Remotely-managed tunnel
If you created a Cloudflare Tunnel from the dashboard, the tunnel runs as a service on your OS.
You can modify the Cloudflare Tunnel service with one or more general-purpose tunnel parameters.
On Linux, Cloudflare Tunnel installs itself as a system service using systemctl. By default, the service will be named cloudflared.service. To configure your tunnel on Linux:
-
Open
cloudflared.service.Terminal window sudo systemctl edit --full cloudflared.service -
Modify the
cloudflared tunnel runcommand with the desired configuration flag. For example,[Unit]Description=Cloudflare TunnelAfter=network.target[Service]TimeoutStartSec=0Type=notifyExecStart=/usr/local/bin/cloudflared tunnel --loglevel debug --logfile /var/log/cloudflared/cloudflared.log run --token <TOKEN VALUE>Restart=on-failureRestartSec=5s[Install]WantedBy=multi-user.target -
Restart
cloudflared.service:Terminal window sudo systemctl restart cloudflared -
To verify the new configuration, check the service status:
Terminal window sudo systemctl status cloudflared● cloudflared.service - cloudflaredLoaded: loaded (/etc/systemd/system/cloudflared.service; enabled; preset: enabled)Active: active (running) since Wed 2024-10-09 20:02:59 UTC; 2s agoMain PID: 2157 (cloudflared)Tasks: 8 (limit: 1136)Memory: 16.3MCPU: 136msCGroup: /system.slice/cloudflared.service└─2157 /usr/bin/cloudflared tunnel --loglevel debug --logfile /var/log/cloudflared/cloudflared.log run --token eyJhIjoi...
On macOS, Cloudflare Tunnel installs itself as a launch agent using launchctl. By default, the agent will be called com.cloudflare.cloudflared. To configure your tunnel on macOS:
-
Stop the
cloudflaredservice.Terminal window sudo launchctl stop com.cloudflare.cloudflared -
Unload the configuration file.
Terminal window sudo launchctl unload /Library/LaunchDaemons/com.cloudflare.cloudflared.plist -
Open
/Library/LaunchDaemons/com.cloudflare.cloudflared.plistin a text editor. -
Modify the
ProgramArgumentskey with the desired configuration flag. For example,<plist version="1.0"><dict><key>Label</key><string>com.cloudflare.cloudflared</string><key>ProgramArguments</key><array><string>/opt/homebrew/bin/cloudflared</string><string>tunnel</string><string>--logfile</string><string><PATH></string><string>--loglevel</string><string>debug</string><string>run</string><string>--token</string><string><TOKEN VALUE> </string></array> -
Load the updated configuration file.
Terminal window sudo launchctl load /Library/LaunchDaemons/com.cloudflare.cloudflared.plist -
Start the
cloudflaredservice.Terminal window sudo launchctl start com.cloudflare.cloudflared
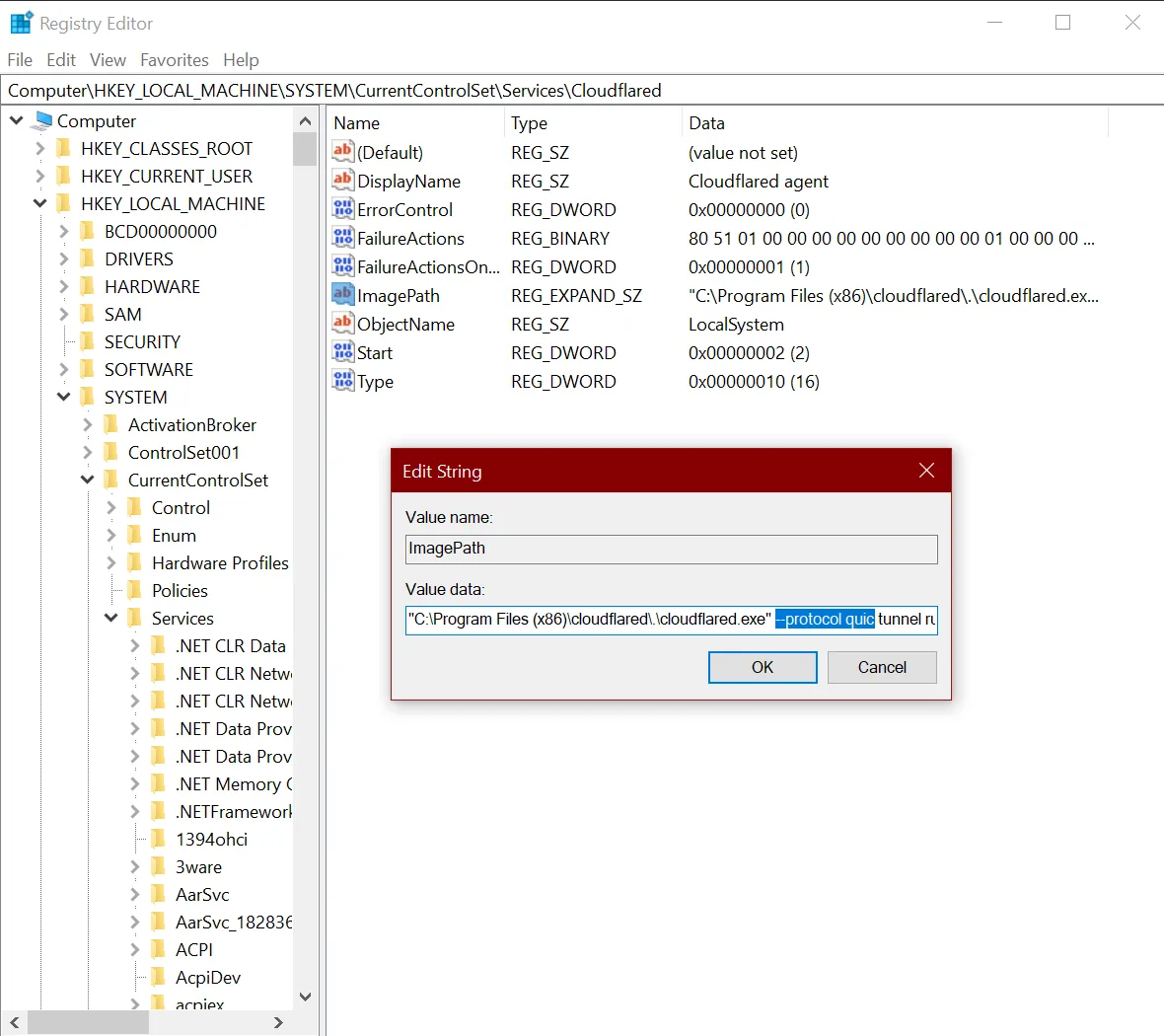
On Windows, Cloudflare Tunnel installs itself as a system service using the Registry Editor. By default, the service will be named cloudflared. To configure your tunnel on Windows:
-
Open the Registry Editor.
-
Go to HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Services > cloudflared.
-
Double-click ImagePath.
-
Modify Value data with the desired configuration flag. For example,
C:\Program Files (x86)\cloudflared\.\cloudflared.exe tunnel --loglevel debug --logfile <PATH> run --token <TOKEN VALUE>
To configure how cloudflared sends requests to your public hostname services:
- In Zero Trust ↗, go to Networks > Tunnels.
- Choose a tunnel and select Configure.
- Select the Public Hostname tab.
- Choose a route and select Edit.
- Under Additional application settings, modify one or more origin configuration parameters.
- Select Save hostname.
A remotely-managed tunnel only requires the tunnel token to run. Anyone with access to the token will be able to run the tunnel.
To get the token for a remotely-managed tunnel:
- In Zero Trust ↗, go to Networks > Tunnels.
- Select a
cloudflaredtunnel and select Edit. - Copy
cloudflaredinstallation command. - Paste the installation command into any text editor. The token value is of the form
eyJhIjoiNWFiNGU5Z...
Make a GET request to the Cloudflare Tunnel token endpoint. The token value can be found in the result:
{ "success": true, "errors": [], "messages": [], "result": "eyJhIjoiNWFiNGU5Z..."}Cloudflare recommends rotating the tunnel token at a regular cadence to reduce the risk of token compromise. You can rotate a token with minimal disruption to users as long as the tunnel is served by at least two cloudflared replicas. To ensure service availability, we recommend performing token rotations outside of working hours or in a maintenance window.
To rotate a tunnel token:
-
Refresh the token on Cloudflare:
- In Zero Trust ↗, go to Networks > Tunnels.
- Select a
cloudflaredtunnel and select Edit. - Select Refresh token.
- Copy the
cloudflaredinstallation command for your operating system. This command contains the new token.
-
Generate a random base64 string (minimum size 32 bytes) to use as a tunnel secret:
Terminal window openssl rand -base64 32AQIDBAUGBwgBAgMEBQYHCAECAwQFBgcIAQIDBAUGBwg= -
Make a
PATCHrequest to the Cloudflare Tunnel endpoint:Terminal window curl --request PATCH \https://api.cloudflare.com/client/v4/accounts/{account_id}/cfd_tunnel/{tunnel_id} \--header 'Content-Type: application/json' \--header "Authorization: Bearer <API_TOKEN>" \--data '{"name": "Example tunnel","tunnel_secret": "AQIDBAUGBwgBAgMEBQYHCAECAwQFBgcIAQIDBAUGBwg="}'{"success": true,"errors": [],"messages": [],"result": {"id": "f70ff985-a4ef-4643-bbbc-4a0ed4fc8415","account_tag": "699d98642c564d2e855e9661899b7252","created_at": "2024-12-04T22:03:26.291225Z","deleted_at": null,"name": "Example tunnel","connections": [],"conns_active_at": null,"conns_inactive_at": "2024-12-04T22:03:26.291225Z","tun_type": "cfd_tunnel","metadata": {},"status": "inactive","remote_config": true,"token": "eyJhIjoiNWFiNGU5Z..."}} -
Copy the
tokenvalue shown in the output.
After refreshing the token,
cloudflaredcan no longer establish new connections to Cloudflare using the old token. However, existing connectors will remain active and the tunnel will continue serving traffic. -
On half of your
cloudflaredreplicas, updatecloudflaredto use the new token. For example, on a Linux host:Terminal window sudo cloudflared service install <TOKEN> -
Restart
cloudflared:Terminal window sudo systemctl restart cloudflared.service -
Confirm that the service started correctly:
Terminal window sudo systemctl status cloudflaredWhile these replicas are connecting to Cloudflare with the new token, traffic will automatically route through the other replicas.
-
Wait 10 minutes for traffic to route through the new connectors.
-
Repeat steps 2, 3, and 4 for the second half of the replicas.
The tunnel token is now fully rotated. The old token is no longer in use.
If your tunnel token is compromised, we recommend taking the following steps:
-
Refresh the token using the dashboard or API. Refer to Step 1 of Rotate a token without service disruption.
-
Delete all connections between
cloudflaredand Cloudflare:Terminal window curl --request DELETE \https://api.cloudflare.com/client/v4/accounts/{account_id}/cfd_tunnel/{tunnel_id}/connections \--header "Authorization: Bearer <API_TOKEN>"This will clean up any unauthorized connections and prevent users from connecting to your network.
-
On each
cloudflaredreplica, updatecloudflaredto use the new token. For example, on a Linux host:Terminal window sudo cloudflared service install <TOKEN> -
Restart
cloudflared:Terminal window sudo systemctl restart cloudflared.service -
Confirm that the service started correctly:
Terminal window sudo systemctl status cloudflared
The tunnel token is now fully rotated. The old token is no longer in use.
Minimum permissions needed to create, delete, and configure tunnels for an account:
Additional permissions needed to route traffic to a public hostname: