Rate limiting parameters
The available rate limiting rule parameters are described in the following sections.
- Data type: String
- Field name in the API:
expression(rule field)
Defines the criteria for the rate limiting rule to match a request.
- Data type: Boolean
- Field name in the API:
requests_to_origin(optional, with the opposite meaning of the Cloudflare dashboard option)
If this parameter is disabled (or when the requests_to_origin API field is set to true), only the requests going to the origin (that is, requests that are not cached) will be considered when determining the request rate.
In some cases, you cannot disable the Also apply rate limiting to cached assets parameter due to configuration restrictions. Refer to Configuration restrictions for details.
- Data type: Array<String>
- Field name in the API:
characteristics
Set of parameters defining how Cloudflare tracks the request rate for the rule.
Use one or more of the following characteristics:
| Dashboard value | API value | Notes |
|---|---|---|
| N/A(implicitly included) | cf.colo.id(mandatory) | Do not use in expressions |
| IP | ip.src | Incompatible with IP with NAT support |
| IP with NAT support | cf.unique_visitor_id | Incompatible with IP |
| Header value of (enter header name) | http.request.headers["<header_name>"] | Use lowercased header name in API and Missing field versus empty value |
| Cookie value of (enter cookie name) | http.request.cookies["<cookie_name>"] | Recommended configurations and Missing field versus empty value |
| Query value of (enter parameter name) | http.request.uri.args["<query_param_name>"] | Missing field versus empty value |
| Host | http.host | |
| Path | http.request.uri.path | |
| AS Num | ip.src.asnum | |
| Country | ip.src.country | |
| JA3 Fingerprint | cf.bot_management.ja3_hash | |
| JA4 | cf.bot_management.ja4 | |
| JSON string value of (enter key) | lookup_json_string(http.request.body.raw, "<key>") | Missing field versus empty value and lookup_json_string() function reference |
| JSON integer value of (enter key) | lookup_json_integer(http.request.body.raw, "<key>") | Missing field versus empty value and lookup_json_integer() function reference |
| Form input value of (enter field name) | http.request.body.form["<input_field_name>"] | Missing field versus empty value |
| JWT claim of (enter token configuration ID, claim name) | lookup_json_string( http.request.jwt.claims["<token_configuration_id>"][0], "<claim_name>") | Requirements for claims in JWT, missing field versus empty value and JWT Validation reference |
| Body | http.request.body.raw | |
| Body size (select operator, enter size) | http.request.body.size | |
| Custom (enter expression) | Enter a custom expression. You can use a function such as substring() or lower(), or enter a more complex expression. | Functions |
The available characteristics depend on your Cloudflare plan. Refer to Availability for more information.
- Data type: String
- Field name in the API:
counting_expression(optional)
Only available in the Cloudflare dashboard when you enable Use custom counting expression.
Defines the criteria used for determining the request rate. By default, the counting expression is the same as the rule matching expression (defined in If incoming requests match). This default is also applied when you set this field to an empty string ("").
The counting expression can include HTTP response fields. When there are response fields in the counting expression, the counting will happen after the response is sent.
In some cases, you cannot include HTTP response fields in the counting expression due to configuration restrictions. Refer to Configuration restrictions for details.
- Data type: Integer
- Field name in the API:
requests_per_period
The number of requests over the period of time that will trigger the rule.
- Data type: Integer
- Field name in the API:
period
The period of time to consider (in seconds) when evaluating the request rate. The available values vary according to your Cloudflare plan.
The available API values are: 10, 60 (one minute), 120 (two minutes), 300 (five minutes), 600 (10 minutes), or 3600 (one hour).
- Data type: String
- Field name in the API:
action(rule field)
Action to perform when the rate specified in the rule is reached.
Use one of the following values in the API: block, challenge, js_challenge, managed_challenge, or log.
If you select the Block action, you can define a custom response using the following parameters:
- Data type: String
- Field name in the API:
response>content_type(optional)
Defines the content type of a custom response when blocking a request due to rate limiting. Only available when you set the rule action to Block.
Available API values: application/json, text/html, text/xml, or text/plain.
- Data type: Integer
- Field name in the API:
response>status_code(optional)
Defines the HTTP status code returned to the visitor when blocking the request due to rate limiting. Only available when you set the rule action to Block.
You must enter a value between 400 and 499. The default value is 429 (Too many requests).
- Data type: String
- Field name in the API:
response>content(optional)
Defines the body of the returned HTTP response when the request is blocked due to rate limiting. Only available when you set the rule action to Block.
The maximum field size is 30 KB.
- Data type: Integer
- Field name in the API:
mitigation_timeout
Once the rate is reached, the rate limiting rule applies the rule action to further requests for the period of time defined in this field (in seconds).
In the dashboard, select one of the available values, which vary according to your Cloudflare plan. The available API values are: 0, 10, 60 (one minute), 120 (two minutes), 300 (five minutes), 600 (10 minutes), 3600 (one hour), or 86400 (one day).
Customers on Free, Pro, and Business plans cannot select a duration when using a challenge action — their rate limiting rule will always perform request throttling for these actions. With request throttling, you do not define a duration. When visitors pass a challenge, their corresponding request counter is set to zero. When visitors with the same values for the rule characteristics make enough requests to trigger the rate limiting rule again, they will receive a new challenge.
Enterprise customers can always configure a duration (or mitigation timeout), even when using one of the challenge actions.
- Data type: Integer
- Field name in the API:
mitigation_timeout
Defines the exact behavior of the selected action.
The action behavior can be one of the following:
-
Perform action during the selected duration: Applies the configured action to all requests received during the selected duration. To configure this behavior via API, set
mitigation_timeoutto a value greater than zero. Refer to For duration for more information.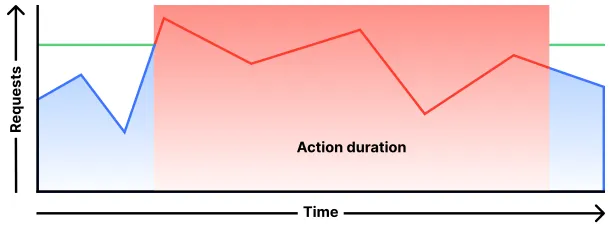
-
Throttle requests over the maximum configured rate: Applies the selected action to incoming requests over the configured limit, allowing other requests. To configure this behavior via API, set
mitigation_timeoutto0(zero).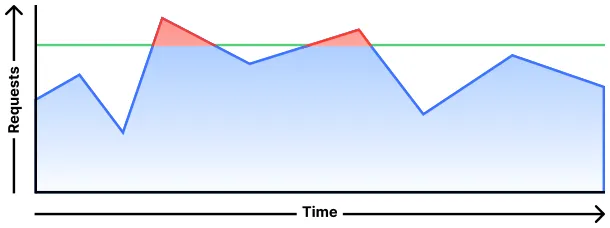
Use IP with NAT support to handle situations such as requests under NAT sharing the same IP address. Cloudflare uses a variety of privacy-preserving techniques to identify unique visitors, which may include use of session cookies. Refer to Cloudflare Cookies for details.
You cannot use both IP with NAT support and IP as characteristics of the same rate limiting rule.
You should not use the cf.colo.id characteristic (data center ID) as a field in rule expressions. Additionally, cf.colo.id values may change without warning. For more information about this rate limiting characteristic, refer to How Cloudflare determines the request rate.
If you use the Header value of characteristic in an API request (with http.request.headers["<header_name>"]), you must enter the header name in lower case, since Cloudflare normalizes header names on the Cloudflare global network.
If you use the Header value of, Cookie value of, Query value of, JSON string value of, lookup_json_integer(...), or Form input value of characteristic and the specific header/cookie/parameter/JSON key/form field name is not present in the request, the rate limiting rule may still apply to the request, depending on your counting expression.
If you do not filter out such requests, there will be a specific request counter for requests where the field is not present, which will be different from the request counter where the field is present with an empty value.
For example, to consider only requests where a specific HTTP header is present in the context of a specific rate limiting rule, adjust the rule counting expression so it contains something similar to the following:
and len(http.request.headers["<header_name>"]) > 0
Where <header_name> is the same header name used as a rate limiting characteristic.
If you use Cookie value of as a rate limiting rule characteristic, follow these recommendations:
- Create a custom rule that blocks requests with more than one value for the cookie.
- Validate the cookie value at the origin before performing any demanding server operations.
To use claims inside a JSON Web Token (JWT), you must first set up a token validation configuration in API Shield.
-
If the rule expression includes IP lists, you must enable the Also apply rate limiting to cached assets parameter.
-
The rule counting expression, defined in the Increment counter when parameter, cannot include both HTTP response fields and IP lists. If you use IP lists, you must enable the Also apply rate limiting to cached assets parameter.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark