SSO integration
Cloudflare Zero Trust allows you to integrate your organization's identity providers (IdPs) with Cloudflare Access. Your team can simultaneously use multiple providers, reducing friction when working with partners or contractors.
Adding an identity provider as a login method requires configuration both in Zero Trust ↗ and with the identity provider itself. Consult our IdP-specific documentation to learn more about what you need to set up.
-
In Zero Trust ↗, go to Settings > Authentication.
-
In the Login methods card, select Add new.
-
Select the identity provider you want to add.
If you do not see your identity provider listed, these providers can typically still be enabled. If they support OIDC or OAuth, select the generic OIDC option. If they support SAML, select the generic SAML option. Cloudflare supports all SAML and OIDC providers and can integrate with the majority of OAuth providers. If your provider supports both SAML and OIDC, we recommend OIDC for ease of configuration.
-
Fill in the necessary fields to set up your identity provider.
Each identity provider will have different required fields for you to fill in. Step-by-step instructions are shown in the dashboard side panel. Alternatively, refer to the IdP-specific documentation.
-
Once you have filled in the necessary fields, select Save.
-
Add the following permission to your
cloudflare_api_token↗:Access: Organizations, Identity Providers, and Groups Write
-
Add an identity provider to Zero Trust using the
cloudflare_zero_trust_access_identity_provider↗ resource. For example, to add a Microsoft Entra ID integration:resource "cloudflare_zero_trust_access_identity_provider" "microsoft_entra_id" {account_id = var.cloudflare_account_idname = "Entra ID example"type = "azureAD"config {client_id = var.entra_id_client_idclient_secret = var.entra_id_client_secretdirectory_id = var.entra_id_directory_idsupport_groups = true}}Each identity provider integration has different required attributes. You will need to obtain these attribute values from your identity provider. For more information, refer to the IdP-specific documentation.
If you do not see your identity provider listed, these providers can typically still be enabled. If they support OIDC or OAuth, use the generic OIDC option. If they support SAML, use the generic SAML option. Cloudflare supports all SAML and OIDC providers and can integrate with the majority of OAuth providers. If your provider supports both SAML and OIDC, we recommend OIDC for ease of configuration.
Your IdP will now be listed in the Login methods card.
To test if an IdP is correctly configured, go to Settings > Authentication. Next, select Test next to the IdP you would like to test. This will attempt to connect to the IdP to verify if a valid connection is established.
If your provider is connected, another window will open in your browser, with this message:
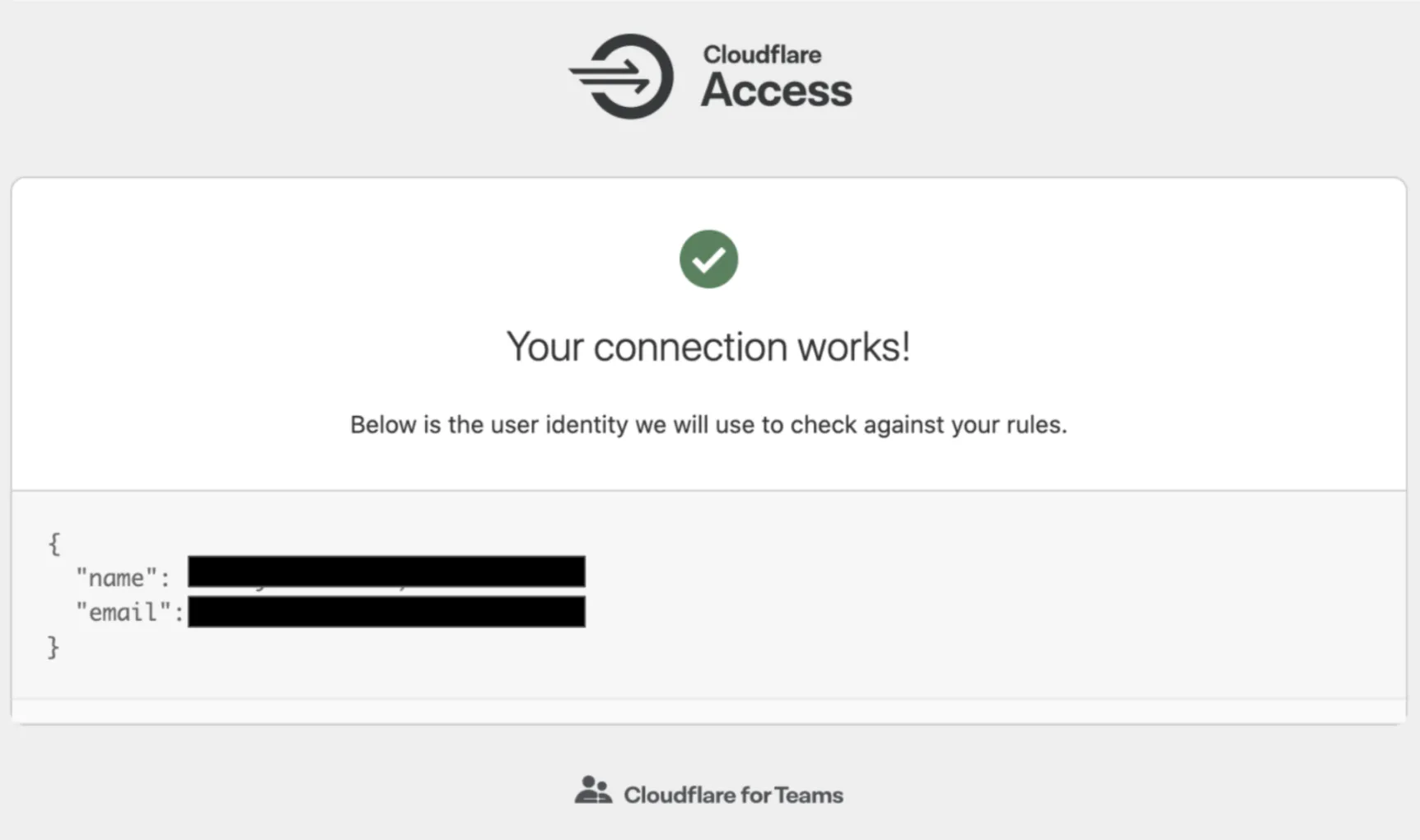
If your provider is not connected, another window will open in your browser. Along with an error message, you will receive a detailed explanation of why the test has failed.
We recommend that you use our dashboard to configure your identity providers. However, if you would like to use the Cloudflare API ↗, each of the identity provider topics covered here include an example API configuration snippet as well.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark