Changelog
Saved views for Threat Events
TL;DR: You can now create and save custom configurations of the Threat Events dashboard, allowing you to instantly return to specific filtered views — such as industry-specific attacks or regional Sankey flows — without manual reconfiguration.
Threat intelligence is most effective when it is personalized. Previously, analysts had to manually re-apply complex filters (like combining specific industry datasets with geographic origins) every time they logged in. This update provides material value by:
- Analysts can now jump straight into "Known Ransomware Infrastructure" or "Retail Sector Targets" views with a single click, eliminating repetitive setup tasks
- Teams can ensure everyone is looking at the same data subsets by using standardized saved views, reducing the risk of missing critical patterns due to inconsistent filtering.
Cloudforce One subscribers can start saving their custom views now in Application Security > Threat Intelligence > Threat Events ↗.
Cloudforce One Threat events graphs are now visible in the dashboard
We have introduced dynamic visualizations to the Threat Events dashboard to help you better understand the threat landscape and identify emerging patterns at a glance.
What's new:
- Sankey Diagrams: Trace the flow of attacks from country of origin to target country to identify which regions are being hit hardest and where the threat infrastructure resides.

- Dataset Distribution over time: Instantly pivot your view to understand if a specific campaign is targeting your sector or if it is a broad-spectrum commodity attack.

- Enhanced Filtering: Use these visual tools to filter and drill down into specific attack vectors directly from the charts.
Cloudforce One subscribers can explore these new views now in Application Security > Threat Intelligence > Threat Events ↗.
Enhanced Logo Matching for Brand Protection
We have significantly upgraded our Logo Matching capabilities within Brand Protection. While previously limited to approximately 100% matches, users can now detect a wider range of brand assets through a redesigned matching model and UI.
- Configurable match thresholds: Users can set a minimum match score (starting at 75%) when creating a logo query to capture subtle variations or high-quality impersonations.
- Visual match scores: Allow users to see the exact percentage of the match directly in the results table, highlighted with color-coded lozenges to indicate severity.
- Direct logo previews: Available in the Cloudflare dashboard — similar to string matches — to verify infringements at a glance.
- Expose sophisticated impersonators who use slightly altered logos to bypass basic detection filters.
- Faster triage of the most relevant threats immediately using visual indicators, reducing the time spent manually reviewing matches.
Ready to protect your visual identity? Learn more in our Brand Protection documentation.
Threat actor identification with "also known as" aliases
Identifying threat actors can be challenging, because naming conventions often vary across the security industry. To simplify your research, Cloudflare Threat Events now include an Also known as field, providing a list of common aliases and industry-standard names for the groups we track.
This new field is available in both the Cloudflare dashboard and via the API. In the dashboard, you can view these aliases by expanding the event details side panel (under the Attacker field) or by adding it as a column in your configurable table view.
- Easily map Cloudflare-tracked actors to the naming conventions used by other vendors without manual cross-referencing.
- Quickly identify if a detected threat actor matches a group your team is already monitoring via other intelligence feeds.
For more information on how to access this data, refer to the Threat Events API documentation ↗.
URL Scanner now supports PDF report downloads
We have expanded the reporting capabilities of the Cloudflare URL Scanner. In addition to existing JSON and HAR exports, users can now generate and download a PDF report directly from the Cloudflare dashboard. This update streamlines how security analysts can share findings with stakeholders who may not have access to the Cloudflare dashboard or specialized tools to parse JSON and HAR files.
Key Benefits:
- Consolidate scan results, including screenshots, security signatures, and metadata, into a single, portable document
- Easily share professional-grade summaries with non-technical stakeholders or legal teams for faster incident response
What’s new:
- PDF Export Button: A new download option is available in the URL Scanner results page within the Cloudflare dashboard
- Unified Documentation: Access all scan details—from high-level summaries to specific security flags—in one offline-friendly file
To get started with the URL Scanner and explore our reporting capabilities, visit the URL Scanner API documentation ↗.
Cloudflare Threat Events now support STIX2 format
We are excited to announce that Cloudflare Threat Events now supports the STIX2 (Structured Threat Information Expression) format. This was a highly requested feature designed to streamline how security teams consume and act upon our threat intelligence.
By adopting this industry-standard format, you can now integrate Cloudflare's threat events data more effectively into your existing security ecosystem.
-
Eliminate the need for custom parsers, as STIX2 allows for "out of the box" ingestion into major Threat Intel Platforms (TIPs), SIEMs, and SOAR tools.
-
STIX2 provides a standardized way to represent relationships between indicators, sightings, and threat actors, giving your analysts a clearer picture of the threat landscape.
For technical details on how to query events using this format, please refer to our Threat Events API Documentation ↗.
Threat insights are now available in the Threat Events platform
The threat events platform now has threat insights available for some relevant parent events. Threat intelligence analyst users can access these insights for their threat hunting activity.
Insights are also highlighted in the Cloudflare dashboard by a small lightning icon and the insights can refer to multiple, connected events, potentially part of the same attack or campaign and associated with the same threat actor.
For more information, refer to Analyze threat events.
Report logo misuse to Cloudflare directly from the Brand Protection dashboard
The Brand Protection logo query dashboard now allows you to use the Report to Cloudflare button to submit an Abuse report directly from the Brand Protection logo queries dashboard. While you could previously report new domains that were impersonating your brand before, now you can do the same for websites found to be using your logo wihtout your permission. The abuse reports wiull be prefilled and you will only need to validate a few fields before you can click the submit button, after which our team process your request.
Ready to start? Check out the Brand Protection docs.
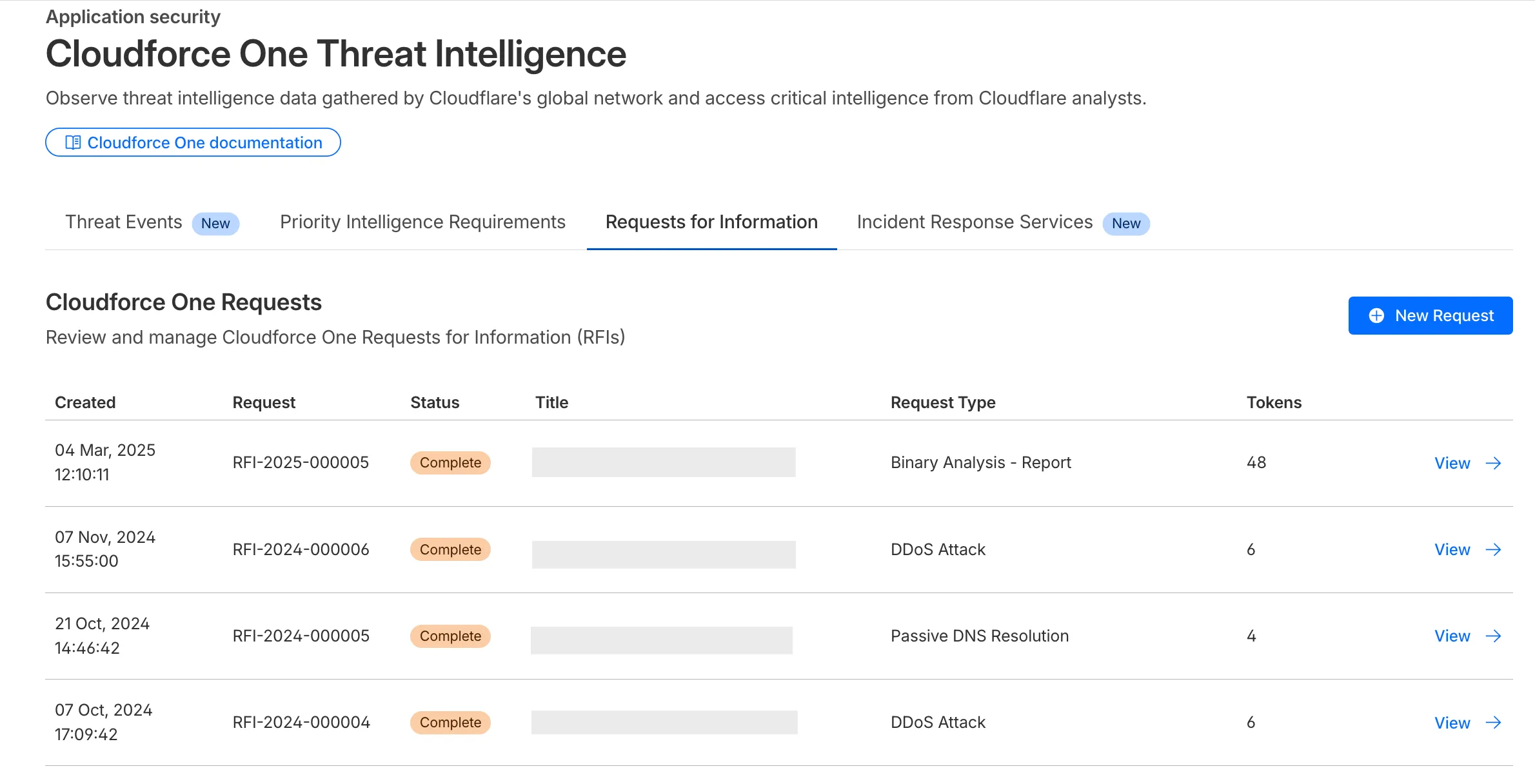
Cloudforce One RFI tokens are now visible in the dashboard
The Requests for Information (RFI) dashboard now shows users the number of tokens used by each submitted RFI to better understand usage of tokens and how they relate to each request submitted.
What’s new:
- Users can now see the number of tokens used for a submitted request for information.
- Users can see the remaining tokens allocated to their account for the quarter.
- Users can only select the Routine priority for the
Strategic Threat Researchrequest type.
Cloudforce One subscribers can try it now in Application Security > Threat Intelligence > Requests for Information ↗.
New Application Security reports (Closed Beta)
Cloudflare's new Application Security report, currently in Closed Beta, is now available in the dashboard.
Go to Security reportsThe reports are generated monthly and provide cyber security insights trends for all of the Enterprise zones in your Cloudflare account.
The reports also include an industry benchmark, comparing your cyber security landscape to peers in your industry.
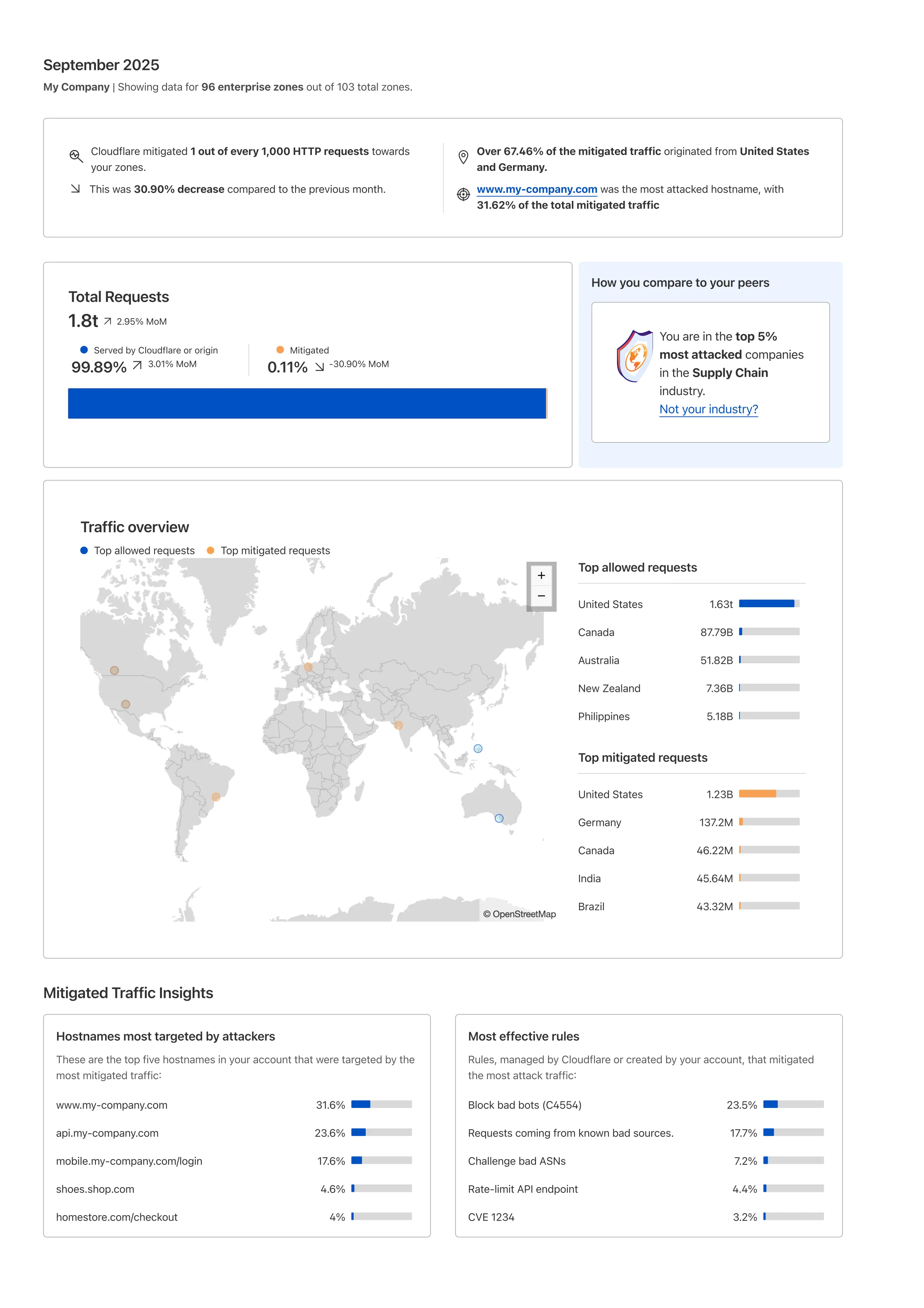
Learn more about the reports by referring to the Security Reports documentation.
Use the feedback survey link at the top of the page to help us improve the reports.
Save time with bulk query creation in Brand Protection
Brand Protection detects domains that may be impersonating your brand — from common misspellings (cloudfalre.com) to malicious concatenations (cloudflare-okta.com). Saved search queries run continuously and alert you when suspicious domains appear.
You can now create and save multiple queries in a single step, streamlining setup and management. Available now via the Brand Protection bulk query creation API.
New APIs for Brand Protection setup
The Brand Protection API is now available, allowing users to create new queries and delete existing ones, fetch matches and more!
What you can do:
- create new string or logo query
- delete string or logo queries
- download matches for both logo and string queries
- read matches for both logo and string queries
Ready to start? Check out the Brand Protection API in our documentation.
URL Scanner now supports geo-specific scanning
Enterprise customers can now choose the geographic location from which a URL scan is performed — either via Security Center in the Cloudflare dashboard or via the URL Scanner API.
This feature gives security teams greater insight into how a website behaves across different regions, helping uncover targeted, location-specific threats.
What’s new:
- Location Picker: Select a location for the scan via Security Center → Investigate in the dashboard or through the API.
- Region-aware scanning: Understand how content changes by location — useful for detecting regionally tailored attacks.
- Default behavior: If no location is set, scans default to the user’s current geographic region.
Learn more in the Security Center documentation.
- Security Center now has a role called Brand Protection. This role gives you access to the Brand Protection feature on the API and Cloudflare dashboard. Brand Protection role also gives you access to the Investigate platform, where you can consume the Threat Intel API and URL scanner API calls.
- On the URL scanner, customers who search for a report will now get a list of all reports related to that specific hostname. A hash is also available in the security report. By selecting the hash, the dashboard will list reports containing the same hash.
- Customers can now export all matches from a saved query. Select your Query name > select the three dots > Export matches.
- Customers can now create a
security.txtfile file to provide the security research team with a standardized way to report vulnerabilities.
- Customers can now archive multiple Security Insights at the same time. Go to Security Center > Security Insights and select the insights to archive.