en/issues/tracking-your-work-with-issues/using-issues/creating-an-issue)
## Quick edit
To quickly create a pull request using the edit button:
1. [Log in to GitHub](https://github.com/login).
2. Go to the page you want to edit in the [Cloudflare Docs](https://developers.cloudflare.com/)
3. Select
**Edit** or **Edit page**
Every page in the Cloudflare Docs (including this one) has an **Edit** button on the right sidebar and an **Edit page** button on the very bottom of the page.  The page's Markdown opens.
Note
The first time you create a pull request in the cloudflare-docs repo, you will see a GitHub landing page that says "You need to fork this repository to propose changes." Select **Fork this repository**. All of your future pull requests for cloudflare-docs will write to a new branch on your fork.
4. Make your edits and select **Commit changes**.
5. In the form, update the **Commit message** with the product you changed in brackets and a brief description of your changes. For example “\[Images] Fixed broken link."
6. Update the **Extended description** with more details about what you changed and why. The more details, the better.
7. Select **Propose changes** > **Create pull request** > **Create pull request** again.
## Full development
To edit and create a pull request with the [full development workflow](https://docs.github.com/en/codespaces/developing-in-a-codespace/using-source-control-in-your-codespace):
1. [Log in to GitHub](https://github.com/login) and [fork the cloudflare-docs repository](https://docs.github.com/en/pull-requests/collaborating-with-pull-requests/working-with-forks/fork-a-repo).
2. If you are editing in your web browser (with [Codespaces](https://docs.github.com/en/codespaces)), move on to step 3.\
If you are editing on your local machine (with [Visual Studio Code](https://code.visualstudio.com/)):
* (Required) Install [Node.js](https://nodejs.org/en) (version 22 or later).
* (Recommended, but not required) Install [Volta](https://volta.sh/) for easier package management.
* (Required) [Clone the fork to your local machine.](https://docs.github.com/en/repositories/creating-and-managing-repositories/cloning-a-repository)
3. Create a branch from your fork (or from your clone).
4. Make your edits.
Preview your edits
To preview your edits, you need to install `npm`.
```bash
npm install
```
Then, run `npm run dev`.
```bash
npm run dev
```
A link will appear in the terminal, `https://localhost:1111/`, where you can preview your edits. This link automatically updates with any new edits you make.
1. Commit your changes.
2. Push your commits to your branch and then back to your fork.
3. Return to GitHub and create a pull request from your committed changes. In the description form, add the product you changed in brackets and a brief description of your changes. For example “\[Images] Fixed broken link."
## After you create an issue or PR
After you create an issue or PR, a member of the Cloudflare organization will review your suggestion. Here is what to expect:
* A member of the Cloudflare organization may tag others for technical or content reviews or feedback.
* If your suggestion requires more information, a member of the Cloudflare organization may comment with a follow-up or clarification question. If they add the `more-information-needed` tag, the issue or pull request will automatically close if you do not respond within 14 days.
* If your changes are approved:
* For GitHub issues, a Cloudflare member might create and link a new pull request that addresses your request. When they merge the PR, they will also close your issue.
* For GitHub PRs, the Cloudflare member will merge your PR.
* If your suggestion is not approved, the Cloudflare member will respond with the reasoning and close your issue or PR.
Thank you for contributing to our open-source ecosystem and being a part of the Cloudflare community.
</page>
<page>
---
title: Components · Cloudflare Style Guide
description: When you are contributing to the Cloudflare Docs, you can use our
custom components to add additional formatting, such as buttons, tabs, and
collapsible sections.
lastUpdated: 2025-11-18T13:57:55.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/components/
md: https://developers.cloudflare.com/style-guide/components/index.md
---
When you are [contributing to the Cloudflare Docs](https://developers.cloudflare.com/style-guide/contributions/), you can use our custom components to add additional formatting, such as buttons, tabs, and collapsible sections.
This guide shows you the basics of importing and adding a component to a page. Refer to each component page in this Style Guide to learn the specific props and requirements for each.
Our components are based on [Astro components](https://docs.astro.build/en/basics/astro-components/) and are written in [MDX](https://docs.astro.build/en/guides/markdown-content/), an extended version of Markdown. [Learn more about the Cloudflare Docs framework](https://developers.cloudflare.com/style-guide/how-we-docs/our-site/#site-framework).
## Add a component to a page
To add a component to a page:
1. Import the component to the page by adding this text directly below the [frontmatter](https://developers.cloudflare.com/style-guide/frontmatter/):
```mdx
import { COMPONENT_NAME } from "~/components";
;
```
For example, if you were to add [the `DashButton` component](https://developers.cloudflare.com/style-guide/components/dash-button/) to the [Images getting started page](https://developers.cloudflare.com/images/get-started/), the top of the MDX file corresponding to that page would look like the following:
```mdx
---
pcx_content_type: get-started
title: Getting started
sidebar:
order: 2
---
import { DashButton } from "~/components";
;
```
2. Add the component to the page by adding this text anywhere on the page you want the component to appear:
```mdx
<COMPONENT_NAME PROP_NAME="PROP_VALUE" />
```
For example, if you were to add the `DashButton` component to some steps in the [Images getting started page](https://developers.cloudflare.com/images/get-started/), here is how the MDX file would look:
```mdx
1. In the Cloudflare dashboard, go to the **Transformations** page.
<DashButton url="/?to=/:account/images/transformations" />
2. Go to the specific zone where you want to enable transformations.
```
This is how this example would display after it is published:
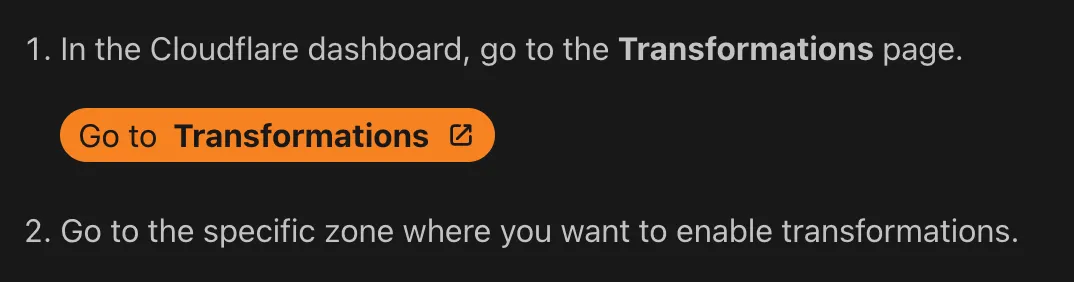
## Choose the right component
To choose the right component for your use case, browse this table which contains our most commonly used components and a visual example of each. For full documentation on all available components and their use cases, browse the individual component pages in this Style Guide.
| Component | Description & visual example |
| - | - |
| [`APIRequest`](https://developers.cloudflare.com/style-guide/components/api-request/) | Styled API request block. Generate executable cURL API commands with the required API token permissions.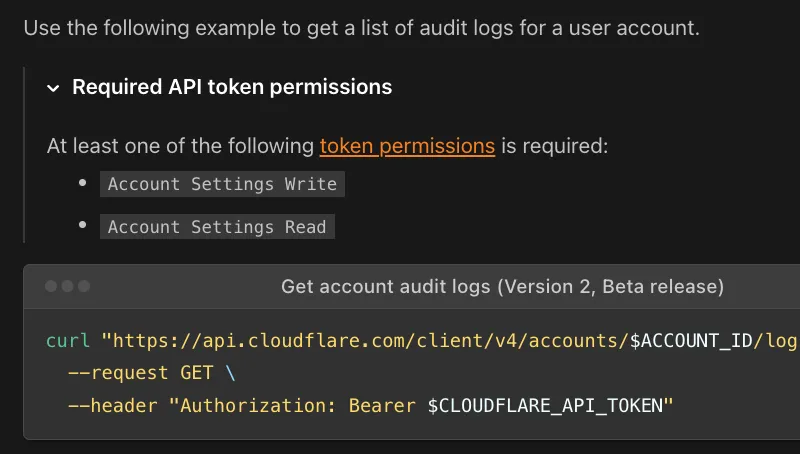 |
| [`Badge`](https://developers.cloudflare.com/style-guide/components/badges/) | Small descriptive pill. Label content with status, version, category, or other short metadata. |
| [`DashButton`](https://developers.cloudflare.com/style-guide/components/dash-button/) | Dashboard deep-link button. Directly link users from documentation into a specific, relevant section of the Cloudflare Dashboard.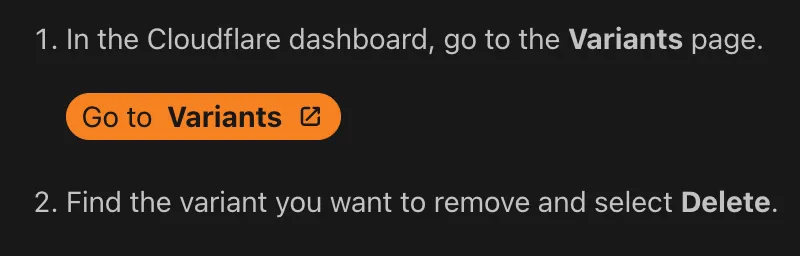 |
| [`Details`](https://developers.cloudflare.com/style-guide/components/details/) | Click-to-expand content block. Hide non-essential, complex, or advanced technical content, allowing users to expand the section when needed.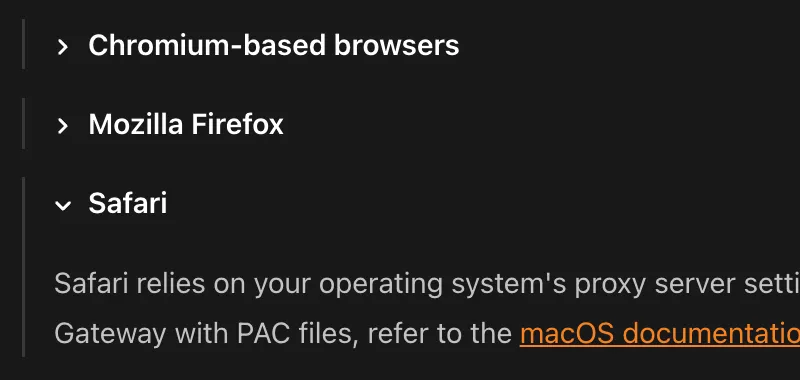 |
| [`DirectoryListing`](https://developers.cloudflare.com/style-guide/components/directory-listing) | Auto-generated sub-page list. Automatically generate a navigable list of links to sub-pages within a specified documentation folder path. |
| [`Feature`](https://developers.cloudflare.com/style-guide/components/feature/) | Product feature list item. Highlight a product feature with a description and a direct link button. |
| [`FeatureTable`](https://developers.cloudflare.com/style-guide/components/feature-table/) | Product plan comparison table. Display detailed feature information, including availability across different Cloudflare pricing plans.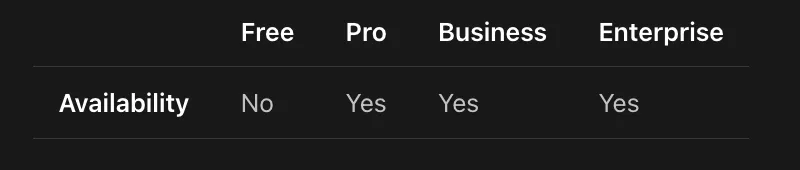 |
| [`GlossaryTooltip`](https://developers.cloudflare.com/style-guide/components/glossary-tooltip/) | Hover-activated glossary popup. Provide non-disruptive, hover-activated definitions for technical terms pulled from the documentation glossary.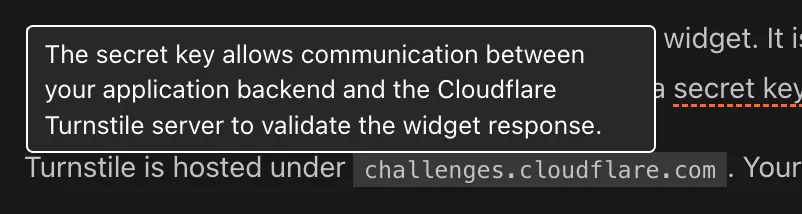 |
| [`LinkCard`](https://developers.cloudflare.com/style-guide/components/link-cards/) | Navigational cards. Present related tutorials, concepts, or guides in a visually engaging format. |
| [`PackageManagers`](https://developers.cloudflare.com/style-guide/components/package-managers) | Command switcher tabs. Display equivalent installation or execution commands for different package managers. |
| [`Plan`](https://developers.cloudflare.com/style-guide/components/plan/) | Product plan availability badge. Show the plan required for a product or specific feature. |
| [`RelatedProduct`](https://developers.cloudflare.com/style-guide/components/related-product/) | Formatted product reference. Visually highlight and link to a specific, complementary Cloudflare product, also featuring the product's logo. |
| [`ResourcesBySelector`](https://developers.cloudflare.com/style-guide/components/resources-by-selector/) | Filterable code example library. Pull and display lists of code examples and resources based on tags and content type. |
| [`Stream`](https://developers.cloudflare.com/style-guide/components/stream/) | Embeddable video player. Display a video player optimized for Cloudflare Stream. |
| [`Tabs` and `TabItem`](https://developers.cloudflare.com/style-guide/components/tabs/) | Switchable content tabs. Allow easy switching between content views for different code languages or configuration methods. |
| [`Type` and `MetaInfo`](https://developers.cloudflare.com/style-guide/components/type-highlighting/) | Pill-shaped data type badge and metadata annotation about a field or property. `Type` indicates API parameter data types (`String`, `Integer`) and `MetaInfo` indicates metadata constraints (`Required`, `Optional`, `Read-only`).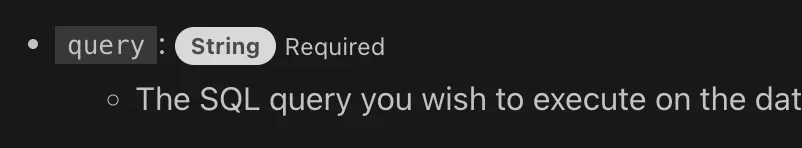 |
| [`WranglerConfig`](https://developers.cloudflare.com/style-guide/components/wrangler-config/) | Tabbed Wrangler config display. Show Wrangler configuration files (JSONC and TOML) and bindings with automatic format switching. |
| [`YouTube`](https://developers.cloudflare.com/style-guide/components/youtube/) | Embeddable video player. Embeds a YouTube video player with a specified video ID. |
</page>
<page>
---
title: Product docs content strategy · Cloudflare Style Guide
description: "The purpose of Cloudflare's developer documentation content strategy is to:"
lastUpdated: 2025-07-15T13:59:35.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/documentation-content-strategy/
md: https://developers.cloudflare.com/style-guide/documentation-content-strategy/index.md
---
The purpose of Cloudflare's developer documentation content strategy is to:
* Create and document standard templates to streamline content creation
* Document specific content types to help identify customers' specific needs
* Enable life cycle management to maintain and optimize a smaller set of pages
* Suggest easier navigation paths
Strategically speaking, the mission and guiding principles translate into the following initiatives:
* Improve the entire ecosystem of customer-facing product content, placing major emphasis on consistency, quality, accuracy, and timeliness
* Create a cohesive and compelling story around our products and their functionality
* Develop content that increases product adoption, deflects support, and makes customers successful
* Partner with various internal departments and stakeholders in creating and sustaining a rich, consistent content experience across all Cloudflare products
* Devise new and better ways to give users the information they need, when and where they need it
Adoption of this content strategy will be impacted by product releases, resourcing, and company goals.
## Purpose statements
For each purpose statement, the documentation team will define the approach to solve the content problem for a product.
This approach includes:
### Information architecture
* Where content should live on the site
* Linking strategy
### Content
* What content is included and what is optional
* How the content is written
## Content requirements
Content requirements help the contributor ensure they have answered the user question and have not lost the purpose of the content after moving into execution.
* [Content types](https://developers.cloudflare.com/style-guide/documentation-content-strategy/content-types/)
* [Component attributes](https://developers.cloudflare.com/style-guide/documentation-content-strategy/component-attributes/)
* [Information architecture](https://developers.cloudflare.com/style-guide/documentation-content-strategy/information-architecture/)
* [Writing guidelines](https://developers.cloudflare.com/style-guide/documentation-content-strategy/writing-guidelines/)
* [Accessibility guidelines](https://developers.cloudflare.com/style-guide/documentation-content-strategy/accessibility/)
* [File conventions](https://developers.cloudflare.com/style-guide/documentation-content-strategy/file-conventions/)
</page>
<page>
---
title: Fixtures · Cloudflare Style Guide
description: This folder stores test fixtures to be used in CI.
lastUpdated: 2025-03-31T14:01:11.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/fixtures/
md: https://developers.cloudflare.com/style-guide/fixtures/index.md
---
This folder stores test fixtures to be used in CI.
</page>
<page>
---
title: Formatting · Cloudflare Style Guide
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/formatting/
md: https://developers.cloudflare.com/style-guide/formatting/index.md
---
* [Code block guidelines](https://developers.cloudflare.com/style-guide/formatting/code-block-guidelines/)
* [Code conventions and format](https://developers.cloudflare.com/style-guide/formatting/code-conventions-and-format/)
* [Dates and times](https://developers.cloudflare.com/style-guide/formatting/dates-and-times/)
* [Example values](https://developers.cloudflare.com/style-guide/formatting/example-values/)
* [External references](https://developers.cloudflare.com/style-guide/formatting/external-references/)
* [File types and extensions](https://developers.cloudflare.com/style-guide/formatting/file-types-and-extensions/)
* [Footnotes](https://developers.cloudflare.com/style-guide/formatting/footnotes/)
* [Keyboard keys](https://developers.cloudflare.com/style-guide/formatting/keyboard-keys/)
* [Notes and other notation types](https://developers.cloudflare.com/style-guide/formatting/notes-and-other-notation-types/)
* [Numbers and units of measurement](https://developers.cloudflare.com/style-guide/formatting/numbers-and-units-of-measurement/)
* [Product name and pluralization](https://developers.cloudflare.com/style-guide/formatting/product-name-and-pluralization/)
* [UI elements](https://developers.cloudflare.com/style-guide/formatting/ui-elements/)
* [URLs and domain names](https://developers.cloudflare.com/style-guide/formatting/urls-and-domain-names/)
* [Structure](https://developers.cloudflare.com/style-guide/formatting/structure/)
</page>
<page>
---
title: Frontmatter · Cloudflare Style Guide
description: >
You can customize individual Markdown and MDX pages in Starlight by setting
values in their frontmatter.
For example, a regular page might set title and description fields.
lastUpdated: 2024-10-14T11:03:17.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/frontmatter/
md: https://developers.cloudflare.com/style-guide/frontmatter/index.md
---
Frontmatter contains the metadata for a page, such as the `title`. It is written as YAML, between `---`, at the top of the page.
For example, this is the frontmatter for the page you're on now!
```mdx
---
title: Frontmatter
description: |
You can customize individual Markdown and MDX pages in Starlight by setting values in their frontmatter.
For example, a regular page might set title and description fields.
sidebar:
order: 3
---
```
For more information on the available fields, please refer to [Starlight's documentation](https://starlight.astro.build/reference/frontmatter/).
</page>
<page>
---
title: Grammar · Cloudflare Style Guide
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/grammar/
md: https://developers.cloudflare.com/style-guide/grammar/index.md
---
* [Parts of speech](https://developers.cloudflare.com/style-guide/grammar/parts-of-speech/)
* [Punctuation marks and symbols](https://developers.cloudflare.com/style-guide/grammar/punctuation-marks-and-symbols/)
</page>
<page>
---
title: How we docs · Cloudflare Style Guide
description: This section shares how Cloudflare approaches docs strategically,
covering topics like how we built our site and how we think about redirects.
lastUpdated: 2025-07-15T13:59:35.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/style-guide/how-we-docs/
md: https://developers.cloudflare.com/style-guide/how-we-docs/index.md
---
This section shares how Cloudflare approaches docs strategically, covering topics like `how we built our site` and `how we think about redirects`.
The goal is twofold because it:
* Encourages deep thinking about how we approach things (and if they could be better).
* Contributes back to the open-source ecosystem. We get a lot of benefits from being open source and we want to give back.
We hope you learn from the topics below. As always, [submit an issue](https://github.com/cloudflare/cloudflare-docs/issues/new) if you find something inaccurate or unclear.
* [AI consumability](https://developers.cloudflare.com/style-guide/how-we-docs/ai-consumability/)
* [Content reviews](https://developers.cloudflare.com/style-guide/how-we-docs/reviews/)
* [Image maintenance](https://developers.cloudflare.com/style-guide/how-we-docs/image-maintenance/)
* [Links](https://developers.cloudflare.com/style-guide/how-we-docs/links/)
* [Metadata](https://developers.cloudflare.com/style-guide/how-we-docs/metadata/)
* [Our site](https://developers.cloudflare.com/style-guide/how-we-docs/our-site/)
* [Redirects](https://developers.cloudflare.com/style-guide/how-we-docs/redirects/)
* [How we AI](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-ai/)
* [How we video](https://developers.cloudflare.com/style-guide/how-we-docs/how-we-video/)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Support docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/404/
md: https://developers.cloudflare.com/support/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Cloudflare Status · Cloudflare Support docs
description: Cloudflare provides updates on the status of our services and
network at https://www.cloudflarestatus.com/, which you should check if you
notice unexpected behavior with Cloudflare.
lastUpdated: 2025-06-11T12:06:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/cloudflare-status/
md: https://developers.cloudflare.com/support/cloudflare-status/index.md
---
Cloudflare provides updates on the status of our services and network at <https://www.cloudflarestatus.com/>, which you should check if you notice unexpected behavior with Cloudflare.
Beyond looking at the page itself, there are programmatic ways to consume this information.
## Configure notifications
Cloudflare offers a dedicated notification called **Incident Alert**, which lets you know when Cloudflare is experiencing an incident.
You can configure this notification to send via [email](https://developers.cloudflare.com/notifications/get-started/), [Webhooks](https://developers.cloudflare.com/notifications/get-started/configure-webhooks/), or [PagerDuty](https://developers.cloudflare.com/notifications/get-started/configure-pagerduty/).
## Use the API
Cloudflare also provides status information through the [Cloudflare Status API](https://www.cloudflarestatus.com/api).
Endpoints are displayed with examples using cURL and our embeded JavaScript widget (if available).
## Related resources
* [Available RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/) (for the [Cloudflare changelog](https://developers.cloudflare.com/changelog/))
* [API deprecations](https://developers.cloudflare.com/fundamentals/api/reference/deprecations/)
* [Planned maintenance windows](https://developers.cloudflare.com/support/disruptive-maintenance/)
</page>
<page>
---
title: Contacting Cloudflare Support · Cloudflare Support docs
description: Learn how to contact Cloudflare Support via community, chat, or
phone. Get help with issues, verify identity, and understand SLAs for
different plans.
lastUpdated: 2025-12-15T10:06:24.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/contacting-cloudflare-support/
md: https://developers.cloudflare.com/support/contacting-cloudflare-support/index.md
---
## Guidelines for contacting Cloudflare support
Cloudflare Support *cannot* perform the following actions:
* Make configuration or account changes on a customer’s behalf
* Provide sensitive account info over the phone
* Troubleshoot or debug customer's code and its logic
* Troubleshoot or answer questions about domains not associated with the Cloudflare account email address used to contact support
Warning
**Do not share** any sensitive information, such as passwords, credit card numbers, private keys, or API keys with Cloudflare.
Before notifying Cloudflare of an issue with your site, refer to the [Cloudflare Status Page](https://www.cloudflarestatus.com/). If reporting issues with your site, ensure to provide adequate details in the support case *(refer to [Getting help with an issue](#getting-help-with-an-issue) for more information)*.
***
## Methods of contacting Cloudflare support
As a Cloudflare customer, you can contact Cloudflare for support via the community portal or by opening a support case, live chat, or phone. Support options can vary depending on your plan.
| | Enterprise | Business | Pro | Free |
| - | - | - | - | - |
| [Community](https://community.cloudflare.com/) Join the community to ask basic troubleshooting questions and to view the latest resources (such as tips for resolving common issues and configuration guidance). | Yes | Yes | Recommended | Recommended |
| [Discord](https://discord.cloudflare.com/) Join the Discord community to ask basic troubleshooting questions (mainly focused on the Developer Platform). | Yes | Yes | Recommended | Recommended |
| [Support case](#getting-help-with-an-issue) Use to troubleshoot specific issues or errors. Response times depend on your plan. | Yes | Yes | Yes | No\* |
| **Chat** Use to troubleshoot specific issues or errors. Response times depend on your plan. | Yes | Yes | No | No |
| **Emergency Phone** Use phone support to reach out during emergencies such as site outages or DDoS attacks. | Yes | No | No | No |
***
Note
Customers on Free plans are encouraged to utilize our Cloudflare Community and will only receive standard case support for billing, account, and registrar issues.
## Verifying your identity on phone calls
*(For Enterprise Emergency Phone Support)*
For account security, you must verify your identity and account ownership in the Cloudflare dashboard before discussing account settings and sensitive details with Cloudflare Support. There are two verification options:
* a single-use token that automatically refreshes every thirty (30) seconds, or
* an [authenticator app token](https://developers.cloudflare.com/fundamentals/user-profiles/2fa/#configure-totp-mobile-application-authentication) on your mobile device.
### Authenticating your account
1. In the Cloudflare dashboard, go to the **Support** page and select the account you are calling about.
[Go to Support](https://dash.cloudflare.com/?to=/:account/support)
1. Click on the **Technical Support** tile and then the **Emergency Phone Line** tile.
2. To authenticate using a single-use token, click on the **Get a single-use token** button. A pop-up window will appear with your Unique Customer Id and One Time Passcode. The code automatically refreshes every 30 seconds.

1. To authenticate using an authenticator app, click **Configure authenticator app** and follow the [configuration instructions](https://developers.cloudflare.com/fundamentals/user-profiles/2fa/#configure-totp-mobile-application-authentication) on the following screen. After configuration, the token code will appear in your mobile authentication application.
2. When calling the emergency phone line, you can authenticate automatically by entering your ID and Code when requested.
***
## Getting help with an issue
To submit a support case, follow these steps:
1. In the Cloudflare dashboard, go to the **Support** page and select the account you require assistance for.
[Go to Support](https://dash.cloudflare.com/?to=/:account/support)
1. Click on the **Technical Support** tile, or for billing issues click **Billing** and then click **Create a Case** at the bottom of the following screen.
2. Choose the category and subcategories that best define your issue.
3. Choose the affected domains (if applicable).
4. Enter a detailed summary of the issue you’re experiencing.
5. Complete the case submission fields as completely as possible with the following information. *(**Please note** that missing information will increase the time it takes to resolve your issue and our team may not be able to investigate without enough information. Please review [Gathering information for troubleshooting sites](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/gathering-information-for-troubleshooting-sites/) and make sure you include all needed information.)* - A detailed description of the issue with the following information:
* Timestamp (UTC)
* ZoneName/ZoneID
* Problem frequency
* Steps to reproduce the issue, with actual results vs expected results - Any necessary information for a technical investigation
* A description of the actual results vs expected results
* Steps to reproduce the issue, with example URLs
* Exact error messages
* [HAR files](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/gathering-information-for-troubleshooting-sites/#generate-a-har-file)
* Screenshots
* Relevant logs from the origin web server
* Output from [test tools](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/gathering-information-for-troubleshooting-sites/) such as MTR, traceroute, dig/nslookup, and cURL - Priority level, impact to service / production - Any collaborators whom you wish to be cc'd on the case
6. Click **Submit Case**
\*\* Available to certain plan types only. Refer to chart above for details.
### Accepted file formats in cases and chats
You can only upload the following file types in a case or a chat:
*Image*
* png, jpg, gif, ico, tiff
*Video*
* mp4, avi, webm
*Text*
* har, txt, csv, eml, css, html, json, tf
*Packet Capture*
* pcap, pcapng, cap
Cloudflare Support only accepts the WARP diagnostics as compressed files. Please do not upload ZIP or RAR files when sharing [HAR files](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/gathering-information-for-troubleshooting-sites/#generate-a-har-file), and please do not share compressed documents like DOCX, XLSX, or PPTX.
The maximum file size is **20 MB**. If you need to share a larger file, please provide a link to the file using Google Drive or a similar sharing platform of your choice.
When sending Cloudflare Support packet captures, please do the following:
1. Filter for relevant traffic. Use a display filter and then save [export specified packets](https://www.wireshark.org/docs/wsug_html_chunked/ChIOExportSection.html) to reduce the file size.
2. Include the name of the device and interface/tunnel in the file name.
3. Describe what each packet capture shows.
### View open support cases
1. In the Cloudflare dashboard, go to the **Support** page.
[Go to Support](https://dash.cloudflare.com/?to=/:account/support)
1. Click on **Get help**
2. Select the account you require assistance for
3. Click on the **Technical Support** tile followed by **View My Cases**.
4. You will be redirected to the portal where you can see your own cases and cases you are CC'd on.
### Add participants to open support tickets
1. In the Cloudflare dashboard, go to the **Support** page and select the account you require assistance for.
[Go to Support](https://dash.cloudflare.com/?to=/:account/support)
1. Click on the **Technical Support** tile followed by **View My Cases**.
2. You will be redirected to the portal where you can see your own cases and cases you are CC'd on.
3. Select the case you want to add participants to.
4. Enter their email in the `Case Participants` box in the top right and click **Add**.
***
## Live chat support
You can also use the **live chat** (Business and Enterprise plans, only) to ask specific questions that don’t require a lot of technical investigation:
1. Log in to your **Cloudflare dashboard** and select the **account** you need assistance with.
2. Access the **Live Chat** based on your plan type:
* **Enterprise Customers**: Click the **Chat icon** in the bottom right corner of the screen to open the Cloudflare Chat widget immediately.
* **Business Plan Customers**:
* In the Cloudflare dashboard, go to the **Support** page and select the account you require assistance for. [Go to Support](https://dash.cloudflare.com/?to=/:account/support)
* Click on the **Technical Support** tile followed by **Chat with an agent**.
* Fill-out the required form to start a Chat session.
The Cloudflare Chat widget will open, send an initial message describing your problem to start chatting with an agent.
***
## Service Level Agreements and Objectives
### How we prioritize your issue
Cloudflare support responds to every case received in the following priority order:
* Premium Enterprise
* Standard Enterprise
* Business
* Pro
* Free
Cloudflare Support strives to respond to our customers as quickly as possible. Urgent issues (site down, under attack) are prioritized for the quickest response possible. Please explicitly specify the priority level and impact to your production service when reaching out to Cloudflare support.
Below are definitions of the priority levels Cloudflare assigns to cases and the associated Service Level Agreement (SLA) or Service Level Objective (SLO). Whenever possible, responses are provided quicker than the noted SLAs.
### Priority definitions
* P1 Urgent- Critical Business Impact: Severe disruption to your business operations. This issue requires immediate and ongoing attention from both Cloudflare as well as yourself as it directly affects revenue, users, or business continuity.
* *Example*: Your websites, applications, or services are completely unavailable or severely impaired across multiple regions or ISPs.
* *Example*: A confirmed, active security attack is causing major disruptions, such as denial of service, data breaches, or account compromises.
* P2 High - High Business Impact: Significant but localized service or security disruption. While not a full outage, this issue affects business operations and requires urgent resolution.
* *Example*: A recurring or persistent issue is affecting a portion of your users, such as degraded performance, intermittent outages, or limited accessibility.
* *Example*: A past, confirmed security attack has resulted in measurable impact, requiring investigation and mitigation to prevent recurrence.
* P3 Normal - Moderate Business Impact: Limited service impact or suspected security concerns. The issue does not pose an immediate risk but requires attention for continued reliability.
* *Example*: Your service is operational, but you are experiencing minor disruptions, such as performance fluctuations, unexpected behavior, or non-critical bugs.
* *Example*: A suspected security threat has been detected but is currently mitigated (e.g., an attack that Cloudflare successfully blocked).
* P4 Low - Low Business Impact: General inquiries and non-urgent requests. The issue does not impact your service availability or business operations.
* *Example*: You are requesting feature enhancements or recommendations for improving security or performance.
* *Example*: You have questions about Cloudflare’s products, documentation, or best practices.
### Premium SLA
* P1 Urgent- initial response in 1 hour
* P2 High - initial response in 2 hours
* P3 Normal - initial response in 24 hours
* P4 Low - initial response in 24 hours
### Enterprise SLA
* P1 Urgent - initial response in 2 hours
* P2 High - initial response in 4 hours
* P3 Normal - initial response in 48 hours
* P4 Low - initial response in 48 hours
### SLOs for other plans
* PAYGO and Free customers - No SLAs are offered, but customers are responded to in the order in which their request is received. For a quicker answer, we highly recommend searching or posting on our [Community forums](https://community.cloudflare.com/).
## Supported languages
For Enterprise support, Cloudflare provides support in English, but makes a best effort to offer help in the following languages:
* Chinese
* French
* German
* Japanese
* Portuguese
* Spanish
## Supported regions
Cloudflare offers worldwide support, which covers:
* Asia-Pacific
* Europe, Middle East, and Africa
* North and South America
</page>
<page>
---
title: Customer Incident Management Policy · Cloudflare Support docs
description: Cloudflare believes that openness and transparency are intrinsic to
the delivery of our service, and is dedicated to establishing the trust of our
customers and of the Internet community at large. Cloudflare operates a
global network which impacts the lives and prosperity of hundreds of millions
of people, and we are therefore extremely mindful of that responsibility.
lastUpdated: 2025-09-26T09:58:28.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/customer-incident-management-policy/
md: https://developers.cloudflare.com/support/customer-incident-management-policy/index.md
---
## Purpose
Cloudflare believes that openness and transparency are intrinsic to the delivery of our service, and is dedicated to establishing the trust of our customers and of the Internet community at large. Cloudflare operates a global network which impacts the lives and prosperity of hundreds of millions of people, and we are therefore extremely mindful of that responsibility.
This Standard Operating Procedure (SOP) defines how Cloudflare deals with all incidents and problems impacting its production environment and the ways in which Cloudflare communicates the nature and impact of these incidents to Enterprise customers, both planned and unplanned, regardless of severity. This procedure specifies how these efforts are uniformly followed in order to
* maximize environment uptime,
* minimize client impact,
* reduce the time to repair, and
* share information with our customers and the Internet community.
***
## Scope
This SOP applies to Cloudflare customers and customer services as consumed by customers. The SOP is applicable to all customer production environments at Cloudflare including:
* Cloudflare’s public website ([www.cloudflare.com](http://www.cloudflare.com/))
* Cloudflare’s APIs (Application Programming Interfaces)
* Outbound third-party interfaces (e.g. credit card authorizations, etc.)
* Network infrastructure owned or managed by Cloudflare for production services
* Vendor software, hardware and services that affect any part of Cloudflare production
***
## Background
Cloudflare wants to build a better Internet. In order to deliver an improved experience to millions of Internet users, Cloudflare’s internal operations must follow excellent service delivery processes and procedures. Cloudflare’s procedures therefore follow many industry-standard best practices, some of which specifically follow patterns of the Information Library Infrastructure Technology (ITIL). This SOP follows the best practices of the ITIL Problem Management methodology.
***
## Definitions
Categories of key incident terms: All events are conditions which can instigate alerts; some alerts are incidents of note (and some are not); all incidents must be triaged (sometimes through automation, sometimes through human interaction); some incidents are problems; some subset of problems are "major" and instigate Status Page updates; some major incidents have a high priority (P1) which requires the creation of an Incident Report.
Key terminology:
**Event**
Any identifiable and discrete thing which can be logged by one of Cloudflare’s production applications or systems
**Alert**
An event of potential interest which is identified and communicated via one of Cloudflare’s monitoring systems
**Incident**
A report or alert which has a high probability of affecting Cloudflare’s production systems, or an alert condition which only exists for a short period of time because the affected service is restored to health before a Problem condition is identified
**Problem**
An identified and categorized incident which has a negative impact on the optimal health and/or performance of Cloudflare’s production systems or applications
**Incident Report**
A public report which describes the nature of a service Problem, Cloudflare’s overall response to the Problem, and efforts to reduce or eliminate future impact
**Post Mortem Review**
A review meeting initiated in response to severe and/or critical Problem. All Post Mortem meetings focus on the details of an Incident Report generated by a Cloudflare engineer with skills or experience appropriately suited to address to the nature of the Problem.
**SRE**
The Systems Reliability Engineers are the group responsible for the first-level support of all incidents
**CSUP**
The Customer Support group is the team responsible for responding to all customer-generated requests, and for all customer communications during any identified Problem.
**JIRA**
Cloudflare ticketing system used for the tracking of incidents, work orders and problems
**Severity / Priority Level**
Value of “P0, P1, P2 or P3” based on the severity of Problem impacting the Cloudflare network and customers
**SLA**
Service Level Agreement – internal or contractual obligation for a specific level of service (usually measured in actions per unit of time)
**SLO**
Service Level Objective – internal or contractual objective for a specific level of service (usually measured in actions per unit of time)
**Incident Commander**
Cloudflare resource responsible for ensuring the Problem is being addressed properly, time is being kept, escalations are being made, clients are being updated, and that resources are being engaged as needed
**The Internet Community**
Cloudflare’s primary stakeholder group. Cloudflare secures and optimizes over 4,600,000 websites, and the average Internet user interacts with Cloudflare websites over 500 times per week.
**Third Party**
Non-Cloudflare vendor or service provider who partners with CloudFlare in the delivery of systems or services to the client
**Stakeholder**
Person, group or company that is affected by an incident either as the provider (e.g. Cloudflare person, third party) or consumer (client)
**RCA**
Root Cause Analysis – Thorough review of the underlying cause of a problem
**Remediation**
All necessary steps to resolve the root cause of a problem and ensure that it will not happen again
**Status Page**
The primary tool which Cloudflare uses to publicly share information about its service delivery and any Incidents or Problems impacting Cloudflare services: [https://www.cloudflarestatus.com](https://www.cloudflarestatus.com/)
The Status Page is hosted by a Third Party ([Statuspage.io](http://statuspage.io/)) which is not dependent on Cloudflare’s services for operation.
***
## Roles and responsibilities
The following roles and responsibilities are associated with the management of incidents within Cloudflare:
**Cloudflare Management**
Review and approve procedures. Ensure that all staff members are trained on procedures. Notify customers and third parties, as necessary, of their role in procedures. Initiate and oversee Post Mortem Reviews for critical Incident Reports.
**On-call SRE**
One or more SREs who are assigned for on-call shifts to respond to all critical alerts. Identifies and responds to an Incident, assesses and classifies the severity of the Incident, and potentially escalates an impacting Incident as a Problem. Act as escalations and administration of the issue from start to finish.
**On-call Network Engineers**
One or more Network Engineers who are assigned for on-call shifts to respond to critical alerts. Coordinates with the SRE team, who provide the primary Incident Manager during any identified problem.
**On-call CSUP**
One or more CSUP engineers who are assigned for shifts to respond to all customer requests. Responsible for all customer communications during all identified Problems. Responsible for communicating all planned maintenance.
**SRE Team**
The overall Systems Reliability Engineering team who support the efforts of the on-call SREs. Assume the role of Incident Manager during an identified problem. Implement appropriate Cloudflare-supported production changes to resolve issues.
**Cloudflare Engineering Teams (DBA, Network, nginx, Security, etc.)**
Support the Incident Manager during problem resolution. Join bridge calls, if requested. Ensure documentation is captured while diagnosing and correcting issues and proper escalation to other responsible groups is executed. Participate in Post Mortem reviews of some Incident Reports, as requested by Cloudflare Management.
***
## Standard Operating Procedure
This section details the procedures for incident and problem management. At a high-level, these processes relate as follows:
* Incident Management: The overall process for observing and responding to alerts, including: assessing the potential impact and severity of an Incident, classifying the Incident as a Problem, assigning a priority to the Problem, or dismissing the Incident as a non-impacting event if a problem condition cannot be identified.
* Problem Management: The process of identifying the scope and extent of a Problem, assigning an appropriate severity level (P0, P1, P2, P3), the actions to resolve the Problem and restore the optimal state for production services, and the communication of the Problem to appropriate parties.
* Resolution Management: The process of investigating the causes and conditions which lead to a problem condition, reporting on the overall manner by which a problem was managed and resolved, and any subsequent analysis of how the conditions and causes of a problem may be prevented in the future.
***
The primary goal of Incident Management is to identify and react to potential problems as quickly as possible, and thereby minimize impact to production services and provide the best possible levels of service quality and availability. The best possible levels of service quality and availability would be that all services operated exactly as designed 100% of the time, and were available and accessible 100% of the time.
Because we accept that a combination of forces within our control, and forces beyond our control, will eventually impact service health, we define Service Level Objectives (SLOs), and Service Level Agreements (SLAs), to describe what degradations in service health are acceptable for various services within Cloudflare’s network. SLAs and SLOs are expressed as percentages of periods of time (monthly and annually.)
The level of information given about an incident may vary, but the following information must be collected before an incident is classified and prioritized:
* Submitter Source (monitoring alert or alternate source)
* Customer(s) (if applicable)
* System or application (and hostname, if applicable)
* Time of alert
* Scope of impact: estimated number of systems, users, or regions impacted
* Type of impact: general scope of service impairment (e.g., loss of all access, degraded performance, dependent applications impacted, observed customer impact)
All Incidents which are classified as Problems, regardless of source, which have a priority of P0 or P1, will be logged within the Cloudflare ticketing system, JIRA. Some alerts will indicate conditions which may not be immediately impacting to service levels, and as necessary, will be categorized as Problems with a P2 or P3 priority.
The JIRA system is the system of record for all incident information, and all other sources of documentation regarding a Problem (e.g. alert history, screen-shots, work logs, chat conversations) are attached to the original JIRA ticket created in response to an Incident.
### Incident Classifications
After acknowledging an alert, SRE immediately triages the alert by correlating it to a category and priority level. When creating new JIRA tickets for high priority (P0 and P1) Problems, SRE will ensure that each ticket is classified correctly by including its Category and Priority.
### Priority Level
All tickets will be categorized according to the following 4 levels of priority. The criteria listed are general guidelines. Conditions described below should explicitly define a priority level; however at the discretion of SRE or Cloudflare management, problems may be assigned a higher level of priority, as needed:
**P0**
* Complete loss of access to the Cloudflare application or API.
* Degraded access to the Cloudflare application or API (⪯ 98% as measured worldwide or from any major region).
* Complete loss of access to, or major performance degradation to, a Tier-1 Data Center.
* Degraded performance of any Tier-1 global transit provider (⪰ 20% packet loss worldwide or 30% packet loss from any major region).
* Degraded access to or performance of any critical system.
**P1**
* Intermittent or degraded Site-wide performance degradation.
* Loss of an important function such as reporting.
* Loss of access to the Cloudflare application from one of the social media or external CloudFlare websites
* Outage to important outbound third-party interface.
* Inoperability of the site for one of the enterprise clients or distribution partners.
* Corruption or loss of customer data.
**P2**
* Sporadic or localized performance issue.
* System issues with no noticeable client impact yet (e.g. high CPU).
* Single client outage/degradation.
**P3**
* Operational issues, procedural problems or service requests that have little or no effect on end-users and can be handled on an as-available basis.
* The default severity assigned to all tickets that have not yet been reviewed or assigned a severity level.
### Category
For proper tracking and communications, high priority (P0 and P1) problems will be assigned to categories. These categories (ticket labels) correspond to the publicly communicated categories which are listed on Cloudflare’s public Status Page.
Lower priority (P2 and P3) tickets may be categorized using labels and nomenclature which are specific to various Engineering and Non-engineering teams within Cloudflare. These various labels and categories are not listed on this document.
### Security and Privacy Incidents
It is critical to understand that incidents that are classified under the categories of Security and Privacy require special handling and procedures. Customers should report these incidents directly to Cloudflare by [Contacting Cloudflare Support](https://developers.cloudflare.com/support/contacting-cloudflare-support/), who will follow specified incident procedures as defined by the Cloudflare Security & Privacy teams.
### High Severity / Priority Incidents
P0 and P1 incidents obviously have more impact to the business and therefore, have some special upfront requirements to ensure that they are handled in the most expeditious fashion possible.
### Incident Manager
For all P0 and P1 issues, the on-duty Incident Manager should be contacted immediately. A schedule of incident managers will be posted to ensure that SRE knows who to contact at any given time. The incident manager is a critical resource responsible for the following:
* Validation of the severity of an issue
* Tracking of the issue from submission to resolution
* Representation of clients’ best interest
* Logging of all actions and times
* Direction of personnel toward the fastest possible resolution
* Ensuring that clients and internal management are notified of status according to pre-determined time periods (or upon change in status)
* Performing client, internal or third-party escalations when time limits are being exceeded or appropriate progress is not being made
* Ensuring that a meaningful explanation is applied to the ticket upon resolution
* Making certain that the initial submitter agrees that the issue is resolved before the ticket is closed
***
## Incident Communications
External communications during an incident are critical for:
* Notifying the stakeholders that Cloudflare is aware of the issue and is pursuing resolution
* Reassuring clients that the matter is under review and that Cloudflare is looking out for their best interests
* Issues do not drag on unnecessarily and appropriate escalations are being made
* Informing key internal stakeholders of important incidents
Major types of communications during an incident include:
* [StatusPage](https://www.cloudflarestatus.com/)
* [Support tickets](https://developers.cloudflare.com/support/contacting-cloudflare-support/)
* Incident Reports
Status Page will be created using templates by CSUP team member on-call as soon as an incident is identified.
***
## Post-Mortem reviews
Cloudflare believes that all critical problems should never recur. To that end, all P0 problems will instigate the publication of an Incident Report (IR), which includes a Root Cause Analysis (RCA) of the problem and the overall factors which lead up to the Incident. All IR publications will be followed by a Post Mortem meeting, a meeting in which engineers and managers review and agree upon the details of the IR, the conclusions of the RCA, and any follow-up remediation steps which will be taken to ensure that the problem condition(s) do not recur.
### Problem Management and Post-Mortem
Problem Management differs from Incident Management in that its main goal is the detection of the underlying causes of an Incident and their subsequent resolution and prevention.
### Root Cause Analysis and Remediation
#### **Problem Ticket**
An RCA is a Root Cause Analysis report. A Jira Problem ticket is the logging and tracking of events that may warrant an RCA. This is a process by which the subject matter experts (SME) for an area will review a P0 or P1 issue searching for the underlying cause of the issue. Once this is determined, the SMEs need to create a remediation plan to address the cause(s). The ultimate deliverable is a well-documented ticket to track the remediation to completion and, if required, a well-written incident report to be sent to an internal team and/or client.
The above points are still applicable even if it is a third party provider or vendor supplying the RCA. When the RCA information is received from a third party, we must ensure that the Problem ticket is updated with all relevant information including outstanding remediations to be tracked.
#### **IR Report**
The Incident Report (“IR”) is the primary method of communication to the client on an issue and may contain some or all parts of what is written within the ticket.
The person writing the report will vary depending on the severity of the issue and the responsible area. Upon completion of the draft report, it is critical to ensure that the report is reviewed by Cloudflare management for content, commitments and professional presentation. Once the report is approved it may be published to the client.
***
## Problem review
The above sections have detailed the handling of the incident and the root cause process for ensuring permanent remediation. The last part of the incident and problem management process is to ensure that key metrics, trends and reporting are done to ensure that the process is being followed correctly, SLAs are being met and below-the-surface issues are not being missed.
### Reporting
The ticket criteria that need to be reported for both open and closed tickets include the following:
* Severity
* Category/Sub-category
* Responsible Group
* Age/Days Open
Wherever possible, this data should be reported graphically to show visible trends. These reports should be published to internal Cloudflare managers and area owners.
### Analysis and Accountability
Each area owner for tickets will be responsible for not only ensuring that their tickets are closed within prescribed or reasonable time frames, but also reviewing the reports and looking for trends, concerns and repeat issues. Based on this analysis, further Problem tickets should be opened to remediate any issues that may not have surfaced via a P0 or P1. This will allow continuous improvement and should ultimately reduce new ticket counts by further dealing with root causes.
### Incident Management Review Meetings (Post-mortem)
As part of all departmental staff meetings, group managers should be reviewing the ticket open and trending reports with the following objectives:
* Discussion of areas of success or concern
* Review of opportunities for improvement by the area owners
* Agreement on areas that warrant a new Problem ticket to be opened for remediation tracking
</page>
<page>
---
title: Disruptive Maintenance · Cloudflare Support docs
description: Planned maintenances will be published on the status page using a
calendar that is updated on a daily basis.
lastUpdated: 2025-06-11T12:06:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/disruptive-maintenance/
md: https://developers.cloudflare.com/support/disruptive-maintenance/index.md
---
## Scheduled Maintenance Windows
Planned maintenances will be published on the status page using a *calendar* that is updated on a daily basis.
During these maintenance windows, customers may experience a slight increase in latency to the edge location which is under maintenance.
Note
All dates in the calendar are in UTC Timezone.
### Maintenance Calendar links
[Download iCal](https://calendar.google.com/calendar/ical/c_83vui762nfm498l9a0ciojbju0%40group.calendar.google.com/public/basic.ics) [Add to Google Calendar](https://calendar.google.com/calendar/u/0?cid=Y184M3Z1aTc2Mm5mbTQ5OGw5YTBjaW9qYmp1MEBncm91cC5jYWxlbmRhci5nb29nbGUuY29t)
### Notifications
Scheduled maintenances can also be sent out via [Cloudflare Notifications](https://developers.cloudflare.com/notifications/).
Maintenance Notification
**Who is it for?**
Customers interested in knowing about planned [Cloudflare maintenance](https://developers.cloudflare.com/support/troubleshooting/disruptive-maintenance/) for specific data centers. The notification lets you know when maintenance has been scheduled, changed, or canceled on an entire point of presence.
**Other options / filters**
You can filter maintenance notifications for specific points of presence and updates (scheduled, changed, canceled).
**Included with**
All Cloudflare plans.
**What should you do if you receive one?**
If the notification is announcing new scheduled maintenance, you may want to add the maintenance to your calendar. During these maintenance windows, you may experience a slight increase in latency to the edge location which is under maintenance.
Refer to [Cloudflare Notifications](https://developers.cloudflare.com/notifications/get-started/) for more information on how to set up an alert.
## Unplanned Maintenance
Cloudflare operates a redundant [anycast network](https://www.cloudflare.com/en-gb/learning/cdn/glossary/anycast-network/) that is capable of automatically removing locations from our network if they require unplanned maintenance or experience an emergency event. In such cases, traffic will be rerouted automatically to alternative locations.
To check for unplanned maintenance, you can confirm at all times if a location was re-routed by verifying if its status is listed as "Re-routed" in our status page <https://www.cloudflarestatus.com>. Exceptionally, an incident may be declared for maintenance at a location, in which case updates will be available in our status page at <https://www.cloudflarestatus.com>.
## Interconnections at locations under maintenance
If you have a [CNI connection](https://developers.cloudflare.com/network-interconnect/) with Cloudflare at a re-routed location, it may become temporarily unavailable during planned or unplanned maintenance, and regular internet routing may be used instead to reach your network.
In the Magic family of products, the routing is defined explicitly using [static routes](https://developers.cloudflare.com/magic-wan/configuration/manually/how-to/configure-routes/#create-a-static-route) to send traffic to the specified tunnels, with customer-configured priorities. If you have a CNI tunnel, we strongly recommend that you also add routes to an alternative tunnel, such as a fallback Internet tunnel, to make sure your traffic can be routed at all times.
## Related resources
* [Available RSS feeds](https://developers.cloudflare.com/fundamentals/new-features/available-rss-feeds/) (for the [Cloudflare changelog](https://developers.cloudflare.com/changelog/))
* [Subscribe to Cloudflare Status](https://developers.cloudflare.com/support/cloudflare-status/)
* [API deprecations](https://developers.cloudflare.com/fundamentals/api/reference/deprecations/)
</page>
<page>
---
title: Third-Party Software · Cloudflare Support docs
description: Below you will find links to the relevant sections for Third-Party
Software support-focused material.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/third-party-software/
md: https://developers.cloudflare.com/support/third-party-software/index.md
---
Below you will find links to the relevant sections for Third-Party Software support-focused material.
* [Content Management System (CMS)](https://developers.cloudflare.com/support/third-party-software/content-management-system-cms/)
* [Forum Software](https://developers.cloudflare.com/support/third-party-software/forum-software/)
* [Others](https://developers.cloudflare.com/support/third-party-software/others/)
</page>
<page>
---
title: Troubleshooting · Cloudflare Support docs
description: Below you will find links to the relevant sections for
Troubleshooting support-focused material.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/support/troubleshooting/
md: https://developers.cloudflare.com/support/troubleshooting/index.md
---
Below you will find links to the relevant sections for Troubleshooting support-focused material.
* [General Troubleshooting](https://developers.cloudflare.com/support/troubleshooting/general-troubleshooting/)
* [HTTP Status Codes](https://developers.cloudflare.com/support/troubleshooting/http-status-codes/)
* [Restoring Visitor IPs](https://developers.cloudflare.com/support/troubleshooting/restoring-visitor-ips/)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Tenant docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/tenant/404/
md: https://developers.cloudflare.com/tenant/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Get started · Cloudflare Tenant docs
description: Having access to Cloudflare’s provisioning capabilities allows you
to more easily create and manage Cloudflare accounts. The following steps will
get you started on making API calls to provision accounts, users, and
services.
lastUpdated: 2025-08-20T20:59:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/tenant/get-started/
md: https://developers.cloudflare.com/tenant/get-started/index.md
---
Having access to Cloudflare’s provisioning capabilities allows you to more easily create and manage Cloudflare accounts. The following steps will get you started on making API calls to provision accounts, users, and services.
## Before you begin
### Channel and Alliance partner account setup
Before using the Tenant API, you need to [create an account](https://developers.cloudflare.com/fundamentals/account/create-account/), [verify your email address](https://developers.cloudflare.com/fundamentals/user-profiles/verify-email-address/), and [add your billing information](https://developers.cloudflare.com/billing/create-billing-profile/).
After you sign your partner agreement with Cloudflare, Cloudflare will add [certain entitlements](https://developers.cloudflare.com/tenant/structure/) to your account that allow you to provision and manage custom accounts. If you have signed your partner agreement and your account has not yet been enabled, MSP partners should contact `partners@cloudflare.com` and Agency Partners should contact `agency@cloudflare.com`.
### API access
You also need to [retrieve your API key](https://developers.cloudflare.com/fundamentals/api/get-started/keys/#view-your-global-api-key) to authenticate your requests to the Tenant API.
For more details on using the Cloudflare API, refer to our [API overview](https://developers.cloudflare.com/fundamentals/api/).
## Step 1 - Create an account
Each customer or team that uses Cloudflare should have their own account. This ensures proper security and access of resources. Each account acts as a container of zones and other resources. Depending on your needs, you may even provision multiple accounts for a single customer or team.
When you create an account with the Tenant API, your Cloudflare user owns that account from creation, ongoing management, and finally deletion.
* Dashboard
To create an account under your tenant using the dashboard:
1. Log into the [Cloudflare dashboard](https://dash.cloudflare.com).
2. Go to **Tenants** > **Managed Accounts**.
3. Select **Create Account**.
4. Enter the **Account Name**, **Account Description**, and **Tenant Unit**.
5. Choose the appropriate account subscription.
6. Select **Add Account**.
* API
To create an account using the API, make a `POST` request to the `/accounts` endpoint and include the following values:
* `name` string
* The name of the account that is displayed in the Cloudflare dashboard.
* `type` enum
* Valid values are `standard` (default) and `enterprise`. For self-serve customers, use `standard`. For enterprise customers, use `enterprise`.
* `unit` object
* Information related to the tenant unit.
* `id` string
* (optional) ID of the unit to create this account on. Needs to be specified if user administers multiple tenants. Unit ID is the `unit_tag` from your [tenant details](https://developers.cloudflare.com/tenant/how-to/get-tenant-details/).
### Know-Your-Customer (optional)
All KYC parameters are text fields, have a 120 character limit, and are optional unless enforced by the Tenant.
* `business_name` string
* (optional) The name of the business associated with this account.
* `business_address` string
* (optional) The address of the business associated with this account.
* `business_email` string
* (optional) The email of the business associated with this account.
* `business_phone` string
* (optional) The phone number of the business associated with this account.
* `external_metadata` string
* (optional) External metadata for this account.
```bash
curl "https://api.cloudflare.com/client/v4/accounts" \
--header "X-Auth-Email: <EMAIL>" \
--header "X-Auth-Key: <API_KEY>" \
--header "Content-Type: application/json" \
--data '{
"name": "<ACCOUNT_NAME>",
"type": "standard"
}'
```
A successful request will return an HTTP status of `200` and the following response body:
```json
{
"result": {
"id": "2bab6ace8c72ed3f09b9eca6db1396bb",
"name": "<ACCOUNT_NAME>",
"type": "standard",
"settings": {
"enforce_twofactor": false
}
},
"success": true,
"errors": [],
"messages": []
}
```
A request with a unit ID:
```bash
curl "https://api.cloudflare.com/client/v4/accounts" \
--header "X-Auth-Email: <EMAIL>" \
--header "X-Auth-Key: <API_KEY>" \
--header "Content-Type: application/json" \
--data '{
"name": "<ACCOUNT_NAME>",
"type": "standard",
"unit": {
"id": "1a2b3c4d5e6f7g8h"
}
}'
```
A request with a unit ID and KYC:
```bash
curl "https://api.cloudflare.com/client/v4/accounts" \
--header "X-Auth-Email: <EMAIL>" \
--header "X-Auth-Key: <API_KEY>" \
--header "Content-Type: application/json" \
--data '{
"name": "<ACCOUNT_NAME>",
"type": "standard",
"business_name": "Cloudflare",
"business_email": "email@business.com",
"business_address": "San Francisco",
"business_phone": "1234567890",
"external_metadata": "{'\''testKey'\'': '\''testValue'\''}",
"unit": {
"id": "1a2b3c4d5e6f7g8h"
}
}'
```
## Step 2 - Grant user access
Now that you have created an account, you need to either give your customer direct access to Cloudflare or build an interface for them to interact with.
The first method gives customers control over all aspects of Cloudflare, while the latter allows you to integrate your customer's Cloudflare experience into a dashboard that you control and that they may already be familiar with.
### Option 1 - Direct access to Cloudflare
When you grant user access to an account, Cloudflare will send an invitation to the user so they can get access to the account. If they do not already have a Cloudflare user, Cloudflare will take them through the process of creating one. Once created, they will be given access to the account and any zones already created.
#### Using the dashboard
If you want to give customers access to their individual accounts, it is the same as if you were [inviting a teammate](https://developers.cloudflare.com/fundamentals/manage-members/manage/#add-account-members) to help manage your account.
#### Using the API
You can also grant access to the Cloudflare dashboard by using the API.
```bash
curl 'https://api.cloudflare.com/client/v4/accounts/<CUSTOMER_ACCOUNT_ID>/members' \
--header "X-Auth-Email: <EMAIL>" \
--header "X-Auth-Key: <API_KEY>" \
--header "Content-Type: application/json" \
--data '{
"email": "<CUSTOMER_EMAIL>",
"roles": ["<USER_ROLE>"]
}'
```
In most cases, you will want to create new users with a role of `Administrator` which always has the ID `05784afa30c1afe1440e79d9351c7430`.
If your customer is on an Enterprise plan, they have access to a broader set of user roles. To get a full list of available roles, send a [`GET`](https://developers.cloudflare.com/api/resources/accounts/subresources/roles/methods/list/) request to the API.
### Option 2 - Access via an interface
If you want greater control over how customers use Cloudflare or if you want your customers to use an existing dashboard of yours that they already know, use the Cloudflare API to build this experience.
This means that you will be making API calls to Cloudflare on behalf of your customers. To avoid getting [rate limited](https://developers.cloudflare.com/fundamentals/api/reference/limits/) by our API, Cloudflare recommend that you create accounts and users for each of your customers. Changes made by customer `A` should go through user `A` and changes made by customer `B` should go through user `B`.
Note
This capability is not enabled by default. If you need this functionality, contact [Cloudflare Support](https://developers.cloudflare.com/support/contacting-cloudflare-support/).
To grant access via an interface, you need to create a service user, as no one will log in to the dashboard with them. If you are planning to use this method, Cloudflare will enable you to see the API key in order to make API calls as this user.
```bash
curl "https://api.cloudflare.com/client/v4/users" \
--header "X-Auth-Email: <EMAIL>" \
--header "X-Auth-Key: <API_KEY>" \
--header "Content-Type: application/json" \
--data '{
"email": "<ID@example.com>"
}'
```
```json
{
"result": {
"id": "60758bd48392a06215ae817bc35084b6",
"email": "<ID@example.com>",
"first_name": null,
"last_name": null,
"username": "17bd2796b374cec14976ac3bced85c05",
"telephone": null,
"country": null,
"created_on": "2019-02-21T23:20:28.645256Z",
"modified_on": "2019-02-21T23:20:28.645256Z",
"two_factor_authentication": {
"enabled": false,
"locked": false
},
"api_key": "xxx"
},
"success": true,
"errors": [],
"messages": []
}
```
## Step 3 - Create a zone
Now that you have a customer account and customer users (or service users), you need to create a zone.
To do this, send a [`POST`](https://developers.cloudflare.com/api/resources/zones/methods/create/) request to the `/zones` endpoint (including the customer account ID you received in [Step 1](#step-1---create-an-account)).
```bash
curl "https://api.cloudflare.com/client/v4/zones" \
--header "X-Auth-Email: <EMAIL>" \
--header "X-Auth-Key: <API_KEY>" \
--header "Content-Type: application/json" \
--data '{
"name": "example.com",
"account": {
"id": "<CUSTOMER_ACCOUNT_ID>"
}
}'
```
## Step 4 - Create a zone plan subscription
Now that you have a zone provisioned for the customer, you can add the appropriate zone plan based on your reseller agreement.
To create a zone subscription, typically used to upgrade a zone's plan from `PARTNERS_FREE` to a paid [Zone plan](https://developers.cloudflare.com/tenant/reference/subscriptions/#zone-plans), send a [POST](https://developers.cloudflare.com/api/resources/zones/subresources/subscriptions/methods/create/) request to the `/zones/{zone_id}/subscription` endpoint and include the following values:
* `rate_plan` object
* Contains the zone plan corresponding to what customers would order in the dashboard. For a list of available values, refer to [Zone subscriptions](https://developers.cloudflare.com/tenant/reference/subscriptions/#zone-plans).
* `component_values` array
* Additional services depending on your reseller agreement, such as additional `page_rules`.
* `frequency` string
* How often the subscription is renewed automatically (defaults to `"monthly"`).
```bash
curl 'https://api.cloudflare.com/client/v4/zones/{zone_id}/subscription' \
--header "Authorization: Bearer <API_TOKEN>" \
--header "Content-Type: application/json" \
--data '{
"rate_plan": {
"id": "<RATE_PLAN>"
},
"frequency": "annual"
}'
```
```bash
curl 'https://api.cloudflare.com/client/v4/zones/{zone_id}/subscription' \
--header "Authorization: Bearer <API_TOKEN>" \
--header "Content-Type: application/json" \
--data '{
"rate_plan": {
"id": "PARTNERS_BIZ"
},
"component_values": [
{
"name": "page_rules",
"value": 50
}
]
}
```
## Step 5 - Create other subscriptions
Depending on your agreement, you may be allowed to resell other add-on services. These are provisioned as account-level subscriptions.
To create an account subscription, send a [POST](https://developers.cloudflare.com/api/resources/accounts/subresources/subscriptions/methods/create/) request to the `/accounts/{account_id}/subscriptions` endpoint and include the following values:
* `rate_plan` object
* Contains the account subscription corresponding to a specific add-on service. For a list of available values, refer to [Available subscriptions](https://developers.cloudflare.com/tenant/reference/subscriptions/).
* `component_values` array
* Additional services depending on your reseller agreement, such as additional endpoints for load balancing or additional seats for Cloudflare Zero Trust. If not included, the subscription includes the default values associated with each purchase.
* `frequency` string
* How often the subscription is renewed automatically (defaults to `"monthly"`).
```bash
curl 'https://api.cloudflare.com/client/v4/accounts/{account_id}/subscriptions' \
--header "Authorization: Bearer <API_TOKEN>" \
--header "Content-Type: application/json" \
--data '{
"rate_plan": {
"id": "<RATE_PLAN_NAME>"
}
}'
```
## Step 6 - Configure zone and services
Once you have added the necessary subscriptions, you or your customer can move on to configuring various services and fine-tuning account and zone settings.
Configuration can be done by anyone with access to the account (as well as the correct user permissions). This process does not differ from configuring any other Cloudflare account. For additional guidance, refer to our [Product docs](https://developers.cloudflare.com/).
</page>
<page>
---
title: Glossary · Cloudflare Tenant docs
description: The following terms are used throughout the Tenant API docs. For
more details on how these concepts interact with each other, refer to Tenant
structure.
lastUpdated: 2025-08-20T20:59:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/tenant/glossary/
md: https://developers.cloudflare.com/tenant/glossary/index.md
---
The following terms are used throughout the Tenant API docs. For more details on how these concepts interact with each other, refer to [Tenant structure](https://developers.cloudflare.com/tenant/structure/).
## Tenant
A **Tenant** is a special type of Cloudflare account that contains other accounts and resources.
## Tenant admin
Once you sign a partner agreement with Cloudflare, we create a special Tenant account and then add your user to that account as a **Tenant admin**. Cloudflare can add multiple users as Tenant admins upon request.
Tenant admins then become the default [**Super administrator(s)**](https://developers.cloudflare.com/fundamentals/manage-members/roles/) for all accounts and zones contained within the Tenant.
This means that each Tenant admin's user API key can be used to provision accounts based on the catalog specified in your partner agreement.
If needed, you can also [create additional **Super administrators**](https://developers.cloudflare.com/fundamentals/manage-members/manage/).
## Account
An entity that contains various settings, users, and resources (zones, Zero Trust applications, Workers).
## User
A member of a Cloudflare account with their own user profile and [an associated role](https://developers.cloudflare.com/fundamentals/manage-members/roles/) that specifies their privileges within that account.
## Resource
A resource is an entity owned by an account, which could be a zone/domain, a Workers instance, or a Zero Trust application.
</page>
<page>
---
title: How to · Cloudflare Tenant docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/tenant/how-to/
md: https://developers.cloudflare.com/tenant/how-to/index.md
---
* [Manage accounts](https://developers.cloudflare.com/tenant/how-to/manage-accounts/)
* [Manage subscriptions](https://developers.cloudflare.com/tenant/how-to/manage-subscriptions/)
* [Get account details](https://developers.cloudflare.com/tenant/how-to/get-account-details/)
* [Get tenant details](https://developers.cloudflare.com/tenant/how-to/get-tenant-details/)
</page>
<page>
---
title: Reference · Cloudflare Tenant docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/tenant/reference/
md: https://developers.cloudflare.com/tenant/reference/index.md
---
* [Available subscriptions](https://developers.cloudflare.com/tenant/reference/subscriptions/)
</page>
<page>
---
title: Tenant structure · Cloudflare Tenant docs
description: Cloudflare helps Channel and Alliance partners manage their and
their customers' accounts through a Tenant structure.
lastUpdated: 2025-08-20T20:59:04.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/tenant/structure/
md: https://developers.cloudflare.com/tenant/structure/index.md
---
Cloudflare helps Channel and Alliance partners manage their and their customers' accounts through a Tenant structure.

## Tenants and Tenant admins
A **Tenant** is a special type of Cloudflare account that contains other accounts and resources.
Once you sign a partner agreement with Cloudflare, we create a special Tenant account and then add your user to that account as a **Tenant admin**. Cloudflare can add multiple users as Tenant admins upon request.
Tenant admins then become the default [**Super administrator(s)**](https://developers.cloudflare.com/fundamentals/manage-members/roles/) for all accounts and zones contained within the Tenant.
This means that each Tenant admin's user API key can be used to provision accounts based on the catalog specified in your partner agreement.
If needed, you can also [create additional **Super administrators**](https://developers.cloudflare.com/fundamentals/manage-members/manage/).
## Accounts, users, and resources
This Tenant structure gives your account streamlined administrative access to customer:
* Accounts[1](#user-content-fn-1)
* Users[2](#user-content-fn-2)
* Resources[3](#user-content-fn-3)
At the same time, this structure keeps your customers' data and settings separate from each other.
## Footnotes
1. An entity that contains various settings, users, and resources (zones, Zero Trust applications, Workers).
[↩](#user-content-fnref-1)
2. A member of a Cloudflare account with their own user profile and [an associated role](https://developers.cloudflare.com/fundamentals/manage-members/roles/) that specifies their privileges within that account.
[↩](#user-content-fnref-2)
3. A resource is an entity owned by an account, which could be a zone/domain, a Workers instance, or a Zero Trust application.
[↩](#user-content-fnref-3)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Terraform docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/terraform/404/
md: https://developers.cloudflare.com/terraform/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Additional configurations · Cloudflare Terraform docs
lastUpdated: 2024-12-09T11:01:03.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/terraform/additional-configurations/
md: https://developers.cloudflare.com/terraform/additional-configurations/index.md
---
* [WAF Managed Rules configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/waf-managed-rulesets/)
* [DDoS managed rulesets configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/ddos-managed-rulesets/)
* [Rate limiting rules configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/rate-limiting-rules/)
* [WAF custom rules configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/waf-custom-rules/)
* [Transform Rules configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/transform-rules/)
* [Single Redirects](https://developers.cloudflare.com/rules/url-forwarding/single-redirects/terraform-example/)
* [Bulk Redirects](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/terraform-example/)
* [Configuration Rules](https://developers.cloudflare.com/rules/configuration-rules/examples/define-single-configuration-terraform/)
* [Origin Rules](https://developers.cloudflare.com/rules/origin-rules/examples/define-single-origin-terraform/)
* [Cache Rules](https://developers.cloudflare.com/cache/how-to/cache-rules/terraform-example/)
* [Snippets](https://developers.cloudflare.com/rules/snippets/create-terraform/)
* [Workers](https://developers.cloudflare.com/workers/platform/infrastructure-as-code/)
</page>
<page>
---
title: Advanced topics · Cloudflare Terraform docs
lastUpdated: 2024-12-09T11:01:03.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/terraform/advanced-topics/
md: https://developers.cloudflare.com/terraform/advanced-topics/index.md
---
* [Best practices](https://developers.cloudflare.com/terraform/advanced-topics/best-practices/)
* [Import Cloudflare resources](https://developers.cloudflare.com/terraform/advanced-topics/import-cloudflare-resources/)
* [Provider customization](https://developers.cloudflare.com/terraform/advanced-topics/provider-customization/)
* [Remote R2 backend](https://developers.cloudflare.com/terraform/advanced-topics/remote-backend/)
</page>
<page>
---
title: Install Terraform · Cloudflare Terraform docs
description: Terraform ships as a single binary file. The examples below include
installation information for popular operating systems.
lastUpdated: 2024-08-20T21:10:02.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/terraform/installing/
md: https://developers.cloudflare.com/terraform/installing/index.md
---
Terraform ships as a single binary file. The examples below include installation information for popular operating systems.
For official instructions on installing Terraform, refer to [Install Terraform](https://developer.hashicorp.com/terraform/tutorials/certification-associate-tutorials/install-cli).
Warning
Terraform maintains your configuration state, which can be broken when you make configuration changes through both Terraform and either the Cloudflare Dashboard or API.
To avoid this state, make sure you manage Terraform resources only in Terraform. For more details, refer to our [best practices](https://developers.cloudflare.com/terraform/advanced-topics/best-practices/).
## Mac
The easiest way to install Terraform on macOS is with Homebrew.
```sh
brew tap hashicorp/tap
brew install hashicorp/tap/terraform
```
## Linux
You can install the `terraform` binary via your distribution's package manager. For example:
```sh
sudo apt install terraform
```
Alternatively, you can fetch a specific version directly and place the binary in your `PATH`:
```sh
wget -q https://releases.hashicorp.com/terraform/1.4.5/terraform_1.4.5_linux_amd64.zip
unzip terraform_1.4.5_linux_amd64.zip
```
```sh
Archive: terraform_1.4.5_linux_amd64.zip
inflating: terraform
```
```sh
sudo mv terraform /usr/local/bin/terraform
terraform version
```
```sh
Terraform v1.4.5
```
## Windows
1. Download the 32 or 64-bit executable from the [Download Terraform](https://developer.hashicorp.com/terraform/downloads) page.
2. Unzip and place `terraform.exe` somewhere in your path.
## Other
For additional installers, refer to the [Download Terraform](https://developer.hashicorp.com/terraform/downloads) page.
</page>
<page>
---
title: Troubleshooting · Cloudflare Terraform docs
description: The following pages are useful for troubleshooting Terraform issues.
lastUpdated: 2024-12-09T11:01:03.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/terraform/troubleshooting/
md: https://developers.cloudflare.com/terraform/troubleshooting/index.md
---
The following pages are useful for troubleshooting Terraform issues.
* [403 Authentication error when creating DNS records](https://developers.cloudflare.com/terraform/troubleshooting/authentication-error-dns-records/)
* [Rule IDs change when I modify a ruleset](https://developers.cloudflare.com/terraform/troubleshooting/rule-id-changes/)
</page>
<page>
---
title: Tutorials · Cloudflare Terraform docs
description: Before you begin, install Terraform. Each tutorial builds on the
previous, so you should complete the tutorials in the order shown below.
lastUpdated: 2025-09-09T22:06:23.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/terraform/tutorial/
md: https://developers.cloudflare.com/terraform/tutorial/index.md
---
Before you begin, [install Terraform](https://developers.cloudflare.com/terraform/installing/). Each tutorial builds on the previous, so you should complete the tutorials in the order shown below.
Note
If you are upgrading from v4, review the [migration guide](https://github.com/cloudflare/terraform-provider-cloudflare/blob/main/docs/guides/version-5-upgrade.md) for breaking changes.
## [1 – Initialize Terraform](https://developers.cloudflare.com/terraform/tutorial/initialize-terraform/)
* Brief introduction.
* Introduction of `terraform init`, `plan`, `apply`, and `show`.
* Resource covered: [`cloudflare_dns_record`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/dns_record) (DNS record).
## [2 – Track your history](https://developers.cloudflare.com/terraform/tutorial/track-history/)
* Store Cloudflare configuration in source control.
## [3 – Configure HTTPS settings](https://developers.cloudflare.com/terraform/tutorial/configure-https-settings/)
* Modify zone settings.
* Resource covered: [`cloudflare_zone_setting`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/zone_setting).
## [4 – Improve performance and reliability](https://developers.cloudflare.com/terraform/tutorial/use-load-balancing/)
* Add load balancing rules.
* Resources covered:
* [`cloudflare_load_balancer`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/load_balancer)
* [`cloudflare_load_balancer_pool`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/load_balancer_pool)
* [`cloudflare_load_balancer_monitor`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/load_balancer_monitor)
## [5 – Add exceptions with page rules](https://developers.cloudflare.com/terraform/tutorial/add-page-rules/)
* Add page rule.
* Resource covered: [`cloudflare_page_rule`](https://registry.terraform.io/providers/cloudflare/cloudflare/latest/docs/resources/page_rule).
* Increase security level for a specific URL: `/expensive-db-call`.
* Add a redirect (URL forward) with a `301` status code from `/old-location.php` to `/expensive-db-call`.
## [6 – Revert configuration](https://developers.cloudflare.com/terraform/tutorial/revert-configuration/)
* Review change history.
* Roll back changes.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Time Services docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/time-services/404/
md: https://developers.cloudflare.com/time-services/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Network Time Protocol · Cloudflare Time Services docs
description: Network Time Protocol (NTP) is an Internet protocol designed to
synchronize time between computer systems communicating over unreliable and
variable-latency network paths. Cloudflare offers its version of NTP for free
so you can use our global anycast network to synchronize time from our closest
server.
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/time-services/ntp/
md: https://developers.cloudflare.com/time-services/ntp/index.md
---
[Network Time Protocol](https://tools.ietf.org/html/rfc1305) (NTP) is an Internet protocol designed to synchronize time between computer systems communicating over unreliable and variable-latency network paths. Cloudflare offers its version of NTP for free so you can use our [global anycast network](https://www.cloudflare.com/network/) to synchronize time from our closest server.
## Background
NTP works by having a client send a query packet out to an NTP server that then responds with its clock time. The client then computes an estimate of the difference between its clock and the remote clock and attempts to compensate for any network delay. The NTP client then queries multiple servers and implements algorithms to select the best estimate.
Cloudflare does not implement leap smearing: NTP includes a Leap Indicator field [spec](https://tools.ietf.org/html/rfc5905#section-7.3) and the kernel will apply the leap second correction at the appropriate time. This is the behavior servers in `pool.ntp.org` share. Using servers that smear time along with servers that do not may lead to unpredictable and anomalous results.
## Next steps
For more background information about NTP, refer to the [introductory blog](https://blog.cloudflare.com/secure-time/).
To enable NTP on your device, refer to our [Usage guide](https://developers.cloudflare.com/time-services/ntp/usage/).
</page>
<page>
---
title: Network Time Security · Cloudflare Time Services docs
description: Network Time Security (NTS) provides cryptographic security for the
client-server mode of the Network Time Protocol (NTP). This allows users to
obtain time in an authenticated manner.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/time-services/nts/
md: https://developers.cloudflare.com/time-services/nts/index.md
---
[Network Time Security](https://datatracker.ietf.org/doc/html/rfc8915) (NTS) provides cryptographic security for the client-server mode of the Network Time Protocol (NTP). This allows users to obtain time in an authenticated manner.
## Background
The NTS protocol is divided into two phases:
1. **NTS Key Exchange**: Establishes the necessary key material between the NTP client and the server, using a [Transport Layer Security (TLS) handshake](https://www.cloudflare.com/learning/ssl/what-happens-in-a-tls-handshake/) (the same public key infrastructure as the web). Once the keys are exchanged, the TLS channel is closed and the protocol enters the second phase.
2. **NTS Extension Fields for NTPv4**: Authenticates NTP time synchronization packets using previously established key material. For more information, refer to [RFC 8915](https://tools.ietf.org/html/rfc8915).
## Next steps
NTS is gaining support in many NTP implementations, including [Chrony](https://chrony-project.org/documentation.html), [NTPsec](https://www.ntpsec.org/), and [ntpd-rs](https://github.com/pendulum-project/ntpd-rs). Read the relevant documentation for guidance on setting them up to point to our time service, `time.cloudflare.com`. Also see [Netnod's documentation](https://www.netnod.se/netnod-time/how-to-use-nts) for configuring NTS clients.
</page>
<page>
---
title: Roughtime · Cloudflare Time Services docs
description: Roughtime is a simple, flexible, and secure authenticated time
protocol developed by Google.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/time-services/roughtime/
md: https://developers.cloudflare.com/time-services/roughtime/index.md
---
[Roughtime](https://roughtime.googlesource.com/roughtime) is a simple, flexible, and secure authenticated time protocol developed by Google.
## Background
Endpoints on the Internet often synchronize their clocks using the [Network Time Protocol (NTP)](https://developers.cloudflare.com/time-services/ntp/). NTP provides precise synchronization, but is frequently deployed without a means of authentication. This is due to a [combination of issues](https://www.usenix.org/conference/usenixsecurity16/technical-sessions/presentation/dowling).
As a result, a man-in-the-middle attacker can easily influence a victim’s clock. By moving them back in time, the attacker can, for example, force a victim to accept an expired (and possibly compromised) TLS certificate or session ticket.
For many applications, *precise* network time is not essential. It is sufficient to have *accurate* time to mitigate these kinds of attacks, such as within 10 seconds of real time. This observation is the primary motivation behind Roughtime.
## Next steps
For more technical details on Roughtime, refer to the [introductory blog post](https://blog.cloudflare.com/roughtime/).
To get started, refer to [Get the Roughtime](https://developers.cloudflare.com/time-services/roughtime/usage/). For more practical guidance on using the Roughtime, refer to our [how-to guide](https://developers.cloudflare.com/time-services/roughtime/recipes/).
</page>
<page>
---
title: Terms of use · Cloudflare Time Services docs
description: By using Cloudflare's suite of time services, you agree to
Cloudflare Website and Online Services Terms of Use.
lastUpdated: 2025-08-07T14:37:31.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/time-services/tos/
md: https://developers.cloudflare.com/time-services/tos/index.md
---
By using Cloudflare's suite of time services, you agree to [Cloudflare Website and Online Services Terms of Use](https://www.cloudflare.com/website-terms/).
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Turnstile docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/404/
md: https://developers.cloudflare.com/turnstile/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Additional configurations · Cloudflare Turnstile docs
description: "Refer to the following pages for more information about
Turnstile's additional configurations:"
lastUpdated: 2025-08-13T20:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/turnstile/additional-configuration/
md: https://developers.cloudflare.com/turnstile/additional-configuration/index.md
---
Refer to the following pages for more information about Turnstile's additional configurations:
* [Hostname management](https://developers.cloudflare.com/turnstile/additional-configuration/hostname-management/)
* [Pre-clearance support](https://developers.cloudflare.com/cloudflare-challenges/concepts/clearance/#pre-clearance-support-in-turnstile)
* [Ephemeral IDs](https://developers.cloudflare.com/turnstile/additional-configuration/ephemeral-id/)
* [Remove Cloudflare branding with Offlabel](https://developers.cloudflare.com/turnstile/additional-configuration/offlabel/)
</page>
<page>
---
title: Changelog · Cloudflare Turnstile docs
description: Subscribe to RSS
lastUpdated: 2025-02-13T19:35:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/changelog/
md: https://developers.cloudflare.com/turnstile/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/turnstile/changelog/index.xml)
## 2024-08-12
* Added [`[flexible]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#widget-size) width widget size.
* Added new dimensions for Turnstile's compact size.
* Added a Feedback Report toggle on the widget's configuration.
## 2024-04-10
* Added [`[refresh-timeout]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#refresh-a-timed-out-widget) and document new automatic interactive timeout-refresh.
## 2024-03-25
* Added more [supported languages](https://developers.cloudflare.com/turnstile/reference/supported-languages).
## 2023-12-18
* Added [Pre-Clearance mode](https://developers.cloudflare.com/turnstile/concepts/pre-clearance-support/).
## 2023-08-24
* Added [Client-side errors](https://developers.cloudflare.com/turnstile/troubleshooting/client-side-errors/).
## 2023-07-31
* Added [`[turnstile.isExpired]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#access-a-widgets-state).
* Added `uk` language.
## 2023-05-25
* Added idempotency support for `POST /siteverify` requests via the `idempotency_key` parameter.
## 2023-04-17
* Added references to Turnstile Public API.
* Added references for [`[after-interactive-callback]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#explicitly-render-the-turnstile-widget), [`[before-interactive-callback]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#explicitly-render-the-turnstile-widget), and [`[unsupported-callback]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#explicitly-render-the-turnstile-widget).
## 2023-03-06
* Added [`[execution]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#explicitly-render-the-turnstile-widget) and [`[appearance]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#explicitly-render-the-turnstile-widget).
## 2023-02-15
* Added the [`[turnstile.ready]`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#explicitly-render-the-turnstile-widget) callback.
## 2023-02-01
* Added the [`[data-]language`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#configurations) parameter.
## 2022-12-12
* [`POST /siteverify`](https://developers.cloudflare.com/turnstile/get-started/server-side-validation/) supports JSON requests now.
## 2022-11-11
* Added [`retry` and `retry-interval`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#configurations) for controlling retry behavior.
## 2022-10-28
* Renamed the `[data-]expired-callback` callback to [`[data-]timeout-callback`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#configurations) (called when the challenge times out).
* Added the [`[data-]expired-callback`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#configurations) callback (called when the token expires).
## 2022-10-24
* Added [`response-field` and `response-field-name`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#configurations) for controlling the input element created by Turnstile.
* Added option for changing the [size of the Turnstile widget](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#widget-size).
## 2022-10-13
* Added validation for action: `/^[a-z0-9_-]{0,32}$/i`
* Added validation for cData: `/^[a-z0-9_-]{0,255}$/i`
## 2022-10-11
* Added [`turnstile.remove`](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/#remove-a-widget)
</page>
<page>
---
title: Community resources · Cloudflare Turnstile docs
description: Community resources for our customers to help them integrate Turnstile.
lastUpdated: 2025-12-18T17:16:11.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/community-resources/
md: https://developers.cloudflare.com/turnstile/community-resources/index.md
---
Community resources for our customers to help them integrate Turnstile.
Warning
These resources are made by the **community** and not maintained directly by Cloudflare.
As such, Cloudflare is not liable for any damages arising from using them.
Note
Did we miss your library? [Contribute to our list](https://developers.cloudflare.com/style-guide/contributions/)
## Client-side rendering libraries
Libraries that only support the client-side rendering of Turnstile:
* React
* [react-turnstile](https://www.npmjs.com/package/react-turnstile)
* [@marsidev/react-turnstile](https://www.npmjs.com/package/@marsidev/react-turnstile)
Note
Cloudflare recommends [@marsidev/react-turnstile](https://www.npmjs.com/package/@marsidev/react-turnstile) when rendering Turnstile. We have deployed an implementation of the library and can confirm that it is safe to use and works as expected.
* Vue
* [vue-cloudflare-turnstile](https://www.npmjs.com/package/vue-cloudflare-turnstile)
* [cfturnstile-vue3](https://www.npmjs.com/package/cfturnstile-vue3)
* [vue-turnstile](https://www.npmjs.com/package/vue-turnstile)
* [Angular](https://www.npmjs.com/package/ngx-turnstile)
* Svelte
* [svelte-turnstile](https://www.npmjs.com/package/svelte-turnstile)
* [@battlefieldduck/turnstile-svelte](https://www.npmjs.com/package/@battlefieldduck/turnstile-svelte)
## Server-side validation libraries
Libraries that only support the server-side validation of Turnstile:
* [fastify-cloudflare-turnstile](https://www.npmjs.com/package/fastify-cloudflare-turnstile)
## Full-stack libraries
Libraries that both support the both client-side rendering and server-side validation of Turnstile:
* [Nuxt](https://www.npmjs.com/package/@nuxtjs/turnstile)
* [Laravel](https://github.com/romanzipp/Laravel-Turnstile)
* [Phoenix](https://github.com/jsonmaur/phoenix-turnstile)
## Integrations
Turnstile integrations for popular content management systems:
* [Craft CMS](https://plugins.craftcms.com/turnstile)
* [Google Forms](https://github.com/ModMalwareInvestigation/turnstile-for-forms)
* [SilverStripe](https://github.com/webbuilders-group/silverstripe-turnstile)
* [Statamic](https://statamic.com/addons/aryeh-raber/captcha)
* [WordPress](https://wordpress.org/plugins/simple-cloudflare-turnstile)
## Other
Other resources related to integrating Turnstile:
### TypeScript definitions
* [turnstile-types](https://www.npmjs.com/package/turnstile-types)
* [@types/cloudflare-turnstile](https://www.npmjs.com/package/@types/cloudflare-turnstile)
### Widget management
* [Cloudflare.NET](https://github.com/Alos-no/Cloudflare.NET) (C#/.NET)
### Additional support
* [Cloudflare Community](https://community.cloudflare.com/c/website-application-performance/turnstile/83)
* [Cloudflare Developers Discord server](https://discord.com/channels/595317990191398933/1025131875397812224)
</page>
<page>
---
title: Concepts · Cloudflare Turnstile docs
description: "Refer to the following pages for more information about Turnstile's concepts:"
lastUpdated: 2025-08-13T20:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/turnstile/concepts/
md: https://developers.cloudflare.com/turnstile/concepts/index.md
---
Refer to the following pages for more information about Turnstile's concepts:
* [Turnstile widgets](https://developers.cloudflare.com/turnstile/concepts/widget/)
* [Cloudflare Challenges](https://developers.cloudflare.com/cloudflare-challenges/)
</page>
<page>
---
title: Extensions · Cloudflare Turnstile docs
description: "Refer to the following pages for more information about Turnstile extensions:"
lastUpdated: 2025-08-13T20:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/turnstile/extensions/
md: https://developers.cloudflare.com/turnstile/extensions/index.md
---
Refer to the following pages for more information about Turnstile extensions:
* [Pages Plugin](https://developers.cloudflare.com/pages/functions/plugins/turnstile/)
* [Implement Turnstile with Google Firebase](https://developers.cloudflare.com/turnstile/extensions/google-firebase/)
* [Waiting Room Analytics](https://developers.cloudflare.com/waiting-room/waiting-room-analytics/#turnstile-widget-traffic)
</page>
<page>
---
title: Get started · Cloudflare Turnstile docs
description: This guide will get you started on setting up the Turnstile widget
to protect your website from bots while maintaining a seamless user
experience.
lastUpdated: 2025-12-22T18:29:54.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/get-started/
md: https://developers.cloudflare.com/turnstile/get-started/index.md
---
This guide will get you started on setting up the Turnstile widget to protect your website from bots while maintaining a seamless user experience.
## Prerequisites
Before you begin, you must have:
* [A Cloudflare account](https://developers.cloudflare.com/fundamentals/account/create-account/)
* A website or web application to protect
* Basic knowledge of HTML and your preferred server-side language
***
## Process
Turnstile widgets are the foundation of your bot protection implementation.
Each widget gets its own unique sitekey and secret key pair, and options for configurations.
| Component | Description |
| - | - |
| Sitekey | Public key used to invoke the Turnstile widget on your site. |
| Secret key | Private key used for server-side token validation. |
| Configurations | Mode, hostnames, appearance settings, and other options. |
Important
Regardless of how you create and manage your widgets, you will still need to [embed the widget](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/) on your webpage and [validate the token](https://developers.cloudflare.com/turnstile/get-started/server-side-validation/) on your server.
Implementing Turnstile involves two essential components that work together:
1. Client-side: [Embed the widget](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/)
Add the Turnstile widget to your webpage to challenge visitors and generate verification tokens.
2. Server-side: [Validate the token](https://developers.cloudflare.com/turnstile/get-started/server-side-validation/)
Verify the tokens on your server using the Siteverify API to ensure they are authentic and have not been tampered with.
Turnstile is designed to be an independent service. You can use Turnstile on any website, regardless of whether it is proxied through the Cloudflare network. This allows for flexible deployment across multi-cloud environments, on-premises infrastructure, or sites using other CDNs. The client-side widget and server-side validation steps are completely self-contained.
Refer to [Implementation](#implementation) below for guidance on how to implement Turnstile on your website.
***
## Implementation
Follow the steps below to implement Turnstile.
### 1. Create your widget
First, you must create a Turnstile widget to get your sitekey and secret key.
Select your preferred implementation method:
[Cloudflare dashboard ](https://developers.cloudflare.com/turnstile/get-started/widget-management/dashboard/)[API ](https://developers.cloudflare.com/turnstile/get-started/widget-management/api/)[Terraform](https://developers.cloudflare.com/turnstile/get-started/widget-management/terraform/)
### 2. Embed the widget
Add the Turnstile widget to your webpage forms and applications.
Refer to [Embed the widget](https://developers.cloudflare.com/turnstile/get-started/client-side-rendering/) to learn more about implicit and explicit rendering methods.
Testing
You can test your Turnstile widget on your webpage without triggering an actual Cloudflare Challenge by using a testing sitekey.
Refer to [Testing](https://developers.cloudflare.com/turnstile/troubleshooting/testing/) for more information.
### 3. Validate tokens
Implement server-side validation to verify the tokens generated by your widgets.
Refer to [Validate the token](https://developers.cloudflare.com/turnstile/get-started/server-side-validation/) to secure your implementation with proper token verification.
Testing
You can test the dummy token generated with testing sitekey via Siteverify API with the testing secret key. Your production secret keys will reject dummy tokens.
Refer to [Testing](https://developers.cloudflare.com/turnstile/troubleshooting/testing/) for more information.
## Additional implementation options
### Mobile configuration
Special considerations are necessary for mobile applications and WebView implementations.
Refer to [Mobile implementation](https://developers.cloudflare.com/turnstile/get-started/mobile-implementation/) for more information on mobile application integration.
### Migration from other CAPTCHAs
If you are currently using reCAPTCHA, hCaptcha, or another CAPTCHA service, Turnstile can be a drop-in replacement. You can copy and paste our script wherever you have deployed the existing script today.
Refer to [Migration](https://developers.cloudflare.com/turnstile/migration/) for step-by-step migration guidance from other CAPTCHA services.
***
## Security requirements
* Server-side validation is mandatory. It is critical to enforce Turnstile tokens with the Siteverify API. The Turnstile token could be invalid, expired, or already redeemed. Not verifying the token will leave major vulnerabilities in your implementation. You must call Siteverify to complete your Turnstile configuration. Otherwise, it is incomplete and will result in zeroes for token validation when viewing your metrics in [Turnstile Analytics](https://developers.cloudflare.com/turnstile/turnstile-analytics/).
* Tokens expire after 300 seconds (5 minutes). Each token can only be validated once. Expired or used tokens must be replaced with fresh challenges.
***
## Best practices
### Security
* Protect your secret keys. Never expose secret keys in client-side code.
* Rotate your keys regularly. Use API or dashboard to rotate secret keys periodically.
* Restrict your hostnames. Only allow widgets on domains that you control.
* Monitor the usage. Use analytics to detect unusual patterns.
### Operational
* Use descriptive names. Name widgets based on their purpose, such as "Login Form" or "Contact Page".
* Separate your environments. Use different widgets for development, staging, and production.
* Keep track of which widgets are used at which locations.
* Store your widget configurations in version control when using Terraform.
</page>
<page>
---
title: Migration · Cloudflare Turnstile docs
description: If you are using alternative CAPTCHA services, you can switch to
Cloudflare Turnstile using the guides below to assist with the upgrade
process.
lastUpdated: 2025-08-13T20:53:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/migration/
md: https://developers.cloudflare.com/turnstile/migration/index.md
---
If you are using alternative CAPTCHA services, you can switch to Cloudflare Turnstile using the guides below to assist with the upgrade process.
[Get started with Turnstile](https://developers.cloudflare.com/turnstile/get-started/) if there is no guide available yet.
## Guides
* [reCAPTCHA](https://developers.cloudflare.com/turnstile/migration/recaptcha/)
* [hCAPTCHA](https://developers.cloudflare.com/turnstile/migration/hcaptcha/)
</page>
<page>
---
title: Cloudflare Turnstile plans · Cloudflare Turnstile docs
description: "Cloudflare Turnstile is available on the following plans:"
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/plans/
md: https://developers.cloudflare.com/turnstile/plans/index.md
---
Cloudflare Turnstile is available on the following plans:
Free plan
The Free plan is best for:
* Personal websites and blogs
* Small to medium businesses
* Development and testing environments
* Most production applications
Enterprise plan
The Enterprise plan is best for:
* Large enterprises with high-volume traffic
* Organizations requiring advanced bot detection and device fingerprinting
* Organizations requiring custom branding, companies with strict compliance requirements
* Multi-domain or complex hosting environments
| | Free | Enterprise |
| - | - | - |
| Pricing | Free | Contact Sales |
| Number of widgets | Up to 20 widgets | Unlimited |
| All widget types | Yes | Yes |
| Unlimited challenges (traffic or verification requests) | Yes | Yes |
| Hostname management | 10 hostnames per widget | Maximum of 200 hostnames per widget |
| Any hostname widget (no preconfigured hostnames) | No | Yes |
| Analytics lookback | 7 days maximum | 30 days maximum |
| Pre-clearance support | Yes | Yes |
| Ephemeral IDs | No | Yes |
| Offlabel (remove Cloudflare branding) | No | Yes |
| WCAG 2.1 AA compliance | Yes | Yes |
| Community support | Yes | Yes |
Notes
* If you upgrade from Free to Enterprise, your existing widgets and configurations will be preserved during the upgrade process.
* Free users are limited to 20 widgets per account. Customers with Enterprise Bot Management and Enterprise Turnstile can have this limit increased. Contact your account team to discuss your requirements.
* Turnstile can be used independently without requiring other Cloudflare services.
</page>
<page>
---
title: Reference · Cloudflare Turnstile docs
description: "Refer to the following pages for more information about Turnstile:"
lastUpdated: 2025-08-13T20:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/turnstile/reference/
md: https://developers.cloudflare.com/turnstile/reference/index.md
---
Refer to the following pages for more information about Turnstile:
* [Content Security Policy](https://developers.cloudflare.com/turnstile/reference/content-security-policy/)
* [Turnstile Privacy Addendum](https://www.cloudflare.com/turnstile-privacy-policy/)
* [Supported languages](https://developers.cloudflare.com/turnstile/reference/supported-languages/)
* [Supported browsers](https://developers.cloudflare.com/cloudflare-challenges/reference/supported-browsers/)
</page>
<page>
---
title: Troubleshooting · Cloudflare Turnstile docs
description: "Refer to the following pages for more information about
troubleshooting Turnstile:"
lastUpdated: 2025-08-13T20:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/turnstile/troubleshooting/
md: https://developers.cloudflare.com/turnstile/troubleshooting/index.md
---
Refer to the following pages for more information about troubleshooting Turnstile:
* [Test your Turnstile implementation](https://developers.cloudflare.com/turnstile/troubleshooting/testing/)
* [Rotate secret key](https://developers.cloudflare.com/turnstile/troubleshooting/rotate-secret-key/)
* [Client-side errors](https://developers.cloudflare.com/turnstile/troubleshooting/client-side-errors/)
* [Challenge solve issues](https://developers.cloudflare.com/cloudflare-challenges/troubleshooting/challenge-solve-issues/)
* [Feedback reports](https://developers.cloudflare.com/turnstile/troubleshooting/feedback-reports/)
</page>
<page>
---
title: Turnstile Analytics · Cloudflare Turnstile docs
description: Use Turnstile Analytics to view the number of challenges issued,
the challenge solve rate, and the metrics of issued challenges.
lastUpdated: 2025-09-04T15:24:34.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/turnstile-analytics/
md: https://developers.cloudflare.com/turnstile/turnstile-analytics/index.md
---
Turnstile Analytics provides you with a view of the top widget statistics across different metadata dimensions to understand where your traffic is coming from, which environments have the highest challenge activity, and whether certain sources are disproportionately failing or bypassing challenges, allowing you to fine-tune your security settings, apply more granular mitigations, and proactively respond to evolving threats.
## Available statistics
* **Top Hostnames**: If the Turnstile widget is placed across multiple hostnames, this will display the highest traffic hostnames where challenges are being issued.
* **Top Browsers**: A breakdown of browsers that are most commonly encountering Turnstile challenges, helping customers spot trends in visitor traffic.
* **Top Countries**: View the top originating countries for visitors completing challenges, which can help identify regional traffic anomalies.
* **Top User Agents**: Identify which user agents are generating the most Turnstile challenge requests.
* [**Top ASNs**](https://cloudflare.com/learning/network-layer/what-is-an-autonomous-system): Displays the highest volume of challenges issued from specific Autonomous System Numbers (ASNs), helping customers detect potential bot activity.
* **Top Operating Systems**: Shows which operating systems are most common among visitors passing or failing challenges.
* [**Top Source IPs**](https://cloudflare.com/learning/ddos/glossary/ip-spoofing): Identify the highest-volume IP addresses issuing Turnstile challenges, which can be useful in identifying attack sources or repeated challenge failures.
## View widget metrics
To see an overview of your widget analytics:
[Go to **Turnstile** ](https://dash.cloudflare.com/?to=/:account/turnstile)
The metrics show changes in the solve rate, widget traffic, and top actions for your widget.
Refer to the pages below for more information about Turnstile Analytics:
* [Challenge outcome](https://developers.cloudflare.com/turnstile/turnstile-analytics/challenge-outcomes/)
* [Token validation](https://developers.cloudflare.com/turnstile/turnstile-analytics/token-validation/)
</page>
<page>
---
title: Tutorials · Cloudflare Turnstile docs
description: View tutorials to help you get started with Turnstile.
lastUpdated: 2025-10-31T11:34:53.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/turnstile/tutorials/
md: https://developers.cloudflare.com/turnstile/tutorials/index.md
---
View tutorials to help you get started with Turnstile.
| Name | Last Updated | Difficulty |
| - | - | - |
| [Fraud detection with Ephemeral IDs](https://developers.cloudflare.com/turnstile/tutorials/fraud-detection-with-ephemeral-ids/) | 27 days ago | Advanced |
| [Protect your forms](https://developers.cloudflare.com/turnstile/tutorials/login-pages/) | 8 months ago | Beginner |
| [Conditionally enforce Turnstile](https://developers.cloudflare.com/turnstile/tutorials/conditionally-enforcing-turnstile/) | 10 months ago | Intermediate |
| [Exclude Turnstile from E2E tests](https://developers.cloudflare.com/turnstile/tutorials/excluding-turnstile-from-e2e-tests/) | about 1 year ago | Intermediate |
| [Integrate Turnstile, WAF, & Bot Management](https://developers.cloudflare.com/turnstile/tutorials/integrating-turnstile-waf-and-bot-management/) | over 1 year ago | Beginner |
## Demo
Learn how you can use Turnstile within your existing application.
Explore the following demo applications for Turnstile.
* [Turnstile Demo:](https://github.com/cloudflare/turnstile-demo-workers) A simple demo with a Turnstile-protected form, using Cloudflare Workers. With the code in this repository, we demonstrate implicit rendering and explicit rendering.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare use cases
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/use-cases/404/
md: https://developers.cloudflare.com/use-cases/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Build AI Applications · Use cases · Cloudflare use cases
description: Build and deploy ambitious AI applications to Cloudflare's global network.
lastUpdated: 2025-08-19T11:42:14.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/use-cases/ai/
md: https://developers.cloudflare.com/use-cases/ai/index.md
---
Build and deploy ambitious AI applications to Cloudflare's global network.
## Reference architectures
Diagrams, design patterns, and detailed best practices to help you generate solutions with Cloudflare products.
[Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[You can connect a Cloudflare Worker to get data from Google BigQuery and pass it to Workers AI, to run AI Models, powered by serverless GPUs.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[Multi-vendor AI observability and control](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-multivendor-observability-control/)
[By shifting features such as rate limiting, caching, and error handling to the proxy layer, organizations can apply unified configurations across services and inference service providers.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-multivendor-observability-control/)
[Composable AI architecture](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[The architecture diagram illustrates how AI applications can be built end-to-end on Cloudflare, or single services can be integrated with external infrastructure and services.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[Content-based asset creation](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-asset-creation/)
[AI systems combine text-generation and text-to-image models to create visual content from text. They generate prompts, moderate content, and produce images for various applications.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-asset-creation/)
[Retrieval Augmented Generation (RAG)](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
[RAG combines retrieval with generative models for better text. It uses external knowledge to create factual, relevant responses, improving coherence and accuracy in NLP tasks like chatbots.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
[Automatic captioning for video uploads](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-video-caption/)
[By integrating automatic speech recognition technology into video platforms, content creators, publishers, and distributors can reach a broader audience, including individuals with hearing impairments or those who prefer to consume content in different languages.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-video-caption/)
## Demo apps
## Tutorials
Step-by-step guides to help you build and learn.
[Create and secure an AI agent wrapper using AI Gateway and Zero Trust](https://developers.cloudflare.com/cloudflare-one/tutorials/ai-wrapper-tenant-control/)
[This tutorial explains how to use Cloudflare AI Gateway and Zero Trust to create a functional and secure website wrapper for an AI agent.](https://developers.cloudflare.com/cloudflare-one/tutorials/ai-wrapper-tenant-control/)
[Whisper-large-v3-turbo with Cloudflare Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-workers-ai-whisper-with-chunking/)
[Learn how to transcribe large audio files using Workers AI.](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-workers-ai-whisper-with-chunking/)
[Llama 3.2 11B Vision Instruct model on Cloudflare Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/llama-vision-tutorial/)
[Learn how to use the Llama 3.2 11B Vision Instruct model on Cloudflare Workers AI.](https://developers.cloudflare.com/workers-ai/guides/tutorials/llama-vision-tutorial/)
[Store and Catalog AI Generated Images with R2 (Part 3)](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-store-and-catalog/)
[In the final part of the AI Image Playground series, Kristian teaches how to utilize Cloudflare's R2 object storage.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-store-and-catalog/)
[Build a Retrieval Augmented Generation (RAG) AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-retrieval-augmented-generation-ai/)
[Build your first AI app with Cloudflare AI. This guide uses Workers AI, Vectorize, D1, and Cloudflare Workers.](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-retrieval-augmented-generation-ai/)
[Using BigQuery with Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/using-bigquery-with-workers-ai/)
[Learn how to ingest data stored outside of Cloudflare as an input to Workers AI models.](https://developers.cloudflare.com/workers-ai/guides/tutorials/using-bigquery-with-workers-ai/)
[Add New AI Models to your Playground (Part 2)](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux-newmodels/)
[In part 2, Kristian expands upon the existing environment built in part 1, by showing you how to integrate new AI models and introduce new parameters that allow you to customize how images are generated.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux-newmodels/)
[Build an AI Image Generator Playground (Part 1)](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux/)
[The new flux models on Workers AI are our most powerful text-to-image AI models yet. Using Workers AI, you can get access to the best models in the industry without having to worry about inference, ops, or deployment.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/image-generator-flux/)
[How to Build an Image Generator using Workers AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/)
[Learn how to build an image generator using Workers AI.](https://developers.cloudflare.com/workers-ai/guides/tutorials/image-generation-playground/)
[Explore Workers AI Models Using a Jupyter Notebook](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-workers-ai-models-using-a-jupyter-notebook/)
[This Jupyter notebook explores various models (including Whisper, Distilled BERT, LLaVA, and Meta Llama 3) using Python and the requests library.](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-workers-ai-models-using-a-jupyter-notebook/)
[Create a fine-tuned OpenAI model with R2](https://developers.cloudflare.com/workers/tutorials/create-finetuned-chatgpt-ai-models-with-r2/)
[In this tutorial, you will use the OpenAI API and Cloudflare R2 to create a fine-tuned model.](https://developers.cloudflare.com/workers/tutorials/create-finetuned-chatgpt-ai-models-with-r2/)
[Fine Tune Models With AutoTrain from HuggingFace](https://developers.cloudflare.com/workers-ai/guides/tutorials/fine-tune-models-with-autotrain/)
[Fine-tuning AI models with LoRA adapters on Workers AI allows adding custom training data, like for LLM finetuning.](https://developers.cloudflare.com/workers-ai/guides/tutorials/fine-tune-models-with-autotrain/)
[Explore Code Generation Using DeepSeek Coder Models](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-code-generation-using-deepseek-coder-models/)
[Explore how you can use AI models to generate code and work more efficiently.](https://developers.cloudflare.com/workers-ai/guides/tutorials/explore-code-generation-using-deepseek-coder-models/)
[Choose the Right Text Generation Model](https://developers.cloudflare.com/workers-ai/guides/tutorials/how-to-choose-the-right-text-generation-model/)
[There's a wide range of text generation models available through Workers AI. In an effort to aid you in your journey of finding the right model, this notebook will help you get to know your options in a speed dating type of scenario.](https://developers.cloudflare.com/workers-ai/guides/tutorials/how-to-choose-the-right-text-generation-model/)
[Deploy a Worker that connects to OpenAI via AI Gateway](https://developers.cloudflare.com/ai-gateway/tutorials/deploy-aig-worker/)
[Learn how to deploy a Worker that makes calls to OpenAI through AI Gateway](https://developers.cloudflare.com/ai-gateway/tutorials/deploy-aig-worker/)
[OpenAI GPT function calling with JavaScript and Cloudflare Workers](https://developers.cloudflare.com/workers/tutorials/openai-function-calls-workers/)
[Build a project that leverages OpenAI's function calling feature, available in OpenAI's latest Chat Completions API models.](https://developers.cloudflare.com/workers/tutorials/openai-function-calls-workers/)
## Customer spotlights
Explore case studies on [AI companies building on Cloudflare](https://workers.cloudflare.com/built-with/collections/ai-workers/).
## Code examples
Examples ready to copy and paste.
[Use fetch() handler](https://developers.cloudflare.com/workers-ai/features/function-calling/embedded/examples/fetch/)
[Learn how to use the fetch() handler in Cloudflare Workers AI to enable LLMs to perform API calls, like retrieving a 5-day weather forecast using function calling.](https://developers.cloudflare.com/workers-ai/features/function-calling/embedded/examples/fetch/)
[Stream OpenAI API Responses](https://developers.cloudflare.com/workers/examples/openai-sdk-streaming/)
[Use the OpenAI v4 SDK to stream responses from OpenAI.](https://developers.cloudflare.com/workers/examples/openai-sdk-streaming/)
Note
Cloudflare also offers detailed code examples for various [AI models](https://developers.cloudflare.com/workers-ai/models/) and [Model providers](https://developers.cloudflare.com/ai-gateway/usage/providers/).
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Vectorize docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/vectorize/404/
md: https://developers.cloudflare.com/vectorize/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Best practices · Cloudflare Vectorize docs
lastUpdated: 2025-02-21T09:48:48.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/vectorize/best-practices/
md: https://developers.cloudflare.com/vectorize/best-practices/index.md
---
* [Create indexes](https://developers.cloudflare.com/vectorize/best-practices/create-indexes/)
* [Insert vectors](https://developers.cloudflare.com/vectorize/best-practices/insert-vectors/)
* [List vectors](https://developers.cloudflare.com/vectorize/best-practices/list-vectors/)
* [Query vectors](https://developers.cloudflare.com/vectorize/best-practices/query-vectors/)
</page>
<page>
---
title: Architectures · Cloudflare Vectorize docs
description: Learn how you can use Vectorize within your existing architecture.
lastUpdated: 2025-10-13T13:40:40.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/vectorize/demos/
md: https://developers.cloudflare.com/vectorize/demos/index.md
---
Learn how you can use Vectorize within your existing architecture.
## Reference architectures
Explore the following reference architectures that use Vectorize:
[Fullstack applications](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[A practical example of how these services come together in a real fullstack application architecture.](https://developers.cloudflare.com/reference-architecture/diagrams/serverless/fullstack-application/)
[Ingesting BigQuery Data into Workers AI](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[You can connect a Cloudflare Worker to get data from Google BigQuery and pass it to Workers AI, to run AI Models, powered by serverless GPUs.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/bigquery-workers-ai/)
[Composable AI architecture](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[The architecture diagram illustrates how AI applications can be built end-to-end on Cloudflare, or single services can be integrated with external infrastructure and services.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-composable/)
[Retrieval Augmented Generation (RAG)](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
[RAG combines retrieval with generative models for better text. It uses external knowledge to create factual, relevant responses, improving coherence and accuracy in NLP tasks like chatbots.](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
</page>
<page>
---
title: Examples · Cloudflare Vectorize docs
description: Explore the following examples for Vectorize.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/vectorize/examples/
md: https://developers.cloudflare.com/vectorize/examples/index.md
---
Explore the following examples for Vectorize.
* [LangChain Integration](https://js.langchain.com/docs/integrations/vectorstores/cloudflare_vectorize/)
* [Retrieval Augmented Generation](https://developers.cloudflare.com/reference-architecture/diagrams/ai/ai-rag/)
* [Agents](https://developers.cloudflare.com/agents/)
</page>
<page>
---
title: Get started · Cloudflare Vectorize docs
lastUpdated: 2025-02-21T09:48:48.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/vectorize/get-started/
md: https://developers.cloudflare.com/vectorize/get-started/index.md
---
* [Introduction to Vectorize](https://developers.cloudflare.com/vectorize/get-started/intro/)
* [Vectorize and Workers AI](https://developers.cloudflare.com/vectorize/get-started/embeddings/)
</page>
<page>
---
title: Platform · Cloudflare Vectorize docs
lastUpdated: 2025-02-21T09:48:48.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/vectorize/platform/
md: https://developers.cloudflare.com/vectorize/platform/index.md
---
* [Pricing](https://developers.cloudflare.com/vectorize/platform/pricing/)
* [Limits](https://developers.cloudflare.com/vectorize/platform/limits/)
* [Choose a data or storage product](https://developers.cloudflare.com/workers/platform/storage-options/)
* [Changelog](https://developers.cloudflare.com/vectorize/platform/changelog/)
* [Event subscriptions](https://developers.cloudflare.com/vectorize/platform/event-subscriptions/)
</page>
<page>
---
title: Reference · Cloudflare Vectorize docs
lastUpdated: 2025-02-21T09:48:48.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/vectorize/reference/
md: https://developers.cloudflare.com/vectorize/reference/index.md
---
* [Vector databases](https://developers.cloudflare.com/vectorize/reference/what-is-a-vector-database/)
* [Vectorize API](https://developers.cloudflare.com/vectorize/reference/client-api/)
* [Metadata filtering](https://developers.cloudflare.com/vectorize/reference/metadata-filtering/)
* [Transition legacy Vectorize indexes](https://developers.cloudflare.com/vectorize/reference/transition-vectorize-legacy/)
* [Wrangler commands](https://developers.cloudflare.com/vectorize/reference/wrangler-commands/)
</page>
<page>
---
title: Tutorials · Cloudflare Vectorize docs
description: View tutorials to help you get started with Vectorize.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/vectorize/tutorials/
md: https://developers.cloudflare.com/vectorize/tutorials/index.md
---
View tutorials to help you get started with Vectorize.
## Docs
| Name | Last Updated | Difficulty |
| - | - | - |
| [Build a Retrieval Augmented Generation (RAG) AI](https://developers.cloudflare.com/workers-ai/guides/tutorials/build-a-retrieval-augmented-generation-ai/) | about 1 year ago | Beginner |
## Videos
Welcome to the Cloudflare Developer Channel
Welcome to the Cloudflare Developers YouTube channel. We've got tutorials and working demos and everything you need to level up your projects. Whether you're working on your next big thing or just dorking around with some side projects, we've got you covered! So why don't you come hang out, subscribe to our developer channel and together we'll build something awesome. You're gonna love it.
Use Vectorize to add additional context to your AI Applications through RAG
A RAG based AI Chat app that uses Vectorize to access video game data for employees of Gamertown.
Learn AI Development (models, embeddings, vectors)
In this workshop, Kristian Freeman, Cloudflare Developer Advocate, teaches the basics of AI Development - models, embeddings, and vectors (including vector databases).
</page>
<page>
---
title: Vectorize REST API · Cloudflare Vectorize docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/vectorize/vectorize-api/
md: https://developers.cloudflare.com/vectorize/vectorize-api/index.md
---
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Version Management docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/version-management/404/
md: https://developers.cloudflare.com/version-management/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: About · Cloudflare Version Management docs
description: Version Management works through a combination of environments and versions.
lastUpdated: 2025-08-20T18:25:25.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/version-management/about/
md: https://developers.cloudflare.com/version-management/about/index.md
---
Version Management works through a combination of **environments** and **versions**.
```mermaid
stateDiagram-v2
V2: Version 2
V22: Version 2 <br/>(applied manually)
V23: Version 2 <br/>(promoted from Development)
V24: Version 2 <br/>(promoted from Staging)
Revert: Production (rollback)
V1: Version 1 <br/>(rolled back due to issues)
V2 --> Development
Development --> Staging
Staging --> Production
Production --> Revert
state Development {
V22
}
note right of Development
At each level, test then promote the version.
end note
state Staging {
V23
}
state Production {
V24
}
state Revert {
V1
}
note right of Revert
Once promoted into an environment, a version can be rolled back.
end note
```
## Environments
An environment is a place to test different versions of your zone configurations.
After you [enable](https://developers.cloudflare.com/version-management/how-to/enable/) version management, you will have the ability to create default environments:
* **Development**: Meant to validate that changes work correctly. The default [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/) are that the `cf.zone.name` matches your zone name, the `Edge Server IP` is a specific value, and the request contains a cookie with `development=true`.
* **Staging**: Meant to test changes before sending them to **Production**. The default [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/) are that the `cf.zone.name` matches your zone name and the `Edge Server IP` is a specific value.
* **Production**: Meant to hold all configurations applied to your zone. You cannot edit the [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/) - which are just that the `cf.zone.name` is equal to your zone's name - and cannot delete this environment. This environment has a read-only check enabled, so versions promoted to this environment will become read-only as well.
When you [create](https://developers.cloudflare.com/version-management/how-to/versions/#create-version) a new version, that version will be available to apply to your **Development** environment (or whatever environment has the lowest rank). Once you test a version in your **Development** environment, you would promote that version to the **Staging** environment and - with no issues - then promote it to **Production**.
To send traffic to specific environments, send requests to that environment that match the pattern specified in its [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/).
## Versions
A version is a collection of configurations related to your zone, such as WAF custom rules and [other optimization configurations](https://developers.cloudflare.com/version-management/reference/available-configurations/).
Once you [enable](https://developers.cloudflare.com/version-management/how-to/enable/) Version Management, Cloudflare will automatically create:
* **Version Zero**, think about this as the configuration of your current zone. Once default environments are created, Version Zero is automatically deployed to them, guaranteeing no disruption in your live traffic. This Version is also permanently editable. In case you decide to disable Zone Versioning, Version Zero will become your zone again.
* **Global Configuration**, you can find all the configurations here that are not supported by Version Management.
Important
Any changes made to the **Global Configuration** will immediately apply to your zone and all versions of your zone, affecting live traffic.
On the Environments page, you can create default environments for **Production**, **Staging**, and **Development**.
When your version is ready, you would then test and promote it through various environments until it reaches **Production** (or whatever your final environment is).
You can create a new version at any time by choosing to [**Clone**](https://developers.cloudflare.com/version-management/how-to/versions/#create-version) an existing version, which automatically copies over configurations from an existing version.
Version configurations are applied to zone traffic when you [promote a version](https://developers.cloudflare.com/version-management/how-to/environments/#promote-a-version) to a new environment and then send traffic to that environment that matches the pattern specified in its [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/).
</page>
<page>
---
title: Changelog · Cloudflare Version Management docs
description: Subscribe to RSS
lastUpdated: 2025-02-13T19:35:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/version-management/changelog/
md: https://developers.cloudflare.com/version-management/changelog/index.md
---
[Subscribe to RSS](https://developers.cloudflare.com/version-management/changelog/index.xml)
## 2024-02-26
**Support for API Shield**
* [API Shield](https://developers.cloudflare.com/api-shield/) no longer prevents Version Management enablement and zone settings configurations.
## 2023-09-20
**Support for Bot Management**
* Version Management now supports versioning for [Bot Management](https://developers.cloudflare.com/bots/plans/bm-subscription/).
</page>
<page>
---
title: Get started · Cloudflare Version Management docs
description: "\tLearn how to enable Version Management in the Cloudflare dashboard."
lastUpdated: 2025-10-09T15:47:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/version-management/get-started/
md: https://developers.cloudflare.com/version-management/get-started/index.md
---
Follow this tutorial to start testing and deploying zone configuration changes with Version Management.
## Enable versioning
By default, Version Management is not enabled on a zone.
To enable [Version Management](https://dash.cloudflare.com/?to=/:account/:zone/versioning):
1. Log in to the Cloudflare dashboard.
[Go to **Account home**](https://dash.cloudflare.com/?to=/:account/home)
2. Select your account and zone.
3. Go to **Version Management**.
4. Select **Enable versioning**.
Note
If you cannot enable Version Management, make sure your zone, account, and user meet the [requirements](https://developers.cloudflare.com/version-management/#requirements).
## (Optional) Create additional environments
Once you [enable](https://developers.cloudflare.com/version-management/how-to/enable/) Version Management, Cloudflare will automatically create:
* **Version Zero**, think about this as the configuration of your current zone. Once default environments are created, Version Zero is automatically deployed to them, guaranteeing no disruption in your live traffic. This Version is also permanently editable. In case you decide to disable Zone Versioning, Version Zero will become your zone again.
* **Global Configuration**, you can find all the configurations here that are not supported by Version Management.
Important
Any changes made to the **Global Configuration** will immediately apply to your zone and all versions of your zone, affecting live traffic.
On the Environments page, you can create default environments for **Production**, **Staging**, and **Development**.
These environments each serve a specific purpose and are accessed differently:
* **Development**: Meant to validate that changes work correctly. The default [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/) are that the `cf.zone.name` matches your zone name, the `Edge Server IP` is a specific value, and the request contains a cookie with `development=true`.
* **Staging**: Meant to test changes before sending them to **Production**. The default [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/) are that the `cf.zone.name` matches your zone name and the `Edge Server IP` is a specific value.
* **Production**: Meant to hold all configurations applied to your zone. You cannot edit the [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/) - which are just that the `cf.zone.name` is equal to your zone's name - and cannot delete this environment. This environment has a read-only check enabled, so versions promoted to this environment will become read-only as well.
Based on your organization's needs, you may need to create additional environments to test and roll out changes.
For more details, refer to [Create environment](https://developers.cloudflare.com/version-management/how-to/environments/#create-environment).
## Update configurations
Before making changes, make sure you are inside the correct version of your zone.
To change between different versions of your zone:
1. Log in to the Cloudflare dashboard.
[Go to **Account home**](https://dash.cloudflare.com/?to=/:account/home)
2. Select your account and a domain that has version management. The Global Configuration of your domain will load.
3. Go to the product or feature you wish to modify.
* **If the product or feature is available for versioning**: The last version you were working on will load.
* **If the product or feature is NOT available for versioning**: Your Global Configuration will load, and any changes you make will impact live traffic.
4. Ensure that the configuration or version displayed in the domain summary bar is the one you would like to work on. If not, select the version in the domain summary bar to open the version switcher.
Note
If you are on a product that is not available for versioning, you will not be able to switch to another version, and can only make changes under your Global Configuration.
The Domain Summary is accessible from all pages and allows you to quickly switch between versions and domains.
From within a version, you can update configurations just as you would with your normal zone configurations. Any changes are saved automatically.
## Test version
Once you have made changes to a version, apply that version to your lowest-ranked environment.
1. Log in to the Cloudflare dashboard.
[Go to **Account home**](https://dash.cloudflare.com/?to=/:account/home)
2. Select your account and zone.
3. Go to **Version Management**.
4. Go to **Environments**.
5. On your lowest-ranked environment, use the **Version** dropdown to select your desired version.
To test your version, send requests to that environment that match the pattern specified in its [traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/).
For more details about what happens to these requests, refer to the version's [metrics](https://developers.cloudflare.com/version-management/how-to/versions/#view-metrics).
## Promote version
Next, [promote](https://developers.cloudflare.com/version-management/how-to/environments/#change-environment-version) your version through your different environments.
To promote a version:
1. Log in to the Cloudflare dashboard.
[Go to **Account home**](https://dash.cloudflare.com/?to=/:account/home)
2. Select your account and zone.
3. Go to **Version Management**.
4. Select **Environments**.
5. On the environment in which you tested the version, select **Promote**. This option will only be available if the lower-ranked environment has a different version than the higher-ranked environment.
Promoting a version to a read-only environment will make the version permanently read-only.
After promoting to each environment, test the new version in your new environment.
## Repeat
For new changes to your zone, [create a new version](https://developers.cloudflare.com/version-management/how-to/versions/#create-version) and repeat this process.
## Delete specific version
The versions created in Version Management are immutable and cannot be deleted to ensure that changes are tracked and can be rolled back if needed.
You can, however, create a new version and clone the configuration from the previous version, making any necessary changes before promoting it to your desired environment. This solution allows you to effectively "delete" the old version by no longer using it.
</page>
<page>
---
title: How to · Cloudflare Version Management docs
lastUpdated: 2024-08-27T14:57:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/version-management/how-to/
md: https://developers.cloudflare.com/version-management/how-to/index.md
---
* [Enable](https://developers.cloudflare.com/version-management/how-to/enable/)
* [Manage environments](https://developers.cloudflare.com/version-management/how-to/environments/)
* [Manage versions](https://developers.cloudflare.com/version-management/how-to/versions/)
* [Compare versions](https://developers.cloudflare.com/version-management/how-to/compare-versions/)
</page>
<page>
---
title: Reference · Cloudflare Version Management docs
lastUpdated: 2024-08-27T14:57:59.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/version-management/reference/
md: https://developers.cloudflare.com/version-management/reference/index.md
---
* [Available configurations](https://developers.cloudflare.com/version-management/reference/available-configurations/)
* [Traffic filters](https://developers.cloudflare.com/version-management/reference/traffic-filters/)
* [Read-only environments](https://developers.cloudflare.com/version-management/reference/read-only-environments/)
</page>
<page>
---
title: Application Security - Dashboard walkthrough | Cloudflare Docs
description: In this video, learn how to navigate the Cloudflare Application
Security dashboard and how to use each page to monitor, investigate, and
manage security protections.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/app-sec-dashboard/
md: https://developers.cloudflare.com/videos/app-sec-dashboard/index.md
---
In this video, learn how to navigate the Cloudflare Application Security dashboard and how to use each page to monitor, investigate, and manage security protections.
Transcript
Cloudflare Application Security dashboard for individual domains allows you to manage
application security features that protect the domain from various web attacks and
threats. I'll walk you through the interface,
show you what goes under them and how to use each page to monitor,
investigate, and manage your security protections.
First, select the domain you would like to manage your application security on.
Once you have selected a domain, open up the Application Security dashboard by
clicking security on the navigation bar here.
Now on the overview page.
The Security Overview page gives you a high level summary of your security posture for
this domain. You'll find alerts for Misconfigurations detected threats and
suggested actions on how to improve your security posture.
This is a good place to start and review what needs attention across your environment.
Under analytics, you can analyze security data across two different views traffic and
events. Use this page to understand what kind of traffic your domain is receiving and how
Cloudflare is securing your domain based on the detection tools that are enabled.
This page also serves as a starting point to identify how you may want to configure your
application security settings based on the patterns of traffic you're receiving.
The traffic tab shows data on incoming HTTP requests to your domain,
including ones that have not been affected by any security tools.
The events tab shows data on security actions that have been performed by Cloudflare
Security tools on incoming requests.
Under web assets, you can manage and monitor the security of various types of web related
assets. For example, use the endpoints tab to get recommendations and insights about your
endpoint usage. Use the Schema Validation tab to protect your origin from invalid API
requests and malicious payloads.
Schema validation works by validating requests against your own API schema.
The Client Side Resources tab is used to monitor resources such as scripts,
connections, and cookies that are running on your visitor's web browsers for your domain.
If you notice unexpected scripts or connections on the dashboard.
Check them here for signs of malicious activity.
Security rules is where you manage and define what security actions are.
Perform on incoming requests.
Under the Security Rules tab.
You can manage and create different types of rules to secure your domain.
You can create your own custom security rules from scratch or use predefined templates to
help you get started. Under the DDoS protection tab,
you'll find a DDoS rulesets that mitigate DDoS attacks on your domain.
The DDoS Attack Protection rule sets are automatically managed and updated by
Cloudflare, so you only need to use this tab if you want to create an override rule that
changes how Cloudflare DDoS protection functions.
In settings, you can configure Cloudflare detection tools and your domain security
posture. Security settings and detection tools are categorized by the type of threat
they detect and mitigate.
Use the filters on this page to find detection tools and settings that are
relevant to your security needs.
Thank you for choosing Cloudflare.
For more information, please refer to our developer documentation.
</page>
<page>
---
title: Application Security - Get started guide | Cloudflare Docs
description: In this video, learn how to get immediate protection against the
most common attacks.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/app-sec-get-started/
md: https://developers.cloudflare.com/videos/app-sec-get-started/index.md
---
In this video, learn how to get immediate protection against the most common attacks.
Transcript
Cloudflare Application Security Dashboard allows you to manage application security
features that protect your domains and applications from various web attacks and
threats. In this video, you'll learn how to get immediate protection
against the most common attacks.
Use analytics to monitor and investigate traffic patterns and events.
Handle false positives.
Create custom rules with filters.
Depending on your plan, some functionalities may or may not be
available to you. For more information, visit our developer documentation.
Before you can start reviewing analytics or fine tuning rules,
you need to set up and enable rules that will inspect and mitigate incoming threats.
Let's start by setting up Cloudflare's managed rule set.
This rule set contains multiple rules designed to detect known vulnerabilities and
common attack vectors.
It's updated weekly and also includes emergency patches for zero day threats.
If you're on a free plan, the free managed rule set is already deployed
by default, so you don't have to do anything for this step.
First, log in to the Cloudflare dashboard, select your account and domain and go to
Security Settings. Second, in the Web Application Exploits category,
locate the Cloudflare managed rule set and turn it on.
By enabling this rule set, you immediately get broad protection with low
false positives. Once you've enabled this rule set,
you can go to the analytics page to start understanding how your rules are working.
Keep in mind the system needs time to collect data,
so if you just enable the rule sets, allow some time for incoming traffic to be
analyzed by Cloudflare.
Let's check out analytics page.
There are two different views in analytics.
The traffic tab shows all incoming HTTP requests to your domain,
including ones that aren't mitigated by any security rules.
The events tab only shows requests that triggered a Cloudflare Security action,
such as block, challenge, or lock.
Let's start with the traffic tab.
Here you can identify patterns of traffic through filters like request properties.
Path source, IP action taken, or rule ID.
Let's take a look at an example.
Say that you only want to see only post requests for the login path that contain
leaked credentials. First click Add filter and enter path equals login.
Click apply. Then add the following additional filters HTTP method equals post
leaked credentials. Scan results equals username and password leaked.
Hover on served by origin, then click filter.
Now that you're filtering by requests that have actually reached origin with leaked
credentials, you notice that these requests all come from the same IP address.
The IP address is displayed in the source IP column in sample logs.
Also available in top statistics source IPS.
Let's add that IP to the filters.
Source IP equals to the IP we see here.
Not only can you use filters to analyze specific kinds of requests,
you can also use filters as a starting point for creating your own security rules.
Let's create a rule using the filters we just applied.
This rule will represent a security challenge to post requests that contain leaked
credentials coming from the IP address we specified.
Click Create Custom Security Rule.
A preview side panel will appear.
This preview shows you the beginning of the rule you're building.
We still need to decide what action happens when requests match this rule.
So let's select Configure Rule action.
Now you've been brought to the Rule Builder page under the Security Rule section.
First let's give a rule a name.
Next you'll see that the rule expression contains the filters you just applied in the
analytics page. The rule expression specifies the conditions that must be met for the rule
to run. You can build a rule expression by either using the expression builder or by
manually writing the rule expression.
Now let's select the action we want this rule to perform on matching requests.
Each of the challenge actions use Cloudflare's Challenge platform to verify
whether a visitor to a domain is a real human,
and not a bot or automated script.
An interactive challenge presents visitors with a challenge they need to solve for the
request to be successful.
A JavaScript challenge asks the visitor's web browser to solve a JavaScript based challenge
in the background. Unlike interactive challenges,
this type of challenge does not require interactions from a visitor.
A managed challenge allows Cloudflare to dynamically choose the appropriate type of
challenge to present to a visitor, based on the characteristics of their
requests. Aside from the challenge actions, we can choose block to completely block all
requests that match this rule or skip to skip other rules from a selection of options.
Enterprise accounts also have the option to log requests that match a rule.
These logged requests can then be found in the Security Analytics under the events tab.
In this example, we're going to choose Managed Challenge as the action to take on
requests that match this rule.
Lastly, we can use a Select Order dropdown to select whether to place this rule at the
beginning or end of the execution order.
Rules that match a request are executed in the way they're placed in,
starting from one. If multiple rules match with the request and a preceding rule is a
terminating action, such as a block, no subsequent rules will be performed.
If you want to place this rule in a specific place of the execution order,
we can edit this after we deploy the rule.
Now that we've finished building our rule, select deploy.
Now you're at the Security Rules Overview page where you manage and create custom
security rules. And here's the rule we just created.
If you ever want to edit a rule you created or move its position in the execution order,
just press the three dots to the right of the rule to find these actions.
Occasionally, legitimate requests may also get blocked by rule from a managed rule set
that's created and maintained by Cloudflare.
These are known as false positives.
Let's head back to the analytics page and go to the events tab.
Filter by action block and surface managed rules.
You can adjust the time frame if necessary.
by managed rules, don't just disable the entire rule set.
First, check for common properties between block requests that should be allowed,
such as the same path like login.
Then expand the log details for any of these block requests you'd like to follow and copy
the rule ID. Take note of the managed Rule set name to allow these requests.
To bypass this rule, you can either add an exception to skip the rule for request to a
specific path, or you can configure an override to disable the rule.
Let's see how you would create an exception for specific path in security rules.
Select create rule. Manage rules.
Enter a name for the exception in field we enter URI path in operator equals in value
login. Then select Skip specific rules from a managed rule set and then choose Select
Ruleset for the managed rule you previously identified.
Choose select rules. Search for the rule you want to skip using the rule ID and select it
using the checkbox. Select next.
Review your configuration in rules being skipped and select deploy.
Now let's look at configuring a rule override for that specific rule.
The override will change the rule for all incoming requests.
Select the rule name to open the sidebar, then select view.
In Security rules, select browse rules.
Search for the rule you want to skip using the rule ID you copied.
To disable the rule for all requests, set the status to off.
Select next and then save.
This keeps your overall protection in place while allowing valid traffic through for
known cases. You can now set up application security features to protect your domains and
applications. For more information, please refer to our developer documentation.
</page>
<page>
---
title: China network - CDN global acceleration for Mainland China | Cloudflare Docs
description: In this video, Jess Liu discusses Cloudflares CDN Global
Acceleration (formerly China Express), including solutions for high latency on
dynamic content, accelerating API calls, accessing Cloudflare One services
like WARP and Magic WAN from within mainland China, and securely connecting
private enterprise networks.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/china-network-acceleration/
md: https://developers.cloudflare.com/videos/china-network-acceleration/index.md
---
In this video, Jess Liu discusses Cloudflares CDN Global Acceleration (formerly China Express), including solutions for high latency on dynamic content, accelerating API calls, accessing Cloudflare One services like WARP and Magic WAN from within mainland China, and securely connecting private enterprise networks.
Transcript
In the last video, we discussed that if your origin is outside of mainland China and has
dynamic content that cannot be cashed within China,
your users may still encounter increased latency,
leading to poor user experience.
In this video, we'll go over three main use cases that we can help address dynamic
content outside of mainland China.
Access to global services and private network connectivity.
So depending on your use case, you can choose what best suits your needs.
Hello, I'm Jez from Cloudflare here to teach you about our Cloudflare solutions for
mainland China. If your origin is outside of mainland China and has dynamic content that
cannot be cached within China, CN Global Acceleration,
formerly known as China Express, can help you with this by leveraging
dedicated private tunnels established through our trusted local partners including JD
cloud, CME and CBC tech, we ensure seamless and efficient content
delivery. Here's how it works.
Traffic received from our China Network data centers is routed to our premium data
centers, which have global acceleration privileges that are designed to handle
dynamic traffic with ease.
This includes typical use cases like web API calls,
as well as more complex scenarios such as dynamic traffic management or multi origin
configurations. For example, customers using Cloudflare SaaS features like
Once processed, the traffic is transferred through a partner's dedicated private tunnel
to the global public internet, ensuring high performance and reliability.
Besides accelerating dynamic content, you can also reliably access Cloudflare One
services like Warp, Magic WAN, and travel SIM cards.
With Warp Global acceleration, Warp client can be extended to China for your
users under Pre-signed agreements to access the same Zero Trust Network access services,
just as the rest of your global users, while experiencing stable connectivity
anywhere within China, no matter if you're at home or a coffee shop.
Once you receive our dedicated China IPS through Cloudflare and have Warp setup up,
all you need to do is override the following.
Warp endpoints for each device.
Warp endpoint API endpoint and endpoint.
Verify the colocation center is your desired location under Warp preferences.
And now you should be able to access global services.
As for users who are temporarily in China, we can offer travel SIM cards,
which connect to our Warp client for a seamless and secure mobile acceleration
abroad. By inserting the SIM card or applying the eSIM to an employee's phone,
corporate devices, whether it be laptops or tablets,
can then connect to their organization's Warp client through mobile hotspot.
Lastly, if your goal is to scale and accelerate private enterprise networks from
China, Magic WAN Global Acceleration can help you with that.
You can securely connect to any traffic source,
such as offices and data centers to Cloudflare network,
while configuring routing policies tailored to your corporate networking needs from
China. To extend Magic WAN into China, we provide a customer premises equipment or a
CPE device which will be shipped to your China based location once the CPE is
connected to the internet in your physical location.
Traffic from users who are using the same internet in that location will be routed
through our dedicated private tunnel to any resource or service to make the process
effortless. Our team will help you in configuring the CPE.
To sum up. Our solutions are designed to meet your specific needs and can be selected a la
carte if you need to optimize dynamic data delivery,
whether it's API calls or to integrations or special use cases within a China network
zone. Cdn global acceleration is the ideal choice.
Looking to connect to global services across China with company enforced policies?
Choose Warp Global Acceleration for managing Enterprise networking or accessing global
services from your China based offices.
Magic WAN global acceleration is your go to solution.
Thanks for watching. You can reach out to our sales team to learn more.
</page>
<page>
---
title: China network - How to speed up your web traffic inside mainland China |
Cloudflare Docs
description: In this video, Jess Liu walks us through the main features of
Cloudflares China Network. They cover how the China Network works, including
integrated caching, in-country China name servers, and compliance with ICP
regulations. They also briefly discuss Cloudflare's CDN Global Acceleration
(formerly China Express), an option for accelerating dynamic content that
cannot be cached.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/china-network-inside-china/
md: https://developers.cloudflare.com/videos/china-network-inside-china/index.md
---
In this video, Jess Liu walks us through the main features of Cloudflares China Network. They cover how the China Network works, including integrated caching, in-country China name servers, and compliance with ICP regulations. They also briefly discuss Cloudflare's CDN Global Acceleration (formerly China Express), an option for accelerating dynamic content that cannot be cached.
Transcript
Do you have users in mainland China who are experiencing high latency accessing your
services? Cloudflare China network solution can help you solve this easily.
Hello, I'm Jess from Cloudflare here to teach you about our China network products.
Sometimes when the internet users in mainland China visit your website on Cloudflare global
network. They are connected to data centers outside of mainland China,
and these longer distances will lead to high latency and low availability,
creating a slow and poor user experience.
We can speed up these web services easily with Cloudflare China network solution,
How first Cloudflare China network provides caching in mainland China through our partner
This means for your users in mainland China, their requests will go to the nearest data
center inside of mainland China instead of any external Cloudflare data center.
Shorter distance means faster content delivery.
These data centers are fully integrated with Cloudflare global network.
You'll have access to the same configuration tools for cache WAF origin rules and other
settings, all within a single dashboard.
The same goes for name servers in Mainland China.
If the majority of your users are located within Mainland China,
we offer the option of an Inchina name server that will help speed up DNS resolution.
Second, the China network is designed to follow mainland China's ICP regulations.
This means we can guarantee your web service will always remain accessible to users in
mainland China, without interruptions from local internet service providers or ISPs.
If you're not sure how ICP works, our China based partners can help you with
the ICP filing and maintenance.
Third, for dynamic content that cannot be cached in the data centers within mainland
China, such as API calls or web apps, users may still experience increased latency
if your origin is located outside of mainland China.
So for these cases, we offer the option of China Express,
which will accelerate both DNS resolution and traffic for origin content.
Watch our video on China Express to learn more.
Thus, the China network solutions sound like something that will help you reach out to our
sales team to learn more.
</page>
<page>
---
title: Content compression | Cloudflare Docs
description: In this video, learn how Cloudflare compresses content between
Cloudflare and your website visitors and between Cloudflare and your origin
server.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/content-compression/
md: https://developers.cloudflare.com/videos/content-compression/index.md
---
In this video, learn how Cloudflare compresses content between Cloudflare and your website visitors and between Cloudflare and your origin server.
</page>
<page>
---
title: Create an API token | Cloudflare Docs
description: In this video, learn the difference between account and user API
tokens how to create one.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/create-api-tokens/
md: https://developers.cloudflare.com/videos/create-api-tokens/index.md
---
In this video, learn the difference between account and user API tokens how to create one.
Transcript
An API token allows secure, fine grained access to specific resources
without exposing your full account credentials.
They have a limited lifespan and expire automatically.
This reduces risk if they are compromised.
For example, if you want to grant someone access to specific apps or data.
You can create an API token for them.
There are two types of tokens user token and account token.
User tokens are directly tied to an individual and their account.
While account tokens are typically tied to services which can help prevent an
interruption in service.
If an employee leaves their organization.
In this video, we'll walk through how to create an API token in the Cloudflare
dashboard. Before you begin, make sure you know your account and zone IDs.
So let's do that. First, the account ID identifies your Cloudflare
account, while the zone ID identifies a specific domain you've added to Cloudflare.
From the accounts page, locate your account at the end of the account
row, open the menu and select Copy Account ID.
If you only have one account, it looks a little bit different.
Login and go to the account home page next to your account name,
select the menu button from the drop down.
Choose Copy Account ID to find your zone ID, log in and go to the accounts page.
Select your account, then go to the overview page for your domain.
Scroll to the API section near the bottom.
Here you'll see the zone ID and an option to click to copy.
This section also lists your account ID for convenience.
Now we can create an API token to create a token.
Start from the Cloudflare dashboard.
For a user token, go to profile API tokens.
For an account token, go to Manage Account account API tokens.
You will only see this option if you are a Superadmin.
Select Create token. You can choose from predefined templates or build a custom token.
For example, let's use the Edit Zone DNS template.
Give your token a descriptive name such as DNS updates for example.com.
The template will fulfill permissions, but you can adjust them as needed.
Next assign permissions.
Permissions are organized by account, user or zone and usually offer either read
access or edit access.
Edit allows full control, create, read, update,
delete, and list, while read provides viewing rights only.
Then select the resources the token applies to.
For instance, granting zone DNS read access for example.com will let the token view DNS
records for that zone only.
If the token is used on a different zone, it will return an error.
Optionally, you can add restrictions such as filtering by client IP or setting a time to
live value for the token.
Click continue to summary to review your selections.
If everything looks correct, choose Create Token.
The dashboard will now display your new token secret.
Copy it immediately to a secure location.
The secret is shown only once.
Anyone with a token can perform the actions you've authorized,
so treat it like a password.
With that, you've successfully created an API token and can begin using it with a
Cloudflare API. For more information, visit our developer documentation.
</page>
<page>
---
title: Configure Full encryption mode | Cloudflare Docs
description: In this video, learn how to configure your site to use Full encryption mode.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/full-ssl-encryption/
md: https://developers.cloudflare.com/videos/full-ssl-encryption/index.md
---
In this video, learn how to configure your site to use Full encryption mode.
</page>
<page>
---
title: Understand how Cloudflare works | Cloudflare Docs
description: Learn how Cloudflare makes the Internet safer, faster, and more
reliable for everyone through the connectivity cloud.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/how-cf-works/
md: https://developers.cloudflare.com/videos/how-cf-works/index.md
---
Learn how Cloudflare makes the Internet safer, faster, and more reliable for everyone through the connectivity cloud.
</page>
<page>
---
title: "Life of a Request: The First Hop - Into the Smart Network | Cloudflare Docs"
description: Imagine your request is a letter you are trying to send to a friend
across the country. Instead of going through the slow, traditional postal
service, Cloudflare acts as a hyper-efficient courier company with a fleet of
delivery hubs all over the world.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/life-of-a-request-1/
md: https://developers.cloudflare.com/videos/life-of-a-request-1/index.md
---
Imagine your request is a letter you are trying to send to a friend across the country. Instead of going through the slow, traditional postal service, Cloudflare acts as a hyper-efficient courier company with a fleet of delivery hubs all over the world.
</page>
<page>
---
title: "Life of a Request: The Fast Lane - Caching and Smart Routing |
Cloudflare Docs"
description: After your request hits Cloudflare's secure network at the nearest
data center where it's checked for security threats with a clean bill of
health, it's time to get it to its destination at lightning speed.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/life-of-a-request-2/
md: https://developers.cloudflare.com/videos/life-of-a-request-2/index.md
---
After your request hits Cloudflare's secure network at the nearest data center where it's checked for security threats with a clean bill of health, it's time to get it to its destination at lightning speed.
</page>
<page>
---
title: "Life of a Request: The Finish Line - Serving the Content | Cloudflare Docs"
description: Once a request is routed to the nearest Cloudflare data center and
then intelligently sped along its way, it moves to the final leg of the
journey and how we serve content faster than ever.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/life-of-a-request-3/
md: https://developers.cloudflare.com/videos/life-of-a-request-3/index.md
---
Once a request is routed to the nearest Cloudflare data center and then intelligently sped along its way, it moves to the final leg of the journey and how we serve content faster than ever.
</page>
<page>
---
title: How to set up a load balancer | Cloudflare Docs
description: Unexpected traffic spikes can crash your website, but Cloudflare
Load Balancing helps keep your apps online and fast. In this step-by-step
tutorial, learn how to create a public load balancer in just five steps -
select a hostname, add an origin pool, attach a health monitor, choose a
traffic steering method, and configure custom rules. We'll also explain the
difference between public and private load balancers and guide you through
using session affinity, fallback pools, and proxy modes.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/load-balancing/
md: https://developers.cloudflare.com/videos/load-balancing/index.md
---
Unexpected traffic spikes can crash your website, but Cloudflare Load Balancing helps keep your apps online and fast. In this step-by-step tutorial, learn how to create a public load balancer in just five steps - select a hostname, add an origin pool, attach a health monitor, choose a traffic steering method, and configure custom rules. We'll also explain the difference between public and private load balancers and guide you through using session affinity, fallback pools, and proxy modes.
</page>
<page>
---
title: Manage account members | Cloudflare Docs
description: In this video, learn how to define the roles and permission scope
for members associated with an account.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/manage-account-members/
md: https://developers.cloudflare.com/videos/manage-account-members/index.md
---
In this video, learn how to define the roles and permission scope for members associated with an account.
Transcript
Account members are users who have access to your Cloudflare account.
Each member's access is controlled by policies which define their roles and the
scope of their permissions.
In order to grant access to account members.
You must be a super administrator with a verified email address.
In this video, we'll walk through how to view members,
add new members, edit their permissions, resend invitations,
and revoke access in Cloudflare dashboard.
Let's first take a look at how to view members.
Start by logging in to the Cloudflare dashboard and selecting your account.
Go to Manage Account Members.
Here you can see the list of current account members.
Now let's move on to adding account members.
On the members page to invite someone new, select invite.
Enter one or more email addresses.
Define the scope of their access.
Choose one or more roles such as administrator or billing.
Click continue to summary.
Review the details, then select invite.
If the person already has a Cloudflare account and you're on an enterprise plan,
you can use Direct Add instead of sending an email invitation.
If you want to change a member's access and permissions.
First open the record and select edit, adjust their roles or scope,
then select continue to summary.
Review the changes and select update.
If an invite is pending and the user hasn't accepted,
this is how you can resend it from the member's page.
Find a pending user, open the record and choose Resend Invite to revoke someone's
access. Expand their record.
Select, revoke and confirm.
If you were added as a member and you want to remove yourself.
Go to the member's page, locate your record and select leave.
If you're a super administrator and you need to leave the account,
you can invite another super administrator before you remove yourself.
You cannot delete the account itself, but other super administrators will retain
full privileges. Cloudflare also supports user groups,
which let you manage permissions for a set of members collectively.
Members inherit all roles assigned to the group in addition to any directly assigned
permissions. For more information on account members and user groups,
visit our developer documentation.
</page>
<page>
---
title: Onboard your domain to Cloudflare | Cloudflare Docs
description: Learn how Cloudflare secures and accelerates your website using its
global network and reverse proxy technology. In this video, we explain how
connecting your domain to Cloudflare protects your origin server, enhances
performance, and keeps your site online—even during attacks. You'll see how
DNS, nameservers, and proxy status work together to route and safeguard
traffic. Whether you're self-hosting or using serverless platforms like
Cloudflare Workers, this guide helps you understand the onboarding process and
why Cloudflare is essential for modern web infrastructure.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/onboard-domain-cf/
md: https://developers.cloudflare.com/videos/onboard-domain-cf/index.md
---
Learn how Cloudflare secures and accelerates your website using its global network and reverse proxy technology. In this video, we explain how connecting your domain to Cloudflare protects your origin server, enhances performance, and keeps your site online—even during attacks. You'll see how DNS, nameservers, and proxy status work together to route and safeguard traffic. Whether you're self-hosting or using serverless platforms like Cloudflare Workers, this guide helps you understand the onboarding process and why Cloudflare is essential for modern web infrastructure.
Transcript
Cloudflare operates a global network that makes your online presence faster and protect
it from cyber attacks.
When you connect a website or app to Cloudflare,
we act as both the authoritative DNS provider and a reverse proxy that sits between your
visitors and your origin servers.
When a visitor or an attacker tries to reach your website,
those requests are first routed to the Cloudflare network instead of your origin
server. Cloudflare processes those requests, mitigating malicious traffic while speeding
up legitimate traffic.
Our services are customizable to give you granular control over your traffic.
You can write rules to cache, load, balance and redirect requests,
modify headers, execute code, and more.
Many of our services are on by default, such as DDoS protection and caching,
so your traffic will automatically be safer and faster.
To make this possible, you need to onboard your domain to
Cloudflare. The most common way to onboard your domain is to update your DNS name
servers to the Cloudflare name servers we provide you,
which makes Cloudflare your authoritative DNS provider.
You do this at the provider you purchase your domain name from,
such as a registrar. If you need a new domain,
you can purchase one at cost from the Cloudflare registrar,
which is automatically configured to use our name servers.
Let's review the basics of name servers and DNS.
A name server is a service operated by your authoritative DNS provider that acts as a
source of truth for your domain's DNS records.
Dns records map a human readable hostname, such as example.com,
to machine readable IP addresses or data.
The IP address listed in a DNS record identifies where your origin server is
hosted. These DNS records tell your authoritative DNS provider how to respond to
DNS queries for your domain.
So altogether, DNS allows internet browsers such as Google Chrome to find the correct
content. Then the browser can make HTTP requests to load the content for your
visitors. If you're not using a reverse proxy such as Cloudflare.
The browser makes HTTP requests directly to the IP address of your origin server.
This is not secure because your origin is exposed to the internet without protection.
When Cloudflare is in front of your origin, we act as both your authoritative DNS
provider and a reverse proxy for your HTTP requests.
We respond to DNS queries with Cloudflare IP addresses,
which makes your HTTP traffic go through Cloudflare instead of directly to your
origin. This process is called reverse Proxying,
which allows us to hide and therefore protect your origin server.
Furthermore, we highly recommend blocking traffic that doesn't come through Cloudflare
by configuring your origins firewall to only allow Cloudflare IP addresses or using
Cloudflare Tunnel. You can identify which traffic is proxy in the DNS records table in
the Cloudflare dashboard.
If the proxy status is set to proxy, requests for those hostname will flow through
the Cloudflare network.
This will start happening once you update your nameservers.
If the status is as DNS only.
Requests for those hostnames will only use Cloudflare for DNS resolution.
Let's follow an HTTP request as it gets processed by Cloudflare when someone visits
or tries to attack your website or app.
That request will be routed to the Cloudflare data center that's closest to that visitor.
If a request is from a legitimate user, we check if it's for a resource that's in the
Cloudflare cache. If we don't have it cached,
we proxy the request to your origin server.
We then cache the origins response.
So the next time Cloudflare sees a request for the same resource,
we can deliver it straight away.
We block suspicious requests from reaching your origin,
only allowing legitimate users and speeding up their experience.
So you will always have the most up to date security posture,
including protection from Sierra de vulnerabilities,
advanced DDoS attacks, and more.
Cloudflare is an extension of your infrastructure,
keeping your site safe and highly available.
Get started with onboarding your domain today.
</page>
<page>
---
title: SASE - The evolution of corporate networks | Cloudflare Docs
description: In this video, we discuss Cloudflare One, our Secure Access Service
Edge (SASE) platform and how it has been designed to revolutionize the
corporate network and enable companies with their Zero Trust strategy. Legacy
network design is struggling to address today's challenges of security,
performance, and monitoring needs. Many IT teams are trying to evolve their
corporate network with point solutions and finding the lack of integration and
performance an issue.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/sase-1-evolution-corp-networks/
md: https://developers.cloudflare.com/videos/sase-1-evolution-corp-networks/index.md
---
In this video, we discuss Cloudflare One, our Secure Access Service Edge (SASE) platform and how it has been designed to revolutionize the corporate network and enable companies with their Zero Trust strategy. Legacy network design is struggling to address today's challenges of security, performance, and monitoring needs. Many IT teams are trying to evolve their corporate network with point solutions and finding the lack of integration and performance an issue.
Transcript
Hi, I'm Simon here at Cloudflare,and I'm going to talk about our SASE platform
to help you modernize your corporate network.
Many company networks have been built ontechnology that simply can't cope with
today's security, performance and monitoringneeds.
The demands on a corporate network haveevolved dramatically over the past few years.
Those working in IT and networking are reallystruggling with the fact that users,
their devices, and the applications and datathey need to access are distributed all over
the place, beyond the perimeter of theclassic corporate network.
They're trying to address this problem withlegacy approaches, which increase cost and
complexity, and can result in a solution thatdoesn't perform that well,
leading to really irritated users.
So in response to these challenges,the concept of SASE has evolved.
It stands for Secure Access Service Edge.
It's a new approach to networking andsecurity,
which reduces complexity,as well as bringing stronger access controls
and improved performance for the protectionof applications,
users, devices and your company data.
But how does it work? First,let's go back and let's look at how
networking and security solutions used to bedesigned.
Decades ago, employees would travel into anoffice and use the company's local network,
which was made up of that network,plus also connections to branch offices,
maybe a data center, and various otherlocations via private leased lines using
technologies such as MultiProtocol LabelSwitching or MPLS.
You are paying for expensive privateconnectivity with dedicated bandwidth,
and typically all Internet access wasbackhauled through these connections to a
single data center, where firewalls andproxies would then inspect the traffic and
apply the security controls.
But over time, as the available Internetbandwidth increased for less cost,
the need for these dedicated lines diminishedand software defined networks,
commonly known as SD-WAN became popular,helping businesses better manage traffic and
optimize usage of cheaper Internet basedIPsec tunnels versus these expensive leased
lines. However, SD-WAN still left businessesmanaging complex on premises appliances and
having to deal with configuration changes andsoftware updates.
Also, firewalls associated with these SD-WANappliances were relatively limited and often
paired with extra hardware for a morecomplete security solution.
While all this was going on,the proliferation of devices such as laptops
and smartphones were allowing employees towork from anywhere,
so VPNs were added into the mix,where people could dial up to the VPN and
access their company network. Often all theirInternet access was also funneled through
these VPN connections,so the same security policies office users
had would also be applied to the remote usertraffic and it all came back through that
company data center. And this approach isreally hard to manage with multiple vendors
and different appliances and differentdashboards to configure the policies across
all these technologies,and they're not really designed to work well
in the modern distributed workplace.
But today, it's not just users and devicesthat have left the office and company
network, but the applications and data liveall over the place as well.
They've migrated out of the data center intocloud infrastructure such as AWS,
Azure and Google. Some applications have beencompletely reimagined as SaaS apps,
where companies no longer run the servers,but just rent access to tenants in large
software deployments,you know, such as Salesforce or Workday and
Zoom. And users are not just taking a shorttrip away from the office anymore.
Some people don't even visit one.
They're working from home,in coffee shops, even on airplanes.
And sometimes they might visit an office,yet the same needs still exist:
the right person should get access to theright applications and data.
Latency or the performance of the applicationshould be really high quality and all while
using secure devices and being protected fromInternet threats such as phishing campaigns
and ransomware attacks.
Because of this constant need for everyone toaccess anything from anywhere,
SASE architectures evolved where theintelligence in the network has migrated out
of these on premises appliances and now intomassively scalable global cloud networks.
So how does Cloudflare SASE platform work?
Well, first, and probably most importantly,we've built a massive network spread all over
the globe. We've deployed thousands ofservers in data centers in hundreds of
cities, creating peering relationships withthousands of other networks.
On top of all of that,we've ensured that we have connectivity in
all the important Internet exchanges.
These are places where all the bigconnectivity of the Internet is shared.
To give you an idea of the scale of this hugenetwork,
and it can deal with the largest denial ofservice attacks that have ever been seen.
The scale and performance of this network isreally important because from a SASE
perspective, you're going to be routing allyour user,
device and network traffic into it.
Every server in our network runs all thecapabilities you need to inspect and secure
traffic. So access controls,traffic routing,
caching, all run on the server that your useror network is connecting to.
So now, instead of all the security controlsand network logic spread across a variety of
different vendors and appliances and servicesthat you're having to maintain,
it's centralized in a cloud service thatoperates and points all over the globe,
so that each user or network is connected toa fast local data center.
And Cloudflare SASE platform is part of agreater connectivity cloud.
So what's a connectivity cloud?
It's a unified platform of cloud nativeservices that spans networking,
security and application performance,and it's designed to help companies regain
control over their technology infrastructure.
Our connectivity cloud goes way beyond justprotecting employees and their access to
company resources. It's also used to protectpublic assets like websites and APIs.
In fact, we run one of the world's fastestDNS servers.
We've even exposed the underlying componentsof our platform,
letting developers write and run their codedirectly on our network.
Then they can extend our existing services orbuild entirely new applications,
leading you to an infinite amount of thingsyou can build.
So to summarize Cloudflare SASE platform,which runs in our connectivity cloud,
allows companies to reimagine their companynetwork.
Users connect to Cloudflare's global networkvia a data center that's close to them,
and that server then ensures that they don'taccess phishing sites on the Internet, or it
gives them secure access to an internalcompany application.
All of this is happening in millisecondsacross our vast network.
Because we can deliver all these capabilitiesin a single platform instead of different
vendor solutions, it means that companies cancentralize all that management into a single,
well-integrated dashboard.
This ultimately drives down your cost lesstime used to manage the services,
less or often no hardware to purchase andmaintain,
and it's cheaper to purchase the actual finalsolution.
Well, thanks for watching.
This video is part of a series which explainshow to build your new corporate network using
Cloudflare SASE platform.
Watch other videos in this series to learnmore.
Hi, I'm Simon from Cloudflare.
Congrats on finding this video.
We also cover a wide variety of topicsincluding application security,
corporate networking,and all the developer content the Internet
can hold. Follow us online and thanks forwatching!
</page>
<page>
---
title: SASE - Stop hosting your VPN service | Cloudflare Docs
description: Cloudflare's SASE platform can replace your traditional, expensive
VPN appliances, which deliver poor performance for users and create more
security risks than solve them. Cloudflare's Zero Trust Network Access (ZTNA)
service is a more secure, highly scalable cloud solution. In this video, we
look at how easily you can deploy Cloudflare to secure access to internal
resources.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/sase-2-stop-your-own-vpn/
md: https://developers.cloudflare.com/videos/sase-2-stop-your-own-vpn/index.md
---
Cloudflare's SASE platform can replace your traditional, expensive VPN appliances, which deliver poor performance for users and create more security risks than solve them. Cloudflare's Zero Trust Network Access (ZTNA) service is a more secure, highly scalable cloud solution. In this video, we look at how easily you can deploy Cloudflare to secure access to internal resources.
Transcript
Corporate networks are often used to allowemployees to access sensitive information in
private, self-hosted applications,such as an internal wiki,
a HR system, or a source code repository.
While some applications have migrated intothe cloud as SaaS apps,
there are still applications that are run andmaintained by IT.
These days, most of these self-hostedapplications run in a web server and are
deployed either in a private data center orin a public cloud such as AWS,
Azure, or Google. Access to theseapplications is usually limited to internal
employees, but it's common to allow some formof restricted access to partners or
contractors. The old way of doing things wasto have users either come into a physical
office or connect remotely via a VPN,giving them access to that corporate network
so they could access the application.
But these VPN solutions use on premiseshardware appliances through which every user
request passes, creating a bottleneck and asecurity risk.
In fact, recently, many on premises VPNvendors such as Cisco,
Checkpoint, and Fortinet have reported a widerange of vulnerabilities which requires IT
and security teams to scramble to updatetheir systems.
But there's another way to do this.
Did you know that Cloudflare can be used toeasily create secure access to these
self-hosted applications using our SASEplatform?
That's part of our connectivity cloud?
Well, similar to how a legacy VPN works,but using a much,
much more modern cloud approach.
Let's take a look at how we improve on theold way of doing things,
and create greater security for applicationaccess.
The first objective is to create connectivitybetween the user's browser and the
application. Right. So there are two parts tothis. The connection from Cloudflare to the
app and the connection between the user andCloudflare.
Cloudflare is going to sit in the middle andapply security policies and use its vast
network to protect the application andimprove response times.
For the first part, to create connectivityfrom Cloudflare to the app,
we use tunnels that a variety of differentmethods you can use.
You can connect on premises networks toCloudflare via IPsec or GRE tunnels,
typically using your existing networkhardware,
or if your applications are running at a datacenter where Cloudflare already has its
servers, we can connect directly from yourservers to our servers inside that data
center. But for this example,we're going to talk about using a software
agent. It's just a small daemon that isinstalled either directly on the application
server or runs on a dedicated server on thesame local network.
The software then creates a secure tunnelback to Cloudflare.
This tunnel maintains a constant connectionto two Cloudflare data centers,
so it's always available,and now your traffic can flow between your
Cloudflare network and the application.
Now for the second part,we need to connect your users to Cloudflare,
which we're going to do in this example usingpublic DNS.
We'll associate a public hostname with theapplication.
Request to this hostname will resolve toCloudflare,
which in turn proxies and routes traffic downthe tunnel to the application,
but hold on a second. A public DNS record anda tunnel directly to the server?
If we didn't take this any further,we could now access this internal application
from anywhere just by heading to the newpublic hostname.
What we need to do is add authentication andauthorization into the mix.
Because Cloudflare is now in front of accessto the application,
we can integrate with your existing companyidentity providers.
So anyone attempting to access is firstredirected to your identity provider to
authenticate. Now this is where it getsinteresting because you can add multiple
identity providers in front of the sameapplication.
So for example, you might use your maincompany directory where all your employee
accounts reside, but you might also integratea separate identity service just for
contractors, partners and other third partyusers.
We also support consumer identity providerssuch as Facebook,
Google or GitHub. In fact,any SAML or OAuth identity service can be
used. Now, these identity integrations don'tjust provide authentication.
It's possible to import user and groupinformation.
Which brings us on to the next step.
Now that we've ensured a user hasauthenticated,
we can start to leverage their identityinformation and other data to create an
access policy that defines who should andshould not get access to the application.
Let's build a policy here in real time.
A range of different attributes can be usedthat define who is allowed or denied access.
We started by adding an identity provider,so users first need to authenticate.
Let's take it a little further and leveragegroup information from the same identity
service. We can say only users in the fulltime employees group have access to the
internal wiki. The identity service can alsotell us how they authenticated.
So let's add that to our policy.
The requirement that they must haveauthenticated using MFA or multi-factor
authentication. In fact,let's say that they have to specifically use
a hard token such as a FIDO certified key.
Finally, we only want users working fromCanada,
the US or Germany to access the application.
So let's add to the policy that only trafficcoming from IP addresses geolocated in those
countries is allowed. Now,full time employees working from somewhere in
Canada who have authenticated using a strongset of credentials will be able to access the
company wiki. Let's take a look at this inaction.
The user just needs to navigate to the publichostname,
authenticate, and bingo!
They have access from anywhere in the worldwith only a browser to our privately hosted
application. Simple. What a difference fromthe old way of doing things.
Also, it's important to note that all trafficfrom browser to application is secured using
standard TLS and SSL encryption,keeping the application data safe.
Let's turn our attention a little bit toperformance.
We already mentioned that Cloudflare is a lotmore efficient than a traditional VPN.
Let's think about somebody in Germany tryingto access the wiki.
Cloudflare uses something called Anycastnetworking,
which means that a request to the hostnamewill resolve to the nearest Cloudflare data
allowing us to ensure fast connectivity fromuser to application.
So our user in Germany might on ramp toCloudflare at a data center in Berlin,
whereas our Canadian user might on ramp inVancouver,
and their requests are authenticated and thepolicy evaluated all close to the end user
and if authorized, their request is thenrouted via the most efficient network path to
the Cloudflare data center that is thennearest the application.
To further improve performance,there are many more things we can do.
Any of Cloudflare's existing performanceservices and network benefits apply to your
application traffic. So,for example, we can leverage Cloudflare's
caching technologies so that any static datafrom the wiki such as images,
files, videos is all cached locally at thedata center that the user is accessing.
Something your old VPN could never do.
Setting up access like this can be typicallydone in less than an hour,
and it doesn't take long to migrate an entirecompany's internal application
infrastructure. Unlike your VPN,access to each application only exposes that
specific service. You don't need to worryabout firewalling off SSH and RDP,
because Cloudflare is only allowing access tothe specific application over HTTPS.
This is called network micro-segmentation andreally reduces concerns of access gained by
lateral movement. Changes to authenticationpolicies can easily be made in our dashboard
and in just a matter of seconds,the entire global network is updated.
Well, thanks for watching.
This video is part of a series which explainshow to build your new corporate network using
Cloudflare SASE platform.
Watch the other videos in this series tolearn more.
Hi, I'm Simon from Cloudflare.
Congrats on finding this video.
We also cover a wide variety of topicsincluding application security,
corporate networking,and all the developer content the Internet
can hold. Follow us online and thanks forwatching!
</page>
<page>
---
title: SASE - Secure remote access to your critical infrastructure | Cloudflare Docs
description: In this video, learn how Cloudflare's SASE platform can provide
highly secure access to your critical infrastructure by leveraging a modern
ZTNA service to implement Zero Trust principles Applications, databases and
their servers are running in a variety of locations from on-premises data
centers to cloud hyperscalers, making the need to secure administrative access
more important than ever.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/sase-3-secure-remote-access/
md: https://developers.cloudflare.com/videos/sase-3-secure-remote-access/index.md
---
In this video, learn how Cloudflare's SASE platform can provide highly secure access to your critical infrastructure by leveraging a modern ZTNA service to implement Zero Trust principles Applications, databases and their servers are running in a variety of locations from on-premises data centers to cloud hyperscalers, making the need to secure administrative access more important than ever.
Transcript
Secure Access Service Edge or SASE solutionsincorporate Zero Trust Network Access or ZTNA
to provide access to applications such as aninternal wiki or a HR system.
But what about critical high risk servicessuch as a database administration tool or
service requiring access via SSH or RDP?
In these cases, it's important to be able toensure tight security from the device all the
way to the application and allow authorizedusers who are using strong authentication on
trusted devices. Let's say we need to secureaccess to a database admin app such as
pgAdmin, a common web interface for Postgresdatabases,
and also access to SSH on the same server.
Imagine we have an example environment,and in it we've already created connectivity
from the server to Cloudflare,using a software agent that maintains a
secure tunnel from the private network wherethe Pgadmin server is running back to the
Cloudflare network. No private server IPaddresses are going to be exposed to the
Internet. We're essentially connecting thisserver to our new corporate network managed
by Cloudflare. Once connected,there are two methods by which we can access
our private server. Method one is to create apublic hostname which resolves to Cloudflare,
which in turn proxies and routes the trafficfor that specific hostname to that
application at the end of our tunnel.
And this method allows anyone,anywhere, on any device to easily access the
application. But that's not enough.
In this scenario we want to implement eventighter security.
So method two is to configure the tunnel toproxy access only to the server IP with no
public DNS record, and only for trusted userswith managed devices that are connected to
the Cloudflare network.
So none of this server has any publicexposure.
Now, to provide access to only databaseadmins,
there are a few things we need to do.
We need to use an internal hostname thatresolves to our server.
We need to connect to the user device to theCloudflare managed network.
And we need to identify who the user is andif their device has a good security posture.
So let's first look at how we do the internalDNS resolution.
Because nobody likes using IP addresses toaccess services with the exception of
So we really should always be usinghostnames.
With Cloudflare, it's as simple as connectinga private DNS service to the network,
and then building a policy that says anyrequest from a user or a network,
anywhere on the Cloudflare network,for an internal domain,
should be answered by that specific DNSservice.
In this example, we're going to connect it toCloudflare using exactly the same tunnel
software that we're using for the databaseserver.
So at this point we have our database admintool that's connected to Cloudflare and we
have an ability to resolve the IP address ofthat private network using an internal
hostname. Next, we need to securely connectthe user device to Cloudflare so that all
traffic destined for our database server isover secure channels.
We do this using a similar piece of softwarewe used on the server,
but one that's designed for user devices.
It supports macOS, windows,Linux, iOS and Android and connects the
device to Cloudflare using a secure tunnel.
But the agent can actually provideinformation about the security posture of the
device, and we'll talk about that later whenwe look at the policy itself.
So once the user device is connected toCloudflare,
requests for private applications areresolved using the internal DNS service,
and traffic is routed from the device throughCloudflare through secure tunnels down to the
private IP the application is running on.
Now we have secured connectivity all the wayfrom the device to the server.
The last thing we need to do is actuallywrite a policy which enforces access only to
users that you authorize,and that the device they're on meets a
certain level of security.
We use information from our device agent,and also leverage your existing identity and
device services to help build that policy.
Cloudflare is typically integrated with oneor more identity providers.
Usually, your company has a central directoryfor employees,
but you can also add more.
For example, you might manage contractors ina different directory.
Cloudflare can also integrate with XDRplatforms such as CrowdStrike and
SentinelOne, and these give us information wecan use in the policy regards to the security
posture of the device,such as if the device is free of malware.
For our own agent, we can provide informationabout the device,
such as is the hard disk encrypted or if thelocal firewall is enabled.
So now we have all the information about theuser,
their device, and how they're connected toCloudflare.
A policy can be created which only allowsusers who have authenticated using a strong
factor, such as MFA using a hard token,that they also exist in a group such as IT
administrators, and they're using a securedevice free of malware.
This policy sits in front of access to boththe database admin tool and the SSH service.
Finally, because you might want to record ofall access to the database administration
tool, you can optionally inject a page afterauthentication asking for justification for
access to the app and that gets audited andlogged in Cloudflare.
So in summary, you've seen an example of howCloudflare can protect access to some of your
critical infrastructure using our SASEplatform.
We can help lock down access to servers onlyfrom highly authenticated users on tightly
managed devices that must be connected toyour new corporate network or managed by
Cloudflare. Well, thanks for watching.
This video is part of a series which explainshow to build your new corporate network using
Cloudflare SASE platform.
You can watch the other videos in this seriesto learn more.
Hi, I'm Simon from Cloudflare.
Congrats on finding this video!
We also cover a wide variety of topicsincluding application security,
corporate networking,and all the developer content the Internet
can hold. Follow us online and thanks forwatching!
</page>
<page>
---
title: SASE - Connect and secure from any network to anywhere | Cloudflare Docs
description: Build your new corporate network with Cloudflare, connecting any
network into our modern SASE platform and secure applications, users, devices
and your company data. In this video, you will learn all of the different
methods of connecting networks to Cloudflare and what services can be used to
improve security and performance.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/sase-4-connect-secure/
md: https://developers.cloudflare.com/videos/sase-4-connect-secure/index.md
---
Build your new corporate network with Cloudflare, connecting any network into our modern SASE platform and secure applications, users, devices and your company data. In this video, you will learn all of the different methods of connecting networks to Cloudflare and what services can be used to improve security and performance.
Transcript
When looking at Secure Access Service Edge orSASE platforms,
we often talk about a user getting remoteaccess into some privately hosted
application. The focus is often user toapplication,
where the goal is network micro-segmentation,
and a user can only access an applicationover a specific address and port.
But corporate networks exist to carry trafficin many other ways.
Let's take, for example,a retail coffee company with many coffee
shops each providing customers free access tothe Internet with their guest Wi-Fi,
but also connecting employees to internalapplications.
Each shop also houses point of sale devices,security cameras,
and other network enabled equipment that needaccess to the Internet,
but also might require access to otherprivate networks to back up data or be
monitored by internal tools.
IT staff also need to remotely access thesedevices from a corporate office network.
A lot of this traffic is private and shouldonly remain on the corporate network.
This is where Cloudflare's Connectivity Cloudreally comes into its own.
The ability to mesh together differentnetworks,
applications and users no matter where theyare.
Let's dive deeper into our coffee companyexample.
Right. First, they have their mainheadquarters in Seattle.
Most HQ employees live locally and about halftravel into the office,
with the other half working remote at home.
each with a few employees in each.
And then they have an internal company wiki,which is running in a virtual environment in
Amazon Web Services with its own virtualprivate network.
And then finally, the security cameras at alltheir coffee shops need to back up data to a
central service that you've got running onservers that you run and host in a rack in a
data center in San Jose.
You see how these network locations are allquite different.
Cloudflare has a variety of ways all thesenetworks can be connected together.
Let's start by connecting the headquartersnetwork in Seattle.
We can use something called Magic WAN,which is our service that creates IPsec
tunnels from the headquarters office back tothe Cloudflare network and assign a private
network range to it. This is using regularstandard IPsec protocols and can easily
leverage functionality in a network,router or firewall that exists at
headquarters. Next, let's look at each coffeeshop.
You can ship out to each location a physicaldevice running Cloudflare's Magic WAN
connector. It's essentially a lightweightappliance that can be plugged into the local
ISP router. Each connector creates an IPsecconnection back to Cloudflare,
and each device can be administered remotelyvia the Cloudflare dashboard private network.
Ranges can then be assigned to each coffeeshop.
And now we have the beginnings of a newmodern corporate network.
So IT admins in the Seattle office can nowremotely access point of sale devices in each
coffee shop location. Also,because we want to provide customers in each
shop free Internet access using the guestWiFi,
all traffic from that location is now routedthrough Cloudflare,
and we can use our secure web gateway toblock any access to malicious websites,
and this keeps customers safe while they siptheir cappuccinos.
But what about the IT staff working fromhome?
They're not connected to any of thesenetworks. No worries!
They can use our device agent,which connects them to Cloudflare,
and in turn gives them access to this newcorporate network as if they were connected
in headquarters. Now it can manage thedevices in each coffee shop,
no matter if they're on a plane,sitting in an office,
or in a coffee shop. When each network oruser connects,
it does so to the nearest Cloudflare datacenter,
which is a key feature of our network wherewe use Anycast IP networking to ensure secure
connections to users and offices are made tothe geographically nearest Cloudflare data
center, so that traffic is then secured andoptimized as close as possible to the user or
peering relationships,allowing us to ensure fast connectivity from
user to the network. Think of it like havinga coffee shop in every neighborhood so
everyone doesn't have to walk far to get acup of coffee.
But what about those camera backups?
Remember, the backup service is running in adata center in San Jose.
Most likely than not. Cloudflare is alsorunning our own servers in the same data
center, and you can offer direct connectionsfrom Cloudflare to your network switches,
further extending your corporate network.
And even if your servers are not in the exactsame data center,
we can create a virtual connection directlyfrom your rack to the nearest Cloudflare data
center. Now we've got everything connected.
Let's add a new application into the mix.
Let's say the company is launching a newinternal company wiki,
and they're running the service in AWS,Amazon Web Services.
We don't need to connect the entire AWSprivate network.
We just install a software agent on the wikiserver that creates a secure tunnel back to
Cloudflare, and connects that application tothe network,
that anyone on that network can now accessthe application policies and Cloudflare
control who can access the wiki,ensuring users authenticate with valid
credentials and are using secured devices.
You can see that Cloudflare is able toconnect to a wide variety of networks,
from the physical office locations to virtualapplication networks in the cloud,
as well as direct your servers running inyour data centers.
So much of the complexity from legacy networkarchitectures is abstracted into our
Connectivity Cloud , making life much easierfor IT and network admins.
And once connected to Cloudflare,it's not just about routing traffic.
Firewalling, DNS, Load Balancing,protecting from denial of service attacks,
content caching, and a lot more are alleasily enabled.
Any traffic destined for the Internet canalso be filtered to ensure only access to
legitimate sites, and blocking any unsafetransfer of company data.
The flexibility of Cloudflare's ConnectivityCloud allows you to connect all sorts of
networks and applications and users.
It's possible to recreate your classiccorporate network and then apply on top of it
all the modern Zero Trust services to ensurehigh security without compromising the user
experience. Well, thanks for watching.
This video is part of a series which explainshow to build your new corporate network using
Cloudflare SaaS platform.
Watch the other videos in this series tolearn more.
Hi, I'm Simon from Cloudflare.
Congrats on finding this video.
We also cover a wide variety of topicsincluding application security,
corporate networking,and all the developer content the Internet
can hold. Follow us online and thanks forwatching!
</page>
<page>
---
title: SASE - Protect your users from Internet risks | Cloudflare Docs
description: The Internet has become part of your corporate network; however,
browsing the web comes with hidden risks including malware, phishing attacks,
and malicious websites. In this video, we will explore how Cloudflare's Secure
Web Gateway (SWG) helps keep users safe by filtering and inspecting Internet
traffic in real time. Whether you are protecting a remote workforce or
securing an entire organization, Cloudflare ensures that users can access the
web securely — without sacrificing speed or productivity.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/sase-5-protect-users/
md: https://developers.cloudflare.com/videos/sase-5-protect-users/index.md
---
The Internet has become part of your corporate network; however, browsing the web comes with hidden risks including malware, phishing attacks, and malicious websites. In this video, we will explore how Cloudflare's Secure Web Gateway (SWG) helps keep users safe by filtering and inspecting Internet traffic in real time. Whether you are protecting a remote workforce or securing an entire organization, Cloudflare ensures that users can access the web securely — without sacrificing speed or productivity.
Transcript
Cloudflare's Connectivity Cloud hosts acomplete Secure Access Service Edge,
or SASE platform, which allows organizationsto create a new corporate network leveraging
the latest in zero trust security approachesand cloud based networking.
Many companies start by connectingapplications,
networks and user devices to Cloudflare touse Zero Trust Network Access,
or ZTNA to authorize users to connect toself-hosted applications and private
networks. But connecting devices and networksinto Cloudflare can also help secure public
Internet access and increase visibility andcontrol over company data.
Let's take a look at an example of a companythat has already connected its corporate HQ
network, along with a few branch offices andmany remote user devices.
You can see that all these methods of onramping traffic to Cloudflare result in user
traffic flowing through our network.
Sometimes the traffic is destined for aprivate application or network,
but a lot of the traffic is just heading forthe public Internet.
Cloudflare has the ability to inspect thattraffic using another part of our SASE
platform, the Secure Web Gateway.
It can examine traffic either at the DNSrequest,
the network level, or we can even inspect thecontents of a HTTP request.
Do you want to deny users from accessingwebsites known to be part of a phishing
campaign or ransomware attack,or only allow users coming from IP addresses
in the US to access your Workday instance?
Or more seriously, do you want to preventemployees from sending sensitive information
like financial data or source code to AIsites like ChatGPT?
Policies in the Secure Web Gateway allow youto achieve this,
and they can be written using a wide varietyof attributes.
We can even isolate a website by running notin the user's browser,
but by rendering it in our headless browser,running on our own network.
And then we send the results down to the userdevice,
and this protects them from any nasty coderunning in that website.
Let's take a look at the different ways ourSecure Web Gateway can help protect your
organization. The first method to protect anyuser or device is to look at their DNS
requests. Some of the most common policiesare simply designed to prevent access to
known high risk websites.
To make your life easier,Cloudflare manages large lists of sites that
are known to be dangerous.
Either they've been found to distributemalware or they're part of a phishing
campaign. All you need to do is include thatcategory in the deny policy,
and users will be blocked from visiting them.
Cloudflare keeps the sites in each categoryup to date.
So we have an amazing view into what's badout there on the Internet.
You could never maintain this amount of datayourself.
Policies can be applied at the user level orbe based on network location.
You might wish to implement a policy thatlimits certain websites depending on the
country the network request is coming from.
You can even subscribe to government cyberdefense lists of known malicious websites.
You can also use a DNS policy to simplifysome of your IT infrastructure.
A policy can override the IP address returnedfrom a DNS request and point to a service
that might be local. For example,you might configure all employee laptops to
use a single hostname for connecting to theoffice printer.
Let's say it's printer dot company dot local.
Then, if a user is attempting to print in theSeattle office,
Cloudflare will replace the IP address forthat host with the local office printer.
But if the same user then travels to theLondon office,
the same laptop makes the same request toprint and Cloudflare replaces the IP address
now for the London printer.
The second method of protection is by usingnetwork policies.
So for all your networks connected CloudflareSASE platform,
it's possible to write simplefirewall-like-rules.
These are often used to allow access tospecific services on private IP addresses.
Say for example, you have a lot of windowsservers running in your corporate network and
you want to ensure only IT admins are allowedto connect to them over RDP.
How? Well, when users access Cloudflare usingour device agent,
network access policies can use identityinformation such as the method of
authentication, what groups the user is in aspart of the policy.
Device security posture can also be takenfrom that device agent,
making sure that IT admins access Windowsservers only using secured company managed
devices. The third and the one with the mostcontrol is HTTP policies,
since it allows you to inspect the actualHTTP traffic.
For devices where a Cloudflare certificatehas been deployed,
the TLS and SSL connection terminates atCloudflare,
where you can inspect the traffic and applyyour policies.
You can build policies that limit theuploading or downloading of files based on
their file type, or prevent HTTP POST or PUTto prevent the certain upload of content to
any websites. We also have a sandboxingfeature where we can use AV scanning to
examine certain files being downloaded andquarantine them if they contain malicious
content. But the true power of inspectingHTTP traffic is when it's combined with our
DLP policies. Here, we can match any part ofthe HTTP request,
either the body of the request or if a filecontains specific content,
and then protect that data from leaving yourorganization or being downloaded to insecure
devices. We have built-in DLP profiles formatching common data,
such as health or financial information,source code or privately identifiable
information such as social security or taxidentifiers.
You can also create your own DLP profiles byeither defining patterns to match sensitive
data, or just by uploading a list of knowncustomer accounts.
Now, when users attempt to download or uploadany content that matches these profiles,
you have the ability to block it.
Sometimes the risk for a website isn't wellknown.
For example, you might deem social mediawebsites to be a little risky,
but your marketing department still requiresaccess.
Newly registered domains might sometimes bepart of a phishing campaign,
or they might just be a legitimate newwebsite.
In these examples, Cloudflare has a reallycool capability.
You can write a policy that when a user makesa request for a website you think is a little
risky, instead of their machine receiving allthe content directly,
we spin up a headless browser on our networkand render the content first.
Here we isolate any potential bad behavior ina secure,
isolated environment. We then send theresults of the render page down to the user's
device, and you can optionally turn on andoff certain capabilities,
such as the ability to enter text into theweb page or download files.
We call this Remote Browser Isolation.
You can also use this service to limit accessto SaaS application data for a certain set of
users. You might, for example,want to allow contractors or partners to have
access to your Salesforce instance,and you can use our Browser Isolation to
prevent copy and paste,printing or downloading of Salesforce data.
So in summary, Cloudflare has a powerfulrange of capabilities to protect users from
the threat of bad actors on the Internet,while also identifying company data and
protecting its use. You can ensure safebrowsing by blocking known malicious
websites, detect when company data is beinguploaded to unapproved cloud storage,
or downloaded to insecure devices.
You can even isolate the entire website sothat users are protected from any dangerous
activity. Well, thanks for watching!
This video is part of a series which explainshow to build your new corporate network using
Cloudflare SASE platform.
Watch the other videos in this series tolearn more.
Hi, I'm Simon from Cloudflare.
Congrats on finding this video!
We also cover a wide variety of topicsincluding application security,
corporate networking,and all the developer content the Internet
can hold. Follow us online and thanks forwatching!
</page>
<page>
---
title: Manage SSL version or cipher mismatch errors | Cloudflare Docs
description: In this video, learn how to manage an SSL version or cipher mismatch error.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/ssl-cipher-mismatch/
md: https://developers.cloudflare.com/videos/ssl-cipher-mismatch/index.md
---
In this video, learn how to manage an SSL version or cipher mismatch error.
</page>
<page>
---
title: SSL/TLS concepts | Cloudflare Docs
description: In this video, learn the key concepts relevant to Cloudflare SSL/TLS.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/strict-ssl-concepts/
md: https://developers.cloudflare.com/videos/strict-ssl-concepts/index.md
---
In this video, learn the key concepts relevant to Cloudflare SSL/TLS.
</page>
<page>
---
title: Configure Strict encryption mode | Cloudflare Docs
description: In this video, learn how to configure your site to use Strict
(SSL-Only Origin Pull) encryption mode.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/strict-ssl-encryption/
md: https://developers.cloudflare.com/videos/strict-ssl-encryption/index.md
---
In this video, learn how to configure your site to use Strict (SSL-Only Origin Pull) encryption mode.
</page>
<page>
---
title: The Online Address Book | Cloudflare Docs
description: This video focuses on the first prerequisite for using a tunnel, a
domain name. It uses the metaphor of an online address book to explain DNS and
how Cloudflare manages your domain.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/the-online-address-book/
md: https://developers.cloudflare.com/videos/the-online-address-book/index.md
---
This video focuses on the first prerequisite for using a tunnel, a domain name. It uses the metaphor of an online address book to explain DNS and how Cloudflare manages your domain.
</page>
<page>
---
title: WARP - Understand Cloudflare WARP basics | Cloudflare Docs
description: In this episode, we explain the core features of the Cloudflare
WARP client and how to troubleshoot common issues. After watching, you will
have an understanding of the GUI, the differences between the consumer and
corporate WARP, device profiles, the various operating modes of WARP, split
tunneling, and more.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/warp-1-basics/
md: https://developers.cloudflare.com/videos/warp-1-basics/index.md
---
In this episode, we explain the core features of the Cloudflare WARP client and how to troubleshoot common issues. After watching, you will have an understanding of the GUI, the differences between the consumer and corporate WARP, device profiles, the various operating modes of WARP, split tunneling, and more.
Transcript
Hi, I'm Jess from Cloudflare.
Welcome. In this video,you'll learn the basics of Cloudflare WARP.
Our support team will always be here to help,
but this guide is all about empowering you tounderstand and solve issues faster on your
own. We will learn the Cloudflare WARP clientand how it differs from the consumer version
the different operating modes of WARP,split tunneling exclude versus include modes,
and the WARP GUI and its intended versusactual state.
These are the basic concepts that willprepare you to troubleshoot any issues you
may encounter. Let's get started with What isthe Cloudflare WARP client?
Cloudflare WARP client allows you to protectcorporate devices by securely and privately
sending traffic from those devices toCloudflare's global network,
where Cloudflare Gateway can apply advancedweb filtering.
is available to the public for free.
The corporate version integrates withCloudflare Zero Trust,
giving your IT team the ability to managesecurity policies,
control traffic routing,and monitor usage.
If you're not sure which version of WARPyou're currently using,
you can tell them apart easily by its color.
The consumer version will display WARP inred,
whereas the corporate version will displayZero Trust in blue.
If your intention is to use the corporateversion,
make sure you're seeing a blue Zero TrustWARP banner by authenticating with your
Cloudflare Zero Trust organization.
Next, what is the device profile?
A device profile represents a different setof parameters assigned to your device,
based on its relationship with the policyattributes.
You can create multiple profiles and applydifferent settings based on your user's
identity, the device location,and other criteria.
IT administrators can assign different deviceprofiles to their users.
For example, depending on office locations,teams,
device types, operating systems,or other attributes,
users might have different routes that needto be excluded from their WARP Tunnel,
or different DNS settings to accommodatelocal development services.
All right, it's important to know that WARPclient can operate in different modes,
because each mode controls the types oftraffic sent to Cloudflare Gateway
differently. The WARP mode determines whichZero Trust features are available on the
device. Selecting the right mode depends onyour organization's needs.
For example, for Internet security or remoteaccess gateway with WARP or Secure Web
Gateway without DNS filtering would be ideal,
and the latter should only be used in caseswhere Cloudflare cannot control DNS
resolution on the device.
Both Gateway with DoH and Proxy Mode are usedfor Internet filtering.
Gateway with DoH is only DNS traffic,while Proxy Mode is only HTTP traffic.
Lastly, Device Information Only mode would beuseful for clientless access or browser based
remote access to use device posture withoutproxying traffic to Cloudflare.
If you encounter a problem,understanding which mode you're in will help
you narrow down where the problem might be.
And that's because WARP modes arecombinations or absences of particular
features. For example,Gateway with WARP includes both DNS and
Tunnel components. So when you'retroubleshooting,
you have to look at both the DNS and Tunnelcomponents as opposed to Gateway with DoH
where you will only have to look at the DNScomponent.
But don't worry, you don't have to memorizeall of this.
You can always refer to our documentation.
Next up, split tunneling,a feature that allows you to control what IP
traffic goes through the WARP virtualinterface or tunnel.
There are two ways to configure it.
The first mode is exclude IPs and domains.
This is the default setting.
All traffic will be sent to CloudflareGateway except for IPs and domains you
specify. The second mode is include IPs anddomains.
Only traffic destined to IPs or domains youspecify will be sent to Cloudflare Gateway.
All other traffic will bypass Gateway andwill no longer be filtered by your network or
HTTP policies. Secure Web Gateway without DNSfiltering and Device Information Only mode
will automatically disable domain based splittunneling.
So if you're experiencing issues related todomains,
it's good to check your WARP mode.
And lastly, here's a common point ofconfusion.
The toggle button in the WARP GUI shows theintended state,
not the actual state. For example,if the toggle is on,
it means that the client intends to connect,but the actual status may show disconnected
if there's an issue. So always check themessage below the toggle for the current
connection state. You now understand thefoundation of WARP client components.
If you want to learn more,we also have additional resources on
Cloudflare docs. Thanks for watching and seeyou soon!
</page>
<page>
---
title: WARP - Understand Cloudflare WARP through diagnostic logs | Cloudflare Docs
description: In this more advanced episode, we explain how to use warp-diag
files to identify and resolve connection issues with the WARP client. You will
learn how to locate and interpret three key files - warp-status,
warp-settings, and daemonlog. The video also provides troubleshooting tips,
including specific keyword searches and guidance on how to cross-reference
logs to identify a bigger picture of the problem.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/warp-2-diagnostic-logs/
md: https://developers.cloudflare.com/videos/warp-2-diagnostic-logs/index.md
---
In this more advanced episode, we explain how to use warp-diag files to identify and resolve connection issues with the WARP client. You will learn how to locate and interpret three key files - warp-status, warp-settings, and daemonlog. The video also provides troubleshooting tips, including specific keyword searches and guidance on how to cross-reference logs to identify a bigger picture of the problem.
Transcript
Hi, I'm Jess from Cloudflare.
Welcome. This is a WARP troubleshooting videowhere you'll learn how to interpret warp-diag
files. This is a more advanced episode,so if you come across any concepts you aren't
fully familiar with, we also have a WARPbasics video that brings you up to speed.
And as always, our support team will be hereto help.
Here's what we will go through.
What are warp-diag files?
How to download and navigate the warp-diagfiles,
warp-status file, warp-settings file,daemon.log file,
and a few additional tips for analyzing them.
Let's get started. So what are warp-diagfiles?
They contain valuable information about thedevice connection status,
configuration, and WARP logs.
These files are your first line of defensewhen troubleshooting any issues.
Each of these files serves different purposesand contains specific information,
such as combination of logs and outputscreated when warp-diag runs.
Now where are the WARP files?
When WARP is installed,a command line tool called warp-diag is also
installed. Simply running the commandwarp-diag in a terminal will generate a zip
file and place it on the user's desktop.
Each time warp-diag is run,a new set of logs will be generated,
and now we can start by unzipping the fileproduced by warp-diag and opening its content
in a text editor. I'm using VS Code here,but any other text editor will also work.
In this video, we'll only look at threeparticularly useful ones for initial
troubleshooting: warp-status,warp-settings,
and daemon.log. So now I'll walk you througheach of these files and tell you why they're
useful for troubleshooting.
First, let's take a look at warp-status.
This file is straightforward.
It contains the status of the client whenwarp-diag was executed.
The connection status is useful to know whenyou're analyzing any files that are outputs
of common command line tools such as listinginterfaces,
printing the routing table,and current DNS configuration.
And that's it! On to warp-settings.
This file contains all of the currentlyactive settings configured for the device,
such as the modes and device profile.
This file can help verify if the settingsyou're making in a dashboard are actually
being applied locally.
We should always check this file to see ifthere are any unexpected values.
For example, let's say the user you'retroubleshooting for is expected to have a
specific device profile like office users,meaning their devices should be connected to
a corporate network. First,confirm that warp -settings has the correct
profile ID. If the profile ID is not theexpected value,
this might be an indication that the userisn't matching the rules you've defined in
your Cloudflare device profile settings.
Also, if any specific changes have been madeto the device profile settings,
you can use this file to ensure the user isreceiving those updates.
For example, if you've updated a deviceprofile to use the MASQUE tunneling type
instead of WireGuard,you can verify that the user has received
that update and will indeed attempt toconnect via MASQUE.
Daemon.log is a fairly detailed file thatcontains everything going on in WARP,
such as the debug logs.
But before we open the file,what is the WARP daemon?
It's the background process of WARP,also known as service,
depending on your operating system.
When WARP is installed,it's installed as both daemon,
the background process,and as a GUI, which is the interface you see
here. The GUI, warp-diag and warp-cli can allcommunicate with the Daemon.
There are multiple Daemon.log files and theirname chronologically.
Let's go over the file now.
Line by line, we'll look at how daemon.logshould look like when WARP connects as
expected. When WARP starts,it prints out its version information,
so we'll start there. Search for the string"warp \_ service :
Version :" and look for the most recententry.
That should be your current session.
Our team is optimizing warp-diag constantly,so the string we mentioned in this video
might change slightly in the future.
The registration contains all the necessaryinformation to connect the WARP client,
which is stored securely on the machine.
If the GUI detects a missing registration,it may attempt to obtain one if configured to
do so. Otherwise, it'll display missingregistration.
Once the registration is loaded,WARP will attempt to connect,
but only if configured to do soautomatically.
Otherwise, it will only attempt to connect ifit was previously connected.
After registration, WARP will then retrievethe device profile remotely via an API.
This includes the device configurations andmode that will be used.
It's very important to be aware that thedevice profile can be further influenced by a
local configuration file,which is used by an MDM provider,
such as Intune or Kandji.
For more information on Cloudflare MDMconfiguration,
you can refer to our documentation.
At this point, which components connect isdetermined by the mode.
If the mode contains the Tunnel component,for example Secure web gateway without DNS
filtering, we'll see "Initiate WARP." if themode contains the DNS component like Gateway
with DoH, we'll see "Initiate DNS".
If it contains both, like Gateway with WARPwill eventually see both.
Let's now review each.
Starting with initiate WARP for modes withthe Tunnel component.
The Tunnel component includes a firewall.
It starts off by allowing the tunnel endpointthrough the firewall and attempting to
This makes sure the end user will beconnected as fast as possible,
and this process is called Happy Eyeballs.
Once connected, a network interface iscreated and it begins the task of updating
the routing table and the firewall accordingto the exclude or include split tunnel
entries. These entries can be either domainsor IPs.
WARP will update the routing tableimmediately for any IPs,
but for domains, it will rely on a DNSresolution for these domains and will update
the routing table upon completion.
Once that's completed,WARP performs two connectivity tests,
one in the tunnel and one out of the tunnel.
Moving on to initiate DNS and this is formodes with DNS component.
For DNS, WARP will set itself as the defaultDNS global provider,
and forward all DNS requests to Cloudflarevia DNS over HTTPS or DoH.
And in order to do that,the following sequence needs to complete
successfully. First, attempt to connect tothe DoH endpoint.
Second, receive a DNS response from that DoHendpoint.
Fourth, update the system to use these IP'sas the DNS provider.
If all four steps happen without error,WARP then performs a series of DNS
connectivity checks. These are end to endtests which confirm that WARP is successfully
receiving DNS requests,forwarding them to Cloudflare for resolution,
and receiving a valid response.
Here are some additional tips to maketroubleshooting easier.
You should use the search function in yourtext editor to quickly locate terms like
error, DNS, or disconnected.
Also look for patterns such as repeatedentries.
These can point to specific issues.
And finally cross-referencing files from warp-settings,
warp-s tatus and daemon.log can revealinsights and a bigger picture.
For example, if warp -status showsdisconnected,
check daemon.log for error details and warp-settings for potential misconfigurations.
There are other files that provide morespecific information depending on your issue.
Our team is optimizing warp-diag constantly,so you might find more files in the future.
For an updated view on what you can find inwhich file,
check out our troubleshooting guide. You nowunderstand the basics of warp-diag .
If you're still experiencing issues afterfollowing these steps,
don't hesitate to reach out to our supportteam.
We're always here to help.
Thanks for watching and see you soon.
</page>
<page>
---
title: What is Cloudflare Tunnel? | Cloudflare Docs
description: Learn how Cloudflare Tunnel is like a private, secure pathway from
your computer to the Internet, so you don't have to leave the front door (your
network) wide open.
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/videos/what-is-cf-tunnel/
md: https://developers.cloudflare.com/videos/what-is-cf-tunnel/index.md
---
Learn how Cloudflare Tunnel is like a private, secure pathway from your computer to the Internet, so you don't have to leave the front door (your network) wide open.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Web Application Firewall (WAF) docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/404/
md: https://developers.cloudflare.com/waf/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Account-level WAF configuration · Cloudflare Web Application Firewall
(WAF) docs
description: The account-level Web Application Firewall (WAF) configuration
allows you to define a configuration once and apply it to multiple Enterprise
zones in your account.
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/account/
md: https://developers.cloudflare.com/waf/account/index.md
---
Note
This feature requires an Enterprise plan with a paid add-on.
The account-level Web Application Firewall (WAF) configuration allows you to define a configuration once and apply it to multiple Enterprise zones in your account.
Configure and deploy custom rulesets, rate limiting rulesets, and managed rulesets to multiple Enterprise zones, affecting all incoming traffic or only a subset (for example, all traffic to `/admin/*` URI paths in both `example.com` and `example.net`).
At the account level, WAF rules are grouped into rulesets. You can perform the following operations:
* Create and deploy [custom rulesets](https://developers.cloudflare.com/waf/account/custom-rulesets/)
* Create and deploy [rate limiting rulesets](https://developers.cloudflare.com/waf/account/rate-limiting-rulesets/)
* Deploy [managed rulesets](https://developers.cloudflare.com/waf/account/managed-rulesets/)
</page>
<page>
---
title: Analytics · Cloudflare Web Application Firewall (WAF) docs
description: "Refer to the following pages for more information on the available
analytics dashboards for Cloudflare security products:"
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/waf/analytics/
md: https://developers.cloudflare.com/waf/analytics/index.md
---
Refer to the following pages for more information on the available analytics dashboards for Cloudflare security products:
* [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/)
* [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/)
</page>
<page>
---
title: Changelog for managed rulesets · Cloudflare Web Application Firewall (WAF) docs
description: The WAF changelog provides information about changes to managed
rulesets and general updates to WAF protection.
lastUpdated: 2025-09-26T16:00:48.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/change-log/
md: https://developers.cloudflare.com/waf/change-log/index.md
---
The WAF changelog provides information about changes to managed rulesets and general updates to WAF protection.
## Changelog for managed rulesets
Cloudflare has a regular cadence of releasing updates and new rules to WAF managed rulesets. The updates either improve a rule's accuracy, lower false positives rates, or increase the protection due to a change in the threat landscape.
The release cycle for new rules happens on a 7-day cycle, typically every Monday or Tuesday depending on public holidays. For updates of existing rules, Cloudflare will initially deploy the updated rule as a `BETA` rule (denoted in rule description) and with a `beta` tag, before updating the original rule on the next release cycle. Cloudflare will deploy the updated or new rules into logging only mode (*Log* action), with `beta` and `new` tags. Most newly created rules will carry both the `beta` and `new` tags. Logging only mode allows you to identify any increases in security event volumes which look like potential false positives. On the following Monday (or Tuesday) the rules will change from logging only mode to the intended default action (**New Action** column in the changelog table), with the `beta` and `new` tags removed.
Cloudflare may also add rules on the same 7-day release cycle in disabled mode to make the remediation logic available to customers, who can activate the rule if needed. Having these rules in place allows Cloudflare to perform impact testing and performance checks without affecting traffic. These deactivated rules will not have the `beta` and `new` tags assigned to them.
Cloudflare is very proactive in responding to new vulnerabilities, which may need to be released outside of the 7-day cycle, defined as an Emergency Release.
Warning
[Ruleset overrides and tag overrides](https://developers.cloudflare.com/ruleset-engine/managed-rulesets/override-managed-ruleset/) apply to existing and **future** rules in the managed ruleset, which includes changes in regular and emergency releases.
If you do notice a new or updated rule generating an increased volume of security events, you can disable or change the rule from its *Default* action. Once you change a rule to use an action other than the default one, Cloudflare will not be able to override the rule action.
[View scheduled changes](https://developers.cloudflare.com/waf/change-log/scheduled-changes/)
[Subscribe to RSS](https://developers.cloudflare.com/changelog/rss/waf.xml)
## General updates
For more general updates to the WAF, refer to [general updates](https://developers.cloudflare.com/waf/change-log/general-updates/).
</page>
<page>
---
title: Concepts · Cloudflare Web Application Firewall (WAF) docs
description: The Cloudflare Web Application Firewall (Cloudflare WAF) checks
incoming web and API requests and filters undesired traffic based on sets of
rules called rulesets. The matching engine that powers the WAF rules supports
the wirefilter syntax using the Rules language.
lastUpdated: 2025-10-17T11:29:44.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/concepts/
md: https://developers.cloudflare.com/waf/concepts/index.md
---
The Cloudflare Web Application Firewall (Cloudflare WAF) checks incoming web and API requests and filters undesired traffic based on sets of rules called rulesets. The matching engine that powers the WAF rules supports the wirefilter syntax using the [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/).
What is a Web Application Firewall?
A Web Application Firewall or WAF creates a shield between a web app and the Internet. This shield can help mitigate many common attacks. For a more thorough definition, refer to [Web Application Firewall explained](https://www.cloudflare.com/learning/ddos/glossary/web-application-firewall-waf/) in the Learning Center.
## Rules and rulesets
A [rule](https://developers.cloudflare.com/ruleset-engine/about/rules/) defines a filter and an action to perform on the incoming requests that match the filter.
A [ruleset](https://developers.cloudflare.com/ruleset-engine/about/rulesets/) is an ordered set of rules that you can apply to traffic on the Cloudflare global network.
## Main components
The Cloudflare WAF includes:
* [Managed Rules](https://developers.cloudflare.com/waf/managed-rules/) (for example, the [Cloudflare Managed Ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/)), which are signature-based rules created by Cloudflare that provide immediate protection against known attacks.
* [Traffic detections](https://developers.cloudflare.com/waf/detections/) (for example, bot score and attack score) that enrich requests with metadata.
* User-defined rules for your specific needs, including [custom rules](https://developers.cloudflare.com/waf/custom-rules/) and [rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/).
## Detection versus mitigation
The two main roles of the Cloudflare WAF are the following:
* **Detection**: Run incoming requests through one or more [traffic detections](https://developers.cloudflare.com/waf/detections/) to find malicious or potentially malicious activity. The scores from enabled detections are available in the [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) dashboard, where you can analyze your security posture and determine the most appropriate mitigation rules.
* **Mitigation**: Blocks, challenges, or throttles requests through different mitigation features such as [custom rules](https://developers.cloudflare.com/waf/custom-rules/), [Managed Rules](https://developers.cloudflare.com/waf/managed-rules/), and [rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/). Rules that mitigate traffic can include scores from traffic scans in their expressions to better address possibly malicious requests.
Warning
Enabling traffic detections will not apply any mitigation measures to incoming traffic; detections only provide signals that you can use to define your attack mitigation strategy.
### Available traffic detections
The WAF currently provides the following detections for finding security threats in incoming requests:
* [**Attack score**](https://developers.cloudflare.com/waf/detections/attack-score/): Checks for known attack variations and malicious payloads. Scores traffic on a scale from 1 (likely to be malicious) to 99 (unlikely to be malicious).
* [**Leaked credentials**](https://developers.cloudflare.com/waf/detections/leaked-credentials/): Scans incoming requests for credentials (usernames and passwords) previously leaked from data breaches.
* [**Malicious uploads**](https://developers.cloudflare.com/waf/detections/malicious-uploads/): Scans content objects, such as uploaded files, for malicious signatures like malware.
* [**Firewall for AI**](https://developers.cloudflare.com/waf/detections/firewall-for-ai/): Helps protect your services powered by large language models (LLMs) against abuse.
* [**Bot score**](https://developers.cloudflare.com/bots/concepts/bot-score/): Scores traffic on a scale from 1 (likely to be a bot) to 99 (likely to be human).
To enable traffic detections in the Cloudflare dashboard, go to the Security **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
Note
Currently, you cannot manage the [bot score](https://developers.cloudflare.com/bots/concepts/bot-score/) and [attack score](https://developers.cloudflare.com/waf/detections/attack-score/) detections from the **Settings** page. Refer to the documentation of each feature for availability details.
***
## Rule execution order
Cloudflare evaluates different types of rules when processing incoming requests. The rule execution order is the following:
1. [IP Access Rules](https://developers.cloudflare.com/waf/tools/ip-access-rules/)
2. [Firewall rules](https://developers.cloudflare.com/firewall/cf-firewall-rules/) (deprecated)
3. [Custom rulesets](https://developers.cloudflare.com/waf/account/custom-rulesets/)
4. [Custom rules](https://developers.cloudflare.com/waf/custom-rules/)
5. [Rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/)
6. [Managed Rules](https://developers.cloudflare.com/waf/managed-rules/)
7. [Cloudflare Rate Limiting](https://developers.cloudflare.com/waf/reference/legacy/old-rate-limiting/) (previous version, deprecated)
Rules are evaluated in order. If there is a match for a rule with a [terminating action](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/), the rule evaluation will stop and the action will be executed immediately. Rules with a non-terminating action (such as *Log*) will not prevent subsequent rules from being evaluated and executed. For more information on how rules are evaluated, refer to [Rule evaluation](https://developers.cloudflare.com/ruleset-engine/about/rules/#rule-evaluation) in the Ruleset Engine documentation.
For more information on the phases where each WAF feature will execute, refer to [WAF phases](https://developers.cloudflare.com/waf/reference/phases/).
</page>
<page>
---
title: Custom rules · Cloudflare Web Application Firewall (WAF) docs
description: Custom rules allow you to control incoming traffic by filtering
requests to a zone. They work as customized web application firewall (WAF)
rules that you can use to perform actions like Block or Managed Challenge on
incoming requests. You can also use the Skip action in a custom rule to skip
one or more Cloudflare security features.
lastUpdated: 2026-02-06T14:49:59.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/custom-rules/
md: https://developers.cloudflare.com/waf/custom-rules/index.md
---
Custom rules allow you to control incoming traffic by filtering requests to a zone. They work as customized web application firewall (WAF) rules that you can use to perform actions like *Block* or *Managed Challenge* on incoming requests. You can also use the *Skip* action in a custom rule to [skip one or more Cloudflare security features](https://developers.cloudflare.com/waf/custom-rules/skip/).
In the [new security dashboard](https://developers.cloudflare.com/security/), custom rules are one of the available types of [security rules](https://developers.cloudflare.com/security/rules/). Security rules perform security-related actions on incoming requests that match specified filters.
Like other rules evaluated by Cloudflare's [Ruleset Engine](https://developers.cloudflare.com/ruleset-engine/), custom rules have the following basic parameters:
* An [expression](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/) that specifies the criteria you are matching traffic on using the [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/).
* An [action](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/) that specifies what to perform when there is a match for the rule.
Custom rules are evaluated in order, and some actions like *Block* will stop the evaluation of other rules. For more details on actions and their behavior, refer to [Actions](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/).
To define sets of custom rules that apply to more than one zone, use [custom rulesets](https://developers.cloudflare.com/waf/account/custom-rulesets/). At the zone level, all customers can create and deploy custom rulesets. Custom rulesets at the account level require an Enterprise plan with a paid add-on.
Note
Currently, the Cloudflare dashboard does not support working with custom rulesets at the zone level. You will need to [use the Cloudflare API](https://developers.cloudflare.com/waf/custom-rules/create-api/) to configure or deploy these rulesets.
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Number of rules | 5 | 20 | 100 | 1,000 |
| Supported actions | All except Log | All except Log | All except Log | All |
| Regex support | No | No | Yes | Yes |
| Number of custom rulesets (zone) | 1 | 2 | 5 | 10 |
| Account-level custom rulesets | No | No | No | Paid add-on |
The maximum number of custom rules applies to an entire [phase](https://developers.cloudflare.com/ruleset-engine/about/phases/). Each scope (zone or account) has a separate maximum number of rules, counted in the following way:
* Zone: All custom rules plus all the rules across custom rulesets defined at the zone level.
* Account: All the rules across custom rulesets defined at the account level.
***
## Next steps
Refer to the following pages for instructions on creating custom rules:
* [Create a custom rule in the dashboard](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/)
* [Create a custom rule via API](https://developers.cloudflare.com/waf/custom-rules/create-api/)
* [WAF custom rules configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/waf-custom-rules/)
For examples of using custom rules to address common use cases, refer to [Common use cases](https://developers.cloudflare.com/waf/custom-rules/use-cases/).
</page>
<page>
---
title: Traffic detections · Cloudflare Web Application Firewall (WAF) docs
description: Traffic detections check incoming requests for malicious or
potentially malicious activity. Each enabled detection provides one or more
attributes classifying incoming requests. These attributes are available as
filters in the Security Analytics dashboard, and use can use them in rule
expressions.
lastUpdated: 2026-02-06T14:49:59.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/detections/
md: https://developers.cloudflare.com/waf/detections/index.md
---
Traffic detections check incoming requests for malicious or potentially malicious activity. Each enabled detection provides one or more attributes classifying incoming requests. These attributes are available as filters in the [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) dashboard, and use can use them in rule expressions.
Once enabled, detections are always on, even if there are no security rules configured with the attributes that detections provide. This means that you can use detection results in [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) to identify traffic patterns and check for potentially malicious traffic. For example, you can analyze incoming traffic based on attack score, bot score, [content scan results](https://developers.cloudflare.com/waf/detections/malicious-uploads/), or the [presence of personally identifiable information (PII)](https://developers.cloudflare.com/waf/detections/firewall-for-ai/) in large language model (LLM) prompts.
Cloudflare currently provides the following detections for finding security threats in incoming requests:
* [WAF attack score](https://developers.cloudflare.com/waf/detections/attack-score/)
* [Leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/)
* [Malicious uploads detection](https://developers.cloudflare.com/waf/detections/malicious-uploads/)
* [Firewall for AI (beta)](https://developers.cloudflare.com/waf/detections/firewall-for-ai/)
* [Bot score](https://developers.cloudflare.com/bots/concepts/bot-score/)
## Availability
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Malicious uploads detection | No | No | No | Paid add-on |
| Leaked credentials detection | Yes | Yes | Yes | Yes |
| Leaked credentials fields | Password Leaked | Password Leaked, User and Password Leaked | Password Leaked, User and Password Leaked | All leaked credentials fields |
| Number of custom detection locations | 0 | 0 | 0 | 10 |
| Attack score | No | No | One field only | Yes |
| Firewall for AI (beta) | No | No | No | Yes |
For more information on bot score, refer to [Bot scores](https://developers.cloudflare.com/bots/concepts/bot-score/).
## Turn on a detection
To turn on a traffic detection:
* New dashboard
1. In the Cloudflare dashboard, go to the Security **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
2. Filter by **Detection tools**.
3. Turn on the desired detections.
* Old dashboard
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com/), and select your account and domain.
2. Go to **Security** > **Settings**.
3. Under **Incoming traffic detections**, turn on the desired detections.
Enabled detections will run for all incoming traffic.
Notes
On Free plans, the leaked credentials detection is enabled by default, and no action is required.
Currently, you cannot manage the [bot score](https://developers.cloudflare.com/bots/concepts/bot-score/) and [attack score](https://developers.cloudflare.com/waf/detections/attack-score/) detections from the **Settings** page. Refer to the documentation of each feature for availability details.
## More resources
For more information on detection versus mitigation, refer to [Concepts](https://developers.cloudflare.com/waf/concepts/#detection-versus-mitigation).
</page>
<page>
---
title: Get started · Cloudflare Web Application Firewall (WAF) docs
description: The Cloudflare Web Application Firewall (Cloudflare WAF) checks
incoming web and API requests and filters undesired traffic based on sets of
rules called rulesets.
lastUpdated: 2026-02-04T11:12:58.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/get-started/
md: https://developers.cloudflare.com/waf/get-started/index.md
---
The Cloudflare Web Application Firewall (Cloudflare WAF) checks incoming web and API requests and filters undesired traffic based on sets of rules called rulesets.
This page will guide you through the recommended initial steps for configuring the WAF to get immediate protection against the most common attacks.
Refer to [Concepts](https://developers.cloudflare.com/waf/concepts/) for more information on WAF concepts, main components, and roles.
Note
This guide focuses on configuring WAF for individual domains, known as zones. The WAF configuration is also available at the account level for Enterprise customers with a paid add-on.
## Before you begin
* Make sure that you have [set up a Cloudflare account](https://developers.cloudflare.com/fundamentals/account/) and [added your domain](https://developers.cloudflare.com/fundamentals/manage-domains/add-site/) to Cloudflare.
* Users on the Free plan have access to the Cloudflare Free Managed Ruleset, a subset of the Cloudflare Managed Ruleset. The Free Managed Ruleset is deployed by default on Free plans and is not specifically covered in this guide.\
If you are on a Free plan, you may skip to [5. Review traffic in security dashboards](#5-review-traffic-in-security-dashboards).
## 1. Deploy the Cloudflare Managed Ruleset
The [Cloudflare Managed Ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/) protects against Common Vulnerabilities and Exposures (CVEs) and known attack vectors. This ruleset is designed to identify common attacks using signatures, while generating low false positives. Rule changes are published on a weekly basis in the [WAF changelog](https://developers.cloudflare.com/waf/change-log/). Cloudflare may also add rules at any time during emergency releases for high profile zero-day protection.
* New dashboard
1. In the Cloudflare dashboard, go to the Security **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
2. (Optional) Filter by **Web application exploits**.
3. Turn on **Cloudflare managed ruleset**.
* Old dashboard
1. Log in to the [Cloudflare dashboard](https://dash.cloudflare.com), and select your account and domain.
2. Go to **Security** > **WAF** and select the **Managed rules** tab.
3. Under **Managed Rulesets**, select **Deploy** next to the Cloudflare Managed Ruleset.
Default settings and ruleset customization
By default, the Cloudflare Managed Ruleset enables only a subset of rules and it is designed to strike a balance between protection and false positives. You can review and enable additional rules based on your application technology stack.
In particular situations, enabling the managed ruleset can cause some false positives. False positives are legitimate requests inadvertently mitigated by the WAF. For information on addressing false positives, refer to [Troubleshoot managed rules](https://developers.cloudflare.com/waf/managed-rules/troubleshooting/#troubleshoot-false-positives).
If you are testing the WAF against pentesting tools, it is recommended that you enable all rules by using the following ruleset configuration:
* **Ruleset action**: *Block*
* **Ruleset status**: *Enabled* (enables all rules in the ruleset)
For more information on configuring the Cloudflare Managed Ruleset in the dashboard, refer to [Cloudflare Managed Ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/#configure-in-the-dashboard).
## 2. Create custom rule based on WAF attack score
Note
WAF attack score is only available to Business customers (limited access to a single field) and Enterprise customers (full access).
[WAF attack score](https://developers.cloudflare.com/waf/detections/attack-score/) is a machine-learning layer that complements Cloudflare's managed rulesets, providing additional protection against [SQL injection](https://www.cloudflare.com/learning/security/threats/sql-injection/) (SQLi), [cross-site scripting](https://www.cloudflare.com/learning/security/threats/cross-site-scripting/) (XSS), and many [remote code execution](https://www.cloudflare.com/learning/security/what-is-remote-code-execution/) (RCE) attacks. It helps identify rule bypasses and potentially new, undiscovered attacks.
If you are an Enterprise customer, do the following:
1. Reach out to your account team to get access to WAF attack score.
2. [Create a custom rule](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/) using the Attack Score field:
* **When incoming requests match**:
| Field | Operator | Value |
| - | - | - |
| WAF Attack Score | less than | `20` |
* **Choose action**: Block
If you are on a Business plan, create a custom rule as mentioned above but use the [WAF Attack Score Class](https://developers.cloudflare.com/waf/detections/attack-score/#available-scores) field instead. For example, you could use the following rule expression: `WAF Attack Score Class equals Attack`.
## 3. Create custom rule based on bot score
Note
Bot score is only available to Enterprise customers with [Bot Management](https://developers.cloudflare.com/bots/get-started/bot-management/). Customers on Pro and Business plans may enable [Super Bot Fight mode](https://developers.cloudflare.com/bots/get-started/super-bot-fight-mode/) instead.
Customers with access to [Bot Management](https://developers.cloudflare.com/bots/get-started/bot-management/) can block automated traffic (for example, from [bots scraping online content](https://www.cloudflare.com/learning/bots/what-is-content-scraping/)) using a custom rule with bot score, preventing this traffic from hitting your application.
[Create a custom rule](https://developers.cloudflare.com/waf/custom-rules/create-dashboard/) using the Bot Score and Verified Bot fields:
* **When incoming requests match**:
| Field | Operator | Value | Logic |
| - | - | - | - |
| Bot Score | less than | `20` | And |
| Verified Bot | equals | Off | |
* **Choose action**: Managed Challenge
For a more comprehensive example of a baseline protection against malicious bots, refer to [Challenge bad bots](https://developers.cloudflare.com/waf/custom-rules/use-cases/challenge-bad-bots/#general-protection).
For more information about the bot-related fields you can use in expressions, refer to [Bot Management variables](https://developers.cloudflare.com/bots/reference/bot-management-variables/).
Once you have deployed the Cloudflare Managed Ruleset and rules based on attack score and bot score you will have achieved substantial protection, limiting the chance of false positives.
## 4. Optional - Deploy the Cloudflare OWASP Core Ruleset
After configuring the Cloudflare Managed Ruleset and attack score, you can also deploy the [Cloudflare OWASP Core Ruleset](https://developers.cloudflare.com/waf/managed-rules/reference/owasp-core-ruleset/). This managed ruleset is Cloudflare's implementation of the OWASP ModSecurity Core Rule Set. Its attack coverage significantly overlaps with Cloudflare Managed Ruleset by detecting common attack vectors such as SQLi and XSS.
Warning
The Cloudflare OWASP Core Ruleset is prone to false positives and offers only marginal benefits when added on top of Cloudflare Managed Ruleset and WAF attack score. If you decide to deploy this managed ruleset, you will need to monitor and adjust its settings based on your traffic to prevent false positives.
* New dashboard
1. In the Cloudflare dashboard, go to the Security **Settings** page.
[Go to **Settings**](https://dash.cloudflare.com/?to=/:account/:zone/security/settings)
2. (Optional) Filter by **Web application exploits**.
3. Turn on **OWASP Core**.\
This will deploy the Cloudflare OWASP Core Ruleset with the default configuration: paranoia level = *PL1* and score threshold = *Medium - 40 and higher*.
* Old dashboard
1. Go to your domain > **Security** > **WAF** and select the **Managed rules** tab.
2. Under **Managed Rulesets**, select **Deploy** next to the Cloudflare OWASP Core Ruleset.\
This will deploy the ruleset with the default configuration: paranoia level = *PL1* and score threshold = *Medium - 40 and higher*.
Ruleset configuration
Unlike the signature-based Cloudflare Managed Ruleset, the Cloudflare OWASP Core Ruleset is score-based. You select a certain paranoia level (levels vary from *PL1* to *PL4*, where *PL1* is the lowest level), which enables an increasing larger group of rules. You also select a score threshold, which decides when to perform the configured action. Low paranoia with a high score threshold usually leads to fewer false positives. For an example of how the OWASP Core Ruleset is evaluated, refer to [OWASP evaluation example](https://developers.cloudflare.com/waf/managed-rules/reference/owasp-core-ruleset/example/).
Follow one of these strategies to configure the ruleset according to your needs:
* Start from a strict configuration (paranoia level = *PL4*, score threshold = *Low - 60 and higher*). Reduce the score threshold and paranoia level until you achieve a good false positives/true positives rate for your incoming traffic.
* Alternatively, start from a more permissive configuration (paranoia level = *PL1*, score threshold = *High - 25 and higher*) and increase both parameters to adjust your protection, trying to keep a low number of false positives.
For more information on configuring the Cloudflare OWASP Core Ruleset in the dashboard, refer to [Configure in the dashboard](https://developers.cloudflare.com/waf/managed-rules/reference/owasp-core-ruleset/configure-dashboard/#ruleset-level-configuration).
## 5. Review traffic in security dashboards
Note
Users on the Free plan only have access to Security Events.
After setting up your WAF configuration, review how incoming traffic is being affected by your current settings using the following dashboards:
* Use [Security Analytics](https://developers.cloudflare.com/waf/analytics/security-analytics/) to explore all traffic, including traffic not affected by WAF mitigation measures. All data provided by [traffic detections](https://developers.cloudflare.com/waf/concepts/#available-traffic-detections) is available in this dashboard.
* Use [Security Events](https://developers.cloudflare.com/waf/analytics/security-events/) to get more information about requests that are being mitigated by Cloudflare security products.
Enterprise customers can also obtain data about HTTP requests and security events using [Cloudflare Logs](https://developers.cloudflare.com/logs/).
## 6. Optional - Next steps
After configuring the WAF based on the information in the previous sections, you should have a strong base protection against possible threats to your applications.
You can explore the following recommendations to get additional protection for specific use cases.
### Allowlist certain IP addresses
Create a custom rule to [allow traffic from IP addresses in allowlist only](https://developers.cloudflare.com/waf/custom-rules/use-cases/allow-traffic-from-ips-in-allowlist/).
### Block specific countries
Create a custom rule to [block traffic from specific countries](https://developers.cloudflare.com/waf/custom-rules/use-cases/block-traffic-from-specific-countries/).
### Define rate limits
Create a rate limiting rule to [apply rate limiting on a login endpoint](https://developers.cloudflare.com/waf/rate-limiting-rules/use-cases/#example-1).
### Prevent credential stuffing attacks
Use [leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/) to prevent [credential stuffing](https://www.cloudflare.com/learning/bots/what-is-credential-stuffing/) attacks on your applications.
### Prevent users from uploading malware into your applications
Note
Available to Enterprise customers with a paid add-on.
[Use WAF content scanning](https://developers.cloudflare.com/waf/detections/malicious-uploads/get-started/) to scan content being uploaded to your application, searching for malicious content.
### Get additional security for your APIs
Note
Available to Enterprise customers.
Cloudflare protects your APIs from new and known application attacks and exploits such as SQL injection attacks. API-specific security products extend those protections to the unique risks in APIs such as API discovery and authentication management.
For more information on Cloudflare's API security features, refer to [Cloudflare API Shield](https://developers.cloudflare.com/api-shield/).
</page>
<page>
---
title: Glossary · Cloudflare Web Application Firewall (WAF) docs
description: Review the definitions for terms used across Cloudflare's WAF documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/glossary/
md: https://developers.cloudflare.com/waf/glossary/index.md
---
Review the definitions for terms used across Cloudflare's WAF documentation.
| Term | Definition |
| - | - |
| allowlist | An allowlist is a list of items (usually websites, IP addresses, email addresses, etc.) that are permitted to access a system. |
| attack score | A number from 1 (likely malicious) to 99 (likely clean) classifying how likely an incoming request is malicious or not. Allows you to detect new attack techniques before they are publicly known. |
| blocklist | A blocklist is a list of items (usually websites, IP addresses, email addresses, etc.) that are prevented from accessing a system. |
| content object | A content object is any binary part of a request body (as detected by Cloudflare systems) that does not match any of the following content types: `text/html`, `text/x-shellscript`, `application/json`, `text/csv`, or `text/xml`. |
| credential stuffing | Credential stuffing is the automated injection of stolen username and password pairs (known as "credentials") into website login forms, trying to gain access to user accounts. |
| firewall | A firewall is a security system that monitors and controls network traffic based on a set of security rules. |
| leaked credentials | Leaked credentials refers to sensitive authentication information disclosed in some way (for example, due to misconfigurations, data breaches, or simple human error), allowing other parties to gain access to digital resources.Credentials may include usernames, passwords, API keys, authentication tokens, or private keys. |
| LLM | A machine learning model that can comprehend and generate human language text. It works by analyzing massive data sets of language. |
| mitigated request | A request to which Cloudflare applied a terminating action such as block or challenge. |
| paranoia level | Classifies rules of the OWASP managed ruleset according to their aggressiveness. |
| prompt injection | The process of overwriting the system prompt for a large language model (LLM), which instructs the LLM on how to respond to user input. |
| rate limiting | Rate limiting is a technique used in computer systems to control the rate at which requests are processed. It can be used as a security measure to prevent attacks, or to limit resource usage in your origin servers. |
| rule characteristics | The set of parameters of a rate limiting rule that define how Cloudflare tracks the rate for the rule. |
| SIEM | A Security Information and Event Management (SIEM) solution collects, analyzes, and correlates data to help manage security incidents, detect anomalies, and meet compliance requirements. |
| threat score | The threat score was a score from `0` (zero risk) to `100` (high risk) classifying the IP reputation of a visitor. Currently, the threat score is always `0` (zero). |
</page>
<page>
---
title: Managed Rules · Cloudflare Web Application Firewall (WAF) docs
description: "Cloudflare provides pre-configured managed rulesets that protect
against web application exploits such as the following:"
lastUpdated: 2025-12-10T18:13:35.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/managed-rules/
md: https://developers.cloudflare.com/waf/managed-rules/index.md
---
Cloudflare provides pre-configured managed rulesets that protect against web application exploits such as the following:
* Zero-day vulnerabilities
* Top-10 attack techniques
* Use of stolen/leaked credentials
* Extraction of sensitive data
Managed rulesets are [regularly updated](https://developers.cloudflare.com/waf/change-log/). Each rule has a default action that varies according to the severity of the rule. You can adjust the behavior of specific rules, choosing from several possible actions.
Rules of managed rulesets have associated tags (such as `wordpress`) that allow you to search for a specific group of rules and configure them in bulk.
## Available managed rulesets
* [**Cloudflare Managed Ruleset**](https://developers.cloudflare.com/waf/managed-rules/reference/cloudflare-managed-ruleset/): Created by the Cloudflare security team, this ruleset provides fast and effective protection for all of your applications. The ruleset is updated frequently to cover new vulnerabilities and reduce false positives.\
Ruleset ID: efb7b8c949ac4650a09736fc376e9aee
* [**Cloudflare OWASP Core Ruleset**](https://developers.cloudflare.com/waf/managed-rules/reference/owasp-core-ruleset/): Cloudflare's implementation of the Open Web Application Security Project, or OWASP ModSecurity Core Rule Set. Cloudflare routinely monitors for updates from OWASP based on the latest version available from the official code repository.\
Ruleset ID: 4814384a9e5d4991b9815dcfc25d2f1f
* [**Cloudflare Exposed Credentials Check**](https://developers.cloudflare.com/waf/managed-rules/reference/exposed-credentials-check/): Deploy an automated credentials check on your end-user authentication endpoints. For any credential pair, the Cloudflare WAF performs a lookup against a public database of stolen credentials. Cloudflare recommends that you use [leaked credentials detection](https://developers.cloudflare.com/waf/detections/leaked-credentials/) instead of this ruleset.\
Ruleset ID: c2e184081120413c86c3ab7e14069605
* **Cloudflare Free Managed Ruleset**: Available on all Cloudflare plans. Designed to provide mitigation against high and wide impacting vulnerabilities. The rules are safe to deploy on most applications. If you deployed the Cloudflare Managed Ruleset for your site, you do not need to deploy this managed ruleset.\
Ruleset ID: 77454fe2d30c4220b5701f6fdfb893ba
The following managed rulesets run in a response phase:
* [**Cloudflare Sensitive Data Detection**](https://developers.cloudflare.com/waf/managed-rules/reference/sensitive-data-detection/): Created by Cloudflare to address common data loss threats. These rules monitor the download of specific sensitive data — for example, financial and personally identifiable information.\
Ruleset ID: e22d83c647c64a3eae91b71b499d988e
## Availability
The managed rulesets you can deploy depend on your Cloudflare plan.
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | Yes | Yes | Yes | Yes |
| Free Managed Ruleset | Yes | Yes | Yes | Yes |
| Cloudflare Managed Ruleset | No | Yes | Yes | Yes |
| Cloudflare OWASP Core Ruleset | No | Yes | Yes | Yes |
| Cloudflare Exposed Credentials Check | No | Yes | Yes | Yes |
| Cloudflare Sensitive Data Detection | No | No | No | Paid add-on |
## Customize the behavior of managed rulesets
To customize the behavior of managed rulesets, do one of the following:
* [Create exceptions](https://developers.cloudflare.com/waf/managed-rules/waf-exceptions/) to skip the execution of managed rulesets or some of their rules under certain conditions.
* [Configure overrides](https://developers.cloudflare.com/waf/managed-rules/deploy-zone-dashboard/#configure-a-managed-ruleset) to change the rule action or disable one or more rules of managed rulesets. Overrides can affect an entire managed ruleset, specific tags, or specific rules in the managed ruleset.
Exceptions have priority over overrides.
Important
Ruleset overrides and tag overrides apply to both existing and **future** rules in the managed ruleset. If you want to override existing rules only, you must use rule overrides.
## Zone-level deployment
At the zone level, you can only deploy each managed ruleset once. At the [account level](https://developers.cloudflare.com/waf/account/managed-rulesets/) you can deploy each managed ruleset multiple times.
## Important remarks
Cloudflare analyzes the body of incoming requests up to a certain maximum size that varies according to your Cloudflare plan:
* For Enterprise customers, the maximum body size is 128 KB.
* For other paid plans, the limit is lower by default — reach out to your account team or to Cloudflare Support to increase the limit.
* For users in the Free plan, the limit is 1 MB.
This means that the behavior of specific managed rules that analyze request bodies can vary according to your current plan. For example, the OWASP Core Ruleset might have a higher rate of false positives with larger payload sizes because analyzing more data increases the likelihood that the total score exceeds the [threshold](https://developers.cloudflare.com/waf/managed-rules/reference/owasp-core-ruleset/concepts/#score-threshold).
If included in your plan, you can use [request body fields](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/?field-category=Body) such as `http.request.body.truncated` or `http.request.headers.truncated` in [custom rules](https://developers.cloudflare.com/waf/custom-rules/) that apply appropriate actions to requests that have not been fully analyzed by Cloudflare due to the maximum body size.
</page>
<page>
---
title: Rate limiting rules · Cloudflare Web Application Firewall (WAF) docs
description: Rate limiting rules allow you to define rate limits for requests
matching an expression, and the action to perform when those rate limits are
reached.
lastUpdated: 2026-02-06T14:49:59.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waf/rate-limiting-rules/
md: https://developers.cloudflare.com/waf/rate-limiting-rules/index.md
---
Rate limiting rules allow you to define rate limits for requests matching an expression, and the action to perform when those rate limits are reached.
In the [new security dashboard](https://developers.cloudflare.com/security/), rate limiting rules are one of the available types of [security rules](https://developers.cloudflare.com/security/rules/). Security rules perform security-related actions on incoming requests that match specified filters.
Some Enterprise customers can create [rate limiting rulesets](https://developers.cloudflare.com/waf/account/rate-limiting-rulesets/) at the account level that they can deploy to multiple Enterprise zones.
## Rule parameters
Like other rules evaluated by Cloudflare's [Ruleset Engine](https://developers.cloudflare.com/ruleset-engine/), rate limiting rules have the following basic parameters:
* An [expression](https://developers.cloudflare.com/ruleset-engine/rules-language/expressions/) that specifies the criteria you are matching traffic on using the [Rules language](https://developers.cloudflare.com/ruleset-engine/rules-language/).
* An [action](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/) that specifies what to perform when there is a match for the rule and any additional conditions are met. In the case of rate limiting rules, the action occurs when the rate reaches the specified limit.
Besides these two parameters, rate limiting rules require the following additional parameters:
* **Characteristics**: The set of parameters that define how Cloudflare tracks the rate for this rule.
* **Period**: The period of time to consider (in seconds) when evaluating the rate.
* **Requests per period**: The number of requests over the period of time that will trigger the rate limiting rule.
* **Duration** (or mitigation timeout): Once the rate is reached, the rate limiting rule blocks further requests for the period of time defined in this field.
* **Action behavior**: By default, Cloudflare will apply the rule action for the configured duration (or mitigation timeout), regardless of the request rate during this period. Some Enterprise customers can configure the rule to [throttle requests](https://developers.cloudflare.com/waf/rate-limiting-rules/parameters/#with-the-following-behavior) over the maximum rate, allowing incoming requests when the rate is lower than the configured limit.
Refer to [Rate limiting parameters](https://developers.cloudflare.com/waf/rate-limiting-rules/parameters/) for more information on mandatory and optional parameters.
Refer to [How Cloudflare determines the request rate](https://developers.cloudflare.com/waf/rate-limiting-rules/request-rate/) to learn how Cloudflare uses the parameters above when determining the rate of incoming requests.
## Important remarks
* Rate limiting rules are evaluated in order, and some actions like *Block* will stop the evaluation of other rules. For more details on actions and their behavior, refer to [Actions](https://developers.cloudflare.com/ruleset-engine/rules-language/actions/).
* Rate limiting rules are not designed to allow a precise number of requests to reach the origin server. In some situations, there may be a delay (up to a few seconds) between detecting a request and updating internal counters. Due to this delay, excess requests could still reach the origin server before Cloudflare enforces a mitigation action (such as blocking or challenging) in our global network.
* Applying rate limiting rules to verified bots might affect Search Engine Optimization (SEO). For more information, refer to [Improve SEO](https://developers.cloudflare.com/fundamentals/performance/improve-seo/).
***
## Availability
| Feature | Free | Pro | Business | Enterprise with app security | Enterprise with Advanced Rate Limiting |
| - | - | - | - | - | - |
| Available fields in rule expression | Path, [Verified Bot](https://developers.cloudflare.com/ruleset-engine/rules-language/fields/reference/cf.bot_management.verified_bot/) | Host, URI, Path, Full URI, Query, Verified Bot | Host, URI, Path, Full URI, Query, Method, Source IP, User Agent, Verified Bot | General request fields, request header fields, Verified Bot, Bot Management fields[1](#user-content-fn-1) | General request fields, request header fields, Verified Bot, Bot Management fields[1](#user-content-fn-1), request body fields[2](#user-content-fn-2) |
| Counting characteristics | IP | IP | IP, IP with NAT support | IP, IP with NAT support | IP, IP with NAT support, Query, Host, Headers, Cookie, ASN, Country, Path, JA3/JA4 Fingerprint[1](#user-content-fn-1), JSON field value[2](#user-content-fn-2), Body[2](#user-content-fn-2), Form input value[2](#user-content-fn-2), Custom |
| Custom counting expression | No | No | Yes | Yes | Yes |
| Available fields in counting expression | N/A | N/A | All rule expression fields, Response code, Response headers | All rule expression fields, Response code, Response headers | All rule expression fields, Response code, Response headers |
| Counting model | Number of requests | Number of requests | Number of requests | Number of requests | Number of requests, [complexity score](https://developers.cloudflare.com/waf/rate-limiting-rules/request-rate/#complexity-based-rate-limiting) |
| Rate limiting action behavior | Perform action during mitigation period | Perform action during mitigation period | Perform action during mitigation period | Perform action during mitigation period, Throttle requests above rate with block action | Perform action during mitigation period, Throttle requests above rate with block action |
| Counting periods | 10 s | All supported values up to 1 min[3](#user-content-fn-3) | All supported values up to 10 min[3](#user-content-fn-3) | All supported values up to 65,535 s[3](#user-content-fn-3) | All supported values up to 65,535 s[3](#user-content-fn-3) |
| Mitigation timeout periods | 10 s | All supported values up to 1 h[3](#user-content-fn-3) | All supported values up to 1 day[3](#user-content-fn-3) | All supported values up to 1 day[3](#user-content-fn-3) [4](#user-content-fn-4) | All supported values up to 1 day[3](#user-content-fn-3) [4](#user-content-fn-4) |
| Number of rules | 1 | 2 | 5 | 5 or more[5](#user-content-fn-5) | 100 |
Footnotes
1: Only available to Enterprise customers who have purchased [Bot Management](https://developers.cloudflare.com/bots/plans/bm-subscription/).
2: Availability depends on your WAF plan.
3: List of supported counting/mitigation period values in seconds:\
10, 15, 20, 30, 40, 45, 60 (1 min), 90, 120 (2 min), 180 (3 min), 240 (4 min), 300 (5 min), 480, 600 (10 min), 900, 1200 (20 min), 1800, 2400, 3600 (1 h), 65535, 86400 (1 day).\
Not all values are available on all plans.
4: Enterprise customers can specify a custom mitigation timeout period via API.
5: Enterprise customers must have application security on their contract to get access to rate limiting rules. The number of rules depends on the exact contract terms.
## Footnotes
1. Only available to Enterprise customers who have purchased [Bot Management](https://developers.cloudflare.com/bots/plans/bm-subscription/). [↩](#user-content-fnref-1) [↩2](#user-content-fnref-1-2) [↩3](#user-content-fnref-1-3)
2. Availability depends on your WAF plan. [↩](#user-content-fnref-2) [↩2](#user-content-fnref-2-2) [↩3](#user-content-fnref-2-3) [↩4](#user-content-fnref-2-4)
3. Supported period values in seconds:\
10, 15, 20, 30, 40, 45, 60 (1 min), 90, 120 (2 min), 180 (3 min), 240 (4 min), 300 (5 min), 480, 600 (10 min), 900, 1200 (20 min), 1800, 2400, 3600 (1 h), 65535, 86400 (1 day). [↩](#user-content-fnref-3) [↩2](#user-content-fnref-3-2) [↩3](#user-content-fnref-3-3) [↩4](#user-content-fnref-3-4) [↩5](#user-content-fnref-3-5) [↩6](#user-content-fnref-3-6) [↩7](#user-content-fnref-3-7) [↩8](#user-content-fnref-3-8)
4. Enterprise customers can specify a custom mitigation timeout period via API. [↩](#user-content-fnref-4) [↩2](#user-content-fnref-4-2)
5. Enterprise customers must have application security on their contract to get access to rate limiting rules. The number of rules depends on the exact contract terms. [↩](#user-content-fnref-5)
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
## Next steps
Refer to the following resources:
* [Create a rate limiting rule in the dashboard for a zone](https://developers.cloudflare.com/waf/rate-limiting-rules/create-zone-dashboard/)
* [Create a rate limiting rule via API for a zone](https://developers.cloudflare.com/waf/rate-limiting-rules/create-api/)
For Terraform examples, refer to [Rate limiting rules configuration using Terraform](https://developers.cloudflare.com/terraform/additional-configurations/rate-limiting-rules/).
***
## Related resources
* [Learning Center: What is rate limiting?](https://www.cloudflare.com/learning/bots/what-is-rate-limiting/)
* [Cloudflare Rate Limiting (previous version, now deprecated)](https://developers.cloudflare.com/waf/reference/legacy/old-rate-limiting/): Documentation for the previous version of rate limiting rules (billed based on usage).
</page>
<page>
---
title: Reference · Cloudflare Web Application Firewall (WAF) docs
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/waf/reference/
md: https://developers.cloudflare.com/waf/reference/index.md
---
* [Alerts for security events](https://developers.cloudflare.com/waf/reference/alerts/)
* [WAF phases](https://developers.cloudflare.com/waf/reference/phases/)
* [Legacy features](https://developers.cloudflare.com/waf/reference/legacy/)
</page>
<page>
---
title: Additional tools · Cloudflare Web Application Firewall (WAF) docs
description: "The Cloudflare WAF offers the following additional tools:"
lastUpdated: 2025-09-22T16:52:07.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/waf/tools/
md: https://developers.cloudflare.com/waf/tools/index.md
---
The Cloudflare WAF offers the following additional tools:
* [Browser Integrity Check](https://developers.cloudflare.com/waf/tools/browser-integrity-check/)
* [Enable security.txt](https://developers.cloudflare.com/security-center/infrastructure/security-file/)
* [Privacy Pass](https://developers.cloudflare.com/waf/tools/privacy-pass/)
* [Replace insecure JS libraries](https://developers.cloudflare.com/waf/tools/replace-insecure-js-libraries/)
* [Security Level](https://developers.cloudflare.com/waf/tools/security-level/)
* [Scrape Shield](https://developers.cloudflare.com/waf/tools/scrape-shield/)
* [User Agent Blocking](https://developers.cloudflare.com/waf/tools/user-agent-blocking/)
* [Validation checks](https://developers.cloudflare.com/waf/tools/validation-checks/)
* [Lists](https://developers.cloudflare.com/waf/tools/lists/)
* [IP Access rules](https://developers.cloudflare.com/waf/tools/ip-access-rules/)
* [Zone Lockdown](https://developers.cloudflare.com/waf/tools/zone-lockdown/)
</page>
<page>
---
title: Troubleshooting · Cloudflare Web Application Firewall (WAF) docs
description: Review common troubleshooting scenarios for Cloudflare WAF.
lastUpdated: 2024-09-06T15:21:19.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/waf/troubleshooting/
md: https://developers.cloudflare.com/waf/troubleshooting/index.md
---
* [Bing's Site Scan blocked by a managed rule](https://developers.cloudflare.com/waf/troubleshooting/blocked-bing-site-scans/)
* [Issues sharing to Facebook](https://developers.cloudflare.com/waf/troubleshooting/facebook-sharing/)
* [SameSite cookie interaction with Cloudflare](https://developers.cloudflare.com/waf/troubleshooting/samesite-cookie-interaction/)
* [FAQ](https://developers.cloudflare.com/waf/troubleshooting/faq/)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Waiting Room docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/404/
md: https://developers.cloudflare.com/waiting-room/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: About · Cloudflare Waiting Room docs
description: Waiting Room queues visitors when your traffic approaches a
previously defined threshold that might otherwise bring an application down.
lastUpdated: 2024-08-13T21:59:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/about/
md: https://developers.cloudflare.com/waiting-room/about/index.md
---
Waiting Room queues visitors when your traffic approaches a previously defined threshold that might otherwise bring an application down.

## User flow
Once you have [created and activated a waiting room](https://developers.cloudflare.com/waiting-room/get-started/) for a specific application page:
* If a page is not experiencing heavy traffic, a visitor accesses the page directly.
* If page traffic approaches a [user-defined threshold](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/#session-duration), a visitor enters a virtual waiting room until it is their turn to access the page:
* Each user receives a [cookie](https://developers.cloudflare.com/waiting-room/reference/waiting-room-cookie/) to manage the dynamic outflow of requests from the waiting room to the origin website in [First In First Out (FIFO)](https://developers.cloudflare.com/waiting-room/reference/queueing-methods/#first-in-first-out-fifo) order.
* While in the waiting room, the user's browser automatically refreshes every 20 seconds to give them updated information about their estimated wait time.
* When a user exits the waiting room and reaches your application, they can leave and re-enter without waiting for the length of time specified by the [session duration](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/#session-duration).
* Because waiting rooms support dynamic inflow and [outflow](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/#session-duration), new spots appear more quickly and estimated wait times are lower and more accurate.
## Architecture
Waiting Room is built on [Workers](https://developers.cloudflare.com/workers/) that runs across a global network of Cloudflare data centers.
When a request comes to a host or path covered by a Waiting Room, that request goes to a Waiting Room Worker in the closest geographic data center. The Worker then needs to make a decision: whether to send users to the queue or the website.
That decision itself depends on two factors: [admin-defined thresholds](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/) and the Waiting Room state.
For admin-defined thresholds, the two measures that matter are `total active users` and `new users per minute`:
* `total active users` is a target threshold for how many simultaneous users you want to allow on the pages covered by your waiting room.
* `new users per minute` defines the target threshold for the maximum rate of user influx to your website per minute.
A sharp spike in either of these values might result in queuing. Another configuration that affects how we calculate `the total active users` is `session duration`. A user is considered active for `session duration` minutes since the request is made to any page covered by a waiting room.
The other factor is the Waiting Room state, which is maintained at the local data center level but then also changes continuously based on the traffic around the world. Each data center works with its own Waiting Room state. This state is a snapshot of the traffic pattern for the website around the world available at that point in time. The advantage of using this approach - making decisions at the Worker level - is that we can make decisions without any significant latency added to the request. The algorithm for Waiting Room dynamically allocates a certain number of slots available to each Worker based on the Waiting Room state. Queueing starts when the slots run out within the Worker. The lack of additional latency added enables the customers to turn on the waiting room all the time without worrying about extra latency to their users.
The Waiting Room state is updated with global information every few seconds. We have a pipeline set up in Cloudflare [Durable Objects](https://developers.cloudflare.com/durable-objects/) that ensures changes in traffic get propagated around the world. This architecture ensures that we do not introduce additional latency, as well as that we are making decisions with as near-time accuracy as possible.
For even more details about the architecture and why we made these decisions, refer to our [deep-dive technical blog](https://blog.cloudflare.com/how-waiting-room-queues).
</page>
<page>
---
title: Additional options · Cloudflare Waiting Room docs
description: Beyond creating a waiting room, you may want to further customize
how your waiting room functions.
lastUpdated: 2024-09-12T14:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/waiting-room/additional-options/
md: https://developers.cloudflare.com/waiting-room/additional-options/index.md
---
Beyond [creating a waiting room](https://developers.cloudflare.com/waiting-room/get-started/), you may want to further customize how your waiting room functions.
* [Create scheduled events](https://developers.cloudflare.com/waiting-room/additional-options/create-events/)
* [Embed in an iFrame](https://developers.cloudflare.com/waiting-room/additional-options/embed-waiting-room-in-iframe/)
* [Combine with Cloudflare for SaaS](https://developers.cloudflare.com/waiting-room/additional-options/ssl-for-saas/)
* [Test a waiting room](https://developers.cloudflare.com/waiting-room/additional-options/test-waiting-room/)
* [Waiting Room Rules](https://developers.cloudflare.com/waiting-room/additional-options/waiting-room-rules/)
</page>
<page>
---
title: API reference · Cloudflare Waiting Room docs
lastUpdated: 2024-12-16T22:33:26.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/api-reference/
md: https://developers.cloudflare.com/waiting-room/api-reference/index.md
---
</page>
<page>
---
title: Get started · Cloudflare Waiting Room docs
description: "Before you start this tutorial, make sure you have:"
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/get-started/
md: https://developers.cloudflare.com/waiting-room/get-started/index.md
---
***
## Before you begin
Before you start this tutorial, make sure you have:
* Reviewed the [About](https://developers.cloudflare.com/waiting-room/about/) Waiting Room page.).
* Reviewed your [rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/) to make sure they allow at least one request every 20 seconds (required for automatic page refreshes).
***
## Step 1 — Plan out your waiting room
Before you create your waiting room, think about how you want it to appear and operate.
### Location
Which page will you cover with a waiting room? You can only have one waiting room per page, so you need to identify the high-traffic areas of your website.
Specify the URL for your page by setting the `hostname` and `path` in your [configuration settings](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/).
Advanced Waiting Room customers can also [specify multiple hostname and path combinations](https://developers.cloudflare.com/waiting-room/how-to/place-waiting-room/) for the same zone.
### Access method
You can direct visitors to your high-traffic page:
* Directly (via URL)
* Indirectly (via [a redirect](https://developers.cloudflare.com/rules/url-forwarding/bulk-redirects/))
### Queue activation
When you [activate your waiting room](#step-3--activate-your-waiting-room), choose whether:
* [**All visitors**](#queue-all-visitors) to be queued, in preparation for a product release or other time-based event.
* Only [**some visitors**](#queue-some-visitors) to be queued, as traffic reaches the thresholds defined in `Total active users` and `New users per minute`.
## Step 2 — Create your waiting room
Create your waiting room by:
* Using the [dashboard](https://developers.cloudflare.com/waiting-room/how-to/create-waiting-room/).
* Using the [API](https://developers.cloudflare.com/waiting-room/how-to/create-waiting-room/).
### Appearance (optional)
Some customers can [customize the design](https://developers.cloudflare.com/waiting-room/how-to/customize-waiting-room/) of their waiting room by editing the page's HTML and CSS.
If you have this ability, think about how you want the page to appear.
### Prepare your waiting room for mobile application traffic
If you need to manage traffic in a non-browser environment such as a mobile app or web app, use a [JSON-friendly waiting room](https://developers.cloudflare.com/waiting-room/how-to/json-response/) that can be consumed via your API endpoints. Note that if you have a mobile app or web app that depends on resources that would be protected by a waiting room, you will need to update those clients to handle Waiting Room appropriately.
## Step 3 — Activate your waiting room
Depending on your [queue activation](#queue-activation), you may deploy your waiting room differently.
### Queue some visitors
To queue visitors only when necessary:
1. Go to **Traffic** > **Waiting Room**.
2. On a waiting room, set **Enabled** to **On**.
3. Your waiting room will begin queueing visitors once it approaches the target traffic thresholds defined in [**Total active users**](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/) and in [**New users per minute**](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/).
### Queue all visitors
To queue all visitors prior to a time-based offering, set up a pre-queue as part of a [waiting room event](https://developers.cloudflare.com/waiting-room/additional-options/create-events/#create-an-event-from-the-dashboard).
To start queueing all new visitors without a scheduled event:
1. Go to **Traffic** > **Waiting Room**.
2. On a waiting room:
1. Ensure **Enabled** is set to **On**.
2. Set **Queue-all** to **On**.
3. Your waiting room will begin queueing all new visitors and will not allow any new visitors to the path protected by your waiting room. Queue-all will override all other waiting room settings, including event settings.
Note
Only new visitors will be queued. Active users that are already on your website will continue there and will not return to the queue until their session expires.
1. To begin allowing visitors to the path protected by your waiting room, set **Queue-all** to **Off**.
## Step 4 — Next steps
After you have created and deployed your first waiting room, you might also want to:
* [Test your waiting room](https://developers.cloudflare.com/waiting-room/additional-options/test-waiting-room/) before it goes live.
* [Monitor your traffic](https://developers.cloudflare.com/waiting-room/how-to/monitor-waiting-room/) in real time.
* [Troubleshoot](https://developers.cloudflare.com/waiting-room/troubleshooting/) potential issues.
</page>
<page>
---
title: Glossary · Cloudflare Waiting Room docs
description: Review the definitions for terms used across Cloudflare's Waiting
Room documentation.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/glossary/
md: https://developers.cloudflare.com/waiting-room/glossary/index.md
---
Review the definitions for terms used across Cloudflare's Waiting Room documentation.
| Term | Definition |
| - | - |
| downtime | Downtime is the duration during which a system, service, or equipment is not operational or unavailable for use. |
| error page | An error page is a webpage shown to users when they try to access a specific webpage or resource that is unavailable due to a server error, broken link, or other issues. It typically includes details about the encountered error and offers potential solutions or guidance to help users navigate the problem. |
| iFrame | An iFrame, short for Inline Frame, is an HTML element used to embed and display external content within a webpage, allowing the incorporation of another document or web page seamlessly within the main document. |
| JSON-friendly | JSON-friendly refers to data or formats that are easily and naturally represented in JSON (JavaScript Object Notation), a lightweight data interchange format, without requiring complex transformations or modifications. |
| legitimate traffic | Legitimate traffic refers to authorized and permissible network activity, data transmissions, or communications that adhere to established norms and rules within a given system or network. |
| non-browser traffic | Non-browser traffic refers to data exchanges and communication occurring between devices or systems that do not involve web browsers, such as a mobile app or web apps. |
| SEO crawlers | SEO crawlers, or web crawlers, are automated programs employed by search engines to systematically browse and index web content, gathering information about the structure and relevance of pages to determine search result rankings. |
| Set-Cookie | Set-Cookie is an HTTP header used by web servers to send a cookie to a user's browser during an HTTP response, enabling the server to store information on the client side, often used for session management and user preferences. |
| traffic management | The process of controlling and optimizing the flow of network data to ensure efficient and reliable communication. |
| virtual waiting room | A virtual waiting room is an online system or feature that manages and controls access to a website or service during periods of high traffic, preventing server overload by placing users in a queue until they can be accommodated, ensuring a more equitable and efficient user experience. |
</page>
<page>
---
title: Common tasks · Cloudflare Waiting Room docs
description: "When working with Cloudflare Waiting Room, you will commonly
perform the following tasks:"
lastUpdated: 2024-09-12T14:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/waiting-room/how-to/
md: https://developers.cloudflare.com/waiting-room/how-to/index.md
---
When working with Cloudflare Waiting Room, you will commonly perform the following tasks:
* [Access Waiting Room](https://developers.cloudflare.com/waiting-room/how-to/waiting-room-dashboard/)
* [Create a waiting room](https://developers.cloudflare.com/waiting-room/how-to/create-waiting-room/)
* [Place a waiting room](https://developers.cloudflare.com/waiting-room/how-to/place-waiting-room/)
* [Customize a waiting room](https://developers.cloudflare.com/waiting-room/how-to/customize-waiting-room/)
* [Monitor waiting room status](https://developers.cloudflare.com/waiting-room/how-to/monitor-waiting-room/)
* [Control user session settings](https://developers.cloudflare.com/waiting-room/how-to/control-user-session/)
* [Control waiting room traffic](https://developers.cloudflare.com/waiting-room/how-to/control-waiting-room/)
* [Edit and delete waiting rooms](https://developers.cloudflare.com/waiting-room/how-to/edit-delete-waiting-room/)
* [Get JSON response for mobile and other non-browser traffic](https://developers.cloudflare.com/waiting-room/how-to/json-response/)
</page>
<page>
---
title: Features by plan type · Cloudflare Waiting Room docs
description: The features available for a waiting room depend on your plan type.
You can only have one plan per zone.
lastUpdated: 2025-08-18T14:27:42.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/plans/
md: https://developers.cloudflare.com/waiting-room/plans/index.md
---
The features available for a waiting room depend on your plan type. You can only have **one plan** per zone.
One basic waiting room is included in all Business and Enterprise plans. On an Enterprise plan, you can purchase advanced waiting room(s) to unlock all of the additional advanced features.
| | Free | Pro | Business | Enterprise |
| - | - | - | - | - |
| Availability | No | No | Yes | Yes |
| Number of rooms | 0 | 0 | 1 | 1 (default)*With advanced:* Custom (can purchase more) |
| Customized templates | No | No | No | Advanced add-on |
| Queueing methods | No | No | First In First Out (FIFO) | First In First Out (FIFO) (default)*With advanced:* FIFO, Random, Reject, Passthrough |
| Configure multiple hostnames and paths | No | No | No | Advanced add-on |
| Disable session renewal | No | No | No | Advanced add-on |
| JSON-friendly response | No | No | No | Advanced add-on |
| Customize queuing status code | No | No | Yes | Yes |
| Scheduled events | No | No | No | Advanced add-on |
| Waiting Room rules | No | No | No | Advanced add-on |
| Session Revocation | No | No | No | Advanced add-on |
| SEO Crawler Bypassing | No | No | Yes | Yes |
| Turnstile Widget Mode | No | No | Invisible only | Invisible (default)*With advanced:* Invisible, Managed, Non Interactive |
| Turnstile Fail Action | No | No | Log only | Log only (default)*With advanced:* Log only & Infinite queue |
Note
Enterprise customers can preview this product as a [non-contract service](https://developers.cloudflare.com/billing/preview-services/), which provides full access, free of metered usage fees, limits, and certain other restrictions.
## How do I get started?
To get started with Waiting Room, review our [setup guide](https://developers.cloudflare.com/waiting-room/get-started/).
</page>
<page>
---
title: Reference · Cloudflare Waiting Room docs
description: "Use the following reference information when setting up and
deploying your waiting rooms:"
lastUpdated: 2024-09-12T14:53:06.000Z
chatbotDeprioritize: true
source_url:
html: https://developers.cloudflare.com/waiting-room/reference/
md: https://developers.cloudflare.com/waiting-room/reference/index.md
---
Use the following reference information when setting up and deploying your waiting rooms:
* [Best practices](https://developers.cloudflare.com/waiting-room/reference/best-practices/)
* [Configuration settings](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/)
* [API commands](https://developers.cloudflare.com/waiting-room/reference/waiting-room-api/)
* [Cookies](https://developers.cloudflare.com/waiting-room/reference/waiting-room-cookie/)
* [Queueing method](https://developers.cloudflare.com/waiting-room/reference/queueing-methods/)
</page>
<page>
---
title: FAQ · Cloudflare Waiting Room docs
description: Below you will find answers to our most commonly asked questions
about the Waiting Room.
lastUpdated: 2025-06-03T16:48:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/troubleshooting/
md: https://developers.cloudflare.com/waiting-room/troubleshooting/index.md
---
Below you will find answers to our most commonly asked questions about the Waiting Room.
* [Configuration](#configuration)
* [Features and products](#features-and-products)
* [User behavior](#user-behavior)
* [Monitor your waiting room](#monitor-your-waiting-room)
***
## Configuration
### Can I display my waiting room page in another language?
Yes. For more details, refer to [Customize a waiting room](https://developers.cloudflare.com/waiting-room/how-to/customize-waiting-room/).
### Why does my waiting room look different than how I designed it?
If you have [customized your waiting room template](https://developers.cloudflare.com/waiting-room/how-to/customize-waiting-room):
1. Preview your template before deploying it to production.
2. If you encounter any issues, check for proper syntax and a closing backslash (/).
Note
Only Enterprise customers can customize the appearance of their waiting room.
### What can I update when my waiting room is actively queueing?
You can update a [waiting room's template](https://developers.cloudflare.com/waiting-room/how-to/customize-waiting-room) and those changes will be visible to users in near-real time. We recommend these updates as a way to engage with users and provide updated information or expectations.
You can also update the [configuration settings](https://developers.cloudflare.com/waiting-room/reference/configuration-settings) of a waiting room, but only make these changes when necessary. These changes may impact the estimated wait time shown to end users and cause unnecessary confusion.
## Features and products
### Which features are included in my Waiting Room plan?
To check which features are available to different plan types, refer to [Plans](https://developers.cloudflare.com/waiting-room/plans/).
### How does Waiting Room interact with other Cloudflare products?
Some Cloudflare products run before a waiting room acts on traffic:
* DDoS Mitigation
* Web Application Firewall (WAF)
* Bot Management
* Page Rules
Other Cloudflare products run after a waiting room acts on traffic:
* Workers
## User behavior
### What happens if a user refreshes their tab when in a waiting room?
A manual tab refresh has no effect on a user's position in your waiting room.
However, if they close their tab and then try to access the application again during active queueing, they will lose their spot and have to go to the back of the queue.
### What happens if a queued user leaves the queue?
When a user joins the queue, they are placed into a bucket which is their general position in line. When a user leaves the queue (closes the browser or tab), their place in line is held for five minutes after the last refresh. This grace period allows users to keep their position in line if they experience a brief disconnection. After five minutes, the grace period expires and they are no longer counted as waiting in the queue.
## Monitor your waiting room
### Why do I observe a few users being queued in the dashboard?
Some users might be queued before your waiting room reaches is limit due to architectural designs. For more details on the behavior and how to fix it, refer to [Queueing activation](https://developers.cloudflare.com/waiting-room/how-to/monitor-waiting-room#queueing-activation).
### Why are some users not being queued in my waiting room?
If you notice users not being queued to your waiting room, make sure the path you defined exactly matches the path of your website.
The path is case-sensitive, so if you have a waiting room set up for `/Black-Friday-Sale` and users go to `/black-friday-sale`, they will bypass your waiting room.
For more details, refer to [Best practices](https://developers.cloudflare.com/waiting-room/reference/best-practices).
### Why are users being blocked from entering my waiting room?
If you have Rate Limiting, check your [rate limiting rules](https://developers.cloudflare.com/waf/rate-limiting-rules/).
The Waiting Room queue page refreshes every 20 seconds by populating the refresh header. If you have a rule set to block requests from a specific IP within 20 seconds, the user in the waiting room will be blocked. Make sure your rules allow at least one request every 20 seconds.
Your user also might not have [cookies](https://developers.cloudflare.com/waiting-room/reference/waiting-room-cookie) enabled. If they do not enable cookies and your waiting room is actively queueing traffic, they will not reach your endpoint until the queueing stops.
### Why is the estimated wait time increasing for some users?
Estimated wait times may increase if the rate of users leaving your site decreases. The estimated wait time is updated upon each page refresh based on the most recently available information about the rate of slots opening up on your site and the number of users ahead of the user in line. To make this increase less likely, you could limit the amount of time users are allowed to spend on your site by disabling session renewal. Be aware that, if you change your traffic settings, estimated wait times will change as well.
### Why is `new users per minute` low when there is capacity available?
The `new users per minute` metric tracks how many users were accepted to the origin in the last minute. It is only incremented when a queued user refreshes and is accepted to the origin. If the waiting room queueing method is set to `fifo`, we will wait until all queued users in a minute-based bucket are accepted before moving to the next bucket. If many of the users in a bucket have abandoned the queue, then the waiting room must wait until their place in line expires before moving on to the next bucket. This can cause `new users per minute` to be low when only a small percentage of queued users are actually still waiting.
This is often noticed if there is a large amount of automated traffic which does not handle cookies properly. Since bots usually do not persist cookies from one request to the next, they end up counting as multiple inactive users in the queue and prevent full utilization of available slots. For this reason, we recommend leveraging [Bots Management](https://developers.cloudflare.com/bots/) products to keep bots out of the queue. Waiting Room Advanced customers can try our [Turnstile](https://developers.cloudflare.com/turnstile/) integration, which prevents bots from clogging the line by putting them in an infinite queue.
### Why are my Waiting Room analytics and Google analytics not matching?
Waiting Room relies on a session cookie to count and keep track of active users. The duration for which a user is considered active depends on the waiting room configuration. The key setting involved in this calculation is [session duration](https://developers.cloudflare.com/waiting-room/reference/configuration-settings/#session-duration). By default, Waiting Room considers a user active from the time of their last request made with a session cookie, until the configured session duration elapses. Customers with an advanced Waiting Room setup can modify this behavior by [disabling session renewal](https://developers.cloudflare.com/waiting-room/how-to/control-user-session/#disable-session-renewal-to-limit-browsing-time) and/or explicitly [revoking sessions](https://developers.cloudflare.com/waiting-room/how-to/control-user-session/#revoke-a-users-session-using-origin-commands) using an origin command.
If the session duration is set to a higher value, a user who makes only a single request will be considered active for longer than they actually were. This can cause the `Total Active Users` metric to appear higher than the active users metric reported by Google Analytics for the same time period, as Google Analytics only counts users who made requests during that specific period.
For example, if the session duration is set to 30 minutes and you look at the last 10 minutes of active users in Google Analytics, the number of active users reported by Waiting Room will be higher, since it includes users from the last 30 minutes.
Another key difference is that Waiting Room runs on requests made to the origin, while Google Analytics requires a user-agent to run JavaScript (via Google Tag). Waiting Room creates new sessions and tracks user metrics based on the HTTP request path, without requiring any additional JavaScript execution by a user-agent. In contrast, Google Analytics requires user-agents to execute JavaScript and make a secondary request to report details to Google Analytics. If a large portion of the traffic is automated, it may not be captured by Google Analytics. However, Waiting Room analytics will count such traffic as new users and consider them active for the configured session duration.
### Why did my traffic exceed the New Users Per Minute threshold?
Waiting Room is a distributed system, and achieving perfect global counting in real time is challenging due to the time required for state propagation across data centers worldwide. The budgeting logic is structured around both data center-specific and global budgets. Data center budgets are allocated based on the historical traffic received by each data center, while global budgets (a portion of the total available budget) are maintained to allow new users to enter from any data center globally.
In the case of a rapid spike — rising to several thousand users within a minute — the global state propagation process takes approximately two minutes, resulting in a delay before all data centers become aware of the spike. If this information is not disseminated quickly enough to other locations, temporary overshooting may occur, particularly when lower limits are in place.
This occurs because the portion of the budget reserved for new users to enter a data center is equally available to all data centers. Until the usage of this budget is synchronized across all data centers, each data center may consume a portion that collectively exceeds 100% of the global budget allocated for new users.
</page>
<page>
---
title: Waiting Room Analytics · Cloudflare Waiting Room docs
description: Waiting Room Analytics gives you historical insights into the
traffic going through your waiting room compared to your waiting room
settings. Data is stored for the past 30 days.
lastUpdated: 2025-10-09T07:47:46.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/waiting-room/waiting-room-analytics/
md: https://developers.cloudflare.com/waiting-room/waiting-room-analytics/index.md
---
Waiting Room Analytics gives you historical insights into the traffic going through your waiting room compared to your waiting room settings. Data is stored for the past 30 days.
Using Waiting Room Analytics, you can:
* Evaluate peak traffic flow through your waiting room and onto your site.
* Determine how long users spent in the waiting room.
* Use analytics to help calibrate your waiting room settings.
## Dashboard Analytics
To access your waiting room’s analytics in the dashboard:
1. In the Cloudflare dashboard, go to the **Waiting Room** page.
[Go to **Waiting Room**](https://dash.cloudflare.com/?to=/:account/:zone/traffic/waiting-rooms)
2. Expand the waiting room you would like to review metrics for, to display a preview of your waiting room analytics. The preview gives you insights into peak traffic through your waiting room over the last 24 hours including: Maximum active users, Maximum queued users and Typical time in queue for queued users.
3. Select **View More** under the Waiting Room Analytics section to get more historical analytics for your waiting room.
4. The time range for all of the metrics displayed defaults to the last 24 hours. To change the time range, select from the drop down. You can select any time range from the last 30 days that is a minimum of 30 minutes.
## Event Analytics
If your waiting room has a completed scheduled event, you can quickly access the event’s analytics by expanding the row for the waiting room you are interested in and selecting the event time. The link opens the analytics view for that waiting room, including information from the pre-queueing period to the end of the event.
To save this event information, you can either select **Download data** or **Print report**. If you delete the event, the time period link will no longer appear in your dashboard. If you edit the timing of the event, the time period link will update as well.
If you do not get a link to your event’s analytics, one of the following may have happened:
* Your event has not happened yet.
* Your event started more than 30 days ago.
## Metrics
These are metrics available in the Analytics dashboard and how they are calculated.
### Time in queue
Time in queue summary values give you an insight into the user experience by indicating how long queued users spent waiting to enter your application. It displays the time waited for the typical user, as well as for those who waited the longest, for the time period you have selected. These values are an indicator of the impact your waiting room settings combined with the traffic to your waiting room had on wait times.
If wait times are higher than you would like, and you feel comfortable doing so, you could consider taking any or all of the following actions:
* Increase `total_active_users` configured value.
* Increase `new_users_per_minute` configured value.
* Decrease `session_duration`.
* Disable session renewal.
Note
Note that wait times are only calculated for users who went from the waiting room to your origin.
### Time on origin
Time on origin summary values estimate how long users spent on the pages covered by your waiting room before leaving. For the time period selected, you will have access to the estimated time spent on origin for the typical user, as well as the time on origin for those who spend the most time on your site. Keep in mind that if your session renewal is disabled and there is no active queueing, users are issued a new waiting room session every `session_duration` minutes. Therefore, these users may be staying for multiple sessions. The time on origin for these users restarts each time a session expires.
The following are some takeaways you could have depending on the time on origin values.
You may want to increase session duration, giving users more time to make subrequests, and/or enable session renewal if:
* You have session renewal disabled.
* You have frequent, active queueing with long wait times.
* The typical time on origin is around 70% of your configured session duration.
These may be indicators that users need more time to complete their desired tasks on your site.
You may want to decrease session duration and/or disable session renewal if:
* Your top 5% time on origin is less than 70% of your configured session duration.
* You are seeing high queue times and do not want to increase traffic limits.
These may be indicators that users do not need as much time on your site and are taking up spots on your origin.
### Active users vs. queued users
The Active users chart is a time series chart that displays the maximum active users on any URLs covered by your waiting room as well as maximum queued users. These values are shown compared to your configured active user target threshold.
A new user is a novel request made to any URLs covered by the waiting room. Waiting Room counts the request as new if no waiting room cookie is tied to the request. Once the request is made, a waiting room cookie is issued. If there is an active queue, the user will be considered a queued user. Once that user makes it through the queue and onto the site, they are now an active user and remain active as long as they keep making HTTP requests to waiting room URLs at least once every `session_duration` minutes.
To identify and hone in on peak traffic, select a longer time period, such as 30 days. Then, drag your cursor to the left and right of any time period you would like to check with more granularity to zoom in. You can zoom in until each bar represents a one minute interval. All other metrics on the page will update automatically to reflect the data behind the time period selected.
To check for more details about a particular moment in time, hover over a bar on the graph. This displays a tooltip which will indicate the following for the time period that bar represents:
* Maximum active users reached
* Maximum queued users reached
* Configured active user target values
Queueing may occur below your configured limits, and active users may sometimes exceed your configured limits. Refer to the [Queuing activation](https://developers.cloudflare.com/waiting-room/how-to/monitor-waiting-room/#queueing-activation) section for more information.
### New users per minute
The New users per minute chart shows how many new users per minute passed through the waiting room to your origin compared to your configured New users per minute target threshold. Like the Active users chart, you can zoom in by highlighting to the left and right of the time period you are interested in, which will update the other chart as well as summary values. As you zoom out, each data point is averaged. Therefore, as you zoom in, values may fluctuate.
### Turnstile Widget Traffic
The Turnstile widget traffic chart shows the number of challenges issued per minute and the distribution of traffic seen with these challenges. Traffic is categorized into three main categories:
* Likely Human - This represents the number of challenges that were successfully solved.
* Likely Bots - This represents the number of unsolved challenges.
* Bots - This represents the number of failed challenges.
If your waiting room has the infinite queue option enabled, you will see a line on the graph representing the number of refresh requests from bots in the infinite queue.
## GraphQL Analytics
You can query your Waiting Room analytics data via GraphQL API. Waiting Room analytics provides near real-time visibility into your Waiting Room, allowing you to visualize the traffic to your application and how it is managed respecting the configured limits.
Here are some query examples to get started:
Fetch values for total active users and new users per minute over a certain period.
This is a simple query to fetch metrics values. You can filter the data with the zone tag and query the `waitingRoomAnalyticsAdaptive` dataset. In this example, we have applied this query only on two metrics, but you can explore the schema and fetch the raw values from the GraphQL dataset without applying any aggregation methods.
```bash
{
viewer {
zones(filter: {zoneTag: "example-zone"}) {
waitingRoomAnalyticsAdaptive(limit: 3, filter: {datetime_gt: "2023-03-05T19:14:30Z", datetime_lt: "2023-03-07T19:13:00Z", waitingRoomId: "example-waiting-room-id"}) {
totalActiveUsers
newUsersPerMinutes
}
}
}
```
```json
{
"data": {
"viewer": {
"zones": [
{
"waitingRoomAnalyticsAdaptive": [
{
"newUsersPerMinute": 77,
"totalActiveUsers": 1023
},
{
"newUsersPerMinute": 113,
"totalActiveUsers": 1009
},
{
"newUsersPerMinute": 99,
"totalActiveUsers": 927
}
]
}
]
}
},
"errors": null
}
```
Find the average of total active users and new users per minute over a certain period, and aggregate this data over a period of 15 minutes.
This query calculates the average of total active users and new users per minute. The time dimension in the query is 15 minutes, therefore the data is aggregated over 15 minutes for the selected time period.
```bash
{
viewer {
zones(filter: {zoneTag: "example-zone"}) {
waitingRoomAnalyticsAdaptiveGroups(limit: 10, filter: {datetime_geq: "2023-03-15T04:00:00Z", datetime_leq: "2023-03-15T04:45:00Z", waitingRoomId: "example-waiting-room-id"}, orderBy: [datetimeFifteenMinutes_ASC]) {
avg {
totalActiveUsers
newUsersPerMinute
}
dimensions {
datetimeFifteenMinutes
}
}
```
```json
{
"data": {
"viewer": {
"zones": [
{
"waitingRoomAnalyticsAdaptiveGroups": [
{
"avg": {
"newUsersPerMinute": 119,
"totalActiveUsers": 1180
},
"dimensions": {
"datetimeFifteenMinutes": "2023-03-15T04:00:00Z"
}
},
{
"avg": {
"newUsersPerMinute": 146,
"totalActiveUsers": 961
},
"dimensions": {
"datetimeFifteenMinutes": "2023-03-15T04:15:00Z"
}
},
{
"avg": {
"newUsersPerMinute": 144,
"totalActiveUsers": 1015
},
"dimensions": {
"datetimeFifteenMinutes": "2023-03-15T04:30:00Z"
}
}
]
}
]
}
},
"errors": null
}
```
Find the weighted averages of time on origin (50th percentile) and total time waited (90th percentile) for a certain period and aggregate this data over one hour.
This query calculates the weighted averages of the metrics for a certain period of time aggregated hourly.
```bash
{
viewer {
zones(filter: {zoneTag: "example-zone"}) {
waitingRoomAnalyticsAdaptiveGroups(limit: 10, filter: {datetime_geq: "2023-03-15T04:00:00Z", datetime_leq: "2023-03-15T04:45:00Z", waitingRoomId: "example-waiting-room-id"}, orderBy: [datetimeHour_ASC]) {
avgWeighted {
timeOnOriginP50
totalTimeWaitedP90
}
dimensions {
datetimeHour
}
}
```
```json
{
"data": {
"viewer": {
"zones": [
{
"waitingRoomAnalyticsAdaptiveGroups": [
{
"avgWeighted": {
"timeOnOriginP50": 99.19,
"totalTimeWaitedP90": 1625.63
},
"dimensions": {
"datetimeHour": "2023-03-15T04:00:00Z"
}
}
]
}
]
}
},
"errors": null
}
```
## Why is there no data for my waiting room?
If you are not seeing any historical data for your waiting room, one or more of the following may be true:
* Your waiting room was not receiving any traffic for the time period you are inspecting.
* Your waiting room was not enabled for the time period you are inspecting.
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare WARP client docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/warp-client/404/
md: https://developers.cloudflare.com/warp-client/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Get started · Cloudflare WARP client docs
description: "Before installing and setting up the WARP Client, ensure that your
device meets the following system requirements:"
lastUpdated: 2025-08-20T21:45:15.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/warp-client/get-started/
md: https://developers.cloudflare.com/warp-client/get-started/index.md
---
Consumer WARP
This documentation is for the consumer version of WARP. If you are using WARP with Cloudflare Zero Trust, refer to the [Zero Trust documentation](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/).
Before installing and setting up the WARP Client, ensure that your device meets the following system requirements:
## Android
| | |
| - | - |
| **OS version** | 5.0+ |
[Download for Android](https://play.google.com/store/apps/details?id=com.cloudflare.onedotonedotonedotone)
## iOS
| | |
| - | - |
| **OS version** | iOS 11+ |
[Download for iOS](https://apps.apple.com/us/app/id1423538627)
## Linux
| | |
| - | - |
| **OS version** | CentOS 8, RHEL 8, Debian 12, Debian 13, Fedora 34, Fedora 35, Ubuntu 22.04 LTS, Ubuntu 24.04 LTS |
| **Processor** | AMD64 / x86-64 or ARM64 / AArch64 |
| **HD space** | 75 MB |
| **Memory** | 35 MB |
| **Network interface type** | Wi-Fi or LAN |
| **MTU** | 1381 bytes recommended [1](#user-content-fn-1) |
## Footnotes
1. Minimum 1281 bytes with [Path MTU Discovery](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/) [↩](#user-content-fnref-1)
[Download for Linux](https://pkg.cloudflareclient.com/)
## macOS
| | |
| - | - |
| **OS version** | Sonoma 14.0+, Sequoia 15.1+ (15.0.x is not supported), Tahoe 26.0+ |
| **Processor** | M series |
| **HD space** | 75 MB |
| **Memory** | 35 MB |
| **Network interface type** | Wi-Fi or LAN |
| **MTU** | 1381 bytes recommended [1](#user-content-fn-1) |
## Footnotes
1. Minimum 1281 bytes with [Path MTU Discovery](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/) [↩](#user-content-fnref-1)
[Download for macOS](https://downloads.cloudflareclient.com/v1/download/macos/ga)
## Windows
| | |
| - | - |
| **OS version** | Windows 10 LTSC, Windows 11, Windows 365 Cloud PC running Windows 11 |
| **Processor** | AMD64 / x86-64 or ARM64 / AArch64 |
| **.NET Framework version** | 4.7.2 or later |
| **HD space** | 184 MB |
| **Memory** | 3 MB |
| **Network interface type** | Wi-Fi or LAN |
| **MTU** | 1381 bytes recommended [1](#user-content-fn-1) |
## Footnotes
1. Minimum 1281 bytes with [Path MTU Discovery](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/deployment/mdm-deployment/path-mtu-discovery/) [↩](#user-content-fnref-1)
[Download for Windows](https://downloads.cloudflareclient.com/v1/download/windows/ga)
</page>
<page>
---
title: FAQ · Cloudflare WARP client docs
description: Below you will find answers to our most commonly asked questions
regarding the WARP client. If you cannot find the answer you are looking for,
refer to the community page to explore more resources.
lastUpdated: 2025-10-21T14:33:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/warp-client/known-issues-and-faq/
md: https://developers.cloudflare.com/warp-client/known-issues-and-faq/index.md
---
Below you will find answers to our most commonly asked questions regarding the WARP client. If you cannot find the answer you are looking for, refer to the [community page](https://community.cloudflare.com/) to explore more resources.
## Why am I not connecting to a closer Cloudflare data center?
As our [Network Map](https://www.cloudflare.com/network/) shows, we have locations all over the globe. However, in the Advanced Connection stats of our application, you may notice that the server you are connecting to is not necessarily the one physically closest to your location. This can be due to a number of reasons:
* We work hard to prevent it, but sometimes your nearest server might be having problems. [Check the system status](https://www.cloudflarestatus.com/?_ga=2.155811579.1117044671.1600983837-1079355427.1599074097) for more information.
* Your Internet provider may choose to route traffic along an alternate path for reasons such as cost savings, reliability, or other infrastructure concerns.
* Not all Cloudflare locations are WARP enabled. We are constantly evaluating performance and how users are connecting, bringing more servers online with WARP all the time.
## Does WARP reveal my IP address to websites I visit?
No. 1.1.1.1 + WARP replaces your original IP address with a Cloudflare IP that consistently and accurately represents your approximate location. This happens regardless of whether the site is on the Cloudflare network or not. Refer to our [blog post](https://blog.cloudflare.com/geoexit-improving-warp-user-experience-larger-network/) for more information on this topic.
Note
If you grant a website access to your microphone or camera, traffic will [bypass WARP](#known-issues) and your original IP address will be visible.
## Why has my throughput dropped while using WARP?
Cloudflare WARP is in part powered by [1.1.1.1](https://developers.cloudflare.com/1.1.1.1/), the world's fastest DNS resolver. When visiting sites or going to a new location on the Internet, you should see fast DNS lookups. WARP, however, is built to trade some throughput for enhanced privacy, by encrypting all traffic both to and from your device. While this is not noticeable at most mobile speeds, on desktop systems in countries where high-speed broadband is available, you may notice a drop. We think the tradeoff is worth it and continue to work on improving performance all over the system.
## "What about the performance of the WARP app?
Cloudflare WARP and the 1.1.1.1 with WARP applications go through performance testing that includes battery, network and CPU on a regular basis. In addition, both applications are used by millions of users worldwide that help us stay on top of issues across a wide variety of devices, networks, sites and applications.
## What is the version of .NET Framework required for the Windows client?
The WARP client for Windows requires .NET Framework version 4.7.2 or later to be installed on your computer.
## Known issues
* Applications or sites that rely on location information to enforce content licensing agreements (for example, certain games, video streaming, music streaming, or radio streaming) may not function properly. We are working on a product update that will allow these clients to work, by not sending their traffic through WARP.
* Refer to [Known Limitations](https://developers.cloudflare.com/cloudflare-one/team-and-resources/devices/warp/troubleshooting/known-limitations/) for information on devices, software, and configurations that are incompatible with Cloudflare WARP.
* WARP does not proxy WebRTC traffic. Applications or sites that have access to your microphone or camera, such as for live video calls or online gaming, will bypass WARP. As a result, your IP address will be visible to these websites.
</page>
<page>
---
title: Legal · Cloudflare WARP client docs
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/warp-client/legal/
md: https://developers.cloudflare.com/warp-client/legal/index.md
---
* [Privacy Policy](https://www.cloudflare.com/application/privacypolicy/)
* [Application Terms of Service](https://www.cloudflare.com/application/terms/)
* [Third party licenses](https://developers.cloudflare.com/warp-client/legal/3rdparty/)
</page>
<page>
---
title: Privacy · Cloudflare WARP client docs
description: The WARP Client application uses a VPN profile and/or service that
enables us to intercept and secure your DNS queries and to transmit data from
your device through the Cloudflare network, depending on the services you have
enabled. We only collect limited DNS query and traffic data (excluding
payload) that is sent to our network when you have the app enabled on your
device. All information is handled in accordance with our Privacy Policy.
lastUpdated: 2025-09-23T20:48:09.000Z
chatbotDeprioritize: false
tags: Privacy
source_url:
html: https://developers.cloudflare.com/warp-client/privacy/
md: https://developers.cloudflare.com/warp-client/privacy/index.md
---
The WARP Client application uses a VPN profile and/or service that enables us to intercept and secure your DNS queries and to transmit data from your device through the Cloudflare network, depending on the services you have enabled. We only collect limited DNS query and traffic data (excluding payload) that is sent to our network when you have the app enabled on your device. All information is handled in accordance with our [Privacy Policy](https://www.cloudflare.com/application/privacypolicy/).
## What does Cloudflare do with your data?
When not part of a Cloudflare for Teams organization, Cloudflare stores the absolute minimum amount of data we believe is required to provide the service. We will not sell, rent, share or otherwise disclose your personal information to anyone except as necessary to provide our services or as otherwise described in our Privacy Policy without first providing you with notice and the opportunity to consent. We do not use the data to identify who you are or what you are doing on the Internet beyond the exceptions below. We do not store any data except as set forth in our Privacy Policy. Such data may include: your app installation ID, the amount of data transferred through Cloudflare's network, and your average speed when you are using the WARP Client application.
## How Cloudflare Uses User Data:
### Registration ID
Cloudflare uses a random identifier generated when you install the app to give you referral bonuses for referring the app to others.
### Data Transferred
Cloudflare tracks the amount of data your WARP installation has transferred to keep track of your WARP+ usage. When you refer friends to WARP, this quota is increased.
### Average Speed
Cloudflare uses this data to understand how much faster the WARP Client application is making your Internet connection. Knowing this information helps us improve the application in your region and on your mobile carrier or Internet provider.
### Aggregate Usage
Cloudflare tracks the aggregate amount of traffic by website and by region. Knowing this information helps Cloudflare plan better when we should build future data centers.
</page>
<page>
---
title: WARP modes · Cloudflare WARP client docs
description: The WARP client has several modes to better suit different connection needs.
lastUpdated: 2025-10-22T21:11:06.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/warp-client/warp-modes/
md: https://developers.cloudflare.com/warp-client/warp-modes/index.md
---
The WARP client has several modes to better suit different connection needs.
## 1.1.1.1
1.1.1.1 is Cloudflare’s public DNS resolver. It offers a fast and private way to browse the Internet. It also offers a DNS encryption service through DNS over HTTPS (DoH) or DNS over TLS (DoT) for increased security and privacy.
Refer to [1.1.1.1 resolver](https://developers.cloudflare.com/1.1.1.1/encryption/) to learn more about DNS encryption.
## 1.1.1.1 with WARP
The WARP application uses [MASQUE](https://blog.cloudflare.com/zero-trust-warp-with-a-masque/) to encrypt and send traffic from your device directly to Cloudflare's global network. This ensures Internet traffic between your device and the Internet is secure and private, while also preventing third parties from accessing your traffic. All traffic[1](#user-content-fn-1) tunneled over the MASQUE connection is encrypted using [post-quantum cryptography](https://blog.cloudflare.com/post-quantum-zero-trust/) to protect against [harvest-now-decrypt-later attacks](https://www.nist.gov/cybersecurity/what-post-quantum-cryptography).
If the site you are visiting is already a Cloudflare customer, the content is immediately sent to your device. If not, Cloudflare uses its global network of data centers to devise the shortest path to the site. For more information, refer to our blog post [Introducing WARP: Fixing Mobile Internet Performance and Security](https://blog.cloudflare.com/1111-warp-better-vpn/).
Warning
WARP does not provide anonymity, and it is not designed to prevent servers you communicate with from identifying you. WARP also does not allow you to pretend to be accessing the Internet from a different country.
## WARP via Local Proxy
Currently, this mode is available on desktop clients only. When WARP is configured as a local proxy, only the applications that you configure to use the proxy (HTTPS or SOCKS5) will have their traffic sent through WARP. This allows you to pick and choose which traffic is encrypted — for example, your web browser or a specific application. Everything else will not be encrypted and will be sent over a regular Internet connection.
Because this feature restricts WARP to just applications configured to use the local proxy, leaving all other traffic over the Internet unencrypted by default, we have hidden it in the **Advanced** menu. To turn it on:
1. Navigate to **Preferences** > **Advanced** and select **Configure Proxy**.
2. On the window that opens, check the box and configure the port you want to listen on.
This will enable the **WARP via Local Proxy** option in the **WARP Settings** menu.
If you enable [FIPS compliance](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/tls-decryption/#fips-compliance) for TLS decryption, you must [disable QUIC](https://developers.cloudflare.com/cloudflare-one/traffic-policies/http-policies/http3/#force-http2-traffic) in your users' browsers. Otherwise, HTTP/3 traffic will bypass inspection by the WARP client.
## WARP+ Unlimited
While WARP can take advantage of the many Cloudflare data centers around the world to give you a more private and robust connection, WARP+ Unlimited subscribers get access to a larger network. More cities to connect to means you are likely to be closer to a Cloudflare data center, which can reduce latency and improve your browsing speed.
WARP+ Unlimited is a paid, monthly subscription that can be purchased via the Apple App Store or Google Play Store.
To subscribe to WARP+ Unlimited:
1. On an iOS or Android device, launch the **1.1.1.1: Faster Internet** app.
2. Select **Settings** > **Upgrade to WARP+**. A dialog will appear with the subscription price.
3. To confirm your subscription, select **Subscribe to WARP+ Unlimited**. All payments are handled by the Apple/Google app store, and the payment information associated with your Apple/Google account will be charged for these subscriptions.
WARP+ Unlimited is now active on this device. You can use your license key on up to five devices.
## Footnotes
1. Post-quantum cryptography requires the following minimum WARP versions:\
**Android**: 2.4.3\
**iOS**: 1.11.1\
**Windows, macOS, and Linux**: 2025.6.1335.0 [↩](#user-content-fnref-1)
</page>
<page>
---
title: 404 - Page Not Found · Cloudflare Web Analytics docs
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/web-analytics/404/
md: https://developers.cloudflare.com/web-analytics/404/index.md
---
# 404
Check the URL, try using our [search](https://developers.cloudflare.com/search/) or try our LLM-friendly [llms.txt directory](https://developers.cloudflare.com/llms.txt).
</page>
<page>
---
title: Cloudflare Web Analytics · Cloudflare Web Analytics docs
description: Cloudflare Web Analytics provides free, privacy-first analytics for
your website without changing your DNS or using Cloudflare’s proxy. Cloudflare
Web Analytics helps you understand the performance of your web pages as
experienced by your site visitors.
lastUpdated: 2025-09-23T20:48:09.000Z
chatbotDeprioritize: false
tags: Privacy
source_url:
html: https://developers.cloudflare.com/web-analytics/about/
md: https://developers.cloudflare.com/web-analytics/about/index.md
---
Cloudflare Web Analytics provides free, privacy-first analytics for your website without changing your DNS or using Cloudflare’s proxy. Cloudflare Web Analytics helps you understand the performance of your web pages as experienced by your site visitors.
All you need to enable Cloudflare Web Analytics is a Cloudflare account and a JavaScript snippet on your page to start getting information on page views and visitors. The JavaScript snippet (also known as a beacon) collects metrics using the Performance API, which is available in all major web browsers.
Web Analytics supports Adaptive Bit Rate (ABR). Cloudflare's servers will select the best resolution for each chart or table depending on the size of the data, the date range, your network connection, and other factors. For more information, refer to [Explaining Cloudflare's ABR Analytics](https://blog.cloudflare.com/explaining-cloudflares-abr-analytics/).
The data displayed in Web Analytics is real user monitoring (RUM). For more information, refer to [Real User Monitoring](https://en.wikipedia.org/wiki/Real_user_monitoring).
Cloudflare Web Analytics does not collect or use your visitors’ personal data.
[Get started](http://dash.cloudflare.com/sign-up/web-analytics)
[Learn more](https://developers.cloudflare.com/web-analytics/data-metrics/)
</page>
<page>
---
title: Changelog for beacon.min.js · Cloudflare Web Analytics docs
description: Cloudflare occasionally updates the beacon.min.js file to improve
Web Analytics functionality. The table below includes a log of what changed in
the beacon.min.js file and when.
lastUpdated: 2025-02-13T19:35:19.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/web-analytics/changelog/
md: https://developers.cloudflare.com/web-analytics/changelog/index.md
---
Cloudflare occasionally updates the `beacon.min.js` file to improve Web Analytics functionality. The table below includes a log of what changed in the `beacon.min.js` file and when.
[Subscribe to RSS](https://developers.cloudflare.com/web-analytics/changelog/index.xml)
## 2024-06-11
Enhanced to include reporting of Server-Timing headers.
## 2024-05-22
Introducing new metric fields, transferSize and decodedBodySize are included.
## 2024-04-17
Introducing new metric fields, deliveryType (dt) and navigationType (nt) are included.
## 2023-10-18
Manages A/B testing tags.
## 2023-07-25
Fixed ETag format in the response header.
## 2023-07-13
Fixed the issue that was causing an illegal invocation error.
## 2023-04-19
Reports additional LCP diagnostic information using web-vitals library's attribution build.
## 2023-04-06
Updated webpack configuration to output code in ECMAScript 3 (ES3) format.
## 2023-03-23
Updated Google's web-vitals library (version 3.1.1) and removed experimental `server-timing` header.
## 2022-10-17
Updated to report new metrics such as time to first byte (TTFB), interaction to next paint (INP), and first contentful paint (FCP). Additionally, it reports `navigator.webdriver`, `server-timing` header (experimental), and protocol info (`nextHopProtocol`).
## 2021-12-14
Improved site filtering.
## 2021-11-16
When using the automatic installation feature of the JavaScript Beacon (available only to customers proxied through Cloudflare - also known as orange-clouded customers), [Subresource Integrity (SRI)](https://developer.mozilla.org/en-US/docs/Web/Security/Subresource_Integrity) is now enabled by default. SRI is a security feature that enables browsers to verify that resources they fetch are delivered without unexpected manipulation.
## 2021-09-01
Improved to report debugging information for Core Web Vitals.
## 2021-05-28
`startsWith` function replaced with `indexOf` function, which prevents rendering if multiple beacon scripts are loaded.
## 2021-05-12
Reporting endpoint changed from `/cdn-cgi/beacon/performance` to `/cdn-cgi/rum` (for Browser Insights only).
</page>
<page>
---
title: Configuration options · Cloudflare Web Analytics docs
description: Customize your Web Analytics views by using filters and rules.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/web-analytics/configuration-options/
md: https://developers.cloudflare.com/web-analytics/configuration-options/index.md
---
Customize your Web Analytics views by using filters and rules.
* [Filters](https://developers.cloudflare.com/web-analytics/configuration-options/filters/)
* [Rules](https://developers.cloudflare.com/web-analytics/configuration-options/rules/)
</page>
<page>
---
title: Data and metrics · Cloudflare Web Analytics docs
description: In this section, you can find information about the data and
metrics available in Web Analytics.
lastUpdated: 2024-08-13T19:56:56.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/web-analytics/data-metrics/
md: https://developers.cloudflare.com/web-analytics/data-metrics/index.md
---
In this section, you can find information about the data and metrics available in Web Analytics.
* [High-level metrics](https://developers.cloudflare.com/web-analytics/data-metrics/high-level-metrics/)
* [Page load time](https://developers.cloudflare.com/web-analytics/data-metrics/page-load-time-summary/)
* [Core Web Vitals](https://developers.cloudflare.com/web-analytics/data-metrics/core-web-vitals/)
* [Dimensions](https://developers.cloudflare.com/web-analytics/data-metrics/dimensions/)
* [Data origin and collection](https://developers.cloudflare.com/web-analytics/data-metrics/data-origin-and-collection/)
</page>
<page>
---
title: FAQs · Cloudflare Web Analytics docs
description: Below you will find answers to our most commonly asked questions.
If you cannot find the answer you are looking for, refer to the community page
to explore more resources.
lastUpdated: 2025-10-20T10:08:59.000Z
chatbotDeprioritize: false
source_url:
html: https://developers.cloudflare.com/web-analytics/faq/
md: https://developers.cloudflare.com/web-analytics/faq/index.md
---
Below you will find answers to our most commonly asked questions. If you cannot find the answer you are looking for, refer to the [community page](https://community.cloudflare.com/) to explore more resources.
* [Errors](#errors)
* [Setup](#setup)
* [Functionality](#functionality)
## Errors
### When I add the beacon to my website and load the webpage, I see an error that includes `is not allowed by Access-Control-Allow-Origin` (CORS). What is happening?
This error usually occurs when the hostname of the site loading the analytics does not match the name of the analytics site configured in the dashboard. Double-check that they are identical.
Cloudflare matches hostnames based on a postfix. For example, if you set up analytics for `example.com`, we will allow analytics from `www.example.com`, `blog.staging.example.com`, and `fooexample.com`. However, we will not allow analytics from `example.com.br`.
You may also see this error if the site does not send a `Referer` or `Origin` header. The `Referer` header is required (do not try to use the `Referrer-policy` header instead). We have a change in-flight now that only the `Origin` header will be required – we believe there is no way to disable that in the browser.
### The analytics beacon is blocked by ad-blockers (including adblockplus, Brave, DuckDuckGo extension, etc). Why is that?
Cloudflare is aware that the analytics beacon is blocked by these services.
While Cloudflare Web Analytics uses a JavaScript beacon, Cloudflare’s edge analytics cannot be blocked because we can measure every request that is received. Edge analytics are available to any customer who proxies traffic through Cloudflare. Currently, users on Pro, Business, and Enterprise plans get advanced web analytics powered by our edge logs.
### Why am I not seeing all the metrics for single-page application (SPA) or multiple-page application (MPA)?
Every route change that occurs in the single-page app will send the measurement of the route before the route is changed to the beacon endpoint. The measurement for the last route change will be sent whenever the user leaves the tab or closes the browser window. That will trigger `visibilityState` to a hidden state. Whenever that happens, Beacon JS sends the payload using the [Navigator.sendBeacon method](https://developer.mozilla.org/en-US/docs/Web/API/Navigator/sendBeacon) that should not be cancelled even when the browser window is closed. However, due to compatibility, old browsers would fallback to using AJAX (`XmlHttpRequest`), which can be cancelled when the browser window is closed, so the last payload that gets sent to the beacon endpoint can be lost. Also, due to various network conditions, there can be data loss when the payload is sent to the beacon endpoint.
### For the same site, why would I see more data reported with an automatic setup?
Unless you are using Rules to control which pages to be measured, using [automatic setup](https://developers.cloudflare.com/web-analytics/get-started/#sites-proxied-through-cloudflare) will inject the JS snippet on all pages (sub-domains) under the zone.
If you used a [manual setup](https://developers.cloudflare.com/web-analytics/get-started/#sites-not-proxied-through-cloudflare) instead, only those pages that render the JS snippet will be reported.
Note
Since only one JS snippet can be rendered and used per page, you cannot have multiple snippets on the same page.
### My website is proxied through Cloudflare, but Web Analytic's automatic setup is not working.
If you have a `Cache-Control` header set to `public, no-transform`, Cloudflare proxy will not be able to modify the original payload of the website. Therefore, the Beacon script will not be automatically injected to your site, and Web Analytics will not work. Refer to [Origin cache control](https://developers.cloudflare.com/cache/concepts/cache-control/) for more information.
***
## Setup
### I am proxying my site through Cloudflare. Should I manually add the JS beacon?
You can, but you do not have to. Cloudflare Web Analytics is designed primarily for customers who do not use Cloudflare's proxy to measure their web traffic.
Existing Cloudflare customers can access analytics collected from our edge on the **Analytics** tab of the dashboard. You can also enable Web Analytics to measure performance using JavaScript.
Using a domain proxied through Cloudflare with [automatic setup](https://developers.cloudflare.com/web-analytics/get-started/#sites-proxied-through-cloudflare) will report stats back to your own domain's `/cdn-cgi/rum` endpoint. If you have installed JS snippet yourself (a [manual setup](https://developers.cloudflare.com/web-analytics/get-started/#sites-not-proxied-through-cloudflare)), it will report back to `cloudflareinsights.com/cdn-cgi/rum` endpoint.
### Can I add Web Analytics to my site using a tag manager like Google Tag Manager (GTM)?
Yes. Instead of embedding the script using a tag manager as shown here:
```html
<script
defer
src="https://static.cloudflareinsights.com/beacon.min.js"
data-cf-beacon='{"token": "$SITE_TOKEN"}'
></script>
```
Add the following script:
```html
<script
defer
src="https://static.cloudflareinsights.com/beacon.min.js?token=$SITE_TOKEN"
></script>
```
### Can I use the same JS Snippet for a different domain?
No. However, if the apex domain (also known as "root domain" or "naked domain") is the same, you can use the same site tag. For example, if you have provided us a hostname `example.com` when registering a site, you can use the JS snippet from that site for `abc.example.com` and `def.example.com` since they use the same apex domain. When payload gets sent to the beacon endpoint, we validate the hostname with postfix matching, so if your domain shares the same apex domain, that would work.
### Can I use automatic setup with a DNS-only domain (CNAME setup)?
No, you can only use the [automatic setup](https://developers.cloudflare.com/web-analytics/get-started/#sites-proxied-through-cloudflare) with JS snippet injection if traffic to your domain is proxied through Cloudflare (orange-clouded).
If you have a DNS-only domain, you will have to do a [manual setup](https://developers.cloudflare.com/web-analytics/get-started/#sites-not-proxied-through-cloudflare) instead.
### What prevents the JS Snippet from being added to a page?
For Cloudflare to automatically add the JavaScript snippet, your pages need to have valid HTML.
For example, Cloudflare would not be able to enable Web Analytics on a page like this:
```html
Hello world.
```
For Web Analytics to correctly insert the JavaScript snippet, you would need valid HTML output, such as:
```html
<!DOCTYPE html>
<html>
<head>
<title>Title
Hello world.