Changelog
Cloudflare One Product Name Updates
We are updating naming related to some of our Networking products to better clarify their place in the Zero Trust and Secure Access Service Edge (SASE) journey.
We are retiring some older brand names in favor of names that describe exactly what the products do within your network. We are doing this to help customers build better, clearer mental models for comprehensive SASE architecture delivered on Cloudflare.
- Magic WAN → Cloudflare WAN
- Magic WAN IPsec → Cloudflare IPsec
- Magic WAN GRE → Cloudflare GRE
- Magic WAN Connector → Cloudflare One Appliance
- Magic Firewall → Cloudflare Network Firewall
- Magic Network Monitoring → Network Flow
- Magic Cloud Networking → Cloudflare One Multi-cloud Networking
No action is required by you — all functionality, existing configurations, and billing will remain exactly the same.
For more information, visit the Cloudflare One documentation.
Anycast IPs displayed on the dashboard
Cloudflare WAN now displays your Anycast IP addresses directly in the dashboard when you configure IPsec or GRE tunnels.
Previously, customers received their Anycast IPs during onboarding or had to retrieve them with an API call. The dashboard now pre-loads these addresses, reducing setup friction and preventing configuration errors.
No action is required. All Cloudflare WAN customers can see their Anycast IPs in the tunnel configuration form automatically.
For more information, refer to Configure tunnel endpoints.
BGP over GRE and IPsec tunnels
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using IPsec and GRE tunnel on-ramps (beta).
Using BGP peering allows customers to:
- Automate the process of adding or removing networks and subnets.
- Take advantage of failure detection and session recovery features.
With this functionality, customers can:
- Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via IPsec and GRE tunnel on-ramps.
- Secure the session by MD5 authentication to prevent misconfigurations.
- Exchange routes dynamically between their devices and their Magic routing table.
For configuration details, refer to:
Configure Cloudflare source IPs (beta)
Cloudflare source IPs are the IP addresses used by Cloudflare services (such as Load Balancing, Gateway, and Browser Isolation) when sending traffic to your private networks.
For customers using legacy mode routing, traffic to private networks is sourced from public Cloudflare IPs, which may cause IP conflicts. For customers using Unified Routing mode (beta), traffic to private networks is sourced from dedicated, non-Internet-routable private IPv4 range to ensure:
- Symmetric routing over private network connections
- Proper firewall state preservation
- Private traffic stays on secure paths
Key details:
- IPv4: Sourced from
100.64.0.0/12by default, configurable to any/12CIDR - IPv6: Sourced from
2606:4700:cf1:5000::/64(not configurable) - Affected connectors: GRE, IPsec, CNI, WARP Connector, and WARP Client (Cloudflare Tunnel is not affected)
Configuring Cloudflare source IPs requires Unified Routing (beta) and the Cloudflare One Networks Write permission.
For configuration details, refer to Configure Cloudflare source IPs.
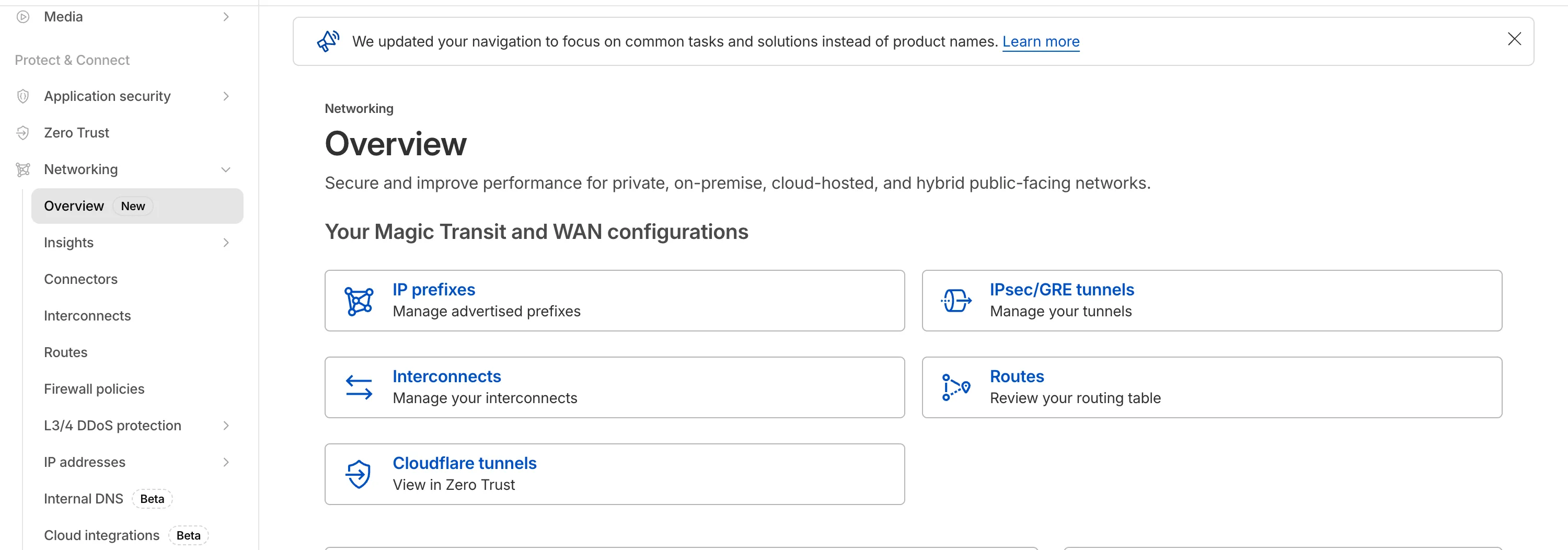
Network Services navigation update
The Network Services menu structure in Cloudflare's dashboard has been updated to reflect solutions and capabilities instead of product names. This will make it easier for you to find what you need and better reflects how our services work together.
Your existing configurations will remain the same, and you will have access to all of the same features and functionality.
The changes visible in your dashboard may vary based on the products you use. Overall, changes relate to Magic Transit ↗, Magic WAN ↗, and Magic Firewall ↗.
Summary of changes:
- A new Overview page provides access to the most common tasks across Magic Transit and Magic WAN.
- Product names have been removed from top-level navigation.
- Magic Transit and Magic WAN configuration is now organized under Routes and Connectors. For example, you will find IP Prefixes under Routes, and your GRE/IPsec Tunnels under Connectors.
- Magic Firewall policies are now called Firewall Policies.
- Magic WAN Connectors and Connector On-Ramps are now referenced in the dashboard as Appliances and Appliance profiles. They can be found under Connectors > Appliances.
- Network analytics, network health, and real-time analytics are now available under Insights.
- Packet Captures are found under Insights > Diagnostics.
- You can manage your Sites from Insights > Network health.
- You can find Magic Network Monitoring under Insights > Network flow.
If you would like to provide feedback, complete this form ↗. You can also find these details in the January 7, 2026 email titled [FYI] Upcoming Network Services Dashboard Navigation Update.
Breakout traffic visibility via NetFlow
Magic WAN Connector now exports NetFlow data for breakout traffic to Magic Network Monitoring (MNM), providing visibility into traffic that bypasses Cloudflare's security filtering.
This feature allows you to:
- Monitor breakout traffic statistics in the Cloudflare dashboard.
- View traffic patterns for applications configured to bypass Cloudflare.
- Maintain visibility across all traffic passing through your Magic WAN Connector.
For more information, refer to NetFlow statistics.
Automatic Return Routing (Beta)
Magic WAN now supports Automatic Return Routing (ARR), allowing customers to configure Magic on-ramps (IPsec/GRE/CNI) to learn the return path for traffic flows without requiring static routes.
Key benefits:
- Route-less mode: Static or dynamic routes are optional when using ARR.
- Overlapping IP space support: Traffic originating from customer sites can use overlapping private IP ranges.
- Symmetric routing: Return traffic is guaranteed to use the same connection as the original on-ramp.
This feature is currently in beta and requires the new Unified Routing mode (beta).
For configuration details, refer to Configure Automatic Return Routing.
Designate WAN link for breakout traffic
Magic WAN Connector now allows you to designate a specific WAN port for breakout traffic, giving you deterministic control over the egress path for latency-sensitive applications.
With this feature, you can:
- Pin breakout traffic for specific applications to a preferred WAN port.
- Ensure critical traffic (such as Zoom or Teams) always uses your fastest or most reliable connection.
- Benefit from automatic failover to standard WAN port priority if the preferred port goes down.
This is useful for organizations with multiple ISP uplinks who need predictable egress behavior for performance-sensitive traffic.
For configuration details, refer to Designate WAN ports for breakout apps.
DNS filtering for private network onramps
Magic WAN and WARP Connector users can now securely route their DNS traffic to the Gateway resolver without exposing traffic to the public Internet.
Routing DNS traffic to the Gateway resolver allows DNS resolution and filtering for traffic coming from private networks while preserving source internal IP visibility. This ensures Magic WAN users have full integration with our Cloudflare One features, including Internal DNS and hostname-based policies.
To configure DNS filtering, change your Magic WAN or WARP Connector DNS settings to use Cloudflare's shared resolver IPs, 172.64.36.1 and 172.64.36.2. Once you configure DNS resolution and filtering, you can use Source Internal IP as a traffic selector in your resolver policies for routing private DNS traffic to your Internal DNS.
Custom IKE ID for IPsec Tunnels
Now, Magic WAN customers can configure a custom IKE ID for their IPsec tunnels. Customers that are using Magic WAN and a VeloCloud SD-WAN device together can utilize this new feature to create a high availability configuration.
This feature is available via API only. Customers can read the Magic WAN documentation to learn more about the Custom IKE ID feature and the API call to configure it.
Bidirectional tunnel health checks are compatible with all Magic on-ramps
All bidirectional tunnel health check return packets are accepted by any Magic on-ramp.
Previously, when a Magic tunnel had a bidirectional health check configured, the bidirectional health check would pass when the return packets came back to Cloudflare over the same tunnel that was traversed by the forward packets.
There are SD-WAN devices, like VeloCloud, that do not offer controls to steer traffic over one tunnel versus another in a high availability tunnel configuration.
Now, when a Magic tunnel has a bidirectional health check configured, the bidirectional health check will pass when the return packet traverses over any tunnel in a high availability configuration.
Terraform V5 support for tunnels and routes
The Cloudflare Terraform provider resources for Cloudflare WAN tunnels and routes now support Terraform provider version 5. Customers using infrastructure-as-code workflows can manage their tunnel and route configuration with the latest provider version.
For more information, refer to the Cloudflare Terraform provider documentation ↗.
Magic Transit and Magic WAN health check data is fully compatible with the CMB EU setting.
Today, we are excited to announce that all Magic Transit and Magic WAN customers with CMB EU (Customer Metadata Boundary - Europe) enabled in their account will be able to access GRE, IPsec, and CNI health check and traffic volume data in the Cloudflare dashboard and via API.
This ensures that all Magic Transit and Magic WAN customers with CMB EU enabled will be able to access all Magic Transit and Magic WAN features.
Specifically, these two GraphQL endpoints are now compatible with CMB EU:
magicTransitTunnelHealthChecksAdaptiveGroupsmagicTransitTunnelTrafficAdaptiveGroups
Virtual Cloudflare One Appliance with KVM support (open beta)
The KVM-based virtual Cloudflare One Appliance is now in open beta with official support for Proxmox VE.
Customers can deploy the virtual appliance on KVM hypervisors to connect branch or data center networks to Cloudflare WAN without dedicated hardware.
For setup instructions, refer to Configure a virtual Cloudflare One Appliance.
Cloudflare One Appliance supports multiple DNS server IPs
Cloudflare One Appliance DHCP server settings now support specifying multiple DNS server IP addresses in the DHCP pool.
Previously, customers could only configure a single DNS server per DHCP pool. With this update, you can specify multiple DNS servers to provide redundancy for clients at branch locations.
For configuration details, refer to DHCP server.
Configure your Magic WAN Connector to connect via static IP assigment
You can now locally configure your Magic WAN Connector to work in a static IP configuration.
This local method does not require having access to a DHCP Internet connection. However, it does require being comfortable with using tools to access the serial port on Magic WAN Connector as well as using a serial terminal client to access the Connector's environment.
For more details, refer to WAN with a static IP address.
Establish BGP peering over Direct CNI circuits
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering allows customers to:
- Automate the process of adding or removing networks and subnets.
- Take advantage of failure detection and session recovery features.
With this functionality, customers can:
- Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
- Secure the session by MD5 authentication to prevent misconfigurations.
- Exchange routes dynamically between their devices and their Magic routing table.
Refer to Magic WAN BGP peering or Magic Transit BGP peering to learn more about this feature and how to set it up.
Sites feature available to all Magic WAN customers
All Magic WAN customers now have full access to the Magic WAN sites feature. Customers can configure a Magic WAN site either with or without a Magic WAN connector.
Magic WAN Connector configurable health checks
Health check rate on Magic WAN Connector IPsec tunnels are now configurable.
BGP support for Cloudflare Network Interconnect (CNI)
Magic WAN customers can now establish BGP peering over Direct CNI circuits. Customers can now dynamically exchange routes and path availability status between their router device and the Magic WAN table.
LAN Policy improvements for the Magic WAN Connector
Magic WAN Connector LAN Policy now supports unidirectional traffic flows and port-ranges.
Early access testing for BGP on CNI 2.0 circuits
Customers can exchange routes dynamically with their Magic virtual network overlay via Direct CNI or Cloud CNI based connectivity.
Magic WAN Connector sends WARP client traffic to Internet
All Magic WAN Connectors now route WARP client traffic directly to the Internet, bypassing IPsec tunneling, to prevent double encapsulation of WARP traffic.
Updates to High Availability on the Magic WAN Connector
The High Availability feature on Magic WAN Connector now supports additional failover conditions, DHCP lease syncing, and staggered upgrades.
ICMP support for traffic sourced from private IPs
Magic WAN will now support ICMP traffic sourced from private IPs going to the Internet via Gateway.
Application based prioritization
The Magic WAN Connector can now prioritize traffic on a per-application basis.
WARP virtual IP addresses
Customers using Gateway to filter traffic to Magic WAN destinations will now see traffic from Cloudflare egressing with WARP virtual IP addresses (CGNAT range), rather than public Cloudflare IP addresses. This simplifies configuration and improves visibility for customers.
Network segmentation
You can define policies in your Connector to either allow traffic to flow between your LANs without it leaving your local premises or to forward it via the Cloudflare network where you can add additional security features.