Configurations
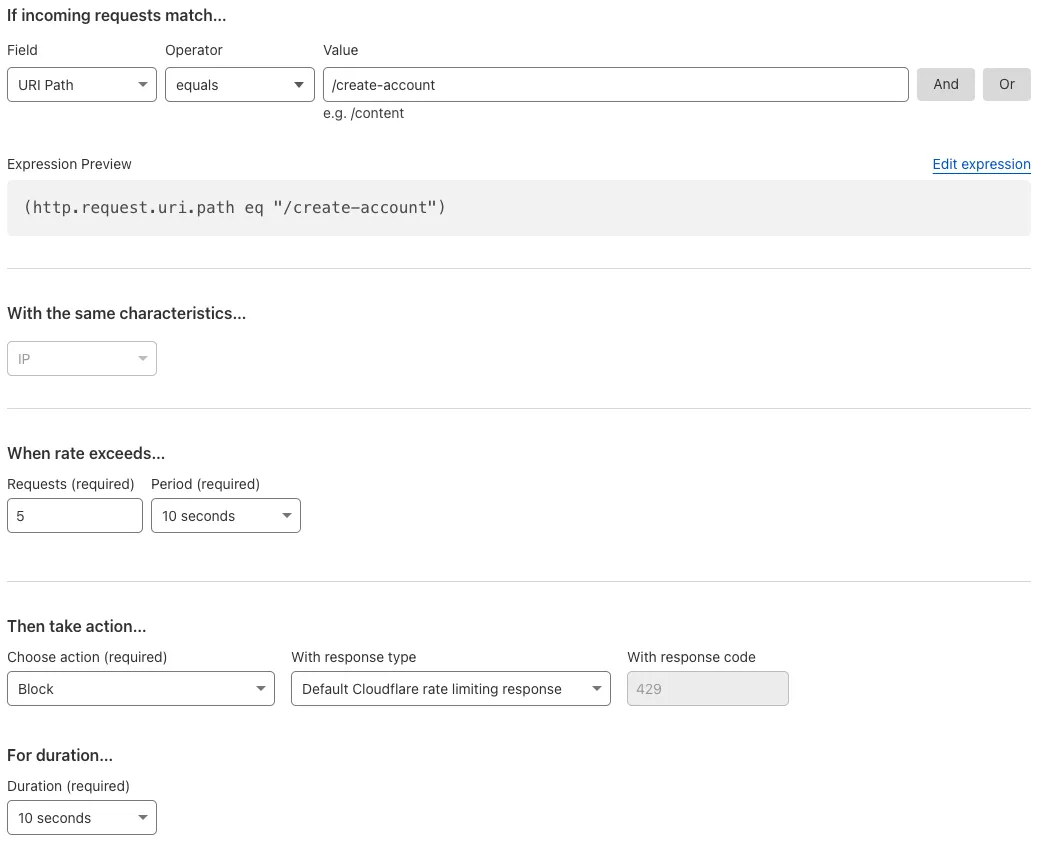
Let's step through an example. If your /create-account page is being attacked, you will create a rule to limit the amount of requests, per counting characteristic, that you feel comfortable permitting through to your origin.
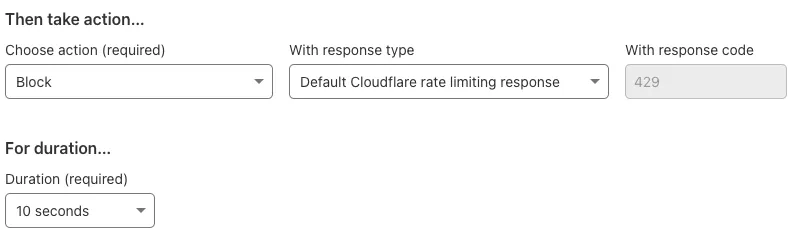
The rule below is being created on the free plan, which limits configuration options. The rule will trigger if the URI path matches /create-account, from the same IP address, after 5 requests and within a 10 second window, within each Cloudflare datacenter, globally.
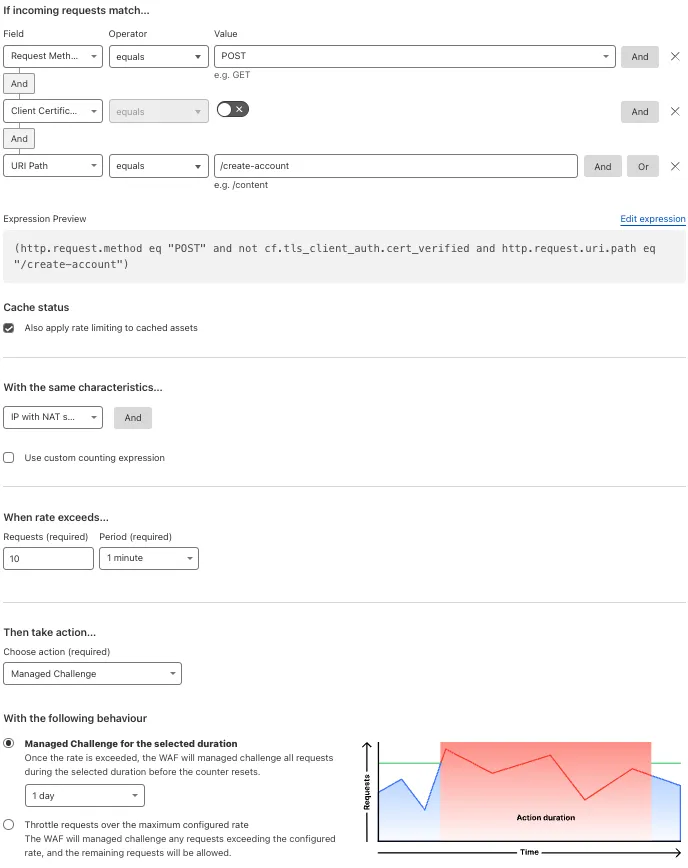
In the previous module, we reviewed the various configurations available per plan. Using the same endpoint as an example, let us walk through another example, but with the additional advanced configurations.
The rule below is being created on the enterprise plan, so we are no longer limited to default configurations.
- The rule will also limit the number of requests to
/create-account, but will only trigger againstPOSTrequests. In the basic example, even requests with theGETmethod will increment the counter. - Requests that do not have a client certificate (mTLS), will increment the counter.
- Requests will be counted using the IP with NAT support characteristic.
- Within a 1 minute period, for each counted entity, if the number of requests exceeds 10, then the user will be presented with a
Managed Challengefor a custom duration of 1 day.
Rules that match identical criteria can be stacked together. For example, instead of creating just a single rule for /create-account, you can create multiple rules that match the same path but have different counting characteristics or request limits to protect against a threat that might behave dynamically.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark