Connect to a private database using Tunnel
Hyperdrive can securely connect to your private databases using Cloudflare Tunnel and Cloudflare Access.
When your database is isolated within a private network (such as a virtual private cloud ↗ or an on-premise network), you must enable a secure connection from your network to Cloudflare.
- Cloudflare Tunnel is used to establish the secure tunnel connection.
- Cloudflare Access is used to restrict access to your tunnel such that only specific Hyperdrive configurations can access it.
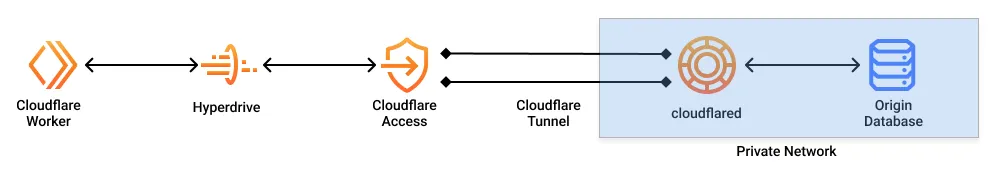
A request from the Cloudflare Worker to the origin database goes through Hyperdrive, Cloudflare Access, and the Cloudflare Tunnel established by cloudflared. cloudflared must be running in the private network in which your database is accessible.
The Cloudflare Tunnel will establish an outbound bidirectional connection from your private network to Cloudflare. Cloudflare Access will secure your Cloudflare Tunnel to be only accessible by your Hyperdrive configuration.
All of the tutorials assume you have already completed the Get started guide, which gets you set up with a Cloudflare Workers account, C3 ↗, and Wrangler.
- A database in your private network, configured to use TLS/SSL.
- A hostname on your Cloudflare account, which will be used to route requests to your database.
First, create a Cloudflare Tunnel in your private network to establish a secure connection between your network and Cloudflare. Your network must be configured such that the tunnel has permissions to egress to the Cloudflare network and access the database within your network.
-
Log in to Zero Trust ↗ and go to Networks > Tunnels.
-
Select Create a tunnel.
-
Choose Cloudflared for the connector type and select Next.
-
Enter a name for your tunnel. We suggest choosing a name that reflects the type of resources you want to connect through this tunnel (for example,
enterprise-VPC-01). -
Select Save tunnel.
-
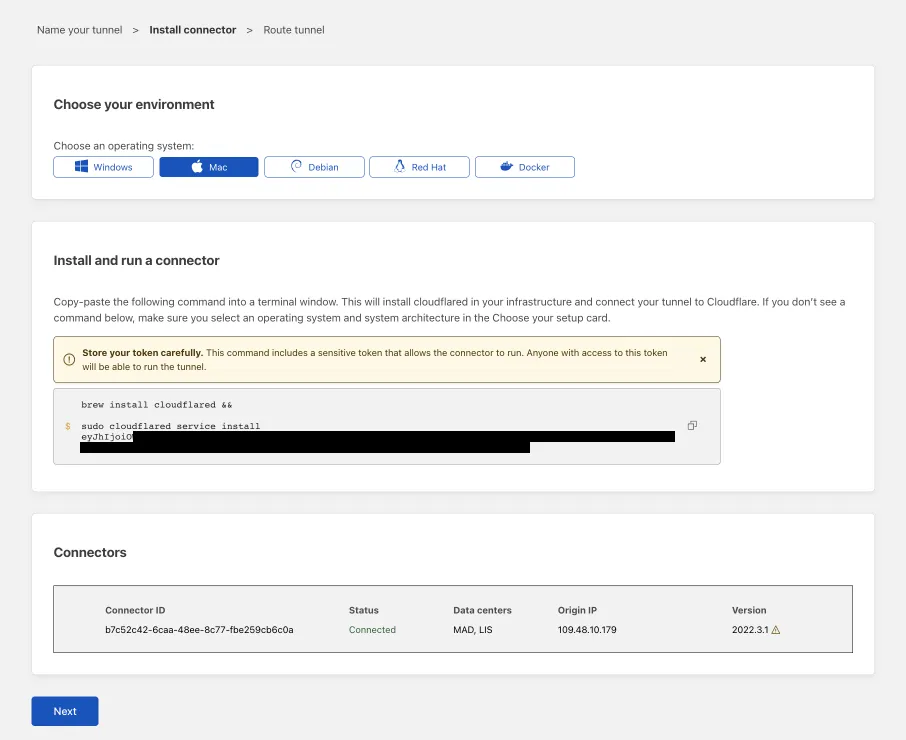
Next, you will need to install
cloudflaredand run it. To do so, check that the environment under Choose an environment reflects the operating system on your machine, then copy the command in the box below and paste it into a terminal window. Run the command. -
Once the command has finished running, your connector will appear in Zero Trust.
-
Select Next.
Your tunnel must be configured to use a public hostname so that Hyperdrive can route requests to it. If you don't have a hostname on Cloudflare yet, you will need to register a new hostname or add a zone to Cloudflare to proceed.
-
In the Public Hostnames tab, choose a Domain and specify any subdomain or path information. This will be used in your Hyperdrive configuration to route to this tunnel.
-
In the Service section, specify Type
TCPand the URL and configured port of your database, such aslocalhost:5432ormy-database-host.database-provider.com:5432. This address will be used by the tunnel to route requests to your database. -
Select Save tunnel.
To restrict access to the Cloudflare Tunnel to Hyperdrive, a Cloudflare Access application must be configured with a Policy that requires requests to contain a valid Service Auth token.
The Cloudflare dashboard can automatically create and configure the underlying Cloudflare Access application, Service Auth token, and Policy on your behalf. Alternatively, you can manually create the Access application and configure the Policies.
Create a Hyperdrive configuration in the Cloudflare dashboard to automatically configure Hyperdrive to connect to your Cloudflare Tunnel.
- In the Cloudflare dashboard ↗, navigate to Storage & Databases > Hyperdrive and click Create configuration.
- Select Private database.
- In the Networking details section, select the tunnel you are connecting to.
- In the Networking details section, select the hostname associated to the tunnel. If there is no hostname for your database, return to step 1.2. Connect your database using a public hostname.
- In the Access Service Authentication Token section, select Create new (automatic).
- In the Access Application section, select Create new (automatic).
- In the Database connection details section, enter the database name, user, and password.
The service token will be used to restrict requests to the tunnel, and is needed for the next step.
-
In Zero Trust ↗, go to Access > Service auth > Service Tokens.
-
Select Create Service Token.
-
Name the service token. The name allows you to easily identify events related to the token in the logs and to revoke the token individually.
-
Set a Service Token Duration of
Non-expiring. This prevents the service token from expiring, ensuring it can be used throughout the life of the Hyperdrive configuration. -
Select Generate token. You will see the generated Client ID and Client Secret for the service token, as well as their respective request headers.
-
Copy the Access Client ID and Access Client Secret. These will be used when creating the Hyperdrive configuration.
Cloudflare Access will be used to verify that requests to the tunnel originate from Hyperdrive using the service token created above.
-
In Zero Trust ↗, go to Access > Applications.
-
Select Add an application.
-
Select Self-hosted.
-
Enter any name for the application.
-
In Session Duration, select
No duration, expires immediately. -
Select Add public hostname. and enter the subdomain and domain that was previously set for the tunnel application.
-
Select Create new policy.
-
Enter a Policy name and set the Action to Service Auth.
-
Create an Include rule. Specify a Selector of Service Token and the Value of the service token you created in step 2. Create a service token.
-
Save the policy.
-
Go back to the application configuration and add the newly created Access policy.
-
In Login methods, turn off Accept all available identity providers and clear all identity providers.
-
Select Next.
-
In Application Appearance, turn off Show application in App Launcher.
-
Select Next.
-
Select Next.
-
Save the application.
To create a Hyperdrive configuration for your private database, you'll need to specify the Access application and Cloudflare Tunnel information upon creation.
# wrangler v3.65 and above requirednpx wrangler hyperdrive create <NAME-OF-HYPERDRIVE-CONFIGURATION-FOR-DB-VIA-TUNNEL> --host=<HOSTNAME-FOR-THE-TUNNEL> --user=<USERNAME-FOR-YOUR-DATABASE> --password=<PASSWORD-FOR-YOUR-DATABASE> --database=<DATABASE-TO-CONNECT-TO> --access-client-id=<YOUR-ACCESS-CLIENT-ID> --access-client-secret=<YOUR-SERVICE-TOKEN-CLIENT-SECRET>resource "cloudflare_hyperdrive_config" "<TERRAFORM_VARIABLE_NAME_FOR_CONFIGURATION>" { account_id = "<YOUR_ACCOUNT_ID>" name = "<NAME_OF_HYPERDRIVE_CONFIGURATION>" origin = { host = "<HOSTNAME_OF_TUNNEL>" database = "<NAME_OF_DATABASE>" user = "<NAME_OF_DATABASE_USER>" password = "<DATABASE_PASSWORD>" scheme = "postgres" access_client_id = "<ACCESS_CLIENT_ID>" access_client_secret = "<ACCESS_CLIENT_SECRET>" } caching = { disabled = false }}This will create a Hyperdrive configuration using the usual database information (database name, database host, database user, and database password).
In addition, it will also set the Access Client ID and the Access Client Secret of the Service Token. When Hyperdrive makes requests to the tunnel, requests will be intercepted by Access and validated using the credentials of the Service Token.
To test your Hyperdrive configuration to the database using Cloudflare Tunnel and Access, use the Hyperdrive configuration ID in your Worker and deploy it.
You must create a binding for your Worker to connect to your Hyperdrive configuration. Bindings allow your Workers to access resources, like D1, on the Cloudflare developer platform. You create bindings by updating your Wrangler file.
To bind your Hyperdrive configuration to your Worker, add the following to the end of your Wrangler file:
{ "hyperdrive": [ { "binding": "HYPERDRIVE", "id": "<YOUR_DATABASE_ID>" } ]}[[hyperdrive]]binding = "HYPERDRIVE"id = "<YOUR_DATABASE_ID>" # the ID associated with the Hyperdrive you just createdSpecifically:
- The value (string) you set for the
name(binding name) will be used to reference this database in your Worker. In this tutorial, name your bindingHYPERDRIVE. - The binding must be a valid JavaScript variable name ↗. For example,
binding = "hyperdrive"orbinding = "productionDB"would both be valid names for the binding. - Your binding is available in your Worker at
env.<BINDING_NAME>.
If you wish to use a local database during development, you can add a localConnectionString to your Hyperdrive configuration with the connection string of your database:
{ "hyperdrive": [ { "binding": "HYPERDRIVE", "id": "<YOUR_DATABASE_ID>", "localConnectionString": "<LOCAL_DATABASE_CONNECTION_URI>" } ]}[[hyperdrive]]binding = "HYPERDRIVE"id = "<YOUR_DATABASE_ID>" # the ID associated with the Hyperdrive you just createdlocalConnectionString = "<LOCAL_DATABASE_CONNECTION_URI>"Use Postgres.js to send a test query to validate that the connection has been successful.
Install the Postgres.js driver:
npm install postgresCreate a new sql instance and pass the Hyperdrive parameters:
import postgres from "postgres";
export interface Env { // If you set another name in the Wrangler configuration file as the value for 'binding', // replace "HYPERDRIVE" with the variable name you defined. HYPERDRIVE: Hyperdrive;}
export default { async fetch(request: Request, env: Env, ctx: ExecutionContext) { // NOTE: if `prepare: false` is passed when connecting, performance will // be slower but still correctly supported. const sql = postgres( env.HYPERDRIVE.connectionString, { // Workers limit the number of concurrent external connections, so be sure to limit // the size of the local connection pool that postgres.js may establish. max: 5,
// If you are using array types in your Postgres schema, it is necessary to fetch // type information to correctly de/serialize them. However, if you are not using // those, disabling this will save you an extra round-trip every time you connect. fetch_types: false, }, );
try { // A very simple test query const result = await sql`select * from pg_tables LIMIT 10`;
// Clean up the client, ensuring we don't kill the worker before that is // completed. ctx.waitUntil(sql.end());
// Return result rows as JSON return Response.json({ result: result }); } catch (e) { console.log(e); return Response.json({ error: e.message }, { status: 500 }); } },} satisfies ExportedHandler<Env>;Now, deploy your Worker:
npx wrangler deployIf you successfully receive the list of pg_tables from your database when you access your deployed Worker, your Hyperdrive has now been configured to securely connect to a private database using Cloudflare Tunnel and Cloudflare Access.
If you encounter issues when setting up your Hyperdrive configuration with tunnels to a private database, consider these common solutions, in addition to general troubleshooting steps for Hyperdrive:
- Ensure your database is configured to use TLS (SSL). Hyperdrive requires TLS (SSL) to connect.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark