Changelog
Access bulk policy tester
The Access bulk policy tester is now available in the Cloudflare Zero Trust dashboard. The bulk policy tester allows you to simulate Access policies against your entire user base before and after deploying any changes. The policy tester will simulate the configured policy against each user's last seen identity and device posture (if applicable).

HTTP redirect and custom block page redirect
You can now use more flexible redirect capabilities in Cloudflare One with Gateway.
- A new Redirect action is available in the HTTP policy builder, allowing admins to redirect users to any URL when their request matches a policy. You can choose to preserve the original URL and query string, and optionally include policy context via query parameters.
- For Block actions, admins can now configure a custom URL to display when access is denied. This block page redirect is set at the account level and can be overridden in DNS or HTTP policies. Policy context can also be passed along in the URL.
Learn more in our documentation for HTTP Redirect and Block page redirect.
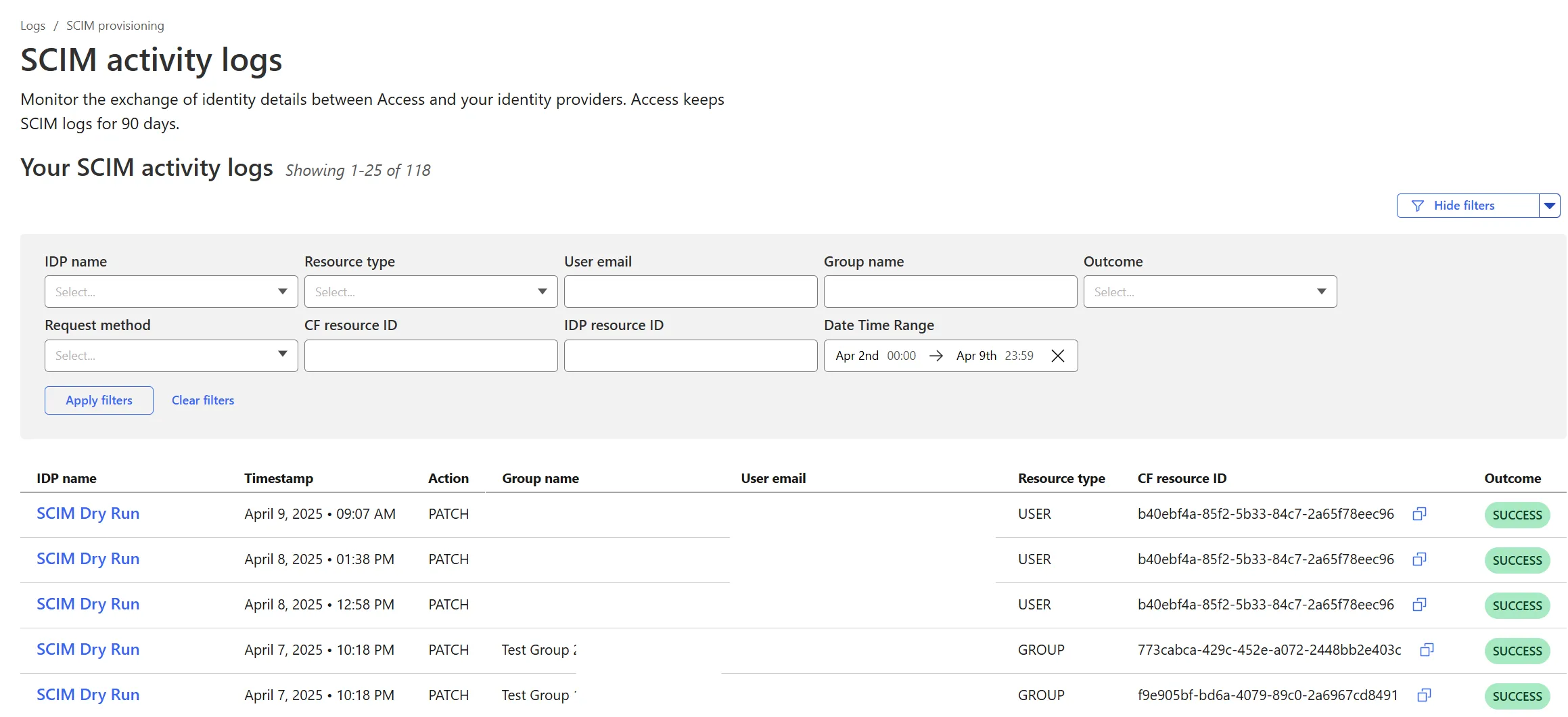
Cloudflare Zero Trust SCIM User and Group Provisioning Logs
Cloudflare Zero Trust SCIM provisioning now has a full audit log of all create, update and delete event from any SCIM Enabled IdP. The SCIM logs support filtering by IdP, Event type, Result and many more fields. This will help with debugging user and group update issues and questions.
SCIM logs can be found on the Zero Trust Dashboard under Logs -> SCIM provisioning.
WARP client for macOS (version 2025.2.664.0)
A new GA release for the macOS WARP client is now available on the Stable release downloads page. This release contains a hotfix for captive portal detection and PF state tables for the 2025.2.600.0 release.
Changes and improvements
- Fix to reduce the number of browser tabs opened during captive portal logins.
- Improvement to exclude local DNS traffic entries from PF state table to reduce risk of connectivity issues from exceeding table capacity.
Known issues
- macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.4 or later.
WARP client for Windows (version 2025.2.664.0)
A new GA release for the Windows WARP client is now available on the Stable release downloads page. This release contains a hotfix for captive portal detection for the 2025.2.600.0 release.
Changes and improvements
- Fix to reduce the number of browser tabs opened during captive portal logins.
Known issues
-
DNS resolution may be broken when the following conditions are all true:
- WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
- A custom DNS server address is configured on the primary network adapter.
- The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
WARP client for Linux (version 2025.2.600.0)
A new GA release for the Linux WARP client is now available on the Stable release downloads page. This release contains support for a new WARP setting, Global WARP override. It also includes significant improvements to our captive portal / public Wi-Fi detection logic.
Changes and improvements
- Improved captive portal detection to make more public networks compatible and have faster detection.
- WARP tunnel protocol details can now be viewed using the
warp-cli tunnel statscommand. - Fixed an issue with device revocation and re-registration when switching configurations.
- Added a new Global WARP override setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
WARP client for macOS (version 2025.2.600.0)
A new GA release for the macOS WARP client is now available on the Stable release downloads page. This release contains support for a new WARP setting, Global WARP override. It also includes significant improvements to our captive portal / public Wi-Fi detection logic.
Changes and improvements
- Improved captive portal detection to make more public networks compatible and have faster detection.
- Improved error messages shown in the app.
- WARP tunnel protocol details can now be viewed using the
warp-cli tunnel statscommand. - Fixed an issue with device revocation and re-registration when switching configurations.
- Added a new Global WARP override setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
Known issues
- macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
WARP client for Windows (version 2025.2.600.0)
A new GA release for the Windows WARP client is now available on the Stable release downloads page. This release contains support for a new WARP setting, Global WARP override. It also includes significant improvements to our captive portal / public Wi-Fi detection logic.
Changes and improvements
- Improved captive portal detection to make more public networks compatible and have faster detection.
- Improved error messages shown in the app.
- Added the ability to control if the WARP interface IPs are registered with DNS servers or not.
- Removed DNS logs view from the Windows client GUI. DNS logs can be viewed as part of
warp-diagor by viewing the log file on the user's local directory. - Fixed an issue that would result in a user receiving multiple re-authentication requests when waking their device from sleep.
- WARP tunnel protocol details can now be viewed using the
warp-cli tunnel statscommand. - Improvements to Windows multi-user including support for fast user switching. If you are interested in testing this feature, reach out to your Cloudflare account team.
- Fixed an issue with device revocation and re-registration when switching configurations.
- Fixed an issue where DEX tests would run during certain sleep states where the networking stack was not fully up. This would result in failures that would be ignored.
- Added a new Global WARP override setting. This setting puts account administrators in control of disabling and enabling WARP across all devices registered to an account from the dashboard. Global WARP override is disabled by default.
Known issues
-
DNS resolution may be broken when the following conditions are all true:
- WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
- A custom DNS server address is configured on the primary network adapter.
- The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
Secure DNS Locations Management User Role
We're excited to introduce the Cloudflare Zero Trust Secure DNS Locations Write role, designed to provide DNS filtering customers with granular control over third-party access when configuring their Protective DNS (PDNS) solutions.
Many DNS filtering customers rely on external service partners to manage their DNS location endpoints. This role allows you to grant access to external parties to administer DNS locations without overprovisioning their permissions.
Secure DNS Location Requirements:
-
Mandate usage of Bring your own DNS resolver IP addresses ↗ if available on the account.
-
Require source network filtering for IPv4/IPv6/DoT endpoints; token authentication or source network filtering for the DoH endpoint.
You can assign the new role via Cloudflare Dashboard (Manage Accounts > Members) or via API. For more information, refer to the Secure DNS Locations documentation ↗.
Cloudflare One Agent for Android (version 2.4)
A new GA release for the Android Cloudflare One Agent is now available in the Google Play Store ↗. This release includes a new feature allowing team name insertion by URL during enrollment, as well as fixes and minor improvements.
Changes and improvements
- Improved in-app error messages.
- Improved mobile client login with support for team name insertion by URL.
- Fixed an issue preventing admin split tunnel settings taking priority for traffic from certain applications.
Cloudflare One Agent for iOS (version 1.10)
A new GA release for the Android Cloudflare One Agent is now available in the iOS App Store ↗. This release includes a new feature allowing team name insertion by URL during enrollment, as well as fixes and minor improvements.
Changes and improvements
- Improved in-app error messages.
- Improved mobile client login with support for team name insertion by URL.
- Bug fixes and performance improvements.
WARP client for macOS (version 2025.2.460.1)
A new beta release for the macOS WARP client is now available on the Downloads page. This release contains significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
Changes and improvements
- Improved captive portal detection to make more public networks compatible and have faster detection.
- Improved error messages shown in the app.
- WARP tunnel protocol details can now be viewed using the
warp-cli tunnel statscommand. - Fixed issue with device revocation and re-registration when switching configurations.
Known issues
- macOS Sequoia: Due to changes Apple introduced in macOS 15.0.x, the WARP client may not behave as expected. Cloudflare recommends the use of macOS 15.3 or later.
WARP client for Windows (version 2025.2.460.1)
A new beta release for the Windows WARP client is now available on the Downloads page. This release contains significant improvements to our captive portal / public Wi-Fi detection logic. If you have experienced captive portal issues in the past, re-test and give this version a try.
Changes and improvements
- Improved captive portal detection to make more public networks compatible and have faster detection.
- Improved error messages shown in the app.
- Added the ability to control if the WARP interface IPs are registered with DNS servers or not.
- Removed DNS logs view from the Windows client GUI. DNS logs can be viewed as
part of
warp-diagor by viewing the log file on the user's local directory. - Fixed issue that would result in a user receiving multiple re-authentication requests when waking their device from sleep.
- WARP tunnel protocol details can now be viewed using the
warp-cli tunnel statscommand. - Improvements to Windows multi-user including support for fast user switching. If you are interested in testing this feature, reach out to your Cloudflare account team.
- Fixed issue with device revocation and re-registration when switching configurations.
- Fixed issue where DEX tests would run during certain sleep states where the networking stack was not fully up. This would result in failures that would be ignored.
Known issues
-
DNS resolution may be broken when the following conditions are all true:
- WARP is in Secure Web Gateway without DNS filtering (tunnel-only) mode.
- A custom DNS server address is configured on the primary network adapter.
- The custom DNS server address on the primary network adapter is changed while WARP is connected.
To work around this issue, reconnect the WARP client by toggling off and back on.
Cloudflare One Agent now supports Endpoint Monitoring
Digital Experience Monitoring (DEX) provides visibility into device, network, and application performance across your Cloudflare SASE deployment. The latest release of the Cloudflare One agent (v2025.1.861) now includes device endpoint monitoring capabilities to provide deeper visibility into end-user device performance which can be analyzed directly from the dashboard.
Device health metrics are now automatically collected, allowing administrators to:
- View the last network a user was connected to
- Monitor CPU and RAM utilization on devices
- Identify resource-intensive processes running on endpoints
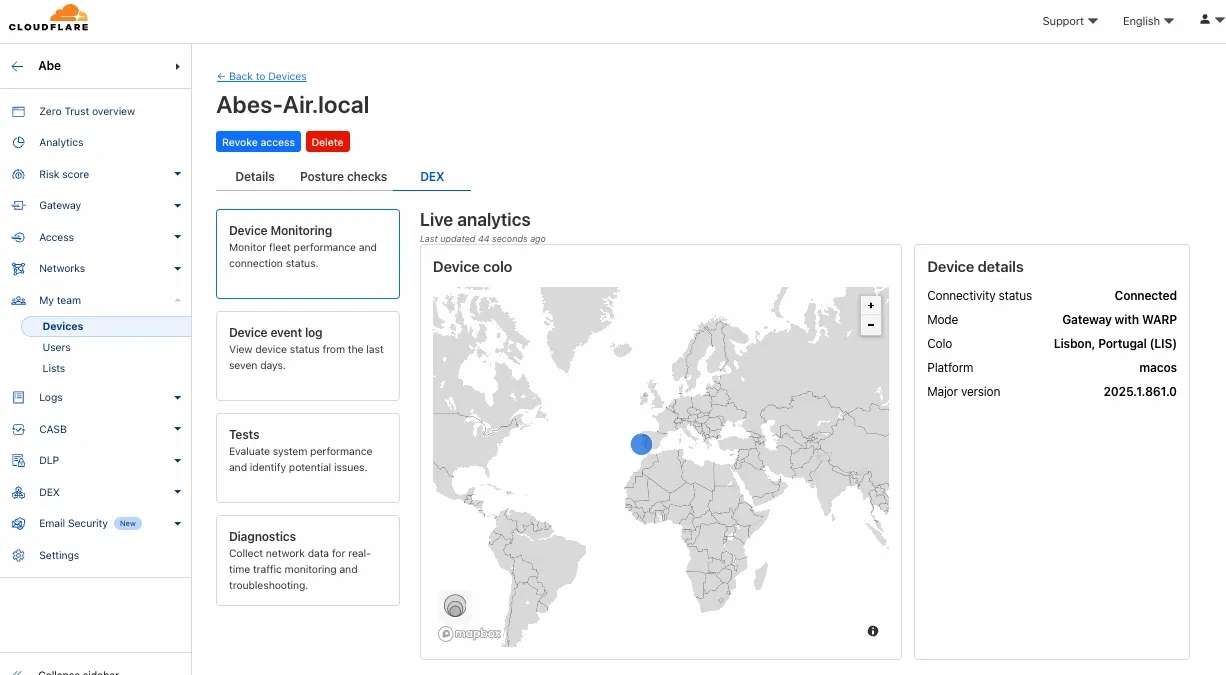
This feature complements existing DEX features like synthetic application monitoring and network path visualization, creating a comprehensive troubleshooting workflow that connects application performance with device state.
For more details refer to our DEX documentation.
Gain visibility into user actions in Zero Trust Browser Isolation sessions
We're excited to announce that new logging capabilities for Remote Browser Isolation (RBI) through Logpush are available in Beta starting today!
With these enhanced logs, administrators can gain visibility into end user behavior in the remote browser and track blocked data extraction attempts, along with the websites that triggered them, in an isolated session.
{ "AccountID": "$ACCOUNT_ID", "Decision": "block", "DomainName": "www.example.com", "Timestamp": "2025-02-27T23:15:06Z", "Type": "copy", "UserID": "$USER_ID"}User Actions available:
- Copy & Paste
- Downloads & Uploads
- Printing
Learn more about how to get started with Logpush in our documentation.
New SAML and OIDC Fields and SAML transforms for Access for SaaS
Access for SaaS applications now include more configuration options to support a wider array of SaaS applications.
SAML and OIDC Field Additions
OIDC apps now include:
- Group Filtering via RegEx
- OIDC Claim mapping from an IdP
- OIDC token lifetime control
- Advanced OIDC auth flows including hybrid and implicit flows

SAML apps now include improved SAML attribute mapping from an IdP.
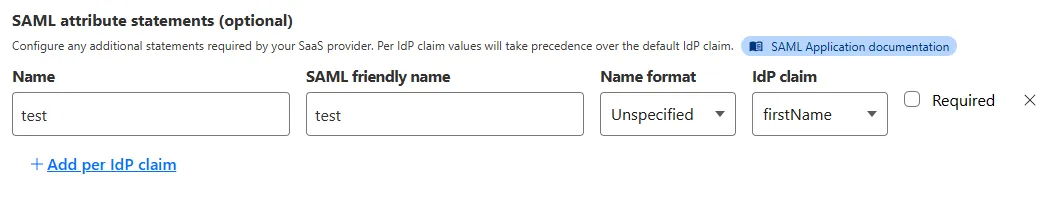
SAML transformations
SAML identities sent to Access applications can be fully customized using JSONata expressions. This allows admins to configure the precise identity SAML statement sent to a SaaS application.

Configure your Magic WAN Connector to connect via static IP assigment
You can now locally configure your Magic WAN Connector to work in a static IP configuration.
This local method does not require having access to a DHCP Internet connection. However, it does require being comfortable with using tools to access the serial port on Magic WAN Connector as well as using a serial terminal client to access the Connector's environment.
For more details, refer to WAN with a static IP address.
Block files that are password-protected, compressed, or otherwise unscannable.
Gateway HTTP policies can now block files that are password-protected, compressed, or otherwise unscannable.
These unscannable files are now matched with the Download and Upload File Types traffic selectors for HTTP policies:
- Password-protected Microsoft Office document
- Password-protected PDF
- Password-protected ZIP archive
- Unscannable ZIP archive
To get started inspecting and modifying behavior based on these and other rules, refer to HTTP filtering.
Detect source code leaks with Data Loss Prevention
You can now detect source code leaks with Data Loss Prevention (DLP) with predefined checks against common programming languages.
The following programming languages are validated with natural language processing (NLP).
- C
- C++
- C#
- Go
- Haskell
- Java
- JavaScript
- Lua
- Python
- R
- Rust
- Swift
DLP also supports confidence level for source code profiles.
For more details, refer to DLP profiles.
Troubleshoot tunnels with diagnostic logs
The latest cloudflared build 2024.12.2 ↗ introduces the ability to collect all the diagnostic logs needed to troubleshoot a cloudflared instance.
A diagnostic report collects data from a single instance of cloudflared running on the local machine and outputs it to a cloudflared-diag file.
The cloudflared-diag-YYYY-MM-DDThh-mm-ss.zip archive contains the files listed below. The data in a file either applies to the cloudflared instance being diagnosed (diagnosee) or the instance that triggered the diagnosis (diagnoser). For example, if your tunnel is running in a Docker container, the diagnosee is the Docker instance and the diagnoser is the host instance.
| File name | Description | Instance |
|---|---|---|
cli-configuration.json | Tunnel run parameters used when starting the tunnel | diagnosee |
cloudflared_logs.txt | Tunnel log file1 | diagnosee |
configuration.json | Tunnel configuration parameters | diagnosee |
goroutine.pprof | goroutine profile made available by pprof | diagnosee |
heap.pprof | heap profile made available by pprof | diagnosee |
metrics.txt | Snapshot of Tunnel metrics at the time of diagnosis | diagnosee |
network.txt | JSON traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
raw-network.txt | Raw traceroutes to Cloudflare's global network using IPv4 and IPv6 | diagnoser |
systeminformation.json | Operating system information and resource usage | diagnosee |
task-result.json | Result of each diagnostic task | diagnoser |
tunnelstate.json | Tunnel connections at the time of diagnosis | diagnosee |
For more information, refer to Diagnostic logs.
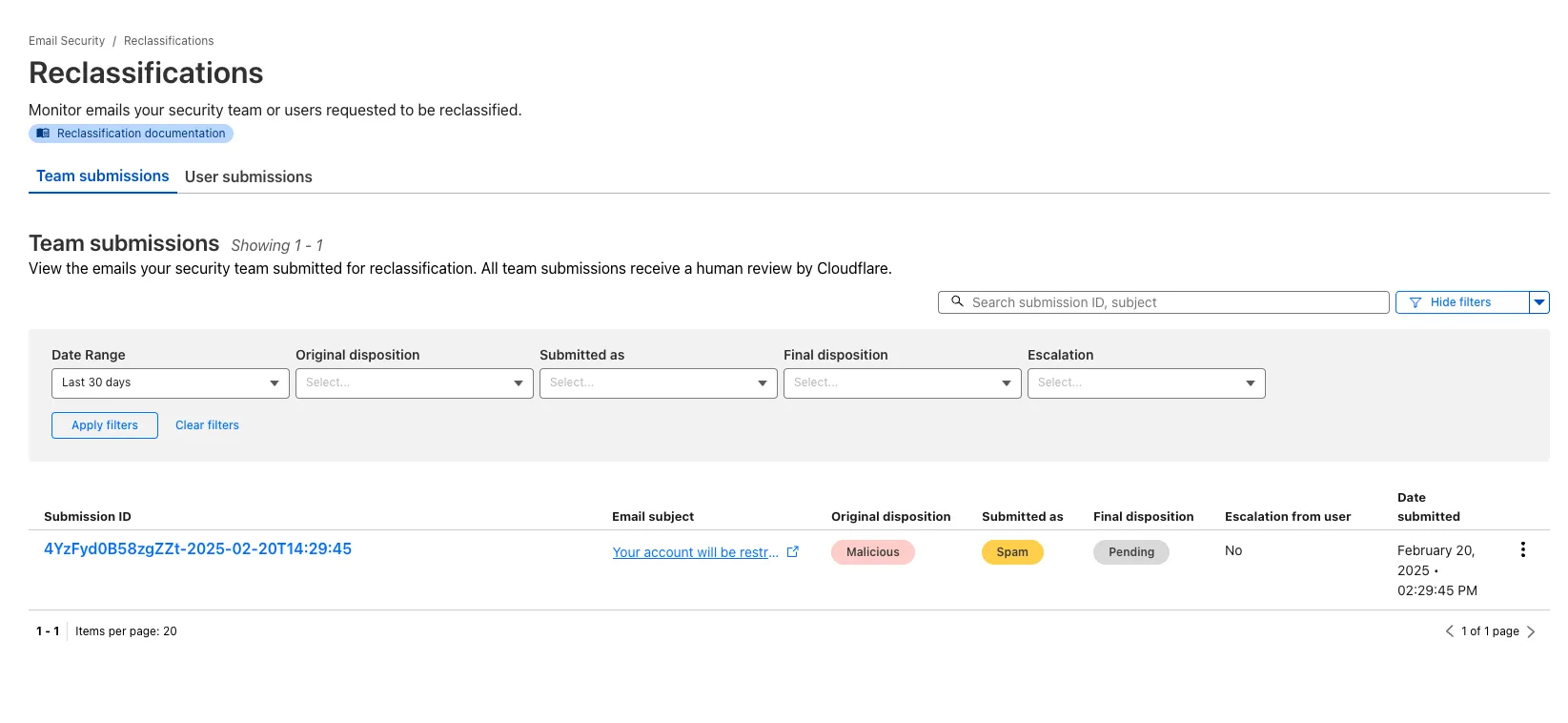
Increased transparency for phishing email submissions
You now have more transparency about team and user submissions for phishing emails through a Reclassification tab in the Zero Trust dashboard.
Reclassifications happen when users or admins submit a phish to Email Security. Cloudflare reviews and - in some cases - reclassifies these emails based on improvements to our machine learning models.
This new tab increases your visibility into this process, allowing you to view what submissions you have made and what the outcomes of those submissions are.
Establish BGP peering over Direct CNI circuits
Magic WAN and Magic Transit customers can use the Cloudflare dashboard to configure and manage BGP peering between their networks and their Magic routing table when using a Direct CNI on-ramp.
Using BGP peering with a CNI allows customers to:
- Automate the process of adding or removing networks and subnets.
- Take advantage of failure detection and session recovery features.
With this functionality, customers can:
- Establish an eBGP session between their devices and the Magic WAN / Magic Transit service when connected via CNI.
- Secure the session by MD5 authentication to prevent misconfigurations.
- Exchange routes dynamically between their devices and their Magic routing table.
Refer to Magic WAN BGP peering or Magic Transit BGP peering to learn more about this feature and how to set it up.
Generate customized terraform files for building cloud network on-ramps
You can now generate customized terraform files for building cloud network on-ramps to Magic WAN.
Magic Cloud can scan and discover existing network resources and generate the required terraform files to automate cloud resource deployment using their existing infrastructure-as-code workflows for cloud automation.
You might want to do this to:
- Review the proposed configuration for an on-ramp before deploying it with Cloudflare.
- Deploy the on-ramp using your own infrastructure-as-code pipeline instead of deploying it with Cloudflare.
For more details, refer to Set up with Terraform.
Find security misconfigurations in your AWS cloud environment
You can now use CASB to find security misconfigurations in your AWS cloud environment using Data Loss Prevention.
You can also connect your AWS compute account to extract and scan your S3 buckets for sensitive data while avoiding egress fees. CASB will scan any objects that exist in the bucket at the time of configuration.
To connect a compute account to your AWS integration:
- In Zero Trust ↗, go to CASB > Integrations.
- Find and select your AWS integration.
- Select Open connection instructions.
- Follow the instructions provided to connect a new compute account.
- Select Refresh.
Search for custom rules using rule name and/or ID
The Magic Firewall dashboard now allows you to search custom rules using the rule name and/or ID.
- Log into the Cloudflare dashboard ↗ and select your account.
- Go to Analytics & Logs > Network Analytics.
- Select Magic Firewall.
- Add a filter for Rule ID.

Additionally, the rule ID URL link has been added to Network Analytics.
For more details about rules, refer to Add rules.
Exchange user risk scores with Okta
Beyond the controls in Zero Trust, you can now exchange user risk scores with Okta to inform SSO-level policies.
First, configure Zero Trust to send user risk scores to Okta.
- Set up the Okta SSO integration.
- In Zero Trust ↗, go to Settings > Authentication.
- In Login methods, locate your Okta integration and select Edit.
- Turn on Send risk score to Okta.
- Select Save.
- Upon saving, Zero Trust will display the well-known URL for your organization. Copy the value.
Next, configure Okta to receive your risk scores.
- On your Okta admin dashboard, go to Security > Device Integrations.
- Go to Receive shared signals, then select Create stream.
- Name your integration. In Set up integration with, choose Well-known URL.
- In Well-known URL, enter the well-known URL value provided by Zero Trust.
- Select Create.
Explore product updates for Cloudflare One
Welcome to your new home for product updates on Cloudflare One.
Our new changelog lets you read about changes in much more depth, offering in-depth examples, images, code samples, and even gifs.
If you are looking for older product updates, refer to the following locations.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark