Eliminate long-lived credentials and enhance SSH security with Cloudflare Access for Infrastructure
Organizations can now eliminate long-lived credentials from their SSH setup and enable strong multi-factor authentication for SSH access, similar to other Access applications, all while generating access and command logs.
SSH with Access for Infrastructure uses short-lived SSH certificates from Cloudflare, eliminating SSH key management and reducing the security risks associated with lost or stolen keys. It also leverages a common deployment model for Cloudflare One customers: WARP-to-Tunnel.
SSH with Access for Infrastructure enables you to:
- Author fine-grained policy to control who may access your SSH servers, including specific ports, protocols, and SSH users.
- Monitor infrastructure access with Access and SSH command logs, supporting regulatory compliance and providing visibility in case of security breach.
- Preserve your end users' workflows. SSH with Access for Infrastructure supports native SSH clients and does not require any modifications to users’ SSH configs.
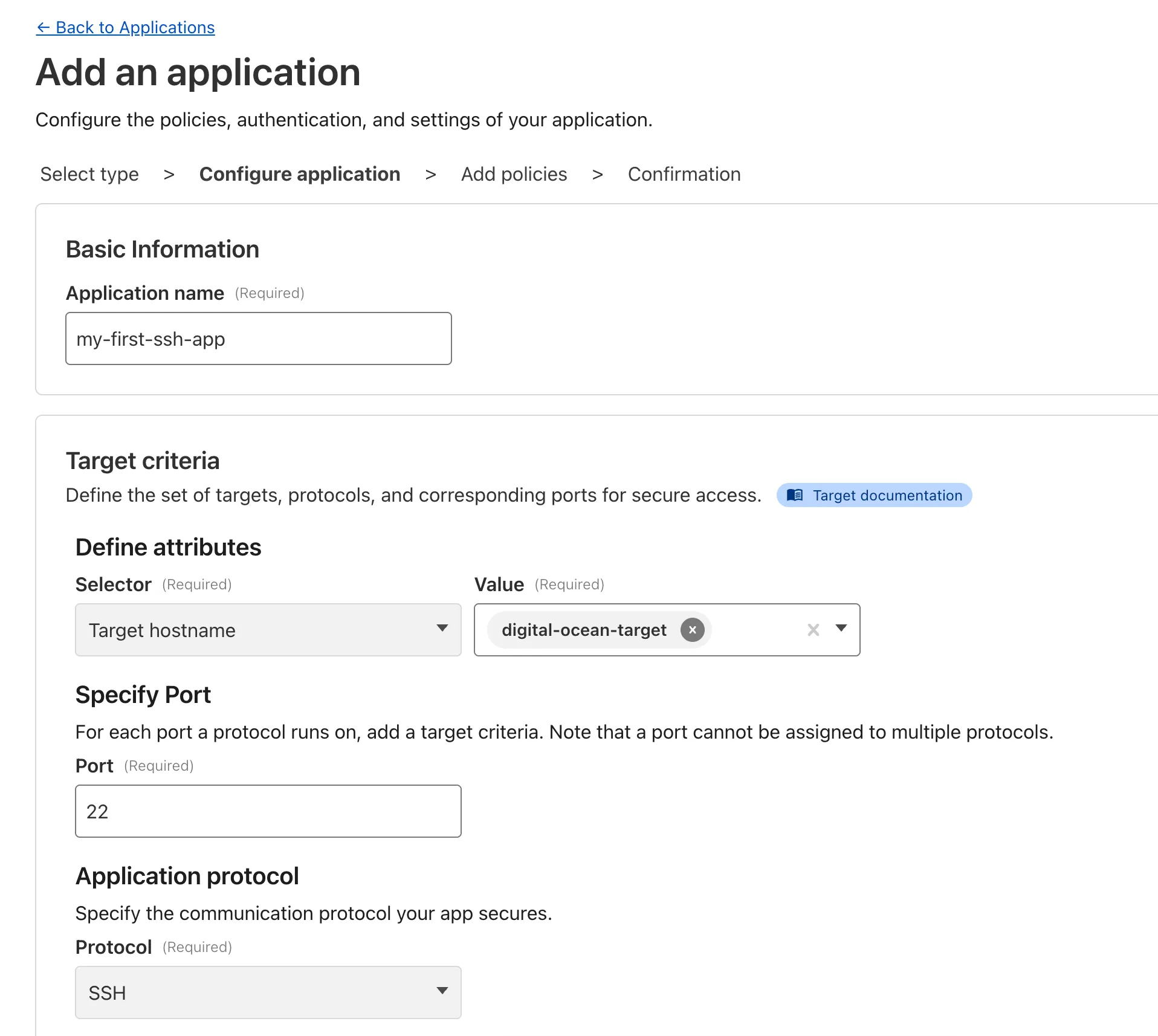
To get started, refer to SSH with Access for Infrastructure.